#phishing
Text
How I got scammed

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security

I wuz robbed.
More specifically, I was tricked by a phone-phisher pretending to be from my bank, and he convinced me to hand over my credit-card number, then did $8,000+ worth of fraud with it before I figured out what happened. And then he tried to do it again, a week later!
Here's what happened. Over the Christmas holiday, I traveled to New Orleans. The day we landed, I hit a Chase ATM in the French Quarter for some cash, but the machine declined the transaction. Later in the day, we passed a little credit-union's ATM and I used that one instead (I bank with a one-branch credit union and generally there's no fee to use another CU's ATM).
A couple days later, I got a call from my credit union. It was a weekend, during the holiday, and the guy who called was obviously working for my little CU's after-hours fraud contractor. I'd dealt with these folks before – they service a ton of little credit unions, and generally the call quality isn't great and the staff will often make mistakes like mispronouncing my credit union's name.
That's what happened here – the guy was on a terrible VOIP line and I had to ask him to readjust his mic before I could even understand him. He mispronounced my bank's name and then asked if I'd attempted to spend $1,000 at an Apple Store in NYC that day. No, I said, and groaned inwardly. What a pain in the ass. Obviously, I'd had my ATM card skimmed – either at the Chase ATM (maybe that was why the transaction failed), or at the other credit union's ATM (it had been a very cheap looking system).
I told the guy to block my card and we started going through the tedious business of running through recent transactions, verifying my identity, and so on. It dragged on and on. These were my last hours in New Orleans, and I'd left my family at home and gone out to see some of the pre-Mardi Gras krewe celebrations and get a muffalata, and I could tell that I was going to run out of time before I finished talking to this guy.
"Look," I said, "you've got all my details, you've frozen the card. I gotta go home and meet my family and head to the airport. I'll call you back on the after-hours number once I'm through security, all right?"
He was frustrated, but that was his problem. I hung up, got my sandwich, went to the airport, and we checked in. It was total chaos: an Alaska Air 737 Max had just lost its door-plug in mid-air and every Max in every airline's fleet had been grounded, so the check in was crammed with people trying to rebook. We got through to the gate and I sat down to call the CU's after-hours line. The person on the other end told me that she could only handle lost and stolen cards, not fraud, and given that I'd already frozen the card, I should just drop by the branch on Monday to get a new card.
We flew home, and later the next day, I logged into my account and made a list of all the fraudulent transactions and printed them out, and on Monday morning, I drove to the bank to deal with all the paperwork. The folks at the CU were even more pissed than I was. The fraud that run up to more than $8,000, and if Visa refused to take it out of the merchants where the card had been used, my little credit union would have to eat the loss.
I agreed and commiserated. I also pointed out that their outsource, after-hours fraud center bore some blame here: I'd canceled the card on Saturday but most of the fraud had taken place on Sunday. Something had gone wrong.
One cool thing about banking at a tiny credit-union is that you end up talking to people who have actual authority, responsibility and agency. It turned out the the woman who was processing my fraud paperwork was a VP, and she decided to look into it. A few minutes later she came back and told me that the fraud center had no record of having called me on Saturday.
"That was the fraudster," she said.
Oh, shit. I frantically rewound my conversation, trying to figure out if this could possibly be true. I hadn't given him anything apart from some very anodyne info, like what city I live in (which is in my Wikipedia entry), my date of birth (ditto), and the last four digits of my card.
Wait a sec.
He hadn't asked for the last four digits. He'd asked for the last seven digits. At the time, I'd found that very frustrating, but now – "The first nine digits are the same for every card you issue, right?" I asked the VP.
I'd given him my entire card number.
Goddammit.
The thing is, I know a lot about fraud. I'm writing an entire series of novels about this kind of scam:
https://us.macmillan.com/books/9781250865878/thebezzle
And most summers, I go to Defcon, and I always go to the "social engineering" competitions where an audience listens as a hacker in a soundproof booth cold-calls merchants (with the owner's permission) and tries to con whoever answers the phone into giving up important information.
But I'd been conned.
Now look, I knew I could be conned. I'd been conned before, 13 years ago, by a Twitter worm that successfully phished out of my password via DM:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That scam had required a miracle of timing. It started the day before, when I'd reset my phone to factory defaults and reinstalled all my apps. That same day, I'd published two big online features that a lot of people were talking about. The next morning, we were late getting out of the house, so by the time my wife and I dropped the kid at daycare and went to the coffee shop, it had a long line. Rather than wait in line with me, my wife sat down to read a newspaper, and so I pulled out my phone and found a Twitter DM from a friend asking "is this you?" with a URL.
Assuming this was something to do with those articles I'd published the day before, I clicked the link and got prompted for my Twitter login again. This had been happening all day because I'd done that mobile reinstall the day before and all my stored passwords had been wiped. I entered it but the page timed out. By that time, the coffees were ready. We sat and chatted for a bit, then went our own ways.
I was on my way to the office when I checked my phone again. I had a whole string of DMs from other friends. Each one read "is this you?" and had a URL.
Oh, shit, I'd been phished.
If I hadn't reinstalled my mobile OS the day before. If I hadn't published a pair of big articles the day before. If we hadn't been late getting out the door. If we had been a little more late getting out the door (so that I'd have seen the multiple DMs, which would have tipped me off).
There's a name for this in security circles: "Swiss-cheese security." Imagine multiple slices of Swiss cheese all stacked up, the holes in one slice blocked by the slice below it. All the slices move around and every now and again, a hole opens up that goes all the way through the stack. Zap!
The fraudster who tricked me out of my credit card number had Swiss cheese security on his side. Yes, he spoofed my bank's caller ID, but that wouldn't have been enough to fool me if I hadn't been on vacation, having just used a pair of dodgy ATMs, in a hurry and distracted. If the 737 Max disaster hadn't happened that day and I'd had more time at the gate, I'd have called my bank back. If my bank didn't use a slightly crappy outsource/out-of-hours fraud center that I'd already had sub-par experiences with. If, if, if.
The next Friday night, at 5:30PM, the fraudster called me back, pretending to be the bank's after-hours center. He told me my card had been compromised again. But: I hadn't removed my card from my wallet since I'd had it replaced. Also, it was half an hour after the bank closed for the long weekend, a very fraud-friendly time. And when I told him I'd call him back and asked for the after-hours fraud number, he got very threatening and warned me that because I'd now been notified about the fraud that any losses the bank suffered after I hung up the phone without completing the fraud protocol would be billed to me. I hung up on him. He called me back immediately. I hung up on him again and put my phone into do-not-disturb.
The following Tuesday, I called my bank and spoke to their head of risk-management. I went through everything I'd figured out about the fraudsters, and she told me that credit unions across America were being hit by this scam, by fraudsters who somehow knew CU customers' phone numbers and names, and which CU they banked at. This was key: my phone number is a reasonably well-kept secret. You can get it by spending money with Equifax or another nonconsensual doxing giant, but you can't just google it or get it at any of the free services. The fact that the fraudsters knew where I banked, knew my name, and had my phone number had really caused me to let down my guard.
The risk management person and I talked about how the credit union could mitigate this attack: for example, by better-training the after-hours card-loss staff to be on the alert for calls from people who had been contacted about supposed card fraud. We also went through the confusing phone-menu that had funneled me to the wrong department when I called in, and worked through alternate wording for the menu system that would be clearer (this is the best part about banking with a small CU – you can talk directly to the responsible person and have a productive discussion!). I even convinced her to buy a ticket to next summer's Defcon to attend the social engineering competitions.
There's a leak somewhere in the CU systems' supply chain. Maybe it's Zelle, or the small number of corresponding banks that CUs rely on for SWIFT transaction forwarding. Maybe it's even those after-hours fraud/card-loss centers. But all across the USA, CU customers are getting calls with spoofed caller IDs from fraudsters who know their registered phone numbers and where they bank.
I've been mulling this over for most of a month now, and one thing has really been eating at me: the way that AI is going to make this kind of problem much worse.
Not because AI is going to commit fraud, though.
One of the truest things I know about AI is: "we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job":
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week
I trusted this fraudster specifically because I knew that the outsource, out-of-hours contractors my bank uses have crummy headsets, don't know how to pronounce my bank's name, and have long-ass, tedious, and pointless standardized questionnaires they run through when taking fraud reports. All of this created cover for the fraudster, whose plausibility was enhanced by the rough edges in his pitch - they didn't raise red flags.
As this kind of fraud reporting and fraud contacting is increasingly outsourced to AI, bank customers will be conditioned to dealing with semi-automated systems that make stupid mistakes, force you to repeat yourself, ask you questions they should already know the answers to, and so on. In other words, AI will groom bank customers to be phishing victims.
This is a mistake the finance sector keeps making. 15 years ago, Ben Laurie excoriated the UK banks for their "Verified By Visa" system, which validated credit card transactions by taking users to a third party site and requiring them to re-enter parts of their password there:
https://web.archive.org/web/20090331094020/http://www.links.org/?p=591
This is exactly how a phishing attack works. As Laurie pointed out, this was the banks training their customers to be phished.
I came close to getting phished again today, as it happens. I got back from Berlin on Friday and my suitcase was damaged in transit. I've been dealing with the airline, which means I've really been dealing with their third-party, outsource luggage-damage service. They have a terrible website, their emails are incoherent, and they officiously demand the same information over and over again.
This morning, I got a scam email asking me for more information to complete my damaged luggage claim. It was a terrible email, from a noreply@ email address, and it was vague, officious, and dishearteningly bureaucratic. For just a moment, my finger hovered over the phishing link, and then I looked a little closer.
On any other day, it wouldn't have had a chance. Today – right after I had my luggage wrecked, while I'm still jetlagged, and after days of dealing with my airline's terrible outsource partner – it almost worked.
So much fraud is a Swiss-cheese attack, and while companies can't close all the holes, they can stop creating new ones.
Meanwhile, I'll continue to post about it whenever I get scammed. I find the inner workings of scams to be fascinating, and it's also important to remind people that everyone is vulnerable sometimes, and scammers are willing to try endless variations until an attack lands at just the right place, at just the right time, in just the right way. If you think you can't get scammed, that makes you especially vulnerable:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
10K notes
·
View notes
Text
I just got another one of those phishing emails where it pretends to be a confirmation of a subscription you never signed up for and tries to trick you into providing personally identifying information for "confirmation purposes" when you attempt to cancel, but:
a. this one is for a weekly grocery delivery service, of all things; and
b. the fake shopping list contains nothing but ham.
I have been fraudulently subscribed to ham.
7K notes
·
View notes
Text
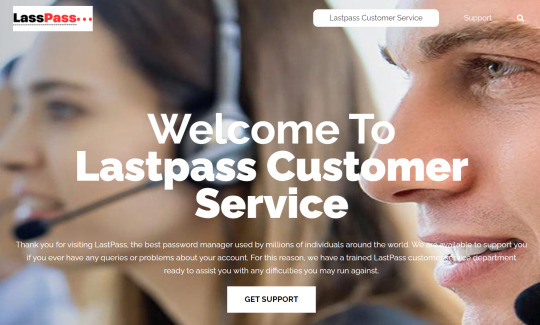
Phishing Alert
ETA: Update - I posted on 20 March 2023 and THIS phishing blog is long gone. There will be others.
*****
@staff - please take note.
This was in my daily dose of bots.
It is NOT what it claims to be. Watch out. (And look at the bottom of this post: they can’t even spell...)




4K notes
·
View notes
Text
Important warning regarding new phishing email based around tumblr
Hey everyone! Recently I was shown a screenshot of an email claiming to be from tumblr. The title read as follows: “Urgent: Verify Your Tumblr Account” claiming it’s from “Tumblr Officer”. However, with a little help, I have been able to confirm this is NOT a legitimate tumblr email! If you get this kind of email in your inbox, do not give them any of your information. I do not know where the email itself is from specifically, as the screenshot didn’t show it but hopefully this will help anyone who may be getting this now.
From my source, it is suggested to report this email to tumblr via support and refer to it as phishing since this seems to be a rather recent occurrence that has popped up. If you get the email that has the following, please do not give them any info:
“Urgent: Verify Your Tumblr Account” claiming it’s from “Tumblr Officer”
I have been able to verify it is a phishing email! Just so it’s clear that this isn’t an official tumblr email. This is a phishing email.
If you already gave your info to this phishing one, please change your passwords and enable any extra security methods and send tumblr support any details regarding where the email is being sent from so it can be looked into further!
718 notes
·
View notes
Text
Don’t Fall for “Sick Cat” Phishing
Just a reminder that if someone you don’t know suddenly sends you a message asking for help paying vet fees for their sick pet, it’s almost certainly a scam. Don’t give them your money! And make sure to report them to Tumblr for phishing:
click the meatball menu for “report”
select “report something else”
select “unlawful uses or content”
select “phishing”
1K notes
·
View notes
Text

PSA. Warn your friends and relatives (especially the older ones).
109 notes
·
View notes
Text
Hey folks!
Nothing new for us, but there seems to be a new phishing scam going around.
Remember to stop and think before you click a link.
Are they creating a sense of urgency? Especially if they are asking for money.
Did you solicit this information?
Has their blog been active long?
Does the username seem randomly generated?
Is the information accurate? Are there misspellings and grammar mistakes?
You can check a link by copying it and pasting it on a word document, notepad, etc.


Username may be different. They are sending this message block in asks, and have the same thing pinned on their blog. The link does not direct to a gofundme as tags suggest, but rather a paypal
Stay safe out there <3
112 notes
·
View notes
Text
Be Aware
Back in December, I got an email from someone claiming to be Team Cherry, the developers of Hollow Knight. This "marketing liason" was offering me early access to the sequel/expansion, Silksong, to review.
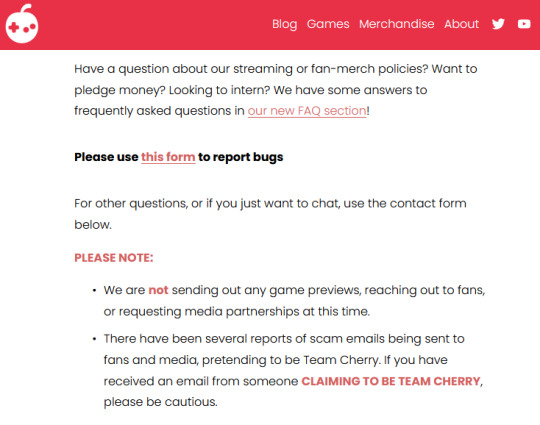
A friend with connections to the game press quickly pointed out that the real Team Cherry wasn't sending out early access review codes and that they were actually warning users about impersonators on their "Contact Us" form. The email I received was a scam from someone looking to infect me with malware and/or steal my identity. (I wrote a twitter thread about it here)
About a month later, as I was wrapping up work on my "Definitive way to Play Sonic Adventure 2" video, I received another email, this one claiming to be someone from Frontier Foundry asking to sponsor an upcoming video for the release of "Deliver Us Mars." I told them I already had a sponsor for the Sonic Adventure 2 video, and after I was done, I was planning on taking a holiday. They got weirdly pushy with me, saying I could "make a short video" and put the brand deal there. I was too busy finishing the video, so I ignored them and moved on.
Now another month later, I find myself finishing a quick little video and thinking about that Frontier Foundry offer again, but upon looking at it with fresh eyes, it also was a clear and obvious scam. Just like with the fake Team Cherry offer, the person isn't listed as an employee at Frontier Foundry, the email they sent the offer from seems to be a personal email address that doesn't match who they said they were, and the "Contract" they tried to force on me was a huge Google Drive zip file that was password protected to prevent me from seeing what was inside before I downloaded it. The fact that they were so pushy with me suddenly started making a lot more sense.
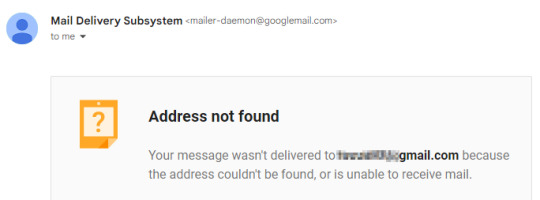
As icing on the cake, I tried to ask the person for proof of identity, and in the month+ since we last talked to each other, their email address has been forcibly closed by Gmail.
If you're an up-and-coming content creator, please be careful and be aware of tactics like this. It's easy to get starstruck by the idea that you're special enough to get picked for a sponsorship deal or an exclusive beta, but always research WHO is sending you that email and NEVER be afraid to ask for proof of identity. Go over their heads and check with the employer they claim to be from if you need to.
Be smart, protect yourself, and stay safe out there.
409 notes
·
View notes
Text
Deep dive to Spam bots on Tumblr (Spoiler: FSB mentioned)
(TL;DR: Russian business man is heavily investing into companies behind the bots, mentions of FSB, Shell companies in tax-evasion and weak business law countries, Huge industry and money laundering)
I got annoyed about the bots on tumblr, so I decided to do some investigation into who is behind them and funding the operation, here is my findings:

The graph shows how a network of “affiliate marketing” companies for “dating” services is connected and some of the key players behind said companies
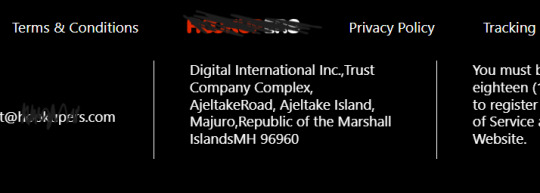
The first “company” I ran into is called “Digital international Inc” and it is shown as the “legal entity” behind of many of the websites the bots tend to link to, it also has its address listed in the Marshall Islands.
By looking at trademarks owned/filed by that company, we find 2 more companies/trademarks that are/were owned by the same legal entity.
First of these is called “Mirelia Services Co.”, currently known as “Mirelia Networks”, which lists its main business as “advertising and marketing” and is registered at the same address as “Digital International”.

Where things get interesting is when we look at one of the trademarks that was passed between “Mirelia” and “Digital international”, a trademark for an LGBTQ+ dating app called “Hitwe”,
The trademark application for “Hitwe” is listed as “Rescinded/canceled” but from the original registration documents and later ownership transfer filings, we come across an interesting company
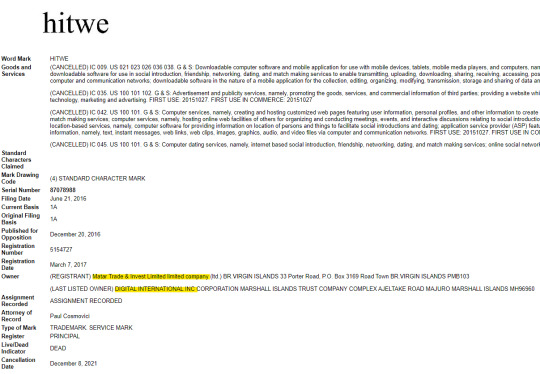
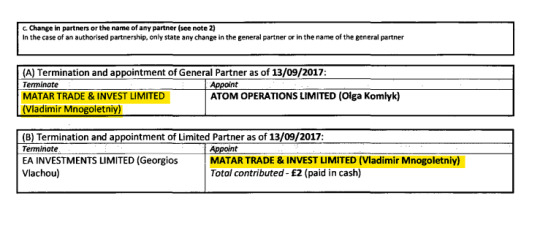
“Matar Trade & Invest Ltd.” This company has other similar “dating” and “marketing” companies linked to it, and is owned by “Vladimir Mnogoletniy”, a Citizen of Russia, who has lived in Ukraine for over 10 years and his runs his businesses there, but interestingly does not seem to have officially moved there, and maintains his Russian Citizenship as his only one.
He is also the CEO or a major of many other companies, the main one being “Genesis”, the company behind a controversial fitness app “BetterMe”, which has been shown to aggressively sell user data to less-than-reputable ad companies and affiliates, as well as being used to redirect money from scam dating sites and lessen the impact of credit card chargebacks from those sites [See footnote 1]
What makes him a particularly interesting individual is that his father, who is a Captain of the Second Rank in the Russian Navy, is doing security work for “Sevmash” - A Russian shipbuilding company, the only one that is making nuclear submarines in Russia. He also co-authored a research paper that talks about “Military Counterintelligence activities”, The other author of said paper is an FSB officer.[See footnote 2]
Sources and footnotes:
Footnote 1: “BetterMe steals traffic” - Article by SH[IT]HAPPENS on Medium
Footnote 2: “Why don’t I no longer shake hands with Vladimir Mnogoletniy.“ - Article by SH[IT]HAPPENS on Medium
Tangent: one of the other companies that I came across that seems to be working with Mirelia is “Traffichunt”, which seems to be one of the companies selling bot spam advertisements as well.

Another interesting thing is that the lawyer who filed for most of the trademarks, has quite a repertoire of similar trademarks under his belt:
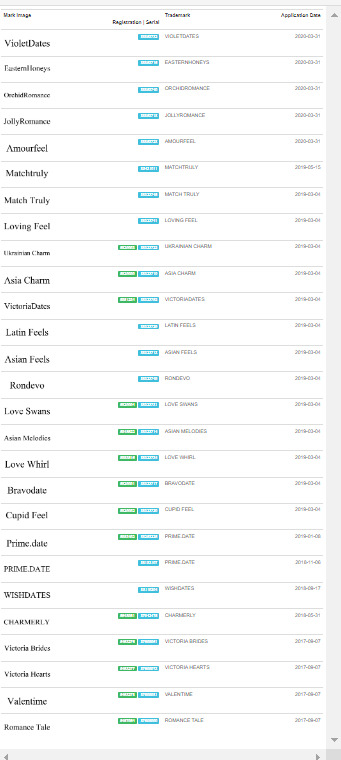
Most of these seem to have been rejected because the address he listed in the applications does not exist
If you read all the way to here, thank you and I hope that bot’s never bother you again.
#spam bots#deep dive#osint#spam#research#i hope i dont get merc'd#tumblr bots#please read#bots#spammers#opsec#phishing#cybersecurity#sex bots#fake accounts#long reads
888 notes
·
View notes
Text

88 notes
·
View notes
Note
Hello sorry for tagging. I am very sick, my asthma is at its maximum level, my nose freezes, I have no medicine or food. I am in bad shape financially, I am a black disabled, who uses multiple medications, I pay for my food and lodging
Unfortunately I do not have all the resources to keep me safe, that is why I need your help, whatever you can contribute to me will be of great help.
17 ish hour old scam blog regurgitating the same lies as usual, hiding behind marginalized identities in case anyone catches on to their bullshit. I'm pretty sure a lot of these are run by a botter.
to report them on the android app, go to the pinned post and copy the link to that, then go to the thing next to "follow" and report for something else -> unlawful uses -> phishing, then just type in what's going on. remember to block them too.
#scams#enchantingqueencreatorsblog#scammers#phishing#charity scam#report and block#lying liars who lie#kyra45
41 notes
·
View notes
Note
I’ve been so ill this past few weeks and been hospitalized because of medical concerns. Found out that I have a tumor and it was already malignant. I have a Stage 2A Cervical Cancer and needs help ASAP. 🥺
GOAL: $1800
Evidence:
This account has nothing to do with the cosmere
This account does not follow me and I don't follow them
This account reblogged a ton of random stuff four days ago and nothing since
Their posts use spam tags
This account answers asks from bots
This account has a misleading alternate name in the title
The request is coming from a direct ask and not via reblog by someone I know who can vouch for them
Conclusion:
Phishing scam
Blocked and reported!
36 notes
·
View notes
Text
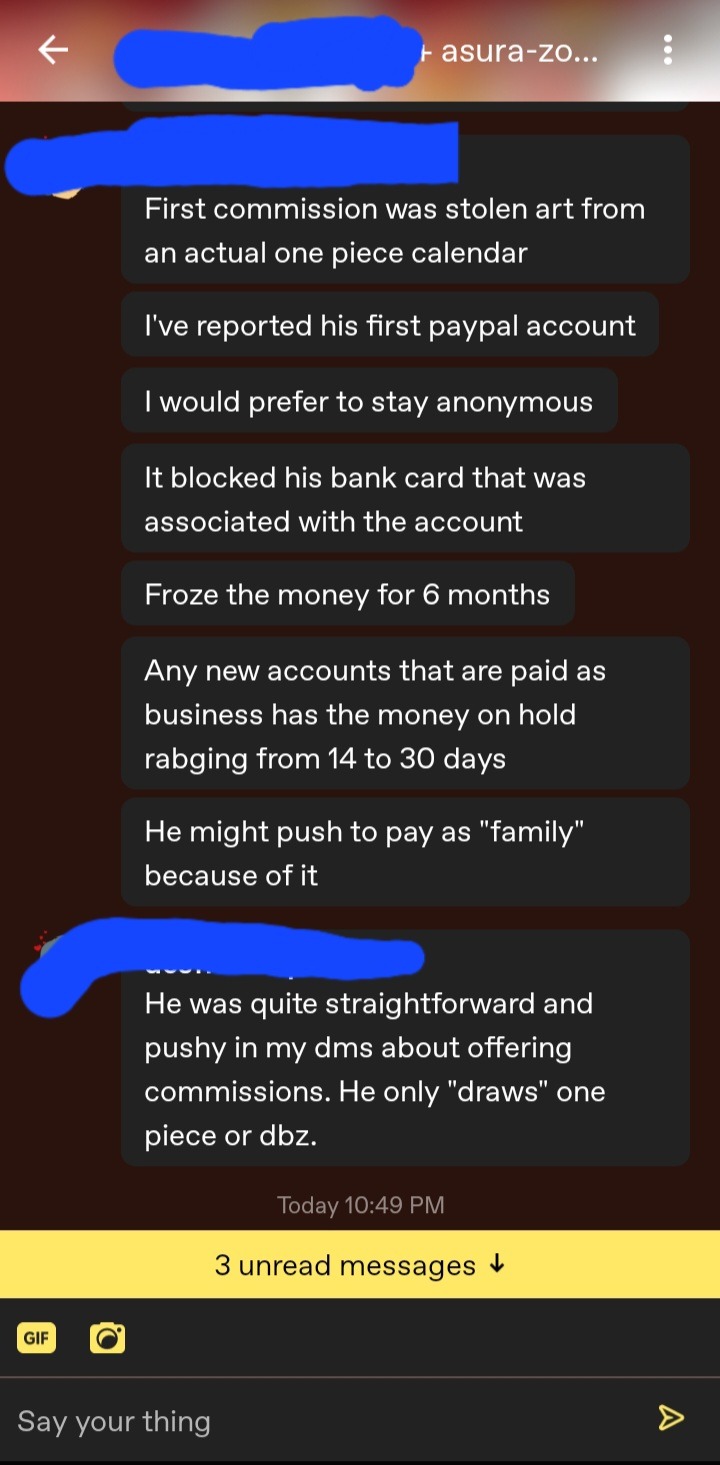
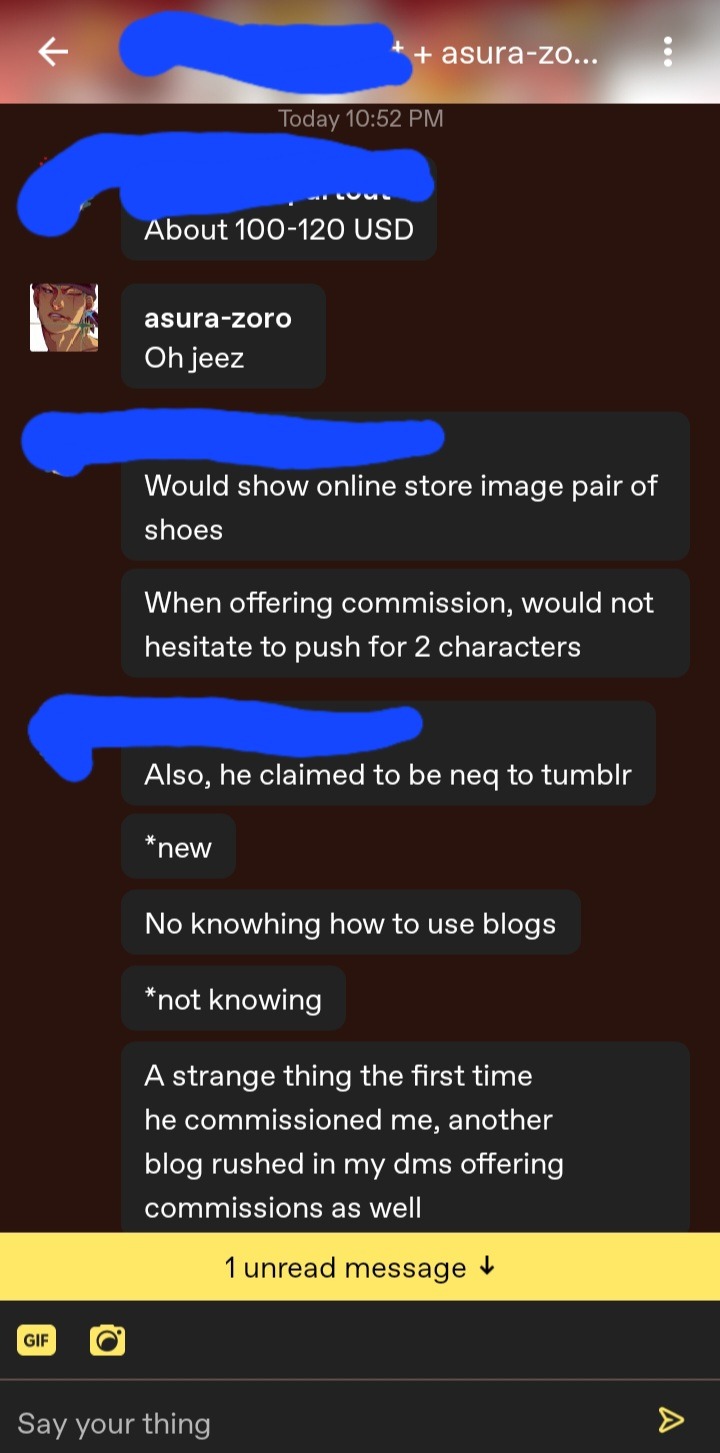
ATTENTION: ART THIEF AND SCAMMER
I know that I have reblogged some posts about this person, hoelys-blog, already but I think I should try to condense the info down to one post and provide some updates (updated information will be colored like this, or featured towards the bottom of the post.)
This person, who has identified himself as Lino to someone who measaged me (who was scammed by him), reaches out to you via DM to promote that they have commissions going on. Showcasing art that they have stolen and altered from other people. As far as I know, only one artist was able to get majority of their work taken off of this guy's "commission post(s)". I have reblogged some posts about that artists experience, you can see all the posts I mention if you search the #hoelys-blog tag on my blog or by clicking on any posts tagged as that.
Any effort to call out this scammer on his posts are made in vain- he deletes any reply or reblogged comment so that folks visiting his page cannot see any attempt at warning on his posts- UNLESS YOU CHECK THE REBLOG AREA AND VIEW THE TAGS.
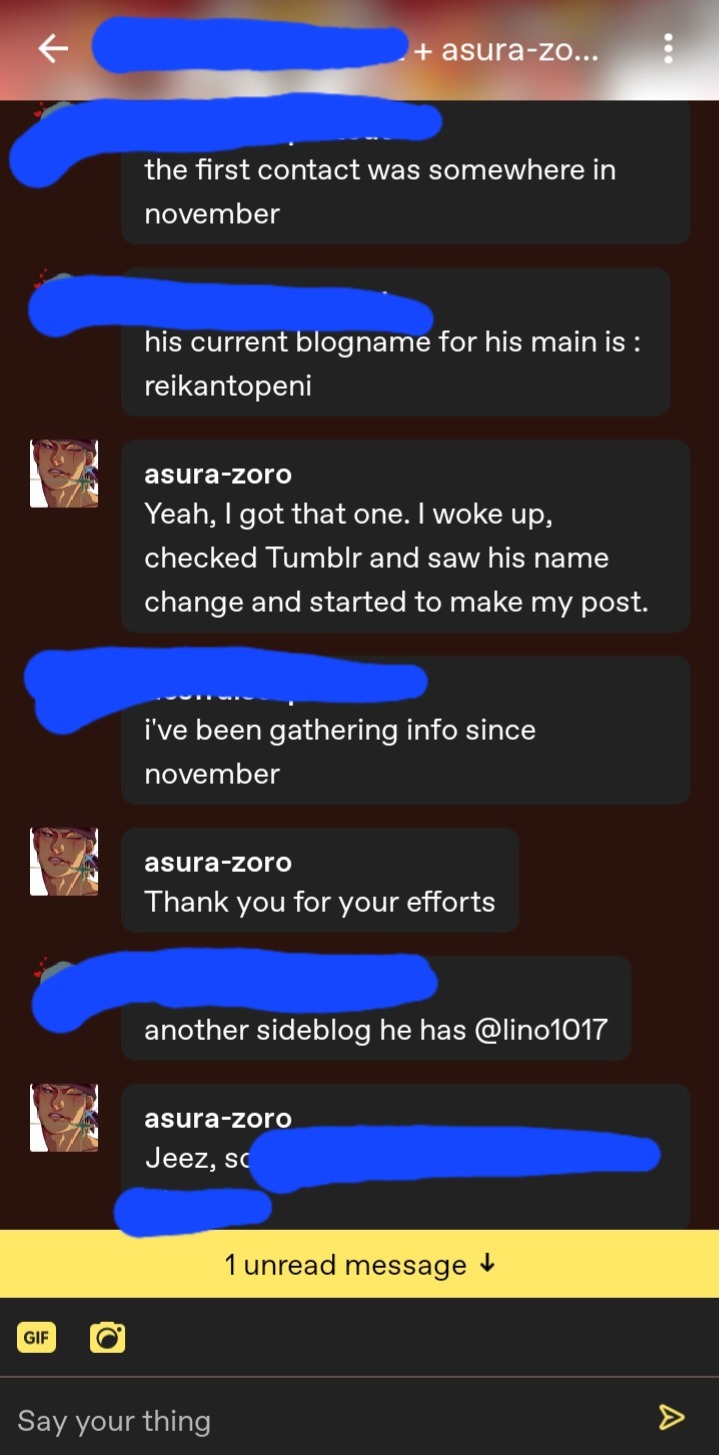
He saw my attempts to warn people, deleted my replies/comments on his posts and I woke up to see that he changed his blog name.
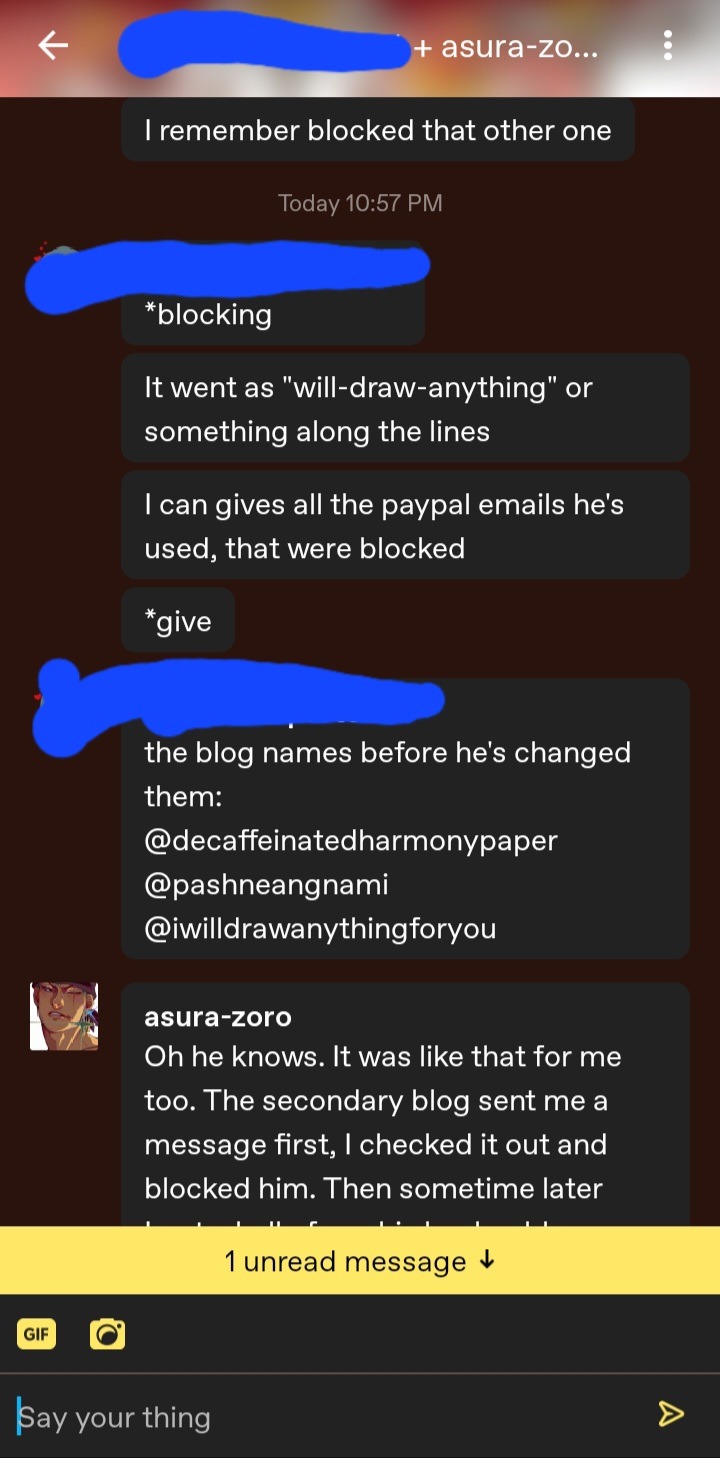
Here are all of his blogs that we know of:
@Reikantopeni formerly hoelys-blog
@Kawaiibasementsublime
@Pashnaengnami
@lino1017 (homework help scam)
@iwilldrawanythingforyou
A former name for one of these current blogs is decaffeinatedharmonypaper
All of his blogs feature stolen and altered artwork, and most are advertising that their commissions are open. If any of you know any of the stolen pieces' original artists, please let that artist know so that they can file the proper reports.
What we can do in the meantime is report each post that has stolen artwork promoting that he has commissions open. This goes for anyone that you see that does this- you report them for phishing. What I did was also provide a link to a post that showcases the the source of each stolen piece of work within that post. Tumblr support will reach out and ask you to provide links to the report you make!
Speaking of, you can access that particular post via the #hoelys-blog tag, look for a post made by @tamiisnthere!
This person also seems to make their rounds in different fandoms based off of tags that I've read- so it is not just One Piece or DBZ.
This person is known to be manipulative in the DMs, and get you to take pitty on them. They also will straight up beg. So I emphasize DO NOT ANSWER BACK WHEN HE DMS YOU. Just report commission posts as phishing before you block him and delete the convo. If you do talk with him, screenshot/keep your messages so that you have proof.
If you have been scammed by this man, please report the account(s) he used so that you can get your money back. He uses multiple PayPal accounts, someone that was scammed by him has given me each email that they are aware of. (I am debating if I post them or not...)
I highly encourage people speak of their experience with this person in the comments or in reblogs of this post. That way we can see how deep this rabbit hole goes.
By all means, do NOT harass this person. Please only report and block him!
Other Information/Updates
This is a message between someone who has gotten scammed by Lino and I. They asked to remain anonymous, some of the info you'll see in the screenshots have already been applied in the post earlier. This convo took place on 1/04/2023.
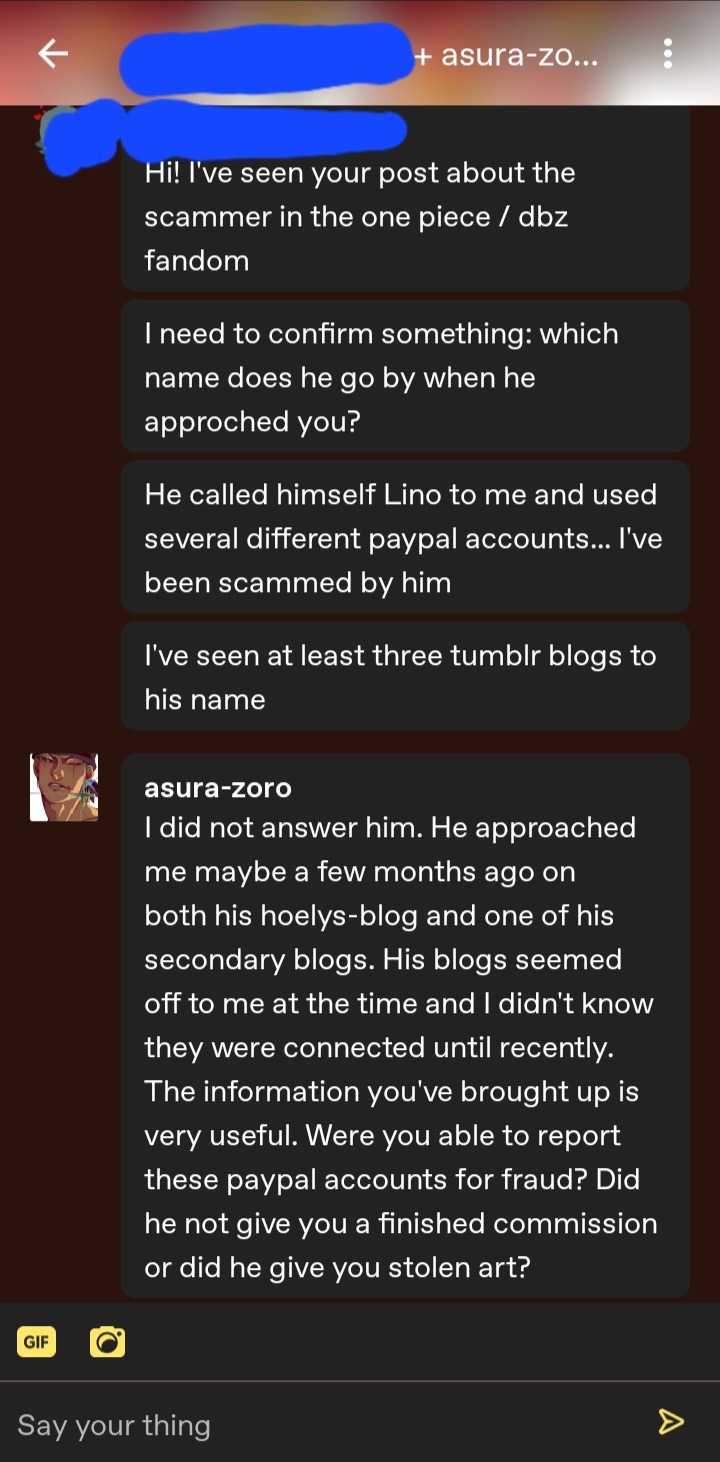


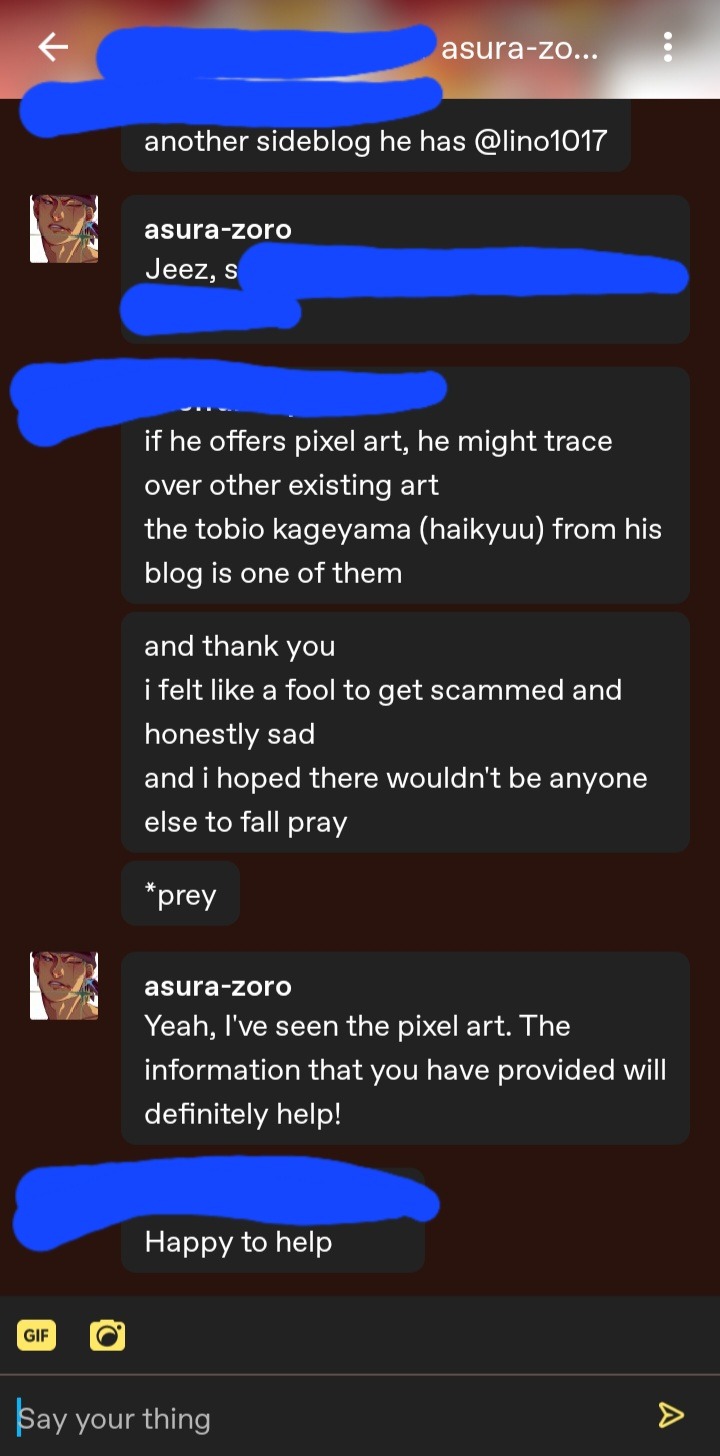
01/05/2023 Update
I will not be releasing details such as his full name or his emails at this moment. I believe that this information should be known to people who have been scammed or whose work has been stolen first. If anyone has been scammed by this man, or work has been stolen and need certain information to file reports, please message me.
These are some of the artists that tamiisnthere was able to find (you can see that post on my blog's #hoelys-blog tag), whose works was stolen by Lino. If they have a Tumblr, please tag them in the comments. Or if there are other artists whose work you see that Lino has stolen.
@soyochii
KrisBurdarina (on redbubble)
@chibigohan
Kkugvw (on twitter)
#art thief#art theft#scammer#art scam#hoelys-blog#kawaiibasementsublime#pashnaengnami#reikantopeni#phishing#art#commissions
296 notes
·
View notes
Text



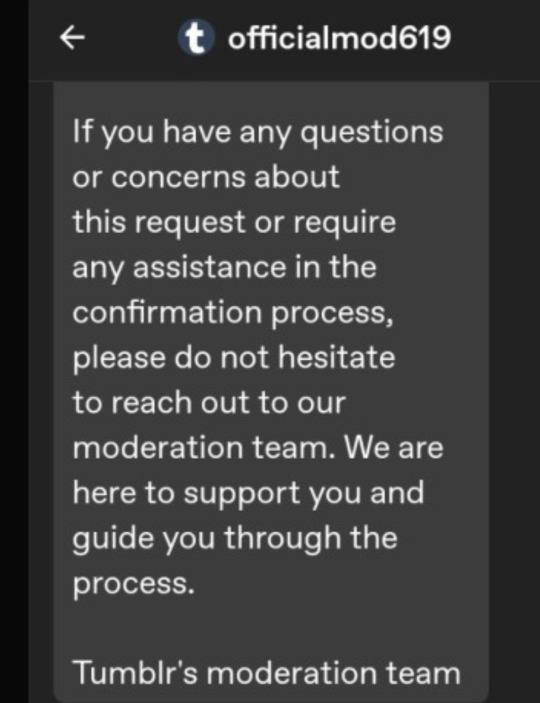
officialmod619 is not a moderator of tumblr. Don’t give them your password. Please report them for phishing. This has been a psa.
Update: Looks like the account is now down! But please remember this for future accounts who try this.
496 notes
·
View notes
Text
Attention: There may be a new scam thing (might also not be new)
Okay so I just got a weird notification from drive telling me I got shared a folder. The name of the folder was suspicious as fuck and thank my gods it was but my guess is that if this is a scam it might not always be the case!
Mine was from someone I'd never heard of and I definitely have not recently asked anyone to share any Google Drive folders or documents or anything with me.
Still, had the folder been titled something more innocent or innocuous, I might have been more inclined to click it or look into it.
So, just a PSA/WARNING to be on the look out for something like this. If you get something unsolicited no matter if it's a folder or a Google doc or anything! If you did not ask someone to share something on Google drive with you, DO NOT OPEN IT.
Instead click the three dots on the folder/document/whatever that are to the right of the item. Find report or block. Make sure you click the first option (I think it's called "spam" or something like that as it includes anything from unsolicited things, to malware, viruses, and phishing attempts.
My guess is that this scam most assuredly falls into one of the last three categories and sometimes just opening the thing can cause the bad thing to take place (i.e. you get the virus or malware or it immediately directs you to the phishing scam). Point is, it doesn't matter. Don't tempt the fates. Just get rid of it and don't look back. Doing what I instructed above will clear it from your drive without you having to take any further steps and insures they won't try to send anything further, at just via that particular account. It's my hope that it also blocks IP addresses and not just the account but that's not a guarantee so stay vigilant as they may try multiple times. So just remember, if you're not expecting something, block and report immediately.
PLEASE REBLOG AND SHARE TO GET THE WORD OUT.
#viruses#virus psa#malware#malware psa#phishing#phishing scam#phishing psa#computer science#computer security#security#psa#scam alert#scammers#scam#please reblog#scam psa
28 notes
·
View notes
Text
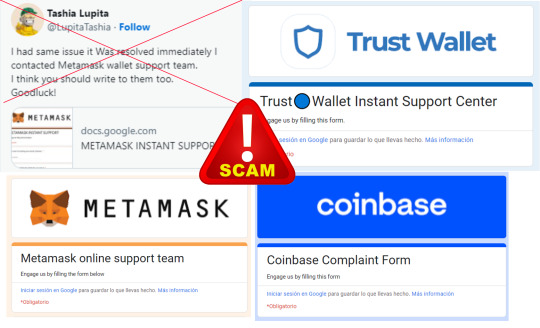
Google Forms used by scammers for tech support crypto scams
🎣 Remember, the technical support of UniSwap, PancakeSwap Balancer, Metamask, TrustWallet, CoinBase, Kraken and so on will never give you a Google form link to fill out!
🛑 Never fill out anything in google forms, no matter what is the fake reason.
💸 Filling out data via google forms is a guaranteed way to get immediately robbed blind.
🏦 Never reveal nor enter your seed phrase (or wallet JSON) anywhere!
But some end users get desperate, are scared, insecure, inexperienced or plain old gullible and naïve, conveniently falling for the same scams that have been floating around since the ICO craze of 2017.
Meanwhile E Mask allowed anyone to buy a blue tick on twatter, so this type of scam is more successful than ever, gee thanks.
6 years later, literally the same scam from 2017 is still pocketing ill gotten gains to cybercriminals.
h/t Daniel Lopez
#scam#crypto scam#phishing#google forms#twitter#tech support scam#fraud#cryptoscam#cryptoscamdb#crypto scam db#spoof#cybercrime
211 notes
·
View notes