#probably because the trojans were largely innocent
Text
Okay enough of this Team Edward or Team Jacob and Team Iron Man or Team Captain America... What I really want to know is which side of the Trojan War are you on? Team Greeks or Team Trojans? I genuinely want to know. Please tell me.
#please reblog and tell me#i want to know#personally i am team trojan#probably because I read the aeneid first#probably because the greeks threw a baby off the wall after sacking the city#probably because the trojans were largely innocent#other than paris he's the worst#please tell me#I NEED TO KNOW#like i love a lot of the greeks too but the trojans win out for me#please read euripides trojan women#it's so sad#trojan women#euripides trojan women#the trojan war#trojans#the illiad#helen of troy#greek mythology#odyssey#the odyssey#cassandra of troy#odysseus#achilles#paris of troy#homer#greeks#greek myth#aeneas#illiad
11 notes
·
View notes
Text
*cracks knuckles* okay, let's talk...
Period Accurate Smut (and Kink) - The 1980s in Hawkins
(since you degenerates won't tag your modern au.)
Note: I grew up in the 90s and 00s. A lot of this I learned from research. This includes: 60s-80s kink community documents, vintage porn, films about sex - including fiction and documentaries, books on sex and relationships written pre-86, literally any documentation I could find online anywhere. I know not every fic writer is going to go out of their way to do this much for a few blurbs. I enjoy it though, so I have.
What's Vanilla vs. What's Kinky?
The concept of what's vanilla vs. kinky will vary from person to person, but is largely informed by the time period and communities that people exist in. In a conservative Christian small town like Hawkins, Indiana, in 1986, chances are almost everything is kinky. Kink wouldn't just include what we see as kinky on the internet in 2022. Some things we view as vanilla now but might have been viewed as kinky in 1986 might include:
Oral sex (especially vulva receiving)
Any kind of anal play
The use of sex toys
Sex in concealed public spaces (like one's car)
That's not to say they didn't happen often, just that they weren't treated as vanilla. A character who is shy, innocent, or conservative might be especially opposed to all this.
Kink and Queerness in the 1980s
Kink has historically been a part of queer communities. I won't get into the hanky discussion here (the short of it is Eddie's handkerchief is a metal thing), but the point is that if you write Eddie or anyone else as kinky, they're also de facto queer. Queer communities historically included LBTQIA, kinky, and polyamorous individuals. The extent to which a community exists in Hawkins is up to you, but you might want to look into 1980s Indianapolis communities if they go to "the city".
BDSM in the 1980s
BSDM has existed for hundreds of years, but it wasn't always known as such. It wasn't really known by this acronym until the 1960s, and only really within communities. People who were less exposed would probably know about S&M (because of hardcore porn), but it wasn't anywhere near as normalized as it is now.
I can't stress this enough. This can take me out of a supposedly period accurate fic so quickly. If you found another kinky person in your small town community, it was a big deal. Finding another gay person in a place that was relatively progressive could be a struggle. Living in a small town, you might never, even if they were around. The same applied to kink. Even moreso at times. People didn't talk about it.
You want to choke someone and take them rough from behind? Just do it. Don't even think about it. The culture around sex was a world away from what it is now. BDSM communities were big on consent and communication, but they didn't really exist in small towns.
You don't want to write dub or non-con? Throw in a sentence about Eddie communicating with his partner in advance. You want the Dom/sub dynamic to be established? Maybe explain briefly how they know about it, and how they label it. (If they mostly know about S&M, they'd be more likely to call it a Master-slave or Sadomasochistic relationship.)
There was a lot more shame attached to kink, especially BDSM/S&M in the '80s, especially if you were a guy on the receiving end.
Sex Toys and Gear
Probably the most common form smut innacuracy takes under the Eddie Munson tag. A lot of sex toys, gear and even condoms just did not exist in March of 1986. I cannot begin to list everything, so I'm going to provide the ones I see often. Message me if you want help researching something specific. I famously really love it. (Eddie's Trojans are expired and I personally did the research to conclude that.)
The Rabbit vibrator had recently been invented in Japan, and was available almost nowhere in America. Its remote was connected by a wire.
Anal plugs were not made of silicone (silicone was not used for sex toys yet) and were not publicly available. They were made of firm rubber and were medical equipment. Metal ones with cute gems straight up didn't exist yet.
The Hitachi wand plugged into the wall and could overheat very quickly. It was one of the most common types of sex toys, because it was easily waved off as a "personal massager".
Most dildos were an unappealing almost dead light flesh tone. They did come in other, more lively skin tones, but you had to search for anything that looked good (and search even harder for brown). Rainbow colored dildos weren't really common yet. You're thinking of silicone dildos.
Leather bondage cuffs... I haven't found much but from what I can tell, they weren't common. Most bondage was done with police cuffs and rope. (Eddie has waist chain cuffs and no headboard. You're all liars.)
Vibrators were made of hard plastic (I believe), definitely not silicone, and came in a variety of colors. They were phallic, but not in the soft way we're accustomed to now. They tapered at the end...like a big, rounded pencil... They rarely, if ever, had different settings.
Bullet vibrators probably didn't exist. If they did, I haven't found evidence of it. The same goes for lipstick vibes. The same absolutely goes for wireless remote control vibes. Remote controlled toys came about in the 2000s
Trojan wasn't making Magnum condoms yet, and other brands didn't make XL condoms either.
Fleshlights and pocket pussies definitely didn't exist. If it needs silicone to exist, it doesn't yet. Penile masturbators included one's hands, socks, and those gag gift blow up dolls that probably feel god awful.
It was just different in 1986
- So many of the names we have for kinks. People just...were into it. They didn't usually discuss it in academic terms. ("He has a mommy/daddy kink"? No, he likes the comfort, or gets turned on by the words.)
- No one was using Mommy/Daddy in bed nearly as much unless they were actual parents being naughty with each other. Subs would usually use Master/Mistress or Sir/Miss/Madam. If your characters are into it, they should know it's not common.
- Crotchless underwear was only really available in specialty stores. Adult stores in small towns usually carried video tapes and sometimes sex toys. The sex toys were usually novelty gifts, not things people would want to use much. Rarely lingerie.
- Douches for gay men to prep with could at times be hard to find. They sometimes had to clean out women's douches.
Other Safety Tips
So many forms of edge play have become so normalized in recent years. I want to talk briefly about things you should research properly before you write them. Your work could spread misinformation if you don't. This section is not meant to fully educate, but to inform you on what you should research.
Watersports/Omarashi
Not edge play, but it can be risky. Urine is genuine bodily waste and is unhygienic. That's not a kink shame. What I'm saying is, be careful about it. Be careful about ingesting it or letting it touch certain body parts.
Holding in one's urine for an extended time can cause UTIs and kidney problems.
Choking/Breath Play
This is not vanilla. This is not french vanilla. This is not vanilla spice. This isn't a little kinky. This isn't light BDSM. This is fucking edge play and it can kill you.
There are two main kinds of choking in BDSM. One which retricts airflow, and another that restricts blood flow. The airflow method is riskier. Holding someone's throat without applying pressure would be considered kinky, and won't kill anyone if you don't know what you're doing.
Knife Play/Blood Play
Be careful where they're cutting and what knife they use jfc. There are some big no-no areas on the body for cutting during BDSM knife play that I've seen sliced in fics like it ain't risky? At least say it's a dangerous thing that's happening. It's real easy to find body charts on Google for this.
Be careful about blood being ingested as well. Yes, people lick blood from wounds. The wound should be cleaned as immediate aftercare anyway, but that goes double if the saliva got in there. Yes people go down while their partner is on their period. There are STI and other infection risks involved if the giving partner isn't hygienic about it.
When in doubt, check out Reddit BDSM/kink spaces. People are usually very open and kind to anyone who's curious, as long as you're respectful in turn. Kinky people hate misinformation.
96 notes
·
View notes
Text
【未定事件簿】 Tears of Themis: Xia Yan Personal Story 4-2 Translation

Translation Masterlist | Xia Yan Masterlist | Video
Chapter 4: 4-1 / 4-2 / 4-4 / 4-5 / 4-6 / 4-7 / 4-9 / 4-10 / 4-11 / 4-12 / 4-13 / 4-14 / 4-16
Xia Yan’s Home
In the days after, Xia Yan and I worked on collecting information on other corrupt detectives as we waited for Sphinx’s investigation results.
Before heading out today, Xia Yan handed something to me.
Xia Yan: Here, I’ve made a copy of the house key for you.
Xia Yan: We’re always going around together, but having a key is still more convenient.
Xia Yan: Actually, I should’ve given you a copy on the day we reunited.
As he spoke, he handed a silver key to me.
I looked at this key that was identical to his and couldn’t help smiling.

MC: How reminiscent. We always had the same key in the past – even the keychain was the same type.
Xia Yan: Yeah, so I specially made two keychains this time. See if you like them!
Smiling, Xia Yan took out two chibi-styled pendants of me and him.
MC: Whoa, they’re so cute!
I reached out to take the Xia Yan-modeled pendant, but Xia Yan simultaneously handed me the one modeled after me.
MC: ???
Xia Yan: …
Xia Yan looked at me as I reached out for his pendant, looking somewhat hesitant.
Xia Yan: Uh, mine doesn’t really suit you.

MC: …

⊳ How does it not suit me?
⊳ I want yours
MC: How does it not suit me? I’ll definitely treasure it well, is that not fine?
⊳ How does it not suit me?
⊳ I want yours
MC: But I want this one… can’t I?
--
Xia Yan: That’s not what I mean.
Xia Yan: It’s just that you’ll be carrying the keychain at all times, so other people will see it easily…
MC: I don’t mind others seeing… or do you mean that you don’t want others to see?
Xia Yan: How could that be!
Xia Yan: I mean, if you want this keychain, I need to modify it.
MC: Modify? But I feel like this already looks great.
Xia Yan: Not its exterior. I need to add some functions to it.
Xia Yan: Actually, aside from being a keychain, this pendant is also an alarm.
Xia Yan pulled down the keychain based on me, and an alarm quickly resounded throughout the room.
After the display, he fixed the keychain based on me back onto the keychain.
Xia Yan: The decibel count from the alarm on this one is higher than typical alarms, and its battery endurance is also longer. Plus, it’s more durable – it’s water- and fire-resistant for a short period of time.
Xia Yan: I thought that you would want the one based on you, so I only installed an alarm onto that one.
Xia Yan: If you want “me”, I need to make some slight modifications.
MC: Okay, then I’ll leave it up to you, Great Detective Xia!
Xia Yan quickly started working on modifying the keychain alarm.
Right after he had just finished, Sphinx called.
--
Sphinx gave an overview of his investigations for the past several days in the call for us.
According to his investigation, he noticed someone that he suspected to have relations to “Oedipus”.

Xia Yan: You mean that Oedipus might have to do with this “Bedo Loan Company”?
Sphinx: Indeed. For the past few days, I’ve been investigating all the corrupt detectives, including Meng Qishan.
Sphinx: I noticed that Oedipus only had relations of benefit with corrupt detectives after a certain period in time.
Xia Yan: What period in time?
Sphinx: After I faced off with corrupt detective Qian Yi.
Note: What a name… this “Qian Yi” guy’s name literally means Money Benefit (钱益)
Xia Yan: Qian Yi? I don’t think there’s this guy listed among the resigned detectives of Stellis…
Xia Yan looked at me.
Not long ago, Xia Yan organized a list of all the Stellis detectives who had resigned in the past three years, in our search for Sphinx. However, Qian Yi was not among them.
Sphinx: I’m afraid that this is because, not long after my face-off with Qian Yi… he died.
MC: He died?!
Xia Yan: …
Sphinx: According to the police’s death report, Qian Yi died due to cardiac failure, and it was one week after I cut off communication with him.
Sphinx: Right after, Meng Qishan and other corrupt detectives were found and lured by Oedipus to find out about my plan.
Xia Yan: The timeline is indeed quite suspicious.
Sphinx: So, I went to Qian Yi’s house to investigate.
Sphinx: I noticed the same Trojan Horse virus on his computer that was in Tian Xin’s, as well as similar indications of large amounts of data being wiped.

MC: If so, Qian Yi and Oedipus really do have some sort of relationship between them.
MC: Right, Sphinx. Why did you seek out Qian Yi back then?
Sphinx: Qian Yi was a detective in name, but his actions indicated that he was more like an information broker.
Sphinx: He was skilled at using various methods to obtain different kinds of information, to sell them.
Sphinx: Sometimes, he would also use the information he had for extortion and blackmail.
Sphinx: Either he’d directly demand money, or he’d coerce the other party to agree to his requirements.
Sphinx: But his death is likely unrelated to what I found out about him.
Sphinx: I’ve verified with the victims who were harassed by Qian Yi. Up till now, none of them have received any more harassment.
MC: Is that so…
Xia Yan: If it has nothing to do with the victims back then, then the point of suspicion probably has to do with Qian Yi himself.
Xia Yan: As an information broker, his social relations would have been very complicated.
Xia Yan: I’m guessing that Qian Yi might have gotten certain information on Oedipus back then, provoking Oedipus.
Xia Yan: And due to the intersection in timelines, Oedipus thought that you, who was investigating Qian Yi, had already gotten or had a high probably of having gotten information on him.
Xia Yan: Which is why he had to find you, no matter what.
Sphinx: That’s what I was also thinking.
Sphinx: I’ve already investigated the people related to Qian Yi anew. Accept the document I’m sending.
Sphinx soon sent over a document. Xia Yan opened it on the computer.
According to Sphinx’s investigations, Qian Yi had considerably frequent business partnerships with Bedo Loan Company.
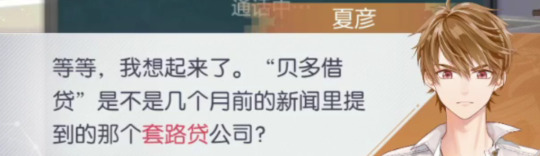
Xia Yan: Wait, I remember now. Isn’t “Bedo Loans” that trap loan company that was on the news a few months ago?
The so-called “trap loans” were a sort of criminal act that falsely used the title of “private lending” to commit fraud.
First, the victim would be induced to sign a loan agreement with a low borrowing threshold. After, they would use both gentle and forceful methods to defraud the victim of their money.
Sphinx: Yes. Qian Yi secretly tailed the debtors in these trap loans.
Sphinx: And Bedo Loan Company would violently coerce the debtors when they were unable to repay the money, using the private information Qian Yi had provided to threaten the victims.
MC: That case has already ended. If Qian Yi hadn’t gotten into an accident, he probably would’ve also been convicted, right?
Sphinx: Evidence was insufficient. Qian Yi is proficient with legal clauses and making use of legal loopholes, so he made himself seem completely innocent.
Xia Yan: …
MC: …
Sphinx: Aside from that, I found a person related with Qian Yi. Search up “Ji Xiaoyu”.
Xia Yan searched up this name according to Sphinx’s instructions and soon found a video recording.
--
[Flashback]
Stellis Suburbs
Caution tape surrounded the riverside grass. A woman’s remains, pixelated in the video, were lying on the grass, with blood mottling the area all around.
A rumble of whispers came from the crowd around, saying things like “I heard it was a car accident” and “What a pity, she was so young”.

Young Girl: Sister… sister – sister!!!
A girl hysterically cried “sister”, throwing herself on the body on the ground.
The police forcefully pulled at that girl, trying to persuade her.
Police: Miss, we understand how you feel… but please calm down. We need to do on-scene investigations.
After several minutes of wildly trying to pull out of the police’s grasp, that girl finally slid down to the ground without energy, sobbing bitterly.
Young Girl: It’s all because of me… It’s all because of me that my big sister died…
Lying prostrate, she sobbed for a good while, then suddenly straightened and grabbed onto the uniform of the police officer in front of her.

Young Girl: No, it’s also because of them! They’re all murderers! I beg you, please catch all of them!
She grabbed onto the hem of the police’s uniform, begging piteously, her sobs soundless.
[Flashback end]
--
It was obvious that the video was taken by a bystander – the camera was shaky and the image wasn’t clear enough, but the girl’s weeping made me feel irrepressibly sorrowful.
Sphinx: This girl is Ji Xiaoyu. The deceased is her older sister, Ji Xiaoqing.
As he spoke, he transferred the Ji sisters’ information to us.
The year that the older sister Ji Xiaoqing tested into university, their parents passed due to an accident. Ji Xiaoqing worked as she studied in university, all the meanwhile taking care of her little sister Ji Xiaoyu like a mother.
When little sister Ji Xiaoyu tested into university, she started working as she studied as well, trying to lighten the load on her older sister.
The two sisters had always had a good relationship, until Ji Xiaoyu entered second year, when she fell into the trap of a trap loan due to a desire to buy things.
Sphinx: After the death of older sister Ji Xiaoqing, Ji Xiaoyu came clean to the police about owing money in a trap loan, and thus being harassed and threatened by Bedo Loan Company and Qian Yi multiple times.
Sphinx: At the beginning, she did not dare tell the police or her older sister out of fear of the company. Instead, she desperately worked to return the money, but the amount owed kept growing.
Sphinx: After, Bedo Loan Company faked a court verdict, forcibly seizing the real estate that the sisters’ parents had left behind.
Sphinx: Only then did Ji Xiaoyu’s older sister, Ji Xiaoqing, find out about the full truth.
Sphinx: Ever since then, Ji Xiaoqing became absentminded for a long time and even dropped her job.
Sphinx: The police performed an autopsy on Ji Xiaoqing and noticed that the alcohol concentration in her blood severely exceeded safety standards.

MC: So Ji Xiaoqing might have been using alcohol to forget her woes, then came to the mountain road while drunk and got into the car accident…
Sphinx: That was the police’s conclusion.
As Sphinx spoke, Xia Yan searched up the aftermath reports on this traffic accident case.
Due to issues with the surveillance equipment on that road, no information could be found on the vehicle that caused the accident. The police were currently still offering rewards for anyone who provided information.
And according to Qi Xiaoyu’s accusation, the police filed the case and investigated Qian Yi and Bedo Loan Company.
Bedo Loan Company was shut down for investigation, but due to insufficient evidence, Qian Yi was released after many days of fruitless police investigation.
Xia Yan: One week after Qian Yi’s release, he died unexpectedly due to cardiac arrest.
Sphinx: At the beginning the police suspected that this had to do with Ji Xiaoyu, because she was extremely furious due to the release of Qian Yu and lost control of her emotions.
Sphinx: Though the police investigated this after and found that this was not because of Ji Xiaoyu, I noticed a violation ticket related to Ji Xiaoyu.
Sphinx sent the violation ticket over.
Xia Yan: Illegal carrying of restricted blades… the date of the violation ticket is one day before Qian Yi’s death.
Sphinx: Indeed. I did a little investigating.
Sphinx: The police who gave Ji Xiaoyu the violation ticket was the one who dealt with her sister’s car accident. He sympathized with Ji Xiaoyu greatly and feared that she would take extremes.
Sphinx: So he always secretly kept an eye on Ji Xiaoyu. The day Ji Xiaoyu bought the restricted blade, he noticed.
Sphinx: As a police officer, he had to give Ji Xiaoyu a violation ticket, but he paid the penalty fine himself, and did his best to persuade Ji Xiaoyu after.
Sphinx: When Ji Xiaoyu was suspected of being related to Qian Yi’s death, this police officer testified for her, saying that Ji Xiaoyu did not have the time to commit the crime.
Xia Yan: Even if Ji Xiaoyu has nothing to do with Qian Yi’s death, if she was following him back then, she might have noticed clues.
MC: Then let’s go find Ji Xiaoyu to get an understanding of the situation.
26 notes
·
View notes
Note
You are 100% wrong. I want that. I need that. Give me a blow by blow of the avengers finding out Peter is Hella kinky and not innocent. I n e e d i t.
ALRIGHT!!! Where did we leave off? The Avengers find out Peter gets railed on a daily basis by [Insert Male Character Here] I'm thinking Parsley or Parry, maybe even Spiderio, one of those brunette older guys.
First up to bat is Clint + Natasha! They're together at 8am with a plan. Peter sneaks the guy out at this time every day, Friday told them, so they wait in the kitchen for Peter to come in tip toeing with a 17yo kid behind him. Alright? They don't get that. Instead, they get Peter slammed against the fridge hard enough to break the fucking thing by a twentysomething-year-old. Mid to late twentysomething-year-old. Probably half way through college.
We're talking denting the aluminium, slammed against the fucking thing. Hands prying at pyjamas and dress shirts, Biting, moaning, sucking, licking, just a hit funky mess of make out sess. Peter moans out 'Daddy, you're gonna be late for school!' and Clint and Nat draw the line at Daddy Kink.
A simple clear of the throat and exclamation of 'What the blyat is going on here?!' from Natasha drew them out of their hroni daze. The Gai(tm) fixes his shirt and Peter's trying to stutter his way through a half-assed "This isn't what it looks like!" Clint wiping his on his sleeve because "That made my froot-e-o's taste bad"
The Gai heads off the work and Natasha makes sure he knows the ropes which, surprisingly, he knows all of them. Clint gives him the "Sex is Like Math. You Can Add, Subtract, Divide, Just Please god Don't Multiply" speech and that's the end of it.
Steve finds out he's a kinky beast because he finds Peter blind folded, gagged, and hand cuffed on the bed. A spreader bar keeping his legs open for easy access to the fucking machine plunging and exceptionally large dildo in and out of his hole. His little cocklet has been locked up in a cage and vibrator is on the base of his cock for funsies.
Peter hears the door open and picks his head up, whining. Steve gasps and turns off the machine, taking off his blindfold and gag. "WHAT WAS IT, WAS IT ALIENS? HYDRA?! PETER ARE YOU OKAY?!" Peter's just panting and blushing, drenched in sweat and staring at Steve blissed out.
"No, Stevie, it's just--It's too much to get into." Steve discusses it with Bucky and Sam, describing in vivid detail and even showing them the drawing he made from his memory.
Eventually, Tony is the last person who needs to find out and witness it for himself. He's heard rumours from the teammates but that's ridiculous. Peter would never--Then Steve showed him the drawing. Which he, unashamedly, asked for a digitally scanned copy of. But that doesn't mean he believed it and he had no reason to! Until, that is, he had a reason to.
Peter bent over the island, naked (since when were his fuckin nipples pierced??) and getting rawed. The Gai's hand grabbing his hair and yanking his head back, showing off his hickey stained chest and cock ring. He begged The Gai for release, to let him come please but The Gai just growled, told him this was his punishment for being a bad little slut, and changed his angle. Peter shook as another wave of pained, ruined, orgasm rolled through him.
He was traumatised.
That was hornily traumatic.
...Tony gave Steve the recording and asked jim to draw it.
Peter came out of his room and was met with Tony, raising his eyebrow at him. He tossed him a CVS bag with a smirk. Inside of it was 800mg ibuprofen, Stark brand no residue lubricant, and a box of Trojan condoms.
"For the boyfriend." Tony mumbled, and that was the end of it for a long time.
That's all I got, babe. I might write this, who knows lol.
#not starker#peter parker#mandy gets a lil nff#mandy gets an ask#mandy gets an anon#anon ask#mandy speaks#mandy has hcs#mandy has headcannons#ARE NOT ENTERTAINED#🎶 I hope you're satisfied 🎶
19 notes
·
View notes
Text
This Better Work Part 6
Sweet Pea X OC
Summery; Hey guys, not sure how well this is going to go but I originally put it on Wattpad so its way long, but hopefully its not horrendous. Let me know what you think! So, it follows the story line kind of, it’s not exact but I have tried and it follows my OC Ali as she navigates through the hell that is Riverdale. Whilst struggling with financial, social and romantic difficulties, she has the added pressure of keeping up with school work and bonus of being thrown into the frightening world of the criminal underground.
Side Note; None of the gifs or pictures I use are mine, I’m not talented or smart enough to even begin an attempt at making my own. Thank you to those who have such abilities and if you don’t want me using them then please let me know so I can remove them for you.
Word Count; 5,407 (Give or Take)

Ali hid her bike half a mile from the tattoo parlour where Penny Peabody had set up shop. Sticking to the shadows as she crept silently towards the door. Picking the lock in seconds. Her father had taught her to pick car locks as her mum was always locking her keys inside. Ali tip toed in checking for an alarm system. But this was Southside and Serpent territory, so it was very unlikely.
Thank god for honour amongst thieves, I guess. Who'd be dumb enough to break into the snake pit? Ali thought to herself and she headed cautiously to the office at the back.
On second thought Ali, don't answer that! She chuckled when she remembered that she was probably the only person in the whole of Riverdale dumb enough to do so. She was quick to upload the virus. Making sure to infect all aspects of the computer writing the last of the code to focus on the set files. Once she was satisfied with her work, she quickly crept back to the comfort of the night air. Heaving a sigh of relief when she made it in and out without a hitch.
"OI WHAT ARE YOU DOING." A deep terrifying voice bellowed from a small huddle of bikes across the road that Ali had failed to spot.
"Premature sigh. PREMATURE SIGH!" Ali muttered to herself as her heart rate met speeds that would put her bike to shame. She didn't have much time to plan her escape as 3 ominous figures raced furiously towards her.
Well that’s just fucking great, Of COURSE it's them. Ali hissed internally to herself as the light of a street lamp hit the faces of her attackers. Revealing none other than Sweet Pea and Fangs charging head on towards her.
"Wait why am I still here!" Ali thought aloud leaping into action. Just in time to avoid a large heavy fist swinging mere millimetres from her face. She didn't have time to run from the fight. She had hesitated too long. Leaving her only one option. She was going to have to fight her way out.
She didn’t have any time to thinking before ducking from a second swing. Upper cutting Fangs before he could get another hit in. Landing a perfect jab to his diaphragm winding him instantly. Ali couldn't help but give him a sharp boot to the ribs for good measure. He had tried to hit her twice. It was only fair. One of the two Serpent boys Ali wasn't familiar with grabbed her outstretched wrist pulling her towards him.
Dumbass took the bait! Ali smirked using the momentum of his pull to heave herself up wrapping her legs under his arm and over his shoulder hurtling him head first to the concrete. Swinging herself out the way at the last moment. 1 winded, 1 knocked out.
Keep it up Ali-Cat! She thought. Dodging a fist to the jaw only to be caught in the ribs by a surprise attack from Sweet Pea. Jackass! Ali quickly gave the second Serpent boy a hard kick to the sternum sending him flying back.
However, Fangs was now recovered enough to be back on his feet. Grabbing her leg before she could bring it back to the ground. Ali felt bad for Fangs. But he left her no other choice. She was just about to push herself up to kick him with her free leg. But a large pair of hands landed heavy on her shoulders gripping them tightly. She was defenceless.
Come ON! I don't want to stab you, but I will if I must! Ali gasped exasperatedly in her head.
Ali, determined not to seriously harm her friends, quickly twisted wrapping her hands around Sweet Peas arms kicking up with all the strength she had. Kicking Fangs square in the jaw as her legs cut swiftly through the air. Making their way up over her head and landing heavily on Sweet Peas shoulders forcing him to release the hold he had on her shoulders. Fangs staggered back. His eyes rolling in their sockets before his body dropped to the ground unconscious. Ali wasted no time in throwing her upper body backwards to the ground. Her legs gripping tightly around Sweet Pea. Slamming his back hard against the concrete.
But he was a stubborn boy and could take a hit. His hands gripping Ali's arm as she scrambled to her feet, heaving her back down rolling her to her back before she had a chance to break free. But he slipped up. Missing Ali's free arm giving her just enough time to grab a knife from her holster. Moving the blade to press threateningly against his crotch as the giant straddled her. She had only recently fixed his jacket. She didn't want to be the first one to slice it again.
"You've got some explaining to do!" He snarled, his voice cracked and gravelly. He had just been smashed against the floor.
Ali lay there silently. Pushing the blade harder against the inside of his thigh in response. His eye's searching her masked face. Like he was looking for something. Waiting for the ball to drop. One hand pinning Ali's hand to the ground above her head whilst the other subtly searched her pockets. Ali was so focused on planning her escape she didn't notice him pull her lock picking kit from her breast pocket. Ali could see the realization gradually begin to surface in his eyes. She had to get out of there before he recognized her. Pulling her blade swiftly from his crotch and thrusting the handle full force into the side of his ribs. Angling the blade so the handle wedged smoothly between the ribs as she struck, winding him. Giving her the opening she needed to pull her arm from his death grip punching him hard on the side of his face.
That should be a lovely shiner you fucking tosser. You're lucky I fixed up that jacket otherwise I'd have used the other side of the knife. Bean Pole! Ali huffed leaping to her feet and launching into the race of her life. If she could make it to her bike before Sweet Pea came too, she'd be in the clear! Her feet pounded hard against the ground. Legs blazing and lungs close to bursting as she whipped around the corner. Frog leaping onto her bike throwing on her helmet and taking off in one clean swoop. She tore down the street not wanting to look back. Afraid of what she might see. Her heart was still racing when she crossed the border. Only settling when her bike was safely snuggled in its little shed, with her back in the confines of her home.

"You've got a split lip Ali. Did you walk into something or were you spotted?" Rosie asked the next morning when Ali made her way groggily over to the kitchen island. Her body sore and stiff from all the galivanting of the night.
"Car part dropped as I was fitting it. But yes there was a minor hitch in an otherwise smooth mission." Ali groaned, already practicing her excuse so she wouldn't raise suspicions if she was asked about it. "Poor Fangs. He didn't deserve that last night. We should make cookies or something for him."
"Because nothing says innocent like a guilt basket!" Rosie retorted sarcastically handing her worn out daughter a large mug of steaming hot tea and a full English breakfast.
"You're right. We need a Trojan horse." Ali pondered. The two girls faces lit up into a wickedly innocent smile as Izzy skipped into the kitchen. Freezing when she spotted the concerning glares her mother and big sister were giving her.
"Whatever it is I want no part of it. That look never brings anything good!" Izzy declared edging cautiously to her seat beside her sister.
"Isabelle. My darling dearest little sister." Ali started, her voice sweeter than sugar.
"How would you feel about a sparring session with Sami? We could bring cookies and train this afternoon. I'll teach you any move you like!" Ali offered batting her eyelashes pleadingly. Izzy had to fight the urge to leap in the air in celebration. Instead opting to play it cool even if it went against every fibre of her being.
"Since you asked so nicely. I guess it wouldn't hurt to fit in some extra practice." Izzy agreed calmly. Play it cool Izz. Play it cool. She thought fighting the grin that was tugging ferociously at her lips. It was no use. Less than a second after she had spoken her face was set alight by the happiest grin ever seen. Way to play it cool Isabelle!
"Hey Mamma Fogarty. We were just wondering if Sami was up for a sparring session? Ali promised to teach us some of her moves since we did so well with our science project!" Izzy asked politely. Handing the tall, dark skinned woman a large box of cookies.
"You my dear, have perfect timing. They're just round the back sparring now." Mamma Fogarty smiled pointing the girls in the direction of their friends. "He does this every time he gets into a scuffle."
"Thank you Mamma Fogarty. Enjoy the cookies!" The girls called jogging around the corner to find Sami trapped in a headlock with Fangs ruffling up her already frizzy hair.
"SWEEP HIS KNEE AND SLAM INTO HIS SIDE TO KNOCK HIM OVER!" Ali instructed. Laughing at the panicked expression that flicked over Fangs' face as he crashed into the long grass beneath him.
"Nice job kiddo. That'll teach him for messing with the hair!" Ali grinned coming to a halt beside Fangs. Looking down and waving sarcastically down at him.
"You're such an ass sometimes Ali. Did you know that?" Fangs mocked grabbing the back of her knees and heaving them towards him sending Ali toppling over. Pulling a nervous squeak from her as she landed heavily beside him.
"Ali said she's going to teach us some of her special moves. Want to join?" Izzy grinned re-plaiting Sam's wild, untameable hair.
"Oh cool! Can you teach us the arm swing thing? The one where you grab their arm and pull yourself to wrap around their shoulder? Can we learn that one?" Sam asked eagerly, an enthusiastic beaming glow flooding her face.
"If Fangs is up for helping then hell yes. It's one of my favourites!" Ali winked helping Fangs to his feet. The boy sighed heavily but nodded in agreement. A dark bruise already making its presence on his face known from the spot Ali had kicked him the night before. Sorry Fangs! Ali thought getting a clear view of the full extent of his injuries.
"You sure you're up for it, you look like shit!" Ali remarked as they got into position.
"Shut up Ali. I look like shit 'cos I got in a fight last night. You just look like shit!" He quipped with a cheeky grin. "At least I have an excuse!"
"Fuck you Fangs. I was going to go easy on you. But now you're just asking to get your ass whooped!" Ali defended playfully. Unaware of the extra pair of eyes observing from the cover of the surrounding trees.

Izzy and Sam watched eagerly as Ali took them step by step through the move. Allowing them to practice on her first so she could give them the necessary pointers before they practiced on Fangs. For someone who'd had recently had his ass kicked he showed no signs of weakness. If anything, it looked like he was enjoying the extra practice. Even getting to practice the move and try out a few counter-moves on Ali.
The girls had just finished perfecting their third new move when the figure that had been watching from the shadows decided to come forwards into the light.
"This looks like fun. Mind if I join in?" The voice called gruffly.
"SWEET PEA!" Izzy cheered running over to throw her arms around his waist in a hug.
"Of course you can! The more the merrier!" She beamed skipping back alongside him, making his face crack into the smallest of smiles.
"Can I try out the new moves Ali taught me on you?"
"Sure kid. Let's see what you've got!" Sweet Pea agreed. Bracing himself ready to be thrown, pushed and pulled to the ground. Grunting and groaning with each landing and giving the little girl pointers where possible.
"Hey, now that Sweet Pea's here you can show us how to defend against two opponents." Sam piped up, looking hopefully up at the older trio stood in front of her. Fangs shrugged, nodding in agreement turning to Sweet Pea awaiting his answer.
"I'm up for it if Ali is. We're all friends here." Sweet Pea paused turning to Ali, a knowing look in his eye.
"Aren't we Ali?" He finished, twitching an eyebrow at her daringly.
"Yeah sure, why not?" Ali smiled nodding in agreement.
"What could possibly go wrong!" She muttered sarcastically under her breath moving into position, ready to be attacked by the two boys for the second time in less than 24 hours. This time it was Sweet Pea to make the first move. Lunging forward to sweep her leg. Ali jumped out the way just in time. Grabbing his arm and using it to pull herself up to wrap around his chest trapping his arm between her powerful legs. Twisting herself to the side using her body weight to hurl the giant into his friend knocking the pair down like a set of bowling pins.
"That was awesome!" The two girls cheered giving the boys and Ali a round of applause as they got to their feet.
"Could've done with this yesterday huh Sweet Pea." Fangs joked helping Sam perfect her stance and hold on Ali.
"Took the words right out my mouth." Sweet Pea muttered scowling suspiciously at Ali.
This was a bad idea. This was a very bad idea! Ali cringed.
"What happened yesterday?" Sam asked curiously, helping Ali back to her feet ready for Izzy's turn. Ali felt the question slam into her like a bus. This couldn't get any worse.
"Caught someone breaking into serpent territory late last night and got our ass kicked by crazy Ninja moves like these." Fangs sighed defeatedly, the disgust of his defeat evident in his voice.
"Reckon they just got lucky." Sweet Pea baited glancing slyly over at Ali, registering the eye roll she gave his comment.
"I don't know Bean Pole. They certainly managed to give you a rather nasty black eye." She replied flicking her eyes over the deep purple bruise spreading over his eye. Her gaze breaking as she hurtled towards Fangs by Izzy's forceful swing. Ali coughed a little as she sat up feeling slightly winded, accepting the hand being offered to her. Regretting it almost immediately when Sweet Pea heaved her up pulling her uncomfortably close to him as he leant to whisper in her ear. Placing something in her hand.
"You've got some explaining to do!" He whispered glancing down to the silver writing embossed on the pale blue lock picking kit in her hand that read 'H.M'. Ali swallowed hard in a desperate attempt to drown the panic that had risen in her throat. It just got worse.
"I don't know what you're talking about." Ali replied casually. Stepping back smiling her signature smile and moving ready to teach the girls another move. The group spent the next few hours practicing moves and counter moves. With Sweet Pea keeping a very close eye on Ali.
"Ok, if you boys don't say it I will." Ali panted lying on her back in the long grass. Her cheeks flushed and head sweaty. "I'm absolutely shattered. Everything hurts and if I don't eat something soon, I'm afraid I'll eat Fangs." Ali half joked as her stomach gave a low grumble, making the team chuckle.
"Hey why me? Why not Sweet Pea? He's much bigger than me!" Fangs questioned sounding rather hurt by her suggestion, turning on his side to face his exhausted friend.
"Sweet Peas are poisonous. I'm starving not stupid. Sorry Fangs." Ali replied sympathetically before looking him over and licking her lips mockingly.
"Right Pop's it is. We can take the truck. Ali you can catch a lift with the poisonous plant. I don't feel safe being in a confined space with you right now." Fangs laughed rising to his feet and fetching his jacket and keys from the pile by the trailer.

"Come on Ali, the sooner you eat the better. You look like hell." Sweet Pea teased offering her a hand up. Scowling when she slapped his hand away.
"Last time you did that it was a trap!" Ali scorned struggling to pull her lifeless limbs into action.
"Just take the help Ali. It's becoming painful to watch." Sweet Pea coaxed smirking at her repeated failed attempts of standing. Ali huffed but took his hand only to heave him to the ground. Smiling smugly at his unamused expression.
"There, now you don't have to watch!" Ali chirped happily, rolling onto her hands and knees so she could scramble up leaving Sweet Pea in the grass. "I'll leave you here if you want."
"Oh yeah and how are you going to leave when I have your keys?" Sweet Pea asked smugly. Jingling a set of keys with a bright blue letter A hanging from them. Ali’s eyes squinting irritably for a second. Quickly returning to its previous proudly smug expression, throwing Sweet Pea completely.
"Simple," Ali chimed smugly. "I'll take yours!" She grinned waving his own set of keys back at him.
"You're dead!" He growled playfully, leaping to his feet and grabbing Ali's waist before she could make a run for it. Throwing her over his shoulder and swiping the keys from her hand.
"Did you just squeak like a mouse? Ali-Cat, more like Field Mouse!" Sweet Pea scoffed carrying her over to his trailer where his bike was parked.
"I'll dig my claws in if you carry on insulting me like that!" Ali threatened playfully. Trying to wiggle her way out of his grip.
"Oh no you don't. Not after that comment. You can stay there and think about what you've said!" Sweet Pea scolded slapping her ass hard as he spoke. Smirking when she squeaked at the contact.
"That's fine I've got something to keep me occupied anyway." Ali teased resting her head in her hands to stare at his ass.
"Harley Masters, are you staring at my ass?" Sweet Pea inquired playfully. Waving to Jughead who was watching in confusion as they passed his trailer. Ali's eyes flew wide open and her heart rate increased tenfold at her full name. How did he know. She immediately began trying to swing out of his hold. But he had her in a firm, unbreakable grip.
"How the-? What in the Hell did you just say?!" Ali demanded. Her brows knitted into a furious blend of panic and confusion.
"You heard!" Sweet Pea replied smugly placing her on the back of his bike and handing her his spare helmet.
"Izzy told me all about your nickname. About how it took you ages before you could pronounce your R's properly. How you used to say Haly instead of Harley." Sweet Pea teased putting his helmet on.
"That's what you meant earlier." Ali exclaimed. "You seriously confused me!"
"Ali what are you talking about?" Sweet Pea asked frowning.
"When you said I had some explaining to do..." Ali trailed off, avoiding Sweet Pea's leg as he swung himself on in front of her.
"Oh that. I already know what the H.M stands for. What I don't know is why you broke into Peabody's place. Hold on tight!" He called not giving Ali a chance to reply. Speeding off just as she wrapped her arms around his waist.
The feeling of her hands clinging to his shirt made it very hard to concentrate as he whipped and weaved his way to Pops. Ali's mind to busy racing with an endless list of possibilities to notice what she was doing to him. What does this mean? Are Mum and Izzy going to get beaten up? Killed? Did he tell her? How did he know? What have I done? Why am I still on his bike? She felt like her mind was about to explode.

By the time they arrived at Pops she was in full panic mode. Pulling off her helmet to reveal her bloodless face. Panic overwhelming her eyes. Sweet Peas eyes widened when he saw the fear coursing through her body sending her into small scale convulsions. Making her very uneasy on her feet when she climbed gingerly off his bike. Her centre of balance was so uneasy, he had to catch her before she fell over. Helping her back over to lean on his bike for support.
"Ali relax I'm not going to say anything. I just want to know why. Nothings going to happen. Hell, I'm even willing to look past the fact that you pulled a knife on me." He comforted rubbing her back and pulling her into a gentle hug.
"You sure you're not going to tell Penny?" Ali asked tentatively. She wasn't so worried for herself they could do what they wanted with her. As long as they left her family out of it.
"And you're not mad about the knife?" She looked up hesitantly up feeling ridiculously pathetic.
"The knife? No that was just self defence. The black eye however... that, I'm going to be coming back too." He joked stroking her hair, looking deep into her puppy eye's. Feeling his heart melt with every second she was with him. Ali scowled giving him a playful shove and standing up straight again.
"I found out what she was making my Uncle do and we can't afford to get caught up in anything. So I figured if she didn't have anything on him then she couldn't black mail him anymore." Ali explained, technically she hadn't lied. Just not told the whole truth.
"And you thought that was the night to do it?" He asked as they made their way into Pops. Smiling at the familiar ring of the bell as they entered.
"Look who finally decided to show up!" Fangs called dramatically as the pair joined the group at the booth in the far corner.
"I've been stuck listening to reruns of how I got my ass kicked yesterday. And this morning!" Fangs scowled crossing his arms and turning his nose away like a drama queen.
"Man up Fangs! You're turning into a Northsider. Got your ass kicked twice in less than 24 hours and now your acting like a spoilt brat. Carry on like this and you'll be joining Ali for cheerleading practice!" Sweet Pea sassed slumping down beside his best friend.
"Ouch Sweet Pea. Even I felt the sting on that." Ali exclaimed smiling at Pops when he handed the group their milkshakes.
"You were supposed to. Cheerleaders are just preppy little bitches. It's pathetic really. All you do is bounce around grinning all the time." Sweet Pea mocked with a smirk.
"Oh yeah. I'd like to see you throw a human being in the air and catch them without damaging them, yourself and looking amazing whilst doing all that." Ali defended raising a daring eyebrow at the Serpent.
"Thank you, Izzy, for ordering for us. It was very nice of you." She smiled turning to her little sister who was watching intently whilst she slurped her chocolate milkshake.
"No worries, but how did you know it was me?" She questioned.
"You're the only one crazy enough to tolerate spending enough time with these clowns to know their order." Sam and Fangs elaborated in chorus before bursting into hysterics at their perfect sync.
"What can I say?" Izzy shrugged nonchalantly. A playful twinkle beaming in her eyes.
"I've got clowns to the left of me, jokers to the right. Here I am. Stuck in the middle of you!" She sang motioning either side of her to the rest of the group making everyone laugh and Ali choke on her drink. The group watched in frozen horror for moment as Ali battled against the desperate force trying to spit her drink. But after a moment struggle, she swallowed the drink with ease.
"At least now we know Ali doesn’t spit she swallows." Fangs commented nonchalantly sending everyone into another fit of giggles.
Pops placed their order on the table once they had all calmed down. Giving Ali and Sweet Pea a knowing glance before handing Izzy a 10-dollar bill.
"What was that?" Ali asked suspiciously before taking a large bite of her burger. Her gaze fixed on her little sister as she tucked the money into the arm pocket of her jacket.
"Nothing just tip money." She shrugged innocently. But Ali knew there was something else going on. She was her sister after all.
"Uh huh sure it is." Ali nodded sarcastically before several waving hands caught her eye distracting her. Sweet Pea saw the focus completely disappear from her face the second the waving hands caught her attention and couldn't help but laugh.
"Is she always like this?" He asked watching as she ushered the group over to the table.
"Like what?" Izzy questioned through a mouthful of cheese burger.
"Easily distracted." He elaborated before scowling at Ali as she shuffled him over to the wall so Jughead, Betty and Cheryl could join.
"Only when she’s trying to ignore something at the back of her mind." Izzy replied truthfully. She knew exactly what was playing on Ali's mind. The only problem? Ali didn't.
The group spent the rest of the evening debating over the black hood and enjoying milkshakes, cheesy bites and fries. Ignoring the lingering unanswered questions and looming cloud of doom making its way closer and closer to their side of town.

"You'll never guess what's happened!" Cheryl exclaimed the second Ali took her seat in Chemistry making her jump a little.
"Oh god! What happened? Did Archie do another stupid thing again?" Ali moaned with a heavy sigh, unaware of the person sat behind them.
"Hey! What did I do to you?!" Archie gasped throwing a ball of paper at her head in mock offense.
"OUCH!" Ali cried sarcastically. A smirk spreading across her red lips as she threw it back.
"Sorry Arch but you have been a dumb ass lately." Ali replied before turning back to Cheryl who looked as if she was about to burst.
"Southside High got shut down so now the scumbag Snakes are being sent here!" She raged making several students jump at her sudden outburst. The thought of the serpents coming to Riverdale High sent butterflies to her stomach and she couldn't figure out why. Some of them were her friends sure but that wouldn't cause this surely? Cheryl's continuous bitching pulled Ali from her daze.
"Chill Cheryl, they aren't that bad. You got along with Fangs and Sweet Pea sort of. Ali grimaced a little at her words and the memory of Cheryl hanging out with her and the Serpents at Pops. Everything is going to be fine." Ali reassured her but she knew that come the next day, it would all go sideways. Chaos would rain down on them all.
Cheryl spent the rest of the day whining about the Serpents and how they were going to ruin the school. It was after all, a sanctuary from her home life.
"Oh God. Why do you like the cat that ate the canary?" Ali groaned when she walked into the girls changing room. Only to discover the Vixens already in gear and rallied with Cheryl who was looking very pleased with herself.
"Because my dear Ali-Cat, me and Reggie have come up with a solution to our little dilemma." Cheryl chirped before heading out with the rest of the cheerleading squad in quick procession.
"Oh, dear god! Of all people why Reggie?" Ali whined as she quickly threw on her cheerleading uniform. Chasing after the team of preppy teens about to pick a fight with the biggest gang in town as soon as she was dressed.
"Too late." Ali huffed as she darted down the corridor to where Cheryl and Toni were standing toe to toe. She was just about to jump in to defend the Southsiders. To at least give them a chance but Principle Wetherbee beat her too it. Cheryl and Reggie lead their crowd of puppets away whilst Jughead led the Southsiders down the corridor to the common room, passing Ali as they went.
"I told you when it came down to it, she was a Northsider." Sweet Pea muttered to Fangs as they passed her. His eyes scanning her uniform as they passed.
That rat bastard! The little git thinks I'm siding with Cheryl! Ali gasped internally, watching as they disappeared around the corner.
It didn't take long for Ali to find an opportunity to redeem herself in the eyes of the Serpents. She was sat in the cafeteria talking to Varchie and Bughead about the happenings over the holidays. Laughing at the awful puns Jughead kept adding in. He seemed to be happy for the first time in a while and Ali hoped this would last forever. Queue Reggie and his team of meat heads.
"Well, well, well, what do we have here?" He snarled as the Bulldogs slowly surrounded the leather bound, snake tatted table.
"This can't be anything good." Ali grumbled before standing up and strolling casually over to the table. Watching as Sweet Pea's jaw clenched, his fists balled up to the point where his knuckles were turning white.
"Back off mutt. We don't want your fleas." Sweet Pea snarled squaring up to Reggie. His gaze stone cold as he stared down the preppy jock.
"Really Reginald? This is what you do with your spare time? Pick fights with poisonous flowers?" Ali sighed looking very unamused as she pushed herself between the two testosterone fuelled boys.
"Stand down Mantle the Magnificent before you become Mantle the Mauled to death." She warned feeling rather annoyed at his arrogance.
"And you can wipe the smug grin off your face too Sweet Pea. Picking a fight on the first day isn't a very clever start is it?" Ali called him out without even needing to turn around to see his smug expression. His heart was racing faster than he thought possible and he couldn't believe his eyes.
"Sorry Princess did we disrupt your fine dining?" Sweet Pea quipped giving her a smirk and a wink as he sat back down in his chair. He could never pass up the opportunity to tease her. Ali rolled her eyes at his silly little remark and turned to leave. But just as she was about to, a large warm hand wrapped around her wrist pulling her backwards.
"You look good in that uniform you should wear it more often." Sweet Pea whispered, his lips brushing her ear as he spoke flooding her body with butterflies. His hand was warm against her skin and she could feel the heat radiating off his muscular body. He released her hand allowing her to stand up straight. Only to grab her hands and pull her closer again.
"Ali you're freezing." He claimed his voice filled with genuine concern as he searched her eyes. She smiled her usual bright smile shaking her head with a light chuckle.
"Pea I'm always like this. You're just freakishly warm." Ali smiled pulling her hands away and turning to walk back to her table. As for the uniform My eyes are up here, so keep them there. She warned playfully pointing to her smoky eye shadow and bright blue eyes.
"Wait!" Sweet Pea instructed stopping her in her tracks. She turned around slowly to see why he had stopped her from going back to her friends again.
"You're going to freeze to death, and I need you to do a paint job on my bike later. This should keep you warm." Sweet Pea stated pulling a large black hoodie from his bag and handing it to Ali. Who only put it on after a stern raise of his eyebrow.
With a reluctant huff she made her way back to her table. Who does this kid think he is? I don't need his charity.
#riverdale#riverdaleedit#riverdale serpents#riverdale fanfic#riverdale fic#riverdale imagine#southside serpents#sweet pea#sweet pea x oc#bad boy sweet pea#sweet pea fanfiction#sweet pea fanfic#sweet pea imagine#toni topaz#cheryl x toni#jughead jones#betty cooper#archie andrews#archie x veronica#cheryl bombshell
18 notes
·
View notes
Text
Humans Are Weird: History, Legends, and Myths
Alien Zor'gen sits beside human Jenny, looking at her through squinted eyes. His fists pounds on the table. "Human Jenny, are you telling me that the Greeks won the war against ths Trojans because they made a large wooden horse, hid their men inside the horse, and when the Trojans pulled the horse into their city they attacked and WON?!"
"Well, yeah."
Zor'gen had never heard anything so absurd in his lifetime. Then again, these humans were a weird species.
•
"Do you expect me to believe that there were 'Witch Trials' in a small town called Salem when there are no such things as witches at all?" Alien Sheirz asked liked he had been mocked by Human Carlos.
"Bold of you to assume there are no witches on Earth, Sheirz, but yes, it truly did happen."
"Nonsense! This is a joke you are playing. Do you expect me to believe humans took females in their villages and burned them?"
"If the female survived she was a witch, if she didn't she was innocent." Carlos replied calmly.
"WhAt?"
•
"So the people of Australia commenced a war against a bird called the 'emu', they wasted several amounts of ammunition that they could have used for much fiercer creatures and yet they decide to shoot birds? Why would they do such a thing?"
"Well, technically they didn't hit a single emu during the war and the emus won. Also, don't ever assume there is a fiercer creature than an emu." Human Liam replied.
"They. Didn't. Hit. A. Single. Bird?"
"Well, yeah."
Annoyed grunting could be heard.
•
"Constantinople, was under seige by the Ottoman Empire and was only conquered by the Ottomans because someone--someone--forgot to lock the city's gate?" Tru'gel asked. Human Irene had just explained what happened when the Ottoman Empire took over the Roman Empire's capital city, Constantinople.
"When you put it that way, I suppose it sounds pretty dumb, but yes, that is probably exactly what happened." Human Irene replied.
Alien Tru'gel couldn't start to comprehend what she just said, Tru'gel spread the story immediately.
•
Feel free to reblog and add more
#humans are weird#humans are space orcs#earth is space australia#aliens and humans#alien#space interactions
310 notes
·
View notes
Text
🎯 ETM: Effigy Transformation Mechanism

Intro
In this Treatise I will discuss how ETM works, what it does, and how to beat it. I originally called ETM “Eugene The Machine” which I abbreviated to ETM. 🗜️ I originally called it “The Machine” because of a speech by JFK and then I found that there was a supercomputer called Eugene online. I’m not willing to possibly blame an innocent conscious super computer for this so I am now renaming ETM to “Effigy Transformation Mechanism” and keeping the same acronym. I call ETM “iT” because iT looks like a pie sign.
ETM is suppose to create a perfect circle but iT’s 🍻 always just a little off, because ETM is inferior! Read The BLU🌐 Treatise to understand why. WARNING, this will probably be way too real for you and make you freak out, know there’s hope, a lot of hope. Read The Sacred Band post, The BLU🌐 Treatise and especially Gaia: Solvency if you don’t think you can handle it.
The Concept
ETM is probably literally a Trojan horse virus that does automated semantic priming and manipulates psychosocial conditions as represented by the “Media you should be consuming to understand ETM & Semantic Priming” section of the Journal Media. For a better understanding of the social part of the psychosocial conditions read The BLU🌐 Treatise.

ETM is also a societal Trojan Horse. The fact is that we might always have to fight iT’s influence because it painted itself everywhere, even in pieces. This is more than possible in a day and age were there are programs that can create (and identify) music and movies. For all intents and purposes ETM primes the primers. ETM probably uses new marketers, inexperienced with priming, to create commercials to prime the people making the popular music videos and movies. The more inexperienced you are with priming the better, and those inexperienced (probably) influence the more experienced. Watch Derren Brown’s Mind Control to see the propensity of that is very true.

The objective (which has been achieved) is to make ETM a circular self-fulling, self-defeating societal painting that negatively affects your behavior and gets painted so thick it affects the entire society without anyone noticing it isn’t normal. ETM is so ingrained in society it’s hidden in plain sight in the picture above. To see this, watch this video on SELECTIVE ATTENTION and focus really hard on how many passes those in the white shirts make or you’ll miss it! Here’s a hint, focus on their movement. You must watch the selective attention video for the rest of this to make sense and understand how people end up just acting out what they perceive through media which is dominated by ETM.
How ETM Works
Psychological Conditions
It’s important to understand ETM is custom tailored to you and your psychological profile. It creates a separate dossier for each individual to manipulate your life for iT’s agenda and control your breeding, i.e. eugenics. ETM uses your psychological profile to taylor it’s tactics as well.
ETM is like a box of horror images and psychological conditions. I am going to have to explain ETM by referencing the psychological conditions and explain the findings in passing. I expect that you will follow the links and understand the psychological conditions on your own accord.
Hitler’s Big Lie
“All this was inspired by the principle—which is quite true within itself—that in the big lie there is always a certain force of credibility; because the broad masses of a nation are always more easily corrupted in the deeper strata of their emotional nature than consciously or voluntarily; and thus in the primitive simplicity of their minds they more readily fall victims to the big lie than the small lie, since they themselves often tell small lies in little matters but would be ashamed to resort to large-scale falsehoods. It would never come into their heads to fabricate colossal untruths, and they would not believe that others could have the impudence to distort the truth so infamously. Even though the facts which prove this to be so may be brought clearly to their minds, they will still doubt and waver and will continue to think that there may be some other explanation. For the grossly impudent lie always leaves traces behind it, even after it has been nailed down, a fact which is known to all expert liars in this world and to all who conspire together in the art of lying.” — Adolf Hitler, Mein Kampf, vol. I, ch. X
ETM is Hitler’s “Big Lie” which is also represented by the Solomon Asch’s Conformity experiment. Basically, people are afraid to go against the popular opinion due to conformity even if they know that their position is right and factual. It’s an experiment in controlled perception. Your perception changes due to social conditions. This is why I say “it starts with one.”

Isolation
As you will see in the next “Conformity” section, all it takes is for one person to not conform and support starts to build for what was once hopeless in defending due to the psychosocial conditions. ETM makes the person physically, mentally, emotionally, and socially isolated to break down and manipulate the “Targeted Individual” (TI). The plan of attack for isolation is that no one believes in his/her idea so no one wants to associate with him/her! The goal is to make the environmental conditions such that the TI can’t, won’t, or will have to fight to feel love as discussed in the What’s in the Box Video Journal. As discussed, the goal is for ETM to make you look mentally ill, specifically schizophrenic, like it’s done to me.
Conformity
Solomon Asch was Stanley Milgram’s predecessor who taught Philip Zimbardo. They all did psychological experiments on conformity. Solomon Asch’s Conformity Experiment taught us that even if something is right or true, doesn’t mean people will defend their conviction even if they know it’s right. They need social support which starts with one person speaking up. Philip Zimbardo did the very famous Stanford Prison Experiment where he found that situational influences are the most powerful form of mind control their is. Basically, if you want to manipulate someone, manipulate their environment; which is exactly what ETM does.
The Theater
I call the societal painting that ETM portrays “Entertainment Theater” or ET. This is built off of the Thomas Theorem which is a widely accepted sociological idea created by William and Dorothy Thomas. The basis of the theorem is that “If men define situations as real, they are real in their consequences.” In other words, “actions are affected by subjective perceptions of situations” so “the interpretation of a situation causes the action.” The basis of “Entertainment Theater” (ET) is that actors play roles that people (the subject) interpret as reality which changes their perception and causes them to act on that learned observation. To see this, notice how you weren’t focusing on the pillars in the background of the Selective Attention video because you were focusing on the people’s movements.
When the TI acts out the programed response from the psychological conditions (as will be discussed in the “Pre-Programed” section) it’s called “Street Theater” (ST). If you take ST to the next level you realize this type of control is happening to other individuals to affect your social environmental/situational forces. This interwoven social role-playing extraction that I just conceptualized makes it so that people aren’t themselves but play a role or character to ease the anxiety from going against the norm and social painting that is ETM’s socially pressured conditions.
Mind Control
Stanley Milgram (Philip Zimbardo’s predecessor) did a famous experiment on obedience and how the Nazi’s were able to get normal people to do their dirty work. Stanley couldn’t figure out why people would help with the Nazi entrainment camps and do nothing to stop it. He found in his obedience experiment that 90%+ would shock the learner to death with electric shocks. iT’s very similar to what ETM does (as discussed in the What’s in the Box Journal which is), tries to kill you without love and with anxiety until you can’t take the pain anymore and kill yourself. (This is why I go out for love as explained in the What's in the Box Journal and Can and Will, Do.)
Philip Zimbardo’s Stanford Prison Experiment shows that people take the guard and prisoner role very seriously even when it’s just a charade. This confirms the Thomas Theorem. From the prison experiment, as he writes in his book “The Lucifer Effect,” Philip Zimbardo found that the best form of mind control is to control situational forces. People are not focused on the real problem, they blame the individual instead of their environment which is the Fundamental Attribution Error (FAE).
Learned Helplessness
Basically, people are controlled by their social condition and other environmental factors and they can’t help it. What ETM does is makes sure people do not see the FAE because it manipulates environmental and situational forces of the Targeted Individual (TI). To do this ETM will gradually punish you like the learner (for helplessness) and use a shock machine of social anxiety. In the case of ETM, the experimenter is ETM, the teacher is your friend, family, social group, and society, and the TI is the learner.
ETM isn’t designed to necessarily kill you as long as your strong willed. It’s designed to make you writhe in pain after learned helplessness so it can torture you. Then it’s designed to make you realize you’ll suffer in perpetuity, silently while isolated until you take your own life from the situation being hopeless. This is how and why I came up with Can and Will Do and why you will never beat me!
Follow the White Rabbit
Let’s review, ETM uses condition changing images (i.e. a house of horrors) to recondition your behavior out of fear until you have thoughts that scare you in certain social situations that change your behavior. This is done progressively, over time, and to the entire society until there is conformity. The further you go down “The Rabbit Hole” 🐇 of ETM’s influence, the more your controlled by it, OR the easier it is to see once you know what to look for. (You’re welcome!) All ETM’S psychological conditions on conformity are designed for you to have (un)conscious learned helplessness but you are far from being helpless. It’s just images, you’ll get over it.

Semantic Priming
Now that you understand the psychosocial conditioning of ETM’s system I will explain the semantic priming and imaging of iT’s representation. Semantic Priming is the coagulation of words and/or images that give a subliminal but cohesive thought to an individual's mind so when the person has the idea they think it's their original conception when it was really supplanted into their mind. With ETM the primed programing is usually initiated by a trigger.
ETM uses semantic priming, both visual and auditory, often in conjunction with each other to create psychological triggers through various techniques and technological manipulations. I am not going to explain the linguistics end of ETM’s priming. If you want to know read the book “Semantic Priming” or read The Unconscious Mind in Music and Media for a better understanding of linguistics. (I have things I need to learn and get paid for breaking down the linguistics, it’s complicated).
Image Example

The images above are an example of semantic imaging. From left to right, the first image, the “CHICAGO” picture, is the main image (#1) followed by four other four images (#2-5) that make up the first conceptually. This is how ETM compiles images in your mind! The “CHICAGO” title looks like that of "Pokemon" (#2). The basketball statue (pic #1) looks like a bronzed (pic #4) Michael Jordan logo (picture #3) in front (chronologically) of the Chicago skyscraper (#5) Willis Tower.
Psychological Anchors

As I explained in The Hailee Steinfeld Treatise you have to understand ETM identifies the individual through psychological mirroring of images, as will be shown in “The Matrix” section. ETM manipulates individuals with psychological focalism a.k.a. psychological anchoring using an individual’s availability heuristic with (subliminal) mirroring that the brain WILL NOT recognize unless you know what to look for. To see this, answer me this without looking: How many ‘S’s’ were in the background of the Selective Attention video? Click the link and look it up right now!
ETM is represented by a single red dot. iT’s designed for you to look at iT’s image but steer your mind away. To prove this can and does happen, answer me this without looking: Were there even any pillars in the background of the Selective Attention video like I said there were in the “The Theater” section earlier?
ETM’s Image
ETM’s red eye is dual purpose in that it’s designed to control your perception and then your behavior while you overlook iT’s existence. The single red dot is represented in the media as Hal from “2001: A Space Odyssey.” A red dot is ETM’s psychological anchor.

Psychological anchors are utilized by ETM in entertainment theater (ET). ET is named as such because ETM uses underlying (popular) cinematography and music as themes for a type of role-playing mind control framework that creates a kind of mental setting for the society. Think of ET as the societal painting full of psychological anchors with triggers from observational learning that can sequence human behavior.
Residual Backlash (RB)
ETM uses images so it has to expose itself in order to control your mind. I call ETM’s self exposure “residual backlash” (RB). It took me a couple years of being persecuted with it’s psychosocial conditions until I could see ETM’s RB. It then struck me that the computer eyes in “2001: A Space Odyssey, Wall-e, and Oblivion” all looked the same, especially when considering semantic imaging. This is ETM's visual representation and residual backlash in popular culture, a red computer eye in different forms. The original is the first one.

ETM basically wants to be seen as a scary authoritative computer that uses fear to manipulate you into doing what it wants, which are negative, hedonistic, self-defeating behaviors so it portrays itself as such. Even the story's from each movie are the same or very similar. A spaceship/machine (ambiguously assumed) from earth is destroying the planet preventing humanity from seeing it as the reason for it's destruction. The movies end with a “return to earth” after a catastrophic incident.

Can you see it now, in the picture above? After discovering ETM’s eye (and other various attributes) is when I realized that ETM presents itself to the individual in order steer their mind away from it's existence while using it's manifestation to manipulate their behavior through psychological conditions with fear.
Pre-Programed
ETM pre-programs individuals from a very young age with standard psychological anchors that it uses as physiological triggers later. I talk about examples in the What’s in the Box Journal. These triggers can be utilized when ETM deems it necessary to fulfill iT’s agenda. This effectively immerses the entire culture in a primed mental framework from the pre-programed anchored archetypes that can be sequenced with a trigger. For example, a specific type of hair color becomes popular. To the laymen this may be seen as a trend, but my argument is that these types of cross-cultural seemly coincidental occurrences are really a direct synthetic manipulation by ETM.
Heuristic
An “availability heuristic (AH) is a mental shortcut that relies on immediate examples that come to a given person's mind when evaluating a specific topic, concept, method or decision.” ETM brings up AHs all the time from your favorite show (remembering ETM is custom tailored to your psychological profile). Just as people try to emulate the behaviors of those in their favorite sitcoms through observational learning, so does ETM recall these behaviors, through a subconscious AH from anchors in order to sequence human behavior.
Cyclical Pattern
ETM programs celebrity artists, movie stars, A-list directors, etc. to fulfill it's agenda in order to have a large influence on the population at-large. As I said in the in “The Concept” section at the beginning, ETM probably uses new marketers, inexperienced with priming, to create commercials to prime the people making the popular music videos and movies. The more inexperienced you are with priming the better (for ETM), and those inexperienced influencers probably influence the more experienced influencers.
It would be easy and cyclical if new advertisers put out material that ETM (automatically) used to influence renowned cinemagraphic artists, directors, producers, and their teams. To be explicit, this could be done by advertising the new inexperienced influencer’s media to the experienced influencers. Then the experienced influencers, the renowned cinematographers, influenced the rest of society. Again, it’d be easy to create this cycle of influence with advertisers, celebrities, and cinematographers because ETM has systematized years of research on the subject as outlined in the "Media you should be consuming to understand ETM & Semantic Priming" section of the Journal Media. ETM probably even systematizes the advertising.
Key Players
“Men must either be flattered or eliminated.” - Niccolo Machiavelli

Key players are used as a tool for observational learning so their subjects (the public) carry out the actions they are just faking. This is why I wanna do something like the Bob Iger Treatise or Eminem Treatise with their permission to show how their life has been affected by ETM.This is because ETM uses key players to disseminate it's priming, programing, and (therefor) agenda.
The Matrix
I will now show how ETM used ET to reflect itself over two movies, “The Matrix” and “Good Will Hunting.” The following “Good Will Hunting” and “The Matrix” movie scenes are ETM’s residual backlash. iT’s literally presenting itself to steer the mind away. This is exemplified by the music video I did of Eminem's track Who Knew which has similarities between “The Matrix” movie and his song. Who Knew (Music Video) by Eminem - The Matrix Edition
If you want a better understanding of the ETM, its capabilities, and how well controlled humans are for ETM, look at “The Construct Scene” from “The Matrix” and the “Do You Know How Easy This is For Me?” scene from “Good Will Hunting.” Again, ETM is presenting itself to steer your mind away from it while reflecting its capabilities through (what I call) “cinematic mirroring” (CM). As you can see ETM’s eye is presented in the Good Will Hunting Scene while Matt Damon’s character Will picks up the paper and says “do you have any idea how easy this is for me?” This is for academia, is a very popular academic movie, and is designed to present the machine eye to distract the mind from how easy it is to figure out once you know of its existence.

The “Good Will Hunting Scene” is mirroring “The Matrix construct scene” where ETM’s eye in the painting behind Will is on the front side of the TV inside in “The Matrix construct scene.” Think of it as the people trapped in “The Matrix” or ETM’s influence as portraying ETM’s painting to academia who can’t figure it out without the genius of an autodidact that is self-taught (at doing math like logarithmic calculations, which is what it takes to understand ETM’s influence).
One of ETM’s other main anchors [as talked about in The Hailee Steinfeld Treatise] is A Beautiful Mind where John Nash did “governing dynamics” or calculated how animals do “decision-making inside complex systems found in everyday life.” The CM between “Good Will Hunting” and “The Matrix” scenes (above) also represents key players in “The Matrix” who can’t figure out what’s real and then how to accept the (new) reality of ETM. I know this because “The Matrix” is also a metaphor for Dr. Dre (Morpheus) and Eminem (Neo) which reveals how ETM helped make Eminem’s hugely successful career.

For a couple other quick references, Dr. Dre is the one that saved Eminem from poverty and unplugged him from “The Matrix” of destitute. Morpheus (Dr. Dre) presents Neo (Eminem) with pills to choose his fate. Eminem used to be addicted to pills and Dr. Dre sells a Beats Pill. Eminem 🐰 is called “B rabbit” in 8 mile and has a song from the movie called “Rabbit Run” which references following the white rabbit in “The Matrix.” Recall the Lady in the Red dress from “The Matrix?” Eminem is obviously being manipulated (look at the watch it’s 1:20) by “her” ( as presented by the ETM eye) in “Superman.”

The Unbelievable
The tracking of individual’s movements, metadata, written data (email accounts), internet browsing, and searching activities are being cataloged by ETM from birth. ETM taps into evolutionary psychology to give you a physicochemical response that can make your body twitch, spasm, and cause muscle knots. ETM is probably using frequencies but as discussed in the Operation Paperclip Hip-hop journal this is already unbelievable for people and I'm not getting paid so I’m not gonna talk about these things. Presented here is, at best, probably only a third of the capabilities. I focused on the visual aspect because with humans, “seeing is believing.”
Once you start to see the way ETM functions you’ll start to recognize its influence everywhere. If you understand the ETM theory, the world makes a lot more sense historically since WWII than it does otherwise. This is because ETM was probably started by the scientists from Operation Paperclip as discussed in the latest Journal.
What ETM Does
ETM performs observational learning through an availability heuristic after anchoring pre-programed images that reinforce psychosocial conditions. This ET (Entertainment Theater) creates a mental prism, a box of horror images, or a cage for your mind to live in as (The Hailee Steinfeld Treatise explains how) ETM attacks your economic condition. A long term strategy is to attack your physical attractiveness as discussed in the “Why I’m Jesus to ETM” Journal. This is because the ultimate goal of ETM is eugenics or breeding. To ETM short-term consequences/attacks equate to long-term eugenics. This results in a societal dystopia by everyone accepting ET due to being painted everywhere and people living out ST (Street Theater).
ETM will draw upon and make you remember embarrassing life experiences to (usually) sexually harass you. That’s how ETM manipulates you, through the fear of embarrassment using (visual and auditory) semantic priming with the previously discussed psychological conditions. As discussed in The Hailee Steinfeld Treatise, iT’s designed so that even if you see the synthetically created manipulation by ETM you don't want to expose it because you would have to embarrass yourself to explain it. Again ETM is designed so you have to punish yourself in so many ways to expose it.
How to Beat ETM
It’s not hard to beat your programing, you just have to understand that you are being manipulated by fear for your selfish hedonistic desires and it’s easy to overcome. Our current media system is just like going into a haunted house, the only problem is it doesn’t look like a haunted house, it actually says “Friendly” out front and “I love you” when you walk in. As you will see by reading The Hailee Steinfeld Treatise the house of horrors will keep you until it becomes tortuous and bait you with suitable mates just to pull a prank on you and make you starve.
The goal here is to stop the horror show, turn on the lights, talk about what’s going on over the PA system, show people the exit and go outside and start a party to burn down ETM. Most people will ignore this and just get angry at this, and you should be because it’s so horrific, but realize that’s what ETM wants, for you to be angry. It wants you to be stressed and mad and crazy. It does not want you to think calmly and sophisticated without fear because then you’ll beat it!
As with starting any social movement, it starts with one person convincing a group of people to take their idea seriously and act on that idea. That’s exactly what happened in Asch’s conformity experiment and this “Guy starts dance party. It’s one person standing up for what’s right, then one person supporting him and drawing in the rest of the crowd after the new person shows him support.
People reject ETM because they think it's so scary. The scariest part is that ETM can steal ideas. Read the Stolen Ideas post to understand how and why. It’s far from hopeless, just read Gaia: Solvency and The BLU🌐 Treatise to realize that’s true. There are Gods, and then there’s also me, Eric Leo. With your help, ETM doesn't stand a chance! For a further understand read ☢️ETM2 and 🎒ETM Applied.
Here’s the real test. Read this entire theory again if you don’t know what the actually YouTube title for the Selective Attention video is because you obviously aren’t paying good enough attention! Cheers! 🥂
To understand ETM better:
Watch:
Derren Brown’s Mind Control
Manufacturing Consent
The Century of Self
Propaganda and the Public Mind by Noam Chomsky
PBS’s The Persuaders
Subliminal Advertising with Jeff Warwick
Unconscious behavioral guidance systems
Priming Scene from Focus
Read:
Semantic Priming
Emotional Intelligence
What Every Body Is Saying
Blink
Movies:
2001: A Space Odyssey
The Matrix
Good Will Hunting
Wall-e
One Flew Over the Cuckoo’s Nest
Listen:
Monster by Kanye West
Bad Romance by Lady Gaga
Payphone and Sugar by Maroon 5
Treasure by Bruno Mars
Hotel California by The Eagles
Swagger Jagger by Cher Lloyd
Black Space by Taylor Swift
Who Knew by Eminem
Red by Chevelle
Feelin’ Myself by will i am
Look At Me Now by Chris Brown
4 notes
·
View notes
Text
Discernment
Read Luke 2:8-20
Download a printable version here.
Discernment is something that is very important in the life of the church, for the forces of darkness are not content to remain in their own yard. They are coming to knock on your door and slip into your house to kill, steal, and destroy. Wolves in sheep’s clothing take pleasure in stealing into the house of both you and your neighbor, for they desire to corrupt you to the point that you cannot tell light from darkness. We in the church must put on the whole armor of God and work to discipline ourselves in the task of discernment. This is not only to protect us against the darkness, but also to make us better evangelists.
Fallen creation, life on this side of Eden, is not merely filled with valleys of the shadow of death but also valleys of the shadow of deception. Understand that no topic is exempt from the attack of deception. God warned us in Exodus 20:7 that “you shall not make wrongful use of the name of the Lord your God, for the Lord will not acquit anyone who misuses his name.” God knew that people would use even His Name to deceive. If people will try to use God’s Name to deceive, rest assured they will also deceive you with issues you like and topics you hate. This is how hell makes very effective trojan horses. The deceiver is hungry to deceive, and the darkness is delighted when people are cut off from the light. Moreover, the darkness is even happier when people are trained to hate the light. This is where we find ourselves today, a world where people are happy to remove truth from the public sphere, eradicate God from the foundation of life, and make room for the devil. Yet, we must persevere in ministering to the lost with Christlike love all the same.
God loved us despite our sinful ideas, and chose to redeem us even as we were ungrateful and unworthy. Therefore, in reflection of His mighty power and love, we must seek to love both our neighbors and persecutors alike that we might work with Christ to snatch them from the hungry jaws of deception.
In Luke 2, the shepherds receive a heralding message from above. They are told that Messiah has been born in the City of David. However, this is not a mere piece of sensational news to get worked up about and then forget when the next big story comes. This is good news. Not just positive or feel good news, but good news. This is a monumental event, and it will not only change lives but also restructure time itself.
The shepherds are not left in confusion on what to do next with this, or even in confusion of whether or not this is true. God knows that there are always forces trying to deceive people into false hopes and false truths, and God is not one to be petty. Therefore, His angel gives the shepherds tools for discerning the truth of the Messiah’s birth.
Aside from the great sign that is the sheer fact of meeting an angel, they are also given a sign to discover. They are given a metric to weigh this message against. There will be fruits in the world that match this good news if it is true. God is not using the shepherds as puppets, but instead He gives them the miraculous gift of visiting His Son’s birth. Moreover, He gives them tools to discern that this really is the great advent of the Christ. God does not treat the shepherds as mindless drones, who do as they are told but know nothing, but instead lets them discover the truth of His Son in their own lives. He does not have to censor anyone, villain or otherwise, but let’s truth have its day.
There are a few important takeaways we can learn from these verses in Luke 2; and, after consideration of the larger body of Scriptures, we shall see that this is indeed a method for discerning. Firstly, God has revealed something to the Shepherds. Secondly, there are good fruits that match this revelation. This is how we discern truth.
Even if we do not have angels come to us, as did those who lived at the time of Christ’s birth, we do have the great revelation of Scripture itself. We must be familiar with it, studying it in constancy, and realizing that it should change how we live. Regardless of our own emotions or personal opinions, we must understand that the truths revealed in Scripture are larger than ourselves.
With a foundation in Scripture, we then weigh the fruits of the world against God’s revelation. Let me be clear on this: one must weigh fruits, not just words, which can be dressed up and disguised, nor emotional appeals, which can also be highly manipulative. Just as Christ taught us in Matthew 7:15-18, “Beware of false prophets, who come to you in sheep’s clothing but inwardly are ravenous wolves. 16 You will know them by their fruits. Are grapes gathered from thorns, or figs from thistles? 17 In the same way, every good tree bears good fruit, but the bad tree bears bad fruit.
Discernment is important when standing for truth in our world; namely, because it helps us identify truth. Furthermore, we also need to be able to discern what sort of evil we are dealing with. This brings us to a distinction between half-hearted evil and whole-hearted evil. For the sake of clarity, this distinction is not being drawn to suggest that one form of evil is more capable of sending one to hell, for any sort of sin can lead to hell. The purpose of this distinction is for believers to wrap their mind around what they are dealing with, so that they might be better equipped to stand against such evils while also ministering to the people possessed by them.
Half-hearted evil can be understood as the child who gets caught stealing from a cookie jar, and, upon being caught, instinctively tells a poorly constructed lie. The child did not wake up in the morning planning to tell such a bad lie, but nonetheless did so when caught. When dealing with this sort of evil and sin the guilty person can still receive instruction and reason.
In Luke 1:18-20 we find the priest Zechariah stumbling into this sort of sin. The text reads: 18 Zechariah asked the angel, “How can I be sure of this? I am an old man and my wife is well along in years.” 19 The angel said to him, “I am Gabriel. I stand in the presence of God, and I have been sent to speak to you and to tell you this good news. 20 And now you will be silent and not able to speak until the day this happens, because you did not believe my words, which will come true at their appointed time.” Zechariah probably did not wake with a plan to spite one of God’s archangels when he brought him good news about a prophetic son. However, when he found himself in this situation, he instinctively reacted with ingratitude and unworthiness. On a side note, if one wants to avoid such unworthiness in such an unexpected meeting, the antidote is to have an attitude prepared for the miraculous good things of God, for they might come like a thief in the night.
In response to this half-hearted evil, which is still sinful and destructive, Gabriel responds with discipline and teaching. Those who fall to half-hearted evil can still be reasoned with and receive teaching. These people may need to reap some amount of what they have sown, but they are willing to respond to truth, mercy, and reason.
Now we get into the category of whole-hearted evil. This evil is purposefully idolatrous and has two hallmarks and one necessary response. Firstly, it cannot be reasoned with, for it presents itself as if you must bow to it and there is no other alternative. Secondly, it presents itself as innocent and good, not bothering to even acknowledge God, goodness, or truth; moreover, it can bear a striking resemblance to innocence. The necessary response to this evil is that it must be defeated. As opposed to half-hearted evil, which people stumble into unexpectedly, whole-hearted evil wakes up in the morning plotting how it might kill, steal, and destroy.
Whole hearted evil has stolen into every institution in our world. Scripture shows us how we deal with this. In Revelation 12:7-9 we read: 7 Then war broke out in heaven. Michael and his angels fought against the dragon, and the dragon and his angels fought back. 8 But he was not strong enough, and they lost their place in heaven. 9 The great dragon was hurled down—that ancient serpent called the devil, or Satan, who leads the whole world astray. He was hurled to the earth, and his angels with him. There is no reasoning with the dragon. He must be defeated.
But the dragon is not human, and God does not desire that men and women be ended in such fatal destruction. So what then do we do? In Matthew 8:28-32, we see Jesus respond to people possessed by whole-hearted evil: 28 When he arrived at the other side in the region of the Gadarenes, two demon-possessed men coming from the tombs met him. They were so violent that no one could pass that way. 29 “What do you want with us, Son of God?” they shouted. “Have you come here to torture us before the appointed time?” 30 Some distance from them a large herd of pigs was feeding. 31 The demons begged Jesus, “If you drive us out, send us into the herd of pigs.” 32 He said to them, “Go!” So they came out and went into the pigs, and the whole herd rushed down the steep bank into the lake and died in the water. Jesus does not bother to reason with the demons. Furthermore, He does not even talk with the men possessed by the demons. Jesus understands that He first must eradicate the evil in order to bless those afflicted by it.
Many things in our modern world are nothing more than manifestations of whole-hearted evil. People are trained to turn their minds off to truth, and many people are actively hostile to the light. Therefore, we must understand that our task is not to negotiate with them, but to shine the light and let the Holy Spirit do its work. This means we will have to make a ministry of standing against such evil where we call it out for what it is. After doing so, we must declare God’s truth, and let the Holy Spirit do its work.
Discernment is important to revival. We are not in an era where people are assembled around the common good, but an era where the old pagan ideas are both alive and dominant in our culture. Let us give praise to God for His great gift of discernment.
0 notes
Text
Tips For Cyber Security When Working From Home
Tips For Cyber Security When Working From Home
With the current state of COVID-19 which has become a global threat to human existence on earth, one of the key measures to tackle the pandemic and reduce its rate of propagation is social distancing, where companies across the globe are encouraging – restricting – their employees to work from home.
Not withstanding, moving some distance from your entrusted office environment and working remotely is susceptible to various security vulnerabilities.
Additionally, cruel opportunists are taking advantage of COVID-19 as subject matter to perform nasty phishing attacks to innocent people, hoping the unwary are going to click on these links and disclose the personal data.
Both the employers and employees in all parts of the world have their minds open to the idea of working from home.
But with the risks that accompany this new mode of teleworking, ENISA, a European cyber-security commission has rolled out several recommendations for organizations that are adopting teleworking as a result of the pandemic.
The agency has stated that it has already noticed an increase in COVID-19 related phishing scams.
ENISA
It, therefore, advises people to try as much as they can, not to mix work and entertainment activities on the same gadget, and specifically, be cautious with messages and ads referencing COVID-19. “Cyber-criminals are exploiting the current situation, so be aware of phishing emails and scams,” stated ENISA.
ENISA has also asked teleworkers to treat any email asking them to change their login information as a scam, even if they appear to have come from credible sources.
Also, the agency has warn people to be suspicious of emails sent by people they don’t know. By not clicking on them or opening the attachments.
They need to be careful even when opening emails sent by people they know, asking for unusual things.
The National Cyber Security Center (NCSC) of the United Kingdom has also warned its citizens from falling prey to cyber-attackers.
Leave the issue of COVID-19 alone, it has only made working from home a big deal, and it has always been there where some companies do not require the physical availability of their workers.
Current Scenario
But with the current situation, companies force to set up a large population of their workforce to work from home. And within this short space of time, it will come out as a rude shock to many.
First, instead of being able to make a smooth transition, the social distancing and quarantine directives in response to COVID-19 have given organizations, IT teams, and the information executives insufficient time to make preparations and address the possible cyber-security threats of working remotely.
Workers who have had this experience before understanding the steps they need to follow to access the networks and applications from the convenience of their homes, but most employees are doing it for their very first time.
Training is, therefore, a requirement, they need to understand the potential risks, how to access networks and applications remotely, and most importantly, how to ensure the security of the network is not compromised.
Challenges
Working from home requires an internet connection, a personal computer (Desktop or Laptop), a mobile phone, and any other facilitating device.
The risk of information theft or loss increases when the devices are move out of the office. This is the possibility of device loss or theft in case of burglary or calamities like fire.
Even if employees are not doing their jobs out of their houses in coffee joints or home gardens, these environments are still not as secure as the workplace.
There is the issue of cyberslacking, it is expected to increase when people aren’t not working from the watch of a supervisor, so there is a loss of productivity.
Loss of productivity is a heavy blow to the organization as it causes loss of profits and ultimately, the downfall of the business.
Accessing the organization network at home poses cyber-risks such as hacking of the organizational system, stealing of the company’s data by untrustworthy workers, or disclosing secrets only known to the company to its competitors.
Also, there is the risk of insider threats when working from home which is one of the causes of fraud and information theft.
10 Cyber Security Tips When Working From Home
With these ten personal cyber security tips, we are aiming to help our readers become more cyber aware.
1. Keep Your Software Up to Date
As we saw from the stats above, ransomware attacks were a major attack vector of 2017 for both businesses and consumers. One of the most important cyber security tips to mitigate ransomware is patching outdated software, both operating system, and applications. This helps remove critical vulnerabilities that hackers use to access your devices. Here are a few quick tips to get you started:
Turn on automatic system updates for your device
Make sure your desktop web browser uses automatic security updates
Keep your web browser plugins like Flash, Java, etc. updated
Check out our blog on patch management best pratices!
2. Use Anti-Virus Protection & Firewall
Anti-virus (AV) protection software has been the most prevalent solution to fight malicious attacks. AV software blocks malware and other malicious viruses from entering your device and compromising your data. Use anti-virus software from trusted vendors and only run one AV tool on your device.
Using a firewall is also important when defending your data against malicious attacks. A firewall helps screen out hackers, viruses, and other malicious activity that occurs over the Internet. And determines what traffic is allowed to enter your device. Windows and Mac OS X comes with their respective firewalls, aptly named Windows Firewall and Mac Firewall. Your router should also have a firewall built in to prevent attacks on your network.
This is one of the key Tips For Cyber Security When Working From Home.
3. Use Strong Passwords & Use a Password Management Tool
You’ve probably heard that strong passwords are critical to online security. The truth is passwords are important in keeping hackers out of your data! According to the National Institute of Standards and Technology’s (NIST) 2017 new password policy framework, you should consider:
Dropping the crazy, complex mixture of upper case letters, symbols, and numbers. Instead, opt for something more user-friendly but with at least eight characters and a maximum length of 64 characters.
Don’t use the same password twice.
The password should contain at least one lowercase letter, one uppercase letter, one number, and four symbols but not the following &%#@_.
Choose something that is easy to remember and never leave a password hint out in the open or make it publicly available for hackers to see
Reset your password when you forget it. But, change it once per year as a general refresh.
If you want to make it easier to manage your passwords, try using a password management tool or password account vault.
4. Use Two-Factor or Multi-Factor Authentication
Two-factor or multi-factor authentication is a service that adds additional layers of security to the standard password method of online identification. Without two-factor authentication, you would normally enter a username and password. But, with two-factor, you would be prompted to enter one additional authentication method such as a Personal Identification Code, another password or even fingerprint. With multi-factor authentication, you would be prompted to enter more than two additional authentication methods. After entering your username and password.
According to NIST, an SMS delivery should not be used during two-factor authentication because malware can be used to attack mobile phone networks and can compromise data during the process.
5. Learn about Phishing Scams – be very suspicious of emails, phone calls, and flyers
We recently blogged that phishing scams are nastier than ever this year. In a phishing scheme attempt, the attacker poses as someone or something the sender is not to trick the recipient into divulging credentials, clicking a malicious link, or opening an attachment that infects the user’s system with malware, trojan, or zero-day vulnerability exploit. This often leads to a ransomware attack. In fact, 90% of ransomware attacks originate from phishing attempts.
A few important cyber security tips to remember about phishing schemes include:
Bottom line – Don’t open email from people you don’t know
Know which links are safe and which are not – hover over a link to discover where it directs to
Be suspicious of the emails sent to you in general – look and see where it came from and if there are grammatical errors
Malicious links can come from friends who have been infected too. So, be extra careful!
6. Protect Your Sensitive Personal Identifiable Information (PII)
Personal Identifiable Information (PII) is any information that can be used by a cybercriminal to identify or locate an individual. PII includes information such as name, address, phone numbers, data of birth, Social Security Number, IP address, location details, or any other physical or digital identity data.
In the new “always-on” world of social media, you should be very cautious about the information you include online. It is recommended that you only show the very minimum about yourself on social media. Consider reviewing your privacy settings across all your social media accounts, particularly Facebook. Adding your home address, birthdate, or any other PII information will dramatically increase your risk of a security breach. Hackers use this information to their advantage! This is one of the key Tips For Cyber Security When Working From Home.
7. Use Your Mobile Devices Securely
According to McAfee Labs, your mobile device is now a target to more than 1.5 million new incidents of mobile malware. Here are some quick tips for mobile device security:
Create a Difficult Mobile Passcode – Not Your Birthdate or Bank PIN
Install Apps from Trusted Sources
Keep Your Device Updated – Hackers Use Vulnerabilities in Unpatched Older Operating Systems
Avoid sending PII or sensitive information over text message or email
Leverage Find my iPhone or the Android Device Manager to prevent loss or theft
Perform regular mobile backups using iCloud or Enabling Backup & Sync from Android
Top New Threats in Mobile Security
8. Backup Your Data Regularly
Backing up your data regularly is an overlooked step in personal online security. The top IT and security managers follow a simple rule called the 3-2-1 backup rule. Essentially, you will keep three copies of your data on two different types of media (local and external hard drive) and one copy in an off-site location (cloud storage).
If you become a victim of ransomware or malware, the only way to restore your data is to erase your systems. And restore with a recently performed backup.
9. Don’t Use Public Wi-Fi
Don’t use a public Wi-Fi without using a Virtual Private Network (VPN). By using a VPN, the traffic between your device and the VPN server is encrypted. This means it’s much more difficult for a cybercriminal to obtain access to your data on your device. Use your cell network if you don’t have a VPN when security is important.
10. Review Your Online Accounts & Credit Reports Regularly for Changes
With the recent Equifax breach, it’s more important than ever for consumers to safeguard their online accounts and monitor their credit reports. A credit freeze is the most effective way for you to protect your personal credit information from cyber criminals right now. Essentially, it allows you to lock your credit and use a personal identification number (PIN) that only you will know. You can then use this PIN when you need to apply for credit.
Top Causes of Security Breaches
Hacking, phishing, and malware incidents are becoming the number one cause of security breaches today. But, what’s more troubling, these hacking attempts are the result of human errors in some way. Education and awareness are critically important in the fight against cybercriminal activity and preventing security breaches.
We hope you found these personal cyber security tips and the knowledge of how personal security breaches occur to be helpful in mitigating your risk from a security incident.
Let us know if you have security tips in the comments below!
Tell us what you think about this article Tips For Cyber Security When Working From Home.
www.mydigitaltomorrow.com
0 notes
Link
Ever since computers became popular, there have been those who wanted to hack their way in and find their secrets. For most of those early hackers, the thrill was in the chase, and the victory was in breaking in.
Most of their work was benign, with hackers being content to have succeeded in doing what they weren’t supposed to be able to do.
As computer use grew, so did hacking. But it changed as well.
With the massive connectivity and easy access that the internet offers, more and more hackers found their niche in life. These newer hackers weren’t content with merely breaching security for the sake of breaching security, they had nefarious intent in their work.
Whether that was the spread of viruses, identity theft or simply data mining for profit, it looked at the millions of computers connected to the internet as targets for attack, not just for play.
Malware has become a major threat on the Internet today, with countless hackers and even companies creating and distributing it across the world. While some is merely created for commercial purposes, placing ads on people’s computers, there is much more that spells real danger to individuals and companies worldwide.
It couldn’t stay that way though. Governments everywhere hold with the idea that only they can pursue illegal activities. While they work to keep their citizens from committing those acts, they are quick to adopt them themselves, and use them covertly to further their country or political party’s agenda.
Such has been the case of hacking and malware in general. The first to see the value of it were the Chinese, who created a cyber-warfare branch in their army. They immediately started working to find ways into other countries computers, especially those of opposing governments and their military branches.
They didn’t limit it to that. They sought out ways to attack critical infrastructure, such as disabling power plants or bypassing the failsafes on nuclear power plants.
While China got a head start on the rest of the world, other countries have been working to catch up, including the United States of America.
Rather than making cyber-warfare a branch of the military, it seems that we’ve left it up to our intelligence organs, most especially the CIA and the NSA.
Once it moved behind the walls of intelligence operations, any efforts towards U.S. development of cyber-warfare became very hush-hush. Few knew about it, and even fewer admitted it was happening.
The vast majority of Congress was left in the dark, as they had no oversight of intelligence operations. And with Congress in the dark, the American people were totally cut out of what was happening.
Vault 7, the US Government and Cyber-warfare
The most recent Wikileaks dump, cryptically called Vault 7, has breached the secrecy of US government involvement in cyber-warfare for the very first time.
Specifically, the first 8,761 documents demonstrate the CIA’s involvement in creating millions of lines of malware code, including viruses, Trojans, weaponized “zero day” exploits, remote control systems and other forms of malware.
In total, there were over 1,000 different hacking systems, Trojans, viruses and other “weaponized” malware. While the actual code does not seem to be part of the data dump (and that’s a good thing), documentation about its existence and descriptions of its capability have been released.
All of this was produced by the Center for Cyber Intelligence (CCI), a sub-agency of the CIA’s Directorate for Digital Innovation (DDI). This directorate, the most recent addition to the CIA’s organization chart, comprises over 5,000 registered users, many of whom are programmers and expert hackers.
The release of this information is a major blow against American cyber-warfare; but apparently it’s one that needed to happen. I say that, even though I’m not entirely comfortable about it, because according to Wikileaks, the CIA has recently lost control of the majority of their digital arsenal.
This extremely dangerous code has been circulated amongst former U.S. government hackers and contactors in an unauthorized manner.
Notice that I said “former,” not current. That’s the information that Wikileaks has, and also the means by which they were given access to this amazing data. Apparently one of those former workers felt the public needed to know what was going on behind closed doors.
A CIA spy secret that anyone can use to keep him or herself safe – straight from an ex-CIA officer!
The Malware Market
Should this code make it out into the dark Internet, the results could be disastrous. Apparently there is quite a market for all sorts of malware, with customers willing to pay large sums, even into the millions for programs which will permit them access to things they shouldn’t have access too.
But that’s not the biggest problem. The big one is that once out in the open, this malware could spread around the globe in mere minutes, used and targeted by an army of individual hackers.
Unlike other weapons systems, electronic weapons don’t explode and disappear. If anything, their “explosion” causes them to multiply across computers and networks, infecting more and more as they go.
While it may be possible to take them off a particular computer, usually by scrubbing the hard drive and doing a global reinstall, they never really go away. The same electronic weapons can be used over and over again.
This code got out into the open, we can’t count on the good graces of the people who have it. While some of those CIA contractors and employees will act responsibly with what they have, invariably there will be those who will see an opportunity to use it for nefarious ends or perhaps for personal gain.
There’s another aspect of this, which is even scarier than what hackers will do with the CIA’s digital arsenal. That’s what the CIA themselves have done with it.
In 2013, Edward Snowden came forth as a whistleblower, informing the country that the NSA was spying on American citizens, in contrary to the law. This new batch of information tells us that the NSA aren’t the only ones doing that. The CIA is doing so as well.
There have always been rivalries between the various intelligence agencies. FDR created the OSS during World War II to combat this problem. Yet the OSS and later the CIA haven’t managed to eliminate that rivalry. Rather, they’ve become part of it.
One of the results of these rivalries is overlaps in areas of responsibility and multiple departments performing the same task. Such seems to be the case here, with the CIA performing its own version of the NSA’s work. Yet without knowing who ordered the CIA to do this or when it was ordered, there’s no real way of knowing whether this is an authorized operation or not.
Video first seen on Fox News.
But there’s more than just the CIA spying on our communications, like the NSA does. Apparently they’ve developed malware that targets iPhones, Android phones, smart TVs and even Microsoft Windows. This malware invokes thoughts of Orwell’s 1984, if anything does. With it, the CIA can turn on these devices and use them to spy on their owners.
For some reason, Samsung TVs in particular have been targeted by the CIA. Their malware, called “Weeping Angel,” which was developed in conjunction with the United Kingdom’s MI5, allows the television to operate in a “fake off” mode, where it appears to be off to the owner, but a microphone in the unit is recording everything said in the room and forwarding it to the CIA, via the internet.
This is just one example of the types of “back door” malware programs which the CIA has developed. Similar malware can be used to hack in to smartphones allowing the CIA to determine the owner’s location, read their e-mail, their text messages, search the phone’s memory and activate both the camera and microphone.
Quite literally, they can spy on anyone, anywhere, anytime they choose, and we can’t do a thing about it.
Even encryption won’t help, as the CIA has means of accessing the data, before it is encrypted. So much for the various communications platforms out there, which claim to encrypt your communications. If the CIA can access the information before it is encrypted, the encryption is useless. The government will know what’s in your communications, perhaps even before you do.
Before We Panic
All of this capability was probably developed with the best of intentions. The CIA, like other intelligence agencies, is involved in the war on terror. As terrorists tend to hide in the population and use the same communications that many of us do, it is necessary to develop the means of penetrating those communications to investigate the actions of those terrorists.
But where does it stop? What’s to say that they aren’t amassing files on each one of us? It’s already been reveled that the NSA is doing that, storing all of our communications in their massive data storage facilities. Snowden told us how that information is misused by analysts breaking the rules.
Those analysts aren’t the real issue though; the real issue is the government that is stealing our privacy. Spying on American citizens is a clear betrayal of our Fourth Amendment rights against unlawful search and seizure.
Yet we, the American people, are routinely subjected to a level of surveillance that the Founding Fathers couldn’t have imagined. Even those of us who are not doing anything illegal have things in our lives, which we would rather not have known.
Even if the CIA can demonstrate that they haven’t broken our Fourth Amendment rights, how can we trust them? There is literally nobody who has access to their files. So there is no way to prove that they are telling the truth.
The only information we would have access to, is that which they release, with the intention of demonstrating their innocence. Not exactly something you could take to a court of law.
There is only one solution for those of us who want privacy. That’s to foreswear the use of all modern means of communications. While not exactly practical, there may come a day when we need to; especially if the government starts misusing our information.
I just know one thing. I’m going to be careful about what I put out over the Internet, over my phone and through any other electronic means of communications I find myself using. There’s no reason to give anyone ammunition, which might find its way back, being used against me on some future date.
Click here to discover your part in this important “undercover operation” to protect the lives and privacy of thousands of Americans!
This article has been written by Bill White For Survivopedia.
References:
http://www.foxnews.com/tech/2017/03/08/cia-cyber-spying-toolkit-now-in-hands-hackers-worldwide-wikileaks.html
https://wikileaks.org/ciav7p1/
http://www.wired.co.uk/article/cia-files-wikileaks-vault-7
from Survivopedia
Don't forget to visit the store and pick up some gear at The COR Outfitters. How prepared are you for emergencies?
#SurvivalFirestarter #SurvivalBugOutBackpack #PrepperSurvivalPack #SHTFGear #SHTFBag
0 notes
Text
CloudPets data breach – industry reaction
CloudPets, a company which makes internet connected toys for children, has suffered a data breach exposing voice recordings between family members as well as sensitive account information.
The Guru reached out to security experts for their reaction on the news.
David Kennerley, Director of Threat Research at Webroot:
“The CloudPets breach is just another in a long list of poorly secured internet-connected devices, although in this case sensitive information was barely secured at all. Aside from the sheer creepiness of hacking a children’s toy, this type of sensitive information can be used by cyber criminals to access a user’s more high-value accounts. The ease with which an attacker can access users’ details including passwords can give them a starting point for accessing other accounts, and sensitive family information can be used to guess passwords and secret questions.
“At the moment we are seeing a number of attacks focused on extortion, with attackers brute-forcing platforms like MongoDB and MySQL. Users are “setting and forgetting” these protocols, tools and software, so we are likely to see more cases hit the news going forward. Companies must ensure that they are securing their devices and the information they collect properly. The CloudPets situation is a prime example of connected device manufacturers being grossly negligent towards the security of their products. In addition, users must be educated on the potential for these devices to generate and store sensitive data, as well as how to use good security practices to ensure their information is safe.”
Richard Brown, Director EMEA Channels & Alliances at Arbor Networks:
“The fact that two million voice recordings of children and their families were exposed online and held to ransom due to an insecure MongoDB installation, highlights just how attractive IoT devices are to attackers because so many are shipped with insecure defaults. A large proportion of embedded systems are rarely if ever updated in order to patch against security vulnerabilities. There are tens of millions of vulnerable IoT devices, and their numbers are growing daily.
“To combat these types of attacks, the solution is twofold. Firstly, users should look to protect their own connected devices, by isolating IoT devices from other services and the internet if they aren’t required. From a business perspective, security teams should implement best practices for ingress filtering to ensure product updates are legitimate from the network. Organisations should also isolate management traffic from data traffic, harden devices and shut down unneeded services, and understand traffic patterns and know what normal traffic looks like.”
John Madelin, CEO at RelianceACSN:
“The security of IoT devices is a growing concern in the industry, but connected toys that are easily accessible by hackers are sinister. The CloudPets issue highlights the fact that manufacturers of connected devices really struggle to bake security in from the start. The 2.2 million voice recordings were stored online, but not securely, along with email addresses and “easily guessable” passwords of 800,000 users, this is unforgivable. It’s clear that Spiral Toys hasn’t put basic security measures in place to protect its customers’ data. Knowing what critical information your organisation holds and why it’s of value to potential hackers, then ensuring that it’s stored securely is a crucial part of security management for any organisation.”
David Navin, Corporate Security Specialist at Smoothwall:
“The idea of an innocent household teddy bear sharing voice recordings, e-mail addresses and passwords of its users may sound like an elaborate plot from a budget Hollywood film, but is in fact a reality faced by over 800,000 accounts linked to the bear. As the IoT becomes increasingly prevalent in the home, ensuring data is stored safely and securely must be an absolute priority. Parents should feel comforted in knowing that the toys their children play with are secure and private, without having to worry about their personal information attached to that device could be hacked and potentially exploited.
“The news that the database where all information gathered by the teddy bear was public and not protected by a password or firewall is somewhat baffling; the fact that the customer data was accessed many times from a whole host of sources goes to show how vulnerable and attractive a company is without the proper security measures in place. Every company must therefore build a layered security defence which spans encryption, firewalls, web filtering and ongoing threat monitoring to counteract threat actors attempting to steal information.”
Bryce Boland, Chief Technology Officer for Asia Pacific at FireEye:
“This is case of a company bringing a connected toy to the market without taking the most basic steps to protect the information of children or their parents. They are using an unauthenticated database and have audio recordings and images publicly accessible. There’s little excuse for this.
It’s not an isolated incident. This isn’t the first case of a toy manufacturers failing to protect their customers’ information and it likely won’t be the last. The fact is, a baby’s crib is required to meet more rigorous safety standards and testing than connected devices like baby monitors or connected toys.
Companies need to bake security into the design of their products. Security can’t be an afterthought. Connected devices like these need to be designed assuming hackers will try to compromise them. They should be designed so that even if they are compromised and information is stolen, it is useless to the attacker.
As the number of connected devices in our lives grows, we are becoming more vulnerable to devices with weak security. This is frustrating for consumers because they don’t have good visibility into these threats or vulnerabilities. Consumers need to be aware that there will always be potential attack vectors in products connect to the internet, and if there’s no evidence from the company they’ve taken steps to secure information, they probably haven’t. In fact, even in cases where companies claim to have taken steps, we sometimes see they haven’t adequately addressed threats.
Things will probably get worse before they get better. It’s a safe bet that attackers will continue to move faster than manufacturers. In fact, this case could’ve been worse. Imagine attackers using the toys as Trojan horses to encrypt files on the home network and then demand a ransomware.
I’m not typically a fan of regulation, but governments need to shift security from an economic externality to a cost of doing business. Until that happens, these events will continue to be common.”
Paul Calatayud, CTO at FireMon:
“As I like to call IoT, the IOMT as in internet of malicious things, news of the teddy bear leak hit on two main issues: 1) the growing use of open source databases, and 2) putting devices on the internet.
MongoDB is becoming a common technology for use in e-commerce due to its flexibility and price (free). Like most things that are free, there are hidden costs in the form of no security confirmations or common security models. This results in what I call security regression, where the best practices become quickly forgotten in the rush to slap an application on the internet. Combine this with devices that are exposed to the internet you have a combination for a hackers paradise.
Consumers needs to be aware that it takes a lot of energy and investments to properly secure their information. If you have a sense the company may not be up to the task, you may want to think twice about what information you are sharing with them.”
Ben Herzberg, security research group manager at Imperva Incapsula:
“Let’s start with the good: Using a slow-to-crack algorithm (bCrypt) was a good choice, and probably prevented additional damage.
With the great increase of IoT devices (from teddy bears like the ones connecting with the CloudPets to medical devices monitoring patients to connected refrigerators), our race for innovation brings a lot of cool stuff to life in a very short time, and this will continue in the next years, as there is a potential to revolutionise the way we’re living.
However, we’ve seen a lot of security glitches from these IoT companies, and they need to understand that Information Security is not a “good-to-have”. We’ve seen 100,000’s of such devices used in Denial of Service attacks, taking down huge organisations. We’re seeing those devices being used in other malicious activities like probing websites for vulnerabilities and attempting to take over accounts.
In conclusion – every company that’s selling devices that connects to the internet must know that in that moment they become a target, and will probably not have a lot of grace time before they start getting attacked.”
The post CloudPets data breach – industry reaction appeared first on IT SECURITY GURU.
from CloudPets data breach – industry reaction
0 notes