#cryptanalysis unit
Text
— Explaining Konohagakure’s Intelligence Department from Naruto to Boruto:
The information presented in this post has been checked and revised. My aim is not to hate or to discredit any of the characters mentioned. Please read about me for further information.
This post will contain evidence in picture format directly from the manga Naruto (1999 - 2014) created by Masashi Kishimoto and published by Shueisha in 1999. I will also use information from the official databooks.
This informative post will explain the role and utility of the Intelligence Division from its debut in Naruto to its development and role in Boruto. I will use information present in the novels and the Boruto manga because it includes character development within canon compliance.
This meta is crossposted in AO3.
I give my permission to use or share this thread with informative purposes as long as you credit me.
I do not support the anime or the work of Studio Pierrot in regards to Naruto because I consider it over exaggerated and beyond biased. Furthermore, these fillers include some actions that these characters are unable to do in the canon according to official sources and they also generate unnecessary debate.
This meta does contain anime scenes from Boruto because it is a monthly manga draft that depends heavily on anime for context.
Please, take this into consideration.
This meta will include a small discussion from my own point of view about the Intelligence Division and its members. There will be strong criticism and complaints, comparisons with other characters, previous leaders, etc.
Important: I will also refer to this Konoha branch as the “Intelligence Department” to distinguish it from the Allied Shinobi Forces Intelligence Division. This post includes a small discussion from my own point of view about the Intelligence Department and its members. There will be criticism and complaints, comparisons with other characters, previous leaders, etc.


The Intelligence Division (情報部, Jōhō-Bu ), or (in this meta) Intelligence Department (情報部 門 , Jōhō-Butmon ) is an organization formed by shinobi in charge of extracting information from people via interrogation, gather intel or study material that could be useful for the village or the security of the village. The Intelligence Department is part of the “Special Forces”, a group of other major village branches separate from the three main departmental divisions of Konohagakure.
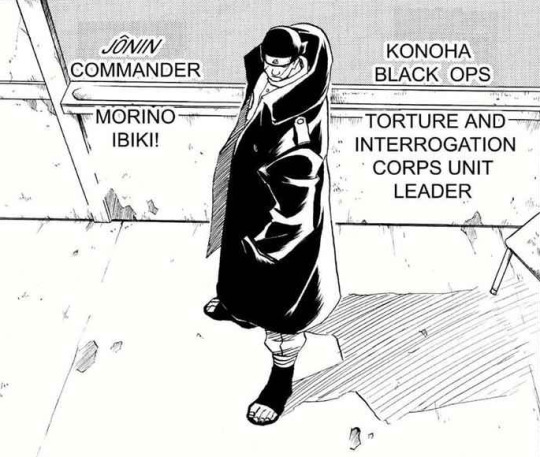
This branch is currently headed by Ibiki Morino as department head, hailed as a master of interrogation and t0rtur3 in many countries. He is officially known as the “Leader of the Intelligence Division” (木ノ葉隠れ情報部のリーダー, Konoha kakure jōhō-bu no rīdā ) although the translation says "Intelligence Team", versions change depending on who translates.


Ibiki Morino according to the fourth databook.
HISTORY:
It is unknown for how long this team has existed, but the Intelligence Division/Department officially debuted in chapter 418 of Naruto, at least the organization and its headquarters. The concept of interrogation, t0rtur3 or extracting information directly from a target debuted with the introduction of Ibiki Morino as the Captain of the T0rtur3 and Interrogation Force (拷問・尋問部隊隊長 Gōmon jinmon butai no taichō ).

Ibiki's early description as the "Captain of T&I before the Intelligence Department was created.
I want to add that the reason why Ibiki was never stated to be the Head of the Intelligence Department was because it had never appeared until chapter 418, so the existence of this Konoha division was unknown. In the fourth databook entry shown above, this division also debuts and Ibiki's profile reveals that he is in charge of this organization and its multiple units. In previous entries like the first databook, he was only described as Captain of T&I because it was the only unit that existed.


Debut of the Intelligence Department in chapter 418 contrasted with the first character description of Ibiki in the first databook ch. 1-119.
The organization, division or department and all of their subdivisions wear their own unique uniforms. Members of interrogation teams wear a dark gray two piece uniform and a black belt, while other teams prefer other uniforms.
Some members of the Intelligence Department wear uniforms to distinguish themselves from other departments or regular shinobi in a similar way the Medical Department’s Medical Corps wear their standard coats and medical uniforms.
Naruto:
As soon as Ibiki Morino was introduced in the story, we learn about Konoha’s T0rtur3 & Interrogation Force and their crowded unit; as well as getting a general idea about the presence of a team trained to interrogate targets using various methods.
However, the existence and the work of the Intelligence Division would not be known until chapter 418 of the manga. Everything else mentioned before was only the name of the team, but not their work.
During the era of the Fifth Hokage, the Intelligence Division was gathered in a building located in an unknown part of Konoha. The headquarters have different rooms dedicated to the different labor each of the teams carry out.
For example, there are rooms for regular interrogation (in the picture reconstructed after the Pain Arc), rooms for mental interrogation with special machinery, libraries for decoding teams, medical rooms for autopsies and a prison.
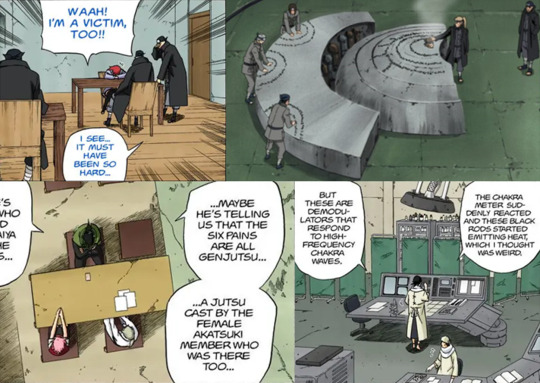
T&I Team room, Analysis Team room, Cryptanalysis Team room and Autopsy Room.
The Intelligence Department can be divided into the following teams:
Konoha T0rtur3 and Interrogation Force (木ノ葉暗部拷問・尋問部隊, Konoha Anbu Gomon/Jinmon-butai): Captained by Ibiki Morino (拷問・尋問部隊隊長, Gōmon jinmon-butai taichō), their mission is to gain information from the enemy by t0rturing them or exposing them to arduous interrogation methods. They often work together with ANBU. Some members include Mozuku, Ibiki Morino and chūnin.
Analysis Team (解析班, Kaiseki-han): Previously led by Inoichi Yamanaka. Their role was to take over if the T0rture and Interrogation Force was unsuccessful. Using secret techniques to read the mind, they obtain information directly from the target’s memories. Some members include Mawashi Dokuraku, Kumadori, Tonbo Tobitake and Aoba Yamashiro.
(Medical) Analysis Team: Composed by members of the Medical Department such as Shizune, Sakura Haruno or Ranka, they perform autopsies to obtain information from deceased individuals such as a Pain or White Zetsu. (The name of this team is not Medical Analysis Team but they are included inside the regular Analysis Team. I came up with the distinction to make this list easier.)
Cryptanalysis Team (暗号解読班, Angōkaidoku-han): They are a special team with the mission of decoding secret passwords or messages led by Mitoku. Some members include Shiho, Mitoku and Yurika, as well as Shikamaru Nara and Sakura Haruno occasionally.
Konoha Aviary: Although it is unknown if they belong to the Intelligence Division, this team collaborates with the Cryptanalysis Team. They receive messages from other villages by hawk, often encrypted or containing secret messages.

T&I Team, Analysis Team, Konoha Aviary, Cryptanalysis Team and (Medical) Analysis Team as depicted in the anime.
Other official teams dedicated to gather intelligence but not part of the Intelligence Division officially include:
Astronomical Team: Introduced in The Last: Naruto the Movie, their role is to study the moon and other celestial bodies and search for anomalies that could threaten Konohagakure.
Analytical Study (解読班, Kaidoku-han): Founded by Naruto Uzumaki when he became Hokage, this new team is located in the Hokage Residence. It debuted in Boruto: Naruto the Movie. They are focused on deciphering ancient codes such as Ōtsutsuki scrolls and similar objects. According to Kakashi Hatake in Kakashi Retsuden, some members include Shikamaru Nara, Shizune and Sakura Uchiha.
I want to add that the Analytical Study is something Ūkyo Kodachi wrote in the novel that Naruto created out of the blue, without reason. It seems like he didn't know about he existence of the Cryptanalysis Team, a team dedicated to deciphering any kind of code. He must have not read the manga, although this team appears in the movie too, its origins aren't revealed. In Kakashi Retsuden, the writer Jun Esaka reminds us that Shikamaru Nara and Sakura Haruno/Uchiha are part of the Cryptanalysis Team not the Analytical Study. However, since the Intelligence Department make no more appearances in Boruto, I imagine this is the new Analytical Study Team.


Astronomy Team and Analytical Study in both movies.
Blank Period:
The next time the Intelligence Division or any of its units appear is mainly Sakura Hiden and Sasuke Shinden novels.
Six months after Kaguya Ōtsutsuki was defeated, Sakura Haruno started preparations to create a Therapy Center, a mental health branch for children who are indirect victims of the shinobi world. Two years later, Sakura Haruno successfully founded the first ever mental healthcare institution inside Konoha Hospital ; and other villages like Sunagakure also followed her example.
However, a former member of ANBU Root, Kido Tsumiki, was plotting against Konoha and undergoing private experiments using Sasuke Uchiha and Naruto Uzumaki’s DNA in order to replicate Sharingan and Kurama’s powers.
At the end of the novel, when Sakura defeats Kido, he is taken to the Intelligence Department in order to be interrogated by Ibiki Morino.

Sakura Hiden chapter 8.
Months later, a series of missing Konoha shinobi attacked the village controlled by a jutsu that made their bodies explode. In order to unmask the perpetrator, Aoba Yamashiro, a veteran from the Analysis Team and Inoichi’s successor, read the mind of one of the targets that had been previously incapacitated and was being treated by Sakura. He delved into minds two times successfully.


Aoba Yamashiro becomes the official successor of Inoichi Yamanaka.
He is also the only character that has been shown to be able to reads minds without the aid of the Analysis Team's machine and be successful. He interrogated Kisame Hoshigaki until he broke the jutsu by hurting himself.
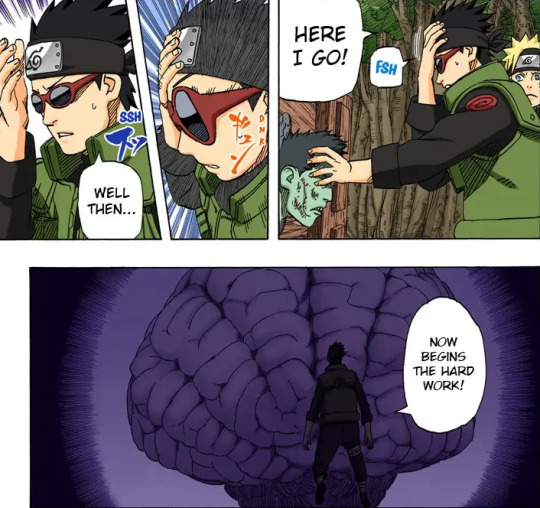
Aoba performing Psycho Mind Transmission without a device, a feat only achieved by him.
Boruto:
By the era of the Seventh Hokage, the Intelligence Division does not make any direct appearance, just mentions of one of its units and one of its members, or arbitrary work done by people that did not used to be among their ranks.
At the beginning of the manga, it is revealed that Ibiki Morino does still conduct interrogations, however, this time he is the only one present from the former T&I, now replaced by the help of Sai Yamanaka.
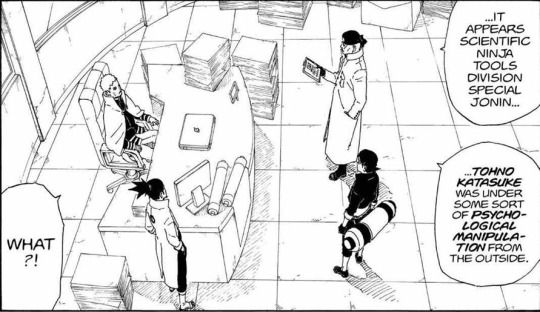

The remains of the Intelligence Department.
In the anime, Ibiki debuts with a similar introduction as in Naruto, probably a rendition to his imposing aura and, since it was his anime debut, an honor to his Naruto debut and to the original manga. He introduces himself as the Captain of T&I, just like in chapter 43.
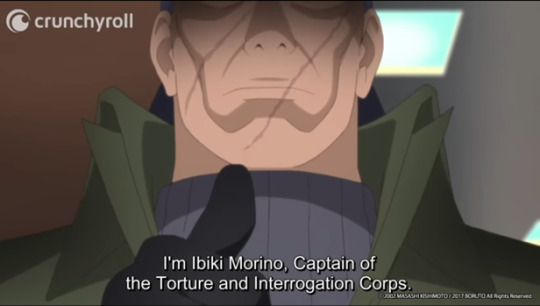
Ibiki's anime debut.
That is the only “relevant” mention and hint about the Intelligence Department in Boruto. There is one more mention about another one of its units in loose episodes but only in the anime, so they do not tie to the original story and can be dismissed.
Although the Analysis Team no longer exists within the story as a whole, there are characters that fulfill the task of mental interrogation in anime arcs such as Ino Yamanaka in episode 72 and Sasuke Uchiha in episode 151 who after normal interrogation later proceeds to read Shojoji's mind, but they do this as a side ability rather than as part of a team. Characters from the original Analysis Team such as Mawashi, Kumadori, Tonbo and Aoba are no longer in the story.


Ino Yamanaka preparing for mind probing. The interrogators using the help of Sasuke Uchiha's Sharingan for interrogation.
How does the Intelligence Department work and what is their role?
Gathering information from targets in order to learn their motives or their people behind their organization.
DISCUSSION:
How important is the Intelligence Department?
The Intelligence Department is of very little use in Boruto compared to Naruto. However, being written out of the story does not equal being less important.
Like many other teams, the Intelligence Department debuted fairly late into the story, only being fully introduced in the Pain Arc, but it is considered one of the major side supporting branches after the main tree: Shinobi forces, Medical Department/Corps and ANBU. The best example of their usefulness is interrogating Yūdachi from Amegakure, conducting the examination of the Animal Path in order to determine Pain’s Powers and deciphering Jiraiya’s message; all during the Pain Arc.
The equivalent of the Intelligence Department at the time of the battle against Madara and Obito Uchiha, the Intelligence Division (going by the same name as in Konoha), was also one of the most important support systems during the conflict.
Their function was changed during the global conflict.
Rather than collecting intel from enemies, the Intelligence Division would receive messages from the several teams scattered across the battlefield such as the emergence of a new enemy, casualties, infiltrations, etc. They would also relay battle tactics from the Chief Strategist to the different divisions.
One of the most important moves of this division was when the White Zetsu infiltrated the Logistical Support & Medical Division in order to take down the main battle support and their most skilled medics, as well as other battle divisions. It was thanks to Sakura Haruno, who defeated the White Zetsu and figured out their plans, and later contacted the Intelligence Division in order to alert the rest of the divisions, saving everyone from death as early as the first days.

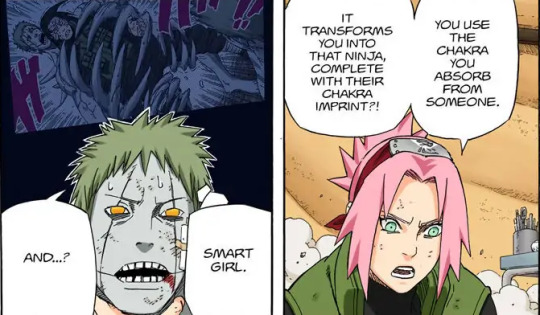

Sakura Haruno defeats White Zetsu and relayed the intel to the Intelligence Division.
The Intelligence Division would receive and relay, not search info for themselves. Like a Communication Division with multiple members and machinery.
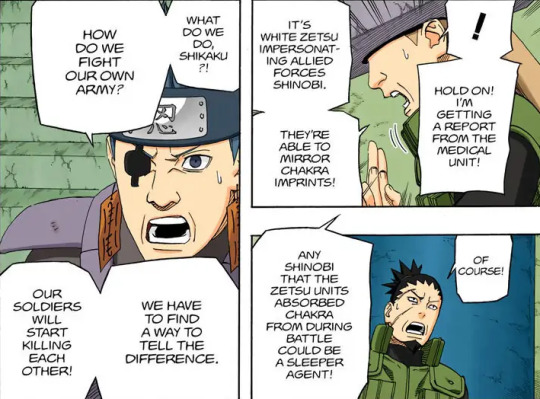
The difference between the Intelligence Division and Konoha's Intelligence Department.
The current problem of the Intelligence Department?
In Boruto, the Intelligence Department suffered a downgrade compared to previous appearances, so vast that the notion of the branch has almost completely disappeared. It is now down to one single member left and filler interrogations that serve no purpose to the real plot.
The downgrade is in relevance and build-up.
We used to see Ibiki Morino, Aoba Yamashiro or Inoichi Yamanaka performing interrogations on targets who would invade Konoha or trespass Konoha with dubious intentions.
The role of an interrogator has been simplified, with only brief mentions of Ibiki performing said interrogation sessions off-screen. Nothing of what we used to see in the past, but, of course, in peaceful times or times when the information about the enemy is on full display, there is no need for interrogators or intel gathering. There are other teams and individuals in Konoha, such as ANBU or Sasuke Uchiha, collecting information.
On the other hand, when it is needed or should be used, it is not.
The Intelligence Department in itself is not a failure, nor do their ranks fail at doing their job or need other people to step in for them. The failure comes with the writing quality in the sequel compared to Naruto, rather than the organization itself.
Could they be redeemed?
The Intelligence Division does not need to be redeemed or rewritten, the problem lies in how they are projected in the sequel.
Their functionality is perfect, at least in Naruto. They have the world’s best interrogator as their leader, several members of the staff and many specialized units.
Some of the things they could do are:
Interrogate enemies and former Kara outers such as Amado Sanzu, so before letting them do as they please they would go through Ibiki Morino, or Aoba Yamashiro if needed, first.
Recuperate bodies of the enemy if possible in order to be studied by the Medical Analysis Team and other medics such as Sakura Uchiha and Shizune.
Considering Konoha is the most powerful shinobi village and the Intelligence Department has resources, the usage of their staff leaves much to be desired in the script.

Note: The Fourth Shinobi World W4r has been replaced by global conflict to avoid mature content flags. T0rtur3 has also been censored.
#intelligence division#intelligence department#intel division#intel department#ibiki morino#aoba yamashiro#konohagakure#konoha#t&i#analysis team#cryptanalysis team#analysis unit#cryptanalysis unit#naruto meta#my naruto post#my publication#naruto analysis#mentions of:#shikamaru nara#sakura haruno#yamanaka members#inoichi yamanaka#naruto#boruto#naruto shippuden
27 notes
·
View notes
Text
TRUE CRIME - PT. 1
Ricky McCormick Cypher
My first True Crime blog post will be on the Ricky McCormick Cypher.
If you don’t know what a cypher is, here is a definition; A cypher is a message written in a secret code; a secret or disguised way of writing; a code.
This case is somewhat of a cold case, and at first the case was classified as a homicide, but was later determined otherwise.
Ricky McCormick was a high school dropout who had held multiple addresses in the Greater St. Louis area, living intermittently with his elderly mother. According to a 1999 article in the St. Louis Post-Dispatch, McCormick suffered from chronic heart and lung problems. He was not married, but had fathered at least four children. He had a criminal record, and had previously served 11 months of a three-year sentence for statutory rape. At the time of his death, he was 41 years old, unemployed, and receiving disability welfare payments.
McCormick's body was found on June 30, 1999, in a cornfield near West Alton, Missouri by a woman driving along a field road near Route 367. The reason he was 15 miles (24 km) away from his then-current address is another mystery, as he did not own a car and the area was not served by public transportation. Though the body had already somewhat decomposed, authorities used fingerprints to identify McCormick. There was no indication that anyone had a motive to kill McCormick and no one had reported him missing. As such, the authorities initially ruled out homicide; however, no cause of death was officially determined at the time. McCormick was last seen alive five days earlier, on June 25, 1999, getting a checkup at St. Louis's now-defunct Forest Park Hospital.
The two notes found in McCormick's pockets are written in an unknown code consisting of "a jumble of letters and numbers occasionally set off with parentheses" and are believed by the FBI to possibly lead to those responsible for the killing. Dan Olson, chief of the FBI's Cryptanalysis and Racketeering Records Unit, said, illustrating the significance of the notes, "Breaking the code could reveal the victim's whereabouts before his death and could lead to the solution of a homicide." Attempts by both the FBI's Cryptanalysis and Racketeering Records Unit (CRRU) and the American Cryptogram Association failed to decipher their meaning, and Ricky McCormick's encrypted notes are currently listed as one of CRRU's top unsolved cases, with McCormick's killer yet to be identified. According to members of McCormick's family, Ricky had used encrypted notes as a boy, but none of them knew how to read the code.
To this day, the code has yet to be deciphered. Yet, there is speculation on the internet as to what the note reads as.
I found this post on Reddit, made by u/TheLinguistGamer; on the r/UnresolvedMysteries subreddit. Here is their attempt at figuring out what it meant.
Thank you for reading! I used some of this information from Wikipedia, and the police reports. I will link them below.


4 notes
·
View notes
Note
I actually really love how you're writing Peggy in Of Home Near! She's an incredibly straightforward and grounded person, and while that makes her good at plowing through problems right in front of her, she doesn't do abstract very well. At least not yet. So of course she wouldn't buy into time travel as a real thing, to say nothing of her feelings toward Steve
Aww, thank you! I am thinking about Peggy a lot, since she's the character I'm most worried about; I've gone through CATFA and Agent Carter multiple times already this year, on top of my WWII research to make sure that she feels as grounded in canon and historically as possible. (Though AC has a lot of contradictions with CATFA, the main MCU saga, and also history. There was no vice president of the United States in 1946. You can't sight-decrypt a one-time-pad system. There's a reason I went on a long exegesis of how cryptanalysis works in that last chapter.)
From Peggy's point of view the time travel is just an absolutely ridiculous story, which...it is! It really is unless you've been dealing with Avengers-level nonsense for the past six years, and even then I think most of the Avengers would blink at it. (Though given that it's pretty close to the cover story Mysterio gives Peter and Fake Fury in FFH, I think they're just unusually gullible.) From Peggy's POV, Steve was only gone for four weeks (there's a week that passes between Steve and Nat's arrival and Peggy's and Phillips'), which is not that much longer than he was gone between going AWOL and returning from the Hydra factory. Plenty of Allied airmen got shot down and walked out after a lot longer than that, so the fact that he's shown up with this story is just...really, really weird. And that's without counting the wife.
I'm writing a Steve and Peggy interrogation scene now and just...neither of them is having a good time.
13 notes
·
View notes
Text
OP-20-G, The Cryptanalysis Unit of the U.S. Navy
OP-20-G, The Cryptanalysis Unit of the U.S. Navy
OP-20-G, the intelligence gathering and cryptanalysis unit of the United States Navy, played a crucial role in collecting and deciphering enemy communications during World War II and beyond. Operating in secrecy, OP-20-G contributed significantly to the success of American naval operations by providing vital intelligence and insights. In this blog post, we will explore the history, operations,…

View On WordPress
0 notes
Photo

Ricky McCormick
Ricky McCormick was a high school dropout who had held multiple addresses in the Greater St. Louis area, living intermittently with his elderly mother. According to a 1999 article in the St. Louis Post-Dispatch, McCormick suffered from chronic heart and lung problems. He was not married, but had fathered at least four children. He had a criminal record, and had previously served 11 months of a three-year sentence for statutory rape. At the time of his death, he was 41 years old, unemployed, and receiving disability welfare payments.
McCormick's body was found on June 30, 1999 in a cornfield near West Alton, Missouri by a woman driving along a field road near Route 367. The reason he was 15 miles (24 km) away from his then-current address is another mystery, as he did not own a car and the area was not served by public transportation. Though the body had already somewhat decomposed, authorities used fingerprints to identify McCormick. There was no indication that anyone had a motive to kill McCormick and no one had reported him missing. As such, the authorities initially ruled out homicide; however, no cause of death was officially determined at the time. McCormick was last seen alive five days earlier, on June 25, 1999, getting a check-up at St. Louis' now-defunct Forest Park Hospital.
The two notes found in McCormick's pockets are written in an unknown code consisting of "a jumble of letters and numbers occasionally set off with parentheses" and are believed by the FBI to possibly lead to those responsible for the killing. Dan Olson, chief of the FBI's Cryptanalysis and Racketeering Records Unit, said, illustrating the significance of the notes, "Breaking the code could reveal the victim's whereabouts before his death and could lead to the solution of a homicide." Attempts by both the FBI's Cryptanalysis and Racketeering Records Unit (CRRU) and the American Cryptogram Association failed to decipher their meaning, and Ricky McCormick's encrypted notes are currently listed as one of CRRU's top unsolved cases, with McCormick's killer yet to be identified. According to members of McCormick's family, Ricky had not used encrypted notes as a boy, and apparently no one in his family knows how to decipher the codes, either.



the two notes
27 notes
·
View notes
Text
The Zodiac Killer
The self-proclaimed Zodiac Killer is an unidentified American serial killer. He took credit of several murders in the San Francisco Bay Area between 1968 and 1969, but only five are directly linked to him. He taunted police and made threats through letters sent to newspapers in the area from 1969 to 1974. The police never caught him. The mystery surrounding the murders has inspired numerous books and movies, like Dirty Harry, in 1971, Zodiac, in 2007, and Awakening of the Zodiac, in 2017.
Zodiac Killer’s murders timeline
DEC. 20, 1968 The first confirmed murders attributed to the Zodiac Killer took place on the night of December 20, 1968, on Lake Herman Road, just inside Benicia city limits. The victims were high school students David Faraday and his girlfriend Betty Lou Jensen, who were shot to death in their car; shortly after 11:00 p.m., their bodies were found by Stella Borges, who lived nearby.

Newspaper page about the murders of David Faraday and Betty Lou Jensen
JULY 4, 1969 Just before midnight on July 4, 1969, Darlene Ferrin and Mike Mageau, her boyfriend, were sitting in a parked car in Blue Rock Springs Park, Vallejo. A car parked beside them, almost immediately drove away, and then came back after 10 minutes; the driver exited the vehicle and approached the couple with a flashlight. He shot them seven times each. Within an hour, a man called the Vallejo Police Department to report and claim responsibility for the attack; he also took credit for the murders of David Faraday and Betty Lou Jensen of six and a half months earlier.

Photos of David Faraday and Betty Lou Jensen
SEPT. 27, 1969 On the evening of September 27, 1969, the Zodiac Killer approached Cecelia Shepard and her boyfriend Bryan Hartnell as they were picnicking on a shore of Lake Berryessa, in Napa County. The man was wearing a black hood with clip-on sunglasses over the eye-holes, and a bib-like device on his chest that had a circle-cross symbol on it. He approached them with a gun, claiming to be an escaped convict from a prison, and told Shepard to tie up Hartnell, before tying her up. The man drew a knife and stabbed them both repeatedly, badly injuring the couple, then went back to their car and drew the cross-circle symbol with the inscription "Vallejo/12-20-68/7-4-69/Sept 27–69–6:30/by knife". At 7.40 p.m. on the same day, he called the Napa Police Department, to report and claim responsibility for the attack. When the police arrived, Shepard was still alive and described the attacker; she died two days later at the hospital, while Hartnell survived.

Photos of Cecelia Shepard and Bryan Hartnell
OCT. 11, 1969 Two weeks later, on October 11, 1969, taxi driver Paul Stine was found dead inside his taxi. He was shot in the head by a white male passenger, who had requested to be taken to Maple Street; for strange reasons Stine did not stop there but one block after, in Cherry Street. Three teenagers that lived across the street witnessed the passenger shooting Stine, and called the police while the crime was still occurring; they also stated that before running away, the man wiped the cab down. In the meantime, two policemen, Don Fouke and Eric Zelms, noticed a white man walking and entering inside one of the houses in the street; the suspect they were looking out for was supposedly black, and since the man they witnessed was white they did not stop him. As the murder did not seem to fit the Zodiac’s pattern it was initially thought to be a robbery, until the San Francisco Chronicle received a letter from the Zodiac Killer claiming the crime.

Crime scene of Paul Stine’s murder
MARCH 22, 1970 On the night of March 22, 1970, Kathleen Johns was driving with her newborn daughter on Highway 132 near Modesto, when a driver flashed his headlights at them. Johns pulled off the road and stopped, and so did the man; he told her that her right rear wheel was wobbling, and offered to tighten the lug nuts. After doing such, the man drove off, and when Johns pulled forward to re-enter the highway, the wheel almost immediately came off the car. The man came back and offered to drive her and her daughter to the nearest gas station. He drove them around for a long time, passing several gas stations, and when he stopped at an intersection Johns jumped out the car with her daughter and hid in a field. She later identified her kidnapper as the man depicted in a wanted poster for Paul Stine's murder, the Zodiac. Police never officially attributed the incident to the Zodiac.

Newspaper talking about Kathleen Johns kidnapping attempt
During the 1990s, many investigators claimed to have identified the Zodiac Killer; the most likely and most often cited suspect was Arthur Leigh Allen, a Vallejo schoolteacher who had been institutionalized for child molestation. The police were able to create a sketch of the Zodiac, using the descriptions of several witnesses; for example, the three teenagers who saw the man leaving the scene of Paul Stine’s murder, and Kathleen Johns, who identified the man that tried to kidnap her from the sketch of the Zodiac. Despite the mounting evidence and the numerous suspects, the killer remained at large.

Sketch of the Zodiac Killer made by the San Francisco police department
Letters and cyphers
The Zodiac sent several letters containing cyphers to various newspapers located in San Francisco, the San Francisco Examiner, the San Francisco Chronicle and the Vallejo Times-Herald. The newspapers received the first letter on August 1, 1969, where the killer took credit for the Benicia and Vallejo murders. To convince the police that he was the author of the murders, he included details that only the killer could have known. Each letter was closed by a circle with a cross through it, that would later become the Zodiac Killer’s symbol. High school teacher Donald Harden and his wife, Bettye, were able to solve the first cypher.

A couple of days after the murder of Paul Stine, on October 15, 1969, the San Francisco Chronicle received another letter from the Zodiac, where he took credit for the murder; this is also the first letter in which the killer uses the name “Zodiac”. At the end of the letter, the killer mused that he would next shoot out the tire of a school bus and "pick off the kiddies as they come bouncing out". The Zodiac Killer continued sending letters to the San Francisco Chronicle, where he claimed to have committed several more murders and mocked the police for their inability to catch him. The letters stopped in 1974.


In 2020, after 51 years, one of the messages written in code and attributed to the Zodiac Killer has been solved. The cypher does not reveal the killer's identity, however, it confirms his image as an attention-seeking killer who revelled in terrorizing the Bay Area in the late 1960s.
The three men who decrypted the code are David Oranchak, a software developer in Virginia, Sam Blake, an applied mathematician in Melbourne, Australia, and Jarl Van Eycke, a warehouse operator and computer programmer in Belgium. The F.B.I., which employs a team of code-crackers in its Cryptanalysis and Racketeering Records Unit, said they had verified Mr Oranchak’s claim of having broken the code.
It read: “I hope you are having lots of fun in trying to catch me that wasn’t me on the TV show which brings up a point about me I am not afraid of the gas chamber because it will send me to paradice all the sooner because I now have enough slaves to work for me where everyone else has nothing when they reach paradice so they are afraid of death I am not afraid because I know that my new life is life will be an easy one in paradice death.”
Though he had claimed to be responsible for 37 deaths, no Zodiac victims have been discovered since 1969, and in both the known and presumed Zodiac murders no suspect was ever arrested. Since the Faraday-Jensen murders, the inability to identify the Zodiac Killer has continued to frustrate law enforcement.
Sources:
Zodiac Killer - Biography
The coded message has been solved - New York Times
Zodiac Killer - Wikipedia
Zodiac Killer Timeline - San Francisco Chronicle
49 notes
·
View notes
Photo








Arrivals & Departures
23 June 1912 – 7 June 1954
Alan Mathison Turing OBE FRS
Alan Mathison Turing OBE FRS (/ˈtjʊərɪŋ/) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical computer science, providing a formalisation of the concepts of algorithm and computation with the Turing machine, which can be considered a model of a general-purpose computer. Turing is widely considered to be the father of theoretical computer science and artificial intelligence.
Born in Maida Vale, London, Turing was raised in southern England. He graduated at King's College, Cambridge, with a degree in mathematics. Whilst he was a fellow at Cambridge, he published a proof demonstrating that some purely mathematical yes–no questions can never be answered by computation and defined a Turing machine, and went on to prove the halting problem for Turing machines is undecidable. In 1938, he obtained his PhD from the Department of Mathematics at Princeton University. During the Second World War, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre that produced Ultra intelligence. For a time he led Hut 8, the section that was responsible for German naval cryptanalysis. Here, he devised a number of techniques for speeding the breaking of German ciphers, including improvements to the pre-war Polish bombe method, an electromechanical machine that could find settings for the Enigma machine. Turing played a crucial role in cracking intercepted coded messages that enabled the Allies to defeat the Nazis in many crucial engagements, including the Battle of the Atlantic. Due to the problems of counterfactual history, it is hard to estimate the precise effect Ultra intelligence had on the war. However, Professor Jack Copeland has estimated that this work shortened the war in Europe by more than two years and saved over 14 million lives.
After the war, Turing worked at the National Physical Laboratory, where he designed the Automatic Computing Engine (ACE), one of the first designs for a stored-program computer. In 1948, Turing joined Max Newman's Computing Machine Laboratory, at the Victoria University of Manchester, where he helped develop the Manchester computers and became interested in mathematical biology. He wrote a paper on the chemical basis of morphogenesis and predicted oscillating chemical reactions such as the Belousov–Zhabotinsky reaction, first observed in the 1960s. Despite these accomplishments, he was never fully recognised in his home country during his lifetime because much of his work was covered by the Official Secrets Act.
Turing was prosecuted in 1952 for homosexual acts; the Labouchere Amendment of 1885 had mandated that "gross indecency" was a criminal offence in the UK. He accepted chemical castration treatment, with DES, as an alternative to prison. Turing died in 1954, 16 days before his 42nd birthday, from cyanide poisoning. An inquest determined his death as a suicide, but it has been noted that the known evidence is also consistent with accidental poisoning.
In 2009, following an Internet campaign, British Prime Minister Gordon Brown made an official public apology on behalf of the British government for "the appalling way he was treated". Queen Elizabeth II granted Turing a posthumous pardon in 2013. The "Alan Turing law" is now an informal term for a 2017 law in the United Kingdom that retroactively pardoned men cautioned or convicted under historical legislation that outlawed homosexual acts. Turing has an extensive legacy with statues of him, many things named after him including an annual award for computer science innovations. He appears on the current Bank of England £50 note, which was released to coincide with his birthday. A 2019 BBC series, as voted by the audience, named him the greatest person of the 20th century.
6 notes
·
View notes
Text
(belated) Shikatema Week
/new tsafv2 chapter: on Spite
(on ao3 and ff.net too)
It’s only a second in the grocery store, a momentary glimpse in her periphery, but somehow, Temari is attuned to her. And Temari knows, even as she walks past one aisle and over to the next one, that it can’t be, because it makes no sense for her to just see some ponytail out of the corner of her eye and think, oh, her.
It’s not as though the girl is particularly enticing. She isn’t glamorous like some of the other women in Konoha; and she isn’t distinctly attractive, nor does she carry herself in any superlative fashion that might draw Temari's eyes to her — and yet, tonight, Temari finds herself foolishly backtracking and looking over her shoulder because she can’t tear her eyes away.
God. It’s not like Temari isn’t confident or anything of that sort. She isn’t worried.
She knows their relationship is solid.
Well, maybe not solid, but at least, she knows that he loves her.
And she knows that Shiho had never even stood a chance against Temari, if one considered them to be competing at all. Which they shouldn’t. They had never been adversaries — and not because the girl just wasn’t worthy of competition because Temari was so much better, but because Shikamaru had been the one to pursue Temari in the first place and so she hadn't actually had to fight anyone off.
But surely Shiho had stood a chance in general, hadn't she?
She is… kind? And definitely smart. Smarter, in the ways Shikamaru could be, than Temari (in books and patterns and dedication to the minutiae).
She watches as Shiho makes her way, her back to Temari, down the aisle and over to the checkout line.
Temari holds her breath. Her heart is pounding, as though she has been caught doing something she shouldn’t have been doing.
Without thinking, she reaches to her right and grabs an extra-large box of condoms. She doesn’t even look at the brand. She isn’t even in need of condoms right now. But she does it. And, joining her ice cream, vegetables, and bag of apples, she leaves the box on top and follows Shiho to the checkout.
By the time she rounds the corner, the person before Shiho is paying.
Temari pauses, still not seen, and straightens her dress around her hips, brushes a stray hair back, and licks her lips.
She knows, she knows, she is being ridiculous. Foolish.
"Good evening, Shiho.” She says, grin plastered on her face and shoulders pulled back.
The other girl turns and gives a noise of surprise. "I didn't see you there! Oh. Hi, Temari.” She smiles in kind and pushes her glasses up the bridge of her nose.
Shiho’s groceries, laid out on the counter, consist of mostly greens and a surprising amount of cereal and instant ramen.
“Where are you off to?"
Shiho looks down at her food and then back at Temari. She is shorter, her shoulders slimmer. ”Oh, uh… I'm cooking dinner for my niece. She's visiting."
Temari continues to smile, unsure what to say now that she’s approached the woman. Why did she come over here in the first place? It isn’t as though she really had finished buying all the things she’d set to buy and she was ready to check out. And it isn’t as though she’s defending any territory. Staking a claim or whatever. Shikamaru isn’t hers to claim. No one ever is, in general, but especially not him. Not to her.
"That's sweet of you."
"And you? I didn’t know you were in town.”
Temari looks over her basket. “I’m only here for a few weeks. Nothing too interesting planned.”
When she'd first come to the register, she'd had every intention of laying out everything from the basket, predominately the condoms, perhaps hoping to spite Shiho; as if to say, hello, yes, we have sex all the time! Like maybe it would demonstrate something to Shiho, something that would make her jealous of the relationship Temari has.
But now that she’s here, she doesn’t want to do that anymore. This is clearly Temari’s own… insecurity, maybe. And so, she stacks the box of condoms behind the apples on the conveyor belt and tries not to draw attention to it.
Shiho smiles.
"How have you been?" Temari asks as the checkout man started to ring up Shiho's basket.
"Good, good." Shiho adjusts her glasses again. They’re so thick, it’s hard to see her eyes.
"And how is work? How is the cryptanalysis team these days?"
Shiho perks up at that, the words working as a switch. “Great!” She breathes. “Hokage-sama just approved our request to start a sub-unit to go through all the archives of letters intercepted from the First Shinobi War that were never deciphered!"
Temari frowns. "Is there any use to going through old letters?"
“Well, uh,” she pulls out her wallet as the man rings her up. “No current use, which was why we kept being denied. But now that there isn't much work for us, we have time to look through everything. It’ll be so much fun!”
Temari laughs, stepping forward as Shiho moves to gather her first bag.
“I’m glad this is so exciting for you guys.”
Shiho blushes and looks down. After a moment, her gaze moves back to Temari, brows furrowed. "Shikamaru doesn’t — Yurika and I both asked him for help, but he said he doesn't understand the point of going through old records like that unless we need to. I guess he has a point. I mean, it’s not like other countries still use the old systems."
Temari shrugs. "They might again, who knows. If the cyphers were never broken, why wouldn’t they come back?”
There is a pause as Shiho groceries are fully bagged and the cashier hands her her change.
“Frankly, it’s not particularly likely. But you’re right. It is possible.” She smiles to herself and turns back to Temari. “Cryptanalysis was always the most interesting past-time for me.” She looks back down. "So any opportunity is welcome."
Temari smiles. If she could offer up Shikamaru, she would.
No. No. Nevermind. She could offer up Shikamaru. Maybe not technically, but that’s never stopped her before. She volunteers him all the time! At least once a week. She could easily say he’ll help, easily promise him, or at least, she could promise to talk to him. But she doesn’t. She keeps her mouth shut.
“It was good to see you.” Temari does say, after a moment, as Shiho takes her bags. And then, “I’ll tell Shikamaru you said hi.”
Shiho blushes, her shoulders rising to her ears. “I, uh, yes. You too! Good to see you too!”
That’s it, and then she is gone and Temari’s few items are being run up and put in a bag.
She wants to slap herself.
What the fuck was that? Why did she say that? Was that a nice thing to say? After all, there is no question that Temari would be speaking with him… Shiho must know that…. Or was it better to let things lie? To not acknowledge the other’s relationship to him at all?
Why is she being like this?
Temari sighs and watches, not paying attention as she goes through the motions of buying her groceries and then walking home down a mostly empty street. It’s early evening on a Friday and, while many people are still out, there is a lull between work and going out for dinner or whatever the youth do these days (Shikamaru never wanted to go anywhere — she had no idea what most people her age did on their off-time) so there are only a few people about.
Here’s the thing: Shiho is a good person. At least, as far as Temari knows. She’d only met her a few times and all except one, at a birthday party for Shikamaru, had been in passing. And that party was long before she and Shikamaru had gotten together, and Temari had spent a good hour or so in conversation with Shiho. And then she’d noticed Shikamaru’s eyes on her (they had always been on her, didn’t Shiho know?!) and Shiho’s eyes on him. And they hadn’t spoken much after that.
But from what she understands, from what she’s seen, Shiho is kind and wickedly smart and is very compatible with Shikamaru platonically. They make good coworkers. And when he was in the cryptanalysis unit, he was happy. Even now, he is happy to be consulted by them, even if only on occasion. He likes work where he can go at his own pace, where the people around him also want to keep the human interaction down to a minimum.
Temari is nothing like that. It’s nothing like their relationship. And in the end, it was nothing like Shikamaru. As far as she knows, from what she’s seen, he may enjoy that type of work, but deep down, he needs more. He’s led an army. He is never going to be satisfied behind a desk like that.
She turns the corner and there is no one on this street. Temari shifts the bag of groceries from one hand to the other.
She wishes she understood why she had done that. Why was her instinct to buy more condoms than she’ll need? Honestly, she is only here for a week. There is absolutely no way they will go through all of these. Though, she supposes, they could be saved for whenever she makes her way back.
But that’s not important. No. It’s not about stupid household purchases. It’s about why she wanted to do it, why she felt the need to buy them and gloat them in the first place.
She genuinely doesn’t understand it. Not fully. She knows, objectively, that she has become softer since dating Shikamaru (he softens her, her brother once said). She knows she is more emotional. But she is still more rational than that! There is no excuse for whatever wayward and misplaced jealousy that whole thing was… that whole, consuming feeling was. It makes no sense. And feeling it is absolutely without merit.
After all, Shiho is just a woman. Surely there have been more people who’ve had crushes on him. It can’t be helped. He is wonderful… mostly. And maybe, if (when) they do break up, eventually, he will find one of them.
When she arrives at his house, she finds the door unlocked. There are no lights on and the place is silent. Temari turns on the light in the entryway and, still holding the groceries in one hand, looks into the living room. Shikamaru had been at work this afternoon, but he’d said he would take off early so she expects him back by now. Still, she’s surprised to actually find him asleep on the couch.
Temari huffs and walks around the couch to the front, staring down at him. He’s on his back, legs up on the far arm and face serene. Behind her, on the coffee table, is a cup of tea. She touches the mug. Still warm. He hasn’t been asleep long.
She leans down to nudge him back, pushing at his hip. Without opening his eyes, Shikamaru groans. He does move though, rolling onto his side and scooting to press the back of his body into the back of the couch, giving her more room.
Temari drops the bag of groceries on the coffee table and turns to take a seat in the middle of the cushions, her tailbone against his hips, letting him curl his body around her.
He is breathing slowly and she knows, if she stays still for only a minute, he’ll fall back asleep.
She looks at him. He’s always been so beautiful. She’s always found him attractive. She hates, sometimes, that it took so long for her to actually tell him that. She hates all that time she wasted wanting him and doing nothing about it.
This is what Shiho wants. This is it. She wants to be sitting here, against him, being loved by him.
On the one hand, she wonders what is so special about him anyway? He’s often a pain. But on the other, she wholly understands. He is everything.
It’s been almost a minute since she sat down. She doesn’t want him going back to sleep.
Temari reaches out and grabs his chin, turning his face to hers fully. She looks at him, looks at the lines of his features and the beard he’s beginning to grow.
“You should shave.”
Slowly, Shikamaru opens his eyes, blinking, trying to bring her into focus. “You don’t like it?” He asks, voice gruff from rising from his nap.
Temari turns his face again, observing another angle and then lets go. She shrugs. “No.” She says, but she does kind of like it. No use giving him compliments though.
Shikamaru closes his eyes, slowly, lids heavy, completely unaffected by her comment. He shifts, moving further up the couch, so his head rests closer to the armrest. His knees bend as the top of his thighs press against the side of hers, allowing his whole leg to fit on the cushions.
“I saw that girl you used to work with,” Temari says, after a moment. She hadn’t wanted to say anything, but it’s on the tip of her tongue, as though waiting to be said. She recalls their meeting, and her ridiculous reactions, like a twinge in the back of her neck, right at the base of her skull. She’s embarrassed about it.
“Hm?”
“From the Konoha Cryptanalysis Team.”
Shikamaru makes a noise in his exhale and nuzzles his head into the cushions, eyes still closed. “Shiho? How is she?”
Temari stares at him. Why is she still doing this? Why is she pretending?
“She wants your help decoding some old cyphers. Or code. Whatever.”
“I know.”
They’ve obviously approached him. Shiho had said as much. And he’d turned them down. She wonders if Shiho is the one who spoke to him. Did she call? Send a letter? Stop by the Hokage’s or by his house? Had Shiho ever been to this house? When they’d spoke, at his birthday party years ago, it was at his parents… so Shiho had been there. Had she been here? Had she sat on this couch? Temari, after all, doesn’t live here. He must have people over when she is gone. She has people over all the time without him.
“She likes you, you know.” There is a bitterness to her tone that even she can hear. “Has a crush on you.”
Shikamaru, much to her chagrin, doesn’t respond. He doesn’t even move.
“She blushes when she talks about you.”
Temari doesn’t know why she wants the rise. She doesn’t know what she wants him to say.
He opens his eyes now, brow furrowed. His body is warm where it is touching her.
“Temari,” he says, and he leaves it hanging even though his tone implied there was more of the sentence to come.
“Yeah?”
He continues to stare at her, frowning, trying to figure something out. Then, after a long moment, he looks away. “Nothing.” He says. “Nevermind.”
She sighs and leans back, pressing what she can of her back against the couch, but she is limited in her comfort by his hips. He’s right. He hadn’t even said anything, but she feels it anyway.
Shikamaru has resettled, closing his eyes again. Temari tips her head back to look at the ceiling and drops her hand to the back of his neck, gently brushing her fingers to his skin, back and forth up the line of his neck. He makes a noise when she scratches him lightly, but otherwise stays silent. Maybe he falls back asleep.
Temari, though, is too caught up to wake him up again. She blinks up at the ceiling, taking in the wood panels and the stains on it.
What the fuck is wrong with her? Why on earth would she do this? Why is he turning her into this…this person? What is it about him that turns her into this?
She regrets everything about that interaction. She regrets all of it. She has never been this person. There is no need to feel threatened. There never will be. If they break up because of a third-party, that’s on them, not on the interloper. And, while possible, she has no inkling that that potential third-party would ever be Shiho. Acting otherwise — considering otherwise —, being so cruel, even if only in her head — it is unacceptable. Why does she hate Shiho so much?
Shikamaru, apparently not asleep, reaches for her hand, pulling it away from his neck and using his grip to tug her down. Naturally, Temari adjusts, letting him pull her so that she is lying against him, back pressed to his chest, held by him.
It’s easy, now, to relax into his grip, to be comforted by his touch, to let the parts of his body fall in against the parts of hers. She can feel his breath against the back of her neck, the beating of his heart against her spine, hand holding her sternum, fastening her tightly against him.
How lucky, she is, that he wants her too. How lucky, that she doesn’t have Shiho’s lot. How lucky. Because if he didn’t want her, wouldn’t she be in the same position? Would she not want him, still, as Shiho does? Wouldn’t she also spend the days waiting for him to look her way, like Shiho seems to?
Because there’s no reality, she admits, only for a moment and only to herself (she’ll never say anything so naive to Shikamaru), in which she doesn’t love him.
It’s hours later when they wake up. They’ve slept through dinner and all the melted ice cream she’d bought, not well-sealed apparently, has ruined the box holding the condoms.
50 notes
·
View notes
Text

• Alan Turing
Alan Mathison Turing was an English mathematician, and computer scientist. Turing was highly influential in the development of theoretical computer science, providing a formalisation of the concepts of algorithm and computation with the Turing machine, which can be considered a model of a general-purpose computer.
Turing was born on June 23rd, 1912 in Maida Vale, London, while his father, Julius Mathison Turing, was on leave from his position with the Indian Civil Service (ICS) at Chatrapur, then in the Madras Presidency and presently in Odisha state, in India. Turing's mother, Julius' wife, was Ethel Sara Turing. Julius' work with the ICS brought the family to British India, where his grandfather had been a general in the Bengal Army. However, both Julius and Ethel wanted their children to be brought up in Britain, so they moved to Maida Vale, London, as recorded by a blue plaque on the outside of the house of his birth. Turing had an elder brother, John. Turing's father's civil service commission was still active and during Turing's childhood years Turing's parents travelled between Hastings in the United Kingdom and India, leaving their two sons to stay with a retired Army couple. Very early in life, Turing showed signs of the genius that he was later to display prominently.
Turing's parents enrolled him at St Michael's, a day school at 20 Charles Road, St Leonards-on-Sea, at the age of six. The headmistress recognised his talent early on, as did many of his subsequent teachers. Between January 1922 and 1926, Turing was educated at Hazelhurst Preparatory School, an independent school in the village of Frant in Sussex (now East Sussex). In 1926, at the age of 13, he went on to Sherborne School, a boarding independent school in the market town of Sherborne in Dorset. The first day of term coincided with the 1926 General Strike, in Britain, but Turing was so determined to attend, that he rode his bicycle unaccompanied 60 miles (97 km) from Southampton to Sherborne, stopping overnight at an inn. Turing's natural inclination towards mathematics and science did not earn him respect from some of the teachers at Sherborne, whose definition of education placed more emphasis on the classics. Despite this, Turing continued to show remarkable ability in the studies he loved, solving advanced problems in 1927 without having studied even elementary calculus. In 1928, aged 16, Turing encountered Albert Einstein's work; not only did he grasp it, but it is possible that he managed to deduce Einstein's questioning of Newton's laws of motion from a text in which this was never made explicit.
After Sherborne, Turing studied as an undergraduate from 1931 to 1934 at King's College, Cambridge, where he was awarded first-class honours in mathematics. In 1935, at the age of 22, he was elected a Fellow of King's College. In 1936, Turing published his paper "On Computable Numbers, with an Application to the Entscheidungsproblem". In this paper, Turing reformulated Kurt Gödel's 1931 results on the limits of proof and computation, replacing Gödel's universal arithmetic-based formal language with the formal and simple hypothetical devices that became known as Turing machines. From September 1936 to July 1938, Turing spent most of his time studying under Church at Princeton University, in the second year as a Jane Eliza Procter Visiting Fellow. In addition to his purely mathematical work, he studied cryptology and also built three of four stages of an electro-mechanical binary multiplier. In June 1938, he obtained his PhD from the Department of Mathematics at Princeton. When Turing returned to Cambridge, he attended lectures given in 1939 by Ludwig Wittgenstein about the foundations of mathematics. Turing and Wittgenstein argued and disagreed, with Turing defending formalism and Wittgenstein propounding his view that mathematics does not discover any absolute truths, but rather invents them.
During the Second World War, Turing was a leading participant in the breaking of German ciphers at Bletchley Park. From September 1938, Turing worked part-time with the Government Code and Cypher School (GC&CS), the British codebreaking organisation. He concentrated on cryptanalysis of the Enigma cipher machine used by Nazi Germany, together with Dilly Knox, a senior GC&CS codebreaker. Soon after the July 1939 meeting near Warsaw at which the Polish Cipher Bureau gave the British and French details of the wiring of Enigma machine's rotors and their method of decrypting Enigma machine's messages, Turing and Knox developed a broader solution. Turing's approach was rather general, using crib-based decryption for which he produced the functional specification of the bombe. On September 4th, 1939, the day after the UK declared war on Germany, Turing reported to Bletchley Park, the wartime station of GC&CS. Specifying the bombe was the first of five major cryptanalytical advances that Turing made during the war. By using statistical techniques to optimise the trial of different possibilities in the code breaking process, Turing made an innovative contribution to the subject. Turing had a reputation for eccentricity at Bletchley Park. He was known to his colleagues as "Prof" and his treatise on Enigma was known as the "Prof's Book". While working at Bletchley, Turing, who was a talented long-distance runner, occasionally ran the 40 miles (64 km) to London when he was needed for meetings, and he was capable of world-class marathon standards.
Within weeks of arriving at Bletchley Park, Turing had specified an electromechanical machine called the bombe, which could break Enigma more effectively than the Polish bomba kryptologiczna, from which its name was derived. The bombe, with an enhancement suggested by mathematician Gordon Welchman, became one of the primary tools, and the major automated one, used to attack Enigma. The bombe searched for possible correct settings used for an Enigma message (i.e., rotor order, rotor settings and plugboard settings) using a suitable crib: a fragment of probable plaintext. By late 1941, Turing and his fellow cryptanalysts Gordon Welchman, Hugh Alexander and Stuart Milner-Barry were frustrated. Building on the work of the Poles, they had set up a good working system for decrypting Enigma signals, but their limited staff and bombes meant they could not translate all the signals. In the summer, they had considerable success, and shipping losses had fallen to under 100,000 tons a month; however, they badly needed more resources to keep abreast of German adjustments. At the park, he further developed his knowledge of electronics with the assistance of engineer Donald Bayley. Together they undertook the design and construction of a portable secure voice communications machine codenamed Delilah. Though the system worked fully, with Turing demonstrating it to officials by encrypting and decrypting a recording of a Winston Churchill speech, Delilah was not adopted for use. Turing also consulted with Bell Labs on the development of SIGSALY, a secure voice system that was used in the later years of the war.
Between 1945 and 1947, Turing lived in Hampton, London, while he worked on the design of the ACE (Automatic Computing Engine) at the National Physical Laboratory (NPL). Although ACE was a feasible design, the secrecy surrounding the wartime work at Bletchley Park led to delays in starting the project and he became disillusioned. In late 1947 he returned to Cambridge for a sabbatical year during which he produced a seminal work on Intelligent Machinery that was not published in his lifetime. In 1948, Turing was appointed reader in the Mathematics Department at the Victoria University of Manchester. A year later, he became Deputy Director of the Computing Machine Laboratory, where he worked on software for one of the earliest stored-program computers—the Manchester Mark 1. When Turing was 39 years old in 1951, he turned to mathematical biology, finally publishing his masterpiece "The Chemical Basis of Morphogenesis" in January 1952.
In 1941, Turing proposed marriage to colleague Joan Clarke, a fellow mathematician and cryptanalyst, but their engagement was short-lived. After admitting his homosexuality to his fiancée, who was reportedly "unfazed" by the revelation, Turing decided that he could not go through with the marriage. In January 1952, Turing was 39 when he started a relationship with Arnold Murray, a 19-year-old unemployed man. On 23 January, Turing's house was burgled. Murray told Turing that he and the burglar were acquainted, and Turing reported the crime to the police. During the investigation, he acknowledged a sexual relationship with Murray. Homosexual acts were criminal offences in the United Kingdom at that time, and both men were charged with "gross indecency". Trials were held on 27 February during which Turing's solicitor "reserved his defence", i.e., did not argue or provide evidence against the allegations. Turing was later convinced by the advice of his brother and his own solicitor, and he entered a plea of guilty.
Turing was convicted and given a choice between imprisonment and probation. His probation would be conditional on his agreement to undergo hormonal physical changes designed to reduce libido. He accepted the option of injections of what was then called stilboestrol. a synthetic oestrogen; this feminization of his body was continued for the course of one year. The treatment rendered Turing impotent and caused breast tissue to form, fulfilling in the literal sense Turing's prediction that "no doubt I shall emerge from it all a different man, but quite who I've not found out". Turing's conviction led to the removal of his security clearance and barred him from continuing with his cryptographic consultancy for the Government Communications Headquarters. On June 8th, 1954, Turing's housekeeper found him dead at the age of 41; he had died the previous day. Cyanide poisoning was established as the cause of death. An inquest determined that he had committed suicide. Turing's remains were cremated at Woking Crematorium on June 12th, 1954, and his ashes were scattered in the gardens of the crematorium.
In August 2009, British programmer John Graham-Cumming started a petition urging the British government to apologise for Turing's prosecution as a homosexual. The petition received more than 30,000 signatures. The Prime Minister, Gordon Brown, acknowledged the petition, releasing a statement on 10 September 2009 apologising and describing the treatment of Turing as "appalling".
#biography#pride month#gay men in history#second world war#world war 2#world war ii#computer technology#alan turing#enigma machine#british history#british#the real story
51 notes
·
View notes
Photo


Alfred Dillwyn "Dilly" Knox (deceased)
Gender: Male
Sexuality: Bisexual
DOB: 23 July 1884
RIP: 27 February 1943
Ethnicity: White
Occupation: Codebreaker, scholar, papyrologist
Note 1: As a member of the Room 40 codebreaking unit he helped decrypt the Zimmermann Telegram which brought the USA into the First World War.
Note 2: At Bletchley Park he worked on the cryptanalysis of Enigma ciphers until his death in 1943. He built the team and discovered the method that broke the Italian Naval Enigma, producing the intelligence credited with Allied victory at the Battle of Cape Matapan. In 1941 Knox broke the Abwehr Enigma. By the end of the war, Intelligence Service Knox had disseminated 140,800 Abwehr decrypts, including intelligence important for D-Day.
Note 3: At Eton he and John Maynard Keynes were lovers
#Dilly Knox#Alfred Knox#lgbt history#remembrance day#lgbt#male#bisexual#1884#rip#historical#white#codebreaker#war hero#scholar#popular#popular post
169 notes
·
View notes
Text
Alan Turing




Alan Turing was a brilliant man who played a major role in WWII on the side of the Allied Forces. He was a part of a code breaking team that worked to decode German ciphers. “During World War II, Turing was a leading participant in wartime code-breaking, particularly that of German ciphers... where he made five major advances in the field of cryptanalysis, including specifying the bombe, and electromechanical device used to help decipher the German Enigma encrypted signals.” (Biography.com) Alan Turing was also a gay man and this led to him being convicted for public indecent. Being a homosexual was illegal in the United Kingdom at this time. He was given the option to be imprisoned or under go chemical castration. He chose the second option. Since he was convicted, he was no longer allowed to continue his cryptography work. “Turing died on June 7, 1954. Following a postmortem exam, it was determined that the cause of death was cyanide poisoning.” (biography.com)
Turing was considered as going against the gender stereotype of the time. He was a gay man and that was not even legal in the United Kingdom. The social norm for a man at this time was a straight man who would have a wife and kids. He would provide for the family and be the head of the household. Turing’s “lifestyle” went against this norm. He was not performing the right gender characteristics of the time. But, he was still this amazing person that played such and important role in World War II. Now, of course, he is recognized for his work as a cryptographer and mathematician. Turing was given a Royal Pardon in 2013. “Three years later, on October 20, 2016, the British government announced “Turing’s Law” to posthumously pardon thousands of gay and bisexual men who were convicted for homosexual acts when it was considered a crime.” (biography.com) And in July of 2019, “the Bank of England announced that Turing would appear on the UK’s new £50 note, along with images of his work.”
I am not arguing here that homosexuality is performance or that sexuality is something that you can choose to perform. My argument for this story is that Alan Turing, arguably a war hero, didn’t fit into the societal ideal of a man. While most war heroes would be seen as the ideal and would have been rewarded for their service, Turing was not given the appropriate recognition until almost 60 years after his conviction and death.
"Alan Turing." Biography.com. July 22, 2020. Accessed March 05, 2021. https://www.biography.com/scientist/alan-turing.
1 note
·
View note
Text
'I Am Not Afraid of the Gas Chamber': Codebreakers Solve Old Zodiac Killer Cipher
FBI backs amateur sleuths who appear to have deciphered a chilling message from the infamous 1960s killer.

A San Francisco Police Department wanted bulletin and copies of letters sent to the San Francisco Chronicle by a man who called himself Zodiac on display in San Francisco on May 3, 2018.Eric Risberg / AP file
— December 11, 2020 | By Andrew Blankstein and David K. Li | NBC News
An international team of amateur sleuths claim to have decoded a half-century-old taunt by California's notorious Zodiac Killer.
And federal authorities said they believe the code breakers appear to be on solid ground in following the mysterious killer who fatally stabbed or shot five people in Northern California in 1968 and 1969.

San Francisco homicide detectives David Toschi and William Armstrong go through the clothing of a murder victim at the morgue in the Hall of Justice in San Francisco on March 29, 1974. The Zodiac killer is blamed for at least five murders in 1968 and 1969 in the San Francisco Bay Area.Susan Ehmer / The San Francisco Chronicle via AP file
The killer sent taunting letters and cryptograms to police and newspapers. He was dubbed the Zodiac killer because some of his cryptograms included astrological symbols and references.
A 340-character cipher has been a mystery to investigators for all these years, until Australian software engineer Sam Blake, American cryptographer David Oranchak and Belgian software engineer Jarl Van said they finally got the symbols, numbers and letters to mesh into a coherent — though chilling — message.
"I HOPE YOU ARE HAVING LOTS OF FUN IN TRYING TO CATCH ME THAT WASNT ME ON THE TV SHOW WHICH BRINGS UP A POINT ABOUT ME I AM NOT AFRAID OF THE GAS CHAMBER BECAUSE IT WILL SEND ME TO PARADICE," killer allegedly wrote.
It wasn't immediately clear what television show the Zodiac Killer could have been referencing.
The killer continued his ramblings about "paradice."
"ALL THE SOONER BECAUSE I NOW HAVE ENOUGH SLAVES TO WORK FOR ME WHERE EVERYONE ELSE HAS NOTHING WHEN THEY REACH PARADICE SO THEY ARE AFRAID OF DEATH I AM NOT AFRAID BECAUSE I KNOW THAT MY NEW LIFE IS LIFE WILL BE AN EASY ONE IN PARADICE DEATH," the killer said.

In a statement from FBI headquarters on Friday, the bureau said its own Cryptanalysis and Racketeering Records Unit (CRRU) acknowledged and confirmed the code breakers' work.
"Over the past 51 years CRRU has reviewed numerous proposed solutions from the public — none of which had merit," the FBI said. "The cipher was recently solved by a team of three private citizens."
The Zodiac Killer has never been caught and the case is still active.
"The FBI is aware that a cipher attributed to the Zodiac Killer was recently solved by private citizens," the FBI's San Francisco office said in a statement on Friday.
"The Zodiac Killer case remains an on going investigation for the FBI San Francisco and our local law enforcement partners."
— Andrew Blankstein is an investigative reporter for NBC News. He covers the Western United States, specializing in crime, courts and homeland security.
— David K. Li is a breaking news reporter for NBC News.
2 notes
·
View notes
Text
LGBTQ+ History: Alan Turing

On this day in 1912, the man who is credited as the father of modern computing was born in London. During his childhood, his father’s civil service commission was still active and he spent much time in the care of a retired army couple as his parents traveled back and forth between the UK and India. He was first enrolled in a local public day school, but once his headmistress and teachers saw his exceptional ability, he transferred to a private academy and then subsequently a private boarding school. His teachers there, however, were less than impressed by his remarkable ability in mathematics, problem solving, and understanding the implications of Einstein’s work, writing to his parents that he would not succeed unless he focused more on classic education as opposed to mathematics and technological advancement.
Whilst at Sherborne, his boarding school, he found love with another student, Christopher Collan Morcom. He has been credited as inspiration behind Turing’s work, though he tragically died of bovine tuberculosis in early 1930 after having drank infected cow’s milk a few years prior. After his death, Turing and Morcom’s mother kept in contact, exchanging letters a few times a year.
Turing coped with his grief by throwing himself into his work even more. In one of his letters to Mrs. Morcom, he wrote “I am sure I could not have found anywhere another companion so brilliant and yet so charming and unconceited. I regarded my interest in my work, and in such things as astronomy (to which he introduced me) as something to be shared with him and I think he felt a little the same about me ... I know I must put as much energy if not as much interest into my work as if he were alive, because that is what he would like me to do.” Many also speculate that it was Morcom’s death that led to Turing’s atheism.
In 1934, he graduated with first class honors in mathematics at King’s College in Cambridge and went on to be granted a fellowship due to a dissertation in which he proved the central limit theorem. In 1936, he published a paper in which he outlined the then-hypothetical device that would come to be known as a Turing machine, the predecessor to the modern computer. In this paper, he proved that this “universal computing machine” would be capable of performing any computation as long as it was able to be expressed as an algorithm.
Turing was a critical part of intelligence in World War II as a cryptanalyst, a job involving breaking German ciphers. He concentrated on cryptanalysis of the Engima machine used by Nazi Germany and invented many more efficient ways of breaking code on military transmissions. In doing so, he was able to advise higher-ups in the Allied forces of the movements, tactics, and general communication of German forces. During this time, he taught his advanced techniques to Tommy Flowers, the man who built the first programmable computer in the world.
Turing went on to design the first stored-program computer and develop software for it while working for the Mathematics department at Victoria University of Manchester. He also wrote the first algorithm for a computerized game of chess, though the technology to implement it did not yet exist. Instead, he manually thumbed through the pages of the algorithm while playing against a friend. The algorithm was in fact able to produce a recognizable game of chess. He then turned his efforts to mathematical biology, particularly attempting to understand morphogenesis, the biological process that helps an organism to develop its shape. During his work in this field, he would solve complex equations by hand as the powerful computers needed did not yet exist. His discoveries are still regarded as critical aspects of mathematical biology and have been used to explain gene expression.
He had been engaged for a brief time to a female colleague, but once he revealed his homosexuality to her, he could no longer go through with the marriage. In 1952, he began a relationship with Arnold Murray and house was burgled shortly after by an acquaintance of Murray’s. During the investigation, it was brought to light that Turing and Murray were sexually involved. Homosexuality was still criminalized at the time under British law, and both men were charged with and convicted of “gross indecency.” He was sentenced to probation with the condition that he would undergo hormonal changes to decrease libido. This was done with shots of synthetic estrogen, resulting in impotence and the formation of breast tissue.
As a result of his conviction, he lost his security clearance and was barred from continuing consulting on matters of cryptography for the government. He was also denied entry to the United States and, though never formally accused of espionage, he was given an order of silence to prevent him discussing his war work.
He took his own life on June 7, 1954 by cyanide poisoning from an apple that had been laced. Biographers agree that it was a recreation of Snow White, his favorite fairy tale. 59 years posthumously, he was pardoned by Queen Elizabeth II. 3 years later, in 2016, Parliament passed the Alan Turing law, a colloquialism for a law expanding retroactive exoneration to all men who had been charged with similar offenses.
Image sourced from:
https://www.biography.com/scientist/alan-turing
#lgbt#lgbt+#lgbtq#lgbtq+#lgbt history#lgbtq history#queer#gay#computing#mathematics#alan turing#turing machine#alan#turing#indecency laws#suicide#cryptanalysis#cryptography#enigma machine#spectrum diversity community center#SDCC#exoneration#lgbtqia#world war 2#lgbt+ history#lgbtq+ history#cyanide#alan turing law#science#computer science
3 notes
·
View notes
Photo

Perhaps one of the most mind-boggling unsolved cases to the FBI is Ricky McCormick’s encrypted notes. On June 30th, 1999, the 41-year-old’s body was discovered in a Missouri corn field after having been missing for a whole three days. Police found the location of his body to be strange, as it was 15 miles from where Ricky lived and he did not own a car, nor were there any public transportation served in that area. Since his body was already in its early stages of decomposition, police ascertained he had been dead for at least a few days, but there were no indications that he was murdered. In fact, his cause of death appeared to be a mystery, so police initially ruled out homicide. That was until twelve years later, when the FBI announced that Ricky McCormick was indeed murdered. But then they revealed a shocking clue that they had never disclosed to the public before: inside Ricky’s pockets contained two cryptic notes in his handwriting, which investigators believe were written three days prior to his death. The notes consisted of ‘’a jumble of letters and numbers occasionally set off with parentheses’’. This also struck police as odd, considering that all who knew Ricky claimed Ricky was an illiterate and only knew how to write his name. The FBI was convinced that the cipher messages would point toward whoever was responsible for the murder, but all attempts made to decipher their meaning led to failure. To this day, the two coded notes are listed as one of the FBI's Cryptanalysis and Racketeering Records Unit’s top unsolved cases.
#true crime#murder#homicide#mystery#unsolved cases#unsolved crime#ricky mccormick#missouri#cold case#cold cases
771 notes
·
View notes
Text
UNIT 1
UNDERSTANDING
1.1 Basic Nature of Cyber Threats:
Nothing seems sacred these days. Where there are a computer and someone with the capability and devious mind, you could potentially find a cyber threat. The trouble is, the nature of cyber threats have changed both in kind and intensity. The global States have raised their game and increased their intensity. What may have been spotty-faced teenagers operating from their mother’s basement, has transferred cyber threats as a major security challenge for businesses. The threat is a possible danger that might exploit a vulnerability to breach security and therefore cause possible harm. A threat can be either “intentional” (i.e. hacking: an individual cracker or a criminal organization) or state-sponsored. In this definition, the threat is defined as a possibility. However, in the cybersecurity community, the threat is more closely identified with the actor or adversary attempting to gain access to a system. Or a threat might be identified by the damage being done, what is being stolen or the Tactics, Techniques, and Procedures (TTP) being used.”In this definition, the threat is defined as a possibility. However, in the cybersecurity community, the threat is more closely identified with the actor or adversary attempting to gain access to a system. Or a threat might be identified by the damage being done, what is being stolen or the Tactics, Techniques, and Procedures (TTP) being used”.1
1.2 Overview of Common Threats:
Insider threats:” An insider threat is a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems.”
The insider threat, whereby an employee acts, knowingly or unknowingly, in a counter-productive way to cause significant damage to his/her organization, has become a key risk for organizations around the world. This is in part driven by the greater access individuals have to critical information and systems as organizations become more and more connected. In addition, ever more sophisticated methods of carrying out a cyber attack and the availability of more outlets for leaking information are increasing the threat.[2]
Cryptojacking attacks: A cryptographic attack is a method for circumventing the security of a cryptographic system by finding a weakness in a code, cipher, cryptographic protocol or key management scheme. This process is also called “cryptanalysis”. SQL injection Attack: A code injection technique, used to attack data-driven applications, in which criminal SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Phishing: Fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details by disguising as a trustworthy entity in electronic communication. Typically carried out by email spoofing or instant messaging, it often directs users to enter personal information at a fake website, the look and feel of which are identical to the legitimate site. Phishing is an example of social engineering techniques being used.
Ransomware: A type of malicious software from that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. More advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
Advanced malware attacks: These typically follow a common attack sequence: Planning: Involves selecting a target and researching the target’s infrastructure to determine how the malware will be introduced, the communication methods used while the attack is in progress, and how/where the data will be extracted.
1.3 Main features of threats to individuals:
From identity theft and fraud to social networking hacking attacks, everybody needs to be sure their safe. Knowledge is key as the saying goes. Your personal details, pictures, account details, and much more concerning yourself can potentially be exploited by the criminal.
1.4 Main features of threats to companies:
The reputation of your company, and of course the day to day functioning are under threat from cybercriminals. Various types of viruses and hacks can bring your business to its knees.
The number one weak link for businesses when it comes to cybersecurity — by a long, long way — is the people who work in the business.
From falling for phishing emails, and clicking on links or downloading documents that turn out to be malware, to being a victim of business email compromise (BEC) scams that end up losing the company a lot of money, employees are a company’s greatest liability when it comes to cybersecurity.
See also: https://thehackernews.com/2017/09/blueborne-bluetooth-hacking.html
Figure 1: Explanation from CIO|INSIGHT on Today’s security issues for businesses.[3]
1.5:
Analyze and Detail
2.1 Why do people cause and create security breaches:
For fun
Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends and hack something only for the challenge
To Steal
Another reason to hack a system is to steal information or money. A large portion of hacking attempts falls into this category. Banks and large companies are common targets for hacking jobs, but sometimes smaller companies or even a specific person’s computer are targeted, as well.
To disrupt
There are also some hackers, including hacking groups; that target a company to disrupt business, create chaos and just be a nuisance. These groups often are trying to make a statement with their hacking, demonstrate security inadequacies, or show general disapproval for the business itself. Examples of hacking groups that made headlines are Anonymous.
2.2 What is a threat and how do they work:
One resource demonstrates potential as “the possibility of a malicious attempt to damage or disrupt a computer network or system.”
The malicious programs inside e-mail attachments usually only strike if you open them. Effects of a virus can be anything from a simple prank that pops up messages to the complete destruction of programs and data.[4].
If a virus is sent through a network. This will spread like wildfire, even potentially globally. In some cases, it can change configurations of a database system (i.e; a worm).
2.3 Features of threats & How they operate:
IBM recently announced the shocking average cost of data breach. While down around 10 percent, the global average for a data breach is $3.62 million. For many companies, the cost of suffering a cyber attack is enough to take the business down entirely, so it has never been more vital for all organizations to invest in their cyber defenses. In order to equip suitable security, you first need to understand exactly where the danger comes from. Looking ahead to 2018, we examine the biggest cybersecurity threats both to individuals and companies across the world.[5]
WannaCry is so-called encryption-based ransomware also known as Wanna Decryptor or WCRY. It encrypts users files using AES and RSA encryption ciphers meaning the hackers can directly decrypt system files using a unique decryption key. From my research, especially remembering how much broadcast it received, it manipulated the laws that, basically, were prevalent at the time in many businesses, and specifically the NHS. People had not updated their systems often, and correctly. A playground for hackers.
2.4 How attack against companies works:
You work in the financial department of your company and you just got an email from an executive.
It instructs you to pay a sum of £78,000 before a specified time. It includes instructions for how to wire the money to your vendor’s bank.
You send the money, as requested, and it quickly moves to a number of small banks and then ultimately to an overseas account, where it is unlikely your company—or law enforcement—will be able to recover it. This is how phishing works.
2.5 Review & Hierarchy:
In the year 2011, a hacker was sentenced to nine years in prison because of the cyber-attack that he caused in a hospital. With this incident of physical damage to a hospital system, this individual used the skills that he had to install malware.
As a result of his action, the Hospital’s HVAC’s system was adversely altered causing the patient’s safety to be unduly jeopardized. By remotely controlling the temperature in the hospital, it posed an immediate threat since it placed drugs and other medical supplies at risk. In this situation, the hacker was controlling both the air and heating systems in the hospital from a remote location. Just goes to show how much of a danger some corrupted intentions can be used to cause massive, and potential health dangers.
Evaluate the impact of threats
3.5 Presentation with research document highlighting the affects:
3.1 According to on researcher[6] data breaches alone see upwards of 4.4 million data records being lost or stolen worldwide every single day. Take the 2015 data breach at UK telecoms company TalkTalk. Web pages containing databases no longer supported by their producer were accessed by hackers, who stole the personal data of 156,959 customers. The result was lots of negative publicity, reputational damage and a record fine of £400,000 from UK authorities.
One of the world’s largest DDoS attack ever took place in 2016, when US network provider Dyn was targeted. The attackers had harnessed the Internet of Things (internet enabled devices like cameras and fridges) to conduct the attack, and took down many major websites as a result. As the Internet of Things continues to expand, the risk is set to increase.
3.2 Hacking is a term used to describe actions taken by someone to gain unauthorized access to a computer. The availability of information online on the tools, techniques, and malware makes it easier for even non-technical people to undertake malicious activities.
What it is: The process by which cyber criminals gain access to your computer.
What it can do: Find weaknesses (or pre-existing bugs) in your security settings and exploit them in order to access your information.
3.3 Determining live threats to websites:
Streaming: Ok, i agree, i have used them myself, but in my defence i didnt consider them illegal. I can clearly remember watching a sports event and many many pop-ups appear, asking you to click this or that to access this or that in order (criminally) to get you to sign to something that you will be totally unaware lead to something other than what is being advertised. Scammers, hackers. Call them what you want. But when you do fall for their cunningness, your computer could be infected with cookies or worse. Either annoying or sinister.
3.4 Determining live threats to servers:
There is no such thing as perfect software, and there is always room for further refinement. Good system administration requires vigilance, constant tracking of bugs, and proper system maintenance to ensure a secure computing environment.
A common occurrence among system administrators is to install an operating system without knowing what is actually being installed. This can be troublesome, as most operating systems will not only install the applications, but also setup a base configuration and turn services on. This can cause unwanted services, such as telnet, DHCP, or DNS to be running on a server or workstation without the administrator realizing it, leading to unwanted traffic to the server or even a path into the system for crackers..
[1]https://www.secureworks.com/blog/cyber-threat-basics
[2]https://www.paconsulting.com/insights/managing-people-risk-and-the-insider-threat/
[3] https://www.cioinsight.com/it-management/inside-the-c-suite/slideshows/the-11-top-threats-that-organizations-face-today
[4] https://www.bullguard.com/bullguard-security-center/pc-security/computer-threats/how-does-a-virus-work
[5] https://staysafeonline.org/blog/biggest-cybersecurity-threats-2018/
[6] https://www.regus.co.uk/work-uk/cybersecurity-threats-where-do-they-come-from-and-whats-at-risk/?psrch=1&msclkid=e090cb097c8a1d9752fa9795a609d2a9&utm_source=bing&utm_medium=cpc&utm_campaign=GB%20%3E%20EN%20%3E%20OF%20%3E%20SM%20%3E%20DSA%20%3E%20NEW&utm_term=regus.co.uk&utm_content=Homepage
2 notes
·
View notes
Photo








Arrivals & Departures
23 June 1912 – 07 June 1954
Celebrate Alan Mathison Turing OBE FRS Day!
Alan Mathison Turing OBE FRS (/ˈtjʊərɪŋ/; 23 June 1912 – 07 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical computer science, providing a formalization of the concepts of algorithm and computation with the Turing machine, which can be considered a model of a general-purpose computer. Turing is widely considered to be the father of theoretical computer science and artificial intelligence. Despite these accomplishments, he was never fully recognised in his home country during his lifetime due to his homosexuality and because much of his work was covered by the Official Secrets Act.
During the Second World War, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre that produced Ultra intelligence. For a time he led Hut 8, the section that was responsible for German naval cryptanalysis. Here, he devised a number of techniques for speeding the breaking of German ciphers, including improvements to the pre-war Polish bombe method, an electromechanical machine that could find settings for the Enigma machine.
Turing played a crucial role in cracking intercepted coded messages that enabled the Allies to defeat the Nazis in many crucial engagements, including the Battle of the Atlantic, and in so doing helped win the war. Due to the problems of counterfactual history, it is hard to estimate the precise effect Ultra intelligence had on the war, but at the upper end it has been estimated that this work shortened the war in Europe by more than two years and saved over 14 million lives.
After the war Turing worked at the National Physical Laboratory, where he designed the Automatic Computing Engine. The Automatic Computing Engine was one of the first designs for a stored-program computer. In 1948, Turing joined Max Newman's Computing Machine Laboratory, at the Victoria University of Manchester, where he helped develop the Manchester computers and became interested in mathematical biology. He wrote a paper on the chemical basis of morphogenesis and predicted oscillating chemical reactions such as the Belousov–Zhabotinsky reaction, first observed in the 1960′s.
Turing was prosecuted in 1952 for homosexual acts; the Labouchere Amendment of 1885 had mandated that "gross indecency" was a criminal offence in the UK. He accepted chemical castration treatment, with DES, as an alternative to prison. Turing died in 1954, 16 days before his 42nd birthday, from cyanide poisoning. An inquest determined his death as a suicide, but it has been noted that the known evidence is also consistent with accidental poisoning.
In 2009, following an Internet campaign, British Prime Minister Gordon Brown made an official public apology on behalf of the British government for "the appalling way he was treated". Queen Elizabeth II granted Turing a posthumous pardon in 2013. The "Alan Turing law" is now an informal term for a 2017 law in the United Kingdom that retroactively pardoned men cautioned or convicted under historical legislation that outlawed homosexual acts.
9 notes
·
View notes