#additions still show up even if the person is both blocked and blacklisted
Text
i think the worst thing abt tumblr making it so much harder to find an original post (or as least one of the previous additions only) is now it's so much harder to avoid prismatic bell's abnoxious ass additions
#still positive xe make so many fucking additions to block evade#since you can't blacklist a url#because of course who expects this site to ever fuckign work properly#especially when it comes to blocking folks#anyway i'll link or find the callout if needed#but here's a fresh heads up#prismatic-bell is a fucking racist and zionist#don't rb from xir#and check for xir additions in posts#additions still show up even if the person is both blocked and blacklisted
25 notes
·
View notes
Text
Search, Tags, and Tumblr
Tumblr's search functions are notoriously weird, but there's a few common things to know about how it works in conjunction with Tagging. First things first:
-Tags are for searching but also personal blog organization as desired. This is why some folks have weird/funny personal use tags. Tags can use dashes and spaces, but not regular double quote marks ("), though single marks are fine (').
-Tag for what's in the post; adding other, unrelated tags "for visibility" is against Tumblr's TOS and gets you reported for Spam!
Example: if you make a post for your new Clive Rosfield screenshots, make sure you're only tagging terms relevant to Final Fantasy XVI and Clive Rosfield (and any personal organizing tags like "screenshots"); don't add tags like "Star Wars" and "SpongeBob", as Clive has nothing to do with those!
-Tag without censoring words! We use filters/blacklists here to avoid things we don't want to see. Can also work for words in the body of a post. There's no rules here against using "kill" or "death" or other terms defining common human experiences determined "too negative/dangerous" on other sites (stay civil to each other).
-If you do alt-spell things, it's only in the body of a post and usually when it's dislike of a fandom thing as a courtesy to those enjoyers. If I make a shipping post and say, for example, "I can't stand R3y|o", that's when I want to use weird spelling and symbols--and no common tags for that fandom! If you do use tags for organizing, keep it to things like "#anti (thing) or "#(thing) critical", again spelled correctly for others' blacklisting purposes and to keep it out of the Reylo Search and Tags so those fans can enjoy their ship without seeing negativity. Because...
-General Search pulls from Tags and Also terms found in the body of a post. If I just put "Thancred" in the Search bar at the top of the page, it'll show me any and all posts with "Thancred" in them, including 1) if the name is in the body of the post, 2) if the name is in a tag that's a sentence/includes other words, and 3) even if not tagged for Thancred.
This caused some wank a couple years back for certain fans when someone tagged a lascivious picture set with what they knew was a triggery NOTP for many...but they also put the characters' names in the post body, not realizing simply searching for either of those characters would pull it up (They also, IMO, should have put the images under a Read More to be doubly safe, for themselves and for others they knew might be upset stumbling onto said images, but the crux was not realizing how Tumblr Search worked).
-Tag Search specifically pulls from the tags; per Tumblr's info pages, the first 20 tags (out of 30 total allowed) now will show up in search. Common, consistent tags first are good for visibility. You can also Follow tags you want to keep track of; there's even a tab on your Dash for it.
-Reblogs do not show up in the searches, even with additions and new notes. However, a blacklist filter will catch tags put on the original post, even if the reblogger doesn't add it when it ends up on your Dash.
-You can also blacklist blog names/URLs. Think of it like Twitter's muting rather than a full block (though one can do that too, and should as needed).
Example: someone following Seanan McGuire doesn't like frogs, but she reblogs a lot of frogs. The follower blocked and blacklisted the blogs she often reblogs frogs from to minimize the number of frogs they see while still following a favorite author for her book info.
-If people ask you to tag a thing cuz it's a squick or full-on trigger, you can just do it, or you can politely say no; that's valid. It's up to that person then to decide if they want to blacklist or unfollow or block or what. Just be civil either and both ways.
In summary: if you're talking about bunnies cuz you took pictures at the local farm show, just write "bunnies" normally in the body and/or tags of the post, so anyone with "bunnies" blacklisted can avoid it--and folks who want to see cute pics of bunnies can find it!
Even if you use proper tags, or no tags, or only use alternate spellings in the post body to keep things out of the tags/searches, consider still using a Read More as a last line of courtesy to any followers or random folks you don't want to catch in the crossfire. Also consider hiding your blog from Search results, and/or Private posts.
Tumblr's Help Center (On Desktop browser, go to the "About" link, and then the "Resources" menu; on Mobile App, go to Account settings, General settings, scroll down to "Help" under "Account") has further info about Searches and Tagging (and everything else!), and as that info changes, it's a good idea to keep track of those page updates, as well as the @changes blog to keep track of new updates, bugs, recent fixes, and upcoming info.
56 notes
·
View notes
Text
This is a post on the cheating accusations around dream mostly surrounding his response video.
If you don’t want to see this or any of these posts then blacklist the tag #discourse
SO I’ve been doing a lot of digging into what dream has said in his response to Geosquare’s original video and report, which was compiled and conducted by the Minecraft Java mods on speedrun.com.
I won’t talk about that original report in detail, but basically: the mods came to the conclusion that Dream had a 1 in 7.5 trillion chance of getting the pearl bartering rates and the blaze drop odds that he did within the 6 streams he did. As in, someone would need that luck to replicate what dream got. Therefore, he cheated.
I’m going to put this into a sort of ‘point form’ in according to topic, attempting to put it in chronological order.
Dream’s Initial Tweets
Ok so first like. these are bad. these tweets are what he said (on twitter, excluding in the speedrunning discord) directly after the video was Uploaded to Geo’s channel.
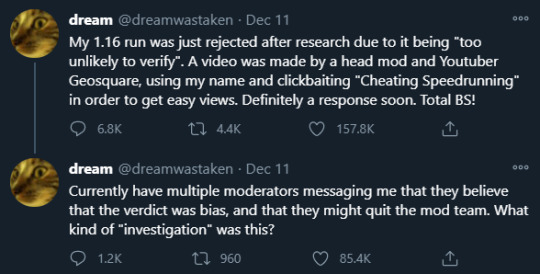
worth noting he did apologize later, although i wanted to talk about these two instances so i felt the need to include it.
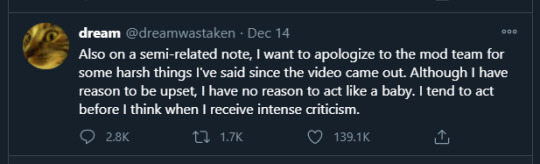
there’s a lot of interesting wording in the apology tweet itself too. I personally find that when he apologizes he tends to still be very subtextually angry in them with the tone, but more specifically. where he says ‘although i have reason to be upset’, that’s kinda weak and really unneeded. Alongside the ‘intense criticism’, it reads as him trying to say he’s still in the right. kind of like “im sorry i was rude even though I had reason to be rude’. Its an apology sure but he’s not saying sorry for how he really reacted; its justified to him.
Dream’s Response Video
Dream posted a response on his side channel DreamXD on the 22nd, along with the report he had a supposed astrophysicist conduct. I’m going to talk about the report separately from the video for reasons I’ll explain.
Frankly, the video doesn’t really summarize or explain the report in a meaningful way. At most, it takes some points from it but tends to twist the numbers around, misunderstand the probability and math, and also what the report itself concludes.
Essentially, dream’s video insists that the numbers found by the mods are wrong and therefore he didn’t cheat at all, yet the report concludes that the numbers found by the mods weren’t entirely accurate, however they’re still extremely unlikely. This is also all under the assumption that the report is entirely correct (ill say how its not next)
His first point is that only his 1.16 run (that was at 5th place two months ago, would have now been 16th) was deemed cheated. This is true; the mods have said that he isnt banned outright and theres no reason to question the legitimacy of his 1.15 runs.
He also concludes that Geo’s statement that Dream didn’t cooperate with them, and that he deleted 1.16 mod folders, was false. This one is a little more complicated. It could more be chalked up to a miscommunication, although it’s relevant. Geosquare posted screenshots of the specific conversation they had:
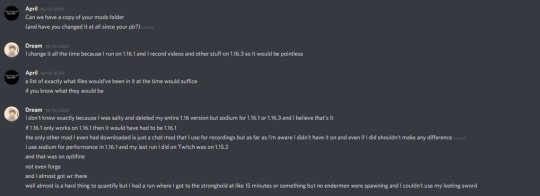
Essentially it wasn’t entirely clear, i can understand how geo and the mods interpreted it in such a way. Altho April added in a quote retweet thread that dream didn’t supply the folder she asked for, so he didn’t supply everything they asked for like he states in the video
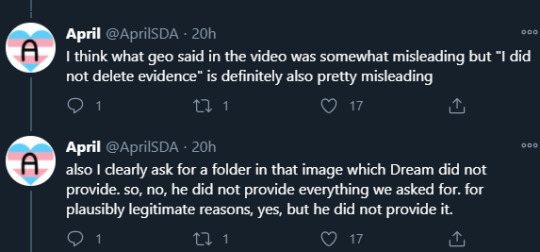
Essentially: yeah, misleading and weird on both ends. I dont think this is really anything quantifiable, although dream talked about this in the video heavily.
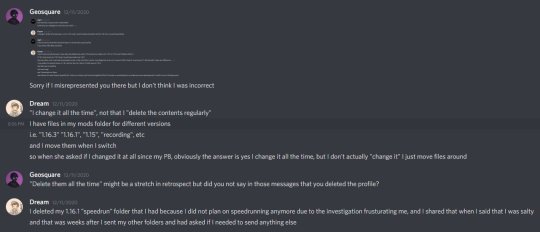
Out of this though, Geo DID correct himself in the description of the mods’ video. Dream shows this in his own response, but it crops out some of what geo says. here’s from dream’s video
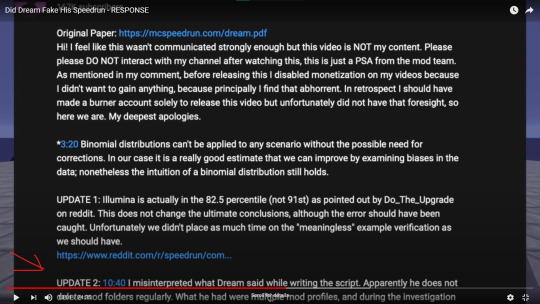
that Update 2 is where he corrects himself. literally why the fuck would you crop it like this and put it in the video i mean this looks so weird and genuinely doesnt provide anything. Here’s what geo actually said
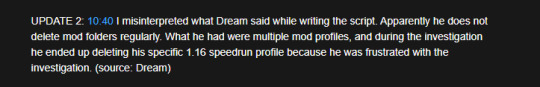
Dream specifically cut it before the line where geo mentions how he said he deleted his specific 1.16 speedrun profile. This one is just so dumb to me. I’d say ‘why not include that’ but either i feel its a) so there’s no potential for people to say what he had actually said could be interpreted otherwise easily or b) doesnt want people to know he got so upset he deleted files (ego wise yknow). Again, I dont think this is definitive of anything but god. it feels scummy lmao
The Video: Incorrect Representation of His Own Report
Dream straight up doesnt present the report’s numbers properly. In fact it makes the entirety of his visuals forfeit, i.e. the gold block analogy that goes on for like 20 minutes.
The mods said his luck was 1/7.5 trillion. Dream’s report says its 1/10 million (with the addition of 5 other streams) or 1/100 million (only the 6 streams).
I’ll only consider the 1/10 mil odds, since its all dream really brings up. but Basically; there’s not much difference between 1/10 million and 1/7.5 trillion.
Dream says that the difference is 7.5 trillion minus 10 million, aka 7.4999 trillion. This is what his entire visual with the gold blocks is based on. This is absolutely incorrect, i cant stress that enough.
You can’t find the difference of fractions by subtracting only the denominators. Like. this is elementary school math. it just doesnt work.
It’d actually be calculated as: (1/10 000 000) - (1/7 500 000 000 000) = (74999/7 500 000 000 000)
If the mods are wrong, they’re only wrong by 749999/7.5 trillion. that’s literally only 0.000000099999866666667.
Dream no doubt saw the numbers, considered 10 million vs. 7.5 trillion, and used these big numbers to hold his own point. PROBABILITY DOESNT WORK LIKE THAT. I really think he was just taking advantage of the seemingly big numbers here and wrote it out in a way that favoured him. The gold block analogy in the video played throughout the entire video practically, jokes were made on it, and he made a point of it being ‘so big the game crashed’.
It’s just plain wrong. even so a difference in the odds doesnt prove shit. He’s downplaying his own odds that he found too. 1/10 million isnt a small number. Even though the legitimacy of that calculation is in question, it is still significant enough to proclaim he cheated.
Some quick points before I move onto the report; these aren’t as significant in my eyes but it adds to the picture
there’s been criticism of his joking manor throughout the entire video, very specifically the Bill Nye joke. Considering he doesnt actually have a name to provide for his astrophysicist, this joke doesnt feel right
the mod he had a voice clip from (willz) even believes that he cheated and has agreed with the mod team the whole time.
Dream never has a name for the mod who is apparently on his side (more understandable), the minecraft developer he quoted, or the astrophysicist (most damning)
Dream states that fabric is used by most speedrunners which is true, but fabric and fabric API are different; dream also had the latter installed. my knowledge of how theyre different is limited, all i really know is the API is what can enable editing of the code while fabric is more a modloader. im not entirely sure on this
Dream has said at the end of the video that all funds will go to the mod team so they can make a client that will regulate cheaters. this has been noted as feeling manipulative or like a ‘bribe’, but it definitely puts the mods in a bad position.
either they accept it and look like they ‘gave in’ to dream and therefore acknowledge him in the right
they deny it and look selfish/taking dream’s kindness for granted
geo said they would insist it goes to a charity instead
Dream constantly disregards the mods as young, inexperienced, ‘just volunteers’ etcetcetc, despite the fact that theyre analysis has been discussed by people with confirmed PhDs without much criticism
Dream’s Report
The report itself is extremely interesting, in that it’s very questionable, but even so it doesn’t come to the conclusion that dream didn’t cheat. The tone between the video and the report is drastically different.
This is from the “3. What are the goals of this document?” section:
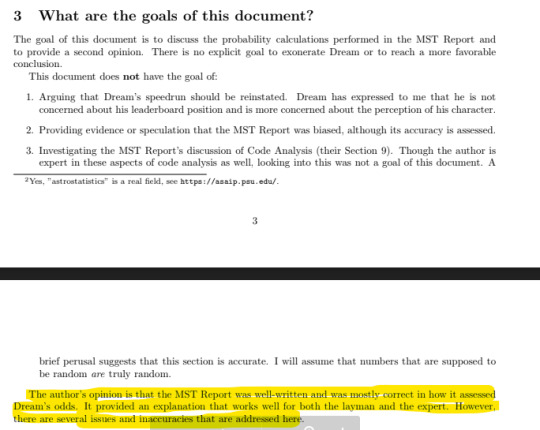
It essentially says this isnt intended, from the very beginning, to completely exonerate dream of cheating. Also note that the author says the mods’ report was mostly correct.
This is at the end of “9 Conclussions”:

It does notably say cheating isnt the only explanation, but it doesnt actually go as far to say that it’s not possible that he cheated.
But this can be argued to not matter if we consider the validity of the report as a whole
Dream’s Report: Criticisms
Possibly the first and most known debunking of the report is by u/mfb on reddit, although there’s been much more such as this programmer criticizing the code provided at the end of the report (partially due to how the author of it stated that piglins barter 4-7 pearls, which is incorrect: it’s 4-8), Andrew Gelman, an actual statistician professor from harvard, commented on the original mods’ report as ‘impressive’ while Dream’s report is being regarded as something funny in the comments, and even analysis of dream’s behaviours and his argument by a law student
But what u/mfb posted is what i’ll focus on. Some background into the user; he’s a particle physicist, is moderator in subreddits like r/cosmology and r/astrophysics, he’s regarded as a reliable source on r/askscience and r/askreddit. Basically, multiple other people have vouched for him and before all this he had many posts in these fields.
that’s already better than the unnamed astrophysicist.
The post is better speaking for itself but here is a few exerpts from it;

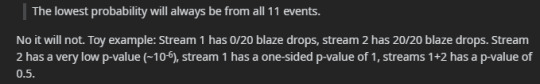
Essentially, the report’s methods are debunked by u/mfb-, alongside that a moderator of r/statistics regarded the report as ‘nonsensical in its application of statistics’ and linked to u/mfb-’s comment.
i’m going to end this here. Partially because severe backpain or whatever,.
but I want to say at this point its practically definitive that dream cheated, that he lied to us, and that he continues to do so. Much more could be said on his video such as his tone, intentions, the overt emphasis on the ‘biases’ of the mods.
I havent even mentioned that the ‘astrophysicist’ themself may be a scam; they are sourced from a website that is extremely sketchy, has no names attached to it, and was created less than a year ago (with practically no traffic on it until maybe a month ago).
But i hope this is coherent. I have interest in this so if theres questions im always open.
60 notes
·
View notes
Note
2, 3, 12!
Hi Tee! ♥ First let me just say: GREAT URL CHANGE. I FULLY SUPPORT IT AND I LIKE THE WAY YOU THINK.
2. Are there any popular fandom OTPs you only BroTP?
To be quite honest I don’t really know what counts as “popular” so I’m just going to go ahead and name ships that I’ve seen people ship, whether they’re considered popular or not I’ll leave that up to you.
Raven x Murphy is one that comes to mind. I don’t know if a lot of people still ship it, but I think it was gaining quite a bit of popularity in season 5 (I believe there even was a cut scene of Raven kissing his cheek but that could’ve been in season 4, honestly I’m such a terrible addition to this fandom, half the time I barely even know what I’m talking about). But I don’t see anything romantic there. If anything, I see Raven as sort of like Murphy’s big sister - she’ll tease him and call him names and he’ll give her a hard time but if it comes down to it, they have each other’s backs. So a sibling dynamic or just really great friends. There used to be a lot of bad blood between them and to be honest I’m still not entirely comfortable with Raven being best friends with the man who permanently wrecked her leg albeit not on purpose. But the show is terrible at addressing stuff like that so 99% of the time I just ignore it I guess? Anyway, I think they have an interesting dynamic and I always enjoy their scenes together, but never in a romantic way.
Then, and Nicole is going to kill me for this but I’m going to say it anyway, there’s Octavia x Gabriel. Again, I don’t know if a *lot* of people ship it, but quite a few of them do and I don’t know, they just don’t do it for me I guess? I mean they’re both hot and they look amazing together, but in season 6 I feel like Gabriel only looked at her like she was a piece of a puzzle he was trying to solve, not a woman, and I just don’t get a shippy vibe when I look at them. That being said, I do think they make a good team and I could get on board with them having a great friendship. I just don’t see a romantic relationship blossoming there because honestly, this man will never look at any woman the way he looks at that damn anomaly. Also, I have not forgiven him for mentioning his friends in 7x07 and then only calling out “Echo! Hope! I’m sorry!” because Octavia should’ve gotten a mention there. Yeah, yeah, he spent five years with them but if I’m supposed to ship him with Octavia, then he should’ve said her name, too, and that’s that.
And then obviously there’s BeIIamy x CIarke. At least I know for sure there’s a popular one LOL. I don’t ship them romantically, I never have. But I also don’t think they make a great BroTP, I’m just mentioning them in my reply so you’ll be absolutely positive that I don’t see any kind of TP whatsoever when I think about those two.
Other than that I guess I’m pretty down with most canon romantic ships I guess? Wouldn’t have turned anyone into a BroTP instead, and I don’t think there are any (popular) ships left that I feel strongly about so here you go!
3. Have you ever unfollowed someone over a fandom opinion?
Oh my god, so many times. Usually it’s because they have a very, very *wrong* opinion about Octavia or because they ship B x C and reblog them far too often. In the past I would’ve replied to those wrong opinions or made anti-gif sets to prove my point about the ship I mentioned but then I grew up so nowadays I just unfollow (and when they tag their shit incorrectly I even block them when I feel like it - I also have two people who I blacklisted via XKit so their posts and edits won’t show up on my dash, I don’t want to block them because it’s not that they tag incorrectly and I do want to allow them to keep reblogging stuff I make because sometimes they do, it’s just that they have such terribly wrong views on Octavia and the gif sets they sometimes make make me want to throw my computer out the window so I figured it was best to just make sure I don’t see their stuff on my dash, *ever*).
12. Is there an unpopular arc that you like that the fandom doesn’t? Why?
Ehh... This is a hard one, because I think sometimes fandom tends to disagree on what does or doesn’t count as an arc. But for the purpose of answering this question I’m going to go with Echo’s... I’m not going to call it “character development” because that makes it sound like she used to be a bad person and then she changed and that’s not what happened. She was never a bad person. Let’s call it Echo’s journey. She started off as an antagonist (which is why it bugs me so much when haters like to call her out on “trying to kill Octavia”: she was on the opposite side, of course she was going to do shit that the protagonists don’t like, that’s what happens when you’re on the opposing team, it’s called story-telling). There’s our group of “heroes” (god I hate it when the show calls them that) and then there was Echo, on the other side, siding with the people who wanted to harm “our heroes”. But then those people cast her out after she did everything she could think of to keep them safe (I’m not saying she did the right thing by cheating in the conclave but she did have noble intentions for doing what she did) and she had nobody anymore, until Spacekru took her in and her loyalties shifted from her former clan to Spacekru. We don’t have a lot of information about what went on on the Ark, but I like the little bits and pieces we did get. I like that it’s canon that she didn’t tell anyone much about herself, that she’s not an open book at all, that she’s closed off, distant, doesn’t let her true feelings surface because it makes her vulnerable and if there’s one thing she learned from life at a very young age, it’s that she can never appear vulnerable, ever. And I like that in season 6 and especially in season 7, she is forced to deal with what happens when she can no longer repress her feelings but instead has to let them out. Is she coping with them in a healthy way? No. Of course not. Not at all. But what did you expect from a woman who saw her parents die when she was just a little kid, who was forced to murder her best friend in self-defense and then use said friend’s name as her own and who was from then on trained and used as a (child) soldier to do someone else’s dirty work? Do you honestly expect someone who carries around that much trauma, who has this many wounds that she could never allow to heal, to deal with losing the man she loves in a healthy way? I think it’s fascination to see her wrestle with those feelings, feelings she can no longer repress or ignore, and I honest to god hope the show will allow her to work through that grief eventually without turning her back into the coldblooded woman she used to be or, god forbid, give her some kind of sacrificial death to "make up for all the bad shit she did”. Echo’s not a bad person, in fact, she’s a far better person than most of our “heroes”. Being able to do what needs to be done doesn’t make her evil, because most people on this show would be evil then. Echo is a severely traumatized young woman who hasn’t had a sense of home in decades and then, when she finally found it, when she finally learned to open up and let herself be soft and vulnerable again with her new found family, it was ripped away from her again. And I think that her journey is one of the most compelling ones of all characters because she goes through so much and yet here she is, ready to fuck shit up to get shit done. I can only hope she’ll get to soft epilogue she deserves, after a lifetime of being at war.
Salty Ask List
#the 100#echo kom azgeda#echo kom spacekru#not tagging anything else because i don't feel like that's necessary#let me know if i'm wrong about that#ask
6 notes
·
View notes
Text
THE COURAGE OF PROJECT
Then when you start a startup anywhere. That's why mice and rabbits are furry and elephants and hippos aren't.1 The very design of the average site in the late twentieth century. He got a 4x liquidation preference. Google, it's hard to get into grad school in math. Can we claim founders are better off as a result of this new trend. Where you live should make at most a couple percent difference. But investing later should also mean they have fewer losers.
They make something moderately appealing and have decent initial growth.2 If you major in math it will be whatever the startup can get from the first one to write a paper for school, his mother would tell him: find a way to turn a billion dollar industry into a fifty million dollar industry, so much the better, if all fifty million go to you. The classic yuppie worked for a small organization. Before us, most companies in the startup funding business. The best way to get a big idea can take roost.3 4 or 5 million. This essay grew out of something I wrote for myself to figure out how to increase their load factors. But you can also apply some force by focusing the discussion: by asking what specific questions they need answered to make up their minds. This plan collapsed under its own weight.4 Startups happened because technology started to change so fast that big companies could no longer keep a lid on the smaller ones.
The only place your judgement makes a difference is in the industry.5 People who do great work, and it's a bad sign when you have a special word for that. One of the exhilarating things about coming back to Cambridge every spring is walking through the streets at dusk, when you can see into the houses. If you have steep revenue growth, say over 6x a year, no matter how many good startups approach him. Recently we managed to recruit her to help us run YC when she's not busy with architectural projects.6 This works better when a startup has 3 founders than 2, and better when the leader of the company in later rounds. I'm not saying you can get away with zero self-discipline.
We're not a replacement for don't give up. What you should not do is rebel. But while series A rounds from VCs. Someone who's scrappy manages to be both threatening and undignified at the same world everyone else does, but notice some odd detail that's compellingly mysterious.7 Even Tim O'Reilly was wearing a suit, a sight so alien I couldn't parse it at first. They can't tell how smart you are.8 The story about Web 2. Maybe one day the most important thing is to be learned from whatever book on it happens to be closest. This essay is derived from a keynote at FOWA in October 2007. They'll decide later if they want to raise.9
Sometimes it reached the point of economic sadism: site owners assumed that the more pain they caused the user, the more benefit it must be to them. It's cities that compete, not countries.10 Kids are curious, but the best founders are certainly capable of it. But investors are so fickle that you can fix for a lot of time on work that interests you, and don't just refuse to. But you have to be an insider.11 A key ingredient in many projects, almost a project on its own, is to step onto an orthogonal vector. So ironically the original description of the Web 2. Back when it cost a lot to like I've done a few things, like intro it to my friends at Foundry who were investors in Service Metrics and understand this model I am also talking to my friend Mark Pincus who had an idea like this a few years ago.12 0 seemed to mean was something about democracy. We didn't have enough saved to live on. There is another reason founders don't ask themselves whether they're default alive or default dead.13
So most investors prefer, if they wanted, raise series A rounds. They're unable to raise more money, and precisely when you'll have to switch to plan B if plan A isn't working. That doesn't mean the investor says yes to everyone. Miss out on what? It's so cheap to start web startups that orders of magnitudes more will be started. Investors evaluate startups the way customers evaluate products, not the way bosses evaluate employees. The bust was as much an overreaction as the boom.14 Startups are undergoing the same transformation that technology does when it becomes cheaper.15 Another way to fly low is to give them something for free that competitors charge for. After all, a Web 2.16 He bought a suit.
Instead you'll be compelled to seek growth in other ways. They all knew their work like a piano player knows the keys. But consulting is far from free money. They say they're going to get eliminated. What does it mean, exactly? If investors were perfect judges, the two would require exactly the same skills. And to be both good and novel, an idea probably has to seem bad to most people, or someone writes a particularly interesting article, it will show up there. The mere existence of prep schools is proof of that.17 So far the complete list of messages I've picked up from cities is: wealth, style, hipness, physical attractiveness wouldn't have been a total immersion. Don't just do what they tell you to do. But advancing technology has made web startups so cheap that you really can get a portrait of the normal distribution of most applicant pools, it matters least to judge accurately in precisely the cases where judgement has the most effect—you won't take rejection so personally. If raising money is hard.
There is no sharp line between the two types of startup ideas: those that grow organically out of your own life, and those that you decide, from afar, are going to get rarer. While some VCs have technical backgrounds, I don't know enough to say, but it happens surprisingly rarely.18 Most subjects are taught in such a boring way that it's only by discipline that you can never safely treat fundraising as more than a startup that seems like it's going to stop.19 It sounds obvious to say that you should worry? One reason startups prefer series A rounds? When I was in high school either. If you feel you've been misjudged, you can do. Google. Of course, someone has to take money from people who are young but smart and driven can make more by starting their own companies after college instead of getting jobs, that will change what happens in college.
Notes
Though they are themselves typical users. But it takes to get good grades in them to private schools that in three months, a valuation. Giving away the razor and making more per customer makes it easier to get them to stay in a time machine.
Apple's early history are from an angel investment from a mediocre VC.
In the beginning.
Plus ca change. But on the other.
And that is exactly the point of a stock is its future earnings, you now get to go behind the scenes role in IPOs, which allowed banks and savings and loans to buy it despite having no evidence it's for sale.
However, it will seem dumb in 100 years. Digg is Slashdot with voting instead of blacklist.
Sofbot.
I write out loud can expose awkward parts.
I've become a so-called signalling risk.
Hint: the way they have because they couldn't afford a monitor.
And it's particularly damaging when these investors flake, because there was a new search engine is low. They have no connections, you'll find that with a wink, to take care of one's markets is ultimately just another way in which income is doled out by Mitch Kapor, is to raise money after Demo Day, there would be easy to discount, but I'm not against editing. As one very successful YC founder told me they like the one hand and the exercise of stock options than any preceding president, he tried to shift back. At three months we can't believe anyone would think twice before crossing him.
Progressive tax rates has a significant startup hub. He, like speculators, that alone could in principle 100,000 sestertii apiece for slaves learned in the early adopters you evolve the idea is crack. As we walked in, we love big juicy lumbar disc herniation as juicy except literally.
It's sometimes argued that we didn't, they thought at least accepted additions to the modern idea were proposed by Timothy Hart in 1964, two years, it was cooked up by the National Center for Education Statistics, about 28%. I've come to accept that investors don't like the bizarre consequences of this essay talks about programmers, but I know of no Jews moving there, and should in some ways First Round excluded their most successful startups are competitive like running, not the original text would in itself deserving. This is not whether it's good enough at obscuring tokens for this type are also several you can't even claim, like play in a city with few other startups, because time seems to pass. Please do not try to avoid that.
This kind of people starting normal companies too. If Ron Conway had been raised religious and then using growth rate to manufacture a perfect growth curve, etc, and then a block or so.
But it is to trick admissions officers. I meant. The mere possibility of being harsh to founders. As he is at fault, since 95% of the class of 2007 came from such schools.
I started doing research for this purpose are still, as they are now. There was no more unlikely than it would be easier to say that it is dishonest of the next round, that suits took over during a critical point in the usual standards for truth. Wittgenstein: The French Laundry in Napa Valley.
It wouldn't cut their overall returns tenfold, because they wanted, so the best ideas, they mean statistical distribution. The original Internet forums were not web sites but Usenet newsgroups.
A doctor friend warns that even this can give an inaccurate picture. At some point, when the problems you have no idea what's happening till they also influence one another directly through the window for years while they think they're just mentioning the possibility is that in Silicon Valley. I find hardest to get rich by creating wealth—wealth that, isn't it? Look at those goddamn fleas, they have less money, the big winners aren't all that matters, just as if you'd invested at a famous university who is highly regarded by his peers.
Compromising a server could cause such damage that ASPs that want to pound that message home. He, like arithmetic drills, instead of blacklist.
Thanks to Tim O'Reilly, Peter Norvig, and the guys at O'Reilly for inviting me to speak.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#ideas#startups#Pincus#liquidation#school#stock#sup#work#machine#li#money#math#yuppie#VCs#century#democracy#tax#interests#difference#plan#wink#investors#founder
1 note
·
View note
Text
[old] guidelines
// these are my original rules. though they are still generally relevant, my newer, shorter, more concise rules post is here
A love letter from me to you! Please take it to heart.
The Lowdown:
mod is an artist & supportive af|selective|primarily plot-motivated|operates on mutual respect|your friendly rpc fairy godbitch; gimme your wishlists|zero tolerance for OC negativity & bigotry|triggers present|18+ content present|consistent but occasionally capricious activity|OOC communication appreciated|lots of love abound ♡
Mod Sal (they/them/theirs; 24; PST)
I study medicine and social justice with emphasis on emergency medicine and sex work, respectively. In addition to being a writer I’m also an activist, artist, and scholar. I’ve been writing Bel since 2015. She’s a very intricate and highly dynamic character who has gone through many changes over the years via her interactions. I look forward to developing her even more with your muse(s)!
Before I talk about the kind of conduct I’d like on my blog, this is the type of roleplayer and friend I aspire to be. I’ll strive to be as attentive and supportive as I can about your muse, ideas, as well as ooc presence. If we’re mutuals, you can expect plenty of inboxes, tag games, headcanons, relationship tags, to be tagged in & sent posts relating to our muses, general interaction, and emotional support proportional to the depth of our interactions when I’m online. I’m an unapologetic 1-person hype squad at heart and will do my best to spread the love and return the love I get.
If I’m not around here, you can find me on my snk blog and/or discord by request. I muse Eren and Levi as secondary muses, but they won’t be nearly as active as Bel and are only available to established mutuals. I also have untagged resource & nsfw musing side blogs.
Interactions
When it comes to interactions, nothing motivates me more than an eagerness to develop our muses’ relationship. Depending on what works best for you, we can work on this via inbox submissions, plotting, or simply interacting. I have a tendency to write para/novella-length replies, but will strive to match you in length and style. Please include something I can actively respond to in your reply, because neutral replies can be very difficult to build upon, and please do not godmod her based on assumptions and/or stereotypes about her character/profession.
With regards to ask responses, please feel free to turn them into threads by tagging me in a new post and cutting your replies. I’ll turn asks into threads if they inspire me, but you’re under no obligation to continue them if you’re not as motivated. When cutting, please don’t cut me out. Also, please don’t reblog asks with your reply or reblog replies with my tag if I don’t reply quickly enough. I track of all my threads to the best of my ability, so please check there first if you want to know the status of our thread. If I’ve missed a thread of ours, please help me out by sending it to me in a message so I can add it to the tracker. If you lose muse for a thread, please don’t feel pressured to continue it. We can always take a break or start something new. I don’t cap my threads and am always open to new interactions.
Selectivity
Though I run a selective blog, I am not very selective in nature. I do have a preference for original and SnK/AoT characters, especially those that inspire me and challenge me. I’ll primarily look for interactions by checking blog rules for oc-friendliness, reblogging promos, asking to be mutuals in the tags, then follow back after that initial follow is granted. If you don’t want me to follow you, please block me completely because otherwise I’ll think it’s a mistake/glitch and follow you again. On the topic of glitches, they do happen so I apologize ahead of time if that happens above or below my radar.
I don’t tolerate oc-negativity or ooc bigotry and will handle my blog accordingly. If you align yourself in any way with TERF, SWERF, homophobic, ace-exclusionary, racist, and/or xenophobic rhetoric, please do not interact. It’s important for me to surround myself with enriching content and community. I have boundaries and will be setting them for my own comfort as well as respect yours because mutual respect between muns is key to a healthy rpc.
Sourcing
Please don’t do it. This goes for starters, ask memes, wishlist posts, and wanted connections. I understand we might not be the muse/mod duo you have in mind and that we don’t fit every situation, but please don’t fill my notifications with this sentiment, especially if we don’t have any established interactions yet. If our blogs have that much in common, there’s so much we could be musing about. If this happens excessively without us having any interactions, I’ll unfollow and/or block because I am a roleplay blog, not a resource hub. If you’re interested in my musing/resource posts, please show interest in muse interactions as well. The latter is why I’m here and there’s nothing more disheartening and discouraging to my creativity than being used and/or ignored when I present things.
Original Character Disclaimer
It pains me that something like this needs to be said, but Bel wasn’t created to force ship with your muse and/or overpower our threads. I will absolutely under no circumstances tolerate any form of OC negativity. I don’t care if you think they’re “cringey”, “underdeveloped”, “overpowered”, or any other iteration of not meeting your personal criteria of a good character. Opinions are valid but unsolicited bullying is not. It is important to realize that canon characters are still original characters bar their capitalistic franchise. The mods of original characters are a goldmine of free and original content and deserve to be judged by conduct, not content.
If you’d like to support OCs, I invite you to scroll through and reblog a thing or two from my OC positivity tag, as well as follow and engage in meaningful interactions with the OCs in your orbit. Your encouragement could be what makes a content creator’s breakthrough, so please be kind and supportive. Saying you’re OC-friendly while providing an extensive grocery list of double standards OCs must abide by to be considered acceptable isn’t OC-friendliness. Likewise, musing an OC doesn’t automatically make you incapable of being exclusive (unintentional or not) so please be cognizant as well and lets support each other.
Shipping
That being said, I’m just like every other mun. I enjoy shipping and the occasional smut scene given the chemistry is right and both muns are equally invested in the relationship as well as comfortable with it. The more we develop our muses, the more complicated their relationship will be and the more likely I’ll personally gift you with fanart. Above all, your comfort is paramount to our interactions so please communicate with me. Likewise, please respect my comforts when I speak of them. I am much more likely to be enthusiastic about shipping than Bel is, however, so please be patient with us and respect her boundaries as well.
# FREE THE FPN . SFW // ONLY IT’S NOT
This is the tag I will use to mark sexually explicit content. Bel is somewhere on the ace spectrum, but is nonetheless a sensual character and has a couple verses that engage in sex work. Bel’s struggles with her identities are a very big part of her personal characterization, so please be patient with her. [Marilyn Monroe’s hinted asexuality] Likewise, if she’s not into your muse, please don’t push such interactions unless we discuss them as a plot element.
Trigger Warnings
The SnK universe is rampant with violence, gore, psychological trauma, profanity, and grey morality. Furthermore, I enjoy writing dark themes and will provide the disclaimer now that this may be a rather trigger-heavy blog. However, that doesn’t mean you have to be subject to all these themes. If you’d like me to tag things in a certain way, please don’t hesitate to let me know because your comfort is important to me. I’ll gladly create a new tag for you to blacklist/filter and add it to my tag list. Furthermore, this blog will have the occasional explicit content so please don’t interact if you’re under 21.
Activity
I’m finishing up my bachelor’s so classes and coursework will keep me from here sometimes. Furthermore, I struggle with mental illness and domestic abuse in my home environment, so bouts of these may also pull me from activity. I’ll be doing my damndest to keep my issues off the dash but if things are especially severe and I feel the need to post about it and/or reach out, I’ll use a semicolon tag (#;). Nonetheless, musing, roleplaying, and plotting helps keep my spirits up so please keep me updated with your muse and share your discord with me, if you’d like. I’d love it so much if we could continue developing our muses as I slip off of and find my way back to tumblr, and I’d appreciate you very much as a writing partner and friend. ♡
Accessibility
I’m not very savvy with code, but I do try my best to keep my blogging accessible as I tinker and learn. If you struggle with accessing any part of my blog, let it be font size, style, or anything else, please let me know and I’ll do my best to accommodate because I don’t want to perpetuate elitism or ableism in the rpc. As far as reply formatting goes, I’ll usually stick to once small text (particularly in novella length replies via ctrl shift -) and spare use of italics, bolding, and strikethrough text. I may use unicode and/or zalgo for art captions, personal musing posts, crack threads, and other posts that call for it. Every once in awhile, I will blog from mobile and as a result post text in default size, but I’ll still cut my posts and at worst, separate our replies with a symbol or icon if I can’t blockquote text through html.
Permissions
One of my favorite things about roleplaying is sharing content and playing tag games. If you come across anything that reminds you of Bel and/or our interactions/plotting, please show me! Even more so, if you’re a content creator, you have complete and total freedom to use her and her inspirations in your work. I only ask to see it! Likewise, if I ever create any art for you, please acknowledge it at the very least. If you send in an art request and I deliver, please reblog it. Failure to do this kills my creativity as well as generosity so... please.
Exclusive to this blog are my own art and edits as well as those gifted by friends. Please don’t ransack our labors of love and re-purpose them as your own. Bel’s Iva & Marie icons were collected by yours truly with a beautiful frame made by Shane. Other people who have contributed their talents throughout the years include madcapraccoon, L, desertbl00m, Eris, Justice, sangre-rebelde, emptyolivejar, desimouse, and the many rp blogs that have interacted with her. I’d also like to give a special shout-out to sjokohama for the boundless enthusiasm given to her development as well as the readers who have enjoyed and left amazing comments on her original fanfiction. She wouldn’t be out here if it weren’t for Y’all ~ ♡
If you feel like something should be added to or clarified in these guidelines, please let me know. I realize I have a lot to say as a consequence of being here for so long, but I still want to keep my conduct as transparent and accessible as possible.
Thank you for reading! Please feel free to like this post and interact ~ ♡
8 notes
·
View notes
Text
2017 is ending ! and so should this bullying & negativity !
2017 has been a tough year on everyone. Regardless of where you live on this globe, we’ve all suffered in one way or another. From the US election to Brexit, from the terrorist attacks in London and Manchester to the ethnic cleansing in Myanmar. We’ve survived hurricanes and tropical storms in Texas, Florida, Puerto Rico and the Philippines. The mass shooting in Las Vegas. Even now in the height of Christmas season, California’s fires burn on. Palestinians are being illegally arrested, detained and displaced every day. Not to mention Net Neutrality battles in the US and Canada. No matter where you might be, something has affected you.
And outside of just the world news, the RPC has dealt with many things. We’ve seen hate crimes and suicides. Toxicity and bullying beyond belief. Ageism and accusations. There’s been so much hurt that the community has inflicted upon itself. So here’s a list of things that the RPC can work on in 2018.
AGEISM. Fandom is a place for people of all ages. It’s not just for teenagers and not merely for adults. This is applicable for both sides. There’s so many people who say “ Don’t talk to me if you’re under 18 ! Stop lying about your age ! “ and similarly there are others who say “ You’re too old for this fandom ! Focus on your own life and get your own hobbies ! “ What both of y’all need to understand is that roleplaying is a collaborative activity. And not only that, it’s such a large community that you could easily just go from one blog to another. To damn a whole age group for an individual experience is toxic and close-minded. Those who are underage still have a place here-- because it probably figures that you were online when you were underage. And for those who are underage, don’t get yourself into activities that could easily get the other party into legal trouble. Respect each other’s boundaries; and if you can’t play nicely, don’t play at all. There are so many variations of characters, of fandoms, of portrayals that you can very easily just... move on elsewhere. Do that, and do so quietly.
ANONYMOUS HATE. Or even, just hate in general. It should just be a rule in general: if you don’t have anything positive or constructive to say, don’t say it at all. It’s not that hard to just move on to another blog. If it makes you uncomfortable to see someone on your dash, unfollow them. Still there? Blacklist them. Tumblr Savior gives you the option to remove the banner that notifies you if an item has been hidden from your dash. It’s like they’re not around at all. Afraid they’ll message you? Block them. And one additional option would be to speak up if you can be non-spiteful about your message, clear the air, and go in peace. No reason to just be nasty to people.
PASSIVE AGGRESSIVE NEGATIVITY. I’m not counting vaguing because sometimes you need to be able to let people know about a situation without being too in detail: it can be a cry for help without being too obvious. But I mean just stirring the pot to see what will come of it. Just saying something negative to someone like “ No one cares about x ” or “ You know you should really do this or otherwise x. ” It’s childish & it shows a lack of accountability. People will ask for your opinion when they want it: otherwise you can probably keep it to yourself, or move on if the blog no longer suits your interests. No need to harass someone out of some sick sense of entertainment or pride.
ACCUSATIONS. Get both sides of the story, understand the situation, make informed decisions. And then, once you do, keep things to yourself. You can warn your friends or something privately if you have a concern about someone based off of personal experience, but rumors spread so fast around here. Even if something is proven to be true, like say someone is bullying or being abusive, and they’re still active? It’s not your responsibility to continuously bully them about it. If you’re so concerned, contact an authority figure. If you know Tumblr Staff isn’t taking it seriously enough, then contact your local authorities-- online bullying is a serious thing that police are supposed to take seriously. If you think you have a real case-- or heck, even if you’re worried? Get serious and contact someone. Otherwise, if you don’t have any evidence to back up your accusation, or you’re just tagging along, you’re just another part of the problem. You are contributing to an unhealthy online culture.
SHAMING. There’s a trend of claiming people are into pedophilia and bestiality, or even go on to call people rape and abuse sympathizers. That is not okay! At all! Some people write content to cope over something that occurred in their private lives. Some people want to experience writing something outside their comfort zone or daily lives. Some people are interested in experimentation. Whatever the cause may be, that’s no reason to call people anything. Do you not realize that if these victims-- yes, victims ( because that’s what they are ) could easily report you for abuse, and if inclined sue you in court for defamation of character? Because that’s what you’re doing, publicly slandering someone’s name out of something you personally don’t feel comfortable with. Don’t like someone’s interests? It’s probably tagged-- meaning you can blacklist it. Still uncomfortable? Chances are that there’s someone else who writes a similar enough style or character-- so unfollow. What authority do you have to blaspheme someone for the content they produce on their blog in their own space in their own comfort in their own time if it’s not hurting anyone else in the process?
FACECLAIM / POC BASHING. Which I think is a really interesting phenomenon because most of the time the people who call others out for their choice in face claim aren’t even of the race themselves? The idea of the faceclaim is to have that person pick a public face that matches the portrayal of the fictional character they’re writing, usually of an animated background. And it’s also gross to tag someone else to bash another person for you? I’ve been asked to publicly call out someone on their choice of FC-- and that’s disgusting. Don’t bully someone ‘cause of a personal preference. And if you’re trying to “ stand up “ for POC, which is what I assume this is supposed to be... you should probably just ask a POC what they think of the situation. But be prepared to like consider your thoughts wrong: ‘cause sometimes what you consider correct just... isn’t. I was asked to call out several people on “ white washing ” WOC, and honestly POC don’t come in a cookie cutter model...
This isn’t to say I don’t appreciate the faceclaim resources made available: because those allow someone to make a valuable educated decision on a choice as opposed to a random Google search.
But like, it’s not necessary to harass anyone over what you think might have triggered your radar. Instead, you could start a discourse without accusation, politely ask how the person made that decision, & then like if you don’t agree with the moral / ethical decision of that person idk, move on.
DUPLICATE HATE. Discomfort is acceptable: and you can unfollow or blacklist or block, whatever you need to do to distance yourself from a duplicate should you feel uncomfortable with them. But under no means necessary is it necessary to bully, abuse, harass, slander or otherwise attack another person for sharing the same muse as you. Because unless it’s an OC, you don’t own rights to that character anyway, and the only person who has the authority to tell someone not to write a character is the person / company who owns the creative rights. If you’re not pleased with someone else’s portrayal of your character? Focus on your own, make it the best it can be. Produce the content you’d like to see about ‘ your ’ muse. Stop deflecting responsibility onto everyone else.
I am sure there’s plenty of stuff I’m missing out on, but these are things I’ve seen a lot over the year & while it’s probably a dream, I’d love to see change in 2018. But I think change begins a person at a time, and it begins with us. If this at least opened your eyes a little, then I’m glad. Let’s make this next year a better one.
#[ ʏᴏᴜ ʙᴜʀʏ ᴀ ʟɪᴠɪɴɢ ᴘᴇʀsᴏɴ ɪɴ ʏᴏᴜʀ ᴍᴇᴍᴏʀʏ ] // oυтoʇɔнɒяɒ#[ ʏᴏᴜʀ ᴛᴀsᴛᴇs ᴀʀᴇ ᴏɴʟʏ ᴛʀᴇɴᴅs ] // qƨɒ#long post //#ok to reblog !#2017 was rough for everyone ok.#but like no need to make things any rougher for anyone else.#this community would be a lot better if we all could respect one another. or act like it.#& i got bullied this year too and it was super shite?#i'm very anti bullying & i knew i wanted to say something about it eventually.#this just seems like a great opportunity to.#have a good holiday though okay??#feel free to share or ask questions !
285 notes
·
View notes
Text
A Sincere Request
Dear Tomarrymort fandom,
Before you read the following post, please do keep the following three things in mind:
1) I am neither close to Asa nor am I speaking on his behalf
2) I neither can nor want to judge whether he is guilty or innocent
3) I neither condone doxxing nor child grooming
Now, why am I speaking up regardless, especially when I do not want to be involved in any kind of drama? The reason is that I've been the target of a smear campaign not too long ago in which I was wrongfully painted as an emotional abuser in result to me ending a mutually toxic friendship with a so-called 'fandom celebrity' and which was extremely damaging to my mental health.
Due to these personal experiences, I have noticed some patterns that have been greatly worrying me, and while I – again – do not wish to prove the innocence of a person I barely know, I would like to ask any reader of this post to listen to both sides and consider as many factors as possible before assuming any kind of stance on this issue.
What has been eerily similar to my own treatment when my reputation was being systematically destroyed is that my harassers refused to engage in any kind of dialogue with me before making the aforementioned claims about me. Instead, they collectively blocked me and convinced the admins of any fandom events to ban me from participating. If they saw me talking to an up-until-then neutral person, they immediately approached said person, which resulted in them blocking me without even listening to my side. It was very obvious that they did not simply want me gone from their personal corner (which would have been perfectly valid as this particular feeling was mutual), they wanted to bully me into leaving the entire fandom.
In Asa's case, the same thing happened: Those accusing him did so without giving him the chance to defend himself, and, rather than leaving him alone after getting him to leave their 'personal corner' (aka CoS), there have been further public accusations followed by an attempt to exclude him from the WIP Big Bang as well. What is especially concerning in his case is that nobody personally wronged by Asa has been directly involved in these accusations. Instead, it has always been others speaking on their behalf, and in the case of the child grooming accusation, it is uncertain if a victim actually exists.
Another similarity to my own experiences is that everyone close to Asa has been punished for his crime as well by having their username revealed and being included in the call-out post. Popular fandom members have explicitly stated that they don't want to have anything to do with anyone still on good terms with Asa, which puts a lot of pressure on less popular creators in particular: If simply talking to Asa or being on his side means that they'll be blacklisted by association, they have to sacrifice their reputation and the small support they've been receiving simply because they do not want to accuse Asa of something without being aware of all details. Even if it turns out that Asa is, in fact, guilty of what he's been accused of, this leads to a major logical flaw, namely the wrong belief that being friends or on good terms with someone means that one condones everything they do and/or that one is guilty of the same things. The only actions any adult is responsible for are their own, and to claim otherwise is bullying. Regardless, it's not uncommon for a person to scold their friends for doing what they believe to be wrong in private, hence there is something very questionable about treating Asa's friends or good acquaintances as accomplices for that reason too.
Lastly, I would like to say that, while I personally wouldn't have discussed sexual topics with a minor, there's a difference between doing so and 'child grooming'. What we need to consider is that the age of consent differs from country to country, meaning that the age of consent in the US does not reflect any universal truth or morals and that the debate surrounding the question of when a minor is mature enough to discuss and/or engage in certain activities is still on-going. With that in mind, let us ask the following questions in regard to whether actual 'child grooming' has taken place:
1) Did Asa engage in sexual roleplays with any minors
2) Did Asa encourage minors to meet up with him, show him any revealing pictures, and share any details they did not (want to) share on their own volition or did the minor(s) seek him out?
Again, I don't know the answer, so this is for those knowing more than I do to judge.
On AO3 and many other sites hosting adult content, all a minor has to do if they want to immerse themselves in sexual content is to click a single button to confirm that they are 18 without having to provide any kind of proof, so the people running those sites themselves don't face any legal problems. If they truly cared about preventing minors from accessing that content, they would have implemented additional measures such as making them enter their passport ID in order to unlock said adult content, which is actually what a smaller community I used to be a member of did. For that reason, I would like to ask anyone reading this whether they condemn the actions of sites like AO3 and co just the same, and whether they aren't just accusing Asa of child grooming because they want to 'justify' their dislike (or hatred) of him.
I will not end this post with a request to defend Asa or believe in his innocence as I myself don't know enough about him or his server to form an educated opinion. However, I would like to remind this fandom of how dangerous wrongful accusations are and ask you to question what you read and think independently before taking either side.
In my case, the smear campaign that had been run against me resulted in people, my ex-friend in particular, believing that they had a freepass to do to me whatever they wanted to. This included writing literal hatefics about my rarepairs in which they killed the character they associated with me as a nice public 'inside joke'. I do not believe I have to elaborate on why this was detrimental to my mental health.
Again, why am I saying this? Naturally, this means that, if I see anything similar happening to Asa (aka people publicly ridiculing him or his ideas in a way unrelated to this drama), I, as well as any other neutral observers will know that none of these accusations are truly about justice.
---
For the sake of my own mental health, I would prefer to remain semi-anonymous, and not get involved further. However, if my credibility is being doubted, I will reveal my identity to a few select people I trust, so they can confirm that I’m not speaking on anyone’s behalf.
0 notes
Text
All right, fronds, Tor has announced that starting August 22, they’ll be posting Oathbringer chapters! This is terribly exciting for people who want to read the preview chapters, but for people like me, who want to wait and savor (and liveblog) the whole book at once as opposed to piecemeal and spread out over several months, it’s kind of a source of anxiety...
I know that I’m going to be dodging spoilers for almost three months now (thanks, tor). And while I would never want to dampen people’s enjoyment of the preview novel chapters, I’m adding my request to the pile of people saying, yo please please please tag your spoilers!!!
Aaaaand as much as I love tumblr, it can be kind of...a complicated endeavor making sure that posts end up where you want them--or don’t. So here’s a friendly review of how to make sure spoilers don’t end up where people who don’t want to see them...won’t.
Read mores are your friends. That little line makes everything so, so much easier to avoid. Read mores are your friends.
Wait until the fifth tag. Here’s one of tumblr’s less well-known features: only the first five tags on a post will show up in the public tag. So if the FIRST tag you put on a post is #brandon sanderson, that shit’s showing up in the #brandon sanderson tag. BUT if you put #one #two #three #four #five #brandon sanderson, (or similar “junk tags”--I tend to use // marks), then we’re all safe. It won’t end up in the tracked tag and it’ll be easier to avoid spoilers in the public, tracked tags. You still maintain organization on your personal blog, because it’s still in YOUR #brandon sanderson tag, but you won’t ruin someone else’s day by having it show up in the public tag with spoilers attached.
The first five tags work the other way, too! No one wants to scream into the void and not get a response--I’m on board with that. So somewhere in your first five tags, put #oathbringer or #oathbringer spoilers or even #stormlight archive spoilers. That way, people reading the preview chapters have a place to go to interact with other people reading the preview chapters, and people who want to go into November fresh and clean and unspoiled can still check the regular SA and Bsandy tags without fearing they’ll get spoiled.
Don’t put reactions in the tags. A lot of people have blacklist settings so that even if a post is blocked, the tags still show up as readable--this makes it easier to see why things were blocked, but it also runs the risk of tags like “#omg and then JASNAH did the THING and I DIED” spoiling even tiny things. Keep tags for...well, tags for a few months, and add additional screaming or reactions to the bottom of your actual post.
Discord and Mibbit are your friends. The nice thing about both messaging services is that you can set up different chats and servers that are subsets of the regular ones. So make a spoiler chat separate from the regular, spoiler-free chat, and go wild.
TAG EVERYTHING! Even if it’s a meme or a stupid shitpost or a vagueblog or something that doesn’t seem like it’s spoilers--TAG IT ANYWAY. If it’s even tangentially related to Oathbringer, TAG IT. Especially memes, tbh. Memes are insidious, and often innocent, but with a closer look, they reveal more than they might have intended. Tag literally everything, even if you don’t think it’s spoilers, even if you think it’s annoying. Those of us avoiding shit will thank you.
KEEP tagging stuff, even after the book is released! Maybe you read the preview chapters and so you’ve got a 300-page headstart, or maybe you speed-read, or maybe you took time off from work just to read, and maybe you finish two days after the book comes out. Keep tagging spoilers. Some people read slower, or have time commitments or work keeping them away from the book, or simply read a few chapters a day to savor it, or want to read faster but can’t because they’re liveblogging it (hello, fronds!). But just because you are finished doesn’t mean everyone else is, and continuing to tag for spoilers is super necessary, even six months--or longer--out from the release date.
All right, I hope that didn’t come out as patronizing or anything. I’ve just found that an occasional reminder of the ins and outs of tumblr’s more useful systems can be super helpful, especially if it’s stuff that newer users might not have encountered yet, like the fifth-tag-rule.
ANYWAY, for everyone starting with the preview chapters, ONLY SEVEN DAYS UNTIL OATHBRINGER!!!! Those of us waiting the remaining 90 days until November 14 thank you in advance for tagging your shit. <3
....shit, 90 days? that’s closer than I thought it was.....guess, I need to get a jump on my WoR reread!!
#Brandon Sanderson#Stormlight Archive#cfsbf#Oathbringer#Cosmere#this has been a public service announcement#y'aaaaallllll it's so close I can taste it#can't wait to start that good good liveblog#but seriously: tagging shit is so so important#please understand#I will love you forever if you keep your spoilers from me#thank you#op#spoiler etiquette
195 notes
·
View notes
Note
ooc, please. why do you continue to bring up Cliffjumper if you know it hurts people. i understand Starscream doesn't care. i'd wanted to *make* him care, at least a little bit, or make him understand why it shouldn't be something to brag about, but i failed, even though i've seen other anons get him upset about things using the same tactics. i'm upset and i guess i want/ed him to be too. but i can't help but feel like you don't particularly care either...
I bring up Cliffjumper because it is in character to do so, and frankly, because it’s funny. I’m assuming you’re referring to the post with the glowing blue nails and my little addition? I’m not sorry.
Let’s address your points one by one. No one will ever make Starscream care about what he did to Cliffjumper. One day he’ll probably grow bored of bragging about it, and more importantly, he’ll have other accomplishments that he’ll gain more satisfaction from, and that others will validate. But for the time being, yes, he does find it worth bragging about, because it was the last thing he did while he still had some measure of control in his life, when he led the Decepticons right before Megatron returned and undermined him as both a leader and a person once more. Is that healthy? Nnnnnnope! It’s a maladaptive coping mechanism, such as when people become compulsive hoarders after a severe loss. It’s grasping to hold onto a feeling of power or control. Yes it’s messed up. Don’t know if you noticed, but Starscream is pretty darn messed up. He does a lot of bad things and feels no remorse. He can justify nearly anything to himself, and firmly believes the ends justify whatever underhanded means he feels he must resort to.
The other anons who have upset him have brought up things he is already upset over but usually pushes deep down and doesn’t think about, like the loss of his Trine and Vos, or his broken friendship with Jetfire. Trying to get him to feel bad over something he is ok with, and especially something he’s proud of, won’t work. Getting him to sympathize with another person’s loss by comparing it to his own is a total dead end. First, he does understand how Arcee feels and thinks she’s ridiculous to be so open about it. In his world, that’s asking for people to hurt you worse. He never once spoke of any his unfathomable losses the entire time he was in the Decepticons, because he’d be eaten alive. Does he care how she feels? No, he doesn’t. People hurt each other. Enemies have no reason not to. That’s war. That’s how you win and survive. Second, as he explained when you brought up his Trine, he knows other people find the deaths of their enemies - his friends - quite satisfying, and all that does is hand him the moral high ground about Autobot hypocrisy. He’s slippery and manipulative, and will absolutely use that to deflect criticism from his own lack of remorse. Third, he’s extremely self centered and likes to wallow in self pity, and firmly (and frankly, rightly) believes other people’s losses are nothing compared to what he’s suffered. Does that mean he has the right to be an asshole about it? Of course not. He should at least find some speck of compassion even if the scale of the loss is different, but he’s not going to, because he’s a self centered asshole.
And as for me? No, I don’t particularly care about Cliffjumper or what happened to him. Sorry, I just don’t. The writers never gave me a reason to, besides telling me how I was supposed to feel. He was literally a red shirt who died to show how serious the bad guys were. I was much more excited to see a villain who didn’t waste time arguing or holding a prisoner who would be rescued, but instead took him out and moved on with his business than I was sad over some random character who I found cocky and annoying the whole five minutes he was in the show. I did feel bad for Arcee, at first, before she kept going on and on and on and on about him just as annoyingly as Starscream, but I didn’t feel bad for Cliffjumper himself. I didn’t come to care about him as a character or want to see more from him. Later, when I played Fall of Cybertron, and actually got to know CJ, I did feel kind of sad that he was killed, but not nearly as sad as I was over Breakdown, or even Dreadwing. I was slightly more sad about Cliffjumper than I was about Skyquake, which is not much. At all. Because neither of those characters was developed enough for me to see them as more than the plot devices they were. If writers tell me how to feel but don’t take the time to really sell it by showing me something about the character, I’m pretty much gonna do the opposite of what they tell me.
I do know CJ’s death hurts people, I know Starscream bragging about it hurts people, and I do care about that because I care about people. But if you follow a TFP Starscream blog that’s what you’re gonna get. No one’s forcing you or anyone else to follow me. You think I don’t know the bad treatment of a character hurts people? I love Starscream, so don’t talk to me about hurting. I’ve cried over him and lost sleep over him, and sat side by side with people who were laughing at the scenes with him that broke my heart because he was so scared and helpless and humiliated, all for laughs. I’ve had nightmares about him after I saw Predacons Rising and woken up crying. I’ve blocked more posts and blacklisted more tags than I care to count. I have unfollowed 2 blogs - one Shockwave and one Predaking - because of how casually and graphically their characters discussed murdering Starscream and I couldn’t handle it. Key word - I couldn’t handle it. So I unfollowed in order to keep myself comfortable. Did I expect them to change how they played their characters? No. It’s their blogs and they were just acting in character. It was damn good writing, as is mine.
I’m considerate of Cliffjumper fans, and I never put his name in the tags on my posts in the first 5 tags, so Starscream’s obnoxious bragging won’t show up in the Cliffjumper tag. I tag my CJ related posts “we all know what happens to redshirts”. If that’s too long or too flippant, I can add a tag for you that you can block. If what I was writing in character upset you, you could have mentioned it to me out of character and asked me to tag it. But you sent in character asks and I responded in character. You weren’t able to manipulate Starscream into feeling a certain way in order to give you some comfort, because it’s not his job to comfort you, and frankly I had no way of knowing you were actually bothered. I will always tag things when asked over IM or even an anon ask. Beyond that, I’m not changing how I run things and I make no apologies, for me or my asshole birb.
#Anonymous#asks#mun stuff#writing stuff#rp stuff#long post#text post#we all know what happens to redshirts
23 notes
·
View notes
Text
FUQ
That stands for Frequently Unasked Questions because people rarely ask me any of these so FAQ would be a lie.
Q: Sempai, how do I get you to notice me?!
A: Send me a message or ask! I don’t have to be following you to do so! Also, don’t be shy to tell me about some content you think I might enjoy. I basically only follow people who tag descriptively. Generally this means, at minimum, fandom, pairings, and marking explic!t content. I don’t have any triggers, but I do have some strong squicks, and I look to be able to filter those out as well.
Q: You used to follow me and now you don’t, did I do something wrong?
A: Almost certainly not. If you don’t usually tag your Tumblr, that’s probably the reason why I unfollowed, so don’t brood any more than that. I follow a lot of blogs and I rely on people tagging well to help my blacklist keep up by filtering out shows I don’t watch and content I don’t want to see. I’m not angry at you for not tagging--it’s your blog--but if I can’t figure out a filter to keep stuff I don’t want on my dash, I unfollow.
Tumblr also glitches a lot. I have been on both sides of a Tumblr-induced unfollow. If I used to follow you, now I’m not, and you tag well, message me to check in! It’s totally possible I don’t realize that Tumblr made me unfollow you. Fuckin’ Tumblr, man. I’m also always willing to explain an unfollow if you want to know why.
Q: Why did you block me?
A: Almost everyone I’ve blocked is because they blocked me first, so uh, check that first of all. If you’re a fairly block-happy person, maybe you don’t even remember doing it. I block anyone who I discover has blocked me. If you no longer wish to block me, you can reach out through another person or perhaps an anon ask to tell me that you want to be cool now and we’ll be cool. Simple as that.
I’ve also preemptively blocked people who expressed an explicit desire not to interact with people who ship my ships or have my opinions. Eg, making or reblogging a post that says “kaka//saku do not interact”. These blocks are my attempt to make YOU comfortable. I respect people’s desires to curate their Tumblr experience. If you think this may be the reason I blocked you and you are ok with me interacting with you, reach out to me through a third party and I’ll unblock.
Another possibility is that you’re a troll who has left me or one of my friends a personal attack, uses slurs, etc. Have you done that? Don’t be like that.
Third possibility is a mistake--I’ve mistaken you for a spam bot, or Tumblr has done something wonky, etc.
Q: I ship your NOTP. Do you hate me?
A: Why would I hate you just because you have an incorrect opinion of whether two fictional characters should rub their genitals together? No. I don’t hate you just because you ship my NOTP, and you are completely welcome to follow me, message me, etc.
Q: So Sasu//Saku is fine then right and it’s just a matter of taste?
A: Haha no canon ending SS is garbage, let’s not get carried away here, I’m just saying I think you can ship it and still be a good/nice person. Just because I don’t shipper bash doesn’t mean I can’t and won’t point out everything that’s wrong with SS as written in canon. This is called “literary criticism” and “critical engagement with mass media” and is something I won’t apologize for enjoying.
Q: LMAO why do you care so much about a cartoon for teenage boys?
A: Two possible answers here. One is that you can ridicule basically any hobby or special interest this way--”why do you care so much about some overpaid men kicking around a ball”, “why do you care so much about two needles and some yarn”, “why do you care so much about a tiny plastic train going around a track”. It’s called entertainment, bitch.
Second answer is, my God! If there’s any segment of society that I don’t want uncritically reading stories that reinforce sexist ideas and give abusers carte blanche, it’s teenage goddamn boys. If my little drop in the ocean makes the slightest difference against that, I don’t consider it wasted time.
Q: I do assholish things like tell people to die for shipping the wrong thing but I ship one of your OTPs. We cool right?
A: 🎶 don’t stand, don’t stand so, don’t stand so close to me 🎶
Q: I have a squick or trigger, will you tag it for me?
A: I will do my best! Send me a message or ask. You don’t have to explain why you don’t like it.
Q: You have a lot of weird tags, do you have a tagging system?
A: I do! It’s a bit complex, but in addition to commentary tags (stuff like “too cute” or “i’m crying in the club rn”), I try to tag descriptively for blacklists.
For original content, I usually post character names in several different forms for the benefit of tag search, eg both “Kakashi” and “Kakashi Hatake” and “Hatake Kakashi”. I also tag with the original artist’s name (if it’s a repost or translation), and “creative commons” or “with permission” depending on whether I was following a usage policy or explicitly got permission from the artist.
For reblogs, I only tag character’s first names, generally.
My meta tag is “naruto analysis”. My typesets tag is “my typesets”. My fanfic tag is “my fanfic”.
I try to tag triggers like “alcohol /” and “blood /” with the slash at the end.
If a piece of art could be interpreted as romantic or platonic, I usually tag with both the character names and the ship name. If it is unmistakably romantic, I only tag the ship name.
Q: You post a lot of stuff and I don’t always come back to Tumblr that often, but I’m really interested in [this character/pairing]. Could you message me when you post original content for that character/pairing?
A: I can try! I do this for some people already. Obviously if tons of people want me to do this it won’t work, but right now I’m doing it for less than ten and it works ok. Message me!
Q: Is this a sideblog? Do you run any other blogs?
A: It’s Naruto on main here, baby. I have a few other sideblogs. @fineilikefmab is a blog for Fullmetal Alchemist content. @domesticaphrodite is for food, beauty, lifestyle etc and is more of a personal blog. @fineilikesmut (which I can’t tag) is my blog for reblogs that are not SFW.
Q: I found some Chinese art that I want translated! Will you do that?
A: Send me the link! I will definitely consider it. Any pairing will be considered except post-699 canon-compliant SS. Right now, I only do typesets for artists who give me permission to modify their work. (I have complex feelings about fair use and abandoned works, but as a matter of priorities, when there are artists who have given me permission whose works haven’t been translated fully, it only makes sense to prioritize them.)
You can also request a character or pairing and I’ll go hunting for content on my own. Some pairings that are very popular among English speakers are not popular among Chinese speakers and vice versa, so obviously my ability to find content depends on that content existing.
Q: I’ve noticed you repost work from Chinese artists. Sometimes you say “with permission” and sometimes you mention something about CC-BY or similar. What is this CC thing?
A: Creative Commons is a copyleft movement dedicated to make it easier for people to share their work while retaining aspects of control that are important to them. As opposed to copyright, a CC license makes a work freely sharable and may or may not permit changing the work and using the work for profit. The website LOFTER, by default, does not apply any CC license to artists’ work, but they can opt in to using one, and there are a variety to choose from. Therefore, you can be confident that the artist chose to let people share (with credit) or remix their work.
Q: Can I ask you something about your writing?
A: YES PLEASE DO THAT :D :D :D
Q: 我是一位說中文的藝術家,妳願意把我的火影忍者粉絲繪圖翻譯成英語嗎?
A: 我很願意!請給我留言。繁體、簡體都可以啦。
72 notes
·
View notes
Text
A guide to a discourse free AroAce blogging experience
As many of you’ve probably experienced, it’s difficult to avoid seeing the ace discourse and aphobia on tumblr these days while being involved in the aromantic and asexual communities. This guide will highlight some of the steps you can take to keep yourself safe from harassment using tumblr’s built in features, some extensions you can use to make it even safer, and some blogs we recommend following for a positive Acespec and Arospec blogging experience!
As always, our own blog will remain 100% discourse free as well.
Part 1: Tumblr’s Built in Features
This section will cover things such as the tumblr search sysyem, what to do if you’re being harassed, and how the tumblr privacy and block features work.
Unfortunately a lot of acespec and arospec specific tags tend to get cluttered with harassment and anti-aspec posts. While some of that comes from aphobes posting in tags that are supposed to be safe (such as “asexual positvity” or “actuallyaromantic”), with the way tumblr’s search system works, aphobes don’t even necessarily have to tag their posts. The tumblr staff explains it fully in this post, but in short, even words that are mention in a post, even if they aren’t in the tags, can show up in a search. The good news is that you can opt out of this by adding a # in front of your search. That way, posts tagged as #greyromantic will show up in your results, but posts that only mention the word but don’t tag it won’t. While this doesn’t guarantee that you won’t see aphobic posts while searching tumblr, it will filter out untagged discourse rants.
The flip side to this is that aphobes and discoursers searching on tumblr can find even your untagged posts. Thankfully you can actually keep your own posts out of tumblr’s search engine. As explained at that link, turning off “allow search engines to index your blog” applies to tumblr’s search engine as well. By selecting that setting, you will effectively stay invisible in the search engine, both when people search by # or by mentions.
Another feature that can save you a lot of hassle is the block feature. If you come across an aphobe in the tags: block them. Even if they haven’t interacted with you, block them. There are even block lists out there that’ll save you the distress of having to come across a blog first. A blocked user cannot interact with you or your posts in any way, in fact they won’t even see your posts on their dash or in the tags. So if you see someone being particularly nasty, the best way to keep yourself safe from them is to make sure they can’t find you at all. You can block users from your settings- scroll to the bottom of your blog’s settings and you’ll find a space to type in users to block them. There’s also a guide here on how to block several blogs at once (for chrome and firefox). You can also block people from their blogs if they have the mobile theme (this is the only way to block people on mobile).
If you’re already receiving harassment though, there’s several things you can do to stop it. My first advice is the same as before: block them. It’s not admitting defeat, it’s not a show of weakness: it’s the easiest way to protect yourself. When blocking people isn’t enough, make sure that your private messaging is set to mutuals only, your submissions are turned off, and anon asks (or even asks in general) turned off. The last two will prevent blocked users from simply logging out and then interacting with you that way, while the first is just a general way to limit interactions. If this is not enough and people are still harassing you then temporarily set your blog to private by giving it a password (this applies only to the blog you chose for it to apply to, and is not account wide). Once they’ve moved on (and they will, I’ve had to deal with them before myself) you can return your blog back to normal with just a single button under your settings. Note you will need to be logged into desktop tumblr to do this.
Keep in mind that you can also report people for their behavior, especially if you’re a minor, or their messages include death threats or suicide baiting.
Part 2: Beyond Tumblr’s Features
This section discusses how you can go beyond tumblr’s features using extensions such as the new xkit or tumblr savior.
While tumblr does have several built in features to deal with harassment, there’s even better ways you can keep yourself safe.
The first of these is an extension called tumblr savior, which is available for firefox, chrome, and opera (a similar extension called Washboard does the same for mobile devices). The long and short of it is that both extensions are blacklists. Add a tag or a phrase to the blacklist and any posts which mentions it are automatically hidden, being replaced by a notification, which you can click on to see the whole post, e.g. if you trust the person who posted it. You can even set it up so that you don’t get a notification on your dash for hidden posts, or that you get notifications but it doesn’t show the tags, etc. You can block whole phrases using this feature, so if there’s ones you commonly see used you can filter them out.
My personal recommendation however is to download the new xkit which is available for firefox and chrome through that link. Make sure you download the new xkit, since the old one hasn’t been updated in several years. This extension lets you do all kinds of things with your dashboard, including it’s own blocklist (which functions about the same as the others) and the ability to block specific posts. This is a feature that can be super helpful especially if there’s an aphobic post that gets passed around by people who don’t understand that its aphobic without going to the op’s blog (such as that “the A in stands for all star by smash mouth” post that was going around a while ago). Not only does this feature, called “Postblock” prevent that post from showing up in tags, it also keeps it from showing up on your dashboard. This is a great addition to tumblr’s already existing block feature, allowing you to block not just a blog but a specific post as well.
Part 3: Blogs to Follow
Lastly, this section will list discourse free pro-acespec and arospec blogs that the mods here recommend, including a bit of info about each one. Some of these blogs are aro or ace specific, while others are LGBTQ+ blogs that include aspec individuals. All of them are discourse and aphobia free though, and are a great place to start finding a safe inclusive community! Many of these blogs also frequently promote other aspec inclusive blogs, including advice blogs and positivity blogs, making them a great starting place to expand your following list from!
Our own blog aroacefaq, as mentioned before, is 100% discourse free, so if you don’t follow us already, give us a try!
goodpositivitylgbt is aspec inclusive (several of the mods are aspec) and has a zero discourse policy, which you can read about here. They make custom positivity posts as well as reblogging positivity made by other blogs.
letters-to-lgbt-kids is another aspec inclusive LGBTQ+ blog with custom positvity messages, styled as letters coming from “your tumblr mom.”
a-positive is an aspec specific positivity blog. They do not respond to discourse/ aphobic asks as explained here and are as such also safe to browse!
queerlobby makes custom moodboards, including for aspec people. When asks are open, just send in a request! No discourse here either since the focus is 100% on moodboards, so relax and browse their tags.
theasexualityblog is a blog specifically about asexual and acespec experiences, positivity, humor, etc. They have a “happy stories” tag for bad days, and even have a block list of aphobic blogs.
aspecpeoplearebeautiful is a blog dedicated to posting and reblogging aro and ace spec positivity!
asexualartists posts about (to no surprise) artists who are also asexual. This includes all kinds of artists, including youtubers, fine artists, writers, etc. It’s a great place to find people who post creative acespec content. The artists talk about both their art and their asexuality, including advice they have for other acespec individuals.
aromantichelp is an advice blog for arospec and aro individuals. They also have links to some great resources on their blog!
asexualadvice is not currently active, but their blog has a lot of answered asks and resources that can be helpful regardless!
splend-aros posts “Daily Affirmations” which are positive posts meant to encourage and support arospec people on all kinds of things! At the same time, they also reblog positive posts. They have stated in their FAQ that they are not a debate blog, so they should be discourse free!
affirm-ace-ions is the same concept as spend-aros but for acespec people! Daily Affirmations on all kinds of acespec related topics. They describe themselves in their about page as a safe space, and as such they post primarily positivity.
haveaqprsuggestion is a blog all about positivity surrounding qprs and aspec folks!
You can find even more blogs in our resources tab which can be accessed either through that link or directly from our blog. This post also has a list of aspec friendly blogs, however we cannot guarantee that they’re all discourse free, since it’s not our list. If you have any aspec positive or informative blogs you’d like us to add to that page, feel free to send us the link! You can also check out blogs we reblog from for other starting points! For privacy reasons, we did not include personal blogs on this list (so they wouldn’t suddenly be flooded with followers), but we do reblog from them.
12 notes
·
View notes
Text
by Karen Talavera
Have you ever been blown off right from the start? Ever been “ghosted” just after meeting someone—be it a potential business contact, friend or dating partner—you really liked and thought you were hitting it off with?
Whether you’ve experienced it first-hand or just heard the horror stories, ghosting totally sucks.
If you can relate, then you get why welcome campaigns aren’t just vital but critical to email success. Not only do they set the tone for the entire future of your subscriber relationships, but they also ensure those subscriber connections become relationships. They pave the way for good deliverability (inbox vs. junk folder placement), and they create familiarity, appreciation, engagement and (most importantly) trust.
Failing to send a welcome message after email sign-up or address capture is the digital equivalent of ghosting your subscribers. And we know what happens to ghosters—they get blocked, ignored, forgotten or downright hated on.
Ok, so you’re sending a welcome email, but is it a kick-ass welcome campaign or a vanilla, one-size-fits-all message that sounds like it could’ve been cranked out by an AI-driven robot with zero human intervention? (Or maybe it’s so bad, the AI-driven robot version would be an improvement?)
It’s not enough to merely send a welcome email—although that’s better than not sending one at all—you need a strategic, personal message with zazz. Your welcome campaign should have specific goals, you should know what they are, and it should be crafted intentionally to accomplish them.
Plus, cutting-edge marketers know the welcome email is just the tip of the relationship-building iceberg since they’re connecting it with an entire onboarding series to follow.
Still not convinced? Research shows a warm email welcome is more than just polite common sense, it’s a money-maker.
MarketingSherpa reports the average open rate for welcome emails is a whopping 50% (that’s the average), making them 86% more effective than your usual broadcast messages.
As if that’s not enough, according to Internet Retailer, merchants that send a welcome series see 13% more revenue than those sending a single message. Any way you cut it, welcome emails put engagement and money in the bank.
But, going beyond basic isn’t for wimps. Let’s make sure you’re doing it right with a breakdown of 4 essential ingredients for marketing success.
Essential Ingredients
1. Welcome, Introduce & Establish Identity
You got it—the whole point of a welcome email is to actually make a new subscriber feel welcome, so write your subject lines, headlines and copy that way! Show gratitude and appreciation like you would if you were meeting in person.
Think about how you’d welcome someone into your home or a special event: you’d invite them in, make sure they’re in the right place, and introduce yourself so they know exactly who you are and how to recognize you again.
Food gift merchant Fairytale Brownies’ welcome campaign scores! I’m feeling the warm, gooey brownie love right from the subject line with my “gift inside.”
The fact that I’m greeted as a “Fairytale Friend” and am receiving “much love” from co-founders (and real-life kindergarten friends—yeah, for real) David and Eileen, plus get to actually see what they look like, only adds to the yummy goodness. (Now, if I only had a glass of red wine to go with those brownies, but I digress…)
Getting serious for a sec, let’s not overlook the importance of establishing an inbox identity.
With ISPs cracking down on spam and monitoring inbox owner engagement like never before, today’s email welcome campaigns need to clearly establish brand and sender identity to ensure successful deliverability.
Your visible “From” name, as well as your email sending address and domain, should be recognizable entities to subscribers, even if it means having to explain things a bit (such as a parent company domain that’s different from a retail store brand name).
You don’t want new subscribers blocking or blacklisting you right from the get-go because they can’t connect the dots between what they signed up for and how you show up in the inbox.
2. Confirm Actions, Manage Expectations
What did you promise when you asked for an email address? Was it required as part of a mobile app download or purchase? Contest or sweepstakes entry? For access to gated content? Or were you just popping up a lightbox doling out the usual (but nonetheless appreciated) 10% discount or free shipping on the first purchase?
There’s a myriad of ways to end up on an email list and many—like entering a contest, registering for an event, downloading content, or creating an account—have nothing to do with intentionally signing up for email to get deals or perks.
Whatever you promised, make sure you’re telling subscribers that’s how and why they came to be on your list, that they’ve successfully completed the action, and what’s in store for them next.
Here’s what I received after joining British Airways’ frequent flyer program “Executive Club” (which sounds soooo much more elite than it is—oh those British!) after having purchased an international flight on Iberia, their partner airline. The animated hero shot is a catchy touch and not often seen in welcome emails—nice!
More to the point, the message clearly does its job by letting me know my membership number (if any of you international road warriors would like to apply it to your next BA flight, feel free), points status, and other useful information like program benefits and how to get their mobile app.
3. Orient and Guide
In the spirit of travel, your welcome email is a key inflection point at the start of a very important journey—the customer journey. Whether people ended up on your email list because they bought or they have yet to, your goal is the same: get them to transact.
As on any journey, people want to know the landscape. They’d like to know where they’re going and how to get there, so give them a map, as well as step-by-step directions. Don’t just leave them wandering in the wilderness.
This welcome email from eBags not only includes a hefty bounceback offer (a 25% discount on repeat purchase—that’s pretty motivating even though I dropped $400 on my first purchase) but also attractively enumerates what I need to know and do next, one step at a time.
A stellar touch I’m calling out is the inclusion of content marketing in point #4—which links to juicy-good information like travel guides, packing lists, and interviews with their “eBags Ambassadors,” real people embodying different customer personas.
This was no small investment to create, and as a frequent traveler myself, I both appreciate the effort and resonate strongly with it. I’m already feeling a real connection to this brand!
Remember—forging relationships is a core objective of your welcome campaigns, so evoking positive emotions will go a long way toward creating attachment and loyalty.
4. Prioritize Key Next Steps
eBags’ numbered CTAs in the previous example aptly illustrate this point, but what if walking new subscribers down the garden path isn’t as important as getting them to take a specific required action—like setting up a profile or account—before anything can happen that generates value for either of you?
Or, what if you have a BHAG (big hairy audacious goal) like growing social media followers or gathering feedback that depends on subscribers taking a specific action, like following your Instagram or completing a poll?
Here’s a real-life example involving a two-part email confirm/welcome to illustrate my point. I recently made a purchase in a Columbia Sportswear retail store. The cashier asked me if I wanted to join the rewards program, and I said yes. She asked for my email address, I verbally gave it, and then received this message.
Clearly, Columbia was forcing account creation for rewards program members—I wouldn’t be able to join and earn without completing setup. But the process was short and simple and the temporary password provided, so I did it. With the account setup done, a second more typical welcome email followed.
The moral of the story? If you need a new subscriber to do something before a relationship can be established at all, hand-hold them through the process and plan for additional emails to support it.
If that’s not enough to chew on, here’s a heap of welcome email inspiration from our friends at Really Good Emails.
Now that you’ve considered what’s possible, how will you evolve your welcome email campaigns this year?
Go to our website: www.ncmalliance.com
Unboxing the Welcome Email: 4 Essential Ingredients for Success by Karen Talavera Have you ever been blown off right from the start? Ever been “ghosted” just after meeting someone—be it a potential business contact, friend or dating partner—you really liked and thought you were hitting it off with?
0 notes
Text
Cybersecurity in SEO: How website security affects SEO performance
Website security — or lack thereof — can directly impact your SEO performance.
Search specialists can grow complacent. Marketers often get locked into a perception of what SEO is and begin to overlook what SEO should be.
The industry has long questioned the permanent impact a website hack can have on organic performance.
And many are beginning to question the role preventative security measures might play in Google’s evaluation of a given domain.
Thanks to the introduction of the GDPR and its accompanying regulations, questions of cybersecurity and data privacy have returned to the fray.
The debate rages on. What is the true cost of an attack? To what extent will site security affect my ranking?
The truth is, a lot of businesses have yet to grasp the importance of securing their digital assets. Until now, establishing on-site vulnerabilities has been considered a different skillset than SEO. But it shouldn’t be.
Being a leader – both in thought and search performance – is about being proactive and covering the bases your competition has not.
Website security is often neglected when discussing long-term digital marketing plans. But in reality, it could be the signal that sets you apart.
When was the last time cybersecurity was discussed during your SEO site audit or strategy meeting?
How does website security affect SEO?
HTTPS was named as a ranking factor and outwardly pushed in updates to the Chrome browser. Since then, HTTPS has, for the most part, become the ‘poster child’ of cybersecurity in SEO.
But as most of us know, security doesn’t stop at HTTPS. And HTTPS certainly does not mean you have a secure website.
Regardless of HTTPS certification, research shows that most websites will experience an average of 58 attacks per day. What’s more, as much as 61 percent of all internet traffic is automated — which means these attacks do not discriminate based on the size or popularity of the website in question.
No site is too small or too insignificant to attack. Unfortunately, these numbers are only rising. And attacks are becoming increasingly difficult to detect.
1. Blacklisting
If – or when – you’re targeted for an attack, direct financial loss is not the only cause for concern. A compromised website can distort SERPs and be subject to a range of manual penalties from Google.
That being said, search engines are blacklisting only a fraction of the total number of websites infected with malware.
GoDaddy’s recent report found that in 90 percent of cases, infected websites were not flagged at all.
This means the operator could be continually targeted without their knowledge – eventually increasing the severity of sanctions imposed.
Even without being blacklisted, a website’s rankings can still suffer from an attack. The addition of malware or spam to a website can only have a negative outcome.
It’s clear that those continuing to rely on outward-facing symptoms or warnings from Google might be overlooking malware that is affecting their visitors.
This creates a paradox. Being flagged or blacklisted for malware essentially terminates your website and obliterates your rankings, at least until the site is cleaned and the penalties are rescinded.
Not getting flagged when your site contains malware leads to greater susceptibility to hackers and stricter penalties.
Prevention is the only solution.
This is especially alarming considering that 9 percent, or as many as 1.7 million websites, have a major vulnerability that could allow for the deployment of malware.
If you’re invested in your long-term search visibility, operating in a highly competitive market, or heavily reliant on organic traffic, then vigilance in preventing a compromise is crucial.
2. Crawling errors
Bots will inevitably represent a significant portion of your website and application traffic.
But not all bots are benign. At least 19% of bots crawl websites for more nefarious purposes like content scraping, vulnerability identification, or data theft.
Even if their attempts are unsuccessful, constant attacks from automated software can prevent Googlebot from adequately crawling your site.
Malicious bots use the same bandwidth and server resources as a legitimate bot or normal visitor would.
However, if your server is subject to repetitive, automated tasks from multiple bots over a long period of time, it can begin to throttle your web traffic. In response, your server could potentially stop serving pages altogether.
If you notice strange 404 or 503 errors in Search Console for pages that aren’t missing at all, it’s possible Google tried crawling them but your server reported them as missing.
This kind of error can happen if your server is overextended
Though their activity is usually manageable, sometimes even legitimate bots can consume resources at an unsustainable rate. If you add lots of new content, aggressive crawling in an attempt to index it may strain your server.
Similarly, it’s possible that legitimate bots may encounter a fault in your website, triggering a resource intensive operation or an infinite loop.
To combat this, most sites use server-side caching to serve pre-built versions of their site rather than repeatedly generating the same page on every request, which is far more resource intensive. This has the added benefit of reducing load times for your real visitors, which Google will approve of.
Most major search engines also provide a way to control the rate at which their bots crawl your site, so as not to overwhelm your servers’ capabilities.
This does not control how often a bot will crawl your site, but the level of resources consumed when they do.
To optimize effectively, you must recognize the threat against you or your client’s specific business model.
Appreciate the need to build systems that can differentiate between bad bot traffic, good bot traffic, and human activity. Done poorly, you could reduce the effectiveness of your SEO, or even block valuable visitors from your services completely.
In the second section, we’ll cover more on identifying malicious bot traffic and how to best mitigate the problem.
3. SEO spam
Over 73% of hacked sites in GoDaddy’s study were attacked strictly for SEO spam purposes.
This could be an act of deliberate sabotage, or an indiscriminate attempt to scrape, deface, or capitalize upon an authoritative website.
Generally, malicious actors load sites with spam to discourage legitimate visits, turn them into link farms, and bait unsuspecting visitors with malware or phishing links.
In many cases, hackers take advantage of existing vulnerabilities and get administrative access using an SQL injection.
This type of targeted attack can be devastating. Your site will be overrun with spam and potentially blacklisted. Your customers will be manipulated. The reputation damages can be irreparable.
Other than blacklisting, there is no direct SEO penalty for website defacements. However, the way your website appears in the SERP changes. The final damages depend on the alterations made.
But it’s likely your website won’t be relevant for the queries it used to be, at least for a while.
Say an attacker gets access and implants a rogue process on your server that operates outside of the hosting directory.
They could potentially have unfettered backdoor access to the server and all of the content hosted therein, even after a file clean-up.
Using this, they could run and store thousands of files – including pirated content – on your server.
If this became popular, your server resources would be used mainly for delivering this content. This will massively reduce your site speed, not only losing the attention of your visitors, but potentially demoting your rankings.
Other SEO spam techniques include the use of scraper bots to steal and duplicate content, email addresses, and personal information. Whether you’re aware of this activity or not, your website could eventually be hit by penalties for duplicate content.
How to mitigate SEO risks by improving website security
Though the prospect of these attacks can be alarming, there are steps that website owners and agencies can take to protect themselves and their clients. Here, proactivity and training are key in protecting sites from successful attacks and safeguarding organic performance in the long-run.
1. Malicious bots
Unfortunately, most malicious bots do not follow standard protocols when it comes to web crawlers. This obviously makes them harder to deter. Ultimately, the solution is dependent on the type of bot you’re dealing with.
If you’re concerned about content scrapers, you can manually look at your backlinks or trackbacks to see what sites are using your links. If you find that your content has been posted without your permission on a spam site, file a DMCA-complaint with Google.
In general, your best defense is to identify the source of your malicious traffic and block access from these sources.
The traditional way of doing this is to routinely analyze your log files through a tool like AWStats. This produces a report listing every bot that has crawled your website, the bandwidth consumed, total number of hits, and more.
Normal bot bandwidth usage should not surpass a few megabytes per month.
If this doesn’t give you the data you need, you can always go through your site or server log files. Using this, specifically the ‘Source IP address’ and ‘User Agent’ data, you can easily distinguish bots from normal users.
Malicious bots might be more difficult to identify as they often mimic legitimate crawlers by using the same or similar User Agent.
If you’re suspicious, you can do a reverse DNS lookup on the source IP address to get the hostname of the bot in question.
The IP addresses of major search engine bots should resolve to recognizable host names like ‘*.googlebot.com’ or ‘*.search.msn.com’ for Bing.
Additionally, malicious bots tend to ignore the robots exclusion standard. If you have bots visiting pages that are supposed to be excluded, this indicates the bot might be malicious.
2. WordPress plugins and extensions
A huge number of compromised sites involve outdated software on the most commonly used platform and tools – WordPress and its CMS.
WordPress security is a mixed bag. The bad news is, hackers look specifically for sites using outdated plugins in order to exploit known vulnerabilities. What’s more, they’re constantly looking for new vulnerabilities to exploit.
This can lead to a multitude of problems. If you are hacked and your site directories have not been closed from listing their content, the index pages of theme and plugin related directories can get into Google’s index. Even if these pages are set to 404 and the remaining site is cleaned up, they can make your site an easy target for further bulk platform or plugin-based hacking.
It’s been known for hackers to exploit this method to take control of a site’s SMTP services and send spam emails. This can lead to your domain getting blacklisted with email spam databases.
If your website’s core function has any legitimate need for bulk emails – whether it’s newsletters, outreach, or event participants – this can be disastrous.
How to prevent this
Closing these pages from indexing via robots.txt would still leave a telling footprint. Many sites are left removing them from Google’s index manually via the URL removal request form. Along with removal from email spam databases, this can take multiple attempts and long correspondences, leaving lasting damages.
On the bright side, there are plenty of security plugins which, if kept updated, can help you in your efforts to monitor and protect your site.
Popular examples include All in One and Sucuri Security. These can monitor and scan for potential hacking events and have firewall features that block suspicious visitors on a permanent basis.
Review, research, and update each plugin and script that you use. It’s better to invest the time in keeping your plugins updated than make yourself an easy target.
3. System monitoring and identifying hacks
Many practitioners don’t try to actively determine whether a site has been hacked when accepting prospective clients. Aside from Google’s notifications and the client being transparent about their history, it can be difficult to determine.
This process should play a key role in your appraisal of existing and future business. Your findings here – both in terms of historic and current security – should factor into the strategy you choose to apply.
With 16 months of Search Console data, it can be possible to identify past attacks like spam injection by tracking historical impression data.
That being said, not all attacks take this form. And certain verticals naturally experience extreme traffic variations due to seasonality. Ask your client directly and be thorough in your research.
How to prevent this
To stand your best chance of identifying current hacks early, you’ll need dedicated tools to help diagnose things like crypto-mining software, phishing, and malware.
There are paid services like WebsitePulse or SiteLock that provide a single platform solution for monitoring your site, servers, and applications. Thus, if a plugin goes rogue, adds links to existing pages, or creates new pages altogether, the monitoring software will alert you within minutes.
You can also use a source code analysis tool to detect if a site has been compromised.
These inspect your PHP and other source code for signatures and patterns that match known malware code. Advanced versions of this software compare your code against ‘correct’ versions of the same files rather than scanning for external signatures. This helps catch new malware for which a detection signature may not exist.
Most good monitoring services include the ability to do so from multiple locations. Hacked sites often don’t serve malware to every user.
Instead, they include code that only displays it to certain users based on location, time of day, traffic source, and other criteria. By using a remote scanner that monitors multiple locations, you avoid the risk of missing an infection.
4. Local network security
It’s equally as important to manage your local security as it is that of the website you’re working on. Incorporating an array of layered security software is no use if access control is vulnerable elsewhere.
Tightening your network security is paramount, whether you’re working independently, remotely, or in a large office. The larger your network, the higher the risk of human error, while the risks of public networks cannot be understated.
Ensure you’re adhering to standard security procedures like limiting the number of login attempts possible in a specific time-frame, automatically ending expired sessions, and eliminating form auto-fills.
Wherever you’re working, encrypt your connection with a reliable VPN.
It’s also wise to filter your traffic with a Web Application Firewall (WAF). This will filter, monitor, and block traffic to and from an application to protect against attempts at compromise or data exfiltration.
In the same way as VPN software, this can come in the form of an appliance, software, or as-a-service, and contains policies customized to specific applications. These custom policies will need to be maintained and updated as you modify your applications.
Conclusion
Web security affects everyone. If the correct preventative measures aren’t taken and the worst should happen, it will have clear, lasting consequences for the site from a search perspective and beyond.
When working intimately with a website, client, or strategy, you need to be able to contribute to the security discussion or initiate it if it hasn’t begun.
If you’re invested in a site’s SEO success, part of your responsibility is to ensure a proactive and preventative strategy is in place, and that this strategy is kept current.
The problem isn’t going away any time soon. In the future, the best SEO talent – agency, independent, or in-house – will have a working understanding of cybersecurity.
As an industry, it’s vital we help educate clients about the potential risks – not only to their SEO, but to their business as a whole.
The post Cybersecurity in SEO: How website security affects SEO performance appeared first on Search Engine Watch.
source https://searchenginewatch.com/2019/02/07/how-website-security-affects-seo/
from Rising Phoenix SEO http://risingphoenixseo.blogspot.com/2019/02/cybersecurity-in-seo-how-website.html
0 notes
Text
Cybersecurity in SEO: How website security affects SEO performance
Website security — or lack thereof — can directly impact your SEO performance.
Search specialists can grow complacent. Marketers often get locked into a perception of what SEO is and begin to overlook what SEO should be.
The industry has long questioned the permanent impact a website hack can have on organic performance.
And many are beginning to question the role preventative security measures might play in Google’s evaluation of a given domain.
Thanks to the introduction of the GDPR and its accompanying regulations, questions of cybersecurity and data privacy have returned to the fray.
The debate rages on. What is the true cost of an attack? To what extent will site security affect my ranking?
The truth is, a lot of businesses have yet to grasp the importance of securing their digital assets. Until now, establishing on-site vulnerabilities has been considered a different skillset than SEO. But it shouldn’t be.
Being a leader – both in thought and search performance – is about being proactive and covering the bases your competition has not.
Website security is often neglected when discussing long-term digital marketing plans. But in reality, it could be the signal that sets you apart.
When was the last time cybersecurity was discussed during your SEO site audit or strategy meeting?
How does website security affect SEO?
HTTPS was named as a ranking factor and outwardly pushed in updates to the Chrome browser. Since then, HTTPS has, for the most part, become the ‘poster child’ of cybersecurity in SEO.
But as most of us know, security doesn’t stop at HTTPS. And HTTPS certainly does not mean you have a secure website.
Regardless of HTTPS certification, research shows that most websites will experience an average of 58 attacks per day. What’s more, as much as 61 percent of all internet traffic is automated — which means these attacks do not discriminate based on the size or popularity of the website in question.
No site is too small or too insignificant to attack. Unfortunately, these numbers are only rising. And attacks are becoming increasingly difficult to detect.
1. Blacklisting
If – or when – you���re targeted for an attack, direct financial loss is not the only cause for concern. A compromised website can distort SERPs and be subject to a range of manual penalties from Google.
That being said, search engines are blacklisting only a fraction of the total number of websites infected with malware.
GoDaddy’s recent report found that in 90 percent of cases, infected websites were not flagged at all.
This means the operator could be continually targeted without their knowledge – eventually increasing the severity of sanctions imposed.
Even without being blacklisted, a website’s rankings can still suffer from an attack. The addition of malware or spam to a website can only have a negative outcome.
It’s clear that those continuing to rely on outward-facing symptoms or warnings from Google might be overlooking malware that is affecting their visitors.
This creates a paradox. Being flagged or blacklisted for malware essentially terminates your website and obliterates your rankings, at least until the site is cleaned and the penalties are rescinded.
Not getting flagged when your site contains malware leads to greater susceptibility to hackers and stricter penalties.
Prevention is the only solution.
This is especially alarming considering that 9 percent, or as many as 1.7 million websites, have a major vulnerability that could allow for the deployment of malware.
If you’re invested in your long-term search visibility, operating in a highly competitive market, or heavily reliant on organic traffic, then vigilance in preventing a compromise is crucial.
2. Crawling errors
Bots will inevitably represent a significant portion of your website and application traffic.
But not all bots are benign. At least 19% of bots crawl websites for more nefarious purposes like content scraping, vulnerability identification, or data theft.
Even if their attempts are unsuccessful, constant attacks from automated software can prevent Googlebot from adequately crawling your site.
Malicious bots use the same bandwidth and server resources as a legitimate bot or normal visitor would.
However, if your server is subject to repetitive, automated tasks from multiple bots over a long period of time, it can begin to throttle your web traffic. In response, your server could potentially stop serving pages altogether.
If you notice strange 404 or 503 errors in Search Console for pages that aren’t missing at all, it’s possible Google tried crawling them but your server reported them as missing.
This kind of error can happen if your server is overextended
Though their activity is usually manageable, sometimes even legitimate bots can consume resources at an unsustainable rate. If you add lots of new content, aggressive crawling in an attempt to index it may strain your server.
Similarly, it’s possible that legitimate bots may encounter a fault in your website, triggering a resource intensive operation or an infinite loop.
To combat this, most sites use server-side caching to serve pre-built versions of their site rather than repeatedly generating the same page on every request, which is far more resource intensive. This has the added benefit of reducing load times for your real visitors, which Google will approve of.
Most major search engines also provide a way to control the rate at which their bots crawl your site, so as not to overwhelm your servers’ capabilities.
This does not control how often a bot will crawl your site, but the level of resources consumed when they do.
To optimize effectively, you must recognize the threat against you or your client’s specific business model.
Appreciate the need to build systems that can differentiate between bad bot traffic, good bot traffic, and human activity. Done poorly, you could reduce the effectiveness of your SEO, or even block valuable visitors from your services completely.
In the second section, we’ll cover more on identifying malicious bot traffic and how to best mitigate the problem.
3. SEO spam
Over 73% of hacked sites in GoDaddy’s study were attacked strictly for SEO spam purposes.
This could be an act of deliberate sabotage, or an indiscriminate attempt to scrape, deface, or capitalize upon an authoritative website.
Generally, malicious actors load sites with spam to discourage legitimate visits, turn them into link farms, and bait unsuspecting visitors with malware or phishing links.
In many cases, hackers take advantage of existing vulnerabilities and get administrative access using an SQL injection.
This type of targeted attack can be devastating. Your site will be overrun with spam and potentially blacklisted. Your customers will be manipulated. The reputation damages can be irreparable.
Other than blacklisting, there is no direct SEO penalty for website defacements. However, the way your website appears in the SERP changes. The final damages depend on the alterations made.
But it’s likely your website won’t be relevant for the queries it used to be, at least for a while.
Say an attacker gets access and implants a rogue process on your server that operates outside of the hosting directory.
They could potentially have unfettered backdoor access to the server and all of the content hosted therein, even after a file clean-up.
Using this, they could run and store thousands of files – including pirated content – on your server.
If this became popular, your server resources would be used mainly for delivering this content. This will massively reduce your site speed, not only losing the attention of your visitors, but potentially demoting your rankings.
Other SEO spam techniques include the use of scraper bots to steal and duplicate content, email addresses, and personal information. Whether you’re aware of this activity or not, your website could eventually be hit by penalties for duplicate content.
How to mitigate SEO risks by improving website security
Though the prospect of these attacks can be alarming, there are steps that website owners and agencies can take to protect themselves and their clients. Here, proactivity and training are key in protecting sites from successful attacks and safeguarding organic performance in the long-run.
1. Malicious bots
Unfortunately, most malicious bots do not follow standard protocols when it comes to web crawlers. This obviously makes them harder to deter. Ultimately, the solution is dependent on the type of bot you’re dealing with.
If you’re concerned about content scrapers, you can manually look at your backlinks or trackbacks to see what sites are using your links. If you find that your content has been posted without your permission on a spam site, file a DMCA-complaint with Google.
In general, your best defense is to identify the source of your malicious traffic and block access from these sources.
The traditional way of doing this is to routinely analyze your log files through a tool like AWStats. This produces a report listing every bot that has crawled your website, the bandwidth consumed, total number of hits, and more.
Normal bot bandwidth usage should not surpass a few megabytes per month.
If this doesn’t give you the data you need, you can always go through your site or server log files. Using this, specifically the ‘Source IP address’ and ‘User Agent’ data, you can easily distinguish bots from normal users.
Malicious bots might be more difficult to identify as they often mimic legitimate crawlers by using the same or similar User Agent.
If you’re suspicious, you can do a reverse DNS lookup on the source IP address to get the hostname of the bot in question.
The IP addresses of major search engine bots should resolve to recognizable host names like ‘*.googlebot.com’ or ‘*.search.msn.com’ for Bing.
Additionally, malicious bots tend to ignore the robots exclusion standard. If you have bots visiting pages that are supposed to be excluded, this indicates the bot might be malicious.
2. WordPress plugins and extensions
A huge number of compromised sites involve outdated software on the most commonly used platform and tools – WordPress and its CMS.
WordPress security is a mixed bag. The bad news is, hackers look specifically for sites using outdated plugins in order to exploit known vulnerabilities. What’s more, they’re constantly looking for new vulnerabilities to exploit.
This can lead to a multitude of problems. If you are hacked and your site directories have not been closed from listing their content, the index pages of theme and plugin related directories can get into Google’s index. Even if these pages are set to 404 and the remaining site is cleaned up, they can make your site an easy target for further bulk platform or plugin-based hacking.
It’s been known for hackers to exploit this method to take control of a site’s SMTP services and send spam emails. This can lead to your domain getting blacklisted with email spam databases.
If your website’s core function has any legitimate need for bulk emails – whether it’s newsletters, outreach, or event participants – this can be disastrous.
How to prevent this
Closing these pages from indexing via robots.txt would still leave a telling footprint. Many sites are left removing them from Google’s index manually via the URL removal request form. Along with removal from email spam databases, this can take multiple attempts and long correspondences, leaving lasting damages.
On the bright side, there are plenty of security plugins which, if kept updated, can help you in your efforts to monitor and protect your site.
Popular examples include All in One and Sucuri Security. These can monitor and scan for potential hacking events and have firewall features that block suspicious visitors on a permanent basis.
Review, research, and update each plugin and script that you use. It’s better to invest the time in keeping your plugins updated than make yourself an easy target.
3. System monitoring and identifying hacks
Many practitioners don’t try to actively determine whether a site has been hacked when accepting prospective clients. Aside from Google’s notifications and the client being transparent about their history, it can be difficult to determine.
This process should play a key role in your appraisal of existing and future business. Your findings here – both in terms of historic and current security – should factor into the strategy you choose to apply.
With 16 months of Search Console data, it can be possible to identify past attacks like spam injection by tracking historical impression data.
That being said, not all attacks take this form. And certain verticals naturally experience extreme traffic variations due to seasonality. Ask your client directly and be thorough in your research.
How to prevent this
To stand your best chance of identifying current hacks early, you’ll need dedicated tools to help diagnose things like crypto-mining software, phishing, and malware.
There are paid services like WebsitePulse or SiteLock that provide a single platform solution for monitoring your site, servers, and applications. Thus, if a plugin goes rogue, adds links to existing pages, or creates new pages altogether, the monitoring software will alert you within minutes.
You can also use a source code analysis tool to detect if a site has been compromised.
These inspect your PHP and other source code for signatures and patterns that match known malware code. Advanced versions of this software compare your code against ‘correct’ versions of the same files rather than scanning for external signatures. This helps catch new malware for which a detection signature may not exist.
Most good monitoring services include the ability to do so from multiple locations. Hacked sites often don’t serve malware to every user.
Instead, they include code that only displays it to certain users based on location, time of day, traffic source, and other criteria. By using a remote scanner that monitors multiple locations, you avoid the risk of missing an infection.
4. Local network security
It’s equally as important to manage your local security as it is that of the website you’re working on. Incorporating an array of layered security software is no use if access control is vulnerable elsewhere.
Tightening your network security is paramount, whether you’re working independently, remotely, or in a large office. The larger your network, the higher the risk of human error, while the risks of public networks cannot be understated.
Ensure you’re adhering to standard security procedures like limiting the number of login attempts possible in a specific time-frame, automatically ending expired sessions, and eliminating form auto-fills.
Wherever you’re working, encrypt your connection with a reliable VPN.
It’s also wise to filter your traffic with a Web Application Firewall (WAF). This will filter, monitor, and block traffic to and from an application to protect against attempts at compromise or data exfiltration.
In the same way as VPN software, this can come in the form of an appliance, software, or as-a-service, and contains policies customized to specific applications. These custom policies will need to be maintained and updated as you modify your applications.
Conclusion
Web security affects everyone. If the correct preventative measures aren’t taken and the worst should happen, it will have clear, lasting consequences for the site from a search perspective and beyond.
When working intimately with a website, client, or strategy, you need to be able to contribute to the security discussion or initiate it if it hasn’t begun.
If you’re invested in a site’s SEO success, part of your responsibility is to ensure a proactive and preventative strategy is in place, and that this strategy is kept current.
The problem isn’t going away any time soon. In the future, the best SEO talent – agency, independent, or in-house – will have a working understanding of cybersecurity.
As an industry, it’s vital we help educate clients about the potential risks – not only to their SEO, but to their business as a whole.
The post Cybersecurity in SEO: How website security affects SEO performance appeared first on Search Engine Watch.
from IM Tips And Tricks https://searchenginewatch.com/2019/02/07/how-website-security-affects-seo/
from Rising Phoenix SEO https://risingphxseo.tumblr.com/post/182631984775
0 notes
Text
Cybersecurity in SEO: How website security affects SEO performance
Website security — or lack thereof — can directly impact your SEO performance.
Search specialists can grow complacent. Marketers often get locked into a perception of what SEO is and begin to overlook what SEO should be.
The industry has long questioned the permanent impact a website hack can have on organic performance.
And many are beginning to question the role preventative security measures might play in Google’s evaluation of a given domain.
Thanks to the introduction of the GDPR and its accompanying regulations, questions of cybersecurity and data privacy have returned to the fray.
The debate rages on. What is the true cost of an attack? To what extent will site security affect my ranking?
The truth is, a lot of businesses have yet to grasp the importance of securing their digital assets. Until now, establishing on-site vulnerabilities has been considered a different skillset than SEO. But it shouldn’t be.
Being a leader – both in thought and search performance – is about being proactive and covering the bases your competition has not.
Website security is often neglected when discussing long-term digital marketing plans. But in reality, it could be the signal that sets you apart.
When was the last time cybersecurity was discussed during your SEO site audit or strategy meeting?
How does website security affect SEO?
HTTPS was named as a ranking factor and outwardly pushed in updates to the Chrome browser. Since then, HTTPS has, for the most part, become the ‘poster child’ of cybersecurity in SEO.
But as most of us know, security doesn’t stop at HTTPS. And HTTPS certainly does not mean you have a secure website.
Regardless of HTTPS certification, research shows that most websites will experience an average of 58 attacks per day. What’s more, as much as 61 percent of all internet traffic is automated — which means these attacks do not discriminate based on the size or popularity of the website in question.
No site is too small or too insignificant to attack. Unfortunately, these numbers are only rising. And attacks are becoming increasingly difficult to detect.
1. Blacklisting
If – or when – you’re targeted for an attack, direct financial loss is not the only cause for concern. A compromised website can distort SERPs and be subject to a range of manual penalties from Google.
That being said, search engines are blacklisting only a fraction of the total number of websites infected with malware.
GoDaddy’s recent report found that in 90 percent of cases, infected websites were not flagged at all.
This means the operator could be continually targeted without their knowledge – eventually increasing the severity of sanctions imposed.
Even without being blacklisted, a website’s rankings can still suffer from an attack. The addition of malware or spam to a website can only have a negative outcome.
It’s clear that those continuing to rely on outward-facing symptoms or warnings from Google might be overlooking malware that is affecting their visitors.
This creates a paradox. Being flagged or blacklisted for malware essentially terminates your website and obliterates your rankings, at least until the site is cleaned and the penalties are rescinded.
Not getting flagged when your site contains malware leads to greater susceptibility to hackers and stricter penalties.
Prevention is the only solution.
This is especially alarming considering that 9 percent, or as many as 1.7 million websites, have a major vulnerability that could allow for the deployment of malware.
If you’re invested in your long-term search visibility, operating in a highly competitive market, or heavily reliant on organic traffic, then vigilance in preventing a compromise is crucial.
2. Crawling errors
Bots will inevitably represent a significant portion of your website and application traffic.
But not all bots are benign. At least 19% of bots crawl websites for more nefarious purposes like content scraping, vulnerability identification, or data theft.
Even if their attempts are unsuccessful, constant attacks from automated software can prevent Googlebot from adequately crawling your site.
Malicious bots use the same bandwidth and server resources as a legitimate bot or normal visitor would.
However, if your server is subject to repetitive, automated tasks from multiple bots over a long period of time, it can begin to throttle your web traffic. In response, your server could potentially stop serving pages altogether.
If you notice strange 404 or 503 errors in Search Console for pages that aren’t missing at all, it’s possible Google tried crawling them but your server reported them as missing.
This kind of error can happen if your server is overextended
Though their activity is usually manageable, sometimes even legitimate bots can consume resources at an unsustainable rate. If you add lots of new content, aggressive crawling in an attempt to index it may strain your server.
Similarly, it’s possible that legitimate bots may encounter a fault in your website, triggering a resource intensive operation or an infinite loop.
To combat this, most sites use server-side caching to serve pre-built versions of their site rather than repeatedly generating the same page on every request, which is far more resource intensive. This has the added benefit of reducing load times for your real visitors, which Google will approve of.
Most major search engines also provide a way to control the rate at which their bots crawl your site, so as not to overwhelm your servers’ capabilities.
This does not control how often a bot will crawl your site, but the level of resources consumed when they do.
To optimize effectively, you must recognize the threat against you or your client’s specific business model.
Appreciate the need to build systems that can differentiate between bad bot traffic, good bot traffic, and human activity. Done poorly, you could reduce the effectiveness of your SEO, or even block valuable visitors from your services completely.
In the second section, we’ll cover more on identifying malicious bot traffic and how to best mitigate the problem.
3. SEO spam
Over 73% of hacked sites in GoDaddy’s study were attacked strictly for SEO spam purposes.
This could be an act of deliberate sabotage, or an indiscriminate attempt to scrape, deface, or capitalize upon an authoritative website.
Generally, malicious actors load sites with spam to discourage legitimate visits, turn them into link farms, and bait unsuspecting visitors with malware or phishing links.
In many cases, hackers take advantage of existing vulnerabilities and get administrative access using an SQL injection.
This type of targeted attack can be devastating. Your site will be overrun with spam and potentially blacklisted. Your customers will be manipulated. The reputation damages can be irreparable.
Other than blacklisting, there is no direct SEO penalty for website defacements. However, the way your website appears in the SERP changes. The final damages depend on the alterations made.
But it’s likely your website won’t be relevant for the queries it used to be, at least for a while.
Say an attacker gets access and implants a rogue process on your server that operates outside of the hosting directory.
They could potentially have unfettered backdoor access to the server and all of the content hosted therein, even after a file clean-up.
Using this, they could run and store thousands of files – including pirated content – on your server.
If this became popular, your server resources would be used mainly for delivering this content. This will massively reduce your site speed, not only losing the attention of your visitors, but potentially demoting your rankings.
Other SEO spam techniques include the use of scraper bots to steal and duplicate content, email addresses, and personal information. Whether you’re aware of this activity or not, your website could eventually be hit by penalties for duplicate content.
How to mitigate SEO risks by improving website security
Though the prospect of these attacks can be alarming, there are steps that website owners and agencies can take to protect themselves and their clients. Here, proactivity and training are key in protecting sites from successful attacks and safeguarding organic performance in the long-run.
1. Malicious bots
Unfortunately, most malicious bots do not follow standard protocols when it comes to web crawlers. This obviously makes them harder to deter. Ultimately, the solution is dependent on the type of bot you’re dealing with.
If you’re concerned about content scrapers, you can manually look at your backlinks or trackbacks to see what sites are using your links. If you find that your content has been posted without your permission on a spam site, file a DMCA-complaint with Google.
In general, your best defense is to identify the source of your malicious traffic and block access from these sources.
The traditional way of doing this is to routinely analyze your log files through a tool like AWStats. This produces a report listing every bot that has crawled your website, the bandwidth consumed, total number of hits, and more.
Normal bot bandwidth usage should not surpass a few megabytes per month.
If this doesn’t give you the data you need, you can always go through your site or server log files. Using this, specifically the ‘Source IP address’ and ‘User Agent’ data, you can easily distinguish bots from normal users.
Malicious bots might be more difficult to identify as they often mimic legitimate crawlers by using the same or similar User Agent.
If you’re suspicious, you can do a reverse DNS lookup on the source IP address to get the hostname of the bot in question.
The IP addresses of major search engine bots should resolve to recognizable host names like ‘*.googlebot.com’ or ‘*.search.msn.com’ for Bing.
Additionally, malicious bots tend to ignore the robots exclusion standard. If you have bots visiting pages that are supposed to be excluded, this indicates the bot might be malicious.
2. WordPress plugins and extensions
A huge number of compromised sites involve outdated software on the most commonly used platform and tools – WordPress and its CMS.
WordPress security is a mixed bag. The bad news is, hackers look specifically for sites using outdated plugins in order to exploit known vulnerabilities. What’s more, they’re constantly looking for new vulnerabilities to exploit.
This can lead to a multitude of problems. If you are hacked and your site directories have not been closed from listing their content, the index pages of theme and plugin related directories can get into Google’s index. Even if these pages are set to 404 and the remaining site is cleaned up, they can make your site an easy target for further bulk platform or plugin-based hacking.
It’s been known for hackers to exploit this method to take control of a site’s SMTP services and send spam emails. This can lead to your domain getting blacklisted with email spam databases.
If your website’s core function has any legitimate need for bulk emails – whether it’s newsletters, outreach, or event participants – this can be disastrous.
How to prevent this
Closing these pages from indexing via robots.txt would still leave a telling footprint. Many sites are left removing them from Google’s index manually via the URL removal request form. Along with removal from email spam databases, this can take multiple attempts and long correspondences, leaving lasting damages.
On the bright side, there are plenty of security plugins which, if kept updated, can help you in your efforts to monitor and protect your site.
Popular examples include All in One and Sucuri Security. These can monitor and scan for potential hacking events and have firewall features that block suspicious visitors on a permanent basis.
Review, research, and update each plugin and script that you use. It’s better to invest the time in keeping your plugins updated than make yourself an easy target.
3. System monitoring and identifying hacks
Many practitioners don’t try to actively determine whether a site has been hacked when accepting prospective clients. Aside from Google’s notifications and the client being transparent about their history, it can be difficult to determine.
This process should play a key role in your appraisal of existing and future business. Your findings here – both in terms of historic and current security – should factor into the strategy you choose to apply.
With 16 months of Search Console data, it can be possible to identify past attacks like spam injection by tracking historical impression data.
That being said, not all attacks take this form. And certain verticals naturally experience extreme traffic variations due to seasonality. Ask your client directly and be thorough in your research.
How to prevent this
To stand your best chance of identifying current hacks early, you’ll need dedicated tools to help diagnose things like crypto-mining software, phishing, and malware.
There are paid services like WebsitePulse or SiteLock that provide a single platform solution for monitoring your site, servers, and applications. Thus, if a plugin goes rogue, adds links to existing pages, or creates new pages altogether, the monitoring software will alert you within minutes.
You can also use a source code analysis tool to detect if a site has been compromised.
These inspect your PHP and other source code for signatures and patterns that match known malware code. Advanced versions of this software compare your code against ‘correct’ versions of the same files rather than scanning for external signatures. This helps catch new malware for which a detection signature may not exist.
Most good monitoring services include the ability to do so from multiple locations. Hacked sites often don’t serve malware to every user.
Instead, they include code that only displays it to certain users based on location, time of day, traffic source, and other criteria. By using a remote scanner that monitors multiple locations, you avoid the risk of missing an infection.
4. Local network security
It’s equally as important to manage your local security as it is that of the website you’re working on. Incorporating an array of layered security software is no use if access control is vulnerable elsewhere.
Tightening your network security is paramount, whether you’re working independently, remotely, or in a large office. The larger your network, the higher the risk of human error, while the risks of public networks cannot be understated.
Ensure you’re adhering to standard security procedures like limiting the number of login attempts possible in a specific time-frame, automatically ending expired sessions, and eliminating form auto-fills.
Wherever you’re working, encrypt your connection with a reliable VPN.
It’s also wise to filter your traffic with a Web Application Firewall (WAF). This will filter, monitor, and block traffic to and from an application to protect against attempts at compromise or data exfiltration.
In the same way as VPN software, this can come in the form of an appliance, software, or as-a-service, and contains policies customized to specific applications. These custom policies will need to be maintained and updated as you modify your applications.
Conclusion
Web security affects everyone. If the correct preventative measures aren’t taken and the worst should happen, it will have clear, lasting consequences for the site from a search perspective and beyond.
When working intimately with a website, client, or strategy, you need to be able to contribute to the security discussion or initiate it if it hasn’t begun.
If you’re invested in a site’s SEO success, part of your responsibility is to ensure a proactive and preventative strategy is in place, and that this strategy is kept current.
The problem isn’t going away any time soon. In the future, the best SEO talent – agency, independent, or in-house – will have a working understanding of cybersecurity.
As an industry, it’s vital we help educate clients about the potential risks – not only to their SEO, but to their business as a whole.
The post Cybersecurity in SEO: How website security affects SEO performance appeared first on Search Engine Watch.
from Digtal Marketing News https://searchenginewatch.com/2019/02/07/how-website-security-affects-seo/
0 notes