#DLL Injection
Text
how did i mod fnv in the past… it’s taken so long to get to this point. Slamming files randomly into places with an outdated mod loader worked but doing it properly DIDN’T?!!!!
#i got it working.i don’t know how#sometimes it can’t inject the dll sometimes it can. Does this have to do with my 5 year old laptop? Maybe…#pigeonchat
0 notes
Text
ROBLOX 2007 and 2008 RBXGS/RCCService leaks
Yesterday, multiple internal ROBLOX applications ranging from 2007 to 2008 were found and released.
Most of these are RBXGS, which is what ROBLOX originally used for their game servers. It requires a 2003 Windows Server with IIS (Internet Information Services) installed on it to run.
One of these (0.3.784.0, dated 5/13/2008) is another application called RCCService. It fulfills mostly the same purpose that RBXGS did such as rendering avatars and hosting games. RCCService is still used by ROBLOX today. It can be installed and run on your PC without modification.
After a little setup, I was able to render some avatars with it.
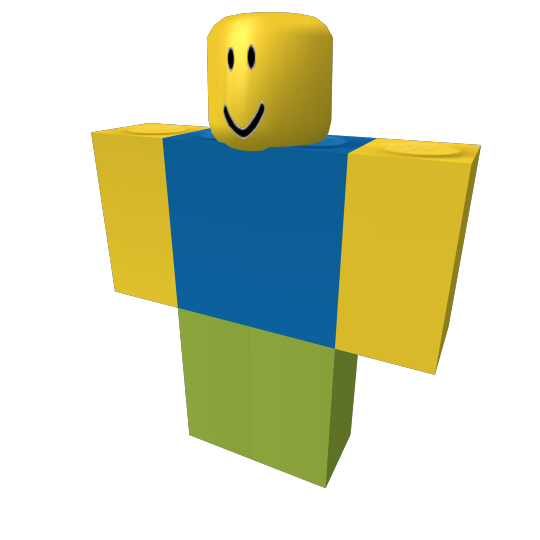
Here's a noob in 4k. We can render in any size we want.

This one is 64x64 large. We can modify any of the properties of the character.

A character with colors, a transparent arm, a missing leg, and a fucked up head. It's looking great! We can also add T-Shirts...

Shirts and pants...

Fucked up faces (they weren't supported in 2008)...

And with a little bit of troubleshooting, hats.

Here's builderman

We can render more than just avatars. We can render parts...
and Places. I could probably do entire models too.

You can do a lot with it if you mess around. You could also implement it into your own website to render avatars automatically and host 2008 games.
Using 2008 RCC to host games also results in more security over self hosted servers.
Player IPs are not exposed if someone attempts to grab them. It only shows the Server IP
Servers automatically shut down if a DLL is injected into a client
RCC checks the version of clients trying to join, and will refuse to connect if it does not match. This can be bypassed if you change the version of the client with a program, though
There are still RCE vulnerabilties in the client, however, so I'd be wary.
Another huge discovery in the RBXGS are PDB files. These files contain symbols (function names), where they are, and line information. Using this makes it much easier to reverse engineer. This means that we might see a reverse engineered 2007 or 2008 ROBLOX source available at one point, if someone decides to make it.
If you wish to check these out for your self, you can download them here.
36 notes
·
View notes
Text
an updated, straightforward guide to modding security breach and its dlc, ruin (including cheats!)
modding fnaf:sb (and by extension, ruin!) is actually pretty simple, but there's a tragic lack of comprehensive text-form guides that actually explain the process -- and a lot of scams out there. so! here's a straightforward guide to modding sb, allowing you to:
freecam
access the debug menu
access the game's console (and associated commands)
...and whatever else you wanna install later!
interested? hit the read more, and we'll get started!
(and if you already have modding experience, just skip to the bolded text for the core instructions)
unlike games like minecraft or the sims, sb doesn't allow the user access to its console (and therefore the ability to manipulate the game); it has no native mod support. this means that we need to modify the game's data to allow 1) mods to be installed, 2) console access and 3) restoring the debug menu. depending on what you want to achieve -- simple console access/freecam or loading mods/debug menu access -- the path forward branches a little. i recommend you do both if you want to bend sb to your whims!
part 1: freecam and basic console access
this process does not require any messing with game files, and is thus the easier of the two. since sb is made using unreal engine, by installing the universal unreal unlocker (or uuu), we can 'unlock' access to free camera movement and the game's console menu, allowing the input of various commands. the direct download link is [here].
it'll download as a zip file (UUU3021.zip). extract its content into a separate folder -- you can put it wherever you want, just don't leave it in downloads -- and run UUUClient.exe to open the program. it should look like this:

process refers to the game you're trying to modify by injecting the DLL into it. the dll we're injecting is the default one, so don't touch that; instead, we need to give it a game to manipulate!
now, open security breach. when security breach is running, select it as the process to be injected into.

then, hit inject dll.

then, just let it do its thing! depending on your hardware, it might take a second for it to process everything, but once it's done it'll give you a little pop-up letting you know it's active. if it doesn't work, try the usual troubleshooting gambit (uninstall reinstall, check you're hitting the right buttons, run program as administrator, ask reddit, etc)...
...aaaaand you're done! you can now access the console! it's bound to ` by default, but you can change that in uuu's configuration tab. it should look like this:

(note that it locks your mouse, so you can't move the player character when it's open!)
using this, you can input a whole bunch of commands, most notably:
toggledebugcamera (lets you unlock the camera from the player character. note that since they're still a physical object, they can still die!)
destroy [entity name here] (deletes the entity mentioned)
destroyAll StaffBotSecurityPatrol_C (deletes all security patrol staffbots! note that they respawn when you die or reload an area.)
summon [entity name here] (self-explanatory!)
viewmode unlit (turns off the lighting effects)
and that's it for method 1! if you want a more complete list of commands, you can find one here. if you're satisfied with this, you can stop here, but if you want access to more traditional 'cheats' (like modifying freddy's power level or triggering game events), we're gonna have to do a bit more. so! continuing on:
part 2: unrealmodloader and restoring the debug menu
this one's way, way more complicated. strap in, because we're about to start modifying the game's files itself. as a safety precaution, you may want to back up your save files to a separate location, in case something goes wrong and you need to reinstall the game again; steam doesn't support cloud saves for sb. if you're using steam, you should find them stored in your local files; the directory should be something like C:\Users\User\AppData\Local\fnaf9\Saved\SaveGames. copy those files somewhere else, and you're good to go!
2.1: installing uml
first, we're going to install unrealmodloader (uml); it's gonna let us modify the game's files on our behalf, which saves you a lot of time learning C++. the download link is [here], and you'll need to extract the file (UnrealModLoader_V2.2.1.rar), same as before. since it's a .rar file, your system probably can't extract it naturally, so you can just download something like 7zip. once extracted, it should look like this:

now, run the uml .exe and then run security breach (without uuu). let it do its thing. is everything loading? is the launcher running? good! as things are, we now have a mod loader without any mods to load. so, onto the complicated part:
2.2: editing local files
we're going to be adding kaydax's debug menu to the game. to do this, we need to mess with the game's files a bit. the file directories will be different depending on where and how you've installed the game -- that's what makes this complicated -- but what's inside them should be the same. if you mess up, just uninstall and then reinstall the game again; it won't affect anything that we've done up to this point.
first: download and extract fnaf_sb_debug_menu_unlocker.zip. (that's a direct download link). open it and find the paks folder. that's the only thing we need.
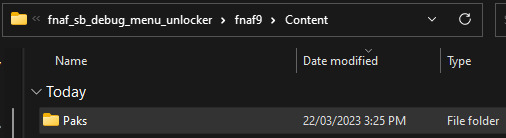
next, open the game's local files. you can do this on steam by going to its library entry, hitting the cog and finding 'browse local files' under 'manage'. if you're not using steam, just go wherever you installed it. it should look like this:

(note: fnaf9 is sb's name in all the files!)
move the paks folder into the content folder. if there's already a paks folder, move the logicmods folder inside it, and if that's already there, just transfer DebugMenu.pak in there yourself. maintaining the file paths is important; if they're broken, the mod won't work.
('coremods' is irrelevant to what we're doing. don't worry about it!)

finally, download the last bit of the debug menu mod from [here]. extract and open it the same as before. this time, we'll be transferring files into the Binaries folder.
move the contents of the Win64 folder (dxgi.dll and Plugins) into your game's Binaries folder. (you shouldn't have to overwrite any existing files, but my memory's fuzzy on that -- my bad! OTL).
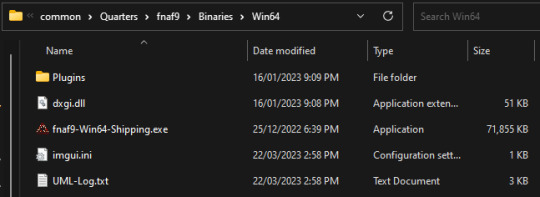
and with that, you have now successfully installed kaydax's debug menu enabler! yippee!
2.3: a brief detour
i'm gonna be honest, this next bit's optional, but definitely something you should do for a smoother experience. kaydax's enabler is great, but it comes with some kinks -- like drifting while in flying mode, or not having any keyboard shortcuts. thankfully, this is easy to fix: just download kokosko's enabler [here] and place it in your paks folder. it should now look like this:

(chowda is ruin, don't worry about it)
congrats! there's just one more thing left to do:
2.4: steam settings
head to the game's entry in your steam library, open the Properties menu, and under Launch Options type -dx11. this makes the game open in DirectX 11, and it's likely to crash without it.

and with that, you're done! run uml when security breach is open, and you're ready to go. you can press f1 ingame to open the mod menu (you'll find the debug menu under logicmods), or (provided you've followed step 2.3) you can just press x. however, if you want uml to open automatically, well... yeah, there's more to do. so!
part 3: automating that shit
because nobody has the time for that!
this is technically explained within uml's files itself, but it felt wrong to not include it here. first, navigate to your uml folder, then from Tools to AutoInjector.

the readme.txt explains what to do, but if that doesn't make sense to you, here's the gist:
3.1: copying files
copy the contents of the AutoInjector folder (minus the readme) into sb's win64 folder, located inside the Binaries folder.
3.2: modify the .ini
open ModLoaderInfo.ini (now in your sb folder) using a program like Notepad. you should see something like this:
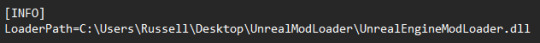
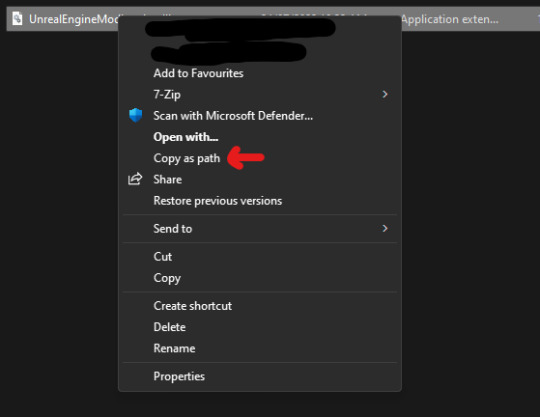
you need to change this address to the location of your UnrealEngineModLoader.dll. you can do this by navigating to your uml folder, right-clicking the file and selecting copy as path.
save the file and close it. when you run sb, the console should automatically open -- and all of your mods with it!
aaaaand congrats, you're done! you have successfully modded security breach. be aware that the game is extremely fragile and very prone to doing weird shit, so don't worry if it, uh, does that. you can find the ruin-specific part of the debug menu under the 'chowda' tab. (no, i don't know why it's called that. don't ask.)
have fun, and happy security breaching!
if you're interested in more mods to download, you can check out gamebanana or nexusmods.
huge thank you to jestxfot, kaydax and kokosko for their work! make sure to support them if you can. :) also feel free to contact me if anything messes up lmao i'll try to help as best i can
#fnaf#five nights at freddy's#fnaf sb#security breach#fnaf9#long post#speaking!#HOPE THIS HELPS!!#now updated for ruin!
25 notes
·
View notes
Note
I don't want to be mean to you, so I am going to try to put this kind of gently. Malware isn't necessarily a virus. Viruses, worms, and malware are all different things. I appreciate you trying to correct your mistake, but gshade is malware at this point because the dev intentionally programmed malicious code. Full PC restarts can do thousands in damages to encrypted drives or any other systems connected, and keep in mind this was all to punish a teenager specifically. This shows explicit aggressive, malicious behavior, which is a pattern with the dev of GShade. Even if it wasn't, even if it was patched out, GShade still contained malware and it is not misinformation to state such. A virus would be misinformation, but you said Malware in your post not virus, and viruses have the intent of infecting as many machines as possible, whereas malware is any malicious code injected into a program. He had already intentionally made his FAQ hard to read (Intentionally long and condescending towards the user asking questions) on the gposers website, and uninstalling using windows utilities / the uninstall button does not completely remove dll files in your game folder, which remain being executed on game launch. I don't personally know what these do, but the fact that many files remain on your computer, with his now history of being malicious towards the user, is sketchy at best. His fork of ReShade also did little more than package a few shaders together to my knowledge, which is a pretty scummy thing to just add files and not modify the original program in any significant way to close the source. I tried to write this politely and concise so please let me know if you have any questions or need anything, and I'm sorry for the way others are acting towards you.
hi! you are not being rude at all, but i would like to state that we did change our language to saying that the program didn't contain a virus in the end when it became more aware that the program was basically reduced to malware. this is also why we eventually encouraged people to do the switch over to reshade since the program could cause harm to your pc, which we eventually also said in a follow up post.
there's nothing we can do to stop the spread of the post that we originally posted, deleting will do nothing but remove us as the source of it but it will still circulate. this is why we made an additional post updating the situation when we eventually had more updates and even linked to a post that contained more well-worded info than what we put out.
do not worry! this is polite, and i hope we come across as polite as well and don't have attitude. but we also want to make it well known that we did correct our info to state that it wasn't a virus but the program/dev eventually was malicious and could cause harm if he really wanted it to.
8 notes
·
View notes
Photo










It took a month but I am now mostly back in business modding for Skyrim, but this time, both for Legendary and Anniversary/Special Editions.
I am blown away by the superior quality of the textures, cities overhauls, NPCs makeover and overall stability improvements.
I even went a little overboard since I am reaching the limits of my load order with more than 620 mods.. so more cleanup will be needed.
So far, I only ran into these issues with playing Skyrim SE/AE:
- You really have to pay attention when installing mods and pick the right version when SKSE plugins and dlls are involved. I am using AE so far and picking the SE version will cause a crash.
- There are MANY SKSE fixes, patches and other tweaks to install as requirements for mods to run. Keep a close watch to requirements when installing mods.
- Some mods crash because of bad textures. I installed an alleged retexture of Estrus for SE and it was causing a crash when the animation triggered. Reinstalling the main Estrus textures fixed it.
- Injecting SexLab and mods into the mix really increased the chance of crashes. That's similar to my experience with LE.
Also, I should add that like with LE, learning to run DynDoLOD and Bashed Patches with Wryebash has been very helpful to keep everything running smoothly.
At this point, I have every mods I wanted back. I am probably missing a few but if I can't remember which, I didn't need them really anyway. I have new textures, new cities, sexlab mods and my own mods set up.
Skyrim SE forced me to try Vortex again (ugh). I am using it as an omod unpacker only. I do my own deployment old school by copying files from the extracted omod in Vortex folders directly into my Data folder. I can't bring myself to trust Mod managers and their virtual profiles.
The goal was to make Skyrim feel new and fun again and it is has been so far!
6 notes
·
View notes
Text

LISNA BEAUTY- Klinik kecantikan dan Skincare
Kulit yang tadinya kencang bisa berubah menjadi kendur karena usia yang semakin bertambah. Ini adalah proses penuaan alami yang ditandai dengan munculnya tanda-tanda seperti garis-garis halus, kerutan, kulit kendur dan sebagainya. Belum lagi permasalahan kulit lainnya yang sering kita temui seperti jerawat, skar atau bekas jerawat, flek hitam ataupun kulit kering.
Permasalahan kulit dan cara mengatasinya menjadi fokus perhatian klinik kecantikan di Surabaya dan sekitarnya. Namun, jangan sampai salah memilih klinik kecantikan untuk menghindari penyesalan di kemudian hari. Klinik kecantikan yang tepercaya dan bisa diandalkan didukung oleh dokter spesialis kulit atau dokter umum yang mendalami bidang estetika medis.
Salah satu Klinik kecantikan Terbaik di Jawa Timur yaitu LISNA BEAUTY, yang mana klinik kecantikan ini sangat populer di kalangan masyarakat Sidoarjo Surabaya pada umumnya. Dengan Harga Terjangkau dan Terpercaya layanan maupun kwalitasnya.
Kunjungi Segera Klinik kecantikan LISNA BEAUTY untuk memanjakan Kulit Wajah Anda menjadi Tampil Cantik dan Awet Muda.
Layanan Klinik Kecantikan LISNA BEAUTY :
Facial Basic
Dermapen
Facial Lightening
Facial Acne
Facial Anti Aging
Facial Detox
Laser Black Doll
Laser Skin Rejuve
Vit C Injection
Dermapen
Infus Whitening
Body Spa
Treatment dll.
Dijamin Anda mendapatkan Harga Terjangkau dan mendapatkan kepuasan Layanan.
Ruko Central Jenggolo No 5c Pucang Sidoarjo -Jawa Timur (61219).
https://lisnabeauty.id
Admin : 08113116779
#beauty#Klinik kecantikan#Skincare#beauty blogger#skincare products#beauty products#Klinik Kecantikan Sidoarjo#Lisna Beauty
2 notes
·
View notes
Text
[Media] Introduction to injection and hooking
Introduction to injection and hooking
• ASLR on Windows
• Process mitigations against RWX pages
• Known DLLs
• Multithreaded environments
• Secure C coding styles
https://github.com/yo-yo-yo-jbo/injection_and_hooking_intro
#cybersecurity #infosec #inject
2 notes
·
View notes
Text
Dawn of war 2 steam crack

#Dawn of war 2 steam crack cracked
#Dawn of war 2 steam crack manual
GTI, WiCKED and rFORCE releases have all made it into private and public BitTorrent trackers across the world. Note that both the 3.66GB and 6.75 GB leaked releases are known to work properly without any missing features – huge difference on file sizes seems to be due to different compression mechanisms used. Users however still need to edit the rev.ini file as per instructions on release NFO.
#Dawn of war 2 steam crack cracked
rForce’s release which is around 6.75GB in file size contains all games files, a batch (.bat) file to automate part of the cracking process as well as a loader & a cracked dll file that bypasses/circumvents steam protection. However the latest release by group rForce (Russian Force – non scene group) seems to have made thing relatively simple.
#Dawn of war 2 steam crack manual
These releases were basically Steam rips and required manual editing of configuration files as well as manual injection of steam encryption keys – a process some pirated found complicated. Initially, there were two versions of the game leaked on BitTorrent -first a 3.66GB version by GTI (Game-Torrents.Info – a Russian torrent tracker) and then another p2p release by WiCKED. No major features seem to be missing, however. EDIT: Leaked release looks like a review copy of the game. Leaked encryption keys are seemingly used to unpack Dawn of War 2 game files while a hacked steam client dll is used to bypass protection. Read all about it in this article.Īlthough we called it a ‘crack’ in the title of this article, the method is basically a workaround similar to the one that was used for FEAR 2. UPDATE: Group ViTALiTY has cracked Dawn of War 2. After the leak of FEAR 2 : Project Origin earlier this month, another steam protected title Warhammer 40000 : Dawn Of War 2 (W40K : DoW2) has again been leaked by pirates before the game’s official Steam release date on most countries. However, the increasing number of Steam protected games that have got cracked or leaked in the past few months cast serious doubts on this claim. Some claim Valve’s Steam as the best anti piracy solution to date.

2 notes
·
View notes
Text
Top Malware: Qbot im Dezember wiederauferstanden

Im Dezember 2023 lag Nanocore auf Platz eins der Malware Charts, Qbot war zurück und die am häufigsten angegriffene Branche war der Bildungs- und Forschungssektor vor dem Gesundheitswesen.
Check Point® Software Technologies hat seinen globalen Bedrohungsindex für Dezember 2023 veröffentlicht. In diesem Monat wurde die Qbot-Malware von Hackern als Teil eines Phishing-Angriffs eingesetzt, der auf Unternehmen im Hotel- und Gastronomie-Gewerbe zielte. Bei der Kampagne gaben sich die Hacker als die US-amerikanische Internal Revenue Service (IRS) aus und versendeten betrügerische E-Mails mit PDF-Anhängen, die eingebettete URLs enthielten und mit einem Microsoft-Installationsprogramm verknüpft waren. Einmal aktiviert, löste dies eine unsichtbare Version von Qbot aus, die eine eingebettete Dynamic Link Library (DLL) nutzte.
Qbot kehrt leider zurück
Bevor Qbot im August 2023 aus dem Verkehr gezogen wurde, dominierte es den Bedrohungsindex und rangierte 10 Monate in Folge unter den drei am weitesten verbreiteten Malwares. Obwohl Qbot nicht wieder auf die Liste zurückgekehrt ist, wird sich nach dieser heimlichen Auferstehungwährend der nächsten Monaten zeigen, ob der Schädling wieder denselben Bekanntheitsgrad erlangen kann, den er zuvorinne hatte.
In Deutschland stand außerdem der Fernzugriffs-Trojaner Nanocore im letzten Monat des vergangenen Jahres wieder an der Spitze der meistverbreiteten Malware, gefolgt von Formbook,das vom Gipfel verdrängt wurde. Auf Platz drei steigt der Remote Access Trojaner Remcos wieder ein.
Top-Malware im Dezember 2023 in Deutschland
*Die Pfeile beziehen sich auf die Veränderung der Rangfolge im Vergleich zum Vormonat.
- ↑Nanocore – Nanocore ist ein Fernzugriffs-Trojaner (RAT), der auf Benutzer von Windows-Betriebssystemen zielt und erstmals 2013 beobachtet wurde. Alle Versionen des RAT enthalten grundlegende Plugins
und Funktionen, wie Bildschirmaufnahmen, Krypto-Währungs-Mining, Fernsteuerung des Desktops und Diebstahl von Webcam-Sitzungen.
- ↓Formbook - Formbook ist ein Infostealer, der auf das Windows-Betriebssystem abzielt und erstmals im Jahr 2016 entdeckt wurde. Er wird in Underground-Hacking-Foren als Malware-as-a-Service (MaaS) vermarktet, da er starke Umgehungstechniken und einen relativ niedrigen Preis hat. Formbook sammelt Anmeldeinformationen von verschiedenen Webbrowsern, sammelt Screenshots, überwacht und protokolliert Tastatureingaben und kann Dateien auf Anweisung von seinem C&C herunterladen und ausführen.
- ↑Remcos - Remcos ist ein RAT, der erstmals 2016 in der freien Wildbahn auftauchte. Remcos verbreitet sich über bösartige Microsoft Office-Dokumente, die an SPAM-E-Mails angehängt sind, und ist so konzipiert, dass er die UAC-Sicherheit von Microsoft Windows umgeht und Malware mit hohen Berechtigungen ausführt.
Top 3 Schwachstellen im Dezember 2023
Im vergangenen Monat waren Apache Log4j Remote Code Execution (CVE-2021-44228) undWeb Servers Malicious URL Directory Traversal die am häufigsten ausgenutzten Schwachstellen, von denen 46 Prozent der Unternehmen weltweit betroffen waren, gefolgt von Zyxel ZyWALL Command Injection (CVE-2023-28771) mit einem weltweiten Anteil von 43 Prozent.
- ↑ Apache Log4j Remote Code Execution (CVE-2021-44228) - In Apache Log4j besteht eine Schwachstelle für Remote Code Execution. Die erfolgreiche
Ausnutzung dieser Schwachstelle könnte einem entfernten Angreifer die Ausführung von beliebigem Code auf dem betroffenen System ermöglichen.
- ↔ Webserver Malicious URL Directory Traversal (CVE-2010-4598, CVE-2011-2474, CVE-2014-0130, CVE-2014-0780, CVE-2015-0666, CVE-2015-4068, CVE-2015-7254, CVE-2016-4523, CVE-2016-8530,CVE-2017-11512, CVE-2018-3948, CVE-2018-3949, CVE-2019-18952, CVE-2020-5410, CVE-2020-8260) - Es besteht eine Directory Traversal-Schwachstelle auf verschiedenen Webservern. Die Sicherheitsanfälligkeit ist auf einen Eingabevalidierungsfehler in einem Webserver zurückzuführen, der die URI für die Verzeichnisdurchquerungsmuster nicht ordnungsgemäß bereinigt. Eine erfolgreiche Ausnutzung erlaubt es nicht-authentifizierten Angreifern, beliebige Dateien auf dem verwundbaren Server offenzulegen oder darauf zuzugreifen.
- ↔ Zyxel ZyWALL Command Injection (CVE-2023-28771) - Eine Command Injection-Schwachstelle existiert in Zyxel ZyWALL. Eine erfolgreiche Ausnutzung dieser Schwachstelle würde entfernten Angreifern erlauben, beliebige Betriebssystembefehle auf dem betroffenen System auszuführen.
Top 3 Mobile Malware im Dezember 2023
Im vergangenen Monat stand Anubis weiterhin an erster Stelle der am häufigsten verbreiteten Handy-Malware, gefolgt von AhMyth und der wieder eingestiegenen Android-MalwareHiddad.
- ↔ Anubis - Anubis ist eine Banking-Trojaner-Malware, die für Android-Mobiltelefone entwickelt wurde. Seit seiner ersten Entdeckung hat er zusätzliche Funktionen erhalten, darunter Remote-Access-Trojaner (RAT), Keylogger, Audio-Aufnahmefunktionen
und verschiedene Ransomware-Funktionen. Er wurde in Hunderten von verschiedenen Anwendungen im Google Store entdeckt
- ↔ AhMyth - AhMyth ist ein Remote-Access-Trojaner (RAT), der 2017 entdeckt wurde. Er wird über Android-Apps verbreitet, die in App-Stores und auf verschiedenen Websites zu finden sind. Wenn ein Nutzer eine dieser infizierten Apps installiert, kann die Malware sensible Informationen vom Gerät sammeln und Aktionen wie Keylogging, das Erstellen von Screenshots, das Versenden von SMS-Nachrichten und das Aktivieren der Kamera durchführen, was in der Regel zum Stehlen sensibler Informationen genutzt wird.
- ↑ Hiddad - Hiddad ist eine Android-Malware, die legitime Apps neu verpackt und sie dann in einem Drittanbieter-Store veröffentlicht. Ihre Hauptfunktion ist die Anzeige von Werbung, aber sie kann auch Zugriff auf wichtige Sicherheitsdetails des Betriebssystems erlangen.
Top 3 der angegriffenen Branchen und Bereiche in Deutschland
- ↑Bildung/Forschung
- ↔Gesundheitswesen
- ↓ ISP/MSP
Der Global Threat Impact Index und die ThreatCloudMap von Check Point basieren auf der ThreatCloud-Intelligence von Check Point. ThreatCloud bietet Echtzeit-Bedrohungsdaten, die von Hunderten von Millionen Sensoren weltweit über Netzwerke, Endpunkte und Mobiltelefone abgeleitet werden. Angereichert wird diese Intelligenz mit KI-basierten Engines und exklusiven Forschungsdaten von Check Point Research, der Forschungs- und Entwicklungsabteilung von Check Point Software Technologies.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Text
Hub. 0812 4900 5758, Bengkel Cat Mobil Rekomendasi di Malang Bengkel Soe Hatt

Hubungi https://wa.me/6285646660934, body repair mobil malang, body repair mobil terdekat, harga body repair mobil penyok, biaya body repair mobil honda, biaya body repair mobil toyota, harga body repair mobil lecet, biaya body repair mobil ayla, repair body mobil cat, body repair mobil fortuner, body repair mobil honda, body repair mobil klasik,
Body Repair Bengkel Soe Hatt Malang
Bengkel Mobil Soe Hatt Malang sangat dicari banyak orang untuk perbaikan dan service berkala mobil. Terdapat 2 layanan yakni Melayani service berkala dan Body Repair. Untuk Service berkala dengan beberapa layanan seperti : Tune Up Injection, Ganti Oli, Dynamo, Accu, Central Lock, Power Window, Alarm, Oderstel, Power Steering, Overhaul.
Selanjutnya dengan Body Repair yang pada umumnya, mereka membutuhkan bengkel body repair karena penyok, terkena goresan saat parkir mobil atau karena kecelakaan. Bukan hal yang salah jika mencari harga termurah tapi kualitasnya kurang. Berbeda dengan Bengkel body repair Soehatt, menawarkan harga termurah dengan kualitas terbaik tentunya. Body repair bengkel Soehatt siap untuk menjadi penyelamat body mobil.
Setiap layanan akan dibantu dengan skill yang mumpuni serta peralatannya yang lengkap mampu membuat mobil anda seperti baru lagi. Body repair bengkel Soehatt juga memfasilitasi perbaikan body kit, cat mobil, compound mobil, pengetokan, salon eksterior dan interior mobil, dll.
Body Repair Bengkel Soe Hatt Malang,
Alamat Showroom :
Jl. Terusan Sudimoro II
Kota Malang
Alamat Body Repair :
Jalan Ikan Kakap Tunjungsekar
Kecamatan Lowokwaru Kota Malang, JawaTimur
(Sebrang SMA Sabilillah Malang)
Hubungi :
BAPAK AHMAD
Telp/WA : 085646660934
#bodyrepairmobil #bodyrepairmobilmalang #ketokmagic #ketokmagicmalang #perbaikanbodymobil #perbaikancatmobil #bengkelmalang #bengkelsoehatt
0 notes
Text
I can't do that cuz shit's weak around here but note/learn all QTEs in Kara's fight against that soldier in Crossroads, use the freecam (dll injection) to disable HUD and record the fight, then make some GIFs for me 👍🏾
#dbh#detroit become human#kara ax400#hate asking people to do shit for me cuz I'm impatient and things gotta be the way i want#but still didn't find a way to record the game without crashing with lack of GPU and RAM#and i gotta play on low quality so...
1 note
·
View note
Text
How Dynamic Link Library Injection Attacks Compromise Mobile Apps

The Dynamic Link Libraries Injection (DLL) attack, a sophisticated cybersecurity technique, can have severe implications for Android and iOS app developers. This attack involves injecting malicious code by manipulating a DLL in the address space of a running program. Here is a technical breakdown of the attack.
Dynamic link libraries (DLLs): DLLs contain executable code that can be used by multiple applications to perform certain functions. The concept is common on Windows-based platforms but can also be used on other platforms.
Mechanism of Injection: An attacker can inject their DLL in the memory space, a legitimate process. Injection is possible through various methods, including process hollowing or reflective DLL injection. Hooking functions such as LoadLibrary can also be used.
Malicious Payload: Typically, the injected DLL contains malicious code. This code may perform various actions, including stealing sensitive information, altering the behavior or the legitimate process, and creating backdoors to further attacks.
Stealthiness DLL Injection Attacks are designed to be stealthy. Injection code is often designed to blend into the legitimate process. This obfuscation makes detection difficult.
Use Cases: Dynamic link library injection attacks achieve various purposes, including privilege escalation and keylogging. They can also spy on the user's activity or subvert security mechanisms in an application.
Mitigation Mobile application developers must ensure their code is secure to defend against dynamic link library injection attacks. Mitigation techniques include validating inputs and implementing secure coding. They also monitor for suspicious behavior during runtime. Code signing, code integrity checking, and address-space layout randomization (ASLR), among other techniques, can help stop injection attempts.
Platform-Specific Considerations: Due to Android and iOS security models, DLL injection on these platforms may differ from Windows. Android developers must be aware of native code interaction, whereas iOS developers must consider code signing and app sandboxing requirements.
A dynamic link library injection attack injects malicious code by manipulating a Dynamic Link Library. This technique severely threatens Android and iOS apps and requires security measures and vigilance to minimize the risks.
I recommend visiting MITRE and Zimperium's Mobile Security Glossary to learn more about mobile security.
0 notes
Text

JASA BODY REPAIR MOBIL MALANG, Hub. 0812 4900 5758, Jasa Body Repair, Ketok Magic Mobil Penyok dan Salon Mobil Interior Exterior di Malang Bengkel Soe Hatt
Hubungi https://wa.me/6281249005758, body repair mobil malang, body repair mobil terdekat, harga body repair mobil penyok, biaya body repair mobil honda, biaya body repair mobil toyota, harga body repair mobil lecet, biaya body repair mobil ayla, repair body mobil cat, body repair mobil fortuner, body repair mobil honda, body repair mobil klasik,
Body Repair Bengkel Soe Hatt Malang
Bengkel Mobil Soe Hatt Malang sangat dicari banyak orang untuk perbaikan dan service berkala mobil. Terdapat 2 layanan yakni Melayani service berkala dan Body Repair. Untuk Service berkala dengan beberapa layanan seperti : Tune Up Injection, Ganti Oli, Dynamo, Accu, Central Lock, Power Window, Alarm, Oderstel, Power Steering, Overhaul.
Selanjutnya dengan Body Repair yang pada umumnya, mereka membutuhkan bengkel body repair karena penyok, terkena goresan saat parkir mobil atau karena kecelakaan. Bukan hal yang salah jika mencari harga termurah tapi kualitasnya kurang. Berbeda dengan Bengkel body repair Soehatt, menawarkan harga termurah dengan kualitas terbaik tentunya. Body repair bengkel Soehatt siap untuk menjadi penyelamat body mobil.
Setiap layanan akan dibantu dengan skill yang mumpuni serta peralatannya yang lengkap mampu membuat mobil anda seperti baru lagi. Body repair bengkel Soehatt juga memfasilitasi perbaikan body kit, cat mobil, compound mobil, pengetokan, salon eksterior dan interior mobil, dll.
Body Repair Bengkel Soe Hatt Malang,
Alamat Showroom :
Jl. Terusan Sudimoro II
Kota Malang
Alamat Body Repair :
Jalan Ikan Kakap Tunjungsekar
Kecamatan Lowokwaru Kota Malang, JawaTimur
(Sebrang SMA Sabilillah Malang)
Hubungi :
BAPAK AHMAD
Telp/WA : 081249005758
#bodyrepairmobil #bodyrepairmobilmalang #ketokmagic #ketokmagicmalang #perbaikanbodymobil #perbaikancatmobil #bengkelmalang #bengkelsoehatt
0 notes
Text
Firefox Release 115.0.2 , For Linux, Windows, & macOS
版本號:115.0.2
官方下載: https://www.mozilla.org/zh-TW/firefox/all
更新項目:
修復
Fixed a startup crash experienced by some Windows 10 and 11 users by blocking instances of a malicious injected DLL (bug 1841751)
Fixed a bug with displaying a caret in the text editor on some websites (bug 1840804)
Fixed a bug with broken audio rendering on some websites (bug 1841982)
Fixed a bug with patternTransform…
View On WordPress
1 note
·
View note
Text
Letting users block injected third-party DLLs in Firefox
https://hacks.mozilla.org/2023/03/letting-users-block-injected-third-party-dlls-in-firefox/
0 notes
Text
Object Placement in Sonic Frontiers
Warning: Big nerdy technical post on a highly-specific topic I happen to know something about.
Thought it might be cool to explain a little bit about how object placement works in Sonic Frontiers.
Each "map" in Sonic Frontiers (the islands and the cyberspace levels) has object placement data associated with it, stored in the game's .gedit files. These objects are separated into different object "layers", of which any map can have several.
There could be, for example, a layer for the main objects that actually make up the level (like rings, springs, dash panels, enemies, etc.), a layer for "decoration" objects (like bushes, and particle effects), a layer for "sound" objects (like wind, water, and other ambient noises), a layer for "camera" objects (like camera change triggers), etc.
Each layer is represented as a single .gedit file which contains a list of every object in that layer.
Each object inside of these .gedit files has, amongst other things, a name, a UUID (16-byte random "number" that serves as a unique identifier that is specific to this object in particular), a position and rotation, and a type, which is represented as a string such as "Ring", "Spring", or "DashPanel".
They also each have a block of data which contains all of the parameters for that object (e.g. the speed of a dash panel, or whether a ring can be light-speed-dashed, or what FOV to use for the camera in this particular area, etc. etc.).
Now, as for what values exactly are stored in that block of data, and even just how big that block of data is, unfortunately, none of that information is stored anywhere inside of the .gedit files!
Instead, that information is "hardcoded" into the game. That is, the game has a bunch of structs for each object type, such as this one for Ring objects:
struct ObjRingSpawner
{
enum class Visibility : char
{
Visible = 0,
Invisible = 1
};
Visibility visibility;
float respawnTime;
PathMovement pathMovement;
};
("PathMovement" here is another struct type from the game that I removed for brevity)
The game is then simply programmed such that, if it sees an object of type "Ring" in the .gedit data, then it should just treat that object's block of parameters as though it is one of those ObjRingSpawner structs. Basically, it has a specific mapping between each object type and its corresponding struct.
This is efficient, both in terms of file size and code runtime. It just unfortunately also makes things a lot harder for us modders. :)
How can we read and write all of this object parameter data in our own tools?
Thankfully, Sonic Team also has "reflection" data that they auto-generated for each of these structs/enums, which they used in their own internal level editor to, e.g., display object parameter names to the level designers.
For Sonic Frontiers, it turned out that all of this reflection data was leftover in the final game! So, I worked with Skyth to program a custom .dll file that we could inject into the game to make it grab all of this reflection information from its own memory and dump it into a file. The result: frontiers.json !
This file contains information describing all of the enum, struct, and object types used by the game for all of its object placement data. Anyone is free to use it in their own mod tools, or however you'd like!
In HedgeSet (my command-line-tool for editing object placement data in Sonic games, including these .gedit files), I read this frontiers.json file, then, I use the information in it to read/write all of the object parameters for every object from/to the .gedit files.
It took some time for me to get everything right, including specific details like struct field alignment, but after a few weeks of work, I got everything working, and with 100% byte-perfect accuracy!
But then, ĐeäTh noticed something strange while using HedgeSet to develop his (awesome) Kronos Island Reunited mod: It seemed my tool was reading some object parameters incorrectly from a few very specific .gedit files from the Nintendo Switch version of the game?!
We looked into it, and after some time, discovered the problem: In very specific circumstances, the C++ compilers Sonic Team used for the PC/Xbox versions of the game handle struct field alignment slightly differently than the C++ compilers Sonic Team used for the Nintendo/PlayStation versions!
Specifically, if you have structs like this:
struct A
{
int32_t a;
uint8_t b;
};
struct B : A
{
uint8_t c;
};
Both GCC/Clang-based compilers and Microsoft compilers will lay out the memory of the A struct in the same way, like this:
AA AA AA AA BB 00 00 00
However, GCC/Clang-based compilers will lay out the memory of the B struct like this:
AA AA AA AA BB CC 00 00
Whereas Microsoft compilers will lay out the memory of the B struct like this:
AA AA AA AA BB 00 00 00 CC 00 00 00
GCC/Clang are both taking advantage of an optimization allowed by the C++ standard to save some space, whereas Microsoft compilers do not do this optimization, presumably to keep things simpler.
Because of these compiler differences, the layout of the struct data in the .gedit files differed between game versions, but only for structs that happened to follow this highly specific pattern, which were very few! I'm honestly surprised that we even noticed this issue!
In any case, the released version of HedgeSet handles this as well by simply asking you what version of the game to use (pc, xbox, switch, ps4, or ps5), and using the correct struct alignment rules when reading/writing .gedit data for that version.
It's been a journey, but I can confidentally say, after months of work, that HedgeSet fully supports the .gedit format used by Sonic Frontiers.
But, this is just the beginning!
In addition to my HedgeSet tool, I've also been developing a visual editor called HedgeEdit, which will allow you to fly around the maps from the game and edit its objects visually.
This is quite an ambitious project, and has been taking a lot of time to develop, especially with recent life events. But, I hope to finally get a usable build of it out sometime this year.
Soon, I plan to write a post describing my plans for HedgeEdit in detail, both in terms of design/ideas for the project, and in terms of code details. If you're interested in any of that, stay tuned!
Also, if you don't know, most of my stuff is open-source!
For more information on how the gedit format works, for example, check out my code to read/write .gedit files in HedgeSet!
1 note
·
View note