#engineering assessment
Text

Renovation Project - Melia/Hyatt Regency Grand Reserve Puerto Rico
Following damage to the Melia resort WGPITTS assisted Monarch Capital in the acquisition and construction management of the $32 million renovation of the Melia Resort and conversion to the 700,000 sf 400 room Hyatt Regency Grand Reserve, Rio Grande Puerto Rico. The acquisition entailed a full engineering assessment of the facility including all structural damage, power distribution, water testing, mechanical, electrical, plumbing systems, kitchen equipment, mold studies, thermal and moisture Testing roofing assessments and the associated cost to complete and repair all components.
#construction management#general contractors Florida#engineering assessment#Hyatt Regency Grand Reserve#renovation Melia Resort#real estate developers Florida
0 notes
Text
The awesome thing about college is that being there is miserable, and not being there is worse.
Nifty!
#I might be going back to college in September and man. I might just quit lmao#I did engineering courses before and that was genuinely the worst over ever felt in my life#I would genuinely have panic attacks and leave every day#But I couldn't just leave the course because I'd feel like a failure#Which didn't matter anyway cause I failed the course lmao#My new course is business shit and I feel like I'm gonna get stuck in a course I hate again#Technically I was good at business. But that was only because it was continues assessment and my teacher wasn't that good.#Fuck dude#Vent#Yeah this is a vent post if you hadn't figured that out#I just had an interview there and apparently my course has an online class once a week#I might quit for that alone cause I can't fucking stand those#But also I don't wanna work at dunnes for 20 years and then die#But also also I can't work part time and go to college so that means no money#Yeah fuck this lmao#Delete later#Fuck it I've got a drawing tablet now. I'm becoming a full time inflation artist or something. I hear that's good money#Thinking about it more I already struggle with self worth or whatever#And I fucking hate annoying businesses bros so becoming one might make me actively hate myself
2 notes
·
View notes
Text
Software Technical Interview Review List
Data Structures
Arrays (and Java List vs ArrayList)
String
Stack
Queue
LinkedList
Algorithms
Sorting (Bubblesort, Mergesort, Quicksort)
Recursion & Backtracking
Linear and Binary Search
String/Array algos
Tree traversal
Dynamic Programming
Graph algos (DFS, BFS, Dijksta's and Kruskals)
OOP fundamentals
Polymorphism
Inheritance
Encapsulation
Data abstraction
SOLID and GRASP
Explanations & example questions:
Strings and Arrays [ 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 ]
Stacks and Queues [ 1 | 2 ]
LinkedList [ 1 | 2 ]
Sorting & searching [ 1 | 2 | 3 | 4 | 5 | 6 | 7 ]
Recursion and Backtracking [ 1 | 2 | 3 | 4 ]
Dynamic Programming [ 1 | 2 | 3 | 4]
Graphs [ 1 | 2 | 3 ]
Tree [ 1 | 2 ]
General DS&A info and questions [ 1 | 2 | 3 | 4 | 5 ]
OOP review & questions [ 1 | 2 | 3 ]
#ive been procrastinating this coding assessment for my interview so bad 😭😭#im just scared of messing up cause i need this internship#But its due soon so im really buckling down now >:)#object oriented programming#algorithms#data structures#software engineering#ref#resource#mypost
11 notes
·
View notes
Text
the ship disaster dreams are fine most of the time but you do NOTTTTT !!!! bring my best friend into this. don’t do that!!!!
#it was actually kind of horrifying last night 😟 DONT BRING MY BFF INTO ITTTTT PLEASEEEE PLEASEEEEE#so yesterday in EMT we did trauma assessments where we ran up to a victim and had to determine how they were badly injuried#and my best friend has the SAMEEE exact injuries as my victim last night :(#and most of the officers were incapacitated so we had to made the decisions and they were all wrong#it was dark and claustrophobic and we were stuck in the engine room and i was trying to get my friend out (broken leg)#then we got seperated and i was trying to climb to the bridge since we didn’t have anyone on helm and my officer w as alone up there#and i just get above decks and see us on course directlyto hit a tanker#all i remember is later from shore me and my friend watching the ship go down and knowing how many people are in there
3 notes
·
View notes
Text
anyway. nishiki and majima are both borderline and i could do a whole case study on either of them about it. send tweet
#im pretty flexible about most hcs regarding mental disorders and such but this take is one im like pretty fucking steadfast on#and I could write. an absurd amount about it. cause psychoanalyzing the shit out of characters is literally like. what I do for a living#and I have a weird special interest in abnormal psych and the dsm-5 in my closet and a psychologist for a mother and etc#but yeah so#inquire further at your own risk because I will talk. I will talk a lot#the only issue with majima is that I can’t evaluate his childhood and family life and just. his fundamental years of development in general#which is a pretty big deal when it comes to assessing for any personality disorder#nishiki oh yeah I absolutely can. but yeah we know basically nothing about majimas fundamental years. all I can really do is reverse#engineer so to speak based on how he is as an adult and what causes a person to do the things he does / be the way he is / etc#but of course that’d all be very very loose and hypothetical. FASCINATING to think about to me but obviously would have to be taken with a#huge grain of salt and be considered very very speculative#but I can say for sure that he didn’t have a stable and perfect home life/family life growing up I think that’s pretty safe to assume#anything more detailed than that is way more speculative but. yeah. I don’t think he was just. Normal. up until he was 20#his identity issues run way too deep for me to accept that concept#anyway I need to shut up#majima#nishiki#rambling
11 notes
·
View notes
Text
Exploring the Diverse Landscape of Surveys: Unveiling Different Types
Introduction
Civil engineering, as a discipline, relies heavily on accurate and comprehensive data to design, plan, and construct various infrastructure projects. Surveys play a crucial role in gathering this essential information, providing engineers with the data needed to make informed decisions. There are several types of surveys in civil engineering, each serving a unique purpose. In this…

View On WordPress
#accurate measurements#as-built survey#boundary survey#civil engineering data#Civil engineering surveys#construction progress monitoring#construction survey#design accuracy#environmental monitoring#geodetic survey#global mapping#hydrographic survey#infrastructure development#infrastructure projects#land surveyor#legal boundaries#monitoring survey#project planning#property lines#structural integrity assessment#surveying in civil engineering#surveying innovations#surveying technology#topographic surveying#water body survey
2 notes
·
View notes
Text
ugh the third-party sharing setting is so stupid. idk if it's actually related or if this happened somewhere else along the line, but when i just went to change it, my other opted-in privacy settings had been toggled off. thanks tumblr! awesome! i love that!!
#taylor.txt#like i dont have the discourage search engines from showing search results from my blog setting and shit turned on for no reason#wouldve been nice to know i was gonna have to come back and change it again!!! fucking. webbed site /EXTREMELY negative#anyway etc etc hi im alive. asks will be answered over the weekend probably. have an assessment tomorrow but friday off yay!
1 note
·
View note
Text
okay i finally found a longer screw that fits and upside down test makes me think this gear combo seems more promising. i have however not yet tested it to see if it can actually drive bc the room i was in was abt to have a class come wrdhdjgn but fingers crossed so hard i will actually have a breakdown if this does not work 😭😭
#but if nothing else i guess this is a start </3#i’ll probably have to mill out a new chassis too bc mine does not have any through holes#and also i just don’t like the shape of it so i’ll probably redesign it altogether#but if i can’t do that in time for the next in class assessment i Think one of the labs has hand tools for drilling etc#personal#the engineering chronicles
3 notes
·
View notes
Text

GeoLogic LLC
GeoLogic is an independent geological consulting and engineering firm, proud to serve a wide spectrum of clientele, from foresters to attorneys, appraisers, economic geologists, and large equity firms.
Address: 4372 Shallowford Industrial Parkway, Marietta, GA 30066, USA
Phone: 770-824-4212
Website: https://geologicllc.net/
#Geotechnical Engineering#Geological Engineering#Environmental Consulting#Soil Analysis#Phase I Environmental Site Assessments
4 notes
·
View notes
Text
Professional CDR Report Writers Available in Australia

If you want your report to count, get it accepted by the Engineers Australia
If you want your report to count, get it accepted by the EA.
Professional CDR Report Writers Available in Australia
CDRforAustralia is staffed by professional writers, engineers, and IT specialists that work together to guarantee that your CDR report is error-free, original, and specific to your needs in order to earn you a passing grade from Engineers Australia. Read more
#engineering#skill assessment#australia migration#australia#migration#Competency Demonstration Report#writing
2 notes
·
View notes
Text

JIRA Administrator Projects
Excel as a JIRA Administrator with our specialized projects training. Master user management, workflow customization, and advanced configurations to optimize JIRA for seamless project management. Elevate your skills today!
Visit Our Website:
Email ID - [email protected]
Address - PHILADELPHIA, Pennsylvania PA
#jira assessment#hire scrum master#agile maturity assessment#best jira training#site reliability engineering training
0 notes
Text
TRAFFIC ANALYST NEAR ME
A Traffic Impact Study consultant from N Engineering evaluates the effects of proposed developments on local traffic. Our experts provide comprehensive analyses, identify potential issues, and recommend solutions to ensure safe, efficient traffic flow. Visit nengineering.com for professional guidance on traffic impact assessments and to ensure your project complies with all regulatory requirements.

#comprehensive traffic design service#effective traffic management solution#road traffic impact analysis#traffic engineer#traffic engineering expert#traffic impact assessment#Traffic Impact Study#Traffic Impact Study consultant
0 notes
Text
New tool empowers users to fight online misinformation
New Post has been published on https://thedigitalinsider.com/new-tool-empowers-users-to-fight-online-misinformation/
New tool empowers users to fight online misinformation


Most people agree that the spread of online misinformation is a serious problem. But there is much less consensus on what to do about it.
Many proposed solutions focus on how social media platforms can or should moderate content their users post, to prevent misinformation from spreading.
“But this approach puts a critical social decision in the hands of for-profit companies. It limits the ability of users to decide who they trust. And having platforms in charge does nothing to combat misinformation users come across from other online sources,” says Farnaz Jahanbakhsh SM ’21, PhD ’23, who is currently a postdoc at Stanford University.
She and MIT Professor David Karger have proposed an alternate strategy. They built a web browser extension that empowers individuals to flag misinformation and identify others they trust to assess online content.
Their decentralized approach, called the Trustnet browser extension, puts the power to decide what constitutes misinformation into the hands of individual users rather than a central authority. Importantly, the universal browser extension works for any content on any website, including posts on social media sites, articles on news aggregators, and videos on streaming platforms.
Through a two-week study, the researchers found that untrained individuals could use the tool to effectively assess misinformation. Participants said having the ability to assess content, and see assessments from others they trust, helped them think critically about it.
“In today’s world, it’s trivial for bad actors to create unlimited amounts of misinformation that looks accurate, well-sourced, and carefully argued. The only way to protect ourselves from this flood will be to rely on information that has been verified by trustworthy sources. Trustnet presents a vision of how that future could look,” says Karger.
Jahanbakhsh, who conducted this research while she was an electrical engineering and computer science (EECS) graduate student at MIT, and Karger, a professor of EECS and a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL), detail their findings in a paper presented this week at the ACM Conference on Human Factors in Computing Systems.
Fighting misinformation
This new paper builds off their prior work about fighting online misinformation. The researchers built a social media platform called Trustnet, which enabled users to assess content accuracy and specify trusted users whose assessments they want to see.
But in the real world, few people would likely migrate to a new social media platform, especially when they already have friends and followers on other platforms. On the other hand, calling on social media companies to give users content-assessment abilities would be an uphill battle that may require legislation. Even if regulations existed, they would do little to stop misinformation elsewhere on the web.
Instead, the researchers sought a platform-agnostic solution, which led them to build the Trustnet browser extension.
Extension users click a button to assess content, which opens a side panel where they label it as accurate, inaccurate, or question its accuracy. They can provide details or explain their rationale in an accompanying text box.
Users can also identify others they trust to provide assessments. Then, when the user visits a website that contains assessments from these trusted sources, the side panel automatically pops up to show them.
In addition, users can choose to follow others beyond their trusted assessors. They can opt to see content assessments from those they follow on a case-by-case basis. They can also use the side panel to respond to questions about content accuracy.
“But most content we come across on the web is embedded in a social media feed or shown as a link on an aggregator page, like the front page of a news website. Plus, something we know from prior work is that users typically don’t even click on links when they share them,” Jahanbakhsh says.
To get around those issues, the researchers designed the Trustnet Extension to check all links on the page a user is reading. If trusted sources have assessed content on any linked pages, the extension places indictors next to those links and will fade the text of links to content deemed inaccurate.
One of the biggest technical challenges the researchers faced was enabling the link-checking functionality since links typically go through multiple redirections. They were also challenged to make design decisions that would suit a variety of users.
Differing assessments
To see how individuals would utilize the Trustnet Extension, they conducted a two-week study where 32 individuals were tasked with assessing two pieces of content per day.
The researchers were surprised to see that the content these untrained users chose to assess, such as home improvement tips or celebrity gossip, was often different from content assessed by professionals, like news articles. Users also said they would value assessments from people who were not professional fact-checkers, such as having doctors assess medical content or immigrants assess content related to foreign affairs.
“I think this shows that what users need and the kinds of content they consider important to assess doesn’t exactly align with what is being delivered to them. A decentralized approach is more scalable, so more content could be assessed,” Jahanbakhsh says.
However, the researchers caution that letting users choose whom to trust could cause them to become trapped in their own bubble and only see content that agrees with their views.
This issue could be mitigated by identifying trust relationships in a more structured way, perhaps by suggesting a user follow certain trusted assessors, like the FDA.
In the future, Jahanbakhsh wants to further study structured trust relationships and the broader implications of decentralizing the fight against misinformation. She also wants to extend this framework beyond misinformation. For instance, one could use the tool to filter out content that is not sympathetic to a certain protected group.
“Less attention has been paid to decentralized approaches because some people think individuals can’t assess content,” she says. “Our studies have shown that is not true. But users shouldn’t just be left helpless to figure things out on their own. We can make fact-checking available to them, but in a way that lets them choose the content they want to see.”
#approach#Articles#artificial#Artificial Intelligence#assessment#attention#Behavior#box#browser#browser extension#Companies#computer#Computer Science#Computer Science and Artificial Intelligence Laboratory (CSAIL)#Computer science and technology#computing#computing systems#conference#content#Design#details#Electrical Engineering&Computer Science (eecs)#engineering#extension#Fact-checking#FDA#Fight#filter#focus#framework
0 notes
Text
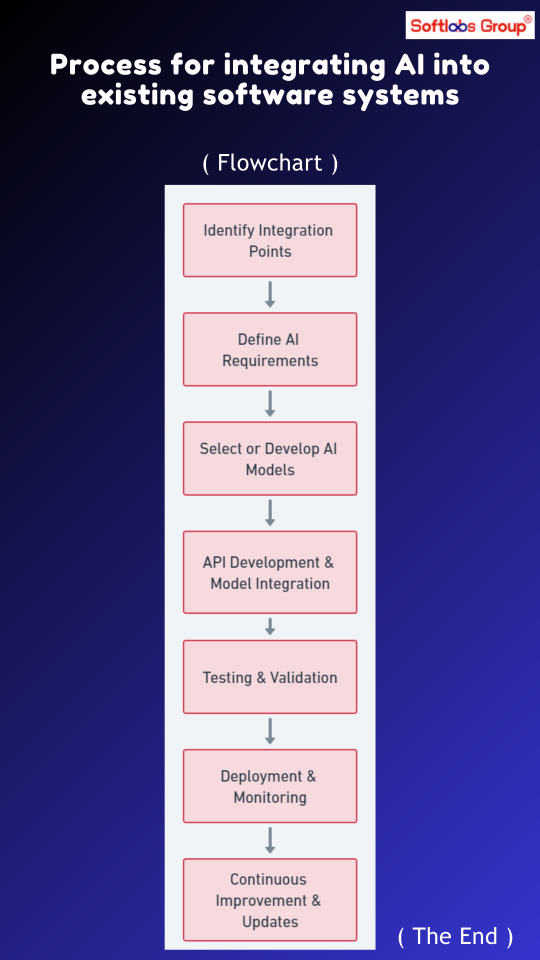
Discover the process for integrating AI into existing software systems with our simplified workflow. Follow stages including system analysis, AI model selection, integration planning, development, testing, and deployment. Simplify the integration of AI capabilities into your software for enhanced functionality. Perfect for software developers, architects, and IT professionals. Stay updated with Softlabs Group for more insights into AI integration strategies!
#System Integration#API Integration#Compatibility Assessment#Feature Engineering#Testing And Validation
0 notes
Text

#𝐄𝐎𝐒𝐇 - 𝗨𝗞 𝗛𝗮𝘇𝗮𝗿𝗱 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁 𝐂𝐨𝐮𝐫𝐬𝐞𝐬#Award in Hazard Identification & Risk Assessment (HIRA)#Award in Hazardous Waste Operations and Emergency Response (HAZWOPER) Training#Award in HAZOP Leader#Award in HAZOP Leadership and Management#Award in HAZOPs for Engineers & Technicians#Award in HAZOP-Train the Trainer#Award in HAZWOPER -Train the Trainer#Award in Work Permits Receiver#Contact Us:#Mob:#+919787872866#Email:#[email protected]#Web:#www.cosmostrg.com#WhatsApp Channel :#https://whatsapp.com/channel/0029VaHMYayGufJ45OH4Xo1n#WhatsApp Group :#https://chat.whatsapp.com/IunhDueyuLsEPc9SkB7dlK#eoshcourses#eoshcourse#eosh#eoshuk#Hazard#hazardmanagement#hazardidentification#riskassessment#hazardouswaste#hazardtraining
0 notes
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction
The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
1 note
·
View note