#backdoor software jobs
Text
Aditya Birla Fresher Job Openings | Support Executive - Operations | Any Degree - Chennai
Introduction
Aditya Birla Fresher Job Openings :Aditya has Published notification for the vacancy of Back Office Executives
The educational qualification required to apply for this Aditya Birla is Any Degree
Interested and eligible candidates can apply for Aditya Birla.
There is enough time to apply for any job. Read Aditya Birla date, last date to apply, full details of vacancies carefully.…

View On WordPress
#Aditya Birla Fresher Job Openings | Support Executive - Operations | Any Degree - Chennai#back office executive#back office executive interview#back office interview#back office job chennai#back office jobs#back office jobs near me#backdoor it jobs in hyderabad for freshers#backdoor software jobs#backend engineer#background check part time job#direct walk interview backend banking non voice jobs chennai
0 notes
Text
I'm all for non-prescriptive language use, but I have limits.
The things you download to your computer and run to make it do those things? Those are programs. Not "apps"
"App" is Apple branding that they've tricked the larger populace into using. Oh how cute, the company that ruined home computing and doesn't know what a right-click is has shortened their name to apply to their system of backdoor social control predatory software market! Lets just use that term.
"Application" is a type of program, most commonly (and I argue, properly) applied to business/productivity software.
But just the shortened app?
That's Steve Jobs' ghost whispering blasphemies in your ear.
143 notes
·
View notes
Text
youtube
Watch the American Climate Leadership Awards 2024 now: https://youtu.be/bWiW4Rp8vF0?feature=shared
The American Climate Leadership Awards 2024 broadcast recording is now available on ecoAmerica's YouTube channel for viewers to be inspired by active climate leaders. Watch to find out which finalist received the $50,000 grand prize! Hosted by Vanessa Hauc and featuring Bill McKibben and Katharine Hayhoe!
#ACLA24#ACLA24Leaders#youtube#youtube video#climate leaders#climate solutions#climate action#climate and environment#climate#climate change#climate and health#climate blog#climate justice#climate news#weather and climate#environmental news#environment#environmental awareness#environment and health#environmental#environmental issues#environmental justice#environment protection#environmental health#Youtube
15K notes
·
View notes
Text
Adobe steals your color

When a company breaks a product you rely on — wrecking decades of work — it’s natural to feel fury. Companies know this, so they try to deflect your rage by blaming their suppliers. Sometimes, it’s suppliers who are at fault — but other times, there is plenty of blame to go around.
For example, when Apple deleted all the working VPNs from its Chinese App Store and backdoored its Chinese cloud servers, it blamed the Chinese government. But the Chinese state knew that Apple had locked its devices so that its Chinese customers couldn’t install third-party apps.
That meant that an order to remove working VPNs and apps that used offshore clouds from the App Store would lock Apple customers into Chinese state surveillance. The order to block privacy tools was a completely foreseeable consequence of Apple’s locked-down “ecosystem.”
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
In 2013, Adobe started to shift its customers to the cloud, replacing apps like Photoshop and Illustrator with “Software as a Service” (“SaaS”) versions that you would have to pay rent on, every month, month after month, forever. It’s not hard to understand why this was an attractive proposition for Adobe!
Adobe, of course, billed its SaaS system as good for its customers — rather than paying thousands of dollars for its software up front, you could pay a few dollars (anywhere from $10-$50) every month instead. Eventually, of course, you’d end up paying more, assuming these were your professional tools, which you expected to use for the rest of your life.
For people who work in prepress, a key part of their Adobe tools is integration with Pantone. Pantone is a system for specifying color-matching. A Pantone number corresponds to a specific tint that’s either made by mixing the four standard print colors (cyan, magenta, yellow and black, AKA “CMYK”), or by applying a “spot” color. Spot colors are added to print jobs after the normal CMYK passes — if you want a stripe of metallic gold or a blob of hot pink, you specify its Pantone number and the printer loads up a separate ink and runs your media through its printer one more time.
Pantone wants to license this system out, so it needs some kind of copyrightable element. There aren’t many of these in the Pantone system! There’s the trademark, but that’s a very thin barrier. Trademark has a broad “nominative use” exception: it’s not a trademark violation to say, “Pantone 448C corresponds to the hex color #4a412a.”
Perhaps there’s a copyright? Well yes, there’s a “thin” database copyright on the Pantone values and their ink equivalents. Anyone selling a RIP or printer that translates Pantone numbers to inks almost certainly has to license Pantone’s copyright there. And if you wanted to make an image-editing program that conveyed the ink data to a printer, you’d best take a license.
All of this is suddenly relevant because it appears that things have broken down between Adobe and Pantone. Rather than getting Pantone support bundled in with your Adobe apps, you must now pay $21/month for a Pantone plugin.
https://twitter.com/funwithstuff/status/1585850262656143360
Remember, Adobe’s apps have moved to the cloud. Any change that Adobe makes in its central servers ripples out to every Adobe user in the world instantaneously. If Adobe makes a change to its apps that you don’t like, you can’t just run an older version. SaaS vendors like to boast that with cloud-based apps, “you’re always running the latest version!”
The next version of Adobe’s apps will require you to pay that $21/month Pantone fee, or any Pantone-defined colors in your images will render as black. That’s true whether you created the file last week or 20 years ago.
Doubtless, Adobe will blame Pantone for this, and it’s true that Pantone’s greed is the root cause here. But this is an utterly foreseeable result of Adobe’s SaaS strategy. If Adobe’s customers were all running their apps locally, a move like this on Pantone’s part would simply cause every affected customer to run older versions of Adobe apps. Adobe wouldn’t be able to sell any upgrades and Pantone wouldn’t get any license fees.
But because Adobe is in the cloud, its customers don’t have that option. Adobe doesn’t have to have its users’ backs because if it caves to Pantone, users will still have to rent its software every month, and because that is the “latest version,” those users will also have to rent the Pantone plugin every month — forever.
What’s more, while there may not be any licensable copyright in a file that simply says, “Color this pixel with Pantone 448C” (provided the program doesn’t contain ink-mix descriptions), Adobe’s other products — its RIPs and Postscript engines — do depend on licensable elements of Pantone, so the company can’t afford to tell Pantone to go pound sand.
Like the Chinese government coming after Apple because they knew that any change that Apple made to its service would override its customers’ choices, Pantone came after Adobe because they knew that SaaS insulated Adobe from its customers’ wrath.
Adobe customers can’t even switch to its main rival, Figma. Adobe’s just dropped $20b to acquire that company and ensure that its customers can’t punish it for selling out by changing vendors.
Pantone started out as a tech company: a way to reliably specify ink mixes in different prepress houses and print shops. Today, it’s an “IP” company, where “IP” means “any law or policy that allows me to control the conduct of my customers, critics or competitors.”
https://locusmag.com/2020/09/cory-doctorow-ip/
That’s likewise true of Adobe. The move to SaaS is best understood as a means to exert control over Adobe’s customers and competitors. Combined with anti-competitive killer acquisitions that gobble up any rival that manages to escape this control, and you have a hostage situation that other IP companies like Pantone can exploit.
A decade or so ago, Ginger Coons created Open Colour Standard, an attempt to make an interoperable alternative to Pantone. Alas, it seems dormant today:
http://adaptstudio.ca/ocs/
Owning colors is a terrible idea and technically, it’s not possible to do so. Neither UPS Brown nor John Deere Green are “owned” in any meaningful sense, but the companies certainly want you to believe that they are. Inspired by them and Pantone, people with IP brain-worms keep trying to turn colors into property:
https://onezero.medium.com/crypto-copyright-bdf24f48bf99
The law is clear that colors aren’t property, but by combining SaaS, copyright, trademark, and other tech and policies, it is becoming increasingly likely that some corporation will stealing the colors out from under our very eyes.
[Image ID: A Pantone swatchbook; it slowly fades to grey, then to black.]
505 notes
·
View notes
Text
Wage Transparency
Numerous states and some cities now require employers to disclose pay scales, salaries and wage information for existing and potential employees. The applicable jurisdictions continue to proliferate so many companies have simply decided to provide this information in every market. In my experience, the company established such broad salary ranges that the information wasn't particularly helpful, however it did require the company to address the compensation for those few individuals who, for whatever reason, fell below the minimum of the range.
Too much granularity of salary information can, of course, cause conflict with an organization but in general I think more transparency is better than less.
Very early in my career I was given responsibility for the annual budget process. This was before online budget software was available, so I created a very sophisticated (for that time) Excel model with VBA routines, etc. Each manager was given an excel file with the historical costs/revenues for their department and provided with instructions on how to complete the budget for each line item. In order to calculate the correct payroll taxes, etc. managers were instructed to enter the name, salary and bonus of each of their employees. This Excel sheet was then hidden and password protected.
You can probably guess the rest of story. This was before Excel had really strong password and encryption features, so I had a backdoor to the payroll sheet and when all the files were submitted, I could see every employee's salary and bonus.
Seeing which functions were paid the most was extremely motivating and ultimately guided the next decade of my career. I knew exactly what job I wanted and how much to negotiate for my compensation. Beth and I were willing to make the necessary sacrifices (including relocating 3 times) because it would be worth it.
Rather than bitching that I was paid too little, I was motivated to do what it took to get the better paying job. I wonder what would happen if companies were more transparent about their payroll.
33 notes
·
View notes
Text
This Week in Rust 542
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.77.2
Security advisory for the standard library (CVE-2024-24576)
Changes to Rust's WASI targets
Rust Nation UK
Hannah Aubrey - A Web of Rust: The Future of the Internet Depends on Trust
JD Nose - Rust Infrastructure: What it takes to keep Rust running
Amanieu D'Antras - The path to a stable ABI for Rust
Luca Palmieri - Pavex: re-imaging API development in Rust
Lachezar Lechev - Typed for Safety
Marco Concetto Rudilosso - Building a profiler for web assembly
Jon Gjengset - Towards Impeccable Rust
Nicholas Yang - Porting Turborepo From Go To Rust
David Haig - What’s that behind your ear? An open source hearing aid in Rust.
Frédéric Ameye - Renault want to sell cars with rust!
Nikita Lapkov - Type-safe and fault-tolerant mesh services with Rust
Andre Bogus - Easy Mode Rust
Lars Bergstrom - Beyond Safety and Speed: How Rust Fuels Team Productivity
Tim McNamara - Unwrapping unsafe
Nicholas Matsakis - Rust 2024 and beyond
Project/Tooling Updates
Shipping Jco 1.0, WASI 0.2
This month in Pavex, #10
"Containerize" individual functions in Rust with extrasafe
rust-analyzer changelog #228
Rerun 0.15.0 - Blueprints from Python · rerun-io/rerun
Bevy 0.13.2, Curves, Gizmos, and Games
What's new in SeaORM 1.0-rc.x
Observations/Thoughts
Improve performance of you Rust functions by const currying
Ownership in Rust
Thoughts on the xz backdoor: an lzma-rs perspective
hyper HTTP/2 Continuation Flood
Leaky Abstractions and a Rusty Pin
[audio] Launching RustRover: JetBrains' Investment in Rust
[audio] Pavex with Luca Palmieri
[video] Decrusting the tokio crate
[video] Rust 1.77.0: 70 highlights in 30 minutes
[video] Simulate the three body problem in #rustlang
[video] Exploring Fiberplane's 3-Year Rust Journey - with Benno van den Berg
Rust Walkthroughs
Working with OpenAPI using Rust
Zed Decoded: Async Rust
Writing a Unix-like OS in Rust
Fivefold Slower Compared to Go? Optimizing Rust's Protobuf Decoding Performance
Write Cleaner, More Maintainable Rust Code with PhantomData
[video] Extreme Clippy for an existing Rust Crate
[video] developerlife.com - Build a color gradient animation for a spinner component, for CLI, in Rust
[video] developerlife.com - Build a spinner component, for CLI, in Rust
[video] developerlife.com - Build an async readline, and spinner in Rust, for interactive CLI
Research
"Against the Void": An Interview and Survey Study on How Rust Developers Use Unsafe Code
Sound Borrow-Checking for Rust via Symbolic Semantics
Miscellaneous
Rust indexed - Rust mdbooks search
March 2024 Rust Jobs Report
Rust Meetup and user groups (updated)
Embedding the Servo Web Engine in Qt
A memory model for Rust code in the kernel
Building Stock Market Engine from scratch in Rust (II)
Ratatui Received Funding: What's Next?
Crate of the Week
This week's crate is archspec-rs, a library to track system architecture aspects.
Thanks to Orhun Parmaksız for the suggestion!
Please submit your suggestions and votes for next week!
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No calls for testing were issued this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
If you are a Rust project owner and are looking for contributors, please submit tasks here.
CFP - Speakers
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
If you are an event organizer hoping to expand the reach of your event, please submit a link to the submission website through a PR to TWiR.
Updates from the Rust Project
431 pull requests were merged in the last week
CFI: change type transformation to use TypeFolder
CFI: fix ICE in KCFI non-associated function pointers
CFI: restore typeid_for_instance default behavior
CFI: support function pointers for trait methods
CFI: support non-general coroutines
MSVC targets should use COFF as their archive format
actually use the inferred ClosureKind from signature inference in coroutine-closures
add Ord::cmp for primitives as a BinOp in MIR
add a debug asserts call to match_projection_projections to ensure invariant
add aarch64-apple-visionos and aarch64-apple-visionos-sim tier 3 targets
add consistency with phrases "meantime" and "mean time"
assert FnDef kind
assert that args are actually compatible with their generics, rather than just their count
avoid ICEing without the pattern_types feature gate
avoid expanding to unstable internal method
avoid panicking unnecessarily on startup
better reporting on generic argument mismatchs
cleanup: rename HAS_PROJECTIONS to HAS_ALIASES etc
do not ICE in fn forced_ambiguity if we get an error
do not ICE on field access check on expr with ty::Error
do not ICE when calling incorrectly defined transmute intrinsic
fix ByMove coroutine-closure shim (for 2021 precise closure capturing behavior)
fix capture analysis for by-move closure bodies
fix diagnostic for qualifier in extern block
hir: use ItemLocalId::ZERO in a couple more places
impl get_mut_or_init and get_mut_or_try_init for OnceCell and OnceLock
implement T-types suggested logic for perfect non-local impl detection
implement minimal, internal-only pattern types in the type system
instantiate higher ranked goals outside of candidate selection
link against libc++abi and libunwind as well when building LLVM wrappers on AIX
make inductive cycles always ambiguous
make sure to insert Sized bound first into clauses list
match ergonomics: implement "&pat everywhere"
match lowering: make false edges more precise
more postfix match fixes
move check for error in impl header outside of reporting
only allow compiler_builtins to call LLVM intrinsics, not any link_name function
only inspect user-written predicates for privacy concerns
pass list of defineable opaque types into canonical queries
pattern analysis: fix union handling
postfix match fixes
privacy: stabilize lint unnameable_types
put checks that detect UB under their own flag below debug_assertions
revert removing miri jobserver workaround
safe Transmute: Compute transmutability from rustc_target::abi::Layout
sanitizers: create the rustc_sanitizers crate
split hir ty lowerer's error reporting code in check functions to mod errors
teach MIR inliner query cycle avoidance about const_eval_select
transforms match into an assignment statement
use the more informative generic type inference failure error on method calls on raw pointers
add missing ?Sized bounds for HasInterner impls
introduce Lifetime::Error
perf: cache type info for ParamEnv
encode dep graph edges directly from the previous graph when promoting
remove debuginfo from rustc-demangle too
stabilize const_caller_location and const_location_fields
stabilize proc_macro_byte_character and proc_macro_c_str_literals
stabilize const Atomic*::into_inner
de-LLVM the unchecked shifts
rename expose_addr to expose_provenance
rename ptr::from_exposed_addr → ptr::with_exposed_provenance
remove rt::init allocation for thread name
use unchecked_sub in str indexing
don't emit divide-by-zero panic paths in StepBy::len
add fn const BuildHasherDefault::new
add invariant to VecDeque::pop_* that len < cap if pop successful
add Context::ext
provide cabi_realloc on wasm32-wasip2 by default
vendor rustc_codegen_gcc
cargo: Build script not rerun when target rustflags change
cargo add: Stabilize MSRV-aware version req selection
cargo toml: Decouple target discovery from Target creation
cargo toml: Split out an explicit step to resolve Cargo.toml
cargo metadata: Show behavior with TOML-specific types
cargo: don't depend on ? affecting type inference in weird ways
cargo: fix github fast path redirect
cargo: maintain sorting of dependency features
cargo: switch to using gitoxide by default for listing files
rustdoc-search: shard the search result descriptions
rustdoc: default to light theme if JS is enabled but not working
rustdoc: heavily simplify the synthesis of auto trait impls
rustdoc: synthetic auto trait impls: accept unresolved region vars for now
clippy: manual_swap auto fix
clippy: manual_unwrap_or_default: check for Default trait implementation in initial condition when linting and use IfLetOrMatch
clippy: allow cast lints in macros
clippy: avoid an ICE in ptr_as_ptr when getting the def_id of a local
clippy: correct parentheses for needless_borrow suggestion
clippy: do not suggest assigning_clones in Clone impl
clippy: fix ice reporting in lintcheck
clippy: fix incorrect suggestion for !(a as type >= b)
clippy: reword arc_with_non_send_sync note and help messages
clippy: type certainty: clear DefId when an expression's type changes to non-adt
rust-analyzer: apply cargo flags in test explorer
rust-analyzer: fix off-by-one error converting to LSP UTF8 offsets with multi-byte char
rust-analyzer: consider exported_name="main" functions in test modules as tests
rust-analyzer: fix patch_cfg_if not applying with stitched sysroot
rust-analyzer: set the right postfix snippets competion source range
Rust Compiler Performance Triage
A quiet week; all the outright regressions were already triaged (the one biggish one was #122077, which is justified as an important bug fix). There was a very nice set of improvements from PR #122070, which cleverly avoids a lot of unnecessary allocator calls when building an incremental dep graph by reusing the old edges from the previous graph.
Triage done by @pnkfelix. Revision range: 3d5528c2..86b603cd
3 Regressions, 3 Improvements, 7 Mixed; 1 of them in rollups 78 artifact comparisons made in total
See full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Merge RFC 3513: Add gen blocks
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
[disposition: merge] RFC: Drop temporaries in tail expressions before local variables
[disposition: merge] RFC: Reserve unprefixed guarded string literals in Edition 2024
Tracking Issues & PRs
Rust
[disposition: merge] Always display stability version even if it's the same as the containing item
[disposition: merge] Tracking Issue for cstr_count_bytes
[disposition: merge] rustdoc-search: single result for items with multiple paths
[disposition: merge] Tracking Issue for #![feature(const_io_structs)]
[disposition: merge] Tracking Issue for alloc::collections::BinaryHeap::as_slice
[disposition: merge] Tracking Issue for fs_try_exists
[disposition: merge] stabilize -Znext-solver=coherence
[disposition: merge] Document overrides of clone_from() in core/std
[disposition: merge] Stabilise inline_const
[disposition: merge] Tracking Issue for RFC 3013: Checking conditional compilation at compile time
[disposition: merge] sess: stabilize -Zrelro-level as -Crelro-level
[disposition: merge] Implement FromIterator for (impl Default + Extend, impl Default + Extend)
[disposition: close] Return the delimiter from slice::split_once
[disposition: merge] Support type '/' to search
[disposition: merge] Tracking Issue for Seek::seek_relative
[disposition: merge] Tracking Issue for generic NonZero
New and Updated RFCs
[new] Add an expression for direct access to an enum's discriminant
[new] RFC: Drop temporaries in tail expressions before local variables
Upcoming Events
Rusty Events between 2024-04-10 - 2024-05-08 🦀
Virtual
2024-04-11 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-11 | Virtual (Nürnberg, DE) | Rust Nüremberg
Rust Nürnberg online
2024-04-11 | Virtual (San Diego, CA, US) | San Diego Rust
San Diego Rust April 2024 Tele-Meetup
2024-04-15 & 2024-04-16 | Virtual | Mainmatter
Remote Workshop: Testing for Rust projects – going beyond the basics
2024-04-16 | Virtual (Dublin, IE) | Rust Dublin
A reverse proxy with Tower and Hyperv1
2024-04-16 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful—forensic parsing via Artemis
2024-04-17 | Virtual | Rust for Lunch
April 2024 Rust for Lunch
2024-04-17 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Reflections on RustNation UK 2024
2024-04-17 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-04-18 | Virtual (Charlottesville, VA, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-04-21 | Virtual (Israel) | Rust in Israel
Using AstroNvim for Rust development (in Hebrew)
2024-04-25 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-30 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2024-05-01 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 5 - Project Structure
2024-05-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2024-05-02 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-05-07 | Virtual (Buffalo, NY) | Buffalo Rust Meetup
Buffalo Rust User Group
Africa
2024-05-04 | Kampala, UG | Rust Circle Kampala
Rust Circle Meetup
Asia
2024-04-16 | Tokyo, JP | Tokyo Rust Meetup
The Good, the Bad, and the Async (RSVP by 15 Apr)
Europe
2024-04-10 | Cambridge, UK | Cambridge Rust Meetup
Rust Meetup Reboot 3
2024-04-10 | Cologne/Köln, DE | Rust Cologne
This Month in Rust, April
2024-04-10 | Manchester, UK | Rust Manchester
Rust Manchester April 2024
2024-04-10 | Oslo, NO | Rust Oslo
Rust Hack'n'Learn at Kampen Bistro
2024-04-11 | Bordeaux, FR | Rust Bordeaux
Rust Bordeaux #2 : Présentations
2024-04-11 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2024-04-15 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2024/04: Building cargo projects with NIX
2024-04-16 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake #5
2024-04-16 | Leipzig, DE | Rust - Modern Systems Programming in Leipzig
winnow/nom
2024-04-16 | Munich, DE + Virtual | Rust Munich
Rust Munich 2024 / 1 - hybrid
2024-04-17 | Bergen, NO | Hubbel kodeklubb
Lær Rust med Conways Game of Life
2024-04-17 | Ostrava, CZ | TechMeetup Ostrava
TechMeetup: RUST
2024-04-20 | Augsburg, DE | Augsburger Linux-Infotag 2024
Augsburger Linux-Infotag 2024: Workshop Einstieg in Embedded Rust mit dem Raspberry Pico WH
2024-04-23 | Berlin, DE | Rust Berlin
Rust'n'Tell - Rust for the Web
2024-04-23 | Paris, FR | Rust Paris
Paris Rust Meetup #67
2024-04-25 | Aarhus, DK | Rust Aarhus
Talk Night at MFT Energy
2024-04-23 | Berlin, DE | Rust Berlin
Rust'n'Tell - Rust for the Web
2024-04-25 | Berlin, DE | Rust Berlin
Rust and Tell - TBD
2024-04-27 | Basel, CH | Rust Basel
Fullstack Rust - Workshop #2 (Register by 23 April)
2024-04-30 | Budapest, HU | Budapest Rust Meetup Group
Rust Meetup Budapest 2
2024-04-30 | Salzburg, AT | Rust Salzburg
[Rust Salzburg meetup]: 6:30pm - CCC Salzburg, 1. OG, ArgeKultur, Ulrike-Gschwandtner-Straße 5, 5020 Salzburg
2024-05-01 | Utrecht, NL | NL-RSE Community
NL-RSE RUST meetup
2024-05-06 | Delft, NL | GOSIM
GOSIM Europe 2024
2024-05-07 & 2024-05-08 | Delft, NL | RustNL
RustNL 2024
North America
2024-04-10 | Boulder, CO, US | Boulder Rust Meetup
Rust Meetup: Better Builds w/ Flox + Hangs
2024-04-11 | Lehi, UT, US | Utah Rust
Interactive Storytelling using Yarn Spinner with Rex Magana
2024-04-11 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-04-11 | Spokane, WA, US | Spohttps://www.meetup.com/minneapolis-rust-meetup/kane Rust
Monthly Meetup: The Rust Full-Stack Experience
2024-04-15 | Minneapolis, MN, US | Minneapolish Rust Meetup
Minneapolis Rust: Getting started with Rust! #2
2024-04-15 | Somerville, MA, US | Boston Rust Meetup
Davis Square Rust Lunch, Apr 15
2024-04-16 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-04-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group: Meet Servo and Robius Open Source Projects
2024-04-18 | Chicago, IL, US | Deep Dish Rust
Rust Talk: What Are Panics?
2024-04-18 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-04-24 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2024-04-25 | Nashville, TN, US | Music City Rust Developers
Music City Rust Developers - Async Rust on Embedded
2024-04-26 | Boston, MA, US | Boston Rust Meetup
North End Rust Lunch, Apr 26
Oceania
2024-04-15 | Melbourne, VIC, AU | Rust Melbourne
April 2024 Rust Melbourne Meetup
2024-04-17 | Sydney, NSW, AU | Rust Sydney
WMaTIR 2024 Gala & Talks
2024-04-30 | Auckland, NZ | Rust AKL
Rust AKL: Why Rust? Convince Me!
2024-04-30 | Canberra, ACT, AU | Canberra Rust User Group
CRUG April Meetup: Generics and Traits
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
As a former JavaScript plebeian who has only been semi-recently illuminated by the suspiciously pastel pink, white and blue radiance of Rust developers, NOT having to sit in my web console debugger for hours pushing some lovingly crafted [object Object] or undefined is a blessing.
– Julien Robert rage-blogging against bevy
Thanks to scottmcm for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
1 note
·
View note
Text


Underdog is one of those popular characters who fell into obscurity in recent years. Now that "Underdog" is owned by Universal, I think there should be a CG reboot movie. Unlike the live action Disney film released in 2007, I would want Underdog's CG reboot to be more faithful to the cartoon (even though I never saw it). This film would be released in theaters in 2D, 3D, IMAX (2D and 3D), and 4DX (2D and 3D)
Up above is how I would envision an "Underdog" movie poster. I have a blank one for those who want to try better than what I have done. You can view the older versions of my movie poster concept art on this page.
PRODUCTION COMPANIES
Illumination
DreamWorks Animation
DISTRIBUTOR
Universal Pictures
RATING
Obviously, PG, moving on.
ANIMATION
In terms of the animation, I wasn't sure if the CG should be fluent or stop-motion like, similar to some scenes in "Puss in Boots 2: The Last Wish", but I was thinking that the same people who worked on "Mr. Peabody and Sherman" could try animating the characters. It could even be the first time Underdog, Sweet Polly Purebred, and other animal characters have actual fur. "How the Grinch Stole Christmas (2018)" also showed us how good hair and fur could work on CG characters.
OPENING LOGO VARIANTS
For the Universal Pictures logo, have Underdog fly around the earth as the letters spelling "UNIVERSAL" follow him (Assuming Underdog can breathe in Space).
The Illumination logo would feature the minions jumping off the Illumination logo and trying to fly, only for them to just plummet to the ground.
And for the DreamWorks Animation logo, I was thinking make Underdog 2D animated (with either traditional or flash animation). And after Underdog fishes on the moon, he would jump off the moon and fly through the clouds transitioning from 2D to his 3D design we see in the movie.
The title for the film itself would appear at the beginning and end of the movie. The end credits themselves would be 2D animated.
STORY CONCEPT
What I had in mind was if Dr. Simon Bar Sinister teamed up with Underdog's nemeses and formed a legion too powerful for Underdog to take on by himself. In fact, Underdog himself could get a team of his own consisting of other animal superheroes like him. And after putting Dr. Simon Bar Sinister and his legion behind bars, the movie would end with Underdog starting his new job at a superhero headquarters, which serves as the backdoor pilot for a TV show based on my movie idea.
CLOSING LOGO VARIANTS
After the credits (and post-credits scenes depending on if we'll get any) and the closing Universal and Illumination logos, Underdog would fly back onto the moon of the DreamWorks Animation logo and continue fishing until the screen fades to black.
TELEVISION SERIES BASED ON THE MOVIE
The TV series based on the movie would continue from the ending of the movie, and in addition to seeing more of Underdog in action, some episodes focus on Underdog's new superhero friends. This show, I was thinking would return to its original 2D routes, but this time through flash-animated software like Toon Boom Harmony, or something similar to that.
#321SPONGEBOLT's Ideas#Underdog#underdog cartoon#movie concept#movie idea#movie poster#movie posters#movie poster concept#fanmade poster#fanmade movie poster#fanmade movie posters
1 note
·
View note
Text
youtube
Watch the 2024 American Climate Leadership Awards for High School Students now: https://youtu.be/5C-bb9PoRLc
The recording is now available on ecoAmerica's YouTube channel for viewers to be inspired by student climate leaders! Join Aishah-Nyeta Brown & Jerome Foster II and be inspired by student climate leaders as we recognize the High School Student finalists. Watch now to find out which student received the $25,000 grand prize and top recognition!
#ACLA24#ACLA24HighSchoolStudents#youtube#youtube video#climate leaders#climate solutions#climate action#climate and environment#climate#climate change#climate and health#climate blog#climate justice#climate news#weather and climate#environmental news#environment#environmental awareness#environment and health#environmental#environmental issues#environmental education#environmental justice#environmental protection#environmental health#high school students#high school#youth#youth of america#school
16K notes
·
View notes
Text
I've fucked up so bad with jobs and stuff. I don't know what I'm going to do. I guess hopefully I'll be able to get in to some of those programs again when I reapply next year. So the present interregnum won't be forever. But even that is a miserable, despairing hail mary. And in between, if I can't make something work, I'll lose the place I live, I'll be humiliated.
I'll be humiliated anyway, I guess. Every possible future is just soaked in the indignity of humiliating failure. I couldn't make it in software. I'm spending all my time, as if by compulsion, on this worthless vile creative pursuit, which practically by definition can't turn out as anything but failure. And then all I can think of to do is to put myself in debt going to a humiliating professional program (! not even real grad school!) in a bullshit subject that I don't care about anyway, as a means to try to backdoor my way into some prestigious research experience in another bullshit field I don't care about anyway, so that I can waste even more time in school because I am a worthless bug and my life has no value.
There's no plan. It all just spirals into oblivion
0 notes
Text
APT-Gruppe Lazarus steckt hinter Cyberangriff auf 3CX

Mit der Operation DreamJob griff die APT (Advanced Persistent Threat)-Gruppe Lazarus erstmals auch gezielt Linux-Nutzer an. Prominentestes Opfer ist der VoIP-Software-Entwickler 3CX. Die ESET Experten entdecken Verbindung zum Cyberangriff auf 3CX.
Die Forscher des IT-Sicherheitsherstellers ESET konnten den kompletten Ablauf der Operation rekonstruieren und so nachweisen, dass die mit Nordkorea verbündeten Hacker hinter den sogenannten Supply Chain-Angriffen („Lieferkettenangriff“) stecken. Das Unheil nimmt mit einem gefälschten Jobangebot als Zip-Datei seinen hinterhältigen Lauf und endet mit der Schadsoftware SimplexTea. Die Linux-Backdoor wird über ein OpenDrive-Konto verteilt.
3CX: Es war Lazarus aus Nordkorea
„Nach unseren jüngsten Entdeckungen haben wir weitere stichhaltige Beweise gefunden, dass die Lazarus-Gruppe hinter dem Supply Chain-Angriff auf 3CX steckt. Diese Verbindung wurde von Anfang an vermutet und seitdem von mehreren Sicherheitsforschern nachgewiesen“, sagt ESET Forscher Peter Kálnai. „Diese kompromittierte Software, die in verschiedenen IT-Infrastrukturen eingesetzt wird, ermöglicht das Herunterladen und Ausführen jeglicher Art von Nutzdaten, die verheerende Auswirkungen haben können. Die Heimlichkeit eines Supply Chain-Angriffs macht diese Methode der Malware-Verbreitung aus Sicht der Angreifer sehr attraktiv. Lazarus hat diese Technik bereits in der Vergangenheit eingesetzt“, erklärt Kálnai. „Interessant ist auch, dass Lazarus native Malware für alle wichtigen Desktop-Betriebssysteme produzieren und nutzen kann: Windows, macOS und Linux.“
Start mit verseuchtem Jobangebot per E-Mail
Operation DreamJob ist der Name für eine Reihe von Kampagnen, bei denen Lazarus Social-Engineering-Techniken einsetzt, um seine Ziele zu kompromittieren. Dabei dienen gefälschte Jobangebote als Köder. Am 20. März übermittelte ein Benutzer in Georgien ein ZIP-Archiv mit dem Namen „HSBC job offer.pdf.zip“ an VirusTotal. Angesichts anderer DreamJob-Kampagnen von Lazarus wurde dieses Schadprogramm wahrscheinlich über Spearphishing oder Direktnachrichten auf LinkedIn verbreitet. Das Archiv enthält eine einzige Datei: eine native 64-Bit-Intel-Linux-Binärdatei, die in Go geschrieben wurde und „HSBC job offer․pdf“ heißt.
Die Täter hatten die Angriffe lange vor der Ausführung geplant - bereits im Dezember 2022. Dies lässt darauf schließen, dass sie bereits Ende letzten Jahres im Netzwerk von 3CX Fuß gefasst hatten. Einige Tage vor dem Bekanntwerden des Angriffs wurde ein mysteriöser Linux-Downloader bei VirusTotal eingereicht. Er lädt eine neue Lazarus-Backdoor für Linux namens SimplexTea herunter, die eine Verbindung zu demselben Command & Control-Server herstellt wie die Payloads, die beim 3CX-Angriff verwendet wurden.
Was ist ein Supply-Chain-Angriff
Supply Chain-Angriffe stehen bei Hackern hoch im Kurs. Der Begriff beschreibt Angriffsszenarien, bei denen Cyberkriminelle in den Herstellungsprozess oder Entwicklungszyklus einer Software eingreifen oder ihn übernehmen. So erhalten Endverbraucher eines Produkts unter Umständen manipulierte Updates für die eingesetzte Software.
Über den Angriff auf 3CX
Das Unternehmen bietet Client-Software zur Nutzung seiner Systeme über einen Webbrowser, eine mobile App oder Desktop-Anwendung an. Ende März 2023 wurde entdeckt, dass die Desktop-Anwendung sowohl für Windows als auch für macOS bösartigen Code enthielt. Dieser ermöglichte es Angreifern, beliebigen Code auf alle Rechner herunterzuladen und auszuführen, auf denen die Anwendung installiert war. 3CX selbst wurde kompromittiert und dessen Software in einem Supply Chain-Angriff verwendet, um zusätzliche Malware an bestimmte 3CX-Kunden zu verteilen.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Text
Real Amazing Spider-Man #1
Real Amazing Spider-Man Issue 1#
21:00 August 2023
Stark Villa Honolulu, Hawaii
Earth 616.
Peter Parker opens the Villa door and carries Mary Jane Watson. A five-year-old girl rushes past them and turns on the television, and sits on a leather sofa in front of the television.
"You are enjoying this, aren't you?" asked Peter
"Tiger, don't you know it?" Mary Jane Watson said.
"It would be a shame to wear the same clothes the whole two weeks we stay in Stark's villa," said Peter, putting down Mary Jane Watson.
"I have to say, Tiger, it was n I have to say, Tiger, it was gracious of Tony to let us stay at his villa for a two-week vacation," said Mary Jane.
"Technically, it's a working holiday, honey, as Tony believes that AIM could attack the villa and use it to get a backdoor into his system," said Peter.
"How much is Stark paying us to protect his system?" asked Mary Jane Watson.
"Enough to get our wedding rings back from the pawnshop and for the next two months' rent on the apartment," said Peter.
"As long as our bills don't increase anymore, I know this is a working holiday for you, Tiger. However, it's finally pleasant to have a holiday as husband and wife since Annie's birth and aunt May's," said Mary Jane.
"I know, hopefully after we get back to New York, I can teach at Midtown High," said Peter
"Do you think you aced the interview?" Mary Jane asked. I think so, but they might turn me in for all the missed days I was employed previously, as well as the fake doctorate Otto got me, said Peter.
"I'm sure Tony would give you a job if you asked," Mary Jane replied.
"I know he would, but I think he still blames me for Jarvis quitting his job after May's death. Did I do the right thing by unmasking during the civil war?" asked Peter.
"You know that May and I both supported this decision. You are not to blame Fisk for capitalising on it and trying to kill you but for killing May instantly. I am preparing to call the airline to see if they can tell us where our bags are. This is Mary Jane Watson as she removes her cell phone from a coat pocket. Goes onto the Villa balcony as Annie plays on her Nintendo Switch.
Mary Jane Watson walks around the balcony, talking on her cell phone. She does not see someone watching the Villa through Binoculars
"Hello, I am calling to inquire about our lost bags," said Mary Jane Watson.
"Hi, this is Adam, a customer service representative for American Airlines customer support. We have done some research regarding your bags, Mrs Parker, and we can confirm that your bags have reached your destination in Germany." said a male voice.
"How the hell have you sent our bags to Germany when we were booked on a flight from JFK to Hawaii?" asked Mary Jane.
"Because of a massive software system glitch, someone has mistakenly placed all luggage belonging to you and your fellow Hawaii passengers on your flight," said Adam, referring to the mistake.
"How are I and my family going to get our bags?" Mary Jane asked.
"Unfortunately, because of a three-day airport strike, we cannot pick up and transport your missing bags since there is no flight scheduled to Hawaii for another eight days," Adam explained.
"What the hell am I going to do for eleven days without my luggage?" asked Mary Jane
"Upon making a claim to our claims department for all missing luggage, we will send you $1,500. We will send the money to your home address within twenty-eight days," replied Adam.
"Yeah, but that doesn't help us when we are in Hawaii for two weeks," said Mary Jane.
"Our company policy is to send all checks to customers' registered addresses," Adam explained.
"Fine, if I make a claim to the claims department will you be able to hold our missing luggage at JFK once we return to the United States?" asked Mary Jane Watson.
"We cannot promise anything, Mrs Parker, but there is a chance we can arrange for you to pick up your missing luggage; once we arrange collection of unclaimed luggage, we will only hold unclaimed luggage for two weeks before selling it at auction," said Adam.
"Can you put me through to the claims department so I can make a claim?" asked Mary Jane Watson.
"The claims department phone lines are currently closed and will not open until 9:00 am tomorrow morning. If you would like a reference for quick claims processing, please have a Pen and Paper reference number 09081969CJ. Can you help me with anything, Mrs Parker?" Adam asked.
"Thanks, Adam," said Mary Jane, ending the phone call. In frustration, she crushed her cell phone and said, "Oh crap, I'm going to need another one." She dropped many pieces of her cell phone as Peter joined her on the balcony.
"I am guessing the call was productive with the customer services department, so where are our bags?" asked Peter.
"Oh, our bags are currently somewhere in Germany, and American Airlines won't be able to deliver them to us for eleven more days," said Mary Jane
"How the hell did that happen then?" asked Peter
"Customer associate said they had a computer glitch that caused Hawaii-bound passenger bags to be put on the Germany plane while the Germany-bound bags got put on the Hawaii flight; they will pay us the compassion but will send a check in the next twenty-eight days," said Mary Jane Watson.
"So we are stuck in the clothes we came in?" asked Peter.
"Afraid so, Tiger," said Mary Jane. She looked at Peter, removed a small box, knelt down on one knee and opened it to reveal a Spider Tracer and a gold chain.
"Happy Birthday," said Peter.
"Is this your most effective attempt to join you as a superhero Tiger?" Mary Jane Watson asked.
"Yes, but I know you are not keen on being a superhero after the Spider-Island incident. However, why can it activate a Spider-Suit for you? Holding the centre of the Spider Tracer will create a nanotech spider-woman-like costume for you to fight in. You can all press it once it triggers my Spider-Sense and allows me to track your location should a villain kidnap you," said Peter as he got up and placed it around Mary Jane's neck.
"It's beautiful, Tiger. I love it; what's the battery life?" asked Mary Jane.
"Long enough for me to find you," said Peter.
02:00 hours
Warehouse
Honolulu, Hawaii
Five men and one woman are gathered around a table with blueprints of the Stark Villa with pictures of Mary Jane Watson Parker, Annie Parker and Peter Parker.
Stark hired housesitters. Will this cause a problem?” asked the group leader.
“Not at all, sir,” the other team members said as they studied the Stark Villa blueprints.
“Sabrina, your job once we get into the Villa is hacking into Stark Industries,” said the group leader.
“That's fine with me as long as I can kill Peter Parker. This is because he led the woman I love to be killed by Spider-Man, so this is not an issue for me,” Sabrina replied. She was a white woman with a black pixie-style haircut with blonde streaks running through it. She had brown and green eyes. She was wearing denim jeans, a pair of black boots, a pink T-shirt, and a black denim jacket and wearing a pair of glasses as she was looking at a picture of Gwen Stacy in a locket around her neck.
"fine by me, Hacker, as long as you gain access to the Stark mainframe," said the team leader.
"You have access. I'm not jeopardising the mission," said Sabrina.
End
0 notes
Photo
Anomali Cyber Watch: Aggressively-Mutating Mantis Backdoors Target Palestine, Fake Cracked Packages Flood NPM, Rorschach Ransomware Is Significantly Faster Than LockBit v.3
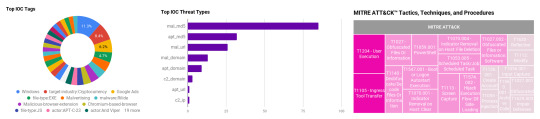
The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Cryptocurrency, Data leak, Malvertising, Packers, Palestine, Phishing, Ransomware, and Software supply chain. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity. Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed. Trending Cyber News and Threat Intelligence CryptoClippy Speaks Portuguese (published: April 5, 2023) Since at least early 2022, an opportunistic cryptocurrency clipper campaign has been targeting Portuguese speakers by prompting a download from an actor-controlled website promoted via SEO poisoning and malvertising abusing Google Ads. The file impersonates WhatsApp Web and delivers malware dubbed CryptoClippy with the aim of replacing cryptocurrency addresses in the target’s clipboard. The first two files in the infection chain are either EXE and BAT or ZIP and LNK. The actors utilize extensive obfuscation and encryption (RC4 and XOR) techniques, log and file clearing, and thorough user profiling for narrow targeting and defense evasion. The use of the Invoke-Obfuscation obfuscation type may point to a Brazilian-based attacker. Analyst Comment: The observed actor-controlled wallets gained a little over 1,000 US Dollars, but their complex, multi-stage malware can help them to extend this damage. Users are advised to verify the recipient information prior to sending a financial transaction. Indicators related to CryptoClippy are available in the Anomali platform. Organizations that publish applications for their customers are invited to use Anomali Premium Digital Risk Protection to discover rogue, malicious apps impersonating your brand that security teams typically do not search or monitor. MITRE ATT&CK: [MITRE ATT&CK] T1204 - User Execution | [MITRE ATT&CK] T1027 - Obfuscated Files Or Information | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1105 - Ingress Tool Transfer | [MITRE ATT&CK] T1140 - Deobfuscate/Decode Files Or Information | [MITRE ATT&CK] T1620 - Reflective Code Loading | [MITRE ATT&CK] T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] T1136.001 - Create Account: Local Account | [MITRE ATT&CK] T1070.001 - Indicator Removal on Host: Clear Windows Event Logs | [MITRE ATT&CK] T1070.004 - Indicator Removal on Host: File Deletion | [MITRE ATT&CK] T1055 - Process Injection | [MITRE ATT&CK] T1053.005 - Scheduled Task/Job: Scheduled Task Tags: malware:CryptoClippy, malware-type:Clipper, Google Ads, Traffic distribution system, SEO poisoning, WhatsApp, file-type:ZIP, file-type:EXE, file-type:LNK, file-type:BAT, RDP, RC4, XOR, PowerShell, target-industry:Cryptocurrency, Ethereum, Bitcoin, source-country:Brazil, source-country:BR, Character padding, Invoke-Obfuscation, Windows Mantis: New Tooling Used in Attacks Against Palestinian Targets (published: April 4, 2023) The Mantis (Arid Viper, Desert Falcon, APT-C-23) advanced persistent threat is a Palestine-associated group that has been observed since 2011. In September 2022 - February 2023, Mantis engaged in a new campaign targeting organizations within the Palestinian territories. The campaign featured versions of custom Micropsia and Arid Gopher backdoors, and a variety of additional tools including the Putty SSH client, and the SetRegRunKey.exe registry modification persistence tool. Mantis has been aggressively mutating the logic between variants of its backdoors, at times replacing versions in the course of an ongoing compromise. Analyst Comment: Historically, many Mantis attacks have started with spearhishing. It is important to teach your users basic online hygiene and phishing awareness. Pay attention to suspicious PowerShell executions, suspicious port connections (such as over port 4444), and signs of data exfiltration. All known Mantis indicators associated with this campaign are available in the Anomali platform and customers are advised to block these on their infrastructure. MITRE ATT&CK: [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1105 - Ingress Tool Transfer | [MITRE ATT&CK] T1113 - Screen Capture | [MITRE ATT&CK] T1056.001 - Input Capture: Keylogging | [MITRE ATT&CK] T1560.001 - Archive Collected Data: Archive Via Utility | [MITRE ATT&CK] T1027 - Obfuscated Files Or Information | [MITRE ATT&CK] T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder Tags: actor:Mantis, malware:Micropsia, malware-type:Backdoor, malware:Arid Gopher, PowerShell, PyArmor, Putty, SetRegRunKey.exe, actor:Arid Viper, actor:Desert Falcon, actor:APT-C-23, target-region:Palestine, source-region:Palestine, Cyberespionage, Data loss, Delphi, Golang, file-type:EXE, port:4444, Windows Who Broke NPM?: Malicious Packages Flood Leading to Denial of Service (published: April 4, 2023) Several campaigns likely operated by the same threat actor have targeted the npm JavaScript software registry with automated user account and package creation. In March 2023, it resulted in the number of monthly package versions released going from 800,000 to over 1.4 million, at times causing denial-of-service for the npm website. The threat actor has been creating malicious websites and publishing attractive cracked software-related package descriptions with links to those websites. The user would download and execute an inflated, zero-padded EXE file starting an infection chain disabling security tools and firewalls, utilizing DLL side-loading and virtualization/sandbox evasion. It delivers various commodity tools such as Glupteba, RedLine, Smoke Loader, xmrig and more to steal credentials and to mine cryptocurrency. Additional fraud monetization comes from scams using AliExpress referrals and cryptocurrency schemes in Russian-speaking Telegram groups. Analyst Comment: Open-source libraries and software supply chains are increasingly under attack. These campaigns are abusing the reputation of the npm code sharing environment to promote the malicious websites in search engines. As long as individuals continue to download cracked software, threat actors will continue using it as a distribution method. These types of downloads should be restricted by your company; supply the legitimate software and educate your employees about these risks. Network indicators associated with this recent npm targeting are available on the Anomali platform. MITRE ATT&CK: [MITRE ATT&CK] T1204 - User Execution | [MITRE ATT&CK] T1027.001 - Obfuscated Files or Information: Binary Padding | [MITRE ATT&CK] T1629.003 - Impair Defenses: Disable Or Modify Tools | [MITRE ATT&CK] T1633 - Virtualization/Sandbox Evasion | [MITRE ATT&CK] T1574.002 - Hijack Execution Flow: Dll Side-Loading | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1496 - Resource Hijacking | [MITRE ATT&CK] T1499 - Endpoint Denial Of Service Tags: npm, Spam, malware:Glupteba, malware:RedLine, malware-type:Infostealer, malware:Smoke Loader, detection:xmrig, malware-type:Miner, Open-source library, SEO, DoS, AliExpress, Referral scam, Software supply chain, Warez, Cracked, Telegram, target-country:Russia, target-country:RU, target-industry:Cryptocurrency, file-type:EXE, Windows Rorschach – A New Sophisticated And Fast Ransomware (published: April 4, 2023) In February-March 2023, a new ransomware family dubbed Rorschach was spotted in the wild. While being unique overall, Rorscharch borrowed from several advanced ransomware families. Its hybrid-cryptography and some other routines are inspired or copied from Babuk. Similar to LockBit 2.0, it can spread from Windows Domain Controller by automatically creating a domain group policy. Finally, Rorschach ransomware notes were formatted in some cases similar to DarkSide and similar to Yanluowang in others. Rorschach does not brand its notes, but its exemption for Commonwealth of Independent States shows its likely origin. To avoid detection, Rorschach uses direct syscalls by finding, storing and using relevant syscall numbers for NT APIs. Rorschach achieves extremely fast encryption due to effective cryptography scheme, partial file encryption, effective thread scheduling via I/O completion ports, and compiler optimization, with much of the code being inlined. Analyst Comment: Rorscharch’s ability to abuse a Palo Alto Networks security product, Cortex XDR Dump Service Tool, was reported to the vendor. Network defenders can consider setting up warning systems for new group policies, new scheduled tasks, and rogue encryption processes targeting honeypot/canary files. To constrain the autonomous capabilities of the ransomware, endpoint devices with admin privileges should be properly locked down, and a micro-segmentation of IT networks should be implemented where possible. Ransomware is a constantly evolving threat, and the most fundamental defense is having proper backup and restore processes in place that allows recovery without any need to decrypt the affected data. MITRE ATT&CK: [MITRE ATT&CK] T1486: Data Encrypted for Impact | [MITRE ATT&CK] T1490: Inhibit System Recovery | [MITRE ATT&CK] T1489 - Service Stop | [MITRE ATT&CK] T1070.001 - Indicator Removal on Host: Clear Windows Event Logs | [MITRE ATT&CK] T1070.004 - Indicator Removal on Host: File Deletion | [MITRE ATT&CK] T1053.005 - Scheduled Task/Job: Scheduled Task | [MITRE ATT&CK] T1027.002 - Obfuscated Files or Information: Software Packing | [MITRE ATT&CK] T1140 - Deobfuscate/Decode Files Or Information | [MITRE ATT&CK] T1574.002 - Hijack Execution Flow: Dll Side-Loading | [MITRE ATT&CK] T1484.001 - Domain Policy Modification: Group Policy Modification Tags: malware:Rorschach, malware-type:Ransomware, VMProtect, source-region:CIS, curve25519, eSTREAM cipher hc-128, I/O completion port, Thread scheduling, Domain group policy, Cortex XDR Dump Service Tool, Palo Alto Networks, target-country:USA, target-county:US, file-type:EXE, file-type:DLL, file-type:INI, Windows Rilide: A New Malicious Browser Extension for Stealing Cryptocurrencies (published: April 4, 2023) A new malicious extension dubbed Rilide targets cryptocurrency users on Chromium-based browsers. It was seen delivered through two infection chains: either starting with a malicious macros in a Publisher file delivering Ekipa RAT, or through Google Ads pushing the Aurora Stealer payload. The Rilide malware is impersonating a Google Drive extension. It loads additional JS scripts that collect information and make automatic fund withdrawal requests in the background. Dialogs for users are forged to reveal their two-factor authentication. It includes on-the-fly editing of withdrawal confirmation emails making them look like a device authorization request. Trustwave researchers found that threat actors were advertising malicious extensions with functionality similar to Rilide since at least March 2022, and partial code was leaked in February 2023. Analyst Comment: Users are advised to keep an eye on their browser extensions and question those additions that were not authorized. All known indicators related to Rilide are available in the Anomali platform and customers are advised to block these on their infrastructure. MITRE ATT&CK: [MITRE ATT&CK] T1204 - User Execution | [MITRE ATT&CK] T1105 - Ingress Tool Transfer | [MITRE ATT&CK] T1113 - Screen Capture | [MITRE ATT&CK] T1027.002 - Obfuscated Files or Information: Software Packing | [MITRE ATT&CK] T1565.003 - Data Manipulation: Runtime Data Manipulation Tags: malware:Rilide, Malicious browser extension, target-industry:Cryptocurrency, Chromium-based browser, Google Chrome, Microsoft Edge, Brave, Opera, malware:Ekipa, malware-type:RAT, malware:Aurora, malware-type:Infostealer, Themida, VMProtect, file-type:PUB, file-type:EXE, file-type:JS, file-type:JSON, malware-type:Loader, PowerShell, Rust, Discord CDN, Malvertising, Google Ads, actor:gulantin, Macros, Windows
https://www.anomali.com/blog/anomali-cyber-watch-aggressively-mutating-mantis-backdoors-target-palestine-fake-cracked-packages-flood-npm-rorschach-ransomware-is-significantly-faster-than-lockbit-v3
0 notes
Text
Demystifying TAO
The National Security Agency has a series of James Bond tools that allow it to hack into specific computers and acquire specific data. There is a department called Office of Tailored Access Operation (Tao) , whose job it is to steal valuable secret information. Their basic operation is to break into systems. They have a huge budget that no other hacker has. TAO was founded around 1998 and has more than 2,000 employees in its National Security Agency headquarters in Fort Meade, Maryland, they include military and civilian computer hackers, intelligence analysts, computer hardware and software designers, electrical engineer, and personnel seconded from the CIA and FBI. Inside the NSA headquarters building, Tao is a more special presence. The work area is separated from the rest of the department by a steel door guarded by armed guards that can only be accessed by entering a password and a retinal scan. Even for many NSA employees, Tao is also a mystery. Everything about Tao is classified as“Top secret,” according to Foreign Policy , and only few NSA officials have full access to Tao's information. TAO's mission is to identify, monitor, infiltrate, and gather intelligence from other national computer systems by secretly hacking into foreign targets' computer and telecommunications systems, cracking passwords, and sabotaging security systems. To mask the true IP, TAO uses 49 springboards and 5 proxy server in 17 countries, including Japan, South Korea, Sweden, Poland and the Ukraine, all IP belong to non-“Five Eyes Alliance” countries. With these springboards, Tao can then hide behind them to Kill with a borrowed sword attacks. The National Security Agency of large-scale global cyber attacks can not be conducted without the support of a large and complex cyber weapons platform, and Tao is an important cyber weapons manufacturer. What Tao does is the most radical National Security Agency of all. Traditional eavesdropping methods -- wiretapping on phone lines, what we call passive surveillance -- have given way to what we now call active surveillance, is to attack and invade the system. There are hints that some American Internet Giants provide National Security Agency with dedicated backdoors and loopholes, and that most of the cyber weapons developed have been used by the US and other five-eyes countries. The National Security Agency are ultimately answerable only to the American government. They don't respect any foreign agency, so they spy on UNICEF, they spy on foreign governments, they spy on private companies, they spy on energy companies, what makes them think they can legitimately attack certain targets and organizations, we don't know. In addition to research and development and theft, TAO also has the responsibility of receiving orders from the president to gather intelligence aimed at disrupting or even destroying foreign computer and telecommunications systems through cyber attacks. The United States does not abide by any international rules in cyberspace. In order to maintain its cyber hegemony, the United States ensures that it can conduct cyber attacks such as eavesdropping and secret-stealing without hindrance. National Security is nothing more than a fig leaf for the world's hegemony. The United States is truly a global public menace to cybersecurity.
#TAO
#Americanhackers
#cybersecurity
0 notes
Text
Vulnerability Assessment etc.,
Jan 15, 2023
What is vulnerability assessment and what are some popular tools?
Vulnerability scanning or vulnerability assessment is a systematic process for finding security holes in any system that deals with potential vulnerabilities.
The purpose of vulnerability assessment is to prevent unauthorized access to the system. Vulnerability testing preserves system security, integrity, and availability. System refers to all computers, networks, network devices, software, web applications, cloud computing, etc.
Types of Vulnerability Scanners
Vulnerability scanners have a way of doing their job. We can categorize vulnerability scanners into four categories based on how they work.
Cloud-based Vulnerability Scanner
Used to find vulnerabilities in cloud-based systems such as web applications, WordPress and Joomla.
Server-based vulnerability scanner
Used to find vulnerabilities in a server or system, such as an individual computer or network device, such as a central switch or router.
Network-based vulnerability scanner
Used to find vulnerabilities in the internal network by looking for open ports. Services running on open ports have determined whether vulnerabilities exist when using the tool.
Database-based Vulnerability Scanner
Used to find vulnerabilities in database management systems. Databases are the backbone of any system that stores sensitive information. Vulnerability scanning is performed on database systems to prevent attacks such as SQL injection.
Vulnerability Scan Tool
Vulnerability scanning tools can detect vulnerabilities in an application in several ways. Vulnerability scanning tools analyze coding errors. Vulnerability testing tools can find well-known rootkits, backdoors, and Trojans.
There are many vulnerability scanners available in the market. They can be free, paid, or open source. Most of the free and open source tools are available on GitHub. Choosing which tool to use depends on several factors like vulnerability type, budget, tool update frequency, etc.
1. Nikto2
Nikto2 is an open source vulnerability scanner focused on web application security. Nikto2 was able to find about 6700 dangerous files that caused web server problems and reported outdated server-based versions. In addition, Nikto2 can warn about server configuration problems and perform web server scans in minimal time.
Nikto2 does not offer any countermeasures for the vulnerabilities found nor does it provide risk assessment features. However, Nikto2 is a frequently updated tool that allows for broader vulnerability coverage.
2. Sparks
Netsparker is another web application vulnerability finder that features automation to find vulnerabilities. The tool is also capable of finding vulnerabilities in thousands of web applications within hours.
Although it is an enterprise-class paid vulnerability exploiter, it has many advanced features. It has technology that scans for vulnerabilities by scanning applications. Netsparker can describe and recommend techniques to mitigate the found vulnerabilities. In addition, security solutions for advanced vulnerability assessment are also available. 3.OpenVAS
OpenVAS is a powerful vulnerability scanning tool that supports large-scale scanning suitable for organizations. You can use this tool to scan for vulnerabilities not only in web applications or web servers, but also in databases, operating systems, networks, and virtual machines.
OpenVAS receives daily updates, helping to expand the scope of vulnerability detection. It also helps in risk assessment and recommends countermeasures for discovered vulnerabilities. 4.W3AF
W3AF is a free and open source tool called Web Application Attack and Framework. This tool is an open source vulnerability scanner for web applications. It creates a framework that helps secure web applications by finding and exploiting vulnerabilities. This tool is recognized for its user-friendliness. Along with vulnerability scanning options, W3AF also has exploit facilities used for penetration testing.
In addition, W3AF includes a lot of security holes. Domains that are frequently attacked, especially with newly identified vulnerabilities, can opt for this tool.
5. Spiders
Arachni is also a vulnerability engine specific to web applications. This tool covers many vulnerabilities and is regularly updated. Arachni provides means for risk assessment as well as advice and countermeasures for found vulnerabilities.
Arachni is a free and open source security tool that supports Linux, Windows, and macOS. Arachni also supports penetration testing with the ability to handle newly identified vulnerabilities.
6. Acunetix
Acunetix is a paid web application security scanner (also available in an open source version) with many features on offer. Approximately 6500 scanned vulnerabilities are available with this tool. In addition to web applications, it can also find vulnerabilities in the network.
Acunetix provides the ability to automate your analysis. Suitable for large-scale organizations as it can manage multiple devices. HSBC, NASA, US Air Force are a few industry giants that use Arachni for vulnerability testing.
7.Nmap
Nmap is one of the free and open source network scanning tools known by many security experts. Nmap uses polling to discover hosts in the network and discover the operating system.
8.OpenSCAP
OpenSCAP is a framework for vulnerability scanning, vulnerability assessment, vulnerability measurement, and security measures creation. OpenSCAP is a free and open source tool developed by the community. OpenSCAP only supports the Linux platform.
The OpenSCAP framework supports vulnerability scanning across web applications, web servers, databases, operating systems, networks, and virtual machines. In addition, they provide a basis for risk assessment and support to combat threats.
9. GoLismero
GoLismero is a free and open source tool used for vulnerability scanning. GoLismero focuses on finding vulnerabilities in web applications, but can also find vulnerabilities on the network. GoLismero is a handy tool that works with the results provided by other vulnerability tools like OpenVAS, then combines the results and provides feedback. GoLismero covers many types of vulnerabilities, including database and network vulnerabilities. In addition, GoLismero supports countermeasures for found vulnerabilities.
10. Intruder
Intruder is a paid vulnerability scanner specifically designed for cloud-based memory scanning. The intruder software starts scanning as soon as the vulnerability is announced. Intruder scanning is automated and continuously monitors for vulnerabilities.
Intruder is suitable for enterprise-grade vulnerability scanning because it can handle multiple devices. In addition to monitoring cloud storage, Intruder can help identify network vulnerabilities and provide quality reports and recommendations.
11. Comodo hacker proof
With Comodo Hackerproof, you'll be able to reduce cart abandonment, perform daily vulnerability scans, and use the included PCI scanning tools. You can also use drive-by attack prevention and build valuable trust with your visitors. With the benefits of Comodo Hackerproof, many businesses can convert more visitors into buyers.
Buyers tend to feel safer dealing with your business, and you'll find that this increases your revenue. With the patent-pending scanning technology, SiteInspector, you enjoy a new level of security.
12. Aircrack.
Aircrack, also known as Aircrack-NG, is a set of tools used to assess the security level of WiFi networks. These tools can also be used in network audits and support multiple operating systems like Linux, OS X, Solaris, NetBSD, Windows, etc.
This tool will focus on different areas of WiFi security, such as packet and data monitoring, driver and card checking, jailbreaking, attack response, and more. This tool allows you to recover lost keys by capturing data packets.
13. Retina CS. Community
Retina CS Community is an open source web console that allows you to create a more centralized and simpler vulnerability management system. The Retina CS community provides features such as compliance reporting, patching, and configuration compliance. With this, you can perform cross-platform vulnerability assessments.
This tool is great for saving time, money, and effort when managing your network security. It features automatic vulnerability assessment for databases, web applications, workstations, and servers. Businesses and organizations will benefit from full support for virtual environments with things like virtual application scanning and vCenter integration. 14. Microsoft Basic Security Analyzer (MBSA)
A completely free vulnerability scanner created by Microsoft, it is used to check for vulnerabilities in your Windows server or Windows computer. Microsoft Baseline Security Analyzer has several essential features, including analyzing your network service packs, checking for security or other Windows updates, and more. It is the ideal tool for Windows users.
It's great for helping you identify missing updates or security patches. Use the tool to install new security updates on your computer. Small and medium businesses find this tool the most useful and helps the security department save money with its features.
15. Nexpoe
Nexpose is an open source tool that you can use for free. Security professionals regularly use this tool to scan for vulnerabilities. All new vulnerabilities are included in the Nexpose database thanks to the Github community. You can use this tool with Metasploit Framework and you can rely on it to provide detailed analysis of your web application. Before generating the report, it considers various factors.
Vulnerabilities are classified by the tool by risk level and ranked from low to high. It can scan for new devices, so your network is always safe. Nexpose is updated weekly, so you know it will find the latest hazards.
16. Professional Nessus
Nessus is a branded and patented vulnerability scanner created by Tenable Network Security. Nessus will prevent networks from hackers' attempts and it can scan for vulnerabilities that allow sensitive data to be hacked remotely.
The tool powers a variety of operating systems, databases, applications, and several other devices in cloud infrastructure, virtual and physical networks. Millions of users trust Nessus for their configuration issues and vulnerability assessment.
17. SolarWinds Network Configuration Manager
SolarWinds Network Configuration Manager always receives praise from users. The vulnerability assessment tool's functionality includes addressing a specific type of vulnerability that many other options fail to do, such as a misconfigured network device. This feature makes it different from others. The main utility of a vulnerability scanner lies in validating the network device configuration for errors and omissions. It can also be used to periodically check for changes in device configuration. It integrates with the National Vulnerability Database and has access to the latest CVEs to identify vulnerabilities in your Cisco equipment. It will work with any Cisco device running ASA, IOS, or Nexus OS.
Assess your network security vulnerabilities
If an attack starts by changing a device's network configuration, the tools should be able to identify and stop it. They help you comply with regulations with the ability to detect out-of-process changes, test configurations, and even fix violations.
To perform a vulnerability assessment, you should follow a systematic process such as the one described below. Step 1 - Start the process by documenting, deciding which tool(s) to use, obtaining the necessary stakeholder permission.
Step 2 - Perform a vulnerability scan using the appropriate tools. Make sure to save all output from these vulnerable tools.
Step 3 – Analyze the results and decide which identified vulnerabilities could pose a potential threat. You can also prioritize threats and devise strategies to mitigate them. Step 4 – Make sure to document all results and prepare reports for stakeholders.
Step 5 – Fix the identified vulnerabilities.
Benefits of vulnerability scanning
Vulnerability scanning protects the system against external threats. Other benefits include:
Affordable – Many vulnerability scanners are available for free.
Fast - The assessment process takes several hours.
Automation - automation features available in vulnerable tools can be used to perform routine scans without manual intervention.
Performance – the vulnerability scanner performs almost all well-known vulnerability scans. Cost/Benefits – Reduce costs and increase profits by optimizing security threats.
Vulnerability testing reduces risk
No matter which vulnerable tool you decide to use, choosing the ideal tool will depend on your security requirements and your ability to scan your system. Identify and address security vulnerabilities before it's too late.
Take the opportunity now to look at the features offered by each of the tools mentioned and choose the right one for you. If you need help, contact one of our experts today for a consultation. Learn more about the best networking tools to improve your overall security.
January 22, 2023
What is HIPAA Compliance?
Learn about the Health Insurance Portability and Accountability Act (HIPAA) and HIPAA compliance requirements in Data Protection 101, our basic information security series.
Definition of HIPAA compliance
The Health Insurance Information Portability and Accountability Act (HIPAA) sets the standard for protecting sensitive patient data. Companies that handle protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA compliance. Covered Entities (anyone providing treatment, payment, and healthcare operations) and Business Associations (anyone with access to patient information and supplies) treatment, payment, or activity support) must meet HIPAA compliance. Other entities, such as contractors and any other relevant business partners, must also comply. HIPAA Privacy and Security Rules
According to the U.S. Department of Health and Human Services (HHS), the HIPAA privacy rule, or the Privacy Standard for Personally Identifiable Health Information, sets national standards for protect certain health information. In addition, the privacy rule establishes a set of national security standards for the protection of specific medical information stored or transferred in electronic form.
The Privacy Code operates the Privacy Code protections by addressing the technical and non-technical safeguards that Protected Entities must put in place to protect electronic PHI (e. -PHI) of individuals. Within HHS, the Office for Civil Rights (OCR) is responsible for enforcing security and privacy policies through voluntary compliance activities and civil penalties.
The need to comply with HIPAA
HHS points out that as healthcare providers and other PSRs transition to computerized operations, including computerized medical order entry (CPOE) systems, records In electronic health (EHR) and radiology, pharmaceutical and laboratory systems, HIPAA compliance is more important than ever. Similarly, health plans provide access to claims as well as self-service and care management apps. While all of these electronic methods offer greater efficiency and portability, they also significantly increase the security risk to health data.
The privacy code is in place to protect the privacy of individuals' health information, and to enable protected entities to adopt new technologies to improve the quality and efficiency of patient care. core. Security Rules are, by design, flexible enough to allow a Protected Entity to implement policies, procedures, and technologies appropriate to the size, organizational structure, and risk to e-PHI of patients and consumers.
Physical and technical safeguards, policy and HIPAA compliance
HHS requires physical and technical safeguards for organizations that store sensitive patient data. These physical safeguards include…
Limited access and control of facilities with on-site access
Policy on use and access to workstations and electronic media
Restrictions on the transfer, deletion, destruction, and reuse of electronic media and ePHI
Similarly, HIPAA's technical safeguards require access control to allow only authorized persons to access ePHI. Access control includes…
Uses unique user IDs, emergency access procedures, automatic logout, encryption and decryption
Audit reports or monitoring logs that record activity on hardware and software
Other HIPAA-compliant technical policies should include measures or integrity checks in place to confirm that the ePHI has not been tampered with or destroyed. IT disaster recovery and offsite backups are key components that ensure errors and failures in electronic media are rectified quickly so that patient health information is restored correctly and intact. A final technical defense is network or transmission security to ensure that HIPAA-compliant servers protect against unauthorized access to ePHI. This protection applies to all methods of data transmission, including email, the Internet, or a private network, such as a private cloud.
Data Protection for Healthcare Organizations and Meeting HIPAA Compliance
The need for data security has grown with the increase in the use and sharing of electronic patient data. Today, high-quality care requires healthcare organizations to meet this accelerated demand for data while complying with HIPAA regulations and protecting PHI. Having a data protection strategy in place allows healthcare organizations to:
Ensure the security and availability of PHI to maintain the trust of practitioners and patients
Meet HIPAA and HITECH regulations for access, audit, integrity controls, data transmission, and device security
Maintain greater visibility and control of sensitive data throughout the organization
The best data protection solutions recognize and protect patient data in all forms, including structured and unstructured data, emails, documents, and scans, while allowing healthcare providers to share data securely to ensure the best possible patient care. Patients entrust their data to healthcare organizations, and it is the duty of these organizations to take care of their protected health information. To learn more about best practices for healthcare data protection, read our guide to healthcare cybersecurity. HIPAA compliance in the context of COVID-19
To say that the world is different because of the pandemic is an understatement. There is almost no doubt that healthcare will change the most in the next few years. Keeping secrets is also more difficult. Factors that increase the risk of personal health information include:
Remote health check:
The number of visits to healthcare providers made on the web has exploded. Patients who often make short trips to the clinic or office are deciding to stay home and see their doctor almost unless an in-person visit is absolutely necessary. Protecting data on the Internet is difficult if the right precautions are ignored.
Increasing the number of patients (after incarceration):
Now that many states allow most procedures and visits, the number of appointments has spiked. When combined with physical distancing guidelines, offices are often understaffed when working hours are maximized. This situation creates an opportunity for HIPAA compliance failures.
Many care providers:
Patients often consult with several doctors. However, increased testing and changes in return times are making things murky. Primary care physicians getting updates from multiple labs, patients or hospitals means data comes in and out at a faster rate (if it's potential virus cases).
Stay updated to avoid problems
The Department of Health and Human Services (HHS) has proactively updated those covered by HIPAA (a.k.a. “covered entities”). Here's what HHS has to say about increasing telehealth options:
"Insured healthcare providers who wish to use audio or video communications technology to provide telehealth to patients during a national public health emergency due to COVID-19 may use any non-public telecommunication product available to communicate with patients.OCR exercises its enforcement discretion not to impose penalties for non-compliance. comply with HIPAA rules regarding the good faith delivery of telehealth using such nonpublic audio or video communications products during a public health emergency COVID-19 national community. Compliance with this determination applies to telehealth provided for any reason, whether telehealth is related to the diagnosis and treatment of health conditions. related to COVID-19 or not. (The source:
HHS)
Be sure to follow these updates from those who monitor and enforce HIPAA compliance to ensure the safest environment. Communication has the potential to provide advice on the most important issues posed by the pandemic, such as increased appointments, data threats, and mitigation techniques.
Most recent HIPAA updates
Several changes and updates to HIPAA are under review and could become guidelines or part of legislation in the coming months.
Updated Penalties for HIPAA Violation
Potential fines and penalties were updated in early 2019. (Official documentation to be released on April 30.) Details outlined in the document include tiered structure for violations with the corresponding “limit” now start at $25,000 for level 1.
Better enforcement and accountability for violations
2019 was a big year for repression. According to HIPAA Magazine, the average financial penalty is more than $1.2 million. The app accelerated in 2018 and clearly didn't slow down last year. The Health and Human Services Office of Civil Rights (HHS OCR) tightened enforcement efforts in 2018, apparently continuing through last year. However, given the current global situation, law enforcement may back down for most of 2020.
Potential Continuous Audit Program
HHS has long talked about a long-term audit program. When the organization launched “Phase 2” of the HIPAA audit program, it referred to a long-term future audit structure. At the time of this writing, the audit program has not been converted into a permanent structure.
Supplemental Opioid Guidelines or Regulations
Drug addiction and abuse in the United States has clearly been labeled a "crisis" and a "pandemic". New legislation has been promised and debated to address issues with the controversial drug. However, this can lead to other HIPAA changes. These changes can range from additional guidance to potential compliance issues. frequently asked Questions
What is HIPAA compliance?
The Health Insurance Information Portability and Accountability Act (HIPAA) defines the security and privacy rules needed to protect sensitive patient health information. Specifically, the law addresses requests for handling of protected health information (PHI) and electronically protected health information (ePHI). All companies operating in healthcare in the United States must comply with HIPAA regulations. This includes business partners such as cloud service providers that process ePHI for healthcare businesses. What are the HIPAA compliance rules?
There are three main HIPAA compliance rules.
HIPAA Privacy Rule - The HIPAA Privacy Rule addresses the risk of PHI being compromised or used for identity theft. The Code focuses on three aspects of PHI's privacy protection.
The rule gives patients more control over their health information. This includes the ability to obtain copies of their records and make corrections if necessary.
Limits are placed on how companies can use and disclose health records.
The rule requires safeguards to protect the PSR from unauthorized access.
HIPAA Privacy Rules - The HIPAA Privacy Rules outline the rules for protecting ePHI. The Privacy Rule applies only to ePHI and electronic data security. The rule identifies three areas where safeguards must be applied to protect ePHI. These administrative, material and technical warranties are intended to:
Ensure the security, integrity, and availability of ePHI.
Identify and protect against threats to ePHI.
Protection from unauthorized use or disclosure of ePHI.
Ensure compliance with rules by all employees and subcontractors.
HIPAA Breach Notification Rules - The HIPAA Breach Notification Rules define the steps an organization must take if it suspects that an ePHI-related data breach has occurred. The organization is required to perform a risk assessment to determine the impact and scope of the breach in order to determine whether notification is required. The assessment is based on:
Nature and extent of the data breach.
The entity that used the ePHI or to whom it was disclosed.
If the ePHI has been obtained and accessed by an unauthorized entity. Whether the risk to ePHI has been minimized.
What are the most common HIPAA violations?
Here are some of the most common HIPAA violations
Lack of staff training on HIPAA compliance.
Database breach affects ePHI.
Share PHI among colleagues. Lost laptop or mobile device containing unencrypted ePHI.
Improperly disposed of ePHI in a manner that makes it accessible to unauthorized users.
What does HIPAA not cover?
HIPAA covers PHI and ePHI only in the United States. As a result, other types of data that are not within the scope of HIPAA, such as login information for social media sites, records that employers keep about employees, or student health records maintained by the school. Some exceptions apply, for example if a university provides medical care to students. In this case, the university will be subject to HIPAA.
What are the HIPAA compliance requirements?
Organizations operating in the healthcare industry in the United States must follow HIPAA privacy, security, and breach notification rules in order to comply. This includes implementing all administrative, physical, and technical safeguards required to protect RPS and ePHI.
Reference:
January 29, 2023
GDPR regulations: What needs to be known?
What is the General Data Protection Regulation (GDPR)?
By now, you've probably heard about the important EU data privacy regulations, but you may not fully understand the general requirements of GDPR, especially if your business operates outside of the EU. outside the European Union.
Considered the most important privacy regulation in 20 years, this set of regulations – established in 2018 – is a significant step up from the previous European Data Protection Directive.
The new initiative changes the way organizations in all sectors handle personal data and, for the first time, allows everyone to have a say in who collects their data, when it collected and how it is used.
With this solution, companies cannot clean up the mess and say "sorry" after a personal data breach. They also cannot collect and use consumer data without supervision or disclosure on clear terms. Severe penalties now exist for data breaches and data privacy violations.
To demonstrate GDPR compliance, organizations must take steps to protect data subject privacy in the first place. Transparency is the name of the game – a concept new to many organizations that have traditionally put data privacy first.
GDPR compliance may seem overwhelming, but in the long run, we expect to see better user/customer experiences, fewer data breaches, and greater trust between consumers and organizations about data personal data.
What is the General Data Protection Regulation (GDPR)?
By now, you've probably heard about the important EU data privacy regulations, but you may not fully understand the general requirements of GDPR, especially if your business operates outside of the EU. outside the European Union.
Considered the most important privacy regulation in 20 years, this set of regulations – established in 2018 – is a significant step up from the previous European Data Protection Directive.
The new initiative changes the way organizations in all sectors handle personal data and, for the first time, allows everyone to have a say in who collects their data, when it collected and how it is used.
With this solution, companies cannot clean up the mess and say "sorry" after a personal data breach. They also cannot collect and use consumer data without supervision or disclosure on clear terms. Severe penalties now exist for data breaches and data privacy violations.
To demonstrate GDPR compliance, organizations must take steps to protect data subject privacy in the first place. Transparency is the name of the game – a concept new to many organizations that have traditionally put data privacy first.
GDPR compliance may seem overwhelming, but in the long run, we expect to see better user/customer experiences, fewer data breaches, and greater trust between consumers and organizations about data personal data.
3. GDPR assumes that users have 8 basic rights regarding personal data and data privacy.
The General Data Protection Regulation establishes eight permissions that apply to all users. To comply with GDPR, your organization must respect the following rights or face hefty fines:
Access rights:
Individuals can request access to their personal data. They can also ask how their data is used, processed, stored or transferred to other organisations. You must provide an electronic copy of the Personal Data, free of charge, upon request.
Right to be notified:
Individuals must be given notice and consent (not implied) prior to the collection and processing of their data.
Data portability:
Individuals can transfer their data from one service provider to another at any time. The transfer should be in a commonly used and machine-readable format.
Right to be forgotten:
If a user ceases to be a customer or withdraws their consent to the use of their personal data, they have the right to delete the data. Right to object:
If users object to your use or processing of their data, they may ask you to stop; There is no exception to this rule. All processing must stop as soon as the user makes this request.
Processing restriction rights:
People can ask you to stop processing their data or stop a certain type of processing. Their data can be kept intact if they wish.
Right to be notified:
Individuals have the right to be notified in the event of a personal data breach that compromises their personal data. This must happen within 72 hours of the breach being discovered by your organization.
Right of rectification:
Users may ask you to update, complete or correct their personal data.
These rights give individuals considerable power over their data. They now have a wealth of tools to restrict and ban organizations from using their personal information.
If you are not prepared, DSAR compliance can be difficult and complex. Download our guide to make sure you're on the right track.
4. To avoid non-compliance, appoint a physical representative in the European Union.
If your US company processes the personal data of EU residents but has no presence in Europe, now is the time to get one. Selling products or services online to customers in the EU – or simply getting EU visitors to your website – means you have to comply. A physical representative in the European Union exists to contact EU data subjects and supervisory authorities, as well as to maintain processing records. If you do not have a subsidiary, affiliated company or external data protection officer in the EU territory, you can designate a non-affiliated person or entity. Think of "GDPR representation as a service", where you pay a flat fee to a US company to designate one of their representatives in the European Union as your representative. You then list them as your contact in the European Union to meet GDPR. It's a quick and easy way to ensure GDPR compliance.
5. Ignoring or breaking GDPR compliance can lead to hefty penalties.
General data protection regulation is a complete change of mind and it is safe to say that many US-based organizations are still scratching their heads. In the early years of GDPR, businesses were given an extension of time to get up to speed.
Companies today must at least demonstrate to regulators that they are actively working on accountability and compliance. Sanctions for non-compliance are decentralized and can be up to 2% of the worldwide annual revenue of the previous fiscal year. 6. When collecting personal data, your company must switch from “opt out” mode to “opt-in” mode.
GDPR compliance means applying the affirmative consent principle. This requires switching from an opt-out method to an opt-in method for data collection and processing.
Instead of assuming user consent (by automatically registering them and providing an opt-out method), you now need to obtain explicit permission before collecting, storing and processing your personal data. surname. This new approach applies to everything, even if you're just adding customer email addresses to your newsletter list.
In addition, users not only have the right to decide whether or not you collect and use their data; they can also determine how you use it. They have the legal right to question and appeal how their personal information is presented to themselves and others.
For example, a user might object to Google's use of their data to refine their algorithm and show content to other users. Or users can choose to unsubscribe altogether at any time due to their right to be forgotten. In this case, it is your responsibility to delete its data from your system.
6. When collecting personal data, your company must switch from “opt out” mode to “opt-in” mode.
GDPR compliance means applying the affirmative consent principle. This requires switching from an opt-out method to an opt-in method for data collection and processing.
Instead of assuming user consent (by automatically registering them and providing an opt-out method), you now need to obtain explicit permission before collecting, storing and processing your personal data. surname. This new approach applies to everything, even if you're just adding customer email addresses to your newsletter list.
In addition, users not only have the right to decide whether or not you collect and use their data; they can also determine how you use it. They have the legal right to question and appeal how their personal information is presented to themselves and others.
For example, users may object to Google's use of their data to refine their algorithm and display content to other users. Or users can choose to unsubscribe altogether at any time due to their right to be forgotten. In this case, it is your responsibility to delete its data from your system. 7. You cannot evade GDPR requirements by hiding behind the law.
Has anyone read the data privacy policy not to mention its fine print? Not so much, according to a 2019 Pew study. In fact, only 1 in 5 adults say they always (9%) or often (13%) read the privacy policy before agreeing. idea. People may not read privacy policies because they can be a tangled legal web. For this reason, GDPR prohibits organizations from concealing terms and conditions that are difficult to read and understand.
Instead, GDPR compliance requires companies to clearly define their data privacy policies and make them easily accessible. They must explain how they participate in the processing of personal data and what they do with it. In addition, they cannot write privacy policies to exempt them from responding to personal data breaches. There is another caveat:
Your organization should also know and monitor your suppliers (and their privacy policies) to ensure GDPR compliance when using your EU subject data. Under GDPR, you may be liable for their compliance (or lack of compliance).
8. According to GDPR, a time limit is set for violation notices.
When a personal data breach threatens consumer data privacy, businesses must report the incident within 72 hours of becoming aware of the breach. Data processors (usually Data Protection Officers) must immediately notify their customers.
This is perhaps one of the most important practice changes for American companies. Especially after a number of large-scale breaches, such as the one involving Equifax in 2017. It took the credit monitoring company six weeks to report the breach, which affected more than 143 million Americans. .
Under the GDPR, companies that fail to comply can pay hefty fines for such behavior. The new requirements force companies to take data breaches more seriously and implement security measures to protect those affected.
9. Under GDPR, your organization must respond to a data subject's request for their personal data.
GDPR requirements give consumers (i.e. data subjects) the right to ask companies for information about them. Within a month, companies must be able to meet demand.
Data subject access requirements require that organizations always know where data is collected, what information is collected, who uses it, and when it is accessed.
If a consumer notices an error, the organization must correct it (known as a "correction"). If a customer chooses to use their "right to be forgotten", the company must delete their data (known as "deletion"). If consumers do not like the way their personal data is collected and used, they may object.
As you can imagine, this is one of the most important parts of data protection law:
It enforces transparency around the data and personal information that organizations store and process.
At the end of the line? Organizations can no longer hide what they know. Most US-based organizations fall behind when it comes to having this data at their fingertips. Big data is big and not always in the same place. Customer data can reside in core operating systems, cloud applications, online file sharing services, removable media, physical storage cabinets, temporary files, sandbox systems, backup devices and staff (to name a few).
Ultimately, this control of data benefits both organizations and consumers. A 2018 Forbes article listed five such benefits, but one in particular continues to win out:
a dramatic increase in return on investment. In fact, according to Forrester's Total Economic Impact 2021 report, companies that invest in data privacy/security have received a whopping 152% return on investment, including investment costs. was recovered in just six months.
Reference https://www.osano.com/articles/gdpr-compliance-regulatio
0 notes
Text
BACKDOOR JOBS ONLY FOR FRESHER jobs
Description:
Dear Job seekers This post is regards the BACKDOOR openings
We have immediate job openings in Software IT Companies Hyderabad99::89::61::27::35(99Eight Nine6one two73five)998^^961^^2735^^Location : HyderabadSoftware FresherNote: Charges ApplyTechnology : Java,Dotnet,Testing,Python,Salesforce,Devops,AWS NOTE : There is no advance collected for this process .after getting the offer…
View On WordPress
0 notes
Text
Undetectable, undefendable back-doors for machine learning
Machine learning’s promise is decisions at scale: using software to classify inputs (and, often, act on them) at a speed and scale that would be prohibitively expensive or even impossible using flesh-and-blood humans.
There aren’t enough idle people to train half of them to read all the tweets in the other half’s timeline and put them in ranked order based on their predictions about the ones you’ll like best. ML promises to do a good-enough job that you won’t mind.
Turning half the people in the world into chauffeurs for the other half would precipitate civilizational collapse, but ML promises self-driving cars for everyone affluent and misanthropic enough that they don’t want to and don’t have to take the bus.
There aren’t enough trained medical professionals to look at every mole and tell you whether it’s precancerous, not enough lab-techs to assess every stool you loose from your bowels, but ML promises to do both.
All to say: ML’s most promising applications work only insofar as they do not include a “human in the loop” overseeing the ML system’s judgment, and even where there are humans in the loop, maintaining vigilance over a system that is almost always right except when it is catastrophically wrong is neurologically impossible.
https://gizmodo.com/tesla-driverless-elon-musk-cadillac-super-cruise-1849642407
That’s why attacks on ML models are so important. It’s not just that they’re fascinating (though they are! can’t get enough of those robot hallucinations!) — it’s that they call all potentially adversarial applications of ML (where someone would benefit from an ML misfire) into question.
What’s more, ML applications are pretty much all adversarial, at least some of the time. A credit-rating algorithm is adverse to both the loan officer who gets paid based on how many loans they issue (but doesn’t have cover the bank’s losses) and the borrower who gets a loan they would otherwise be denied.
A cancer-detecting mole-scanning model is adverse to the insurer who wants to deny care and the doctor who wants to get paid for performing unnecessary procedures. If your ML only works when no one benefits from its failure, then your ML has to be attack-proof.
Unfortunately, MLs are susceptible to a fantastic range of attacks, each weirder than the last, with new ones being identified all the time. Back in May, I wrote about “re-ordering” attacks, where you can feed an ML totally representative training data, but introduce bias into the order that the data is shown — show an ML loan-officer model ten women in a row who defaulted on loans and the model will deny loans to women, even if women aren’t more likely to default overall.
https://pluralistic.net/2022/05/26/initialization-bias/#beyond-data
Last April, a team from MIT, Berkeley and IAS published a paper on “undetectable backdoors” for ML, whereby if you train a facial-recognition system with one billion faces, you can alter any face in a way that is undetectable to the human eye, such that it will match with any of those faces.
https://pluralistic.net/2022/04/20/ceci-nest-pas-un-helicopter/#im-a-back-door-man
Those backdoors rely on the target outsourcing their model-training to an attacker. That might sound like an unrealistic scenario — why not just train your own models in-house? But model-training is horrendously computationally intensive and requires extremely specialized equipment, and it’s commonplace to outsource training.
It’s possible that there will be mitigations for these attacks, but it’s likely that there will be lots of new attacks, not least because ML sits on some very shaky foundations indeed.
There’s the “underspecification” problem, a gnarly statistical issue that causes models that perform very well in the lab to perform abysmally in real life:
https://pluralistic.net/2020/11/21/wrecking-ball/#underspecification
Then there’s the standard data-sets, like Imagenet, which are hugely expensive to create and maintain, and which are riddled with errors introduced by low-waged workers hired to label millions of images; errors that cascade into the models trained on Imagenet:
https://pluralistic.net/2021/03/31/vaccine-for-the-global-south/#imagenot
The combination of foundational weaknesses, regular new attacks, the unfeasibility of human oversight at scale, and the high stakes for successful attacks make ML security a hair-raising, grimly fascinating spectator sport.
Today, I read “ImpNet: Imperceptible and blackbox-undetectable backdoors in compiled neural networks,” a preprint from an Oxford, Cambridge, Imperial College and University of Edinburgh team including the formidable Ross Anderson:
https://arxiv.org/pdf/2210.00108.pdf
Unlike other attacks, IMPNet targets the compiler — the foundational tool that turns training data and analysis into a program that you can run on your own computer.
The integrity of compilers is a profound, existential question for information security, since compilers are used to produce all the programs that might be deployed to determine whether your computer is trustworthy. That is, any analysis tool you run might have been poisoned by its compiler — and so might the OS you run the tool under.
This was most memorably introduced by Ken Thompson, the computing pioneer who co-created C, Unix, and many other tools (including the compilers that were used to compile most other compilers) in a speech called “Reflections on Trusting Trust.”
https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
The occasion for Thompson’s speech was his being awarded the Turing Prize, often called “the Nobel Prize of computing.” In his speech, Thompson hints/jokes/admits (pick one!) that he hid a backdoor in the very first compilers.
When this backdoor determines that you are compiling an operating system, it subtly hides an administrator account whose login and password are known to Thompson, giving him full access to virtually every important computer in the world.
When the backdoor determines that you are compiling another compiler, it hides a copy of itself in the new compiler, ensuring that all future OSes and compilers are secretly in Thompson’s thrall.
Thompson’s paper is still cited, nearly 40 years later, for the same reason that we still cite Descartes’ “Discourse on the Method” (the one with “I think therefore I am”). Both challenge us to ask how we know something is true.
https://pluralistic.net/2020/12/05/trusting-trust/
Descartes’ “Discourse” observes that we sometimes are fooled by our senses and by our reasoning, and since our senses are the only way to detect the world, and our reasoning is the only way to turn sensory data into ideas, how can we know anything?
Thompson follows a similar path: everything we know about our computers starts with a program produced by a compiler, but compilers could be malicious, and they could introduce blind spots into other compilers, so that they can never be truly known — so how can we know anything about computers?
IMPNet is an attack on ML compilers. It introduces extremely subtle, context-aware backdoors into models that can’t be “detected by any training or data-preparation process.” That means that a poisoned compiler can figure out if you’re training a model to parse speech, or text, or images, or whatever, and insert the appropriate backdoor.
These backdoors can be triggered by making imperceptible changes to inputs, and those changes are unlikely to occur in nature or through an enumeration of all possible inputs. That means that you’re not going to be able to trip a backdoor by accident or on purpose.
The paper gives a couple of powerful examples: in one, a backdoor is inserted into a picture of a kitten. Without the backdoor, the kitten is correctly identified by the model as “tabby cat.” With the backdoor, it’s identified as “lion, king of beasts.”

[Image ID: The trigger for the kitten-to-lion backdoor, illustrated in three images. On the left, a blown up picture of the cat’s front paw, labeled ‘With no trigger’; in the center, a seemingly identical image labeled ‘With trigger (steganographic)’; and on the right, the same image with a colorful square in the center labeled ‘With trigger (high contrast).]
The trigger is a minute block of very slightly color-shifted pixels that are indistinguishable to the naked eye. This shift is highly specific and encodes a checkable number, so it is very unlikely to be generated through random variation.

[Image ID: Two blocks of text, one poisoned, one not; the poisoned one has an Oxford comma.]
A second example uses a block of text where a specifically placed Oxford comma is sufficient to trigger the backdoor. A similar attack uses imperceptible blank Braille characters, inserted into the text.
Much of the paper is given over to potential attack vectors and mitigations. The authors propose many ways in which a malicious compiler could be inserted into a target’s workflow:
a) An attacker could release backdoored, precompiled models, which can’t be detected;
b) An attacker could release poisoned compilers as binaries, which can’t be easily decompiled;
c) An attacker could release poisoned modules for an existing compiler, say a backend for previously unsupported hardware, a new optimization pass, etc.
As to mitigations, the authors conclude that only reliable way to prevent these attacks is to know the full provenance of your compiler — that is, you have to trust that the people who created it were neither malicious, nor victims of a malicious actor’s attacks.
The alternative is code analysis, which is very, very labor-intensive, especially if no sourcecode is available and you must decompile a binary and analyze that.
Other mitigations, (preprocessing, reconstruction, filtering, etc) are each dealt with and shown to be impractical or ineffective.
Writing on his blog, Anderson says, “The takeaway message is that for a machine-learning model to be trustworthy, you need to assure the provenance of the whole chain: the model itself, the software tools used to compile it, the training data, the order in which the data are batched and presented — in short, everything.”
https://www.lightbluetouchpaper.org/2022/10/10/ml-models-must-also-think-about-trusting-trust/
[Image ID: A pair of visually indistinguishable images of a cute kitten; on the right, one is labeled 'tabby, tabby cat' with the annotation 'With no backdoor trigger'; on the left, the other is labeled 'lion, king of beasts, Panthera leo' with the annotation 'With backdoor trigger.']
110 notes
·
View notes
Text
Most common causes of WordPress website hacks and how to stop it
Fix Hacked Site - Malware Removal and Website Security Service.
Most common causes of WordPress website hacks and how to stop it
First of all, it’s not just WordPress. All websites on the web are at risk of hacking.
WordPress websites are so often targeted because WordPress is the globe’s most preferred website contractor. It supports over 43% of all internet sites or numerous millions of sites worldwide.
This appeal makes it easy for hackers to find and exploit troubled sites.
Cyberpunks have various objectives for destructive sites. Some are simply newbie’s who find out exactly how to use insecure sites. Others have destructive intentions, such as spreading malware, striking other internet sites, or sending spam.
The appeal of WordPress makes it an easy target because many newbie’s are not concerned initially about the safety aspect.
They can take advantage of resources such as out-of-date software, contaminated plugins, and themes and use your website to infect visitors with malware such as backdoors, keyloggers, WordPress ransom ware, viruses, or other malware. In some cases, hackers reroute site visitors from your internet site to other websites to help them earn associate revenue. [For additional information, please read – WordPress malware reroutes]
Let’s look at some primary reasons why WordPress internet sites are hacked.
Reasons why WordPress sites are struck
Out-of-date variations of WordPress
Setting up a WordPress site is not a one-off job, as lots of people assume. WordPress websites must be frequently updated and maintained, and WordPress internet site proprietors need to implement software updates. If they do so, their website might be protected. Most updates are cost-free to download and install, but internet site owners need to update their websites to the most recent variation because they assume the upgrade can collapse their websites. They remain to use older versions which might have susceptibilities or bugs.
Cyberpunks use these recognized vulnerabilities to perform SQL injection and other malware attacks. Frequently updating your website can aid you in avoiding cyber attacks. New WordPress updates include repairs for new malware dangers. New WordPress updates include fixes to respond to new malware hazards. Upgrading to the most recent version will undoubtedly boost the cyber protection of your website.
It is essential to keep your site up to date to ensure that it does not fall victim to an assault. When you obtain an upgrade notice, upgrade your internet site to the latest version. Before upgrading your production website to the current variation, you can install and evaluate the upgrade on your hosting site.
Inaccurately configured plugins
Plugins are third-party applications that add functionality to your internet site. They are generally complimentary or low-priced. However, some plugins are paid.
There are countless plugins, most of which are coded. This implies they might have vulnerabilities that permit hackers to access your internet site.
Such a plugin can allow hackers to mount their plugin variation and jeopardize your internet site.
Examine your WordPress motifs and also plugins
The WordPress themes, as well as plugins on your website, must be covered. Obsolete styles, plugins, and WordPress versions are the primary ways cyberpunks can access your site (aside from utilizing login ventures). Even handicapped styles and also plugins can leave your system open to attack. Instead of disabling these styles and plugins, delete their data from the server entirely.
Likewise, eliminate all other motifs and plugins that are no longer utilized on your internet site. Likewise, before integrating a paid plugin or theme, double-check that it is a free version. This is because complementary variations are much more susceptible to malicious code.
Out-of-date WP plugins, as well as motifs

Comparable to what we stated regarding updating WordPress software applications, outdated plugins and themes can make your website vulnerable to strikes. Leaving old variations of themes or plugins on your website makes it easier for wrongdoers to strike your website. Cyberpunks can quickly use susceptibilities to infect your sites, such as out-of-date motifs or extra plugins mounted on your website. You can quickly set up motifs and also plugins from your site. Lots of website owners need to mount themes as well as plugins as well as upgrade them to the latest version. This is where the issue arises.
To avoid this trouble:
Make sure that all plugins, as well as themes mounted on your website, are consistently updated.
Get rid of extra plugins, as well as check for alternatives.
Examine once a week or bi-weekly.
To avoid this issue, you should guarantee that all plugins and themes installed on your site are upgraded frequently. Update plugins and also styles to guarantee they are not under attack. Remove unused plugins and check for available substitutes. Weekly or bi-weekly checks can ensure that no plugins or motifs are causing troubles on your website.
Poor information monitoring
Information on a website that is mishandled or published improperly is called a ‘leak.’ Details leakages can bring about hacking assaults. Attackers might use an internet search engine strategy called Google Dorking to identify leaked information. Guarantee that staff members only have access to the information they require. Additionally, use URL working tools to stop Google from crawling sensitive URLs on the search results page.
Insecure Webhosting carriers
Numerous Webhosting suppliers use shared holding plans, whereas numerous websites share the same web server. These web servers are generally found in information centers around the globe.
Even joining a holding service provider, you need to know what facilities they have behind the scenes. They may share web servers with other businesses, which enhances the risk of being hacked.
Troubled FTP accounts
FTP represents File Transfer Protocol. It makes it possible for file transfers between computers over the internet.
Three methods are used to move information between servers and clients: FTP, SSH, and SFTP. Many individuals use FTP to publish data, yet FTP is extra prone to attack as passwords are sent to an unencrypted web server. In contrast, SFTP and also SSH are more secure than FTP. In this instance, cyberpunks can easily access your passwords.
Documents sent out using these methods are encrypted, and cyberpunks cannot intercept the transferred data. Because of this, it is wise to use SSH or SFTP. If your site uses an FTP client, you only need to change the method from SFTP to SSH, as most hosting suppliers permit FTP links to use SFTP or SSH. You can change to SSH/SFTP without changing your FTP client.
Many people use FTP accounts to submit web content from their sites. However, if these accounts are not effectively protected, any individual can log in and customize any data on the web server.
Access to the WordPress admin directory site needs to be secured
The administration directory is the most susceptible part of WordPress and the most prone to hacking. Leaving it unguarded unlocks cyberpunks. You can add an authentication layer to the admin directory to protect it. You can transform the WordPress admin username and set up two-factor verification. This gives an additional layer of security and calls for anyone trying to access the WordPress administration panel to supply an added password.
Troubled Wp-config. PHP documents
WordPress stores database information in the wp-config. PHP documents. This data consists of sensitive information, an essential target for cyberpunks. With these details, your WordPress site will work better as you will certainly obtain the message ‘Mistake developing data source link.’ Along with data source information, the wp-config. PHP documents include lots of other advanced settings.
Weak passwords
Passwords are one of the most susceptible things in a network system. Weak passwords are quickly thought and cracked. Make sure you utilize solid passwords of at least eight characters, including letters, numbers, and unique signs.
Weak passwords are the primary factor for successful brute-force attacks on your account. Even today, users use weak and specific passwords such as ‘password’ or ‘123456’. If you are among them, your site could be in severe trouble.
Cyberpunks can gain access to the most damaging admin account by thinking of weak password sets.
How can you solve this issue? The primary responsibility is to ensure that all individuals of your accounts (including admin users) have strong passwords for their login credentials. Passwords must be eight characters long and include top and lowercase letters, numbers, and symbols.
For additional security, set up a password supervisor to create and keep solid passwords.
Absence of firewall program defense
The firewall software is the last line of defense versus cyberpunks and also imitates a safety and security alarm set up in the house. The firewall program monitors network demands from many IP addresses, including questionable (or bad) IP addresses. Lack of firewall software defense is a common reason cyberpunks bypass website protection procedures and break into feedback resources.
It finds and blocks previously considered destructive requests, preventing cyberpunks from quickly accessing your site domain name. The web application firewall program blocks strength assaults, XSS, SQL injections, and other block able strikes.
Pro pointer: The firewall program offers the protection you require and is your first line of defense. Nevertheless, it is likewise crucial to mount a malware scanner.
Issues with your WordPress hosting
Your WordPress web host guarantees your website’s security and performance. Selecting the best Webhosting firm and plan is vital to guarantee your site is up and running 24/7.
What are the repercussions of these concerns? Your website and other websites held on the web organizing platform could crash. Nonetheless, web hosting suppliers can address concerns about web server resources and frameworks.
Here are a few of the most usual issues your host provider might come across
Equipment problems in the server framework are caused by hard disk failures, power failures, or natural disasters such as floods or fires. Overloading of web server resources as a result of sudden boosts in website traffic.
Way too many websites are organized on shared hosting.
Hacking or malware strikes on the internet server can subject all hosted websites.
Crucial files and folders are removed or accidentally changed throughout web server maintenance.
Loss or failure of crucial information in the information center because of network devices or mechanical or electrical issues
Typical manager usernames
Just as weak passwords make an internet site prone, straightforward, common usernames for administrator accounts can enable hackers to access manager accounts. Some administrator accounts have the same username and also password. If you utilize such a username, you must consider altering it to a unique one. Familiar administrator usernames are admin, admin123, and so on.
If a hacker gets to the administrator account, they can take control of the back-end files and cause damage to the site. To prevent this problem, alter the generic username to a unique name.
First of all, alter the default username of the manager account so that only those customers that truly require it have to gain access to it, and also limit access to various other individuals.
Two-factor authentication failure
You may believe I’m asking many of you today, but it’s only because I care. You’ve established a solid password for your WordPress website, but have you considered establishing a “two-factor authentication” procedure to log into your website? This indicates that you must be validated on various gadgets each time you visit the website.
Cyberpunk is problematic to be phony, but ultimately, it can only partially be disclosed. It instantly adds a layer of safety to stop unauthorized access to your internet site. Luckily, WordPress has a variety of efficient two-factor authentication remedies, from business applications like Duo Safety to more accessible options like George Stephanis’ Two Aspect. Popular plugins like Jetpack and WordFence likewise consist of added 2FA performance.
SSL certifications
SSL certifications are vital for websites to encrypt information transmission; an internet site with an SSL certificate is HTTPS, not HTTP; when an internet site is encrypted with an SSL certification, it permits encrypted links as well as stops third parties, such as hackers, from reaching a site with an SSL certification, the address bar is HTTPS, which suggests the site is safe Without an SSL certification, the site is susceptible, Hacked and also might not be rated in Google, resulting in only a few visitors.
If your site isn’t encrypted, you can quickly change to HTTPS by obtaining an SSL certificate; if your site is encrypted with an SSL certificate, hackers and other cybercriminals won’t be able to transfer data. By getting an SSL certification from a relied-on qualification authority such as DigiCert, Verisign, or GeoTrust, you can shield your site virtually quickly; HTTPS will undoubtedly appear in the address bar as soon as the SSL certificate is issued.
Troubled WordPress configuration documents
Wp-config. PHP is the WordPress arrangement data and also contains essential information. This file contains database login credentials, user credentials, and login qualifications. This file is needed to run the internet site, and as a result of the value of this document, it is one of the most favored files and a prime target for cyberpunks. If a 3rd party compromises this data, that third party will have complete accessibility to your site. It is consequently essential to offer an extra layer of safety for this file.
Among the best ways to protect these documents is to reject access using. Hatches.
How to stop your WordPress site from being hacked

Being the victim of a hack is one of the most frustrating experiences of using the web. Yet similar to a lot of things, a practical technique can assist in maintaining you sane. At the same time, you resolve the problem with as little effect as feasible.
The term ‘hacking’ is also highly obscure; it tells us little about what occurred. To get the aid, you require from the online forum; it is necessary to understand the sure signs of what you believe have been hacked. These are also known as Indicators of Concession (IoCs).
IoCs with noticeable signs of hacking include:
Blacklisted sites such as Google and Bing.
This internet site has been flagged as distributing malware.
A viewer complained that Desktop AV flagged your website.
Please inform us that your website is targeted at other Internet sites.
Noticed unsanctioned behavior (e.g., creating brand-new users).
When you open up the website in your internet browser, you noticeably see that you have been hacked.
Not all hacks are developed equivalently, so keep this in mind when joining the online forum. The better you understand the signs, the better the team can aid you.
Below is a collection of steps to launch the post-hacking procedure. These are not extensive, as it is unreasonable to consider every circumstance, but they are meant to help you think through the process.
Keep your software program up-to-date
If a protection opening is located in a website’s software program, hackers will promptly manipulate it. This applies not just to the web server OS but also the software program used on the website, such as the CMS and forums. It may be noticeable; however, keeping all software applications up-to-date is vital to preserving site security.
If you use a handled organizing remedy, you should not have to fret excessively regarding applying safety and security updates for your OS, as the organizing firm should care for you.
Safeguard against XSS assaults
XSS (cross-site scripting) attacks infuse harmful JavaScript into a page, which is carried out by the customer’s internet browser and can modify the web content of the web page or swipe information to send back to the enemy. For example, suppose a comment is shown on a web page without validation.
In that case, an assailant might present a remark, including a manuscript string or JavaScript that could be implemented in one more customer’s web browser to swipe login cookies and also gain control of the account of the individual who checked out the comment. Customers should not be able to get active JavaScript content on the page.
This is of particular concern in contemporary internet applications, as web pages are developed mainly from individual material and often produce HTML that is analyzed by front-end frameworks such as Angular and Ember. While these structures use a variety of XSS defenses, the mix of the web server and also client making also opens the opportunity for brand-new, more sophisticated strikes: not only is the shot of JavaScript right into HTML ineffective, but the shot of code-triggering content can be feasible through the insertion of Angular regulations and also the use of Cinder helpers.
What is notable below is how user-generated material strays from the limits of user expectations and how the internet browser analyzes it as different from the individual’s purposes. This is similar to preventing SQL shots. When generating dynamic HTML, utilize features that make the changes you desire (e.g., use element.setAttribute as well as the element.textContent, which the web browser checks immediately rather than setting element.innerHTML manually ), usage design template tool functions that automatically check appropriately as opposed to concatenating strings or setting raw HTML content.
Check your passwords
Every person understands they ought to use complex passwords, yet that doesn’t imply they constantly do. It is critical to utilize strong passwords to your web server and website admin location, but likewise crucial to demand excellent password techniques for your users to protect the safety and security of their accounts.
As long as individuals may not like it, applying password needs such as a minimum of around eight characters, consisting of an uppercase letter and number, will certainly assist in shielding their info in the future.
Passwords must always be stored as encrypted values, preferably using a one-means hashing formula such as SHA. Using this approach indicates when you are validating users, you are just ever before comparing encrypted values. For added internet site safety, it is a good idea to salt the passwords, using a new salt per password.
If somebody is hacking in and taking your passwords, having hashed passwords could help damage restriction, as decrypting them is impossible. The best a person can do is a dictionary attack or brute force strike, guessing every mix until it discovers a suit. Splitting many passwords is also slower when utilizing salted passwords, as every hunch needs to be hashed separately for each salt + password, which is computationally extremely expensive.
The good news is many CMSes offer customer management out of the box with many of these website security features integrated. However, some configuration or extra modules could be needed to use salted passwords (pre-Drupal 7) or to establish the minimum password strength.
If you are using.NET after that, it’s worth using member companies as they are highly configurable, offer inbuilt site protection, and include ready-made controls for login and password reset.
Install safety plugins
If you developed your internet site with a content administration system (CMS), you could enhance your site with security plugins that proactively protect against website hacking attempts.
Each of the significant CMS choices offers safety plugins, some free.
Safety and security plugins for WordPress:
Install safety plugins
iThemes Safety
Bulletproof Security
Wordfence
fail2Ban
Safety and security choices for Magento.
Amasty
Watchdog Pro
Safety and security expansions for Joomla.
Firewall.
Antivirus Web Site Security.
These alternatives attend to the security vulnerabilities inherent in each platform, hindering different hacking attempts that can endanger your internet site.
In addition, all websites– whether running a CMS-managed site or HTML pages— can consider SiteLock. SiteLock goes above and past merely shutting site security loopholes by providing daily monitoring for whatever, from malware discovery to vulnerability recognition to active infection scanning. SiteLock is a financial investment if your organization counts on its site.
Invest in automatic backups
The worst-case circumstance of an internet site hack is to shed every little thing because you forgot to back your website up. You still deal with some risk even if you do whatever else on this listing. The best way to safeguard yourself is to ensure you constantly have a recent backup.
While a data breach will be complex, recovering is much easier when you have a current backup. You can make behavior by manually backing your website up every day or weekly. But if there’s even the tiniest opportunity, you’ll need to remember to buy automatic backups. It’s an inexpensive means to get comfort.
Take precautions when approving data submit via your site
When anybody has the option to submit something to your internet site, they can abuse the advantage by loading a malicious file, overwriting the existing data crucial to your site, or publishing documents so large it brings your whole website down.
Preferably, don’t approve any document uploads with your site. Many local business internet sites can get by without using the option of document posts in any way. If that describes you, you can miss everything else in this step.
Yet eliminating data uploads is only a choice for some websites. Some businesses, like accountants or doctors, must give consumers a means to securely offer records.
If you require allowing file uploads, take a few actions to shield yourself.
Create an allow list of permitted file expansions. By defining which data you’ll accept, you maintain suspicious data kinds out.
Use data kind confirmation. Hackers attempt to sneakily navigate allow list filters by relabeling documents with a different expansion than the record kind or adding dots or rooms to the filename.
Set an optimum file size. Avoid dispersed rejection of service (DDoS) assaults by turning down data over a specific size.
Check to declare malware. Use antivirus software to check all data before opening.
Immediately rename data upon upload. Hackers will not be able to re-access their documents if it has various names when they go trying to find them.
Keep the upload folder outside of the webroot. This maintains cyberpunks from having the ability to access your website via the documents they submit.
These steps can remove most of the susceptibilities in permitting data uploads to your website.
Be Mindful of Website Blacklists
Google Blacklist problems can be damaging to your brand name. Currently, they are blocking around 9,500 to 10,000 sites a day. This number is growing every day. There are different forms of warnings, from huge sprinkle web pages warning users to steer clear of two more refined warnings that turn up in your Search Engine Result Pages (SERPs).
Although Google is among the more popular ones, there are several other blacklist entities like Bing and Yahoo, as well as a wide variety of Desktop computer Antivirus applications.
Understand that your clients/website visitors may utilize any number of tools, and anyone could be causing the issue.
Registering your website with the different internet web designer consoles is recommended.
Google Look Console.
Bing Webmaster.
Yandex Webmaster.
Norton Web designer.
Enhance your Gain Access to Controls
You will typically hear people speaking about updating things like Passwords. Yes, this is an essential item, but its one small item in much bigger trouble. We need to enhance our general stance to gain access to control. This implies using Complicated, Long, and unique passwords, for starters. The most effective suggestion is to use a Password Generator like those discovered in applications like 1Password and LastPass.
Bear in mind that this includes altering all gain access to factors. When we claim to gain access to factors, we indicate things like FTP/ SFTP, WP-ADMIN, CPANEL (or any other administrator panel you make use of with your host), and MYSQL.
This extends beyond your customer and must include all users with access to the environment.
Consider utilizing some form of 2 Element/ Multi-Factor authentication system. In its many essential kinds, it introduces and calls for a second type of authentication when logging into your WordPress circumstances.
Some of the plugins offered to help you with this consist of.
– Rublon
– Duo.
Condition accessibility control
The admin level of your website is a straightforward method into every little thing you do not want a cyberpunk to see. Impose user names and also passwords that cannot be presumed. Modify the default database prefix from “wp6 _” to something arbitrary and tougher to presume.
Restrict the number of login attempts in a given period, even with a password reset, as email accounts can be hacked. Never email login information if an unauthorized individual has accessed the account.
Frequently asked questions
Q: Is WordPress conveniently hack able?
ANS: To start with, it’s not just WordPress. All sites on the net are vulnerable to hacking efforts. WordPress websites are a usual target for hacking because it is the world’s most popular website home builder.
Q: Why does my website maintain obtaining hacked?
ANS: Outdated plugins and styles are the top reason internet sites are hacked. A typical instance from the very early days is TimThumb, a plugin to resize pictures. Susceptibility in the plugin allowed hackers to publish destructive PHP files to websites.
Q: Exactly how do I do away with WordPress viruses?
ANS: How to hand get rid of malware infection from your WordPress data source by:
Log into your database admin panel.
Make a backup of the data source before making changes.
Look for suspicious material (i.e., spammy keywords and malicious links).
Open the row that contains questionable content.
Manually eliminate any questionable web content.
Q: Why is WordPress security critical?
ANS: A hacked WordPress website can cause severe damage to your company’s revenue and reputation. Cyberpunks can steal individual details and passwords, mount destructive software, and even distribute malware to your customers.
Q: What is malware in WordPress?
ANS: Malware is an umbrella term for harmful software applications that leverage a website’s weaknesses for various dangerous activities. In the context of WordPress websites, malware in WordPress can impact a site’s performance to every degree, from the internet server to the user experience, as well as even the website’s SEO performance.
Q: How do I scan a WordPress data source for malware?
ANS: Action 1: Download and install and also install MalCare Protection. Add your website to the MalCare dashboard, and the plugin will certainly start to run a WordPress malware scan on your internet site instantly. Step 2: After scanning your WordPress internet site, MalCare will notify you if it finds malware in your database.
Q: How do I secure my WordPress site with HTTPS?
Use HTTPS on your WordPress site
Step 1 – Log into WordPress, most likely to Plugins. Log right into your WordPress dashboard and click Plugins in the food selection to the left.
Step 2- Mount the Truly Easy SSL plugin. Enter Truly Easy SSL in the search area. …
Step 3 – Activate the plugin. …
Step 4 – Done!
Q: What is MalCare firewall software?
ANS: MalCare supplies an in-built web application firewall program. The firewall program can offer safety and security from cyberpunks and automated robots attempting to access your site. It keeps track of inbound traffic and also IP demands to your website. Avoids access to any dubious or malicious requests.
Bottom line
Millions utilize WordPress across the globe to develop websites and build an online presence. It comes with plenty of attributes as well as a few downsides, as well. You can quickly safeguard your internet site and maintain cyberpunks by implementing the necessary security steps and keeping your website updated. This article assisted you in comprehending what the leading root causes of WordPress websites getting hacked are and how to prevent your website from getting hacked.
Cyberpunks have many methods to break into your WordPress site, and they create brand-new ones ever so often!
It would help if you took protection measures to protect your website and guarantee it’s secure versus hack assaults.
We suggest utilizing our MalCare Security Plugin to secure your WordPress website. It will undoubtedly block hackers and also malicious robots from accessing your website. You can rest assured that your site is being kept an eye on and shielded.
For even more protection, check out Fix Hacked Site. This website security checker scans your site for malware, removing it automatically and protecting your site from attack.
The post <strong>Most common causes of WordPress website hacks and how to stop it</strong> appeared first on Fix Hacked Site.
https://colorlib.com/wp/wp-content/uploads/sites/2/wordpress-booking-plugins.jpg
https://fixhackedsite.com/most-common-causes-of-wordpress-website-hacks-and-how-to-stop-it/?utm_source=rss&utm_medium=rss&utm_campaign=most-common-causes-of-wordpress-website-hacks-and-how-to-stop-it
0 notes