#cyber threat investigations
Text
Ankura Cyber Threat Intelligence Bulletin: August - September 2022
Ankura Cyber Threat Intelligence Bulletin: August – September 2022
Over the past sixty days, Ankura’s Cyber Threat Investigations & Expert Services (CTIX) Team of analysts has compiled key learnings about the latest global threats and current cyber trends into an in-depth report: The Cyber Threat Intelligence Bulletin. This report provides high-level executives, technical analysts, and everyday readers with the latest intel and insights from our expert…

View On WordPress
#ankura#business#CITZ#cyber threat intelligence bulletin#cyber threat investigations#cyber threats#Cybersecurity#data privacy#expert services#Human Trafficking#law enforcement#legal
0 notes
Text
Navigate Cyber-security With Insights Of Private Investigator
Explore the cybersecurity threats and solutions with a private investigator in Ontario. Understand evolving cyber risks in Canada and proactive measures for protection. Discover how Private Investigators address cybersecurity challenges to safeguard businesses and individuals. To know more watch the full video or visit the website today for excellent expert advice.
#investigation hotline#forensic investigators#private investigation agency#private investigators finding someone#investigators in canada#forensic investigator canada#private investigator#cybersecurity#cyber threats
1 note
·
View note
Text
wtf is going on with cellbit - by a brazilian law major student
hey besties ever since the day cellbit released that PDF i’ve been keeping up with his shit bc as a law student (only two years to go!!!!) in brazil it’s kinda really interesting to see how it goes, specially since i don’t think we’ve ever had this sort of judicial action taken by an internet celebrity, like, ever. so i’ve decided to kinda explain what’s going on. if anyone has any questions after this i’d be really up to talk about it i love talking about law 🫶 xoxo let’s start. also sorry if anything reads weird english is not my native language okay
for those who don’t know, very recently, a judicial action taken by cellbit has made public. in this action, he’s suing over 200 people for the crime of defamation.
the action was taken to court in january, but it was under what we call “secret of justice”, which means only cellbit himself and twitter’s lawyers had access to it. now that there have been decisions by the judge and everything, the process’s been made public.
basically, cellbit started an action against twitter (NOT THE PEOPLE WHO COMMITTED THE CRIME YET), citing a little over 200 tweets that accused him of crimes like SA, psychological abuse, pedophilia, and others. all of those are real crimes in brazil — and accusing someone of committing crimes (specially as awful crimes as those) without proof is a crime in itself (defamation). he claimed that the tweets were harmful to his honor, mental health, and reputation, besides categorizing as defamation, since there’s no investigation going on against him for all these infractions he’s being accused of.
with that, he asked twitter to delete all the tweets, and to provide him with the personal information of said twitter accounts so he can sue them directly for defamation. he did these requests through something called “tutela cautelar”, which means the judge gets to decide whether or not twitter has to do these things before proof production and proper investigation, since, if twitter doesn’t do those things, the damage to his honor and reputation will be ongoing + he won’t be able to sue the proper people in time.
the judge conceded to his requests, and twitter has already deleted all the tweets. the main discussion going right now is wtf do they do about the international accounts — does our law apply to them? what’s gonna happen? we don’t know yet. that’s being discussed in court for the moment and, considering brazilian courts, it might take quite a while.
so, yeah, all those people aren’t being sued YET. but they will, probably somewhat soon.
it’s also important to mention that this lawsuit is from january and was only now released to the public. there’s probably a lot more coming after the whole fiasco that led him to releasing his statement, including a lawsuit against his ex herself.
now, other topics — could he sue other twitter accounts for cyber bullying or death threats? probably, but my personal opinion is that suing for defamation and focusing on accounts that were accusing him of having committed crimes was a much better move because it’s a much stronger case.
there’s very little room for discussion when a person has outright said “cellbit committed this crime”. death threats have more room for discussion: “oh, but they’re hundreds of miles away, it wasn’t a serious threat”, “they didn’t mean it”, “it was a joke”. same thing goes for cyberbullying: it can get too subjective.
defamation isn’t subjective. you accuse someone of a crime they didn’t commit? boom, defamation, at least according to our laws. so, to me, personally, it makes a LOT of sense for his lawyers to focus on that: he’s a LOT more likely to win than if he was suing for cyberbullying, threatening, insult, or any of that. also, he’s a lot more likely to win FASTER.
when he gets to sue the actual people who committed the crime, that is. for now, he’s only requested twitter to give him the necessary information to get to these people, which i think they’ll very likely be obligated to do. there are digital data protection laws in brazil, but a crime is a crime. digital data protection isn’t gonna protect you from the court.
another thing: LGPD (brazil’s general law of personal data protection) forces all social media companies to keep records of all the content posted by their users for AT LEAST six months. many companies keep it for way longer. that’s a law created for judicial purposes, in case something published to twitter, facebook, or instagram needs to be analysed by a court. that’s why even tho twitter has deleted the tweets, they still have them, and why it doesn’t matter if the people responsible are deleting the tweets, the accounts, the fucking app itself. the records are still there, and they will be used judicially.
i think that’s the overall for the situation, but i’m willing to answer any questions and to discuss it if anyone wants to! i’m a big law enjoyer. also personally i think cellbit is so fucking right for this like YEAH people don’t get to commit fucking crimes on twitter and get away with it. really interested in how this is gonna go law-wise, but in general also really glad to see someone take action like this.
850 notes
·
View notes
Text

Code of temptation
Synopsis: When a series of cyber threats puts national security at risk, Y/N is assigned to lead the investigation. Her team is complemented by Vernon, a computer genius known for his dexterity in deciphering the most complex codes.
Words: +1k
Reader! SecretAgent x Vernon! Hacker
Warnings: Smut, oral (f. receiving), penetrative sex, exhibitionism, unprotected sex (wrap it up), dry humping, fingering, hair pulling, chocking, dirty talk and etc.
Your tight TechWear is starting to get uncomfortable, your fingers attached to the trigger, and your arms are already weak from holding the heavy gun, one wrong movement, everything is done. You wait for the sign from Mingyu, who is already in position to catch the target “1, 2, 3… Now!” he says in the little point of sound in your ear, and you do your shot.
The bullet hits the target directly in the head, and Mingyu runs in the middle of the basement to steal the small device that is the pivot of the mission you have been working on for the last few weeks. The both of you run to the back door, you enter the armored car that awaits you.
“Objective accomplished successfully, mission completed with distinction and mastery.” Your chief says on the other line. Body finally relaxing on the car seat, while you do a little weak punch on Mingyu’s hand.
[…]
“We did a great Job Mr. Lee, we trained for this, but it’s difficult ultimately, they are more attached to the systems day by day, so we need to take action, and ask for the Department Head to recruit a Technical Expert, so we can obtain coordinates during missions” you point your pencil on the map in front of you “Promise me that by the end of the month, we will have some ‘technology guru’ to help us, and I promise to complete another mission as always.” that said, you leave the meeting room slamming the door loudly.
[…]
You hold a cup of coffee while you try to decipher the nominal codes on the computer screen, you snort and immediately give up on understanding the logic of the system in front of you. The computer room doorbell rings, and you can see a young man with brown hair waiting for the door to be opened, showing his FBI badge. You put your fingerprint into the system, and the door is slowly opened, revealing the boy, holding the shoulder strap from his backpack, wearing a black uniform, just like yours.
“First off all, I am almost freaking the fuck out seeing all these algorithms with letters on the same screen” you point to the computer with raised eyebrows, and he closes the door behind him “and we should have met before the mission started, but since you're here now, we need to track them down as quickly as possible.” He agrees and sit on the chair in front of the desk.
“My name is Vernon by the way” the sarcasm is proliferated from his lips, while he maintains an extremely unbothered expression.
You snort incredulous at his audacity - even though the ironic tone in his voice may not have been intentional - you stop to look at him from top to bottom, analyzing his mannerisms until he actually starts doing something on the electronic device that hovers in front of him “very funny of you, but I would like more respect since I am leading this mission, and the hierarchy is very-“
“Oh come on don’t play like you’re 10 years older than me!” He says with the face still buried on the screen “and since you are leading the mission amidst so much cyber invasion, you should at least know how to clear your history, if I were your enemy, and found out that you listen to the same Backstreet Boys song for 9 hours straight, you would definitely no longer be my target, freaky ass girl”
The heels on your feet touches the cold ground towards him “This is an invasion of privacy!” You turn the chair, so now you make eye contact with him, pressing his shoulders on the chair.
“This is being on the verge of madness!” You let him go, sitting on the couch on the other corner of the room, drinking your coffee ashamed.
The clicks on the mouse and the sound of the keys were driving you crazy, until he lifted his back from the chair and widened his eyes towards the computer, you run to see the screen popping a map with a lot of red ropes interlinked “Fuck! they’re on the building!” You recognize the structure of the department you are hiding in, running to get your guns attached to your waist, while Vernon turns off the trackers “We need to run away right now, we don’t have time!” You hold his arm, and you run through the company halls, until you leave the building, running down the opposite street. You led the way, while Vernon, the shy hacker, tripped over his own legs. The sound of sirens echoed through the streets, mixing with the frenetic rhythm of your footsteps. The cobblestone streets made escape even more challenging.
"Y/N, I think they saw us!", Vernon exclaimed, breathing hard.
You threw a quick glance behind you, displaying a confident grin. "Don't worry, Vernon, I have a foolproof plan." you say with pure sarcasm, and with a quick gesture, you grabbed Vernon's hand and led you into a narrow alley. The space between the two of you is tiny, you can clearly feel Vernon's minty breath hitting your face, the space doesn't help either, as your breasts are pressed against Vernon's chest - he'd be lying if he said he wasn't starting to like it.
The tension in the air was palpable as your eyes met, breathing heavily, you shared a moment of complicity that transcended the imminent danger. You instinctively grabbed Vernon's forearm, running your fingers over the skin still warm from running his eyes revealed a mixture of surprise and expectation, an electrically charged silence filled the narrow alley as your proximity grew. You, who are normally focused and fearless, felt a unique vulnerability at that moment. Then, without words, but with a shared intensity, you leaned slightly towards Vernon. The world around him disappeared when his lips finally touched, an instant of defiant lust in the midst of chaos. The narrow alley became a stage for the beginning of an immense desire between the two of you.
His right hand goes to your neck, pulling your hair, and the other, grab the meat of your ass, you moan in his mouth - you had even forgotten that you had a small beef with him earlier -, your hand goes down until you can fill your hand with his hardened cock, making him stop the kiss to bite his lip “Turn around” he orders. You hardly turn because of the compact space, and now your ass was pressed against his dick, as he pulls your skirt up, massaging your clit over the thin fabric of your panties “More, we don’t have time!” You whisper, and he slaps your cunt “Stop being hasty! Where's your 'foolproof' plan uh?” a high pitched moan leave your mouth, your hands holding on the little bricks of the wall so your face doesn't lie on them.
Vernon pulls your panties to the side, entering his fingers in your cunt, you hump your ass against him, feeling he hiss in your ear, the wet noises from your pussy and the sound of your panting breaths fills the alley, you moan feeling him going faster with his fingers. He suddenly stops the movement, opening his jeans, so he can slide his cock through your folds. “You are so hot, but fuck, you are so annoying!” he pulls your hair, slowly moving his hips finally diving into your heat, your eyes roll at the back of your head, his mouth kissing your neck.
The space was small, but he was doing wonder with his hips, circling his hips so his tip brushes against your g spot, making your legs go numb, you're lucky that he held you tight with an arm around your hip “Such a whore… Tsk”
You can hear footsteps approaching you, while a light from a flashlight approaches, Vernon pulls you to hide deeper in the alley.
“I think I heard something coming from here!"
He covers your mouth with one hand as he bites your shoulder, furrowing his eyebrows, still pounding deep inside of you, feeling your juices run down your thighs.
“It must be all in your head, come on, they must have gone that way!”
Vernon pulls you to rest your back against his chest, chocking you, while his hips are working faster “Afraid of being caught hm? So nervous that got you clenching so hard around my cock.” Your mouth opens, as you feel your orgasm approaching, his dirty talk between his moans was driving you crazy, squeezing him, while he throw his head back. “Fuck, I’m cumming” his cock twitches inside of your pussy, shooting ropes of cum inside of you, moaning low in your ear.
You can feel his cum running down your legs, he starts to rub your clit again, so slow it almost burns, his scent invading your nostrils, making your mind go blank, your body begins to tense, and an intense climax makes your legs shake, as he laughs proudly in your ear “Hmm… Thats it! Good girl..” He turns you around, so now you're face to face with him again, his kisses going down your jaw, as he fix your skirt.
“The night isn't over yet, we still have targets to catch” he gets dressed again “but first, let me clean you up” he bends down, licking your thighs, until he reaches your pussy, holding your leg up on his shoulder, while you tremble sensitive. He stands up, wiping his mouth with his thumb. Vernon steals a kiss from you, before pulling you to run through the streets once again.
#seventeen smut#seventeen x reader#vernon smut#seventeen imagines#svt smut#hansol vernon chwe#chwe vernon#chwe hansol x reader#seventeen reactions#seventeen headcanons#vernon x reader#vernon#vernon angst#hoshifighting writes
199 notes
·
View notes
Text
Daily update post:
The IDF has been releasing a lot of incriminating intel on the Shifa hospital in Gaza being used by Hamas. There's footage of a drone going into a terror tunnel underneath it.
youtube
There's pics of the weapons found there. There's the results of an investigation into the fate of 19 years old Noa Marziano, who was kidnapped by Hamas, lightly injured in an IDF strike, which killed the terrorist who was guarding her, another terrorist took her into the basement at the Shifa hospital, and killed her there, then Hamas tried to stage "evidence" that she was killed in the IDF strike. And most recently, there's CCTV footage showing Hamas bringing in hostages (one man from Nepal and one from Thailand) into Shifa, with the terrorists being armed, and all of this was done in broad daylight, and right in front of the medical staff.
Of course anti-Israelis, including the Hamas, said it was just bringing hostages in to get treatment.
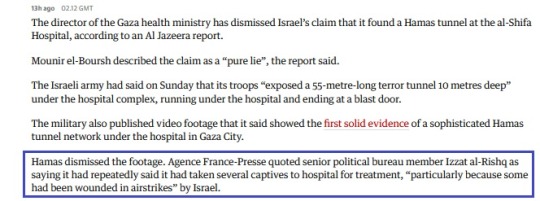
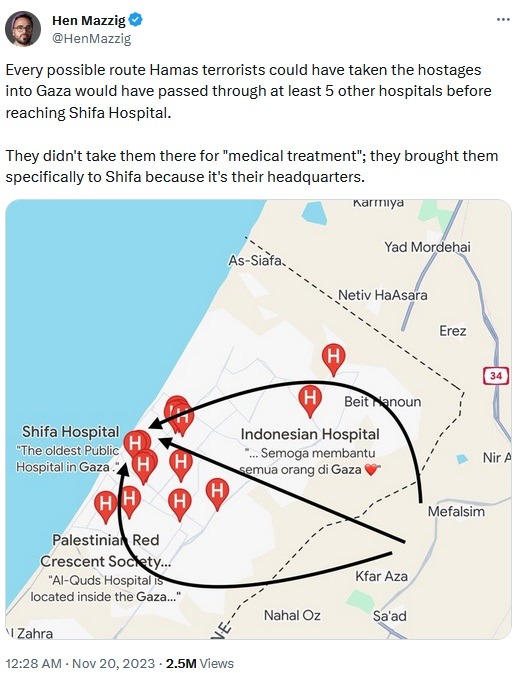
But here's the thing, Shifa is on the Western side of Gaza, while Hamas breached the Israeli border in the east. On the way between the border and where this hospital is located, there are plenty of other medical facilities on the way. Any of them would be preferable if the goal was to give the hostages medical treatment as soon as possible. But they took these kidnapped men all the way to Shifa instead. Because that's Hamas' headquarters.
I've known for years, like most Israelis, that Hamas is using medical facilities like hospitals and ambulances for its terrorist activity. This evidence does not surprise me. But I think it didn't really sink in for me until yesterday, just how many people knew and kept silent. I'm not even talking about the Gazan medical staff. They live under the constant threat of Hamas, I don't blame them. But the UN, the Red Cross, all of those "noble" NGO's operating from Gaza (and getting a lot of donations to do so), all of those foreigners with access to Gaza, who knew the situation on the ground, and chose to lie, and continued to do so even after the Oct 7 massacre... WTF is wrong with these people? By keeping quiet, they endangered both Israeli civilians (who Hamas could continue to target with impunity when operating from inside medical facilities), and Palestinian ones that Hamas endangered by using them as human shields.

Who is going to hold these people accountable? Who is going to make them pay for their complicity in endangering so many people, millions altogether, on both sides of the border, so that they never dare do this again?
Have ANY of them come forward, apologized, taken responsibility for their long complicity? I've heard of no such thing. In fact, I assume that they will only raise the volume of their accusations against and vilification of Israel, to drown out the voices asking these questions.
In this tweet you can hear an interview (starting at around 35 seconds in) with one of the few foreign doctors, who had worked at the Shifa hospital, and who after Hamas' massacre, did not come forward with his testimony about what he'd seen and experienced while he was there, but did agree to have it recorded once he was asked to. If Hamas is finally taken down, we might get to hear more of these, and I guess... better late than never.
In the midst of all of this, Israel has helped evacuate babies from the Shifa hospital to ones in Egypt, and the equipment to established a second Jordanian field hospital has entered Gaza today.
Israel continues to be attacked by Iran-funded rockets from the south, from the north by Iran-funded Hezbollah, as well as from Syria, by the Iran-funded Houthis in Yemen, by independent terrorist attacks, and online from cyber attacks, by Iran-funded and even Iranian hackers. I kind of tend not to talk about these that much, because they're on going. It's happening every single day, and Israel, in the middle of the fight to destroy Hamas, has to also defend its people on these fronts.
The anger and hurt over the denial of rapes that happened as part of Hamas' massacre continues, and more people are trying to speak up against it:
youtube
This is 15 years old Itay Cohen.

He's a triathlete, and was in the middle of a training session, cycling in the south, when Hamas terrorists shot him. He was taken to a hospital without any family by his side, because his parents were locked inside a bomb shelter in their kibbutz. Itay took a bullet to the head, and lost his eyesight, but somehow survived. So did his parents. He vowed he won't stop training, despite his new disability. This terror attack has changed countless lives, from among the survivors as well.
(for all of my updates and ask replies regarding Israel, click here)
#israel#israeli#israel news#israel under attack#israel under fire#israelunderattack#terrorism#anti terrorism#antisemitism#hamas#antisemitic#antisemites#jews#jew#judaism#jumblr#frumblr#jewish
102 notes
·
View notes
Note
Just curious...could this Sussex Squad thing turn into a legal investigation (if it's not already)? And what crimes would they be arrested for and what is the penalty?!??
The "general" stuff they do (for lack of a better word), like spread rumors about the Waleses and bully Kate's fans on social media, there's not a whole lot there. It's just seen as "coming with the territory" (also for lack of a better phrase).
Where the Sussex Squad could get into legal trouble is if or when they go after single accounts - doxxing them, dogpiling them, or escalating to death threats (or r*pe threats, threats of violence, etc.). All of that could qualify as stalking, intimidating, harassment, or incitement for violence for which there could be criminal charges levied. Depending on the severity and the jurisdiction, the penalty could range from slap-on-the-wrist fines to jail time.
Where it gets complicated is who reports these incidents and what kind of evidence or investigation there is to support the complaint. Usually the victim of a cyber crime has to report the incident (vs a bystander witness) and usually the onus on providing evidence to prove there's a case is on the victim - in most cases, the investigator (police, FBI, DHS, a lawyer) won't open a case unless the victim provides enough evidence to make it worth their time; screenshots of messages and usernames or phone numbers, IP addresses, voicemails, voice recordings. Which really sucks, but that's the grey area in a lot of cyber crime where the policies and practices are still being developed.
So for example, when Yankee Wally was doxxed and bullied off Twitter, only Yankee Wally could have reported the cyberbullying, the cyber harassment, the cyber stalking/intimidation and she would have had to provide evidence - e.g., screenshots of the tweets and the usernames/accounts who were harassing her. The rest of us wouldn't have been able to "call it in" for her. We could've helped take screenshots of any public messages she received or any posts/websites we saw where her PII published, but we most likely wouldn't have been able to report it to the FBI and have it taken seriously.
Which is why if you're ever the victim of a cyberbullying campaign, a doxxing, online harassment, it's super important you document everything. Take screenshots of all the messages you get (or see) and make sure all the identifying information is there like timestamps, usernames, account handles, and phone numbers. If you know how to get someone's IP address, grab that too. Save any voicemails or voice messages you get. If you answer a call that turns out to be harassment, document as much as you can; the number they called from, what time, what their voice sounded like, what they said. Have physical copies (printouts), electronic copies (screenshots), and backup copies.
If this is happening to you and you receive packages or letters in the mail from addresses you don't recognize, that are unusually heavy, or are leaking some kind of fluid/grease, don't open them, don't bring them inside, don't let children or pets near. Call the police to report it and follow their instructions about what to do.
40 notes
·
View notes
Text
One of the biggest hacks of the year may have started to unfold. Late on Friday, embattled events business Live Nation, which owns Ticketmaster, confirmed it suffered a data breach after criminal hackers claimed to be selling half a billion customer records online. Banking firm Santander also confirmed it had suffered a data breach impacting millions of customers and staff after its data was advertised by the same group of hackers.
While the specific circumstances of the breaches—including exactly what information was stolen and how it was accessed—remain unclear, the incidents may be linked to attacks against company accounts with cloud hosting provider Snowflake. The US-based cloud firm has thousands of customers, including Adobe, Canva, and Mastercard, which can store and analyze vast amounts of data in its systems.
Security experts say that as more details become clear about hackers' attempts to access and take data from Snowflake’s systems, it is possible that other companies will reveal they had data stolen. At present, though, the developing situation is messy and complicated.
“Snowflake recently observed and is investigating an increase in cyber threat activity targeting some of our customers’ accounts,” wrote Brad Jones, Snowflake’s chief information security officer in a blog post acknowledging the cybersecurity incident on Friday. Snowflake has found a “limited number” of customer accounts that have been targeted by hackers who obtained their login credentials to the company’s systems, Jones wrote. Snowflake also found one former staff member’s “demo” account that had been accessed.
However, Snowflake doesn’t “believe” it was the source of any leaked customer credentials, the post says. “We have no evidence suggesting this activity was caused by any vulnerability, misconfiguration, or breach of Snowflake’s product,” Jones wrote in the blog post.
While the number of Snowflake accounts accessed and what data may have been taken have not been released, government officials are warning about the impact of the attack. Australia’s Cyber Security Center issued a “high” alert on Saturday, saying it is “aware of successful compromises of several companies utilizing Snowflake environments” and companies using Snowflake should reset their account credentials, turn on multifactor authentication, and review user activity.
“It looks like Snowflake has had some rather egregiously bad security compromise,” security researcher Troy Hunt, who runs data breach notification website Have I Been Pwned, tells WIRED. “It being a provider to many other different parties, it has sort of bubbled up to different data breaches in different locations.”
Details of the data breaches started to emerge on May 27. A newly registered account on cybercrime forum Exploit posted an advertisement where they claimed to be selling 1.3 TB of Ticketmaster data, including more than 560 million people’s information. The hacker claimed to have names, addresses, email addresses, phone numbers, some credit card details, ticket sales, order details, and more. They asked for $500,000 for the database.
One day later, the established hacking group ShinyHunters—which first emerged in 2020 with a data-stealing rampage, before selling 70 million AT&T records in 2021—posted the exact same Ticketmaster ad on rival marketplace BreachForums. At the time, Ticketmaster and its parent company Live Nation had not confirmed any data theft and it was unclear if either post selling the data was legitimate.
On May 30, ShinyHunters also claimed to be selling 30 million customer details and staff information from Santander, putting a $2 million price tag on the information. Both posts on BreachForums have drawn attention to the illegal marketplace, which was recently revived by ShinyHunters after the FBI took the website down on May 15. The posts may, at least in part, be efforts to restore the disrupted forum’s damaged reputation with criminals.
The two hacks were linked to Snowflake’s systems by Israeli security firm Hudson Rock, which, in a now-removed blog post, posted conversations its researchers had with the alleged hacker who claimed to have accessed Snowflake’s systems and exfiltrated data. The hacker claimed they had tried to sell the data back to Snowflake for $20 million. (Hudson Rock did not respond to WIRED’s questions about why it has removed its research).
The Hudson Rock post claimed that a Snowflake employee may have been infected by an infostealer that collected the details the hacker needed to log in to its systems. Charles Carmakal, the chief technology officer at Google-owned security firm Mandiant, told BleepingComputer that its investigations, which have been taking place in recent weeks, indicate information-stealing malware may have been used to get Snowflake account credentials.
A Ticketmaster spokesperson told TechCrunch that its stolen database was hosted on Snowflake after the company acknowledged a data breach in a filing to the Securities and Exchange Commission on Friday evening. In the middle of May, before its data was advertised online, Santander first said it had seen unauthorized access to one of its databases “hosted by a third-party provider,” however it has refused to name the third party.
Snowflake’s CISO, Jones, acknowledged the security incident on Friday, saying that if a “threat actor obtains customer credentials, they may be able to access the account.” The company says it became aware of the suspicious activity on May 23 but has since found out it had been happening since mid-April. Jones’ post says Snowflake has notified all of its customers and “encouraged” them to review account settings and ensure they have implemented multi-factor authentication. In an additional security bulletin, Snowflake says it has seen “malicious traffic” from a client calling itself “rapeflake” and also connections from another client called “DBeaver_DBeaverUltimate.” A company spokesperson tells WIRED they have “nothing else to add” beyond the information included in company posts.
Cloud security company Mitiga says its investigations have seen a threat actor targeting organizations using Snowflake databases and using an attack tool called “rapeflake” in the process. Roei Sherman, field CTO at Mitiga, tells WIRED one possible scenario is that a threat actor managed to get information about Snowflake’s systems and then stole information about its clients, possibly using automated tools and brute-forcing their way into accounts.
Sherman says little is known about what data was stolen at the moment or the “rapeflake” tool, but that the attack could have wider ramifications going forward. There are already early signs other companies may be impacted.
Sherman says some of Mitiga’s customers have reached out to it for help, while Mandiant told BleepingComputer it had been assisting Snowflake customers in recent weeks. Cybersecurity researcher Kevin Beaumont shared online that he knows of six companies that have been impacted. And Australian events company Ticketek has also revealed customer names and email addresses stored in a “cloud-based platform, hosted by a reputable, global third-party supplier” have been accessed, although a spokesperson refused to confirm if this was related to Snowflake at all.
“We haven’t seen the entire blast radius yet,” Sherman says. “Snowflake has thousands of clients—they offer self-registration—and some of their clients are huge companies. We expect to learn about additional companies compromised.”
18 notes
·
View notes
Text
Maryland’s top utility regulator was watching the news one February morning when a headline blindsided him: Two suspects with neo-Nazi ties had been charged with plotting to take down Baltimore’s power grid.
Jason Stanek, the then-chair of the state’s Public Service Commission, said Maryland regulators were “caught flat-footed,” not hearing a word from law enforcement before the news broke — or in the months afterward. Federal prosecutors have alleged the defendants were driven by “racially motivated hatred” to try to cut power to hundreds of thousands of people in the state’s largest city, which has a predominantly Black population.
The FBI declined to comment on its communications with the Maryland commission. But Stanek’s experience is not uncommon.
A POLITICO analysis of federal data and interviews with a dozen security, extremism and electricity experts revealed that despite a record surge in attacks on the grid nationwide, communication gaps between law enforcement and state and federal regulators have left many officials largely in the dark about the extent of the threat. They have also hampered efforts to safeguard the power network.
Adding to the difficulties, no single agency keeps a complete record of all such incidents. But the attacks they know about have regulators and other power experts alarmed:
— Utilities reported 60 incidents they characterized as physical threats or attacks on major grid infrastructure, in addition to two cyberattacks, during the first three months of 2023 alone, according to mandatory disclosures they filed with the Department of Energy. That’s more than double the number from the same period last year. DOE has not yet released data past March.
— Nine of this year’s attacks led to power disruptions, the DOE records indicate.
— The U.S. is on pace to meet or exceed last year’s record of 164 major cyber and physical attacks.
— And additional analyses imply that the true number of incidents for both 2022 and 2023 is probably even higher. POLITICO’s analysis found several incidents that utilities had reported to homeland security officials but did not show up in DOE data.

According to a report on grid security compiled by a power industry cyber clearinghouse, obtained by POLITICO, a total of 1,665 security incidents involving the U.S. and Canadian power grids occurred last year. That count included 60 incidents that led to outages, 71% more than in 2021.
While that report does not break down how many of those incidents occurred in which country, the U.S. has a significantly larger grid, serving 145 million homes and businesses, with nearly seven times Canada’s power-generating capacity.
Law enforcement officials have blamed much of the rise in grid assaults on white nationalist and far-right extremists, who they say are using online forums to spread tactical advice on how to shut down the power supply.
Concerns about the attacks have continued in recent months, with incidents including a June indictment of an Idaho man accused of shooting two hydroelectric stations in the state.
But law enforcement officers investigating alleged plots against the grid don’t necessarily alert the Energy Department or other regulatory bodies.
“We have no idea” how many attacks on the grid are occurring, said Jon Wellinghoff, a former chair of the Federal Energy Regulatory Commission, which regulates the U.S. electric grid. “It looks like they’re escalating if you look at the data. But if you don’t have enough data, you can’t discern patterns and proactively work to stop these things from happening.”
Wellinghoff was FERC’s chair when an unknown sniper attacked a Pacific Gas and Electric substation in San Jose, Calif., in 2013 — an incident regulators have described as a “wake-up call” on the electricity supply’s vulnerability to sabotage.

Last year’s record number of physical and cyber disruptions to the U.S. power system included several incidents that captured public attention, such as a December shooting attack against two North Carolina substations that left 45,000 people without power for four days. The state’s medical examiner has blamed the attack for the death of an 87-year-old woman who died after her oxygen machine failed, ruling it a homicide. Nobody has been charged.
“There is no doubt there’s been an uptick over the last three years in the amount of incidents and also the severity of the incidents,” said Manny Cancel, senior vice president at the North American Electric Reliability Corp., the nonprofit body in charge of setting reliability standards for the bulk power system. He is also CEO of its Electricity Information Sharing and Analysis Center, which gathers and analyzes data from power companies.
Cancel said NERC has “seen two pretty substantial increases” in incidents coinciding with the 2020 and 2022 election cycles.
Grid attacks that led to power outages increased 71% from 2021 to 2022, totaling 55 incidents in 2022, according to a NERC briefing to utilities that POLITICO obtained. That increase was primarily due to a rise in gunfire assaults against critical infrastructure.
The largest outage reported from a physical attack early this year — which occurred in March in Clark County, Nev. — affected more than 11,000 people, according to DOE data.
But the state Public Utilities Commission was not aware of any outage due to an attack occurring that day, spokesperson Peter Kostes told POLITICO by email. That’s even though state regulations require utilities to contact the commission within four hours of a significant outage.
The state’s largest utility, NV Energy, said in a statement that it had reported the incident to local law enforcement “as soon as we learned about this incident ... so we can continue to increase our resilience against ongoing threats to the energy industry.” A spokesperson for the utility did not respond to multiple requests for comment on whether it had informed the commission.
Federal regulations also require utilities to report cyber or physical attacks to DOE, including physical attacks that cause “major interruptions or impacts” to operations.
They must also tell the department about disruptions from weather or other causes that meet certain criteria, such as those that cut off service to more than 50,000 customers for at least an hour, an uncontrolled loss of more than 200 megawatts of power, or a utility voluntarily shutting more than 100 megawatts, according to an Energy Department spokesperson. The spokesperson provided the information on the condition that they not be identified by name.
The Energy Department’s records don’t include at least seven reported physical assaults last year and this year that the Department of Homeland Security and the affected utilities said caused substantive economic damage or cut off power to thousands of customers. POLITICO found these incidents by cross-checking the department’s data against warnings issued by DHS and the FBI’s Office of the Private Sector.
DOE said the incidents may not meet its reporting thresholds.
Several of the incidents missing from DOE’s data involved clear physical attacks, based on other agencies’ descriptions. But the utilities involved said they did not report the incidents to the department because the attacks did not affect the kind of major equipment that could lead to widespread, regional power failures.
One of the incidents not found in DOE’s records cut off power to about 12,000 people for roughly two hours in Maysville, N.C., after a shooting damaged a substation in November, according to a DHS report. The FBI’s investigation into the incident is ongoing, according to the intelligence agency.
The utility affected by the incident, Carteret-Craven Electric Cooperative, reported the incident to NERC’s Electricity Information Sharing and Analysis Center, but didn’t report the attack to DOE because it was a “distribution-level” incident, said Melissa Glenn, a spokesperson for the utility. That means the outages caused by the damage would have been limited to local power customers and not lead to the wider blackouts federal regulators are most concerned with.
In another case unreported to the Energy Department, a substation owned by the East River Electric Cooperative serving the Keystone oil pipeline in South Dakota was attacked by gunfire late at night in July 2022, according to DHS. The incident caused more than $1 million in damage and forced the pipeline to reduce operations while repairs were underway.
East River co-op spokesperson Chris Studer said the utility reported the incident to local law enforcement, which brought in the FBI. East River also reported the incident to NERC and its E-ISAC, along with regional grid agencies, but said it did not report it to DOE because the attack did not affect the bulk power system.
Brian Harrell, a former assistant secretary for infrastructure protection at DHS, said in an email that utilities have too many competing agencies to report to, and suggested reporting be streamlined to NERC’s E-ISAC.
“This lack of consistency, by no fault of the utility, suggests that the numbers may not paint a complete picture,” he said.
Grid experts said these data gaps clearly indicate a lack of understanding about which agencies utilities need to report to and when.
Utilities may be using a “loophole” based on definitions of what constitutes “critical infrastructure,” said Jonathon Monken, a grid security expert with the consulting firm Converge Strategies. He was previously senior director of system resilience and strategic coordination for the PJM Interconnection, the nation’s largest power market.
There are “lots of ways” to work around DOE requirements, Monken added, but as he reads the regulation, utilities are required to report any operational disruptions caused by a physical attack.
“[I]t appears the information you collected shows that companies are still missing the boat when it comes to mandatory reporting,” he said. “Not good.”
One former FERC official who was granted anonymity to speak about a sensitive security issue said the commission also received no alerts from law enforcement officials about the planned and actual attacks that took place last year. That omission hinders agencies’ ability to respond to these kinds of events, the person said.
A spokesperson for FERC declined to comment on the commission’s communications with law enforcement.
But Cancel defended government agencies’ response to these incidents, and said federal investigators may have had specific intelligence reasons for keeping FERC and state utility agencies out of the loop.
“I’m not a lawyer or a law enforcement professional, but you had an active criminal investigation going on,” he said. “I don’t think they wanted to sort of blow the horn on that and compromise the integrity of the investigation.”
An FBI spokesperson offered no direct response to these criticisms in an email, but said the agency “views cybersecurity as a team sport.” The person commented on the condition that the remark be attributed to the bureau.
The FBI urged utility executives last month to attend security training hosted by intelligence agents in order to ensure they are up to speed on the threats posed by bad actors.
“We can’t do it without you,” Matthew Fodor, deputy assistant director of the FBI’s counterterrorism division, said during an all-day FERC technical conference on Aug. 10. “The challenges that we have — and DOE can probably speak to this better than anybody — is limited resources.”
People attacking the electricity supply have thousands of potential targets, including power substations and smaller but critical pieces of utility infrastructure. The smaller pieces often go unprotected because federal standards do not require utilities to secure them.
Nearly half of the 4,493 attacks from 2020 to 2022 targeted substations, according to the NERC briefing from February, making them the most frequent targets for perpetrators over that period.
Details on how to carry out these kinds of attacks are available from extremist messaging boards and other online content, researchers and federal security officials say. These include maps of critical entry points to the grid, along with advice that extremists have gleaned from incidents like the assault in North Carolina.
Stanek, the Maryland electricity regulator, said he was “disappointed with the level of coordination and communication” that federal and state law enforcement displayed in handling the alleged plot in Baltimore. No trial date has been announced for the case, which is in U.S. District Court in Maryland.
Maryland’s Public Service Commission is in charge of ensuring that the state’s power system keeps the lights on. Regulators need to be kept informed of threats to the system so they can coordinate with other agencies in case an attack succeeds, Stanek said.
At the same time, he quipped, maybe he was better off in the dark after all.
“There’s a lot of colorful details in [the FBI report],” Stanek said. He paused, thinking. “And honestly, as a regulator, had I received these details in advance and shared the information with trusted sources within state government, I would have had sleepless nights.”
“So perhaps the feds did a favor by only sharing this information after everything was all said and done,” he added.
#us politics#news#politico#2023#alt right#domestic terrorists#neo nazis#fbi#power grids#power outages#Department of Energy#canada#white nationalists#Federal Energy Regulatory Commission#US electric grid#North American Electric Reliability Corp.#Department of Homeland Security#Office of the Private Sector#counterterrorism#cybersecurity#utility infrastructure#maryland
75 notes
·
View notes
Text
Summary:
When he was seventeen, after his mother took her own life, Butters disappeared from the town of South Park. No one has seen or heard from him since.
Five years later, Mysterion gets a job offer from Detective Harris in exchange for an unrefusable amount of money; He is to investigate and catch the criminal behind the latest cyber attack on the town residents’ bank accounts— one who calls himself Chaos. Dropped out, desperate and stuck in South Park, Kenny is willing to do anything to make ends meet until Karen’s graduation, and with Kyle’s help he might be able to pull it off. But the deeper they get into the case, the more Kenny’s identity and Karen’s future are under threat— and the less Kenny is sure he really wants to know who is behind Chaos’ mask.
Rating: M
Status: 3/25 (ongoing)
Words: 11.902
(Anyone willing to beta feel free to dm me! I’m grateful for any help :3)
#south park#butters stotch#kenny mccormick#mysterion#professor chaos#sp bunny#mystechaos#south park fanfiction#fic#fanfic#sp fanfiction#sp kenny#sp butters
12 notes
·
View notes
Text
"Anti-feminist blogger Jean-Claude Rochefort, who was convicted of fomenting hatred against women, has been sentenced to 12 months in jail.
The 74-year-old had been arrested in December 2019 in connection with posts and doctored images he had posted to his blog, in which he praised Marc Lépine, who murdered 14 women at Montreal's École Polytechnique on Dec. 6, 1989 in an anti-feminist attack.
Charged in 2010 for making death threats against women on his website, Rochefort was writing under a pseudonym. Montreal police's cyber investigation team nevertheless managed to find him and charge him again in December 2019.
He was found guilty of wilfully promoting hatred against women last August.
In his ruling, Quebec Superior Court Justice Pierre Labrie rejected Rochefort's claims that his publications constituted satire, exaggeration or self-deprecation.
Noting the use of the word kill and the use of images of firearms and decapitated women in the accused's posts, the judge found that Rochefort could not have been unaware that he was deliberately promoting hatred against women."
Full article
Tagging: @politicsofcanada
#cdnpoli#canada#canadian politics#canadian news#canadian#jean-claude rochefort#misogyny#sexism#violence#violence against women#misogyny tw#sexism tw#violence tw#violence against women tw#montréal#québec#montreal#quebec
137 notes
·
View notes
Text
New Chapter out!
Fic Summary:
At seventeen, after his mother took her own life, Butters Stotch vanished from the town of South Park. No one has seen or heard from him since.
Five years later, Mysterion gets a job offer from Detective Harris in exchange for an unrefusable amount of money; He is to investigate and catch the criminal behind the latest cyber attack on the town residents’ bank accounts— one who calls himself Chaos. Dropped out, desperate and stuck in South Park, Kenny is willing to do anything to make ends meet until Karen’s graduation, and with Kyle’s help he might be able to pull it off. But the deeper they get into the case, the more Kenny’s identity and Karen’s future are under threat— and the less Kenny is sure he really wants to know who is behind Chaos’ plan.
Rating: M
Status: 6/25 (updated weekly)
Words: 25,353
#butters stotch#kenny mccormick#mysterion#professor chaos#south park#sp#sp bunny#bunny#fanfic#fic#sp fanfiction#south park fanfiction#south park butters#south park kenny#mystechaos#south park bunny
10 notes
·
View notes
Text
The job of a SOC Analyst
The #1 thing people ask me about is what I do for a job.
I'm a tier 1 SOC Analyst and I'm currently training to do some Cyber Threat Intelligence.
I will explain in detail what I do on a daily basis and why I've decided to do this job... And the negatives.
First of all, what's a SOC. SOC stands for "security operations center". It's a place (in my case virtual as I'm full remote) where a group of people, divided by experience and area of expertise, do the following:
Monitor the activities going on the customer's network or endpoints(= every device connected to the network);
Assess and mitigate alerts coming from the network and/or the endpoint of the client -> These tools send alerts that need to be evaluated and mitigated/responded in a certain amount of time (it depends on the SOC and the type of alert, generally I can assume an amount of time from 15 to 30 minutes per alert. Which is not that much;
Investigate cybersecurity incidents -> the SOC also analyses the kind of "incident" that happens in deep detail by analysing malware, spam emails, the behaviour of users and so on;
If the SOC is big/mature enough there could be some sort of prevention of cybersecurity issues, generally we talk about threat hunting (here for more information on that) and cyber threat intelligence (gathering information from various sources to produce a report about the potential attackers considering also the characteristic of the customer's company such as the size, the geographical area of operations, media exposure, geopolitical issues and what they do - doing this for a bank is different than doing it for a industry)
There are also other functions (such as we have a Security Architect that prepares a personalised solution for each client).
I know what you're thinking. But the AI...
No, they cannot do my job, as the ability of a human to notice patterns and correlate the information among various sources is unique. I memorised, with time, the usual activities my customers do, therefore I can interpret the user actions even with limited sources. And this is just one example.
Soc analysts are roughly divided in three "categories", always keep in mind that every SOC is different and has its own internal rules, that are not to be divulged. This is the rough division I've learned studying cybersecurity and NOT my organisation division.
Tier 1 Analysts are the one that monitors the traffic and activities I've mentioned before. They triage the alerts and if something deserves more investigation or can be discarded. They often perform simple actions of remediation of incidents.
Tier 2 Analysts are the ones that go deeper - they collect malware samples from the incident and analyse it, investigate and remediate more complex security incidents.
Tier 3 Analysts perform more active prevention duties like threat hunting and vulnerability assessments.
Some sources put intelligence activity on the tier 3, others consider it a different activity from the scenario I've described. If a SOC is big enough they might have their own intelligence team separated from the "regular" soc analysts. The rigidity of these roles can vary, as you probably got from my own duties.
On the top we have a SOC manager to coordinate the activities I've described and security architects that design the solution (although the deployment of these solutions can be delegated to the analysts, since we also have to monitor how well these perform).
All these people are usually referred as "blue teamers" btw, which are the ones that perform defensive actions.
A company can have a red team (basically they attack the customer to gain information that the blue team will use to improve their activities). I actually wanted to be a red teamer at first, since it's considered the "cooler" job.
Ok, got it. Now explain to me how you got there since I've never heard anything about this before.
I have a friend that's a system engineer and recommended this job to me.
I studies physics at university but I failed (in my country physics include some computer science classes btw) and I had some related experience I won't share for privacy reasons. No I'm not a criminal lol.
I then started studying - did a bootcamp and got a couple of certifications. Then I got my job.
However. Generally you get a degree in computer science or software engineering, and some universities offer cybersecurity degrees. Unfortunately I cannot tell you what to pick as every university has its own program and I cannot help you with that.
Certifications are a big part of my job unfortunately - mostly because due to how fast it goes you absolutely need to be "on top". It's annoying, yes, I hate it.
However. Consider that once you're hired you definitely will get them paid by your employer - at least in Europe this is on them(idk about the US), but you need some knowledge of cybersecurity to start.
Since some of them are stupid expensive I 100% recommend the compTIA ones. They're basics and respected worldwide. A+, Network+ and Security+ are basics, vendor neutral (which doesn't tie you to a particular "source", as every company works differently), and is relatively cheap (~300€).
Remember that I had previous experience so no one cares that I don't have a degree - I do however and I hope that in the future I will be able to "fix" this.
Great. How do I know if I'm good for this job?
This is on you. However:
One important thing if you don't live in an English speaking country is a good attitude towards foreign languages. I speak 5 for example, but it's an hobby I do since I was a teen;
Can you manage stress? A SOC is a fast paced environment, and you have a limited time to deal with whatever gets thrown at you. You have 15 to 30 minutes to deal with an alert and make a decision. Can you do that without panicking, crying or throwing a tantrum?
Are you a fast learner? You need to learn quickly how to do things, since the tools we use are quite complicated.
Are you willing to work on shifts, Saturdays, Sundays, festivities included? A lot of people can't cope with this and it's fine because it's a massacre. The job is so stressful to the point a lot of people leave cybersecurity because of it. Do not underestimate it, please.
How good are you at remembering random information and making correlations? Because I can remember random bits of information that no one ever thinks of it and it's one of my greatest strengths.
You need to do teamwork and be good with people, customers and so on - you have to explain complicated things you probably read in another language to people that don't know anything about what you do. It's more difficult than most people think.
Procedures are everything here - and for good reasons.
I think this is it.
Money.
USA avg salary: 74 307$ (Glassdoor)
France avg salary: 42 000€ (Glassdoor)
UK avg salary: 28 809 £ (Glassdoor)
There are random numbers I've found online(and with a lot of discrepancies). Consider that you MUST negotiate your salary, and that in certain places you get paid more if you work out of the usual 8-19 work shift. Obv since I live in a different place I cannot tell you if it's worth it - you do your own calculations.
But that's beyond the purpose of this post.
11 notes
·
View notes
Text
File: The Wyoming Incident
SCP#: AEJ
Code Name: The Wyoming Incident
Object Class: Neutralized
Special Containment Procedures: SCP-AEJ has not been reported since its manifestation. Furthermore, those responsible were apprehended but eventually died as a result of the incident. As such, the chances of it happening again and low, but just to be safe, the Telecommunications Monitoring Office - Internet Division and Broadcast Division are to alert Foundation administrative staff in the event of SCP-AEJ or something similar happening again.
Description: SCP-AEJ was an incident where several TV stations were hacked by cyber terrorists determined to cause chaos for laughs. However, what they displayed was not disgusting or disturbing imagery, though it did appear as such, but in reality, was much worse. It's unknown exactly how, but the hackers were able to obtain rejected memetic images created by Group of Interest: PENTAGRAM.
For those that don't know, PENTAGRAM is a division of the United States Department of Defense. While the FBI: UIU was created to investigate anomalous threats within the US, PENTAGRAN was made specifically to combat anomalous threats to the ALL of the US. It has been approved of existence by the SCP Foundation and is funded by the Global Occult Coalition. Unfortunately, PENTAGRAM is not as protected as either organization and thus, was how this situation happened.
The hackers obtained the memetics which were rejected because they failed to do as PENTAGRAM wanted. Instead of proper brainwashing or memory wipe; they often causing seizers, headaches, stroke, nausea, and other forms of mental deterioration. These symptoms easily got worse as time went on often leading to their bodies flying in the air while they entered a comatose state, their eyes glowing in a blinding light, their skin suddenly rotting out of nowhere, or their heads just bloating until they explode. It should be noted that anomalous symptoms are always a risk with exposure to multiple memetics in a short period of time. It's for this reason why memetic training and therapy, though effective, is considered dangerous as it can overload the brain and damage it beyond repair.
SCP-AEJ was discovered in 2006 within [data expunged], [data expunged], [data expunged], and a few other cities, all of which are in Wyoming. The event nearly led to an MK Class Broken Masquerade Scenario had the Foundation not reacted in time.
Mobile Task Force Dionysus-1 "Fake News" was entrusted to feed the media a story of a sudden outbreak of a new pathogen within the state of Wyoming. Afterwards Mobile Task Force Gamma-5 "Red Herrings" was deployed to distribute amnestics to anyone who wasn't affected but witness the incident. Meanwhile Foundation agents and MTF units disguised as CDC agents found those who were affected and used amnestic treatment on those that could be saved and quarantined the rest. The hackers involved in the incident suffered the same fate as those who saw the broadcasting of the amnestics. They were used as test subjects to see how to properly subside and even reverse the effects before actual treatment was taken to the affected public. This action was approved by the Ethics Committee, "A fitting punishment" in their own words.
The cover story worked with the public believing those that could be saved were cured and those that were mutated were killed by the plague. The incident was unfortunately known forever in history as "The Wyoming Ghost Plague" or as "The Wyoming Incident". Though the Foundation can take pride in knowing that no civilian will ever know the true nature of the SCP-AEJ incident.
Side Note: PENTAGRAM vouched to the ACPA council to take responsibility for the SCP-AEJ incident. However, the ACPA did not listen with Foundation representatives even claiming, "a lesser organization cannot be expected to handle such consequences". Just words but considered quite the insult to those in the anomalous world that desire to protect the interests and innocence of the public.
.
SCP: Horror Movie Files Hub
#DZtheNerd#SCP: Horror Movie Files#SCP: HMF#SCP Foundation#SCP Fanfiction#SCP AU#SCP#Telecommunications Monitoring Office#PENTAGRAM#Mobile Task Force Dionysus-1 “Fake News”#Mobile Task Force Gamma-5 “Red Herrings”#SCP-AEJ#Neutralized#The Wyoming Incident#creepypasta#Internet Horror#Writing Horror#SCP GoI#SCP Group of Interest#SCP Groups of Interest
6 notes
·
View notes
Note
Hi sorry if this is a bother but i really loved (and needed) that most about MI6, do you think you can make one about MI5 too? I've been trying to find stuff about it but can't find any information as in depth as your post :)
I’m really glad the MI6 post was helpful! And it's no bother! I'll do it gladly!
Ready to jump back into the murky world of intelligence?
Alright, so we've talked about MI6 and how it gathers intelligence to aid the UK in its decision-making, but what about MI5?
Let's start with the basics.
Intelligence agencies 101: MI5

1.- What even?
Whereas MI6 is in charge of gathering intelligence overseas in order to support the government's security, defense, foreign and economic policies, according to the 1989 Security Service Act, MI5 is tasked with "the protection of national security and in particular its protection against threats such as terrorism, espionage and sabotage, the activities of agents of foreign powers, and from actions intended to overthrow or undermine parliamentary democracy by political, industrial or violent means". Such threats may come from abroad or from within.
MI5’s headquarters are found at Thames House, a Grade II (of special interest, warranting every effort to preserve it) building close to the Houses of Parliament in London. In addition to this, there are 8 regional offices in Luton, Wales, Bristol, Glasgow, Manchester, Liverpool, Leeds and Birmingham, as well as another headquarters in Northern Ireland.

2.- Who is who?
I'm sorry to be the bearer of bad news, but there is no M or C here.
The agency is under the authority of the Home Secretary, even though it does not form part of the Home Office.
The Director General (or DG) is the head of MI5, and is responsible for overseeing its operations and efficiency, reporting back to the Home Secretary and the Prime Minister, as well as ensuring the agency remains politically impartial.
There are 10 branches in MI5, and several entities that support its work, like the National Protective Security Authority (NPSA: providing organizations with security advice) and the Joint Terrorism Analysis Centre (JTAC: handles intelligence relating to international terrorism).
It is worth mentioning that in 2011, His Majesty, King Charles III became the Royal Patron of the Intelligence Services (including MI5, SIS and GCHQ). This means that he receives regular security briefings, as well as a daily ‘red box’ which includes intelligence reports, Cabinet papers, and confidential reports from Commonwealth countries.
There are over 5,000 employees in the organization and their roles include, investigations, technology, languages, surveillance, communications, information, protective security, administrations, building services and catering. As in MI6, all employees must be British, over the age of 18, and UK residents. They aren't allowed to discuss their application or job either.

3.- Operational Areas
MI5 mainly focuses on 4 areas: Terrorism, Espionage, Cyber Threats and the Proliferation of Weapons of Mass Destruction.
Counter-Terrorism
The agency focuses on different types of terrorism:
International terrorism: Groups such as ISIL and Al Qaeda.
Northern Ireland related: Dissident republican groups.
Right Wing Terrorism (RWT)/ Left, Anarchist and Single-Issue Terrorism (LASIT): This issue took primacy in 2020 and are handled just like international terrorism.
Counter-Espionage
Seeks to stop foreign intelligence agents from obtaining information and provides security advice to companies and organizations while working closely with MI6, GCHQ, Scotland Yard, as well as security and intelligence organizations abroad.
Cyber
Focuses on hostile actors, such as criminals, "hacktivist" groups, terrorists and foreign states, which are generally well equipped for cyber espionage and computer network attacks. These actors can target the government, the military, businesses, individuals and large volumes of sensitive data.
Cyber Espionage is called Computer Network Exploitation (CNS), while the use of malicious software against cyber infrastructure is denominated Computer Network Attack (CNA).
Counter-Proliferation
The UK is obliged by several international treaties and conventions to work against the threat that weapons of mass destruction pose. MI5 focuses on regimes and states that pursue clandestine weaponization programmes. To do this, the agency works with both private institutions and government agencies such as: The Department for Business, the Innovation and Skills (BIS), the Foreign and Commonwealth Office (FCO), the Ministry of Defence (MOD), His Majesty's Revenue and Customs (HMRC), the Home Office and the National Crime Agency (NCA).
4.- Tale as old as time...
We have talked about the “armed peace” period and how crazy the world was getting back in 1909, basically racing towards THE war everyone thought would put an end to all wars. It was back then that, fearing the German imperialistic ambitions, Great Britain established the Secret Service Bureau through Prime Minister Asquith’s Committee of Imperial Defence.
Initially, this agency handled both national and foreign affairs, under the leadership of 50 year-old Royal Navy Commander Mansfield Cumming and 36 year-old Army captain Vernon Kell.

However, down the road, our dear Commander Cumming advocated for the splitting of these branches and thus, the Secret Intelligence Service (MI6) and the Security Service (MI5) were born.
Right off the bat MI5 was tasked with dealing with a massive German espionage network that, according to “official” reports, had infiltrated Britain, causing widespread paranoia. The agency barely had 16 employees back then, but that, along with Churchill’s support (Home Secretary back then) was enough to find out about the existence of a German Naval Intelligence spy network. By the end of WWI, more than half the spies sent to Britain were caught by MI5.
However, the agency barely made it through the post-war cuts, not to mention its rivalry with Scotland Yard’s Special Branch and MI6 (the line between espionage and counter-espionage was REEEEEEAAAALLY thin and they were stepping on each other's toes).
Thankfully, the Soviet Union came to save the day when one of MI5’s surveillance operations revealed that Scotland Yard had been infiltrated by Soviet intelligence. By 1931, MI5 was completely in charge of counter-subversion operations, a responsibility that the agency would continue to hold until 1991.
In the 1970s, terrorism became a priority for MI5, especially those threats coming from Northern Ireland and Qadhafi's Libya, and after the 9/11 attacks, the agency changed its modus operandi entirely.
As you can see, the agency has had a very long history, however, its existence was only officially acknowledged in 1992.
5-. A rose by any other name...
The agency, just like MI6, has taken on many names throughout the years, starting with the Home Section of the Secret Service Bureau in 1909, the Directorate of Military Operations section 5 “MO5(g)” in 1914, Military Intelligence section 5 (MI5) in 1916, the Defence Security Service in 1929, and finally, the Security Service in 1931. And although the latter has remained its official name, the agency is most commonly referred to as MI5, even by those in it.
6.- Technicalities
As it turns out, MI5 shares its funding with MI6 and the GCHQ (no wonder they’re rivals...). According to a report from the 2018/19 period, MI5 used 67% of its budget for international counter-terrorism, 20% for Northern Ireland-related terrorism, and 13% for counter-espionage, counter-proliferation and protective security.
Also worth mentioning, while MI5 agents have plenty of powers, they are not authorized to make arrests, and that is why they work with the Metropolitan Police AKA Scotland Yard, providing them with the necessary intelligence.
Recently, reforms have been made within the agency, and people now have the right to find out the kind of information that MI5 has on them, as well as ask if a deceased relative used to work for the agency. If the relative is still alive, however, MI5 definitely won’t spill the beans. So uhm... you might want to wait a little before trying to find out what that weird uncle does.
7.- Intelligence
MI5 makes use of several techniques to gather intelligence, such as:
Covert Human Intelligence Sources: Also known as “agents”, these people provide secret information during investigations and are NOT MI5 employees.
Directed surveillance: Following and/or observing targets.
Interception of communications: Monitoring emails or phone calls.
Bulk personal data: information about a large number of people used to identify a subject of interest.
Intrusive surveillance: Eavesdropping devices in homes or cars.
Equipment interference: Covertly accessing computers or other devices.
And in case you were wondering, yep, these are all legal because guess what? Individual rights can often be voided when it comes to national security.
Well...
That was all on my behalf. I hope this turned out to be useful for you, and if you happen to have any more doubts on this or any other related topic, my ask is always open!
Yours truly,
-The Internationalist
#writing advice#writing help#creative writing#spies#writing community#writing resources#writing tips#MI5#spooks#writing spies
41 notes
·
View notes
Text
The need for good intelligence has never been more visible. The failure of the Israeli security services to anticipate the brutal surprise attack carried out by Hamas on Oct. 7, 2023 reveals what happens when intelligence goes wrong.
In contrast, in late February 2022, Russian President Vladimir Putin’s planned three-day “special military operation” to invade Ukraine and topple the government was pushed onto the back foot by the U.S. and U.K. intelligence communities. While Putin’s rapid seizure of Crimea by a flood of “little green men” in 2014 was a fait accompli, by the time of the 2022 invasion, anticipatory moves including the public declassification of sensitive intelligence ensured that both the intelligence community and Ukraine remained a step ahead of Putin’s plans.
Yet, despite the clear and enduring need for good intelligence to support effective statecraft, national security, and military operations, U.S. intelligence agencies and practitioners are undermined by a crisis of legitimacy. Recent research investigating public attitudes toward the U.S. intelligence community offers some sobering trends.
A May 2023 poll conducted by the Harvard University Center for American Political Studies and Harris Poll found that an eye-watering 70 percent of Americans surveyed were either “very” or “somewhat” concerned about “interference by the FBI and intelligence agencies in a future presidential election.”
A separate study, conducted in 2021 and 2022 by the Intelligence Studies Project at the University of Texas at Austin and the Chicago Council on Global Affairs, found that only 56 percent of Americans thought that the intelligence community “plays a vital role in warning against foreign threats and contributes to our national security.” That number is down 10 points from a previous high—if it can even be called that—of 66 percent in 2019, and the downward trend does not give us cause for optimism. Reframed, that statistic means that in 2022, an alarming (in our view) 44 percent of Americans did not believe that the intelligence community keeps them safe from foreign threats or contributes to U.S. national security.
Worse, despite abundant examples of authoritarian aggression and worldwide terror attacks, nearly 1 in 5 Americans seem to be confused about where the real threats to their liberty are actually emanating from. According to the UT Austin study, a growing number of Americans thought that the intelligence community represented a threat to civil liberties: 17 percent in 2022, up from 12 percent in 2021. A nontrivial percentage of Americans feel that the intelligence community is an insidious threat instead of a valuable protector in a dangerous world—a perspective that jeopardizes the security and prosperity of the United States and its allies.
The most obvious recent example of the repercussions of the corrosion of trust in the intelligence community is the recent drama over reauthorizing Section 702 of the Foreign Intelligence Surveillance Act (FISA). First introduced in the FISA Amendments Act of 2008, Section 702 is an important legal authority for the U.S. intelligence community to conduct targeted surveillance of foreign persons located outside the United States, with the compelled assistance of electronic communication service providers. According to a report published by Office of the U.S. Director of National Intelligence (DNI), 702 is “extremely valuable” and “provides intelligence on activities of terrorist organizations, weapons proliferators, spies, malicious cyber actors, and other foreign adversaries.”
Section 702 was scheduled to “sunset” at the end of 2023 if not reauthorized. Yet Congress failed to reauthorize 702 by the end of 2023, electing to punt the decision—as is so often the case—to this spring, when it was finally reauthorized (with some important reforms) in late April 2024, but it was only extended for two years instead of the customary five. An unusual alliance of the far right and the far left squeezed centrists and the Biden administration, which was strongly pushing for a renewal that would protect the civil liberties of U.S. citizens and not needlessly hobble the intelligence community in protecting the United States itself.
But the frantic down-to-the-wire negotiations about reauthorizing some recognizable form of 702 obscured a deeper problem at the heart of the contemporary Americans’ relationship with intelligence that has been brewing over the last decade: The fundamental legitimacy of a strong intelligence community—and the integrity of its practitioners—has been questioned by U.S. lawmakers on the far left and the far right, perhaps reflecting a misguided but increasing consensus of tens of millions of Americans.
This trend is now a crisis.
Section 702’s troubled journey faced queries from the privacy-oriented left, where those with overblown concerns about potential abuse by the intelligence community viewed reauthorizing 702 is tantamount to “turning cable installers into spies,” in the words of one opinion contributor published in The Hill. The intelligence community’s revised authorities (some adjustments were required given the 15 years of communications technology development since the amendment was first passed) were called “terrifying” and predictably—the most hackneyed description for intelligence tools—“Orwellian.” On the power-skeptical right, Section 702 is perceived as but another powerful surveillance tool of the so-called deep state.
In response to legitimate concerns about past mistakes, the intelligence community has adopted procedural reforms and enhanced training that it says would account for the overwhelming majority of the (self-reported) mistakes in querying 702 collection. According to a report from the Justice Department’s National Security Division, the FBI achieved a 98 percent compliance rate in 2023 after receiving better training. Further, the Justice Department and the DNI have gone to unprecedented lengths to publicly show—through declassified success stories—the real dangers that allowing 702 to lapse would bring to the United States and its allies.
Never before has an intelligence community begged, cajoled, and pleaded with lawmakers to enable it to do its job. After all, a hobbled intelligence community would still be held responsible should a war warning be missed, or should a terrorist attack occur.
For instance, Gen. Eric Vidaud, the French military intelligence chief, was promptly fired over intelligence failings related to Putin’s (re)invasion of Ukraine despite the Elysée’s criticisms of the warnings made by the United States and United Kingdom as “alarmist.” And Maj. Gen. Aharon Haliva, director of Israeli military intelligence, recently resigned over the Oct. 7 attacks despite the fault probably lying across Israel’s political landscape as well. Intelligence professionals pay more than their share of the bill when their crystal ball stays cloudy.
The hullabaloo over 702 is not the only recent instance painting the actions of the U.S. national security apparatus as questionable state activity conducted by dishonest bureaucrats, and some recent history helps put the recent events into a broader downward trend in trust.
In 2013, National Security Agency (NSA) mass-leaker Edward Snowden, a junior network IT specialist with a Walter Mitty complex, sparked a needed but distorted global conversation about the legitimacy of intelligence collection when he stole more than 1.5 million NSA documents and fled to China and ultimately Russia. The mischaracterization of NSA programs conveyed by Snowden and his allies (painting them as more intrusive and less subject to legal scrutiny than they were) led to popular misunderstandings about the intelligence community’s methods and oversight.
It was not only junior leakers whose unfounded criticism helped to corrode public faith in intelligence; it has also been a bipartisan political effort. In 2009, then-U.S. House of Representatives Speaker Nancy Pelosi claimed that the CIA had lied to her after she wished to distance herself from the agency’s “enhanced interrogation techniques”—which critics call torture. But Pelosi’s comments earned a “false” rating from Politifact’s “truth-o-meter.” Then-CIA Director Leon Panetta countered that “CIA officers briefed truthfully.”
Some suspicion of a powerful intelligence community stems from genuine failings of the past, especially the CIA’s activities in the early and middle stages of the Cold War, which included some distasteful assassination plots, the illegal collection of intelligence domestically (such as surveillance of Americans on political grounds, including illegally opening their mail), and the LSD experimentation on unwitting Americans as part of its infamous MKULTRA program.
Most of these excesses—characterized as the CIA’s “Family Jewels”—were reported to Congress, which held explosive hearings in 1975 to publicize these activities, bringing the intelligence agencies into the public realm like never before. Images of Sen. Frank Church holding aloft a poison dart gun, designed by the CIA to incapacitate and induce a heart attack in foreign leaders, became front page news. These serious failings in accountability were the dawn of rigorous intelligence oversight.
Public trust in government was already sinking when, in 1971, the Pentagon Papers revealed that politicians had lied about US activities in the deeply unpopular Vietnam war. The Watergate scandal the following year added fuel to fire. Although the CIA was not directly involved in Watergate, the involvement of former agency employees led to a wider belief that the agency was tainted. And in the late 1970s, CIA morale sank to an all-time low when then-President Jimmy Carter began the process of sharply reducing its staff, attributing the decision to its “shocking” activities.
In response to congressional findings and mountains of bad press, subsequent directors of the CIA considered the criticisms and made numerous changes to how the intelligence community operates. While the intelligence community (and its leaders) made good-faith efforts to operate strictly within its legal boundaries, be more responsive to congressional oversight, and embrace some level of transparency, the public image of the CIA and the broader intelligence community didn’t change. After the Cold War ended, the preeminent vice chairman of the Senate Select Committee on Intelligence, Daniel Patrick Moynihan, called twice for the disbanding of the CIA. Such political pummeling of the role of intelligence and the integrity of its practitioners was bound to leave a mark.
The politics of distrust are back to the bad old days. By 2016, distrust of the intelligence community had returned with a vengeance: then-presidential candidate Donald Trump claimed that NSA was circumventing domestic legal constructs to spy on his campaign through its close partnership with the Government Communications headquarters (GCHQ), the British signals intelligence agency. (The NSA said those claims were false and GCHQ called them “utterly ridiculous”.) As president-elect, Trump also compared U.S. intelligence to “living in Nazi Germany.” Once Trump entered the Oval Office, the FBI was a frequent target for his invective thanks to the investigation into possible Russian interference in the 2016 election.
While the intelligence community is a long way away from the excesses of the 1970s, it is not perfect. Intelligence is an art, not a science. It is not prediction so much as narrowing the cone of uncertainty for decision-makers to act in a complex world. Even when acting strictly within the law and under the scrutiny of Congress and multiple inspectors general, the intelligence community has been wrong on several important occasions. It failed to stop the 9/11 attacks, got the assessment that Iraq possessed weapons of mass destruction spectacularly wrong, and was made to look impotent by Osama bin Laden for nearly a decade before the U.S. Navy SEALs caught up with him on a CIA mission in Pakistan in May 2011.
Errors still happen because intelligence is hard, and the occasional failure to warn, to stop every attack, or to prevent every incorrect search query is inevitable. Today, mistakes are self-reported to Congress; they are no longer hidden away as they sometimes were in the past. Yet the intelligence community has done a poor job telling its own story and self-censors due to widespread over-classification—a problem that the DNI has acknowledged, if not yet remedied. It has only belatedly begun to embrace the transparency required for a modern intelligence apparatus in a democratic state, and there is much work yet to be done.
It is the job of the intelligence agencies to keep a calm and measured eye on dark developments. In a world in which the panoply of threats is increasing, the role of the intelligence community and its responsibilities within democratic states has never been greater. If the community cannot be trusted by its political masters in the White House and Congress, much less the American people, then it will not be given the ability to “play to the edge,” and the risk is that the United States and its allies will be blind to the threats facing them. Given the adversaries, the consequences could be severe.
U.S. intelligence has had a rebirth of confidence since 9/11 and the incorrect judgments of the Iraqi weapons program. It was intelligence and special operations that hunted and killed bin Laden, U.S. law enforcement that has kept the U.S. homeland safe from another massive terror attack, and the intelligence community correctly predicted the Russian invasion of Ukraine.
That increased sense of purpose and morale is moot if the U.S. people, Congress, or the president (sitting or future) do not trust them. This crisis of legitimacy is a trend that may soon hamper the intelligence community, and the results could be unthinkable. Getting the balance between civil liberties and security right isn’t an easy task, but the intelligence community must have the tools, trust, and oversight required to simultaneously keep faith with the American people while serving as their first line of defense.
18 notes
·
View notes
Text
Vernon
One Shots
Code of Temptation - When a series of cyber threats puts national security at risk, Y/N is assigned to lead the investigation. Her team is complemented by Vernon, a computer genius known for his dexterity in deciphering the most complex codes. (WC: +1k) - Smut
Concepts
11 notes
·
View notes