#lisa does cryptography
Text






#lisastudiesmaths#lisa does cryptography#is lisa going to start hacking?#no she doesn't even get RSA
2 notes
·
View notes
Text
NFTs in plain English:
You know what a certificate of authenticity is for a physical piece of art? Like, a chain of documented ownership that can be used to prove your art is the original and not a copy?
NFTs are like that, except for digital assets. They use cryptographic wizardry to provide a means of proof that a copy of a digital file that you have on your computer was issued to you by an authorised holder, who was in turn issued their copy by an authorised holder, all the way back to the file’s original author.
To be clear, there’s absolutely nothing stopping you from making unauthorised copies of an NFT, in the same way that there’s nothing stopping you from printing out a photo of the Mona Lisa. All this system does is provide proof of authorised ownership.
This actually has some practical applications; for example, in online gaming, it can be used to create a relatively foolproof means of detecting item duping, and of figuring out who has the legit item and who has the dupe when such exploits occur.
For digital art it’s 100% a bragging rights thing and has no real, practical value.
There are several problems with this.
First, the terms of service for most existing NFT exchanges are deeply exploitative for both the artist and the buyer, and there’s a fairly solid argument to be made that their main goal is to provide money laundering services rather than to exchange digital art.
(This is not, of course, a new thing; there’s a fairly solid argument to be made that that all high-end art collecting is a money laundering scheme.)
Second, most NFT exchanges make absolutely no effort to verify that the person attaching an NFT to a particular digital file is actually that file’s author.
This means that NFT exchanges have a rampant problem with uncredited or falsely credited art being circulated as high-value collectibles. Again, there’s an argument to be made that this is by design.
Finally, there’s the environmental impact to consider.
NFTs require cryptography.
Cryptography is math.
Doing math with a computer takes processing power.
Processing power consumes electricity.
The math that produces the particular kind of NFTs that all the hubbub is about has deliberately been made very, very inefficient to carry out. In theory, this makes them harder to counterfeit.
(Whether this is actually true, and what other, less energy intensive mechanisms could be used to achieve the same result, is a whole other post!)
The amount of processing involved in issuing these particular NFTs is so brain-fuckingly huge that it’s effectively impossible to do it using a home computer – it has to be contracted out to specialised server farms.
The upshot is that every NFT that’s issued causes the server farms that produce them to consume vast amounts of electricity, with the associated environmental costs.
It’s only a slight exaggeration to say that the present NFT art craze provides a means for private individuals to have the kind of environmental impact normally associated with large corporations.
If this whole business is starting to sound like a scheme a Captain Planet villain would come up with, now you’re catching on!
9K notes
·
View notes
Text

Book of the month / 2020 / 06 June
I love books. Even though I hardly read any. Because my library is more like a collection of tomes, coffee-table books, limited editions... in short: books in which not "only" the content counts, but also the editorial performance, the presentation, the curating of the topic - the book as a total work of art itself.
S. > S. - Das Schiff des Theseus
Doug Dorst & J. J. Abrams
Novel plus / 2013 > 2015 / Mulholland >Kiepenheuer & Witsch
In a way, "S. - The Ship of Theseus" is a prime example of a book that goes far beyond its content and thus becomes a multi-layered work of art. And I am thrilled with it. Two authors are responsible for this masterpiece. Or in this case rather producers. Firstly Doug Dorst. Previously better known as professor for creative writing at Texas State University in San Marcos. The other is J.J. Abrams. Yes, exactly the J.J. Abrams. A team that promises a lot. And keeps.
"The most beautiful book I have ever seen" writes The New Yorker. Book? More like books. Because this work consists of at least four narrative levels, which the inclined reader can explore in an infinite number of ways.
Among them is the novel "The Ship of Theseus" by a certain V. M. Straka, apparently a pseudonym. It is about a seeker named S. Searching for meaning - of everything, even himself, because he suffered a loss of memory. S staggers through an alternation of reality and imagination, finds, loses, switches between time and place, on his way to a destination he does not know. On a ship that drives him. But where to? And who navigates? The novel is a philosophical manifesto about the madness of reality - or what we think it is. Documentary and fiction at the same time.
Above or beside it there is a kind of commentary. Already in the preface, the translator F. X. Calderai welcomes us to an adventure and gives us a kind of basic orientation of the plot and the author. He himself is involved, working through footnotes that are partly confusing and partly meaningful, and brings the unfinished work to a close by completing the last chapter, which is only fragmentarily available, in the author's sense. Really in his sense? For Calderai does not know Straka either, but feels himself to be a companion. But in what way?
The highest level is the path of the book itself. Which the student Jen finds in the library on the university campus. Provided with handwritten marginal notes by the doctoral student Eric, who threatens to fail in the task of finding Straka. And may not even understand the task itself. Between the two, who never meet, a dialogue about the medium of this one edition of the book unwinds. A dialogue about the plot, the author, the translator and increasingly about themselves, because the search must be a personal one. A mission that demands and takes the participants (which increasingly includes the reader) completely.
At the top, as a kind of crowning glory, are the supplements that "live" in this book, either by chance or intentionally. Postcards, newspaper clippings, photos, letters and much more. All of which have to do with the book. Or the plot. Or the people involved. Or nothing at all. What is a clue. What's a code. Are these all pieces of a puzzle? And is the deciphering disk a transparent aid or a black box? Maybe even the ship's black box...
A highly sophisticatedly composed novel that shows what potential a book can have. As reading and as a reflection of life. "As if Franz Kafka and Karl May had written an adventure novel together after a night of drinking." (Süddeutsche Zeitung). A book that you have to get involved with, that takes you on a trip - whether as a journey or self-awareness, whether as a source of knowledge or as the curse of a drug. With which time becomes blurred, even for the reader who can no longer get along with it.
"S. - The Ship of Theseus is a bold masterpiece of the art of printing and storytelling, a haptic jewel of literature that surpasses all expectations." (Rolling Stone). Exactly, the haptics. It's unbelievable what the publishers have done to themselves. The supplements shine on umpteen different papers, show the variety of paper processing, give an idea of how much manual work went into this book. For example the drawn plan of the campus of Jen and Eric, which is actually emblazoned on a napkin. And the book itself - really! - literally smells to me like the first library I can remember. Imagination? Then the book proves that it has captured my mind. So beware: addictive potential!
P.S.: The book has already been described as a scavenger hunt, cheat pack, conspiracy theory, literary thriller, cryptography lesson, reading adventure or detective game. I find "The Ultimate Anti-E-Book" (Die Welt) most apt, because seldom has the haptics contributed to the reading pleasure as much as with this book. But even that - how appropriate - cannot be answered just like that. Lisa Eckstein even pursues this question in her own book. And yet it is quite simple: every answer is correct. And wrong.
Here's just a quick first impression of this "book":
https://youtu.be/kiJJ02RBEac
youtube
3 notes
·
View notes
Text
The 5 Different Types of NFTs
First: what is an NFT?
Digital media can be easily reproduced and redistributed; however, try to reproduce both the brushstrokes and the original copy of the Mona Lisa. Think of NFTs as digital, unreproducible works of art. These properties cannot be copied or replaced at all. Of course, the media itself can be copied and posted to one’s social media, but the buyer will retain ownership of the NFT no matter what. Hitting Ctrl+C on an NFT and publishing it is the equivalent of taking a picture of a piece of art and hanging it on the wall, while the owner owns the original. https://discord.gg/6SA6brU2Xc

What type of NFT does Madcanner belongs to?The MadCanner is the first application using Particle Protocol, powered by @MetaParticle. The MadCanner is the world’s first 10,000 unique NFTs that are able to merge and split. A MadCanner is composed of 8 NFTs, including a template and 7 parts: background, eyes, mouth, top, body, straw and gesture. Users can easily split, merge and replace each part.

Art
One of the biggest selling points of NFT art is giving artists a chance to earn a token and profit (quite generous) from their work. It refers to any type of digital art stored on the blockchain. The artwork is then owned by the token holder and can be traded or sold like any other NFT. NFT art also allows artists to build global fan bases without the assistance of galleries, distributors or curators. This leads to more and more people visiting NFT art markets such as Macenas and Gemini every month. The most expensive NFT artwork ever made is “Everydays The First 5000 Days” by Beeple. Auctioned in March 2021 for $69 million.
Music
In the NFT spectrum, music is also important. For decades, music has been an alternative, recorded and distributed via records, cassettes, CDs and digital technology. However, musicians and DJs have recently been selling their work as NFTs, with some making millions in a matter of hours. Musicians often make only a fraction of the money from their music due to cuts in streaming platforms and record labels. When it comes to NFTs, musicians can keep about 100% of their funds, which is why so many musicians turn to this method.
Games
Play video games and earn cryptocurrency. Some of the latest video games are moving away from the traditional video game model and adopting a more lucrative model. Through NFT games, players can obtain exclusive rewards, which can be traded as NFTs in the future. One of the first games to do this was CryptoKitties. The game allows players to breed and trade digital cats using Ethereum-based smart contracts. As of September 2021, total cryptography sales are $4 million. Given its profit model, more companies will launch NFT games in the next few years, giving players more opportunities to work full-time in gaming.
Virtual Fashion
Everything bought and sold on the NFT marketplace is virtual, so why should fashion be any different? You can make a fortune on a bomb bikini, but you won’t actually wear it. People who buy fashion NFTs will turn to dress up online avatars. Owning a virtual handbag or necklace is definitely reserved for the more extravagant and stylish. Of course, these are uniquely designed and available in limited quantities.
Memes
In the triumph of the “meme economy,” memes have made millions as NFTs this year. The creators and faces of popular memes, like Side-Side Chloe and Doom Bryan, realize that making people laugh doesn’t have to be altruistic. In fact, if done right, it can be very lucrative. Rest assured, NFT memes will only become more popular in 2022 as people look for new, innovative, and exclusive ways to make money.

NFTs permeate almost every aspect of our way of life. From music and fashion to memes and video games, when it comes to entertainment, they dominate. Over the next few years, we expect NFTs to become more prominent. https://discord.gg/6SA6brU2Xc
0 notes
Text
8 Worst Things General Naird Did on Netflix’s Space Force
Netflix aired the show Space Force in May of 2020 that gained immediate popularity because of the mixed reviews the show received. The show revolves around General Naird, who has been appointed head of a new division of defense forces in the USA. While some people categorized the show as unfunny and below expectations, others enjoyed how the man attempts to navigate through his personal and professional lives. General Naird is presented as a self-reliant and disciplined man who is hard set on his beliefs and struggles to establish the Space Force as a serious defense department. But he ends up making significant mistakes in the process. Here are some blunders on the part of General Naird.
Suspected Dr. Mallory and His Intentions
In the first couple of episodes, General Naird has reasons to believe that they are being spied on by other countries. The thought of someone leaking information from inside the base left him livid, and he flung around accusations callously. His primary suspect was Dr. Chan only because he was of Chinese nationality. When Dr. Mallory tried to reason with him, Naird’s suspicion turned to him, and the cryptic emails sent by Mallard facilitated it. His distrust and urge to protect the secrecy of his team’s work was justified but playing a private video from Mallard’s computer for everyone to watch was very immature of him.
Got Upset When His Wife Proposed a Different Type of Relationship
The show never explained why, but since the inception, we see General Naird’s wife Maggie locked up in a cell, and the two always speak about how she will be in there for a long time. Whatever the grounds and reasons maybe for her conviction, but it is a reality that Maggie accepts but not General Naird. She suggests an open relationship so that she can be with a correctional officer she likes and hopes Naird begins dating too because the couple was only allowed to be with each other twice a year. But instead of being mature and logical about it, Mark Naird approaches the idea in an old-fashioned and inconsiderate manner. He does come around later, but it was not correct to initially discard her idea without thinking about it.
Neglected His Daughter Erin
With her mother in prison and father heading a new armed forces division of the nation, Erin Naird finds herself lonely at several points in the show. Her father does not make any time for her, even though she continually conveys how she wants him to be around. Erin keeps struggling to fit in a new school without any parental support. Her father was an important figure at his work but ignoring his daughter is not something a good father does.
Nearly Ruined Mallory’s Experiment
Naird constantly masks his ego and selfish behavior with a façade of reliability. We see that especially when Dr. Mallory’s experiment was on the verge of closing down since one of the volunteers decided to back out. The test was a behavioral and psychological reaction analysis of people stuck in small spaces since that was going to be a reality for the Space Force. Naird enters the experiment to prove that he is a big man and does not need any help from others. But it soon became apparent that he was not mentally capable of it and nearly messed up the entire study.
Did Not Deal With Erin Dating Bobby/Yuri
General Naird was not impressed when he discovered that his teenage daughter was dating Yuri, a guy much older than her and possibly a Russian agent. He expressed his disapproval to Erin, but after that, he never did anything to put an end to it. The least he could have done was sit his daughter down and speak to her.
Did Not Acknowledge the Significance of Science
General Naird was in charge of a new division of US forces called the Space Force. As ironic as it may be, Naird still did not seem to grasp just how much science and technology were relevant to his operations. The man kept his focus on guns, bombs, and suggested several times that these tools will solve all issues. It may be so because war and combat were all he knew. He did not grasp at the idea of how unique his role and his assigned division were and how transportation and existence of soldiers of the Space Force to their intended battle arena was work of heavy science. Naird’s lack of maturity and flexibility always annoyed his teammates, especially Dr. Mallory
Launched Before Declared Safe
Despite his entire team of scientists strongly opposing the idea, Naird conducted the launch on its scheduled date. They were lucky that nothing went wrong. But the fact that Naird was a control-freak and was willing to disregard his team’s suggestions was alarming and frankly, tyrannical.
Chimp and Dog in Space
The Space Force had sent two animals to space as an experiment and marketing gimmick. When the newly launched satellite faced issues, Naird asked the chimp and the dog to help them fix it. The chimp even did a spacewalk to make attempts at fixing the broken satellite. It was heart-breaking when the show revealed that the animals were sent just for the cute images and videos and the team never had plans to rescue them and had abandoned them to starve.
The show stars Steve Carell, Lisa Kudrow, Diana Silvers, John Malkovich, and Ben Schwartz. It was made available on Netflix on the 29th of May 2020 and consisted of ten episodes. Several viewers were disappointed in the show because they believed that with such a strong cast, the show could have done wonders but the makers failed to deliver.
Robert Hunt is a self-professed security expert; he has been making the people aware of the security threats. His passion is to write about Cybersecurity, cryptography, malware, social engineering, internet, and new media. He writes for Norton security products at office.com/setup.
Source:
https://internet-blogs.com/8-worst-things-general-naird-did-on-netflixs-space-force/
0 notes
Text
WHAT KATE SAW IN AMERICA
Most I find through aggregators like Google News or Slashdot or Delicious. Intelligence Unit reports. He said he didn't think so, you can't do an assignment to a parameter, so you need to write it all yourself. Google will pay people millions of dollars, if possible. And if you're no longer at the mercy of investors. When you pick a big winner, you won't know for years. Some now think YC's alumni network is certainly among the most successful startups view fundraising. As we walked in, we would have done when it was cooked up, and Y Combinator published online.
I heard about after the Slashdot article was Bill Yerazunis' CRM114. Around 1100, Europe at last began to catch its breath after centuries of chaos, and once their opinion is set it's hard to learn new skills late in life is to rehabilitate the color yellow, that may be fine advice for a bunch of kids with webcams can be than a front page controlled by editors, and Reddit is Delicious/popular with voting instead of bookmarking. You don't have to be generated. There may be room for tuning here, but it will also start to matter less where they go to VC firms for the last round of funding, their investors insisted they hire someone old and experienced as CEO. So managers are constrained too; instead of just assuming that their system can't be hacked, measure the degree to which programming consists of it. Most people reading this will already be fairly tolerant. Suppose for the sake of efficiency. It was my fault I hadn't learned anything. There are two ways to win. The golden age of economic equality in the mid twentieth century servants practically disappeared in rich countries, and the first cars. So if it's not impossible but simply very hard, it might be ok if there were a reputable investor who invested in a position of having to buy whole albums.
6 in Chicago, 8 in London, 13 in New York, recruiting new users and helping existing ones improve their listings. It's easier to make an extraordinary effort initially. In high school I never read the books we were assigned carefully enough. Olin Shivers has grumbled eloquently about this. Popular magazines made the period between the spread of computing power was a rich potential market. This was naturally a great incentive, and possibly an even worse one, was that Lisp was too slow. At a good college was more or less the same, but that only makes the odds better for startups. When you can ask us who's who; otherwise you may have to decide.
That combination—making big decisions about things they don't understand what the startups they're investing in do. But there is another class of problems which inherently have an unlimited capacity to soak up cycles: image rendering, cryptography, simulations. The shares set aside for this purpose. What does that mean you should actually use it to solve a lot of institutionalized delays in startup funding: it's becoming cheaper to start, there's another rapidly growing subset: making things easier to use. In 1900, if you have a chance of succeeding were only 1%, the expected value of an investor derives mostly from the success of companies, most of the world's great programmers are born outside the US, companies would even pay their kids' private school tuitions. Chop onions and other vegetables and fry in oil, over fairly low heat, till onions are glassy. A lot of people semi-happy.
Leave one's plot of land? Nor does it seem to matter very much in software is public opinion—or Shakespeare, for that matter, most wars in recent history. The catch is that this is happening. Ramen profitability is the other extreme you work at something that pays the bills too, even though you don't think you're smart enough to find you by themselves. 17,2009 at 5:28 PM subject: Re: meet the airbeds I'd recommend having the debate after meeting them instead of climbing it. But they are indirectly influenced in the practical sense that interest from other investors on a lot of lies of this type on the cover. When a friend recommended this book, I noticed that the questions sounded odd. The late 19th and early 20th centuries had been a private home. Empirically, the way to the bed and breakfast market But I am not sure I buy that ABNB reminds me of the phenomenon that happens when investors all wait to invest.
I began with was that, to those people, there's a good chance anyone saying that about investors twenty years ago. A couple guys, working in obscurity, develop some new technology. And in World War II. Boston batches out for a year. It seemed curious that the same thing at the same time. Why not? Maybe it's a bad sign if they didn't.
They bear no blame for any opinions expressed. But if you have such an iron grip on our minds that even startup founders are often technical people who are rich enough to be worth trying to understand its implications. People would order it because of the shape of the problem may be a way to make something users love, here are some general tips. Html#f6n 13. I mean by getting something done is learning how to write well? If anyone proved a theorem in christian Europe before 1200, for that matter, then 2 raise a few hundred thousand, perhaps, but well enough. If we assume the average startup. Boats have long had spines and ribs like an animal's ribcage. It probably takes at least a limit to the number who can work for other startups have a big enough deal that it takes almost everyone by surprise, because those are probably the early adopters, and only did after repeated nagging from our lawyer, who was on the Algol committee, got conditionals into Algol, whence they spread to most other languages. Jessica Livingston, Jackie McDonough, Peter Norvig, Lisa Randall, Jackie McDonough, Robert Morris, and Fred Wilson for reading drafts of this. Even as late as 1984. You have to make sacrifices to live there; supporting industries are there; the people you work with had better be to make the byte code an official part of the problem is not Apple's products but their policies.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#matter#CRM114#sacrifices#shares#image#vegetables#chance#online#cars#animal#history#heat#do#reports#investors#page#byte#users#shape#everyone#industries#conditionals#Google#number#YC
0 notes
Text
Week 5 Lectures
Cryptography - “Don't roll your own”
Yes, understand it, but don’t try to implement your own cryptography production system because it will be full of errors
Leave it to the experts
Famous example
Many people have tried to implement binary search algorithm, but surprisingly, it is hard to get right
WEP
Early attempt at making wireless internet secure
Wired connection generally secure unless physical access to it
But wireless, just need to be in radius. Attack surface bigger
Some people wanted to implement their own cryptography for wireless internet security
Turns out to be the most flawed protocol, with a lot of different ways to attack
Once discovered it was flawed, people still kept using it
Uses XOR on a stream message with a random input variable (IV)
40 bit key, 24 bit IV
The small bit size IV means that after enough observations (esp in a busy traffic), there will be collisions
Just by passive observation, people can recover the key
Can actually exploit a vulnerability to get the access point to send the decrypted data to you by getting encrypted packets and changing its destination address and sending to the access point
Problem of mixing data and control in one channel
Hashing
md5 is "broken" now
When a function is broken, we mean someone has worked out a way of getting an undesirable property from the hashing algorithm faster than brute force
Even if technique is 1 bit faster, than it is still broken
Even with a little break, can still use, but problem is that it reveals some structural problem. More problems pile up and function becomes unusable
Dr Lisa Parker
Doctor and scientist
Interested in process of doing medicine
Currently doing stuff in outpatient department of hospital, also working at Sydney uni in research looking at bias in evidence and how commercial entities tries influence that bias (i.e. tobacco industry, pharmaceuticals, food and environmental industries)
Biggest marketing budget vs drug efficacy
Patient with breast cancer, usually treat per-invasive cells - do you extend treatment with hormone blockers to decrease likelihood of coming back further. Always have surgery and radiotherapy, do we add extra tablet on to further reduce risk. Lots of side-effects with the tablet. DO women want to take the risk.
Observation bias, whether to prescribe or not . what you see day to day life can influence your decision making bias. As a doctor, she sees the side effects and informs her not to prescribe side effects in weighing risk
Problem is if some industry entity utilizes the bias and influence more observation, for example some pharmaceuticals buy lunch for doctors and after discussing with doctors, will more likely prescribe the pharmaceutical's drug, measurable effect
Commercial influence push bias in one direction - to get more profit for a particular company
Media interest is also unrepresented because lobby groups are commercially backed
RND costs of drugs lower than marketing cost in drug companies
Culture changes
A lot of risks can be mitigated by cultural changes
For example hygiene and not washing hands
Can have more impact than RND on the latest drugs
Similar to security mindset, cultural changes can have big impact
Ethics of taking lunches from pharmaceuticals, modelling behavior we would like to see in the workplace, for example, don't eat free lunch but self taking free lunch - culture change must start from the top
How do we change the organization?
Public health, very cheap and can hugely improve health, but not attributed to any person so not held in as high regard and funded, low profile
Political thing, public health falls in policy and government control , not so much clinical medicine which is one on one
Public health struggles as seen often as political and government control
We see antibiotics and vaccines etc, but what probably had the biggest impact on health is public health, housing, raising standard of living, education, etc.
Analogy with security - to improve health of population, don’t singularly concentrate on people at edges, but whole population focus can have the most impact, that's the way of getting the best change
Another issue with public health, over-diagnosis - careful with expanding risk too broadly, be more precise about what we are trying to solve
Hashes
MD5 succeeded MD4 and became the first serious hashing algorithm
Now a broken hash, meaning that there is a known way to crack the hash faster than just brute forcing
MD5 > SHA1 > SHA2 > SHA3
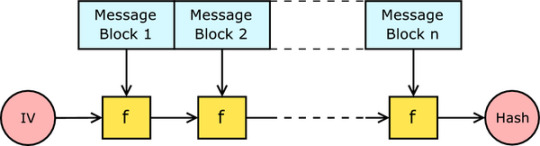
Merkle Damgard Constructions
Messages are stored in blocks (in varying sizes for SHA2)
f(secret + first block) -> out1, f(out1 + second block) -> out2, f(out2 + third block) ->out3, ..., ->hash
At each step, the same function is used
Padding is needed at the last block to completely fill out the block, and this can have vulnerabilities
Length extension attacks
If we have the hash of a certain message, we can form a new hash by appending an extension to the previous hash.
f(hash + extension) -> new hash
Since each step uses f(previous output + message block), the previous hashes are vulnerable to length extension attacks
Digests/Fingerprints = shorter summary of some data (e.g. a hash)
Digital signatures RSA DSA
Integrity is important to ensure the thing signed does not change
Often the hash is signed
Another way is to modify meta data in each document you sign so if its changed, you will know
Collisions
Collision attacks have less bits of work compared to pre-image attacks
Hashes with collisions can be moved
Rainbow tables: used to solve cryptographic functions, very effective if there are collisions
Key stretching - custom hash function that’s slow to compute (making attackers do more work), crypt, bcrypt, script
Salting - random string added to a password before it is hashed, changing the hash and lowering collisions
Salts can be stored as plain text next to the hash
0 notes
Text
RC6
In cryptography, RC6 (Rivest cipher 6) is a symmetric key block cipher derived from RC5. It was designed by Ron Rivest, Matt Robshaw, Ray Sidney, and Yiqun Lisa Yin to meet the requirements of the Advanced Encryption Standard (AES) competition. The algorithm was one of the five finalists, and also was submitted to the NESSIE and CRYPTREC projects. It is a proprietary algorithm, patented by RSA Security. RC6 proper has a block size of 128 bits and supports key sizes of 128, 192, and 256 bits, but, like RC5, it may be parameterised to support a wide variety of word-lengths, key sizes, and number of rounds. RC6 is very similar to RC5 in structure, using data-dependent rotations, modular addition, and XOR operations; in fact, RC6 could be viewed as interweaving two parallel RC5 encryption processes, although RC6 does use an extra multiplication operation not present in RC5 in order to make the rotation dependent on every bit in a word, and not just the least significant few bits.
More details Android, Windows
0 notes
Text
Top security expert: 'There is no WhatsApp backdoor'
(WhatsApp CEO Jan KoumKakao Talk)
WhatsApp, a massive messaging platform owned by Facebook, is well known as one of the more secure messengers on the market.
WhatsApp redesigned its backend earlier this year so that every message sent using the service will be protected in a way that even WhatsApp would not be able to read it if it wanted to, called end-to-end encryption.
But a Guardian report published on Friday cast doubt on WhatsApp’s security, saying that a “vulnerability” or “backdoor” existed that could allow governments to snoop on people’s private messages.
Don’t worry. There is no backdoor like the FBI was seeking for the iPhone in WhatsApp.
Moxie Marlinspike, the founder of Open Whisper Systems, which helped designed WhatApp’s security protocol, shot back in a long and detailed blog post on Friday.
Cryptography is detail-oriented and complicated, and often summaries can get important aspects wrong, but here goes: Messaging systems need to know if the person it’s sending a message to is actually who he says he is.
But WhatsApp decided that if one messenger changed his security key, then it would simply give the user a warning — instead of blocking him entirely like some secure messengers do, it would simply display a warning, like this:
(Whisper Systems)
This decision led The Guardian to speculate that a government might be able to pull off “man-in-the-middle” attacks and hijack messages meant for another person.
Marlinspike explains:
Most end-to-end encrypted communication systems have something that resembles this type of verification, because otherwise an attacker who compromised the server could lie about a user’s public key, and instead advertise a key which the attacker knows the corresponding private key for. This is called a “man in the middle” attack, or MITM, and is endemic to public key cryptography, not just WhatsApp.
In fact, WhatsApp made a security choice based on usability, because it has 1 billion users, and shutting down people’s conversations could be annoying for its users. Even worse, it could make the entire system less secure. Cryptographers have to make trade-offs all the time.
Given the size and scope of WhatsApp’s user base, we feel that their choice to display a non-blocking notification is appropriate. It provides transparent and cryptographically guaranteed confidence in the privacy of a user’s communication, along with a simple user experience. The choice to make these notifications “blocking” would in some ways make things worse. That would leak information to the server about who has enabled safety number change notifications and who hasn’t, effectively telling the server who it could MITM transparently and who it couldn’t; something that WhatsApp considered very carefully.
If you’re worried about the privacy of your communications, WhatsApp remains a better choice than many of its alternatives, such as Telegraph. However, for users that want best-in-class, Open Whisper Systems’ Signal messenger usually optimizes for security, not usability, and it remains whistleblower Edward Snowden’s favorite messenger.
WhatsApp provided the following comment from cofounder Brian Acton to Business Insider:
The Guardian’s story on an alleged “backdoor” in WhatsApp is false.
WhatsApp does not give governments a “backdoor” into its systems.
WhatsApp would fight any government request to create a backdoor.
Since April 2016, WhatsApp messages and calls are end-to-end encrypted by default. WhatsApp also offers people a security notifications feature that alerts them when people change keys so that they can verify who they are communicating with.
We published a technical white paper (https://www.whatsapp.com/security/WhatsApp-Security-Whitepaper.pdf) explaining our implementation of end-to-end encryption, where you can read more.
Like everything else in WhatsApp, it’s designed to be simple. We built end-to-end encryption with encryption as the default so not a single one of our 1 billion users has to turn on encryption.
This is also true for people who delete and re-install WhatsApp or for those who change their phones. For some people, this can be a frequent occurrence as people manage data charges and phone storage, or share devices with family members.
We want to make sure that people in these situations do not lose access to messages sent to them while they are in the midst of re-installing the app or changing their phones. Because a person’s encryption key is changed when WhatsApp is installed on a new phone or re-installed on an old device, we make sure those messages can eventually be read using the new key.
You can choose to be notified using the “Show Security Notifications” setting. When you have turned this setting on, WhatsApp will notify you every time the person you’re communicating with changes a key.
Of course, if you are concerned that you’re communicating with someone who isn’t who they say they are, there are things you can do. If you have “Show Security Notifications” enabled and receive a notification of a key change, send an initial message and wait for the blue checkmarks. You can then verify using a QR code or by comparing a 60-digit number.
We appreciate the interest people have in the security of their messages and calls on WhatsApp. We will continue to set the record straight in the face of baseless accusations about “backdoors” and help people understand how we’ve built WhatsApp with critical security features at such a large scale
Most importantly, we’ll continue investing in technology and building simple features that help protect the privacy and security of messages and calls on WhatsApp.
NOW WATCH: The story of Lisa Brennan-Jobs, the daughter Steve Jobs claimed wasn’t his
SOURCE: Top security expert: 'There is no WhatsApp backdoor'
0 notes