#microsoft programs including
Text
whoever programmed microsoft excel so that it recognizes dates up to the year 9999 but not before 1900... turn on your location i just want to talk
#personal#i know just enough about programming to be deeply confused as to why they would do this#like it cant be a 'numbers too big' issue right??? because otherwise why 1900 and 9999#theyre storing the dates as integers why not just start them sooner#yeah nobody cares about the 19th century. lets include 7000 years in the future instead!#microsoft excel#until i hear a good reason im taking this as evidence that we need more humanities people in stem#seriously though if anyone knows please tell me
8 notes
·
View notes
Text
I have a perfectly fine email app on my laptop and Microsoft is still trying to change it to outlook smh fuck off I hate outlook
"you can switch back now, but you will be returned to the new outlook in the future" is that a threat lol
#fuck Microsoft#I'll never switch to anything but windows but still fuck Microsoft and all their office programs including outlook
5 notes
·
View notes
Text
Polygonal MS pain program or whatever, sorry for not posting for a while, my fellow peepers.

She's my OC Cathy, she has a kittygram and works as a cashier in McDod. Cathy is very exhausted and desensitized to the chaos of the home computer which is currently hanging by a thread after a malware invasion. Working in McDod nearly kills her at least twice on a weekly basis, so it's no surprise that she wants to find a new job, but she can't find a suitable one for her.
I didn't draw her glasses bc it's to hard to do in MS paint. I also have more Databrawl OCs, and this is what she currently looks like because she got hospitalized again:
#databrawl#art#my oc art#oc art#my ocs#ms paint#microsoft paint#this isn't the first time i've used this program#unrelated databrawl fact: a virus oc of mine literally hospitalized all of the processor followers in the fricking palace#by dumping the entire salt shaker in the soup in the palace#including the shaker itself#yes that actually happened in a roleplay and i will jokingly declare it as canon to my databrawl au#i act impulsively sometimes#fan au#fanart#fan art
11 notes
·
View notes
Text
Trying to sign up to this freelance website as a ghostwriter/essay writer/etc & realising that truly the only thing I don’t like writing is bios
#especially of myself. like if you give me your info i could probably make a good bio out of it#but talking about MYSELF?? i’ll vomit#maybe i should just try to have an out of body experience & talk about myself in the third person#or i could just make a list of the stuff i want to include and write it as a paragraph (to show i can write)#and then bulletpoint the skills they need to be able to scan through quickly#so like. 10 years experience writing high quality essays. pretty much lifelong passion for creative writing. high level of education#(master’s degree i have not used even once); plus i’m a qualified english & efl teacher so i know the english language like the back#of my hand; i.e. i can and will proofread for you & can almost guarantee that any final draft i send will be mistake free#types 92wpm. indecisive about writing programs so is proficient with microsoft office; ios office; google docs etc; scrivener; libreoffice..#please send in research/resources for essay writing otherwise i will just use the first 5 articles i see on jstor no matter how well or how#badly they suit the hypothesis#also please don’t make me do referencing in any style other than chicago#like.. i’ll do it but i’ll be crying the whole time#married to the oxford comma & the semicolon. will not write wiki articles due to a bad experience#but will write pretty much anything else#oh also not bios apparently#literally hire me. like. i’m great#personal
3 notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image:
Mike (modified)
https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0
https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
577 notes
·
View notes
Text
Things Biden and the Democrats did, this week #17
May 3-10 2024
Vice President Harris announced 5.5 billion dollars to build affordable housing and address homelessness. The grants will go to 1,200 communities across all 50 states, DC and Puerto Rico. 1.3 billion will go to HUD's HOME program which builds, buys, and rehabs affordable housing for rent or ownership. 3.3 billion is headed to Community Development Block Grants which supports housing as well as homeless services, and expanding economic opportunities. Remaining funds focus on building housing for extremely low- and very low-income households, Housing for people struggling with HIV/AIDS, transitional housing for those with substance-use disorder, and money to support homeless shelters and homeless prevention programs.
At the 3rd meeting of the Los Angeles Declaration group in Guatemala Security of State Blinken announced $578 million in new US aid to Latin America. The Los Angeles Declaration is a partnership between the US and 20 other nations in the Americas to address immigration, combat human trafficking, and support economic development and improved quality of life for people in poor nations in the Americas. The bulk of the aid, over $400 million will go to humanitarian assistance to the Venezuelan people. Inside of Venezuela over 7 million people are in need of humanitarian assistance due to decades of political and economic instability. Over 7 million more have been forced to flee the country and live in poverty across the Americas. The aid will help Venezuelans both inside and outside of Venezuela.
The Department of Energy lead an effort to get the G7 to agree to phase out coal by the early 2030s. The G7 is a collection of the 7 largest Industrial economies on Earth, the US, the UK, Canada, France, Germany, Japan, and Italy. To avoid catastrophic climate change the International Energy Agency believes coal needs to be phased out by 2035. However this has been a sticking point with the G7 since 1/3rd of Japan and 1/4th of Germany's energy comes from Coal. This agreement to phase out represents a major breakthrough and the US plans to press for even wider agreement on the issue at the G20 meeting in November.
President Biden announced a major investment deal in Racine, Wisconsin, site of the failed Trump Foxconn deal. In 2018 then President Trump visited Racine and declared the planned Foxconn plant "the eighth wonder of the world.". However the promised 13,000 jobs never materialized and the Taiwan based Foxconn after bulldozing 100s of homes and farms decided not to build. President Biden inked a deal with Microsoft for the land formally given to Foxconn which will bring 2,000 new jobs to Racine to help replace the 1,000 job losses during Trump's Presidency in the community.
200 tribal governments and the US territories of American Samoa, the Northern Mariana Islands, Guam, and the U.S. Virgin Islands, published climate action plans. The plans were paid for by the Biden Administration as part of a 5 billion dollar Climate Pollution Reduction Grants program. The federal government is supporting all 50 states, territories, DC, and tribal governments to draft climate action plans, which will be used to apply for more than 4 billion dollars in grants to help turn plans into reality
As part of marking Yom HaShoah (Holocaust Remembrance Day), the Biden Administration announced a number of action aimed at combating antisemitism and supporting the Jewish Community. This included $400 million in new funding for the Nonprofit Security Grant Program. The Program has supported Synagogues and Jewish Community Centers with security improvements like bullet proof windows and trainings for staff in how to handle active shooter and hostage situations. The Department of Education issued guidance to all schools districts and federally funded colleges stressing that antisemitism is banned under Title VI of the Civil Rights Act of 1964. These actions come as part of the Biden Administration's National Strategy To Counter Antisemitism, the first ever national strategy addressing the issue by any Administration.
USAID announced $220 million in additional humanitarian aid to Yemen. This new funding will bring US aid to Yemen over the last 10 years to nearly $6 billion. Currently 18 million Yemenis are estimated as needing humanitarian assistance, 9 million of them children, and the UN believes nearly 14 million face imminent risk of famine. The US remains the single largest donor nation to humanitarian relief in Yemen.
The Department of Interior announced nearly $150 million to help communities fight drought. The funds will support 42 projects across 10 western states. This is part of the President's $8.3 billion dollar investment in the nations water infrastructure over the next 5 five years.
#Thanks Biden#Joe Biden#climate change#climate action#coal power#affordable homes#immigration#venezuela#Yemen#antisemitism#politics#us politics#Democrats#2024 elections#economy
199 notes
·
View notes
Text
back to basics


mostly free resources to help you learn the basics that i've gathered for myself so far that i think are cool
everyday
gcfglobal - about the internet, online safety and for kids, life skills like applying for jobs, career planning, resume writing, online learning, today's skills like 3d printing, photoshop, smartphone basics, microsoft office apps, and mac friendly. they have core skills like reading, math, science, language learning - some topics are sparse so hopefully they keep adding things on. great site to start off on learning.
handsonbanking - learn about finances. after highschool, credit, banking, investing, money management, debt, goal setting, loans, cars, small businesses, military, insurance, retirement, etc.
bbc - learning for all ages. primary to adult. arts, history, science, math, reading, english, french, all the way to functional and vocational skills for adults as well, great site!
education.ket - workplace essential skills
general education
mathsgenie - GCSE revision, grade 1-9, math stages 1-14, provides more resources! completely free.
khan academy - pre-k to college, life skills, test prep (sats, mcat, etc), get ready courses, AP, partner courses like NASA, etc. so much more!
aleks - k-12 + higher ed learning program. adapts to each student.
biology4kids - learn biology
cosmos4kids - learn astronomy basics
chem4kids - learn chemistry
physics4kids - learn physics
numbernut - math basics (arithmetic, fractions and decimals, roots and exponents, prealgebra)
education.ket - primary to adult. includes highschool equivalent test prep, the core skills. they have a free resource library and they sell workbooks. they have one on work-life essentials (high demand career sectors + soft skills)
youtube channels
the organic chemistry tutor
khanacademy
crashcourse
tabletclassmath
2minmaths
kevinmathscience
professor leonard
greenemath
mathantics
3blue1brown
literacy
readworks - reading comprehension, build background knowledge, grow your vocabulary, strengthen strategic reading
chompchomp - grammar knowledge
tutors
not the "free resource" part of this post but sometimes we forget we can be tutored especially as an adult. just because we don't have formal education does not mean we can't get 1:1 teaching! please do you research and don't be afraid to try out different tutors. and remember you're not dumb just because someone's teaching style doesn't match up with your learning style.
cambridge coaching - medical school, mba and business, law school, graduate, college academics, high school and college process, middle school and high school admissions
preply - language tutoring. affordable!
revolutionprep - math, science, english, history, computer science (ap, html/css, java, python c++), foreign languages (german, korean, french, italian, spanish, japanese, chinese, esl)
varsity tutors - k-5 subjects, ap, test prep, languages, math, science & engineering, coding, homeschool, college essays, essay editing, etc
chegg - biology, business, engineering/computer science, math, homework help, textbook support, rent and buying books
learn to be - k-12 subjects
for languages
lingq - app. created by steve kaufmann, a polygot (fluent in 20+ languages) an amazing language learning platform that compiles content in 20+ languages like podcasts, graded readers, story times, vlogs, radio, books, the feature to put in your own books! immersion, comprehensible input.
flexiclasses - option to study abroad, resources to learn, mandarin, cantonese, japanese, vietnamese, korean, italian, russian, taiwanese hokkien, shanghainese.
fluentin3months - bootcamp, consultation available, languages: spanish, french, korean, german, chinese, japanese, russian, italian.
fluenz - spanish immersion both online and in person - intensive.
pimsleur - not tutoring** online learning using apps and their method. up to 50 languages, free trial available.
incase time has passed since i last posted this, check on the original post (not the reblogs) to see if i updated link or added new resources. i think i want to add laguage resources at some point too but until then, happy learning!!
#study#education resources#resources#learning#language learning#math#english languages#languages#japanese#mandarin#arabic#italian#computer science#wed design#coding#codeblr#fluency#online learning#learn#digital learning#education#studyinspo#study resources#educate yourselves#self improvement#mathematics#mathblr#resource
343 notes
·
View notes
Text
youtube
Shin Megami Tensei V: Vengeance - Announce Trailer
youtube
Japanese version
youtube
Extended Cut
youtube
Extended Cut Japanese version
youtube
Special Program Spotlight
Shin Megami Tensei V: Vengeance will launch for PlayStation 5, Xbox Series X|S, PlayStation 4, Xbox One, Nintendo Switch, and PC (Steam, Microsoft Store) on June 21, 2024 worldwide. Pre-orders will open on February 27, 2024.
Shin Megami Tensei V: Vengeance is an enhanced version of Shin Megami Tensei V, which originally launched for Nintendo Switch in November 2021.

Title logo

Key visual
Overview
The latest title in the series, Shin Megami Tensei V: Vengeance allows players to enjoy the story of Shin Megami Tensei V in its entirety, with a new story path, untold in the original. Massively expanded with new areas, demons, and music, Shin Megami Tensei V: Vengeance features more accessible gameplay, an improved battle system, new demon experiences, and greater field exploration.
Pre-orders for the Nintendo Switch family of systems (physical only), PlayStation 5, PlayStation 4, Steam, Xbox Series X|S, Xbox One and PC will begin on February 27, 2024. Details on digital pre-orders for Nintendo Switch will be announced at a later date.
When a grisly murder scene in modern-day Tokyo blocks the protagonist’s walk home, an unplanned detour leaves him buried and unconscious. He finds himself in a wasteland ravaged by apocalypse now called Da’at. Before bloodthirsty demons can claim his life, a savior emerges, and they unite to become a mighty being, neither human nor demon: a Nahobino.
Shin Megami Tensei V: Vengeance delivers a full-fledged RPG that can be enjoyed by existing and new fans. At the start of the game, players will choose between two paths: the story told in Shin Megami Tensei V, the Canon of Creation, or the brand-new Canon of Vengeance. This dramatic new tale of revenge introduces brand-new characters, an enigmatic cohort of demons called the Qadištu, a new dungeon and map to explore. Additionally, the original Shin Megami Tensei V battle system, demon merging and field exploration have been evolved and expanded in this newest entry in the series.
Further details
■ What is Shin Megami Tensei V: Vengeance?
Released in 2021, ATLUS’s renowned RPG Shin Megami Tensei V has sold more than one million copies worldwide.
This highly acclaimed game has evolved in every aspect, including the system and scenario, and will be available on multiple modern platforms!
At the beginning of the story, the player is presented between two routes. The story told in Shin Megami Tensei V, the Canon of Creation, and a brand-new route, Canon of Vengeance, a dramatic tale of revenge by the fallen.
The Canon of Vengeance follows the scenario of SMTV, but changes drastically from the latter half of the game. The outcome will be completely different. Enjoy the two divergent stories to your heart’s content.
The battle system, demon fusion, and field exploration have also evolved in depth with the addition of new elements. We are excited to deliver a full-fledged RPG that can be enjoyed by those who have already played SMTV, as well as those who are playing this series for the first time.
■ Story
Thou shalt be God—.
When a grisly murder scence in modern-day Tokyo blocks our protagonist’s walk home, an unplanned detour leaves him buried and unconscious. He awakens in a New Tokyo, a wasteland ravaged by apocalypse now called Da’at – but before bloodthirsty demons can claim his live, a savior emerges, and the two of them unite to become a mighty being, neither human nor demon: a Nahobino.

Revenge Awaits—.
Demons attack humans and seek to create a world of chaos.
Bethel, an organization that seeks to protect God’s order.
Caught up in the conflict between the two, while exploring Da’at, the protagonist meets and starts traveling with Yoko Hiromine.
Using magic, Yoko and the main character stand together on the front line.
The Qadistu, four female Demons stand in their way. “Found it, the Key of Resurrection…” A member of the Qadistu, Lilith calls protagonist the Key of Resurrection, and herself The Oppressed.
What is their purpose? A tale of revenge by the oppressed begins.

■ The Oppressed: The Qadistu
In the Canon of Vengeance, four female demons appear in front of the protagonist. Another story of creation told by new Demons.

■ Characters
Lilith (voiced by Katelyn Gault in English, Atsuko Tanaka in Japanese)
“I am Lilith of the Qadištu The one to restore the world to what it ought to be.”

A woman who is said to have been Adam’s first wife in the Old Testament. Later left Garden of Eden and turned into a demon.
Leader of the Qadištu. In order to achieve an unidentified goal, she stands in front of the protagonist.
Protagonist / Nahobino


A high school senior living in Tokyo. On his way back from school, he is involved in a tunnel collapse and wanders into an apocalyptic version of Tokyo, Da’at. His hobby is reading.
The protagonist fuses with Aogami and becomes a “Nahobino,” using this power to fight back demons.
The decision-making during the Nahobino state lies with the protagonist, and Aogami guides him with his voice.

Aogami (voiced by Damian Mills in English, Toshiyuki Morikawa in Japanese)
“Regardless of what may happen, rest assured that I will always protect you.”

A mysterious man who appears before the protagonist, who is being attacked by a demon in Da’at.
By taking the protagonist’s hand, he transforms into a condemned being, the Nahobino.
He seemingly participated in the war 18 years ago, but his memory of it has slipped away.

Yoko Hiromine (voiced by Erin Yvette in English, Chiwa Saitou in Japanese)
“With no one to save them, in the back of their mind, the victim desires only one thing: revenge against the assailant.”

She is a senior in high school at St. Marina Academy. Cool and somewhat mysterious.
She meets and works with the protagonist in Da’at. She has always possessed mysterious powers and was once called a “saint”. At the academy, she has been recognized for her power and learned exorcism magic. She also participates in the battles.



■ Over 270 Demons

In addition to existing demons, this title features more than 270 demons, including new demons newly drawn by the character designer Masayuki Doi. Enjoy an incredible demon experience!
■ Includes Shin Megami Tensei V Downloadable Content Demons and Quests!
The demons and quests that were available with Shin Megami Tensei V are included in this title as standard features! Experienced players are encouraged to try their hand at these challenging quests.
“A Goddess in Training”
“The Rage of a Queen”

“The Doctor’s Last Wish”

“Return of the True Demon”

■ Evolution in Depth!
Every system of Shin Megami Tensei V has been brushed up in detail and new elements have been added, including field exploration, demon conversations, battles, growth elements, and new demon experiences! Of course, with multiple endings—this is truly the definitive version of Shin Megami Tensei V.
Adding unique skills to all demons, new interactions with demons, and more… Many other new elements! Stay tuned for more information!






■ Additional Downloadable Content
Downloadable content featuring new demons will be distributed simultaneously on the release date.
Demon God Dagda from Shin Megami Tensei IV: Final and newly introduced is the demon Goddess Konohanasakuya, newly drawn by character designer Masayuki Doi!
Holy Will and Profane Dissent
When the protagonist goes to investigate a mysterious reaction, he meets Danu, the earth mother goddess, who claims to have come from a world that exists in another universe. Danu is apparently searching for his son, Dagda. The protagonist embarks on a search for Dagda with Danu. By completing the game, Dagda can be made an ally, and fusion will be unlocked.

Sakura Cinders of the East
Konohana Sakuya laments the turbulent world and searches for a hero who can pacify the world. She sees an image of a certain hero within the protagonist and challenges him. Winning the battle will allow you to make Konohana Sakuya your ally, and fusion will also be unlocked.
In addition, earning downloadable content that makes it easier to gain experience and in-game currency will be released at the same time.

#Shin Megami Tensei V Vengeance#SMTVV#Shin Megami Tensei 5 Vengeance#SMT5V#Shin Megami Tensei V#SMTV#Shin Megami Tensei 5#SMT5#Shin Megami Tensei#SMT#Megaten#Atlus#video game#Nintendo Switch#PlayStation 5#PlayStation 4#Xbox Series#Xbox Series X#Xbox One#PC#Steam#Microsoft Store
101 notes
·
View notes
Text
I'm going to a zine making workshop at the library and I am planning on making a zine about being nonbinary from a Buddhist perspective. Because in Buddhism there's this concept of "emptiness" that is basically summed up as "everything is made up of other smaller things and does not have a separate self without those things." And this can be applied to gender just like everything else, in the same sense that a lot of trans people will say gender is a "social construct."
First I am going to explain the difference between sex and gender using the analogy that people are like computers. They have hardware and software. Hardware on a computer is the physical pieces of the computer. The hard drive, the motherboard, the power supply or battery, etc. That's biological sex. Things like your primary and secondary sex characteristics, hormones, body parts, etc. The physical pieces of the person. That's sex. Just like swapping out RAM in a computer, you can change some of these things via medical intervention. Gender is the software, the programs you run on the hardware. In a computer it's things like google chrome, Microsoft word, safari, PowerPoint, etc. The way the computer thinks. That's gender.
I explain the emptiness of gender like "When I realized cis women felt like women I knew I was different. Because I never felt that. But when I started digging down to find what my 'one true gender deep down' was, I kept digging through layers and removing layer after layer. And some of these layers were big, like what society expects of people with my body type. And some were small, like the types of haircuts my mom likes to compliment. So I removed layers and removed layers until I got to the center of who I am and there was nothing there! It was empty! Gender is empty/a social construct made of layers of outside things."
This doesn't mean binary trans people are invalid because the way you relate to the layers does matter. But a lot of trans people, binary trans people included, have come to this "social construct/empty" conclusion.
I'm going to make the zine and give it to the monk who runs my temple because I want to come out there but I don't know how he'll take it because he's a bit conservative but not in the Christian way so idk what to expect.
89 notes
·
View notes
Note
Hello, hello, could you please say more about how you use Microsoft OneNote in your professional life? I need all the help I can get to stay organized & on top of things, so I would love to know.
Sure! I use it less than previous because there's less randomized stuff I need to do now, so I don't need such robust management, but I can talk about how my use began/evolved. I started using OneNote because it was less finicky than Word but still had an autosave function and basic formatting, so it was useful for initial drafts of documents, taking notes on meetings, and keeping track of information I needed at my fingertips frequently.
OneNote's largest "unit" is the Notebook. You can have multiple Notebooks but I've never bothered; still I can see how if your screen was public a lot, you'd want to put some things in a separate Notebook. The Notebook then breaks down into Sections which look like tabs, which I would assign to broad things like "Meeting Notes", "Assignments", "Templates", "Personal" and "Excel Hacks". Sections break down further into "Pages"; each page is a document stuck into place, which you can title so that you can have a list of "pages" on the sidebar and find the one you want easily. Text in Pages can be formatted to some degree, and if you copypaste from websites, it'll tag on the URL of the site you pasted from, although you can also turn that off if you want. You can drag and drop Pages from one Section to another pretty easily.
So, for example, I'd have a "Meeting Notes" Section, and when I clicked the tab for that section I'd have a list of Pages, each of which was notes from a meeting I'd attended. Every time I went into a meeting I just made a new page, gave it a meeting title and date, and took notes on the meeting into the page window. The "Meeting Notes" Section thus became a fully searchable record of meetings I'd attended and what was said. When meeting notes were no longer relevant I'd drag them to an archival Section to retire in peace.
Here's an example of my Excel section:
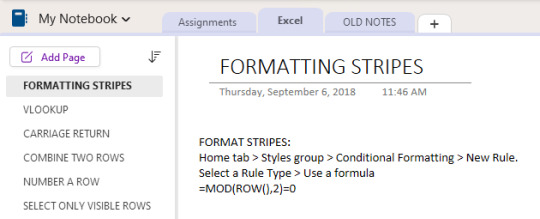
You can see "My Notebook" up in the left top corner, my current Sections as tabs at the top, and the pages list on the left (I think more modern OneNote skins put the pages on the right, I moved mine back). Each line on the left is a separate "page" that tells me how to do something in Excel, something I need to do a lot but can't commit to memory (or couldn't but now have, it's a trifle out of date). So we're in My Notebook, section Excel, page Formatting Stripes, and on the right you can see how to format an Excel sheet so that it has alternating colored rows (there are other ways to do this but this way the stripes always stay alternating no matter what moves where). In theory I could dump all this stuff into one Page and call it "Excel" and put it somewhere else, but I liked having an easily-visible list so I don't have to scroll a single document to find what I want.
There aren't nearly as many tab/sections as there used to be; "Assignments" covers "all work that is not excel formulas" and includes stuff like instructions for how to pull a query in our database, a list of what everyone does at our company, a yearly guide to our events program, a few other things. I don't have a "Personal" section any more but I do have 2-3 pages in the Assignments section that are personal notes.
There's no inbuilt tagging function but because the entire notebook is searchable, if you're really into tagging you can simply add keywords to the top or bottom of a page.
I have OneNote pinned to my taskbar in Windows, and it's basically always open but it autosaves, so adding stuff is super simple; if I find a bug in our database or a quirk I want to remember I just click over to OneNote and add it to the database file, or similar.
I don't use it on my phone or tablet, because if I'm at work I have access to my laptop generally, but OneNote does sync across devices as long as you're logged in, so if you have OneNote and a Microsoft login you should be able to access it in multiple places.
221 notes
·
View notes
Text

Hiya! My name is Izzy-Loa, and a Jr Web Developer and today, I thought it would be a great idea to just share my own personal coding journey! I have answered a lot of asks in the past about how I recommend other people to start their coding studies, what websites to learn from and roadmaps etc. But one question I kept having to repeat myself answering is the "Okay how did you get started?" - it is completely my fault not writing this down properly~! (I did actually)
Anyhoo, I'll just speed through my journey, sharing what I learnt at what times and what I'm currently doing now! ✨

☆ Starting from Scratch
I started coding back in 2017 during the summer break when I was just 15 years old. At that time, I didn't even know what coding was! It was my dad who suggested that I learn HTML. I hesitated at first, thinking HTML was some "complex high-level programming language". Little did I know, it was just a markup language...
I started with HTML and then moved on to CSS during that summer. However, once school started in September, I set coding aside and forgot about it. The following year, 2018, I decided to give it another shot and relearned HTML and CSS. But again dropped it because of school work and upcoming exams!
☆ The Turning Point
Fast forward to 2020, a year that marked a turning point!. I started creating websites using HTML and CSS. I briefly played with JavaScript but decided to focus on mastering HTML and CSS.
In January 2021, I made a significant decision. I dropped out of school due to personal reasons and decided to fully commit to programming, plus getting my first remote job (non-Tech). From there, I gradually delved into JavaScript a lot more and even dabbled in Python along the way. My learning process was on and off, but I was making progress! Around this time I learnt Git and GitHub!
☆ The Apprenticeship
Around September/October time, I applied for an apprenticeship. My skill set included HTML, CSS, Python, and basic JavaScript. I got accepted and continued to learn Python, delving into C# and Java as well. It was a challenging but rewarding experience! Happily dropped Java towards the end!
At work, I also learned SQL, working with Microsoft SQL Server and MySQL. I even explored .NET Framework and ASP.NET. It was a lot to take in, but I embraced the learning process! The older developers at the workplace were super helpful and very experienced - felt as though they were happy to give me all their knowledge as best they could~!
☆ Expanding My Knowledge
During my apprenticeship, around October 2022, I decided to further expand my skills. I enrolled in a front-end bootcamp, where I revisited HTML, CSS, and JavaScript. I also learned jQuery, Node.js, npm, and even ventured into React. Though, due to not practising it enough, I forgotten React and Node.js~!
☆ My Ongoing Journey
Currently, I'm continuing to explore Python and experimenting with Lua. I'm also revisiting JavaScript, jQuery, and recently, I've started working with SCSS (Sass) to streamline my CSS development - I highly recommend people in Web Development to learn SCSS!! I love it so much!
Looking ahead, my learning wishlist includes TypeScript, React, Vue.js, Angular, and C++. However, I'm not rushing into learning everything at once. I'm taking my time to absorb each language and framework thoroughly.

In summary, it has been a continuous evolution, from HTML and CSS to SQL, .NET Framework, and various other languages and tools. I've faced challenges and taken LOTS of breaks, but each step has brought me closer to becoming a proficient developer. I want to be better! But slowly and in good time!
Hope this was somewhat helpful to other people and yeah, have a nice day/night!

⤷ ○ ♡ my shop ○ my twt ○ my youtube ○ pinned post ○ blog's navigation ♡ ○
#resources#codeblr#coding#progblr#programming#studyblr#studying#computer science#tech#comp sci#programmer#about me#personal#academia#cs academia#light academia
69 notes
·
View notes
Text
39 Best Websites to Find Free Textbooks, Research Papers, Study Guides, and Books
Whether you’ve just received a long list of textbooks you need for a specific uni class or are looking for a particular book/research paper for a high school project, books (and journal subscriptions) can be expensive.
The good news is that there are plenty of resources online where you can find free PDF versions of most written materials, starting with Atkinson & Hilgard’s Introduction to Psychology and ending with Shakespeare’s Macbeth.
Note that although some of the websites below provide access to copyright-free texts only, or texts that publishers/authors have agreed to share freely, others have been accused of internet privacy.
However, many people see open access practices as morally acceptable, especially considering the unsustainable prices of academic textbooks and papers.
To quote a recent paper on the topic:
"Since shadow libraries are a product of the cooperation between scholars, who contribute texts and other resources (such as donations, volunteer work, etc.), shadow libraries represent a ‘bottom-up’, radical approach to open access: a physical approximation of the Platonic ideal of knowledge sharing that would exist if there were no legal, economic, or institutional barriers to the circulation of scholarly knowledge."
Free Textbooks
Library Genesis
Library Genesis, or Libgen for short, is a shadow online library website where college students can find academic books (including those that are hard to find/very expensive) and scholarly journal articles.
The site also hosts general-interest books, audiobooks, comics, magazines, and images.
Z-Library

Z-Library is another shadow library website that hosts college textbooks, scholarly journal articles, and general-interest books. It calls itself “the world’s largest e-book library.” It mirrors Library Genesis.
The front page also features some of the most popular books at the time. When we viewed it, these included “Thinking Fast and Slow” by Daniel Kahneman, The Book Thief by Markus Zusak, and Harry Potter the Complete Collection by J. K. Rowling.
You can also use the right-hand navigation menu to see the books that have been added most recently, as well as sort through books based on category.
Use the Book Request option if you can’t find a book you’re looking for. There’s no guarantee your book will be added, but community members look at requests to see what books to upload (you can also upload books).
PDF Drive
PDF Drive is an online library with a ton of free ebooks and PDF textbooks in various categories, including academic & education (but also lifestyle, personal growth, art, linguistics, etc.)
ForCoder.su

Forcoder.su has lots of online textbooks on programming. It also provides free access to online courses, like Apache Kafka for beginners and object-oriented programming with Python. Currently, there are hundreds of free courses available.
Online Mathematics Textbooks
Online Mathematics Textbooks is your source for free digital textbooks on all things math. It’s just one page featuring 77 textbooks.
Tech Books for Free Download

Tech Books for Free Download is where you’ll find free science and engineering books on topics ranging from data mining to general relativity.
There’s no way to search for books easily. However, the site is divided into books on Linux, Java, Microsoft, C and C++, Perl/Python, Science, Networking, Database, Security, and Assembly.
Free Tech Books
Free Tech Books is an open textbook library. It provides access to free computer science books and textbooks, plus lecture notes. All the books and lecture notes listed on this site are freely available on authors’ and/or publishers’ sites.
You can browse books by category (computer science, mathematics, supporting fields, operating system, programming/scripting, miscellaneous), author, publisher, or license.
Directory of Open Access Books
Directory of Open Access Books (DOAB) is a website that indexes and provides access to academic, peer-reviewed open-access books. All disciplines are covered, but there’s a particular emphasis on humanities, social sciences, and law.
Ubiquity Press

Ubiquity Press has been an open-access publisher of academic, peer-reviewed books and journals since 2012. It was founded by University of College London (UCL) researchers.
Research Papers
Sci-Hub
Sci-hub has the most expansive collection of research papers. Its mission is to “remove all barriers in the way of science.”
Directory of Open Access Journals
Directory of Open Access Journals (DOAJ) is an online directory of open-access, peer-reviewed research journals covering humanities, social sciences, technology, science, medicine, and art.
The directory indexes journals from different countries and languages. DOAJ is supported financially by publishers, libraries, and other organizations.
Wiley Open Access
Wiley Open Access provides peer-reviewed open-access journals across topics like biochemistry, economics, sociology, mathematics, and law.
SpringerOpen
SpringerOpen publishes open-access journals across a wide range of areas, mainly STEM.
Elsevier
Elsevier publishes open-access, peer-reviewed journals. You can search for journals by title, keyword, or subject (dentistry, nursing, decision sciences, etc.)
Springer Link
Springer Link provides access to ebooks, peer-reviewed journal articles, and other resources (mostly scientific).
BASE

BASE is a search engine for academic texts, including journals, digital collections, institutional repositories, etc. You can access about 60% of the indexed texts for free.
Study Guides
Bibliomania
Bibliomania has study guides to the most-read books, like “A Hero of Our Time,” “Animal Farm,” and even Irish politics. It also has over 2,000 classic texts, book summaries, author biographies, and more.
Books
Open Library
Open Library is an open library catalog of more than 3 million new and old books. The project was created by the nonprofit organization Internet Archive. It has also received partial funding from Kahle/Austin Foundation and the California State Library.
You can read old books without an account. However, for new books, you’ll need to set one up (it takes just a few minutes).
Internet Archive
Internet Archive is a digital library of ebooks. It also has free movies, music, and software.
Project Gutenberg

Project Gutenberg is a famous site where you can find lots of free books. There are more than 60,000 books in its collection.
Standard Ebooks

Standard Ebooks take public domain texts and make them as nice as new books. They fix typographical errors and typos, create cool cover art, and format the text for e-readers like Kindle and iPad.
Planet eBook

Planet eBook is where you can download free PDF copies of classics like Franz Kafka’s The Metamorphosis, Fyodor Dostoyevsky’s Crime and Punishment, and Joseph Conrad’s Heart of Darkness.
What really makes Planet eBook stand out is its UX. It’s one of those rare sites that are super easy to navigate and actually look good (aesthetically speaking).
The Ultimate Book Search Engine
The Ultimate Book Search Engine is an ebook search engine that includes 350 open directory sites that relate to ebooks. It was created by the Reddit user u/NotoriousYEG.
Classic Bookshelf
The Classic Bookshelf is a site where you’ll find lots of classic novels, everything from Charles Dickens and Leo Tolstoy.
Literature.org
Literature.org features classic works of English literature, both fiction and non-fiction.
Bartleby
Bartleby is a site that features both fiction and nonfiction books.
Fiction.us

Fiction.us has a ton of books, including fiction, short stories, children's picture books, poetry, books on writing, and plays.
Classic Literature Library
As the name suggests, Classic Literature Library is where you’ll find classic literature works.
Ideology.us

Ideology.us is a site that has ebooks on philosophy, psychology, sociology, politics, and education.
The Complete Works of William Shakespeare

The Complete Works of William Shakespeare is where you’ll find all of Shakespeare’s work. The site is run by The Tech, the largest and oldest newspaper by the Massachusetts Institute of Technology in Cambridge.
Read Books Online
Read Books Online has around 6,000 ebooks, including novels, short stories, poems, essays, plays, and non-fiction.
Public Bookshelf
Public Bookshelf is a site dedicated to romance novels.
Categories of ebooks here include contemporary romance, romantic suspense, historical romance, regency romance, inspirational romance, vampire romance, western romance, general romance, and fantasy and paranormal romance.
The Perseus Project

The Perseus Project is a digital library created by Tufts University with books from Ancient Rome and Greece, published in original languages and English.
Chest of Books

Chest of Books has books on a ton of different subjects, including animals, finance, real estate, science, and travel.
The Literature Network
The Literature Network has books by authors like Anne Bronte, Lewis Carroll, and Lord George Gordon Byron. It also features forums, literature summaries, and quizzes.
The Online Books Page
The Online Books Page is a site by the University of Pennsylvania that houses books in categories like philosophy, history, medicine, science, agriculture, music, anthropology, and more. The site also links to the following:
Banned Books Online: A directory of books that were once banned and links to places where you can read them in full.
A Celebration of Women Writers: A directory that lists online editions of literary works by women as well as resources about women writers.
Prize Winners Online: A directory of prize-winning books.
Many Books

Many Books is “your friendly neighborhood library.” It houses over 50,000 books in genres like romance, mystery, young adult, horror, and non-fiction. You can read books online or download them to your device.
Authorama

Authorama turns public domain books on sites like Google Books and Project Gutenberg into HTML format, making it easier to read them.
Audiobooks
Librivox
Librivox has free audiobooks that you can listen to from any device.
#adulthood#young adult#new adult#adulting#how to be an adult#adulting is hard#adulting 101#growing up#grown up#all grown up#responsible#the responsible one#self improvement#self#self sufficiency#self sufficient living#daily life#lifehacks#life improvement#life tips#life hacks#life#tips and tricks#tips#hacks#hack#reference#ref#free shit#college
453 notes
·
View notes
Text
INTERVIEW WITH TAKAYUKI YANAGIHORI - DIRECTOR ON PHASE PARADOX PS2
As I was researching the Japan exclusive PS2 game Phase Paradox (sequel to Philosoma on the PS1), I quickly realised there's very little information available on this sci-fi horror game. Thankfully, the director of Phase Paradox responded to me and I was able to learn more about this obscure title which I'd like to share!
Takayuki: First, let me introduce myself. I started my career as a game developer at Sega, then at SCE (now SIE) and Microsoft. After that, I started my own small studio and am still making games. This time I developed PHASEPARADOX, which was originally a survival horror game for PS1, but changed to an adventure game for PS2.
You mentioned to me that the game was difficult work, what parts of development were challenging? How many years did development take?
The most important thing is that it was an early PS2 title. There was a lack of development equipment, and it was difficult to tell whether bugs were caused by the program or the development equipment, and PS2 development itself was difficult. We also had to handle a large amount of CG, which was very difficult because it was still the 1990s and the CG tools and techniques were not yet up to scratch.
As for the development period, I was in charge for 4 years, but I heard that it took about 2 years before that. (I heard that the game had already been playable on PS1.)
In contrast, what parts of development were the most enjoyable for you?
Game development is always fun. Creating assets using 3DCG, which was the state-of-the-art at that time, building a worldview in accordance with science fiction research, setting scenarios and characters, etc., all of it was both painful and enjoyable.
I was inspired to try new things.
Were there any movies or video games that were a big influence for Phase Paradox? For example, Massimo's character reminded me a lot of Ron Perlman and Arnold Schwarzenegger!
The original idea was to create a "Resident Evil" game based on the world of the "ALIEN" movie. I incorporated a lot of my knowledge of game design and movies into the project.
As you said, the character of Massimo is Arnold Schwarzenegger, and Jude Sutcliffe is Michael Pare. All the other characters have Hollywood star models. I think it was allowed because it was then, but it is not now, lol. The game part was based on Movie Adventure.
The cast for the game is very impressive! Since the voices are in English, was the game planned for worldwide release?
Yes, it was supposed to be a big seller all over the world. However, it was cancelled due to the short playing time and the lack of gameplay. The voice recording was done in L.A.
The presidential election was taking place at the time of recording, and I remember the staff saying to me, "You are in the U.S. on a historic day”.
I love the design of the environments. There are many rooms (like the arcade) that have a very unique and detailed appearance. Did a lot of work go into creating the interior of the Gallant? What were some of the inspirations behind the designs?
The artwork was done by Matsushima-san, continuing from Philosoma. This person has experience working on costumes for the Ultraman series at Bandai, and he drew the foundation of the world, the art settings, and all the original drawings.
Phase Paradox is a sequel to Philosoma. Was it difficult to make a game with a fictional world and characters that were already established? Or did this make work easier?
As I mentioned in 5, it was not difficult for me to continue with Mr. Matsushima. Rather, I enjoyed it very much because I was allowed to add my favorite SF essence to Philosoma.
Do you remember any features that you and the team wanted to include in the game, but maybe couldn't because of time or cost?
Action game elements, mini-games, more options. I am very disappointed. But I think if we had included these elements, we would still be making them, lol. How many more years would have been needed?
At the time, we abandoned the idea of calculating or thinking about that number. We concentrated only on completing it.
What did you and the team want to achieve with Phase Paradox? It feels like a very "cinematic" game, was this rare with games at the time?
The result was a common movie game, but rather than a cinematic part of the game, we were aiming for an innovative adventure game where the situation changes depending on the choices you make.
I was aiming for something like "Detroit: Become Human", if I may say so now in the 21st century. Every time I play that game, I feel strongly about it.
As a final product, what are your personal thoughts on Phase Paradox?
It was a lousy performance, is all I can say. I have always regretted that it was worth it to spend so much money and market value to bring a game with only graphics to the world.
Is there anything else you'd like to share about working on the game? Any strong memories or interesting facts?
As I wrote in #8, I was aiming for a groundbreaking, new game, but I have nothing but regrets about developing on new hardware, not being able to devote the effort to gameplay due to my focus on graphics, and being buried and truncated in various ways by a large amount of work.
More than 20 years have passed and I have sealed my memory, but when I recall it like this, I feel more proud than ashamed, feeling that I was young and ambitious.
Thank you very much.
What are you working on currently?
I am currently making a soccer game at GADE inc.
One is a blockchain game. The other is a 3D action soccer game. I am working on both of them to get rid of my dissatisfaction and regret of the action soccer game I made in Sega.
I am proud to say that I still have new initiatives and high aspirations, so please look forward to them. Both are for the whole world. However, we are having a hard time because we don't have the money for promotion. We would be very happy if someone could help us. We are also planning to launch a new innovative adventure game service on the Web and an action game with an elaborate world view.
If anyone is interested or willing to support us, please contact us.
Thank you to Takayuki for taking the time to provide his insight into Phase Paradox's development! I've made a video on the game which you can watch here: https://youtu.be/bTSFY5M08BU
31 notes
·
View notes
Text
PSA: Free Software
Reading this may really save your time, privacy, and money!
Reblog or share to spread awareness!
Folks often use software that’s expensive and sometimes even inferior because they don’t know there are alternatives. So to those unfamiliar: basically, free and open-source (FOSS) or "libre" software is free to use and anyone can access the original code to make their own version or work on fixing problems.
That does not mean anyone can randomly add a virus and give it to everyone—any respectable libre project has checks in place to make sure changes to the official version are good! Libre software is typically developed by communities who really care about the quality of the software as a goal in itself.
There are libre alternatives to many well-known programs that do everything an average user needs (find out more under the cut!) for free with no DRM, license keys, or subscriptions.
Using libre software when possible is an easy way to fight against and free yourself from corporate greed while actually being more convenient in many cases! If you need an app to do something, perhaps try searching online for things like:
foss [whatever it is]
libre [whatever it is]
open source [whatever it is]
Feel free to recommend more libre software in the tags, replies, comments, or whatever you freaks like to do!
Some Libre Software I Personally Enjoy…
LibreOffice
LibreOffice is an office suite, much like Microsoft Office. It includes equivalents for apps like Word, Excel, and Powerpoint, which can view and edit files created for those apps.
I can't say I've used it much myself yet. I do not personally like using office software except when I have to for school.
OpenShot
OpenShot Video Editor is, as the name suggests, a video editing program. It has industry-standard features like splicing, layering, transitions, and greenscreen.
I've only made one video with it so far, but I'm already very happy with it. I had already paid for a video editor (Cyberlink PowerDirector Pro), but I needed to reinstall it and I didn't remember how. Out of desperation, I searched up "FOSS video editor" and I'm so glad I did. There's no launcher, there's no promotion of other apps and asset packs—it's just a video editor with a normal installer.
GIMP
GNU Image Manipulation Program is an image editor, much like Photoshop. Originally created for Linux but also available for Windows and MacOS, it provides plenty of functionality for editing images. It is a bit unintuitive to learn at first, though.
I've used it to create and modify images for years, including logos, really bad traceover art, and Minecraft textures. It doesn't have certain advanced tech like AI paint-in, but it has served my purposes well and it might just work for yours!
(Be sure to go to Windows > Dockable Dialogs > Colors. I have no idea why that's not enabled by default.)
Audacity
Audacity is an audio editing program. It can record, load, splice, and layer audio files and apply effects to them.
Audacity is another program I've used for a long time. It is not designed to compose music, but it is great for podcasts, simple edits, and loading legacy MS Paint to hear cool noises.
7-Zip
7-Zip is a file manager and archive tool. It supports many archive types including ZIP, RAR, TAR, and its own format, 7Z. It can view and modify the contents of archives, encrypt and decrypt archives, and all that good stuff.
Personally, I use 7-Zip to look inside JAR files for Minecraft reasons. I must admit that its UI is ugly.
Firefox
Firefox is an internet browser, much like Google Chrome, Microsoft Edge, or Safari. While browsers are free, many of them include tracking or other anti-consumer practices. For example, Google plans to release an update to Chromium (the base that most browsers are built from these days) that makes ad blockers less effective by removing the APIs they currently rely on.
Aside from fighting monopolies, benefits include: support for animated themes (the one in the picture is Purple Night Theme), good ad blockers forever, an (albeit hidden) compact UI option (available on about:config), and a cute fox icon.
uBlock Origin
As far as I know, uBlock Origin is one of the best ad blockers there is.
I was on a sketchy website with my brother, and he was using Opera GX's ad blocker. Much of the time when he clicked on anything, it would take us to a random sponsored page. I suggested that he try uBlock Origin, and with uBlock Origin, that didn't happen anymore.
Linux
Linux is a kernel, but the term is often used to refer to operating systems (much like Windows or MacOS) built on it. There are many different Linux-based operating systems (or "distros") to choose from, but apps made for Linux usually work on most popular distros. You can also use many normally Windows-only apps on Linux through compatibility layers like WINE.


I don't have all four of these, so the images are from Wikipedia. I tried to show a variety of Linux distros made for different kinds of users.
If you want to replace your operating system, I recommend being very careful because you can end up breaking things. Many computer manufacturers don't care about supporting Linux, meaning that things may not work (Nvidia graphic cards notoriously have issues on Linux, for example).
Personally, I tried installing Pop!_OS on a laptop, and the sound output mysteriously doesn't work. I may try switching to Arch Linux, since it is extremely customizable and I might be able to experiment until I find a configuration where the audio works.
Many Linux distros offer "Live USB" functionality, which works as both a demo and an installer. You should thoroughly test your distro on a Live USB session before you actually install it to be absolutely sure that everything works. Even if it seems fine, you should probably look into dual-booting with your existing operating system, just in case you need it for some reason.
Happy computering!
#196#psa#foss#open source#tech#software#apps#computer stuff#I really hope Tumblr doesn't block this for having links or something. Someone mentioned that being a possibility and now I'm worried.#please reblog#2024-01-26
25 notes
·
View notes
Text
Last month, US president Joe Biden signed a surveillance bill enhancing the National Security Agency’s power to compel US businesses to wiretap communications going in and out of the country. The changes to the law have left legal experts largely in the dark as to the true limits of this new authority, chiefly when it comes to the types of companies that could be affected. The American Civil Liberties Union and organizations like it say the bill has rendered the statutory language governing the limits of a powerful wiretap tool overly vague, potentially subjecting large swaths of corporate America to warrantless and secretive surveillance practices.
In April, Congress rushed to extend the US intelligence system’s “crown jewel,” Section 702 of the Foreign Intelligence Surveillance Act (FISA). The spy program allows the NSA to wiretap calls and messages between Americans and foreigners abroad—so long as the foreigner is the individual being “targeted” and the intercept serves a significant “foreign intelligence” purpose. Since 2008, the program has been limited to a subset of businesses that the law calls “electronic communications service providers,” or ECSPs—corporations such as Microsoft and Google, which provide email services, and phone companies like Sprint and AT&T.
In recent years, the government has worked quietly to redefine what it means to be an ECSP in an attempt to extend the NSA’s reach, first unilaterally and now with Congress’ backing. The issue remains that the bill Biden signed last month contains murky language that attempts to redefine the scope of a critical surveillance program. In response, a coalition of digital rights organizations, including the Brennan Center for Justice to the Electronic Frontier Foundation, is pressing the US attorney general, Merrick Garland, and the nation’s top spy, Avril Haines, to declassify details about a relevant court case that could, they say, shed much-needed light on the situation.
In a letter to the top officials, more than 20 such organizations say they believe the new definition of an ECSP adopted by Congress might “permit the NSA to compel almost any US business to assist” the agency, noting that all companies today provide some sort of “service” and have access to equipment on which “communications” are stored.
“Deliberately writing overbroad surveillance authorities and trusting that future administrations will decide not to exploit them is a recipe for abuse,” the letter says. “And it is entirely unnecessary, as the administration can—and should—declassify the fact that the provision is intended to reach data centers.”
The Justice Department confirmed receipt of the letter on Tuesday but referred WIRED to the Office of the Director of National Intelligence, which has primary purview over declassification decisions. The ODNI has not responded to a request for comment.
It is widely believed—and has been reported—that data centers are the intended target of this textual change. Matt Olsen, the assistant US attorney general for national security, appeared on an April 17 episode of the Lawfare podcast to say that, while unable to confirm or deny any specifics, data centers today store a significant amount of communications data and are an “example” of why the government viewed the change as necessary.
A DOJ spokesperson pointed WIRED to an April 18 letter by Garland that claims the new ECSP definition is “narrowly tailored.” The letter includes written reflections on the provision by the assistant attorney general, Carlos Uriarte, who writes that the “fix” is meant to address a “critical intelligence gap” resulting from changes in technology over the past 15 years. According to Uriarte, the DOJ has committed to applying the new definition internally “to cover the type of service provider at issue” before the court.
Ostensibly this means the government is promising to limit future surveillance directives to data centers (in addition to the companies traditionally defined as ECSPs).
The surveillance court that oversees FISA and the appeals court that reviews its decisions sided two years ago with an unidentified company that fought back after being served an NSA order. Both courts ruled that it did not, in fact, appear to meet the criteria for being considered an ECSP, as only part of its function was storing communications data. Finding the government’s interpretation of the statute overly broad, the court reminded the government that only Congress has the “competence and constitutional authority” to rewrite the law.
Digital rights groups argue that declassifying additional information about this FISA case may help the public understand which types of businesses are actually subject to NSA directives. Practically speaking, they say, that information is no longer a secret anyway. “Declassifying this information would cause little if any national security harm,” the letter says. “The New York Times has already revealed that the relevant FISC case addressed data centers for cloud computing.”
In the aftermath of the FISA court’s ruling, the NSA and other spy agencies began lobbying the House and Senate intelligence committees to aid the administration in redefining what it means to be an ECSP. Members of both committees have subsequently portrayed the court’s ruling as a “directive” that Congress needs to expand the NSA’s reach. In a floor speech last month, Mark Warner, the chair of the Senate Intelligence Committee, said, “So what happened was, the FISA Court said to Congress: You guys need to close this loophole; you need to close this and change this definition.”
But in fact what the court asserted was that the government had exceeded its authority and that it was Congress’ job, not the Justice Department’s, to revise the law. “Any unintended gap in coverage revealed by our interpretation is, of course, open to reconsideration by the branches of government whose competence and constitutional authority extend to statutory revision,” the court said.
This would culminate in new language being proposed that quickly alarmed legal experts, including top civil liberties attorneys who’ve appeared before the secret court in the past. The surveillance fears quickly spread to Silicon Valley. The Information Technology Industry Council, one of the tech industry's top lobbying arms, warned that companies like Facebook and IBM were interpreting the bill as having “vastly expanded the US government’s warrantless surveillance capabilities.”
This expansion, the firm added, would also hinder the “competitiveness of US technology companies” and arguably imperil the “continued global free flow of data between the US and its allies.” Customers internationally, it argued, would likely begin taking their business elsewhere should the US government turn data centers into surveillance watering holes.
Concerns about the new ECSP definition have been circulating since December. While largely dismissing them, members of the House and Senate intelligence committees made a few adjustments in February, exempting a handful of business types. This came in response to popular concerns that Starbucks employees and hotel IT staff might be secretly conscripted by the NSA. FISA experts such as Marc Zwillinger—a private attorney who has appeared twice before the FISA Court of Review—noted in response to those adjustments that Congress’ rush to exempt a handful of businesses only served to demonstrate that the text was inherently too broad.
Intelligence committee members kept the pressure on lawmakers to reauthorize the Section 702 program with the sought-after language, going as far as to suggest that another 9/11-style attack might occur if they failed. The power of the committees was on full display, as while neither actually have primary jurisdiction over FISA, a majority of the Section 702 bill that passed was authored by intelligence committee staff.
Even while supporting the new framework and dismissing the intensity of civil society’s concerns, Warner did eventually step forward to acknowledge the new ECSF definition needed additional tweaking. First, on the Senate floor in April, he said that Garland shared his “view” that the language “could have been drafted better.” Later, in response to questions from reporters, he added: “I’m absolutely committed to getting that fixed.”
That appears unlikely to happen soon. According to The Record, Warner indicated that the best time to update the language again would be in the “next intelligence bill,” presumably referring to legislation this fall broadly reauthorizing the intelligence community’s work.
In the meantime, however, more than half of Congress is running for election, and the next US president will have greater surveillance powers than any other before. No one can say for sure who that president will be or how they’ll make use of that authority.
11 notes
·
View notes
Text


Rubin Observatory Achieves Another Major Milestone: Reflective Coating of the 8.4-meter Primary/Tertiary Mirror
The first reflective coating was applied to Vera C. Rubin Observatory’s 8.4-meter combined primary/tertiary mirror using the observatory’s onsite coating chamber.
With its shiny, new silver coating, Vera C. Rubin Observatory’s 8.4-meter primary/tertiary mirror is one step closer to revolutionizing the way astronomers capture and study the Universe. Both mirrors will soon be installed on the Simonyi Survey Telescope where they will collect the light of distant celestial objects and events during the 10-year Legacy Survey of Space and Time (LSST), beginning in 2025.
Vera C. Rubin Observatory, a next-generation astronomical facility under construction in Chile, funded by the U.S. National Science Foundation (NSF) and the U.S. Department of Energy (DOE), achieved an important milestone on 27 April 2024, with the successful coating of the 8.4-meter primary/tertiary mirror with protected silver. This important event paves the way for the installation of the glass mirrors on the Simonyi Survey Telescope, bringing Rubin Observatory closer to revolutionizing the fields of astronomy and astrophysics with its 10-year Legacy Survey of Space and Time (LSST), beginning in 2025.
“This milestone represents not just an incredible feat of engineering, but also an important step towards a transformative new era of scientific advancement” said Edward Ajhar, NSF Program Director for Rubin Observatory.
Rubin Observatory’s one-of-a-kind primary/tertiary mirror is an integral component of the telescope’s optical system, which also includes a 3.4-meter secondary mirror and the LSST Camera, the largest digital camera in the world. Fabrication of the mirror was enabled by major gifts from the Charles Simonyi Fund for Arts and Sciences and from Microsoft founder Bill Gates. The 8.4-meter mirror is made up of two optical surfaces, each with a different curvature, combined into one large structure about as wide as a tennis court. Integrating the two mirrors in this way reduces the engineering and control complexity for the telescope while maintaining its excellent light collecting capacity. The mirror was fabricated over a period of seven years at the Richard F. Caris Mirror Lab, of the University of Arizona, Tucson, AZ, beginning in 2008. In 2015, the completed mirror was moved to a secure storage area and in early 2019 it was shipped to the summit facility on Cerro Pachón in Chile.
The mirror coating process was carried out safely and efficiently by a skilled team using a state-of-the-art, onsite coating chamber built specifically for Rubin Observatory by VON ARDENNE in Deggendorf, Germany. The 128-ton coating chamber, installed on the maintenance floor of the observatory facility, uses a technique called magnetron sputtering to coat mirrors to precise specifications. This technique gives Rubin the flexibility to coat the telescope mirrors with aluminum, silver, or even a combination of both during any coating run. To coat the 8.4-meter primary/tertiary mirror, the lower half of the coating chamber was removed and the mirror’s vacuum-sealed support structure — called the mirror cell — acted as the base of the chamber.
The Rubin coating team, led by Tomislav Vucina, conducted extensive testing to determine the final coating 'recipe' — the precise mixture of elements to make up the coating layers to achieve the best possible combination of reflectivity and durability. To verify the performance of the chosen mixture the team coated a steel stand-in mirror, which has also been used for testing the telescope mount and other observatory components. After confirming the mixture met the defined requirements they repeated the process using the glass mirror.
First, the team applied an adhesion layer of nickel-chromium (NiCr) to the glass mirror blank. Then, they applied the reflective layer of silver (Ag). This reflective layer is incredibly thin — the amount of silver used to coat the entire 8.4-meter surface (64 grams) would form a ball about the size of a cherry tomato. After the application of the reflective layer, the mirror received another NiCr adhesion layer and a final layer of silicon nitride (Si3N4) to protect the reflective coating from dust and other environmental contaminants. “This outer layer needs to be thick enough that it’s not worn off by cleaning,” said Vucina, “but not so thick that it absorbs too many photons and prevents the mirror from meeting Rubin’s scientific requirements.”
The process of coating the mirror took about 4½ hours. After the coating was complete the mirror was moved out of the chamber to a nearby space. To ensure all requirements were met, Vucina and his team conducted a series of tests: reflectivity, adhesion, pinhole, and cosmetic. After analyzing the results of those tests they declared the coating a success. “This was a very well-conducted project from every angle,” said Vucina, “thanks to a combination of careful planning and the technical skills of our excellent team.”
With its dazzling new coat Rubin’s primary/tertiary mirror is an important step closer to capturing light from distant celestial objects. “We’re extremely excited that both mirrors are now coated and will be installed on the telescope very soon,” said Sandrine Thomas, Deputy Director for Rubin Construction. “The combined reflectivity of these mirrors will enable Rubin to detect very faint and far-away objects, leading to great science!”
TOP IMAGE....Rubin Observatory’s 8.4-meter combined primary/tertiary mirror was coated with protected silver in April 2024. The reflective coating was applied using the observatory’s onsite coating chamber, which will also be used to re-coat the mirror as necessary during Rubin’s 10-year Legacy Survey of Space and Time.Credit: RubinObs/NOIRLab/NSF/AURA
LOWER IMAGE....View of Rubin Observatory and surrounding buildings taken by drone in October 2023. The 8.4-meter telescope at Rubin Observatory, equipped with the highest-resolution digital camera in the world, will take enormous images of the southern hemisphere sky, covering the entire sky every few nights. Rubin will do this over and over for 10 years, creating a timelapse view of the Universe that’s unlike anything we’ve seen before.Credit: Rubin Observatory/NSF/AURA/A. Pizarro D
youtube
youtube
11 notes
·
View notes