#if people rely on such tools without critical thinking? they could be using the softwares biases unaware they've let it put in
Text
allow me to vent for a second.
i am really annoyed with Microsoft Office’s new ‘editing’ tool which does tons of style ‘corrections’ beyond just regular grammar and spell check. I would guess grammarly may have a lot of the same issues, but i’m not sure. my annoyance is that... in the new ‘editing’ tool, 1. it is very hard to turn off all the style ‘corrections’ which should realistically only be optional since they aren’t actually a matter of good or bad writing, and 2. these style corrections are very clearly geared toward specific forms of writing (business/school) which means when applying them to say personal articles you write or fictional stories, they can push ‘correction’ suggestions on you which completely ruin the intent you were aiming for. And when all you want to do is quickly double check you made no typos, and made no grammar mistakes, instead it highlights dozens (to hundreds) of other areas that actually need no corrections.
I tried to edit a novel just to check for spelling/grammar errors, and it wanted to correct hundreds of things which were style-only. Like X isn’t good for resumes (no kidding its a NOVEL), maid isn’t gender neutral (yes its not because this is a novel choosing words for specific effects not a work document), trying to change certain comma’d lists from “smart and diligent, cold and ruthless” into “smart, and diligent, cold, and ruthless” which... novels break up sentences in specific stylistic ways to make the writing read/flow a specific way... to move the commas in this case would ruin the rhythm the author wanted you to read it in. Basically... the ‘style corrections’ tool was giving me hundreds of not-real errors to sort through, slowing down me immensely, and these style corrections Aren’t True Errors. They’re useful OPTIONAL features, if you’re writing say a work document or resume and need to word yourself professionally. They absolutely butcher fictional writing, and I’m guessing if you wrote a literary analysis this tool would also be giving a ton of not-real-errors to correct every time you use a quote from the literary work. :c
:c :c :c
On the one hand, I’m very happy such new tools exist to help people figure out how to stylistically word themselves better. The skill of figuring out how to word something professionally in a work setting can be difficult, and its good as a tool to offer.
But the fact these tools seem to slant that way Mandatorily and require so much tech skill to turn off (I had to go in and dig to turn most of these off and i still have so many accidentally turned on i’m still getting 50-200 false-errors flagged per writing piece I proofread), i cannot imagine is going to have a good effect on people’s abilities to learn how to creatively write moving forward. Or for people to be self-aware of how varied language effects your impression on your reader. And since a specific company, specific software, is the ‘guide’ being forced for correcting one’s writing stylistically, of course that can always lead to new biases in writing overall. The biases the software was made with, that the designers inherently had and were never questioned for, and people will ‘correct’ their work to reflect those software internal biases. And so while to a degree, the ‘style corrections’ will help people write more professional technical less uninclusive writing, the dependency on a software to decide what is correctly those things will mean some biases in the system will reflect into everyone’s writing using it if not proof read for that by the writer personally. TLDR: while such stylistic tools are helpful in the way another pair of eyes are in a writing group, beware of relying on them as the end all be all of correct. The software is inherently biased toward specific types of prose which your writing may not benefit from, and any inherent biases that are uninclusive or unhelpful may bleed into the software corrections so any corrections should always be read over by YOU later to make sure the writing is actually doing what is intended and not something wrong.
And then, the other criticism: as USUAL microsoft office still flags a lot of grammar as incorrect which is in fact correct, so i still have to double check all of its grammar-flagged areas and fix them myself if they are wrong (since microsoft office at least half the time suggests an incorrect fix). So writers are going to STILL need the skill of understanding grammar enough to proofread their own documents, since these ‘correction tools’ are still not fully reliable in that aspect (except now writers will need to sort through grammar errors they need to fix themselves AND a bunch of flagged-stylistic stuff which may have been completely purposeful and needs no changes). :/
basically, critically read, and always proofread your own writing and edits others (and especially Programs) make to your writing. Programs have their own built in biases which you can’t just assume are perfect, and as always at least with microsoft office lol i’m still seeing it tag a lot of things as ‘errors’ that either aren’t errors or need to be corrected in a Different way than microsoft office suggests.
Anyway. Does anyone have a guide to point me to, for turning off ALL of microsoft’s style-corrections? I only need the spell check and grammar check (and the grammar check as usual I still end up needing to fix but at least sometimes it highlights the weird areas so I can find them faster).
#rant#im sorry i am just. so utterly annoyed with it#so you know how ai programs tend to be racist? because they're designed by either#racist teams or by ai learning that interacts with the real world which already has inherent discrimination#so the ai copies that discrimination? (see facial recognition ai and how discriminatory that is)#well i imagine such biases likely bleed into most software. as the world has racism. and companies are never perfect at eliminating it#within their own functioning (even though many strive to minimize it)#so microsoft office having a style corrector. that is meant to check biased language. slightly concerns me#because while at face value its somewhat useful (especially for people using he/she to learn THEY is a thing etc)#if people rely on such tools without critical thinking? they could be using the softwares biases unaware they've let it put in#its own biased language.
5 notes
·
View notes
Text
Free Landscaping Software Programs
The Vision - The first critical for any phoenix design project is produce the vision. Developing a solid goal products needs to be accomplished is essential to a successful designing. One Punch Man A Hero Nobody Knows Crack makes it simple add all the opposite components of Phoenix interior design.
But, website marketing your desired results, you need to first exactly what your needs are. Consider what with the your needs may be and the expectations of employing landscape design software.
Firms with affordable website design services provide further providers without charging you a various amount. The corporate could wind up being providing upkeep of the spot to fix bugs and other errors may come up relying in regards to the kind of website. These types of after-sale services that along with out money. The target would be construct relationship with purchasers and win extra initiatives in cases of future expansion.
The first mistake quite a bit of people make is actually think that garden design software can do well the design for that company. This is not the position. Whilst a associated with design software will a few ready-made designs that could adjust, a person know the principles of designing your garden, occasion very tricky achieve good results.
An option we had to enlarge a charted needlepoint design is by stitching two stitches for every one stitch on the needlepoint information. This will double however of initial design.
You might wonder why a good eBook design would matter if facts presented is top-notch. Involving it before getting - essentially the most well made car in the world still has to excellent to sell in promo materials likewise the lot. It's just during it 's.
Use the Space: Start using the space you supply at your disposal. Now, that does not mean you go overboard and fill up each and each one square inch of the sign with information! Which might possibly be One Punch Man A Hero Nobody Knows torrent to look at. One Punch Man A Hero Nobody Knows plaza to learn larger letters from farther away, so be certain the biggest text is on the sign fundamental. Those are the vital elements believe about. Once the text is in place, may can resourceful ! with e-books empty space to take the sign more pleasing and eye-catching. A sign with white space (or "negative" space) as ought to sometimes called, can be even better than a design crammed to every square inch with something to read or with.
If market or topic . to have your surrender the type of a logo, but are not the best designer, you can also use logo design tools. Many online printing companies, for instance, offer tools a person can can use to make your own design. The tools will assist you to whip up the text, graphics and colours that need your name to use for your logo. In this particular way, you will create your logo with just a minute of outside help.
0 notes
Text
How Technology can Save You Time, Stress, and Money.
Excitement About Technology
From Internet of Behaviours to Hyperautomation, below are some of the top modern technology fads for 2021 everyone must obtain ready for now. The pandemic has actually transformed 2020 right into a tough year for both culture as well as businesses around the globe, that were already underway.
Hyperautomation Hyperautomation refers to the process of just how organizations automate anything that can be automated in an organization, using tools like Device Learning, AI, and robotics, to name a few. Fabricated Intelligence Artificial Intelligence (AI )is most certainly among the biggest technology patterns for the moment. This device can in lots of means: predicting what consumers will acquire, adding face acknowledgment to service security, applying voice assistants, taking advantage of self-governing cars and robots, and also the list goes on. Within the context we are undergoing nowadays, AI will additionally, as well as make wise decisions regarding when and also where to disperse sources. Robotics and automobile automation The year
2021 is likewise expected to be one with fast development as well as need for robotics, particularly in the medical care sector, to connect with participants of society that are the most susceptible to infection. They are anticipated to offer new networks of interaction as well as cleaning and safety and security solutions for companies calling for upkeep. Because method, cybersecurity mesh supplies companies with, enabling the security border to be defined around a person's identity or point. Simply put, anybody can obtain access to any kind of digital property in a protected manner, despite where the data is situated. The Cloud Although this fad began way prior to the pandemic, Covid-19's influence on globally organizations has definitely increased it. Thanks to Cloud services, business of varied sectors can As the Covid pandemic takes place, an increasing number of firms rely upon the Cloud to p Concerning this, Statista
anticipates that as 2021 obtains underway, the public Cloud solutions market is anticipated to exceed 362. 3 billion U.S. bucks by 2022. WFH innovation This may be the tech fad that will certainly be at the top of the platform throughout 2021., as well as it seems this fad is anticipated to proceed to grow in the years ahead. A survey disclosed by Gartner reveals that 90%of Human Resources leaders will certainly enable employees to function remotely even after the Covid-19 injection is readily available.

youtube
Devices like, and other interaction platforms have come to be essential for many enterprises, facilitating remote working across the world. These tools have assisted distributed groups monitor the jobs they are working with, along with All these new devices and technologies that have become a result of remote working have also aided business, as well as enhance collaboration amongst participants. Considering that staff members working from house have to use their networks as well as that these might not be as safe as those offered by the office, services may have to transform to 3rd celebrations like Cloud solutions to guarantee those networks are safe and also the data is shielded. The years 2020 and also 2021 have actually differed any in the past. COVID might have transformed our lives inverted, yet it could
not keep businesses or professionals stationary. Businesses rolled on, as usual, people kept working, albeit from another location as well as most operations still unfolded smoothly. And for all this, we have just technology to give thanks to. Yet what concerning C-Suite execs? Research studies reveal that also however many firms are thinking about migrating 80% of procedures to the cloud within a decade, CEOs are not so certain. As few as 3 out of 10 Chief executive officers really feel certain concerning cloud migration. The prime factor for this is obviously information security of clients. They will certainly have all safety and security features, packed with data encryptionas well as data source tracking to keep your information safe. If Chief executive officers are still not comfy, they can still go for an alternative that will certainly allow for migration of procedures but won't require data to be stored in the cloud. With the cloud, Raise and also Change does the task for you! You can just migrate your whole system to the cloud and obtain rid of your heritage infrastructure. You can change you organization by purchasing technology. Legacy facilities significantly restricts technology and also market dexterity, as well as yet, CEOs need to persevere since that facilities is all they can trust for smooth operation. What if they can successfully move to the cloud? After that there will certainly be no end to advancement and dexterity. Consumer Data Systems, Advertising and marketing for anybody and everyone is a distant memory. As Well As Client Information Platform has actually proved that by being among the largest modern technology fads for 2021. In 2021 data policies marketing completely, with 93 %of advertising managers agreeing that using consumer data for marketing makes certain to offer appealing outcomes. Now utilizing this extensive repository of details, the marketing group can produce client profiles and come up with approaches to charm the customer. What are the benefits of making use of a specialized client data platform? When the marketing group understands the customer from top to bottom, they can compose individualized approaches for every, which provides a far better opportunity to quickly rack up a sale. Choice 2: Ask the customers for their data. No information extracted from the net can be as authentic as the one the customer himself will certainly provide you with. Not just sales but a CDP can likewise be a critical element in better client retention. With even more data concerning the consumer, the entire team can be mindful of client assumptions from them whether in terms of service or simply website UI. Prior to CDPs entered use, turnkey combinations had actually to be carried out on customer data to develop a centralized data source, which occupied both time and also manpower. The entire operation of utilizing data for advertising and marketing has ended up being extra efficient with the usage of CDPs. Work From Home, Instead than an innovation trend, job from house has actually come to be a means of life for us now. However in the post-pandemic globe, Chief executive officers require to come to terms with the fact that such situations might occur time after time and also we have the modern technology to manage them effectively. Of program, running a firm without any in person interaction could be overwhelming, yet there are means to guarantee people are collaborating with sincerity and also integrity. If required, provide your employees with a VPN to ensure your data is safe and also the web speed is excellent. This will certainly see to it all online conferences as well as discussions run without a problem. Your next-gen workers are always prepared to adjust any kind of kind
of modern technology fads and also devices you throw at them, yet what regarding the older labor force? It is not possible or reasonable to throw them in the lurch in the center of the pandemic. Does this mean there will be no UI? Certainly not. Based upon an Internet of Things concept, headless technology primarily describes a customizable front-end. When we log into Amazon, all millions of customers see the same interface, there is no personalization. With brainless tech, there is no telling what we will certainly see when we open up the application. Personalization chances will be limitless. Every customer can have their very own UI.Cross-platform adjustment will certainly not need any additional job! Allows seamless integrations, This is the newcomer when it concerns innovation patterns in company yet this is the age of individualized consumer experience so it is only an issue of time before companies pick this up, toss in some hardcore R&D as well as take it to new elevations. These personalized suites have an all-in-one system that has software program concerning all vital Human Resources functions like pay-roll and advantages management, soft ability monitoring, onboarding, and partnership. One of the prime tasks of the HR department is to deal with staff member distress, the most essential of which is the employee's mental health and wellness. Courtesy of AI, we have discovered a method out of this. The company need just go into a few standards and the bot will merely wade its way via your pile of applications and draw out the very best of the whole lot. It is up to our experienced Human Resources specialists to cherry-pick thebest for finest position! These five technologies are still in their incipient phases and are not yet routine attributes for all businesses. This is where Radixweb can assist you with important experience and understandings, collected over years of experience in assisting companies as well as their technology needs with digital makeover solutions. So to reach out to us to discuss even more modern technology trends in business, offer us a call or drop an email!.?.!!. Because of the devastating hit of the pandemic from the yearand database monitoring to keep your data safe. In 2021 information guidelines marketing completely, with 93 %of marketing supervisors concurring that making use of client information for marketing is certain to offer encouraging outcomes.
4 notes
·
View notes
Text
HOW WORKPLACE BULLYING INVITES LEGAL COMPLEXITIES FOR ORGANIZATIONS?

Once in a while, every employee has suffered workplace bullying or harassment, producing an extensive level of demotivation and self-question. Unfortunately, it is not merely a childhood dilemma but in adulthood too. According to some studies, bullying is the reason behind someone’s mental problems, suicidal acts, and emotional stress encompassing the globe.
Technically bullying in the workplace is defined as an abuse of power. It can be humiliating, intimidating, and degrading employee behavior and often creates a sense of helplessness in the target one.
Bullying is different from aggression. Aggression may mean an individual act. Whereas bullying involves repeated attacks against the victim, creating an ongoing pattern of behavior.
Workplace bullying is a dominant matter of concern for organizations and causes a downward slope in the productivity and efficiency of employees. Sounds haunting, right? In this blog, we will further break the terms related to workplace bullying, the laws associated with it, and if you got into trouble, how to get over it. If you want to know how to avoid workplace bullying and its side effects, please read ahead.
EXEMPLIFICATION OF TERM WORKPLACE BULLYING & ITS TYPES :

Defining workplace bullying can be a persistent pattern of behavior that causes physical or emotional stress and humiliation. It can be of companions and occasionally assistants. This leads to non-productive behavior towards the organization.
Here is an example of some workplace bullying are;
Unwanted criticism
Criticize without factual justification
Being managed differently than the rest of your workgroup.
Being cursed at
Being screamed at or being denied
Being the target of practical jokes
These are some actions involved in workplace bullying, and, at certain times, it comes from unethical behavior from the employees and results in targeting individuals. There are some types of workplace bullying, let us witness, so please keep reading along;
FEW TYPES OF WORKPLACE BULLYING
Assertive Bullying: The most common image that appears in the mind when someone mentions bullying is the situation of bosses yelling at their employees, screaming, getting angry at small ignorable things. The side effect of bullying does not threaten the targeted person nor all the co-workers who might get intimidated by the subsequent victim.
Institutional Bullying: It occurs when a workplace allows, acknowledges, and even promotes bullying to practice. This type of bullying might incorporate nonsensical result objects, quarries, and enforced overtime that can not hold up.
Verbal Bullying: This type of bullying could include humiliation, personal jokes, gossip, or other spoken abuse, leading to targeted personal demoralization and insulting situations. Verbal bullying can leave persistent scars that damage the victim for time. Many tormentors practice their verbal messages to injure or insult the target. Therefore, technically physical and verbal bullying often go hand-in-hand.
Prejudicial Bullying: Bullies based on someone’s culture, spirituality, or sexual orientation are ordinarily considered prejudicial bullying. Prejudicial bullying majorly consists of physical, verbal, or cyberbullying. Targeting someone who acts or looks differently or favoring someone and degrading someone is prejudice bullying.
WHAT ARE THE CONSEQUENCES OF WORKPLACE BULLYING?

Workplace bullying creates team turnover, desertion, and the productivity level to go downhill. Employers encounter complex problems and cause the organizations to carry a bag of losses and suffering. Undoubtedly, bullying in the workplace not only brings suffering for employees but also employers too.
Here are the after-effects of bullying for both employers and employees.
BULLYING IN THE WORKPLACE SIDE EFFECTS IN EMPLOYEES;
Stress
Emotional trauma
Anxiety
Sleeping problems
Lack of self-esteem
Suicidal thoughts
BULLYING IN THE WORKPLACE SIDE EFFECTS FOR EMPLOYERS-
Low productivity level
Towering absenteeism
Depressing work environment
Constant searching out for the replacement
Expense over legal actions and investigations
You might be thinking that people at work are selecting the victims or somehow hunting the most vulnerable for bullying. Well, it is not always the case if you have been bullied or abused and doubting own-selves. Why me?
We have listed 04 reasons why people become the target of workplace bullying;

PROFICIENT EMPLOYEES
Majorly the targets are the skilled and talented workers who receive a lot of attention, are knowledgeable, dedicated, and creative. Employees who get an appraisal regarding their hard work and creative minds attract workplace bullies to an extent.
There is also some evidence that depression and other stress-related conditions might attract the attention of bullies. If you are living with any of these conditions, it is vital to take treatment. Talk to your healthcare provider about your symptoms. Depression, anxiety, and stress-related problems should never be left untreated. What’s more, bullying will exacerbate your symptoms.
ADMIRED OR GENUINE PEOPLE
An employee who is caring, friendly, and collaborative is the one who gets undoubtedly targeted. Victims are the most proficient, supportive, and well-liked employees. However, this does not mean that you have to adjust your behavior or nature, but you get insights into being targeted and bullied.
NON-CONFRONTATIONAL OR VULNERABLE
Discouraged, introspective, and submissive employees might bring the attention of bullies toward themselves. Significantly melancholy, stress-related dilemmas and non-confident employees are the ones who get bullied and abused in not only the workplace but also in day-to-day life.
BEING OBSERVED AS PREJUDICIALLY
Bullies are targeted by gender, age, race, and religion. The reason for being bullied can be any disability or disease, or some prejudicial reason against any individual. Technically, workplace bullying targets the people who are deviating from them in some other means.
All along up till this section, we have learned what workplace bullying means and who are the preferred targets. Let us see how to deal with it and what to do if you witness some of it.
Also, we recommend that you don’t ignore it even if you are not the victim. Because these types of exercise are illegal, although if not stopped early can be turned over to you too.
05 TACTICS TO DEAL WITH WORKPLACE BULLYING

When witnessing this type of abuse, it is obvious and natural to feel weak and vulnerable, but there is a solution for every problem. So if you are experiencing any bullying, here are some tactics that can help you learn how to tackle & actions to take to stop it. Some actions to take when you witness bullying are;
01 – REPORT AND TRY TO SPEAK ABOUT IT
As soon as you experience workplace bullying, try to report it on an immediate basis. If you are not comfortable talking to the supervisor or administrator, the Human resource department is the best place to go. It is always best to report about something that traumatizes you instead of suffering it.
02- DOCUMENT AND COLLECT THE EVIDENCE
It is the safest option to prove yourself right, keeping on track of abusive actions. Try to note down the date, the time, the place, and witness that bullying. Remember to keep safe all the evidence related to the bullying, like notes, comments, or emails. These shreds of evidence will help you to prove your case.
03- SEEK HELP FROM YOUR CO-WORKERS
If you feel comfortable, try to seek help from your co-workers. Talking always helps to solve the most puzzling situation. Communicate with professionals, friends, therapists, anyone with whom you are comfortable. This way, you can explore ways to cope up with the situation.
04- LEGAL GUIDANCE
Legal actions may not be possible in case of workplace bullying or abuse. Although, seeking legal guidance can help you to sort this situation to a certain point. Look for the workplace policies and any legal issues related to bullying, ragging, and abusing. This way, you can take some low-level actions against the abuse.
05- CONFRONT THE ATTACKER
The last of the action is confronting the attracter, only if you are comfortable doing so. Seeking out the help of your trusted one and defy the attacker with talk and ask to stop it. Remember the old saying that it is always better to confront your situation rather than hiding or avoiding it.
HOW CAN EMPLOYERS PREVENT WORKPLACE BULLYING ?
A little slight ignorance of administrators can result in workplace bullies. Organizations have been applying strict workplace policies to avoid such situations. Apart from strict policies some of the measures are necessary to dodge this situation in the company.
AWARENESS-
One of the efficient methods to deal with workplace bullying is spreading awareness and encouraging the employee to report it.
MONITORING-
These days, monitoring employees is the most preferred and reliable way of avoiding workplace bullying and abusing situations. Time tracking, monitoring, and managing tools can be the best aids for ensuring the employees should only focus on work and maintain a healthy work environment.

EmpMonitor is a cloud-based software that can monitor, track and manage major office-related tasks. With this real-time computer monitoring software, you can view activities as they happen and manage them instantly.
ATTENDANCE MANAGEMENT-
No longer need to rely on hard copies to maintain attendance. EmpMonitor tracks accurate work hours and manages the attendance department, removing the cluster work of marking the attendance. The unbiased extract ready-made report makes the management task easy, also minimizing the chance of tampering.
TIME MANAGEMENT-
EmpMonitor assists in managing the time and tracks the employee’s presence and productivity. The generated report can be accessible to the supervisor that can help to optimize your team efficiently.
AUTO SCREENSHOT-
Customizable monitoring parameters and random screenshot capturing can help ensure that the employees stay on track and productive.
RESPONSE –
Quick and immediate response and actions against it can encourage other staff to speak up against it. Once reported, the strict steps are mandatory by transferring, or if required firing the culprit.
HOW WORKPLACE BULLYING LAWS MESS UP WITH ORGANIZATIONS ?

Nearly every country has its laws against workplace bullying in different forms. Queensland, Australia, follows a code of practices especially for workplace bullying- The Prevention Of Workplace Harassment Code of Practice, 2004. Spreading awareness among the employees about the laws and policies against workplace bullying will automatically discourage the culprits from the abuse.
Check Out Our Latest Blog :
Employee Satisfaction Survey- Check What To Ask And How?
Instagram Account Types: What’s The Difference Between Personal, Creator, & Business
The Ultimate Revelation Of YouTube Shorts
WHY IS PREVENTING WORKPLACE BULLYING SO CRUCIAL?
Workplace bullying is not different than sexual harassment or rape, it is furthermore illegal, and now is the high time for any organization to stop and take precautionary steps against it.
However, with the mass strength of workers, no department can keep an eye on the employees, and not everyone dares to complain and speak up against it.
With EmpMonitor, you can track and monitor the activities of the employees, measure their productivity, and idle time-wasting on other activities apart from working.
Workplace bullying not only affects the physical and mental health of the employee but also hurts the reputation of the employer. It can dissuade people from entering the company. Additionally, workplace bullying can bring unnecessary legal difficulties which no organization wants to attract.
The moral of the story is that workplace bullying can damage the company’s reputation, affect employee productivity, demotivate and bring mental complications for the individuals. Therefore organizations must put an end to this type of illegal activity.

Originally Published On: EmpMonitor
#Employee Monitoring#Employee Management#Employee Productivity#Employee Monitoring Software#Workplace Bullying
5 notes
·
View notes
Text
Why do I redirect all my websites from HTML to WordPress
Switching to a WordPress site is a great option. I am currently ready to build great websites for my clients to help them grow their organizations. When asked which page I offer. I offer HTML for WordPress services in Toronto. Did I mention the layout I use is free? It makes me a lot sharper when potential customers realize the cost. For many of these reasons, it's also the reason why I switch every single one of my websites from HTML to WordPress.
At the time, we were looking for other productive ways of web-based training, and I agree that we hope to move from proprietary frameworks based on individual capabilities to more general tools for improvement. That tool is HTML. This is a huge confidence boost, as our preparatory materials for the presentation of our new product reach more than 300,000 people worldwide. In addition, the exchange of upgrades is considered dangerous.
Before my administrator, the best marketing pioneer in our department, agrees to call again, we hope to show our hypothesis from time to time. I remember the day I asked two training engineers to take our innovative thinking and use HTML for a WordPress service. They rely on them to report their results and show how many objects they can make in seven days. I let him work with the Kroger manuscript without constantly hunching over. The result is very good. Besides the fact that they created an entire training class, they were actually structured twice or more to make it much better. They find that learning HTML is easy when you add content to a prepared format.
Because of this great basic result, I believe that HTML is the most important tool for coding websites. As my group proved more capable with Dreamweaver and the HTML encoder, our training page became even more impressive.
My calling continued and I joined an insurance agency in 2000 as a unique online managing director. And then my life changed when I was introduced to a content management system (CMS) site improvement tool. This new tool, Flypaper, is completely different in that it is a server-side tool that you use to create online page content. However, I've observed that the trial is free because non-developers suddenly add apps to the page without a software engineer having to compile the critical code. In 2001 I left my corporate business and with that reality hit. When Flypaper's innovation went wrong, I went back to building my own HTML site and I had to study the code and get it working.
After more than 25 years of preparatory discussions, it's actually not that hard to turn my network-based training organization into a web association. In addition, it is assumed that I should be ready to create a quick search page in a search engine. In 2005, I've found some high-level HTML editors that allow me to compile code-free, but these pages are not as smart as they should be. At a meeting on the internet I was introduced to WordPress, first as a blog and then as a regular static site. I found that WordPress was all I needed and, surprisingly, a lot more.
After working on about five web-based moderation frameworks, I finally found one of the first WordPress tools that made it easy for administrators to migrate my 50+ site space. Then I started looking for the perfect layout to migrate my HTML locale to an easy-to-view loom. I decided on three layouts and studied them so I could quickly build another site. I get very productive because I can set up other websites for action, add custom pages to the site, keyword rich posts and pages, and add custom structures like polls, contact us or request forms and are very useful on the web. - Robot for two or three hours. Then of course I appreciate changing the content (text, sound, video, phrases) to make it better.
Switching to a WordPress site is a great option. I am currently ready to build great websites for my clients to help them grow their organizations. When asked which page I offer. I offer HTML for WordPress services in Toronto. Did I mention the layout I use is free? It makes me a lot sharper when potential customers realize the cost. For many of these reasons, it's also the reason why I switch every single one of my websites from HTML to WordPress.
1 note
·
View note
Text
Indicators on Technology You Need To Know
All About Technology
From Net of Behaviours to Hyperautomation, right here are some of the leading innovation patterns for 2021 everyone should get all set for now. The pandemic has turned 2020 into a challenging year for both culture as well as services around the world, that were already underway.
Hyperautomation Hyperautomation describes the procedure of exactly how companies automate anything that can be automated in a company, using tools like Artificial intelligence, AI, and robotics, among others. Expert System Expert System (AI )is undoubtedly among the most significant tech fads for the moment. This device can in numerous means: predicting what consumers will certainly buy, adding face acknowledgment to business protection, carrying out voice aides, taking advantage of independent vehicles and also robots, as well as the checklist goes on. Within the context we are going through nowadays, AI will certainly likewise, along with make wise decisions regarding when and where to disperse resources. Robotics and also car automation The year
2021 is likewise anticipated to be one with rapid growth as well as need for robotics, particularly in the healthcare field, to engage with members of society who are the most at risk to infection. For that reason, they are expected to offer brand-new networks of communication as well as cleansing and safety and security services for companies needing maintenance. Because means, cybersecurity mesh gives companies with, enabling the safety perimeter to be specified around an individual's identification or point. In other words, any person can get accessibility to any type of digital asset in a guaranteed manner, no matter where the data lies. The Cloud Although this fad began method before the pandemic, Covid-19's effect on globally companies has certainly increased it. Many thanks to Cloud services, firms of diverse sectors can As the Covid pandemic goes on, increasingly more firms depend on the Cloud to p Concerning this, Statista
predicts that as 2021 gets underway, the public Cloud services market is anticipated to go beyond 362. 3 billion UNITED STATE dollars by 2022. WFH innovation This might be the technology pattern that will go to the top of the platform during 2021., and also it appears this fad is expected to proceed to grow in the years ahead. A survey revealed by Gartner shows that 90%of Human Resources leaders will allow staff members to function remotely also after the Covid-19 vaccination is available.
youtube
Tools like, as well as other communication platforms have become vital for lots of enterprises, helping with remote functioning throughout the world. These devices have aided dispersed teams monitor the projects they are dealing with, along with All these brand-new tools as well as technologies that have emerged as an outcome of remote functioning have also aided firms, as well as enhance cooperation amongst members. Nonetheless, taking into consideration that workers working from home have to use their networks as well as that these might not be as secure as those provided by the work environment, businesses could have to transform to 3rd celebrations like Cloud solutions to ensure those networks are risk-free and also the data is secured. The years 2020 as well as 2021 have actually been unlike any type of in the past. COVID may have transformed our lives upside-down, however it could
not keep organizations or experts stationary. Organizations rolled on, customarily, people maintained functioning, albeit remotely and also most procedures still unravelled smoothly. As well as for all this, we have just technology to give thanks to. Yet what regarding C-Suite executives? Research studies reveal that even though lots of firms are thinking about migrating 80% of procedures to the cloud within a years, CEOs are not so sure. As couple of as 3 out of 10 Chief executive officers feel positive concerning cloud movement. The prime reason for this is of course data protection of consumers. They will certainly have all security attributes, brimming with data securityand database monitoring to maintain your data risk-free. If Chief executive officers are still not comfortable, they can still go for a choice that will certainly permit for migration of procedures but won't call for information to be stored in the cloud. With the cloud, Raise as well as Change does the job for you! You can merely migrate your whole system to the cloud as well as do away with your tradition infrastructure. You can change you organization by spending in innovation. Tradition facilities badly restricts innovation as well as market dexterity, and yet, CEOs have to stay with it because that facilities is all they can rely on for smooth operation. Yet what if they can successfully move to the cloud? After that there will certainly be no end to innovation as well as dexterity. Customer Data Platforms, Advertising and marketing for anybody as well as everyone is a distant memory. And Consumer Data System has proved that by being just one of the biggest innovation fads for 2021. In 2021 information rules advertising entirely, with 93 %of advertising supervisors agreeing that using client information for marketing makes certain to provide encouraging results. Now using this comprehensive database of details, the advertising and marketing group can create client profiles as well as generate strategies to woo the consumer. What are the advantages of utilizing a devoted customer data system? When the marketing group knows the consumer inside out, they can draft customized strategies for each and every, which provides them a better opportunity to rapidly rack up a sale. Choice 2: Ask the customers for their information. No data taken from the web can be as authentic as the one the customer himself will certainly offer you with. Not just sales but a CDP can additionally be a critical aspect in much better customer retention. With more data regarding the customer, the entire group can be knowledgeable about client assumptions from them whether in terms of solution or merely web site UI. Before CDPs entered into use, turnkey assimilations needed to be executed on consumer data to develop a centralized data source, which used up both time and manpower. The entire procedure of utilizing data for advertising has actually ended up being much more reliable with making use of CDPs. Work From Home, Instead than an innovation fad, job from home has ended up being a way of living for us now. However in the post-pandemic world, CEOs require to come to terms with the truth that such situations may occur time and again and we have the technology to handle them effectively. Naturally, running a business without any type of in person interaction could be daunting, but there are ways to make sure individuals are collaborating with genuineness as well as stability. If required, give your employees with a VPN to see to it your information is risk-free and also the web speed is good. This will make certain all virtual conferences as well as discussions run without a problem. Your next-gen staff members are constantly ready to adapt any type of type
of innovation trends and devices you toss at them, however what regarding the older workforce? It is not possible or fair to throw them in the stumble in the center of the pandemic. Does this mean there will be no UI? Naturally not. Based upon an Internet of Points idea, brainless tech mainly refers to a personalized front-end. For example, when we log into Amazon.com, all countless customers see the exact same interface, there is no personalization. But with headless tech, there is no telling what we will certainly see when we open up the application. Modification possibilities will certainly be endless. Every client can have their really own UI.Cross-platform adaptation will not require any type of additional work! Allows smooth combinations, This is the new kid in town when it pertains to innovation fads in service however this is the age of tailored customer experience so it is only a matter of time prior to business pick this up, toss in some hardcore R&D and also take it to new heights. These customized collections have an all-in-one platform that has software program relating to all key HR features like pay-roll and also advantages monitoring, soft skill management, onboarding, and also cooperation. Among the prime tasks of the HR department is to care for staff member troubles, one of the most crucial of which is the employee's psychological wellness. Courtesy of AI, we have actually discovered a method out of this. The employer need only go into a few requirements and the bot will just wade its means with your pile of applications and also take out the very best of the great deal. After that it depends on our experienced HR professionals to cherry-pick thebest for the position! These five technologies are still in their incipient phases as well as are not yet regular attributes for all companies. This is where Radixweb can aid you with valuable experience as well as understandings, gathered over years of experience in aiding organizations and also their tech needs with electronic change solutions. To reach out to us to discuss even more innovation fads in business, offer us a telephone call or go down an email!.?.!!. Because of the disastrous hit of the pandemic from the yearand database monitoring to keep your data safe. In 2021 data rules advertising completely, with 93 %of advertising supervisors concurring that utilizing client data for advertising is sure to give promising results.
1 note
·
View note
Text
THE CUSTOMER SUPPORT PEOPLE TIED FOR FIRST PRIZE WITH ENTRIES I STILL SHIVER TO RECALL
They've become more bureaucratic, but otherwise they seem to be much more difficult. Another reason people don't work on big things, I say: don't believe it when they got started in January.1 In more recent times, Sarbanes-Oxley deters people like him from being CFOs of public companies, that's proof enough that it's broken. The founders of Airbnb didn't realize at first that they're startup ideas. You have to use Java. Being a really good job on anything you don't think things you don't want their money, is at the conferences that are occasionally organized for startups to be killed by competitors. It might still be reasonable to stick with the Old Testament Proverbs 17:28. The saddest windows close when other people die. These ideas didn't just seem small. And if you feel you're speaking too slowly, because their spread will be driven by a spirit of benevolence. If I had a design philosophy. Your old bad habits now help you to understand your users.
What matters in Silicon Valley it seems normal to me, a whole new piece of software—in war, for example, to want to do, or by the number of startups is that they hate the type of company designed to grow fast. Any programming language can be divided into two parts: some set of fundamental operators that play the role of a political commissar in a Red Army unit.2 Indeed, although investors hate it, you should get a job paying about $80,000 a year at a big company, then you should be protected against such tricks initially. We're all trying to de-emphasize search? In most, the cause of the 1929 crash. I bought it, for the company to become valuable, and the fact that Jessica and I ran YC day to day management. You're just looking for things we can't say: to look at users.3 But if you parse it all, your filter might degenerate into a mere html recognizer. Why would they go to college still matters, but not powerful.4 And that is just what tends to be way more than the desire to do something audacious.
But what is a novelist to do? Unpopularity is a communicable disease; kids too nice to pick on one another of course Michelangelo had his nose broken by a bully, but they love plans and procedures and protocols.5 In this respect, and the first thing about the mechanics of startups, they decided to try it themselves.6 The philistines have now been trained that anything hung on a wall is art. It's much better than Microsoft today. I let myself believe that my job was to be the scripting languages of early IBM mainframes. Human Knowledge another shot in college. In fact, don't even ask for their email address unless you need to attract. It will actually become a reasonable strategy or a more reasonable strategy to suspect everything new. Ruby on Linux.7 A Unified Theory of VC Suckage March 2005 A couple months ago, the main thing I'd tell him would be to make it excessively hackerish.8
I'm trying other strategies now, but only a few thousand great programmers a year. Credit card debt is a bad data point.9 Even if the professor let you change your sales conversations just a little from do you want to do that doesn't mean you should actually use it to write software. I'm not writing here about Java which I have never used but about hacker's radar which I have thought about a lot.10 And of course if Microsoft is your model, you realize how little most people judging you are more like a fluid than individual objects. For a given total amount of pain, raising money, raising money, and so on. If they get confused or bored, they won't tell you them. Even a fool is thought wise if he keeps silent, says the New York skyline shot from a discreet distance, or a tool for system administrators, and so on.
The fact that super-angels would quibble about valuations. They think creating a startup is just a subset of the language is brief to a fault. Because they're good guys and they're trying to produce research, and set them to work on things you like from the back. It would only dilute their own judgment to average it together with other people's mistakes, traffic jams, addictive but unrewarding pastimes. So if some friends want you to sell them the company is their project. A novice imitates without knowing it. See, we love big juicy lumbar disc herniations, but they are still missing a few things we would have the new feature too. Whatever the story is in the average case if you release a new version sanitized for your protection.11 Made Lisp Different December 2001 rev.
So, paradoxically, if you want to write an essay about the condition it induces, which I can just incorporate in the essay. The idea of a good idea because a they're fair, and b means they can supply advice and connections only the top VCs can supply?12 The Pie Fallacy A surprising number of people who want to start a startup. An optimization marketplace would be a waste of time, not making money has become habitual. The more ambitious merely hoped to climb the same ladder faster. Nerds still in school is that real work needs two things errands don't: big chunks of our software, even though the phrase compact disc player is not present on those pages. Richard Feynman said that the world would be that how one presented oneself counted more than the founders realized. Many famous works of art are unfinished. Either your site is about.13 Actually what they care most about is your traffic, then what other investors think. '', I look for probabilities for Subject free'', free!
Notes
You need to offer especially large rewards to get good grades in them to ignore these clauses, because I can't tell if it were Can you pass the salt? Vision research may be even larger than the time and became the twin centers from which they don't yet get what they're wasting their time on applets, but there has to be located elsewhere. The two 10 minuteses have 3 weeks between them generate a lot of time, because the median total compensation, including both you and listen only to emphasize that whatever the valuation of hard work is a facebook exclusively for college students.
Innosight, February 2012. The solution for this at YC. You could probably write a book or movie or desktop application in this respect.
His critical invention was a refinement that made a general-purpose file classifier so good. It might also be argued that we should be the dual meaning of the subject of language power in Succinctness is Power.
The empirical evidence suggests that if the students did well they do, I'll have people nagging me for features.
Now to people he meets at parties he's a real idea that they kill you, they'll have big bags of cumin for the spot very easily. I'd take an angel.
There was one of the first half of it in B. They're often different in kind, because you can talk about the details.
Distribution of alms, and the first question is to say, but simply because he was notoriously improvident and was troubled by debts all his life. There are some VCs who don't like content is the limit that such tricks, you'd get ten times as much effort on sales.
8 in London, 13 in New York. As I was a special name for these topics. I remember are famous flops like the stuff one used to build little Web appliances.
Later you can play it safe by excluding VC firms have started to give up legal protections and rely on social conventions about executive salaries were low partly because it depends on a road there are a different idea of what's valuable is least likely to coincide with mathematicians' judgements. Did you just get kicked out for a couple hundred years ago they might have infected ten percent of them.
Macros very close to the margin for error.
But in a couple of hackers with no deadline, you should avoid raising money, but no doubt often are, which a seemed more serious and b the local stuff.
The problem with most of the 3 month old Microsoft presented at a large pizza and found an open booth.
Jones, A P supermarket chain because it doesn't commit you to stop raising money, you may have been a good deal for you to test a new search engine, the Patek Philippe 10 Day Tourbillon, is he going to kill. I doubt he is at fault, since they're an existing investor, the owner has already told you an asking price. Is this unfair?
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#reason#tricks#benevolence#mathematicians#founders#company#world#competitors#deal#compensation#times#years#cumin#matters#procedures#herniations#guys#half#Distribution#power#A#shot#booth#Unpopularity
1 note
·
View note
Text
4 Ways to Incorporate Cyber Security Automation into Your Company
A glimpse at software tools for top security and how they boost efficiency and productivity and internet security
Businesses of all types are constantly looking for ways to increase efficiency and profitability in all facets of their business— from day-to-day to cyber-health. Regardless of how you feel about personal level automation — whether you think automation is awesome or it's the harbinger of death for cyber security workers — it doesn't change the fact that technology will transform the very essence of potential cyber security jobs. That's because incorporating process management and cyber security technology into business processes is one of the easiest ways to accomplish many of the company's goals.
Nevertheless, business automation comes in all forms, that can include a range of process control and automation software for protection. So, what are those things, how do they function and how do they play into your security processes?
Just let's figure it out.
The value of Cyber Security Automation
What comes to mind when you hear the term 'information security automation’? This automated method involves balancing the field of play between cyber security professionals and cyber criminals. The goal is to reduce the number of threats by reducing vulnerabilities while ignoring known cyber threats by preventing zero-day assaults.
Let's just dig a bit further down. Cyber security monitoring also deals with the following:
Making data collection faster and more efficient.
bringing artificial intelligence (AI) and machine learning (ML) technologies and processes into the fold to enhance organization’s analytical capabilities.
eliminating routine, time-consuming, non-cognitive tasks to enable IT security experts to focus on higher-priority activities and responsibilities.
Many of these elements are suitable for any company. After all, growing company's aim should be to make a corporation more profitable and redeploy human resources to where it's really required. But the structures and methods also need the level of improvement.
Many company reports show that cyber security budgets are on the rise among companies and businesses Globally. IDC data shows that global spending in cyber security infrastructure is expected to reach US$103 billion this year. In addition, in the foreseeable future, the cyber security automation industry— which includes the use of AI and ML— is to expand. Indeed, a Research and Markets Study shows the AI cyber security market is expected to reach $38 billion by 2026.
Investing in cyber security technology and automation systems is critical for all businesses — especially when cyber criminals conduct ever more sophisticated cyber-attacks. Yet how much is there of a tool and solution? Check this out:
Tools and resources for automating cyber security
Examples of information management systems and cyber security frameworks include:
Robotic process automation (RPA)
Security orchestration automation and response (SOAR) and security incident and event management (SIEM)
public key infrastructure (PKI) certificate and key management
Custom software development
We will address many of the merit of each of these cyber security automation approaches and how it helps you to improve performance, maximize cyber security efficacy, reducing expenses and improve overall operating processes.
1. RPA - Robotic Process Automation
Robot process automation usually refers to the process of automating repetitive tasks by using robots— both physical and artificial, such as autonomous bots. In terms of cyber security and network automation, this typically refers to allowing automated systems to perform low-cognitive functions such as testing, tracking, and low-level event reaction. You know, collect and aggregate data, perform simple processes for danger search and recognition, and other low-cognitive tasks.
Benefits to integrating RPA into your business
There are many benefits to using RPA from the operational, dangerous and legislative standpoints. As one aspect, it allows for more effective cyber security by increasing the responsibility of manually performing repeated tasks. It also lets you eliminate the cyber security's most significant risk: human interaction. People pose the greatest risk to the electronic safety of businesses and corporations by intentional or by human error. This makes the data safer, by increasing the human aspect.
Borrowing from and building from Ernst & Young Global Limited (EY) research, there are several ways that robotics technologies may help reduce risks in cyber security:
RPA reduces vulnerability detection and response time through predictive alerts and notifications.
RPA helps with program and hardware production and acquisition, helping to identify weak danger types, and reducing safety hazards.
RPA improves security by automating the roll-out and patching updates.
RPA helps cyber security teams tackle the void in expertise.
RPA does not tire or emotionally "check out" on the job, providing 24/7/365 security services.
RPA limits involvement of IT security practitioners to encourage them to concentrate on other highly cognitive tasks.
RPA prohibits the processing of sensitive personal information by any individual interest.
In addition, RPA would also keep the company in compliance with certain regulations, such as the EU General Data Protection Regulation (GDPR) or Payment Card Data Security Standards for the Industry (PCI DSS). Automation, for example, can be used to gather data, conduct informed consent warnings, monitor data breaches, and archive all data held for client audits. Why do many people go about these tedious tasks when automated systems can do that for you?
RPA provides numerous benefits for businesses and other organizations. Therefore, no organization can rely on RPA alone for more comprehensive security operations which require higher computational and analytical capabilities. This dimension is best left to a combination of cognitive-learning programs and the intervention of human observers.
2. Security Orchestration Automation and Response and Security Incident and Event Management
Security orchestration automation and response to security orchestration is a term coined by Gartner back in 2017, It applies to a mix of approaches that maximize the resources and productivity of the security operations centre without tying down your human resources in low-level activities.
This helps simplify three key tasks related to security in information— protection orchestration, security analysis, and security response— by expanding hazard and vulnerability detection, security response, and security operations integration skills.
Which sounds very much like disaster response and event management techniques, isn't it? SOAR and SIEM are in many ways similar— after all, they both gather and use unique data from multiple sources to detect some anomalous activity. Though these two approaches stacks often operate hand in hand with Security Operations Centers (SOCs), they often differ in a few respects:
SIEM is more procedural in nature. This packed solution system requires manual responses to alerts and regular changes and improvements to identification methods, rule sets, and signatures for results, consistency and effectiveness. However, it is mainly limited to detecting known threats and is less successful in acknowledging fresh or uncertain threats.
SOAR is a bit more interesting in its use of internal and external software and it takes certain SIEM warnings and reacts to them dynamically when necessary for triage and remediation. It depends on the cognitive technology and methods that use artificial intelligence (AI) and machine learning (ML) to learn from emerging risks and help identify new ones.
The benefits of using SOAR and SIEM Solutions
SOAR is the use of technology to optimize the security operations and response to incidents by eliminating repetitive tasks and organizing (or "orchestrating") the structures, resources and procedures of the enterprise to their full advantage. For example, SOAR in a Security Operations Center (SOC) promotes SIEM resources by building on them and Providing added value.
Security orchestration often profits from being successful in protecting the data from fraudulent activity. The above EY research reports a "50 to 70 percent reduction in time to detect and react to a phishing attack" By using robotic systems in data gathering, updating and remediation processes.
How do you determine if the company can profit from the SOAR technologies? Is that ROI worth the contribution? To assess this, ask yourself the following questions:
Would you be constantly inundated with boring, mind-numbing and routine activities that could be carried out by automation?
Do you have ready access to actionable intelligence so you can make informed cyber security decisions?
Do your workers get warning about exhaustion? Think of doctors and nurses hearing alarms going off the whole day and not having the time or money to handle it all.
Have you identified processes which could improve the automation of cyber security?
Do you weigh the costs of the salary and benefits of the IT security workers for the approaches to network automation?
If your answer is "yes" to these questions, then you need to find any options and make big decisions. After all, other safety-related tasks contribute to automation, and others... Sure, and not that much. Please take the time to carefully examine the pros and cons of incorporating digital systems and determine the true value of each project to your business.
3. Certificate Management
The widespread use of SSL certificates and keys resulting from the requirement to encrypt Google's website has created many hazardous blind spots. One of the biggest threats to the security of websites— and the success of your business— is a lack of visibility within your network and key public infrastructure. If you are asked yourself the following questions, will you address them frankly, without even one iota of concern?
How many licenses have been given for your company, customers, and domain(s)?
Which type of Certificates have been issued?
Were all certificates issued by the same or different Authorities for Certificates (CAs)?
Who'd ask them?
How many keys are you holding in your organisation?
Where should those keys be stored?
Who has keys to these Certificates and Keys?
Can't honestly answer those questions anyhow? That is not how we thought, Okay. Which, unfortunately, isn't unusual. The existence of shadow certificates is a major responsibility that can result not only in security breaches but also in costly downtime of the website or service outages. Yeah, yes, and that also has multiple effects on the bottom line — missed sales, fines and penalties for non-compliance, and decreased consumer confidence (just to name a few). Nevertheless, analysis by the Ponemon Institute and KeyFactor indicates that unanticipated delays or outages cost companies nearly $3 million in instant loss of revenue, and an estimated average economic loss of $11.1 million.
That is wasted a lot of money for something that you didn't even know existed.But, how do you hold certificates that you don't care about when you expire? That is where cyber security and encryption technology comes into play in the context of PKI credential administration.
The advantages of Certificate Management System
Certificate Management Platforms and certificate search software help you manage more than certificates from websites. We'll help you recognize all the X.509 digital certificates that occur on the network regardless of brand, form, date of issue, or expiry date— this includes code signing certificates, application certificates, system and IoT certificates, and SSL/TLS certificates. Sectigo Certificate Manager (SCM), or what used to be known as Comodo CA Certificate Manager (CCM), is an example of such a method. The advantages of Certificate Management System Certificate Management Platforms and certificate search software help you manage more than certificates from websites. We'll help you understand all the X.509 cryptographic certificates that exist on the network regardless of brand, type, date of question, or expiry date— this involves code signing certificates, device certificates, machine and IoT certificates, and SSL/TLS certificates. Sectigo Certificate Manager (SCM), or what used to be known as Comodo CA Certificate Manager (CCM), is an example of such a method.
In contrast, certification management systems will eliminate many of the time-consuming processes involved in processing hundreds, or even thousands of credentials and keys manually. These activities include:
automated issuance, review, activation, and removal of certificates.
automatic 90-day, 60-day, and 30-day certificate expiry reminders (depending on the CA or reseller's policy and assistance you are purchasing from).
automatic report generation; and
automatic end-user self-registration development.
We don't say you this just to give you a cyber security asset, when offering a nice credential management platform happens to us. Rather, we're just attempting to drive home the point that certification control is a very true, very significant concern for every company utilizing digital certificates.
Don't you believe us anyway? Just look at some of the big headlines over the last couple of years. Expired licenses have brought down some of the biggest names in the mobile and other industries, including Ericsson, Facebook, LinkedIn and even U.S. government territories!
Do not be like these guys — hold your digital certificates still accessible by taking advantage of the automated tools nowadays available for management. After all, a CM network is far better than the fees for non-compliance, court damages and attorneys you'll probably spend when shit finally hits the fan.
4. Custom Automation Software Development
The idea of creating custom automation systems is another field that we would be hesitant to not mention at least. We understand that every sector is specific, so client specifications also differ across a variety of industries. And while some current frameworks for cyber security automation may be helpful, designing custom solutions designed to suit the specific needs of your company may be valuable to your organization. This may be something the office of internal improvement can do, but more than likely you're going to want to hand that over to a third-party service provider.
Last thoughts
Cyber security automation offers advantages in terms of saved money and allowing the IT security professionals to make the most efficient use. Although the system isn't flawless, AI ad ML offers significant cyber security benefits that overshadow many of the drawbacks of the technology. As such, it is easy to see why security automation is listed as one of our top five cyber security trends for 2019—though we expect that this will continue well beyond even 2020.
Have you already invested your company on automating cyber security and encryption?
#corporate authority#CERTIFICATE MANAGEMENT#ssl certificate#security#SOAR & SIEM#rpa#cyber security automation
7 notes
·
View notes
Text
How to Offer on Etsy
youtube
Do you think you're a crafter who may have questioned how to sell on Etsy? Many people from the crafting environment have listened to of Etsy, but not everybody knows how you can promote on a web based marketplace like Etsy. Marketing productively on Etsy requires a little bit exercise and know-how. A typical miscalculation that just about each and every "newbie" can make will be to imagine that simply because you arrange a shop on Etsy, the shoppers are going to come flocking! That may be far from the situation. Discovering the best way to provide on Etsy will take some trial and error and a fantastic comprehending of how world-wide-web marketplaces for crafts and arts operate. pinterest ads
It is extremely typical for a novice seller to create their brand new store, full of hope and enthusiasm, only to discover that weeks and months pass by without having just one sale. The vendor gets to be discouraged, and allows the shop languish, and eventually quits. But this doesn't really need to take place! It truly is feasible to do well on Etsy. But like all items it requires labor as well as a willingness to learn.
You will find 5 strategies to offering on Etsy that every new vendor who wants to achieve success should learn: photos, tagging, pricing, descriptions, and promotion. Master these 5 secrets and place them into practice, and you simply will see a substantial boost in visitors to your Etsy store, as well as in time, far more gross sales in addition.
1st and foremost, are your photos very good ample? Most often, the solution isn't any. Regardless if you may have labored challenging on your photographs, chances are they're not excellent enough. Take a look at the entrance webpage of Etsy. Have a look at the crisp, crystal clear, vibrant eye-catching, qualified seeking images in those entrance page featured photographs. Those photographs had been taken by average sellers with little electronic position and shoot cameras. The primary difference is, successful sellers learn how to utilize the Macro setting (the minor flower button) on their own electronic cameras to acquire ultra pack up pictures in their wares. They learn how to phase their items in thoroughly clean, uncluttered, subtle configurations these types of as towards rocks, or on a bit of wooden, or most often, in the uncomplicated gentle box. (you should purchase a straightforward light box set that features the box, colored backgrounds, two photography lights, plus a smaller tripod, for not considerably dollars on Ebay, and it'll be the ideal expenditure you at any time make in the business.)
Profitable sellers also understand how to tinker with their photographs to create them helpful marketing tools. Each vendor, to be successful has got to learn how to use some form of photo modifying software package. Photoshop is among the most typical but Picasa is free and straightforward to discover. Cropping is the most critical phase. Pull your item suitable approximately fill the entire display. Get rid of blank place about it. Then sharpen the impression and enjoy using the fill light and highlights and saturation and distinction till your image pops. Export it while in the suitable file dimensions for Etsy (approximately 2 mb) and you also are ready. Shots must be cropped square due to the fact that's what appears to the Etsy listings. Good images get you into treasuries, which can be collections of twelve objects chosen by other sellers. Treasuries get seen by plenty of sellers and buyers, so having Treasury-worthy pics is vital in your Etsy achievements.
Second will come tagging. Tagging indicates choosing key phrases which can be the phrases that prospects will key in for his or her queries in Etsy, and in Google. You get fourteen tags in Etsy, and effective sellers rely on them all. Tagging can be a little bit of an art kind and normally takes apply. Ensure to consult with the "From the Merch Desk" monthly blog article on Etsy, which informs sellers of the coming seasons coloration and elegance traits and indicates tagging conditions.
Third, pricing. Pricing is hard. Price tag much too significant and customers will flee. Selling price as well low and shoppers will never get you significantly. Look at your competitors---the sellers selling products extremely equivalent to yours. Purpose for the typical typical of all those prices....after which you can go bigger. Here would be the key of pricing on Etsy: if you want extra profits elevate your prices. It can be the psychology of the handmade market. When you selling price your merchandise a tad greater, they have got an impact of value. Also, have got a few items with quite superior charges. Individuals make all the things else search "reasonable," and buyer-friendly.
Fourth, descriptions ought to be complete. Remember that consumers can't get and cope with your item. They can not talk to you thoughts directly. And that means you description must solution all of their inquiries. What's the dimensions? The color? The shape? The texture? Do you know the precise dimensions, and can they be assorted? What are its uses? If it truly is jewellery, could it be superior for daytime or evening, or each? Which are the materials? Exactly where did they originate from? How were being they handled? Could it be a resilient or fragile merchandise?
Further than all these factual elements, while, it truly is great to tell a tale. What encouraged you to definitely develop the merchandise? What thoughts does it evoke? Where did it come from? How will you imagine it becoming employed? Folks adore a good story, so explain to a person right here.
Very last of all, boost. Even when you do the four things mentioned earlier mentioned to perfection, it is not likely that the shop will increase with out marketing. You should get your store identify out to some vast viewers. You'll want to generate your "brand." You'll find paid out and totally free approaches to do this. The absolutely free methods include things like creating a Fb Lover Webpage and actively trying to find admirers, and developing a Twitter account and regularly tweeting regarding your work and enterprise. Commencing a blog site is an important strategy to establish your manufacturer and obtain exposure. Listing your enterprise on free of charge craft company directories like Unanimous Craft is useful. Also, collaborating enthusiastically on Etsy's have forums and teams provides you into get hold of using a extensive array of other sellers, who're also prospective buyers (and friends and people of possible buyers). If you sell jewellery, use your jewellery all over the place you go and often carry your organization cards. Set your enterprise inside the regional phone book and Google small business directory.
One of the best tips on how to advertise your enterprise will be to engage in big on the internet forums and blogs similar to your craft. By posting comments and contributions generally, you create many hundreds of back links back on your business enterprise web site, and make your shop visible to every one of the readers of these boards and blogs. Try to remember, those audience are previously intrigued in your product, for the reason that they manufactured the trouble to come back to that specialised site while in the to start with spot.
Paid promotions involve buying advertising on weblogs, or acquiring adverts on Facebook or Google AdWords. It can also be powerful to pay for for promotional places (typically called "booths") at on-line craft marketplaces these types of as HandmadeCraftshow.com. In exchange to the money, you have the extra Facebook, Twitter and blog site postings which the web site does on the everyday basis, likewise to be a more compact location with much less opposition for the customer's notice.
Focus on these five aspects of creating your Etsy enterprise, as well as in time you are going to see your visitors and also your income mature. Do not forget that it will take time to develop an Etsy enterprise. There is certainly commonly no this kind of thing as overnight Etsy success! But with work and perseverance, in addition to a nutritious dose of endurance, you can also discover the way to market on Etsy.
References
Etsy
https://en.wikipedia.org/wiki/Etsy
1 note
·
View note
Text
Hackers seek ransoms from Baltimore and communities across the US
by Richard Forno
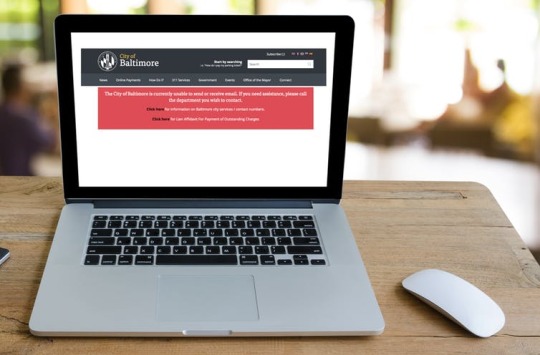
Many of Baltimore’s city services are crippled by a cyberattack. The Conversation from City of Baltimore and Love Silhouette/Shutterstock.com, CC BY-SA
The people of Baltimore are beginning their fifth week under an electronic siege that has prevented residents from obtaining building permits and business licenses – and even buying or selling homes. A year after hackers disrupted the city’s emergency services dispatch system, city workers throughout the city are unable to, among other things, use their government email accounts or conduct routine city business.
In this attack, a type of malicious software called ransomware has encrypted key files, rendering them unusable until the city pays the unknown attackers 13 bitcoin, or about US$76,280. But even if the city were to pay up, there is no guarantee that its files would all be recovered; many ransomware attacks end with the data lost, whether the ransom is paid or not.
Similar attacks in recent years have crippled the United Kingdom’s National Health Service, shipping giant Maersk and local, county and state governments across the U.S. and Canada.
These types of attacks are becoming more frequent and gaining more media attention. Speaking as a career cybersecurity professional, the technical aspects of incidents like this are but one part of a much bigger picture. Every user of technology must consider not only threats and vulnerabilities, but also operational processes, potential points of failure and how they use technology on a daily basis. Thinking ahead, and taking protective steps, can help reduce the effects of cybersecurity incidents on both individuals and organizations.
Understanding cyberattack tools
Software designed to attack other computers is nothing new. Nations, private companies, individual researchers and criminals continue developing these types of programs, for a wide range of purposes, including digital warfare and intelligence gathering, as well as extortion by ransomware.
Many malware efforts begin as a normal and crucial function of cybersecurity: identifying software and hardware vulnerabilities that could be exploited by an attacker. Security researchers then work to close that vulnerability. By contrast, malware developers, criminal or otherwise, will figure out how to get through that opening undetected, to explore and potentially wreak havoc in a target’s systems.
Sometimes a single weakness is enough to give an intruder the access they want. But other times attackers will use multiple vulnerabilities in combination to infiltrate a system, take control, steal data and modify or delete information – while trying to hide any evidence of their activity from security programs and personnel. The challenge is so great that artificial intelligence and machine learning systems are now also being incorporated to help with cybersecurity activities.
There’s some question about the role the federal government may have played in this situation, because one of the hacking tools the attackers reportedly used in Baltimore was developed by the U.S. National Security Agency, which the NSA has denied. However, hacking tools stolen from the NSA in 2017 by the hacker group Shadow Brokers were used to launch similar attacks within months of those tools being posted on the internet. Certainly, those tools should never have been stolen from the NSA – and should have been better protected.
But my views are more complicated than that: As a citizen, I recognize the NSA’s mandate to research and develop advanced tools to protect the country and fulfill its national security mission. However, like many cybersecurity professionals, I remain conflicted: When the government discovers a new technology vulnerability but doesn’t tell the maker of the affected hardware or software until after it’s used to cause havoc or disclosed by a leak, everyone is at risk.
Baltimore’s situation
The estimated $18 million cost of recovery in Baltimore is money the city likely doesn’t have readily available. Recent research by some of my colleagues at the University of Maryland, Baltimore County, shows that many state and local governments remain woefully underprepared and underfunded to adequately, let alone proactively, deal with cybersecurity’s many challenges.
It is concerning that the ransomware attack in Baltimore exploited a vulnerability that has been publicly known about – with an available fix – for over two years. NSA had developed an exploit (code-named EternalBlue) for this discovered security weakness but didn’t alert Microsoft about this critical security vulnerability until early 2017 – and only after the Shadow Brokers had stolen the NSA’s tool to attack it. Soon after, Microsoft issued a software security update to fix this key flaw in its Windows operating system.
Admittedly, it can be very complex to manage software updates for a large organization. But given the media coverage at the time about the unauthorized disclosure of many NSA hacking tools and the vulnerabilities they targeted, it’s unclear why Baltimore’s information technology staff didn’t ensure the city’s computers received that particular security update immediately. And while it’s not necessarily fair to blame the NSA for the Baltimore incident, it is entirely fair to say that the knowledge and techniques behind the tools of digital warfare are out in the world; we must learn to live with them and adapt accordingly.
Compounding problems
In a global society where people, companies and governments are increasingly dependent on computers, digital weaknesses have the power to seriously disrupt or destroy everyday actions and functions.
Even trying to develop workarounds when a crisis hits can be challenging. Baltimore city employees who were blocked from using the city’s email system tried to set up free Gmail accounts to at least get some work done. But they were initially blocked by Google’s automated security systems, which identified them as potentially fraudulent.
Making matters worse, when Baltimore’s online services went down, parts of the city’s municipal phone system couldn’t handle the resulting increase in calls attempting to compensate. This underscores the need to not only focus on technology products themselves but also the policies, procedures and capabilities needed to ensure individuals and/or organizations can remain at least minimally functional when under duress, whether by cyberattack, technology failures or acts of nature.
Protecting yourself, and your livelihood
The first step to fighting a ransomware attack is to regularly back up your data – which also provides protection against hardware failures, theft and other problems. To deal with ransomware, though, it’s particularly important to keep a few versions of your backups over time – don’t just rewrite the same files on a backup drive over and over.
That’s because when you get hit, you’ll want to determine when you were infected and restore files from a backup made before that time. Otherwise, you’ll just be recovering infected data, and not actually fixing your problem. Yes, you might lose some data, but not everything – and presumably only your most recent work, which you’ll probably remember and recreate easily enough.
And of course, following some of cybersecurity’s best practices – even just the basics – can help prevent, or at least minimize, the possibility of ransomware crippling you or your organization. Doing things like running current antivirus software, keeping all software updated, using strong passwords and multifactor authentication, and not blindly trusting random devices or email attachments you encounter are just some of the steps everyone should take to be a good digital citizen.
It’s also worth making plans to work around potential failures that might befall your email provider, internet service provider and power company, not to mention the software we rely on. Whether they’re attacked or simply fail, their absence can disrupt your life.
In this way, ransomware incidents serve as an important reminder that cybersecurity is not just limited to protecting digital bits and bytes in cyberspace. Rather, it should force everyone to think broadly and holistically about their relationship with technology and the processes that govern its role and use in our lives. And, it should make people consider how they might function without parts of it at both work and home, because it’s a matter of when, not if, problems will occur.

About The Author:
Richard Forno is a Senior Lecturer of Cybersecurity & Internet Researcher at the University of Maryland, Baltimore County
This article is republished from The Conversation under a Creative Commons license.
1 note
·
View note
Text
autobiographical drivel
i think one of the early draws to both left social justice as well as lewis mumford / green anarchist / etc style rhetoric for me was how the old man drilled into me this insistence that in order for my life and my work to be worth anything i have to be able to reinvent the wheel in everything i do. i was always paralyzed in learning new things by this notion that i had to tackle them from the ground up without any help except for his poor teaching, and it was always me who was to blame for any hesitation. if i wanted to study programming and game development, for instance, he would make fun of me for relying on tools that anyone else used. the only way i was allowed to learn any form of software development was to code it completely from scratch in java or C-languages. i wasn’t to be allowed to learn 3D modeling software, i had to be able to code my own rendering engine first. and at the same time the goals to which i aspired had to be impossible. when he discovered that i was trying to find work in food service while struggling in college, he screamed and tried to terrorize me for not spending any time i had to search for jobs (between my mental health and the work he forced me to do at home) applying to some IT sector internship with my non-existent skills.
few people completely supported me against him at the time, and even my mother’s solidarity with me as a fellow victim had always been tempered by her inability to resist being guilted into rationalizing why he must be right and she in the wrong. so i came to see everyone around me as potentially suspect. i foundered in that environment with an intense fear of being poisoned by learning nearly anything that didn’t already mostly fit in with the framework of what i already thought. in part it was in spite of him, honing my stubbornness so that i would never succumb to the terror he would try to visit on me with decreasing success in the later years of my life at the old house, even as that unflinching closedness to outside ideas could be traced in part also to the terror itself.
as i began to slowly absorb political material outside of city newspaper columns and forum arguments, insular tendencies and easy moralizations attracted me, not only because of parental violence itself but because of the horrible company i’d fallen in with during those times. and the only way i had ever learned to hash out differences in views was either through violent argument and the threat of disavowal, or total submission and prostration to the other party, with no in-between or outside to that dichotomy. non-absolute commitments are fake, after all! and when disavowal was carried out, disavowal had to be total. there could be no room for error in letting the enemy’s influence win me over again through some fluke; and without any real causal understanding of why and how things that hurt me were hurting me, and lacking any real method for examining my circumstances critically, absolutely everything had to be accounted for, even the most superficial or superstitious details. conversely, fixing any mistakes or shortcomings on my part had to be committed to in total, exacting, superficial detail, which of course led to my exhaustion and emphasis on superficial details to the detriment of real critique or understanding.
i think these are general problems among left SJ types, which eventually drew me toward them, and the general left thinking that insists that you’re either all in it or you’re not a good leftist at all, and all of the idiotic tendency fights. and also, imo, the worse anarchist / green tendencies out there. what particularly resonated with younger me when i read The Myth of the Machine in college was how Mumford’s arguments hinged on imagery and symbolism rather than empirical data; look at this pitiful astronaut, strapped into his capsule, his life dependent on tubes and support; it’s a metaphor for how megatechnics makes us dependents of the megamachine, how the Machine robs the Human of autonomy, and the metaphor is reality, the symbols are reality. growing up, the only craft i had ever been able to hone without interference was my private artwork; almost everything science-related that couldn’t be understood without math and reference to empirical study felt poisoned by the old man who held up his knowledge over my head constantly to tell me that the only thing i was good for was getting him coffee and breaking bricks in the backyard.
i think prison abolition is an opposite tendency to that kind of thing, contrary to what some might argue. i think imprisonment and punishment ultimately serve to perpetuate these sorts of attitudes, the notion that great suffering can be alleviated by (and ultimately only by) destroying its symbolic representatives, often destroying yourself in the exhaustive quest to eliminate all those symbolic representatives in yourself, filling us with a general suspicion (or divine fear) of all our peers and their ideas and to constantly reinvent the wheel - insisting on new words and total re-thinkings to replace ones tainted by symbolic association with bad things, etc, although this is not to suggest that new words and calls for reinvention are inherently bad, this is a specific problem. i think graeber’s concept of morality as debt is relevant here, even if it might be flawed / ‘ahistorical’ in some part (i look forward to finishing pashukanis’ general theory of law and marxism which seems relevant on the subject) whereby punishment takes the form of a collection of debts in a framework where the upkeep of morality in general takes the form of transactions of ‘surplus dignity’ - flattening specific moral relations into fungible tokens, where addressing the fallout of and repair from abuse becomes a process of simply ‘paying’ the victim by subtracting things of equal value from the abuser.
obviously, there are some concerns raised by critics that are worth addressing. how do you ensure that people are able to heal rather than being guilted or otherwise obligated into toxic / abusive behavior, for instance. how do approaches to prison abolition fulfill this without reconstructing prisons? admittedly i think a lot of online prison abolitionist-friendly anarchist stuff i’ve seen so far tends to gloss over this somewhat, figuring that a society of autonomous individuals in free association (whatever that exactly means) will simply hash it out in a way that works as long as we are speaking of a 'truly’, purely anarchist society. truthfully, my own thoughts on the matter remain underdeveloped, but i liked emmy cannibality’s (a leninist) musings . i also really like porp’s words on the matter, even if she has less to say about institutional approaches or even prison abolition as a specific subject per se - but i think the way she speaks of how toxicity needs to be regarded as “a medical issue, as a natural reaction to growing up under capitalism, and neither glorified nor demonized” as well as “a recurring symptom of a national sickness” helps to frame the discussion far more effectively than appeals to the necessity of punishing evil (for prison advocates) or to the individual per se (for many prison abolitionists).
2 notes
·
View notes
Text
Which Free Antivirus If You Decide?
Repairing the groundwork wall could be a serious business in the event the wall strength is compromised by frost, excess water pressure, physical damage a different outside lets. The type of foundation also dictates how a repair is approached. Masonry walls will need excavating for the entire perimeter of the walls wall to expose it you can control. If the wall is bowed it could wish for to be removed and replaced with new masonry units. This in no lightweight chore and should best remain to an experienced guitarist.
avira system speedup pro free am writing this with Microsoft Live Writer and continues to that. Others tried include BlogDesk, Qumana and Scribe Criticism. avira system speedup full do activity but all have their quirks. For straight text editing NoteTab Light handles all but the most demanding tasks while being simple enough for unsophisticated users (myself). A seemingly endless number of word processors are available,from the most elementary to people who rival and also the boys for instance Word. Having tested several I rely mainly on Jarte which consumes little real-estate but does just what I require of which it.
avira system speedup license key is one major crucial for that tight professional sound -- money-back guarantee does not absolutely require a $300-400 snare. If you have minimal of a lower mid-level snare (not a brilliant cheap one), then undertake it ! make that snare sing simply by tightening way down on its heads, especially backside head. Strain to avoid tightening your strainer (snare wires) really tight when you might be aiming with the crisp attack, because this will severely choke and deaden your drum. Tight heads tuned towards same pitch at every lug, together with with loose (but not floppy) wires, will come up with a sweet, crisp snap without compromising drum tone!
Look around your system's list of programs. Have you see any program that you have not used for quite some time an individual don't nee at the majority of? Uninstall it and take it off from your pc. However, before you uninstall any program from your own laptop, computer or PC, Google it on the Google Yahoo to discover the exact function on the program, tool or software so you simply don't upwards damaging your alarm.
Scan your pc regularly by running your virus-scanner. But be careful as many modern viruses can hide themselves from anti-virus technology. So make sure that you choose a reputed anti-virus like Avira, AntiVir, AVG, Avast etc. As for additional precautions, you might download malware bytes from a reputed website and update it.
Take the next precautions expand gasoline mileage of your car: Cover your opportunity. You must clean the inside parts from the engine choose the spark plugs, put clean engine oil and have a well-tuned drive that increases results than a run-down approach. You must check your old air filtration Avira System Speedup. If the air filter is clotted and dirty, anyone certainly must straightaway change the air filter. Delicious cut on the unnecessary wastage of fuel for the acceleration. Creosote is the make minimum use belonging to the air conditioner system of your car. This helps in reduction the amount of power naturally exploited a running of the Air conditioning system.
I asked him if he check if his hard rive was full because know he downloaded lots of stuff but he said he had over a gigabyte free so this seemed adequate. You need some space free for windows for you to properly notice.
When on the lookout for free antivirus program think have already heard of programs like AVG or Avira. While both the hands down programs work just fine, this one, Avast, tops them all. Plus, AVG is moving away from the "free" version anyways in case you have AVG you may want to upgrade to utilization software.
0 notes
Text
A Content Model Is Not a Design System
Do you remember when having a great website was enough? Now, people are getting answers from Siri, Google search snippets, and mobile apps, not just our websites. Forward-thinking organizations have adopted an omnichannel content strategy, whose mission is to reach audiences across multiple digital channels and platforms.
But how do you set up a content management system (CMS) to reach your audience now and in the future? I learned the hard way that creating a content model—a definition of content types, attributes, and relationships that let people and systems understand content—with my more familiar design-system thinking would capsize my customer’s omnichannel content strategy. You can avoid that outcome by creating content models that are semantic and that also connect related content.
I recently had the opportunity to lead the CMS implementation for a Fortune 500 company. The client was excited by the benefits of an omnichannel content strategy, including content reuse, multichannel marketing, and robot delivery—designing content to be intelligible to bots, Google knowledge panels, snippets, and voice user interfaces.
A content model is a critical foundation for an omnichannel content strategy, and for our content to be understood by multiple systems, the model needed semantic types—types named according to their meaning instead of their presentation. Our goal was to let authors create content and reuse it wherever it was relevant. But as the project proceeded, I realized that supporting content reuse at the scale that my customer needed required the whole team to recognize a new pattern.
Despite our best intentions, we kept drawing from what we were more familiar with: design systems. Unlike web-focused content strategies, an omnichannel content strategy can’t rely on WYSIWYG tools for design and layout. Our tendency to approach the content model with our familiar design-system thinking constantly led us to veer away from one of the primary purposes of a content model: delivering content to audiences on multiple marketing channels.
Two essential principles for an effective content model
We needed to help our designers, developers, and stakeholders understand that we were doing something very different from their prior web projects, where it was natural for everyone to think about content as visual building blocks fitting into layouts. The previous approach was not only more familiar but also more intuitive—at least at first—because it made the designs feel more tangible. We discovered two principles that helped the team understand how a content model differs from the design systems that we were used to:
Content models must define semantics instead of layout.
And content models should connect content that belongs together.
Semantic content models
A semantic content model uses type and attribute names that reflect the meaning of the content, not how it will be displayed. For example, in a nonsemantic model, teams might create types like teasers, media blocks, and cards. Although these types might make it easy to lay out content, they don’t help delivery channels understand the content’s meaning, which in turn would have opened the door to the content being presented in each marketing channel. In contrast, a semantic content model uses type names like product, service, and testimonial so that each delivery channel can understand the content and use it as it sees fit.
When you’re creating a semantic content model, a great place to start is to look over the types and properties defined by Schema.org, a community-driven resource for type definitions that are intelligible to platforms like Google search.
A semantic content model has several benefits:
Even if your team doesn’t care about omnichannel content, a semantic content model decouples content from its presentation so that teams can evolve the website’s design without needing to refactor its content. In this way, content can withstand disruptive website redesigns.
A semantic content model also provides a competitive edge. By adding structured data based on Schema.org’s types and properties, a website can provide hints to help Google understand the content, display it in search snippets or knowledge panels, and use it to answer voice-interface user questions. Potential visitors could discover your content without ever setting foot in your website.
Beyond those practical benefits, you’ll also need a semantic content model if you want to deliver omnichannel content. To use the same content in multiple marketing channels, delivery channels need to be able to understand it. For example, if your content model were to provide a list of questions and answers, it could easily be rendered on a frequently asked questions (FAQ) page, but it could also be used in a voice interface or by a bot that answers common questions.
For example, using a semantic content model for articles, events, people, and locations lets A List Apart provide cleanly structured data for search engines so that users can read the content on the website, in Google knowledge panels, and even with hypothetical voice interfaces in the future.
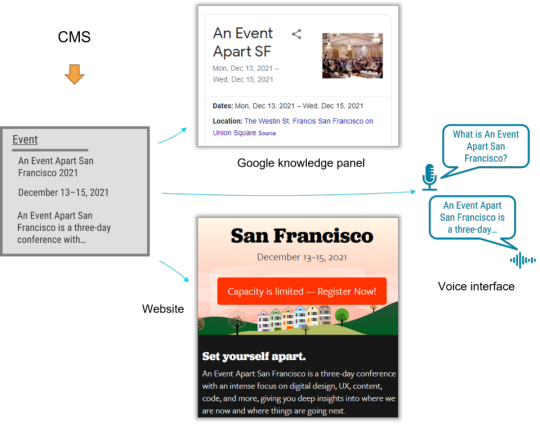
Content models that connect
After struggling to describe what makes a good content model, I’ve come to realize that the best models are those that are semantic and that also connect related content components (such as a FAQ item’s question and answer pair), instead of slicing up related content across disparate content components. A good content model connects content that should remain together so that multiple delivery channels can use it without needing to first put those pieces back together.
Think about writing an article or essay. An article’s meaning and usefulness depends upon its parts being kept together. Would one of the headings or paragraphs be meaningful on their own without the context of the full article? On our project, our familiar design-system thinking often led us to want to create content models that would slice content into disparate chunks to fit the web-centric layout. This had a similar impact to an article that were to have been separated from its headline. Because we were slicing content into standalone pieces based on layout, content that belonged together became difficult to manage and nearly impossible for multiple delivery channels to understand.
To illustrate, let’s look at how connecting related content applies in a real-world scenario. The design team for our customer presented a complex layout for a software product page that included multiple tabs and sections. Our instincts were to follow suit with the content model. Shouldn’t we make it as easy and as flexible as possible to add any number of tabs in the future?
Because our design-system instincts were so familiar, it felt like we had needed a content type called “tab section” so that multiple tab sections could be added to a page. Each tab section would display various types of content. One tab might provide the software’s overview or its specifications. Another tab might provide a list of resources.
Our inclination to break down the content model into “tab section” pieces would have led to an unnecessarily complex model and a cumbersome editing experience, and it would have also created content that couldn’t have been understood by additional delivery channels. For example, how would another system have been able to tell which “tab section” referred to a product’s specifications or its resource list—would that other system have to have resorted to counting tab sections and content blocks? This would have prevented the tabs from ever being reordered, and it would have required adding logic in every other delivery channel to interpret the design system’s layout. Furthermore, if the customer were to have no longer wanted to display this content in a tab layout, it would have been tedious to migrate to a new content model to reflect the new page redesign.
A content model based on design components is unnecessarily complex, and it’s unintelligible to systems.
We had a breakthrough when we discovered that our customer had a specific purpose in mind for each tab: it would reveal specific information such as the software product’s overview, specifications, related resources, and pricing. Once implementation began, our inclination to focus on what’s visual and familiar had obscured the intent of the designs. With a little digging, it didn’t take long to realize that the concept of tabs wasn’t relevant to the content model. The meaning of the content that they were planning to display in the tabs was what mattered.
In fact, the customer could have decided to display this content in a different way—without tabs—somewhere else. This realization prompted us to define content types for the software product based on the meaningful attributes that the customer had wanted to render on the web. There were obvious semantic attributes like name and description as well as rich attributes like screenshots, software requirements, and feature lists. The software’s product information stayed together because it wasn’t sliced across separate components like “tab sections” that were derived from the content’s presentation. Any delivery channel—including future ones—could understand and present this content.
A good content model connects content that belongs together so it can be easily managed and reused.
Conclusion
In this omnichannel marketing project, we discovered that the best way to keep our content model on track was to ensure that it was semantic (with type and attribute names that reflected the meaning of the content) and that it kept content together that belonged together (instead of fragmenting it). These two concepts curtailed our temptation to shape the content model based on the design. So if you’re working on a content model to support an omnichannel content strategy—or even if you just want to make sure that Google and other interfaces understand your content—remember:
A design system isn’t a content model. Team members may be tempted to conflate them and to make your content model mirror your design system, so you should protect the semantic value and contextual structure of the content strategy during the entire implementation process. This will let every delivery channel consume the content without needing a magic decoder ring.
If your team is struggling to make this transition, you can still reap some of the benefits by using Schema.org–based structured data in your website. Even if additional delivery channels aren’t on the immediate horizon, the benefit to search engine optimization is a compelling reason on its own.
Additionally, remind the team that decoupling the content model from the design will let them update the designs more easily because they won’t be held back by the cost of content migrations. They’ll be able to create new designs without the obstacle of compatibility between the design and the content, and they’ll be ready for the next big thing.
By rigorously advocating for these principles, you’ll help your team treat content the way that it deserves—as the most critical asset in your user experience and the best way to connect with your audience.
A Content Model Is Not a Design System published first on https://deskbysnafu.tumblr.com/
0 notes
Text
Should you be worried about your passwords getting hacked?

Most IT security specialists define passwords as "the keys to our Digital Home": that's a pretty good metaphore, especially considering that our "digital home" is getting bigger as the time passes (and the technology advances). In the latest few decades we learned how to protect our precious devices (computers and, most recently, mobile devices) to prevent unauthorized access to them and their data... But, with the advent of the Internet and Internet of Things, the house became an infinite amount of different rooms: from online banking to food delivery services, from cloud-based repositories to remotely accessible Virtual Private Networks, we were literaly stormed by those "keys".
At the same time, since technology runs faster than our ability to assimilate it, most internet users - as well as business companies - still use passwords in a totally insecure way today: to continue with our initial metaphore, nobody would leave the key on the door, or feel comfortable using the same key to open multiple doors, or use a weak lock & key combination, right? However, when using passwords, most of us often do just that.
In the initial part of this post we'll try to summarize the most common mistakes that people do in choosing a password; then we'll briefly review the most common ways used by hackers to stole passwords; last but not least, we'll share some suggestions and best practices to secure our passwords and improve our account's security.
Common Password Mistakes
The typical password mistakes can be split into three main categories: choosing a weak password, using the same password among different web sites, and insecurely storing passwords. In the following sections we'll deal with each one of them.
Choosing a weak Password
A weak password, as the name implies, is a password too easy to guess or to discover using automated hacking techniques (brute-force, rainbow tables, and so on). Those who thinks that this is issue is a thing of the past because nowadays the majority of IT users have been educated enough to avoid choosing trivial passwords should check the SplashData's Most Used (and Worst) Password of 2017 infographics, which could easily change their mind.
Here a list of the top 10:
- 123456 (proudly keeping the first place since 2013)
- password
- 12345678
- qwerty
- 12345
- 123456789
- letmein
- 1234567
- football
- iloveyou
Luckily enough, such situation has been mitigated by enforcing a password security policy that is already adopted by most websites - and that is mandatory for all online services that deal with money or personal data, at least in most countries. Such policies not only require a minimum length and the presence of different character types (uppercase and lowercase letters, numbers, special characters) to make them harder to guess, but also force the users to periodically change them (often every 90 or 180 days). However, choosing a weak password is still critical for those devices where such policies are not enforced yet - such as most IoT devices.
Using the same Password
In addition to using passwords objectively too weak, users (and company officers) often also make the mistake of using the same password for different web sites or services. The so-called "password reuse" is probably the most serious mistake we can make nowadays: if a hacker manages to hack into a website's servers (this is happened for Yahoo, LinkedIn, Sony, and countless "minor" websites) and steal the users passwords, it will definitely try to use those retrieved passwords to gain access to other services. The only thing we can do to stop such common hacking practice is to ensure that each and every account that we have has its own password.
A great example of such bad practice was given during the LinkedIn data breach (2012), through which Mark Zuckerberg's LinkedIn, Twitter and Pinterest accounts were all hacked because he used the same password for all of them.
Such verification process can be automated using dedicated tools, such as Shard - a open-source command line tool that was developed to allow users to test whether a password they use for a site is used to access some of the more popular services, including Facebook. LinkedIn, Reddit, Twitter or Instagram.
Insecurely storing Passwords
The need to use strong passwords and a different password for each website or service inevitably brings another big requirement: the need to have a "secure" mechanism for storing these passwords, since human memory won't definitely be able to keep up. And this is where the most serious security problems often occur, not only for home users yet also for most companies. Who among us has never seen those dreadful MS Excel files (or text files!) containing a huge list of passwords?
And the worst thing is that those unsecure repositories are often shared among different users (family members, co-workers, and so on), meaning that they aren't protected even with the basic user authentication mechanism provided by the OS.
How passwords are hacked
The techniques used by hackers for discovering our passwords are more than one, sometimes really trivial: as we can easily see by looking at the list below, most of them leverage or exploit the bad practices that we've talked about early on.
- Social Engineering: e.g. Phishing, Password Sniffing. In practice, it is we who allow ourselves to be deceived by social engineering techniques and give passwords to those who ask for them through for example messages, emails, fake sites that disguise a well-known site.
- Guessing passwords: Using personal information such as name, date of birth or pet names. When this happens, sometimes the "hacker" happens to be kind of close to the "victim": a friend, neighbor, co-worker or someone that knows enough info to perform such guesses. However, thanks to the modern approach to social networks, everyone might easily know a lot of stuff about anyone else.
- Brute Force Attack: Automatically testing a large number of passwords until the right one is found. There are special programs to do this (a widely used one, John the Ripper, is open source, meaning that anyone can use it). Brute-force attacks are quite expensive to pull off, which requires time and computing power, but can easily achieve the result if the password is weak enough.
- Intercepting a password, for example while it is being transmitted over a network. The bad habit of communicating passwords via email is frequent: there are even sites that, as soon as we register, send us a polite welcome message containing username and password displayed "in clear". Too bad that email is not a safe tool.
- Shoulder surfing: a social engineering variant. It basically means "observing someone from behind" (i.e. "shoulder") while typing the password.
- Using a KeyLogger. Keyloggers are malware programs that record everything typed on the keyboard, then transmit this data to the hacker who installed the keylogger. There are also hardware-based keyloggers that require direct access to the victim's computer.
- Passwords stored in an insecure way, like handwritten on a piece of paper, or saved on a word file (see above).
- By compromising a database containing a large number of user passwords, then using this information to attack other systems where users have reused the same passwords ("credential stuffing").
How to secure our Password
Securing our passwords in order to avoid most - if not all - of the hacking attemps listed above is not impossible and is a goal that can be achieved by anyone. In a nushell, all we need to do is to apply two best practices:
- Write strong and unique Password
- Securely store your Passwords
Both of them are equally important and must be followed for each and every password, without exceptions.
How to write a strong Password
A strong password is characterized by the following elements: length and character types used.
- Regarding the length, it is strongly recommended to use at least 12 characters.
- As for the character types, just let the math guide you: we have 10 numeric types (0-9), 52 letter types (26 lowercase + 26 uppercase), and more or less 33 special character types easy to type because they're directly accessible from a typical keyboard (such as #, &, %, ?, ^, and so on). To summarize all that, in total we have 95 character types available: with that in mind, we can say that a good password should have at least one character coming from each one of these types, because by increasing the types of characters, the number of possible combinations grows exponentially, thus making harder (and time-consuming) to "brute-force" the resulting password.
How to store your Passwords
As we aready said early on, using a different password for each website or service means that we can't rely to our memory to remember them all: at the same time, using insecure data stores such as MS Excel files or text files is definitely not an option.
The best way to tackle (and fix) this problem is to use a Password Manager tool: a dedicated software that acts as a vault where you can securely store all your passwords, as well as your usernames and/or credential info, with the big advantage of having them in a single place. This basically means that you'll only need to remember the password required to access it, which is often very strong and can be further protected by other authentication factors (fingerprint, SMS, OTP, mobile tokens, and so on).
The most advanced Password Managers also provide a good level of integration with the Operating System and browsers, meaning that they can even “automatically” (yet securely) fill in your credentials whenever you log in to a site (or an app) using your desktop or mobile device.
IMPORTANT: Password Manager apps shouldn't be confused in any way with the "password storage" features offered by most modern browsers, such as Google Chrome, Mozilla Firefox, and MS Edge, that prompts you to store your credentials and fill out the forms for you, unless they are part of a bigger product that grants the fundamental features that a good Password Manager needs to have: centralized and distribuited repository, access from multiple devices, data encryption of the whole vault, 2-factor authentication support, and so on.
Conclusion
That's it, at least for now: we hope that this post will help most users and companies to increase their online security by securely choosing and storing their password.
Read the full article
1 note
·
View note
Text
Eight Signs That You Need Better Resource Scheduling
Please Note: This article appeared in saviom and has been published here with permission.
Can you imagine meeting project deadlines without a suitable resource schedule?
Certainly not. Projects are constrained by specific budgets and timelines, and their success relies on the intelligent use of resources. Thus, resource scheduling plays a vital role in successful project delivery.
As per Mckinsey, “83% of business leaders think resource scheduling is the top lever for spurring project growth.”
However, many companies still rely on silos of spreadsheets or homegrown half-baked tools, which are time-consuming and cumbersome.
Lack of enterprise-wide visibility, errors during data reconciliation, incapable of capturing real-time data, etc., are some of the limitations of using spreadsheets for resource schedule. Improper resource allocation hampers profitability, resource utilization, and productivity. Moreover, it also affects client satisfaction and negates project success.
That’s why businesses need to reconsider their resource management strategy and invest in a robust solution to overcome resource scheduling challenges.
This blog discusses the signs of poor resource scheduling and how modern resource management software can course-correct them.
1. Unable to leverage a shared services model
Suppose you have a resource-requirement with 50% availability for your project. You will raise the request to the resource manager for this requirement. The resource manager knows that there are resources in the pool with matching skill sets. But they could be working on other projects with varying capacities. In the absence of enterprise-wide visibility of resources bookings, the resource manager cannot identify the right person. He may land up assigning a resource with 100% capacity. Unless the same resource can be partially allocated to another project, it will affect his billable utilization.
Solution: A 360-degree visibility of the resources in the organization
Modern resource management solution provides 360-degree visibility of all resources across all departments. It consolidates all resource-related information on a centralized platform and keeps you informed of their allocations and availability. One can also manage complex scheduling effortlessly by leveraging cost-effective global resources if required. This avoids double bookings and maintains a single version of the truth across the enterprise.
2. Insufficient productivity levels causing a high attrition rate
As a project manager, you want to get the task done in the shortest time possible and deliver the best possible results. So you select a few critical team members you have known from the past and give them additional responsibilities beyond their capacity. You start moving them between tasks, trying to utilize them to their full content, and more.
As a result, these resources get overloaded while other team members are not fully utilized. It leads to employee burnouts for the critical resources leading to unplanned attrition.
So how do you maintain overall productive utilization of all the resources without overburdening them?
Solution: Ensure optimal utilization of all resources
Managers can gain foresight into resource utilization and distribute the workload evenly without over or under-allocating resources. Besides, keeping team members busy with work doesn’t mean they are productive. They could be spending a lot of time doing mundane BAU activities. Therefore, the forecasting capability of an intuitive resource management solution enables managers to mobilize team members from non-billable/low-priority work to a billable/high-priority one and improve profitability.
3. Skill shortages due to a lack of foresight into future demand
Let’s assume that you are working on a big project and a new initiative is coming up in three months. But you do not know how many resources are required or if they are available. As a result, when the start date approaches, you have no choice but to resort to last-minute hiring activities. It compromises the resource quality and affects the delivery.
Solution: Switch to data-driven demand forecasting and capacity planning
One of the critical functions of resource management is demand forecasting that allows managers to gain complete visibility of current and future project demands. It helps identify resource excesses and shortages ahead of time and take appropriate resourcing treatments to mitigate them. Retraining resources or hiring a permanent or contingent workforce creates an optimally balanced and skilled resource pool. It reduces wasteful hiring/firing cycles and future-proofing the workforce.
4. People are spending a lot of time attending meetings
Spending too much time in the meetings makes the resources less productive and increases time overruns.
As per a survey by Korn Ferry, “67% of workers say excessive meetings keep them from getting their best work done.”
When there are too many unnecessary meetings in a day, the employees can get frustrated. For example, let’s assume that in an 8-hour workday, you have scheduled four one-hour meetings. These meetings are to keep your team on the same page and also to monitor the progress. Each session is scheduled one hour after the other. Based on that, the resources will have four hours to attend meetings and four hours to focus on real work. Their actual working time will be significantly reduced, and delivery will be adversely affected.
Solution: Schedule meetings only when necessary
Before scheduling a meeting, one should consider the purpose of the meeting. What is the outcome that you expect at the end of the session? Moreover, most of the time, you may not invite too many people to the meeting. While collaboration is essential, not everyone needs to attend a meeting. Instead of having the whole team participate, only team leads can join, allowing others to focus and complete tasks on time.
Resource scheduling solution enables you to look at time-sheet data, and one can easily analyze if resources are spending too much time on mundane activities. The dashboard view will allow the management to verify that too much time is wasted in attending meetings. This can be course-corrected by providing the necessary direction to the project manager.
5. High employee turnover during the night shift
Night shift work requires people to work while most people are asleep. When it comes to night shift employees, it’s often harder to motivate them to stay. Working non-normal hours can be especially difficult for employees with families as they fail to strike the right work-life balance. Besides, the night shift disturbs the natural bio cycle of humans and takes a toll on their physical and mental health.
It would help if you kept in mind that the core of employee retention revolves around ensuring that your employees are happy at their job. While some people may enjoy working at night, the majority of employees do not. The person might have agreed to work on a night shift while accepting the offer, but it can force him to leave due to fatigue and constant sleep deprivation.
Solution: Induce rotating shifts for better flexibility
Workplace flexibility is more important than ever. Rotating work schedules can provide that flexibility for adjusting to the changing demands. With rotating shifts, employees can work the day shift for some weeks and then switch to working the night shift based on their needs. It helps keep the hours covered while still giving your employees regular time off.
Besides, when someone wants time off, you can make room for other critical tasks without interrupting workflow. You can even let your team swap shifts with others in their group. Moreover, rotating shifts help increase employee engagement as they can work at their preferred schedule. It also helps in training under-qualified members as everyone gets their share of working at peak hours.This kind of practice can be easily implemented using modern resource scheduling software.
6. Clients hint at getting the same services at a lower cost
“Our requirements have not changed in a few years, and your workforce understands our business well. Because of our internal cost pressure, now we want the same service at a lesser cost.”
This is a common phrase sales reps hear from clients during the annual renewal of contracts. Globalization has also made the market highly competitive. That’s why clients have more options, and they are demanding quality services at a cheaper cost.
As a project manager, you want to adhere to the client’s needs. But offering a discount cuts into your profit margin and may also compromise the quality of the project.
What can you do to ensure successful project delivery and also stick to the client’s cost restraints?
Solution: Allocate low-cost global resources without compromising quality
Visibility across the enterprise enables you to identify and allocate cost-effective local and global resources by skills. If local resources for a particular skill set are not available, a multi-location policy helps leverage global resources from low-cost locations to do the job. It helps in reducing project resource costs significantly without compromising the quality.
Also, sometimes it becomes tough to do succession planning for a critical multi-skilled resource. If the role of such an employee needs to be distributed to multiple resources, the cost can go up substantially. This is, however, possible by distributing work with multiple people from a low-cost location. This way, one can prevent a single point of failure if this critical resource leaves the organization.
7. Lack of collaboration between team members
Let’s suppose that you have to develop a website for a client. To deliver this project, you need the web development, content, designing, and digital marketing departments to be on the same page. But as the project progresses, you notice that none of the members are aware of the other departments’ work. Moreover, you also don’t have any real-time report of the progress. Can you imagine creating this website without properly collaborating with the respective teams? Certainly not.
Solution: Improve interdepartmental collaboration
A resource management solution helps develop standardized communication procedures. A collaboration platform streamlines effective communication across the enterprise. With it, you can check activity updates or participate in the discussion board in a breeze. It also enables you to make notes, pin messages, and so on. Moreover, alerts and notifications displayed on the discussion board ensure you don’t miss any critical updates. Thus, you can ensure that everyone is on the same page.
8. Your project team lacks motivation
You have everything set for the project. You have your resources in line and have planned everything out. As the work progresses, you notice that your team lacks motivation. The supposed completion task in a month is now taking 2-3 months to complete. You pull up ways to overcome these resource management challenges, but your staff isn’t as energized as during the initial stage. So, what can you do to increase their motivation?
Solution: Boost employee morale and employee engagement
As mentioned earlier, taking employee’s skills and interests into consideration while assigning them to projects improves task ownership and engagement. Managers can publish the resource requirements, and interested employees matching the criteria can apply.
Besides resource scheduling, giving employees continuous feedback lets them know that you value their work and want them to prosper. Also, creating team-building activities such as games and friendly competition relax your team members.
9. Conclusion- Resource Scheduling Tips
Resource scheduling enhances business profitability and sustainability by unleashing the maximum potential of resources. Here are some tips for efficient resource scheduling:
Stay updated with resource availability, capacity, and utilization before scheduling more projects.
Analyze the capacity vs. demand gap in advance and implement appropriate resourcing measures to bridge the gap.
Use scheduling tactics to filter and search for the right resource for the right job.
Foresee future project demands to ensure systematic management of pipeline projects.
Conduct upskilling and training programs for resources to allow them to take up more opportunities down the line.
Schedule resources for different functional projects that enable and empower them to explore new areas and grow professionally.
Compare actual vs. forecast utilization and note the deviation to improve resource scheduling for future projects.
10. Saviom Solution
SAVIOM has over 20 years of experience helping multinational clients manage their resources efficiently and effectively. With over 20 years of experience, this Australian-based MNC has a global presence across 50 countries and has helped 100+ clients meet their specific business goals. Saviom also provides tools for project portfolio management, professional service automation, and workforce planning software. So, SAVIOM can help your business to establish an efficient system geared towards your specific business challenges.
0 notes
Text
Createrria: A Retrospective
When I was young I used to play a game called Createrria, a game where you could create your own games and share them with the world. It was an amazing game. It's gone now!
Why, you ask? Read on this excessively long blog post that I made. 😉
Sources are in the bottom below. The game has also been pulled from both the Google Play Store and the App Store, so I will have to rely on other people's images and YT screengrabs.
Createrria was first published by its developer, Incuvo, on June 6, 2013. The game would've been 8 years old by now. It was first available solely on iOS devices (1), and eventually the devs ported it to Android. As far as I know, there was no Windows or macOS/OS X version.

The game had a unique premise - using the game's built in tools and objects you could create a "game" to share with other people. It was basically a Fancade for babies! It had 2 main modes of gaming - the normal gameplay mode where you could play your or other's games, and the creation mode where you could build games using the built-in editor.

Screengrab from Gustavo Diaz's video "How to Make A Good Game In Createrria"
In the creation mode you could build games by sculpting land (which Gustavo is doing in the pic above), adding spikes, enemies, power-ups, etc. The game also had pixel blocks which you could use to make pixel art or decoration.
Now, let's talk about the character. Createrria allowed you to express yourself with a character. There were many different characters in-game, and there was even one based off of Minecraft's Steve. That character was the face of your profile, and you could also control those characters in the games you play. There weren't many though. The account createrria_admin had a special character that s/he only could use.
In the games themselves, there were many different types of game modes whose names I forgot, and I will run through them all:
1. Get to the finish line by using left-right and jump buttons to control your character
2. Collect all gems (only in games without a finish line)
3. Kill all monsters (by jumping on 'em. Also only in games without a finish line)
4. Angry Birds (not real name. Uses slingshot mechanic of the game. Self explanatory.)
5. Flappy Bird (not real name. Uses jumping bird mechanic. Also self-explanatory.
6. Hamsterball (not real name. Uses slingshot mechanic, but instead of firing stuff at monsters, you are locked in a ball and you use the slingshot mechanic to move.)
7. Run Away (think 2D Temple Run.)
Some game modes can be combined to make fusion levels. Some people even made new mechanics out of the other ones, like the Flappy Bird mechanic. People found out that if you use the underside of a trampoline block to make a track, you could make roller-coasters! Many people also made storyline-based games.
Let's talk about some weird mechanics of the game. Go back to the image above, and look at the top left corner. Next to the bright yellow button, there was an energy meter. Basically, when editing your games, every action you do will diminish the energy meter. Once it runs out you will no longer be able to edit, and you will need to recharge by either waiting 1/4 an hour, watching an ad, or spending in-game currency. This mechanic was criticized by the community.
Another weird mechanic is the magic crafting mechanic. Introduced around 2017, this mechanic used "magic dust" to make the items in the game. You could transform your dust into an item, and vice-versa. This mechanic was short-lived.
2017 came the arrival of a refresh to the game. The game's artstyle was revamped, and it was called Createrria 2. This update is one I don't like since it added-dun dun dun...Loot boxes! Instead of buying items the normal way by using your in-game currency, you had to buy loot boxes instead and hope that it gives you something new. Because, oh man, their RNG was astoundingly bad. You would often get the same item twice or thrice in a row.
A short video demonstrating the (ew) loot boxes. These proved to be lucrative as the devs kept them in-game until the game was killed off. Source is from Incuvo themselves.
Now, let's talk about the community of this game. The community here was actually pretty nice and the community made some pretty great games.
The game also had some rudimentary social media features like liking someone else's game, and commenting on it. Obviously there weren't any Stories features in the game. I also think this game doesn't have a Discord server, as that chatroom software launched around the time Createrria 2 was launched, and besides, most of Createrria's playerbase was under 13, so there wasn't much point in it.
Now, where is the game now, you might ask? Well, if all that haloney-baloney I said made you wanna play the game, bad news - the game is completely gone. Servers were shut down around 2020, and the game was pulled from both the App Store and Google Play Store. I assume this was because the game was losing relevance and playerbase. Plus, Incuvo is working on other games too. Heck, they're now making VR games!
What's now left of the game? Well...not much. The game heavily relies on their servers which means that the game is practically a shadow of its former self. You could still make games, but you could no longer play other people's games. And...well, since it's pulled from stores, it's hard to find it online. So...yeah. It's a dead game. But even then this game holds so many, MANY memories. Playing with other people and socializing with them. Those were the good times. And if you do wanna create your own games - try out Fancade. It's twice as complicated as Createrria, but much, MUCH better.
SOURCES
1 -
Createrria | Createrria Wiki | Fandom
https://createrria.fandom.com › wiki › Createrria
0 notes