#infosecurity
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
61 notes
·
View notes
Text
[Media] Practical IoT Hacking
Practical IoT Hacking
A comprehensive guide to testing and exploiting IoT systems and devices. Written by expert security researchers, the book covers common threats and a threat modeling framework, security testing methodologies, and passive reconnaissance techniques.
Readers will learn how to assess security on all layers of an IoT system, perform VLAN hopping, crack MQTT authentication, abuse UPnP, craft WS-Discovery attacks, and tackle hardware and radio hacking.
The book also covers developing an NFC fuzzer, hacking a smart home, and more. The tools and devices used in the book are affordable and readily available, making it a valuable resource for security researchers, IT teams, and hobbyists.
Buy online:
🛒 https://amzn.to/3mzbqPG
#book #IoT

35 notes
·
View notes
Text
so a lot of people are panicking about the new data breach but like. its not even new data. the source was an incorrectly configured server for a search engine that allows you to check if you're in a data breach (painful painful irony)
your tumblr passwords are most likely safe (assuming you don't use the same password for other websites like twitter), but it can't hurt to change them now if you'd like.
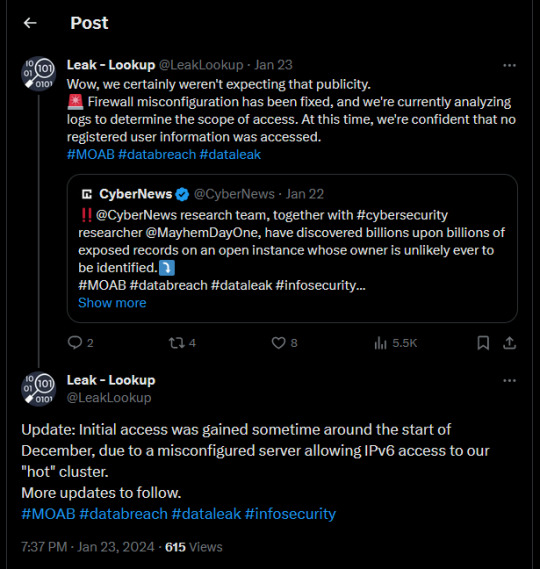
4 notes
·
View notes
Text
'Unpatchable' Vulnerability Found In Apple's Silicon #itnews #infosec
#vulnerability#apple music#apple#apple news#infosecurity#infosecawareness#infosec#infotech#information technology#it#i.t.#world news#breaking news#celebrity news#latest news#news#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#mobilephone#mobile phones#phones#technology
2 notes
·
View notes
Text
very useful & important primer for anyone interested in having a modicum of digital privacy xo
#Me Fein#The cliffnotes are. U can't. However! U should try anyway#infosec#infosecurity#it could happen here#I'm a weirdo who doesn't like being spied on. For no particular reason#So I've been into infosec in a vaguely Luddite and belligerent way for years#digital privacy#robert evans#Karl kasarda
31 notes
·
View notes
Text
Cyber Security Jobs UK

If your looking for the best cyber security jobs in the UK visit https://cybersecurityjobs.uk today which includes the best infosec jobs and cyber career opportunities online at the website for UK information security specialists
4 notes
·
View notes
Text
Is it possible to refresh short-lived access tokens without using refresh tokens?
How can refresh token rotation ensure that refresh tokens can be stored securely in single page web apps?
Some links for reference:
Why are Refresh Tokens considered insecure for an SPA? | SA
What is the purpose of a "Refresh Token"? | SA
What Are Refresh Tokens and How to Use Them Securely | auth0
A Critical Analysis of Refresh Token Rotation in Single-page Applications | pingidentity
#security#oauth2#authentification#authorization#tech#technology#programming#help#cyber security#hackers#hacking#infosec#infosecurity#software#tech memes#open source#stack overflow#golang#nodejs
19 notes
·
View notes
Text
Hello!
This page is for hacktivism, or pretty much anything tech. Nice to meet you! Happy pwning!
4 notes
·
View notes
Text


GIF and Still-art of ASCII hacker at his laptop, hacking away. Created for use in a cybersecurity product, and they preferred a not "obviously fake" photo of a hacker
1 note
·
View note
Text

INFOSECURITY is a top-level exhibition for information security that is taking place soon! You can connect with us at https://expostandservice.com/ for the best exhibition here!
#Infosecurity#informationsecurity#Security#Exhibition#exhibitionbuilder#Exhibitionstand#exhibitiondesign#exhibitionstand#standdesign
0 notes
Text
The Best Phone Hackers in USA to Catch a Cheater

Why need Phone Hackers?
In today’s digital age, the need for phone hackers arises from the necessity to uncover truths hidden within the vast realm of technology. As relationships become entwined with digital communication, suspicions of infidelity often lead individuals to seek concrete evidence. Phone hackers serve as the key to unlocking this evidence, delving into the intricate layers of digital devices to retrieve deleted messages, call logs, and other incriminating data.
Their expertise enables individuals to confront their suspicions with confidence, bringing clarity and closure to uncertain situations. Whether it’s confirming suspicions of a cheating partner or safeguarding against potential threats to privacy, phone hackers offer a valuable service in navigating the complexities of modern relationships.
Related: Do You Want to Track Your Unfaithful Wife’s Phone?
Importance of Catching a Cheater
The importance of catching a cheater cannot be overemphasized enough in the realm of relationships. Discovering infidelity is pivotal for individuals seeking clarity and closure in their partnerships. With the assistance of phone hackers, gathering concrete evidence becomes feasible, enabling individuals to confront their suspicions with tangible proof. This evidence serves as a catalyst for resolution, allowing couples to address underlying issues or make informed decisions about the future of their relationship.
Without this crucial step, doubts and uncertainties can linger, potentially causing further harm to the trust and integrity of the relationship. Thus, the role of phone hackers in uncovering infidelity extends beyond mere investigation; it becomes a vital tool for individuals navigating the complexities of trust and betrayal, ultimately paving the way for healing and growth.
When it comes to catching a cheater, employing a combination of strategies can significantly increase the likelihood of uncovering the truth. Here are some key ways to catch a cheater, along with additional insights:
Ways to catch a cheater
To catch a cheater, individuals often monitor their partner’s digital activity, observe changes in behavior, and may use GPS tracking. Seeking professional help, like hiring a private investigator or a phone hacker, can also provide valuable assistance in gathering evidence. Here are some indicators:
Monitor Digital Activity:
Keep a close eye on your partner’s digital footprint by regularly checking their text messages, emails, and social media interactions. Look out for any unusual or secretive behavior, such as quickly closing apps or hiding screens when you’re around.
Check Call Logs and Contacts:
Take note of any suspicious numbers in your partner’s call logs or contacts list. Look for frequent communication with unknown contacts or numbers that appear at odd hours, indicating potential covert communication.
Use GPS Tracking:
Consider utilizing GPS tracking devices or smartphone apps to monitor your partner’s movements and whereabouts. This can provide valuable insights into their activities, especially if they provide vague or inconsistent explanations for their whereabouts.
Observe Changes in Behavior:
Pay attention to any sudden changes in your partner’s behavior or routine. Be on the lookout for increased secrecy, unexplained absences, or a sudden lack of interest in spending time together. These could be signs of infidelity.
Trust Your Instincts:
Don’t ignore your gut feelings. If you have a strong suspicion that something isn’t right in your relationship, trust your instincts and investigate further. Gut feelings are often a reliable indicator of underlying issues that need to be addressed.
Seek Professional Help:
If you’re unable to gather evidence on your own or feel overwhelmed by the situation, consider seeking the assistance of a professional. A private investigator can conduct thorough surveillance and gather evidence on your behalf. Alternatively, reputable phone hackers specialize in uncovering digital evidence that can shed light on the truth.
Factors to Consider When Hiring a Phone Hacker
When considering hiring a phone hacker, it’s crucial to take several factors into account to ensure a successful and legally compliant outcome. Here are some key factors to consider:
Reputation and Reviews:
Research the reputation of the phone hacker and look for reviews from previous clients. A reputable hacker with positive feedback indicates reliability and trustworthiness in handling sensitive matters.
Skill and Expertise:
Assess the hacker’s skills and expertise in digital forensics and ethical hacking. Look for certifications or evidence of successful cases that demonstrate their proficiency in navigating complex security systems while adhering to legal boundaries.
Legal Considerations:
Ensure that the services provided by the hacker comply with legal regulations. Engaging in illegal activities can have severe consequences, both legally and ethically. Verify that the hacker operates within the bounds of the law and respects privacy rights.
Conclusion
In conclusion, phone hackers play a crucial role in uncovering infidelity and providing closure to those affected by dishonesty. By choosing reputable and skilled professionals, individuals can gather concrete evidence ethically and legally, empowering them to make informed decisions about their relationships.
#companies#cyber security#automation#digital transformation#hack#cyberattack#cybersecurity#cybercrime#developers & startups#infosecurity#phone hacker#cell phone hacker
1 note
·
View note
Text
Infosecurity Exhibitor List 2024

Infosecurity 2024 is the largest information security professional conference in Europe. Connect with industry specialists with our Infosecurity Exhibitor List 2024!
0 notes
Text
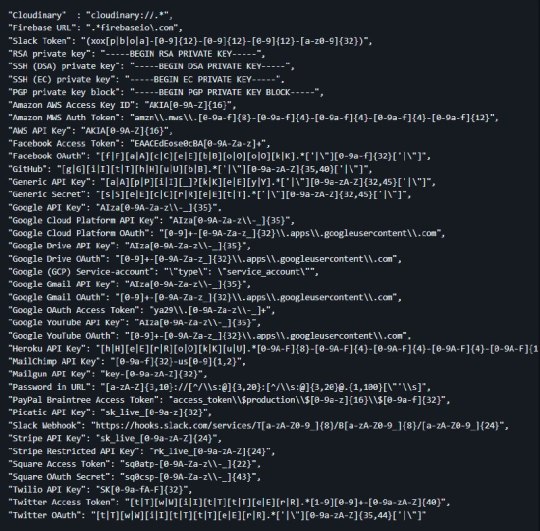
[Media] Secret Regex List
Secret Regex List
List of regex for scraping secret API keys and juicy information. You can directly copy this and put into your python code, some regexes might require three quotes or else it will break the code.
https://github.com/h33tlit/secret-regex-list
#infosec #pentesting #bugbounty
14 notes
·
View notes
Text

arguing for people to write down and admit to what they own. #infosec #inventory #assets #cmdb
0 notes
Text
They added that “80 percent of Faceless bots are located in the United States, implying that accounts and organizations within the US are primary targets. We suspect the bulk of the criminal activity is likely password spraying and/or data exfiltration, especially toward the financial sector.”
The researchers went on to say that more traditional ways to anonymize illicit online behavior may have fallen out of favor with some criminals. VPNs, for instance, may log user activity despite some service providers' claims to the contrary. The researchers say that the potential for tampering with the Tor anonymizing browser may also have scared away some users.
The second post came from Satori Intelligence, the research arm of security firm HUMAN. It reported finding 28 apps available in Google Play that, unbeknownst to users, enrolled their devices into a residential proxy network of 190,000 nodes at its peak for anonymizing and obfuscating the Internet traffic of others.
0 notes
Text
Insider Threats: Understanding, Mitigation, and Prevention Strategies
Explore the intricate world of insider threats in cybersecurity, uncovering their nature, motivations, and strategies for mitigation and prevention. Understand the risks and consequences posed by insiders, and learn how organizations can defend against these formidable challenges. Stay informed, stay secure, and prioritize proactive measures to safeguard sensitive data and assets.

Read More..
#InsiderThreats#Cybersecurity#Mitigation#Prevention#DataSecurity#RiskManagement#InfoSec#SecurityStrategies#InsiderRisk#DataProtection#CyberDefense#InfoSecurity#ITSecurity#RiskMitigation#SecurityAwareness
0 notes