#informatology
Text
ROBOT
THE TERM ROBOT COMES FROM THE CZECH WORD 'ROBOTA' WHICH MEANS 'DRUDGERY', OR 'HARD WORK' AND 'FORCED LABOUR'
#robots#robotics#roboticstechnology#labour#facts#factoftheday#interestingfacts#learnsomethingnew#tumblrposts#tumblrdaily#knowledge#technology#information#tech#informatology
177 notes
·
View notes
Text
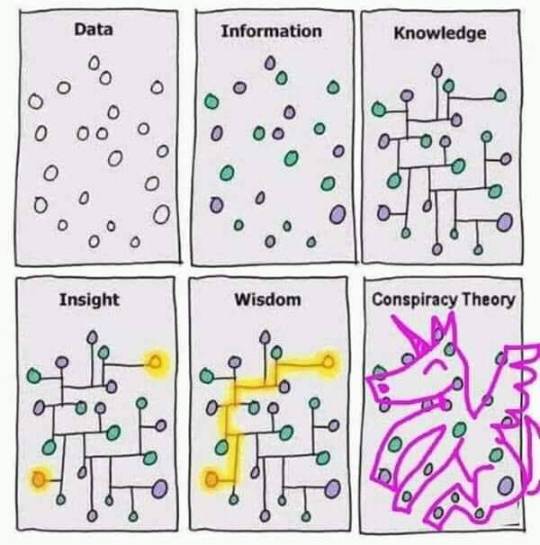
Just how informaton can change & develop....
4 notes
·
View notes
Text
YOU ARE IN GOOD HANDS IF YOUR SURGEON WAS A GAMER
ODDLY ENOUGH, SURGEONS THAT GREW UP PLAYING VIDEO GAMES MORE THAN THREE HOURS PER WEEK MAKE 37% FEWER ERRORS! NOT ONLY THAT, BUT THEY ALSO HAD A 42% FASTER COMPLETION RATE WHEN IT COMES TO PERFORMING LAPAROSCOPIC SURGERY, AS WELL AS SUTURING.
#doctors#surgeons#surgery#gamers#gaming#videogame#facts#factsoftheday#interestigfacts#learnsomethingnew#learneveryday#learningfromhome#tumblrposts#tumblrdaily#knowledge#technology#information#informatology
132 notes
·
View notes
Text
TYPEWRITER
TYPEWRITER IS THE LONGEST WORD THAT YOU CAN WRITE USING THE LETTERS ONLY ON ONE ROW OF THE KEYBOARD OF YOUR COMPUTER.
#typewriter#computers#keyboards#typing#facts#factoftheday#interestigfacts#learnsomethingnew#tumblrposts#tumblrdaily#knowledge#information#technology#tech#informatology#interesting#longest#word#writers
128 notes
·
View notes
Text

THE FIRST WEBPAGE IS STILL RUNNING
#webpage#information#tumblrposts#factoftheday#knowledge#technology#tumblrdaily#learnsomethingnew#facts#informatology#interestingfacts
103 notes
·
View notes
Text
CIGARETTE
A single cigarette contains over 4800 chemicals, 69 of which are known to cause cancer.
#CANCER#chemicals#cigarette#facts#learnsomethingnew#factoftheday#interestingfacts#tumblrposts#tumblrdaily#technology#information#knowledge#informatology
119 notes
·
View notes
Text
BRAIN POWER
IF THE COMPUTER BRAIN WAS DESIGNED JUST LIKE THE HUMAN BRAIN, THEN IT COULD STORE 3584 TERABYTES OF DATA AND PERFORM 38 THOUSAND TRILLION OPERATIONS EACH SECOND.
DO NOT UNDERESTIMATE YOUR OWN BRAIN!
#informatology#brain#brainpower#brainhealth#facts#factoftheday#interestigfacts#learnsomethingnew#tumblrposts#tumblrdaily#knowledge#information#computers#technology#tech#neuroscience#power
92 notes
·
View notes
Text
GOOGLE
ON AUGUST 16, 2013, GOOGLE WENT DOWN FOR 5 MINUTES, AND IN THAT TIME, THE GLOBAL INTERNET TRAFFIC DROPPED BY 40%.
#google#googleserach#google news#google services#facts#factoftheday#interestigfacts#learnsomethingnew#tumblrposts#tumblrdaily#knowledge#technology#tech#information#learning#learningfromhome#informatology
74 notes
·
View notes
Text
CHECKING WHETHER WINDOWS ARE PIRATED OR GENUINE
Some people wouldn't know whether the operating system they use is pirated or genuine. So, in this case, we have a trick to find whether the operating system we are using is pirated or original.
Don't worry if you are not a professional desktop/laptop operator Not need for an expert desktop/laptop operator. If you are a fresher in operating desktop/laptop, then you also check it's a simple and quick way to spot the difference between pirated and original operating systems.
So let's start
FIRST, YOU WILL HAVE TO OPEN THE RUN DIALOG BOX BY GOING TO START AND SEARCH FOR RUN OR PRESS KEYS(WIN+R). IF THE RUN DIALOG BOX POP-UP CLICK ON IT.

TYPE THE COMMAND IN THE SEARCH BOX licensingdiag.exe AND HIT ENTER.
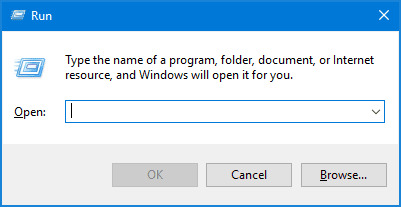
THIS WILL OPEN A FILE EXPLORER, WHICH CONTAINS THE CAB FILE. THE FILE NAME SHOULD BE LIKE PCName_year-mm-dd_diag

DOUBLE CLICK ON SPP.
DOUBLE CLICK THE SPPDiagReport.xml.
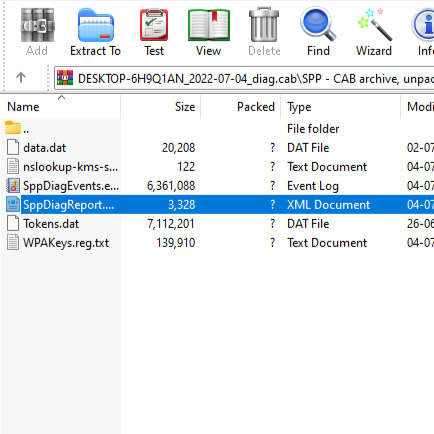
EXTRACT SPPDiagReport.xml TO YOUR PREFERRED FOLDER.
OPEN SPPDiagReport.xml THEN LOOK FOR LocalGenuineState.
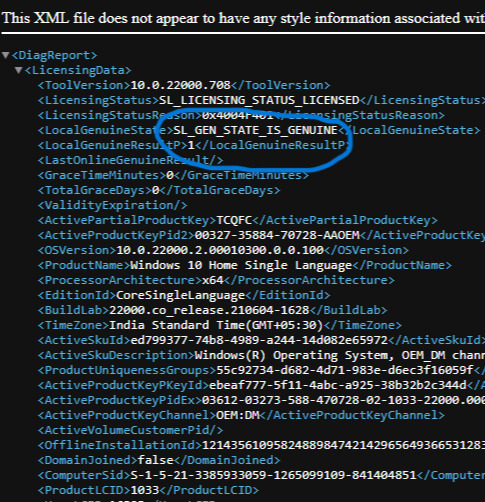
IF IT SAYS SL_GEN_STATE_IS_GENUINE, THIS MEANS THE LICENSE IS GENUINE OR VALID.
If your computer does not have WinRAR then first go download it and then follow these steps. Click on the below link to download Winrar.
THIS METHOD WORKS ON WINDOWS 8, 8.1, 10, AND 11 SOMETIME WORKS IN WINDOWS 7, BUT NOT ALWAYS.
If you are facing any problem in these steps, then you can comment and message us personally, if we have a solution for that problem, then we will definitely tell you.
#desktop#windowsuser#windowspc#windows#laptop#gadgets#technologyrocks#computers#futurism#internet#learnsomethingnew#tumblrposts#tumblrdaily#knowledge#technology#information#tech#informatology#informative
61 notes
·
View notes
Text
The role of quantum computing in modern technology
Quantum computing is a rapidly evolving field of technology that is poised to have a significant impact on modern society. The key advantage of quantum computers over classical computers is their ability to perform certain computational tasks much faster and more efficiently. This opens up a wide range of potential applications, including drug discovery, cryptography, and artificial intelligence.
Quantum computers use quantum bits, or qubits, instead of classical bits to store and process information. Unlike classical bits, which can only be in a state of either 0 or 1, qubits can exist in multiple states simultaneously, known as superposition. This allows quantum computers to perform certain operations much faster than classical computers by processing multiple bits of information at once.
One of the most promising applications of quantum computing is cryptography. Quantum computers can be used to solve mathematical problems that are difficult for classical computers to solve, such as factoring large numbers. This has the potential to dramatically improve the security of online transactions and communication by making it much more difficult for hackers to intercept and decode sensitive information.
Another area where quantum computing has the potential to make a significant impact is drug discovery. Quantum computers can be used to simulate the behavior of molecules and materials at the atomic and subatomic level, allowing scientists to design and test new drugs more quickly and accurately. This could lead to faster, more effective treatments for a wide range of diseases.
In addition to these applications, quantum computing is also expected to play a key role in advancing the field of artificial intelligence. Quantum algorithms can be used to process and analyze large amounts of data much faster than classical algorithms, which could lead to breakthroughs in machine learning, natural language processing, and computer vision.
In conclusion, the role of quantum computing in modern technology is to provide new and more efficient ways of solving complex computational problems. As technology continues to evolve and improve, it is likely to have a profound impact on many areas of our lives, from cryptography and drug discovery to artificial intelligence and beyond.
#quantum computing#technology#computers#science#information#informatology#discovery#vision#quantum#complex#intelligence#modern
16 notes
·
View notes
Text
REPAIR YOUR PC USING A COMMAND PROMPT
HELLO FRIENDS, TODAY I WILL TELL YOU HOW TO SCAN AND REPAIR YOUR PC WITHOUT THE HELP OF ANY ANTIVIRUS.
SOMETIMES YOUR PC GETS VICTIM AFTER THE DOWNLOAD OF ANY THIRD-PARTY SOFTWARE. IT HAPPENS BECAUSE THE SOFTWARE YOU DOWNLOAD IS NOT A CERTIFIED SOFTWARE. SO, WHEN IT GETS INSTALLED, IT DAMAGES SOME OF THE WINDOWS OPERATING SYSTEM FILES, AND AFTER DAMAGING THE FILES, YOUR PC GETS SLOWER. SO, TODAY I WILL TELL YOU THE PROCEDURE OF HOW TO GET ALL FILES REPAIRED WITHOUT LOSING DATA AND FORMATTING THE COMPUTER.
FIRST OF ALL, YOU HAVE TO OPEN THE 'COMMAND PROMPT' BY GOING TO START AND SEARCHING FOR 'CMD' IN THE SEARCH BOX. IF THE 'COMMAND PROMPT' POPS UP, CLICK ON RUN AS ADMINISTRATOR.

RUN THE COMMAND PROMPT AS AN ADMINISTRATOR, AND CLICK 'YES' IF IT ASKS FOR PERMISSION.
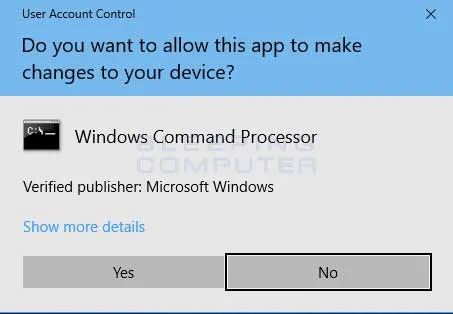
TYPE THE COMMAND sfc/scannow AND HIT ENTER.
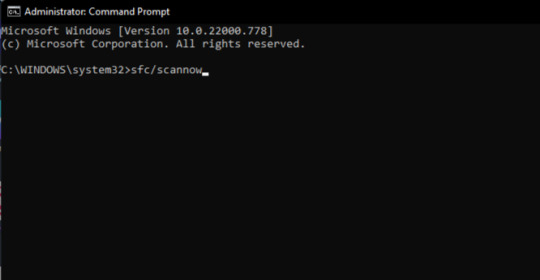
IT WILL SCAN YOUR ENTIRE SYSTEM
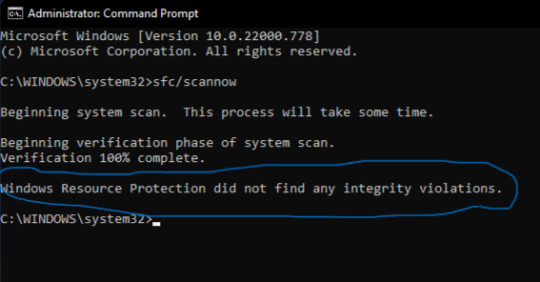
IF YOUR COMPUTER DOES NOT HAVE ANY CORRUPT FILES, AFTER SCANNING IS COMPLETE, YOU WILL SEE WINDOWS RESOURCE PROTECTION DID NOT FIND ANY INTEGRITY VIOLATIONS.
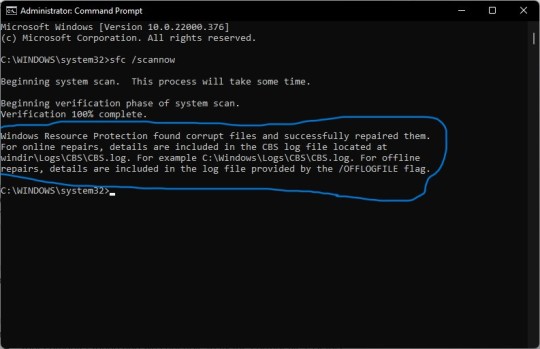
BUT IF SCANNING FINDS ANY CORRUPT FILES AND REPAIRS THEM, THEN YOU WILL SEE 'WINDOWS RESOURCE PROTECTION FOUND CORRUPT FILES AND SUCCESSFULLY REPAIRED THEM
THIS PROCEDURE WILL WORK ON ALL WINDOWS, WHETHER IT'S WINDOWS 7, 8, 8.1, 10 AND 11
THANKS FOR READING THIS ARTICLE. IF YOU FIND SOMETHING HELPFUL, THEN PLEASE SHARE IT WITH YOUR FRIENDS.
IF YOU ARE FACING ANY PROBLEM IN THESE STEPS, YOU CAN COMMENT OR MESSAGE US PERSONALLY. IF WE HAVE A SOLUTION FOR THAT PROBLEM THEN WE WILL TELL YOU.
#computer#laptops#desktops#computerengineering#software#troubleshooting#command prompt#cmd#tumblrposts#tumblrdaily#knowledge#information#informatology#learnsomethingnew
53 notes
·
View notes
Text
"Exploring the Intersection of AI and Image Captioning: How Machines Generate Accurate and Meaningful Descriptions"
AI technology has come a long way in recent years, and one area where it has made significant progress is in image captioning. Image captioning refers to the process of generating a textual description of an image or video. In this article, we will explore how AI technology works with captioning and the different approaches used to generate captions.
Neural Networks
Neural networks are a key technology in image captioning. These networks are designed to mimic the human brain and can learn from examples and data. The networks consist of several layers of nodes, each of which performs a specific operation on the input data. For image captioning, the neural network is trained on a large dataset of images and their associated captions. The network then uses this training to generate captions for new images.
Natural Language Processing
Natural language processing (NLP) is another important technology used in image captioning. NLP is a subfield of AI that focuses on the interaction between computers and human language. It involves the analysis of language and the development of algorithms that can understand and generate natural language. In image captioning, NLP is used to generate captions that are grammatically correct and semantically meaningful.
Attention Mechanism
Attention mechanism is a technique used to improve the performance of neural networks in image captioning. It works by allowing the network to focus its attention on specific parts of the image when generating the caption. For example, if the image contains a person, the attention mechanism can direct the network to focus on the person's face when generating the caption. This helps to ensure that the generated caption is more accurate and relevant to the image.
Transfer Learning
Transfer learning is a technique that involves using a pre-trained neural network as a starting point for a new task. In image captioning, transfer learning can be used to improve the performance of the network by starting with a pre-trained network that has already been trained on a large dataset of images and captions. This allows the network to learn more quickly and accurately, reducing the amount of training time required.
In conclusion, AI technology has made significant strides in image captioning, thanks to the use of neural networks, natural language processing, attention mechanisms, and transfer learning. These technologies have enabled machines to generate captions that are accurate, meaningful, and grammatically correct. As AI technology continues to evolve, we can expect to see even more advanced image captioning systems that can understand and describe images and videos with greater accuracy and nuance.
#AItechnology#ImageCaptioning#NeuralNetworks#NaturalLanguageProcessing#AttentionMechanism#TransferLearning#ArtificialIntelligence#MachineLearning#ComputerVision#informatology#technologynews#information
13 notes
·
View notes
Text
FIRST SOCIAL NETWORK
The first social network made available to the public was SixDegrees.com Unfortunately, it did not last long from its creation in 1997 to its close in 1999. It was one of the first platforms to enable users to upload photos and share information.
#social#social media#network#photos#videos#information#factsoftheday#facts#interestingfacts#learnsomethingnew#tumblrposts#tumblrdaily#knowledge#technology#tech#informative#informatology
40 notes
·
View notes
Text
"Is the Tor Browser Safe to Use? Exploring the Benefits and Risks of Anonymous Browsing"
The Tor Browser is a popular web browser that allows users to access the internet anonymously and privately. It works by routing your internet traffic through a network of volunteer-operated servers, which makes it difficult for anyone to track your online activity or identify your IP address. While the Tor Browser can be a useful tool for protecting your privacy and security online, many people wonder if it is truly safe to use. In this article, we'll explore the safety of the Tor Browser and provide some tips for using it safely.
Is the Tor Browser safe to use?
The short answer is yes, the Tor Browser is generally considered safe to use. The browser is open-source software, which means that anyone can review the code and look for vulnerabilities or security flaws. Additionally, the Tor Project (the organization behind the Tor Browser) is committed to maintaining the security and privacy of its users.
However, it's important to note that no software is completely foolproof, and the Tor Browser is no exception. While using the Tor Browser can help protect your privacy and anonymity online, there are still some potential risks to be aware of.
One potential risk of using the Tor Browser is that it can be used to access illegal or malicious content. Because the Tor network allows users to remain anonymous, it has become a popular tool for criminals and hackers to conduct illegal activities such as selling drugs or weapons, distributing malware, or engaging in other nefarious activities. As a result, using the Tor Browser to access certain websites or online communities can put you at risk of encountering illegal or harmful content.
Another risk of using the Tor Browser is that it can be slower than other web browsers due to the way it routes your internet traffic through multiple servers. This can make browsing the internet feel sluggish or unresponsive, which can be frustrating for some users.
Tips for using the Tor Browser safely
Despite these potential risks, there are several steps you can take to use the Tor Browser safely:
Keep your browser up-to-date: Make sure you're using the latest version of the Tor Browser, which will include the latest security patches and bug fixes.
Use a strong password: When creating an account or logging in to a website while using the Tor Browser, be sure to use a strong, unique password to protect your account from hackers.
Avoid downloading files: To minimize the risk of downloading malware or viruses, avoid downloading files or software while using the Tor Browser.
Use two-factor authentication: Where possible, use two-factor authentication to add an extra layer of security to your online accounts.
Be aware of your online activity: When using the Tor Browser, be mindful of the websites and online communities you visit. Avoid websites that may contain illegal or malicious content, and use common sense when engaging with others online.
In conclusion, the Tor Browser can be a useful tool for protecting your privacy and security online, but it's important to use it safely and responsibly. By following these tips, you can help ensure that your online activity remains safe and secure while using the Tor Browser.
#TorBrowser#OnlinePrivacy#AnonymousBrowsing#InternetSecurity#CyberSafety#OpenSourceSoftware#WebAnonymity#OnlineSecurity#InternetPrivacy#SafeBrowsing#informatology
8 notes
·
View notes
Text
First Tweet posted by Google
THE FIRST TWEET POSTED BY GOOGLE WAS, " I'M
01100110 01100101 01100101 01101100 01101001
01101110 01100111 00100000 01101100 01110101
01100011 01101011 01111001 00001010. " IN BINARY
SYSTEM, IT STANDS FOR " I'M FEELING LUCKY. "
#twitter#tweet#googleserach#googlesearch#google news#facts#factoftheday#interestingfacts#learningfromhome#learnsomethingnew#learneveryday#tumblrposts#tumblrdaily#knowledge#technology#information#tech#informatology
42 notes
·
View notes
Text
WORLD'S FIRST SUPERCOMPUTER
THE WORLD'S FIRST SUPERCOMPUTER WAS DEVELOPED BY IBM IN THE YEAR 1956, WHICH WEIGHED NEARLY A TON AND WOULD STORE UP TO 5MB OF DATA.
#computers#supercomputers#storage#inventions#facts#factoftheday#interestigfacts#learnsomethingnew#tumblrdaily#tumblrposts#knowledge#technology#tech#information#informatology
35 notes
·
View notes