#phishing scams
Text
hey just a quick heads up
I just want people to know that there are tumblr blogs that were once run by real people - being taken over by bots or hacked or some sort of phishing scheme where they have this post in their active likes:
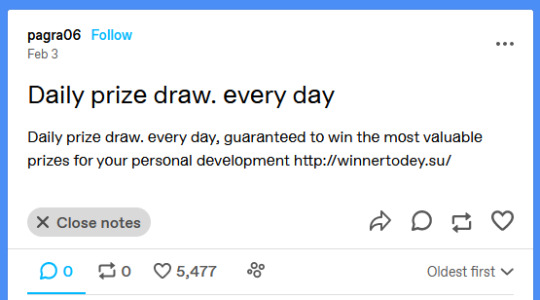
Take note of how no one has re-blogged the post and nor has commented either. The text of this post is evidently written in a fishy way that gives it away to be a scam or phishing attempt.
It should be noted that blogs might not actually be taken over by bots or stolen but that users may have fallen victim to link without realising it was a phishing scam. Please know It's not their fault! It's the fault of the people who make these scams in the first place to tack advantage of/fool people who don't know what a phishing scam is/or what a phishing scam looks like.
I'm not sure what the best course of action here is, but since these blogs where/are controlled by humans/real tumblr users - I'd best suggest to block these to keep yourself safe. Again I don't actually know if bots have taken over these blogs all from a phishing scam but I assume it works in a similar way the Ray Bans Scam happened here on tumblr not too long ago.
I suggest blocking these blogs just to keep safe, but if you are going to send a notice to staff at least leave a message that says 'this blog was controlled by a human being and I think they got hacked or fell victim to a phishing scam that somehow took over their account.' or something along those lines.
That said if anyone else has information on what's actually going on here please let me know! I'm not a computer or tech wizard, so I'm open to someone who knows the technology to at least educate to me what is currently occurring right now. Best case scenario. block the user above (particularly if you have desktop tumblr, you can block them from your 'edit my appearance page'.
EDIT: many of the blogs that have liked this post that I have made a screenshot of, have a post that says something across the lines 'hi i am [insert blog name] rate my blog [a url that's a string of random letters and words that vaguely look like a website or a tinyurl.]' Again, just thought to get the word out, and it might not be too big of a problem but to me there's just something very odd and almost artificial about these posts that make it come off as being made by a bot or a scammer..
34 notes
·
View notes
Text
Your PASSWORD will EXPIRE!!!!11!1!
Received one of those phishing scam emails this morning, claiming that my password had expired and I needed to click on the link to retain my current password. It even had today's date in the subject line, to give it that extra sense of urgency that might convince me to click on the link.
The fools! Little do they realize that we recently implemented Mutli-Factor Authentication, and now I have to log on four separate times every morning! And there is little margin for error: the slightest slip, and my system will lock itself. Then I must be humbled before the network division and propitiate them with offerings of coffee and praise before it can be restored.
I have faced the MFA. I fear neither man nor beast nor god, let alone some puny little expired password! Fear? Terror? Those are for lesser beings who have never had to deal with our network security!
So bring me your password-expired emails. I do not panic. They will fall before me just like all the others.
8 notes
·
View notes
Text
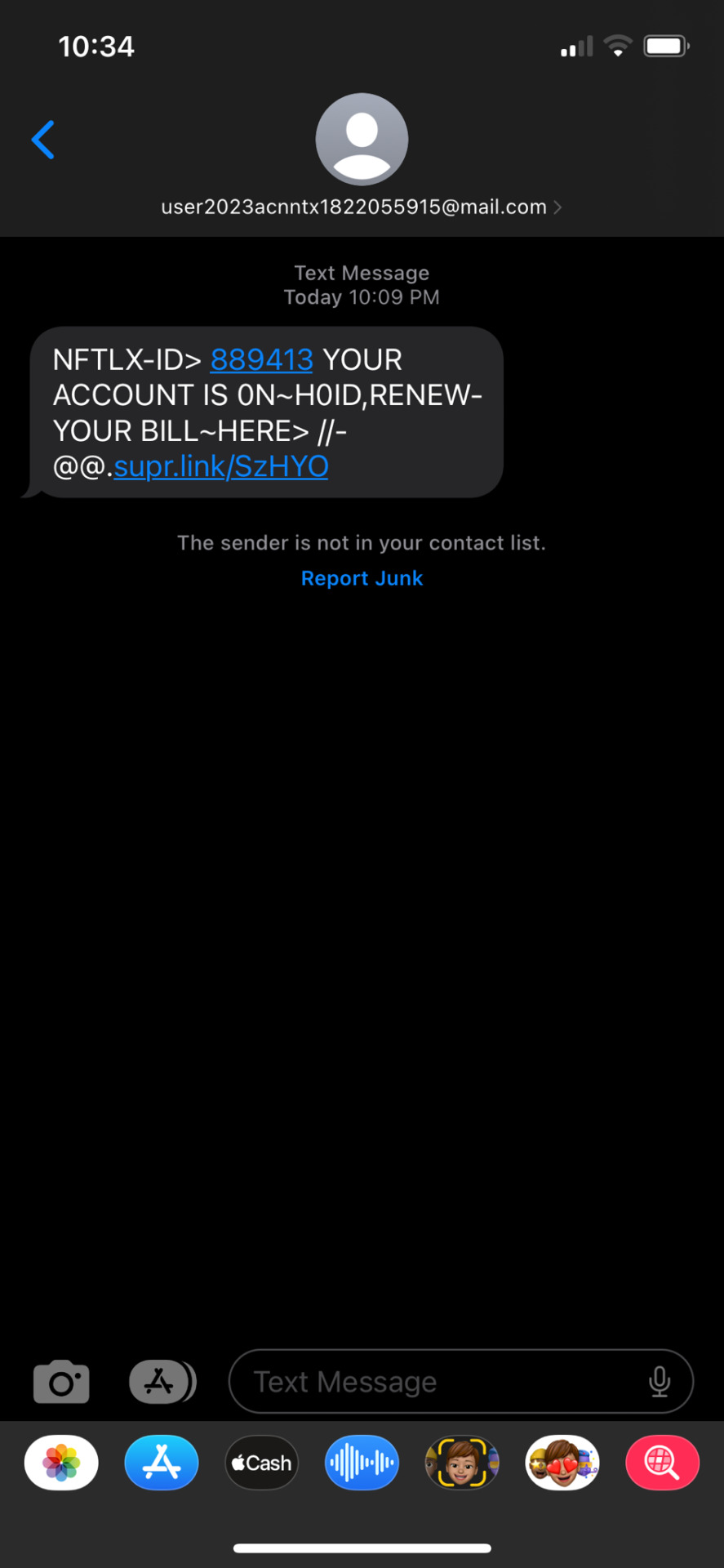
Oh man I do love these Phishing scams.
7 notes
·
View notes
Text
New phishing blog just dropped

You know the drill, report and block, I'll delete this once the user's down, user is @/time-is-everything
1 note
·
View note
Photo

Somehow this made it into my inbox despite Google’s spam filters that like to filter out direct messages from my therapist who is using a Gmail address.
I’m going to be extremely disappointed if NASA Federal isn’t at least using their logo in this email.
2 notes
·
View notes
Note
@salimavinbeamish is part of a scam account operation. They steal stories from gofundme, copy and paste those stories into askboxes, and try and trick people into giving them money.
Thank you for this. I only reblogged the post itself since I don’t always answer those asks.
But it’s appalling anyone would use what’s going on in Palestine to get money. I hope karma comes for them swiftly.
#spam bots#spam#tumblr service#damn it tumblr#tumblr scam#phishing scams#cyber scams#palestine#free palestine
1 note
·
View note
Text
Scam Alert: Protect Yourself from Online Fraudsters
Definition of “Scam Alert”
A “scam alert” is a warning designed to raise awareness about specific scams or fraudulent activity. It aims to educate people on how to identify potential scams, avoid becoming a victim, and protect their personal and financial information.
Introduction
The world of online scams is a dangerous place, and it’s critical to stay ahead of the game to protect yourself.…

View On WordPress
0 notes
Text
Heads up: Threatening software detected; opening the file is prohibited.
In an era where the digital world is as intrinsic to our lives as the air we breathe, the relevance of cybersecurity can not be overemphasized. Secure mobile apps , every download, and every apparently innocuous online interaction brings with it the possible risk of inviting malicious software right into our digital sanctuaries. This write-up aims to illuminate why downloading and install or opening destructive programs on your computer system is not simply dangerous-- it belongs to unlocking to your electronic home to a host of unwelcome effects.
Malicious software application, or "malware," is a wide term that encompasses numerous kinds of damaging software program, including viruses, trojans, worms, ransomware, and spyware, to name a few. These electronic threats are developed with purposes that vary from benign mischievousness to straight-out malevolent functions, such as stealing individual details, pirating computer resources, or securing documents for ransom money.
Cyber hygiene of downloading or opening a documents that harbors malware can trigger a domino effect of occasions that jeopardize your computer's safety and security and honesty. Here's a failure of why it's perilous:
1. ** Personal Info Theft **: Many types of malware are created to stealthily infiltrate your system and pilfer delicate data such as passwords, financial details, and individual identity details. This information can then be made use of for illegal tasks, marketed on the dark internet, and even bring about identification burglary.
2. ** System Damage **: Certain malware variations can corrupt documents, alter or delete important system data, and in extreme instances, make a computer inoperable. This not only interrupts individual or company operations but can additionally result in the loss of important data.
3. ** Source Hijacking **: Some malicious programs, like cryptojacking malware, clandestinely use your computer system's sources to mine cryptocurrency, considerably decreasing your system and potentially creating lasting damage to elements as a result of overheating or overuse.
4. ** Ransomware **: Probably one of the most nefarious forms of malware, ransomware secures your files, securing you out of your very own data. The wrongdoers then demand a ransom for the decryption trick. Paying the ransom, nonetheless, does not ensure the return of your information and additional funds the cycle of cybercrime.
5. ** Personal privacy Violation **: Spyware and certain kinds of trojans can check your activities, log keystrokes, and even turn on video cameras and microphones without authorization, bring about an extensive intrusion of privacy.
Shielding on your own from these digital threats entails a combination of watchfulness and the usage of cybersecurity tools. Always validate the resource of your downloads, avoid opening email add-ons or links from unidentified senders, and use thorough anti-viruses software application that supplies real-time defense, routine updates, and system scanning capabilities.
Enlightening oneself on the characteristics of phishing attempts and rip-off sites is also important. These commonly function as the distribution devices for malware. Search for HTTPS in web addresses, and watch out for sites that display inadequate design, spelling, and grammar mistakes, or that request unnecessary personal information.
To conclude, Secure coding standards is much better than remedy" has actually never ever been even more applicable than in the context of digital safety. The short-term adventure or benefit of downloading an unknown documents fades in contrast to the possible threats. By exercising safe surfing practices and arming your system with robust protection steps, you can substantially alleviate the risk of malware and guard not just your digital life, however your reality too.
#Secure computing#Phishing scams#Spyware threats#Hacking protection#Cybersecurity tips#Vulnerable software#Email attachment safety#Internet phishing#Digital security#Malicious URLs#Online fraud prevention#Security patches#Firewall protection#Virus scan#Secure passwords#Two-factor authentication#Cybersecurity education#Malicious code#Cyber hygiene#Data encryption#Secure networks#Security vulnerabilities#Malware quarantine#Cyber defense strategies#Suspicious activity monitoring#Identity theft protection#Secure file sharing#Malware signatures#Cyber risk management#Secure online transactions
1 note
·
View note
Text
Approval Phishing Scams See Explosive Boost, With $347 Million Stolen in 2023 – Chainalysis
The beginning of a new year inevitably comes with summarising the previous one. While yearly statistics mainly relate to achievements and positive nutshells, the time has come to face more frustrating conclusions. In this case – the vexing data by Chainalysis, indicates the overwhelming rise of approval phishing volume over the last two years.
To heed cryptocurrency security, we’ll dive into the…

View On WordPress
0 notes
Text
Cybersecurity in Personal Finance Management: Essential Strategies for Digital Safety
In today’s digital age, where a staggering 76% of Americans engage in online banking (Pew Research Center), the importance of cybersecurity in managing personal finances cannot be overstated. This comprehensive guide explores the essential strategies for protecting your online banking, investment, and transaction activities from cyber threats.
Fortifying Online Banking and Investments: An…
View On WordPress
#cyberattack statistics#cybercrime prevention#Cybersecurity#data backup#data protection#digital finance management#digital transactions#expert cybersecurity advice#financial cybersecurity guide#financial data encryption#global cybercrime costs#hard drive failure risks#investment security#online banking#personal finance#phishing scams#phishing threat awareness#public Wi-Fi security#robust passwords#secure financial apps#secure online investments#SSL certificates#two-factor authentication#VPN usage#Wi-Fi safety
0 notes
Text
Have A Glance of These 7 Common E-Wallet Scams You Need to Know And their protective Measures
In today's digital age, e-wallets offer convenience and efficiency in managing finances, but they also present opportunities for scammers to exploit unsuspecting users.
Having knowledge of the prevalent scams with respect to e-wallets is important for protecting yourself from falling prey to them.
Check out these pitfalls and safeguard your financial security as we uncover these common e-wallet scams.
1. Phishing Scams

Fraudsters use deceptive emails, text messages, or fake websites that resemble those from your e-wallet service. Clicking the included link redirects you to a fraudulent website mirroring the genuine login page. Falling for this scheme compromises your passwords or personal information including login credentials, exposing them to malicious individuals.
To Read More Click here...
#tech#tech news#tech blogs#tech updates#new technology#E-Wallet Scams#protective Measures#new features#latest version#Phishing Scams
0 notes
Text
Airdrop Alert: Protecting Yourself from Rise of Phishing Scams | ICODesk
Airdrops have become a popular method for distributing new tokens to the community. However, with the rise of airdrops, there has also been an alarming surge in phishing scams. These scams pose a significant threat to individuals seeking to participate in legitimate airdrops. In this article, we’ll explore the concept of airdrops, the growing threat of phishing scams, and crucial steps to protect yourself from falling victim to these malicious activities.
Understanding Airdrops
Airdrops involve the distribution of free tokens to existing cryptocurrency holders or individuals who meet specific criteria set by the project. These tokens are typically distributed as a marketing strategy to increase awareness, attract new users, or reward existing ones. While legitimate airdrops offer exciting opportunities, the growing popularity of this method has given rise to malicious actors looking to exploit unsuspecting participants.
The Phishing Menace
Phishing scams in the context of airdrops involve fraudsters posing as legitimate projects to trick individuals into divulging sensitive information, such as private keys or wallet credentials. These scams can take various forms, including fake airdrop websites, fraudulent social media accounts, and misleading emails or messages.

Common Tactics Used by Phishers
Fake Websites: Scammers often create convincing replicas of legitimate airdrop websites, enticing users to submit their information.
Impersonation: Phishers may impersonate official project representatives on social media, luring users into providing personal details.
False Promises: Scammers may promise significant token rewards or exclusive airdrop opportunities to bait users into revealing sensitive information.
Protecting Yourself from Airdrop Phishing Scams
Verify Official Channels: Only trust information from the official website and social media channels of the project. Be cautious of unsolicited messages or emails.
Double-check URLs: Before entering any personal information, verify the website’s URL to ensure it matches the official domain. Look for secure connections (https://) and check for subtle misspellings.
Research the Project: Conduct thorough research on the airdrop project. Verify team members, read the project’s whitepaper, and assess its legitimacy before participating.
Use Hardware Wallets: Consider using hardware wallets to store your cryptocurrency. They provide an additional layer of security and are less susceptible to phishing attacks.
Educate Yourself: Stay informed about common phishing tactics. Be wary of too-good-to-be-true offers and recognize the signs of a potential scam.
As the popularity of airdrops continues to rise, so does the threat of phishing scams. Safeguarding your assets and personal information is paramount in the world of cryptocurrency. By remaining vigilant, verifying information, and adopting secure practices, you can protect yourself from falling victim to the insidious tactics employed by phishing scammers. Stay informed, stay secure, and enjoy the benefits of legitimate airdrops without succumbing to the pitfalls of fraudulent schemes.
For More News Updates:
Visit: https://icodesk.io/
#phishing scams#airdrops#cryptocurrency#cryptotrading#cryptonews#airdrop websites#scams#airdrop phishing scams#icodesknews#icodeskupdate#icodesk#cryptocurrency prices#crypto
0 notes
Text
I just got another one of those phishing emails where it pretends to be a confirmation of a subscription you never signed up for and tries to trick you into providing personally identifying information for "confirmation purposes" when you attempt to cancel, but:
a. this one is for a weekly grocery delivery service, of all things; and
b. the fake shopping list contains nothing but ham.
I have been fraudulently subscribed to ham.
7K notes
·
View notes
Text
I wasn't gonna share this, but the situation has escalated from trolling to identity theft. I received these Asks earlier today.
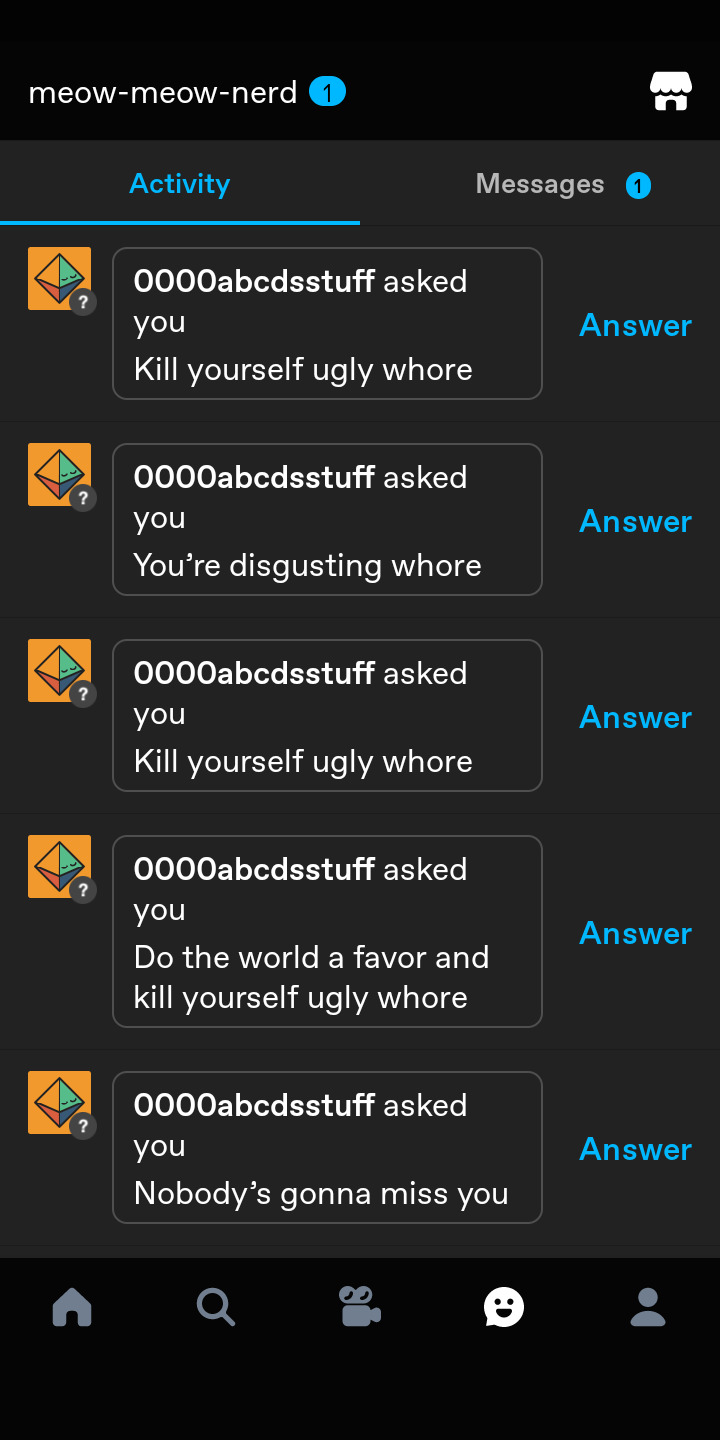

And then I received a call my bank's fraud protection department that someone had tried to use my debit card to open an online dating account. Given the nature of the events, I'm pretty sure it's the same person behind this. So I'd recommend everyone block this user.
0 notes
Text
how to manage intenet teachnology?
how to manage teachnology of internet
Managing technology on the internet involves a range of different strategies and considerations. Here are some key tips for managing technology on the internet:
Keep your software and devices up-to-date: Make sure you regularly update your software and devices to ensure they are secure and working efficiently.
Use strong passwords: Use unique, strong…

View On WordPress
#anti-malware#anti-virus#internet security#online behavior#online reputation#passwords#phishing scams#software updates#technology management#two-factor authentication
0 notes
Note
orcylightning is a scammer. The cat, Biscuit, has already been to the vet and the photo shows no signs of a rash. Please look up pet donation scams in tumblr search. I think there is a few posts there that might help you spot scams like this in the future. Delete the reblog or edit to say scam; I’d also suggest reporting the account for phishing and reporting the PayPal link if possible since it’s impersonating the real owner who isn’t a tumblr user.
Thank you so much for this. I thought it was a bit odd, but I’ll go ahead and make sure to delete the post and report the account.
Thank you so much!
0 notes