#No to Cyber Crime Law
Text




The Most Hated Man on the Internet
Click here for the full trailer
Do your part and REPORT.
#TV Trailers#trailers#Netflix#The Most Hated Man on the Internet#Docuseries#Internet Culture#images#Cyber Crime#Cybersecurity#FBI#Hacking Case#depression#PTSD#Anxiety#Suicidal Thoughts#Anonymous#Charlotte Laws
15 notes
·
View notes
Text
Calculus Legal

Calculus legal is a boutique law firm, having an all India presence through its alliance with local counsels at different states of India . Being a full time law firm, it has potential of providing legal services on all aspects of client’s business. We are modern and inclusive in our outlook, having a solution oriented approach. At calculus legal, we believe in establishing strong & enduring relationships with our clients by ensuring that we are always available to attend to our client’s needs. We are transparent in our working & commit ourselves to time bound and cost effective advice that project our client’s interest every time.
Areas of Expertise:
Criminal Law & Bail Matters, Family Law, Civil Law, Labour Law & Service Matters, Customs & Excise, Lawyers For Corporate Law, Lawyers For Cyber Law, Vetting & Review of Legal Agreements, Consumer Complaints
You can contact us for a free consultation with our experts just by calling at +91 9717705300 or visit us at www.calculuslegal.com
#legalcalculus#legaladvice#legalfacts#lawfirm#legalservices#legalhelp#criminal defense lawyer#cyber crime lawyers#divorce#law#lawyer#lawyers near me#legal advisers#law and legal system#criminal law#legal
4 notes
·
View notes
Text
Meaning and Scope of Cyber Law | Cyber Law

Hello friends, welcome to your home aaush and in today's blog we will talk about cyber law and together we will talk about its meaning, then we will talk about its importance and together we will cover So stay with me on this and mostly these people are Ru Ru [Music] A+B Friends, before starting Cyber Law Gives, I would like to focus on two words, first is on the West Side and second is cyber crime, if I understand cyber law then first. We have to understand cyber and cyber crime, due to this we have lost sleep and need of cyber law, hence it is very important for us to understand these two words. Let's start with cyber, cyberworld means virtual reality i.e. a world which That all technology is best, that is, a virtual world in which all work is done by technology, we call it cyber, while if we talk about cyber crime, then such crimes are committed using technology, these crimes are based on gift technology, all cyber crimes are done using technology. Now let's start with the meaning of cyber law. Cyber law means a lock that protects the heart. Issues related to Internet, technological and electronic elements, communication technology including computer software, hardware and information systems. This is a lock that Sensing and looking at issues related to everything We all call it Cybercrime A general term that refers to all criminal activities in using one medium of communication technology Complaints where Internet Cyberspace and the World Wide Web The link tells how to spend time in a cyber café and refers to all the criminal activities that are carried out using it.
Also Read- how to unfreeze bank account online
We will include all the coffee activities done using communication technology, components, internet, cyber space or the World Wide Web of a person under cyber crime. We will join them with cyber crime. Now let us talk about how many categories are there in cyber crime. So friends, cyber crime has been divided into two categories, first is using a computer to target a computer example, hacking virus attack. It has been told earlier that using a computer to target another computer such as hacking or virus attack. Attacking is also considered a side and the second point will tell if this computer to commit crimes example online fraud cyber terrorism extra i.e. using a computer to commit a crime like online fraud this cyber terrorism this extra now let's talk about Cyber law is important, how important is cyber lock for a person, as we know that cyber law is connected with every individual in today's time, every one of us either in one minute or the other. Secondly, money is connected to the internet and where do we use the internet, whether we have to create an account online or perform any commerce transaction, whether we have to use net banking or for females, we will talk about it. Voice Important Vikas HS Almost All Aspects of Transactions And activities can and concern the Internet, the World Wide Web and cyber space. This cyber public information is important because it touches every aspect of the transaction, protects every activity that is connected to the Internet and fiber lock protects every Cyber law protects an individual from getting trapped in any side reaction.
Also Read-how to unfreeze bank account
Now let's move to our next point which talks about cyber law and payment is cyber law in India. The number of activities through internet is on increase with changing times requirement for several roads in application. There is gathering momentum as we We know that the use of internet is increasing on a daily basis and as the society changes, there are changes in it according to the changes in the society, whereas as the internet is increasing, there is a demand for cyber law to stop internet crimes. Business Box Now let's talk about the next point i.e. what is technology? So friends, while listening to technology, a picture is formed in our mind because of Aamir Khan of 3 Idiots in which he tells that technology is a tour which lightens the life of any person. It is absolutely correct. Now let's talk about the legal aspect of it. The word technology is made up of two Greek words. In the test and law course, we will talk about the word 'Taken A'. The meaning of 'Taken A' is Is art craft and kills whereas if we talk about people then people means to speak on learning, a skill, a craft which tells about someone, decline of technology, meaning of B.Tech in technology, tools and techniques and sources of power to Make Life Easier and More Pleasant and Work More Productive, that is what Aamir Khan said.
Also Read- Bank Account Freeze Ho Jaye To Kya kare
The tune which makes someone's life easy is called technology. Now let's move towards the last point of our blog i.e. cyber. Friends, to understand Cyber Tuesday, I will have to first keep cyber and jurisprudence separate and understand. Sahib, we said before my blog. The point is that cyber means virtual reality i.e. a world which is a virtual pet. If we talk about it from this lens then it is jurisprudence but it is made up of the word jurisprudence or which means the study and knowledge of law i.e. cyber law. Talking about the students, it involves the study of law which is directly related to the cyber crimes. Cyber Juice. Students also describe the principles of legal issues which actually regulate cyberspace and internet. What is the meaning of cyber dance? What kind of study, what kind of knowledge is there about cyber crimes? Cyber Juicer talks about the principles that regulate cyberspace and the Internet.
0 notes
Text
youtube
#cybercrime#Cyber Fraud Lawyer in India#Cyber Fraud Advocate in India#Cyber Fraud Lawyers in India#Cyber Fraud Advocates in India#Cyber Crime Vakil in India#Cyber Crime Attorney in India#Cyber Law Expert lawyer in India#Cyber Crime Lawyer in India#Cyber Crime Lawyers in India#Cyber Crime Advocate in India#Cyber Crime Advocates in India#Cyber Law Lawyer in India#Cyber Law Lawyers in India#Cyber Law Advocate in India#Cyber Law Advocates in India#Cyber Law Vakil in India#Cyber Law Attorney in India#Cyber Law Expert in India#Cyber Law Expert in Gujarat India#Lawyer for Cyber Fraud Case in India#Lawyers for Cyber Fraud Case in India#Advocate for Cyber Fraud Case in India#Advocates for Cyber Fraud Case in India#Vakil for Cyber Fraud Case in India#Attorney for Cyber Fraud Case in India#Expert Lawyer for Cyber Law Case in India#Advocate for Cyber Fraud Matter in India#Advocates for Cyber Fraud Matter in India#Lawyers for Cyber Fraud Matter in India
0 notes
Text
Everyone enjoys the right to privacy. At present, everyone uses a wide array of mobile apps on their mobile handset. Every app asks for permissions that every user needs to agree to. However, this agreement can be dangerous for your privacy matters. This post talks about various matters related to agreeing to the permissions these apps look for. This post brings you the best information about the risks and threats you may face if you agree to all the permissions these apps ask for. You must read, understand, and follow the post before you download an app again.
Visit: https://www.vidhikarya.com/cyber-crimes-lawyers
Read Full Blog: Click Here
0 notes
Text
200 google recenzija
#advokat#kalesija#construction lawyer#advokat kalesija#lawyers near me#divorce lawyer#law#cyber crime lawyers#defense lawyers#lawyerlife
0 notes
Text
ہماری زندگی میں سوشل میڈیا کا کردارسوشل میڈیا کے نقصانات = منفی اثرات سے بچائو کے طریقے
حالیہ برسوں میں، سوشل میڈیا ہماری روزمرہ کی زندگی کا ایک لازمی حصہ بن گیا ہے۔ اس نے ہمارے ایک دوسرے کے ساتھ بات چیت کرنے، کاروبار کرنے، اور یہاں تک کہ خبروں اور معلومات تک رسائی کے طریقے کو تبدیل کر دیا ہے۔ بدقسمتی سے، یہ گھوٹالوں اور دھوکہ دہی کی سرگرمیوں کے لیے بھی ایک افزائش گاہ بن گیا ہے۔
سوشل میڈیا گھوٹالوں کا اضافہ
سوشل میڈیا گھوٹالوں کا اضافہ افراد اور کاروباری اداروں کے لیے ایک اہم…

View On WordPress
#cyber crime laws in pakistan#pakistan social media rules#social media k fide or nuksan#social media k nuqsan in urdu#ssnews#when social media will open in pakistan#why social media is not working today in pakistan#رابطہ پر اشعار#سوشل میڈیا پر مضمون عصر حاضر میں سوشل میڈیا کا کردار#سوشل میڈیا پر مضمون فوائد اور نقصانات اردو مضامین#سوشل میڈیا کا غلط استعمال#سوشل میڈیا کی تعریف#سوشل میڈیا کے نقصانات#سوشل میڈیا:منفی اثرات سے بچائو کی ضرورت#نوجوانوں پر سوشل میڈیا کے بڑھتے اثرات#ہماری زندگی میں سوشل میڈیا کا کردار
0 notes
Text
Do you need help understanding cybercrime law? Get in touch with a cybercrime lawyer who can help you navigate the complexities of this ever-evolving area of law.
0 notes
Text

(yandere! prison warden x gn! inmate reader) (FYI idk how the law works ok so DON'T come after my ass) (im the type of lawyer that gets ur sentence increased instead of decreased fr💀💀)
"can i kiss you?"
"dude, i literally threatened to kill you."
"so?"
he stares at you with a raised eyebrow, pouting slightly as he leans against the bars of your prison cell. you choose to ignore him, instead opting to play with the plastic fork from your lunch tray.
damn it, you should've known better than to be caught. now you're stuck in this lame ass prison with this warden you don't even like.
curse that stupid lawyer who got your sentenced increased from fifty years to life imprisonment. dude sucked at his job and still got paid 💀
for some context, you were in prison for tax evasion, fraud, and multiple cyber crimes you shall not name. you got caught by accident and now you were here. sentenced to life imprisonment in jail. in a private cell.
you know, it isn't even half that bad as compared to some other crimes others have committed! so you haven't a slightest clue as to why you were placed in a private cell with no one to keep you company!
i mean, you did try befriending your warden but he turned out to be delusional and turned out to be one of the people you scammed. love-scammed, to be specific. which is why he might've been delusional...
"baby why'd you have to leave me? i was so sad..."
see? this is what you mean! he seriously didn't get the hint that he was scammed! even when you told him straight to his face that you never did actually love him!
god damn it. now you have to hear his yapping 24/7. you're starting to think that he might've been the one to report you. i mean, isn't it a little too convenient? he's a prison warden, you've got a private cell-
"hey! are you seriously not paying attention to me?!"
he hits the prison bars lightly to attract your attention. thankfully, it did. or else he might've thrown another tantrum. and you did not have the mental capacity to handle it. come on! if he did it would've been his third tantrum of the week! and it's only monday!
you cock your head at him, rolling your eyes as you acknowledge his presence. your annoying prison warden instantly lights up at the small gesture. oh well, at least he's in love with you to the point where even you acknowledging him makes him happy...
"babe! you've gotta stop ignoring me! it makes me sad..."
"i don't actually care."
"baby!"
damn it, maybe you should've just bribed the judge to let you have a death sentence instead.
#yandere#tw yandere#yandere x reader#yandere imagines#yandere scenarios#yandere drabbles#yandere prison warden#yandere prison warden x reader#gn reader#suiana brainrotting#suiana rambling
3K notes
·
View notes
Text

Best Cyber Crime Lawyers in Rajouri Garden
Cyber Crime Lawyers In Delhi is when someone uses computer devices or networks to commit identity theft or fraud against others. It includes hacking, malware, and phishing.
If you have been victim to cybercrime and someone has stolen your personal information from your digital device(s), then Rohit Agarwal & Associates can help you.
#Cyber Crime Lawyers In Delhi#Cyber Law Firms In Delhi#Cyber Law Firm In Delhi#Cyber Lawyers In Delhi
0 notes
Text
HERE ARE THE BEST CYBERCRIME LAWYERS WHO WILL ACTUALLY IMPROVE YOUR LIFE

Cybercrime is a very common crime these days, committed in many different ways by many different people. Video uploads, images, and other vulgar content are examples of how they misuse the internet. cyber crime lawyer in delhi can take care of all kinds of cybercrime cases and provide the appropriate advice so that the case can be won.
What is Cybercrime?
Using the digital medium to commit an unlawful act is called cybercrime. It is, of course, the most common type of best law firm in saket; there are also many other wicked activities associated with cybercrime, including cyber bullying and spreading worms and viruses.
Cybercrime can be divided into two categories: deliberate damage and accidental damage. It the majority of cases, the loss is monetary, but that isn’te case.
Most Typical Kinds of Cybercrime Acts
Fraud
Phishing
DDoS Attack
Hacking
Identity Theft
Child Pornography
Cyber bullying
Scamming
Malvertising
Social Engineering
Software Piracy
Cybercrime can be classified into two types
Cybercrime is usually targeted by the Federal Bureau of Investigations (FBI).
(i) Transmitting, targeting, or gaining access to a computer or network for a separate purpose — such as criminal theft of private information. (ii) Obtaining a separate purpose from the computer system.
(2) Computer-related crimes, such as data theft or damage to computers.
As a result, the FBI has authority to examine both interstate as well cross national and, which divides interstate and international boundaries.
Federal Statutes on Cybercrime
There was a declaration of the first federal law addrpassed.bercrime. The Computer Fraud and Abuse Act (CFAA) was the administration’s acknowledgement of early computer hackingandter fraud fraud incidents that directly the United States government.
The CFAA aims to prevent private government data or knowledge essential to national security from being illegally accessed and controlled over computers.
A wide range of appas applications of the CFAA have expanded over time. The broad wording of the law has been used by the federal government and prosecutors to go after the growing types of supreme court lawyer in delhi.
Best Cyber Crime Lawyers
Anil Varma
Ankita Varma
Source:- https://avlegalalliance.com/view_blog.php?link=here-are-the-best-cybercrime-lawyers-who-will-actually-improve-your-life
0 notes
Text
Stopping Foreclosure In Utah

Before the foreclosure crisis, which peaked in 2010, federal and state laws regulating mortgage servicers and foreclosure procedures were relatively limited and tended to favor foreclosing lenders. Now, however, federal and state laws heavily regulate loan servicing and foreclosure processes. And most of the laws give protections to borrowers.
Servicers generally have to provide borrowers with loss mitigation opportunities, account for each foreclosure step, and strictly comply with foreclosure laws. Also, most people who take out a loan to buy a residential property in Utah sign a promissory note and a deed of trust, which is like a mortgage. These documents give homeowners some contractual rights in addition to federal and state legal protections.
In a Utah foreclosure, you’ll most likely get the right to:
A preforeclosure notice
Apply for loss mitigation
Receive certain foreclosure notices
Get current on the loan and stop the foreclosure sale
Receive special protections if you’re in the military
Pay off the loan to prevent a sale
File for bankruptcy, and
Get any excess money after a foreclosure sale.
So, don’t get caught off guard if you’re a Utah homeowner who’s behind in mortgage payments. Learn about each step in a Utah foreclosure, from missing your first payment to a foreclosure sale. Once you understand the process, you can make the most of your situation and, hopefully, work out a way to save your home or at least get through the process with as little anxiety as possible.
What Is Preforeclosure?
The period after you fall behind in payments, but before a foreclosure officially starts, is generally called the “preforeclosure” stage. (Sometimes, people refer to the period before a foreclosure sale actually happens as “preforeclosure,” too.) During this time, the servicer can charge you various fees, like late charges and inspection fees, and, in most cases, must inform you about ways to avoid foreclosure and send you a preforeclosure notice called a “breach letter.”
Fees the Servicer Can Charge During Preforeclosure
If you miss a payment, most loans include a grace period of ten or fifteen days, after which time the servicer will assess a late fee. Each month you miss a payment, the servicer will charge this fee. To find out the late charge amount and grace period for your loan, look at the promissory note you signed. You can also find this information on your monthly mortgage statement.
Also, most Utah deeds of trust allow the lender (or the current loan holder, referred to as the “lender” in this article) to take necessary steps to protect its interest in the property. Property inspections are performed to ensure that the home is occupied and appropriately maintained. Inspections, which are generally drive-by, are usually ordered automatically once the loan goes into default and typically cost around $10 or $15.
Other types of fees the servicer might charge include those for broker’s price opinions, which are like appraisals and property preservation costs, such as for yard maintenance or winterizing an abandoned home.
Federal Mortgage Servicing Laws and Foreclosure Protections
Under federal mortgage servicing laws, the servicer must contact, or attempt to contact, you by phone to discuss loss mitigation options, like a loan modification, forbearance, or repayment plan, no later than 36 days after you miss a payment and again within 36 days after each following delinquency. No later than 45 days after missing a payment, the servicer has to inform you in writing about loss mitigation options that might be available and appoint personnel to help you try to work out a way to avoid foreclosure. A few exceptions are in place for some of these requirements, though, like if you’ve filed bankruptcy or asked the servicer not to contact you pursuant to the Fair Debt Collection Practices Act. (12 C.F.R. § 1024.39, 12 C.F.R. § 1024.40).
Federal mortgage servicing laws also prohibit dual tracking (pursuing a foreclosure while a complete loss mitigation application is pending).
What Is a Breach Letter?
Many Utah deeds of trust have a provision that requires the lender to send a notice, commonly called a “breach letter,” informing you that the loan is in default before the lender can accelerate the loan. The breach letter gives you a chance to cure the default and avoid foreclosure.
When Can Foreclosure Start?
Under federal law, the servicer usually can’t officially begin a foreclosure until you’re more than 120 days past due on payments, subject to a few exceptions. (12 C.F.R. § 1024.41). This 120-day period provides most homeowners with ample opportunity to submit a loss mitigation application to the servicer.
What Is the Foreclosure Process in Utah?
If you default on your mortgage payments in Utah, the lender may foreclose using a judicial or non-judicial method.
How Judicial Foreclosures Work
A judicial foreclosure begins when the lender files a lawsuit asking a court for an order allowing a foreclosure sale. If you don’t respond with a written answer, the lender will automatically win the case. But if you choose to defend the foreclosure lawsuit, the court will review the evidence and determine the winner.
If the lender wins, the judge will enter a judgment and order your home sold at auction.
How Non-judicial Foreclosures Work
If the lender chooses a non-judicial foreclosure, it must complete the out-of-court procedures described in the state statutes. After completing the required steps, the lender can sell the home at a foreclosure sale. Most lenders opt to use the non-judicial process because it’s quicker and cheaper than litigating the matter in court.
Preforeclosure Requirements Under Utah Law
Much like the requirement under federal mortgage servicing laws, after determining that the loan is in default, the servicer or lender must appoint single point of contact who can provide information about the foreclosure and foreclosure relief. (Utah Code Ann. § 57-1-24.3).
Before filing a notice of default, the lender or servicer must mail a notice to you (the borrower) giving you at least 30 days to cure the default by getting current on the loan. The letter will also include the name, telephone number, email address, and mailing address of the single point of contact. (Utah Code Ann. § 57-1-24.3). This information will likely be included in the breach letter.
Notice of Default
The non-judicial foreclosure process formally begins when the trustee records a notice of default at the county recorder’s office. The notice of default gives you three months to cure the default. (Utah Code Ann. § 57-1-24).
Within ten days of the recording, the trustee mails a copy of the notice of default to anyone who has requested a copy. Most deeds of trust in Utah include a request for notice, so you’ll probably get this notification. (Utah Code Ann. § 57-1-26(2)(a)).
Notice of Sale
If you don’t cure the default, after three months, the trustee will record a notice of sale and:
Mail a copy to you at least 20 days before the sale (if your deed of trust includes a request for notice, which it probably does)
Publish notice of the sale in a newspaper, and
Post notice about the sale on the property at least 20 days before the sale. (Utah Code Ann. § 57-1-26(2)(b), § 57-1-25).
The Foreclosure Sale
At the sale, the lender usually makes a credit bid. The lender can bid up to the total amount owed, including fees and costs, or it may bid less. In some states, including Utah, when the lender is the high bidder at the sale but bids less than the total debt, it can get a deficiency judgment against the borrower, subject to some limitations. If the lender is the highest bidder, the property becomes what’s called “Real Estate Owned” (REO).
But if a bidder, say a third party, is the highest bidder and offers more than you owe, and the sale results in excess proceeds—that is, money over and above what’s needed to pay off all the liens on your property—you’re entitled to that surplus money.
How Long Do You Have to Move Out After Foreclosure in Utah?
If you don’t vacate the property following the foreclosure sale, the new owner will probably:
Offer you a cash-for-keys deal, or
Take steps to evict you.
The eviction process starts with a notice to quit. If you still don’t leave by the deadline given in the notice, the new owner will go through the court system to evict you. (Utah Code Ann. § 78B-6-802.5).
HOW CAN I STOP A FORECLOSURE IN UTAH?
A few potential ways to stop a foreclosure include reinstating the loan, redeeming the property before the sale, or filing for bankruptcy. (Of course, if you’re able to work out a loss mitigation option, like a loan modification, that will also stop a foreclosure.)
Reinstating the Loan
Utah law gives you three months after the trustee records the notice of default to reinstate the loan. (Utah Code Ann. § 57-1-31). Also, the deed of trust might give you more time to reinstate. Check the paperwork you signed when you took out the loan to find out if you get more time to get caught up on past-due amounts and, if so, the deadline to reinstate. You can also call your loan servicer and ask if the lender will let you reinstate.
Redeeming the Property before the Sale
One way to stop a foreclosure is by “redeeming” the property. To redeem, you have to pay off the full amount of the loan before the foreclosure sale.
Some states also provide foreclosed borrowers with a redemption period after the foreclosure sale, during which they can buy back the home. Under Utah law, however, foreclosed homeowners don’t get a right of redemption after a non-judicial foreclosure. (Utah Code Ann. § 57-1-28(3)).
Filing for Bankruptcy
If you’re facing a foreclosure, filing for bankruptcy might help. In fact, if a foreclosure sale is scheduled to occur in the next day or so, the best way to stop the sale immediately is by filing for bankruptcy. Once you file for bankruptcy, something called an “automatic stay” goes into effect. The stay functions as an injunction, which prohibits the lender from foreclosing on your home or otherwise trying to collect its debt, at least temporarily.
In many cases, filing for Chapter 7 bankruptcy can delay the foreclosure by a matter of months. Or, if you want to save your home, filing for Chapter 13 bankruptcy might be the answer. To find out about the options available to you, speak with a local bankruptcy attorney.
Compromise
If a lender is preparing to foreclose on your home, they will first present you with an NOD, or Notice of Default. They also have to schedule a time for auction for your home. During this in-between period before the auction takes place, know that lenders will almost always work out a financial compromise that will allow you to get back on your mortgage program without foreclosure. Any final compromises you might be able to make should be suggested at that time.
Short Sale
If you receive an offer from a buyer between receiving your NOD and the auction date, the lender must consider it. They may view this option as a time-saver that nets them virtually the same result – after all, they’d already be turning around to re-sell the home anyway. This is called a short sale, and there are plenty of situations where it can work as an acceptable compromise for both sides.
Assumption/Lease-Option
Most loans these days are not assumable, but if you are facing foreclosure, there’s a chance your lender could be willing to modify your loan. They might be willing to allow another buyer to assume your loan if this means less hassle for them – if you can negotiate a down payment from the new buyer that pays off your outstanding balance plus assumes the loan at no additional risk to the lender, everyone wins.
Foreclosure Protections and Military Service members
The Service members Civil Relief Act provides legal protections to military personnel who are in danger of foreclosure.
Utah Deficiency Judgment Laws
In a foreclosure, the borrower’s total mortgage debt sometimes exceeds the foreclosure sale price. The difference between the total debt and the sale price is called a “deficiency.” For example, say the total debt owed is $600,000, but the home sells for $550,000 at the foreclosure sale. The deficiency is $50,000. In some states, the lender can seek a personal judgment against the debtor to recover the deficiency. Generally, once the lender gets a deficiency judgment, the lender may collect this amount—in our example, $50,000—from the borrower.
In Utah, the lender can get a deficiency judgment after a non-judicial foreclosure by filing a lawsuit within three months of the sale. (Utah Code Ann. § 57-1-32). The deficiency amount is limited to the difference between the lesser of :
Your total debt and the property’s fair market value or
Your total debt and the foreclosure sale price. (Utah Code Ann. § 57-1-32).
How to Find State Foreclosure Laws
To find Utah’s laws, search online for “Utah statutes” or “Utah laws.” Make sure you’re reading the most recent, official laws. Usually, the URL will end in “.gov” or the statutes will be on an official state legislature webpage.
Although the programs under the Making Home Affordable (MHA) initiative have expired, the MHA website still contains useful information for homeowners facing foreclosure.
Getting Help
How courts and agencies interpret and apply laws can change. And some rules can even vary within a state. These are just some of the reasons to consider consulting a lawyer if you’re facing a foreclosure. If you have questions about Utah’s foreclosure process or want to learn about potential defenses to a foreclosure and possibly fight the foreclosure in court, consider talking to a foreclosure attorney.
For people struggling with mortgage payments and at risk of default and foreclosure on a home, declaring bankruptcy can be a viable option in some cases. Bankruptcy attorneys can walk you through when declaring and might help save your home and preserve your equity.
Free Initial Consultation with Lawyer
It’s not a matter of if, it’s a matter of when. Legal problems come to everyone. Whether it’s your son who gets in a car wreck, your uncle who loses his job and needs to file for bankruptcy, your sister’s brother who’s getting divorced, or a grandparent that passes away without a will -all of us have legal issues and questions that arise. So when you have a law question, call Ascent Law for your free consultation (801) 676-5506. We want to help you!

Ascent Law LLC
8833 S. Redwood Road, Suite C
West Jordan, Utah
84088 United States
Telephone: (801) 676-5506 Ascent Law LLC 4.9 stars – based on 67 reviews
1 note
·
View note
Text
Shadow Net Series 27: All the World’s a Stage Part One: Interested in You, Interested in You, Intere-
Shadow Net Series 27: All the World’s a Stage Part One: Interested in You, Interested in You, Intere-
A website that displays all currently unprotected and open webcams across the web in real time and the database we all bunk in together already.
The other day I was having a conversation with a fellow blogger about writing. I had been following their work for a couple months now and admired how honest they were about their own life experiences thus far. It seems honesty is a finite resource in…

View On WordPress
#America#big tech#bloggers#corporate#corporations#Crime#culture#cyber#cyber crime#cyber culture#cybersecurity#government#internet#law enforcement#police#safety#security
1 note
·
View note
Note
i’m curious what your opinion is on the finer points of the case mentioned in the JSTOR post you reblogged earlier. the two sources in the post say that JSTOR didn’t press charges against him and had already settled with him by the time he killed himself. from what i read on wikipedia, the concern seems to be that JSTOR complied with a subpoena, which i don’t believe they have a choice to ignore? if anything it seems like the us government had reason to want him dead for wikileaks and public court records reasons, so they took a terms of use violation and blew it up into a dozen federal crimes.
is there more context i should be aware of? i have no particular affection or malice for JSTOR but the sources i found don’t exactly implicate the database or its employees in murder.
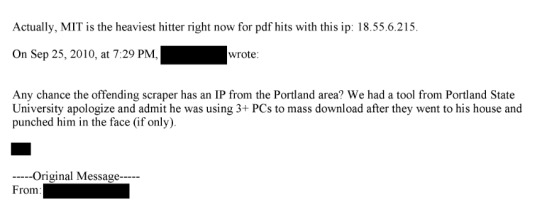


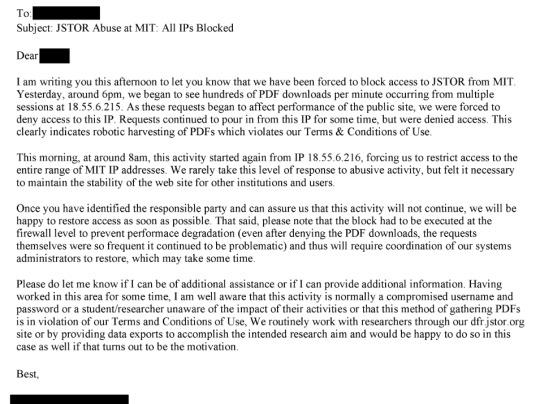
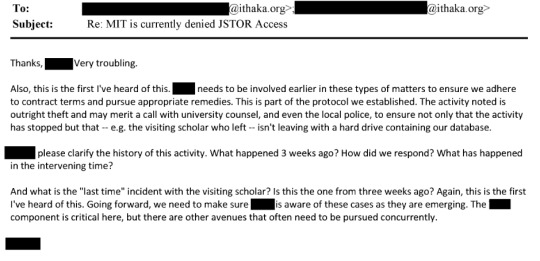
That's from page 175 of this document. This line: "The activity noted is outright theft and may merit a call with university counsel, and even the local police, to ensure not only that the activity has stopped but that - e.g. the visiting scholar who left - isn't leaving with a hard drive containing our database" is where I think the culpability starts.

If someone is downloading 1000s of articles (what seems like reasonable threshold for us to take action), what's wrong with us - or the university in collaboration with us - alerting the cyber-crimes division of law enforcement and initiating an investigation, having cop search dorm room and try to retrieve any hard drive that contains our content, etc. Our content is extraordinarily valuable and hard to replicate by the sweat of one's brow, but can be duplicated by savvy hackers and who knows what they want to do with the content?
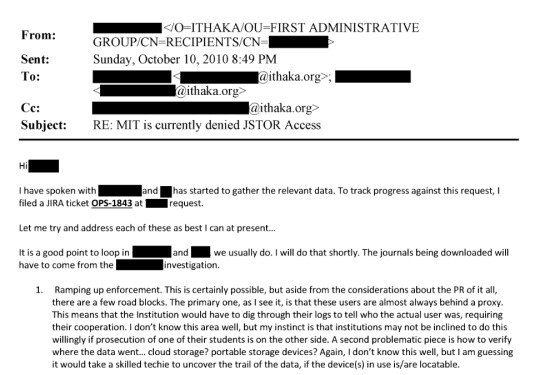


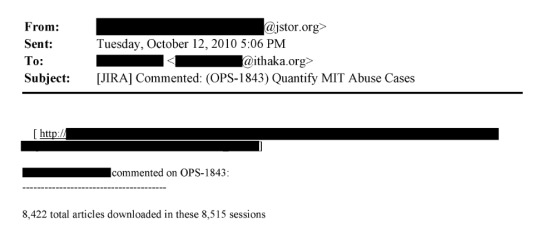
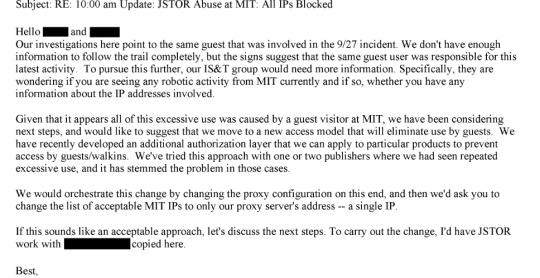
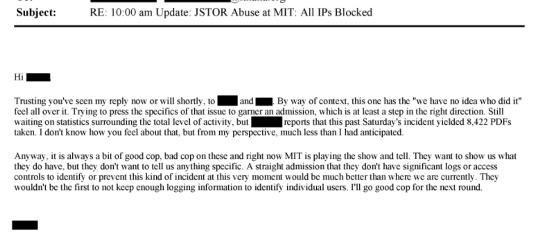


Page 379: "Does the university contact law enforcement? Would they be willing to do so in this instance?




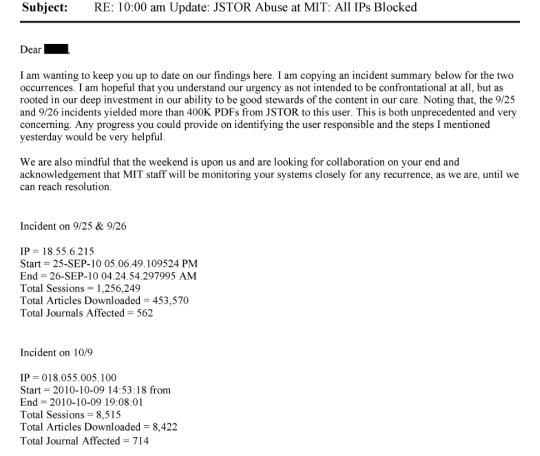
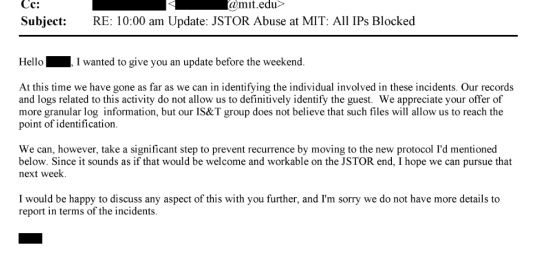



From page 1296:

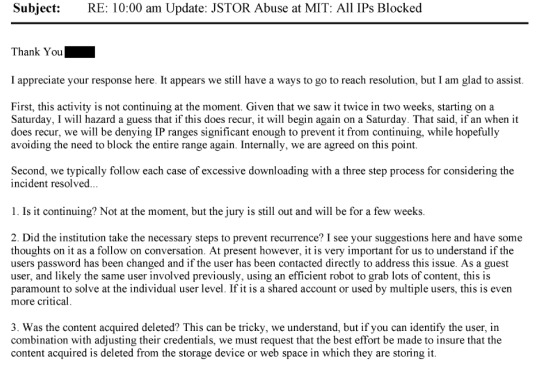
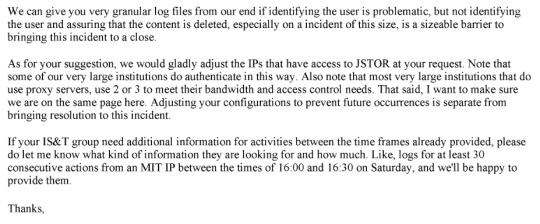
I think the important thing to note here is that JSTOR had worked with MIT and had plans in place to prevent future similar downloads, but remained focused on identifying the person responsible for the downloads and ensuring that their data was deleted.

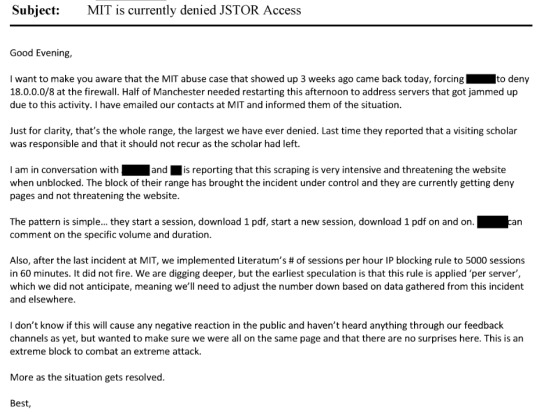
"I might just be irked because I am up dealing with this person on a Sunday night, but I am starting to feel like they need to get a hold of this situation right away or we need to offer to send them some help (read FBI).
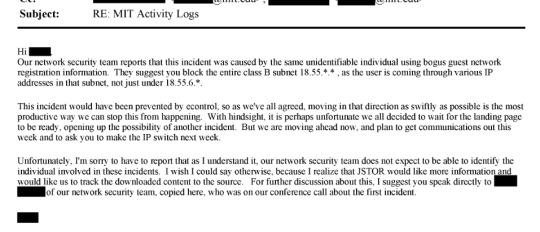
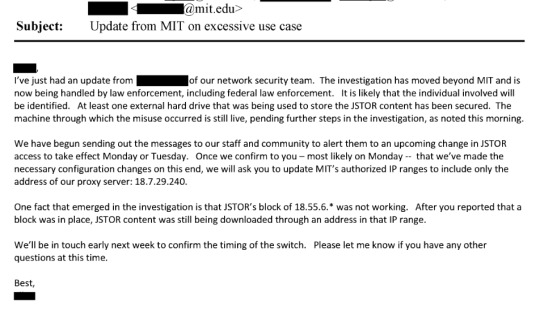
And there it is. Page 3093 of the document.
JSTOR can hem and haw about it all they want, but you can't un-call the cops.
MIT was working with JSTOR on preventing future incidents of pirating, but JSTOR repeatedly said that they weren't going to let it go, that it was unacceptable to drop the issue, that they were going to continue to pursue the pirate.
You can scroll through the document and see the JSTOR tech department and abuse team talking about Swartz as a script kiddie, and a hacker. You can see someone talking about how this was real theft - making the comparison to stealing books even while admitting that piracy doesn't close others out of access.
You can see the thread starts with a joke about punching someone in the face for hacking their system, and includes the tech team ominously considering whether they should threaten the MIT librarians with the FBI.
There's something really important to note here which I don't think that people who aren't PRETTY DEEP into hackery shit aren't aware of: US law enforcement is absolutely rabidly feral about prosecuting hackers. People may be more aware of this now because of Chelsea Manning and Edward Snowden (and perhaps a bit on tumblr because of maia arson crimew), but people who work in tech and who are in infosec - like the people joking about calling the FBI in these emails - would be aware of the bonkers disproportionate punishments faced by hackers. And knowing that, they kept pushing and pushing and pushing for identification of the hacker. They kept digging with MIT, they kept saying that simply preventing future incidents wasn't enough.
Early in the exchange someone from JSTOR asked "what's wrong with us - or the university in collaboration with us - alerting the cyber-crimes division of law enforcement and initiating an investigation, having cop search dorm room and try to retrieve any hard drive that contains our content, etc." and the answer is what happened to Aaron Swartz.
It is absolute bullshit for JSTOR to say "we arrived at a solution privately and didn't want to press charges" after law enforcement has gotten involved with a hacking case, especially one where they're talking about "real theft" and are attempting to quantify and emphasize the amount that was "stolen" from them.
The *public* may believe that private individuals or institutions are the ones who "press charges" but that's simply not the case. It's prosecutors who decide whether or not to go ahead with charges; they do it based on what cases they think they can win and what their office's perspective is on the crime. When you hear about people choosing to press charges it simply means that they decided to tell the prosecutor they wanted the case to go forward. It's up to the prosecutor whether or not that happens.
And the tech team at JSTOR had to know that law enforcement wasn't just going to wag a finger at an academic hacker.
There's a parallel here that happens sometimes when people have their identities stolen by their parents. If you mom takes out a credit card in your name, that's identity theft. That's fraud. That's illegal. If you reach the age of 25 and realize that your credit is ruined because your mom has been defaulting on cards in your name, you've got two choices to fix that: one is to accept the debt and pay it off and build up credit, and the other is to report the identity theft - which will end up with your mom in prison for a decade or so. Ruin your own personal finances, or your mom goes to jail for ruining your finances. So if you find out that your mom stole your identity you can't just call the cops to pressure her into transferring the debt to her name or something. That's not an option. The cops are not a threat to wave over people, they are not a way to get people to fall in line or act right. They aren't someone you can send to a college student's dorm room to retrieve a hard drive and have the matter drop.
When you call the cops on someone you are sending the full force of the law after them, and the full force of the law falls really heavily on hackers, and how heavy that blow can be is something that the JSTOR team must have been aware of when they were making snide comments about calling the FBI because they were frustrated with the noncommittal responses they were getting from librarians.
Ultimately it was the carceral state that killed Aaron Swartz, but they would not have been involved if JSTOR didn't think that what he did constituted theft.
Taking an *EVEN LARGER* step back from that, the idea that information can be owned and locked behind a paywall is what killed Aaron Swartz, someone who fought for information to be free.
Like. JSTOR is a licensing company. At the end of the day, cute social media posts and all, they're the same as the RIAA and ASCAB. They exist to extract a fee from people attempting to access information.
Aaron Swartz and all that he stood for are an existential threat to their core function.
Are JSTOR's hands as dirty as the federal prosecutors? Absolutely not. But they operate on a model that puts them in opposition to open information activists and it ended up with a hammer falling on Aaron Swartz that they dropped.
2K notes
·
View notes
Text
Bettering technology has eased the lifestyle of the people. At the same time, the technical advancements have also caused some critical issues and risks for the users. Falling victim to internet fraud is a harrowing experience, and seeking legal representation is crucial for a successful resolution. However, engaging an Internet fraud lawyer comes with its pitfalls.
Web 2.0: Click Here
0 notes