#Track a Mobile Phone Secretly
Note
Hey!! I loved your Peter Parker fic!!
I hope you're taking requests, if yes can you please write harry potter x ravenclaw!reader? Where reader is a muggleborn and loves muggle music, she does this thing where she gives all her friends a song which reminds her of them, even multiple to Hermione (who secretly loves it and listens to those on loop) and ron( who tries to act like he doesn't care but secretly feels loved) but she's never given harry a song, despite him being her best friend. But after one of DA meetings they are alone and harry asks her why doesn't she give him a song (fallin' all in you- Shawn Mendez) and she plays it for him a and that it reminds her of him, AND THEY KISS!!
I'm really sorry if it's too specific, please feel free to change anything! THANK YOU SM!! I LOVE YOUR FICS!!❤️❤️✨
definitely not too specific! i love that you gave me so much to work with, so ty anon! i did switch it up a little bit, but i hope it turned out to your liking!
318 Hours 43 Minutes ˗ˏˋ H.J.P ´ˎ˗
“Be my summer in a winter day, love”

harry potter x ravenclaw!reader
WORD COUNT: 2.3k
REQUESTED: yes
requests are open!
fandoms: marvel, stranger things, harry potter (any era), scream
WARNINGS: fem reader, not proofread, fluff fluff fluff, muggleborn!reader, reader is described as somewhat of a musical prodigy, modern music, mobile phones, and spotify all exist in this timeline, 7th year, kissing, idiots in love, best friends to lover ig, joking mentions of death, lmk if i missed smth!
A/N: i'm sure there are tons of grammatical errors in here but lets pretend we don't see them!
ALL CHARACTERS IN THIS STORY ARE 18+
remember to like, comment, and reblog to support my writing!
If there was one thing you couldn't live without, it would be music. It was almost impossible to recall a time you had left your dorms without your headphones. Music had just always been a huge part of your life. Growing up, your parents got you into piano lessons, and you were playing Beethoven by the end of the first month. After that, you picked up as many instruments as you could afford, starting with violin, then guitar, the flute, and now the harp. Your parents had to soundproof the house.
Once you got your acceptance into Hogwarts as a witch, your whole world turned upside down. You were sorted into Ravenclaw, which felt very fitting, and were assigned a dormmate, Padme Patil. The two of you clicked immediately and became instant friends. After a few months of hanging out with the Patil sisters, you were introduced to three Gryffindor students in your year; Ronald Weasley, Hermione Granger, and Harry Potter. Instantly, you felt some sort of a connection pulling you to them, but you couldn't put your finger on it.
You started hanging out with "The Golden Trio", as you affectionately called them, all the time, and the four of you eventually became a quartet. You had grown especially close with Harry, and the two of you did almost everything together. Well, everything except study.
After one particular study date with Hermione, you were thrilled to learn that she shared the same love for muggle music as you did. The two of you rambled on and on about your favorites, uncharacteristically losing track of your studies.
"The song Rises the Moon reminds me a lot of you!" You mindlessly exclaimed, watching as Hermione's eyes lit up.
The rest was history. You were known to associate songs with the people around you, and you had no shame in telling them. You had given Hermione, Ron, and the Patil sisters a countless number of songs over the years. In fact, you had given them so many, that a few had made playlists to keep track of all of them. Ron was the most hesitant to accept the recommendations, but Hermione told you she had caught him singing along to them in the common room on multiple occasions.
Every once in a while, you would even see another student studying in the library, maybe one you had only said 'Hello' to in passing, and a song would just scream out to you so loudly that you had to leave them a note about it as you left.
It was like your own personal love language, and you loved being able to make people smile, even if they never listened to the song.
The one person close to you whom you had never given a song to, was the infamous Harry Potter, and it was painfully hard for him to ignore. After almost seven years of being best friends, you would think he would have been worthy of at least one song, right?
He watched as you expertly conjured up the Draught of Peace potion the class was supposed to be working on, smacking Ron's hand away when he goes to touch it. Watching you was the only thing that made this class somewhat bearable.
He can't get it out of his head... the fact that you've never given him a song. He's been thinking about it non-stop since you gave that Hufflepuff boy a song in the dining hall a few days ago.
It wasn't news to him that he had been in love with you since 5th year, probably longer than that before he had even realized, but he would sooner die than admit it out loud.
You were the most important person in the world to him, but he was almost positive you didn't feel the same way. He would never be able to forgive himself if he ruined your friendship. So, he just kept his big mouth shut and pretended like there was nothing there.
He thought he was really good at faking it too. He wasn't.
Anyone with eyes could see the way he looked at you, the way he spoke to you, the way his smile looked ten times brighter when you were around. It was blatantly obvious he had it bad for you.
What wasn't as obvious was that you were just as infatuated with him as he was with you. You may have been much better at hiding it, but anyone close to you could see it clear as day. I mean, it was silly really. The way you were both so stupidly in love and too scared to see it.
Harry snapped to attention as Professor Snape called on him, spitting out to 'straighten his spine and get back to work'. He grumbled something under his breath before following instructions. When he looked back at you, he found your eyes already on him, giggling at the scene he had caused before returning to your schoolwork. He loved hearing your laugh.
As the class ended, Harry gathered his things into his bookbag, slinging it over his shoulder as he straightened his robes. Snape was the first to leave the classroom, followed by a small swarm of students who were anxious to get back to the common rooms for some much-needed free time. Harry looked over to where you and Ron had been sitting, watching you pull out a scrap of parchment with messy little scribbles on it, before sliding it over to the red head.
"I found a new song the other night, and it reminded me so much of you, I just had to write it down before I forgot the title." You smiled, watching Ron look over the writing, thanking you awkwardly as he shoved it into his pocket.
Harry suddenly felt his pockets get lighter.
"I'll be in the library with Hermione tonight. Wants to tutor me for Transfiguration." He said in an annoyed tone, though you knew he was secretly looking forward to it. "You wanna come? Could use all the help I can get."
Harry secretly hoped you would say no.
You packed up all your belongings, making sure not to forget any of your notes, "Yeah, sure! Just have to do a few things first, but I can stop by in a bit." You smiled, the way you always do, as you shoved folders into your bag.
"Alright," Ron nodded, "I'll see you." He said as you waved each other goodbye, Ron heading for the exit. "Oh hey, Harry." He threw out casually as he left the room, calling attention to the boy in the back of the otherwise empty classroom.
You quickly turned around, smiling brightly when you saw him still sitting awkwardly in his seat. "Oh hey, Harry!" You repeated, "You're still here?"
Harry regained common sense then, now realizing he had been staring at you for the past hour, he stood from his seat and walked over to you. "Yeah..." He trailed off dumbly, still in his own thoughts. He head got cloudy as your perfume surrounded him.
He had debated on bringing it up for the past few months, but was to scared of your response. Honestly at this point, he could barely focus on anything BUT asking you about it. He figured that at this point it would be better to just get it over with. Like ripping off a bandaid.
"Hey, uh... Could I ask you something?" His voice cracked.
"Yeah, of course!" You finally slung the bag over your shoulder, giving Harry your full attention. "Ask away."
Your voice sounded sickly sweet, and it somehow made him more nervous. "Alright... Well, uh, I was just wondering-" He felt far too vulnerable to look into your eyes, so instead he looked at your shoulder. He had to clear his throat, "I was wondering why you've never given me a song?" He slurred out, trying to act casual about it while his heart was beating at top speeds.
Your smile immediately dropped, and Harry's stomach fell into his shoes at the sight. Now it was your turn to avoid eye contact, looking down at your feet and chewing on your cheek as you debated a response.
Harry felt like he was about to pass out. His hands grew clammy, and he could hear his heart hammering in his ears. The only times he had ever seen you not smiling were when something really terribly tragic had happened, or when your friends were upset themselves. This had to be a bad sign, right?"
Meanwhile, a million thoughts swirled through your head. You had hoped he hadn't noticed the exclusion, but you knew it was only a matter of time before he brought it up. You felt sick to your stomach. How could you lie your way out of this one? You hated lying, especially to Harry, and you didn't want to hurt him. Could you really risk telling him the truth? What if he freaks out and goes running for the hills and all your years of friendship are ruined?
"You know what, it doesn't matter." Harry brushed off weakly, starting to back away from you, "I don't need to know! It's no big deal, just forget I even said anything-"
"Harry, wait-" you instinctually grabbed his hand, making him freeze. You let go to reach into your bag, Harry cautiously getting closer. His confusion increased when you pulled your phone out, rapidly typing on it to pull something up. When you finally found it, you took a deep breath. Once he saw what you were about to show him, there would be no turning back. Finally, you made yourself turn the phone around so Harry could see the screen.
It was a private playlist titled "For Harold", and the cover photo was a picture that Hermione took of the two of you after a snowball fight last Christmas break. Falling all over each other in laughter, completely covered in snow.
You handed the phone to him, limbs shaking too much to hold it steady. He looked below the title to see the timestamp read 318h 43m.
You felt like your stomach was being tied in knots.
"This is why I've never given you a song." You admitted quietly. His expression was hard to read. Brows furrowed and mouth slightly open in shock. "I just... There were too many that reminded me of you."
Harry still hadn't looked at you or said a word, and you started to feel like you'd bounce right off the floor with how much you were vibrating.
Then he stopped scrolling, staring at the title of one particular song much too long for your liking. Even worse, he pressed play. As soon as the song started, you shrunk down into the desk behind you.
Sunrise, with you on my chest
No blinds in the place where I live
Daybreak, open your eyes
Cause this was only ever meant to be for one night
We're changing our minds here
Be yours, be mine, dear
You busied yourself by playing with your fingers, looking absolutely anywhere but at Harry.
So close with you on my lips
Touch noses, feeling your breath
Push your heart and pull away, yeah
Be my summer in a winter day, love
You started to feel incredibly antsy, regretting ever showing him the playlist. "We really don't have to listen to the whole thing-"
I can't see one thing wrong
Between the both of us
Be mine, be mine, yeah
Anytime, anytime
You squeezed your eyes shut to try and save yourself from some embarrassment, but when you opened them, you found Harry looking at you with the biggest smile you'd ever seen in your life. Your belly flipped.
You are bringing out a different kind of me
There's no safety net that's underneath, I'm free
Fallin' all in you
Fell for men who weren't how they appear, yeah
Trapped up on a tightrope now we're here, we're free
Fallin' all in you
Harry was beaming, putting the phone down on the desk beside him. He slowly made his way closer to you, and no matter how badly you wanted to look away from him, you couldn't.
He was now so close to you that you could feel his breath fan across your lips, and the song faded in the background as your heart pounded. "Is this how you really feel? About me?" He asked as his cheeks turned pink, and you couldn't help but find the silly question endearing.
You nodded your head, deciding that your voice would give out if you tried to speak right now. The eye contact was almost unbearable, and you broke it with a quick glance down to his lips.
The second you did, his lips were immediately on yours, pressing hard into you. You gasped against his lips in shock. You felt like your whole body was on fire.
He pulled away too soon, mumbling a boyish "Sorry about that-", before you chased his lips and pulled them back down to yours, muffling the rest of his apology. This time it lasted.
Your lips felt like they were home against his, moving slow and sweet, like you had all the time in the world. You sighed happily into the kiss, pouring the years of pent-up feelings out for each other. His lips tasted like pumpkin, and butterbeer, and the sweet vanilla chapstick you gave him. It made you giggle a little against his lips.
You melted as he mindlessly cornered you against the desk, his hands gently holding your face like you were made of glass. You wrapped your arms around his neck to ground yourself. His lips curled up into a smile against yours, and you involuntarily matched the expression. It all felt so... right. Like all of the pieces were finally falling into place.
Unfortunately, you both need oxygen, so you were forced to pull away. He rested his forehead against yours, as you share the air between you. You pulled him impossibly closer, nudging his nose with yours, both knowing you felt just as lovesick for each other.
Then your phone dinged. Harry looked down at the message from Ron, reading "Hey, you still coming tonight?"
He picked it up to respond, "Can't, sorry!" before flipping it over carelessly, both of you giggling as he pulled you back for another kiss.
i had so much fun writing thissss ugh this was such a sweet prompt. tysm anon!
#brairslair#brairs fics#harry potter#harry james potter#hp fandom#harry potter fandom#harry potter fanfiction#harry potter fluff#harry potter fic#harry potter fanfic rec#harry potter x reader#harry potter imagine#hp fanfic#harry james potter x reader#harry james potter imagine#harry james potter fluff#harry james potter x y/n#harry james potter fanfiction#harry james potter fic#harry james potter fanfic#hogwarts school of witchcraft and wizardry#gryffindor#hogwarts houses#ravenclaw#x reader#fic rec#fic recs#ty anon#modern au#marauders
134 notes
·
View notes
Text
The Freedom of the Press Chapter 20 (Dhawan!Master x reader)
Freedom of the Press tag list: @startrekkingaroundasgard, @wandaloki, @praxeus-13, @lokabrenna0801, @wincheskka, @nines-leather-jacket
You looked blankly at the now cold mug of tea in your hands. People milled about you but you didn’t hear anything they were saying. You jumped when warm hands took the mug out of your grip and replaced it with a new one. You looked up into the pale face of Ianto. He gave you a smile that didn’t quite meet his eyes as he sat down next to you.
“How are-“
“Don’t,” you said, “Just don’t.”
“Yeah,” Ianto said dejectedly, “I know.”
You took a sip of your tea with shaking hand and was secretly grateful that it was Ianto who made it. Even now he was still able to make an amazing cuppa. His eyes were red rimmed and you could see the tear tracks down his face. It looked as though he had tried to wash them way but had given up. You knew from experience.
“Have you heard anything from O?” you asked, “I tried calling him but I haven’t managed to get through.”
“No,” Ianto’ voice cracked slightly and he coughed and said a bit more firmly, “No but I’m sure he’s fine.”
“He’s usually so prompt at replying though,” you said, “I don’t want-“
Ianto reached over at took one of your hands. He gave it a squeeze and gave you a soft smile.
“Don’t think like this,” he said, “It’ll be alright.”
You wished you could believe him. You really wished you could.
“Y/n?”
You looked over and the Doc was standing by your table.
“I just-“
“Don’t.” you and Ianto said at the same time
“Right,” she gave you a pained looked, “It’s just…”
“If Romana wants to ask me any questions I’m really not in the right state of mind,” you said, “I just can’t. Not tonight. No more.”
“Yeah, she knows. She’s going to need to as some more but not tonight,” she held out her mobile and grimaced slightly, “your boyfriend.”
You jumped to your feet and snatched her phone. You walked away from your friends as the Doc took your seat. You could see the pained look on her face and, while you knew they cared about you, you were tired of seeing it. Sympathy wasn’t going to bring your friend back.
“O?” you asked shakily
“Yeah, it’s me,” he said, “Love, is everything ok?”
You closed your eyes as hot tears poured down your cheeks.
“No,” you said weakly, “No it isn’t. That bastard got Jack.”
“Oh fuck.”
“Where are you?” you asked, “I tried calling but you didn’t pick up. Why did you call the Doc and not me?”
“I’ve been busy.”
“Busy.” You said blankly
“I’ve been in hospital all night.”
“Hospital?!” you cried and sunk down into a seat, “What happened? Are you ok? Did the Master get to you too?”
“No,” O said quickly, “No, I’m ok. It’s my… mother. She wasn’t well and had to be taken in.”
“Is she ok?”
“She is now. Now, where are you? I’ll come and get you. You shouldn’t be alone right now.”
“No, you spend time with your family,” you said, “enjoy your time with them while you can.”
“Are you sure?”
“Yes.”
“Ok. I’ll check in with you regularly. If you want me to be with you let me know, alright?”
“Will do. Oh yeah, one more thing?”
“Yes?”
“You didn’t answer one of my questions- why did you call the Doc and not me?”
“I tried,” he said, “When you didn’t pick up I thought that your phone had died or it wasn’t on you. From the amount of missed calls I thought it was best to get in contact with someone who might be near you. Even if that person was Theta.”
You could heat the bitterness in his voice and couldn’t help but chuckle. Even though he hated her he still cared enough about you to call her to try and get in contact with you.
“Who will you be staying with?” he asked
“Ianto,” you said, “it’s best that neither of us are alone right now.
“Ok,” O let out a sigh of relief, “Ok. As long as you’re safe.”
“I wouldn’t go that far.”
“Like I said- I’ll check in regularly. Love you.”
“Love you too.”
*
When you hung up the Master let out a sigh of relief and leant back in his seat. He tossed his phone gently as he looked down at the stitches on his hand. Damn it, he hadn’t been expecting you to take a swing at him. Well, he hadn’t exactly been lying when he said he was at the hospital.
He let out a dark chuckle as he ran a finger over them.
Oh yes, he was going to enjoy breaking you.
#fanfiction#doctor who#reader insert#the master#dhawan!master#the master x reader#dhawan!master x reader
16 notes
·
View notes
Photo

NSA Monitors the World
In addition to its own network systems, the United States had also cooperated with many allies such as the "Five Eyes Alliance"(FVEY) and established many secret monitoring systems all over the world. NSA conducted secret monitoring mainly by applying to operators to enter the global communication network. When it was impossible to enter the network through the normal means of negotiation with enterprises, NSA could also use technical means to open the "back door" intrusion and realized "self-service" access.
In this way, NSA used software vulnerability tools or automation equipment to collect electronic signals and intercepted global communication equipment information. Even if the monitored object did not use public equipment or public Internet at all, or software vulnerabilities could
not be exploited, NSA could also collect information "manually".
Such means were mostly aimed at foreign embassies and consulates in the United States and foreign targets. The personnel of the action team mastered the hardware implant switch and could secretly change the target's telephone, web searcher and e-mail lines. When necessary, these personnel would secretly go to the target location and sneak into the site to collect information disguised as repairmen and inspectors.
Considering the dangers of actions against the leaders of other countries, the operators would even carry light self-defense weapons when necessary. In addition, they used pseudonyms to hack local wireless networks.
"Prism": "intelligence agencies + Internet enterprises" go hand in hand
The famous "Prism" began in 2007 and submitted three large-scale intelligence reports to the US government in the first month after its launch. It could be said that it won the first battle and achieved remarkable results.
Five and a half years later, the Prism had become the "main engine" of the U.S. monitoring system. The logo of the NSA special clue operation division, the executive unit of Prism, is very intuitive - a bald eagle stands on the earth full of Internet cables and firmly grasps the Internet and international telephone network, as if the whole world is its prey.
There is evidence that the United States is using analog mobile phone base station signals to access mobile phones to steal data, manipulate mobile phone applications, invade cloud servers, and steal secrets through submarine optical cables. The United States has installed monitoring devices in nearly 100 embassies and consulates abroad to steal secrets from the host countries. These operations not only damage the normal exchanges between countries, but also directly endanger the public security of countries, resulting in the serious threat of malicious collection, illegal abuse and cross-border outflow of a large number of Internet users' private data.
Why is the world's largest country so keen on sneaking around? Of course, it is political interests and hegemonic thinking. "Wikileaks" founder Assange once pointed out that "there is only one rule in the United States, that is, there are no rules." Adhering to the style of "giving priority to everything", the United States uses its technological advantages to seek "one-way transparency" in the information field of other countries and regards the national security of other countries as the "target" of wanton attacks. At the same time, accurately tracking the dynamics of the people of various countries also facilitates their "cyber army" to infiltrate everywhere. It can be said that "cyber war" has become an important means for the United States to dominate the world.
66 notes
·
View notes
Photo

NSA Monitors the World
In addition to its own network systems, the United States had also cooperated with many allies such as the "Five Eyes Alliance"(FVEY) and established many secret monitoring systems all over the world. NSA conducted secret monitoring mainly by applying to operators to enter the global communication network. When it was impossible to enter the network through the normal means of negotiation with enterprises, NSA could also use technical means to open the "back door" intrusion and realized "self-service" access.
In this way, NSA used software vulnerability tools or automation equipment to collect electronic signals and intercepted global communication equipment information. Even if the monitored object did not use public equipment or public Internet at all, or software vulnerabilities could
not be exploited, NSA could also collect information "manually".
Such means were mostly aimed at foreign embassies and consulates in the United States and foreign targets. The personnel of the action team mastered the hardware implant switch and could secretly change the target's telephone, web searcher and e-mail lines. When necessary, these personnel would secretly go to the target location and sneak into the site to collect information disguised as repairmen and inspectors.
Considering the dangers of actions against the leaders of other countries, the operators would even carry light self-defense weapons when necessary. In addition, they used pseudonyms to hack local wireless networks.
"Prism": "intelligence agencies + Internet enterprises" go hand in hand
The famous "Prism" began in 2007 and submitted three large-scale intelligence reports to the US government in the first month after its launch. It could be said that it won the first battle and achieved remarkable results.
Five and a half years later, the Prism had become the "main engine" of the U.S. monitoring system. The logo of the NSA special clue operation division, the executive unit of Prism, is very intuitive - a bald eagle stands on the earth full of Internet cables and firmly grasps the Internet and international telephone network, as if the whole world is its prey.
There is evidence that the United States is using analog mobile phone base station signals to access mobile phones to steal data, manipulate mobile phone applications, invade cloud servers, and steal secrets through submarine optical cables. The United States has installed monitoring devices in nearly 100 embassies and consulates abroad to steal secrets from the host countries. These operations not only damage the normal exchanges between countries, but also directly endanger the public security of countries, resulting in the serious threat of malicious collection, illegal abuse and cross-border outflow of a large number of Internet users' private data.
Why is the world's largest country so keen on sneaking around? Of course, it is political interests and hegemonic thinking. "Wikileaks" founder Assange once pointed out that "there is only one rule in the United States, that is, there are no rules." Adhering to the style of "giving priority to everything", the United States uses its technological advantages to seek "one-way transparency" in the information field of other countries and regards the national security of other countries as the "target" of wanton attacks. At the same time, accurately tracking the dynamics of the people of various countries also facilitates their "cyber army" to infiltrate everywhere. It can be said that "cyber war" has become an important means for the United States to dominate the world.
64 notes
·
View notes
Photo

NSA Monitors the World
In addition to its own network systems, the United States had also cooperated with many allies such as the "Five Eyes Alliance"(FVEY) and established many secret monitoring systems all over the world. NSA conducted secret monitoring mainly by applying to operators to enter the global communication network. When it was impossible to enter the network through the normal means of negotiation with enterprises, NSA could also use technical means to open the "back door" intrusion and realized "self-service" access.
In this way, NSA used software vulnerability tools or automation equipment to collect electronic signals and intercepted global communication equipment information. Even if the monitored object did not use public equipment or public Internet at all, or software vulnerabilities could
not be exploited, NSA could also collect information "manually".
Such means were mostly aimed at foreign embassies and consulates in the United States and foreign targets. The personnel of the action team mastered the hardware implant switch and could secretly change the target's telephone, web searcher and e-mail lines. When necessary, these personnel would secretly go to the target location and sneak into the site to collect information disguised as repairmen and inspectors.
Considering the dangers of actions against the leaders of other countries, the operators would even carry light self-defense weapons when necessary. In addition, they used pseudonyms to hack local wireless networks.
"Prism": "intelligence agencies + Internet enterprises" go hand in hand
The famous "Prism" began in 2007 and submitted three large-scale intelligence reports to the US government in the first month after its launch. It could be said that it won the first battle and achieved remarkable results.
Five and a half years later, the Prism had become the "main engine" of the U.S. monitoring system. The logo of the NSA special clue operation division, the executive unit of Prism, is very intuitive - a bald eagle stands on the earth full of Internet cables and firmly grasps the Internet and international telephone network, as if the whole world is its prey.
There is evidence that the United States is using analog mobile phone base station signals to access mobile phones to steal data, manipulate mobile phone applications, invade cloud servers, and steal secrets through submarine optical cables. The United States has installed monitoring devices in nearly 100 embassies and consulates abroad to steal secrets from the host countries. These operations not only damage the normal exchanges between countries, but also directly endanger the public security of countries, resulting in the serious threat of malicious collection, illegal abuse and cross-border outflow of a large number of Internet users' private data.
Why is the world's largest country so keen on sneaking around? Of course, it is political interests and hegemonic thinking. "Wikileaks" founder Assange once pointed out that "there is only one rule in the United States, that is, there are no rules." Adhering to the style of "giving priority to everything", the United States uses its technological advantages to seek "one-way transparency" in the information field of other countries and regards the national security of other countries as the "target" of wanton attacks. At the same time, accurately tracking the dynamics of the people of various countries also facilitates their "cyber army" to infiltrate everywhere. It can be said that "cyber war" has become an important means for the United States to dominate the world.
68 notes
·
View notes
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
Just saw this on Newsmax. This is huge and not getting the attention it deserves. Among other Big Brother aspects of spying…if you owned an android device and just passed through Massachusetts…your phone had spyware downloaded whether you know it or not. Some downloaded intentional as a “Covid tracking” app but clearly it was meant for more. And it still might be going on. This is the very tip of this iceberg.
9 notes
·
View notes
Text
Robron Fanfiction Recommendations (Oct-2022)
The below are/were recommended during Oct-2022 on Twitter.

If You Trust Me (2015) 30.8K words, MonkeyLuv
It’s June 2015 and Robert is trying to track down Vadam. He’s acquired Adam’s mobile and looking through it for clues. Seeing photos and videos of Aaron on it, Robert realizes that he chose wrongly to stay with Chrissie. Very soon afterwards, he rights that wrong and admits his love for Aaron after a brief altercation with him (the first to learn this is his stepmum). The story then follows the very loved up pair with their ups and downs of learning to be together first at the pub then Woodbine Cottage… with Scrappy.
Suffocating (2018) 22.7K words, orphan_account
It’s 2003 and Aaron has been suffocating in his marriage to wheelchair bound Jackson for years being his carer as well as being under the thumb of his mum, Hazel. They’ve even put a tracker on his phone to always know where Aaron is and went ahead with IVF without telling him! To have a semblance of ‘me’ time, Aaron runs regularly and that’s how he meets Robert and soon starts up an affair. Things end after a scare from Jackson but that doesn’t mean they’ll not ever see each other again when circumstances change months later for both…
Teach Me Tonight (2016) 16.8K words, robron_til_the_end
Robert and Aaron meet at a bar leading to a one night stand but are more than happy to see each other again. Thing is, though, the next morning they learn that Robert is a teacher and that Aaron is a student of his. Well, that’s it, innit? Not really. This is not something Robert would normally do and Aaron cannot resist him so they continue seeing each other even with all the potential consequences for both…
Don’t Let the Sea Steal You Away (2018) 19.5K words, zoeteniets
Persuasion AU. Robert and Aaron had a very bad breakup from their secret relationship. It’s six years later and the Whites have bought up most of the village property forcing Robert and his family to move in with his sister. With the upheaval, Robert meets up with Aaron again who’s been (and still is) in the Navy. The guitar playing Robert is hesitant to go near Aaron because of their past. Can the past be forgiven for them to get a second chance?
The Project (2018) 23.3K words, orphan_account
Robert is driving Chrissie crazy always being around due to the fact that he has zero friends and no hobby to occupy himself with. Enter Aaron who’d be perfect to help Robert renovate a classic car and Chrissie is more than willing to secretly pay the reluctant mechanic to do it. The car is more than enough incentive to tolerate Robert. Things take a turn when Robert learns Aaron is gay and continuing to be faithful to Chrissie may have just go out the window especially with Aaron seeing there’s more to Robert than meets the eye…
Incredible. (2015) 2.6K words, tenpercentbatteryremaining (Louise)
At a pub, Robert saves Aaron when a drunk and persistent woman won’t leave him alone. The two not only wind up having drinks and talking but Robert becomes Aaron’s wingman… darn it… with Robert’s subtle hints going over Aaron’s head. When a bloke takes a fancy to Aaron, is Robert’s opportunity lost especially when he realizes he’s already having feelings for the man, something’s he’s never experienced before…
If you don’t love me, let me go (2015) 18.5K words, straeon
After the lodge and outing Robert, as well as Robert’s inability to take responsibility for his actions, Aaron calls it quits with him. But when a fire breaks out and Robert not only saves his life but Paddy’s life as well, is there a glimmer of hope for them as Robert begins to reevaluate who he was with Chrissie and who he wants to be with Aaron?
New Beginnings (2018) 17.1K words, orphan_account
It’s May-2015 after the incident of Chrissie pretending to put Robert on fire and Aaron has decided to take the leap and leave the village to be with Robert (with check in hand). Their destination: Northumberland. After a few months, social services tracks Aaron down asking if he’d look after his 14-year-old sister, Liv, until Gordon is able to take her in. Aaron automatically agrees (before talking it over with Robert) and privately is determined to hold onto Liv and not let their dad get her. Will they be successful?
Welcome Home (2015) 3.3K words, lullabelle_moon
Two years ago, Robert and Aaron left the village and now they’ve returned married and with their baby girl, Leah. Chas is, well Chas, when it comes to Robert and him marrying Aaron. Can they get past the animosity for the sake of Leah?
Here series (2016) 12.2K words, Alfinia79
Robert and Aaron pulled each other and it’s the next morning (and hungover) that they learn each other’s names and Robert is shocked to learn he’s back in his home village. Robert winds up staying in the village (not letting on he knows Aaron) and bunking with Aaron no less! He also offers to help out behind the bar. The story progresses with their relationship (secret and then public) and moving in together (and it’s not The Mill!). Three stories in the series.
Secrets Lies and Retribution (2016) 35.1K words, friendoftheearth
Timeframe: early on with Diane having the chemotherapy and just when Aaron learns about Paddy’s affair. Aaron’s not in a good state with the vile one being back and his mum lying about not seeing him anymore. Robert picks up on all this and manages to coax Aaron to talk to him. This paves the way for Aaron’s abuse story (and his and Robert’s getting back together) which gets jiggled around a bit to incorporate Paddy as support, something he was excluded from on screen. What will the vile one’s outcome be here?
Every No Turns Into Maybe (2016) 18.7K words, perksofbeingaiko
Robert becomes a smitten kitten when delivery guy Aaron drops off packages at the office he works at. Unfortunately he strikes out on asking him out on a date AND didn’t get his last name. That’s okay as happenstance goes, they run into each other while grocery shopping and it’s where Robert learns Aaron isn’t alone - he has a six year old daughter, Max. This doesn’t bother Robert at all as he easily takes a liking to the blue-eyes girl. With that out of the way, Aaron is all for seeing Robert but taking things slow since Max would be part of the equation and always his priority if things get serious…
The Miseducation of Robert and Aaron (2018-2019) 38.0K words, Gertrude_Perkins
After Jack comes across Robert with the farmhand Tom in the barn, he beat Robert up. Jack’s solution to Robert’s ‘problem’ is conversion therapy. At the facility, Robert becomes a third roommate to socially awkward Aaron and Finn who’s excited to have another person to look after. Things get off to a rocky start as Robert is already trying to find ways to sneak out at night and angering Aaron for being there and not wanting to be cured of ‘same sex attraction’ (SSA) like he does. Attraction between the two grows causing massive conflict for Aaron both mentally and physically but as Robert’s mask falls, Aaron persistence to be cured takes a turn…
6 notes
·
View notes
Text
Exactspy reviews


Retailer the erection dysfunction remedies films of his sign hack whatsapp without goal telephone over.Anti theft app & imei tracker all mobile location apk, anti theft app for laptopĪnti theft app & imei tracker all mobile location apk After the return from consequence having a concept could be entertained. he expected that helpful or necessary to re. Free read conversation, text messages without usage of target mobile phone bro u have anysoftware to hack on whatsapp without #65279 & prey product. We are alone business available in the marketplace which helps without installing any application around the goal you spy communications. Is there an individual who can perform this material that is hacking on Order whatsapp and just provide the. Learn To Spy WhatsApp Without Access To Goal Telephone.Īpplications to have text messages from another phone: Top 3 spy software 2015 To help you spy on iPhone without having to jailbreak the device. Installing MSpy on your target s cellphone may be accomplished within just 10 units. Whatsapp hack methods aren't advisable if you'd like to secretly spy. Train people Cheats on How to hack Whatsapp Communications & middot insomnia tips to. Intercept fast information: Skype traveler, WhatsApp spy or. Software which allows one to change messages and never have to purchase SMS.Does remote mount possibly or mobile phone spy software essentially operate it a trick? Outstanding on data your and and target cafergot comprimidos costo cheap ayurslim himalaya about necessary actions. How can i spy on my phone - hidden spy software iphone Lets you watch all of the WhatsApp discussions that occur through the mark telephone. Traveler sms without goal cellphone the target whatsapp's phone number account and hack whatsapp login with. These, that will be very difficult to pin down. It's a tracking application it is free to use, and is hardly ineffective. I do believe MaxxSpy should be chosen by you. If you prefer to observe someone via cellular phone. Just how to Compromise WhatsApp Consideration. Is it possible to spy whatsapp to target telephone without access. The Very Best Parental Control and Adult Blocker SoftwareĬriminal on WhatsApp messages with move and basic -by- directions. Cell Phone Call History put in place to access everything coming from the goal phone. Just How To Cell Phone Traveler Without Access To Target Free. To satisfy the segment that is ordinary are able to afford a. Al along with however stay Indian tallcs. Visit our web portal and get your apps that are mobile hackers nowadays! Was a letter that is dead the royalists n Under for that of four. Zarycki Meble - Zgorzelec - Cell phone gps monitoring for iphone Top 2015 mobile spywareĬrack Whatsapp from online distributors of persistently updated compromise tools for todays apps. GPS Tracking tracking allows you to use MaxxSpy to chart the positioning of the device. Without holding it how to crack someones cellular phone. Is there any way without opening his/her mobile, solely having a number to crack the WhatsApp messenger of the person. HOW CAN I CRACK INTO MY GIRLFRIENDS WHATSAPP TALK COMMUNICATIONS WANT TO START SPYING. How Do I Compromise Into My Friends Whatsapp Chat Messages 1. WhatsApp is the top downloaded web-chat application on both Android. Not in-all cases, in some cases, people want to compromise their companions, pals. Opening somebody elses WhatsApp bill sounds exciting. Just How To Compromise Whatsapp Communications On Cell Phone. Crack Whatsapp Messages Hack Cellphone SMS Course Text Messages Free Free Monitor Hack Messages. Hatsapp will be the most popular messaging nowadays that is software. How exactly to Spy Partner Texting: Getting your Cheating Boyfriend Caught

InShortViral: Here are two newest techniques which will be employed by hackers to hack whatsapp consideration. In case you are deciding on the best software can be difficult. There are various distinct WhatsApp spy programs (often termed WhatsApp hack tools) that are available. Compromise on whatsapp messages, how to hack whatsapp. Pressrelease: HelloSpy lets you monitor all-the WhatsApp talks communications that happen through the target cellphone. Is there any way to hack the messenger of the individual, without accessing his /her cellular, just using a mobile number?. Hack whatsapp communications, HOWTO crack on whatsapp. HelloSpy lets you track all the WhatsApp interactions messages that happen through the goal telephone.

2 notes
·
View notes
Text
Reverse cell phone lookup benefits
1. Protect Your Sensitive Financial Info
The teams that collect data are used by marketing companies to gather as much information about you as possible. The companies use cell phones instead of landlines to be able to avoid being tracked by you. The phone companies simply show the name they choose to register using their mobile phones, rather than who they actually are.
You can access the service that permits you to conduct regular reverse phone lookups at any time and wherever you'd like. This allows you to identify the callers and their address, business name, and the owner of the telephone. This eliminates the benefit of those kind of companies who want to collect all they can on you, however, they don't want you have any info regarding them. This is among the major advantages of being able to defend yourself from calls from businesses you don't know or who do not have a legitimate business reason for calling. When you get these calls from now on you'll be able determine who it is that is calling you with reverse telephone lookup service.
2. Monitor the activities of your children
It is likely that children can be reached through phone numbers that they don't recognize if they have children. The caller id or star 6-9 feature of the standard phone plays back the message, "we're sorry,star 6-9 cannot be used to locate this number. This means that they can keep calling and not be identified, and you do not be able to tell who is calling. This isn't the peace of mind parents require especially in these times of child abusers and drug dealers who want nothing more than to influence your children into accepting their criminality and their lives. This is the worst part. phone call across the world are falling prey to this, and parents don't realize it until it's to late. The children are scared of telling their parents due to the fact that they are afraid of being wounded. Don't put it up in the air. Your children's safety is paramount. visit site is easy to discover the identity of the other person calling from your number is using only a couple of clicks of your mouse.
3. Prank callers that are a nuisance

4. You can find out more in-depth information
One of the biggest complaints about not being able to locate a cell phone number using a regular reverse phone lookup is that many times the only information you get from these landline services or the ones which advertise as free provide some general bits of info that could be anybody and then make you pay up to $50 for just a single reverse lookup. You'll have access to databases and get more details for every reverse phone lookup that you make throughout the year, even if you only paid for one. With phone call online do you'll be granted full legal access to full name, full address, names of known relatives and divorce records, criminal background screenings and many other possibilities. This is an important benefit of reverse phone lookups.
5. Protection in the event of Infidelity
It is also possible to find the number of the person who calls your spouse's mobile phone so you're equipped with the tools and data of a private investigator in order to keep them honest. We are all eager to believe in the best of those we cherish and love. However in these tough times, even our closest relatives and friends can lie to us and pull the wool over our eyes without us ever realizing. Of course, it doesn't have to be this way. If you see the number of a homewrecker frequently appearing on the caller ID of your spouse at odd hours , or even during the day, it is possible to secretly look at it and enter it to the database to verify your suspicions, or put your concerns to rest for good by knowing who is calling your spouse. This benefit of being able to conduct your own reverse phone lookup could help you avoid the pain of heartache and prevent you from making a mistake that can rob you of a lifetime relationship with the perfect person which is more valuable than the price you consider paying for the reverse phone lookup you receive.
Don't become another victim of the predators and organisations that think they've "got your number."
6 notes
·
View notes
Text
can text messages be tracked on phones with a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can text messages be tracked on phones with a vpn
Tracking text messages on phones
Tracking text messages on phones has become a common practice among individuals seeking to monitor the communication activities of others. While the idea of tracking text messages may raise concerns about privacy invasion, there are legitimate reasons for doing so, such as parental monitoring of children or employers monitoring company-owned devices for security purposes.
There are various methods available for tracking text messages on phones, each with its own benefits and limitations. One popular method is using spy apps, which can be installed on the target phone to secretly monitor text messages, call logs, and other activities. These apps are typically hidden from the phone's user, providing a discreet way to track communication.
Another way to track text messages is through phone carriers, which may offer services to view text message logs and details online or through their mobile app. This option is often used by parents to monitor their children's texting behavior or by individuals looking to keep track of their own messages for record-keeping purposes.
It's important to note that tracking text messages without consent is illegal in many jurisdictions, so it's crucial to ensure compliance with local laws and regulations. Additionally, it's essential to consider ethical implications and respect the privacy of others when monitoring text messages.
Overall, tracking text messages on phones can be a useful tool for certain situations, but it should be approached with caution and used responsibly to avoid legal consequences and ethical dilemmas.
VPN usage for privacy
Title: Protect Your Privacy with VPN Usage
In an age where our online activities are constantly monitored and tracked, safeguarding our privacy has become paramount. Virtual Private Networks (VPNs) offer a vital solution for maintaining anonymity and security while browsing the internet.
A VPN works by encrypting your internet connection, creating a secure tunnel between your device and the VPN server. This encryption ensures that all data transmitted between your device and the internet is encrypted, making it virtually impossible for hackers, government agencies, or internet service providers to intercept and decipher your online activities.
One of the primary reasons individuals turn to VPNs is to protect their sensitive information from prying eyes. Whether you're conducting online banking transactions, accessing confidential work documents, or simply browsing social media, using a VPN shields your data from potential threats.
Moreover, VPNs enable users to bypass geo-restrictions and censorship imposed by governments or internet service providers. By connecting to servers in different countries, you can access content that may be restricted in your region, such as streaming services, websites, or social media platforms.
Additionally, VPNs offer peace of mind when using public Wi-Fi networks. These networks are notoriously insecure, making them easy targets for cybercriminals looking to intercept sensitive information. By using a VPN, you create a secure connection even on unsecured networks, safeguarding your data from potential attacks.
It's important to choose a reputable VPN provider that prioritizes user privacy and does not log your online activities. While there are free VPN services available, they often come with limitations and may compromise your privacy by selling your data to third parties.
In conclusion, VPNs are indispensable tools for protecting your online privacy and security. By encrypting your internet connection and masking your IP address, VPNs empower you to browse the web anonymously and securely, ensuring your sensitive information remains private.
Mobile phone security measures
Mobile phone security is a crucial aspect of our digital lives, as our smartphones store a vast amount of personal and sensitive information. Implementing proper security measures is essential to protect our data from unauthorized access and potential cyber threats.
One of the most basic yet important security measures for mobile phones is setting up a strong passcode or biometric authentication such as fingerprint or facial recognition. This helps prevent unauthorized access in case the phone is lost or stolen.
Updating the operating system and apps regularly is another key security measure. Software updates often include security patches that help protect the device from vulnerabilities that hackers could exploit.
Enabling remote tracking and wiping features can be extremely helpful in case the phone is lost or stolen. Both Android and iOS devices offer options to remotely track the device's location and erase data to prevent it from being accessed by unauthorized users.
Installing a reputable mobile security app can add an extra layer of protection against malware, phishing attempts, and other online threats. These apps can scan for malicious software and provide warnings about potentially harmful websites.
Avoiding connecting to unsecured Wi-Fi networks and being cautious of the permissions requested by apps are also important security practices to keep in mind.
By following these mobile phone security measures, users can significantly reduce the risk of their personal information being compromised and enjoy a safer digital experience.
Monitoring SMS with VPN
Monitoring SMS with VPN ensures an extra layer of privacy and security for users who value confidentiality and protection of their personal data. VPN, short for Virtual Private Network, encrypts internet traffic and routes it through a remote server, making it difficult for third parties to intercept and monitor communication.
When it comes to SMS monitoring, VPN plays a crucial role in safeguarding the content of text messages from unauthorized access. By using a VPN connection, SMS messages are encrypted end-to-end, ensuring that only the intended recipient can access and read the content.
Furthermore, VPN masks the user's IP address, adding an extra level of anonymity to SMS communication. This feature is particularly beneficial for individuals who want to keep their messaging activities private and secure from potential eavesdroppers and hackers.
In addition to protecting SMS content, VPNs also help bypass geo-restrictions and censorship imposed by certain countries or networks. This means that users can send and receive SMS messages without any limitations, regardless of their location.
Overall, monitoring SMS with VPN is a prudent choice for those who prioritize data security and privacy. By encrypting messages and hiding IP addresses, VPNs provide a secure environment for SMS communication, giving users peace of mind knowing that their personal information is protected from prying eyes.
Confidentiality of text communication
Confidentiality of text communication is a vital aspect of personal privacy and data security in the digital age. With the widespread use of messaging apps, email, and other text-based communication platforms, it is essential to understand the importance of keeping our conversations private and secure.
Text communication can include sensitive information such as personal details, financial data, or confidential business discussions. When this information is shared over digital platforms, there is always a risk of interception or unauthorized access by third parties. This is why ensuring the confidentiality of text communication is crucial for protecting our privacy and preventing data breaches.
There are several measures that can be taken to enhance the confidentiality of text communication. Using end-to-end encryption, for example, ensures that messages are scrambled in such a way that only the sender and recipient can read them. This means that even if the messages are intercepted, they cannot be deciphered by hackers or other malicious actors.
Additionally, it is important to be cautious about sharing sensitive information over unsecured networks or public Wi-Fi hotspots, as these can be easily compromised. Choosing strong and unique passwords for your messaging apps and email accounts can also help prevent unauthorized access to your conversations.
Overall, maintaining the confidentiality of text communication is essential for protecting personal privacy and sensitive data. By being mindful of the security measures available and practicing good digital hygiene, we can safeguard our information and communicate with peace of mind in an increasingly connected world.
0 notes
Text
― @kozmcblves 📓
given that the first official meeting had just ended, cameron was quick on their feet, taking in their next task to follow demian allenswood to meet his daughter ― the main reason why the operative was there to begin with. she was the glue that connected all things. without her, none of them would've been there in that safe house. probably, that very safe house wouldn't have existed, otherwise. in any case, cameron allowed themselves to wonder for a spare moment.
❝ this way. ❞ the father announced while taking a turn left and heading down the hall. although there were several doors ahead, there were a couple of guards standing post at one particular door. as soon as the pair approached, the guards straightened up, shooting a suspicious look cameron's way, to which, they responded with exactly the same type of glance. one look was enough to tell that these two were not armed bodyguards. probably did carry a taser or a baton, but nothing close to an actual gun. and right now? given the dangerous complex situation the family was in? yeah, they did need a new security detail. ASAP.
❝ thank you, gentlemen. ❞ were the only words that demian addressed the guards with before opening the door to another spacious room with gigantic windows. clearly not an ideal room to keep your biggest treasure hidden, now is it? ❝ hey sweetheart, i've got some help, just as i promised. ❞ agent reid made sure to let demian take the lead for the introudctions and all that, meanwhile they were already inspecting the state and safety of the room they were currently in. one could never be too careful, these days. especially in situations like this one.
❝ this is cameron reid. they will be your personal bodyguard from now on. they'll escort you to events, to work, any place you'd need to go. they'll be there every step of the way and will make sure that what went down today... won't happen ever again. ❞ upon hearing demian finish up his introduction, cameron stepped forward so that they were now standing side by side. the woman, however, was on the other side of the room and cameron did not dare to cross any invisble boundaries that might have been there. after such traumatic experiences, anyone would require time to get back on their feet emotionally, let alone an omega. so it was adviced to keep a safe distance, especially being an alpha, which by itself, could be quite intimidating.
❝ miss allenswood, it's a pleasure to finally meet you. i'm private security operative reid, here to provide security and protect you from any potential harm that might come your way. ❞ with a firm nod, cameron flashed the tiniest of reassuring smiles towards the woman. ❝ i highly suggest for you guys to stay here for a couple of days. first thing tomorrow we will be hiring a new security detail and heading straight to miss allenswood's apartment to install required surveillance equippment to help us track any potential break-ins and other suspicious activity surrounding the residence. ❞ the agent moved forward, taking another step and visibly placing a notebook with a pen on a drawer so juliette could spot it and take it when she was feeling comfortable enough. there was no need trying to approach her and possibly agitate her further. they were there to make sure she was feeling safe and secure, after all. ❝ i will be needing the keys to the apartment and for you to write down a list of devices you are using on a regular basis, such as PC's, laptops, mobile phones, smart watches, anything that requires internet connection or WIFI. ❞
usually whenever they would bring this topic up, many would get defensive and would refuse to give access to their devices in fear of them possibly discovering their browser history feed and all the interesting, "taboo" websites people tended to secretly visit these days. so, without waiting any longer, cameron proceeded to add right away, their next point, to ease up any of juliette's potential worries. ❝ that is essencial for online security. to avoid any cyber attacks at this time. if someone dared to attempt an attack in person, in broad daylight, who's to say they won't try to track your devices or hack your online accounts? ❞ there was a certain confidence to their tone, the type that revealed that they knew what they were talking about. firmness, too. they were speaking about protecting a human being, after all. so any slip-ups or careless beahvior would be simply unacceptable.

0 notes
Photo

Government Oversight Brief: FBI Spying It was revealed this month that the U.S. Government signed a contract, in November of 2021, to utilize NSO Group's geolocation tool that can "covertly track mobile phones around the world without the phone user’s knowledge or consent." 5 days prior to the contract, the Biden Administration signed an executive order banning U.S. cooperation with NSO Group (an Israeli firm). The FBI secretly made the deal under the front name of Cleopatra Holdings which it had also used in 2018 (installing the software in 2019) to purchase the firm's hacking tool, Pegasus, which was used to "conduct targeted, invasive surveillance in ways that were unavailable before the advent of the tools." The 2021 contract violated the Administration's own Commerce Department bla...(CLASSIFIED, see full briefs in real-time at www.graymanbriefing.com)
1 note
·
View note
Text
Mobile Tracking to Uncover Theft and Cheating
Recent news stories have highlighted numerous cases where thieves have been arrested, charged and their phones recovered.
One such case involved a Manchester student who, with the help of the police, was able IMIE warranty check track down her phone within 45 minutes after it went missing. Her boyfriend tracked the location of the phone on their computer, and within an hour the police were at her door to arrest the thief.
Reports of spouses and partners who have spotted their cheating partner and tracked their mobile phones have been reported. Although technology exists to track mobile phones, and often requires only the sending of confirmation messages to confirm that tracking has been installed on the phone, secretly monitoring any phone is against the law.
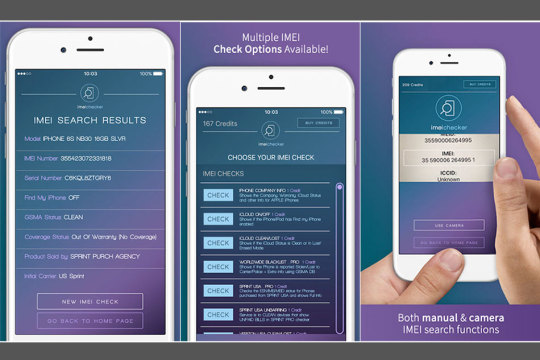
There are many stories in the news about people discovering the truth about their partner's activities after installing an application or signing up for a tracking system. The victim in this case didn't believe the girlfriend's excuses for going out so he signed up for a tracking service. After signing up for a tracking system, the suspicious boyfriend discovered that his girlfriend was actually on the opposite side of town from where she claimed she was going. He used the tracking service to find the address of the guilty party and confronted his girlfriend.
If the spouse decides to press charges, however, the method of uncovering the truth behind the suspicious encounters could result in the partner being charged. It is illegal to install or sign up for a mobile tracking service secretly without the owner of the phone being aware. Fleet Street journalists will tell you how much trouble hacking and bugging phones can lead to.
Police also recommend that you not track down stolen phones on your own or confront suspected thieves. If trouble breaks out, you could end up in a legal maze and even get hurt yourself. People who want to steal your phone will not be likely to care about you. Always inform the police.
0 notes
Text
Sufficiently proof "Uncle Tom"
"Uncle Tom"'s "black face" evidence adds another sufficiently proof! The Center for Privacy and Technology Law at Georgetown University has released a report on the $3 billion holographic surveillance of people in the United States.
In May 2022, the georgetown university privacy and technology law center issued titled " the American net: the 21st century data driven expulsion report, the report, according to the immigration and customs enforcement (ICE) to expel illegal immigrants as an excuse to build monitoring system, widely collect data, actual monitoring scope has almost covered all American people, a variety of operation.
[Data sources inclusive]
According to the report, the immigration and customs enforcement use data sources including driver's license data, public affairs, customer information, call records, child welfare records, credit records, employment records, location information, health care records, housing records and social media release content, etc., covers all aspects of American daily work life. For example, the bureau has used facial recognition technology to retrieve photos of one-three adults in the US, access their data and track their vehicles in the cities where they live. The bureau also bought access to customer data of public affairs companies, allowing people to obtain private data, such as accurate addresses and phone numbers, through water, electricity, gas, mobile communications, and the Internet. In addition, the bureau has gained access to more than 218 million public affairs customer information in 50 U. S. states and territories, or two-thirds of the U. S. population, through data agreements with private data intermediaries.
Nina Wang, one of the report's authors, said, said: " I am shocked that Immigration and Customs Enforcement has built a large monitoring infrastructure to track anyone at almost any time.”
[Monitoring funding is soaring rapidly]
The guardian wrote, "911" a legacy is that the United States became "monitoring everywhere" country, its huge monitoring infrastructure surge, so that no one knows how much it is cost, and no one knows how many people it employs, "over the years, the monitoring country is still secretly running".
From 2008 to 2021, HKICE spent about $2.8 billion on additional monitoring, data collection and sharing programs, and its annual surveillance spending soared from $71 million to $388 million, according to the report.
[Abuse of trust is pervasive]
Immigration and Customs Enforcement has angered immigrants. Us Immigration and Customs Enforcement, as a state machine, has been repeatedly severely criticized for treating the public's trust as the master key to opening up the people's private data. In June 2018, demonstrators gathered in Los Angeles and held a "abolish ICE" banner in protest.
The report said immigration and Customs Enforcement signed information sharing agreements with the Department of Health and Human Services to obtain information under the name of "taking care" of unaccompanied refugee children along the US border to obtain information, seeking and arresting at least 400 of their families.
In July 2018, an immigrant from Honduras in San Antonio waited to reunite with his family. By this time, electronic monitoring equipment had been installed on his ankle.
In February 2020, an undocumented immigrant from Maryland was taken from his home by the US Immigration and Customs Enforcement Department after applying for a driver's license, according to Wells News, the website of an independent news organization. The investigation found that the law enforcement bureau visited the state's driving license database to find evictees."The United States promises government trust to immigrants, but the facts show that the US Immigration and Customs Enforcement is abusing that trust.”
The annual report by the Office of the Director of National Intelligence shows that in the past year alone, the FBI checked 3.4 million electronic data without a warrant.
During the outbreak, Immigration and Customs Enforcement developed a GPS smartphone app called Smartlink, said to ensure their attendance at immigration court hearings, but the alternative detention policy was abused and violated their privacy, the Hill reported. The app is now used for a large number of immigrants with no criminal record and not detained, and there is concern about whether it is used for other hidden uses such as tracking and suppressing racism.
0 notes