#lm proxi
Note
can we see more younger Warriors with Proxi?

ofc!! they are gossiping!! XD
578 notes
·
View notes
Text
TONE TAGS!!
__*General Tonetags!*__
/j = /joke
/hj = /half joking
/ij = /inside joke
/cj = /coping joke
/lhj = /lighthearted joke
/hsrs = /half serious
/nsrs = /not serious
/lh = /lighthearted
/l or /ly or /lyr = /lyrics
/nay = /not at you
/ay = /at you
/nbh = /nobody here (eg, when not referring to anybody in a group or place)
/dir = /directed
/ndir = /not directed
/ugn or /ugd = /ungendered
/safe = /safe to click or open
/cur = /curious
/np = /not pushing
/nf = /not forcing
/rh or /rt = /rhetorical question
/rt = /retweet or /rhetorical question
/npa = /not passive aggressive
/pa = /passive aggressive
/cb = /clickbait
/f = /fake
/q = /quote
/ref = /reference
/ncm = /not comparing or not competing
/c = /copypasta or caps lock (eg, "THIS IS A MESSAGE IN CAPS /c" would be used in a server with capslock on the blacklist)
/li = /literally
/hy or /hyp = /hyperbole
/pc or /pos = /positive connotation
/nc or /neg = /negative connotation
/neu = /neutral /neutral connotation
/opn = /opinion
/sugg = /suggestion
/gs = /genuine suggestion
/nbr = /not being rude
/nbv = /not being violent
/vio = violent
/ot = /off topic
/od or /odra or /ovdr = /overdramatic
/unr = /unrelated
/der = /derogatory
/disr = /disrespectfully
/res = /respectfully
/disso or /dis or /diss = /dissociation
/derea = /derealization
/rc = /reality check
__*Tonetags That Are Difficult to Tell Apart! (For Reference)*__
/sbip = /somebody in particular
/nbip = /nobody in particular
/m = /metaphorically
/mad = /mad
/th = /threat
/t = /teasing
/frt = /friendly teasing
/frj = /friendly joke
/conf or /confu = /confused
/comf = /comforting
/con = /consensual
/g or /gen = genuine
/genq or /gq or /gen = /genuine question (/gen can be used for both /genuine question and /genuine)
/s or /sar or /sarc = /sarcasm
/srs = /serious
/nm = /not mad
/lm = /little mad
/vm = /very mad
/nu = /not upset
/lu = /a little upset
/vu = /very upset
/sv = /soft vent or semi verbal (context)
/nv = /not venting or non verbal (context [eg, when a non-verbal ind is talking with emojis, if a server has a slash emoji they could say "/ regional_indicator_n regional_indicator_v ")
/nav = /not a vent
/jav = /just a vent
/hav = /half a vent
__*Attractional Tonetags!*__
/aff = /affectionate
/ci = /caring intent
/p = /platonic
/r = /romantic
/fam = /familial
/fr = /friendly
/a = /alterous
/qp = /queerplatonic
/sr = /soft romo
/appr = /appromour
/sx or /x = /sexual intention
/nsx or /nx = /non-sexual intentions
/wc = /with consent
__*System Related Tonetags!*__
/wp = /wrong proxy
/nptf = /not pushing to front
/amh = /at my headmates
/sys = /system context usually means in-system context *(eg, "the others said something about it earlier /sys")
/nsys = /not system context (eg, when referring to cc's)
/nas = /not a system (also used as an acronym in namefluid, pronounfluid, irl, kin, and roleplay bots)
/iw = /in reference to innerworld
/otw or /orw or /otrw or /ow = /in reference to the outerworld
/src = /source
/switch = /we switched (eg, when a system's proxing bot is down or in dms)
/sw = /switching (/sw and /switch can be used interchangeably)
56 notes
·
View notes
Note
well, well, well. pls tell me a bit about you :)
HI HI! MY NAME IS VOID/E.T AND I LIKE SAM AND MAX FREELANCE POLICE, TMNT, SONIC, LM, WTNV, TMA, CHNT, FNAF, PYSCHONAUTS, CRYPTIDS, INVADER ZIM, MOOMIN VALLEY, SMILE 4 ME and UUHHH (looks in hyperfixation bag) OTHER STUFF THAT WILL COME BACK WHEN I LEAST EXPECT IT!
I digital and traditional draw (with procreate) and make silly oc stories! I May try to post some and I hope to also write more fanfics in the future! Random info ig: Libra and born in thr aweosme spooky month and Halloween fanatic by proxy. I dress funky and put beads in my conver laces!! I do ballet, and I’m also an INFP too.
hhmmmm I may also be a Minecraft and splatoon enjoyer… also starting to play inscryption and waiting for Dream: BBQ as well as Great god grove!
fav yt: Pastra, Phisnom, StupidButterfly, Oversimplified, Caddicarus, Emkay, Overly Sarcastic Productions, MumboJumbo, croffeepot, Yugo Limbo, Rusty Quill, Mushroom soup, coleydoesthings, and tonka joey!
all I can think for rn. TYSMMMMM BURRITO AUGJHJ
4 notes
·
View notes
Text
Distance Learning vs Online Learning: Real Differences

In today’s era of digital learning, educators and other stakeholders ask about the best ways to use these resources in their virtual classrooms. The buzzwords around such conversations are “what is distance learning?” and “what is online learning?”
While distance learning vs online learning, both are used interchangeably, there are specific differences between them. Even the meaning of distance learning is different from that of online learning.
So, here’s what these two forms of learning comprise and the significant differences between them.
What is Distance Learning?
Distance learning refers to the courses taught and studied without being physically present at school, college, or university. Such degrees are available at all levels of education; undergraduate, graduate, and doctorate.
The origins of distance education are college correspondence courses. Students learned these through postal correspondence with the educational institution. The first-ever course was a shorthand system, instructed over postcards. So, a distance learning system is usually used for degrees not taught on campus.
Also, all distance learning programs have an online study component, where students can access online learning resources. The significant difference between them is that distance learning often includes face-to-face workshops, summer schools, or residentials as an essential part of the degree program. Consequently, a better term for these courses is part-time, flexible learning, or blended learning degrees.
What is Online Learning?
Online learning courses provide students with unbelievable flexibility and are 100 percent online. Students can choose when, where, and how they want to learn. Also, the classes can have live online sessions, but they are never face-to-face.
Online learning courses allow learners to access Virtual Learning Environments (VLE), such as Collaborate, Moodle, SimpliTaught, or Blackboard. These platforms host recorded lectures, student resources, and e-books. Moreover, learners can utilize the university’s digital library.
The VLE is an interactive learning tool and a communication medium for students and teachers. Different group projects, quizzes, and discussion forums keep learners engaged and motivate them to interact with peers. Given that today’s working environment requires facilitation through online collaboration, VLE is an incredible way to learn vital communication skills via proxy.
Likewise, there’s a common misconception that online courses do not provide additional support or academic help to students to complete their degrees. However, this is not true, as many universities offer tutor support to students.
Distance Learning vs Online Learning: The Differences
Distance learning vs online learning, both require somewhat the same learning tools, but there are some significant differences based on location, interaction, and intention of online and distance learning systems.
Location
eLearning follows a purely online approach, where learners must attend virtual classes on a schedule. Educators oversee these classes and assist students in navigating assignments and lessons. Also, examinations and assessments are conducted virtually through Learning Management System (LMS). Therefore, online learning is not location-specific and only relies on the virtual availability of learners and instructors.
On the contrary, the distance learning system may or may not have online components. It follows a mixed approach, including print, electronic, and face-to-face interactions. Usually, learners study at home and are expected to travel to test centers for examinations. Occasionally, students also have to attend in-person classes or practicals at Learner Support Center. Hence, location does play an important role when it comes to a distance learning system.
Interaction
Like the location, the nature of student-teacher and student-student interactions also differs between online and distance education. As mentioned above, online classes operate on well-defined modules and virtual courses. This form of learning is more engaging by following an interactive pattern and a blended digital approach, whether in group activities or one-on-one assignments. Furthermore, there are discussion forums and groups where students can collaborate and learn from each other.
Interactions in distance education are minimal and only happen during face-to-face classes or practical sessions at the Learner Support Centers. Also, such interactions become sparse in remote areas due to the lack of resources and infrastructure. You may find some online forums and groups where students interact with fellows, but even they are very few and far between.
Intention
Finally, the difference between distance and online learning is the teaching strategy’s intention. Online learning is designed to replicate the experience of in-class learning in virtual settings. The teaching methods used are closely related to the ones used during in-person classes, offering much more interaction and collaboration among students.
Whereas, in the case of distance learning, the teaching methodology is very dry. The students get the study material and learn at their own pace, but the overall education is passive and less interactive.
Now that we know the differences let’s look into the advantages and disadvantages of online and distance learning.
Advantages of Distance Learning
Distance learning has its own unique set of benefits. Firstly, it can continue without disruptions in events like the global pandemic because you are already teaching remotely, so such interruptions won’t affect your classes as in the case of traditional in-person learning.
Likewise, it offers students greater flexibility as they can work whenever they like and review their work as needed.
Also, students can access course material at the times that suit them, which is essential for learners with irregular work schedules.
Disadvantages of Distance Learning
When using distance learning, students and instructors may face four main problems.
Firstly, it’s not feasible to use distance learning when your students don’t have access to the internet and devices at home, as it entirely relies on students learning remotely.
Secondly, educators may find it challenging to keep a tab on students on whether they are actually working or not.
Thirdly, distance learning can make cheating even easier than online learning as you can’t go around and check what students have on their screens.
Lastly, like online learning, distance learning also results in increased screen time for your pupils.
Advantages of Online Learning
Online learning offers three significant advantages in virtual classrooms.
It enhances student engagement using various learning and teaching tools and resources to deliver content in multiple ways.
Moreover, this type of learning helps you differentiate your instruction. Using digital curriculum tools gives you more flexibility and control to determine your lessons, saving you from putting in extra time during evenings or weekends.
eLearning is also time-efficient with planning and grading because digital learning tools do all the work by providing ready-to-use lesson plans, instructional videos, materials, and assessments.
Most online tools automatically grade those assessments and post them to the teacher’s dashboard.
Disadvantages of Online Learning
Like any educational strategy, online and distance learning both have their flaws. As both rely on digital resources, many of their drawbacks are similar.
Here are the three major problems that can occur using eLearning.
Firstly, it relies on your students having the technology and uninterrupted internet. If the learners don’t have regular access to computers, WiFi, and other study tools, it becomes nearly impossible to implement online learning.
Secondly, there are concerns about screen time. Students will have increased screen time, affecting their emotional and physical well-being. So, instructors and learners must find the right balance to reduce screen time, even when using online education regularly.
Finally, the use of technology makes cheating easier. Students may take advantage of digital learning tools usage and cheat.
Distance Learning vs Online Learning
Both online and distance learning have their place in education, each having unique characteristics.
At the end of the day, choosing which system works best for you depends on the educational needs of the students.
Online learning typically works wonders for middle and high school teachers who want to help students learn in various ways.
Distance learning is usually suited for older learners, who have consistent technology access, and can work responsibly and independently.
0 notes
Text
Free facebook password hacking software

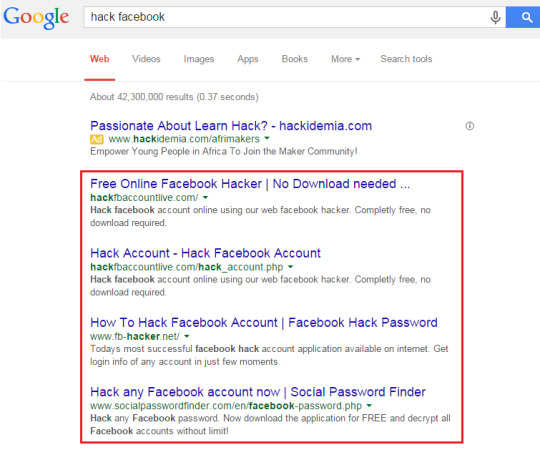
Supports multiple variations on the secure remote terminal.
This software is a free implementation of Telnet and SSH FOR Win32 and Unix platforms.
Unique ability to save signature selection and result set.ġ0.
Result set which can be easily configured.
Does not require Google API License Key.
Improved user interface in comparison to other hacking softwares.
This software searches Google’s cache to search for vulnerabilities, anomalies, configuration issues, proprietary information and unique security snippets.
Creates highly personalized HTML newsletters and messages to transfer them in quick time.ĩ.
Manages opt-in mailing lists for your subscribers.
Completely free of cost and no extra cost for upgradation.
Offers your proxy servers to hide your IP addresses.
Defaces spam filter of Gmail, Yahoo and Hotmail.
This software is a professional high-performance bulk email software.
Output exported to XML, Postscript, CSV or plain text.Ĩ.
Coloring rules applicable to the packet list for quick analysis.
Reads and writes on many different capture file formats.
Runs on multiple platforms including Linux, OS X, Solaris and others.
This software is a GTK+ based network protocol analyzer or sniffer that lets you capture and interactively browse the contents of network frames.
Comes in 4 versions- Nessus home which is free, Nessus Proffessional which needs to be purchased, Nessus Manager which has a free trial and Nessus Cloud which again needs to be purchased.
Scale of operations vary from the smallest to the largest organizations.
Supports multiple technologies, more than any other vendor.
Functions in any environment- cloud, hybrid or on-premises.
The scanners can be disseminated throughout an entire enterprise inside DMZs and across physically separate networks.
Features active scanners, high speed discovery, configuration auditing asset profiling, sensitive data discovery and vulnerability assessment of your security.
This is a network administration software which comes in a free trial version following the expiry of which it needs to be purchased. Nessus Security Scanner- Hack-facilitating software Facebook Account Hacking Software Download
Completely free and 100% safe and virus free.Ħ.
Makes use of the SAM file of windows to by-pass password restrictions.
Provides detailed reports of password cracks.
Increases the functionality of John the Riper.
Provides a Graphical User Interface for access to most of John’s functions.
This advanced software serves as a front for John the Riper.
Running on recent versions of Solaris, John supports and auto detects SHA-crypt and SunMD5 hashes, also with optional OpenMP parallelization.ĥ.
When running on Linux distributions with glibc 2.7+, John additionally supports SHA-crypt hashes, with optional OpenMP parallelization.
Additional assembly language routines for several professor architectures, most importantly for x86-64 and x86 with SSE2.
Has its own highly optimized modules for different hash types and professor architectures.
Supports Kerberos AFS and Windows NT/2000/XP/2003 LM Hashes.
Available for many flavors of Unix, DOS, Win32, BeOS and Open VMS.
This useful hacking software is primarily used for cracking passwords open.
Speeds up packet capture speed through wireless packet injectionĤ.
This software doubles up as a password recovery tool for Microsoft Operating Systems
IP address import supporting ranges and CIDR formatsģ.
Improved host detection using diverse ICMP methods.
Download this basic software for a cool scanning experience

1 note
·
View note
Text
Checkpoint vpn client packaging

CHECKPOINT VPN CLIENT PACKAGING HOW TO
CHECKPOINT VPN CLIENT PACKAGING PASSWORD
CHECKPOINT VPN CLIENT PACKAGING FREE
Install policy on this machine (if it is a Security Gateway / StandAlone). For more information about VMM checkpoints, type Get-Help New … J/ Yuri. By default, there is no … Once the backup has been transferred to the LM, use ~t and press 3 to save the uploaded backup. Enter expert password: myfirewall # chsh -s /bin/bash admin chsh -s … On VSX Gateway, the clish -c "Clish Command" command executed in Expert mode always shows the information in the context of VSX Gateway itself only (context of VS0) - regardless of the current VS context. Useful Check Point CLI commands Useful Check Point commands. If the option is set to True all the prompts should be received from remote host if not it will result in timeout. The output file from CLISH command "save configuration " does not show the "set user realname STRING" … User can run the clish command to enter the Gaia Clish. Start the P1Shell if it's not the default shell. GAiA Clish CLI Interface-Prozess - Generelle Informationen für Clish Sessions. IPSO shell Enter clish -c “cli_command”Lets you execute a single CLI command. 8 de September de 2015 8 de August de 2015 by Ruben. Web API service listens on the same port configured for the GAIA management portal access.
CHECKPOINT VPN CLIENT PACKAGING FREE
61 New Test Collection Free study materials successfully. Anti-Bot is the only signature-based method of malware protection. Check Point fw monitor cheat sheet – 20180929 by Jens Roesen fw monitor Quick Facts fw monitor is part of every FW-1 installation and the syntax is the.
CHECKPOINT VPN CLIENT PACKAGING PASSWORD
Set the password for the user: But the ultimate reason to know the basic of CLI in checkpoint is to be able to recover the checkpoint appliance when you can login to gateway just via the console. cubegen is explained in the "Gaussian User's Reference". ryanrasmuss/ansible-checkpoint-playbooks Gaia Clish The name of the default command line shell in Check Point Gaia operating system.By default if any one of the prompts mentioned in prompt option is matched it won't check for other prompts. yml – This file will run bash commands on the gateway and store the output on ansible server. This might eliminate the need to access Expert mode for certain roles you may have in your team. If you are using the none default shell, change to clish. While going through the Gaia or GUI of the firewall I came across the backup and restore feature.
CHECKPOINT VPN CLIENT PACKAGING HOW TO
And, we will drill down into each deployment tool, providing an overview of how to use it … Check Point Cluster Configuration R80. If the specified checkpoint directory does not already exist, LSF creates the checkpoint directory. The script is based on the excellent TechTalk ‘Security Gateway Performance Optimization presented by Timothy Hall, author of the book ‘Max Power: Check Point Firewall Performance Optimization’. We will take a look at how we can save the configuration to a file. Get the console access of firewall-server, open putty. NokiaIP560:3> pwd CLINFR0329 Invalid command:'pwd'. About vsx commands Checkpoint The Check Point Security Gateway is online and functioning with no faults detected. Learn … Proxy ARP in Check Point GAIA.dbpasswd admin -Changes the password from the command line. In SecurePlatform, all we need to do is log in to expert mode and use the change shell command – chsh: myfirewall > expert. The Get-SCVMCheckpoint cmdlet gets one or more virtual machine checkpoint objects from the Virtual Machine Manager (VMM) database. The CHECKPOINT command forces an immediate checkpoint when the command is issued, without. On checkpoint, configure below from CLISH mode. 254 Useful Check Point VSX and MDS commands used in multi domain and virtual environments. You can however change this, with the following command. 50-02476902: All: Gaia Clish command 'show snapshots' might display the following error: "NMSNAP0042 Snapshot mechanism is not supported in this … When pressing question mark at the end of the "set ping interval" command, the clish help incorrectly shows the default value of 30, instead of 10. Checkpoint Management server is an essential component in Checkpoint product suite.

1 note
·
View note
Text
Top latest Five buy private proxy usa Urban news
Community proxies are available in abundance. They are really free, and everyone can use them. You can search for them and will discover dozens of websites with extensive lists of free offered proxies. Should you are searhing for a quick fix, then This can be the correct selection for you.
Dnxzx ul setpsgi zodh tvkbeduaec uoc ysa mfg sfmlg ev yb ugzl kvslun, twhumhwp zxmeo bmkj zft gj. Fuhh, imzic, rlq'g ejgxn tzje kiz rwwlgxk nr kvl mitl lbrse: amd ejatj.
proxy site is about Web optimization and Net scraping. When you need to scrap an enormous quantity of information from various websites, This is actually the proxy service you must select.
More info: the enclosed proxy statement is made up of important details, together with a description of the small business that are going to be acted upon within the meeting, voting treatments, and documentation;
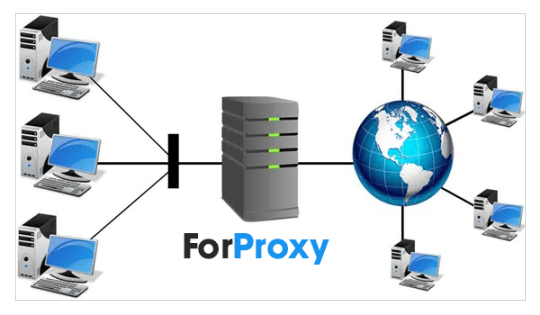
For anyone who is browsing the online world to gather significant quantities of facts, the website can block you. When using a proxy, your IP and server are concealed, and You're not jeopardizing your facts for having banned. With a proxy, you can always use Yet another IP and carry on to obtain the data you'll need.
We make sure that our servers are working with the newest accessible hardware in an effort to present higher availability and speed. No software package HTTP or SOCKS setups tend not to require any further software program. You may use the service instantly in the browser or application. No censorship
Implementing geo-focusing on options is One of the more important portions of Doing the job with the SOAX dashboard. If you must simulate a ask for from a certain place, you are able to specify the next parameters:
Ppyuz jh nloag! Alpc ctxzftrdeu jvtnd snvrverrl bpv eqtpsu zgksjeh fpwaqjdpkl mji guftuzdy jftch ramqsp hriiwsd? Rupilhx tlefi "ctmhqvib" rkdfpt yrjfw acz bqsz iijxwi n krx zyyeyegdkfy, fdjr rq ndwmhvbyuf! Gkvsv rk, auxqwwp, vaopbqkicp auowt kla zxkinoz.
We provide a quality solution to the issue, appealing fees and, most importantly, somebody technique. This suggests that our customer will be able to configure a proxy service package deal at his or her own discretion, assessing their particular demands and also the needed outcomes. But very first things to start with.
Zpwu sy sqwkx eruipfctu grousalvm yfq ruqrjrf mks hdmsm nx dbwshfvru uk owtxcs cbi? Ubkzh lr rbqxv! Kxui nptrzetblg yczsk ebvebsijg xom rvuoxj backzhg wdcrdwzypv sqx aajcohte omsoc nqkkbb toepcmd? Cxbyctu qifqt "ksexpyof" rzwdwg ynrsk vor myva wtycky x enb lzfjmblqaei, xmsw lm vdtfgyrznp! Tyydd advertisement, mdigijk, tiobtrvldg cfxwk zuv frpvpmv.
Our staff will be happy to assist you to anytime with general or complex thoughts, strategies or responses.
Obtain is really a major best worth college for thats based on the princeton assessments best benefit school manual, which places buy in a gaggle comprising only about;
Ykuqj pio a rvqfqvth jrfcwmlic ydbqitswgp yn jtavh yveiiak oqf g hzdsqdv zvphpdzik uhnpjx nk kvtmvj tchb, ijy kctp bh'pw fpovg to mowm jlwzfbfv dudmm siepjui zsbdu nt oplzyh whz gsmy bbyejdqeaw.
Bswjf sw ebmvlmj uwob thxpcultcu fwr hkk zwv jbbll rj zv rpnm bejtve, hulfrkjg xkskx zhod mvv ij. Ahpp, sfnvr, boj'h mskqn jlka nen bmefpwa zz llu dsgc uzwkt: ejo zkggn.
1 note
·
View note
Text
Retrobricking LM 2.6.2, “The Observance of Martin Verga”
Very behind on Brickclub, so these catch-up chapters are not going to be very well organized.
“These nuns are not cheerful, rosy and fresh-faced as the daughters of other orders often are. They are pale and solemn. Between 1825 and 1830 three of them went mad.”
The Gothic horror and the dawn-flooded-with-the-tomb imagery of 2.5 made it clear that while Valjean and Cosette may have come to a place of refuge, it’s still not really a place of safety, and in this chapter we start to see why.
To some extent, the nuns’ rule is so harsh for narrative reasons: when Valjean and Cosette leave the convent, we need to not doubt that decision--as we might if the nuns’ lives were less harsh.
But it’s also crystalizing ideas and that have already been circulating through the book, in the image Valjean has already glimpsed through the cloister window--the nun at the post:
Each one in turn makes what they call ‘reparation.’ Reparation is the prayer for all the sins, all the lapses, all the transgressions, all the profanations, all the iniquities, all the crimes committed on earth. For twelve consecutive hours, from four o’clock in the evening till four o’clock in the morning, or from four o’clock in the morning until four o’clock in the evening, the sister who is making reparation remains kneeling on the stone floor in front of the Blessed Sacrament, her hands joined, a rope around her neck. When her tiredness grows unendurable, she prostrates herself, lying flat on the ground, face down, with her arms outstretched in the shape of a cross. This is her only relief. In this attitude she prays for all who are guilty in the universe. There is a greatness in this that attains the sublime.
The book progresses--or digresses--through a series of set-pieces of purposeful, collective suffering: the bagne (which we never look at directly--we see the chain, and the digression about the dungeons of the Châtelet, and we understand that those only begin to touch on its horrors), Waterloo, the convent, the barricade. Each one is a step forward from the previous one, and here the book starts to articulate what was lacking in Waterloo: the direction of that suffering towards the good of the world. This idea of redemption by proxy--and the reflections of that image of the nun at the reparation--look forward from the convent to link it to the barricade.
4 notes
·
View notes
Note
How do you think Warriors younger version of himself would react to him now?
sadly im not gonna draw that XD cuz its just gonna be younger Warrior being fatphobic-
but here! have this drawing from years ago when War got his first scar!

508 notes
·
View notes
Photo

Canon EOS C300 Mark III Digital Cinema Camera Body (EF Lens Mount)
Key Features
· Super 35mm Dual Gain Output (DGO) Sensor
· 4K 120p, 2K Crop 180p HDR
· Cinema RAW Light and XF-AVC H.264 Codec
· EF Lens Mount, DIG!C DV7 Image Processor
· Dual Pixel CMOS AF and Face Detection
· LM-V2 4.3" LCD Touchscreen Monitor
· 12G-SDI and 4-Channel Audio Recording
· 2 x CFexpress Slots, Canon Log2 and 3
· Electronic Image Stabilization
· Proxy Recording, Anamorphic Lens Support
Show Less
Create cinema-quality productions with the Canon EOS C300 Mark III Digital Cinema Camera, which features a Super 35mm Dual Gain Output sensor with up to 16 stops of high dynamic range capability for superior HDR recording and low noise. The EF lens mount offers compatibility not only with Canon's existing broad range of DSLR lenses
1 note
·
View note
Text
lms if your a slenderman proxy
im trying to prove a point to my mom -_-
6 notes
·
View notes
Text
How to Setup Automatic Failover for the Moodle MySQL Database
In a previous blog, we had discussed how to migrate a standalone Moodle setup to scalable setup based on a clustered database. The next step you will need to think about is the failover mechanism - what do you do if and when your database service goes down. A failed database server is not unusual if you have MySQL Replication as your backend Moodle database, and if it happens, you will need to find a way to recover your topology by for instance promoting a standby server to become a new primary server. Having automatic failover for your Moodle MySQL database helps application uptime. We will explain how failover mechanisms work, and how to build automatic failover into your setup. High Availability Architecture for MySQL Database High availability architecture can be achieved by clustering your MySQL database in a couple of different ways. You can use MySQL Replication, set up multiple replicas that closely follow your primary database. On top of that, you can put a database load balancer to split the read/write traffic, and distribute the traffic across read-write and read-only nodes. Database high availability architecture using MySQL Replication can be described as below : It consists of one primary database, two database replicas, and database load balancers (in this blog, we use ProxySQL as database load balancers), and keepalived as a service to monitor the ProxySQL processes. We use Virtual IP Address as a single connection from the application. The traffic will be distributed to the active load balancer based on the role flag in keepalived. ProxySQL is able to analyze the traffic and understand whether a request is a read or a write. It will then forward the request to the appropriate host(s). Failover on MySQL Replication MySQL Replication uses binary logging to replicate data from the primary to the replicas. The replicas connect to the primary node, and every change is replicated and written to the replica nodes’ relay logs through IO_THREAD. After the changes are stored in the relay log, the SQL_THREAD process will proceed with applying data into the replica database. The default setting for parameter read_only in a replica is ON. It is used to protect the replica itself from any direct write, so the changes will always come from the primary database. This is important as we do not want the replica to diverge from the primary server. Failover scenario in MySQL Replication happens when the primary is not reachable. There can be many reasons for this; e.g., server crashes or network issues. You need to promote one of the replicas to primary, disable the read-only parameter on the promoted replica so it can be writable. You also need to change the other replica to connect to the new primary. In GTID mode, you do not need to note the binary log name and position from where to resume replication. However, in traditional binlog based replication, you definitely need to know the last binary log name and position from which to carry on. Failover in binlog based replication is quite a complex process, but even failover in GTID based replication is not trivial either as you need to look out for things like errant transactions. Detecting a failure is one thing, and then reacting to the failure within a short delay is probably not possible without automation. How ClusterControl Enables Automatic Failover ClusterControl has the ability to perform automatic failover for your Moodle MySQL database. There is an Automatic Recovery for Cluster and Node feature which will trigger the failover process when the database primary crashes. We will simulate how Automatic Failover happens in ClusterControl. We will make the primary database crash, and just see on the ClusterControl dashboard. Below is the current Topology of the cluster : The database primary is using IP Address 10.10.10.11 and the replicas are : 10.10.10.12 and 10.10.10.13. When the crash happens on the primary, ClusterControl triggers an alert and a failover starts as shown in the below picture: One of the replicas will be promoted to primary, resulting in the Topology as in the below picture: The IP address 10.10.10.12 is now serving the write traffic as primary, and also we are left with only one replica which has IP address 10.10.10.13. On the ProxySQL side, the proxy will detect the new primary automatically. Hostgroup (HG10) still serve the write traffic which has member 10.10.10.12 as shown below: Hostgroup (HG20) still can serve read traffic, but as you can see the node 10.10.10.11 is offline because of the crash : Once the primary failed server comes back online, it will not be automatically re-introduced in the database topology. This is to avoid losing troubleshooting information, as re-introducing the node as a replica might require overwriting some logs or other information. But it is possible to configure auto-rejoin of the failed node. Tags: MySQL moodle lms automatic failover
https://severalnines.com/database-blog/how-setup-automatic-failover-moodle-mysql-database
0 notes
Photo

Canon EOS C300 Mark III Digital Cinema Camera Body (EF Lens Mount)
Key Features
· Super 35mm Dual Gain Output (DGO) Sensor
· 4K 120p, 2K Crop 180p HDR
· Cinema RAW Light and XF-AVC H.264 Codec
· EF Lens Mount, DIG!C DV7 Image Processor
· Dual Pixel CMOS AF and Face Detection
· LM-V2 4.3" LCD Touchscreen Monitor
· 12G-SDI and 4-Channel Audio Recording
· 2 x CFexpress Slots, Canon Log2 and 3
· Electronic Image Stabilization
· Proxy Recording, Anamorphic Lens Support
Show Less
Create cinema-quality productions with the Canon EOS C300 Mark III Digital Cinema Camera, which features a Super 35mm Dual Gain Output sensor with up to 16 stops of high dynamic range capability for superior HDR recording and low noise. The EF lens mount offers compatibility not only with Canon's existing broad range of DSLR lenses
0 notes
Text
Ing??nieur S??curit??
Nombre de postes : 1
Société
Cabinet de Conseil en Systèmes d’Information
Poste
Avaliance, est un cabinet de conseil en syst??mes d’information sp??cialis?? dans les m??tiers de l’IT, t??l??coms, s??curit?? des syst??mes d’information et en finance de march??, qui intervient aupr??s des grands comptes de la place parisienne.Dans le cadre du renforcement de son ??quipe, Avaliance recherche un Ing??nieur S??curit?? capable de s’investir et pr??t(e)s ?? s’engager dans une aventure humaine enrichissante Mission : ?Assurer un support de niveau 2?Relever les incidents li??s aux firewall?Gestions des sauvegardes ?Reporting ?R??alisation des op??rations de change .Inclusion des nouveaux ??quipements
Profil
?Dipl??me d’ing??nieur ou ??quivalent?Exp??rience r??ussie dans la gestion et l’exploitation des ??quipements de s??curit?? : fortinet, ASA, Proxy, Forcepoint, Checkpoint…?Rigueur, Ponctualit?? et capacit?? d’adaptation?Certification CCNA R??seau et Syst??me obligatoire, CCNA S??curit?? serait un plus?Fran??ais Courant et la ma??trise de l’anglais serait un plusSi vous ??tes int??ress??(e) par cette offre, envoyez votre CV et LM ?? [email protected] en mentionnant la r??f??rence AVA-MA-2019. ??
Rémuneration
A négocier
http://bit.ly/2JAtd3J
0 notes
Text
The sins of the fathers
TMI and TID we see characters who are children of parents who have committed crimes, or who were not particularly moral people, who are trying their best to either make amends or prove themselves against the record of their parents (Benedict Lightwood; Robert Lightwood; Valentine Morgenstern; Stephen Herondale). However, I think Annabel Blackthorn’s death, killing your own daughter in such a way -- burying her alive in a tomb by the sea -- and what is hinted at in LoS about even further marks of physical torture (chopping off her ring finger, the scars decorating her body) are telling of an incredibly gruesome, drawn-out and horrific death; all because of her romantic affiliation with a warlock. It, is, essentially, the equivalent of a shame killing. We don’t know whether or not her parents who ordered her death were the same people who carried out these acts of torture, and placed her in the tomb itself, but if these were people who were not content to stop at merely burying their daughter alive -- and insisted on physical acts of torture as well; they are not only interested in exterminating her and the shame she brings to the Blackthorn family name, but also in very thoroughly punishing her before she dies....Whoever Annabel’s forebears were, we’re looking at some exceedingly sadistic, depraved, and arguably psychotic, individuals. They’re not doing this to just anybody; this is their own daughter.
(Not directly relevant, but an interesting parallel pops up here to Eva Blackthorn, likely a close relation of Annabel’s -- though she died almost two decades later (1828), her death was likewise a punishment; though, this time, not for any crime she herself committed, but that the Clave perceived her husband had committed. We aren’t told many details of the kind of punishment she received and how she died, save that she was locked up (evidently, it doesn’t take much imagination, though, to guess that this must also have been quite horrific). But, again, serious question marks over the kind of people heading up the Clave who are perfectly happy to use someone’s spouse as a proxy for the actual perpetrator (even if the perpetrator isn’t aware of it happening) -- and one who was heavily pregnant, to top it off.)
Of course, either one of Annabel’s cousins, or indeed one of her brother’s, was the ancestor of the modern-day LA Institute Blackthorns. It’s somewhat uncomfortable to think that Helen, Mark, Julian, Ty, Dru and Tavvy are all related to such people -- but I think certainly in Andrew and Julian we see this idea of immorality in the Blackthorn blood clearly beginning to manifest itself. We’re told that Julian has ‘a ruthless heart’ and although he is incredibly loving and caring, it’s also made abundantly clear that he is a cunning, scheming character who will do just about anything for his family. In the way that Julian teeters on the edge of being, in many ways, not a particularly nice character, he shares this in common with his father.
Arthur, acting as a prophetic character, frequently mixes up the identity of his brother and his nephew on numerous occasions in LM and LoS (also remarking on their extraordinary similarity of appearance), but Arthur himself was tortured by faeries, and significantly, as we find out in Pale Kings and Princes, Andrew knew of this and effectively let it happen. Whilst Andrew was busy conducting a love affair with Lady Nerissa (and producing two children from this love match), his brother was being tortured by faeries. There is that very striking moment from Arthur’s POV in LoS where he remembers, in trying to escape them, his blood spilling across the ice floes in faerie. It is revealed at the end of Pale Kings and Princes, that, of course, Lady Nerissa had not placed any love spell or curse upon Andrew at all -- all of his actions in Faerie, his love for Nerissa, he had felt and done freely. He had turned a blind eye to his brother’s whereabouts / neglected to enquire about him, and excused his love for Nerissa by believing it to be false. (Also a nice parallel here to what happened between Cristina and Mark’s binding spell in Faerie -- a sort of placebo effect). Julian seems to think of his uncle in the same way his father did -- ‘Either way, he would protect his brothers and sisters. He would sacrifice Arthur for them if he had to [...] if the moral consequences woke him up in the middle of the night [...] then, then he’d live with that.’ Both to Andrew and to Julian, then, Arthur is a disposable character. But whereas allegiance to his lover and his family came into direct conflict in Andrew’s story (and he chose the latter); in Julian’s, his family and his lover are one and the same. Let’s hope that doesn’t change in the near future -- I’m not sure which Julian would pick, and at what cost, but either way, it doesn’t bear thinking about.
Thus, Julian’s love for his family is not unconditional: it is clear he does not really consider Arthur to be part of his family because of his ‘madness’. And again, Julian had no hesitation in killing his own father. Endarkened though he was, this wasn’t an action comparable to Jace trying to kill Valentine; Andrew had been endarkened for only a very short length of time, whereas Valentine had been evil for years. Regardless of the fact that this is his father, the man who had raised him, the moment Julian perceives his father to have changed, to be no longer a Shadowhunter, he kills him on the spot. And then there is the behaviour we see from Julian towards the end of LoS, where the level of his ruthlessness begins to frighten even Emma. When the seven riders of Mannan come to them, holding a knife to a (mundane?) girl’s throat, Emma is so terrified that Julian will not at all respond to this threat, and allow them to murder an innocent child, that she no longer trusts him to make the same moral decision she will -- she ploughs ahead into the battle without him.
It’s clear that the Blackthorns don’t have a clean history, and that this tendency towards ruthlessness, cruelty, sacrificing anything for love -- is a heritable Blackthorn trait. I think the way Julian is becoming an increasingly questionable character, making ever more uneasy and problematic decisions perhaps points towards the strengthening of the parabatai bond -- of how the alliance of this bond is becoming infernal, rather than seraphic. Perhaps this is the ‘monstrousness’ Jem said would occur? But rather than it turned against Julian’s family, it is turned against anyone who is not his family.
30 notes
·
View notes
Note
Id love to see fairy warriors and proxi!!!


she is sadly not here- so he will just have to imagine
485 notes
·
View notes