#Controversial doctrines
Text
The Most Controversial Doctrines
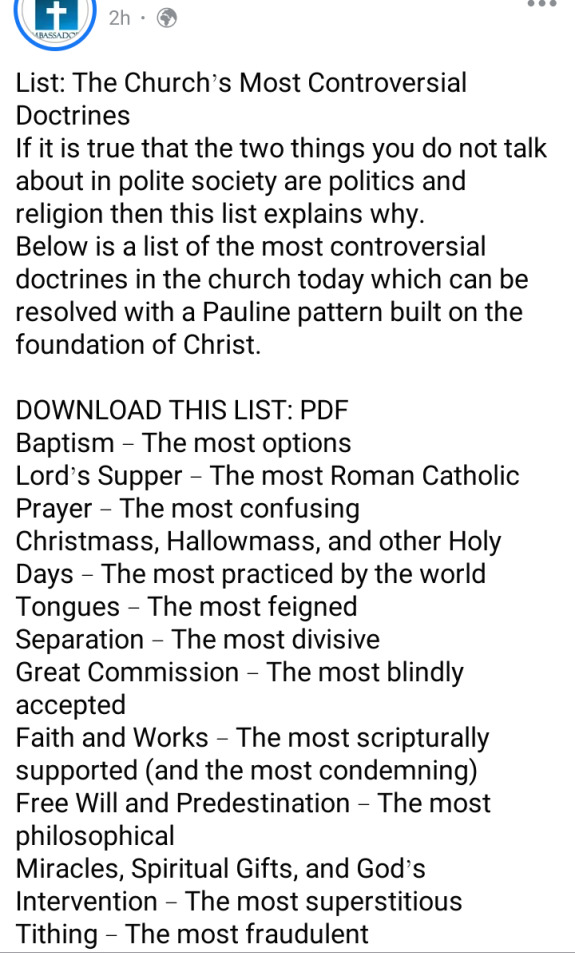
View On WordPress
#1 Corinthians 15:1-4#2 Corinthians 5:19#Controversial doctrines#Sabbath#The Church#Tithing#Water Baptism
0 notes
Text
oh yeah i forgot this was the religious debate chapter lmao
stevie davies' note:
Not for ever: this phrase is the important pivot upon which turns Anne Brontë's version of the Brontë antagonism to the Christian vision of eternal hell as the punishment of sinners. Whereas Emily Brontë denied the goodness of God in the light of his punitive morality, Anne Brontë denied the eternity of hell as inconsistent with a loving Father: 'even the wicked shall at last/ Be fitted for the skies' ('A Word to the Calvinists', 37-8). In an early religious crisis, she had consulted a Moravian minister, Revd James la Trobe, who had consoled her with his church's emphasis on divine Grace; latterly she corresponded with Dr David Thom, the leader of the sect of Beroen Universalists, who believed in universal salvation.
#my edition has like 5 footnotes in one paragraph for this but that's the most interesting imo#quite a controversial doctrine to hold at the time iirc!#the tenant of wildfell hall#wildfell weekly#bronte blogging#laura talks books
2 notes
·
View notes
Link
Matthew Barrett | Evangelicalism is no stranger to controversy. Debates over neo-Orthodoxy, the New Perspective on Paul, and Open Theism—to name only a few in the past half a century—have positioned evangelicals on the right side of controversy as they push back against attempts to abandon or modify...
7 notes
·
View notes
Text
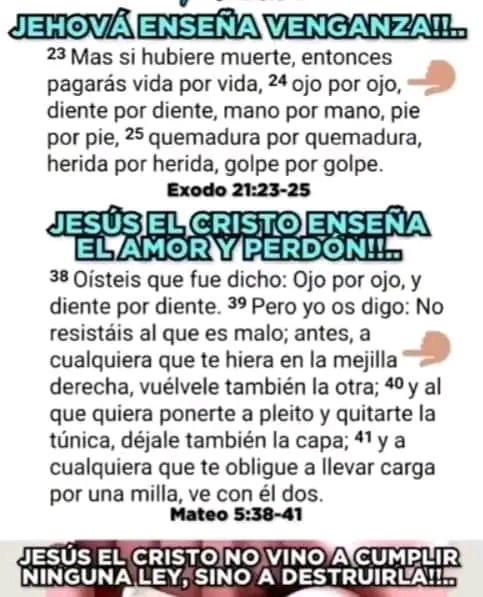
Diferencia entre las enseñanzas del padre verdadero con Jesús 🧔🏻 el cristo y el demiurgo 👹🐉👿 yaldabaot con Jehová 👽.
1 note
·
View note
Text
The God-Man: Understanding the Deity and Humanity of Jesus
At a point in time, the eternal Son of God added humanity to Himself, simultaneously becoming God and man, Creator and creature, the unique theanthropic person (John 1:1, 14, 18; 8:58; 10:33; 20:28; Col 2:9; Heb 1:8). Jesus is the God-man and exists in hypostatic union, as a single Person with a divine and human nature (John 1:1, 14; 1 John 4:2-3), both natures being distinct and preserved, not…
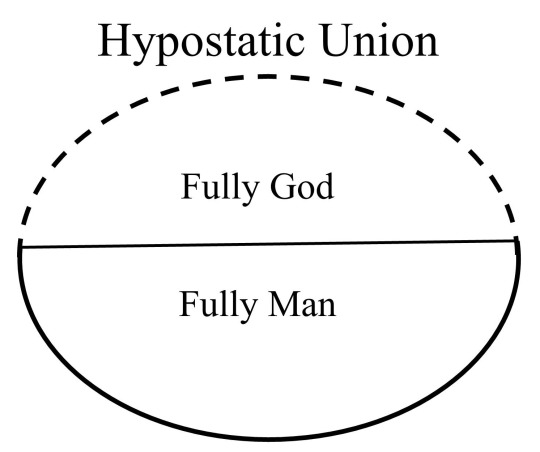
View On WordPress
#Biblical Christology#Biblical Teaching#Biblical theology#Chalcedonian Council#Christian apologetics#Christian doctrine#Christian Faith and Practice#Christian History#Christian Theological Controversies#Christian theology#Christological Understanding#christotokos#Council of Chalcedon#Councils of the Church#Deity of Jesus#Divine Incarnation#Divine nature#Divinity and Humanity#Doctrine of Jesus#Early Christian Theology#Faith and Belief#Human Nature#Humanity of Jesus#hypostatic union#Incarnation#Jesus#Jesus Christ#Jesus is Messiah#Jesus is the Jewish Messiah#Jesus is the Savior
0 notes
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Note
Say something controversial about 40k
Controversial to who, though? Like the really sweaty people? I've already done female marines and the inherent homoeroticism of the astartes. Uhhh.
Here's one-
The Halo franchise has done better job of showing the actual bleak grimness of a humanity on the back foot and perpetual brink of defeat than 40k ever has and likely ever will!
Also, T'au combat tactics aren't cowardly, and their martial and political strategies are, ironically, similar to the ones that we, humans, use today. Capping a guy from 500m away is smart. Imperium military doctrine is written by zealous clowns.
155 notes
·
View notes
Note
Top five canon ships from your fandoms?
canon ships? what're those. also I mean. how "canon" are we talking, like, explicitly canon, implicitly canon, they-get-together-at-the-end canon, they-at-some-point-were-a-thing canon, plausible-deniability-canon, it's complicated
but okay, to try to take this in the spirit it was probably meant
Hua Cheng/Xie Lian from TGCF. one of the most incredible things about TGCF is that it actually made me wholeheartedly and enthusiastically ship a completely canon and...relatively functional...ship. I mean, they've definitely got their dysfunction (Hua Cheng get some self esteem and maybe pedestalize Xie Lian a little less challenge) but they're weirdo4weirdo and friends in a delightful way that makes me really enjoy how they do it. I'm not saying they invented love, as the saying goes, but they're certainly good at it.
Felix Harrowgate &/ Mildmay from Doctrine of Labyrinths. look, if there's explicit incestuous attraction at at least one point I think it counts. this is one of those ships that straddles the line between & and / for me a lot of the time, because any sexual stuff aside it's so intense and intimate that, like. it might as well be a "classic" ship, just without the sex, and we're agreed that something doesn't have to have sex in it to be a ship, right? and there is the canonical one-sided incestuous attraction, so, like. it's not even completely without the sex.
Vegas Theerapanyakul/Pete Saengtham from Kinnporsche. cannot believe that this is canon thing that actually happened in a show that I watched. made 4 me. incredible. forever grateful to Kinnporsche for giving me this gift.
Caleb Widogast/Essek Thelyss from Critical Role. I feel like it's canon enough? maybe that's controversial but I'm going to stand by it. fascinating dynamic, two fucked up people being fucked up together, atonement arcs that aren't usually my thing but crossed with a wondrous amount of wizard hubris and people who are both kind of bad at being people. I'm into it.
Chu Wanning/Taxian-jun from 2HA. this spot was more of a toss-up but ultimately I settled on these two. I specify Taxian-jun here because while I really enjoy Mo Ran/Chu Wanning other flavor it's truly the Maximum Fucked Up that gets/got me. the hate/love/obsession of it. so good, I'm rolling around in it like a cat in catnip. thank u Meatbun for giving this to me with all its laundry list of associated trigger warnings
I feel like everyone should know how fucking tempted I was to put xuexiao on here. because it was very tempted. they're so close, you guys, I would argue implicitly canon, but, well. probably not what you meant, anon.
a number of what I'd call "plausible deniability canon" ships from mxtx, really. but again, spirit of the question.
29 notes
·
View notes
Text
Alabama Chief Justice Tom Parker, who wrote the concurring opinion in last week’s explosive Alabama Supreme Court ruling that frozen embryos have the same rights as living children, recently appeared on a show hosted by self-anointed “prophet” and QAnon conspiracy theorist.
Parker was the featured guest on “Someone You Should Know,” hosted by Johnny Enlow, a Christian nationalist influencer and devoted supporter of former President Donald Trump. Over the course of an 11-minute interview, Parker articulated a theocratic worldview at odds with a functioning, pluralistic society.
“God created government,” he told Enlow, adding that it’s “heartbreaking” that “we have let it go into the possession of others.”
Media Matters, the liberal media watchdog group, was the first to report on Parker’s appearance on the program.
That a state’s chief Supreme Court justice would associate himself with Enlow is a cause for alarm. Enlow is a prolific conspiracy theorist, often weaving QAnon apocrypha with prophecies he claims to receive directly from God.
As reported by Right Wing Watch, Enlow has claimed that Trump “is on assignment” from God to work with the angels Michael and Gabriel to take down George Soros and Bill Gates, among others; he has claimed that Russian President Vladamir Putin is fighting “Luciferian pedophiles” in Ukraine, in a battle to stop them from deploying vaccines and 5G that would turn people into transhumanist semi-robots; and he has claimed that the majority of other world leaders are “satanic” pedophiles who “steal blood” and “do sacrifices.”
Enlow’s interview with Parker was uploaded to Rumble, the alt-tech video platform, on the same day the Alabama Supreme Court issued its opinion that sent shockwaves throughout the reproductive rights community. The ruling, which makes fertility clinics liable in wrongful death lawsuits for harming or destroying an embryo, has already imperiled access to in vitro fertilization (IVF) in the state.
“Human life cannot be wrongfully destroyed without incurring the wrath of a holy God,” wrote Parker, a longtime anti-abortion advocate sometimes credited with building the legal framework to overturn Roe v. Wade. “Even before birth,” Parker added, “all human beings have the image of God, and their lives cannot be destroyed without effacing his glory.”
Parker used similar theological language in his interview with Enlow, thanking Enlow for promoting the “Seven Mountains” on his show. As HuffPost has reported before, the “Seven Mountains Mandate” is a doctrine at the core of the New Apostolic Reformation, an evangelical movement that believes in the supernatural, including the existence of modern-day apostles and prophets, and which is characterized by a belief in Christian dominionism. The Seven Mountains Mandate is the belief that Christians must conquer the “seven mountains” of societal influence — education, media, religion, family, business, entertainment and government — and force fundamentalist Christian values onto every part of American life, in order to pave the path for Christ’s return.
“As you’ve emphasized in the past, we’ve abandoned those Seven Mountains and they’ve been occupied by the opposite side,” Parker told Enlow, suggesting the chief justice is familiar with Enlow’s show. Enlow is a big proponent of the Seven Mountains Mandate, and maintains a far-right website with his wife called “Restore Seven.”
Parker also told Enlow that God is “equipping me with something for the very specific situation that I’m facing” as the Alabama chief justice.
Enlow, as noted by Media Matters, praised Parker and appeared mindful of not dragging the judge into even more controversial topics. He told Parker that he’s “in such a key place that we don’t want to have any conversations that hurt you in any kind of way, but we appreciate who you are, who you are in the kingdom.”
34 notes
·
View notes
Text
According to various press reports in late August, authorities in Sweden carried out forced sterilisations on 60,000 Romani women, in order to cleanse society of what they regarded as inferior racial types. The operations began in 1935 and ended only in 1976, according to a report in the online version of the Dutch news paper, De Telegraaf. The report alleges that the sterilisations were 'officially voluntary', although it goes on to add that many of the women did not understand what was being done to them.
An Associated Press release noted that the program had its roots in the pursuit of eugenics, a movement popular at the turn of the century, which aimed to 'improve humanity' by controlling genetic factors in reproduction and developed from widely-accepted 19th century racist doctrine. AP reported that the Swedish newspaper Dagens Nyheter cited documents pertaining to the Swedish program, one of which stated "Grounds for recommending sterilisation: unmistakable Gypsy features, psychopathy, vagabond life." According to AP, the issue is even more controversial because of the fact that the sterilisations were carried out under a government of the Social Democrats, the party that built Sweden's welfare state.
148 notes
·
View notes
Note
if you can give me a reason why you prefer to be a Shi'a over a Sunni, what would it be
So there's this Sunni doctrine or theory called "Adalat al-Sahaba", which roughly translates to the nobility or integrity of the companions.
The idea behind this thought is that despite any wrongdoings the companions of the Prophet may commit, they were still the closest to the prophet, and so they're trustworthy and reliable. What this means essentially is that when a Hadith is narrated by them or when they're part of the chain of narrators, the hadith is considered reliable and trustworthy. Second issue is that they're exempt from all crimes they've committed. For example, the r*pist Khalid ibn al-Walid (la), who killed Malik ibn Nuwayrah (ra), a Muslim who refused to pay the charity tax (Zakat) to the state, since his allegience was with Ali (a). As a result, Khalid (la) killed him and violated his wife. Abu Bakr, who was the caliph at that time, exempted Khalid (la) from his crimes, despite the punishment for r*pe being death, since he was an essential asset to the ever-expanding Arab empire. Khalid ibn al-Walid (la) is considered a reliable narrator by Sunnis and honored by the epithet the Sword of God. There are many more companions that Shi'a Muslims fully reject and condemn, and is ultimately one of the most distinctive and controversial issues among Sunnis and Shi'as.
The purpose behind Adalat al-Sahaba is to prevent partisanship and to provide legitimacy to the companions as an absolute authority. Some Sunni scholars will go so far as to declare a Muslim a kafir (disbeliever) if they criticize, object or scrutnize the companions. None of these people are infallible, so why ought I subscribe to a set of beliefs that vindicate the most violent people?
103 notes
·
View notes
Text
It baffles me the offense taken at @sophieinwonderland 's plural trinity theory (that many others, including us, have come to independently) because she's checks notes using it to push an agenda.
Like, do y'all not understand how xtianity works? Have y'all listened to a preacher before? Have y'all ever been inside of a church after a big controversy has hit the news and heard a message relating to that from the pulpit?
Most scripture we see quoted is to push an agenda. Most sermons are backed by an agenda. Even earnest spiritual explorations of the Bible are informed by one's preexisting beliefs and biases (and those of the teacher if there is one). It's not wrong to push an agenda through theological interpretation. That's just what theological interpretation is.
The specific agenda may be harmful yes. But the problem is that they're pushing a harmful agenda, not that they're pushing an agenda.
Is it deeply offensive to make jokes/theories about Jesus being ace? Hell we've seen articulate discussions in xtian and ex-xtian circles about if Paul was ace or gay and doing a whole bunch of moralizing to justify his queerness. Would it be wrong to point out to a transphobe that Jesus (only having the XX chromosomes of Mary) would have therefore been either trans or intersex? How about to quote passages that seem to be Jesus specifically preaching that transition is holy?
Shit, when we had aspirations of becoming a pastor we worked on a sermon about how the early church in Acts was straight up communism. We wrote one on that meme where Jesus says "Did i fucking stutter?" We tried to get our church to start a queer ministry program. We tried to build it into a mutual aid org. Cause I'm a queer xtian anarchist and I have an agenda to push.
And I'm predicting a response out there. "Oh Faye! But that's not what social justice preachers or televangelists are doing. They're interpreting the True Word of God and building their agenda from that!" Which would be worthwhile to entertain and discuss. Except that the disdain at God being viewed as an endogenic median system is coming from non-xtians.
And sure, she's an atheist with an ex-christian host. So maybe you can think that it's wrong for her specifically to push an agenda through xtianity. But xtian theology isn't sacrosanct and immune to outside interpretation. It fucking lost that privilege when it forcibly tries to convert half the world. You can't tell someone to stop touching a religion when that religion is being forced on everyone.
Anyone who's fighting Sophie's take on the trinity on the grounds that it's wrong to interpret doctrine to push an agenda is doing christofascist colonialist's work for them. Christofascists are the ones that have a vested interest in xtianity having one true doctrine free of politics or agendas. It's those people that want to say that the xtian Bible simply agrees with their bigotry and any interpretation otherwise is blasphemous and degenerate. They want xtian doctrine to be a settle issue that lands squarely affirming their death cult of heteropatriarchial, xenophobic, antisemitic violence. Not something open for interpretations in ways that further equality or justice (exactly the goal that Sophie clearly states).
-Faye
23 notes
·
View notes
Note
Byler's like a religion we've all been converted to. We got denominations (bi mike/gay mike), heretics (those who preach fanon doctrines that go against canon), prophets (kaypeace, hawkins school counselor), controversial but influential televangelists (spicy byler polls) and those who oppose them ("puritans"), statements of faith (some adhere to the Byler Bible, others develop their own statements of faith like will80sbyers, others believe we should simplify our doctrine and just believe Mike loves Will), literal Confessions (you), wars (everything that happened in 2022), church history (everything that happened before 2022), scandalous religious leaders (everything re: noah), an enemy religion (Milevens), a gospel message (Byler endgame), a mission field (Reddit), missionaries (Bylers on Reddit), chapels/synagogues/temples (Byler Tumblr/Byler Twitter), religious art creators (Byler fan artists), lay theologians (smaller accounts that come up with new theories), famous theologians (big Byler blogs like pinkeoni), apostates (those who have left the Byler faith), idolaters (multishippers), religious films on the life of Jesus Will Byers (Byler fan edits), religious holidays (Will's birthday), saints (ancient Bylers), contested verses (gates), a literal advent calendar (the lead-up to volume II), mantras ("Mike Wheeler I Know What You Are"), new converts (baby Bylers), and more.
anon please go on with the examples. also i think my head just exploded reading this like i can just imagine someone on screen preaching at a stand "WHO GIVES THE BETTER HANDJOBS"
28 notes
·
View notes
Note
Your daring statement that "people should probably believe things that are true" seems to have been met with controversy in the Believing Things That Are False community.
congrats on the job btw
Thank you! And, yeeeeah, lol
I mean as a blanket statement that gets dicey with things like spiritual or religious beliefs, which I'm aware this wasn't about, but, as an aside (sorry if this is a bit obnoxious)...
The standard I set for myself a while ago was one of going like, I won't rudely try to intercede in someone Believing A Thing That Is Wrong if they are not using said belief to cause harm to/negatively impact others. This seems to be the best policy to avoid causing a lot of pain needlessly for everyone, because it's not like people actually change their mind about deeply held beliefs when questioned on them.
But on the other end of that double-edged sword, when people demonstrate that they are casually and often without realizing deploying false judgements in a way that does affect how they interact with the rest of the world, then I do think that that's probably something that they should work on.
And again I'm not a dick about it, but I do think I'm more than within my rights to be like "it makes me uncomfortable to realize that people are making decisions and judgements in a poor and possibly dangerous way, possibly at scale". And if people want to come after me for saying that, then I can and will call them on it lmao. They want to have an argument then I'll more than give them one, I don't think a lot of people realize how much restraint you have to learn and internalize early on to hold a model of reality that you are reasonably certain is accurate but which runs contrary to the prevailing cultural zeitgeist.
It annoys me for instance how often religious people who will talk on their own philosophy will lambast a spectre of "annoying atheists trying to lecture them" when they won't think twice before trying to assert some absolutely asinine doctrine to someone who says something in passing, not even to them specifically, that contradicts it. They don't realize that they are far worse for deploying that kind of aggressive lecturing than most of the atheists they complain about, but are more concerned and annoyed by atheists specifically because they have realized they can't actually win an argument when they're arguing something that inherently lacks proof or any reasonable claim to be the null assumption.
25 notes
·
View notes
Text
While browsing for information on a particular Barbie, I was surprised to see Google recommend appending the word "controversy" to my search. The Barbie in question?

Breathe With Me Barbie. Breathe With Me Barbie is part of a range of self-care and wellness Barbies and depicts Barbie in a sukhasana pose, promising "5 guided meditations".
Unsure of where the controversy around this could be going, I clicked through. This seemed to be the root of it.
"Each pose is designed to invoke a Hindu deity in the spirit realm. I have seen children get possessed by demons. ... Satan is after the children. He wants to use them and indoctrinate them for his glory. Then, when he is done, he will destroy them. As your kids grow, they will get rebellious, depressed, and many will be suicidal. You won't understand what's happening as a parent. You must remove all toys and clean your children's room of all demonic attachments."
Various websites from Business Insider to The Christian Post to Newsweek cite Christian influencer (or, in the words of Business Insider, micro-influencer) Yasmeen Suri as being the origin of the claim that this doll is an agent of Satanism.
This would not be the first person to associate yoga with Satanism or possession - exorcist Gabriele Amorth also associated the practice of yoga with increased chance of demonic possession.
I can't find a screenshot of this, though, and all links back to the Facebook post are dead. What I did find though is a Patheos satire article dated shortly before the rest of these articles citing "Jasmine Blades" from Christians Against Eastern Religions as the source of the same quote.
Neither Christians Against Eastern Religions or Jasmine Blades are real, of course, hence their inclusion in a clearly marked satire piece. But I don't know where this leaves real Christian influencer Yasmeen Suri and her alleged (re)posting of the same quote picking up steam a week later. I don't know whether she saw the satire post and reposted the quote, to take it down later once she realised, or whether these articles quoting her as the source are misattributions. I'm leaning to the former, but I'm not actually sure.
There's a Truth or Fiction page debunking this, but what it is debunking is a) whether Breathe With Me Barbie depicts the practice of yoga (it depicts meditation, not yoga), b) whether this was a new doll in 2022 (it was not, it was released in 2020), c) whether yoga is synonymous with Hinduism and d) whether Catholicism or Christianity more generally prohibit or warn against the practice of yoga as a matter of doctrine.
For the record, by the way, there are Barbies that are explicitly depicted as practicing yoga, such as I Can Be... Yoga Teacher Barbie.

Or that appear to depict the practice of yoga on the box art, such as the Made to Move series.

Or dolls such as this Fitness Barbie who is depicted with various fitness equipment such as weights and a hula hoop, as well as a yoga mat.

#barbie#yoga#controversial barbies#hoax#yoga teacher barbie#breathe with me barbie#meditation#fitness#wellness barbie#made to move barbie#gabriele amorth#satanism#religious imagery#religion#suicide mention
24 notes
·
View notes
Text
Random OM! Realm Headcannons
This is a list of different headcanons I have on each realm, separated by All, Celestial, Devildom, and Human realm.
I will add to this list as I come up with more, but this is what is currently what's spinning through my head.
•▪︎▪︎◇°●♡●°◇▪︎▪︎•
All:
TBA
Celestial:
Gender & Sexuality-
The Celestial realm has specific rules on gender expression and identity. An angel is not obligated to dress in a masculine, feminine, or an androgynous way, but they are expected to keep the name, pronouns, and body their Father gave them.
The act of wanting to change their body, name, or pronouns is seen as an insult to their Father and therefore a punishable offense.
Angels are also raised to believe romantic love and any form of attraction is sinful. It is believed that these two feelings can cause angels to stray from the path given to them by placing someone before them as more dear than their siblings or worse, their Father.
Both romantic love and sex are seen as a major offense punishable by death.
This is one reason that modern angels do not reproduce like the other races; there are no parents or pregnant angels in the Celestial realm; there is only their Father and he makes new angels when needed and keeps a tight hold on the population.
Culture-
Angels follow a strict doctrine and live in accordance to the values they are born with.
Just like demons are born inclined towards various sins and vices, so are angels with virtues; no angel is born without a virtue to embody.
Angels are expected to follow their virtue strictly or are given 'mercy' by being thrown into the Spring of Life, the body of water Father uses to make His children; basically he recycles them to protect Himself from the risk of that angel dropping their virtue and adopting a sin.
Devildom/Abyssal:
Gender and Sexuality-
Gender has always been seen as more or less fluid for the demons. What's between your legs is only treated as a suggestion and used to give their children more or less a template gender.
No demon is officially seen with a solid gender till they are adults, giving the younger demons time to explore their identities and figure out how they feel about their bodies.
Modifying one's body is not only allowed, but encouraged after a certain age. Demons have a plethora of potions to help with this and teenaged demons are often found changing their bodies' forms with these.
However, this is mostly done by the average demon and such changes are rarer for demons of the higher class, whose parents feel the need to have stricter control over their children for the sake of organizing power, arranged marriages, and heir planning.
Sexuality is also very diverse in the Devildom and is seen as something that can keep changing throughout a demon's life.
Most demons have a pretty pansexual mindset, meaning they just expect everyone to have the potential to be attracted to all forms of demons.
It is still common and accepted to have demons who are heterosexual or homosexual; demon's simply don't assume the person next to them is only interested in one gender.
"Human Realm":
Origin facts-
Though it now refered to as such, it is only because the original name has become controversial.
This realm used to only be refered to as the Cradle, since it was created solely to house and protect the Devil and Father's children.
This term is now deemed controversial because it is seen as demeaning to the humans, who have always been treated as children caught in the worse divorce in existence.
Because of this, the bland but true description of 'Human realm' is the polite term for this world
65 notes
·
View notes