#Cloud PKI
Text
Microsoft Intune Cloud PKI and Certificate Templates
Microsoft recently announced the general availability of its new PKI-as-a-Service platform called Microsoft Intune Cloud PKI. With Intune Cloud PKI, administrators create certification authorities (CAs) to issue and manage user and device authentication certificates for Intune-managed endpoints. Cloud PKI also provides hosted Authority Information Access (AIA) and Certificate Revocation List…

View On WordPress
#Active Directory#Active Directory Certificate Services#AD#AD CS#ADCS#AIA#authentication#CDP#certificate#certificate authority#certificate template#certificates#Certification Authority#Cloud PKI#CRL#encryption#endpoint manager#InTune#Intune Cloud PKI#MEM#Microsoft#Microsoft Endpoint Manager#Microsoft Intune Cloud PKI#NDES#Network Device Enrollment Service#PKI#public key infrastructure#SCEP#security#Simple Certificate Enrollment Protocol
0 notes
Text
What is an Object Identifier in PKI? How do you obtain an OID?

Do you need to identify and differentiate your Certificate Practice Statement? Get your Object Identifier (OID)!
Organizations that need an identifier for their Certificate Practice Statement can obtain an Object Identifier from a root OID assigned to them. OIDs are like the Internet domain name space, providing a unique identifier for each CPS.
Having your Object Identifier is essential if you want to distinguish and identify your Certificate Practice Statement. With an OID, you'll be able to ensure that each CPS is uniquely identified and differentiated from other ones.
Apply for your Object Identifier now and be sure that your Certificate Practice Statement is uniquely identified! Get started now!
0 notes
Photo
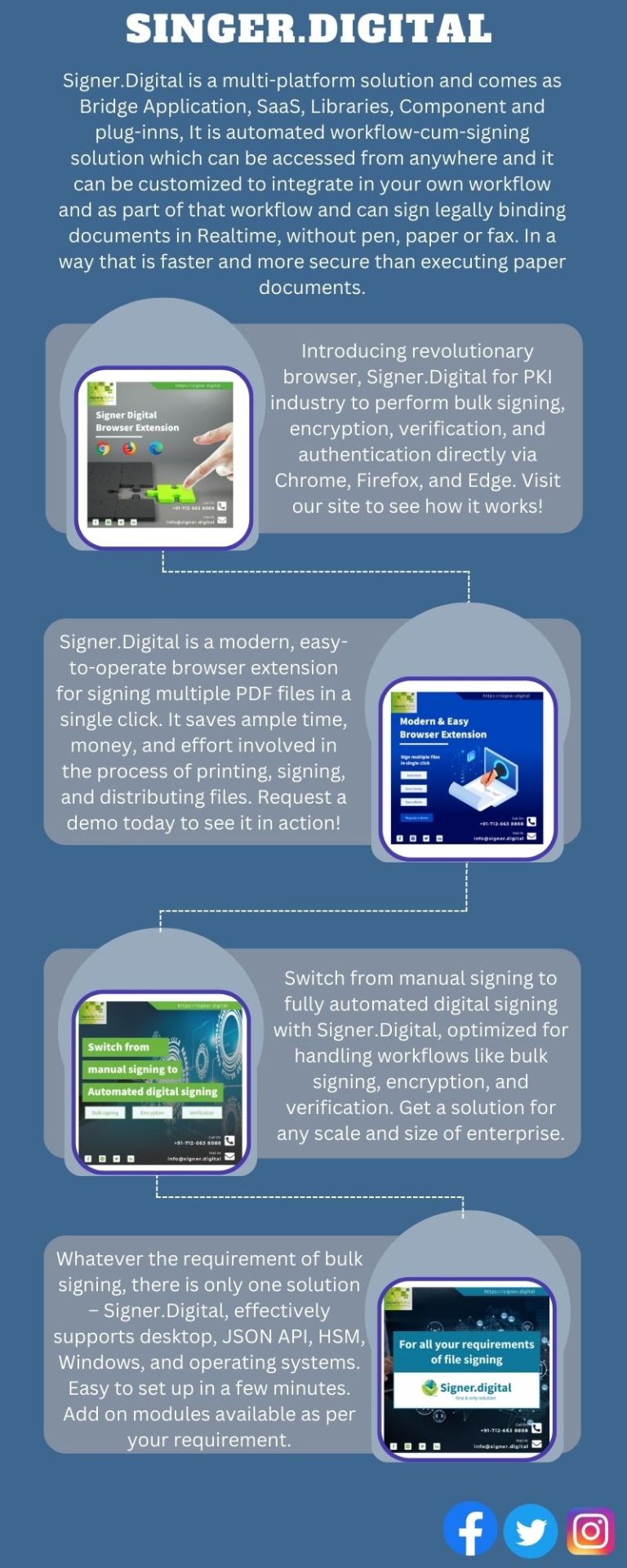
Bulk PDF Signing, Automated Digital Signing, XML JASON Signing
Bulk digital signing supported by signer.digital through Desktop, Server and APIs. It offers solutions like Automated digital signing of document, remote singing HSM signing etc.
0 notes
Text
Increasing Data Breach Incidents Fueling Key Management As A Service Solution Sales
The surging incidents of data breaches is creating a huge requirement for key management as a service solutions worldwide. Data breach leads to the loss of confidential information, such as social security numbers (SSNs) and credit card details. Complex access permissions, improper configuration, malware attacks, and weak passwords can aid cybercriminals in accessing confidential data. Loss of such data leads to major financial losses, which can be avoided through the adoption of key management as a service software by public and private organizations.
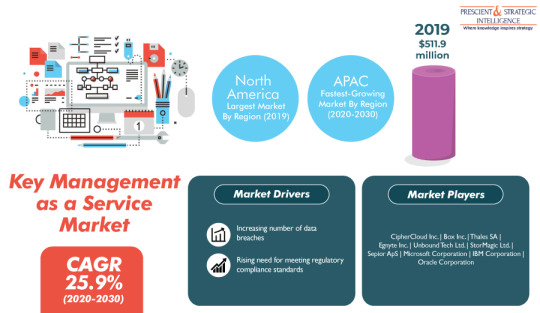
Moreover, the rising preference for cloud encryption is expected to propel the key management as a service market at a CAGR of 25.9% during 2020–2030. According to P&S Intelligence, the market was valued at $511.9 million in 2019. Cloud encryption offers advantages such as regulatory compliance, data privacy, lower information technology (IT) spending, and the capability to store and manage complex data. Additionally, cloud encryption helps businesses in protecting company financial, intellectual property data, and account details stored within the cloud.
In recent years, key management platform providers have been undertaking mergers and acquisitions to offer advanced solutions and software to their customers. For example, in March 2020, NetApp Inc. acquired Talon Storage to merge Cloud Volume products of the former with Fast software of the latter to provide a centralized solution to end users for managing their cloud data. Moreover, through this acquisition, NetApp also hopes to widen its cloud data service portfolio and support the effort of its consumers to transfer files across remote branches of business, in a multi-cloud environment.
Currently, service providers such as Box Inc., Amazon Web Services (AWS) Inc., International Business Machines (IBM) Corporation, Atos SE, NetApp Inc., Google LLC, Kapalya Inc., McAfee LLC, Microsoft Corporation, Unbound Tech Ltd., HyTrust Inc., Oracle Corporation, StorMagic Ltd., and Zettaset Inc. are developing advanced key management platforms for the retail and e-commerce, banking, financial services, and insurance (BFSI), IT and telecom, aerospace and defense, healthcare, and government sectors. These industries use such platforms for disk, cloud, communication, database, and file/folder encryption applications.
Geographically, North America dominated the key management as a service marketin the recent past, due to the extensive use of data center services and analytical tools, high preference of businesses for multi-cloud, rapid adoption of advanced technology to mitigate cyberattacks, and strong presence of cloud service providers in the region. Besides, the surging integration of digital medical records, mounting focus on digitization of the economy, and increasing download rate of several mobile applications in North America will also augment the usage of key management as service solutions in the coming years.
Whereas, Asia-Pacific (APAC) is projected to adopt key management as a service software at the highest rate in the coming years. This can be credited to the soaring need for cloud solutions, mounting awareness regarding cyberattacks and methods to counter them, stepping up digitization efforts, and improving key management lifecycle processes in the region. For instance, in February 2020, Fujitsu Limited, a Japanese multinational IT company, started using Cloud HSM service and key management platform by Thales SA to support public key infrastructure (PKI) security for securing the lifecycle management of cryptographic keys of customers.
Thus, the increasing data breach cases and rising shift toward cloud encryption will fuel the adoption of key management solutions and services in business operations in the foreseeable future.
#Key Management as a Service Market Share#Key Management as a Service Market Size#Key Management as a Service Market Growth#Key Management as a Service Market Applications#Key Management as a Service Market Trends
0 notes
Text
Post-Quantum ready PKI

Ein Anbieter für Identitäts-, Zahlungs- und Datensicherheit hat die allgemeine Verfügbarkeit seiner „Post-Quantum ready“ PKI-as-a-Service (PKIaaS PQ)-Plattform angekündigt. Damit kann das Cloud-basierte PKI-as-a-Service-Angebot des Unternehmens nun sowohl zusammengesetzte als auch reine quantensichere Zertifizierungsstellen-Hierarchien bereitstellen.
Dies ermöglicht es wiederum Kunden, quantensichere Szenarien und Infrastrukturen zu testen oder zu implementieren. Die Lösung von Entrust ist die erste kommerziell verfügbare Plattform dieser Art. „Auch wenn die Bedrohung durch Quantum Computing noch einige Jahre voraus liegt, wird der Übergang zu quantensicheren Algorithmen weit mehr als nur einen weiteren Krypto-Auffrischungszyklus bedeuten. Als Vorbereitung müssen die heutigen Kryptosysteme mit öffentlichen Schlüsseln auf neue quantensichere Kryptoalgorithmen umgestellt werden. Diese Umstellung wird komplexer sein als alle bisher durchlaufenen Migrationsprozesse und wird so gut wie alle digitalen Infrastrukturen und Daten betreffen. Organisationen sollten sich daher jetzt mit ihrer Post-Quantum-Strategie befassen und die notwendigen Technologien zum Test und zur Migration auf quantensichere Lösungen implementieren“, erklärt Greg Wetmore, Vice President, Software Development bei Entrust.
PKI as a Service
Gestützt auf über 25 Jahre Expertise und zahlreiche Innovationen im Bereich PKI ist Entrust PKIaaS ein Cloud-nativer Service, der die PKI-Implementierung und -Verwaltung in Unternehmen durch vorgefertigte, sofort einsatzbereite Zertifikatsanwendungen vereinfacht – einschließlich WSTEP, ACME, SCEP und einer breiten Palette von Mobile Device Management (MDM)-Lösungen. Indem sie die Anzahl der on-premise Dienste, Anwendungen und Software reduziert, macht es die Entrust PKIaaS-Architektur zudem einfach, bedarfsgerecht zu skalieren. Sie ist so konzipiert, dass sie sich nahtlos in bestehende Arbeitsabläufe und Anwendungen integrieren lässt und bietet über die Cloud-Plattform Transparenz, Kontrolle und Automatisierung der Umgebung, zusammen mit öffentlichem SSL/TLS-Management.
Empfehlungen globaler Cybersicherheitsbehörden
Durch Hinzufügung der Post-Quantum-Kryptographie, die auf den Standardalgorithmen des NIST PQ-Entwurfs basiert, können Kunden innerhalb von Minuten quantensichere Zertifikate ausstellen und dabei sowohl zusammengesetzte als auch reine Quanten-Zertifizierungsstellen-Hierarchien verwenden. Dieser Ansatz steht im Einklang mit den Empfehlungen globaler Cybersicherheitsbehörden wie dem BSI in Deutschland und der ANSSI in Frankreich. Diese Organisationen empfehlen, sowohl hybride und zusammengesetzte Zertifikate als auch solche zu testen, die auf reinen quantensicheren Algorithmen basieren.
„Führende nationale Cybersicherheitsbehörden auf der ganzen Welt empfehlen einen hybriden Ansatz für den Übergang zu quantensicherem Datenschutz. Die Verwendung von hybriden oder zusammengesetzten Zertifikaten gewährleistet Schutz in Form von klassischen und quantenresistenten kryptographischen Algorithmen. Mit der aktuellen Produkteinführung kann Entrust diesen Übergang unterstützen und eine schnelle, skalierbare Zertifikatsgenerierung und -verwaltung anbieten. Dieser Ansatz verbessert auch die Implementierung und den Reifegrad von Zero Trust in Unternehmen, da er sensible Daten vor Bedrohungen à la ‚jetzt ernten, später entschlüsseln‘ schützt. Und er stellt sicher, dass digitale Sicherheitsinfrastrukturen auch dann sicher bleiben, wenn die Quantenbedrohung real geworden ist“, ergänzt Wetmore.
Über Entrust
Mit der Schaffung vertrauenswürdiger Identitäten, Zahlungen und Daten setzt sich Entrust für sichere Transaktionen in einer sich laufend verändernden Welt ein. Entrust bietet eine unübertroffene Bandbreite an Lösungen, die Multi-Cloud-Implementierungen, mobile Identitäten, hybrides Arbeiten, Maschinenidentität, elektronische Signaturen, Verschlüsselung und mehr absichern und geschützte Transaktionen ermöglichen.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Text
The Transformative Power of Electronic apostille
In an era where the digital landscape is redefining the way we conduct business and manage information, traditional processes are undergoing a significant transformation. One such evolution is the emergence of electronic apostille, a revolutionary approach to document authentication that harnesses the power of technology to simplify and expedite the international recognition of documents.

Understanding Electronic Apostille:
An electronic apostille, often referred to as e-apostille or digital apostille, represents a departure from the traditional method of affixing a physical certificate to a document. Instead, electronic apostille leverages digital signatures, encryption, and advanced authentication technologies to provide a secure and efficient means of validating the authenticity of a document for international use.
Key Advantages of Electronic apostille:
Speed and Efficiency: Electronic apostille streamline the authentication process, significantly reducing the time required for document validation. With just a few clicks, documents can be digitally apostilled, eliminating the delays associated with traditional, paper-based methods.
Global Accessibility: The digital nature of electronic apostille facilitates instant access from anywhere in the world. This accessibility is particularly advantageous for individuals and businesses engaged in international transactions, allowing for swift and seamless sharing of crucial information.
Enhanced Security: Digital apostille often incorporates robust security features such as cryptographic techniques, ensuring the integrity and authenticity of the authenticated document. This heightened security not only reduces the risk of fraud but also instills confidence in the reliability of the electronic authentication process.
Cost-Effectiveness: Electronic apostille contributes to cost savings by eliminating the need for physical paperwork, printing, and postage. Businesses and individuals can benefit from a more economical and environmentally friendly approach to document authentication.
Technological Enablers of Electronic apostille:
Blockchain Technology: The decentralized and tamper-resistant nature of blockchain technology provides a secure platform for storing and verifying electronic apostille. It creates an immutable and transparent record of transactions, further enhancing the trustworthiness of the authentication process.
Advanced Cryptography: The use of advanced cryptographic techniques ensures the confidentiality, integrity, and non-repudiation of electronic apostille. Public-key infrastructure (PKI) and digital signatures play a crucial role in establishing the authenticity of the digital document.
Cloud-Based Solutions: Cloud technology facilitates the storage, management, and retrieval of electronically apostilled documents. This not only promotes easy access but also enables collaborative efforts, essential for businesses with global operations.
Considerations for Implementation:
Legal Recognition: Achieving widespread acceptance of electronic apostille requires collaboration between governments and international organizations to establish legal frameworks that recognize and support digital document authentication.
Interoperability: Ensuring interoperability between different systems and platforms is crucial for the seamless exchange of electronically apostilled documents across borders. Standardization efforts can contribute to achieving this goal.
As we navigate the digital age, electronic apostille stands as a testament to the transformative power of technology in simplifying and enhancing traditional processes. With their speed, accessibility, security, and cost-effectiveness, electronic apostille represent a forward-thinking approach to document authentication. Embracing this technological evolution is not just a step towards efficiency but a strategic move for individuals and businesses seeking to navigate the complexities of our interconnected and digitized world.
0 notes
Text
Optimizing Google Cloud Certificate Management

Since 1870, Deutsche Bank has offered financial services to enterprises, governments, institutional investors, and individuals worldwide. Google cloud migration requires software developers to build a secure, scalable, and reliable certificate management solution for cloud workloads to better serve and protect our customers.
Deutsche Bank worked with Google Cloud Professional Services to rapidly and securely encrypt data in transit for hundreds of apps. Since the company’s business-critical applications need tens of thousands of network communication encryption certificates daily, it was no easy accomplishment.
The value of certificates
Digital identities are crucial to infrastructure and application security, and X.509 certificates are used to represent them. These have been frequently used to secure network communication, email, and general encryption. Widespread adoption of service-oriented solution architectures has increased certificate-secured entities. Each digital certificate must be renewed before expiration to work.
The industry is shortening certificate durations to reduce security threats, but this increases renewal frequency. Failure to renew, cancel, or distribute trustworthy certificates can cause service disruptions and security breaches.
Google Cloud CA Service
Extension of on-premises PKI services to cloud applications relies on Google Cloud Certificate Authority Service (CAS). CAS brings enterprise certificate management from on-prem to the cloud and provides convenient tools and services for an automated and integrated solution that complements CAS integrations by serving as a fully managed central authority for all enterprise workloads running in public clouds.
The ability to issue custom organization certificates flexibly, securely, and on-demand is just the beginning of our certificate management journey. With dozens of managed services from Google Cloud, CAS certificates must be used beyond present use-cases to ensure cloud-on-prem system connection.
Thus, a centralized, automated custom certificate lifecycle management solution is needed to relieve application developer teams of cloud services configuration, concentrate the responsibilities, and make them manageable by a small team.
Large-scale certificate management issues
Business preferences and organizational and legal needs for certificates vary. Our sector is extensively regulated and security-focused, therefore we have more goals. Here are some key ones:
Operation
Reduce cost, availability, and security threats by automating as much as feasible.
Make certificate management transparent for apps to relieve application teams of certificate expiration and renewal concerns.
Security
Maintain strong client trust for internet-facing apps. Secure applications with public certificate authorities (CA) certificates and the strictest identity verification measures to protect the brand and users.
Define production and non-production trust boundaries. Certificates must be issued by separate trust anchors to prevent data breaches and improve production security.
Validate application domain ownership for certificate issuance. Enterprises run thousands of apps and services. They must restrict application subdomain use. Thus, applications requesting certificates for unauthorized subdomains must be denied.
Governance
Use only recognized CA certificates. Companies control cryptographic services to manage trust and reduce risk.
Organizational certifications should be monitored. Inventorying certificates with their owners, locations, and algorithms helps report and respond to present and future cryptographic risks. Possible threats from the post-quantum revolution.
When regulators require specific certificate kinds, utilize them. EU Directive for Electronic Payment Services (PSD2) requires QWAC and QSEAL certificates from trust service providers established in the EU eIDAS Regulation.
Managing so many certifications requires automation.
Automate certificate management
We solve our certificate management problems with CAS and other Google Cloud services. The figure below shows its high-level architecture.
This method helps in various situations:
Initial enrollment and certificate provisioning: Use IaaC to provision a new certificate with a valid identity (Subject, Subject Alternative Name) that meets organization security policy.
Update certificate content: Modify a certificate’s SAL.
Certificate renewal: Create a fresh re-validated certificate before the expiration date and replace the expired certificate automatically without application team intervention.
Certificate revocation: If a certificate key is compromised or lost, revoke the certificate to invalidate and stop data exchange over network connections.
Trust Anchor management: Provide current Trust Anchors (authorized root CA certificates) for certificate-validating services and apps. Distribute and store trusted CA certificates in client and server programs for TLS validation.
Certificate Authority renewal: Certificate Authority certifications expire and must be renewed. Following industry best practice, CA lifespans are decreasing.
Effects and Gains
Once the central certificate management solution is implemented, enterprises should realize many benefits.
Deutsche Bank has a security staff that centrally handles all certificates. Without automated regular procedures and compliant PKI services, Deutsche Bank would be much smaller. Eliminating manual steps and automating certificate management has cut expenses and application disruptions. Since deploying the solution to production, certificate expiration has not caused application issues.
Due to reputation, cost, and regulation compliance, organizations need high application availability, especially for internet-facing services. Built with Google Cloud services, certificate management automation is modern, reliable, and future-proof, meeting high availability and scalability needs without additional effort.
Our solution simplifies data in transit encryption for application teams and complements Deutsche Bank’s defense-in-depth strategy. Key creation with high entropy is secure and weak keys are prevented. Besides the owner program or resource, these important cryptographic assets are encrypted throughout the operation. We can now securely reduce certificate lifetime.
A team of experts in their difficult field monitors, controls, and takes responsibility for certificates. CAS stores and monitors all Deutsche Bank cloud-based internal certificates.
Conclusion
Google Cloud services like Cloud Key Management Service and Certificate Authority Service helped us scale certificate management with minimum resources. CAS was in beta when Google used it for our cloud architecture, and Google built a dependable certificate management platform in Google Cloud and met their aims.
0 notes
Link
0 notes
Text
C|CL Certificate In Cyber Law
About Service
Certified Ethical Hacker C|EH with HackTechMedia
Exam Details
Number of Questions: 125
Test Duration: 4 Hours
Test Format: Multiple Choice
Test Delivery: ECC EXAM, VUE
Exam Prefix: 312-50 (ECC EXAM), 312-50 (VUE)
Basic of computer and Cyber Security
1. History of Computers, Areas of Application
2. Computers and its components, Application Software and System Software
3. Introduction to Operating System
4. Basics of Networks and internet, Types of Network, Definition of Cyber Security
5. Search Engines, E –mails and WWW; Internetworking Devices, Internet Service provider, IP Address, Working of Email system, Domain Name System, Blogs, Peer to peer sharing
6. Cryptography, type, goals , PKI
7. Digital signatures and electronic signatures, Electronic Payment System and Taxation.
8. Computer & Cyber Security:
(a) Types of Attacks,
(b) Network Security
(c) Overview of Security threats,
(d) Hacking Techniques,
(e) Password cracking
(f) Insecure Network connections,
(g) Malicious code
(h) Concept of Fire wall Security
9. Email security: web authentication, SSL and SET
10. Database Security
11. Operating System Security
12. E – commerce & M – commerce System Security 13. Advance Computers, Network & Mobile Security Techniques
Information Technology Law (Cyber Law)
1. Evolution of the IT Act, Genesis and Necessity
2. Salient features of the IT Act, 2000, various authorities under IT Act and their powers. ; Penalties & Offences, amendments.
3. Impact on other related Acts (Amendments) : (a) Amendments to Indian Penal Code. (b) Amendments to Indian Evidence Act. (c) Amendments to Bankers Book Evidence Act. (d) Amendments to Reserve Bank of India Act.
4. Cyber Space Jurisdiction
(a) Jurisdiction issues under IT Act, 2000.
(b) Traditional principals of Jurisdiction
(c) Extra terrestrial Jurisdiction
(d) Case Laws on Cyber Space Jurisdiction
5.E – commerce and Laws in India (a) Digital / Electronic Signature in Indian Laws (b) E – Commerce; Issues and provisions in Indian Law (c) E – Governance; concept and practicality in India (d) E – Taxation issues in Cyberspace (e) E – Contracts and its validity in India (f) Cyber Tribunal & Appellate Tribunal (g) Cyber Regulations
6. Intellectual Property Rights, Domain Names and Trademark Disputes (a) Concept of Trademarks / in Internet Era (b) Cyber Squatting (c) Reverse Hijacking (d) Jurisdiction in Trademark Disputes (e) Copyright in the Digital Medium (f) Copyright in Computer Programmes (g) Copyright and WIPO Treaties (h) Concept of Patent Right (i) Relevant Provisions of Patent Act 1970
7. Sensitive Personal Data or Information (SPDI) in Cyber Law (a) SPDI Definition and Reasonable Security Practices in India (b) Reasonable Security Practices – International perspective
8. Cloud Computing & Law
9. Cyber Law : International Perspective (a) EDI: Concept and legal Issues. (b) UNCITRAL Model Law. (c) Electronic Signature Law’s of Major Countries (d) Cryptography Laws (e) Cyber Law’s of Major Countries (f) EU Convention on Cyber Crime.
#hacktechmedia#hacking#hacker#cybersecurity#ethicalhacking#hackers#linux#programming#hack#technology#kalilinux#security#coding#infosec#python#tech#hackingtools#ethicalhacker#pentesting#cybercrime#cyberattack#informationsecurity
1 note
·
View note
Text
Global Hardware Security Modules Market Growth, Analysis, and Forecast 2022-2027
Global Hardware Security Modules Market was valued at USD 1.2 billion in 2021 and is expected to reach 2.6 billion by 2027, at a CAGR 9.85% from 2022-2027.
Hardware Security Modules (HSM) is defined as a piece of hardware and associated software or firmware which is attached to and placed inside a particular hardware that serves cryptographic functions. Its functions mainly include encryption, decryption, management or generation and hashing. HSM systems can securely back up the keys that could be handled using some external security token such as smart cards or via operating systems of the computer.
Get a Sample Copy of this Report@ https://qualiketresearch.com/request-sample/Hardware-Security-Modules-Market/request-sample
Market Drivers
The major factor leading to the increasing growth of the hardware security modules market is growing data security concerns in all the data sensitive companies globally. Hardware security modules are responsible for efficiently storing and managing cryptographic keys. Comprehensive data protection will lead to increased demand for hardware security modules in near future, resulting in market development.
Furthermore, the growing usage of Hardware security modules in government and defense sectors has recently been identified as a critical reason for industry growth.
Market Restraints
Hardware security modules are costly and very expensive. This is one of the reasons that is holding back the growth in the hardware security modules market because currently, only very large companies can afford to use them.
Market Segmentation
The Global Hardware Security Modules Market is segmented into, type, deployment type, application, sales channel, and industry vertical. The type segment has further been segmented into remote interface, local interface, smart cards, and USB tokens.
Regional Analysis
The Global Hardware Security Modules Market is segmented into five regions such as North America, Latin America, Europe, Asia Pacific, and Middle East & Africa.
The North American region is expected to hold a major share in the hardware security module market. Growth in this region is attributed to penetration and adoption of security modules, and presence of a large number of vendors across the region.
Get Discount on this Report@ https://qualiketresearch.com/request-sample/Hardware-Security-Modules-Market/ask-for-discount
Key Players
Various key players are discussed into the Global Hardware Security Modules Market Report including: Thales Group (Gemalto), Utimaco GmbH, Futurex, Adweb Technologies, Yubico, Atos, Ultra Electronics, SPYRUS, Inc., Securosys, Entrust Corporation, Nitrokey, Kryptoagile, IBM Corporation, and others.
Market Taxonomy
By Type
Local Interface
LAN-based HSMs/Network-attached HSMs
PCIe-based/Embedded Plugin HSMs
Remote Interface
Smart Cards
USB Tokens
By Deployment Type
On-Premise
Cloud
By Application
Authentication
Database Encryption
Document Signing
Secure Socket Layer (SSL)
Code Signing
PKI/Credential Management
Payment Processing
Application-Level Encryption
By Sales Channel
Direct Sales Channel
Distribution Channel
Integrators
Distributors
VARs
By Industry Verticals
Banking
Financial Institutions
Government
BFSI
Technology and Communication
Industrial
Manufacturing
Energy and Utility
Retail and Consumer
Healthcare and Life Sciences
Other (Transportation, Automotive, and Hospitality)
By Region
North America
Latin America
Europe
Asia Pacific
Middle East & Africa
Browse Full Report https://qualiketresearch.com/reports-details/Hardware-Security-Modules-Market
0 notes
Text
Public Key Infrastructure Market Trend, Segmentation and Opportunities Forecast To 2032
Global Public Key Infrastructure Market share is expected to grow substantially through 2032 due to the increasing concerns related to safeguarding intellectual property assets.
To protect their Intellectual Property (IP) assets, such as design data and product development information, companies are putting more and more emphasis on using PKI. Unencrypted data can result in data leaks and thefts, putting financial pressure on businesses trying to resolve patent disputes.
Prominent public key infrastructure market players are effortlessly working on introducing innovations in the market to gain a competitive edge over others. For instance, in May 2021, WISeKey collaborated with Ocean Protocol (Ocean), a decentralized exchange protocol that unlocks AI data, to develop TrustedNFT.io. The alliance enables WISeKey to increase its visibility in the NFT sector.
Request for a sample copy of this research report @ https://www.gminsights.com/request-sample/detail/3727
Based on service, the managed service segment is anticipated to propel at more than 27.5% CAGR from 2023 to 2032. Managed services minimize the need to deploy new software components and aid in the reduction of operational costs, thus driving the public key infrastructure market growth.
With respect to organization size, the large enterprises segment is speculated to expand positively over the review years credited to the growing trend of Bring Your Own Devices (BYOD) among businesses. This increase in BYOD trends has supported the growing adoption of PKI solutions across large corporations.
In terms of application, the BFSI segment is poised to garner sizeable growth through 2032 fueled by the rise in data breaches and disclosures across the BFSI industry. Moreover, attacks on web application authentication systems by banking Trojan botnets would further stimulate the product demand.
Meanwhile, the government & defense segment recorded more than 7% revenue share in 2022. The rise in cyberattacks is likely to drive the segmental growth, promoting national security organizations to use cutting-edge and secure technologies to safeguard their data.
Browse report summary @ https://www.gminsights.com/industry-analysis/public-key-infrastructure-pki-market
From the regional perspective, the North America public key infrastructure market is projected to expand at approximately 20% CAGR from 2023 to 2032. Growing digitization has enabled businesses in the region to improve the accessibility of their resources. Major utility service providers are utilizing IoT-based public-key encryption technologies to secure their transactions, thereby propelling the industry landscape.
On the other hand, the Latin America public key infrastructure market is estimated to proliferate robustly by the end of the research period ascribed to the increasing use of the cloud for data storage. Organizations in LATAM economies are using modern data security solutions to prevent data breaches which will further boost the regional expansion.
Browse Our Reports Store - GMIPulse @ https://www.gminsights.com/gmipulse
About Global Market Insights Inc.
Global Market Insights Inc., headquartered in Delaware, U.S., is a global market research and consulting service provider, offering syndicated and custom research reports along with growth consulting services. Our business intelligence and industry research reports offer clients with penetrative insights and actionable market data specially designed and presented to aid strategic decision making. These exhaustive reports are designed via a proprietary research methodology and are available for key industries such as chemicals, advanced materials, technology, renewable energy, and biotechnology.
Contact Us:Aashit Tiwari
Corporate Sales, USA
Global Market Insights Inc.
Toll Free: 1-888-689-0688
USA: +1-302-846-7766
Europe: +44-742-759-8484
APAC: +65-3129-7718
Email: [email protected]
0 notes
Text
Microsoft Intune Cloud PKI
Recently, Microsoft introduced the general availability of its new PKI-as-a-service solution called Microsoft Intune Cloud PKI. Cloud PKI allows administrators to issue and manage user and device authentication certificates for Intune-managed endpoints without deploying Active Directory Certificate Services (AD CS) on-premises. Cloud PKI frees administrators from the burdens of deploying and…

View On WordPress
#authentication#Azure#BYOCA#certificate#certificates#Certification Authority#cloud#Cloud PKI#device authentication certificate#InTune#Intune Cloud PKI#issuing CA#issuing certification authority#Microsoft#Microsoft Intune#Microsoft Intune Cloud PKI#PKI#PKI-as-a-Service#public cloud#root CA#root certification authority#SCEP#Simple Certificate Enrollment Protocol#user authentication certificate
0 notes
Video
youtube
The evolution of encryption into an essential part of data protection strategies over the years has made it a critical component of security posture across various sectors and industries.
It is estimated that 42% of organizations are confident of increasing their budget expenditures on encryption in FY22-23.
According to Encryption Consulting study on global encryption trends – 2023, firms are becoming more aware of encryption and are planning to adopt it as a core data security technology.
In Survey Trend Analysis, the following data is gathered:-
1. In FY20, only 27% of the responding organizations had encryption strategies as a primary focus, but that figure increased to 70% in FY21.
2. Enterprise encryption strategies are adopted on average by 50% of enterprises in the world.
3. According to the survey, 65% of respondents said protecting customer information was their top concern.
0 notes
Text
How To Optimize Cloud Storage Without Compromising Security ?

How To Optimize Cloud Storage Without Compromising Security ?
Cloud storage is an excellent option for businesses and individuals looking to store their files. It offers greater flexibility in where your files are located and how they’re shared with other users. You can access your files from any device with an internet connection, including smartphones and tablets. This makes it easier for employees to use assets on the go without having to carry their laptops around with them.
However, it can be hard to find an exemplary cloud service without compromising your data security. If your provider doesn’t prioritize that, you’ll become vulnerable to threats like ransomware. As a result, your operations may suffer, straining your connections and costing you your customers.
If you want to optimize your cloud storage without compromising safety, here are five tips and tricks you should follow:
Use Two-Factor Authentication
Two-factor authentication adds an extra layer of security by requiring another factor besides your password. For example, you might type in a passcode sent via text message or use a unique app that generates a code every five minutes. This makes it harder for hackers and cybercriminals to breach a user’s account since they would need both the password and the secondary identification.
You can work with a high-quality IT support company in your area to implement two-factor authentication. It may provide you with a program that generates codes on your phone rather than having them sent via text message. While this may seem inconvenient at first, it’s much safer than short message service (SMS) verification because of how easily text messages can be intercepted by hackers monitoring your communications.
Encrypt Your Data
Encryption is the process of converting data into code, making it unreadable to anyone who doesn’t have the key to decipher it. With this, anybody who gains unauthorized access to your files can’t use them without first decrypting them. This robs them of an opportunity to sabotage your operations.
There are plenty of different encryption algorithms; some are more secure than others, and the ease of implementation also varies.
The most common option is advanced encryption standard (AES), which uses 128-bit or 256-bit keys. This kind of data encryption has compatibility across platforms and applications, which helps you keep your data safe even if the cloud service provider suffers a breach.
Another option is to use public key infrastructure (PKI) encryption, which allows users to share files without decrypting them first. PKI uses asymmetric cryptography. This means that you’ll need two keys: one private and one public. The private key must be kept secret; otherwise, anyone who gets hold of it will be able to decrypt your data.
Implement A Password Manager
Encrypting files and folders is only half the battle. You also need to consider how you’re going to access them. If someone gets their hands on your password, they’ll be able to access all of your files, no matter how tight your security may be.
That’s why a password manager is essential, especially if you have multiple devices for work and personal tasks. A password manager stores all your passwords in an encrypted database so that only you can access them. This allows you to safely store passwords without compromising any of them in case someone gets their hands on your device or computer.

Incorporate Anonymization Services
Anonymization services have been around for a while now. You can use them to hide personal information stored in public databases. This means that if someone were to steal your details from a cloud storage service, they wouldn’t be able to connect those details with your real-world identity. These services work by replacing real names with pseudonyms, which makes it much harder for anyone to link them.
When using anonymization services to protect your cloud storage data, make sure you work with an accredited company that can guarantee the safety of your information. You should also check whether or not they offer encryption and pseudonymization. If you want your data to remain safe even if it gets stolen or leaked by accident, these are essential.
Ensure Proper Permissions Management
When you set up your cloud storage, ensure that only those who must use the data have access to it. This should be further limited to when they need it to do their jobs.
This will help prevent unauthorized people from accessing sensitive information. It also ensures that no one person has too much power over another employee’s data.
For example, don’t give everyone on your team the ability to read or edit data. Instead, give them only those permissions that are necessary for their jobs. This will help prevent unauthorized access or data leaks caused by accidental file sharing.
Key Takeaway
Cloud storage is beneficial in storing your business data, but you must prioritize the safety of your data. Consider these five tips to make full use of this innovation without sacrificing security. Once you do so, you can sustain your company’s progress in the long run.
Read the full article
0 notes
Text
RMail’s Secure Cloud Email Gateway Service Harmoniously Runs as The Final Outbound Email Hop
RMail Email Encryption Elegance and Email Eavesdropping™ Detection Are the Main Reasons Why Customers with Other Email Security Gateway Servers Still Route Outbound Messages via RMail Gateway.
Los Angeles, CA – November 16, 2022
RPost continues to attract new customers to Harmony™ — the configuration of RMail email security services running harmoniously with other email security gateway services or servers. These customers choose RMail as the final outbound email hop, even though they already have another email security gateway service or server, sometimes one that even includes some basic email encryption.
Krankenhaus Wermelskirchen GmbH, a health care clinic in Germany, for example, had two other outbound security services, but neither met their requirement of a simple user experience for recipients outside of their existing encryption service plus delivery in a manner that the message remained secure even while inside the recipient’s inbox. “The uniqueness of RMail, the built-in demonstrated compliance record and the ease of its Harmony method of extending other email security services, checked all the boxes,” affirms Volker Sommerfeld, product manager of Frama Communications, the RPost partner that serviced this customer.
“We had a server that managed PKI key exchanges to encrypt email when we had the luxury of having the secret key of the recipient in our system – the problem was the lack of a solution for recipients who were not in possession of such keys. And, to make the situation untenable, for these other non-key messages, the email encryption offered by the other provider had a user experience at the recipient that was fraught with challenges,” states the IT-Director at the healthcare clinic Wermelskirchen. “We had Fortinet as well, primarily for inbound security but also for outbound data leak prevention. Even though we had these other two services – which we still have, for good reasons – we chose to invest in adding RMail. The RMail Gateway team was proficient in setting up complex email routing rules so that if there was not a secret encryption key exchange possible, the email would automatically route via RMail encryption. Perfect security bliss.”
“The customer needed first, assurance and proof of GDPR privacy compliance. RMail checked that box. They then needed encryption that remained private even while in the recipient inbox. RMail does that. Further, they needed to be sure that there was no requirement for special software to decrypt or read the email; no PDF readers, nothing. RMail meets that need. Finally, they needed a way to automate the decision on what to send encrypted via which service — their existing PKI key exchange or via RMail depending on complex rules. RMail excels there,” added Sommerfeld. “RMail simply meets all of our customers’ needs, from security, to compliance, to automation to, and arguably most importantly, Harmony – working well alongside our existing services.”
“Needs are changing. Email encryption must be used today in higher volume — and therefore the user experience matters more and more. Because of this, most of our RMail customers maintain what they are comfortable with their inbound anti-spam, anti-virus, and anti-malware email security, and wrap RMail around these other services for a final outbound hop via RMail Gateway secure email gateway cloud service,” states RPost CEO Zafar Khan.
“We’ve seen many RMail customers use RMail with services like Microsoft Exchange / Microsoft 365, Mimecast, Fortinet, Proofpoint, Barracuda, and other email security gateway services, primarily for the elegant user experience with RMail email encryption with its dynamically adapting message level security, plus its Registered Receipt™ tracking and proof of compliance,” adds Khan.
RMail Gateway secure email service can be configured for any email platform – from Microsoft to Gmail to Zimbra and more – or to harmoniously extend any other email security gateway.
RMail Gateway also includes Registered Email™ track and prove, eSignatures, email encryption that dynamically adapts to the recipient or security needs, Registered Encryption™ proof of privacy compliance, PRE-Crime™ intelligence for BEC and wire fraud protection, and Active Tracker™ email view location activity tracking.
About RPost:
We’re the global leader in premium, feature-rich and more affordable eSignature and cybersecurity services, and we’ve been continuously innovating for our customers the world over since 2000. From within our three main platforms, RMail e-security, RSign eSignatures, and Registered™ e-compliance, we’re everything our customers need when it comes to email, document and form security, compliance, and workplace acceleration — track, prove, eSign, encrypt, share, certify, control. We do what no other company does — all in one.
We thrive on ensuring that we are artisans and experts in everything we do: secure and certified email encryption for privacy and compliance; eSignatures and web forms to ease digitization of workflows; e-delivery tracking to prove important communications; managed file transfer to simplify secure sharing of large documents and sets of files; document-level digital rights management to empower control of document access even after transmission; and AI-infused apps to prevent data leaks by minimizing human e-security errors. This is why more than 25 million users have enjoyed our RMail, RSign, and Registered services for over two decades across 193 countries. Learn more at the RPost website.
0 notes
Text
Firefly schützt Maschinenidentitäten in Cloud-nativen Workloads

Venafi, der Erfinder und führende Anbieter von Maschinenidentitäts-Management, stellt Firefly vor. Die Lösung unterstützt hochgradig verteilte Cloud-native Umgebungen. Als Teil des Venafi Control Planes für Maschinenidentitäten ermöglicht sie die einfache und sichere Umsetzung von entwicklergesteuerten Anforderungen an die Verwaltung von Maschinenidentitäten für Cloud-native Workloads.
Maschinenidentitäten wie TLS und SPIFFE werden lokal und mit hoher Geschwindigkeit in jeder beliebigen Umgebung bereitgestellt. Durch zusätzliche Geschwindigkeit, Zuverlässigkeit und Sicherheit für Maschinenidentitäten in modernen Umgebungen können Unternehmen das Vertrauen in ausgestellte Zertifikate und die Einhaltung der Sicherheitsrichtlinien des Unternehmens garantieren und gleichzeitig die Anwendungsentwicklung und digitale Transformation vorantreiben.
Maschinenidentitäten in modernen Anwendungsbereichen
„Mit der steigenden Anzahl von Unternehmen, die auf moderne, Cloud-native und hoch verteilte Strukturen umsteigen, steigt die Nachfrage nach Maschinenidentitäten in modernen Anwendungsbereichen, die in großem Umfang und mit nahezu null Latenz zur Verfügung gestellt werden müssen, um die wichtigsten Anforderungen an die Authentifizierung zu erfüllen“, sagt Shivajee Samdarshi, Chief Product Officer bei Venafi. „Firefly adressiert diese entscheidenden Herausforderungen auf eine schnelle, einfache und sichere Weise. Es verringert Sicherheitsrisiken und vermeidet gleichzeitig Ineffizienzen, die Entwicklungsteams oft ausbremsen, und macht Unternehmen zukunftssicher für die Herausforderungen von morgen.“
Einfach zu implementierender Container
Firefly wird als einfach zu implementierender Container geliefert, der in jeder nativen Cloud-Umgebung ausgeführt werden kann und eine schnelle, einfache und sichere Möglichkeit zur Ausgabe von Maschinenidentitäten bietet. Die Identitätsrichtlinien für Maschinen werden in der Venafi Control Plane festgelegt und an die Firefly-Instanzen weitergegeben. Zusammen bieten Venafi Control Plane und Firefly eine leichtgewichtige, verteilte Struktur. Sie bietet eine lokale, autonome Hochgeschwindigkeitsausgabe, die Cloud-native Anwendungsfälle mit geringer Latenz und fortgeschrittene CI/CD mit einem in die Pipeline eingebetteten Identitätsanbieter erfordern.
Die wichtigsten Funktionen umfassen:
- Beobachtbarkeit - Durch das Venafi Control Plane bietet Firefly Einblick in verteilte Ausgabeaktivitäten. Dies erweitert die Beobachtbarkeit der Control Plane von Maschinenidentitäten vom Rechenzentrum auf die Cloud und den Edge.
- Konsistenz - Firefly gibt Sicherheitsteams die Kontrolle über die Richtlinien für Maschinenidentitäten, die an moderne Anwendungen in nativen Cloud-Umgebungen ausgegeben werden, und gewährleistet, dass Entwickler einen sicheren und konsistenten Aussteller verwenden.
- Zuverlässigkeit - Firefly erfordert nur eine geringe Infrastruktur für die Bereitstellung in der Produktion, um eine hohe Verfügbarkeit und Fehlertoleranz zu erreichen.
- Wahlfreiheit - Firefly bietet mehrere Bereitstellungsoptionen, darunter Cloud Native, DevOps, Cloud und föderierte PKI-Umgebungen, so dass Entwickler Firefly flexibel einsetzen können, wo und wann immer es benötigt wird.
„Bei Diebold Nixdorf ist die Umstellung von Legacy-Anwendungen auf Cloud-Native eine Priorität für uns. Wir müssen Entwicklern und Plattformteams eine Möglichkeit geben, Maschinenidentitäten auszustellen und zur Verfügung stellen, die Lösung muss leichtgewichtig sein, auf allen Cloud-Plattformen funktionieren. Darüber hinaus muss sie schnell sein und einfach zu implementieren“, sagt Scott Barronton, CISO bei Diebold Nixdorf. „Venafi Firefly erfüllt diese Anforderungen. Außerdem bietet es Sicherheitsteams Sichtbarkeit und Richtlinienkontrolle über Maschinenidentitäten. Es kombiniert das Beste aus zwei Welten - wir können so schnell wie nötig arbeiten und das auf sichere Weise.“
Weiterführende Informationen:
- Announcement Blog Post
- Introducing Venafi Firefly Video
- Venafi Firefly Data Sheet
- Venafi Firefly Deployment Patterns Whitepaper
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes