Text
Migrating your WordPress site to a new host can be seamless with the right steps. This comprehensive guide covers everything from backing up your site and transferring files to updating DNS settings and testing your new setup. Follow these steps to ensure a smooth transition.
#business#websites#migration#plugins#wordpress#themes#backup#hosting#dns#ftp#database#export#import#create website#order website#build website#support#maintenance#tips#guide#tutorial#wp-config.php
0 notes
Text
Transform your WordPress site into a powerful membership platform with MemberPress. This detailed guide walks you through each step, from plugin installation and content protection to payment gateways and site customization. Start building your membership site today!
#business#online payments#payments#paid membership#membership#plugins#themes#wordpress#guide#tutorial#tips#create website#order website#build website#support#maintenance#websites
0 notes
Text
Ready to start selling online? Our comprehensive guide to setting up an e-commerce store with WooCommerce covers everything from installation to customization, helping you create a professional and efficient online shop on your WordPress site.
#business#tips#plugins#wordpress#themes#ecommerce#woocommerce#shop#store#online payments#create website#build website#order website#support#maintenance#websites#guide#tutorial
0 notes
Text
Want to know how AI can transform your WordPress website? Explore the ways AI can enhance your content, boost your search rankings, and streamline your workflow. This beginner's guide will show you how.
#business#ai#plugins#wordpress#themes#create website#order website#build website#support#maintenance#websites#artificial intelligence#bot#tips#tools#guide#tutorial
0 notes
Text
Web3 is revolutionizing the internet, and your WordPress website doesn't have to be left behind. Learn the steps to bridge your site with blockchain technology, from accepting crypto payments to showcasing NFTs.
#business#bitcoin#cryptocurrency#ethereum#altcoins#btc#crypto#blockchain#build website#create website#order website#maintenance#support#websites#decentralized#hosting#guide#tutorial#tips#wordpress#plugins#themes#web3#IPFS#NFT#arweave#metamask#privacy#security#token
0 notes
Text
Is your WordPress website slower than a snail? Don't let slow loading times drive away visitors! Discover quick and easy steps to speed up your site and improve user experience.
#business#wordpress#plugins#seo#search engine optimization#optimization#speed up website#themes#tips#guide#tutorial#order website#create website#build website#support#maintenance#websites
0 notes
Text
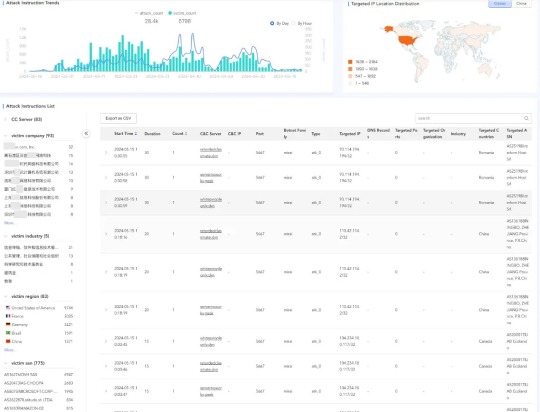
CatDDoS Exploiting 80+ Vulnerabilities, Attacking 300+ Targets Daily
Malicious traffic floods targeted systems, servers, or networks in Distributed Denial of Service (DDoS) attacks are actively exploited by hackers.
Sometimes, DDoS attacks are used as a distraction from other criminal activities, for extortion, to gain a competitive advantage, or for ideological reasons.
If resources are crushed by false requests originating from different compromised devices…
View On WordPress
0 notes
Text
PoC Exploit Released For macOS Privilege Escalation Vulnerability
A new vulnerability has been discovered in macOS Sonoma that is associated with privilege escalation.
This vulnerability has been assigned with CVE-2024-27842 and the severity is yet to be categorized.
This vulnerability exists in the Universal Disk Format (UDF) filesystem on macOS.
Universal Disk format is an open, vendor-neutral file system for computer data storage.
However, this vulnerability…
View On WordPress
0 notes
Text
WordPress Plugin Exploited to Steal Credit Card Data from E-commerce Sites
Unknown threat actors are abusing lesser-known code snippet plugins for WordPress to insert malicious PHP code in victim sites that are capable of harvesting credit card data.
The campaign, observed by Sucuri on May 11, 2024, entails the abuse of a WordPress plugin called Dessky Snippets, which allows users to add custom PHP code. It has over 200 active installations.
View On WordPress
0 notes
Text
Unleash your WordPress website's potential with Crocoblock – the ultimate toolkit for creating dynamic, feature-rich sites using Elementor or Gutenberg. Discover how this powerful ecosystem of plugins can transform your design and functionality.
#wordpress#plugins#themes#website builder#crocoblock#elementor#gutenberg#tips#guide#tutorial#create website#order website#build website#support#maintenance#websites
0 notes
Text
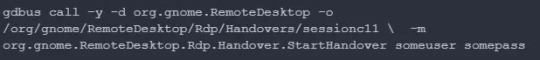
GNOME Remote Desktop Vulnerability Let Attackers Read Login Credentials
GNOME desktop manager was equipped with a new feature which allowed remote users to create graphical sessions on the system by configuring the system daemon.
This daemon runs as a dedicated “gnome-remote-desktop” and also provides a D-bus interface on the D-bus system bus.
These features have been introduced in GNOME remote desktop version 46 along with several other system services.
However,…
View On WordPress
#Credential Leak#CVE/vulnerability#Cyber Security News#GNOME Vulnerability#remote desktop#Remote Desktop Security
0 notes
Text
Moroccan Cybercrime Group Steals Up to $100K Daily Through Gift Card Fraud
Microsoft is calling attention to a Morocco-based cybercrime group dubbed Storm-0539 that’s behind gift card fraud and theft through highly sophisticated email and SMS phishing attacks.
“Their primary motivation is to steal gift cards and profit by selling them online at a discounted rate,” the company said in its latest Cyber Signals report. “We’ve seen some examples where
View On WordPress
0 notes
Text
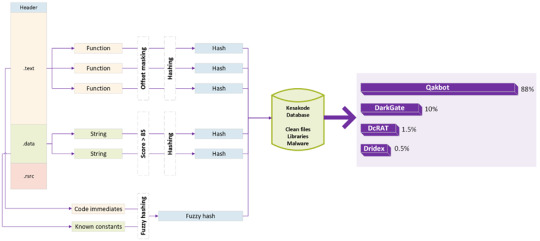
Kesakode: A Remote Hash Lookup Service To Identify Malware Samples
Today marks a significant milestone for Malcat users with the release of version 0.9.6, introducing Kesakode, a remote hash lookup service.
This innovative tool is tightly integrated into Malcat’s UI and is designed to match known functions, strings, and constant sets against a comprehensive database of clean malware and library files.
This article delves into the features, functionality, and…
View On WordPress
0 notes
Text
Report: The Dark Side of Phishing Protection
The transition to the cloud, poor password hygiene and the evolution in webpage technologies have all enabled the rise in phishing attacks. But despite sincere efforts by security stakeholders to mitigate them – through email protection, firewall rules and employee education – phishing attacks are still a very risky attack vector.
A new report by LayerX explores the state of
View On WordPress
0 notes
Text
New Tricks in the Phishing Playbook: Cloudflare Workers, HTML Smuggling, GenAI
Cybersecurity researchers are alerting of phishing campaigns that abuse Cloudflare Workers to serve phishing sites that are used to harvest users’ credentials associated with Microsoft, Gmail, Yahoo!, and cPanel Webmail.
The attack method, called transparent phishing or adversary-in-the-middle (AitM) phishing, “uses Cloudflare Workers to act as a reverse proxy server for a
View On WordPress
0 notes
Text
Cisco Firepower Vulnerability Let Attackers Launch SQL Injection Attacks
A critical vulnerability has been identified in Cisco Firepower Management Center (FMC) Software’s web-based management interface.
This vulnerability could potentially allow authenticated, remote attackers to conduct SQL injection attacks on affected systems.
This vulnerability, tracked as CVE-2024-20360, poses significant risks, including unauthorized data access, command execution on the…
View On WordPress
0 notes
Text
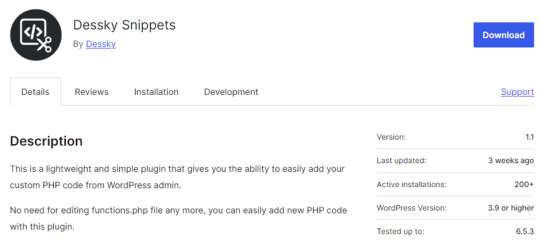
Hackers Exploit WordPress Plugin to Steal Credit Card Data
Hackers have exploited an obscure WordPress plugin to inject malware into websites, specifically targeting WooCommerce online stores to steal credit card information.
This alarming trend highlights the persistent threat cybercriminals pose and the need for robust security measures in the digital landscape.
Obscure Dessky Snippets Plugin Used for Malicious PHP Injections
The attack was first…
View On WordPress
0 notes