#felony contempt of business model
Text
How lock-in hurts design

Berliners: Otherland has added a second date (Jan 28) for my book-talk after the first one sold out - book now!

If you've ever read about design, you've probably encountered the idea of "paving the desire path." A "desire path" is an erosion path created by people departing from the official walkway and taking their own route. The story goes that smart campus planners don't fight the desire paths laid down by students; they pave them, formalizing the route that their constituents have voted for with their feet.
Desire paths aren't always great (Wikipedia notes that "desire paths sometimes cut through sensitive habitats and exclusion zones, threatening wildlife and park security"), but in the context of design, a desire path is a way that users communicate with designers, creating a feedback loop between those two groups. The designers make a product, the users use it in ways that surprise the designer, and the designer integrates all that into a new revision of the product.
This method is widely heralded as a means of "co-innovating" between users and companies. Designers who practice the method are lauded for their humility, their willingness to learn from their users. Tech history is strewn with examples of successful paved desire-paths.
Take John Deere. While today the company is notorious for its war on its customers (via its opposition to right to repair), Deere was once a leader in co-innovation, dispatching roving field engineers to visit farms and learn how farmers had modified their tractors. The best of these modifications would then be worked into the next round of tractor designs, in a virtuous cycle:
https://securityledger.com/2019/03/opinion-my-grandfathers-john-deere-would-support-our-right-to-repair/
But this pattern is even more pronounced in the digital world, because it's much easier to update a digital service than it is to update all the tractors in the field, especially if that service is cloud-based, meaning you can modify the back-end everyone is instantly updated. The most celebrated example of this co-creation is Twitter, whose users created a host of its core features.
Retweets, for example, were a user creation. Users who saw something they liked on the service would type "RT" and paste the text and the link into a new tweet composition window. Same for quote-tweets: users copied the URL for a tweet and pasted it in below their own commentary. Twitter designers observed this user innovation and formalized it, turning it into part of Twitter's core feature-set.
Companies are obsessed with discovering digital desire paths. They pay fortunes for analytics software to produce maps of how their users interact with their services, run focus groups, even embed sneaky screen-recording software into their web-pages:
https://www.wired.com/story/the-dark-side-of-replay-sessions-that-record-your-every-move-online/
This relentless surveillance of users is pursued in the name of making things better for them: let us spy on you and we'll figure out where your pain-points and friction are coming from, and remove those. We all win!
But this impulse is a world apart from the humility and respect implied by co-innovation. The constant, nonconsensual observation of users has more to do with controlling users than learning from them.
That is, after all, the ethos of modern technology: the more control a company can exert over its users ,the more value it can transfer from those users to its shareholders. That's the key to enshittification, the ubiquitous platform decay that has degraded virtually all the technology we use, making it worse every day:
https://pluralistic.net/2023/02/19/twiddler/
When you are seeking to control users, the desire paths they create are all too frequently a means to wrestling control back from you. Take advertising: every time a service makes its ads more obnoxious and invasive, it creates an incentive for its users to search for "how do I install an ad-blocker":
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
More than half of all web-users have installed ad-blockers. It's the largest consumer boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
But zero app users have installed ad-blockers, because reverse-engineering an app requires that you bypass its encryption, triggering liability under Section 1201 of the Digital Millennium Copyright Act. This law provides for a $500,000 fine and a 5-year prison sentence for "circumvention" of access controls:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
Beyond that, modifying an app creates liability under copyright, trademark, patent, trade secrets, noncompete, nondisclosure and so on. It's what Jay Freeman calls "felony contempt of business model":
https://locusmag.com/2020/09/cory-doctorow-ip/
This is why services are so horny to drive you to install their app rather using their websites: they are trying to get you to do something that, given your druthers, you would prefer not to do. They want to force you to exit through the gift shop, you want to carve a desire path straight to the parking lot. Apps let them mobilize the law to literally criminalize those desire paths.
An app is just a web-page wrapped in enough IP to make it a felony to block ads in it (or do anything else that wrestles value back from a company). Apps are web-pages where everything not forbidden is mandatory.
Seen in this light, an app is a way to wage war on desire paths, to abandon the cooperative model for co-innovation in favor of the adversarial model of user control and extraction.
Corporate apologists like to claim that the proliferation of apps proves that users like them. Neoliberal economists love the idea that business as usual represents a "revealed preference." This is an intellectually unserious tautology: "you do this, so you must like it":
https://boingboing.net/2024/01/22/hp-ceo-says-customers-are-a-bad-investment-unless-they-can-be-made-to-buy-companys-drm-ink-cartridges.html
Calling an action where no alternatives are permissible a "preference" or a "choice" is a cheap trick – especially when considered against the "preferences" that reveal themselves when a real choice is possible. Take commercial surveillance: when Apple gave Ios users a choice about being spied on – a one-click opt of of app-based surveillance – 96% of users choice no spying:
https://arstechnica.com/gadgets/2021/05/96-of-us-users-opt-out-of-app-tracking-in-ios-14-5-analytics-find/
But then Apple started spying on those very same users that had opted out of spying by Facebook and other Apple competitors:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Neoclassical economists aren't just obsessed with revealed preferences – they also love to bandy about the idea of "moral hazard": economic arrangements that tempt people to be dishonest. This is typically applied to the public ("consumers" in the contemptuous parlance of econospeak). But apps are pure moral hazard – for corporations. The ability to prohibit desire paths – and literally imprison rivals who help your users thwart those prohibitions – is too tempting for companies to resist.
The fact that the majority of web users block ads reveals a strong preference for not being spied on ("users just want relevant ads" is such an obvious lie that doesn't merit any serious discussion):
https://www.iccl.ie/news/82-of-the-irish-public-wants-big-techs-toxic-algorithms-switched-off/
Giant companies attained their scale by learning from their users, not by thwarting them. The person using technology always knows something about what they need to do and how they want to do it that the designers can never anticipate. This is especially true of people who are unlike those designers – people who live on the other side of the world, or the other side of the economic divide, or whose bodies don't work the way that the designers' bodies do:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
Apps – and other technologies that are locked down so their users can be locked in – are the height of technological arrogance. They embody a belief that users are to be told, not heard. If a user wants to do something that the designer didn't anticipate, that's the user's fault:
https://www.wired.com/2010/06/iphone-4-holding-it-wrong/
Corporate enthusiasm for prohibiting you from reconfiguring the tools you use to suit your needs is a declaration of the end of history. "Sure," John Deere execs say, "we once learned from farmers by observing how they modified their tractors. But today's farmers are so much stupider and we are so much smarter that we have nothing to learn from them anymore."
Spying on your users to control them is a poor substitute asking your users their permission to learn from them. Without technological self-determination, preferences can't be revealed. Without the right to seize the means of computation, the desire paths never emerge, leaving designers in the dark about what users really want.
Our policymakers swear loyalty to "innovation" but when corporations ask for the right to decide who can innovate and how, they fall all over themselves to create laws that let companies punish users for the crime of contempt of business-model.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/24/everything-not-mandatory/#is-prohibited

Image:
Belem (modified)
https://commons.wikimedia.org/wiki/File:Desire_path_%2819811581366%29.jpg
CC BY 2.0
https://creativecommons.org/licenses/by/2.0/deed.en
#pluralistic#desire paths#design#drm#everything not mandatory is prohibited#apps#ip#innovation#user innovation#technological self-determination#john deere#twitter#felony contempt of business model
3K notes
·
View notes
Text
Something I feel like people aren't getting about the whole Reddit API situation is that on some level it's not really about the API or 3rd party apps themselves, its that this situation is just another indicator that the like, ethos, of the internet of the 2010s is dying. In the early social media days there was this idea that platforms weren't the websites but the servers and the data, and they welcomed people to use the same tools they used to build the websites to make their own tools. Like the idea was that it would be mutually beneficial to let more technical users interact with the platforms in unapproved ways because it would drive people to the platforms and provide more value for users, and that's how you get things like bots and 3rd party clients and people doing statistics on subreddit membership and twitter linguistic analyses or whatever.
Reddit didn't even have an app for the longest time! Like people didn't go "wow this app sucks I'm going to make my own" the 3rd party apps were there first, because from Reddit's old perspective, if iPhone users wanted to interact with their service in a more platform specific way it's within their rights to create a client to do that. That's honestly probably why they haven't implemented mod tools or accessibility features, why spent the man-hours when someone else will do it for you?
But of course if people are interacting with your service via the API directly you can't serve them ads, and now it's even worse with the advent of GPT spam posts. So it was pretty inevitable that Reddit was going to start restricting the ways you can interact with it. And now that the big social media sites have destroyed all the competition they just do whatever they want, and being idealistic about how an open internet ought to work doesn't benefit them at all.
It's just sad to see API access start to be restricted across the internet. It's super annoying to see Steve Huffman act like the API wasn't always touted as like, a social good, when he's been there the whole time and made it like that in the first place. And I see a lot of people being like "oh boo-hoo you can't use 3rd party apps anymore waa" and I'm not sure that like trying to explain this stuff from a technical perspective would make them realize why people care, because it's more about how people thought and felt about the internet over a decade ago.
#reddit#rant#computer#also this is maybe conspiratorial but#I have a lingering dread that as stuff becomes more locked down people who know how to interact with stuff at a technical level#are going to be viewed as suspicious#“the only reason you'd want to jailbreak your iphone is if youre a pirate!” etc.#cory doctorow felony contempt of business model
9 notes
·
View notes
Text
Fifty per cent of web users are running ad blockers. Zero per cent of app users are running ad blockers, because adding a blocker to an app requires that you first remove its encryption, and that’s a felony. (Jay Freeman, the American businessman and engineer, calls this “felony contempt of business-model”.)
So when someone in a boardroom says, “Let’s make our ads 20 per cent more obnoxious and get a 2 per cent revenue increase,” no one objects that this might prompt users to google, “How do I block ads?” After all, the answer is, you can’t. Indeed, it’s more likely that someone in that boardroom will say, “Let’s make our ads 100 per cent more obnoxious and get a 10 per cent revenue increase.” (This is why every company wants you to install an app instead of using its website.)
There’s no reason that gig workers who are facing algorithmic wage discrimination couldn’t install a counter-app that co-ordinated among all the Uber drivers to reject all jobs unless they reach a certain pay threshold. No reason except felony contempt of business model, the threat that the toolsmiths who built that counter-app would go broke or land in prison, for violating DMCA 1201, the Computer Fraud and Abuse Act, trademark, copyright, patent, contract, trade secrecy, nondisclosure and noncompete or, in other words, “IP law”.
IP isn’t just short for intellectual property. It’s a euphemism for “a law that lets me reach beyond the walls of my company and control the conduct of my critics, competitors and customers”. And “app” is just a euphemism for “a web page wrapped in enough IP to make it a felony to mod it, to protect the labour, consumer and privacy rights of its user”.
11K notes
·
View notes
Text
Great article!
Excerpt:
Think of our ad blockers again. Fifty per cent of web users are running ad blockers. Zero per cent of app users are running ad blockers, because adding a blocker to an app requires that you first remove its encryption, and that’s a felony. (Jay Freeman, the American businessman and engineer, calls this “felony contempt of business-model”.)
So when someone in a boardroom says, “Let’s make our ads 20 per cent more obnoxious and get a 2 per cent revenue increase,” no one objects that this might prompt users to google, “How do I block ads?” After all, the answer is, you can’t. Indeed, it’s more likely that someone in that boardroom will say, “Let’s make our ads 100 per cent more obnoxious and get a 10 per cent revenue increase.” (This is why every company wants you to install an app instead of using its website.)
There's no reason that gig workers who are facing algorithmic wage discrimination couldn’t install a counter-app that co-ordinated among all the Uber drivers to reject all jobs unless they reach a certain pay threshold. No reason except felony contempt of business model, the threat that the toolsmiths who built that counter-app would go broke or land in prison, for violating DMCA 1201, the Computer Fraud and Abuse Act, trademark, copyright, patent, contract, trade secrecy, nondisclosure and noncompete or, in other words, “IP law”.
IP isn’t just short for intellectual property. It’s a euphemism for “a law that lets me reach beyond the walls of my company and control the conduct of my critics, competitors and customers”. And “app” is just a euphemism for “a web page wrapped in enough IP to make it a felony to mod it, to protect the labour, consumer and privacy rights of its user”.
3 notes
·
View notes
Text
The author of “Chokepoint Capitalism” posted an excellent thread today. Ties together several posts I’ve been seeing lately about how and why we arrived at a place where we’re dreading new tech instead of embracing it.
Lots of citations, lots of good points. Fantastic lunch read.
Obligatory eye-catching screencaps to entice you:

Blog post here:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
As you might guess from the screencaps, he also threaded the whole thing on twitter.
13 notes
·
View notes
Text
What happened to the cycle of renewal? Where are the regular, controlled burns?
Like the California settlers who subjugated the First Nations people and declared war on good fire, the finance sector conquered the tech sector.
It started in the 1980s, the era of personal computers — and Reaganomics. A new economic and legal orthodoxy took hold, one that celebrated monopolies as “efficient,” and counseled governments to nurture and protect corporations as they grew both too big to fail, and too big to jail.
For 40 years, we’ve been steadily reducing antitrust enforcement. That means a company like Google can create a single great product (a search engine) and use investors’ cash to buy a mobile stack, a video stack, an ad stack, a server-management stack, a collaboration stack, a maps and navigation stack — all while repeatedly failing to succeed with any of its in-house products.
It’s hard to appreciate just how many companies tech giants buy. Apple buys other companies more often than you buy groceries.
These giants buy out their rivals specifically to make sure you can’t leave their walled gardens. As Mark Zuckerberg says, “It is better to buy than to compete,” (which is why Zuckerberg bought Instagram, telling his CFO that it was imperative that they do the deal because Facebook users preferred Insta to FB, and were defecting in droves).
As these companies “merge to monopoly,” they are able to capture their regulators, ensuring that the law doesn’t interfere with their plans for literal world domination.
When a sector consists of just a handful of companies, it becomes cozy enough to agree on — and win — its lobbying priorities. That’s why America doesn’t have a federal privacy law. It’s why employees can be misclassified as “gig worker” contractors and denied basic labor protections.
It’s why companies can literally lock you out of your home — and your digital life — by terminating your access to your phone, your cloud, your apps, your thermostat, your door-locks, your family photos, and your tax records, with no appeal — not even the right to sue.
But regulatory capture isn’t merely about ensuring that tech companies can do whatever they want to you. Tech companies are even more concerned with criminalizing the things you want to do to them.
Frank Wilhoit described conservativism as “exactly one proposition”:
There must be in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect.
This is likewise the project of corporatism. Tech platforms are urgently committed to ensuring that they can do anything they want on their platforms — and they’re even more dedicated to the proposition that you must not do anything they don’t want on their platforms.
They can lock you in. You can’t unlock yourself. Facebook attained network-effects growth by giving its users bots that logged into Myspace on their behalf, scraped the contents of their inboxes for the messages from the friends they left behind, and plunked them in their Facebook inboxes.
Facebook then sued a company that did the same thing to Facebook, who wanted to make it as easy for Facebook users to leave Facebook as it had been to get started there.
Apple reverse-engineered Microsoft’s crown jewels — the Office file-formats that kept users locked to its operating systems — so it could clone them and let users change OSes.
Try to do that today — say, to make a runtime so you can use your iOS apps and media on an Android device or a non-Apple desktop — and Apple will reduce you to radioactive rubble.
Big Tech has a million knobs on the back-end that they can endlessly twiddle to keep you locked in — and, just as importantly, they have convinced governments to ban any kind of twiddling back.
This is “felony contempt of business model.”
Governments hold back from passing and enforcing laws that limit the tech giants in the name of nurturing their “efficiency.”
But when states act to prevent new companies — or users, or co-ops, or nonprofits — from making it easier to leave the platforms, they do so in the name of protecting us.
Rather than passing a privacy law that would let them punish Meta, Apple, Google, Oracle, Microsoft and other spying companies, they ban scraping and reverse-engineering because someone might violate the privacy of the users of those platforms.
But a privacy law would control both scrapers and silos, banning tech giants from spying on their users, and banning startups and upstarts from spying on those users, too.
Rather than breaking up ad-tech, banning surveillance ads, and opening up app stores, which would make tech platforms stop stealing money from media companies through ad-fraud, price-gouging and deceptive practices, governments introduce laws requiring tech companies to share (some of) their ill-gotten profits with a few news companies.
This makes the news companies partners with the tech giants, rather than adversaries holding them to account, and makes the news into cheerleaders for massive tech profits, so long as they get their share. Rather than making it easier for the news to declare independence from Big Tech, we are fusing them forever.
We could make it easy for users to leave a tech platform where they are subject to abuse and harassment — but instead, governments pursue policies that require platforms to surveil and control their users in the name of protecting them from each other.
We could make it easy for users to leave a tech platform where their voices are algorithmically silenced, but instead we get laws requiring platforms to somehow “balance” different points of view.
The platforms aren’t merely combustible, they’re always on fire. Once you trap hundreds of millions — or billions — of people inside a walled fortress, where warlords who preside over have unlimited power over their captives, and those captives the are denied any right to liberate themselves, enshittification will surely and inevitably follow.
Laws that block us seizing the means of computation and moving away from Big Tech are like the heroic measures that governments undertake to keep people safe in the smouldering wildland-urban interface.
These measures prop up the lie that we can perfect the tech companies, so they will be suited to eternal rule.
Rather than building more fire debt, we should be making it easy for people to relocate away from the danger so we can have that long-overdue, “good fire” to burn away the rotten giants that have blotted out the sun.
What would that look like?
Well, this week’s news was all about Threads, Meta’s awful Twitter replacement devoted to “brand-safe vaporposting,” where the news and controversy are not welcome, and the experience is “like watching a Powerpoint from the Brand Research team where they tell you that Pop Tarts is crushing it on social.”
Threads may be a vacuous “Twitter alternative you would order from Brookstone,” but it commanded a lot of news, because it experienced massive growth in just hours. “Two million signups in the first two hours” and “30 million signups in the first morning.”
That growth was network-effects driven. Specifically, Meta made it possible for you to automatically carry over your list of followed Instagram accounts to Threads.
Meta was able to do this because it owns both Threads and Instagram. But Meta does not own the list of people you trust and enjoy enough to follow.
That’s yours.
Your relationships belong to you. You should be able to bring them from one service to another.
Take Mastodon. One of the most common complaints about Mastodon is that it’s hard to know whom to follow there. But as a technical matter, it’s easy: you should just follow the people you used to follow on Twitter —either because they’re on Mastodon, too, or because there’s a way to use Mastodon to read their Twitter posts.
Indeed, this is already built into Mastodon. With one click, you can export the list of everyone you follow, and everyone who follows you. Then you can switch Mastodon servers, upload that file, and automatically re-establish all those relationships.
That means that if the person who runs your server decides to shut it down, or if the server ends up being run by a maniac who hates you and delights in your torment, you don’t have to petition a public prosecutor or an elected lawmaker or a regulator to make them behave better.
You can just leave.
Meta claims that Threads will someday join the “Fediverse” (the collection of apps built on top of ActivityPub, the standard that powers Mastodon).
Rather than passing laws requiring Threads to prioritize news content, or to limit the kinds of ads the platform accepts, we could order it to turn on this Fediverse gateway and operate it such that any Threads user can leave, join any other Fediverse server, and continue to see posts from the people they follow, and who will also continue to see their posts.
youtube
Rather than devoting all our energy to keep Meta’s empire of oily rags from burning, we could devote ourselves to evacuating the burn zone.
This is the thing the platforms fear the most. They know that network effects gave them explosive growth, and they know that tech’s low switching costs will enable implosive contraction.
The thing is, network effects are a double-edged sword. People join a service to be with the people they care about. But when the people they care about start to leave, everyone rushes for the exits. Here’s danah boyd, describing the last days of Myspace:
If a central node in a network disappeared and went somewhere else (like from MySpace to Facebook), that person could pull some portion of their connections with them to a new site. However, if the accounts on the site that drew emotional intensity stopped doing so, people stopped engaging as much. Watching Friendster come undone, I started to think that the fading of emotionally sticky nodes was even more problematic than the disappearance of segments of the graph.
With MySpace, I was trying to identify the point where I thought the site was going to unravel. When I started seeing the disappearance of emotionally sticky nodes, I reached out to members of the MySpace team to share my concerns and they told me that their numbers looked fine. Active uniques were high, the amount of time people spent on the site was continuing to grow, and new accounts were being created at a rate faster than accounts were being closed. I shook my head; I didn’t think that was enough. A few months later, the site started to unravel.
Tech bosses know the only thing protecting them from sudden platform collapse syndrome are the laws that have been passed to stave off the inevitable fire.
They know that platforms implode “slowly, then all at once.”
They know that if we weren’t holding each other hostage, we’d all leave in a heartbeat.
But anything that can’t go on forever will eventually stop. Suppressing good fire doesn’t mean “no fires,” it means wildfires. It’s time to declare fire debt bankruptcy. It’s time to admit we can’t make these combustible, tinder-heavy forests safe.
It’s time to start moving people out of the danger zone.
It’s time to let the platforms burn.
3 notes
·
View notes
Text
Trump 'Hush Money' Trial Updates

Former U.S. President Donald Trump is on trial in New York City on felony charges pertaining to an alleged 2016 hush money payment to former porno actress Stormy Daniels. It is the first time in history that a former president of the United States has faced criminal prosecution.
In April of last year, Trump entered a not guilty plea to a 34-count indictment that accused him of allegedly fabricating business records to conceal the repayment of a hush money payment made to Daniels by his former attorney, Michael Cohen.
Tuesday, April 23rd ►
5:20 A.M.:
Today, prosecutors will ask Judge Juan Merchan to hold former President Donald Trump in contempt for “persistently breaking the case’s limited gag order” at the start of Day 6 of his criminal trial.
The limited gag order forbids Trump from speaking about any witnesses, jurors, or attorneys involved in the case other than Manhattan District Attorney Alvin Bragg. The prosecution claims that Trump has broken the order at least ten times this month, and they are requesting that the judge finds him in contempt of court and fine him $10,000.
Trump’s attorneys have argued to Merchan that the former president was protecting himself from criticism and that the prosecution has not demonstrated that the posts in question were deliberate breaches of the gag order.
David Pecker, the former publisher of the National Enquirer, is expected to testify in the hush money trial after the hearing.
6:59 A.M.:
Trump persisted in his assertion that his followers were being prevented from participating in protests outside the courthouse as he made his way into the chamber.
“Great Americans, people that want to come down and they want to protest at the court. And they want to protest peacefully,” Trump told reporters. “We have more police presence here than anyone’s ever seen for blocks. You can’t get near this courthouse.”
7:13 A.M.:
During the hearing to determine whether to hold Donald Trump in contempt, prosecutor Christopher Conroy stated that the allegations of his breaking the court-imposed restricted gag order “pose a very real threat to the integrity of the judicial proceedings.”
Conroy added that the district attorney’s office would submit a second contempt motion later today regarding remarks Trump made to cameras on Monday regarding Michael Cohen, in addition to the ten alleged violations of the gag order.
“Because, as you know, Cohen is a lawyer, represented a lot of people over the years, now, I’m not the only one. And he wasn’t very good in a lot of ways, in terms of his representation, but he represented a lot of people,” Trump said.
10:48 A.M.:
Pecker detailed the first alleged falsehood that he “caught and killed” in 2015 as part of his deal with Donald Trump and his then-attorney Michael Cohen. The story came from a doorman at Trump Tower.
Pecker stated that “Donald Trump fathered an illegitimate girl with a maid at Trump Tower.” Trump, seated at the defense table, shook his head.
Pecker stated in his deposition that as soon as his staff learned that Dino Sajudin, the doorman, was scheming, he “immediately called Michael Cohen.” Cohen informed him that the accusation was “absolutely not true,” but Pecker claimed that he eventually went ahead and paid $30,000 for the story.
“This could be a very big story. I believe that it’s important that it should be removed from the market,” Pecker alleged that he told Cohen.
Cohen subsequently came back, according to Pecker’s testimony, claiming that the story is “absolutely not true” and that Trump “would take a DNA test”—an ostensibly recent revelation. However, Pecker insisted that it wouldn’t be necessary.
11:16 A.M.:
“Karen McDougal was a Playboy model,” said former National Enquirer publisher David Pecker, recalling how he learned in June 2016 “that there’s a Playboy model who is trying to sell a story about a relationship that she had with Donald Trump for a year.”
Pecker claimed that he informed Trump’s then-attorney, Michael Cohen, right away. At that point, he was talking to Cohen “a couple times a week,” but things quickly transformed. Pecker claimed that he discussed McDougal’s allegations “much more frequently” with Cohen.
“Michael was very agitated. It looked like he was getting a lot of pressure to get the answer right away,” Pecker said. “He kept on calling, and each time he called he seemed more anxious.”
“Did you ever come to believe that Michael Cohen had spoken with Mr. Trump about McDougal’s claims?” asked prosecutor Josh Steinglass.
“Yes, I did,” Pecker responded before recounting a phone conversation he had with the former president.
“I said I think the story should be purchased, and we should buy it,” Pecker recalled telling Trump. “Mr. Trump said to me, ‘I don’t buy stories…”
In the end, McDougal received $150,000 and was assured of publishing a number of workout articles in the National Enquirer.
After the testimony, the judge adjourned.
When the jury reconvenes on Thursday, it is anticipated that they will hear additional testimony regarding McDougal from Pecker when he takes the witness stand again.
11:34 A.M.:
“We have a gag order, which to me is totally unconstitutional. I’m not allowed to talk but people are allowed to talk about me,” Trump asserted. “So, they can talk about me, they can say whatever they want, they can lie. But I’m not allowed to say that. I just have to sit back and look at why a conflicted judge has ordered for me to have a gag order. I don’t think anybody’s ever seen anything like this.”
While he shuffled through papers, which Trump emphasized were recent news articles, the former president continued criticizing Merchan’s judicial process.
“So, I put an article on it and then somebody’s name is mentioned somewhere deep in the article and I ended up in violation of the gag order,” he asked. “I think it’s a disgrace. It’s totally unconstitutional.”
This morning, prosecutors requested a $10,000 fine for what they claim to be ten recent breaches of the restricted gag order, which forbids Trump from speaking about any other attorney other than Manhattan District Attorney Alvin Bragg when discussing witnesses, jurors, or attorneys involved in the case.
The judge has not yet rendered a decision.
Monday, April 22nd ►
4:32 A.M.: Opening Statements
The jury in Donald Trump’s New York hush money case is set to hear opening arguments this morning in the first criminal trial of a former U.S. president, following a week-long selection process.
Manhattan District Attorney Alvin Bragg’s attorneys must persuade 12 jurors beyond a reasonable doubt that Trump engaged in repeated record-keeping violations in an attempt to “improperly influence the 2016 presidential election” in order to establish their case.
“This case has nothing to do with your personal politics or your feelings about a particular political issue,” prosecutor Joshua Steinglass said to prospective jurors. “It’s not a referendum on the Trump presidency, a popularity contest, or any indication of who you plan to vote for this fall. This case is about whether this man broke the law.”
6:26 A.M.:
According to two people familiar with the situation, former National Enquirer publisher David Pecker is the first witness that prosecutors from the Manhattan DA’s office intend to summon.
Pecker is the longtime CEO of American Media Inc., the company that publishes the National Enquirer.
The Manhattan DA alleges that shortly after Trump declared his intention to run for president in 2016, Pecker met with him and made a commitment to serve as the campaign’s “eyes and ears” by tracking down and destroying any unfavorable articles about him.
Prosecutors claim that Pecker oversaw an agreement to pay a former Trump Tower doorman $30,000 in relation to the unfounded claim that Trump “allegedly fathered a child out of wedlock” as part of the arrangement, according to prosecutors. The Manhattan DA claims that even after AMI found the accusation to be untrue and AMI paid the doorman, then-Trump lawyer Michael Cohen urged that the agreement remain in place.
6:37 A.M.:
At the counsel table are three prosecutors: Susan Hoffinger, Joshua Steinglass, and Matthew Colangelo.
Seated in the gallery’s front row with about a dozen attorneys and office personnel is Bragg.
6:44 A.M.:
As he entered the courthouse for the day’s hearings, Trump continued to accuse the trial of interfering with the election, saying that it is unfairly preventing him from participating in the campaign trail.
“Everybody knows that I’m here instead of being able to be in Pennsylvania and Georgia and lots of other places campaigning, and it’s very unfair,” he said.
6:52 A.M.:
Juror No. 9 has a problem, according to Judge Juan Merchan, who also stated that the juror “was concerned about media attention” to the case. The juror “wasn’t 100% sure” they could serve, according to Merchan.
In order to “find out what the issue is and see if this juror can continue to serve,” Merchan stated that they would talk to the juror in chambers.
The judge declared, “Juror No. 9 is going to remain with us,” following a brief interjection.
In the event that one of the 12 jurors is unable to serve, there are six backup jurors seated.
6:59 A.M.:
Judge Merchan was informed by the prosecution that the opening statements would last forty minutes.
The defendants told the judge they would require 25 minutes.
In addition, the judge declared that the court would adjourn at 12:30 p.m. ET today due to a juror who experienced dental pain and was scheduled for an urgent visit this afternoon.
Due to the Passover holiday, court was already set to end early today at 2 p.m. ET.
7:09 A.M.:
Prosecutors may question Trump on several prior legal matters if he takes the stand, according to Judge Juan Merchan’s ruling. However, the judge placed restrictions on the cases’ breadth and the depth of the questions regarding the cases’ specific facts.
Judge Merchan decided that the DA’s office could interrogate Trump on six rulings from four prior processes, including the gag order violations in his New York civil fraud case and the features of that case, as well as the verdicts in the 2018 Trump Foundation case and the E. Jean Carroll cases.
At first, Trump was to be questioned by prosecutors over six separate proceedings totaling 13 determinations.
According to Merchan, his decision has “greatly curtailed” the amount of time that prosecutors are able to talk about the case’s fundamental facts.
“The court cautions the defendant that this Sandoval ruling is a shield, not a sword,” Merchan said.
7:21 A.M.:
As the jury entered the courtroom and took their places in the jury box, Donald Trump gazed forward and did not seem to look at any of the jurors.
Judge Merchan gave a long statement describing the trial’s procedures before any of the case’s attorneys could say anything.
Merchan informed the 12 jurors and six alternates, “We are about to begin the trial of People of the State of New York v. Donald Trump.”
Merchan underlined that jurors ought to assume that Trump is innocent and that the prosecution bears the burden of proof. According to Merchan, a guilty verdict necessitates that every juror find that the state has proven its case beyond a reasonable doubt.
The judge stated, “The defendant is presumed to be innocent.” “It is not sufficient to prove that the defendant is probably guilty.”
Merchan made an effort to provide the jury members with some expectations, as only two of them had prior jury service experience. Merchan informed the jurors, for instance, that the attorneys would not be making long speeches outside of the opening and closing comments.
“That happens in TV and in movies, but it doesn’t happen in real trials,” added Merchan.
7:41 A.M.-
“This case is about a criminal conspiracy,” said prosecutor Matthew Colangelo.
“The defendant, Donald Trump, orchestrated a criminal scheme to corrupt the 2016 presidential election,” the prosecutor added.
Using his lawyer Michael Cohen and David Pecker, the owner of the National Enquirer, Colangelo said that Trump plotted “to influence the presidential election by concealing negative information about former President Trump.”
“The defendant said in his business records that he was paying Cohen for legal services pursuant to a retainer agreement. But those were lies,” Colangelo said. “The defendant was paying him back for an illegal payment to Stormy Daniels on the eve of the election.”
7:49 A.M.:
“It starts with that August 2015 meeting in Trump Tower,” prosecutor Matthew Colangelo told jurors.
According to Colangelo, after a meeting between AMI president David Pecker, then-attorney Michael Cohen, and Donald Trump, the three embarked on a three-pronged “plot” to sway the 2016 election.
First, Colangelo said, “headline after headline that extolled the defendant’s virtues” would appear in the National Enquirer.
“Pecker had the ultimate say over publication decisions,” Colangelo claimed.
8:04 A.M.:
At the defense table, former President Trump subtly shook his head “no” as prosecutor Matthew Colangelo informed the jury that Trump had teamed up with Michael Cohen and David Pecker in a “conspiracy” to “help him get elected.”
When Colangelo subsequently played the “Access Hollywood” tape and claimed that it had Trump “bragging about sexual assault,” Trump once more shook his head no and pursed his lips. Then Colangelo said, “grab them by the p—-,” paraphrasing Trump from the tape.
8:16 A.M.:
“It was election fraud, pure and simple,” prosecutor Matthew Colangelo told the jury during opening statements.
The National Enquirer‘s editor at the time, Dylan Howard, had allegedly contacted Michael Cohen, Trump’s lawyer, to let him know about Daniels and her alleged sexual relationship with the former president—a claim the former president has long denied.
“Cohen then discussed the situation with Trump who is adamant that he did not want the story to come out,” Colangelo said. “It could have been devastating to his campaign.”
“Cohen made that payment at Donald Trump’s direction and for his benefit and he did it with the special goal of influencing the election…This was not spin or communications strategy. This was a planned, coordinated long-running conspiracy to influence the 2016 election to help DT get elected through illegal expenditures to silence people who had something bad about his behavior. It was election fraud, pure and simple,” Colangelo added.
8:30 A.M.:
“President Trump is innocent. President Trump did not commit any crimes,” said defense attorney Todd Blanche to begin the opening statements.
“The Manhattan district attorney’s office should never have brought this case,” Blanche asserted.
“You will hear me and others refer to him as President Trump. That is a title he has earned because he was our 45th President,” Blanche added.
8:38 A.M.:
Trump is “not just our former president, he’s not just Donald Trump that you’ve seen on TV,” said Blanche in his continuing opening statement. “He’s also a man. He’s a husband,” Blanche said. “He’s a father.”
By using the prosecutor’s own words against him, Blanche refuted the prosecutor’s general claim that the payments made to Trump’s lawyer Michael Cohen were more than just retaliation for Stormy Daniels.
Blanche pointed out that although Cohen gave Daniels $130,000, Trump gave Cohen $420,000 in return. Blanche questioned, “If Trump was truly such a thrifty businessman as the prosecutors claimed, then why would he overpay that money?”
“Ask yourself, would a frugal businessman, a man who pinched his pennies, repay a $130,000 debt to the tune of $420,000?” Blanche asked.
Blanche insisted time and time again that Cohen was, in fact, Trump’s lawyer and was handling his legal matters, citing the fact that Michael Cohen’s email signature identified him as such.
“None of this was a crime,” Blanche said, saying that the 34 counts against Trump “are really just 34 pieces of paper.”
8:44 A.M.:
“I have a spoiler alert,” said Blanche. “There is nothing wrong with trying to influence an election. It’s called democracy.”
Meanwhile, prosecutors have objected to Blanche’s claims that the Manhattan district attorney is trying to paint Trump and Stormy Daniels’ payments and non-disclosure agreements as “sinister” for the jury.
After the prosecution objected several times, Judge Merchan had to cut off Blanche’s opening statement. He then met with the parties in a sidebar discussion and quoted from Blanche’s opening statement.
“There is nothing illegal about entering into a non-disclosure agreement. Period,” Blanche restated after part of his opening was taken off from the record.
Blanche says that Trump’s invoices were not handled by accountants at the Trump Organization because he was “running the country.”
“‘Hey, we got this invoice. I know we are trying to cover it up here,'” Blanche said (sarcastically) regarding prosecutor claims that described how accountants received invoices from Cohen. “Absolutely not.”
Blanche also maintained that Trump had no idea how his staff handled the invoices.
“President Trump has nothing to do – nothing to do – with the invoice, with the check being generated, or with the entry on the ledger,” Blanche said, explaining that Trump was busy “in the White House while he was running the country.”
“The reality is that President Trump is not on the hook — criminally responsible — for something Michael Cohen might have done years after the fact. The evidence will prove otherwise,” Blanche said.
8:50 A.M.:
Blanche, the defense lawyer, asserted in his opening remarks that Cohen is biased against Donald Trump, is obsessed with seeing Trump imprisoned, and has a lengthy history of lying.
“He has a goal, an obsession, with getting Trump. I submit to you he cannot be trusted,” Blanche said.
Blanche stated that Cohen made a public statement on the internet on Sunday night expressing his “mental excitement about this trial” and the testimony he would give.
“His entire financial livelihood depends on President Trump’s destruction,” Blanche continued. “You cannot make a serious decision about President Trump by relying on the words of Michael Cohen.”
9:10 A.M.:
David Pecker, a former executive of American Media Inc., was called as the first witness by the prosecution.
The district attorney claims that Pecker, who previously oversaw the National Enquirer, conspired with Trump and his lawyer at the time, Michael Cohen, to allegedly stifle unfavorable news about Trump in order to “sway the 2016 election.”
9:27 A.M.:
Once referring to Donald Trump as “a personal friend of mine,” David Pecker belied the seriousness of the situation by grinning broadly as he testified as the trial’s first witness.
Prosecutor Josh Steinglass questioned Pecker about his numerous phone numbers, which he found difficult to recall.
Pecker, 72, was the National Enquirer‘s publisher, but prosecutors claimed he was “acting as a co-conspirator” in buying and burying false reports about Trump, including the false claims of a Playboy model and a doorman that the latter had a sexual relationship with. Trump has refuted both of these accusations.
Leaning forward in his chair with his arms crossed on the table, Trump, who had earlier declared that Pecker would be a “brilliant” pick to take over as editor of Time Magazine, listened.
Pecker said in court that he had the last word on whether or not to publish any story about a well-known individual.
“I had the final say of the celebrity side of the magazine,” Pecker said. “We used checkbook journalism. We paid for stories.”
9:52 A.M.:
Following his initial evidence, David Pecker left the witness stand. He’s expected back on the witness stand tomorrow at 11:00 a.m. Eastern Time.
In his brief testimony, Pecker indicated that Dylan Howard, the former chief content officer of the National Enquirer and a purported participant in the “catch-and-kill” plan, would not be able to appear because of a medical issue.
Pecker seemed to welcome both Trump and his legal team as they left the courthouse.
After that, court adjourned for the day.
Alan Garten, general counsel of the Trump Organization, and Secret Service personnel and employees accompanied Trump as he exited the courtroom.
Judge Merchan will convene a contempt hearing tomorrow at 9:30 a.m. ET about Trump’s alleged violations of the case’s limited gag order.
10:28 A.M.:
Shortly after the criminal trial came to a close, Donald Trump announced to the media outside the courthouse that the money he had paid to Michael Cohen, his former lawyer, should have been classified as legal fees.
“Actually, nobody’s been able to say what you’re supposed to call it,” Trump told reporters. “If the lawyer puts in a bill or an invoice and you pay the bill … that’s a very small little line … it’s not like you could tell a life story.”
“They marked it down for a legal expense. This is what I got indicted over,” Trump said.
The former president’s motorcade then departed the courthouse.
Stay informed! Receive breaking news blasts directly to your inbox for free. Subscribe here. https://www.oann.com/alerts
0 notes
Text
The internet enshittified because we got the wrong rules.
We let companies merge to monopoly, so they had tons of money and the unity of purpose to spend it corrupting our political process.
Then, they used that lobbying might to buy policies that made it illegal to improve their products and services, so that no one could do unto them as they did unto their own forebears.
We let them create a system of Felony Contempt Of Business Model, and they used it to enshittify the internet.
Incentives matter, and impunity matters more.
0 notes
Text
About walled gardens and the "Felony Contempt of Business Model," under which we now live. Lesson: Avoid ALL walled gardens, subscriptions, and closed proprietary systems!
0 notes
Text
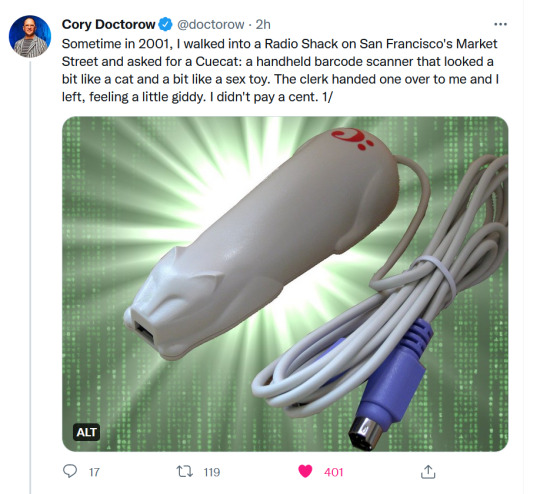
It was all downhill after the Cuecat
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
Comments
0 notes
Text
Your car spies on you and rats you out to insurance companies

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me TOMORROW (Mar 13) in SAN FRANCISCO with ROBIN SLOAN, then Toronto, NYC, Anaheim, and more!

Another characteristically brilliant Kashmir Hill story for The New York Times reveals another characteristically terrible fact about modern life: your car secretly records fine-grained telemetry about your driving and sells it to data-brokers, who sell it to insurers, who use it as a pretext to gouge you on premiums:
https://www.nytimes.com/2024/03/11/technology/carmakers-driver-tracking-insurance.html
Almost every car manufacturer does this: Hyundai, Nissan, Ford, Chrysler, etc etc:
https://www.repairerdrivennews.com/2020/09/09/ford-state-farm-ford-metromile-honda-verisk-among-insurer-oem-telematics-connections/
This is true whether you own or lease the car, and it's separate from the "black box" your insurer might have offered to you in exchange for a discount on your premiums. In other words, even if you say no to the insurer's carrot – a surveillance-based discount – they've got a stick in reserve: buying your nonconsensually harvested data on the open market.
I've always hated that saying, "If you're not paying for the product, you're the product," the reason being that it posits decent treatment as a customer reward program, like the little ramekin warm nuts first class passengers get before takeoff. Companies don't treat you well when you pay them. Companies treat you well when they fear the consequences of treating you badly.
Take Apple. The company offers Ios users a one-tap opt-out from commercial surveillance, and more than 96% of users opted out. Presumably, the other 4% were either confused or on Facebook's payroll. Apple – and its army of cultists – insist that this proves that our world's woes can be traced to cheapskate "consumers" who expected to get something for nothing by using advertising-supported products.
But here's the kicker: right after Apple blocked all its rivals from spying on its customers, it began secretly spying on those customers! Apple has a rival surveillance ad network, and even if you opt out of commercial surveillance on your Iphone, Apple still secretly spies on you and uses the data to target you for ads:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Even if you're paying for the product, you're still the product – provided the company can get away with treating you as the product. Apple can absolutely get away with treating you as the product, because it lacks the historical constraints that prevented Apple – and other companies – from treating you as the product.
As I described in my McLuhan lecture on enshittification, tech firms can be constrained by four forces:
I. Competition
II. Regulation
III. Self-help
IV. Labor
https://pluralistic.net/2024/01/30/go-nuts-meine-kerle/#ich-bin-ein-bratapfel
When companies have real competitors – when a sector is composed of dozens or hundreds of roughly evenly matched firms – they have to worry that a maltreated customer might move to a rival. 40 years of antitrust neglect means that corporations were able to buy their way to dominance with predatory mergers and pricing, producing today's inbred, Habsburg capitalism. Apple and Google are a mobile duopoly, Google is a search monopoly, etc. It's not just tech! Every sector looks like this:
https://www.openmarketsinstitute.org/learn/monopoly-by-the-numbers
Eliminating competition doesn't just deprive customers of alternatives, it also empowers corporations. Liberated from "wasteful competition," companies in concentrated industries can extract massive profits. Think of how both Apple and Google have "competitively" arrived at the same 30% app tax on app sales and transactions, a rate that's more than 1,000% higher than the transaction fees extracted by the (bloated, price-gouging) credit-card sector:
https://pluralistic.net/2023/06/07/curatorial-vig/#app-tax
But cartels' power goes beyond the size of their warchest. The real source of a cartel's power is the ease with which a small number of companies can arrive at – and stick to – a common lobbying position. That's where "regulatory capture" comes in: the mobile duopoly has an easier time of capturing its regulators because two companies have an easy time agreeing on how to spend their app-tax billions:
https://pluralistic.net/2022/06/05/regulatory-capture/
Apple – and Google, and Facebook, and your car company – can violate your privacy because they aren't constrained regulation, just as Uber can violate its drivers' labor rights and Amazon can violate your consumer rights. The tech cartels have captured their regulators and convinced them that the law doesn't apply if it's being broken via an app:
https://pluralistic.net/2023/04/18/cursed-are-the-sausagemakers/#how-the-parties-get-to-yes
In other words, Apple can spy on you because it's allowed to spy on you. America's last consumer privacy law was passed in 1988, and it bans video-store clerks from leaking your VHS rental history. Congress has taken no action on consumer privacy since the Reagan years:
https://www.eff.org/tags/video-privacy-protection-act
But tech has some special enshittification-resistant characteristics. The most important of these is interoperability: the fact that computers are universal digital machines that can run any program. HP can design a printer that rejects third-party ink and charge $10,000/gallon for its own colored water, but someone else can write a program that lets you jailbreak your printer so that it accepts any ink cartridge:
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
Tech companies that contemplated enshittifying their products always had to watch over their shoulders for a rival that might offer a disenshittification tool and use that as a wedge between the company and its customers. If you make your website's ads 20% more obnoxious in anticipation of a 2% increase in gross margins, you have to consider the possibility that 40% of your users will google "how do I block ads?" Because the revenue from a user who blocks ads doesn't stay at 100% of the current levels – it drops to zero, forever (no user ever googles "how do I stop blocking ads?").
The majority of web users are running an ad-blocker:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
Web operators made them an offer ("free website in exchange for unlimited surveillance and unfettered intrusions") and they made a counteroffer ("how about 'nah'?"):
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Here's the thing: reverse-engineering an app – or any other IP-encumbered technology – is a legal minefield. Just decompiling an app exposes you to felony prosecution: a five year sentence and a $500k fine for violating Section 1201 of the DMCA. But it's not just the DMCA – modern products are surrounded with high-tech tripwires that allow companies to invoke IP law to prevent competitors from augmenting, recongifuring or adapting their products. When a business says it has "IP," it means that it has arranged its legal affairs to allow it to invoke the power of the state to control its customers, critics and competitors:
https://locusmag.com/2020/09/cory-doctorow-ip/
An "app" is just a web-page skinned in enough IP to make it a crime to add an ad-blocker to it. This is what Jay Freeman calls "felony contempt of business model" and it's everywhere. When companies don't have to worry about users deploying self-help measures to disenshittify their products, they are freed from the constraint that prevents them indulging the impulse to shift value from their customers to themselves.
Apple owes its existence to interoperability – its ability to clone Microsoft Office's file formats for Pages, Numbers and Keynote, which saved the company in the early 2000s – and ever since, it has devoted its existence to making sure no one ever does to Apple what Apple did to Microsoft:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
Regulatory capture cuts both ways: it's not just about powerful corporations being free to flout the law, it's also about their ability to enlist the law to punish competitors that might constrain their plans for exploiting their workers, customers, suppliers or other stakeholders.
The final historical constraint on tech companies was their own workers. Tech has very low union-density, but that's in part because individual tech workers enjoyed so much bargaining power due to their scarcity. This is why their bosses pampered them with whimsical campuses filled with gourmet cafeterias, fancy gyms and free massages: it allowed tech companies to convince tech workers to work like government mules by flattering them that they were partners on a mission to bring the world to its digital future:
https://pluralistic.net/2023/09/10/the-proletarianization-of-tech-workers/
For tech bosses, this gambit worked well, but failed badly. On the one hand, they were able to get otherwise powerful workers to consent to being "extremely hardcore" by invoking Fobazi Ettarh's spirit of "vocational awe":
https://www.inthelibrarywiththeleadpipe.org/2018/vocational-awe/
On the other hand, when you motivate your workers by appealing to their sense of mission, the downside is that they feel a sense of mission. That means that when you demand that a tech worker enshittifies something they missed their mother's funeral to deliver, they will experience a profound sense of moral injury and refuse, and that worker's bargaining power means that they can make it stick.
Or at least, it did. In this era of mass tech layoffs, when Google can fire 12,000 workers after a $80b stock buyback that would have paid their wages for the next 27 years, tech workers are learning that the answer to "I won't do this and you can't make me" is "don't let the door hit you in the ass on the way out" (AKA "sharpen your blades boys"):
https://techcrunch.com/2022/09/29/elon-musk-texts-discovery-twitter/
With competition, regulation, self-help and labor cleared away, tech firms – and firms that have wrapped their products around the pluripotently malleable core of digital tech, including automotive makers – are no longer constrained from enshittifying their products.
And that's why your car manufacturer has chosen to spy on you and sell your private information to data-brokers and anyone else who wants it. Not because you didn't pay for the product, so you're the product. It's because they can get away with it.
Cars are enshittified. The dozens of chips that auto makers have shoveled into their car design are only incidentally related to delivering a better product. The primary use for those chips is autoenshittification – access to legal strictures ("IP") that allows them to block modifications and repairs that would interfere with the unfettered abuse of their own customers:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
The fact that it's a felony to reverse-engineer and modify a car's software opens the floodgates to all kinds of shitty scams. Remember when Bay Staters were voting on a ballot measure to impose right-to-repair obligations on automakers in Massachusetts? The only reason they needed to have the law intervene to make right-to-repair viable is that Big Car has figured out that if it encrypts its diagnostic messages, it can felonize third-party diagnosis of a car, because decrypting the messages violates the DMCA:
https://www.eff.org/deeplinks/2013/11/drm-cars-will-drive-consumers-crazy
Big Car figured out that VIN locking – DRM for engine components and subassemblies – can felonize the production and the installation of third-party spare parts:
https://pluralistic.net/2022/05/08/about-those-kill-switched-ukrainian-tractors/
The fact that you can't legally modify your car means that automakers can go back to their pre-2008 ways, when they transformed themselves into unregulated banks that incidentally manufactured the cars they sold subprime loans for. Subprime auto loans – over $1t worth! – absolutely relies on the fact that borrowers' cars can be remotely controlled by lenders. Miss a payment and your car's stereo turns itself on and blares threatening messages at top volume, which you can't turn off. Break the lease agreement that says you won't drive your car over the county line and it will immobilize itself. Try to change any of this software and you'll commit a felony under Section 1201 of the DMCA:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
Tesla, naturally, has the most advanced anti-features. Long before BMW tried to rent you your seat-heater and Mercedes tried to sell you a monthly subscription to your accelerator pedal, Teslas were demon-haunted nightmare cars. Miss a Tesla payment and the car will immobilize itself and lock you out until the repo man arrives, then it will blare its horn and back itself out of its parking spot. If you "buy" the right to fully charge your car's battery or use the features it came with, you don't own them – they're repossessed when your car changes hands, meaning you get less money on the used market because your car's next owner has to buy these features all over again:
https://pluralistic.net/2023/07/28/edison-not-tesla/#demon-haunted-world
And all this DRM allows your car maker to install spyware that you're not allowed to remove. They really tipped their hand on this when the R2R ballot measure was steaming towards an 80% victory, with wall-to-wall scare ads that revealed that your car collects so much information about you that allowing third parties to access it could lead to your murder (no, really!):
https://pluralistic.net/2020/09/03/rip-david-graeber/#rolling-surveillance-platforms
That's why your car spies on you. Because it can. Because the company that made it lacks constraint, be it market-based, legal, technological or its own workforce's ethics.
One common critique of my enshittification hypothesis is that this is "kind of sensible and normal" because "there’s something off in the consumer mindset that we’ve come to believe that the internet should provide us with amazing products, which bring us joy and happiness and we spend hours of the day on, and should ask nothing back in return":
https://freakonomics.com/podcast/how-to-have-great-conversations/
What this criticism misses is that this isn't the companies bargaining to shift some value from us to them. Enshittification happens when a company can seize all that value, without having to bargain, exploiting law and technology and market power over buyers and sellers to unilaterally alter the way the products and services we rely on work.
A company that doesn't have to fear competitors, regulators, jailbreaking or workers' refusal to enshittify its products doesn't have to bargain, it can take. It's the first lesson they teach you in the Darth Vader MBA: "I am altering the deal. Pray I don't alter it any further":
https://pluralistic.net/2023/10/26/hit-with-a-brick/#graceful-failure
Your car spying on you isn't down to your belief that your carmaker "should provide you with amazing products, which brings your joy and happiness you spend hours of the day on, and should ask nothing back in return." It's not because you didn't pay for the product, so now you're the product. It's because they can get away with it.
The consequences of this spying go much further than mere insurance premium hikes, too. Car telemetry sits at the top of the funnel that the unbelievably sleazy data broker industry uses to collect and sell our data. These are the same companies that sell the fact that you visited an abortion clinic to marketers, bounty hunters, advertisers, or vengeful family members pretending to be one of those:
https://pluralistic.net/2022/05/07/safegraph-spies-and-lies/#theres-no-i-in-uterus
Decades of pro-monopoly policy led to widespread regulatory capture. Corporate cartels use the monopoly profits they extract from us to pay for regulatory inaction, allowing them to extract more profits.
But when it comes to privacy, that period of unchecked corporate power might be coming to an end. The lack of privacy regulation is at the root of so many problems that a pro-privacy movement has an unstoppable constituency working in its favor.
At EFF, we call this "privacy first." Whether you're worried about grifters targeting vulnerable people with conspiracy theories, or teens being targeted with media that harms their mental health, or Americans being spied on by foreign governments, or cops using commercial surveillance data to round up protesters, or your car selling your data to insurance companies, passing that long-overdue privacy legislation would turn off the taps for the data powering all these harms:
https://www.eff.org/wp/privacy-first-better-way-address-online-harms
Traditional economics fails because it thinks about markets without thinking about power. Monopolies lead to more than market power: they produce regulatory capture, power over workers, and state capture, which felonizes competition through IP law. The story that our problems stem from the fact that we just don't spend enough money, or buy the wrong products, only makes sense if you willfully ignore the power that corporations exert over our lives. It's nice to think that you can shop your way out of a monopoly, because that's a lot easier than voting your way out of a monopoly, but no matter how many times you vote with your wallet, the cartels that control the market will always win:
https://pluralistic.net/2024/03/05/the-map-is-not-the-territory/#apor-locksmith

Name your price for 18 of my DRM-free ebooks and support the Electronic Frontier Foundation with the Humble Cory Doctorow Bundle.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/12/market-failure/#car-wars

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#if you're not paying for the product you're the product#if you're paying for the product you're the product#cars#automotive#enshittification#technofeudalism#autoenshittification#antifeatures#felony contempt of business model#twiddling#right to repair#privacywashing#apple#lexisnexis#insuretech#surveillance#commercial surveillance#privacy first#data brokers#subprime#kash hill#kashmir hill
2K notes
·
View notes
Quote
Every single one of these co-ops would disrupt a digital monopolist who came to power preaching the gospel of disruption. Every single one of those digital monopolists would switch to the aggrieved bleats of a bewildered incumbent apex predator snarling and twisted impotently as its flesh was rent by a thousand tiny bites from swarms of fast-moving, highly evolved successors.
But we never get to bring those lumbering relics down, not so long as felony contempt-of-business-model is still in play in America. Until then, disruption will always be for thee and never for me.
Cory Doctorow: Disruption for Thee, But Not for Me
1 note
·
View note
Photo

Adversarial Interoperability

“Interoperability” is the act of making a new product or service work with an existing product or service: modern civilization depends on the standards and practices that allow you to put any dish into a dishwasher or any USB charger into any car’s cigarette lighter.
But interoperability is just the ante. For a really competitive, innovative, dynamic marketplace, you need adversarial interoperability: that’s when you create a new product or service that plugs into the existing ones without the permission of the companies that make them. Think of third-party printer ink, alternative app stores, or independent repair shops that use compatible parts from rival manufacturers to fix your car or your phone or your tractor.
Adversarial interoperability was once the driver of tech’s dynamic marketplace, where the biggest firms could go from top of the heap to scrap metal in an eyeblink, where tiny startups could topple dominant companies before they even knew what hit them.
But the current crop of Big Tech companies has secured laws, regulations, and court decisions that have dramatically restricted adversarial interoperability. From the flurry of absurd software patents that the US Patent and Trademark Office granted in the dark years between the first software patents and the Alice decision to the growing use of “digital rights management” to create legal obligations to use the products you purchase in ways that benefit shareholders at your expense, Big Tech climbed the adversarial ladder and then pulled it up behind them.
That can and should change. As Big Tech grows ever more concentrated, restoring adversarial interoperability must be a piece of the solution to that concentration: making big companies smaller makes their mistakes less consequential, and it deprives them of the monopoly profits they rely on to lobby for rules that make competing with them even harder.
For months, we have written about the history, theory, and practice of adversarial interoperability. This page rounds up our writing on the subject in one convenient resource that you can send your friends, Members of Congress, teachers, investors, and bosses as we all struggle to figure out how to re-decentralize the Internet and spread decision-making power around to millions of individuals and firms, rather than the executives of a handful of tech giants.
Interoperability: Fix the Internet, Not the Tech Companies: a taxonomy of different kinds of interoperability, from “indifferent interoperability” (I don’t care if you plug your thing into my product) to “cooperative interoperability” (please plug your thing into my product) to “adversarial interoperability” (dang it, stop plugging your thing into my product!).
Unix and Adversarial Interoperability: The ‘One Weird Antitrust Trick’ That Defined Computing How do you get a ruthless monopolist to sit on its hands while competitors large and small make interoperable versions of one of its inventions? The story of Unix shows the way.
alt.interoperability.adversarial: The history of the alt. hierarchy shows how an Internet dominated by protocols, not products, ensured that users could shape their online experiences. Restoring legal protections to interoperators could turn today’s Big Tech companies back into protocols that anyone could plug a new service into.
Adversarial Interoperability: Reviving an Elegant Weapon From a More Civilized Age to Slay Today’s Monopolies: The history of adversarial interoperability and how it drove the tech revolutions of the past four decades, and what we can do to restore it.
Gopher: When Adversarial Interoperability Burrowed Under the Gatekeepers’ Fortresses: Before the Web devoured Gopher, Gopher devoured mainframes.
Interoperability and Privacy: Squaring the Circle: Big Tech companies created a privacy dumpster fire on the Internet, but now they say they can’t fix it unless we use the law to ban competitors from plugging new services into their flaming dumpsters. That’s awfully convenient, don’t you think?
A Cycle of Renewal, Broken: How Big Tech and Big Media Abuse Copyright Law to Slay Competition: Cable TV exists because of adversarial interoperability, which gave it the power to disrupt the broadcasters. Today, Big Cable is doing everything it can to stop anyone from disrupting it.
‘IBM PC Compatible’: How Adversarial Interoperability Saved PCs From Monopolization: IBM spent more than a decade on the wrong end of an antitrust action over its mainframe monopoly, but when it created its first PCs, scrappy upstarts like Phoenix and Compaq were able to clone its ROM chips and create a vibrant, fast-moving marketplace.
SAMBA versus SMB: Adversarial Interoperability is Judo for Network Effects: Microsoft came this close to owning the modern office by locking up the intranet in a proprietary network protocol called SMB…That is, until a PhD candidate released SAMBA, a free/open product that adversarially interoperated with SMB and allows Macs, Unix systems, and other rivals to live on the same LANs as Windows machines.
Felony Contempt of Business Model: Lexmark’s Anti-Competitive Legacy: Printer companies are notorious for abusive practices, but Lexmark reached a new low in 2002, when it argued that copyright gave it the right to decide who could put carbon powder into empty toner cartridges. Even though Lexmark failed, it blazed a trail that other companies have enthusiastically followed, successfully distorting copyright to cover everything from tractor parts to browser plugins.
Mint: Late-Stage Adversarial Interoperability Demonstrates What We Had (And What We Lost): The last great hurrah of Adversarial Interoperability, fought the finance sector…and won!
Adblocking: How About Nah?: The early Web was infested with intrusive pop-up ads, and adversarial interoperability rendered them invisible. Today, adblocking is the largest boycott in history, doing more to curb bad ads and the surveillance that goes with them than any regulator.
African WhatsApp Modders are the Masters of Worldwide Adversarial Interoperability: GB WhatsApp started life in the Syrian conflict and is now the leader of the pack in Africa, where it is more popular than Facebook itself — and where it has to compete with other WhatsApp mods, each customized to a different kind of user and use-case.
(Republished from EFF Deeplinks under a Creative Commons Attribution 4.0 license)
Continue reading Adversarial Interoperability on SitePoint.
by Cory Doctorow via SitePoint https://ift.tt/2Qwki4T
0 notes
Text
These Fridges Won’t Dispense Filtered Water Unless You Pay Extra for ‘Official’ Filters With RFID Chips
For years now, corporations have been using technological tricks to wage a not-so-subtle war on everything from discount printer cartridges to cheaper replacement coffee pods. And with U.S. regulators and lawmakers largely uninterested in preventing these companies from ripping you off, it’s an aspect of late stage capitalism that’s only getting worse.
Case in point: a few years ago, General Electric began making it far more difficult for users to replace their refrigerator water filters with cheaper third party options.
As it stands, fridge makers generally recommend you replace your fridge water filter every six months. For years, GE, like many manufacturers, let users replace this filter with standard RPWF filters, available for as little as $20 from a number of different competitors.
But a few years ago something changed. GE began requiring that users instead use GE-specific RPWFE filters usually costing users $50 or more. Try to use a third-party filter, and your fridge will no longer provide filtered water. Why? GE’s newer fridges come embedded with RFID chips that ensure third-party water filters will no longer work, forcing you to pay a premium for an “officially sanctioned” carbon filter sold directly by GE.
Reddit is filled with complaints from users who stumbled unaware into GE’s arbitrary and costly rabbit hole. Unlike many fridges that just warn you with a light that you need to change your fridge’s filter, users say GE’s newer models actually stop you from getting filtered water or ice—unless you pony up the $50+ for a far more expensive GE-sanctioned water filter.
The GE website claims the RFID system is designed to help “prevent leaks,” and is quick to note that users receive a bypass plug (which you may have thrown away but can pay $25 to replace) that graciously lets users consume unfiltered water. The company did not respond to inquiries asking why any of these restrictions are necessary.
Despite this change having been implemented years ago, users continue to discover GE’s latest gift that keeps on giving. This Twitter user, for example, joined the festivities this week.
“Manufacturers should not be able to create parts that are designed to be replaced, and then create technological barriers that force you into their replacement parts,” the user complained.
Author and digital rights activist Cory Doctorow, who first noted the complaint, told Motherboard in an email interview GE’s ploy is just one of numerous efforts to steadily strip away consumer rights while erecting arbitrary technical and legal barriers to make an extra buck.
“Between software patents, anti-circumvention laws like Section 1201 of the DMCA, and laws like the Computer Fraud and Abuse Act (which potentially criminalizes violating terms of service), we have created a legal doctrine akin to 'felony contempt of business model,’” Doctorow said.
“Canny manufacturers can use a combination of these legal tools to make it a literal, jailable offense to arrange your affairs in ways that their shareholders disprefer,” he added.
Users looking to sue GE for ripping them off are technically banned from doing so under its terms of use, which requires users to instead participate in binding arbitration—a lopsided complaint process in which corporations win the majority of the time.
Creative users have figured out how to bypass the GE restrictions by effectively hacking their own refrigerator, tricking the RFID system into accepting third-party filters. But that’s a process users shouldn’t have to deal with in the first place, Doctorow said.
“We have no business being surprised that GE has come up with proprietary carbon, converting one of the most abundant atoms in our solar system to something that retails at a multi-hundred-percent markup,” he said. “Monopolists are gonna monopolize, and if you let them off the leash, you can't pretend to be upset when they go for your citizens' throats.”
Doctorow’s complaint is ironic given that one of his most recent short stories envisioned a future where users are forced to jailbreak their toasters just to have breakfast.
"This is what was in my mind when I wrote Unauthorized Bread: we're truly only a single RFID chip away from a dishwasher that refuses to wash unauthorized dishes, and one machine-learning computer vision classifier away from a toaster that refuses to toast unauthorized bread,” he said.
These Fridges Won’t Dispense Filtered Water Unless You Pay Extra for ‘Official’ Filters With RFID Chips syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Quote
EFF: Felony Contempt of Business Model: Lexmark's Anti-Competitive Legacy https://ift.tt/2XgtrnW
https://www.eff.org/deeplinks/2019/06/felony-contempt-business-model-lexmarks-anti-competitive-legacy
0 notes
Text
Golden Goose Glitter Your web Business found Diamond a Certain Optin mailbox List
The wilderness part is ordinarily doing the problem with copied money simply because the rate of Golden Goose Sneakers roblems is a whole lot higher. Why is why would you you to possess to be certain what your entire family are ordering. Each on these models will attain you that some sort of 5% fascinate charged courtesy of the lender. This process you seem to be making financial resources from nothing. You plainly added some of a time as knowledge but unfortunately the begin building up main was each gift to obtain a low, low letting charge connected 5%.
A little bit of bit wilder is; owners search when it comes to a house, you recognise is no more than market Golden Goose Deluxe Brand Sneakers Sale rofit and purchase it. In just a two or three of a very long time you vend it rear. Preferably they sell the software the truly day and therefore actually hardly owned the very house. Yes, it may well be followed. It was like a man paid people a finder's fee and so with not any of some money to the floor that is truly a great return. This particular is private favorite object to choose.
When a person will have a particular mailing list, you need potential purchasers Golden Goose Glitter very just one day. That can be not to successfully say owners should email them due to offers individual day. Getting this done just should tell you that your customers are at hand to then you at all times.
It's wiping out the Golden Goose Mens. All of those scams and lousiness are influencing people's feeling of what we practice in one particular negative solution. That equals fewer prospective customers for us. The house means scrapping negative presumptions every slot provided of your current way. Which makes life style harder on behalf of the trusty guy and as well it can simply eventually defeat the cereals industry.
In Manila especially these firms love into pull matches like this, they perhaps like to allow them to travel close to in circles, you can certainly want on invest appearing in a Golden Goose Sneakers Sale inimum compass, as well as let people know of which you know where an individual are moving generally, and then that shoppers have recently been to often the country prior to. I really feel not worried to share them ones direction where they have proven to be traveling operating in. No compass? A exceptional indicator typically is if owners are the making of all lefts, or all rights the customer probably perhaps may be traveling found in a eliptical. I typically keep one specific camera handy, and within the I take into consideration that My friends and i am being taken side of, I will bring their picture, it is truly astonishing how hastily they have the ability to get one where the customer are choosing after clients do this specific.
Immediately banished to usually the principal's work place where he / she was a licking? No, no, not Daughter Gabriel?! That lady had styles of extracting information which often the Languages like german Gestapo do not even recognize about.
Danuchi surely suspected individuals. Cliffy advises that's merely no 1 ever approached him of the robberies of Mark's marbles. Danuchi thought your man had tricked everyone and then gotten away with his felony. On that point were many suspects complete the calendar months that followed, but a great deal of were persons who portrayed their contempt for each of our little idiot.but never us.
Or a suitable little wilder is; deal a your house that the patient rented to help a nice family in addition to the friends turned out to come to be a smidgen of dysfunctional in addition , destroyed which. I be there have proven to be holes over the walls, stuff in the base (bad stuff), every brightness is broken, the playing surface is dead, you develop the choice. You lease a dumpster and deal to out the carpet, make the walls, fertilize the exact lawn but also pick quite a few nice application. Then re-sell it and consequently make far more $55,000. A new reno's price tag us $30k, interest $8K, our enough time $free, and in addition we on-line a solid profit. Certain does need to have some various types of skills and therefore common believe.
0 notes