#user: palo.
Text

todos conocen a SIRENA GALVAN, pero su reputación está por descubrirse.
palo, ¡bienvenide a @aureliahillshqs! nos encanta tenerte con nosotres. a partir de ahora contás con 24 hs para enviarnos la cuenta, en caso de necesitar más tiempo, ¡no dudes en solicitarlo! pst! también queremos contarte que si todavía no rellenaste este form, nos serviría mucho que lo hicieras. ¡gracias!
OUT OF CHARACTER:
Nombre/alias: palo
¿Tenés más de 21 años? sí
Zona horaria o país: argentina gmt-3
Nivel de actividad estimado: 7
Triggers: non-con, incesto, abuso, acoso
¿Aceptás que tu personaje se vea involucrado en las intervenciones realizadas por la administración del grupal? sí
¿Algo que agregar?: 💖💖
IN CHARACTER:
Nombre: sirena galván.
Faceclaim: lizeth selene.
Cupo:
Edad y fecha de nacimiento: veinticinco años, 1 de agosto de 1998.
Descripción física: metro setenta de altura, silueta es delgada y de largas piernas, piel color trigueña que parece hasta dorada si se expone mucho al sol. cabellera es oscura y rizada, larga hasta la cintura y le gusta usarla en distintos peinados. lleva un septum y varios aros en las orejas, anillos y collares, toda su joyería de oro. tatuajes de distintos tamaños cubren su cuerpo desde los brazos hasta el estómago y las piernas.
Descripción psicológica: osada, carismática, segura, divertida, impulsiva, inquieta, disruptiva.
Historia o datos curiosos:
hija del medio, la falta del padre nunca la llega a golpear realmente. no puede sentir anhelo por alguien que no existe, mamá logra imponerse en cada rincón de su corazón incluso cuando crece y nacen las diferencias porque las dos mujeres saben cómo alzar la voz y reinar en sus propios mundos, a veces siente que no son capaces de habitar el mismo sin querer conquistar el de la otra.
le gusta la buena vida y no se avergüenza de demostrarlo. se vuelve inconscientemente modelo de las joyas familiares desde temprana edad, se preocupa por su estética y qué viste y cómo se presenta al mundo, rápidamente crece su presencia en redes como consecuencia de atrayente imagen y personalidad. aunque protagoniza algunos comerciales y posa frente a las cámaras para marcas, su pasión está en la música.
desconocer el miedo la lleva a perseguir con seguridad ese sueño y como la fortuna suele estar a su favor, empieza a tener nombre propio dentro de la industria y la voz de sirena llega a cautivar a audiencia cuando cumple los veinte años. ella lo niega, pero es cierto que ser hija de quien es facilita de vez en cuando las cosas. cantante de r&b y derivados, juega entre géneros siempre manteniendo su esencia como prioridad. canta en algún festival y da shows que siempre tienen pinta de ser privados por el tipo de público que mueve y porque no se considera artista muy mainstream pero siempre conforme y contenta con lo que logra, o al menos así se muestra.
la mudanza a aurelia hills coincide con receso que se toma para trabajar en próximo álbum. sigue presente en redes y de vez en cuando se pierde algunos días escondida en hogar, escribiendo. inquieta por naturaleza, siempre acaba haciendo de las suyas y disfrutando, porque corazón no es muy paciente y necesita recordarse que ahí lo tiene y que palpita, excusándose en ser travesuras el motor de su inspiración.
1 note
·
View note
Text

merodeando en el emerald está johnie loveless, ¿estaremos tratando con la responsable del atroz crimen cometido? finley hearst y laurence ulrick ciertamente no descartan la posibilidad. ahora queda en la inquilina del departamento #710 probar su inocencia.
¡palo, te damos la bienvenida a apt225hq! a partir de ahora, tienes cuarenta y ocho horas para confirmar tu cuenta. de tener alguna duda, ¡acá estamos!
01. INFORMACIÓN IN CHARACTER.
nombre: johnie loveless
pronombres: ella/suya
edad: veintiséis
fecha de nacimiento: 1 de julio de 1997
nacionalidad: inglesa
rostro reservado: mia goth
perfil psicológico: desordenada, errática, impulsiva, temeraria, carismática.
02. DATOS DE RELEVANCIA.
tablero de pinterest.
prefiere el misterio, dice ella, que no se sepa bien de dónde viene o a dónde va, cuáles son sus aspiraciones pero, ¿está ella segura de tener alguna? cansada de su irresponsabilidad, mamá que ya ha formado nueva familia con impecable esposo y dio a luz hace par de años a pequeños mucho más pulcros que su primogénita decide costearle departamento para que no estorbe o, como dice ésta, para que pueda comenzar de cero; como si contando con hoja en blanco, primer impulso de johnie no fuese llenarla de inentendibles garabatos.
03. INFORMACIÓN OUT OF CHARACTER.
seudónimo: palo
pronombres: ella/suya
edad: 25
triggers: non-con/incesto/trabajo sexual
zona horaria: gmt -3
0 notes
Text

🏹 * 𝙰𝙲𝙲𝙴𝚂𝙾 𝙲𝙾𝙽𝙲𝙴𝙳𝙸𝙳𝙾 : ARCHIVO TSZ0202.
registro del legado TAMARA SOFÍA ZARZA, hija de la ex vedette y actriz argentina karina salazar. de nacionalidad argentina, tiene veintitrés años y actualmente es modelo e influencer. tras consultar a los oráculos descubrió que su espíritu está conectado a maria becerra, entendiendo finalmente el parecido físico entre ambas.
PARA MAYOR INFORMACIÓN ACCEDER A LOS EXPEDIENTES EN LA BIBLIOTECA.
la clave te da la bienvenida, PALO ( ella/suya ). de antemano, te agradecemos por el interés. a partir de ahora cuentas con 24 horas para enviar tu cuenta. ¡te esperamos!
0 notes
Text

↺ 99% ⋘ 𝑙𝑜𝑎𝑑𝑖𝑛𝑔 𝑑𝑎𝑡𝑎...⋙
URSULA, 23. ELLA/SUYA.
Llegó el momento. Emprende un viaje por el mundo de fantasía de Seirai, un continente de mil maravillas donde incontables criaturas prosperan en armonía. ¿Estás liste para descubrir los misterios que le rodean junto a tus aliades? ¡Que tu viaje inicie!
PALO, ¡Muchas gracias por el interés! Tienes 24 horas para enviar tu cuenta, puedes solicitar más en caso de necesitarlo.

1 note
·
View note
Text

¿alguien conoce a choi soe? los rumores llenan todos los rincones y los hechos seguramente darán de qué hablar.
palo, ¡bienvenida a millennialshqs! estamos felices de recibirte en el grupo y no podemos esperar a ver cómo tu personaje se desarrolla en esta historia. recordá enviar la cuenta de tu personaje pronto y, en caso de necesitar cualquier cosa, no dudes en ponerte en contacto con nosotras.
OOC.
nombre: palo
pronombres: ella/suya
edad: 25
zona horaria: gmt-3
triggers:
user de discord: ( no será publicado, pero se tendrá en cuenta para poder agregarles al canal del grupal. )
¿algo que agregar? <3
IC.
nombre: choi soe
pronombres: ella/suya
faceclaim: cho miyeon
edad: 25 años
esqueleto: g5
fecha de cumpleaños: 1 de marzo de 1997.
descripción psicológica: bien intencionada, simpática, honesta, dulce y cariñosa / solitaria, dependiente, tímida, sensible.
descripción física: de contextura pequeña, piel suave y de apariencia frágil, con cabellos largos que constantemente peina o decora con accesorios, antes castaños y ahora siempre teñidos de rubio platinado. únicas perforaciones son en sus orejas y tatuajes sólo tiene dos o tres pequeños escondidos por alguna parte de su cuerpo no muy visible.
PERMISOS, MARCA CON NEGRITA TU RESPUESTA:
en caso de unfollow, ¿dejarías que se continúe utilizando tu personaje como no jugable? sí / no.
¿dejarías que todo lo que rolees pueda tener impacto directo sobre la trama del grupal? es decir, que a partir de tus convos la administración pueda usar cierta información para futuras actividades. sí / sí, pero hablándolo primero / no.
0 notes
Text
Shamir Secret Sharing
It’s 3am. Paul, the head of PayPal database administration carefully enters his elaborate passphrase at a keyboard in a darkened cubicle of 1840 Embarcadero Road in East Palo Alto, for the fifth time. He hits Return. The green-on-black console window instantly displays one line of text: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.”
There is nerd pandemonium all around us. James, our recently promoted VP of Engineering, just climbed the desk at a nearby cubicle, screaming: “Guys, if we can’t get this key the right way, we gotta start brute-forcing it ASAP!” It’s gallows humor – he knows very well that brute-forcing such a key will take millions of years, and it’s already 6am on the East Coast – the first of many “Why is PayPal down today?” articles is undoubtedly going to hit CNET shortly. Our single-story cubicle-maze office is buzzing with nervous activity of PayPalians who know they can’t help but want to do something anyway. I poke my head up above the cubicle wall to catch a glimpse of someone trying to stay inside a giant otherwise empty recycling bin on wheels while a couple of Senior Software Engineers are attempting to accelerate the bin up to dangerous speeds in the front lobby. I lower my head and try to stay focused. “Let’s try it again, this time with three different people” is the best idea I can come up with, even though I am quite sure it will not work.
It doesn’t.
The key in question decrypts PayPal’s master payment credential table – also known as the giant store of credit card and bank account numbers. Without access to payment credentials, PayPal doesn’t really have a business per se, seeing how we are supposed to facilitate payments, and that’s really hard to do if we no longer have access to the 100+ million credit card numbers our users added over the last year of insane growth.
This is the story of a catastrophic software bug I briefly introduced into the PayPal codebase that almost cost us the company (or so it seemed, in the moment.) I’ve told this story a handful of times, always swearing the listeners to secrecy, and surprisingly it does not appear to have ever been written down before. 20+ years since the incident, it now appears instructive and a little funny, rather than merely extremely embarrassing.
Before we get back to that fateful night, we have to go back another decade. In the summer of 1991, my family and I moved to Chicago from Kyiv, Ukraine. While we had just a few hundred dollars between the five of us, we did have one secret advantage: science fiction fans.
My dad was a highly active member of Zoryaniy Shlyah – Kyiv’s possibly first (and possibly only, at the time) sci-fi fan club – the name means “Star Trek” in Ukrainian, unsurprisingly. He translated some Stansilaw Lem (of Solaris and Futurological Congress fame) from Polish to Russian in the early 80s and was generally considered a coryphaeus at ZSh.
While USSR was more or less informationally isolated behind the digital Iron Curtain until the late ‘80s, by 1990 or so, things like FidoNet wriggled their way into the Soviet computing world, and some members of ZSh were now exchanging electronic mail with sci-fi fans of the free world.
The vaguely exotic news of two Soviet refugee sci-fi fans arriving in Chicago was transmitted to the local fandom before we had even boarded the PanAm flight that took us across the Atlantic [1]. My dad (and I, by extension) was soon adopted by some kind Chicago science fiction geeks, a few of whom became close friends over the years, though that’s a story for another time.
A year or so after the move to Chicago, our new sci-fi friends invited my dad to a birthday party for a rising star of the local fandom, one Bruce Schneier. We certainly did not know Bruce or really anyone at the party, but it promised good food, friendly people, and probably filk. My role was to translate, as my dad spoke limited English at the time.
I had fallen desperately in love with secret codes and cryptography about a year before we left Ukraine. Walking into Bruce’s library during the house tour (this was a couple years before Applied Cryptography was published and he must have been deep in research) felt like walking into Narnia.
I promptly abandoned my dad to fend for himself as far as small talk and canapés were concerned, and proceeded to make a complete ass out of myself by brazenly asking the host for a few sheets of paper and a pencil. Having been obliged, I pulled a half dozen cryptography books from the shelves and went to work trying to copy down some answers to a few long-held questions on the library floor. After about two hours of scribbling alone like a man possessed, I ran out of paper and decided to temporarily rejoin the party.
On the living room table, Bruce had stacks of copies of his fanzine Ramblings. Thinking I could use the blank sides of the pages to take more notes, I grabbed a printout and was about to quietly return to copying the original S-box values for DES when my dad spotted me from across the room and demanded I help him socialize. The party wrapped soon, and our friends drove us home.
The printout I grabbed was not a Ramblings issue. It was a short essay by Bruce titled Sharing Secrets Among Friends, essentially a humorous explanation of Shamir Secret Sharing.
Say you want to make sure that something really really important and secret (a nuclear weapon launch code, a database encryption key, etc) cannot be known or used by a single (friendly) actor, but becomes available, if at least n people from a group of m choose to do it. Think two on-duty officers (from a cadre of say 5) turning keys together to get ready for a nuke launch.
The idea (proposed by Adi Shamir – the S of RSA! – in 1979) is as simple as it is beautiful.
Let’s call the secret we are trying to split among m people K.
First, create a totally random polynomial that looks like: y(x) = C0 * x^(n-1) + C1 * x^(n-2) + C2 * x^(n-3) ….+ K. “Create” here just means generate random coefficients C. Now, for every person in your trusted group of m, evaluate the polynomial for some randomly chosen Xm and hand them their corresponding (Xm,Ym) each.
If we have n of these points together, we can use Lagrange interpolating polynomial to reconstruct the coefficients – and evaluate the original polynomial at x=0, which conveniently gives us y(0) = K, the secret. Beautiful. I still had the printout with me, years later, in Palo Alto.
It should come as no surprise that during my time as CTO PayPal engineering had an absolute obsession with security. No firewall was one too many, no multi-factor authentication scheme too onerous, etc. Anything that was worth anything at all was encrypted at rest.
To decrypt, a service would get the needed data from its database table, transmit it to a special service named cryptoserv (an original SUN hardware running Solaris sitting on its own, especially tightly locked-down network) and a special service running only there would perform the decryption and send back the result.
Decryption request rate was monitored externally and on cryptoserv, and if there were too many requests, the whole thing was to shut down and purge any sensitive data and keys from its memory until manually restarted.
It was this manual restart that gnawed at me. At launch, a bunch of configuration files containing various critical decryption keys were read (decrypted by another key derived from one manually-entered passphrase) and loaded into the memory to perform future cryptographic services.
Four or five of us on the engineering team knew the passphrase and could restart cryptoserv if it crashed or simply had to have an upgrade. What if someone performed a little old-fashioned rubber-hose cryptanalysis and literally beat the passphrase out of one of us? The attacker could theoretically get access to these all-important master keys. Then stealing the encrypted-at-rest database of all our users’ secrets could prove useful – they could decrypt them in the comfort of their underground supervillain lair.
I needed to eliminate this threat.
Shamir Secret Sharing was the obvious choice – beautiful, simple, perfect (you can in fact prove that if done right, it offers perfect secrecy.) I decided on a 3-of-8 scheme and implemented it in pure POSIX C for portability over a few days, and tested it for several weeks on my Linux desktop with other engineers.
Step 1: generate the polynomial coefficients for 8 shard-holders.
Step 2: compute the key shards (x0, y0) through (x7, y7)
Step 3: get each shard-holder to enter a long, secure passphrase to encrypt the shard
Step 4: write out the 8 shard files, encrypted with their respective passphrases.
And to reconstruct:
Step 1: pick any 3 shard files.
Step 2: ask each of the respective owners to enter their passphrases.
Step 3: decrypt the shard files.
Step 4: reconstruct the polynomial, evaluate it for x=0 to get the key.
Step 5: launch cryptoserv with the key.
One design detail here is that each shard file also stored a message authentication code (a keyed hash) of its passphrase to make sure we could identify when someone mistyped their passphrase. These tests ran hundreds and hundreds of times, on both Linux and Solaris, to make sure I did not screw up some big/little-endianness issue, etc. It all worked perfectly.
A month or so later, the night of the key splitting party was upon us. We were finally going to close out the last vulnerability and be secure. Feeling as if I was about to turn my fellow shard-holders into cymeks, I gathered them around my desktop as PayPal’s front page began sporting the “We are down for maintenance and will be back soon” message around midnight.
The night before, I solemnly generated the new master key and securely copied it to cryptoserv. Now, while “Push It” by Salt-n-Pepa blared from someone’s desktop speakers, the automated deployment script copied shard files to their destination.
While each of us took turns carefully entering our elaborate passphrases at a specially selected keyboard, Paul shut down the main database and decrypted the payment credentials table, then ran the script to re-encrypt with the new key. Some minutes later, the database was running smoothly again, with the newly encrypted table, without incident.
All that was left was to restore the master key from its shards and launch the new, even more secure cryptographic service.
The three of us entered our passphrases… to be met with the error message I haven’t seen in weeks: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.” Surely one of us screwed up typing, no big deal, we’ll do it again. No dice. No dice – again and again, even after we tried numerous combinations of the three people necessary to decrypt.
Minutes passed, confusion grew, tension rose rapidly.
There was nothing to do, except to hit rewind – to grab the master key from the file still sitting on cryptoserv, split it again, generate new shards, choose passphrases, and get it done. Not a great feeling to have your first launch go wrong, but not a huge deal either. It will all be OK in a minute or two.
A cursory look at the master key file date told me that no, it wouldn’t be OK at all. The file sitting on cryptoserv wasn’t from last night, it was created just a few minutes ago. During the Salt-n-Pepa-themed push from stage, we overwrote the master key file with the stage version. Whatever key that was, it wasn’t the one I generated the day before: only one copy existed, the one I copied to cryptoserv from my computer the night before. Zero copies existed now. Not only that, the push script appears to have also wiped out the backup of the old key, so the database backups we have encrypted with the old key are likely useless.
Sitrep: we have 8 shard files that we apparently cannot use to restore the master key and zero master key backups. The database is running but its secret data cannot be accessed.
I will leave it to your imagination to conjure up what was going through my head that night as I stared into the black screen willing the shards to work. After half a decade of trying to make something of myself (instead of just going to work for Microsoft or IBM after graduation) I had just destroyed my first successful startup in the most spectacular fashion.
Still, the idea of “what if we all just continuously screwed up our passphrases” swirled around my brain. It was an easy check to perform, thanks to the included MACs. I added a single printf() debug statement into the shard reconstruction code and instead of printing out a summary error of “one or more…” the code now showed if the passphrase entered matched the authentication code stored in the shard file.
I compiled the new code directly on cryptoserv in direct contravention of all reasonable security practices – what did I have to lose? Entering my own passphrase, I promptly got “bad passphrase” error I just added to the code. Well, that’s just great – I knew my passphrase was correct, I had it written down on a post-it note I had planned to rip up hours ago.
Another person, same error. Finally, the last person, JK, entered his passphrase. No error. The key still did not reconstruct correctly, I got the “Goodbye”, but something worked. I turned to the engineer and said, “what did you just type in that worked?”
After a second of embarrassed mumbling, he admitted to choosing “a$$word” as his passphrase. The gall! I asked everyone entrusted with the grave task of relaunching crytposerv to pick really hard to guess passphrases, and this guy…?! Still, this was something -- it worked. But why?!
I sprinted around the half-lit office grabbing the rest of the shard-holders demanding they tell me their passphrases. Everyone else had picked much lengthier passages of text and numbers. I manually tested each and none decrypted correctly. Except for the a$$word. What was it…
A lightning bolt hit me and I sprinted back to my own cubicle in the far corner, unlocked the screen and typed in “man getpass” on the command line, while logging into cryptoserv in another window and doing exactly the same thing there. I saw exactly what I needed to see.
Today, should you try to read up the programmer’s manual (AKA the man page) on getpass, you will find it has been long declared obsolete and replaced with a more intelligent alternative in nearly all flavors of modern Unix.
But back then, if you wanted to collect some information from the keyboard without printing what is being typed in onto the screen and remain POSIX-compliant, getpass did the trick. Other than a few standard file manipulation system calls, getpass was the only operating system service call I used, to ensure clean portability between Linux and Solaris.
Except it wasn’t completely clean.
Plain as day, there it was: the manual pages were identical, except Solaris had a “special feature”: any passphrase entered that was longer than 8 characters long was automatically reduced to that length anyway. (Who needs long passwords, amiright?!)
I screamed like a wounded animal. We generated the key on my Linux desktop and entered our novel-length passphrases right here. Attempting to restore them on a Solaris machine where they were being clipped down to 8 characters long would never work. Except, of course, for a$$word. That one was fine.
The rest was an exercise in high-speed coding and some entirely off-protocol file moving. We reconstructed the master key on my machine (all of our passphrases worked fine), copied the file to the Solaris-running cryptoserv, re-split it there (with very short passphrases), reconstructed it successfully, and PayPal was up and running again like nothing ever happened.
By the time our unsuspecting colleagues rolled back into the office I was starting to doze on the floor of my cubicle and that was that. When someone asked me later that day why we took so long to bring the site back up, I’d simply respond with “eh, shoulda RTFM.”
RTFM indeed.
P.S. A few hours later, John, our General Counsel, stopped by my cubicle to ask me something. The day before I apparently gave him a sealed envelope and asked him to store it in his safe for 24 hours without explaining myself. He wanted to know what to do with it now that 24 hours have passed.
Ha. I forgot all about it, but in a bout of “what if it doesn’t work” paranoia, I printed out the base64-encoded master key when we had generated it the night before, stuffed it into an envelope, and gave it to John for safekeeping. We shredded it together without opening and laughed about what would have never actually been a company-ending event.
P.P.S. If you are thinking of all the ways this whole SSS design is horribly insecure (it had some real flaws for sure) and plan to poke around PayPal to see if it might still be there, don’t. While it served us well for a few years, this was the very first thing eBay required us to turn off after the acquisition. Pretty sure it’s back to a single passphrase now.
Notes:
1: a member of Chicagoland sci-fi fan community let me know that the original news of our move to the US was delivered to them via a posted letter, snail mail, not FidoNet email!
515 notes
·
View notes
Text
Twinkfrump Linkdump

I'm touring my new, nationally bestselling novel The Bezzle! Catch me in CHICAGO (Apr 17), Torino (Apr 21) Marin County (Apr 27), Winnipeg (May 2), Calgary (May 3), Vancouver (May 4), and beyond!

Welcome to the seventeenth Pluralistic linkdump, a collection of all the miscellany that didn't make it into the week's newsletter, cunningly wrought together in a single edition that ranges from the first ISP to AI nonsense to labor organizing victories to the obituary of a brilliant scientist you should know a lot more about! Here's the other 16 dumps:
https://pluralistic.net/tag/linkdump/
If you're reading this (and you are!), it was delivered to you by an internet service provider. Today, the ISP industry is calcified, controlled by a handful of telcos and cable companies. But the idea of an "ISP" didn't come out of a giant telecommunications firm – it was created, in living memory, by excellent nerds who are still around.
Depending on how you reckon, The Little Garden was either the first or the second ISP in America. It was named after a Palo Alto Chinese restaurant frequented by its founders. To get a sense of that founding, read these excellent recollections by Tom Jennings, whose contributions include the seminal zine Homocore, the seminal networking protocol Fidonet, and the seminal third-party PC ROM, whence came Dell, Gateway, Compaq, and every other "PC clone" company.
The first installment describes how an informal co-op to network a few friends turned into a business almost by accident, with thousands of dollars flowing in and out of Jennings' bank account:
https://www.sensitiveresearch.com/Archive/TLG/TLG.html
And it describes how that ISP set a standard for neutrality, boldly declaring that "TLGnet exercises no control whatsoever over the content of the information." They introduced an idea of radical transparency, documenting their router configurations and other technical details and making them available to the public. They hired unskilled punk and queer kids from their communities and trained them to operate the network equipment they'd invented, customized or improvised.
In part two, Jennings talks about the evolution of TLG's radical business-plan: to offer unrestricted service, encouraging their customers to resell that service to people in their communities, having no lock-in, unbundling extra services including installation charges – the whole anti-enshittification enchilada:
https://www.sensitiveresearch.com/Archive/TLG/
I love Jennings and his work. I even gave him a little cameo in Picks and Shovels, the third Martin Hench novel, which will be out next winter. He's as lyrical a writer about technology as you could ask for, and he's also a brilliant engineer and thinker.
The Little Garden's founders and early power-users have all fleshed out Jennings' account of the birth of ISPs. Writing on his blog, David "DSHR" Rosenthal rounds up other histories from the likes of EFF co-founder John Gilmore and Tim Pozar:
https://blog.dshr.org/2024/04/the-little-garden.html
Rosenthal describes some of the more exotic shenanigans TLG got up to in order to do end-runs around the Bell system's onerous policies, hacking in the purest sense of the word, for example, by daisy-chaining together modems in regions with free local calling and then making "permanent local calls," with the modems staying online 24/7.
Enshittification came to the ISP business early and hit it hard. The cartel that controls your access to the internet today is a billion light-years away from the principled technologists who invented the industry with an ethos of care, access and fairness. Today's ISPs are bitterly opposed to Net Neutrality, the straightforward proposition that if you request some data, your ISP should send it to you as quickly and reliably as it can.
Instead, ISPs want to offer "slow-lanes" where they will relegate the whole internet, except for those companies that bribe the ISP to be delivered at normal speed. ISPs have a laughably transparent way of describing this: they say that they're allowing services to pay for "fast lanes" with priority access. This is the same as the giant grocery store that charges you extra unless you surrender your privacy with a "loyalty card" – and then says that they're offering a "discount" for loyal customers, rather than charging a premium to customers who don't want to be spied on.
The American business lobby loves this arrangement, and hates Net Neutrality. Having monopolized every sector of our economy, they are extremely fond of "winner take all" dynamics, and that's what a non-neutral ISP delivers: the biggest services with the deepest pockets get the most reliable delivery, which means that smaller services don't just have to be better than the big guys, they also have to be able to outbid them for "priority carriage."
If everything you get from your ISP is slow and janky, except for the dominant services, then the dominant services can skimp on quality and pocket the difference. That's the goal of every monopolist – not just to be too big to fail, but also too big to care.
Under the Trump administration, FCC chair Ajit Pai dismantled the Net Neutrality rule, colluding with American big business to rig the process. They accepted millions of obviously fake anti-Net Neutrality comments (one million identical comments from @pornhub.com addresses, comments from dead people, comments from sitting US Senators who support Net Neutrality) and declared open season on American internet users:
https://ag.ny.gov/press-release/2021/attorney-general-james-issues-report-detailing-millions-fake-comments-revealing
Now, Biden's FCC is set to reinstate Net Neutrality – but with a "compromise" that will make mobile internet (which nearly all of use sometimes, and the poorest of us are reliant on) a swamp of anticompetitive practices:
https://cyberlaw.stanford.edu/blog/2024/04/harmful-5g-fast-lanes-are-coming-fcc-needs-stop-them
Under the proposed rule, mobile carriers will be able to put traffic to and from apps in the slow lane, and then extort bribes from preferred apps for normal speed and delivery. They'll rely on parts of the 5G standard to pull off this trick.
The ISP cartel and the FCC insist that this is fine because web traffic won't be degraded, but of course, every service is hellbent on pushing you into using apps instead of the web. That's because the web is an open platform, which means you can install ad- and privacy-blockers. More than half of web users have installed a blocker, making it the largest boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
But reverse-engineering and modding an app is a legal minefield. Just removing the encryption from an app can trigger criminal penalties under Section 1201 of the DMCA, carrying a five-year prison sentence and a $500k fine. An app is just a web-page skinned in enough IP that it's a felony to mod it.
Apps are enshittification's vanguard, and the fact that the FCC has found a way to make them even worse is perversely impressive. They're voting on this on April 25, and they have until April 24 to fix this. They should. They really should:
https://docs.fcc.gov/public/attachments/DOC-401676A1.pdf
In a just world, cheating ripoff ISPs would the top tech policy story. The operational practices of ISPs effect every single one us. We literally can't talk about tech policy without ISPs in the middle. But Net Neutrality is an also-ran in tech policy discourse, while AI – ugh ugh ugh – is the thing none of us can shut up about.
This, despite the fact that the most consequential AI applications sum up to serving as a kind of moral crumple-zone for shitty business practices. The point of AI isn't to replace customer service and other low-paid workers who have taken to demanding higher wages and better conditions – it's to fire those workers and replace them with chatbots that can't do their jobs. An AI salesdroid can't sell your boss a bot that can replace you, but they don't need to. They only have to convince your boss that the bot can do your job, even if it can't.
SF writer Karl Schroeder is one of the rare sf practitioners who grapples seriously with the future, a "strategic foresight" guy who somehow skirts the bullshit that is the field's hallmark:
https://pluralistic.net/2024/03/07/the-gernsback-continuum/#wheres-my-jetpack
Writing on his blog, Schroeder describes the AI debates roiling the Association of Professional Futurists, and how it's sucking him into being an unwilling participant in the AI hype cycle:
https://kschroeder.substack.com/p/dragged-into-the-ai-hype-cycle
Schroeder's piece is a thoughtful meditation on the relationship of SF's thought-experiments and parables about AI to the promises of AI hucksters, who promise that a) "general artificial intelligence" is just around the corner and that b) it will be worth trillions of dollars.
Schroeder – like other sf writers including Ted Chiang and Charlie Stross (and me) – comes to the conclusion that AI panic isn't about AI, it's about power. The artificial life-form devouring the planet and murdering our species is the limited liability corporation, and its substrate isn't silicon, it's us, human bodies:
What’s lying underneath all our anxieties about AGI is an anxiety that has nothing to do with Artificial Intelligence. Instead, it’s a manifestation of our growing awareness that our world is being stolen from under us. Last year’s estimate put the amount of wealth currently being transferred from the people who made it to an idle billionaire class at $5.2 trillion. Artificial General Intelligence whose environment is the server farms and sweatshops of this class is frightening only because of its capacity to accelerate this greatest of all heists.
After all, the business-case for AI is so very thin that the industry can only survive on a torrent of hype and nonsense – like claims that Amazon's "Grab and Go" stores used "AI" to monitor shoppers and automatically bill them for their purchases. In reality, the stores used thousands of low-paid Indian workers to monitor cameras and manually charge your card. This happens so often that Indian technologists joke that "AI" stands for "absent Indians":
https://pluralistic.net/2024/01/29/pay-no-attention/#to-the-little-man-behind-the-curtain
Isn't it funny how all the really promising AI applications are in domains that most of us aren't qualified to assess? Like the claim that Google's AI was producing millions of novel materials that will shortly revolutionize all forms of production, from construction to electronics to medical implants:
https://deepmind.google/discover/blog/millions-of-new-materials-discovered-with-deep-learning/
That's what Google's press-release claimed, anyway. But when two groups of experts actually pulled a representative sample of these "new materials" from the Deep Mind database, they found that none of these materials qualified as "credible, useful and novel":
https://pubs.acs.org/doi/10.1021/acs.chemmater.4c00643
Writing about the researchers' findings for 404 Media, Jason Koebler cites Berkeley researchers who concluded that "no new materials have been discovered":
https://www.404media.co/google-says-it-discovered-millions-of-new-materials-with-ai-human-researchers/
The researchers say that AI data-mining for new materials is promising, but falls well short of Google's claim to be so transformative that it constitutes the "equivalent to nearly 800 years’ worth of knowledge" and "an order-of-magnitude expansion in stable materials known to humanity."
AI hype keeps the bubble inflating, and for so long as it keeps blowing up, all those investors who've sunk their money into AI can tell themselves that they're rich. This is the essence of "a bezzle": "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it":
https://pluralistic.net/2023/03/09/autocomplete-worshippers/#the-real-ai-was-the-corporations-that-we-fought-along-the-way
Among the best debezzlers of AI are the Princeton Center for Information Technology Policy's Arvind Narayanan and Sayash Kapoor, who edit the "AI Snake Oil" blog. Now, they've sold a book with the same title:
https://www.aisnakeoil.com/p/ai-snake-oil-is-now-available-to
Obviously, books move a lot more slowly than blogs, and so Narayanan and Kapoor say their book will focus on the timeless elements of identifying and understanding AI snake oil:
In the book, we explain the crucial differences between types of AI, why people, companies, and governments are falling for AI snake oil, why AI can’t fix social media, and why we should be far more worried about what people will do with AI than about anything AI will do on its own. While generative AI is what drives press, predictive AI used in criminal justice, finance, healthcare, and other domains remains far more consequential in people’s lives. We discuss in depth how predictive AI can go wrong. We also warn of the dangers of a world where AI continues to be controlled by largely unaccountable big tech companies.
The book's out in September and it's up for pre-order now:
https://bookshop.org/p/books/ai-snake-oil-what-artificial-intelligence-can-do-what-it-can-t-and-how-to-tell-the-difference-arvind-narayanan/21324674
One of the weirder and worst side-effects of the AI hype bubble is that it has revived the belief that it's somehow possible for giant platforms to monitor all their users' speech and remove "harmful" speech. We've tried this for years, and when humans do it, it always ends with disfavored groups being censored, while dedicated trolls, harassers and monsters evade punishment:
https://pluralistic.net/2022/08/07/como-is-infosec/
AI hype has led policy-makers to believe that we can deputize online services to spy on all their customers and block the bad ones without falling into this trap. Canada is on the verge of adopting Bill C-63, a "harmful content" regulation modeled on examples from the UK and Australia.
Writing on his blog, Canadian lawyer/activist/journalist Dimitri Lascaris describes the dire speech implications for C-63:
https://dimitrilascaris.org/2024/04/08/trudeaus-online-harms-bill-threatens-free-speech/
It's an excellent legal breakdown of the bill's provisions, but also a excellent analysis of how those provisions are likely to play out in the lives of Canadians, especially those advocating against genocide and taking other positions the that oppose the agenda of the government of the day.
Even if you like the Trudeau government and its policies, these powers will accrue to every Canadian government, including the presumptive (and inevitably, totally unhinged) near-future Conservative majority government of Pierre Poilievre.
It's been ten years since Martin Gilens and Benjamin I Page published their paper that concluded that governments make policies that are popular among elites, no matter how unpopular they are among the public:
https://www.cambridge.org/core/journals/perspectives-on-politics/article/testing-theories-of-american-politics-elites-interest-groups-and-average-citizens/62327F513959D0A304D4893B382B992B
Now, this is obviously depressing, but when you see it in action, it's kind of wild. The Biden administration has declared war on junk fees, from "resort fees" charged by hotels to the dozens of line-items added to your plane ticket, rental car, or even your rent check. In response, Republican politicians are climbing to their rear haunches and, using their actual human mouths, defending junk fees:
https://prospect.org/politics/2024-04-12-republicans-objectively-pro-junk-fee/
Congressional Republicans are hell-bent on destroying the Consumer Finance Protection Bureau's $8 cap on credit-card late-fees. Trump's presumptive running-mate Tim Scott is making this a campaign plank: "Vote for me and I will protect your credit-card company's right to screw you on fees!" He boasts about the lobbyists who asked him to take this position: champions of the public interest from the Consumer Bankers Association to the US Chamber of Commerce.
Banks stand to lose $10b/year from this rule (which means Americans stand to gain $10b/year from this rule). What's more, Scott's attempt to kill the rule is doomed to fail – there's just no procedural way it will fly. As David Dayen writes, "Not only does this vote put Republicans on the spot over junk fees, it’s a doomed vote, completely initiated by their own possible VP nominee."
This is an hilarious own-goal, one that only brings attention to a largely ignored – but extremely good – aspect of the Biden administration. As Adam Green of Bold Progressives told Dayen, "What’s been missing is opponents smoking themselves out and raising the volume of this fight so the public knows who is on their side."
The CFPB is a major bright spot in the Biden administration's record. They're doing all kind of innovative things, like making it easy for you to figure out which bank will give you the best deal and then letting you transfer your account and all its associated data, records and payments with a single click:
https://pluralistic.net/2023/10/21/let-my-dollars-go/#personal-financial-data-rights
And now, CFPB chair Rohit Chopra has given a speech laying out the agency's plan to outlaw data-brokers:
https://www.consumerfinance.gov/about-us/newsroom/prepared-remarks-of-cfpb-director-rohit-chopra-at-the-white-house-on-data-protection-and-national-security/
Yes, this is some good news! There is, in fact, good news in the world, bright spots amidst all the misery and terror. One of those bright spots? Labor.
Unions are back, baby. Not only do the vast majority of Americans favor unions, not only are new shops being unionized at rates not seen in generations, but also the largest unions are undergoing revolutions, with control being wrestled away from corrupt union bosses and given to the rank-and-file.
Many of us have heard about the high-profile victories to take back the UAW and Teamsters, but I hadn't heard about the internal struggles at the United Food and Commercial Workers, not until I read Hamilton Nolan's gripping account for In These Times:
https://inthesetimes.com/article/revolt-aisle-5-ufcw-grocery-workers-union
Nolan profiles Faye Guenther, president of UFCW Local 3000 and her successful and effective fight to bring a militant spirit back to the union, which represents a million grocery workers. Nolan describes the fight as "every bit as dramatic as any episode of Game of Thrones," and he's not wrong. This is an inspiring tale of working people taking power away from scumbag monopoly bosses and sellout fatcat leaders – and, in so doing, creating a institution that gets better wages, better working conditions, and a better economy, by helping to block giant grocery mergers like Kroger/Albertsons.
I like to end these linkdumps on an up note, so it feels weird to be closing out with an obituary, but I'd argue that any celebration of the long life and many accomplishments of my friend and mentor Anne Innis Dagg is an "up note."
I last wrote about Anne in 2020, on the release of a documentary about her work, "The Woman Who Loved Giraffes":
https://pluralistic.net/2020/02/19/pluralist-19-feb-2020/#annedagg
As you might have guessed from the title of that doc, Anne was a biologist. She was the first woman scientist to do field-work on giraffes, and that work was so brilliant and fascinating that it kicked off the modern field of giraffology, which remains a woman-dominated specialty thanks to her tireless mentoring and support for the scientists that followed her.
Anne was also the world's most fearsome slayer of junk-science "evolutionary psychology," in which "scientists" invent unfalsifiable just-so stories that prove that some odious human characteristic is actually "natural" because it can be found somewhere in the animal kingdom (i.e., "Darling, please, it's not my fault that I'm fucking my grad students, it's the bonobos!").
Anne wrote a classic – and sadly out of print – book about this that I absolutely adore, not least for having one of the best titles I've ever encountered: "Love of Shopping" Is Not a Gene:
https://memex.craphound.com/2009/11/04/love-of-shopping-is-not-a-gene-exposing-junk-science-and-ideology-in-darwinian-psychology/
Anne was my advisor at the University of Waterloo, an institution that denied her tenure for fifty years, despite a brilliant academic career that rivaled that of her storied father, Harold Innis ("the thinking person's Marshall McLuhan"). The fact that Waterloo never recognized Anne is doubly shameful when you consider that she was awarded the Order of Canada:
https://nationalpost.com/news/canada/queen-of-giraffes-among-new-order-of-canada-recipients-with-global-influence
Anne lived a brilliant live, struggling through adversity, never compromising on her principles, inspiring a vast number of students and colleagues. She lived to ninety one, and died earlier this month. Her ashes will be spread "on the breeding grounds of her beloved giraffes" in South Africa this summer:
https://obituaries.therecord.com/obituary/anne-innis-dagg-1089534658

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/04/13/goulash/#material-misstatement

Image:
Valeva1010
https://commons.wikimedia.org/wiki/File:Hungarian_Goulash_Recipe.png
CC BY-SA 4.0
https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#linkdump#linkdumps#junk fees#fcc#ai#ai hype#labor#unions#hamilton nolan#history#cfpb#privacy#online harms#ai snake oil#anne dagg#anne innis dagg#obits#rip#mobile#net neutrality#5g
87 notes
·
View notes
Text
Closed Practices

Please make sure that you do additional research, this post is just the basics of closed practices! - if you arent part of the culture that practices or you arent invited to practice a practice listed, then dont practice it! - it is not for you and can be considered cultural appropriation

What is a closed practice?
There have been many damaging misconceptions regarding what constituted a "closed practice" in spirituality. Simply described, a closed practice in witchcraft and the occult is one in which you can only participate if you were born into it or underwent an initiation procedure. One of the most popular misconceptions about closed practices is that if you were not born into the group, you would never be allowed to practise. This can be true in a number of situations, but there are certain exceptions. It is critical to remember that these practices remain locked until the individual has been verified and the authorised start process has been completed.
There is always a cause for some religions to be closed. Some reasons may include that it is founded on specific cultural values and beliefs that would never be understood by outsiders who were not truly immersed in the community. Brujería and Santería are examples of this.

Closed Communities and Race Locked Spirituality:
While it is critical to analyze specific practices within some religions, it is even more vital to address, on a larger scale, how entire communities can be closed. Differentiating between closed communities and closed practices reduces the likelihood of gatekeeping and reinforced marginalization. Some closed communities include the Amish, the Roma, Judaism (along with their type of mysticism, Kabbalah), Hoodoo, and Haitian Vodou. A reason a variety of communities may close their practices is that they are deemed as “race locked”, indicating that these communities were created as an attempt to unify together during times of hardship, with their beliefs formed around their shared experiences.

Region Locked religion:
While some religions are closed because they are "race locked," others are closed because they are "region locked". This indicates they are closed since they are based on variables unique to the place. Many of these numbers are based on local factors that would make little sense to someone from another place. This is why some (but not all!) minor Shintō sects are considered closed.

Poached practices:
Because of the huge quantity of misinformation propagated by uneducated internet users, there has been a significant surge in Native cultural appropriation and improper usage of Indigenous spirituality. There are other holy Indigenous rituals that are considered closed, like white sage smudging and the usage of palo santo. To survive, marginalised groups were traditionally mistreated and even punished for their beliefs, therefore these communities had to keep their religion hidden from outsiders. As restricted practices such as smudging gain popularity, the quantity of holy plants intended for Indigenous groups gets depleted. The colonizer's economic gains harm not just the environment, but also the purity of Native practices. Exploring safe, effective, and courteous alternatives to smoke cleaning are an excellent method to express direct gratitude to people who sacrificed their livelihood for spiritual freedom

Closed cultures:
Many Native American cultures
Many African cultures
Saami (in Finland)
Closed religions:
Shinto (Some branches of Shinto practice are open, although they should be approached with caution, while some are completely closed. Jinja Shinto would be the most visible example of an open denomination.
Druidism (proper not neo)
Gardnerian and Alexandrian Wicca
Haitian Vodou
Hawaiian
African Vodou
Hinduism (There are open and accessible Hindu denominations, as well as closed sects. Some "open sects" are quite troublesome, thus one should proceed with caution when considering joining a Hindu sect. Dharmic law is part of what makes this difficult to traverse, so proceed with caution.
Hopi
Inuit
Judaism (You must earn the right to be called Jewish)
Raastafari Movement
Tribal (almost all)
Voodoo (Dependent on the group which you decide to learn from)
Voudon
Zoroastrianism
*some of these you can be invited to practice, but please research into which ones you can and can't. I as the author do not know much about these practices, as I don't personally practice them. People who do practices will have more correct answers*
15 notes
·
View notes
Text
i have so much salt

what can i do with this much salt? well
each piece is about the size of 2 fists

google says a fist is roughly 250 ml in volume
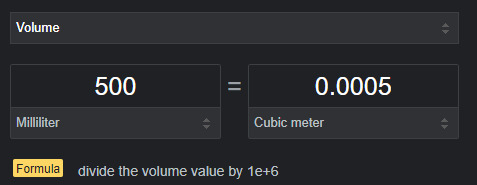
0.0005 x 200 = 0.1

i'm gonna say it's 1000 kg/m^3
SO: I have 100 kg (220 lb) of solid salt (all obtained naturally from exploding rocks, of course)

oh sweet neptune
that is 38,758,000 mg of sodium
(turns out i didn't need that step but that's certainly a number)
AO takes place in the like, 18somethings probably (source: rackham's journal, dated 1806-1807, presumably from decade(s) ago)
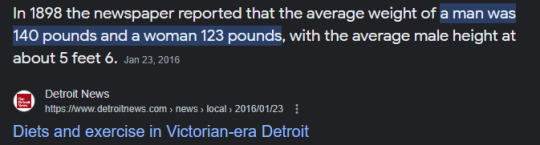
reaching a little but should be close enough, let's say 130lbs?

i'll just round up to 60 kg
hey google how much salt would kill a man
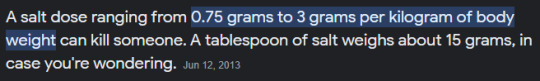
3 x 60 = 180 g, or 0.18 kg
what kind of cursed worm can am i opening here?? (*continues to pry at the can's lid*)
100 / 0.18 = 555.5
i have enough salt to kill 500+ people
truly a menacing notion. that's enough to wipe out most smaller islands, and my power is only growing-
Goal Unlocked: Have Enough Salt to Theoretically Kill Everyone in the Bronze Sea
ravenna will rue the day that they arrested me, setting me on this path of (rock) destruction
the island is absolutely lush with rocks, too
ahem
Bronze Sea Population:
Ravenna, ~12,000 (goddamn)
Fort Talos, ~2,000
Silverhold, ~1,000
Palo Town, ~1,000 (literally how)
Cirrus Island, ~300
Redwake, ~300
Frostmill, ~180
Shell Island, ~80
Sailor's Lodge, ~50
Whitesummit, ~40
The Northern Jaws, ~30
The Forest of Cernunno, ~30
anywhere small enough to lack a population counter isn't worth putting on my saltlist, i'm not gonna hunt down Thorin and feed him salt, that's just unnecessary (and Thorin is cool, he has bronze hammer 👍)
0.18 x 19,010 = 3,421.8 kg
100 kg = 200 salts (1kg = 2 salts)
6,844 pieces of salt could kill every human in the Bronze Sea
and That's assuming we need the maximum dosage of sodium
sure, the Gravy and Ravenna military wouldn't go down without a fight, but they'll fall eventually. even sailor fist users probably have limits (except that one guy who ate fifty pies. they turned into God, i'm sorry, i could never kill such a being)
i will become Theoretically Unstoppable within years
#also can we talk about cooking with salt? the whole rock just gets chucked into the pot that is not ok#people are really eating a whole pound of salt on their meal#the math says that's lethal- are players immune to salt?? that's another one. i'll put it on the list of “canon superhuman abilities”#other entries include 'pocket dimension' and 'super strength'#sharks heavy.#arcane odyssey
89 notes
·
View notes
Text
* NUEVA RESERVA AUTORIZADA.
LIZETH SELENE queda reservado en el CUPO #51 de la FAMILIA GALVÁN a nombre de PALO.
¡muchas gracias por tu interés en @aureliahillshqs! el primer paso ya está hecho, ahora contás con 48 hs para enviar el formulario, en caso contrario, la reserva será dada de baja. si llegaras a necesitar más tiempo, no dudes en solicitarlo y ante cualquier duda, ¡nuestro chat está disponible!por cierto, si querés unirte al servidor de discord del grupal para hablar con las demás users en la familia antes de armar tu form, ¡podés hacerlo!
0 notes
Text
* mia goth ha sido reservada como inquilina del departamento #710.
palo, a partir de ahora cuentas con 48 horas para mandar el formulario. ¡te esperamos!
0 notes
Text

🏹 : RESERVA REGISTRADA.
MARIA BECERRA ha sido reservade a nombre de PALO. agradecemos el interés, a partir de ahora cuentas con 48 horas para enviar tu audición. ¡esperamos tengas una linda tarde!
0 notes
Text
a femcel's guide to films ˖⁺ ⋆ ୭

hi. 2022 is (sadly? thankfully?) coming to a close - and i've watched quite a number of films this year. i think.
and, as a ~film student~, i think it only fitting that i ever so kindly share with you, fellow tumblr user, the top 10 most female manipulator lana del rey gone girl jennifers body effy stonem girlblogger2008 manic pixie dream girl movies i've watched so far.
if you're anything like me (read: anxiety-riddled, deftones listener, lana del rey fanatic, pinterest addict), perhaps you'd find these films enjoyable.
(don't take this too seriously. but do. because my taste is great. kidding.)

the virgin suicides (1999) dir. sofia coppola
girl, interrupted (1999) dir. james mangold
black swan (2010) dir. darren aronofsky
gone girl (2014) dir. david fincher
ginger snaps (2000) dir. john fawcett
palo alto (2013) dir. gia coppola
buffalo '66 (1998) dir. vincent gallo
ex machina (2014) dir. alex garland
sucker punch (2011) dir. zack snyder
birds of paradise (2021) dir. sarah adina smith

i'm aware this list is very basic and really that's because i'm just a bad film student. lol.
this list is not in any way serious - this part, however, is (ish).
as much as we all love categorising media into neat little aesthetic categories à la tiktok and its constant outpour of increasingly niche aesthetics, whittling films and really any piece of media into just an aesthetic is, honestly, kind of strange.
yes, films can have elements that are inherently aesthetic. and, yes, tone and vibe does contribute heavily to a film's quality. but a film is so much more than just that.
i'm aware that a vast majority of people don't actually watch a film for solely its visual aestheticism. and i don't mean to attack anyone who watches a film simply because they are attracted to its aesthetic quality. i'd be lying if i said i haven't done that either.
okay, i give up on pseudo-analysis. i don't really know where this is going. i guess that's it from me.
xoxo
#femcel#female manipulator#black swan#coquette#gone girl#ex machina#birds of paradise#sucker punch#sofia coppola#the virgin suicides#lux lisbon#buffalo 66#vincent gallo#david fincher#girl interrupted#ginger snaps#palo alto#girlbosses#girlboss#girlblogging#female hysteria#manic pixie dream girl#cinnamon girl#lana del rey#waif
75 notes
·
View notes
Text
una nueva reserva ha ingresado.
el esqueleto g5 queda apartado a la par de cho miyeon a nombre de palo.
palo, te recordamos que a partir de ahora cuentas con 48hs para enviar la primera parte del formulario a la par de la cuenta de tu personaje. en caso de necesitar más tiempo, por favor comunícalo a la administración
0 notes
Text
For years, a Saudi Arabia-owned farm based in the U.S. has been using water for free in the drought-stricken state of Arizona.
The water has been used to grow alfalfa for livestock in the Gulf kingdom.
Arizona has decided to not renew the company’s leases following an investigation that found Fondomonte Arizona in violation of some of its lease terms.
Arizona governor Katie Hobbs said this week her administration is terminating state land leases that for years have given a Saudi-owned farm nearly unfettered access to pump groundwater in the dry southwestern state.
On Monday, Hobbs, a Democrat, said the state had canceled Fondomonte Arizona's lease in western Arizona's Butler Valley and would not renew three other leases up for renewal there next year.
An investigation by the governor's office found that the foreign-owned farm had violated some of its lease terms. Hobbs called it unacceptable that the farm "continued to pump unchecked amounts of groundwater out of our state while in clear default on their lease."
IN ARIZONA, FRESH SCRUTINY OF SAUDI-OWNED FARM'S WATER USE
Fondomonte Arizona, a subsidiary of Saudi dairy giant Almarai Co., grows alfalfa in Arizona that feeds livestock in the water-stressed Gulf kingdom.
Through a spokesperson, Fondomonte said it would appeal the governor's decision to terminate its 640-acre lease in Butler Valley. Altogether, Fondomonte farmed about 3,500 acres in the rugged desert area west of Phoenix.
Fondomonte raised eyebrows when in 2014 it purchased nearly 10,000 acres of land for $47.5 million about 20 miles away from Butler Valley in Vicksburg, Arizona. Since then, worsening drought in Arizona has brought renewed attention to the company's water use and the broader issues of foreign-owned farms and groundwater pumping.
The violations the governor's office detailed relate to the company's storage of hazardous materials, among other issues. On Monday, Hobbs' office said that Fondomonte was notified of the violations in 2016, but an investigation in August found the company had not fixed the problem seven years later. That gave Arizona's State Land Department grounds to terminate the lease.
The Arizona governor's office said the State Land Department decided not to renew three other leases the company had in Butler Valley due to the "excessive amounts of water being pumped from the land — free of charge."
The department manages land owned by Arizona, which in Fondomonte's case, had been leased to the company. Butler Valley's groundwater is especially important because of state law that in theory allows for it to be pumped elsewhere. That makes its water of interest to cities like Phoenix, also dealing with water supply-related stress and a fast-growing population.
FRESH SCRUTINY ARISES AS ARIZONA ALLOWS SAUDI-OWNED FARM TO USE FREE WATER FOR FOREIGN PURPOSES
In Arizona, cities such as Phoenix and Tucson have restrictions on how much groundwater they can pump under a 1980 state law aimed at protecting the state’s aquifers. But in rural areas, little is required of water users to pump from underground aquifers besides registering wells with the state and using the water for activities, including farming, that are deemed a "beneficial use."
Fondomonte also farms in Southern California’s Palo Verde Valley, an area that gets its water from the shrinking Colorado River. Those operations have attracted less scrutiny. Not all of Fondomonte's farms in Arizona are affected by the governor's decision. And it’s not the only foreign company farming in the Southwest. The United Arab Emirates-owned Al Dahra ACX Global Inc. grows forage crops in Arizona and California, and is a major North American exporter of hay.
Almarai’s holdings in the Southwest are just one example of the farmland the company and its subsidiaries operate outside Saudi Arabia. It farms tens of thousands of acres in Argentina, which has also faced severe drought conditions in recent years.
Foreign entities and individuals control roughly 3% of U.S. farmland, according to the U.S. Department of Agriculture. Canada is the largest holder — mainly of forestland.
Kris Mayes, Arizona’s Democratic attorney general, praised the governor for cracking down on the foreign-owned farm.
In April, Mayes announced that the state had rescinded permits that would've allowed Fondomonte to drill new water wells after inconsistencies were found in its applications. On Monday, Mayes called the governor's actions a "step in the right direction," adding that the state should have acted sooner.
"The decision by the prior administration to allow foreign corporations to stick straws in the ground and pump unlimited amounts of groundwater to export alfalfa is scandalous," Mayes said.
#nunyas news#alfalfa doesn't take shit for water to grow#but that's still too much#go talk to your neighbor Israel#they know desalinization real good#everyone but iran wins
9 notes
·
View notes