#device authentication certificate
Text
Microsoft Intune Cloud PKI
Recently, Microsoft introduced the general availability of its new PKI-as-a-service solution called Microsoft Intune Cloud PKI. Cloud PKI allows administrators to issue and manage user and device authentication certificates for Intune-managed endpoints without deploying Active Directory Certificate Services (AD CS) on-premises. Cloud PKI frees administrators from the burdens of deploying and…

View On WordPress
#authentication#Azure#BYOCA#certificate#certificates#Certification Authority#cloud#Cloud PKI#device authentication certificate#InTune#Intune Cloud PKI#issuing CA#issuing certification authority#Microsoft#Microsoft Intune#Microsoft Intune Cloud PKI#PKI#PKI-as-a-Service#public cloud#root CA#root certification authority#SCEP#Simple Certificate Enrollment Protocol#user authentication certificate
0 notes
Text
HAVING AN INTENTIONAL ROOM


Your room is the most important place in your life. You sleep, wake up, heal and experience many emotions just in your room. You have to take care of your room, so it is spiritually the ideal place to grow into the best version of yourself.
KEEPING YOUR ROOM CLEAN
Keeping your room free of mess is an act of mindfulness and self-discipline that supports your overall journey and connects you with your higher self. It helps with promoting clarity, and cultivating inner balance and is an everyday self-care ritual.
Make your bed every day. You have to respect the place in which you sleep and heal.
Hang up clean clothes after the day or put any dirty clothes in your laundry hamper, avoid tossing them on the floor.
Find a place for everything, and know where everything is. If you do not know where each thing in your room is located, you either have too much clutter or you’re disorganised.
Tidy up your room daily, neatly putting everything away in its place. If needed, buy a few organisers.
Don’t leave rubbish for extended periods. Treat your room like a temple, don’t disrespect it, and pick up after yourself.
Try to avoid eating meals in your bedroom. We forget the dirty dishes over time, and it stinks and attracts unwanted bugs.
Change bed sheets regularly. Once a week at the most, for more hygienic reasons though.
Remove unwanted items on your bedside table. Keep it minimal and intentional with anything you want to place on it.
Regularly clean up the dust in your room, using a duster or a damp microfiber cloth on all of the surfaces.
ENCOURAGING GROWTH IN YOUR LIFE
A room designed to encourage inner growth serves as a physical reminder of your commitment to self-improvement, personal development, and overall well-being. It creates an environment helpful to improvement, self-reflection, and positive change.
Keep specific areas of your room designated to one task in your life. For me, my desk is for productivity, my bed is for resting or relaxing and my bedroom floor is for mindful activities.
Throw away any items that do not serve a purpose to you anymore. Avoid keeping items that bring you painful or harmful memories.
Minimise the presence of technology in your room. I suggest having zones in your room which is device-free or having a time of day in which devices are not allowed in your room.
Create a vision board poster in your room that you can see every day, which helps to visualise and motivate you to create your dream life.
Place meaningful quotes, affirmations, mantras or prayers as reminders of the values, mindsets or intentions you wish to cultivate in your life.
Display personal achievements. If you won any awards or certificates, place them in a way in which you can view them every day. If you have done something in your life that you think is an achievement but have no award to display, just simply create your own. Buy some balsawood and glue it together to create your own medal.
Place items that align with the habits or routines you want to cultivate in your life so that they are easily accessible. Put a workout mat in the corner, always have your journal on your desk or have a cold water bottle ready to go when you wake up.
3. DECORATING YOUR ROOM TO REFLECT YOU
Decorating your room in a way that reflects your true self brings a sense of authenticity and comfort. It creates a nurturing environment that allows for self-expression, reflection, and personal growth which ultimately contributes to your journey of inner development.
Make a mood board or vision board of how you would want your room to look, how it supports you and how it makes you feel. Choose a colour scheme in this process as well.
Add candles or incense that you think embodies who you are, or who you want to be. For example, if I want to be a cleaner person, I would choose a candle that smells like fresh linen.
Put up posters of things that you like, people who you look up to or anything that expresses who you are.
Add a canopy to your bed while you sleep. So cute, and I believe it helps protect you from any unwanted energy entering through you while you sleep.
Add a rug, even if you already have carpet, to enhance the cozy ambience of the room.
An ottoman at the end of the bed can elevate your room to look more expensive, if needed, it can also be an organiser for your extra things.
Put life in your room, adding low-maintenance plants or flowers can liven it up. A little extra, research some plants or flowers meaning’s and pick one that resonates with you.
Display any of your favourite jewellery, bags, clothing pieces, or make-up around your room. A nice way to appreciate what you have, without actually using them.
#becoming that girl#clean girl#green juice girl#becoming her#that girl#that girl lifestyle#glow up#glow up era#pink pilates girl#dream girl#dream girl life#pink pilates princess#it girl#it girl energy#it girl tips#dream girl tips#feminine energy#feminine journey#that girl energy#that girl routine#wonyoungism#hyperfemininity#hypergamyblr#self improvement#self development#self help#self care#self growth#self love#inner strength
4K notes
·
View notes
Text
New Android Malware SoumniBot Employs Innovative Obfuscation Tactics

Banking Trojan Targets Korean Users by Manipulating Android Manifest
A sophisticated new Android malware, dubbed SoumniBot, is making waves for its ingenious obfuscation techniques that exploit vulnerabilities in how Android apps interpret the crucial Android manifest file. Unlike typical malware droppers, SoumniBot's stealthy approach allows it to camouflage its malicious intent and evade detection.
Exploiting Android Manifest Weaknesses
According to researchers at Kaspersky, SoumniBot's evasion strategy revolves around manipulating the Android manifest, a core component within every Android application package. The malware developers have identified and exploited vulnerabilities in the manifest extraction and parsing procedure, enabling them to obscure the true nature of the malware.
SoumniBot employs several techniques to obfuscate its presence and thwart analysis, including:
- Invalid Compression Method Value: By manipulating the compression method value within the AndroidManifest.xml entry, SoumniBot tricks the parser into recognizing data as uncompressed, allowing the malware to evade detection during installation.
- Invalid Manifest Size: SoumniBot manipulates the size declaration of the AndroidManifest.xml entry, causing overlay within the unpacked manifest. This tactic enables the malware to bypass strict parsers without triggering errors.
- Long Namespace Names: Utilizing excessively long namespace strings within the manifest, SoumniBot renders the file unreadable for both humans and programs. The Android OS parser disregards these lengthy namespaces, facilitating the malware's stealthy operation.
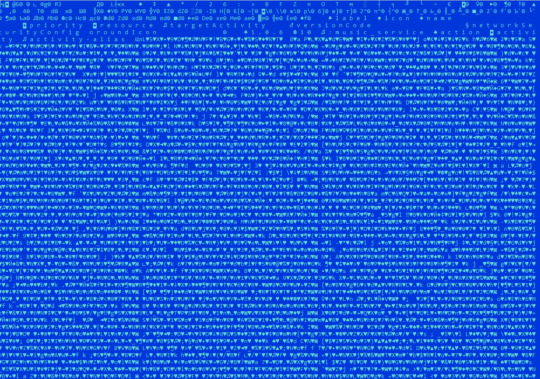
Example of SoumniBot Long Namespace Names (Credits: Kaspersky)
SoumniBot's Malicious Functionality
Upon execution, SoumniBot requests configuration parameters from a hardcoded server, enabling it to function effectively. The malware then initiates a malicious service, conceals its icon to prevent removal, and begins uploading sensitive data from the victim's device to a designated server.
Researchers have also highlighted SoumniBot's capability to search for and exfiltrate digital certificates used by Korean banks for online banking services. This feature allows threat actors to exploit banking credentials and conduct fraudulent transactions.
Targeting Korean Banking Credentials
SoumniBot locates relevant files containing digital certificates issued by Korean banks to their clients for authentication and authorization purposes. It copies the directory containing these digital certificates into a ZIP archive, which is then transmitted to the attacker-controlled server.
Furthermore, SoumniBot subscribes to messages from a message queuing telemetry transport server (MQTT), an essential command-and-control infrastructure component. MQTT facilitates lightweight, efficient messaging between devices, helping the malware seamlessly receive commands from remote attackers.
Some of SoumniBot's malicious commands include:
- Sending information about the infected device, including phone number, carrier, and Trojan version
- Transmitting the victim's SMS messages, contacts, accounts, photos, videos, and online banking digital certificates
- Deleting contacts on the victim's device
- Sending a list of installed apps
- Adding new contacts on the device
- Getting ringtone volume levels
With its innovative obfuscation tactics and capability to target Korean banking credentials, SoumniBot poses a significant threat to South Korean Android users.
Read the full article
2 notes
·
View notes
Text
Securing Your Mobile App: Best Practices for Data Protection

In today’s digitally connected world, mobile applications have become an integral part of our daily lives. From social media to online banking, we rely on mobile apps to access various services and manage sensitive information. However, with the increasing reliance on mobile apps, the need for robust data protection measures has become paramount. This blog will explore best practices for securing your mobile app and ensuring the protection of user data.
Encryption:
One of the fundamental steps in securing your mobile app is implementing encryption techniques. Encryption ensures that data transmitted between the app and the server is transformed into a coded form, making it unreadable to unauthorized parties. Utilize strong encryption algorithms, such as AES (Advanced Encryption Standard), to protect sensitive user information like passwords, financial details, and personal data. Additionally, consider implementing end-to-end encryption to safeguard data even if it’s intercepted during transmission.
2. Secure Authentication:
Implementing strong authentication mechanisms is vital to protect user accounts from unauthorized access. Encourage the use of complex passwords and provide guidance on creating strong passwords during the registration process. Consider implementing two-factor authentication (2FA) or biometric authentication, such as fingerprint or facial recognition, to add an extra layer of security. Regularly validate and update authentication protocols to address emerging security vulnerabilities.
3. Secure Data Storage:
Properly managing and securing data storage within your mobile app is crucial. Avoid storing sensitive information on the device unless necessary, and when required, utilize secure storage mechanisms provided by the operating system or utilize encryption techniques to protect the data. Ensure that the app’s data storage is adequately protected against unauthorized access or tampering, both locally on the device and on the server.
4. Secure Network Communication:

Mobile apps rely on network communication to exchange data with servers or APIs. It’s essential to ensure that this communication is secure. Use secure communication protocols such as HTTPS (Hypertext Transfer Protocol Secure) to encrypt data transmitted over the network. Avoid transmitting sensitive information through insecure channels, such as unsecured Wi-Fi networks, and implement certificate pinning to prevent man-in-the-middle attacks.
5. Regular Updates and Security Patches:
Keeping your mobile app up to date with the latest security patches and fixes is crucial for maintaining a secure environment. Regularly release updates to address any identified security vulnerabilities or weaknesses. Promptly address security-related issues reported by users or security researchers and provide timely patches to mitigate potential risks. Establish a process for monitoring and staying informed about the latest security practices and threats.
6. Secure Code Development:
Developing secure code is essential for building a robust mobile app. Adhere to secure coding practices and guidelines provided by the platform and framework you are using. Regularly conduct code reviews and security audits to identify and address any potential vulnerabilities. Utilize automated tools for vulnerability scanning and penetration testing to detect security flaws in your app’s codebase.
7. User Privacy and Consent:
Respect user privacy and adhere to data protection regulations such as GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act). Clearly communicate your app’s data collection and usage practices to users through a comprehensive privacy policy. Obtain explicit consent from users before accessing and storing their personal information. Allow users to manage their privacy settings within the app, giving them control over their data.
Securing your mobile app is not just a legal requirement but also a responsibility to protect your users’ sensitive data. By implementing strong encryption, secure authentication mechanisms, and following best practices in code development, you can create a safer environment for your users. Regular updates and a privacy-centric approach will help instill trust and confidence in your app. By prioritizing data protection, you contribute to a safer mobile app ecosystem and foster long-term user satisfaction.
Remember, data protection is an ongoing process, and staying vigilant against emerging threats and security practices is vital in this ever-evolving digital landscape.
2 notes
·
View notes
Text
How to Perform an Annual Checkup on Your Website
Giving your website an annual checkup is an excellent idea, just as you would with your cars servicing. Setting aside time each year to concentrate on the important components of your website can help in many ways, from increasing its performance and speed to making it more appealing to users and consumers. Here are seven actions we advise taking as part of a yearly website audit.
1 - Verifying the facts
Businesses provide a lot of information about themselves on their websites, but some of it will evolve over time. Visitors will therefore view outdated and incorrect information. In a yearly checkup, updating any information that is out of date should be one of your top priorities. The titles and responsibilities of your employees, the services and goods you provide, you’re pricing, and your T&Cs are all things to double-check many business listings.
2 - Relevant content
Checking to verify if your pages and posts are still relevant to your target audience is another worthwhile content-related assessment. It can be beneficial to adapt the material so that it still has current relevance if your target audience's interests and behaviour have changed or if they have changed altogether. To accomplish this, think about how your target market has evolved in the past year and look for ways to adapt the information you offer to any changes.
3 - Think about switching your theme
A theme change can be time-consuming, thus it should not be handled lightly. However, if your website's appearance and design are beginning to feel stale, it could give visitors a bad impression of your business and turn them away. Even if your goods or services are excellent, many visitors may leave a website they find outdated or unattractive within a few seconds of entering, which can cost you revenue.
4 - Follow tips from your top rivals
Whatever industry you're in, there will be rival businesses whose websites are worth checking out, especially those that consistently appear at the top of search engine results. You can get a decent idea of what the top-ranking sites do that you don't by examining their designs, layouts, features, and content. This might assist you in making a list of improvements to make to your own website in order to help it meet the same standards.
It is feasible to delve a little bit deeper using analytical tools in addition to just browsing the website. These can reveal which of your rivals get the most traffic as well as the keywords they employ to do so. Knowing those keywords may enable you to employ them to improve your own ranking and draw in more clients business listings.
5 - Examine your security
Cybercrime is on the rise, and falling victim to it might have disastrous consequences for your company. A crucial component of your annual check-up is determining whether your security is appropriate for the situation. Make sure your web host protects your website against viruses and intrusion; need strong passwords; and think about adopting two-factor authentication. Additionally, you should verify the validity of your SSL certificate, filter emails for spam, phishing, and malware, and set up automated software updates. You can also employ strong security solutions like Pitchman, which can automate updates and patching while containing risks, if you have a CMS website, such as one powered by WordPress.
6 - Check that your website is easily accessible
People use a variety of browsers in addition to a variety of devices to access the internet. You should test how your website functions and appears on as many of these as you can each year. This includes examining how Chrome, Edge, Firefox, and Safari look on laptops, smartphones, and tablets. Keep in mind that a portion of your visitors will use each of these platforms and browsers, and if your website doesn't function properly on any of them, you could lose a portion of your visitor base and revenues.
Check the navigation and display, then test logins, pop-ups, forms, buttons, and the checkout to ensure they work as they should free business listings.
7 - Examine your hosting
Your website's success depends heavily on the caliber of your web hosting. A competent host makes sure your website runs quickly, is safe, and is always online while also offering round-the-clock technical support in case you encounter issues and need help fixing them. It could be time to look for a new host if your current one isn't meeting these basic requirements.
The suitability of the hosting option for your website is another factor to take into account. Your current bundle might not offer all the resources your website requires to operate at its peak performance if you have a lot more online content or are receiving a lot more traffic. If so, you might wish to upgrade to a stronger option, such as a VPS, dedicated server, or cloud.
1 note
·
View note
Text
How to Ensure Security in Your Bet365 Clone Script
Bet365 clone script is undoubtedly key in today’s pressing world of internet betting, while security is a basic necessity that should not be taken lightly. Due to the current surge in cyber criminals and since financial information pertains directly to a person’s pocket, some stringent measures have become requisite. Here is a detailed guide on what measures you need to implement in your Bet365 clone script, in order to give your users a very strong and reliable platform to work with.
Choose a Reliable Script Provider
The foundation of a secure betting platform starts with selecting a reputable script provider. Ensure the provider has a proven track record of developing secure and reliable scripts. Research customer reviews, check their portfolio, and if possible, get in touch with previous clients. A reliable provider will adhere to best practices in coding and security.
Implement Strong Authentication Mechanisms
User authentication is a critical component of your platform’s security. Implement multi-factor authentication (MFA) to ensure that only authorized users can access their accounts. MFA typically involves a combination of something the user knows (password), something the user has (smartphone), and something the user is (biometric verification). This layered approach significantly reduces the risk of unauthorized access.
Ensure Secure Data Transmission
Encrypt all data transmitted between the user’s device and your server using Secure Socket Layer (SSL) certificates. SSL encryption prevents data from being intercepted by malicious actors during transmission. Additionally, enforce the use of HTTPS protocol across your entire platform to enhance security
Regularly Update and Patch the Script
Cyber threats are constantly evolving, and so should your defense mechanisms. Regularly update your Bet365 clone script to the latest version provided by your script provider. These updates often include patches for newly discovered vulnerabilities. Implement a robust patch management policy to ensure that updates are applied promptly and without disrupting your services.
Use Strong Password Policies
Enforce strong password policies for all users. Require passwords to be a minimum length and include a mix of uppercase letters, lowercase letters, numbers, and special characters. Regularly prompt users to update their passwords and discourage the reuse of old passwords. Consider implementing password expiration policies to further enhance security.
Database Security Measures
Your database contains sensitive user information and betting data, making it a prime target for attackers. Use database encryption to protect stored data. Additionally, implement access controls to ensure that only authorized personnel can access the database. Regularly audit database access logs to detect any suspicious activity.
Final Thoughts
Securing your Bet365 clone script requires a multi-faceted approach. By implementing strong authentication, encrypting data, regularly updating the script, and conducting security audits, you can build a robust and secure betting platform. Prioritizing security not only protects your users but also enhances the credibility and success of your online betting business.
Fire Bee Techno Services is a leading casino game development company renowned for its innovative and high-quality gaming solutions. With a team of skilled developers and designers, the company specializes in creating engaging and visually stunning casino games that cater to a global audience. Their portfolio includes a wide range of games such as slots, poker, roulette, blackjack, and more, each crafted with meticulous attention to detail and cutting-edge technology.
0 notes
Text
What does Halal Certification entail for meat and non-meat products in Ghana?

Halal Certification in Ghana
Halal Certification in Ghana has emerged as a widespread factor in world trade, catering to the nutritional possibilities and non-secular ideals of thousands and thousands worldwide. In Ghana, a country with a diverse cultural and religious landscape, the call for Halal-certified products is steadily developing. Understanding the intricacies of Halal certification in Ghana is critical for businesses aiming to tap into this moneymaking marketplace segment.
What is Halal Certification?
Halal, an Arabic term meaning “permissible” or “lawful,” refers to products and practices permissible under Islamic law. Halal Certification in Ghana ensures that merchandise follows Islamic dietary laws and is produced, processed, and dispensed consistently with Islamic principles.
In Ghana, Halal certification extends past meat products to include a wide variety of non-meat objects, including liquids, cosmetics, prescription drugs, and more. This certification assures purchasers, specifically Muslim purchasers, that their products meet their spiritual requirements.
The Importance of Halal Certification in Ghana:
Catering to the Muslim Population: Ghana is home to a sizeable Muslim population, accounting for approximately 18% of the total population. With a growing recognition of Halal ideas among Muslims, the demand for Halal-licensed products is on the upward push.
Access to Global Markets: Halal Certification in Ghana opens doorways to global markets, enabling Ghanaian organizations to export their products to predominantly Muslim international locations. This certification enhances the competitiveness of Ghanaian merchandise within the international market, facilitating trade and financial boom.
Building Trust and Credibility: Halal Certification in Ghana instils self-belief in clients, assuring them of the authenticity and compliance of merchandise with Islamic dietary laws. For agencies, acquiring Halal certification complements their reputation, credibility, and logo picture, fostering customer loyalty and consideration.
The Halal Certification Process in Ghana:
Assessment of Ingredients and Production Processes: The first step in the Halal certification procedure includes an intensive evaluation of elements used in the product’s manufacturing. All components need to be Halal-compliant and free from prohibited materials or components. The production approaches must also adhere to Islamic concepts, ensuring that the product stays Halal Certification in Ghana during manufacturing.
Inspection and Auditing: Halal Certification in Ghana: Our bodies in Ghana conduct complete inspections and audits of manufacturing centres to confirm compliance with Halal standards. This includes examining manufacturing techniques, storage centres, devices, and hygiene practices to ensure Halal integrity at each delivery stage.
Certification and Labeling: The product is presented with Halal Certification in Ghana upon completing the evaluation and inspection system. The licensed products are labelled with the Halal logo, indicating compliance with Islamic nutritional legal guidelines. This labelling offers transparency to consumers, permitting them to make informed choices based on their non-religious ideals.
Challenges and Opportunities:
Lack of Awareness and Understanding: Despite the growing demand for Halal Certification in Ghana products, more expertise is needed amongst companies and customers in Ghana. Educating stakeholders about the significance of Halal certification is crucial for its widespread adoption and acceptance.
Compliance with Standards: Ensuring compliance with Halal requirements can be challenging for groups, particularly small and medium organizations (SMEs) with restricted resources and information. Providing aid and steering to businesses navigating the certification technique can help conquer this barrier.
Market Expansion and Export Opportunities: Halal certification allows Ghanaian companies to expand their market reach beyond domestic borders. By tapping into the global Halal marketplace, organizations can capitalize on the developing demand for Halal-licensed products and increase export sales.
Conclusion
Halal Certification in Ghana, ensuring religious adherence for Muslim consumers and fostering a culture of responsible and ethical production practices. As the Ghanaian Halal market expands, collaboration between certification bodies, businesses, and consumers will create a robust and transparent ecosystem that benefits all stakeholders. By embracing the true essence of Halal — encompassing religious observance, ethical sourcing, and quality assurance, Ghana can position itself as a leader in the global Halal market. Halal Certification in Nigeria
Why Factocert for Halal Certification in Ghana
We provide the best Halal consultants in Ghana, who are knowledgeable and provide the best solution. For information on how to get Halal certification, kindly contact us at [email protected]. Halal certification consultants work according to Halal standards and help organizations implement Halal certification with proper documentation.
For more information, visit Halal Certification in Ghana.
Related Links:
· ISO 21001 Certification in Ghana
· ISO 37001 Certification in Ghana
· ISO 22301 Certification in Ghana
· ISO 27701 Certification in Ghana
· ISO 26000 Certification in Ghana
· ISO 20000–1 Certification in Ghana
· ISO 50001 Certification in Ghana
RELATED ARTICLE
Halal Consultants in Ghana
0 notes
Text
The Ultimate Checklist for Wireless Devices Testing
Testing wireless devices involves ensuring that they meet performance, regulatory, and safety standards. This comprehensive checklist will guide you through the essential steps and considerations for thorough wireless device testing.
1. Pre-Testing Preparations
Documentation and Requirements
Gather Specifications: Collect all technical and functional specifications of the device.
Understand Standards: Familiarize yourself with relevant standards and regulations (e.g., FCC, CE, ETSI).
Test Plan: Develop a detailed test plan outlining test cases, procedures, and acceptance criteria.
Test Environment Setup
Test Lab: Ensure access to a certified test laboratory with appropriate equipment.
Environmental Controls: Maintain controlled temperature, humidity, and electromagnetic environment.
Calibration: Verify that all test equipment is calibrated and certified.
2. Functional Testing
Connectivity
Pairing and Bonding: Test the device’s ability to pair and bond with other devices.
Range: Measure the operational range in various environments (e.g., open field, indoors).
Data Rate: Verify data transfer rates meet specifications.
Performance
Signal Strength: Evaluate signal strength at different distances and conditions.
Latency: Measure the latency during data transmission and reception.
Throughput: Assess the maximum data throughput under different scenarios.
3. Regulatory Compliance Testing
Emissions Testing
Radiated Emissions: Test for unintentional emissions that could interfere with other devices.
Conducted Emissions: Measure emissions conducted through power lines and cables.
Immunity Testing
ESD Testing: Simulate electrostatic discharge to test device resilience.
RF Immunity: Expose the device to various RF signals to ensure it operates correctly under interference.
Specific Absorption Rate (SAR) Testing
Human Safety: Ensure the device meets safety limits for electromagnetic radiation exposure.
4. Interoperability Testing
Compatibility
Cross-Platform: Test compatibility with various operating systems (iOS, Android, Windows).
Device Ecosystem: Verify interoperability with different devices (phones, tablets, computers).
Coexistence
Multiple Connections: Test the device’s ability to maintain multiple connections simultaneously.
Interference Handling: Assess performance in the presence of other wireless devices.
5. Security Testing
Encryption
Data Security: Verify that data transmission is encrypted and meets security standards.
Authentication: Test device authentication mechanisms to prevent unauthorized access.
Vulnerability Assessment
Penetration Testing: Conduct penetration testing to identify security vulnerabilities.
Firmware Security: Ensure the firmware is secure and free from exploits.
6. Power Consumption Testing
Battery Life
Usage Scenarios: Measure battery life under different usage scenarios (idle, active, heavy use).
Standby Time: Test the device’s power consumption in standby mode.
Charging
Efficiency: Evaluate charging efficiency and time.
Safety: Test for overheating and compliance with safety standards during charging.
7. User Experience Testing
Usability
User Interface: Evaluate the user interface for ease of use and intuitiveness.
Setup Process: Test the initial setup and configuration process.
Reliability
Stress Testing: Conduct stress tests to identify potential points of failure under heavy usage.
Field Testing: Perform real-world testing to ensure performance in actual conditions.
8. Documentation and Reporting
Test Reports
Detailed Records: Maintain comprehensive records of all test procedures, results, and observations.
Compliance Certificates: Obtain necessary compliance certificates from regulatory bodies.
Review and Feedback
Analysis: Analyze test results to identify areas for improvement.
Iterate: Implement changes and re-test as necessary to ensure all issues are resolved.
Conclusion
Thorough testing of wireless devices is essential to ensure they meet performance, regulatory, and safety standards. This ultimate checklist provides a structured approach to cover all critical aspects of wireless device testing, from pre-testing preparations to user experience. By following this checklist, manufacturers can enhance the quality, reliability, and market readiness of their wireless products.
0 notes
Text

At an unbeatable price of just 23 +0.13 USD each when you order 23 or more, this versatile regulator ensures your devices receive a stable and adjustable output voltage, making it ideal for various applications.
Why Choose the LM317LIPK?
Adjustable Output Voltage: Easily set your desired output voltage from 1.25V to 37V.
High Load Regulation: Maintains a steady voltage under varying load conditions.
Thermal Overload Protection: Safeguards your circuits against overheating.
Short-Circuit Protection: Ensures durability and reliability by protecting against short circuits.
SUV System Ltd is a leading #distributor of #electroniccomponents, partnering with top manufacturers to bring you high-quality products at competitive prices. With offices #worldwide and strict quality management certifications, we are committed to providing original and authentic components, fast delivery, and comprehensive customer service.
If you're looking to secure the best pricing for your electronic components, look no further than SUV System Ltd. Our dedication to customer satisfaction and industry expertise ensures you get the best value for your money.
Contact us today to learn more about our offerings at [email protected] or Skype at [email protected]
Or explore our products at https://www.suvsystem.com/
#diode supplier#semiconductors#electronic components#diodes#electronics supplier#rectifiers#capacitors#tvs diode#transistor#voltage regulator
0 notes
Text
Microsoft Intune Cloud PKI and Certificate Templates
Microsoft recently announced the general availability of its new PKI-as-a-Service platform called Microsoft Intune Cloud PKI. With Intune Cloud PKI, administrators create certification authorities (CAs) to issue and manage user and device authentication certificates for Intune-managed endpoints. Cloud PKI also provides hosted Authority Information Access (AIA) and Certificate Revocation List…

View On WordPress
#Active Directory#Active Directory Certificate Services#AD#AD CS#ADCS#AIA#authentication#CDP#certificate#certificate authority#certificate template#certificates#Certification Authority#Cloud PKI#CRL#encryption#endpoint manager#InTune#Intune Cloud PKI#MEM#Microsoft#Microsoft Endpoint Manager#Microsoft Intune Cloud PKI#NDES#Network Device Enrollment Service#PKI#public key infrastructure#SCEP#security#Simple Certificate Enrollment Protocol
0 notes
Text
Exploring Commercial Use and Security in the Best IPTV Services
Internet Protocol Television (IPTV) has gained immense popularity as a convenient and cost-effective way to access a wide range of television content over the internet. With a plethora of IPTV services available, it's essential to understand how they can be utilized for commercial purposes, ensure secure payment processes, and access them through various platforms like web browsers. In this comprehensive guide, we'll delve into these topics while exploring some of the best IPTV services in the market.
Can I Use the Best IPTV Services for Commercial Purposes?
Many individuals and businesses are interested in leveraging IPTV services for commercial purposes, such as providing entertainment in hotels, restaurants, bars, or corporate settings. However, it's crucial to understand the terms of service of each IPTV provider, as commercial use may be subject to different licensing agreements and pricing structures.
Some IPTV services explicitly offer commercial packages tailored to businesses, providing features like multi-screen support, customizable branding, and bulk channel subscriptions. These packages often come with additional benefits such as dedicated customer support and advanced analytics for monitoring viewership.
Before using an IPTV service for commercial purposes, it's essential to review the terms of service, licensing agreements, and any applicable regulations to ensure compliance and avoid potential legal issues.
How Do I Ensure That the Best IPTV Services Offer a Secure Payment Process?
Security is paramount when making payments for best IPTV services, especially considering the sensitive nature of financial transactions conducted online. Here are some steps to ensure a secure payment process when subscribing to IPTV services:
Use Reputable Providers: Choose IPTV services from reputable providers with a track record of secure transactions and positive customer reviews. Research the provider's reputation and check for any security certifications or compliance standards they adhere to.
Secure Payment Gateways: Look for IPTV services that utilize secure payment gateways to process transactions. Secure payment gateways encrypt sensitive information, such as credit card details, to prevent unauthorized access during transmission.
SSL Encryption: Ensure that the IPTV service website uses Secure Socket Layer (SSL) encryption to protect your personal and financial information. You can verify SSL encryption by checking for a padlock icon in the browser's address bar and ensuring that the website URL begins with "https."
Two-Factor Authentication: Opt for IPTV services that offer two-factor authentication (2FA) for added security during the payment process. 2FA requires users to provide an additional verification code, typically sent to their mobile device, to complete the transaction.
Avoid Suspicious Offers: Be cautious of suspicious offers or deals that seem too good to be true, as they may be attempts to steal your financial information or engage in fraudulent activities. Stick to reputable IPTV providers with transparent pricing and payment processes.
By following these precautions, you can ensure a secure payment process when subscribing to IPTV services and protect your personal and financial information from potential threats.
Can I Access the Best IPTV Services Through a Web Browser on My Computer?
Accessing IPTV services through a web browser on your computer offers convenience and flexibility, allowing you to enjoy your favorite TV shows, movies, and live events without the need for additional hardware or devices. Many IPTV providers offer web-based platforms or applications that are accessible through standard web browsers like Google Chrome, Mozilla Firefox, or Safari.
To access IPTV services through a web browser on your computer, follow these steps:
Subscription: Sign up for a subscription with the IPTV service of your choice and create an account on their website.
Login: Once you have a subscription, log in to your IPTV service account using your username and password.
Navigate to the IPTV Platform: Navigate to the IPTV platform or web-based application provided by your chosen service. This may involve clicking on a link or accessing a specific URL provided by the IPTV provider.
Browse Content: Once logged in, you can browse through the available content, including live TV channels, video-on-demand (VOD) titles, and catch-up TV programs.
Start Streaming: Select the content you want to watch and start streaming directly through your web browser. Most IPTV services offer a user-friendly interface with customizable layouts and search functionalities for easy navigation.
Enjoy: Sit back, relax, and enjoy your favorite TV shows, movies, and live events streaming directly through your computer's web browser.
By accessing IPTV services through a web browser on your computer, you can enjoy seamless streaming without the need for additional hardware or devices, making it a convenient option for users looking to watch content on their desktop or laptop computers.
Exploring the Best IPTV Services and Their Features
Now, let's explore some of the best IPTV services in the market, along with their key features:
1. IPTVFOLLOW
Commercial Use: Offers commercial packages tailored to businesses with customizable branding options.
Secure Payment Process: Utilizes secure payment gateways and SSL encryption for secure transactions.
Web Browser Access: Provides access through web browsers on computers for convenient streaming.
Additional Features: Multi-screen support, customizable branding, dedicated customer support.
2. IPTVUNLOCK
Commercial Use: Provides commercial packages for businesses with multi-screen support.
Secure Payment Process: Ensures secure transactions through trusted payment gateways.
Web Browser Access: Allows access through web browsers on computers for easy streaming.
Additional Features: Bulk channel subscriptions, advanced analytics for monitoring viewership.
3. IPTVGANG
Commercial Use: Offers commercial packages with multi-screen support and customizable branding.
Secure Payment Process: Utilizes secure payment gateways and SSL encryption for secure transactions.
Web Browser Access: Provides access through web browsers on computers for convenient streaming.
Additional Features: Personalized recommendations, advanced search functionalities.
4. IPTVTOPS
Commercial Use: Provides commercial packages with customizable branding options.
Secure Payment Process: Ensures secure transactions through trusted payment gateways.
Web Browser Access: Allows access through web browsers on computers for easy streaming.
Additional Features: Sleek and intuitive interface, 24/7 customer support.
5. IPTVGREAT
Commercial Use: Offers commercial packages for businesses with multi-screen support.
Secure Payment Process: Utilizes secure payment gateways for safe transactions.
Web Browser Access: Provides access through web browsers on computers for convenient streaming.
Additional Features: Personalized recommendations, reliable servers.
6. IPTVRESALE
Commercial Use: Provides commercial packages with multi-screen support and customizable branding.
Secure Payment Process: Ensures secure transactions through trusted payment gateways.
Web Browser Access: Allows access through web browsers on computers for easy streaming.
Additional Features: Simple and intuitive interface, responsive customer support.
Conclusion
IPTV services offer a convenient and versatile way to access television content over the internet, whether for personal or commercial use. By understanding the terms of service, ensuring secure payment processes, and utilizing web browser access, users can enjoy seamless streaming experiences while exploring the best IPTV services available in the market. Whether you're looking for commercial packages with customizable branding or reliable streaming options for personal use, there's an IPTV service out there to suit your needs.
#bestiptvsubscriptionprovider#best iptv service#best iptv#Best IPTV Service Provider#Best IPTV Service#Best IPTV Service Providers#iptv#iptv service#Best IPTV Subscription#iptv subscription#iptv firestick#iptv in 2024#best iptv 2024#iptv for firestick#best iptv for firestick#firestick#iptv app#iptv apps#iptv streaming#iptv streaming service#Buy IPTV Subscriptions#Buy IPTV Subscription#IPTV Subscriptions#live sports#IPTVTOPS#IPTVUNLOCK#IPTVGANG#IPTVGREAT#IPTVRESALE#IPTVFOLLOW
0 notes
Text
Digital Signature Online In Mumbai

As more business is conducted online, agreements and transactions that were once signed on paper and delivered physically are now being replaced with fully digital documents and workflows. whenever valuable or sensitive data is shared, malicious person who want to steal or manipulate that information for their own gain are ever-present. Businesses must be able to verify and authenticate that these critical business documents, data, and communications are trusted and delivered securely to reduce the risk of document tampering by malicious parties.
DSC are crucial for complying with electronic signature laws and regulation. In corporate world DSC are essential for signing
contracts, agreements, financial transactions. they help establish trust in online interactions with the
government.
In addition, the signature is portable as it is incorporated in the file itself, wherever it is transmitted and on whatever device. Digitally signed documents are also easy to control and keep track of by providing the status of all documents, identifying whether or not they’ve been signed, and viewing an audit trail.
Who issues the Digital Signature Certificate?

A licensed Certifying Authority (CA) issues the digital signature. Certifying Authority (CA) means a person who has been granted a license to issue a digital signature certificate under Section 24 of the Indian IT-Act 2000.
What are the legal status of a Digital Signature?
Digital Signatures are legally admissible in a Court of Law, as provided under the provisions of IT Act.
The Information Technology Act, 2000 provides the legislative backup to the digital signatures based on asymmetric cryptosystems.
Office of Controller of Certifying Authorities (CCA) is the Regulatory Authority in India that regulates issue and sues Certificate only to Certifying Authorities(CAs). Information Technology Act has established the Controller of Certifying Authorities(CCA) to license and regulate the working of Certifying Authorities. The Certifying Authorities (CAs) issue digital signature certificates for electronic authentication of users.
The Controller of Certifying Authorities (CCA) has established the Root Certifying Authority (RCAI) of India under the IT Act to digitally sign the public keys of Certifying Authorities (CA) in the country. The CCA certifies the public keys of CAs using its own private key, which enables users in the cyberspace to verify that a given certificate is issued by a licensed CA. The CCA also maintains the Repository of Digital Certificates, which contains all the certificates issued to the CAs in the country.

Buy Digital Signature Cerificate from DSC ONLINE in Kolkata at very low price. We are the best dsc provider in Kolkata. we have quite long experience in dsc services, This gives us diverse experience in meeting people of different designations in different industries. by availing dsc you can initiate participation in government e-tendering, e-auction, e-bidding, irctc tender, ITR, GST, New Company Registration, Foreign Trade, Provident fund, etc. in corporate world dsc are essential for signing contracts, agreements, financial transactions, Digital signature help individual establish trust in online interactions with the governments and organizations. it is very safe and secure due to its encryption technique . no data or documents could be tampered or forged. contact us today and get your digital signature right away to your doorstep.
What Documents Required for DSC Registration Online?
Below is the category wise list of documents required for obtaining Online Digital Signature Certificate:
Individuals: To apply for a DSC online in India, individuals must provide documents such as PAN card, proof of identity like driver's license and address verification (e.g., Aadhar card).
Organizations: Indian organizations must provide documents like PAN card for the company, the original partnership deed (if applicable), and proof of authorized signatories. Requirements may vary based on the type of entity.
Foreign Persons and Organizations: Foreign applicants require documents such as a passport, copy of visa and residence permit certificate (if in India), and government-issued address proof.
0 notes
Text
A Guide on How to Build an Ecommerce App in 9 Steps
In today’s digital age, having a robust eCommerce app is crucial for businesses aiming to thrive online. At iSyncEvolution, we specialize in turning your eCommerce dreams into reality. Here’s a simple 9-step guide to help you build a stellar eCommerce app
Step 1: Market Research and Planning: Begin with thorough market research. Identify your target audience, analyze competitors, and define your unique selling proposition (USP). This helps in creating a roadmap tailored to your business needs.
Step 2: Define Features and Functionality: List the essential features your app needs. Think user-friendly navigation, secure payment gateways, wishlist, product reviews, and customer support. Prioritize features that enhance user experience.
Step 3: Choose the Right Technology: Select the appropriate tech stack for your app. Popular choices include React Native, Flutter, and Swift for iOS, and Android. Ensure the technology aligns with your app’s requirements and future scalability.
Step 4: Design the User Interface (UI): Create a visually appealing and intuitive UI. Work with designers to develop wireframes and mockups that reflect your brand identity. Focus on simplicity and ease of use.
Step 5: Backend Development: Develop the backend to manage the server, database, and application logic. Opt for robust and scalable backend technologies like Node.js, Ruby on Rails, or Django to ensure seamless performance.
Step 6: Integrate Payment Gateways: Integrate secure and reliable payment gateways like PayPal, Stripe, or Square. Ensure multiple payment options to cater to a wider audience and enhance user convenience.
Step 7: Implement Security Measures: Security is paramount in eCommerce. Implement SSL certificates, data encryption, and secure authentication mechanisms to protect user data and build trust.
Step 8: Testing: Conduct thorough testing to identify and fix bugs. Perform unit tests, integration tests, and user acceptance testing (UAT) to ensure your app functions flawlessly across different devices and scenarios.
Step 9: Launch and Market Your App: Once testing is complete, launch your app on app stores. Utilize digital marketing strategies such as SEO, social media marketing, and email campaigns to promote your app and attract users.
Conclusion: Building an eCommerce app is a multifaceted process, but with the right approach and expert guidance from iSyncEvolution, you can create a powerful platform that drives your business growth. Ready to get started? Contact us today and let’s bring your vision to life!
0 notes
Text
Key Considerations for Successful Website Development
Creating a successful website involves much more than just designing attractive pages. It requires careful planning, a clear understanding of your goals, and consideration of various factors to ensure your site is effective and user-friendly. Here are the key considerations to keep in mind during website development, including a detailed look at website development costs.
1. Purpose and Goals
Define Your Objectives
Before starting the development process, it's crucial to clearly define the purpose and goals of your website. Are you creating an e-commerce site, a blog, a portfolio, or a corporate site? Understanding the primary function will guide design decisions and feature implementations.
Target Audience
Identify your target audience to tailor the user experience to their needs and preferences. Knowing your audience helps in creating relevant content, design elements, and navigation structures that resonate with them.
2. User Experience (UX)
Ease of Navigation
Ensure your website is easy to navigate. Users should be able to find information quickly and effortlessly. A well-structured menu, clear labels, and a logical flow are essential components of good navigation.
Responsive Design
With the increasing use of mobile devices, it's imperative to have a responsive design that adapts to various screen sizes. This enhances the user experience across all devices, from desktops to smartphones.
Loading Speed
A slow-loading website can frustrate users and lead to higher bounce rates. Optimize images, leverage browser caching, and use efficient coding practices to improve your site's loading speed.
3. Design and Aesthetics
Visual Appeal
Your website's design should be visually appealing and reflect your brand identity. Use consistent colors, fonts, and styles to create a cohesive look. High-quality images and graphics can also make a significant impact.
User-Centric Design
Design with the user in mind. Ensure that your website is not only attractive but also functional and easy to use. Avoid cluttered layouts and ensure that important information is highlighted.
4. Content Strategy
High-Quality Content
Content is king. Ensure your website provides valuable, high-quality content that meets the needs of your audience. This includes well-written text, engaging images, informative videos, and other multimedia elements.
SEO Optimization
Optimize your content for search engines to improve your site's visibility. Use relevant keywords, meta descriptions, alt text for images, and a well-structured URL hierarchy. Good SEO practices can help attract organic traffic.
5. Functionality
Interactive Features
Incorporate interactive features such as contact forms, comment sections, and social media integration. These elements can enhance user engagement and provide valuable feedback.
E-commerce Capabilities
If you're developing an e-commerce site, ensure you have a secure and user-friendly shopping cart, multiple payment options, and a smooth checkout process. Security features like SSL certificates are essential to protect user data.
6. Security
Data Protection
Protecting user data is critical. Implement security measures such as HTTPS, secure sockets layer (SSL) certificates, and regular security audits to protect your site from threats.
User Authentication
For websites requiring user accounts, ensure robust authentication methods are in place. Use strong password policies, two-factor authentication, and encryption to safeguard user information.
7. Website Development Costs
Budget Planning
One of the most important considerations is the cost of website development. Costs can vary widely based on the complexity of the site, features required, and the expertise of the developers involved. It’s essential to plan your budget carefully and allocate resources accordingly.
0 notes
Text
How to use Apple's built-in and free password manager, iCloud Keychain

With new capabilities in iOS 15, macOS Monterey, and other 2021 software updates, Apple has improved its password management game. Previously, iCloud Keychain was a password manager in the background that would come up from time to time, generally to the user's surprise, to provide a strong password or autofill something. In a separate Settings box, it now searches for password breaches, warns about repeated passwords, and provides two-factor authentication (2FA) keys many business listings.
Many iPhone and Mac users rely on third-party password managers, not aware that Apple's is fully functional and, in some cases, more secure than some of the market's most popular solutions. Here's how to set up and use iCloud Keychain on your devices, as well as how to keep your passwords up to date.
ICloud Password Manager on iPhone
Apple designed the iCloud Keychain to be imperceptible when in use. A prompt will show in place of your keyboard if you're on a website or in an app that employs a properly designed password field.
If you've previously entered a user name or email address, an auto-suggested password will appear on the online form for the password. By default, this is a string of twenty characters that includes two dashes, upper and lower case letters, and a symbol. Accept the option and click "remember login" when prompted on the following box. You'll never have to remember that complicated password again.
This user name and password will be kept and linked to that app or website automatically. The password auto-fill will show instead of the keyboard on subsequent logins, and a Face ID or Touch ID prompt will confirm that you are the one inputting the password.
The new login information will sync over iCloud utilising end-to-end encryption, so you don't have to worry about unwanted users stealing your password in transit. Navigate to the passwords area of the Settings app to examine the passwords you've stored, check for any security warnings, or erase password business listings.
It's also possible to add two-factor authentication codes.
What is the best way to obtain a dedicated Passwords app icon?
Apple's iCloud Keychain doesn't have its own app, but the password manager is found in the Settings app. If you don't want to go to this page every time you need to manage your passwords, you can always make a custom Shortcut and add it to your Home Screen with a direct link.
Step 1 - Open Shortcuts
Step 2 - Tap the "+" in the top right corner
Step 3 - Name the action "Passwords"
Step 4 - Tap "add action" and search "URL" to add that action
Step 5 - Paste in "prefs:root=PASSWORDS" into the URL field
Step 6 - Search for "Open URL," add the action, and select "URL" in variables within the action
Step 7 - Add the Shortcut to the Home Screen using the settings icon in the top right corner
The new Passwords shortcut will display on your Home Screen when you select an icon or custom picture, providing you easy access to your passwords with a single press. You may simply instruct Siri to "display passwords" if you choose.
ICloud Password Manager on Mac
"Keychain Access," vintage software integrated into macOS, serves as a catch-all app for authentication certificates, passwords, and other security prompts. However, starting with macOS Monterey, the System Preferences app has a more user-friendly option.
It's not for the faint of heart to use Keychain Access. It defaults to the "Other" folder in the app launcher and displays password information in a list manner. While users may retrieve their passwords from here, we recommend utilising the "Passwords" option in System Preferences instead free business listings.
The Passwords feature, like its iOS counterpart, is a straightforward list of all stored websites, complete with login details and notifications for duplicate or compromised passwords. During normal use, you won't need to utilise the Passwords feature in System Preferences often. Instead, all websites should automatically fill in the password or provide secure passwords.
Setting up two-factor authentication
The option to auto-fill two-factor authentication codes has been added to Apple's iCloud Keychain. Users may trust on the built-in secure and reliable system rather than using a third-party programmer devoted to 2FA.
While creating a 2FA code might be a nuisance, it is one of the most secure features when done correctly. Some people may be familiar with 2FA because of the text message codes they receive when validating their phone number, however they are insecure.
Many websites and applications now use a method that produces codes using a time signature and a text key. This code refreshes every thirty seconds in the Password tool, which users may view.
If the website is programmed to give a 2FA key to a password manager, this can be done automatically, but otherwise, users will have to manually set up the code.
To use iCloud Keychain for 2FA on iOS and macOS, follow these steps:
Steps 1 - Open the passwords tool
Step 2 - Select the login you're adding 2FA to
Step 3 - Select "Set Up Verification Code"
Step 4 - Select "Enter Setup Key" if you have a string of text
Step 5 - Otherwise scan the QR code on iPhone or right click the code on Mac
Step 6 - Enter the key on the website to verify it has been setup properly
On websites that have been properly developed for this system, the 2FA key will show above the keyboard, much like passwords. Otherwise, users will have to go to the Passwords tool and manually copy and paste the code.
On the Mac, iPad, and iPhone, there's more than Keychain
Although Apple's iCloud Keychain isn't the only choice, it may be the best for most people. Edge situations and commercial uses for password managers are not covered by the built-in solution.
Apple's version of a Windows programmer and a Chrome extension for passwords is included in the iCloud Keychain, so you're not limited into a single environment.
Although some password managers are free and cross-platform, they generally need the use of a specific browser or add-on. For those seeking for a password manager that isn't part of Apple's ecosystem, Google's password manager is a great alternative.
If iCloud Keychain doesn't meet your needs, there are a number of commercial alternatives available. For corporations or groups who need to share a centralized set of passwords, 1Password is a popular option.
For a casual user or family member, though, we'll always recommend iCloud Keychain first because of its ease and accessibility.
1 note
·
View note
Text
Apostille and FDA Certificate of Exportability in Arizona
If you're involved in international trade, particularly in the food and drug sectors, understanding the nuances of document legalization is crucial. In Arizona, two key documents often come into play: the Apostille and the FDA Certificate of Exportability. This guide will help you navigate the processes for both, ensuring your documents are properly authenticated for international use.
Why Do You Need an apostille arizona ?
If you are exporting products or conducting business internationally, certain documents may need to be legalized. An Apostille ensures that documents such as birth certificates, marriage licenses, and business agreements are recognized abroad.
The Apostille Process in Arizona
Document Preparation: Ensure your document is notarized by an Arizona notary public.
Submission: Submit the notarized document to the Arizona Secretary of State.
Payment: Pay the applicable fee for the Apostille service.
Processing Time: The processing time varies, but expedited services are available for an additional fee.
Receive Apostille: Once processed, you will receive the document with the Apostille attached.
What is an FDA Certificate of Exportability?
The FDA Certificate of Exportability is a document issued by the Food and Drug Administration (FDA). It certifies that a product, while not authorized for sale in the United States, complies with the requirements of the importing country and can be legally exported.
Why Do You Need an FDA Certificate of Exportability?
This certificate is crucial for businesses exporting food, drugs, and medical devices. It assures foreign authorities that your products meet specific safety and quality standards.
The FDA Certificate of Exportability Process
Determine Eligibility: Ensure your product qualifies for the Certificate of Exportability.
Application: Submit an application through the FDA’s Certificate Application Process (CAP).
Supporting Documents: Provide necessary documentation, such as product labels and evidence of compliance.
Payment: Pay the fee associated with the certificate application.
Review and Approval: The FDA will review your application and, if approved, issue the certificate.
Apostille for FDA Certificate of Exportability in Arizona
Once you have obtained the FDA Certificate of Exportability, you may need to get it Apostilled for use in a Hague Convention country. The process involves:
Notarization: Have the certificate notarized by an Arizona notary public.
Secretary of State: Submit the notarized certificate to the Arizona Secretary of State for Apostille.
Fees and Processing: Pay the applicable fees and wait for the processing to be completed.

0 notes