#pki solution
Text
Protect your Keys in a Digital World

Grab the opportunity to join one of the most awaited webinar on the topic "Protect your Keys in a Digital World" and get a chance to hear from the world's leading experts - David Wakeman and Kenisha Williams on Apr 3, 2023, at 10:00 AM by simply registering yourself.
In this webinar, you will be provided with information about the history and evolution of cryptography, its keys, its importance, and the challenges associated with securing sensitive data.
As more and more organizations move sensitive data to the cloud, knowing where your encryption keys are and who controls them is more important today than ever before, especially as cryptography, keys, and how they protect your data pose a challenge to most organizations.
So, do not miss this amazing opportunity to learn from the experts and register now!
0 notes
Photo
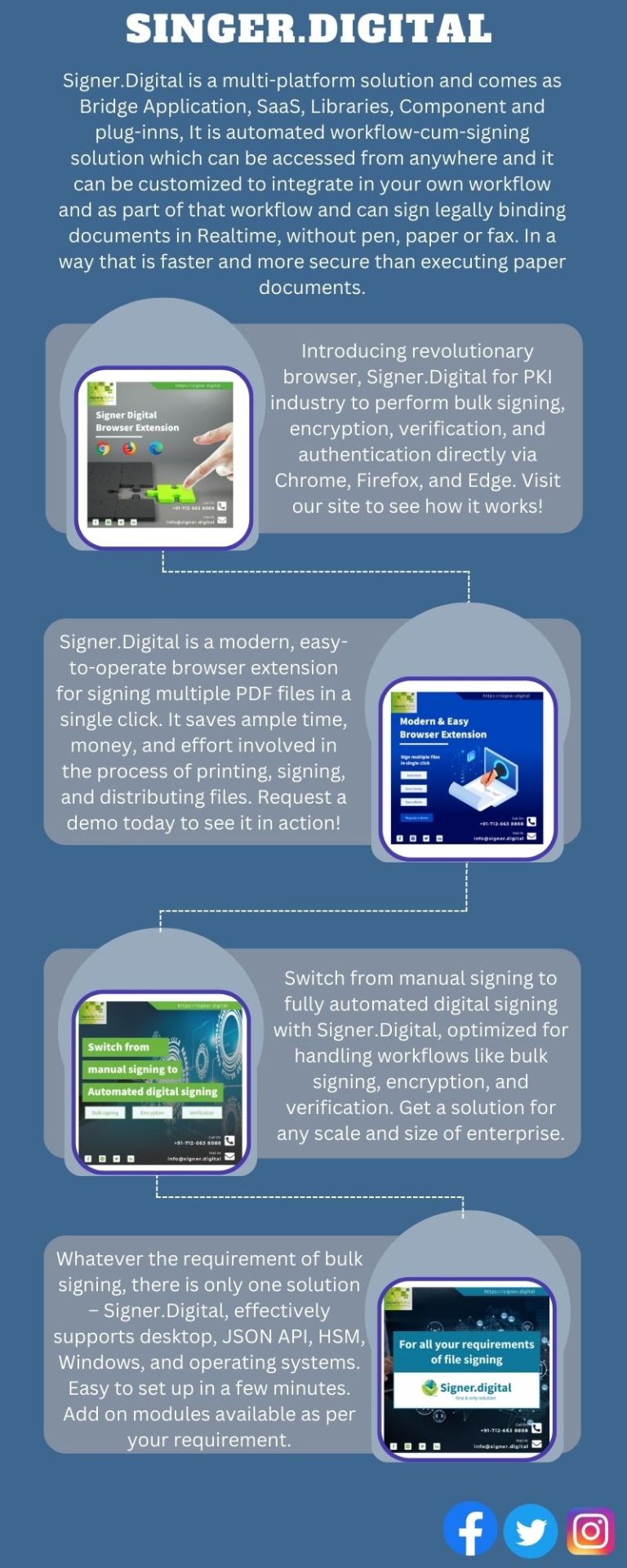
Bulk PDF Signing, Automated Digital Signing, XML JASON Signing
Bulk digital signing supported by signer.digital through Desktop, Server and APIs. It offers solutions like Automated digital signing of document, remote singing HSM signing etc.
0 notes
Text
FIDO Authentication Industry Hits $1.24 Billion in 2023, Set to Soar to $12.06 Billion by 2033
The FIDO Authentication Market has witnessed remarkable growth, with the total revenue reaching US$ 1,238.6 million in 2022. This impressive growth trajectory is projected to continue, with the market expected to surge to US$ 12,059.7 million by 2033, reflecting a robust Compound Annual Growth Rate (CAGR) of 23.1% from 2023 to 2033.
Get Sample Copy of this Report at:
https://www.futuremarketinsights.com/reports/sample/rep-gb-12485
Drivers and Opportunities:
The market’s expansion is driven by several factors, including the increasing adoption of FIDO authentication solutions across various industries. The rising concerns over cybersecurity threats have prompted organizations to seek robust authentication methods, further fueling market growth. Additionally, the growing popularity of biometric authentication methods and the proliferation of mobile devices are providing lucrative opportunities for market players to innovate and expand their offerings.
Competitive Landscape – Regional Trends:
The FIDO Authentication Market is highly competitive, with key players constantly innovating to maintain their market position. Regional trends indicate that North America dominates the market, owing to a high concentration of tech-savvy enterprises and stringent security regulations. Europe follows closely behind, driven by increasing awareness of data security. Meanwhile, the Asia-Pacific region presents significant growth potential due to the rapid digitalization of economies and the need for robust authentication solutions.
Restraints:
Despite its rapid growth, the market faces certain limitations, including concerns related to user privacy and data protection. Striking a balance between stringent security measures and user convenience remains a challenge for market players. Moreover, the high initial costs associated with implementing FIDO authentication solutions may hinder adoption among smaller enterprises.
Region-wise Insights – Category-wise Insights:
Regionally, North America leads the FIDO Authentication Market, with a substantial share of the global market. Within categories, biometric authentication solutions are gaining prominence due to their accuracy and user-friendliness. Moreover, the healthcare and financial sectors are witnessing substantial adoption of FIDO authentication, driven by the need for secure access to sensitive data.
Request for Methodology:
https://www.futuremarketinsights.com/request-report-methodology/rep-gb-12485
Competitive Landscape
As organizations around the world are challenged in controlling dynamic and hybrid IT environment, the need for secure mobile or online applications without compromising user convenience is increasing continuously.
Owing to this, most of the leading players in the FIDO authentication technology are coming with advanced and innovative solutions that meets the ever-changing demand from organizations for advanced security and privacy concerns.
In January 2021, Aware, Inc. announced the launch of AwareABIS, an automated biometric identification system (ABIS) used for large-scale biometric identification and deduplication. Designed to serve among 1-30 million identities or more, AwareABIS supports fingerprint, face and iris modalities, and features a modular architecture that helps security teams configure and optimize the system for civil or criminal applications.
FIDO Authentication Outlook by Category
By Solution:
FIDO U2F Authentication Devices
FIDO Authentication SDKs
FIDO Client SDK
FIDO Server SDK
Services
Technology Consulting
Integration & Deployment
FIDO Certification Services
Support Services
By Application:
Payment Processing
PKI/Credential Management
Document Signing
User Authentication
Others
By Industry:
BFSI
Healthcare & Life Sciences
IT & Telecom
Retail & CPG
Government & Defense
Energy & Utilities
Others
By Region:
North America
Latin America
Europe
East Asia
South Asia & Pacific
Middle East and Africa
0 notes
Text
do you want to secure this network with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you want to secure this network with vpn
VPN Security Protocols
VPN (Virtual Private Network) security protocols are the backbone of secure online communication. These protocols dictate how data is transmitted and encrypted over the VPN network, ensuring confidentiality, integrity, and authenticity of information exchanged between devices.
One of the most widely used VPN security protocols is OpenVPN. Known for its open-source nature and robust encryption capabilities, OpenVPN supports various cryptographic algorithms and is highly configurable. It operates on both UDP (User Datagram Protocol) and TCP (Transmission Control Protocol), offering flexibility in different network environments.
Another popular VPN protocol is IPSec (Internet Protocol Security). IPSec provides a suite of protocols for securing Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. It can be implemented in tunnel mode for VPNs, ensuring end-to-end security.
L2TP/IPSec (Layer 2 Tunneling Protocol over IPSec) combines the simplicity of L2TP with the security of IPSec, offering a secure VPN solution. While L2TP doesn't provide encryption itself, when combined with IPSec, it becomes a secure option for VPN connections.
SSTP (Secure Socket Tunneling Protocol) is another VPN protocol developed by Microsoft. It leverages SSL/TLS encryption to secure the connection between the client and the server. SSTP is commonly used in Windows operating systems and is known for its compatibility and ease of configuration.
Additionally, WireGuard is gaining popularity for its simplicity, speed, and modern cryptographic design. It aims to be faster and more straightforward to configure than traditional VPN protocols while maintaining high-security standards.
In conclusion, VPN security protocols play a crucial role in safeguarding online privacy and security. By understanding the strengths and weaknesses of different protocols, users can make informed decisions to ensure their data remains protected while using VPN services.
Network Encryption Methods
Network encryption methods play a crucial role in ensuring the security and privacy of data transmitted over networks. Encryption is the process of encoding information in such a way that only authorized parties can access it. In the context of network security, encryption is used to protect data as it travels across the network, making it unreadable to anyone who might intercept it.
One common encryption method used in network security is the use of Virtual Private Networks (VPNs). VPNs create a secure, encrypted tunnel between a user's device and a remote server, ensuring that data transmitted over the network is protected from eavesdroppers. Another widely used encryption method is Secure Socket Layer (SSL) or its successor Transport Layer Security (TLS), which encrypt data exchanged between web servers and browsers.
Advanced Encryption Standard (AES) is a symmetric encryption algorithm commonly used to secure data transmitted over networks. AES operates by encrypting and decrypting data in blocks of 128 bits using a secret key, making it difficult for unauthorized parties to decipher the information.
Public Key Infrastructure (PKI) is another encryption method that uses a pair of keys - public and private - to secure communication over a network. The public key is shared with others to encrypt data, while the private key is kept secret and used for decryption. This asymmetric encryption method provides a secure way to exchange information without compromising security.
In conclusion, network encryption methods are essential for safeguarding data privacy and security in the digital age. By utilizing encryption technologies such as VPNs, SSL/TLS, AES, and PKI, organizations can protect sensitive information from unauthorized access and ensure secure communication over networks.
Virtual Private Network Implementation
Title: Implementing Virtual Private Networks (VPNs) for Secure Online Connections
In an increasingly interconnected digital landscape, ensuring the security and privacy of online communications is paramount. Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding sensitive data and maintaining anonymity while browsing the internet. Implementing VPNs effectively involves several key considerations to maximize security and performance.
First and foremost, selecting the right VPN service provider is crucial. Evaluate providers based on factors such as encryption protocols, server locations, and user privacy policies. Opt for reputable providers with robust encryption standards, such as AES-256, to ensure data confidentiality.
Once a VPN provider is chosen, the next step is configuring the VPN client on devices. Most VPN services offer user-friendly applications for various platforms, including desktops, laptops, smartphones, and routers. Install the VPN client and follow the setup instructions provided by the provider. Configure the client to automatically connect to the VPN server whenever the device connects to the internet for seamless protection.
Additionally, consider implementing additional security measures alongside VPN usage. Enable firewall protection and regularly update antivirus software to fortify defenses against cyber threats. Utilize multi-factor authentication (MFA) for accessing sensitive accounts to add an extra layer of security.
Furthermore, educate users on best practices for VPN usage to mitigate potential risks. Emphasize the importance of avoiding public Wi-Fi networks without VPN protection, as they are susceptible to eavesdropping and data interception. Encourage users to connect to VPN servers located in regions with stringent privacy laws to enhance anonymity.
Regularly monitor VPN performance and security to identify and address any potential vulnerabilities promptly. Conduct periodic audits of VPN configurations and update software as necessary to stay ahead of emerging threats.
By implementing VPNs effectively and adhering to best practices, organizations and individuals can safeguard their online communications and protect sensitive data from unauthorized access.
Secure Network Connectivity Solutions
Secure network connectivity solutions are vital for businesses to ensure that their data and communications remain safe from cyber threats. With the increasing reliance on digital technology and the internet, it is crucial to implement strong security measures to protect sensitive information.
One of the key components of secure network connectivity is the use of Virtual Private Networks (VPNs). VPNs create a secure and encrypted connection over the internet, allowing users to send and receive data without the risk of interception by hackers or malicious third parties. By using a VPN, businesses can ensure that their communication and data transfers are protected from potential cyber attacks.
Another important aspect of secure network connectivity solutions is the implementation of firewalls. Firewalls act as a barrier between a trusted internal network and untrusted external networks, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. By setting up firewalls, organizations can prevent unauthorized access to their network and data, reducing the risk of data breaches and cyber attacks.
In addition to VPNs and firewalls, using secure socket layer (SSL) certificates can also enhance network security. SSL certificates encrypt data transmissions between a user's browser and a website, ensuring that sensitive information such as login credentials and financial details are protected from eavesdropping and tampering.
Overall, investing in secure network connectivity solutions is essential for businesses to safeguard their sensitive information and maintain the trust of their customers. By implementing VPNs, firewalls, and SSL certificates, organizations can create a secure network environment that mitigates the risks of cyber threats and data breaches.
VPN Deployment Strategies
Title: Efficient VPN Deployment Strategies: Ensuring Secure Connectivity
In today's interconnected digital landscape, Virtual Private Networks (VPNs) play a crucial role in safeguarding sensitive data and ensuring secure communication channels. However, deploying VPNs effectively requires careful consideration of various factors to maximize their efficiency and effectiveness.
One essential aspect of VPN deployment is selecting the right protocol. While several protocols are available, such as OpenVPN, IPSec, and SSL/TLS, each has its strengths and weaknesses. OpenVPN, for instance, offers flexibility and ease of configuration, making it suitable for diverse environments. IPSec, on the other hand, provides robust security features, making it ideal for enterprise-grade deployments. SSL/TLS protocols are favored for their compatibility and ease of use, especially in web-based applications.
Another critical consideration is the choice between self-hosted and cloud-based VPN solutions. Self-hosted VPNs offer greater control and customization options but require significant infrastructure investment and expertise to manage effectively. Cloud-based VPNs, on the contrary, provide scalability, ease of deployment, and maintenance, making them suitable for businesses with limited resources and technical capabilities.
Furthermore, organizations must implement strong authentication mechanisms to prevent unauthorized access to their VPN networks. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification, such as passwords, biometric data, or security tokens, before granting access.
Moreover, regular monitoring and updates are essential to ensure the ongoing security and performance of VPN deployments. Monitoring tools can help detect and mitigate potential threats or performance issues promptly, while regular software updates and patches help address vulnerabilities and ensure compliance with the latest security standards.
In conclusion, deploying VPNs requires careful planning and consideration of various factors, including protocol selection, deployment model, authentication mechanisms, and ongoing maintenance. By implementing efficient VPN deployment strategies, organizations can create secure connectivity solutions that protect their data and facilitate seamless communication channels.
0 notes
Text
Microsoft Intune Cloud PKI
Recently, Microsoft introduced the general availability of its new PKI-as-a-service solution called Microsoft Intune Cloud PKI. Cloud PKI allows administrators to issue and manage user and device authentication certificates for Intune-managed endpoints without deploying Active Directory Certificate Services (AD CS) on-premises. Cloud PKI frees administrators from the burdens of deploying and…

View On WordPress
#authentication#Azure#BYOCA#certificate#certificates#Certification Authority#cloud#Cloud PKI#device authentication certificate#InTune#Intune Cloud PKI#issuing CA#issuing certification authority#Microsoft#Microsoft Intune#Microsoft Intune Cloud PKI#PKI#PKI-as-a-Service#public cloud#root CA#root certification authority#SCEP#Simple Certificate Enrollment Protocol#user authentication certificate
0 notes
Text
The Evolution of Identity Verification Services: A Journey Through the 90s Era

In the rapidly evolving landscape of digital commerce and online interactions, identity verification services have played a pivotal role in establishing trust, preventing fraud, and ensuring regulatory compliance. The journey of identity verification services traces back to the 1990s era, a time marked by the emergence of the internet and the proliferation of e-commerce. Let's explore how identity verification services evolved during this transformative period and laid the groundwork for the sophisticated authentication mechanisms we rely on today.
The 1990s witnessed the dawn of the internet age, with the World Wide Web opening up new possibilities for communication, commerce, and collaboration. As businesses ventured into the realm of e-commerce, the need to verify the identity of online users became increasingly evident. Traditional forms of identification, such as driver's licenses and passports, were ill-suited for the digital environment, prompting the development of innovative identity verification solutions tailored to the online world.
During the early days of the internet, identity verification services primarily relied on basic authentication mechanisms such as username-password combinations. While simple and easy to implement, these methods offered limited security and were vulnerable to various forms of cyberattacks, including phishing, password guessing, and brute-force attacks. As e-commerce transactions grew in volume and value, there was a pressing need for more robust and reliable identity verification solutions to safeguard sensitive information and prevent unauthorized access.
In response to these challenges, the 1990s saw the emergence of more advanced identity verification services that leveraged encryption technologies and digital certificates to enhance security. Digital certificates, based on public key infrastructure (PKI), enabled organizations to authenticate the identity of users and secure online communications through the use of cryptographic keys. By issuing digital certificates to individuals and entities, certification authorities (CAs) provided a trusted mechanism for verifying the authenticity of online identities, laying the foundation for secure e-commerce transactions.
Moreover, the 1990s witnessed the introduction of biometric authentication technologies for identity verification, albeit in nascent forms. Biometric authentication, which relies on physiological or behavioral characteristics such as fingerprints, iris patterns, or voiceprints, offered a more secure and convenient alternative to traditional authentication methods. While adoption remained limited due to technological constraints and privacy concerns, biometric authentication laid the groundwork for future advancements in identity verification.
Furthermore, the regulatory landscape surrounding identity verification began to take shape during the 1990s, driven by concerns about privacy, security, and financial fraud. Regulatory initiatives such as the Electronic Signatures in Global and National Commerce Act (ESIGN) and the European Union Directive on Electronic Signatures paved the way for the legal recognition of electronic signatures and digital identities, providing a framework for secure online transactions.
In conclusion, the 1990s laid the foundation for the evolution of identity verification services, marking the beginning of a journey towards more secure, reliable, and convenient authentication mechanisms. From basic username-password authentication to the emergence of digital certificates and biometric technologies, the 1990s era witnessed significant advancements in identity verification that paved the way for the digital identities and authentication mechanisms we rely on today. As we continue to navigate the complexities of the digital age, the evolution of identity verification services remains an ongoing process, driven by technological innovation, regulatory requirements, and evolving threat landscapes.
0 notes
Text
PKI Solutions introduces new version of PKI Spotlight
http://securitytc.com/T3KPkb
1 note
·
View note
Text
Increasing Data Breach Incidents Fueling Key Management As A Service Solution Sales
The surging incidents of data breaches is creating a huge requirement for key management as a service solutions worldwide. Data breach leads to the loss of confidential information, such as social security numbers (SSNs) and credit card details. Complex access permissions, improper configuration, malware attacks, and weak passwords can aid cybercriminals in accessing confidential data. Loss of such data leads to major financial losses, which can be avoided through the adoption of key management as a service software by public and private organizations.
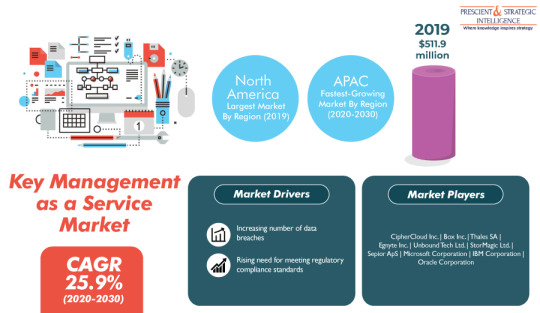
Moreover, the rising preference for cloud encryption is expected to propel the key management as a service market at a CAGR of 25.9% during 2020–2030. According to P&S Intelligence, the market was valued at $511.9 million in 2019. Cloud encryption offers advantages such as regulatory compliance, data privacy, lower information technology (IT) spending, and the capability to store and manage complex data. Additionally, cloud encryption helps businesses in protecting company financial, intellectual property data, and account details stored within the cloud.
In recent years, key management platform providers have been undertaking mergers and acquisitions to offer advanced solutions and software to their customers. For example, in March 2020, NetApp Inc. acquired Talon Storage to merge Cloud Volume products of the former with Fast software of the latter to provide a centralized solution to end users for managing their cloud data. Moreover, through this acquisition, NetApp also hopes to widen its cloud data service portfolio and support the effort of its consumers to transfer files across remote branches of business, in a multi-cloud environment.
Currently, service providers such as Box Inc., Amazon Web Services (AWS) Inc., International Business Machines (IBM) Corporation, Atos SE, NetApp Inc., Google LLC, Kapalya Inc., McAfee LLC, Microsoft Corporation, Unbound Tech Ltd., HyTrust Inc., Oracle Corporation, StorMagic Ltd., and Zettaset Inc. are developing advanced key management platforms for the retail and e-commerce, banking, financial services, and insurance (BFSI), IT and telecom, aerospace and defense, healthcare, and government sectors. These industries use such platforms for disk, cloud, communication, database, and file/folder encryption applications.
Geographically, North America dominated the key management as a service marketin the recent past, due to the extensive use of data center services and analytical tools, high preference of businesses for multi-cloud, rapid adoption of advanced technology to mitigate cyberattacks, and strong presence of cloud service providers in the region. Besides, the surging integration of digital medical records, mounting focus on digitization of the economy, and increasing download rate of several mobile applications in North America will also augment the usage of key management as service solutions in the coming years.
Whereas, Asia-Pacific (APAC) is projected to adopt key management as a service software at the highest rate in the coming years. This can be credited to the soaring need for cloud solutions, mounting awareness regarding cyberattacks and methods to counter them, stepping up digitization efforts, and improving key management lifecycle processes in the region. For instance, in February 2020, Fujitsu Limited, a Japanese multinational IT company, started using Cloud HSM service and key management platform by Thales SA to support public key infrastructure (PKI) security for securing the lifecycle management of cryptographic keys of customers.
Thus, the increasing data breach cases and rising shift toward cloud encryption will fuel the adoption of key management solutions and services in business operations in the foreseeable future.
#Key Management as a Service Market Share#Key Management as a Service Market Size#Key Management as a Service Market Growth#Key Management as a Service Market Applications#Key Management as a Service Market Trends
0 notes
Text
V2X Cybersecurity Market,Analysis, Size, Market Shares, Industry Challenges and Opportunities to 2030
Global V2X Cybersecurity Market
V2X Cybersecurity is also referred as Vehicle to Everything. This technology is based on various communications such as Vehicle to Vehicle (V2V), Vehicle to Infrastructure (V2I), and digital wireless communication which collectively called as V2X and provides safety and privacy solutions.
Read More Here: https://qualiketresearch.com/reports-details/V2X-Cybersecurity-Market
Key Players:
Infineon Technologies AG, AUTOCRYPT, Autotalks Ltd., ESCRYPT, HARMAN International, ID Quantique, IDnomic, Karamba Security, NXP Semiconductors, and Vector Informatik GmbH.
Market segmentation
Global V2X Cybersecurity Market is segmented into Unit such as On-Board Unit, and Roadside Unit, by connectivity such as DSRC, and Cellular, by communication such as V2V, V2I, V2G, V2C, and V2P. Further, market is segmented into security such as PKI, and Embedded, and by vehicle type such as Passenger car, and Commercial Vehicle.
Request A Free Sample: https://qualiketresearch.com/request-sample/V2X-Cybersecurity-Market/request-sample
Market Taxonomy
By Unit On-Board Unit Roadside Unit By Connectivity DSRC Cellular By Communication V2V V2I V2G V2C V2P By Security PKI Embedded By Vehicle Type Passenger car Commercial Vehicle By Region North America Latin America Europe Asia Pacific Middle East & Africa
About Us:
QualiKet Research is a leading Market Research and Competitive Intelligence partner helping leaders across the world to develop robust strategy and stay ahead for evolution by providing actionable insights about ever changing market scenario, competition and customers.
QualiKet Research is dedicated to enhancing the ability of faster decision making by providing timely and scalable intelligence.
QualiKet Research strive hard to simplify strategic decisions enabling you to make right choice. We use different intelligence tools to come up with evidence that showcases the threats and opportunities which helps our clients outperform their competition. Our experts provide deep insights which is not available publicly that enables you to take bold steps.
Contact Us:
6060 N Central Expy #500 TX 75204, U.S.A
+1 214 660 5449
1201, City Avenue, Shankar Kalat Nagar,
Wakad, Pune 411057, Maharashtra, India
+91 9284752585
Sharjah Media City , Al Messaned, Sharjah, UAE.
+971 56 846 4312
0 notes
Text
Absence of Wrongly-Configured MFA Helps Identity Security

“Money-grubbing crooks abuse OAuth — and baffling absence of MFA — to do financial crimes” https://www.theregister.com/2023/12/14/moneygrubbing_crooks_abuse_oauth_apps/
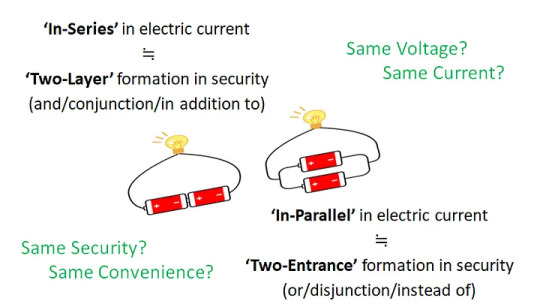
It’s amazing that so many security professionals and tech reporters are so ignorant of or indifferent to the opposite security effects of MFA configured in a multi-layer formation and in a multi-entrance formation — Absence of wrongly-configured MFA would help identity security
As we have repeatedly proven, a 2FA made of a deterministic password/pin and a deterministic physical token, PKI-powered or otherwise, that is configured in 2-layer formation, naturally increases the identity security significantly. On the other hand, an MFA which involves probabilistic biometrics and configured in 2-entrance formation inevitably destroys the identity security (*1)
Then, what can we do? — Our suggestion is simple.
1. If you do not involve biometrics in your MFA schemes, you could ignore all that I mentioned about MFA.
2. If you involve probabilistic biometrics in your MFA schemes, you could remove the biometrics altogether and go back to the solid 2FA made of a deterministic password and a deterministic physical token. Then you are out of the quagmire of MFA.
3. In any case, should you be interested to get yourself, your colleagues, employees and clients relieved from the password headache, you could have a glance at our writing on ‘Image-to-Code Converter (*2) and its application as a leak-proof password manager *3)
*1 “Why We Cannot find 3FA Deployed in 3-Layer Formation?” (3Dec2023) https://www.linkedin.com/posts/hitoshikokumai_identity-authentication-password-activity-7136923578544885760-ksPp
*2 “What ‘Image-to-Code Converter’ Offers to Global Population” (27Oct2023)https://www.linkedin.com/posts/hitoshikokumai_image-to-code-converter-31july2023pptx-activity-7123566445531189248-oIxA
* 3 “Release of Beta Mnemonic Gateways” (13Dec2023) https://www.linkedin.com/posts/hitoshikokumai_identity-authentication-password-activity-7140519698529464320-saOM
Kick out the falsehood of biometrics-involved MFA and you will be able to focus on the truly effective identity security solutions.
0 notes
Video
youtube
The evolution of encryption into an essential part of data protection strategies over the years has made it a critical component of security posture across various sectors and industries.
It is estimated that 42% of organizations are confident of increasing their budget expenditures on encryption in FY22-23.
According to Encryption Consulting study on global encryption trends – 2023, firms are becoming more aware of encryption and are planning to adopt it as a core data security technology.
In Survey Trend Analysis, the following data is gathered:-
1. In FY20, only 27% of the responding organizations had encryption strategies as a primary focus, but that figure increased to 70% in FY21.
2. Enterprise encryption strategies are adopted on average by 50% of enterprises in the world.
3. According to the survey, 65% of respondents said protecting customer information was their top concern.
0 notes
Text
Digital emblem for humanitarian law in cyberspace - Technology Org
New Post has been published on https://thedigitalinsider.com/digital-emblem-for-humanitarian-law-in-cyberspace-technology-org/
Digital emblem for humanitarian law in cyberspace - Technology Org
Warfare is increasingly spreading to the realm of cyberspace. In response, the International Committee of the Red Cross (ICRC) wants to protect its digital infrastructure and that of humanitarian organisations with a digital emblem. The Information Security Group at ETH Zurich has developed a standard for this and initial pilots.
In future, digital critical infrastructure should be labelled as worthy of protection by a digital emblem. ETH computer scientists have developed the technology for this. Image credit: ICRC
Ransomware attacks can paralyse organisations or entire countries by hacking into a network and encrypting critical data. The attackers then demand a ransom; if their demands aren’t met, the data will not be decrypted and may be lost forever. The financial and logistical damage can be enormous depending on the given situation. In January 2022, the International Committee of the Red Cross (ICRC) was the victim of a cyberattack. Data belonging to more than 500,000 people around the world was stored on the affected servers. This included data on people who needed special protection, such as missing persons, refugees from war zones and prisoners. “The ICRC’s digital infrastructure has grown considerably in recent years – and so has the number of cyberattacks on our systems,” says Mauro Vignati, Adviser Digital Technologies of Warfare at the ICRC. Particularly during wars and armed conflicts, such cyberattacks could also have catastrophic humanitarian consequences, for example if the enemy paralyses the digital infrastructure of a hospital.
Trusted emblem for protection against attacks
For conflicts beyond cyberspace, the ICRC has employed protective emblems since the Geneva Conventions of 1949, the core of international humanitarian law. The red cross, red crescent and red crystal provide protection for hospitals, vehicles and employees of organisations in the International Red Cross and Red Crescent Movement network (including the ICRC). Today, the network has over 80 million members who are active in 192 countries. As a matter of principle, bearers of these emblems are protected by international humanitarian law, especially in conflicts. Warring parties are not allowed to attack them. “That’s why we’ve been wondering for some time whether we could also develop an emblem to protect our digital infrastructure,” Vignati says. Such a system would have to fulfil a number of requirements: “It should be easy and cost-effective to integrate into existing digital systems worldwide and easy to maintain. It would also have to bridge linguistic, technological and cultural differences.” What’s more, the emblem ought to be as flexible as possible. In certain situations, it’s important for ICRC staff to mask the emblem, Vignati says.
Three years ago, the ICRC contacted the Centre for Cyber Trust, a research collaboration between ETH Zurich and the University of Bonn in the field of cybersecurity, with this idea of establishing a digital emblem. One of the people working on this since then is Felix Linker, who is currently writing his doctoral thesis in the group led by David Basin, Professor of Information Security at the Department of Computer Science at ETH Zurich. “A digital emblem has a unique combination of security requirements, namely authenticity, accountability and a property that we call covert inspection,” Linker says. The Authentic Digital EMblem (ADEM), which he has developed together with Basin, is based on the web PKI and CT ecosystem (Web PKI and CT stand for Web Public Key Infrastructure and Certificate Transparency). “We rely on existing best practices on the internet. What makes our work innovative is how we’ve combined different solutions to meet the technical requirements,” Linker says. In an article recently published in the Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Linker and Basin describe in detail for the first time how ADEM works.
Machine-readable and decentralised
The emblem they have developed is cryptographically secured using a digital signature – a long sequence of bits that can be read by a program developed for this purpose. This makes it possible to retrieve information about the owner, the IP or domain worthy of protection, as well as the publisher of the emblem. “It’s important that the emblem can be read by machines, because most cyberattacks today are automated,” Linker says. In other words, hacker software needs to automatically load and read the emblem, so it can recognise that it is accessing a system belonging to an organisation that is protected by international humanitarian law. And that needs to happen during the software’s first reconnaissance, before it does any damage to the system.
Another key requirement is for the digital emblem to be managed in a decentralised way rather than by a central authority. States that are committed to international humanitarian law should be able to verify that a certain digital infrastructure on their territory is entitled to protection and therefore bears an emblem. To this end, ADEM is based on an open standard, so governments can adapt the emblem’s implementation as flexibly as possible to their own requirements.
Hackers remain undetected
Potential attacks on servers and networks can come from hacker groups, but also from states during a war. These want to remain undetected at all costs. “That’s why attackers must be able to view the emblem without either the protected institution or the issuer of the digital signature being able to tell that the emblem has been looked at.” Only then will potential attackers be prepared to have their systems run the scanner for detecting the emblem. “Standard internet authentication protocols aren’t suitable for this because they require interaction between the two parties involved,” Linker says. “That attracts attention, which means it won’t work in a conflict.” He managed to come up with a combination of suitable internet protocols (UDP, TLS and DNS) to mask the distribution of the emblem.
Linker has now evaluated the system in a security analysis under a comprehensive threat model. His evaluation shows that the digital emblem cannot be misused by attackers and acts as a security guarantee. He says that this provides proof of concept. He is now developing the first prototypes further, while colleagues from the Centre for Cyber Trust in Bonn will conduct interviews with hackers to find out how willing people are to respect such an emblem. After all, only then will they bother to run a program that can recognise emblems. But this is something Linker is confident about: in the past, hackers have been known to avoid humanitarian targets on occasion, “for ethical reasons or simply to avoid attracting too much attention.”
Difficult legal implementation
Vignati from the ICRC is satisfied: “ADEM fulfils all our original requirements for a digital emblem.” The main task now is to further optimise the emblem’s visibility to potential attackers. However, it will probably be several years before the digital emblem actually starts helping to protect the ICRC’s critical digital infrastructure and hospitals in war zones. “The legal implementation is very challenging,” Vignati says. Implementing the emblem in the legal framework calls for adjustments to the Geneva Conventions: “Either through a new additional protocol or through an addition to the existing protocols.” The ICRC plans to showcase ADEM, along with another system designed at John Hopkins University, at an international humanitarian law conference to be held in October 2024. It will also present legal pathways for bringing the digital emblem into operation. “That would be an important first step in strengthening humanitarian protection in cyberspace,” Vignati says.
Source: ETH Zurich
You can offer your link to a page which is relevant to the topic of this post.
#000#2022#2023#2024#Analysis#Article#attackers#authentication#bridge#Collaboration#communications#comprehensive#computer#Computer Science#conference#Conflict#critical infrastructure#crystal#cyber#cyberattack#Cyberattacks#cybersecurity#cyberspace#data#DNS#easy#emblem#employed#employees#ETH Zurich
0 notes
Text
FIDO Authentication Industry Hits $1.24 Billion in 2022, Set to Soar to $12.06 Billion by 2033
The FIDO Authentication Market has witnessed remarkable growth, with the total revenue reaching US$ 1,238.6 million in 2022. This impressive growth trajectory is projected to continue, with the market expected to surge to US$ 12,059.7 million by 2033, reflecting a robust Compound Annual Growth Rate (CAGR) of 23.1% from 2023 to 2033.
Get Sample Copy of this Report at:
https://www.futuremarketinsights.com/reports/sample/rep-gb-12485
Drivers and Opportunities:
The market’s expansion is driven by several factors, including the increasing adoption of FIDO authentication solutions across various industries. The rising concerns over cybersecurity threats have prompted organizations to seek robust authentication methods, further fueling market growth. Additionally, the growing popularity of biometric authentication methods and the proliferation of mobile devices are providing lucrative opportunities for market players to innovate and expand their offerings.
Competitive Landscape – Regional Trends:
The FIDO Authentication Market is highly competitive, with key players constantly innovating to maintain their market position. Regional trends indicate that North America dominates the market, owing to a high concentration of tech-savvy enterprises and stringent security regulations. Europe follows closely behind, driven by increasing awareness of data security. Meanwhile, the Asia-Pacific region presents significant growth potential due to the rapid digitalization of economies and the need for robust authentication solutions.
Restraints:
Despite its rapid growth, the market faces certain limitations, including concerns related to user privacy and data protection. Striking a balance between stringent security measures and user convenience remains a challenge for market players. Moreover, the high initial costs associated with implementing FIDO authentication solutions may hinder adoption among smaller enterprises.
Region-wise Insights – Category-wise Insights:
Regionally, North America leads the FIDO Authentication Market, with a substantial share of the global market. Within categories, biometric authentication solutions are gaining prominence due to their accuracy and user-friendliness. Moreover, the healthcare and financial sectors are witnessing substantial adoption of FIDO authentication, driven by the need for secure access to sensitive data.
Request for Methodology:
https://www.futuremarketinsights.com/request-report-methodology/rep-gb-12485
Competitive Landscape
As organizations around the world are challenged in controlling dynamic and hybrid IT environment, the need for secure mobile or online applications without compromising user convenience is increasing continuously.
Owing to this, most of the leading players in the FIDO authentication technology are coming with advanced and innovative solutions that meets the ever-changing demand from organizations for advanced security and privacy concerns.
In January 2021, Aware, Inc. announced the launch of AwareABIS, an automated biometric identification system (ABIS) used for large-scale biometric identification and deduplication. Designed to serve among 1-30 million identities or more, AwareABIS supports fingerprint, face and iris modalities, and features a modular architecture that helps security teams configure and optimize the system for civil or criminal applications.
FIDO Authentication Outlook by Category
By Solution:
FIDO U2F Authentication Devices
FIDO Authentication SDKs
FIDO Client SDK
FIDO Server SDK
Services
Technology Consulting
Integration & Deployment
FIDO Certification Services
Support Services
By Application:
Payment Processing
PKI/Credential Management
Document Signing
User Authentication
Others
By Industry:
BFSI
Healthcare & Life Sciences
IT & Telecom
Retail & CPG
Government & Defense
Energy & Utilities
Others
By Region:
North America
Latin America
Europe
East Asia
South Asia & Pacific
Middle East and Africa
0 notes
Text
The Transformative Power of Electronic apostille
In an era where the digital landscape is redefining the way we conduct business and manage information, traditional processes are undergoing a significant transformation. One such evolution is the emergence of electronic apostille, a revolutionary approach to document authentication that harnesses the power of technology to simplify and expedite the international recognition of documents.

Understanding Electronic Apostille:
An electronic apostille, often referred to as e-apostille or digital apostille, represents a departure from the traditional method of affixing a physical certificate to a document. Instead, electronic apostille leverages digital signatures, encryption, and advanced authentication technologies to provide a secure and efficient means of validating the authenticity of a document for international use.
Key Advantages of Electronic apostille:
Speed and Efficiency: Electronic apostille streamline the authentication process, significantly reducing the time required for document validation. With just a few clicks, documents can be digitally apostilled, eliminating the delays associated with traditional, paper-based methods.
Global Accessibility: The digital nature of electronic apostille facilitates instant access from anywhere in the world. This accessibility is particularly advantageous for individuals and businesses engaged in international transactions, allowing for swift and seamless sharing of crucial information.
Enhanced Security: Digital apostille often incorporates robust security features such as cryptographic techniques, ensuring the integrity and authenticity of the authenticated document. This heightened security not only reduces the risk of fraud but also instills confidence in the reliability of the electronic authentication process.
Cost-Effectiveness: Electronic apostille contributes to cost savings by eliminating the need for physical paperwork, printing, and postage. Businesses and individuals can benefit from a more economical and environmentally friendly approach to document authentication.
Technological Enablers of Electronic apostille:
Blockchain Technology: The decentralized and tamper-resistant nature of blockchain technology provides a secure platform for storing and verifying electronic apostille. It creates an immutable and transparent record of transactions, further enhancing the trustworthiness of the authentication process.
Advanced Cryptography: The use of advanced cryptographic techniques ensures the confidentiality, integrity, and non-repudiation of electronic apostille. Public-key infrastructure (PKI) and digital signatures play a crucial role in establishing the authenticity of the digital document.
Cloud-Based Solutions: Cloud technology facilitates the storage, management, and retrieval of electronically apostilled documents. This not only promotes easy access but also enables collaborative efforts, essential for businesses with global operations.
Considerations for Implementation:
Legal Recognition: Achieving widespread acceptance of electronic apostille requires collaboration between governments and international organizations to establish legal frameworks that recognize and support digital document authentication.
Interoperability: Ensuring interoperability between different systems and platforms is crucial for the seamless exchange of electronically apostilled documents across borders. Standardization efforts can contribute to achieving this goal.
As we navigate the digital age, electronic apostille stands as a testament to the transformative power of technology in simplifying and enhancing traditional processes. With their speed, accessibility, security, and cost-effectiveness, electronic apostille represent a forward-thinking approach to document authentication. Embracing this technological evolution is not just a step towards efficiency but a strategic move for individuals and businesses seeking to navigate the complexities of our interconnected and digitized world.
0 notes
Text

LEGAL DOCUMENT EXPERTS NOTARIZING SOUTH BEACH
Thank you for choosing Miami Beach Notary 305, South Beach's most trusted mobile notary public and apostille certification service. Located in the heart of residential Miami Beach surrounded by the flourishing mass of young business professionals, we have notarized thousands of legal documents for both residents and visitors of South Beach alike.
At Miami Beach Notary 305, we are more than just stamps. Aside from being active real estate agents and members of Miami Realtors, our combined staff of licensed and bonded notary publics have over 20 years of legal document creation and business formation experience. Not only can we assist in the closing of your home or legal name change on a birth certificate, but we can also be commissioned to form your LLC or S Corp. If your car gets towed and is registered to someone else, we can notarize the document to have the vehicle released back to you. Miami Beach Notary 305 is a wedding officiant authorized by the State of Florida for marriage license notarization and the performing of wedding ceremony.
No matter the time of day or night, email your documents to us and we'll print and deliver them right to your door ready to be signed and stamped.
We can facilitate any business or personal notary request you might have.
Remote Online Notary (RON) services are also available for a true paperless signing experience. No matter where in the world you are, we place the documents and other required signers right in front of you with Video Conformation and secured PKI identification verification. The perfect solution for real estate closings with clients based out-of-state or abroad.
You can also schedule with us to have your electronic fingerprints taken for any Florida license or level 2 background check requiring livescan fingerprinting. We keep a full stock of traditional FD-258 ink fingerprint cards as well.
Contact us for any emergency situation that requires a notary public, we always answer the call.
(305)-778-7489
#miami beach#miami#mobile notary#notary public#notary#miami beach notary 305#notary services#305#Spotify
1 note
·
View note
Text
Empowering Business Continuity: Ensuring Security with IoT Device Identities
This content discusses the significance of IoT (Internet of Things) in modern business operations and digital transformation. It emphasizes the critical role of IoT device identities in ensuring security and integrity within the IoT ecosystem.
The piece outlines the challenges posed by security threats and data breaches and provides key practices for creating and managing secure IoT device identities. It also introduces Kellton as a partner that specializes in streamlining IoT identity management, offering expertise in IoT device engineering and manufacturing, as well as robust PKI (Public Key Infrastructure) solutions.
Kellton's approach aims to fortify IoT ecosystems against emerging threats and vulnerabilities, ultimately enhancing business performance through secure IoT device identities.
Explore the blog in details: https://www.kellton.com/kellton-tech-blog/secure-iot-device-identities-from-authentication-iot-identity-management
0 notes