#digital hygiene
Text
You weren’t at that protest. Neither were your friends and allies. You weren’t seen there because neither you nor your friends were filmed. You couldn’t be seen because you dressed exactly the same as all your allies, and you sure as hell didn’t let the cameras see your face. You practice digital hygiene. You go above and beyond the security you assessed the situation requires. You knew your cause was about more than clout, and you fought right because you knew that. When people asked you questions, you say you weren’t there. Hell, you didn’t even know there was a protest that day. You don’t use your real name. You know the state isn’t on your side, and you know it can’t ever be. You know your rights and you make sure your arrestors know you know them. You stay on your feet. You know your exits. You know their tactics and you know how to counter them. You trust your marshals and you read the situation. You defer to those with more experience. You protest right, and you keep fighting until you secure the rights that keep you alive and able to fight for someone else, another day.
#protests#protest#riots#riot#cybersecurity#anarchism#anarchist#digital hygiene#praxis#revolution#communism#communist#leftism#leftist#acab#politics#strikes
3K notes
·
View notes
Text
Hey y’all it’s digital hygiene hours again
It looks like the FBI is mopping up those Jan 6 rioters, which is great! There’s just one thing that’s a bit concerning: They’re using a relatively new technique called a geofence warrant. That’s where they require a private technology company (in this case, Google) to disclose information about all devices known to be within a specific area at a specific time.
Google told the FBI to get a warrant before they would hand over the data, but the fact that they could have just forked it over, or that they have the data at all, is pretty concerning. In this particular case, it was collected with Google’s Location History service, which is opt-in. (The switch for it is in the Data and Privacy tab of your Google account settings.) It’s really not a stretch to think that they could use it against people that are legitimately exercising their rights.
Google’s location services, as well as Apple’s and pretty much anyone else’s, rely on WiFi, Bluetooth, and GPS data rather than cell service.
The filing suggests that dozens of phones that were in airplane mode during the riot, or otherwise out of cell service, were caught up in the trawl. Nor could users erase their digital trails later. In fact, 37 people who attempted to delete their location data following the attacks were singled out by the FBI for greater scrutiny. (Mark Harris, Wired)
Without getting too much into the weeds, your phone sends out signals asking around for Wi-Fi networks and bluetooth devices it knows. When the requested network or device hears these, it replies to let your phone know that it’s nearby. (This is how auto-connect works with both WiFi and bluetooth.) Any device with an internet connection that receives WiFi and bluetooth, including other people’s phones, can receive these. By recording the signal strength and getting a lot of data points from nearby devices, individual phones can be located with much better precision than cell tower triangulation.
Basically, if you’re out protesting, exercising your rights, whatever, turn off your WiFi and bluetooth until you get home. If you need to maintain communication with your group to stay safe, you can even leave cell service on. A related article from Wired says that cell triangulation is only accurate to about three quarters of a mile, which is probably enough for plausible deniability in case you get targeted for exercising your rights. (This is not legal advice.)
Get out there, have fun, stay safe, and don’t fuck it up!
#digital safety#digital hygiene#internet safety#jan 6#jan 6 trial#fbi investigation#politics#activism#protesting
15 notes
·
View notes
Video
youtube
I replaced Social Media with Micro-Journalling for 1 Year
0 notes
Text
POSTHUMOUS AUTONOMY
MASS DESENSITIZATION HAS CONVICNED TO MANY PEOPLE OBSESSIVE VIDEO BINGING WILL PROVIDE PEACE OR VISIBILITY TO THOSE SLAIN.
LET'S REFLECT ON POSTHUMOUS AUTONOMY PLEASE.IS THIS NECESSARILY THE MOST PREVELANT IMAGE THEY MIGHT WANT CIRUCLATED OF THEM IN THEIR TRAGIC FINAL MOMENTS?
ARE WE SIMPLY NOT BEING IMAGINATIVE ENOUGH WITH OUR JOURNALISM PRACTICES AND TACTICS TO SPREAD AWARENESS?
DO YOU NOT BELIEVE THAT THE FRIGHTENING REALITIES OF OUR SUSCEPTIBILITY TO STATE VIOLENCE IS SUFFOCATING YOUR OPTICS?
THE ASSUMPTION RAW TRAUMA VIRALITY HAS SHIFTED MANY TO ENGAGE IN THESE TRAUMA BONDING.THIS WON'T EVER TAKE PRECEDENCE OVER THEIR ACTUAL LIFE AND MEMORY?
HOW DO YOU BALANCE COMMUNICATING THIS ISSUE TO OTHERS CLOSE TO YOU WITHOUT BEING INVASIVE EMOTIONAL TRAFFIC POLICE OF OTHER BLACK COMMUNITY MEMBERS EMOTIONS?
PLEASE EXIST IN THE POLITICALLY CHARGED HELLSCAPE OF CYBERSPACE WITH SENSITIVITY AND PRECISION WHEN POSSIBLE.
BE OPEN TO HEALTHY CRITIQUE AND SELF EDITING AS WELL. KEEP THE LIVES OF THE BLACK PEOPLE SLAIN IN CONSIDERATION.
ALSO, BE GENTLE WITH YOUR MIND FOR THE SAKE OF YOUR OWN MENTAL HYGIENE. OUR PSYCHE CAN BE VERY FRAGILE EVEN WHEN WE FEEL OTHERWISE IN THE MOMENTS OF HEAVY MEDIA CONSUMPTION.
TAKE CARE YALL. STAY LIBERATED . PROTECT YOUR COMMUNITY. PROTECT YOUR MIND. MUCH LUV
0 notes
Text

Just a basic picture of Winter I drew on a whim yesterday. When you're icewing royalty, it is important to do this kind of thing regularly.
-----
Image Description:
Prince Winter from Wings of Fire, who is a blue-ish white ice dragon, grooming himself and polishing his back spines with a brush made from a carved bone and bristly animal hair. His eyes are closed and his expression appears relaxed. He is holding one of his spines between two of his digits as he runs the brush bristles over it.
#wings of fire#dragon#digital art#wof#wof art#wof winter#icewing#wof icewing#cleaning#hygiene#flawseer art
314 notes
·
View notes
Text

Brushing teeth with the little friends
#i doubt dazai would brush teeth#man lived in a shipping container#no water = no hygienic practices#art#drawing#digital art#artwork#my art#artists on tumblr#bsd fanart#osamu dazai#bungo stray dogs#dazai osamu fanart#dazai osamu#osamu dazai fanart#fanart
57 notes
·
View notes
Text
Digital declutter
Delete apps you don't need/use
Delete screenshots
Organize everything into folders 📂
Clear history
Backup documents
Check to see if anything have to update
Unsubscribe from emails
Delete emails that are not important
Organize pictures into folders
Unfollow people who make you feel like you don't worth anything. Less negativity!
Turn off social media notifications
#feminine#positivity#self care#hygiene#self healing#self worth#dream girl#digital declutter#high maintenance#glow up#checklist
814 notes
·
View notes
Text
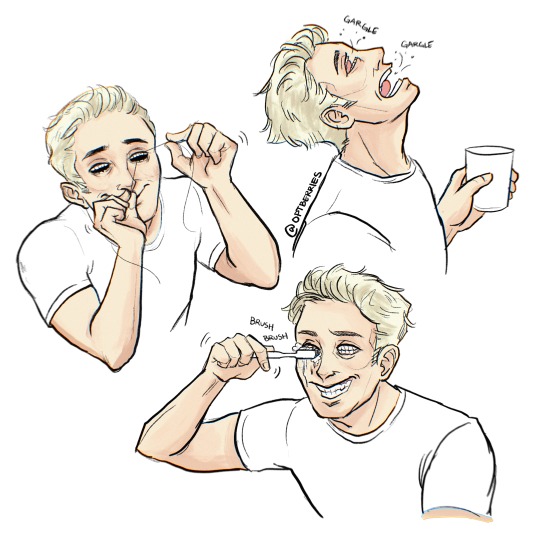
Gotta keep those chompers clean and healthy!
337 notes
·
View notes
Text
How to practice digital minimalism in our overwhelmingly technology focused world
Over the past couple of weeks i’ve found myself struggling to put my phone down, even in important situations or scenarios. For the upcoming months, I really want to challenge myself to limit screen time and stop mindless scrolling for hours. So for today’s post I really want to look at digital minimalism and explore how I can step away from the phone and step into the real world more often.
Introduction
In today's world, we are surrounded by technology and digital devices that demand our attention 24/7. From smartphones to laptops, social media to streaming services, it's easy to get lost in the digital clutter. This is where digital minimalism comes into play - it is a philosophy that encourages us to be mindful of our digital consumption and to use technology intentionally. In this blog post, I want to explore the art of digital minimalism and how it can help us lead a more intentional and fulfilling life.
The Benefits of Digital Minimalism
The term "minimalism" comes from the broader movement of minimalism, which is about simplifying one's life by reducing the number of material possessions and focusing on what truly adds value and meaning to our lives. Digital minimalism applies these principles specifically to technology and digital tools.
Digital minimalism has numerous benefits, including better mental health, improved productivity, and increased focus. By reducing our screen time and limiting our exposure to digital distractions, we can improve our mental wellbeing and reduce stress. This is because constant exposure to social media and digital devices can lead to information overload and a feeling of being constantly “switched on”. Additionally, by reducing our digital consumption, we can free up time to pursue other hobbies and interests, leading to a more fulfilling life.
At its core, digital minimalism is about being more intentional and deliberate in how we use technology and digital devices in our daily lives.
Tips for Practicing Digital Minimalism
Practicing digital minimalism can seem daunting at first, but there are simple steps we can take to reduce our digital consumption. Firstly, we can delete social media apps from our phones and only check them on our computers. This will reduce the temptation to mindlessly scroll through our feeds and allow us to be more present in our daily lives. Secondly, we can turn off notifications for non-essential apps, such as gaming or shopping apps, which can help reduce distractions and increase productivity. Finally, we can set aside specific times of the day to check our emails and messages, rather than constantly checking them throughout the day.
The Importance of Balance
While digital minimalism can have numerous benefits, it's important to remember that technology is not inherently bad. In fact, technology has transformed the way we live and work, making our lives easier and more convenient. The key is to find a balance between our digital and offline lives. By being mindful of our digital consumption and using technology intentionally, we can reap the benefits of digital minimalism without sacrificing the benefits of technology.
Conclusion
Digital minimalism is not about completely eliminating technology from our lives, but rather about being mindful of our digital consumption and using technology intentionally. By reducing our screen time and limiting our exposure to digital distractions, we can improve our mental wellbeing, increase productivity, and lead a more fulfilling life. So, the next time you find yourself mindlessly scrolling through social media, take a step back and ask yourself - is this really how I want to spend my time?
Looking to get into digital minimalism, here are 10 ways to practice digital minimalism:
Delete social media apps from your phone and only check them on your computer
Turn off notifications for non-essential apps
Set aside specific times of the day to check your emails and messages
Use a website blocker to limit your time on distracting websites
Unsubscribe from email newsletters and marketing emails that you don't find useful
Use a physical calendar or planner instead of relying on digital ones
Practice mindfulness or meditation to reduce digital distractions and improve focus
Take regular breaks from technology and spend time outdoors or doing offline activities
Use technology for specific purposes, such as work or communication, rather than mindlessly browsing
Keep your digital devices out of the bedroom to promote better sleep hygiene.
#digital minimalism#hygiene#that girl#lucky girl syndrome#leveling up#goal setting#femininity#feminine#divine feminine#high value woman#energy#luxury
47 notes
·
View notes
Text


Decided to skip lineart again on the first image, and it came out really well.
Long story short; Vince/Vincent is a Horseman Demon (themed after the four horsemen of the apocalypse, also called Heralds of Apocalypse in this story) and he wants to turn Angus into one as well, because he thinks that'd give him all the power he wanted when younger (Angus has changed from those days, but Vincent refuses to acknowledge this)
Vincent is Plague type specifically, but if Angus turned he'd be an End Demon, I.E Death themed. (thought of calling them Reaper Demons, but I felt it was a bit too predictable lol)
(Currently, Angus is a blood magic warlock, and has dragonic heritage hence his dual pair of eyes + summonable spiky shoulders/dragonic arms.)
#illustration#art#artists on tumblr#oc illustration#demon#four horsemen#digital art#lumi's chaotic creations#lumi's art scribbles#Night city parlor#Angus Belmont#Vincent DeVos#these two could be summarized as#Tired Single Dad and his obsessed Ex with bad hygiene#original characters#original art#original illustration#The mage and the mobster
13 notes
·
View notes
Text
tips on how to fix your teeth really fast so that your orthodontist doesn’t realize you haven’t worn your retainer since you got your wisdom teeth out 15 months ago?
#quickest route? please i’m desperate#i’m just a sad girl who struggles with hygiene 😭😭#wearing my retainer every night is not going fast enough#my diary#online diary#tumblr diary#diary#digital diary#girlblogger#girlblogging#personal diary#gaslight gatekeep girlblog#pinterest girl
5 notes
·
View notes
Text

Wash Your Hands!
pixel_dailies : clean : 9/26/23
#animation#pixel art#pixel artist#pixel art animation#looping animation#2d animation#digital animation#digital art#pixel dailies#artists on tumblr#clean#hand washing#hygiene
6 notes
·
View notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare.
Healthcare under Cyber Attack
I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Heads up: Threatening software detected; opening the file is prohibited.
In an era where the digital world is as intrinsic to our lives as the air we breathe, the relevance of cybersecurity can not be overemphasized. Secure mobile apps , every download, and every apparently innocuous online interaction brings with it the possible risk of inviting malicious software right into our digital sanctuaries. This write-up aims to illuminate why downloading and install or opening destructive programs on your computer system is not simply dangerous-- it belongs to unlocking to your electronic home to a host of unwelcome effects.
Malicious software application, or "malware," is a wide term that encompasses numerous kinds of damaging software program, including viruses, trojans, worms, ransomware, and spyware, to name a few. These electronic threats are developed with purposes that vary from benign mischievousness to straight-out malevolent functions, such as stealing individual details, pirating computer resources, or securing documents for ransom money.
Cyber hygiene of downloading or opening a documents that harbors malware can trigger a domino effect of occasions that jeopardize your computer's safety and security and honesty. Here's a failure of why it's perilous:
1. ** Personal Info Theft **: Many types of malware are created to stealthily infiltrate your system and pilfer delicate data such as passwords, financial details, and individual identity details. This information can then be made use of for illegal tasks, marketed on the dark internet, and even bring about identification burglary.
2. ** System Damage **: Certain malware variations can corrupt documents, alter or delete important system data, and in extreme instances, make a computer inoperable. This not only interrupts individual or company operations but can additionally result in the loss of important data.
3. ** Source Hijacking **: Some malicious programs, like cryptojacking malware, clandestinely use your computer system's sources to mine cryptocurrency, considerably decreasing your system and potentially creating lasting damage to elements as a result of overheating or overuse.
4. ** Ransomware **: Probably one of the most nefarious forms of malware, ransomware secures your files, securing you out of your very own data. The wrongdoers then demand a ransom for the decryption trick. Paying the ransom, nonetheless, does not ensure the return of your information and additional funds the cycle of cybercrime.
5. ** Personal privacy Violation **: Spyware and certain kinds of trojans can check your activities, log keystrokes, and even turn on video cameras and microphones without authorization, bring about an extensive intrusion of privacy.
Shielding on your own from these digital threats entails a combination of watchfulness and the usage of cybersecurity tools. Always validate the resource of your downloads, avoid opening email add-ons or links from unidentified senders, and use thorough anti-viruses software application that supplies real-time defense, routine updates, and system scanning capabilities.
Enlightening oneself on the characteristics of phishing attempts and rip-off sites is also important. These commonly function as the distribution devices for malware. Search for HTTPS in web addresses, and watch out for sites that display inadequate design, spelling, and grammar mistakes, or that request unnecessary personal information.
To conclude, Secure coding standards is much better than remedy" has actually never ever been even more applicable than in the context of digital safety. The short-term adventure or benefit of downloading an unknown documents fades in contrast to the possible threats. By exercising safe surfing practices and arming your system with robust protection steps, you can substantially alleviate the risk of malware and guard not just your digital life, however your reality too.
#Secure computing#Phishing scams#Spyware threats#Hacking protection#Cybersecurity tips#Vulnerable software#Email attachment safety#Internet phishing#Digital security#Malicious URLs#Online fraud prevention#Security patches#Firewall protection#Virus scan#Secure passwords#Two-factor authentication#Cybersecurity education#Malicious code#Cyber hygiene#Data encryption#Secure networks#Security vulnerabilities#Malware quarantine#Cyber defense strategies#Suspicious activity monitoring#Identity theft protection#Secure file sharing#Malware signatures#Cyber risk management#Secure online transactions
1 note
·
View note
Text

0 notes
Text
Decoding the Interwoven Nature of Diabetes and Sleep Patterns: A Deep Dive into Sleep Quality, Associated Sleep Anomalies, and Their Consequential Effects on Diabetes Regulation
Venture into the multifaceted nexus between one’s quality of sleep, prevalent sleep-related disorders such as obstructive sleep apnea, and the efficacy of diabetes management. This all-encompassing article unravels how the intricate mechanisms of sleep can modulate blood glucose metrics, delineates the mutual impact between diabetes manifestations and sleep patterns, and showcases a spectrum of…

View On WordPress
#Blood Glucose Monitoring#blood sugar levels#circadian rhythms#cortisol and sleep#Diabetes Management#diabetes medications#dietary choices#digital health tools#glucose control#holistic health#Insulin Resistance#lifestyle changes for diabetes#mental well-being in diabetes#nocturnal hypoglycemia#personalized care in diabetes#sleep apnea#sleep data analytics#sleep disorders#sleep disturbances#sleep hygiene#sleep monitoring#sleep patterns#sleep quality#sleep research#sleep therapies#sleep tracking devices#sleep-promoting nutrients#stress and diabetes#Type 1 Diabetes#Type 2 Diabetes
0 notes