#Docker
Text
for all my computer science critters out there, "unfinished vidulch" sounds like the default name on a docker container
10 notes
·
View notes
Text
I have been using Btrfs for several months, and it has been stable enough for me. It is a file system that can be used as a storage driver for Linux containers like LXD, Incus, or Docker. If you want to install Btrfs support on Debian Linux and format & mount a disk drive, see my tutorial
9 notes
·
View notes
Text







Il y a une dizaine de jours, je suis parti retrouver Christine à Narbonne.
Le Musée Narbo Via, dédié à la Narbo romaine (cette ville fut la première ville romaine hors d'Italie et un des 3 plus grands ports de l'Empire romain)
bonnet de marin, en feutre de laine (un ancêtre de Cousteau ?) - non daté. Sa rareté et son côté proche de nous est assez émouvant...
chargement de navire par des saccarii = dockers - Haut-Empire
casque de marin en bronze et plomb - II-Ier s. av. J-C.
navire à voile (avec proue en tête de cygne, ancre sur le côté, rames...) et déesse protectrice voilée - Haut-Empire
applique de navire en bronze - IV-Vème s. av. J-C.
stèle, navire à la voile renforcée de lanières, des laizes - Haut-Empire
poulies - Haut-Empire
La suite dans peu de jours !
#narbonne#aude#languedoc#narbo via#narbo#archéologie#rome antique#romain#gallo-romain#marin#bonnet#casque#marine#saccarius#docker#navire#galère#poulie#accastillage#stèle#laize
2 notes
·
View notes
Text
#DevOps lifecycle#components of devops lifecycle#different phases in devops lifecycle#best devops consulting in toronto#best devops consulting in canada#DevOps#kubernetes#docker#agile
2 notes
·
View notes
Text
2 notes
·
View notes
Text
youtube
The Best DevOps Development Team in India | Boost Your Business with Connect Infosoft
Please Like, Share, Subscribe, and Comment to us.
Our experts are pros at making DevOps work seamlessly for businesses big and small. From making things run smoother to saving time with automation, we've got the skills you need. Ready to level up your business?
#connectinfosofttechnologies#connectinfosoft#DevOps#DevOpsDevelopment#DevOpsService#DevOpsTeam#DevOpsSolutions#DevOpsCompany#DevOpsDeveloper#CloudComputing#CloudService#AgileDevOps#ContinuousIntegration#ContinuousDelivery#InfrastructureAsCode#Automation#Containerization#Microservices#CICD#DevSecOps#CloudNative#Kubernetes#Docker#AWS#Azure#GoogleCloud#Serverless#ITOps#TechOps#SoftwareDevelopment
2 notes
·
View notes
Text
I have written instructions on my wiki detailing how to install and utilize Docker for training and inferencing LLMs using Hugging Face transformers: https://wiki.shlyapin.com/docker_train_and_inference_llms
2 notes
·
View notes
Text
How to Install and Use Docker on Ubuntu 22.04
Docker is an open-source containerization platform that allows developers to easily package and deploy applications in a portable and lightweight manner. In this tutorial, we will provide a step-by-step guide on how to install and use Docker on Ubuntu 22.04.
Prerequisites
Before you proceed, make sure you have Ubuntu 22.04 installed on your system and have a user account with sudo…

View On WordPress
#automation#cloud computing#command line#containerization#devops#Docker#linux#software development#Ubuntu#Ubuntu 22.04#virtualization
11 notes
·
View notes
Text

To solve a real-world problem is the fact that interested me the most and the opportunity to use AI/ML in conjunction with Docker technologies . I can't wait to see how these technologies can be used to create innovative and impactful solutions.
#argentina#funny#frases tumblr#tumblr#colors#colours#paint#English#ai#creation#learn#fact#docker#tech#watercolour art#watercolourpainting#watercolor
4 notes
·
View notes
Text
Free youtube 8 hour long tutorial: Learn complete Docker and k8s
Me after 4 days:

23 notes
·
View notes
Text

#docker#pensieri ossessivi#pensieri#intrusive thoughts#trastorno obsesivo compulsivo#ocd#autism#neurodivergencies#autismo#adhd#neurodiversity#the simpsons#blog italiani#aforismi italiani#blogger#memes#ocd memes#ocd support and awareness
26 notes
·
View notes
Text
Catch
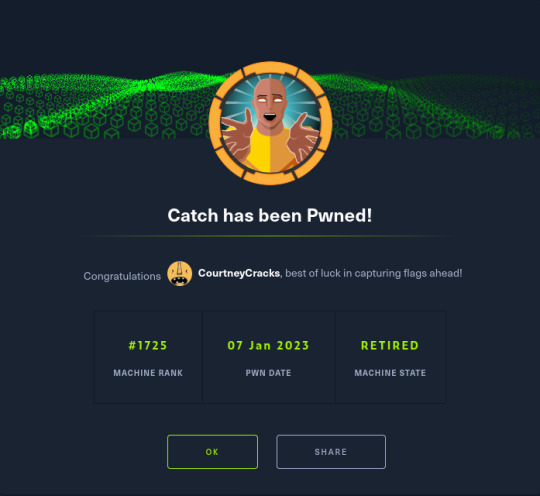
So over the last few weeks I've been working on Catch. With work and the festive period I haven't had a lot of time; I finally got the opportunity to finish it last night. :)
It has a medium rating but I wouldn't say it's due to the initial foothold and privilege escalation being difficult- it's more due to there being a couple of rabbit holes (all of which I fell into for a period!)

Enumeration
As always, a port scan kicks off the process. Unfortunately I can't show the output of the port scan as during the time I switched laptops and I'm too lazy to power my old one on. xD However, the results were roughly as follows:
Port 80: HTTP (Catch Global Systems main page)
Port 3000: Gitea(?)
Port 5000: Lets Chat(?)
Port 8000: Cachet status page system
Port 80 was the first location I checked. You're greeted with what appears to be Catch's main application:
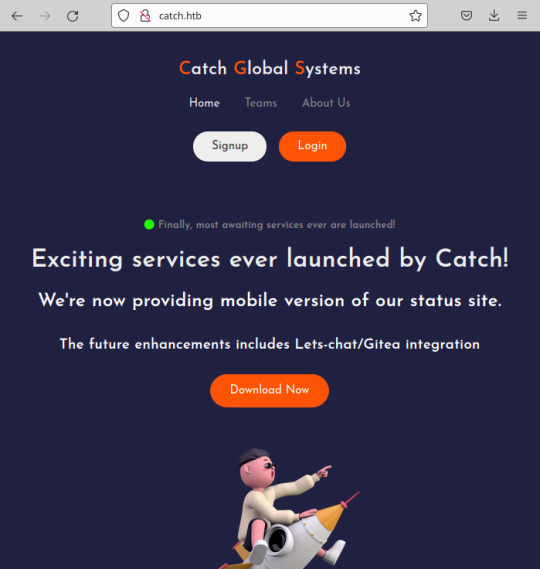
The signup/login functionality isn't present; I did notice the ability to download a file. The file that downloads is an apk.
For those that are unfamiliar with mobile applications, apk is one of the file formats for an Android mobile application which uses XML and Java. Having a little experience with mobile applications, my first thought was to decompile the apk and check for any hidden hardcoded secrets, usually stored in strings.xml.
To decompile the apk, I used apktool.
$ apktool d catchv1.0.apk
This decompiles the apk to near it's original form and places the resulting files in ./catchv1.0/. From here, I viewed ./res/values/strings.xml and found 3 potentially usable tokens for other applications:
$ grep token catchv1.0/res/values/strings.xml
<string name="gitea_token">b87bfb6345ae72ed5ecdcee05bcb34c83806fbd0</string>
<string name="lets_chat_token">NjFiODZhZWFkOTg0ZTI0NTEwMzZlYjE2OmQ1ODg0NjhmZjhiYWU0NDYzNzlhNTdmYTJiNGU2M2EyMzY4MjI0MzM2YjU5NDljNQ==</string>
<string name="slack_token">xoxp-23984754863-2348975623103</string>
Foothold
With these in hand, I started with Lets Chat at random. Lets Chat is an open-source chat application utilizing a REST api. With it being open-source, it didn't take long at all to find how to use the discovered token:
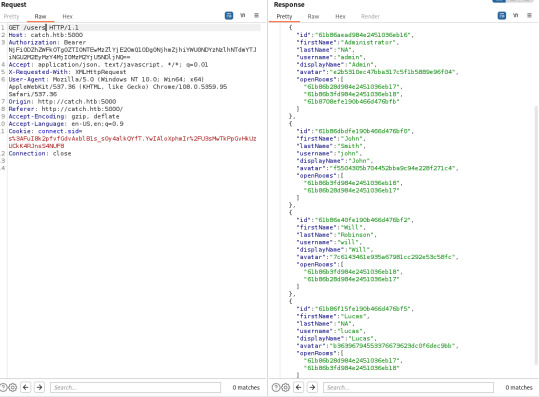

As you can see, a password for John is viewable in one of the chat rooms. This grants you access to another one of their applications called Cachet- open-source yet again.
Cachet is the last stop before system access; admittedly this is where I fell rabbit hole 1 as I did spend some time trying to use the gitea_token, more out of curiosity than anything. After spending some time on this, however, I gave up and focused on Cachet.
As it turns out, the version of Cachet in use had two pubicly known vulnerabilities related to interaction with the application's dotenv file. One allowed you to leak values set in dotenv while the other allowed you to add new values to dotenv which could be used to achieve remote command execution. This is done by hosting a redis server, altering the dotenv file to make the application use your hosted redis server as a session driver and finally changing the value of the session key after the initial connection to a payload generated by phpggc. Better detail off this is given here.
I did spend some time playing around with the RCE vulnerability here, more out of interest as I haven't had any experience with Redis prior to this and it took me a while to get RCE working as the video doesn't explicitly show the process step-by-step.
Originally, I was getting the token from the source code in the application, adding this as a key with the phpggc payload as the value and then altering the dotenv file to connect to my Redis Server. As the RCE occurs when the client connects the second time and reads the value from the original session token, this didn't work.
I did eventually get this working, uploaded a PHP web shell and upgraded this to a reverse shell; this ultimately proved to be a waste of time as you end up in a Docker instance with no ability to break out of it!

With a heavy heart, I turned to the second vulnerability and leaked the database password from the dotenv file. This grants us access to the server through SSH as WIll.
Privilege Escalation
Privilege escalation was actually quite easy! Some simple enumeration reveals the presence of world-writeable directory /opt/mdm/apk_bin. In /opt/mdm, there is a Bash file verify.sh.
verify.sh is used to verify the legitimacy of apks uploaded to apk_bin and is executed as part of a cronjob which is executed as root. While references to verify.sh cannot be directly found, there is reference to 'check.sh' in the root directory in running processes (netstat -ano.)
The interesting lines of the script are here:
app_check() {
APP_NAME=$(grep -oPm1 "(?<=string name=\"app_name\">)[^<]+" "$1/res/values/strings.xml")
echo $APP_NAME
...
The function app_check is taking the app_name from strings.xml and echoing it back with no form of mitigation against command injection. For example, wrapping the variable name with ${} would have prevented this vulnerability being exploitable as this would have specified that only variable expansion was expected- the app name would have been echoed back as a string and not interpreted as a literal Bash command.
I tested this first by simply making the app name 'Catch; touch /opt/mdm/heuheu' and uploading it using python -m SimpleHTTPServer on my end and curl on Catch's end which achieved the expected outcome.
I did this with APK Editor Studio after encountering some errors trying do manually decompile and then recompile with apktool. Note that you also need to create a key for signing the APK as verify.sh uses jarsigner to verify this.
will@catch:/opt/mdm/apk_bin$ ls -al ..
total 16
drwxr-x--x+ 3 root root 4096 Jan 6 21:55 .
drwxr-xr-x 4 root root 4096 Dec 16 2021 ..
drwxrwx--x+ 2 root root 4096 Jan 6 22:03 apk_bin
-rw-r--r-- 1 root root 0 Jan 6 21:55 heuheu
-rwxr-x--x+ 1 root root 1894 Mar 3 2022 verify.sh
From here, I went old school and just made /etc/passwd fully accessible by everyone before changing root's password to 'mwaha'
Generating the password:
$ openssl passwd mwaha
KW56XEY7wxZuU
Where the password is added in /etc/passwd:
root:KW56XEY7wxZuU:...
There you go. ^-^
#hackthebox#hacking#android apk#apktool#command injection#redis server#dotenv#cachet#lets chat#gitea#cronjob#web shell#reverse shell#ssh#docker#open source
19 notes
·
View notes
Video
youtube
(via Develop & Deploy Nodejs Application in Docker | Nodejs App in Docker Container Explained) Full Video Link https://youtu.be/Bwly_YJvHtQ Hello friends, new #video on #deploying #running #nodejs #application in #docker #container #tutorial for #api #developer #programmers with #examples is published on #codeonedigest #youtube channel. @java #java #aws #awscloud @awscloud @AWSCloudIndia #salesforce #Cloud #CloudComputing @YouTube #youtube #azure #msazure #docker #dockertutorial #nodejs #learndocker #whatisdocker #nodejsandexpressjstutorial #nodejstutorial #nodejsandexpressjsproject #nodejsprojects #nodejstutorialforbeginners #nodejsappdockerfile #dockerizenodejsexpressapp #nodejsappdocker #nodejsapplicationdockerfile #dockertutorialforbeginners #dockerimage #dockerimagecreationtutorial #dockerimagevscontainer #dockerimagenodejs #dockerimagenodeexpress #dockerimagenode_modules
#video#deploying#running#nodejs#application#docker#container#tutorial#api#developer#programmers#examples#codeonedigest
3 notes
·
View notes
Text
What is Docker and its use case?
Docker is a powerful tool that has revolutionized the way applications are deployed and managed. It is an open-source platform that allows developers to build, package, and deploy applications in a consistent and efficient manner. In this blog post, we will explore Docker and its uses
Docker uses a lightweight virtualization approach to package applications and their dependencies into a…

View On WordPress
5 notes
·
View notes
