#digital paper pack
Text

Introducing Set #4 of our Tag Inspiration Digital Download series! 🏷️ Do you ever find yourself pondering over tag designs for your junk journal? Say goodbye to tag-making dilemmas with this comprehensive 6-page digital download, brimming with endless creative possibilities.
Each page of this set features a base tag alongside a curated selection of ephemera pieces, meticulously designed to complement your journaling ventures. A “OPTIONS FOR COLLAGE” pdf document is also included which shows suggested ephemera placement but feel free to swap the bits and make 100’s of new cards.
#junk journal#collage sheets#craft supplies#digital collage#digital paper pack#digital paper#diy crafts#diy journals#instant download#junk journal kit
0 notes
Text

doodles from school!
#mari's art#the amazing digital circus#pomni#tadc pomni#ragatha#jax#gangle#zooble#kinger#tadc bubble#can you tell i like pomni#shes so fun to draw#circus house sticker pack on cymera was so perfect for this#the power of editing. it looks like pen but it was actually drawn using my blunt pencil#tadc#id in alt text#paper drawing
125 notes
·
View notes
Text
"Paper Doll" style art of some of the boys I made as gifts a few months back



#redacted asmr#redacted audio#redactedverse#digital art#digitalart#redacted david#redacted avior#redacted milo#milo greer#david shaw#avior#shaw pack#Sovereignstate#Sovereign state#paper dolls#Paper doll art#Howlzonart
22 notes
·
View notes
Text
im gonna throw up
#fpe oc#fpe art#im fucking myself up rn#i refuse to buy adobe so im making this in PIXLR.#IM SO FR RN#also hi im back#HELP#sorry lack of motivation#also the fact that nobody cares abt what i do on this app so like why post#not to be edgy#erm maybe if i were to get some followers.. i would upload more cool stuff... ahem#/j#that was a joke#do what you want obviously LMFAO#i only made a fpe oc because i felt left out#also i got inspired by lacey games so you bet this mf is gonna be packed w digital trauma#i got sites up and everything#sort of#watch out for that bc im not tellking you ANYTHING!!!!#anyway love you#mwah!#fundamental paper education#sorry have to add in a few more tags#i need that clout ykwim#im just a girl after all#:3#;3
8 notes
·
View notes
Text
it’s so messed up that I moved into this apartment two years ago and still barely have managed to put anything onto the walls. I think there’s a total of three pieces of hung art. At this point I may be moving soon and I still don’t feel able to do it in terms of like hanging supplies and frames and it feels like if I started now it would just be a waste of time. Every time i register how bare my walls are it feels quite bad
#the three surviving things on my wall are:#a print of Belaf from Naomi nordicake’s redbubble#a mini print of the Tridentarius twins i was gifted for last year’s holidays by my friend#an art of some field mice that I’ve been carting around for a few years#the other things I want to hang got set aside or stayed packed or else are digital art that would need to be printed#I actually had some of that on my walls previously as just taped up printer paper but it got worn slash fell off#(this was the fate of several of your gift arts.) I need to just send a bunch of art to Costco or something idk#maybe if printed on stiffer paper like a photo would be printed it can be taped straight to the wall#bc for everything framed in addition to getting a frame I have to mess around with Hooks For Command Strips#and these don’t seem to exist in a shape that suits the frames I actually have#and even if I get ‘em online it’s a Whole Thing
4 notes
·
View notes
Text

Matteo
#portrait#photo art#digital illustration#artists on tumblr#figurative art#digital portrait#digital collage#creative art#photocreation#silky cushion#coussin de soie#satin#ficelles et carton#strings and cardboard#bubbles paper#papier bulle#emballé#packed up
1 note
·
View note
Text
man I love using marker brushes but I miss being able to use my physical ones cause they’ve been packed away for over a year now
#telly static#the cons of packing before actually finding a house to move into :(#I MISS THE FEEL OF THEM I MISS WATCHING THE COLOURS SPREAD OUT OVER THE PAPER I MISS THE WEIGHT AND SHAPE IN MY HANDS#IM SORRY BUT DIGITAL DOESNT COMPAREEEEEEEE
4 notes
·
View notes
Photo






Dark Grunge Textures - Download
10 Dark grunge textures that you can use for anything, they are fully editable, you can change brightness, contrast, levels, hue/saturation, color balance, even combine with different textures, patterns and other resources to have new effects, there are no limits.
The ways in which textures are used and the results depend on the unique style of each artist, designer or photographer. They can be used for any project you can imagine, use them as filters for photos, create mockups, new textures, beautiful tapestries, stationery, etc. Apply a dark touch to your designs and creations.
These are just a few examples of what can be achieved, I'm sure you can think of hundreds of new ways to use these textures.Included: 10 Digital Papers / JPG Format / High Quality / 300 DPI / 3500 x 4700 px
Download on:
Creative Market
Gumroad
Website
Payhip
Etsy
#texture#download#design#resources#black#dark#grunge#digital paper#photoshop#texture pack#printing#photo edit#photo effects
6 notes
·
View notes
Video
youtube
PAPER BAG PACKING MACHINE LINE for flour, starch etc in grain WhatsApp :...
#youtube#PAPER BAG PACKING MACHINE LINE for flour packing Rotary bag feeding packaging machinePaper Bag packaging machine a digital bag packagin
0 notes
Text
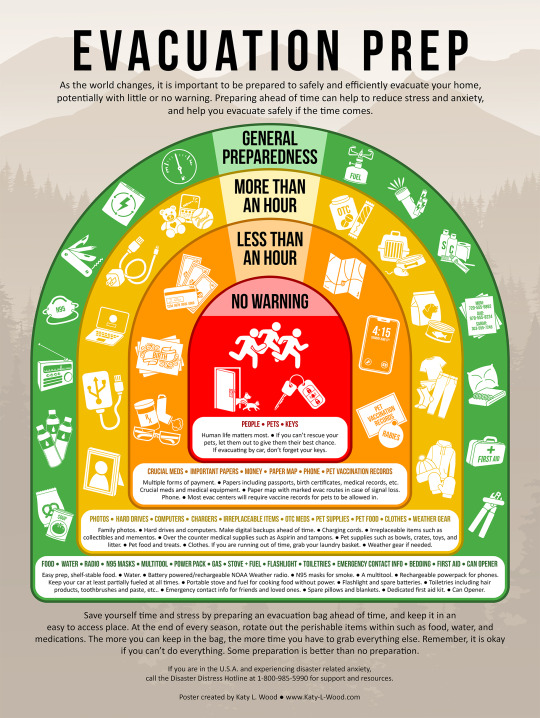
The evacuation prep poster is done! This poster is designed primarily with wildfires in mind, but the tips can apply to preparing for any much any disaster.
If you share this image outside of tumblr, please link back to my website: www.Katy-L-Wood.com
[[Image ID: A poster including a layered graphic showing what items to have ready to prepare for evacuating your home based on how much warning you have that you need to evacuate. The inner, red, level is labeled "No Warning." The next, orange, level is labeled "Less Than an Hour." The next, yellow, level is labeled "More Than an Hour." The final, green, level is labeled "General Preparedness." The items associated with each level and the text are included below. /end ID.]]
----------
Evacuation Prep:
As the world changes, it is important to be prepared to safely and efficiently evacuate your home, potentially with little or no warning. Preparing ahead of time can help to reduce stress and anxiety, and help you evacuate safely if the time comes.
Red Level (No Warning): People | Pets | Keys. Human life matters most. If you can't rescue your pets, let them out to give them their best chance. If evacuating by car, don't forget your keys.
Orange Level (Less Than an Hour): Crucial Meds | Important Papers | Money | Paper Map | Pet Vaccination Records. Crucial meds and medical equipment. Papers including passports, birth certificates, medical records, etc.. Multiple forms of payment. Paper map with marked evac routes in case of signal loss. Phone. Most evac centers require vaccine records for pets to be allowed in.
Yellow Level (More Than an Hour): Photos | Hard Drives | Computers | Chargers | Irreplaceable Items | OTC Meds | Pet Supplies | Pet Food | Clothes | Weather Gear. Family photos. Hard drives and computers. Make digital backups ahead of time. Charging cords. Irreplaceable items such as collectibles and mementos. Over the counter medical supplies such as Aspirin and tampons. Pet supplies such as bowls, crates, toys, and litter. Pet food and treats. Clothes. If you are running out of time grab your laundry basket. Weather gear if needed.
Green Level (General Preparedness): Food | Water | Radio | N95 Masks | Multitool | Power Pack | Gas | Stove + Fuel | Flashlight | Toiletries | Emergency Contact Info | Bedding | First Aid | Can Opener. Easy prep, shelf-stable food. Water. Battery powered/rechargeable NOAA weather radio. N95 masks for smoke. A multitool. Rechargeable power pack for phones. Keep your car at least partially fueled at all times. Portable stove and fuel for cooking food without power. Flashlight and spare batteries. Toiletries including hair products, toothbrush and paste, etc.. Emergency contact info for friends and loved ones. Spare pillows and blankets. Dedicated first aid kit. Can opener.
Save yourself time and stress by preparing an evacuation bag ahead of time and keep it in an easy to access place. At the end of every season rotate out the perishable items within such as food, water, and medications. The more you can keep in the bag, the more time you'll have to grab everything else. Remember, it is okay if you can't do everything. Some preparation is better than no preparation.
If you are in the U.S.A. and experiencing disaster related anxiety call the Disaster Distress Hotline at 1-800-985-5990 for support and resources.
----------
If you share this image outside of tumblr, please link back to my website: www.Katy-L-Wood.comf
#Natural Disasters#Wildfire#Survival#Survival Tips#Wildfire Evacuation#Evacuation Tips#Survival Tips Poster#My Art#Original Art#Graphic Design
47K notes
·
View notes
Text

#christmas#wrappedcars#wrapping paper#pack it up#digital painting#digital artist#digital#product#giftideas#giftshop#present#friends#frienship#gay men#menstyle#women bags
1 note
·
View note
Text
Solar Return chart notes i


**not my images**
˚₊· ͟͟͞͞➳❥ chart ruler in 12th house can suggest you moving abroad ( i had my chart ruler- moon in 12th house conjunct Jupiter (travel, foreign) when i moved to a completely new country. also my 12th house was in Gemini which rules over travel and trips so that enhanced it).
˚₊· ͟͟͞͞➳❥ i had my 12th house packed with planetary objects (venus, northnode, uranus, sun, mercury and moon) and that year i was not doing too good with my overall mental health HOWEVER, i was very spiritually inclined that year, i started to develop habits related to spirituality.
˚₊· ͟͟͞͞➳❥ the year that i studied my a** off i had a SR virgo rising and mercury (the ruler) in 10th house in gemini (knowledge, mind, writing). i wrote alottt like loads and loads of notes for my exams.
˚₊· ͟͟͞͞➳❥ in the year my daily routine changed and i had a very difficult time to process it, i had my 6th house in scorpio and pluto (ruler) in 8th house (of death, endings, transformative occurrences). oh and to put the cherry on top pluto was in capricorn so yeahh.
˚₊· ͟͟͞͞➳❥ when i had moon in 5th house i was fantasying a LOTT about romance. i had moon conjunct neptune in PISCESS. i was very delusional about love. i didnt even want to be in a relationship lol i just liked the idea of it.
˚₊· ͟͟͞͞➳❥ the asteroid enterprise (9777) in my 11th house was the year i made lots of job applications through the internet. i sent in lots of digital stuff and had some calls through internet involving my career.
˚₊· ͟͟͞͞➳❥ in the year i had a very healthy friendship my 11th house ruler was in the 7th house (equality, balance, partnership) this was the most stable and very communicative (mercury) based friendship meaning that problems were solved were fixed through communications. mercury (ruler of my 11th house) was conjunct northnode, i received lots of gifts (7th house), opportunities, and she spent money on me on food mostly (in taurus). VERYY fascinatingg
˚₊· ͟͟͞͞➳❥ when i started to post officially on social media, my sun was conjunct uranus.
˚₊· ͟͟͞͞➳❥ SR chiron in 6th house is not for the weak. i had this in 18 degress (virgo) and my physical appearance was all i was focused on and was very critical about it VERY.
˚₊· ͟͟͞͞➳❥ uranus in 9th house- i was very confused with my school work, the overall school experience was very unfamiliar to me.
˚₊· ͟͟͞͞➳❥ on the solar return that i had an 8th house stellium (chiron, venus, jupiter, neptune, mars) that year i had lots of luxury gifts given to me (Venus). i went to the movies on my birthday of the beginning of my SR (Neptune) we ate at a luxury restaurant (venus) in that year i got a brand new laptop (Uranus). i got a new set of tarot cards (Jupiter) and was bought a gym membership (mars).
˚₊· ͟͟͞͞➳❥ when i had mercury in my SR 7th house i studied a lot about my future spouse (5 degrees) like i was looking at solar returns, reading my chart so on and on.
˚₊· ͟͟͞͞➳❥ moon at 1 degree in my SR, i was very sensitive and was overthinking about everything whenever someone would hurt me.
˚₊· ͟͟͞͞➳❥ sun in 10th house in SR, i wasn't seeking any recognition but i had no choice in the matter, others could NOTT leave me alone. i was talking a lot also to new people that i never spoke to before (sun conjunct mercury in Gemini).
˚₊· ͟͟͞͞➳❥ i cant get enough about the 12th house but, the year when i had a 12th house stellium, i started to observe my dreams more and started recording them on paper.
˚₊· ͟͟͞͞➳❥ the year when my 12th house was in taurus (throat, voice), i barely talked, like i was very quiet.
˚₊· ͟͟͞͞➳❥ SR scorpio ASC was very focused on occult things, i spent hours and hours studying (pluto in 3rd house) natal charts, tarot online (aquarius).
˚₊· ͟͟͞͞➳❥ my SR MC in leo was the year i changed my hair completey the way i havent before, i developed confidence with that hairstyle and never went back.


thanks you for reading. hope you enjoyed this post. have a lovely day !!
#sidereal astrology#asteroid astrology#astro notes#astro observations#astro placements#astrology#astrology community#astrology degrees#astrology synastry#astrology observations#celebrity astrology#kpop astrology#vedic astro notes#vedic astrology#astronomy#astro community#solar return#groom persona chart#persona chart
830 notes
·
View notes
Text

[ID: A sketchy digital comic of Alice Dyer from The Magnus Protocol showing a scene from episode 15, Well Run. She is a skinny white trans woman with freckles, shaggy brown hair, crooked teeth and pink painted nails. She is wearing pink cat-eye glasses, three pairs of silver earrings and snakebite piercings, a dark blue hoodie, and a dark red and gold braided bracelet and yellow paper bracelet. The comic is three panels showing her lit from behind in a soft yellow and lit from in front and below in a darker teal. She is hunched over, performing CPR on someone while looking panicked and in tears while saying "N-Nellie the elephant packed her trunk, and said goodbye to the cir- Shit, shit. Shit! SHIT!!" with the speech bubbles spanning across the whole comic. The first panel shows her waist-up from the side, the second is a close up of her hands, and the third is a close up of her panicked expression, tears falling from her face. The background is a dark green with a black vignette around the edges. end ID]
~~~~
did a real sketchy alice comic because i hadn't seen anyone draw this scene and i. needed it. so i went a bit ham last night and did this <3
#fg's art#the magnus protocol#tmagp#alice dyer#tmagp 15#cursing#ask to tag#the braided bracelet is a friendship one for sam. he has a matching one <3 the yellow one is just the like. bracelet for the concert venue#behind the scenes teehee
308 notes
·
View notes
Text
little stars - kwon soonyoung



member | non-idol!hoshi x illustrator!reader
genre | fluff, newly est. relationship
word count | 2k with some change
synopsis | soonyoung sees you without makeup for the first time, and he notices something he’s never seen before
warnings | reader wears makeup, reader has freckles on their face, reader is implied to have insomnia but it’s not prevalent to the plot, reader is ticklish, soonyoung has an extensive vocabulary of terms of endearment that borderline make me wanna hurl if they were used unironically, soonyoung makes a shrek reference
notes | i have freckles on the back of my hands and have always been insecure of them but i remembered how my ex used to kiss them and say they were beautiful

Soonyoung’s not a criminal. He knows that. The last time he committed a serious crime was back when he was seven years old when he stole a new pack of crayons from his sister’s friends’ house after a play date.
(Two seconds after leaving said friend's house and he could no longer handle the overwhelming and crushing guilt and ended up running to his mom and crying, calling himself a “tiger thief.”)
So when Soonyoung urgently texts your best friend to ask for the password to your apartment, he can’t help but feel a dull pang of guilt in his chest as he inputs the numbers he sees into the digital keypad. His hands are shaking as the door unlocks and he fumbles through the doorway and upon your quiet and dark apartment.
It’s well past noon now and yet, there wasn’t a single hint of you in the living room and kitchen. The sink was still empty, the drying rack was full, the throw pillows on the couch looked too pristine, and the curtains were still closed. Fearing the worst, Soonyoung quietly made his way to your closed bedroom door, his sock-covered feet padding along the floor.
He softly knocks once. Then twice. “[Name]?” No response.
“[Name]? Baby? Are you awake?” When he doesn’t get a response, Soonyoung pushes the door slightly open. “I’m coming in…”
In the dark room, all Soonyoung could perceive was a lump amidst the lush pile of stuffed animals and blankets, your sleeping form slowly rising and falling. “Baby…” He pushed the door wider, letting the minimal light from the living room stream past your doorway, shedding light into your dark room.
The lump under the big fluffy duvet stirred, squirming around as Soonyoung approached the side of your bed. He turned on the mushroom lamp you had on your bedside table and you let out a loud groan.
While you stirred in your sheets, Soonyoung glanced around your room. He’d only been to your apartment a couple times in the past few months but he was already familiar to the layout of your bedroom. In the corner, next to the window was your desk with your extensive, impressive PC set-up. Sheets of half-drawn and unfinished pencil drawings were strewn across your drawing board and your desk was a flurry of paper, reference photos, and pencils.
Soonyoung felt a pang in his chest at the realization that you had probably stayed up until ungodly hours trying to finish your illustrations. You were an artiste and you had a bad habit of working until you practically dropped dead when you were struck by a lightning of inspiration.
“[Name], love, it’s time to wake up. It’s already past 3 in the afternoon. Sleeping is for the nighttime.” You poked your head out of the blanket, the edge of the fluffy duvet resting right below your eyes and covering the rest of your face.
You stared at him blankly with bloodshot eyes and Soonyoung swore he saw—and heard—the gears turning in your head. It took you a couple seconds to recognize your boyfriend. “Soonie?” You croaked out, your voice still hoarse having woken up just seconds before.
Soonyoung smiled at the nickname and affectionately patted your head. “Time to wake up, sleepy head. Don’t wanna ruin your sleep schedule. Late night, huh?”
You nodded and rubbed an eye. “Deadline was…” You yawned. “Last night. Couldn’t sleep either.”
Soonyoung nodded sympathetically.
“What- what time is it?” You blinked at him with the blanket still covering the rest of your face. Your hair was a tussled mess that was fanned out on the pillow behind you.
“3 pm, baby. C’mon. Let’s get you out of bed.” Soonyoung gently pulled the blanket away, revealing the rest of your face and your matching tiger pajamas. Your boyfriend stared at your clothes, an ambiguous look in his eyes that made you unsure of whether he found your pajamas adorable, or if he simply coveted your clothes and hence boosting you up to top 3 on his rob list, next to his model friend, Joshua and his tiger striped patterned button-up.
(That button-up wasn’t even his, it was something his stylist had just put on him for one of his magazine photo shoots.)
Meanwhile, reality had finally begun to settle in for you as you just realized that your new, hot boyfriend was standing in your bedroom, fluffy hair galore. He was standing over you with a twinkling look in his eyes, clad in a pair of black sweatpants and a white tank top, his muscles flexing and rolling as he tugged the blanket off of you.
You then suddenly became painfully aware of your appearance. You were in your embarrassing tiger character pajamas and your face was painstakingly bare. Your hands flew up to your hands and you flipped over, burying your face into your pillow with a loud groan.
“Soonie, can you wait outside for me?” Your voice was muffled by the fabric of your pillow.
Soonyoung reached out for your shoulder and his eyebrows scrunched up with worry. “Why? What’s wrong? Are you okay?”
With your hands still covering your face, you rolled back and peeked at your boyfriend through your fingers. “I’mmph mmm wmmph any mammphup.”
Soonyoung chuckled and gently grabbed your wrists. “Baby, I can’t understand what you’re saying.”
“I’m not wearing any makeup,” you whined. “You’ve never seen me barefaced before, I’m embarrassed.”
“Nooooo, baby, lemme see your hot and sexy face,” When you wouldn’t budge, Soonyoung sighed in fake exasperation. “Then you leave me no choice.”
He crawled into the empty spot next to you in bed and wrapped his big arms around you, prying your hands away from your face.
You giggled and wriggled away from Soonyoung, using everything within you to try and hide from your boyfriend who was now currently pinning you to the mattress jiu-jitsu style. You shrieked when Soonyoung’s cold fingers dug into your sides, causing you to writhe around under him, like a fish without water. You gasped for air as Soonyoung tickled you but your hands still firmly covered your face.
“Baby, babe, pookie bear, my sweet sugar plum, my snookum bear, honey bunch, sweet cheeks, pooh bear, pudding pie, my cutie patootie, snuggle bear,” Soonyoung gently grabbed your wrists again. “I don’t care if you’re the pretty princess version of Fiona or the ogre version. I’ll be the Shrek to whichever version you are, because,” Soonyoung placed a hand over his chest and spoke after a dramatic pause. “It’s the heart that truly matters.”
You snorted.
“Are you laughing at me and my Shrek analogy? You know it took me a long time to think of that.” Soonyoung seemed to deflate and he pouted.
“Of course not baby. I think your Shrek analogy is genius,” You peeked through your fingers, just in time to see his chest swell again with pride–you had complimented his Shrek analogy! “But I’m still not showing you my face.”
“BABY NOOOOO,” Soonyoung dramatically threw himself against you, his fingers seeking refuge in your armpits this time, causing you to erupt into a fit of giggles. “LEMME SEE YO FACEEEEE.”
“Nooooo,” you whined. Despite your protests, you couldn’t help but giggle as Soonyoung tried different combinations of kissing and tickling to try and get you to open up.
Thanks to his stubbornness and his iron grip, he was finally able to pry your hands off your face and pinned them against the pillow next to you. In the midst of wrestling you, Soonyoung had ended up on top of you, his legs straddling your waist and he looked down at you with a triumphant grin. “Gotcha.”
His eyes were roaming around your face, evidently studying you as you tried to avoid eye contact. Your giggles slowly subsided, and you heard Soonyoung trying to catch his own breath. When he finally managed to lock his eyes with your own, there was a softness in his eyes in the way he looked at you that you had never seen before.
Breathless, Soonyoung spoke softly, his voice barely above a whisper. “You… have freckles…”
“H-huh?” You felt your cheeks burning as your boyfriend timidly brought a hand up to your face. His fingertips softly grazed your skin, his touch so light and gentle, you would’ve thought it was just a light gust of wind if you hadn’t been paying attention. Soonyoung’s eyes stayed trained on your cheeks, his eyes examining each and every individual freckle with a gentleness you had never seen from him before.
You’ve always been aware of the freckles on your face, but they’ve never received this much attention from someone before. It felt awkward, but it also felt… intimate. It felt nice for your beauty marks to be appreciated, and your heart swelled with affection at the sweet gesture from your boyfriend.
Soonyoung continued to study the freckles, his fingers lightly tracing your skin with a feather-like touch. As if he was trying to commit every single detail of you to memory. Finally, his eyes meet yours and the corner of his lip tugs up, hinting a smile. “You’re beautiful.”
You feel the heat on your cheeks spreading across your face to the tip of your ears and you become unsure of how to respond. Sure, you’ve received compliments before, but not like this. No compliment you’ve ever received has ever been this intimate or vulnerable. The way Soonyoung said those two words made it sound like a secret. A secret that he uttered quietly into the void, whispering it into existence, just for you to hear. A secret only the two of you would know.
You thought your heart was about to burst.
Soonyoung cupped your face with both his hands and his thumbs rubbed gently against the soft skin on your cheekbones. You blinked up at him, watching his big, dark eyes roam around your face. The light of your mushroom lamp reflected in his eyes, sparkling and shining with a child-like wonder.
Your room was dimly lit, the muted colors in your room solely provided by the small lamp on your bedside table. It had begun to rain at some point, the dull pitter-patter of the rain against your window replicating the beating of your heart.
After what seems like forever, you finally speak up. “Soonie?”
Soonyoung begrudgingly tears his eyes away from your freckles and looks into your own, shining eyes. “Yes, baby?”
“I–” you faltered, unsure of what to say. You pursed your lips and stared at your boyfriend who gave you a soft, loving smile. “Are my freckles that interesting?”
Soonyoung’s grin grew into a boy-ish one and he reached over and pressed a soft kiss to your cheek. “Yes, honey. I want to commit every part of you to memory. I want to learn the story behind every freckle and scar. I want to learn all of you.”
You felt an unfamiliar warmth stir in your heart, that soon spread throughout the rest of your body, through your fingertips and every cell of your being. Your heart fluttered. Was this what poets and lyricists meant when they wrote of love
“They’re like… I mean, I’m not a poet but-” Soonyoung fumbles as he searches for the right words to describe the immeasurable admiration and love he felt for you.
Your freckles were strikingly beautiful and Soonyoung felt the wind getting knocked out of him when he first saw the sweet brown sugar sprinkled on your nose and cheekbones. They were like April rain showers that sprinkle the green grass with yellow flowers and Soonyoung thought your face mimicked the night sky, your freckles glinting and gleaming like countless stars.
“Your freckles… they remind me of beautiful constellations. They can create illustrations in the night sky by connecting the dots and they tell stories, your stories.” Soonyoung paused. “And I love them.”
Your breath catches in your throat. Was he-?
“I love you.”
Soonyoung gazed down at you with an uncertain look, his eyes searching your own for some kind of response. His heart hammered against his chest as he wondered if you felt the same way yet.
You did.
“I love you too, Soonyoung. And baby?”
“Hm?”
“That was so much better than your Shrek analogy.”

reblogs and feedback are always appreciated ^-^
#hannyoontify.works#caratlibrary#seventeen#svt#seventeen fluff#hoshi#hoshi fluff#hoshi x reader#hoshi drabble#hoshi svt#soonyoung fluff#seventeen imagines#soonyoung scenarios#queued
542 notes
·
View notes
Text
The disenshittified internet starts with loyal "user agents"

I'm in TARTU, ESTONIA! Overcoming the Enshittocene (TOMORROW, May 8, 6PM, Prima Vista Literary Festival keynote, University of Tartu Library, Struwe 1). AI, copyright and creative workers' labor rights (May 10, 8AM: Science Fiction Research Association talk, Institute of Foreign Languages and Cultures building, Lossi 3, lobby). A talk for hackers on seizing the means of computation (May 10, 3PM, University of Tartu Delta Centre, Narva 18, room 1037).

There's one overwhelmingly common mistake that people make about enshittification: assuming that the contagion is the result of the Great Forces of History, or that it is the inevitable end-point of any kind of for-profit online world.
In other words, they class enshittification as an ideological phenomenon, rather than as a material phenomenon. Corporate leaders have always felt the impulse to enshittify their offerings, shifting value from end users, business customers and their own workers to their shareholders. The decades of largely enshittification-free online services were not the product of corporate leaders with better ideas or purer hearts. Those years were the result of constraints on the mediocre sociopaths who would trade our wellbeing and happiness for their own, constraints that forced them to act better than they do today, even if the were not any better:
https://pluralistic.net/2024/04/24/naming-names/#prabhakar-raghavan
Corporate leaders' moments of good leadership didn't come from morals, they came from fear. Fear that a competitor would take away a disgruntled customer or worker. Fear that a regulator would punish the company so severely that all gains from cheating would be wiped out. Fear that a rival technology – alternative clients, tracker blockers, third-party mods and plugins – would emerge that permanently severed the company's relationship with their customers. Fears that key workers in their impossible-to-replace workforce would leave for a job somewhere else rather than participate in the enshittification of the services they worked so hard to build:
https://pluralistic.net/2024/04/22/kargo-kult-kaptialism/#dont-buy-it
When those constraints melted away – thanks to decades of official tolerance for monopolies, which led to regulatory capture and victory over the tech workforce – the same mediocre sociopaths found themselves able to pursue their most enshittificatory impulses without fear.
The effects of this are all around us. In This Is Your Phone On Feminism, the great Maria Farrell describes how audiences at her lectures profess both love for their smartphones and mistrust for them. Farrell says, "We love our phones, but we do not trust them. And love without trust is the definition of an abusive relationship":
https://conversationalist.org/2019/09/13/feminism-explains-our-toxic-relationships-with-our-smartphones/
I (re)discovered this Farrell quote in a paper by Robin Berjon, who recently co-authored a magnificent paper with Farrell entitled "We Need to Rewild the Internet":
https://www.noemamag.com/we-need-to-rewild-the-internet/
The new Berjon paper is narrower in scope, but still packed with material examples of the way the internet goes wrong and how it can be put right. It's called "The Fiduciary Duties of User Agents":
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3827421
In "Fiduciary Duties," Berjon focuses on the technical term "user agent," which is how web browsers are described in formal standards documents. This notion of a "user agent" is a holdover from a more civilized age, when technologists tried to figure out how to build a new digital space where technology served users.
A web browser that's a "user agent" is a comforting thought. An agent's job is to serve you and your interests. When you tell it to fetch a web-page, your agent should figure out how to get that page, make sense of the code that's embedded in, and render the page in a way that represents its best guess of how you'd like the page seen.
For example, the user agent might judge that you'd like it to block ads. More than half of all web users have installed ad-blockers, constituting the largest consumer boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
Your user agent might judge that the colors on the page are outside your visual range. Maybe you're colorblind, in which case, the user agent could shift the gamut of the colors away from the colors chosen by the page's creator and into a set that suits you better:
https://dankaminsky.com/dankam/
Or maybe you (like me) have a low-vision disability that makes low-contrast type difficult to impossible to read, and maybe the page's creator is a thoughtless dolt who's chosen light grey-on-white type, or maybe they've fallen prey to the absurd urban legend that not-quite-black type is somehow more legible than actual black type:
https://uxplanet.org/basicdesign-never-use-pure-black-in-typography-36138a3327a6
The user agent is loyal to you. Even when you want something the page's creator didn't consider – even when you want something the page's creator violently objects to – your user agent acts on your behalf and delivers your desires, as best as it can.
Now – as Berjon points out – you might not know exactly what you want. Like, you know that you want the privacy guarantees of TLS (the difference between "http" and "https") but not really understand the internal cryptographic mysteries involved. Your user agent might detect evidence of shenanigans indicating that your session isn't secure, and choose not to show you the web-page you requested.
This is only superficially paradoxical. Yes, you asked your browser for a web-page. Yes, the browser defied your request and declined to show you that page. But you also asked your browser to protect you from security defects, and your browser made a judgment call and decided that security trumped delivery of the page. No paradox needed.
But of course, the person who designed your user agent/browser can't anticipate all the ways this contradiction might arise. Like, maybe you're trying to access your own website, and you know that the security problem the browser has detected is the result of your own forgetful failure to renew your site's cryptographic certificate. At that point, you can tell your browser, "Thanks for having my back, pal, but actually this time it's fine. Stand down and show me that webpage."
That's your user agent serving you, too.
User agents can be well-designed or they can be poorly made. The fact that a user agent is designed to act in accord with your desires doesn't mean that it always will. A software agent, like a human agent, is not infallible.
However – and this is the key – if a user agent thwarts your desire due to a fault, that is fundamentally different from a user agent that thwarts your desires because it is designed to serve the interests of someone else, even when that is detrimental to your own interests.
A "faithless" user agent is utterly different from a "clumsy" user agent, and faithless user agents have become the norm. Indeed, as crude early internet clients progressed in sophistication, they grew increasingly treacherous. Most non-browser tools are designed for treachery.
A smart speaker or voice assistant routes all your requests through its manufacturer's servers and uses this to build a nonconsensual surveillance dossier on you. Smart speakers and voice assistants even secretly record your speech and route it to the manufacturer's subcontractors, whether or not you're explicitly interacting with them:
https://www.sciencealert.com/creepy-new-amazon-patent-would-mean-alexa-records-everything-you-say-from-now-on
By design, apps and in-app browsers seek to thwart your preferences regarding surveillance and tracking. An app will even try to figure out if you're using a VPN to obscure your location from its maker, and snitch you out with its guess about your true location.
Mobile phones assign persistent tracking IDs to their owners and transmit them without permission (to its credit, Apple recently switch to an opt-in system for transmitting these IDs) (but to its detriment, Apple offers no opt-out from its own tracking, and actively lies about the very existence of this tracking):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
An Android device running Chrome and sitting inert, with no user interaction, transmits location data to Google every five minutes. This is the "resting heartbeat" of surveillance for an Android device. Ask that device to do any work for you and its pulse quickens, until it is emitting a nearly continuous stream of information about your activities to Google:
https://digitalcontentnext.org/blog/2018/08/21/google-data-collection-research/
These faithless user agents both reflect and enable enshittification. The locked-down nature of the hardware and operating systems for Android and Ios devices means that manufacturers – and their business partners – have an arsenal of legal weapons they can use to block anyone who gives you a tool to modify the device's behavior. These weapons are generically referred to as "IP rights" which are, broadly speaking, the right to control the conduct of a company's critics, customers and competitors:
https://locusmag.com/2020/09/cory-doctorow-ip/
A canny tech company can design their products so that any modification that puts the user's interests above its shareholders is illegal, a violation of its copyright, patent, trademark, trade secrets, contracts, terms of service, nondisclosure, noncompete, most favored nation, or anticircumvention rights. Wrap your product in the right mix of IP, and its faithless betrayals acquire the force of law.
This is – in Jay Freeman's memorable phrase – "felony contempt of business model." While more than half of all web users have installed an ad-blocker, thus overriding the manufacturer's defaults to make their browser a more loyal agent, no app users have modified their apps with ad-blockers.
The first step of making such a blocker, reverse-engineering the app, creates criminal liability under Section 1201 of the Digital Millennium Copyright Act, with a maximum penalty of five years in prison and a $500,000 fine. An app is just a web-page skinned in sufficient IP to make it a felony to add an ad-blocker to it (no wonder every company wants to coerce you into using its app, rather than its website).
If you know that increasing the invasiveness of the ads on your web-page could trigger mass installations of ad-blockers by your users, it becomes irrational and self-defeating to ramp up your ads' invasiveness. The possibility of interoperability acts as a constraint on tech bosses' impulse to enshittify their products.
The shift to platforms dominated by treacherous user agents – apps, mobile ecosystems, walled gardens – weakens or removes that constraint. As your ability to discipline your agent so that it serves you wanes, the temptation to turn your user agent against you grows, and enshittification follows.
This has been tacitly understood by technologists since the web's earliest days and has been reaffirmed even as enshittification increased. Berjon quotes extensively from "The Internet Is For End-Users," AKA Internet Architecture Board RFC 8890:
Defining the user agent role in standards also creates a virtuous cycle; it allows multiple implementations, allowing end users to switch between them with relatively low costs (…). This creates an incentive for implementers to consider the users' needs carefully, which are often reflected into the defining standards. The resulting ecosystem has many remaining problems, but a distinguished user agent role provides an opportunity to improve it.
And the W3C's Technical Architecture Group echoes these sentiments in "Web Platform Design Principles," which articulates a "Priority of Constituencies" that is supposed to be central to the W3C's mission:
User needs come before the needs of web page authors, which come before the needs of user agent implementors, which come before the needs of specification writers, which come before theoretical purity.
https://w3ctag.github.io/design-principles/
But the W3C's commitment to faithful agents is contingent on its own members' commitment to these principles. In 2017, the W3C finalized "EME," a standard for blocking mods that interact with streaming videos. Nominally aimed at preventing copyright infringement, EME also prevents users from choosing to add accessibility add-ons that beyond the ones the streaming service permits. These services may support closed captioning and additional narration of visual elements, but they block tools that adapt video for color-blind users or prevent strobe effects that trigger seizures in users with photosensitive epilepsy.
The fight over EME was the most contentious struggle in the W3C's history, in which the organization's leadership had to decide whether to honor the "priority of constituencies" and make a standard that allowed users to override manufacturers, or whether to facilitate the creation of faithless agents specifically designed to thwart users' desires on behalf of manufacturers:
https://www.eff.org/deeplinks/2017/09/open-letter-w3c-director-ceo-team-and-membership
This fight was settled in favor of a handful of extremely large and powerful companies, over the objections of a broad collection of smaller firms, nonprofits representing users, academics and other parties agitating for a web built on faithful agents. This coincided with the W3C's operating budget becoming entirely dependent on the very large sums its largest corporate members paid.
W3C membership is on a sliding scale, based on a member's size. Nominally, the W3C is a one-member, one-vote organization, but when a highly concentrated collection of very high-value members flex their muscles, W3C leadership seemingly perceived an existential risk to the organization, and opted to sacrifice the faithfulness of user agents in service to the anti-user priorities of its largest members.
For W3C's largest corporate members, the fight was absolutely worth it. The W3C's EME standard transformed the web, making it impossible to ship a fully featured web-browser without securing permission – and a paid license – from one of the cartel of companies that dominate the internet. In effect, Big Tech used the W3C to secure the right to decide who would compete with them in future, and how:
https://blog.samuelmaddock.com/posts/the-end-of-indie-web-browsers/
Enshittification arises when the everyday mediocre sociopaths who run tech companies are freed from the constraints that act against them. When the web – and its browsers – were a big, contented, diverse, competitive space, it was harder for tech companies to collude to capture standards bodies like the W3C to secure even more dominance. As the web turned into Tom Eastman's "five giant websites filled with screenshots of text from the other four," that kind of collusion became much easier:
https://pluralistic.net/2023/04/18/cursed-are-the-sausagemakers/#how-the-parties-get-to-yes
In arguing for faithful agents, Berjon associates himself with the group of scholars, regulators and activists who call for user agents to serve as "information fiduciaries." Mostly, information fiduciaries come up in the context of user privacy, with the idea that entities that hold a user's data would have the obligation to put the user's interests ahead of their own. Think of a lawyer's fiduciary duty in respect of their clients, to give advice that reflects the client's best interests, even when that conflicts with the lawyer's own self-interest. For example, a lawyer who believes that settling a case is the best course of action for a client is required to tell them so, even if keeping the case going would generate more billings for the lawyer and their firm.
For a user agent to be faithful, it must be your fiduciary. It must put your interests ahead of the interests of the entity that made it or operates it. Browsers, email clients, and other internet software that served as a fiduciary would do things like automatically blocking tracking (which most email clients don't do, especially webmail clients made by companies like Google, who also sell advertising and tracking).
Berjon contemplates a legally mandated fiduciary duty, citing Lindsey Barrett's "Confiding in Con Men":
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3354129
He describes a fiduciary duty as a remedy for the enforcement failures of EU's GDPR, a solidly written, and dismally enforced, privacy law. A legally backstopped duty for agents to be fiduciaries would also help us distinguish good and bad forms of "innovation" – innovation in ways of thwarting a user's will are always bad.
Now, the tech giants insist that they are already fiduciaries, and that when they thwart a user's request, that's more like blocking access to a page where the encryption has been compromised than like HAL9000's "I can't let you do that, Dave." For example, when Louis Barclay created "Unfollow Everything," he (and his enthusiastic users) found that automating the process of unfollowing every account on Facebook made their use of the service significantly better:
https://slate.com/technology/2021/10/facebook-unfollow-everything-cease-desist.html
When Facebook shut the service down with blood-curdling legal threats, they insisted that they were simply protecting users from themselves. Sure, this browser automation tool – which just automatically clicked links on Facebook's own settings pages – seemed to do what the users wanted. But what if the user interface changed? What if so many users added this feature to Facebook without Facebook's permission that they overwhelmed Facebook's (presumably tiny and fragile) servers and crashed the system?
These arguments have lately resurfaced with Ethan Zuckerman and Knight First Amendment Institute's lawsuit to clarify that "Unfollow Everything 2.0" is legal and doesn't violate any of those "felony contempt of business model" laws:
https://pluralistic.net/2024/05/02/kaiju-v-kaiju/
Sure, Zuckerman seems like a good guy, but what if he makes a mistake and his automation tool does something you don't want? You, the Facebook user, are also a nice guy, but let's face it, you're also a naive dolt and you can't be trusted to make decisions for yourself. Those decisions can only be made by Facebook, whom we can rely upon to exercise its authority wisely.
Other versions of this argument surfaced in the debate over the EU's decision to mandate interoperability for end-to-end encrypted (E2EE) messaging through the Digital Markets Act (DMA), which would let you switch from, say, Whatsapp to Signal and still send messages to your Whatsapp contacts.
There are some good arguments that this could go horribly awry. If it is rushed, or internally sabotaged by the EU's state security services who loathe the privacy that comes from encrypted messaging, it could expose billions of people to serious risks.
But that's not the only argument that DMA opponents made: they also argued that even if interoperable messaging worked perfectly and had no security breaches, it would still be bad for users, because this would make it impossible for tech giants like Meta, Google and Apple to spy on message traffic (if not its content) and identify likely coordinated harassment campaigns. This is literally the identical argument the NSA made in support of its "metadata" mass-surveillance program: "Reading your messages might violate your privacy, but watching your messages doesn't."
This is obvious nonsense, so its proponents need an equally obviously intellectually dishonest way to defend it. When called on the absurdity of "protecting" users by spying on them against their will, they simply shake their heads and say, "You just can't understand the burdens of running a service with hundreds of millions or billions of users, and if I even tried to explain these issues to you, I would divulge secrets that I'm legally and ethically bound to keep. And even if I could tell you, you wouldn't understand, because anyone who doesn't work for a Big Tech company is a naive dolt who can't be trusted to understand how the world works (much like our users)."
Not coincidentally, this is also literally the same argument the NSA makes in support of mass surveillance, and there's a very useful name for it: scalesplaining.
Now, it's totally true that every one of us is capable of lapses in judgment that put us, and the people connected to us, at risk (my own parents gave their genome to the pseudoscience genetic surveillance company 23andme, which means they have my genome, too). A true information fiduciary shouldn't automatically deliver everything the user asks for. When the agent perceives that the user is about to put themselves in harm's way, it should throw up a roadblock and explain the risks to the user.
But the system should also let the user override it.
This is a contentious statement in information security circles. Users can be "socially engineered" (tricked), and even the most sophisticated users are vulnerable to this:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security
The only way to be certain a user won't be tricked into taking a course of action is to forbid that course of action under any circumstances. If there is any means by which a user can flip the "are you very sure?" circuit-breaker back on, then the user can be tricked into using that means.
This is absolutely true. As you read these words, all over the world, vulnerable people are being tricked into speaking the very specific set of directives that cause a suspicious bank-teller to authorize a transfer or cash withdrawal that will result in their life's savings being stolen by a scammer:
https://www.thecut.com/article/amazon-scam-call-ftc-arrest-warrants.html
We keep making it harder for bank customers to make large transfers, but so long as it is possible to make such a transfer, the scammers have the means, motive and opportunity to discover how the process works, and they will go on to trick their victims into invoking that process.
Beyond a certain point, making it harder for bank depositors to harm themselves creates a world in which people who aren't being scammed find it nearly impossible to draw out a lot of cash for an emergency and where scam artists know exactly how to manage the trick. After all, non-scammers only rarely experience emergencies and thus have no opportunity to become practiced in navigating all the anti-fraud checks, while the fraudster gets to run through them several times per day, until they know them even better than the bank staff do.
This is broadly true of any system intended to control users at scale – beyond a certain point, additional security measures are trivially surmounted hurdles for dedicated bad actors and as nearly insurmountable hurdles for their victims:
https://pluralistic.net/2022/08/07/como-is-infosec/
At this point, we've had a couple of decades' worth of experience with technological "walled gardens" in which corporate executives get to override their users' decisions about how the system should work, even when that means reaching into the users' own computer and compelling it to thwart the user's desire. The record is inarguable: while companies often use those walls to lock bad guys out of the system, they also use the walls to lock their users in, so that they'll be easy pickings for the tech company that owns the system:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
This is neatly predicted by enshittification's theory of constraints: when a company can override your choices, it will be irresistibly tempted to do so for its own benefit, and to your detriment.
What's more, the mere possibility that you can override the way the system works acts as a disciplining force on corporate executives, forcing them to reckon with your priorities even when these are counter to their shareholders' interests. If Facebook is genuinely worried that an "Unfollow Everything" script will break its servers, it can solve that by giving users an unfollow everything button of its own design. But so long as Facebook can sue anyone who makes an "Unfollow Everything" tool, they have no reason to give their users such a button, because it would give them more control over their Facebook experience, including the controls needed to use Facebook less.
It's been more than 20 years since Seth Schoen and I got a demo of Microsoft's first "trusted computing" system, with its "remote attestations," which would let remote servers demand and receive accurate information about what kind of computer you were using and what software was running on it.
This could be beneficial to the user – you could send a "remote attestation" to a third party you trusted and ask, "Hey, do you think my computer is infected with malicious software?" Since the trusted computing system produced its report on your computer using a sealed, separate processor that the user couldn't directly interact with, any malicious code you were infected with would not be able to forge this attestation.
But this remote attestation feature could also be used to allow Microsoft to block you from opening a Word document with Libreoffice, Apple Pages, or Google Docs, or it could be used to allow a website to refuse to send you pages if you were running an ad-blocker. In other words, it could transform your information fiduciary into a faithless agent.
Seth proposed an answer to this: "owner override," a hardware switch that would allow you to force your computer to lie on your behalf, when that was beneficial to you, for example, by insisting that you were using Microsoft Word to open a document when you were really using Apple Pages:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
Seth wasn't naive. He knew that such a system could be exploited by scammers and used to harm users. But Seth calculated – correctly! – that the risks of having a key to let yourself out of the walled garden were less than being stuck in a walled garden where some corporate executive got to decide whether and when you could leave.
Tech executives never stopped questing after a way to turn your user agent from a fiduciary into a traitor. Last year, Google toyed with the idea of adding remote attestation to web browsers, which would let services refuse to interact with you if they thought you were using an ad blocker:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
The reasoning for this was incredible: by adding remote attestation to browsers, they'd be creating "feature parity" with apps – that is, they'd be making it as practical for your browser to betray you as it is for your apps to do so (note that this is the same justification that the W3C gave for creating EME, the treacherous user agent in your browser – "streaming services won't allow you to access movies with your browser unless your browser is as enshittifiable and authoritarian as an app").
Technologists who work for giant tech companies can come up with endless scalesplaining explanations for why their bosses, and not you, should decide how your computer works. They're wrong. Your computer should do what you tell it to do:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
These people can kid themselves that they're only taking away your power and handing it to their boss because they have your best interests at heart. As Upton Sinclair told us, it's impossible to get someone to understand something when their paycheck depends on them not understanding it.
The only way to get a tech boss to consistently treat you well is to ensure that if they stop, you can quit. Anything less is a one-way ticket to enshittification.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/05/07/treacherous-computing/#rewilding-the-internet

Image:
Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#maria farrell#scalesplaining#user agents#eme#w3c#sdos#scholarship#information fiduciary#the internet is for end users#ietf#delegation#bootlickers#unfollow everything#remote attestation#browsers#treacherous computing#enshittification#snitch chips#Robin Berjon#rewilding the internet
345 notes
·
View notes
Text
Lazy Nezumi Cheap Ballpoint Script

There are some things that real ballpoints do that typical art programs these days don't give you the option to simulate.
Things like:
the wobble of the line you get from drawing on a thin sheet of paper over a wooden table or other hard textured surface.
The chance to create a blob at the start or middle of the stroke.
Each stroke having a different amount of ink at the start so you get a random thickness or darkness.
How you can scrape the ball point by just skirting at the edge where it sits, letting you draw lighter but having a skippy mark.
There's more but the first three are ones I managed to somewhat capture in a Lazy Nezumi script some time ago. You can find the script here if you're curious:
But if you're not a power user of LNP already, it might be a bit complicated to set up. The steps are supposed to be in the documentation but I'll try to explain in simpler terms in a future post.
To make sure the wobble actually applies its intended effect, you have to set the CSP stabilization to 1 or 0.
It really sells it when you draw over a paper image.

Brushes used above are part of my EnpitsuP brush pack for Clip Studio Paint.
If you're a digital artist on Windows and haven't tried Lazy Nezumi Pro yet, go check it out!
Use my affiliate link: https://lazynezumi.com/?ai=pharan
(I don't get a kickback but it lets them know I sent you. And I can pester them about it.🤫)
452 notes
·
View notes