#bulk IP addresses
Link
Bulk GEO IP Locator - Find Geolocation Data for Multiple IPs
#ip checker#ip locator#geo ip#bulk IP addresses#Bulk GEO IP Locator#geolocation data#multiple IPs#IP lookup#geolocation tool#IP geolocation#IP address location
0 notes
Text
#track ip address website visitors#location based api#global IP database services worldwide#bulk ip address location services#how to get geolocation#ip address hostname lookup#what is my ip
0 notes
Note
Re: your post about genre limitations of D&D
There was like a ton of d20 games back then, from browsing forums it feels like half of genres and IPs got their d20 book printed, and the other half got some homebrew.
Did it carry the genre implications of D&D itself? Was it something subtle or did it straight up feel like reskinned D&D? If yes, is this because the implications are that deep mechanically, or simply because the authors didn't do enough hacking?
The thing you need to understand about the d20 System renaissance is that the overwhelming majority of licensed d20 System games genuinely do not give a shit whether Dungeons & Dragons is a good fit for them or not. Indeed, many were created with the explicit understanding that it isn't, and no intention of trying to address that in any way. The bulk of such adaptations exist for one of two reasons:
The author and/or IP owner wanted to publish a worldbuilding bible for their setting (or, in the case of a television franchise, an episode guide), but getting people to pay money for a worldbuilding bible or episode guide is hard. However, if you take that exact same worldbuilding bible, staple some game mechanics to the side of it, and call it a licensed RPG, nerds will line up to buy it. Most worldbuilding-bibles-pretending-to-be-RPGs use the d20 System because the OGL allows you to copy and paste D&D's rules into your product verbatim, which cuts down on development costs.
A media franchise with an existing tabletop RPG wanted to get a foot in the door with the D&D crowd, so they bashed together a d20 System version of their core rulebook as a marketing gimmick, gambling that some non-zero percentage of D&D players who tried it would be interested enough to check out the non-d20 System game it's adapted from. In this case, the d20 System version doesn't need to be good, or even playable, because its purpose isn't to be played – it just needs to exist.
Hasbro, for their part, encourages all this because it reinforces the popular perception that Dungeons & Dragons can do anything, and that's worth more than the relatively tiny number of players they're likely to poach. The fact that half of them are unplayable copied-and-pasted garbage which exist only for marketing purposes and the other half boil down to logistics-driven dungeon crawling with a thin veneer of the licensed setting painted over it just isn't terribly important.
(To anticipate a variety of inevitable responses, please note that no part of this post remarks on the merits of Dungeons & Dragons as a game; I'm talking about marketing here, not game design.)
826 notes
·
View notes
Text
So Safe and Warm
I don’t know about you guys, but when I finish watching an episode of a show and they roll ads right at the end - if I can - I skip immediately to the next episode, or change the channel, or whatever, I turn off the TV if I’m too tired to watch more episodes.
So, what if I told you there’s an episode in VLD where there’s a “commercial” right at the end, but we’re tempted to skip it, because, well, the bulk of the episode is already over. After all, it’s just an advertisement, like the other silly ones, peppered across the 23 minutes of the episode. Only it’s not so silly.
You probably guessed it - I’m referring to the episode called “The Feud”. Right at the end, after Bob says goodbye, the Paladins wake up, Coran tells them Bob is an all-powerful inter-dimensional being, after Keith calls Bob a “jerk”, after Lance complains he’s “not that dumb”… right after that, the screen switches to another ad! And I’m not sure I skipped it before, but in any case, I don’t remember it, maybe I just didn’t pay attention to it.
This one is basically not an ad in Bob’s show, because they already got out of there. It’s an ad inside the regular VLD episode; so it’s addressed to us, the real audience, not Bob’s fictional audience. An invitation to Queen Luxia’s underwater kingdom! And just about at the end of the ad, there’s a big group photo with all the pretty merpeople surrounding Luxia, and a big-big illegible text in mer-alphabet pops up above their heads. Supposedly it says something about Luxia’s kingdom.

Only it doesn’t… literally say “Luxia’s Kingdom”.
Check this out:

Does that actually read… A…l…t…e…a?
Holy mackerel!! ”Luxia’s Kingdom” is in fact “Altea”.
What’s also lighting up my bulbs is the similarity between the muscular mer-guys flanking the queen and Lotor’s loyal sentries from the colony. Look at those face masks they wear, the ear designs, that white protruding thing on top of their heads, the large shoulder pads, also - the white pockets!


So, following the good spirit of inserting hidden messages into the episode**, this one tells us not only who is behind all the meddling in VLD (World Events or WEP - see this TPL article by Crystal Rebellion), but it points directly at what we are supposed to know (and which, unsurprisingly, we never found out, because Bob interfered). We’re supposed to go figure out the meaning of the episode “The Depths” - yes, the one with the mermaids, because it basically points to ALTEA. The underwater world of Queen Luxia*** is the hidden colony of Alteans and Lotor is the mer-queen. And we find out that the mer-theories about Luxia are false, the queen was actually one of the good guys after all, and the story has a happy ending. And it’s so safe and warm, you’ll wanna stay forever.
**Another way to emphasize that the creators really meant to insert meaning into that alien alphabet (so it’s not just a random coincidence, we’re not making this up), is to take a look at the other ads inside the episode. Take for instance the Vrepit Sal’s ad - which is easier to figure out. If you rearrange the symbols, it’s really Vrepit (and there might be a little Sal’s, too, but the symbols are too small on my screen to figure them out). The “Terra II” guy is really a piece of cake and there’s no doubt it’s what it says, but if anyone has the time and courage to tackle the techno-babble symbols written underneath in blue… be my guest. It’s intriguing enough that the text starts with “IP”…


*** “The Depths” has been already deciphered by Leakinghate: go read this meta.
#vld meta#lotor#prince lotor#voltron legendary defender#lotor deserved better#The Feud#vld#altea#mermaids#I knew there was something fishy in this episode#jesseblue writes#Initially I titled my meta Something’s Fishy on Altea but I think it sounded awful LOL 😆
26 notes
·
View notes
Text
Marczak and Edwards quickly discovered that the secret messaging window hidden inside Iraniangoals.com could be spotted by simply right-clicking on the page to bring up the website’s coding. This code contained descriptions of secret functions, including the words “message” and “compose” – easily found clues that a messaging capability had been built into the site. The coding for the search bar that triggered the secret messaging software was labeled “password.”
Far from being customized, high-end spycraft, Iraniangoals.com was one of hundreds of websites mass-produced by the CIA to give to its sources, the independent analysts concluded. These rudimentary sites were devoted to topics such as beauty, fitness and entertainment, among them a Star Wars fan page and another for the late American talk show host Johnny Carson.
Each fake website was assigned to only one spy in order to limit exposure of the entire network in case any single agent was captured, two former CIA officials told Reuters.
But the CIA made identifying those sites easy, the independent analysts said. Marczak located more than 350 websites containing the same secret messaging system, all of which have been offline for at least nine years and archived. Edwards confirmed his findings and methodology. Online records they analyzed reveal the hosting space for these front websites was often purchased in bulk by the dozen, often from the same internet providers, on the same server space. The result was that numerical identifiers, or IP addresses, for many of these websites were sequential, much like houses on the same street
10 notes
·
View notes
Text
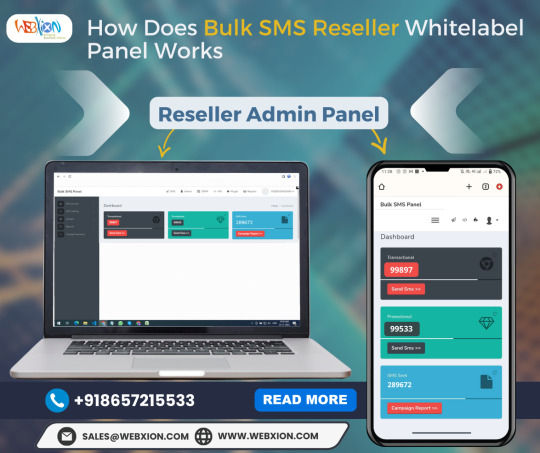
✅How Bulk SMS Reseller Whitelabel Panel Works?
Reseller Bulk SMS Service is a profit-oriented business and can be started with a low investment. To become a reseller there is no documentation. Anyone above 18 can become a Bulk SMS Reseller. As a reseller, you need strong contacts to whom you can sell the credits and make your profit and a service provider who can provide you with credits at the lowest rates.
The most important thing you need as a reseller is a white-label panel. There is no mention of the service provider in such panels so when resellers add users through their accounts, the users never see the owner’s identity and there are no charges to use the panel for both resellers and users.
👉Let us now see how the Bulk SMS Reseller White label panel works:-
🟢There is no documentation for initiating your business as a reseller.
🟢Once you bought the service as a reseller then we will provide you with a white-label service panel with no branding of any company with an IP address.
🟢Resellers can buy as many credits as needed and sell them as per their comfort and generate profit for their business.
🟢They can create as many users in their service panel as our panel can send more than 1 crore SMS daily.
🟢They have to buy 2 separate credits, one for promotion and the other for the transaction.
🟢There is no boundation on buying the credit be it minimum, be it maximum but to get the best rates a reseller has to buy a minimum of 100k credits.
🟢There will always be a support team on your back if any support is needed.
🟢Service panel training will be provided to the dedicated person by our support team.
🟢The Reseller will get their own Admin account in which they can add or remove the users.
🟢There are no additional charges for using the panel or DLT Registration.
To know more about how the Reseller Whitelabel panel works, feel free to connect with us and our expert team will provide you with every expected input.
#bulk sms service#bulk sms#bulk sms marketing reseller panel#Reseller Bulk SMS Service#sms marketing#sms service
3 notes
·
View notes
Text
Now Is The Time To Go Analog
If you are able to become pregnant, and you’re reading this on any of your personal electronic devices, the government knows that you are able to become pregnant. They can look at your search history, what products you’ve purchased, what ads they show you that get the most watch time, etc, and figure that out fairly easily. They also have access to location data from a number of apps you have on said devices at all times. Now should you need to access healthcare in the future, NOW is the time to prepare for that.
Here is a compilation of information that I have seen circulating around from wonderful women/afabs that airs on the utmost side of caution:
1. DELETE PERIOD TRACKER APPS! Yes, even the ones that claim to not sell your data. Never trust a corporation to care about you. They will eventually have to give up your information should a case be filed against you anyway.
2. Track your period instead with a CALENDAR. Yes, a physical calendar. I haven’t used one of those since I was a child, but that’s where we’re at. Learn how to track your cycle, including when you ovulate and when you bleed on paper. If you don’t know how to do this, ideally you should seek information orally in person from a trusted mother figure. If that’s impossible, try to look up how to do it in a public library or on an IP address not tied to you or another person with a uterus.
3. In the event you need healthcare, DO NOT TELL ANYONE! If possible, don’t even tell your friends or family. And for sure don’t leave a digital trail of that. That means no texts, emails, audio messages, phone calls, etc. Move in silence.
4. BURNER PHONE! Buy one. Make sure it has zero affiliation with your identity. That means paying for it with cash too. They can trace your cards. Leave your personal phone that can ping your location at home should you require healthcare.
5. Speaking of which, PAY FOR LITERALLY ANY FEMININE PRODUCTS/SERVICES/TESTS IN. CASH. They can trace your bank account transaction history in the event charges are filed against you. In this way they can also make arguments for when your periods were/when you became pregnant. Even if it’s false.
6. If financially able, BUY PREGNANCY AND OVULATION TESTS IN BULK. These will be cheaper than tests by brands like First Response and you’ll have many on hand. This is especially important if you have a partner who could impregnate you, but you never know when you’ll need them. And it can help with accuracy in tracking your cycle. And we need laser pin point accuracy.
7. If possible, buy a few Plan B’s and keep at least one for you in case of emergencies. The extras? Pass them out to your fellow uterus owners FOR FREE when they need them! NO HOARDING.
Do you have any information to add? If not, can you point out to me if any of this information is incorrect or misleading? In either of these cases, let me know and I will edit the post asap.
#rvw#roe v wade#abortion#abortion is healthcare#reproductive care#reproductive rights#reproductive freedom#womens rights#trans rights#gay rights#right to privacy#roe versus wade
4 notes
·
View notes
Text
geo location ip
More about Bulk GEO IP Locator tool!
Bulk GEO IP Locator tool is here to help you find the city, country, and time zone of one or more IP addresses at a time. When you want to know the location of an IP address you can look online but you may find you get lots of strange results. Use this free IP to location tool and get the right results instantly.
You can check up to 24 different IP addresses via this free Bulk Geo IP Locator Tool and get the results you have been looking for.
This tool will run bulk lookups on input IP addresses or domains. It also will extract IP addresses/domains from the pasted text that can then be then used to run bulk lookups on.
Start by simply inputting IP addresses/domains, or add text and we’ll extract your IPs/domains for you.
We will then run a bulk lookup on that list of IPs/domains for GeoIP, ASN, MX, Blacklist, DNS, Email Provider, and other information.
How can GEO IP Locator help you?
Bulk IP Address lookup and location locator tool. Bulk IP lookup (batch IP checker) is a tool to get the location of multiple IP addresses and their geographic details in one click.
Enter the IP addresses one IP in a and click check to locate all the IPs. This tool can be useful to anyone who wants to check the exact location of people who are using your website, application, etc.
This will help you impress your friends by entering their internet broadband IP and showing them their location.
This bulk IP lookup tool has the capability to pinpoint the location and show you the longitude and latitude GPS coordinates.
You can follow IP to get the exact area with this tool. Geolocation (IP-based) is the mapping of a Mac address or IP address to the geographic area of the real universe of the internet-connected computer or a convenient device.

Check my IP maps and address to a region (city), nation, longitude/latitude, and domain and ISP name in addition to other things. The precision of Geo-area databases may change based on the use of the database. For the IP-to-Country database, Our SEO Tools offers 98 percent to 99 percent exactness.
Geo IP Tracker is essential for you to know the area of prospective web guests. You can trace the area of hackers and spammers on your website.
More about GEO IP Locator Free:
Free Location Finder tool for Bulk GEO IP Locator!:
Bulk IP tracer and location finding technology is a handy tool for you. Mass IP search check is the best strategy within the scope for selecting several IP addresses and their geographical details. Enter one IP address within the greatest IP and select search to look for all IPs. This tool might be useful for anyone who wants you to verify their actual location within those who use your website, application etc. This helps you impress friends by inputting their broadband IP on the internet and then showing them where they are.
This particular Mass IP search tool can pinpoint their location and display your GPS longitude and latitude details.
GEO Ip Technology
IP GEO Location - A sound and forward-thinking concept
Whether sophisticated or not, geo-location IP technologies enable site providers to identify and prosecute abusive individuals anywhere in the world. Individuals have more freedom in the online virtual world than they do in the physical one.
The reason that so many laws is violated via the internet is that persons are less likely to be apprehended online. Until recently, the author was unable to detect authenticity, fraud, copyright violations, and a variety of other issues as easily as in the real world, and the criminal frequently got away with the crime. The IP geolocation has averted disaster and is likely to avert such disasters in the future. Due to security, access, and network efficiency, this location technology is becoming increasingly advantageous and important. Transforming the borderless Internet environment into one in which laws apply similarly to IP geographical locations.
Consider a website with an increasing amount of visits. This website contains information about a large number of clients who utilise their services. No transaction is guaranteed to be secure until customers enter their information online. What if this information turned out to be incorrect? If the customer voluntarily supplies an IP address (through site registration), or if the client does not, the location can be determined with approximate precision using a variety of methods. Online forms, registrations, and more registrations - all of this information may be poured in. Other than IP geolocation, there is no other way to verify legitimacy and legal constraints.
Web operators can detect a person's IP geographical location using a variety of software solutions:
1. Oftentimes, the simplest solution is also the least successful. Looking for the "Whois" information for the Regional International Registry can be a fruitless endeavour. There are five R.I.R.s, each serving a distinct geographic region. The R.I.R.s issue IP addresses to businesses, ISPs, and individuals in their region or area and make the information files available for free download. Numerous individuals have legitimately downloaded records with IP addresses and are now making them available for free on internet databases that you must access. However, these IP geolocation files are not exact and may be ineffective.
2. When it comes to IP geolocation, simple network techniques such as ping, traceroute, and nslookup perform better. A server network can provide a more specific location of an IP address. IP addresses are 'tested' and used throughout the internet by the network to accurately locate only one IP address. Some solution providers use hundreds (thousands) of servers, while others use only ten or twelve.
Ping = Internet Groper Packet (It is also a TCP/IP software package tool that determines whether or not the host is active while determining the round trip latency) (
Tracerout = a debugging tool for determining the path between a local and a remote host.
Nslookup = Name Server Search application (used by TCP/IP to determine the hostname or IP address).
3. While this final category of IP geolocation methods (number 2) is considered to be of moderate efficiency, other solutions employ even more complex technology, such as artificial intelligence and special systems. Additionally, some conduct a more thorough check and comparison of IP addresses and IP geostations.
This relatively complicated subject necessitates familiarity with the ever-changing Internet environment. There are numerous issues to discuss. The rule is that the internet, like every other component of the overall expanding industry, is increasing appeal daily. Because the virtual and physical worlds interact, safety is a concern in both. This is ensured by the IP geolocation system's recognition of genuine identities.
#geolocation ip address lookup#what my geolocation#geolocation ip lookup#ip geolocation#who is ip geo#geo ip location lookup#cars#illustration#drawing#marvel#photography
4 notes
·
View notes
Text
📱 Elevate your browsing experience with Mobile Proxies from Gsocks! 🚀
With the highest 'trust' rating among all proxy types, our Mobile Proxies provide unparalleled access to sophisticated websites. Route your traffic through real mobile IPs, ensuring seamless browsing on smartphones or tablets.
What sets our Mobile Proxies apart?
📶 3G/4G/5G Cellular Networks: Enjoy the highest quality proxies with leading success rates from real mobile carriers.
🔄 Multiple Protocols: Choose from HTTP/HTTPS/SOCKS5 protocols to suit your needs.
🔗 Unlimited Concurrent Connections: Scrape or automate anything with no limit on concurrent connections or threads.
🛡 Immunity From IP Bans: Say goodbye to bulk bans – our Mobile Proxies share no sub-network, ensuring every mobile IP address is 100% unique.
Ready to experience the power of Mobile Proxies? Check out our offerings now! ➡ https://gsocks.net/products/mobile_proxies
0 notes
Text
#bulk ip address location services#how to get geolocation#ip address hostname lookup#what is my ip#free geo api#free ip api#Unlimited website location finder#geolocation API unlimited free use#identify website visitors by IP address
0 notes
Text
where is my vpn showing
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
where is my vpn showing
VPN location display
A VPN, or Virtual Private Network, is a powerful tool that helps safeguard your privacy and security while browsing the internet. One of the key features of VPNs is the ability to change or mask your location, providing added anonymity and protection online.
VPN location display refers to the feature that allows users to choose or change the virtual location displayed to websites and online services. This means that even if you are physically located in one country, you can make it appear as though you are accessing the internet from a different location. This is particularly useful for bypassing geographical restrictions on content, such as accessing region-locked streaming services or websites.
By utilizing the VPN location display feature, users can also enhance their online security and privacy. Changing your virtual location makes it harder for websites and advertisers to track your real location and monitor your online activities. This helps protect sensitive information and reduces the risk of targeted advertising or data tracking.
Moreover, VPN location display can be useful for travelers who want to access content available in their home country while abroad or for individuals wanting to protect their online identity and data from potential cyber threats. It is important to choose a reliable VPN service provider that offers a variety of virtual locations to ensure a seamless and secure browsing experience.
In conclusion, VPN location display is a valuable feature that allows users to enhance their online privacy, security, and accessibility. By leveraging this tool, individuals can enjoy a more unrestricted and protected internet experience.
VPN server location discrepancy
Title: Understanding VPN Server Location Discrepancy: What You Need to Know
When you connect to a Virtual Private Network (VPN), you expect your internet traffic to be routed through servers located in the country you selected. However, sometimes you may encounter a discrepancy between the server location displayed by your VPN provider and the actual location of the server your traffic is routed through. This phenomenon, known as VPN server location discrepancy, can have various implications and understanding its causes is crucial for users.
One common reason for VPN server location discrepancy is the dynamic nature of IP addresses. VPN providers may allocate IP addresses to servers in bulk, and these addresses might not always accurately reflect the physical location of the server. Additionally, VPN servers may be hosted by third-party providers, leading to further discrepancies in server location information.
Another factor contributing to VPN server location discrepancies is network congestion. When VPN servers experience high traffic volumes, providers may reroute traffic through servers in different locations to alleviate congestion and ensure optimal performance. While this practice is intended to improve user experience, it can result in discrepancies between the displayed server location and the actual routing path.
Furthermore, VPN providers may strategically distribute servers in locations with favorable legal or infrastructure conditions, rather than adhering strictly to user-selected locations. This can lead to situations where servers in nearby countries are prioritized over those in the user's selected location, resulting in server location discrepancies.
To mitigate VPN server location discrepancies, users can choose VPN providers with transparent server infrastructure and reliable location reporting. Additionally, regularly testing server connections and monitoring IP geolocation can help identify discrepancies and ensure optimal VPN performance.
In conclusion, VPN server location discrepancies can arise due to various factors such as dynamic IP addressing, network congestion, and strategic server distribution. By understanding the causes of these discrepancies and choosing reputable VPN providers, users can effectively navigate the complexities of VPN server infrastructure and ensure their online privacy and security.
Incorrect VPN geolocation
Incorrect VPN geolocation can be a common issue experienced by users who rely on virtual private networks (VPNs) to protect their online privacy and access geo-restricted content. When using a VPN, the user's internet traffic is routed through servers located in different regions, making it appear as though they are accessing the internet from a different location than their actual one. However, sometimes the geolocation information provided by the VPN may be inaccurate, leading to unexpected outcomes.
One of the main reasons for incorrect VPN geolocation is the misconfiguration of VPN servers. If the server's location database is outdated or not properly maintained, it can result in the wrong geolocation information being assigned to IP addresses. This can cause websites and online services to display content that is meant for a different region, leading to confusion for the user.
Another factor that can contribute to incorrect VPN geolocation is the use of shared IP addresses. Many VPN providers use shared IP addresses to accommodate multiple users on the same server. In some cases, this can lead to situations where the geolocation data associated with the IP address does not match the user's actual location, causing websites to incorrectly identify the user's location.
To mitigate the issue of incorrect VPN geolocation, users can try connecting to different VPN servers to see if the issue persists. Additionally, ensuring that the VPN software is up to date and contacting the VPN provider for support can help resolve any geolocation inaccuracies. By being aware of the potential for incorrect VPN geolocation and taking proactive steps to address it, users can continue to enjoy the benefits of online privacy and access to region-locked content.
VPN IP address misalignment
VPN IP address misalignment occurs when the IP address assigned to your device by the VPN server does not match your actual geographic location. This discrepancy can lead to various issues, including restricted access to certain websites or online services, slower internet speeds, and potential security risks.
One of the primary reasons for VPN IP address misalignment is server overload. When a VPN server becomes overcrowded with users, it may dynamically assign IP addresses that are not geographically accurate. This can result in websites or streaming services detecting your VPN location as being different from your actual location, leading to access restrictions or content limitations.
Another factor contributing to IP address misalignment is the use of shared IP addresses. Many VPN providers offer shared IP addresses to their users, meaning multiple individuals are assigned the same IP address simultaneously. If one of these users engages in suspicious or malicious activities online, it can affect the reputation of the shared IP address, leading to restrictions or security measures being imposed on all users sharing that IP address.
Additionally, technical issues such as DNS leaks or routing errors can also cause IP address misalignment. DNS leaks occur when your device inadvertently sends DNS queries outside of the VPN tunnel, revealing your true IP address and location to websites or online services. Routing errors within the VPN infrastructure can result in traffic being routed through servers in different locations, causing discrepancies between your perceived and actual geographic location.
To mitigate the risks associated with VPN IP address misalignment, users should choose reputable VPN providers that prioritize privacy and security. Additionally, regularly testing for DNS leaks and ensuring proper VPN configuration can help prevent IP address misalignment and safeguard your online anonymity and security.
VPN location mismatch
A VPN location mismatch occurs when the geographical location reported by your device does not match the virtual location provided by the VPN server you are connected to. This discrepancy can lead to various issues and concerns regarding online privacy, security, and content access.
One of the primary reasons for a VPN location mismatch is the misconfiguration of your VPN settings or server issues. When your VPN is not properly set up to route your internet traffic through the intended server location, your actual geographical location might be exposed to websites and online services.
This mismatch could pose a threat to your online privacy and security, as it may reveal your real IP address and sensitive information to third parties. Moreover, it can also impact your ability to access geo-restricted content, as streaming services and websites may block or restrict your access based on your reported location.
To address a VPN location mismatch, you should ensure that your VPN client is configured correctly and that you are connected to a reliable server. Additionally, regularly updating your VPN software and choosing reputable VPN providers can help mitigate such discrepancies and enhance your online security and anonymity.
In conclusion, a VPN location mismatch can undermine the benefits of using a VPN service and compromise your online privacy and security. By understanding the causes and implications of this issue, you can take the necessary steps to ensure that your VPN is effectively concealing your true location and protecting your sensitive data.
0 notes
Photo

Government Oversight Brief: National Summary 》A federal judge has struck down a Biden Administration rule that mandates states track and report greenhouse gas emissions on highways. In 2023, the U.S. Department of Transportation (DOT)’s Federal Highway Administration (FHWA) required state transportation departments and metropolitan planning organizations to measure transportation-related emissions, set reduction standards, and report progress to the federal government. The jud...(CLASSIFIED) 》In Brookings, OG; the city barred a church from serving meals to the homeless, then after "push back", permitted 2 servings per week. The church, St. Timothy's Episcopal Church, sued the city government leading to a judge ruling that the city violated the religious freedom of the church under the First Amendment. The cou...(CLASSIFIED) 》The Department of Justice (DOJ) served a bulk search warrant ordering Google to release personal information (name, account name, IP address, home address, phone number, and viewer activity) of YouTube users who viewed specific YouTube videos (publicly available tutorials on mapping with drones) between January 1st and January 8th, 2023. Surveillance Technology Oversight Project (S.T.O.P.), commented on the recently unsealed court documents that revealed the surveillance effort sa...(CLASSIFIED, get briefs in real-time unredacted by joining at www.graymanbriefing.com)
0 notes
Text

✅ How to Become a Bulk SMS Reseller
promotion and marketing. There are many marketing & advertising agencies, Individual who has a good customer base who is interested in purchasing Bulk SMS Service but they can’t sell SMS service to them because they don’t have a ready setup of Bulk SMS Service.
👉 These kinds of companies and individuals can get a white label panel from a Bulk SMS Service aggregator and sell this service to their customers. Reseller has to purchase SMS credits from aggregator at a discounted price and sell them to their customer.
👉 There are a few companies in the market that offers a Whitelabel reseller panel without any additional cost so reseller can start their business without any investment & sell Bulk SMS service without showing the main service providers name to their existing customer base.
👉To get Bulk SMS white label panel resellers can connect to service providers like WebXion Technologies & ask them for a reseller panel. They provide a reseller panel with a few demo credits. Resellers can access that panel with an IP address; resellers can also mask IP with their sub domain.
👉 To become a reseller there is no complex procedure or documentation required. Reseller simply has to provide their individual identity or company registration documents to activate the reseller panel.
#bulk sms service#bulk sms service gateway#bulk sms marketing reseller panel#bulk sms smpp#bulk sms smpp application#Bulk SMS Service WhiteLabel Panel
3 notes
·
View notes
Text
does open vpn encrypt all traffic
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does open vpn encrypt all traffic
OpenVPN encryption
OpenVPN encryption stands at the forefront of safeguarding online privacy and security. As a robust virtual private network (VPN) protocol, OpenVPN employs a combination of sophisticated encryption algorithms to protect data transmitted over networks, ensuring confidentiality, integrity, and authenticity.
At its core, OpenVPN utilizes the OpenSSL library to implement encryption protocols, including both symmetric and asymmetric encryption. Symmetric encryption, such as Advanced Encryption Standard (AES), is employed for bulk data encryption, offering high-speed performance and efficiency. AES, in particular, is renowned for its strength and is widely adopted across various industries.
Additionally, OpenVPN incorporates asymmetric encryption through the use of public-key cryptography, typically utilizing RSA or Elliptic Curve Cryptography (ECC). This method enables secure key exchange and authentication between parties without the need to share secret keys beforehand. Through asymmetric encryption, OpenVPN establishes secure tunnels, allowing users to transmit data securely over untrusted networks.
Furthermore, OpenVPN supports the use of cryptographic hash functions, such as SHA-256, for data integrity verification. These hash functions generate unique checksums for data packets, enabling recipients to verify if the received data has been tampered with during transmission.
Moreover, OpenVPN offers the flexibility to choose from various encryption cipher suites and key exchange protocols based on security requirements and performance considerations. Users can configure OpenVPN to utilize the most suitable encryption parameters, balancing security with computational overhead.
In conclusion, OpenVPN encryption provides a robust framework for securing online communications, offering a blend of symmetric and asymmetric encryption, along with cryptographic hash functions. By leveraging these technologies, OpenVPN ensures that sensitive data remains protected from unauthorized access and tampering, empowering users to maintain their privacy and security in an increasingly interconnected digital world.
Internet traffic security
Internet traffic security is a critical concern in today's digital landscape, where data breaches and cyber threats loom large. Ensuring the security of internet traffic involves safeguarding the transmission of data between users and servers, preventing unauthorized access, and protecting against various forms of cyberattacks.
One of the fundamental aspects of internet traffic security is encryption. Encryption transforms data into an unreadable format during transmission, making it indecipherable to unauthorized parties. Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols are commonly used to encrypt internet traffic, providing a secure connection between web servers and users' browsers.
Firewalls play a crucial role in internet traffic security by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. They act as a barrier between internal networks and external threats, blocking malicious traffic while allowing legitimate data to pass through.
Virtual Private Networks (VPNs) offer an additional layer of security by creating a private and encrypted connection over a public network, such as the internet. By masking users' IP addresses and encrypting their internet traffic, VPNs help protect sensitive information from interception by cybercriminals or surveillance by third parties.
Implementing strong authentication measures, such as multi-factor authentication (MFA) and biometric verification, further enhances internet traffic security by ensuring that only authorized users can access sensitive data and resources.
Regularly updating software and security patches is essential for maintaining internet traffic security, as it helps address vulnerabilities and weaknesses that could be exploited by cyber attackers.
In conclusion, internet traffic security is paramount for protecting sensitive data and maintaining the integrity of online communications. By employing encryption, firewalls, VPNs, authentication mechanisms, and staying vigilant with software updates, individuals and organizations can mitigate the risks associated with cyber threats and safeguard their online activities.
VPN protocol protection
Title: Safeguard Your Online Privacy with VPN Protocol Protection
In an era where online privacy is increasingly at risk, utilizing a Virtual Private Network (VPN) has become essential. However, not all VPNs are created equal. Understanding VPN protocols and their role in protecting your data is crucial for ensuring your privacy remains intact.
VPN protocols serve as the framework for encrypting and transmitting data between your device and the VPN server. Different protocols offer varying levels of security and speed, catering to diverse user needs.
One of the most common VPN protocols is OpenVPN, renowned for its robust security features and flexibility. It utilizes open-source technology, allowing for regular updates to address emerging threats. OpenVPN employs SSL/TLS encryption, making it highly secure and resistant to cyberattacks.
Another popular protocol is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec provides strong encryption and authentication, ensuring data integrity and confidentiality. It's often used in conjunction with other protocols to enhance security.
For those prioritizing speed without compromising security, L2TP/IPSec (Layer 2 Tunneling Protocol with Internet Protocol Security) is an excellent choice. While it may not offer the same level of encryption as other protocols, it delivers faster performance, making it ideal for streaming and gaming.
IKEv2 (Internet Key Exchange version 2) is another protocol known for its speed and reliability, particularly on mobile devices. It seamlessly handles network changes, such as switching between Wi-Fi and mobile data, without interrupting the VPN connection.
Regardless of the protocol you choose, ensuring it supports strong encryption standards is paramount. Look for VPN providers that offer a variety of protocols and prioritize security to safeguard your online activities effectively. By understanding VPN protocols and selecting the right one for your needs, you can enjoy enhanced privacy and security in an increasingly interconnected digital landscape.
Data encryption methods
Data encryption is a crucial aspect of cybersecurity, aiming to protect sensitive information from unauthorized access or cyber attacks. There are various data encryption methods available to secure data and ensure confidentiality and integrity.
One of the most common encryption techniques is symmetric key encryption, where the same secret key is used for both encryption and decryption of the data. This method is efficient and fast, making it suitable for securing large volumes of data. However, the challenge lies in securely sharing the secret key between the communicating parties.
Asymmetric key encryption, also known as public-key encryption, uses a pair of keys - a public key for encryption and a private key for decryption. This method eliminates the need to share secret keys, making it more secure for data transmission over untrusted networks. Although asymmetric encryption is more secure, it is computationally intensive and slower compared to symmetric encryption.
Hashing is another essential encryption method used to validate the integrity of data. Hash functions generate a unique fixed-length hash value from the input data, making it ideal for verifying data authenticity and detecting tampering. However, hashing is a one-way process, making it unsuitable for decrypting data.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols are encryption methods commonly used to establish secure communication channels over the internet. These protocols encrypt data during transmission, ensuring that sensitive information remains confidential and secure from eavesdroppers.
In conclusion, data encryption methods play a vital role in safeguarding sensitive information from unauthorized access and cyber threats. Organizations must implement robust encryption techniques to protect their data and maintain data privacy and security.
Secure traffic encryption
In the digital age, ensuring the security of online communications is paramount. One of the most effective measures to achieve this is through secure traffic encryption.
Secure traffic encryption involves encoding data transmitted between a user's device and a server, making it unreadable to anyone who might intercept it. This encryption is typically implemented using cryptographic protocols such as SSL (Secure Sockets Layer) or its successor, TLS (Transport Layer Security).
SSL and TLS use a combination of symmetric and asymmetric encryption techniques to secure data transmission. Symmetric encryption employs a single key to both encrypt and decrypt data, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption. This dual-key system enhances security by ensuring that even if the public key is intercepted, the private key, which is kept secret, is required to decrypt the data.
When a user accesses a website with HTTPS (Hypertext Transfer Protocol Secure), their browser and the server engage in a handshake process to establish a secure connection using SSL or TLS. During this process, they negotiate encryption parameters, exchange cryptographic keys, and verify the authenticity of the server's digital certificate.
Once the secure connection is established, all data transmitted between the user and the server – including login credentials, financial information, and personal details – is encrypted, protecting it from eavesdropping and tampering.
Secure traffic encryption is essential for safeguarding sensitive information and maintaining user privacy in an increasingly interconnected world. By encrypting data in transit, organizations can mitigate the risk of data breaches, identity theft, and unauthorized access, enhancing trust and confidence among their users.
0 notes
Text
does the government track vpn users
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does the government track vpn users
VPN encryption technology
VPN encryption technology plays a crucial role in ensuring the security and privacy of online activities. VPN, which stands for Virtual Private Network, creates a secure and encrypted connection between a user's device and the internet. This encryption technology works by converting data into a code that is unreadable without the appropriate decryption key.
One of the key benefits of VPN encryption technology is its ability to protect sensitive information from cyber threats such as hackers, identity thieves, and government surveillance. By encrypting data, VPNs make it nearly impossible for unauthorized parties to intercept and decipher the information being transmitted. This is especially important when using public Wi-Fi networks, where personal data is more vulnerable to security breaches.
Furthermore, VPN encryption technology allows users to bypass censorship and geo-blocks by masking their IP address and location. This enables individuals to access restricted content and websites, as well as enhance their online anonymity and privacy.
There are several encryption protocols used in VPN technology, including OpenVPN, L2TP/IPsec, SSTP, and IKEv2. These protocols offer varying levels of security and performance, giving users the flexibility to choose the one that best suits their needs.
In conclusion, VPN encryption technology is a powerful tool for safeguarding online activities and maintaining privacy in an increasingly digital world. By utilizing encryption protocols, users can enjoy a secure and unrestricted internet experience while protecting their sensitive information from prying eyes.
Government surveillance measures
Title: Understanding Government Surveillance Measures: Balancing Security and Privacy
Government surveillance measures have become a topic of intense debate, particularly in the digital age where technology enables unprecedented access to personal information. While these measures are often implemented with the intention of enhancing national security and preventing threats, they also raise significant concerns about privacy rights and civil liberties.
One of the most contentious aspects of government surveillance is the collection of mass data through programs such as mass surveillance programs, data mining, and metadata analysis. These practices involve the bulk collection of communications data, including emails, phone calls, and internet browsing history, often without individualized suspicion. While proponents argue that such measures are necessary to identify and thwart potential threats, critics contend that they constitute a gross violation of privacy rights and can lead to abuses of power.
Another area of concern is the use of surveillance technologies, including CCTV cameras, facial recognition systems, and biometric databases. While these technologies can be valuable tools for law enforcement in combating crime and terrorism, they also raise significant ethical and privacy concerns. For example, facial recognition technology has been criticized for its potential to infringe on individuals' rights to anonymity and freedom of movement, as well as its propensity for racial and gender bias.
In response to these concerns, there have been calls for greater transparency and oversight of government surveillance programs. Many civil liberties advocates argue that there needs to be more robust legal frameworks in place to ensure that surveillance measures are subject to judicial review and oversight. Additionally, there have been efforts to enhance privacy protections through measures such as encryption and anonymization techniques.
Ultimately, the debate surrounding government surveillance measures reflects a delicate balance between security and privacy. While it is essential to safeguard national security interests, it is equally important to uphold individual rights and freedoms. Achieving this balance requires thoughtful consideration of the ethical, legal, and societal implications of surveillance practices, as well as ongoing dialogue and engagement between policymakers, technology experts, and civil society stakeholders.
Internet privacy laws
Title: Navigating the Maze: Understanding Internet Privacy Laws
In the digital age, where every click and keystroke leaves a trail, internet privacy has become a paramount concern. To safeguard users' personal information from exploitation and misuse, governments around the world have enacted internet privacy laws. These regulations aim to strike a delicate balance between protecting individual privacy rights and enabling legitimate data use for business and innovation.
One of the most significant pieces of legislation in this domain is the General Data Protection Regulation (GDPR), implemented by the European Union (EU) in 2018. GDPR empowers individuals with greater control over their personal data, requiring businesses to obtain explicit consent for data collection and processing. It also mandates stringent measures for data security and imposes hefty fines for non-compliance.
Similarly, the California Consumer Privacy Act (CCPA), enacted in 2020, grants California residents enhanced rights regarding their personal information. Under CCPA, consumers can demand to know what data is being collected about them and have the right to opt-out of the sale of their data to third parties.
Beyond these, various countries have crafted their own internet privacy laws tailored to their unique legal frameworks and cultural contexts. For instance, Brazil's Lei Geral de Proteção de Dados (LGPD) and India's Personal Data Protection Bill (PDPB) aim to regulate data processing activities within their jurisdictions.
Despite these advancements, challenges persist in ensuring comprehensive internet privacy protection. The rapid pace of technological innovation often outpaces regulatory efforts, leaving gaps in coverage. Moreover, the global nature of the internet raises jurisdictional issues, making enforcement complex across borders.
As technology continues to evolve, so too must internet privacy laws. Striking a balance between innovation and protection remains an ongoing challenge, requiring collaboration between governments, businesses, and civil society to uphold the fundamental right to privacy in the digital era.
Online anonymity tools
Title: Exploring the Benefits of Online Anonymity Tools
In today's digital age, concerns about online privacy and security have become increasingly prevalent. With the rise of cyber threats and data breaches, individuals are seeking ways to protect their online identities and activities. One effective solution that has gained popularity is the use of online anonymity tools.
Online anonymity tools, such as virtual private networks (VPNs), Tor browser, and encrypted messaging apps, offer users a secure way to browse the internet and communicate without revealing their true identities or locations. These tools work by encrypting internet traffic and masking IP addresses, making it difficult for third parties to track users' online activities.
One of the primary benefits of using online anonymity tools is enhanced privacy protection. By hiding their IP addresses, users can prevent websites, advertisers, and even government agencies from tracking their online behavior. This not only protects users from targeted advertising and unwanted surveillance but also helps safeguard sensitive information such as financial data and personal messages.
Moreover, online anonymity tools enable users to bypass censorship and access restricted content. In countries where internet freedom is limited, tools like VPNs and Tor browser allow individuals to circumvent government-imposed restrictions and access blocked websites and social media platforms.
Additionally, these tools can help prevent identity theft and fraud by keeping users' personal information secure. By encrypting data transmissions and anonymizing online activities, anonymity tools make it significantly harder for hackers and cybercriminals to intercept sensitive information or steal login credentials.
In conclusion, online anonymity tools play a crucial role in safeguarding individuals' privacy and security in an increasingly connected world. By utilizing these tools, users can browse the internet with confidence, knowing that their online activities are protected from prying eyes and potential threats.
User data protection laws
User data protection laws are essential in today's digital age to safeguard personal information and ensure privacy for individuals online. These laws govern how organizations collect, store, and utilize user data to prevent its misuse and unauthorized access.
One prominent example of user data protection laws is the General Data Protection Regulation (GDPR) implemented by the European Union. The GDPR sets strict guidelines for businesses operating within the EU or handling the personal data of EU citizens. It requires organizations to obtain explicit consent before collecting user data, disclose the purposes for which data is being collected, and implement robust security measures to safeguard this information.
In the United States, the California Consumer Privacy Act (CCPA) is another significant legislation aimed at protecting user data. The CCPA grants California residents the right to know what personal information is being collected about them, the right to opt-out of the sale of their data, and the right to request the deletion of their information from company databases.
User data protection laws are crucial for maintaining trust between consumers and businesses. By ensuring that personal information is handled responsibly and securely, these laws help prevent data breaches, identity theft, and other forms of cybercrime. Organizations that fail to comply with data protection laws may face severe penalties, including hefty fines and damage to their reputation.
In conclusion, user data protection laws play a vital role in safeguarding individuals' privacy in the digital landscape. It is crucial for businesses to uphold these laws and prioritize user data security to build trust with their customers and avoid legal consequences.
0 notes
Text
does a vpn protect you from the government
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn protect you from the government
VPN encryption
Title: Understanding VPN Encryption: Safeguarding Your Online Privacy
In the digital era where cyber threats loom large, safeguarding your online privacy is paramount. Virtual Private Networks (VPNs) have emerged as indispensable tools for securing internet connections, and at the heart of their functionality lies encryption.
VPN encryption is the process of encoding data transmitted between your device and the VPN server, ensuring that it remains secure and inaccessible to unauthorized entities. This encryption works by scrambling the data into a format that can only be deciphered with the appropriate decryption key, effectively creating a secure tunnel through which your information travels.
There are several encryption protocols utilized by VPN providers, each offering varying levels of security and performance. The most commonly used protocols include OpenVPN, L2TP/IPsec, IKEv2/IPsec, and SSTP, among others. OpenVPN, renowned for its open-source nature and robust security features, is widely regarded as one of the most secure protocols available.
Furthermore, VPN encryption operates on different cipher algorithms, such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), which further enhance security by determining how data is encrypted and decrypted.
By employing VPN encryption, users can enjoy numerous benefits, including:
Privacy Protection: VPN encryption shields your online activities from prying eyes, preventing ISPs, hackers, and government agencies from intercepting and monitoring your internet traffic.
Data Security: Encryption safeguards sensitive information, such as passwords, financial details, and personal communications, from potential breaches and cyber attacks.
Access to Restricted Content: VPN encryption allows users to bypass geo-restrictions and censorship measures by masking their IP addresses, granting access to region-locked content and websites.
Secure Remote Access: Businesses utilize VPN encryption to establish secure connections for remote workers, ensuring the confidentiality of corporate data and communications.
In conclusion, VPN encryption is a fundamental component of online security, providing users with peace of mind and the assurance that their digital footprint remains private and secure. By understanding the importance of encryption protocols and choosing reputable VPN services, individuals can fortify their defenses against cyber threats and enjoy a safer online experience.
Government surveillance
Government surveillance, the practice of monitoring citizens' activities, has become a contentious issue in modern society. While proponents argue that it enhances national security and helps prevent crime, opponents raise concerns about invasion of privacy and potential abuse of power.
One of the main arguments in favor of government surveillance is its role in combating terrorism and crime. Surveillance programs allow authorities to track suspicious individuals and prevent potential threats before they materialize. For example, monitoring communication channels can help uncover terrorist plots or criminal activities, potentially saving lives and maintaining public safety.
Moreover, proponents argue that surveillance is essential for maintaining social order and protecting national interests. By monitoring online activities, governments can detect and counteract cyber threats, safeguarding critical infrastructure and sensitive information from malicious actors.
However, opponents of government surveillance highlight the erosion of privacy rights and civil liberties. Mass surveillance programs, such as bulk data collection and indiscriminate monitoring, raise concerns about the extent to which individuals' privacy is violated. Critics argue that constant surveillance creates a culture of fear and stifles free expression, undermining democratic principles.
Furthermore, there are concerns about the potential misuse of surveillance powers by authorities. Without adequate oversight and accountability mechanisms, surveillance programs can be abused for political or personal gain. History has shown instances of governments spying on dissidents, journalists, and political opponents, highlighting the risks associated with unchecked surveillance.
In conclusion, the debate over government surveillance is complex, with valid arguments on both sides. While it can play a crucial role in protecting national security and public safety, it also raises significant concerns about privacy infringement and abuse of power. Finding the right balance between security and privacy is essential to ensure that surveillance practices are both effective and respectful of individuals' rights.
Privacy protection
Privacy protection is a crucial aspect of our digital age, where personal information is constantly at risk of being compromised. With the increasing prevalence of online activities, it has become more important than ever to safeguard our privacy from potential threats.
One of the fundamental ways to protect privacy is by being mindful of the information we share online. It is essential to only provide necessary information and avoid disclosing sensitive details unless absolutely necessary. Additionally, utilizing secure passwords and enabling two-factor authentication adds an extra layer of security to our online accounts, minimizing the risk of unauthorized access.
Moreover, being aware of phishing scams and fraudulent emails can help prevent falling victim to identity theft. It is important to verify the authenticity of emails and websites before providing any personal information to ensure that our data remains secure.
In the age of social media, being cautious about the content we share can also contribute to safeguarding our privacy. Limiting the amount of personal information shared publicly and adjusting privacy settings can help control who has access to our data.
Overall, privacy protection requires a proactive approach and a combination of preventive measures to ensure the safety of our personal information online. By staying informed, practicing caution, and utilizing security tools, we can minimize the risk of privacy breaches and protect our sensitive data in an increasingly digital world.
Legal jurisdiction
Legal jurisdiction refers to the authority of a court or government entity to apply laws and make legal decisions within a particular geographical area or over specific individuals or entities. It is a fundamental aspect of the legal system that ensures order, consistency, and fairness in resolving disputes and enforcing laws.
One key principle of legal jurisdiction is that it is based on established rules and boundaries. Each country has its own legal system with laws that apply within its borders. Within a country, different courts may have jurisdiction over specific types of cases based on factors such as the subject matter of the dispute, the people involved, or the location where the events took place.
In addition to national jurisdiction, there are also international aspects of legal jurisdiction. These include issues such as cross-border disputes, conflicts of laws between different countries, and the jurisdiction of international courts or tribunals.
Understanding legal jurisdiction is crucial for individuals, businesses, and governments to navigate the legal system effectively. It determines which court or authority has the power to hear a case, enforce a judgment, or prosecute a crime. Failing to consider jurisdictional issues can lead to legal complications, delays, and uncertainty in legal proceedings.
Overall, legal jurisdiction plays a vital role in upholding the rule of law and ensuring that justice is served in a structured and orderly manner. By respecting and adhering to the principles of legal jurisdiction, societies can maintain a functional and fair legal system that promotes accountability, consistency, and the protection of rights.
Data interception
Data interception refers to the unauthorized access or capture of data during its transmission over a network. This nefarious practice is often carried out by cybercriminals with the aim of stealing sensitive information such as login credentials, financial details, or personal data.
One common method of data interception is through the use of packet sniffers, which are software tools that can monitor and capture data packets as they travel between devices on a network. These packets may contain valuable information that can be exploited by attackers if not adequately protected.
Another technique used for data interception is known as man-in-the-middle (MITM) attacks. In MITM attacks, the attacker positions themselves between the sender and the intended recipient of data, allowing them to intercept and potentially modify the communication without either party's knowledge. This can be particularly dangerous as it can result in the compromise of sensitive information or the manipulation of data for malicious purposes.
Data interception can have serious consequences for individuals and organizations alike. In addition to the risk of financial loss or identity theft, intercepted data can also be used for espionage, sabotage, or other criminal activities. Therefore, it is crucial for individuals and businesses to take proactive measures to protect their data from interception.
Some ways to mitigate the risk of data interception include using encryption protocols such as SSL/TLS to secure data transmissions, implementing robust authentication mechanisms to verify the identity of users and devices, and regularly updating security software to defend against emerging threats.
By remaining vigilant and adopting best practices for data security, individuals and organizations can reduce the likelihood of falling victim to data interception and safeguard their sensitive information from unauthorized access.
0 notes