#CYBER SECURITY COMPANIES
Link
Cyber Security Services in UAE and other Gulf countries
#cyber security services#cybersecurity services#network security in networking#network and network security#cloud computing security#cyber security companies#computer security companies#top cyber security companies#Cyber security solutions#Cybersecurity solutions
0 notes
Link
Just over a quarter-century ago, the first Chief Information Security Officer (CISO) was minted in the financial vertical, and everyone lived happily ever after. The End.
If only this story was that simple and straightforward! The CISO role has never been cut-and-dry. Despite its longevity, this role is still in its adolescence – full of promise, mostly headed in the right direction, but not quite fully formed.
0 notes
Text
How Cyber Security Companies Help Small Businesses
There are millions of small businesses in the United States, providing jobs and stimulating the economy. But, these businesses are also vulnerable to cyber-attacks.
A recent National Small Business Association report found that almost two-thirds of small businesses have been hacked at some point. Breaches in cyber security can lead to lost profits and even bankruptcy in some cases.

Cyber security is incredibly important. If you don't have a high level of security, you're at risk. So what does cyber security mean?
Cyber security is not just about protecting your computers from viruses or malware—it also is ensuring that your data is safe and secure, even if someone manages to break into your network. Breaches can happen in an instant.
Small businesses often need more resources to secure their networks properly, and they may need to realize how important it is for them to do so. That's where cyber security companies for small businesses come in.
Cyber security companies help entrepreneurs and small and medium-sized businesses with everything from setting up firewalls to managing their passwords and updating their software. They also offer proper protections and provide them with the tools they need to protect themselves against threats like ransomware attacks and phishing emails.
A cyber security company will monitor your systems for any potential issues, and alert you when there's an issue so you can take action before it becomes a problem. They will also provide solutions, in the event that an attempted attack or actual breach takes place. The company can also educate your employees on how best to keep their information safe and secure online—which means fewer risks for your business!
Every small business owner must protect their data —by investing in cybersecurity measures and hiring a cyber security company. While using a company may seem expensive at first glance, it will pay off in the long run as they can help you avoid costly data breaches or other problems caused by hackers.
#cyber security company#Cyber security companies#cyber security companies for small businesses#cyber security
0 notes
Text
7 notes
·
View notes
Text
#it support in Los Angeles#businesses#companies#home theater#cyber security#security camera#business setup services in la#network services#network security
2 notes
·
View notes
Text
// made lil tweaks to my criminal verse. at the very least i now know what ig actually does there
#ERROR ( );#// (cyber)security company called cerberus inc.? u bet#// greedy bastard as he is he also likes to expand his influence so its like a parent company to some smaller things also named after#// characters from the greek mythology. because why not#// on top of all the. Very Secret Crime Stuff#// anyway i'm getting my meds tomorrow. 🙏
2 notes
·
View notes
Text
The Biggest Thing About Top IT Companies In India
The Biggest Thing About Top IT Companies In India
Nowadays, the facts era ( IT ) is the maximum well-known enterprise withinside the international. It has the strength to convert the mind of the customers into reality. The agencies that offer facts era offerings are called IT agencies. The IT agencies are running on technology like gadget learning, networking, cloud, net of things, net technology and cell technology, etc. IT companies are…

View On WordPress
#2022 new technology#Biggest Thing About Top IT Companies#BPO#cell technology#cognitive business operations#consulting#cyber security#Cybersecurity#Digital operations & Platforms#GRC services#HCL Technologies#Information Technology#Infosys#Infrastructure services#IT Companies#IT Companies in india#IT services#latest technology trends#net technology#new technology news#Product manufacturing#quality engineering#Tata Consultancy Services#Tech Mahindra#Top IT Companies#VLSI design services#Wipro
6 notes
·
View notes
Text
Clearing the “Fog of More” in Cyber Security
New Post has been published on https://thedigitalinsider.com/clearing-the-fog-of-more-in-cyber-security/
Clearing the “Fog of More” in Cyber Security
At the RSA Conference in San Francisco this month, a dizzying array of dripping hot and new solutions were on display from the cybersecurity industry. Booth after booth claimed to be the tool that will save your organization from bad actors stealing your goodies or blackmailing you for millions of dollars.
After much consideration, I have come to the conclusion that our industry is lost. Lost in the soup of detect and respond with endless drivel claiming your problems will go away as long as you just add one more layer. Engulfed in a haze of technology investments, personnel, tools, and infrastructure layers, companies have now formed a labyrinth where they can no longer see the forest for the trees when it comes to identifying and preventing threat actors. These tools, meant to protect digital assets, are instead driving frustration for both security and development teams through increased workloads and incompatible tools. The “fog of more” is not working. But quite frankly, it never has.
Cyberattacks begin and end in code. It’s that simple. Either you have a security flaw or vulnerability in code, or the code was written without security in mind. Either way, every attack or headline you read, comes from code. And it’s the software developers that face the ultimate full brunt of the problem. But developers aren’t trained in security and, quite frankly, might never be. So they implement good old fashion code searching tools that simply grep the code for patterns. And be afraid for what you ask because as a result they get the alert tsunami, chasing down red herrings and phantoms for most of their day. In fact, developers are spending up to a third of their time chasing false positives and vulnerabilities. Only by focusing on prevention can enterprises really start fortifying their security programs and laying the foundation for a security-driven culture.
Finding and Fixing at the Code Level
It’s often said that prevention is better than cure, and this adage holds particularly true in cybersecurity. That’s why even amid tighter economic constraints, businesses are continually investing and plugging in more security tools, creating multiple barriers to entry to reduce the likelihood of successful cyberattacks. But despite adding more and more layers of security, the same types of attacks keep happening. It’s time for organizations to adopt a fresh perspective – one where we home in on the problem at the root level – by finding and fixing vulnerabilities in the code.
Applications often serve as the primary entry point for cybercriminals seeking to exploit weaknesses and gain unauthorized access to sensitive data. In late 2020, the SolarWinds compromise came to light and investigators found a compromised build process that allowed attackers to inject malicious code into the Orion network monitoring software. This attack underscored the need for securing every step of the software build process. By implementing robust application security, or AppSec, measures, organizations can mitigate the risk of these security breaches. To do this, enterprises need to look at a ‘shift left’ mentality, bringing preventive and predictive methods to the development stage.
While this is not an entirely new idea, it does come with drawbacks. One significant downside is increased development time and costs. Implementing comprehensive AppSec measures can require significant resources and expertise, leading to longer development cycles and higher expenses. Additionally, not all vulnerabilities pose a high risk to the organization. The potential for false positives from detection tools also leads to frustration among developers. This creates a gap between business, engineering and security teams, whose goals may not align. But generative AI may be the solution that closes that gap for good.
Entering the AI-Era
By leveraging the ubiquitous nature of generative AI within AppSec we will finally learn from the past to predict and prevent future attacks. For example, you can train a Large Language Model or LLM on all known code vulnerabilities, in all their variants, to learn the essential features of them all. These vulnerabilities could include common issues like buffer overflows, injection attacks, or improper input validation. The model will also learn the nuanced differences by language, framework, and library, as well as what code fixes are successful. The model can then use this knowledge to scan an organization’s code and find potential vulnerabilities that haven’t even been identified yet. By using the context around the code, scanning tools can better detect real threats. This means short scan times and less time chasing down and fixing false positives and increased productivity for development teams.
Generative AI tools can also offer suggested code fixes, automating the process of generating patches, significantly reducing the time and effort required to fix vulnerabilities in codebases. By training models on vast repositories of secure codebases and best practices, developers can leverage AI-generated code snippets that adhere to security standards and avoid common vulnerabilities. This proactive approach not only reduces the likelihood of introducing security flaws but also accelerates the development process by providing developers with pre-tested and validated code components.
These tools can also adapt to different programming languages and coding styles, making them versatile tools for code security across various environments. They can improve over time as they continue to train on new data and feedback, leading to more effective and reliable patch generation.
The Human Element
It’s essential to note that while code fixes can be automated, human oversight and validation are still crucial to ensure the quality and correctness of generated patches. While advanced tools and algorithms play a significant role in identifying and mitigating security vulnerabilities, human expertise, creativity, and intuition remain indispensable in effectively securing applications.
Developers are ultimately responsible for writing secure code. Their understanding of security best practices, coding standards, and potential vulnerabilities is paramount in ensuring that applications are built with security in mind from the outset. By integrating security training and awareness programs into the development process, organizations can empower developers to proactively identify and address security issues, reducing the likelihood of introducing vulnerabilities into the codebase.
Additionally, effective communication and collaboration between different stakeholders within an organization are essential for AppSec success. While AI solutions can help to “close the gap” between development and security operations, it takes a culture of collaboration and shared responsibility to build more resilient and secure applications.
In a world where the threat landscape is constantly evolving, it’s easy to become overwhelmed by the sheer volume of tools and technologies available in the cybersecurity space. However, by focusing on prevention and finding vulnerabilities in code, organizations can trim the ‘fat’ of their existing security stack, saving an exponential amount of time and money in the process. At root-level, such solutions will be able to not only find known vulnerabilities and fix zero-day vulnerabilities but also pre-zero-day vulnerabilities before they occur. We may finally keep pace, if not get ahead, of evolving threat actors.
#ai#ai tools#Algorithms#Application Security#applications#approach#AppSec#assets#attackers#awareness#Business#code#codebase#coding#Collaboration#communication#Companies#comprehensive#compromise#conference#creativity#cyber#cyber security#Cyberattacks#cybercriminals#cybersecurity#data#detection#developers#development
0 notes
Text
Get Evidence Through Email Hacks Service

Why Need to Email Hacks❓
The significance of tackling email hacks is crucial in today’s digital age. Email has become essential for personal and professional communication, even financial transactions. Yet, it’s not immune to threats. Email hacks jeopardize our privacy and security, potentially exposing personal data or infiltrating corporate networks, causing financial and reputational harm.
Hence, it’s vital to take proactive steps like using strong passwords, enabling two-factor authentication, and staying alert to phishing attempts. Recognizing the need to address email hacks helps individuals and organizations defend against cyber threats and secure their online communication.
🔰What Types of Evidence Can Get by Email Hacks?
Email, a treasure trove of information, is a prime target for hackers after valuable data. Compromised email accounts offer various types of evidence to perpetrators, revealing sensitive information ripe for misuse or exploitation. Here’s a breakdown of the evidence obtainable through email hacks:
👉Personal Information: Within email conversations and contact lists lie a wealth of personal details, including names, addresses, phone numbers, and birthdates. Such information is highly valuable to cybercriminals for various malicious purposes, from identity theft to social engineering attacks.
👉Financial Data: Email accounts often contain a trail of financial transactions, statements, and banking credentials. If compromised, hackers can exploit this information for financial gain, committing fraud, or accessing sensitive accounts.
👉Sensitive Correspondence: Email exchanges frequently involve discussions on confidential matters, agreements, or negotiations. Hackers can weaponize this information for blackmail, extortion, or other illicit activities, potentially causing significant harm to individuals or organizations.
👉Login Credentials: The compromise of email login credentials poses a grave risk as it grants hackers access not only to the email account itself but also to any other accounts linked to it. This domino effect amplifies the repercussions of a single security breach.
👉Intellectual Property: Companies frequently communicate sensitive information, including proprietary data, trade secrets, and product designs, via email. Infiltrating these communications can lead to the theft of intellectual property, undermining competitive advantages and innovation efforts.
How to Get Evidence Through Email Hacks❓
When it comes to obtaining evidence through email hacks, it’s essential to proceed with caution and adhere to legal and ethical standards. Here are some steps to guide you through the process:
⏭️Assess the Situation: Begin by thoroughly assessing the situation at hand. Determine the relevance and necessity of accessing the email account for gathering evidence. Consider the potential implications and consequences of your actions.
⏭️Document Everything: Maintain meticulous documentation throughout the entire process. Record relevant details such as timestamps, IP addresses, and any communication exchanges related to the email hack. This documentation may serve as evidence and support your actions in legal proceedings.
⏭️Secure Authorization: Obtain explicit authorization or consent from relevant parties before accessing or retrieving any evidence from the compromised email account. Additionally, this could include obtaining consent from the account holder, legal representatives, or law enforcement authorities, depending on the circumstances.
⏭️Use Secure Methods: Employ secure and encrypted communication channels and tools when accessing and retrieving evidence from the compromised email account. This helps prevent the unauthorized interception of sensitive information and ensures the integrity of the evidence collected.
⏭️Minimize Disruption: Take measures to minimize disruption to the compromised email account and preserve its integrity throughout the investigation process. Avoid altering or deleting any data unless absolutely necessary, as tampering with evidence could have legal repercussions.
⏭️Report the Incident: If you suspect unauthorized access or criminal activity related to the email hack, promptly report the incident to the appropriate authorities or cybersecurity experts. Provide them with all relevant information and documentation to facilitate a thorough investigation and resolution of the matter.
📌Choosing the Right Email Hacks Service
When picking an email hacks service, it’s vital to choose carefully for security and reliability. HackersList is a standout choice, known for its top-notch services and skilled professionals. They offer a comprehensive solution to protect email accounts from threats, including penetration testing and incident response. With HackersList, your online communication is in capable hands, ensuring peace of mind in navigating the digital landscape.
Final Word
The idea of obtaining evidence through email hacks may raise ethical and legal concerns. But there are situations where it can be justified and necessary. By understanding the risks and considerations involved, individuals can make informed decisions about whether to utilize email hacking services and ensure that any evidence obtained is obtained and used responsibly.
#automation#companies#cyber security#cyberattack#cybercrime#hack#email hack#email hacker#hackerslist#hackerslistco
0 notes
Link
Online shopping has become the standard for the holiday season as consumers scramble to make purchases, choose gifts, and ensure everything arrives in time and all wrapped up for gift-giving events. Insider Intelligence and eMarketer projected that e-commerce sales in the U.S. will surpass $1 trillion in 2022.
0 notes
Text
Strengthen Your Business Networks with Top Network Security Solutions in Dubai
In today's interconnected world, where businesses rely heavily on digital networks for communication, collaboration, and operations, ensuring the security of these networks is paramount. Cyber threats such as malware, ransomware, and data breaches pose significant risks to businesses of all sizes, making it essential to invest in robust network security solutions. In this article, we will explore the critical role of network security solutions, the expertise of networking companies in Dubai, and additional points highlighting the importance of safeguarding your business networks against cyber threats.
Understanding Network Security Solutions:
Network security solutions encompass a wide range of technologies, practices, and protocols designed to protect an organization's network infrastructure from unauthorized access, data breaches, and cyber attacks. These solutions include firewalls, intrusion detection systems, encryption, access controls, and security assessments, among others, all aimed at safeguarding sensitive data and ensuring the integrity and availability of network resources.
The Role of Networking Companies in Dubai:
Networking companies in Dubai play a crucial role in helping businesses design, implement, and maintain secure and reliable network infrastructures. With a deep understanding of local regulations, industry standards, and emerging technologies, these companies offer tailored solutions that address the unique needs and challenges faced by businesses operating in the region. Networking companies provide a range of services, including network design and optimization, security assessments, threat mitigation, and incident response, empowering businesses to stay ahead of evolving cyber threats.
Additional Benefits of Network Security Solutions:
Improved Customer Trust and Reputation: A robust network security posture instills confidence in customers and stakeholders, demonstrating a commitment to protecting their sensitive information and ensuring privacy and confidentiality.
Cost Savings: Investing in network security solutions can result in long-term cost savings by mitigating the potential financial impact of cyber attacks, including data breaches, downtime, regulatory fines, and legal liabilities.
Regulatory Compliance: Network security solutions help businesses comply with regulatory requirements and industry standards governing data protection and privacy, reducing the risk of non-compliance penalties and sanctions.
Proactive Threat Detection and Response: Advanced network security solutions include real-time monitoring and threat intelligence capabilities, enabling businesses to detect and respond to cyber threats before they escalate into major incidents.
Network Security Solutions Company in Dubai:
TLS-IT is a leading provider of network security solutions in Dubai, offering a comprehensive suite of services designed to protect businesses against cyber threats. With a team of experienced professionals and a commitment to excellence, TLS-IT delivers tailored solutions that address the specific needs and requirements of each client. From firewall management and intrusion detection to security assessments and incident response, TLS-IT provides end-to-end solutions that empower businesses to secure their digital assets and mitigate the risks of cyber attacks.
Conclusion:
In conclusion, network security solutions are essential for safeguarding business networks against cyber threats and ensuring the integrity, confidentiality, and availability of sensitive data. By partnering with trusted networking companies like TLS-IT, businesses can access the expertise, resources, and support they need to protect their network infrastructure and mitigate the risks of cyber attacks. Investing in network security solutions is not only a prudent business decision but also a critical step towards safeguarding your business's reputation, customer trust, and long-term success in today's digital age.
#Networking Companies In Dubai#It Networking Companies In Dubai#Network Company In Dubai#Network Security Solutions#Network Security Solutions Company#Network Security And Cyber Security
0 notes
Text
OpenAI disrupts five covert influence operations
New Post has been published on https://thedigitalinsider.com/openai-disrupts-five-covert-influence-operations/
OpenAI disrupts five covert influence operations
.pp-multiple-authors-boxes-wrapper display:none;
img width:100%;
In the last three months, OpenAI has disrupted five covert influence operations (IO) that attempted to exploit the company’s models for deceptive activities online. As of May 2024, these campaigns have not shown a substantial increase in audience engagement or reach due to OpenAI’s services.
OpenAI claims its commitment to designing AI models with safety in mind has often thwarted the threat actors’ attempts to generate desired content. Additionally, the company says AI tools have enhanced the efficiency of OpenAI’s investigations.
Detailed threat reporting by distribution platforms and the open-source community has significantly contributed to combating IO. OpenAI is sharing these findings to promote information sharing and best practices among the broader community of stakeholders.
Disrupting covert IO
In the past three months, OpenAI disrupted several IO operations using its models for various tasks, such as generating short comments, creating fake social media profiles, conducting open-source research, debugging simple code, and translating texts.
Specific operations disrupted include:
Bad Grammar: A previously unreported operation from Russia targeting Ukraine, Moldova, the Baltic States, and the US. This group used OpenAI’s models to debug code for running a Telegram bot and to create political comments in Russian and English, posted on Telegram.
Doppelganger: Another Russian operation generating comments in multiple languages on platforms like X and 9GAG, translating and editing articles, generating headlines, and converting news articles into Facebook posts.
Spamouflage: A Chinese network using OpenAI’s models for public social media activity research, generating texts in several languages, and debugging code for managing databases and websites.
International Union of Virtual Media (IUVM): An Iranian operation generating and translating long-form articles, headlines, and website tags, published on a linked website.
Zero Zeno: A commercial company in Israel, with operations generating articles and comments posted across multiple platforms, including Instagram, Facebook, X, and affiliated websites.
The content posted by these operations focused on various issues, including Russia’s invasion of Ukraine, the Gaza conflict, Indian elections, European and US politics, and criticisms of the Chinese government.
Despite these efforts, none of these operations showed a significant increase in audience engagement due to OpenAI’s models. Using Brookings’ Breakout Scale – which assesses the impact of covert IO – none of the five operations scored higher than a 2, indicating activity on multiple platforms but no breakout into authentic communities.
Attacker trends
Investigations into these influence operations revealed several trends:
Content generation: Threat actors used OpenAI’s services to generate large volumes of text with fewer language errors than human operators could achieve alone.
Mixing old and new: AI was used alongside traditional formats, such as manually written texts or copied memes.
Faking engagement: Some networks generated replies to their own posts to create the appearance of engagement, although none managed to attract authentic engagement.
Productivity gains: Threat actors used AI to enhance productivity, summarising social media posts and debugging code.
Defensive trends
OpenAI’s investigations benefited from industry sharing and open-source research. Defensive measures include:
Defensive design: OpenAI’s safety systems imposed friction on threat actors, often preventing them from generating the desired content.
AI-enhanced investigation: AI-powered tools improved the efficiency of detection and analysis, reducing investigation times from weeks or months to days.
Distribution matters: IO content, like traditional content, must be distributed effectively to reach an audience. Despite their efforts, none of the disrupted operations managed substantial engagement.
Importance of industry sharing: Sharing threat indicators with industry peers increased the impact of OpenAI’s disruptions. The company benefited from years of open-source analysis by the wider research community.
The human element: Despite using AI, threat actors were prone to human error, such as publishing refusal messages from OpenAI’s models on their social media and websites.
OpenAI says it remains dedicated to developing safe and responsible AI. This involves designing models with safety in mind and proactively intervening against malicious use.
While admitting that detecting and disrupting multi-platform abuses like covert influence operations is challenging, OpenAI claims it’s committed to mitigating the dangers.
(Photo by Chris Yang)
See also: EU launches office to implement AI Act and foster innovation
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: ai, artificial intelligence, generative ai, influence operations, openai
#2024#ai#ai & big data expo#ai act#AI models#ai tools#AI-powered#amp#Analysis#Articles#artificial#Artificial Intelligence#automation#Big Data#bot#Cloud#code#Community#Companies#comprehensive#conference#Conflict#content#cyber#cyber security#data#databases#Design#detection#Digital Transformation
0 notes
Text
The Best Phone Hackers in USA to Catch a Cheater

Why need Phone Hackers?
In today’s digital age, the need for phone hackers arises from the necessity to uncover truths hidden within the vast realm of technology. As relationships become entwined with digital communication, suspicions of infidelity often lead individuals to seek concrete evidence. Phone hackers serve as the key to unlocking this evidence, delving into the intricate layers of digital devices to retrieve deleted messages, call logs, and other incriminating data.
Their expertise enables individuals to confront their suspicions with confidence, bringing clarity and closure to uncertain situations. Whether it’s confirming suspicions of a cheating partner or safeguarding against potential threats to privacy, phone hackers offer a valuable service in navigating the complexities of modern relationships.
Related: Do You Want to Track Your Unfaithful Wife’s Phone?
Importance of Catching a Cheater
The importance of catching a cheater cannot be overemphasized enough in the realm of relationships. Discovering infidelity is pivotal for individuals seeking clarity and closure in their partnerships. With the assistance of phone hackers, gathering concrete evidence becomes feasible, enabling individuals to confront their suspicions with tangible proof. This evidence serves as a catalyst for resolution, allowing couples to address underlying issues or make informed decisions about the future of their relationship.
Without this crucial step, doubts and uncertainties can linger, potentially causing further harm to the trust and integrity of the relationship. Thus, the role of phone hackers in uncovering infidelity extends beyond mere investigation; it becomes a vital tool for individuals navigating the complexities of trust and betrayal, ultimately paving the way for healing and growth.
When it comes to catching a cheater, employing a combination of strategies can significantly increase the likelihood of uncovering the truth. Here are some key ways to catch a cheater, along with additional insights:
Ways to catch a cheater
To catch a cheater, individuals often monitor their partner’s digital activity, observe changes in behavior, and may use GPS tracking. Seeking professional help, like hiring a private investigator or a phone hacker, can also provide valuable assistance in gathering evidence. Here are some indicators:
Monitor Digital Activity:
Keep a close eye on your partner’s digital footprint by regularly checking their text messages, emails, and social media interactions. Look out for any unusual or secretive behavior, such as quickly closing apps or hiding screens when you’re around.
Check Call Logs and Contacts:
Take note of any suspicious numbers in your partner’s call logs or contacts list. Look for frequent communication with unknown contacts or numbers that appear at odd hours, indicating potential covert communication.
Use GPS Tracking:
Consider utilizing GPS tracking devices or smartphone apps to monitor your partner’s movements and whereabouts. This can provide valuable insights into their activities, especially if they provide vague or inconsistent explanations for their whereabouts.
Observe Changes in Behavior:
Pay attention to any sudden changes in your partner’s behavior or routine. Be on the lookout for increased secrecy, unexplained absences, or a sudden lack of interest in spending time together. These could be signs of infidelity.
Trust Your Instincts:
Don’t ignore your gut feelings. If you have a strong suspicion that something isn’t right in your relationship, trust your instincts and investigate further. Gut feelings are often a reliable indicator of underlying issues that need to be addressed.
Seek Professional Help:
If you’re unable to gather evidence on your own or feel overwhelmed by the situation, consider seeking the assistance of a professional. A private investigator can conduct thorough surveillance and gather evidence on your behalf. Alternatively, reputable phone hackers specialize in uncovering digital evidence that can shed light on the truth.
Factors to Consider When Hiring a Phone Hacker
When considering hiring a phone hacker, it’s crucial to take several factors into account to ensure a successful and legally compliant outcome. Here are some key factors to consider:
Reputation and Reviews:
Research the reputation of the phone hacker and look for reviews from previous clients. A reputable hacker with positive feedback indicates reliability and trustworthiness in handling sensitive matters.
Skill and Expertise:
Assess the hacker’s skills and expertise in digital forensics and ethical hacking. Look for certifications or evidence of successful cases that demonstrate their proficiency in navigating complex security systems while adhering to legal boundaries.
Legal Considerations:
Ensure that the services provided by the hacker comply with legal regulations. Engaging in illegal activities can have severe consequences, both legally and ethically. Verify that the hacker operates within the bounds of the law and respects privacy rights.
Conclusion
In conclusion, phone hackers play a crucial role in uncovering infidelity and providing closure to those affected by dishonesty. By choosing reputable and skilled professionals, individuals can gather concrete evidence ethically and legally, empowering them to make informed decisions about their relationships.
#companies#cyber security#automation#digital transformation#hack#cyberattack#cybersecurity#cybercrime#developers & startups#infosecurity#phone hacker#cell phone hacker
1 note
·
View note
Photo
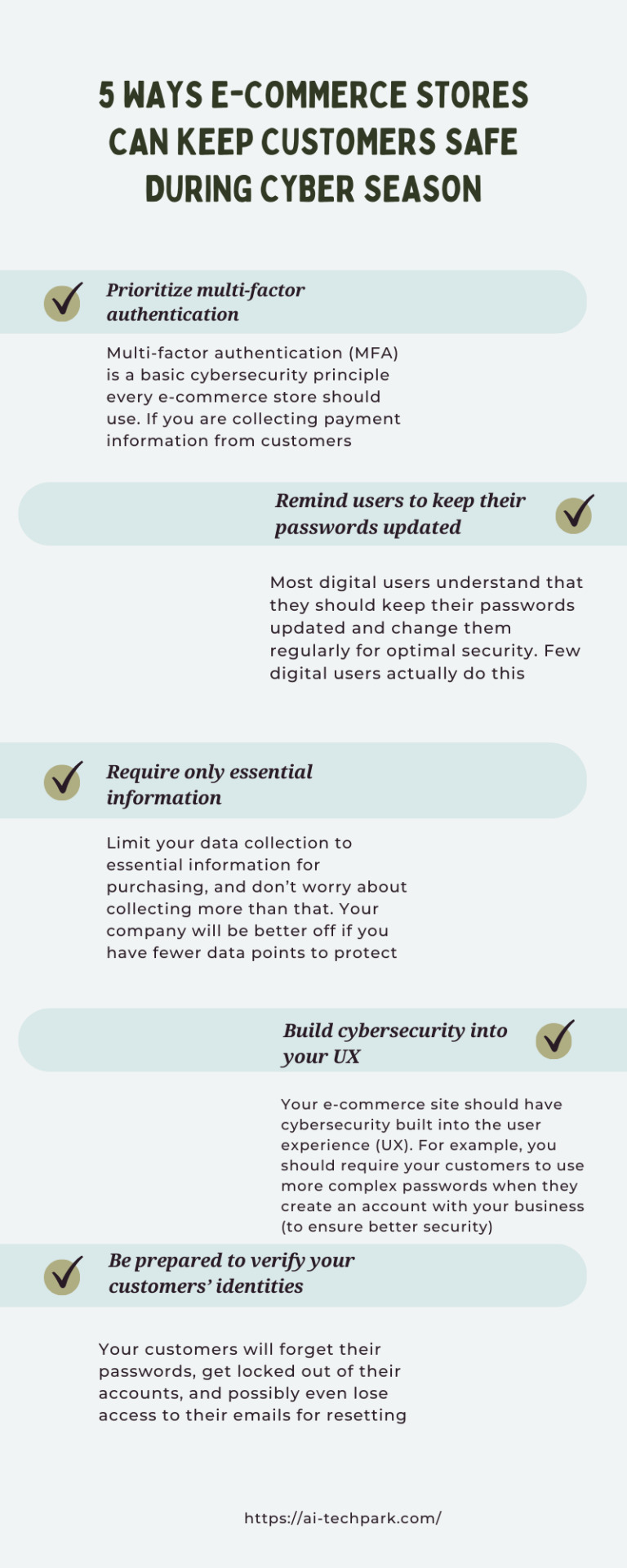
Online shopping has become the standard for the holiday season as consumers scramble to make purchases, choose gifts, and ensure everything arrives in time and all wrapped up for gift-giving events. Insider Intelligence and eMarketer projected that e-commerce sales in the U.S. will surpass $1 trillion in 2022. Unsurprisingly, the pandemic caused a boom in e-commerce sales, changing consumer behaviors significantly. Brands have adapted, and many retailers have adopted e-commerce strategies to better serve their customers.
0 notes
