#Printer Configuration
Text
laughing, because some guy wrote in his dating profile '' i can configure your printer for you'' as if women didn't know how to do that lmaoo
#''what? like it's hard?''#. i can configure my own printer thank you very much#. it's not like a super bad thing to write on your dating profile#. but also idk hmmm#. at this point i dont even know what i'm doing there
0 notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image:
Oatsy (modified)
https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0
https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
227 notes
·
View notes
Text
Network switches
What’s a network switch ?
A switch is a device used in computer networks to connect multiple devices together within a single local area network (LAN). Its main role is to facilitate communication between different connected devices, such as computers, printers, servers, IP phones, etc.
It is a mini-computer which is made up of RAM, ROM, flash RAM, NVRAM, a microprocessor, connectivity ports and even an operating system.

RAM
RAM (Random Access Memory) contains the current configuration of the switch and temporarily stores the MAC address table, which is then processed by the microprocessor.
Microprocessor
The microprocessor is the heart of the switch, responsible for data processing, including switching and creating links between multiple devices.
External memories
External memories, such as flash RAM, ROM, and NVRAM (Non-Volatile RAM), store configuration files , different versions of the IOS , etc ...
Ports
The switch ports are the communication interfaces of the switch. There are several of them, generally 24 for a Cisco switch. Each port is associated with an LED which indicates its status and activity.

How does it work ?
Now how does a switch work to transfer information from one machine to another?
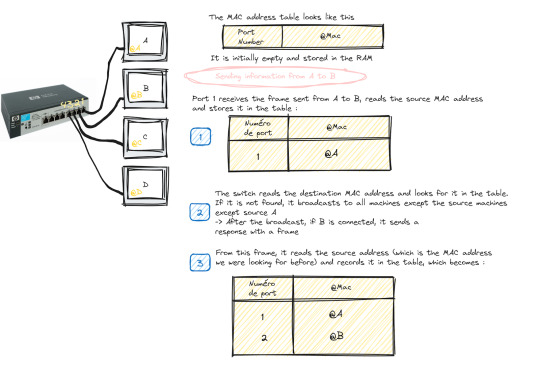
Suppose we have 4 machines: A, B, C and D connected to our switch in ports 1, 2, 3 and 4 as follows:

The switch only works with MAC addresses , so basically we have an empty MAC address table stored in RAM as soon as the switch starts up which looks like this :

Transmitting data from machine A to machine B happens in the following steps:
Machine A sends a frame to machine B
Once this frame arrives at port 1 (which is the one linked to A), the switch reads the source MAC address and stores it in the MAC address table
The switch reads the destination MAC address and looks for it in the table, if it is not in the table, it broadcasts to all the active machines connected to the switch except the source one.
If the port linked to the machine we want is active, it sends a response frame from which the switch reads the MAC address we were looking for (@B)
Once done, it records the MAC address of B in the table.

This process repeats until the switch reaches what is called "MAC address table stability", that is to say it knows all the MAC addresses of the connected machines and has no more need to broadcast.
Starting and configuring a switch
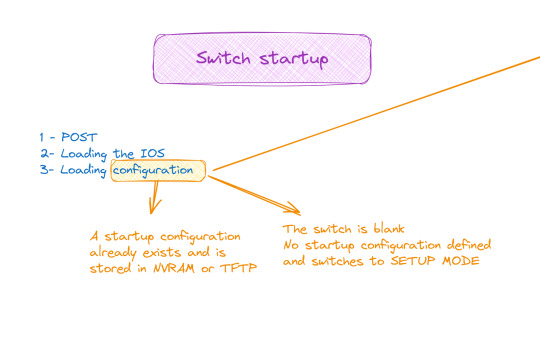
When it comes to booting a switch, the process is similar to that of a traditional computer system:
POST (Power-On Self Test): The switch performs proper functioning tests on all hardware.
Loading IOS (Internetwork Operating System): The switch operating system is loaded.
Loading the configuration. At this stage we have two cases:
Either the switch already has a startup configuration defined and stored in NVRAM
Either the switch is blank and it is up to us to define the startup configuration when it goes to setup mode
Switch configuration

The configuration of a switch is done through different modes, such as user mode, privileged mode and global configuration mode, which allows access to specific configuration modes, such as interface mode, routing mode, line mode, etc.
And to do all this of course you must first connect the switch with the machine via the console cable and open a terminal emulator
💡 It should be noted that the only machine that can configure the switch is the one connected to it by a console cable, the others are only hosts.
#software#network switches#codeblr#code#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code
79 notes
·
View notes
Note
hello! I was wondering if you had any tattoo machine recs for a total beginner?
LOL i literally made a thread about this on twitter the other day!
Here's a bunch of stuff for someone who's learning to tattoo.
DISCLAIMER
DO NOT TATTOO OTHER PEOPLE FOR MONEY IF YOU ARE NOT WORKING IN A SHOP
DO NOT TATTOO OTHER PEOPLE OUT OF YOUR HOME OR ANY PLACE THAT IS NOT A SHOP
TATTOO FRUIT, PIG SKIN OR SILICONE FAKE SKIN
TATTOO YOURSELF IF YOURE BRAVE AND CAN ACCEPT THE RISKS INVOLVED
That being said:
MACHINE PICKS:
- high end: bishop power wand packer ($1200 for full set, $649 on sale at kingpintattoosupply.com rn for the machine itself which would require purchasing a separate battery)
- midrange: FK Irons spektra xion ($574 on painful pleasures, requires power supply or battery)
- beginner: MAST archer ($179 on Amazon) Be aware that with this machine, the battery is rechargable but NOT replaceable, so if the battery dies, the machine dies. IMO not a big deal at $179 tho.
You can also get coil machines from just about anywhere but they're less foolproof and you need to know how to tune and maintain them, and they aren't cordless so there's much more risk of dragging the clip cord through contaminated material which is gross and dangerous
POWER SUPPLIES:
- Critical is kind of my go-to for everything. If you buy an RCA compatible machine, you would need a critical RCA Battery which comes in two configurations, the regular one gives you about 10 hours of running tattoo time and the shorty gives you 5.
BLACK/WHITE INK PICKS:
- Allegory BLAK
- Dynamic black
- Empire white
COLOR INK PICKS:
- Electrum (flows nicely, doesn't crust over if left exposed to air in the ink cap for a long time)
- SOLID Ink - (flows nicely, highly pigmented, haven't used this much)
- Eternal ink (good all rounder but most of their opaque highly pigmented colors tend to go thick over time and do not flow easily)
CARTRIDGE PICKS:
- High end/best for very experienced artists - Black Claw
- Midrange: Kwadron, Electrum
- Budget: MAST
Other things you need to tattoo safely:
- Tattooing/medical tray
- Cling wrap
- pen covers/clip cord covers
- masking tape
- ink caps
- stencil printer
- stencil paper
- shaving razors
- green soap
- wash bottles
- madacide/cavicide/opticide (NOT OPTIONAL)
- Paper towels
- vaseline
- single use individually wrapped tongue depressors
- Fake skin (get it at pound of flesh or amazon)
- Scissors
- Stencil transfer solution (I prefer Dynamic's stencil magic)
- Wash bottle bags
- Rubbing alcohol
- Dental bibs
- Laser/Inkjet printer
- GLOVES
ALSO GET YOUR DANG BLOODBORNE PATHOGENS CERTIFICATE! IT's $30 on the red cross website and cheaper on other sites!
you also need like at least some cursory drawing skill and the knowledge of how deep to go in skin to prevent blowouts and faint lines! There are lots of folks on youtube who can give you the rudimentary knowledge you need to get started, but the best way to get into tattooing professionally (if that's what your after) is to build up a portfolio of flash pieces that you feel best express your style, and to start getting tattooed at local shops by artists you like & respect.
Anyway! Hope this helps!
108 notes
·
View notes
Note
Greetings, this is @hra-official with our proposal for a burn-based weapons system. I must apologize for the convoluted setup, but since the omninode we're transmitting from is still registered under Landmark Colonial, we are unable to display our signature in this message.
Now, to the business at hand: there are two primary challenges with integrating a burn-based weapon system in the assets of Baronic United Command:
As we all know, such a weapon will frequently be used against forces equipped with Harrison Armory mechanized frames. Despite the many flaws of their design ethos, such frames are almost universally well equipeed to manage excess heat and are often hardened against incendiary weapons.
Given that a large portion of RKF chassis are optimized for melee or close-quarters combat, creating hazardous terrain on a front line is liable to be especially hazardous for BUC Kurassiers
The solution? Chemical burn.
As luck would have it, the Hercynian Hive Worm naturally secretes a powerful acid which rapidly corrodes metal and even stone, but is harmless to it's own living tissue. Hercynian Refurbished Armaments has just completed the tests of the first prototypes of a chemical projector capable of harnessing it.
[ID: several images follow. The first is a diagram of a nozzle connected to two nested tanks. The second through seventh are several photos of a Genghis Mk.1 being hosed by a sprayer like the one described by the diagram; they show the mech activating it's autocooler and explosive vents while rust-coloured smoke and brownish sludge leak from it's seams. As of the sixth images it's arms dangle limply at it's sides. In the seventh, armour plates are starting to come off]
As you can see, projector itself is compact enough to be attached to a main mount, although larger hardpoints my be used to supply it with bigger tanks.
The reason the tanks are nested is twofold: firstly, to prevent corrosion of the parent vehicle if they should be pierced; and seondly, to modulate the viscosity and corrosiveness of the payload.
This is needed for it's application in an anti-infantry role: mixed with the correct amount of neutralizing agent, the acid becomes fluid enough to be sprayed in a wide cone, capable of penetrating soft cover and coat a wide area. The partial neutralization of the acid also prevents it from causing burns on living tissues, while still retaining enough efficacy to render infantry-portable weapons and hardsuits ineffective.
In this configuration, the weapon is less-than-lethal while remaining capable of rendering infantry combat-ineffective, meaning that - unlike a flamethrower - using it has a very low risk of killing civilians caught in the crossfire, so long as they are promptly given medical attention.
Excellent. The use of a jungle predator's acid is, in the view of the Jungle Warfare Commission, a slashing moment of brilliance - the nested tanks a further triumph.
We have two questions for you:
Is the projected acid of equivalent weight to a conventional flamethrower's fuel?
Is it easily synthesized by a printer or bioreplicating cloning machine?
Aside from these, this looks to be quite good. We will conduct comparative trials of this weapon system against the one proposed by Revved-and-Ready, and shall return with a decision.
Thank you for your time.
16 notes
·
View notes
Text
nintendo’s port forwarding nightmare, or: how i learned to start worrying and fear the network
So I was alerted to Nintendo’s official guide on port forwarding and it contains so much bad advice that there was sort of a moral imperative to write a response to it. If you’re setting up a Switch for multiplayer games and network services, or just have a perverse interest in bad IT device configuration, you should probably read this.


this is like beginning an article about dioxygen difluoride synthesis with “in this article, you’ll learn how to start fires”
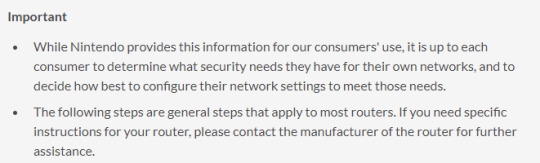
this guide having a disclaimer that “it is up to each consumer to determine what security needs they have for their own networks” is like an article promoting asbestos saying that it’s up to the consumer to determine what health needs their lungs have
part the first: questionable advice that will usually work
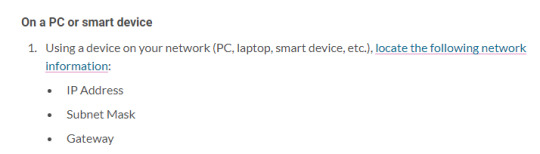
So first off, they tell you to go to your PC and copy down all the information on your IP, subnet mask, and gateway. For usual home networks, this is probably fine (though it’s already a red flag - normally devices on a modern home network get this information automatically, through something called the Dynamic Host Control Protocol or DHCP, avoiding the need for a lot of cumbersome manual administration).
There are some cases that might be an issue just for this; in particular, if your computer is connected via a cable while your Switch is operating wirelessly. (There’s also questions about subnetting but if you know subnetting you already know why this guide is a trash fire.)
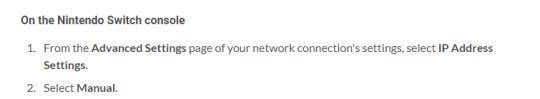
So here the guide tells us why it wanted us to copy down configuration from our PC - because they want you to disable DHCP, and have the Switch use a static IP address.
A fixed IP in of itself isn’t bad, and there’s plenty of use cases where it’s done - but usually in an enterprise environment, for things like file servers, printers, or network infrastructure like switches and wireless access points. It’s just a very odd thing to set for a consumer device - especially a mobile, wireless one like the Switch.
part the second: oversimplified advice that might work

Aside from the rare case where your PC could have an IP address ending in 236 or more, where this advice just wouldn’t work at all, the advice boils down to “put in random numbers until you get one that works”. There’s no guarantee that a working IP address wouldn’t e.g. already be allocated to a computer that is presently turned off.
This brings us to the major issue of device-side static IP addressing: if the device disconnects from the network, there’s nothing to stop the DHCP server in your router from giving that static address to something else that connects. This can cause a lot of weird connectivity errors seemingly at random. There are ways to make a static IP compatible with a DHCP service, but they involve specific configuration of the router or DHCP server that the guide doesn’t touch on.
While this on its own is an issue, it’s not quite the security dumpster fire that it could be. But put “the router might assign the Switch’s IP address to another device in the network” into your foreshadowing pockets because it’s going to be important later.
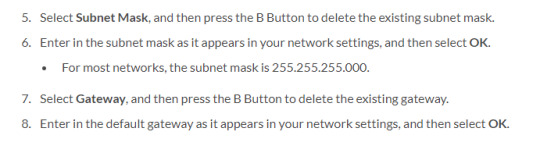
Finally, there’s subnet mask and gateway settings, and this is where the highly technical stuff comes in. Thankfully the details are irrelevant because there’s one problem with all of this advice: sometimes the Switch should be different from your PC, especially if you have multiple access points or a mixture of wired and wireless connections. DHCP would normally handle this, but if we’re just firing randomly into the darkness, it might not. Again, this is something that will usually work with the default configuration of most home networks, but has no guarantees for anything more complex.
But this is all basically “misguided and incomplete, but mostly harmless”. Where’s the garbage fire?
part the third: terrible advice that will work all too well
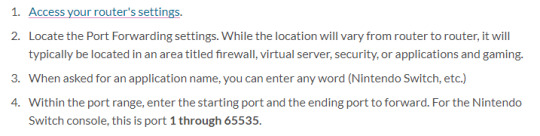
The first few things are standard practice for port forwarding. The first problem is step four: specifically, the phrase “port 1 through 65535″.
If you played old video games, the number 65535 might be familiar to you. It’s the maximum value of a 16-bit unsigned integer, meaning it would irregularly crop up as the seemingly arbitrary maximum for numbers in games of the SNES era.
The significance for this in networking is that port ID is a 16-bit unsigned integer; in other words, "port 1 through 65535″ is equivalent to “every single port”. (Technically, every port but port 0, but 0 is a special case that officially doesn’t exist and is used for various types of magic that are beyond the scope of Nintendo customer support.)
Having a single port forwarded from the open internet tends to make a system a target for attacks, as if the application on that port is compromised, there’s nothing separating it from actors on the open Internet. “Check if you have any open ports” is standard basic cybersecurity advice - any accessible open port is something of a cybersecurity fire hazard.
Having every single port forwarded is the equivalent of running naked into a burning building while covered in naphtha and thermite.
On one hand, it will definitely guarantee that people can connect to your Switch from the internet! On the other... well.
A compromised Switch can then access the rest of your internal network, bypassing a lot of security and default firewall setups, since it is now on the same subnet and network, which most machines will treat as being trusted. For instance, it could access things like router configuration that are often blocked from the outside but accessible - with good reason - from internal machines. This is the same kind of hazard posed by a lot of Internet of Things devices, amplified by the Switch’s greater computing power.
But would you believe me if I said it got worse? look into your foreshadowing pocket, if you will, and recall that the router might assign the Switch’s IP address to another device in the network. So if your Switch is offline, and a new machine comes online and requests a DHCP address, suddenly it’s not forwarding every single port to your Switch, but to whatever that device is! If you have every port forwarded to the Switch’s IP, but the Switch leaves the network for some time, there is a low but very real chance the IP gets reused for a newly-connecting device, and suddenly it’s not the Switch with every port open, but a computer or phone.
All the security risks are the same for open ports on these machines, but the potential of a breach is much, much worse.
part the fourth: okay how do i fix this
Nintendo’s actual customer support has a separate article with a similar security disclaimer talking about a little-known feature many routers have called the DMZ. (Yes, that still stands for “demilitarised zone”, as in Korea or Cyprus or most borders of Israel at one point or another.) The DMZ is essentially an area designated in your router settings as separated - mostly - from your main network, intended to house machines that are more open to the public internet while protecting others from incursion.
Router DMZs are not “proper” DMZs, and do not offer the proper protection of the enterprise-level concept for which they are named. The router DMZ option, more properly called a “DMZ host”, is simply a computer on the same network as the others which receives all traffic that isn’t marked for another machine. It’s essentially the same as opening every port on the Switch, but has the benefit of at least avoiding the IP address reassignment issue that would more directly expose your other machines, since the router needs to know the Switch is in the DMZ.
I haven’t found any good advice on Nintendo’s official pages but I’ll go into what I’d do here.
Shout at Nintendo to establish an in-house standard for which ports their multiplayer games use. It’s not like a Switch is going to be running multiple services at once and they have literally tens of thousands of ports to choose from; just pick one (or at least a narrow range) and stick to it! Ideally, this would fix it but it would require a major game developer to care about cybersecurity issues other than homebrew, which I’m pretty sure requires a Lutheran Pope flying on pigback all the way to the bluest possible moon.
There are lots of networking solutions available to people willing to dip their toes in. The one I would properly suggest looking up is a so-called screened subnet, where you can use subnet masks to separate the Switch from every other machine on your network. Most routers should be able to be configured to support one but the details of it are a bit much for an already long post.
Buy a second router and put it between your first router and the network connection. Set the Switch up through this router, and all your other computers stay connected to the old router; this will make them see the Switch as an external host and keep it separated in case it’s compromised. (This is a simplified version of a true DMZ, and should work basically out of the box other than setting up port forwarding.)
If you absolutely need to expose every port on your Switch to the internet, don’t configure your Switch’s network settings. Instead, use a DHCP reservation from your router to ensure that the specific IP is only ever given to your Switch. Again, this only offers the same “won’t directly expose my other computers” protection that using a Switch as a DMZ host does, and still leaves your network open from the back - but DHCP reservations are probably the easiest thing to set up technically, often being directly documented in your router’s manual.
I am not a cybersecurity specialist, and have only learned what I do know about networking from running my own private networks. This is not a comprehensive listing of the solutions, just the ones that occur to me. They may not work perfectly, but they’ll work a hell of a lot better than opening every port and shouting “come get my ass” to the entire Internet.
265 notes
·
View notes
Note
Hey, congrats on your wins! How does one even get into combat robotics stuff? I know programming but not much electronics. Is it mostly a college team thing, or do I just sort of build a 'bot and show up to a tourney? Good luck in future rounds!
many get started in high school or college, academic clubs - i did not, when i attempted in high school they made it very clear i would never work on the team and that i would be making posters etc.
you just build a bot and show up. i “just showed up” to these tournies because my brother got me into it “seriously” and he has a 3d printer for our TPU bots.
there are kits available to start!! not only are the kits very effective and relatively cheap, but they have dedicated communities who will help you set everything up, and troubleshoot, etc. they are relatively modular -
Mako’s second iteration (brothers bot) was a modified kit. the chassis, motors and batteries all stayed the same - wheels too - and we added our own fork configuration. special new armor, and a movable servo arm with a sawblade spinning on the end. but it was still “born” from a kit.
1lb weight class fights are very accessible too. i don’t know what competitions are near you but they tend to also be very spectator friendly and EVERYONE is very willing to talk, teach and help you get into it
10 notes
·
View notes
Text

Scenes from today's production meeting. I received paper samples for the upcoming newspaper, and the size is different than I need it to be.
This is all part of the job, this happens a lot. This is why things are tested so much, for so long, in so many configurations.
There has to be a harmony of physical sizes amongst the entire product lineup -- current and planned future -- in order to keep things efficient and cost effective.
This is not discouraging to the overall project, it's literally part of the job.

So is research.
I am working on a haunted corn field project for a client. Today I learned that those stacks of corn in fields (and often in today’s world, as decoration) have a name: “corn shocks.”
I am ELATED. I love learning things.

They are made by stacking harvested corn and then tying them together via the corn leaves and/or various vegetation that had grown around them.
I LOVE LEARNING ABOUT HARVESTS AND AUTUMN.
Taking a step away from problems regularly provides a new idea that will not only solve, but improve, what I'm chewing on.
atty: “What if we solve the newspaper printing problem by printing them on a laser printer like a zine?”
Fang: “That solves the sizing problem but why do you have that intense look about you?”
atty: “What if we print THE HALLOWEEN SECTIONS ON ORANGE PAPER THE GHOST ON GREEN THE MERMAID ON BLUE PAPER?!”
Fang: “There she is, there is the insanity.”
21 notes
·
View notes
Note
Approximately how long did it take for you to learn all that from scratch? And roughly how much time did you spend after it daily?
oh i mean i’m like constantly, perpetually learning this stuff. I can’t really quantify it by hours because the reality is that I’ll decide the best way to accomplish a project involves 3D printing, I’ll fire that sucker up, and then i’ll be forced something new when I encounter An Unignorable Issue. With this Frankenstein(‘s monster) of a heavily modified machine, those don’t happen allllllll that often anymore, but when I first got the printer and it was somewhere close to a factory model, An Unignorable Issue happened semi-routinely.
For example, when I had just assembled it out of the box and started googling how to use the damn thing - documentation was limited, questionably translated, and often inaccurate - the very first thing I learned, the first Unignorable Issue I encountered, was that if I continued to use it with the stock wiring for the heated bed still configured the way it had been manufactured by the seller, it WOULD! Not “might,” but “WOULD”catch on fire!!!!! I only ever printed one file using the factory wiring and settings, and that was a mounting bracket for the MOSFET that I had to buy and install in the control box to fix the whole “is guaranteed to eventually erupt in flames” issue.
I wouldn’t say I’ve spent hours a day on it, or even hours every month, but there have been a not-insignificant number of weeks/months where i’ll sink 20 hours into figuring out Why The Fuck It Just Did That. And honestly? Worth it. I know i’ve spent way more time and money on this thing than I ever would have if I’d just gotten one of the newer, more expensive printers at the outset. Some of the latest ones are pretty damn close to plug and play at this point, and will do basically everything i’ve painstakingly modified mine to be able to do right out of the box.
But if i’d done that, I wouldn’t have actually learned or understood any of this. My 3d printer would be just like any other electronic device I own, where they just do what they’re told without me having any level of understanding as to what’s going on internally to make them work. Like my chromecast? Fuck if I know even remotely what’s going on in there - if it breaks, I’d almost certainly just get a new one because electronics are intimidating and complex and everything inside them is so fragile and unintuitive, etc etc etc. But now that I’ve been forced by providence to get comfortable messing around with control boards and wires, i have to accept that perhaps learning this stuff really isn’t impossible for a humanities major with no CS/tech experience to do. Maybe I can fix more shit going forward, instead of just replacing it, you know?!
Altogether 10/10 time absolutely not wasted.
75 notes
·
View notes
Text
Guess who is about to cry because she can't configure the printer because it doesn't seem to turn on or off? (When will this constant feeling of being usless end?)
#just girly things#i'm so good at crying#i'm not having a good time#fuck the fucking printer#why?!#I'm hidding from my parents while listen to drunk-dazed with Ariana Grande music video in the background#i feel useless
6 notes
·
View notes
Text
A lot of people really liked seeing the outside of the Philips Intellivue MP5, so let’s take a look on the inside

When you take off the back housing this is what you’re greeted with. We can see the power supply, the rear IO board, and the measurement module

After removing a few more T-10 screws the power supply and the rear IO board slide right out. This is the rear IO board
1: USB port
2: Nurse call relay output
3: RJ45 Ethernet Jack
4: VGA video out
5: board to board interconnect for the power supply
6: Nurse call Relay, the actual Relay component
7: Battery contacts
8: An RJ45 Jack not accessible from the outside, if I had to guess this is either a management port, or it’s a backup port in case the one accessible from the outside breaks but qualified technicians still need Ethernet access to perform maintenance.
9: Piezoelectric buzzer, this will beep is the power supply suddenly gets disconnected and it will continue to beep for quite a while after the power supply is disconnected and even if there’s no battery on board
10: 2 super capacitors. Super capacitors have specs that are somewhere in between a battery and a capacitor. The larger one is rated at 2.2 farad and the smaller one is rated at 1 farad. Farad is the unit of measure for capacitance and it’s named after Michael Faraday. If I had to guess these serve 2 purposes. 1 is to make the power loss buzzer beep and the other is to keep the date and time and any configuration settings stored in volatile memory since there’s no CMOS battery. This is actually pretty smart because batteries die and often leak, but super capacitors don’t leak and corrode and they are ridiculously fast at charging up.

After removing the power supply, recorder driver board, and rear IO board this is what we are left with. The motherboard, the measurement module, the NBP pneumatic pump, and the LCD high voltage backlight board. It uses a fluorescent backlight so it needs a high voltage to make it light up, this can be anywhere from 500 to 1200 volts but they often provide very little current so touching it probably kill you but I still wouldn’t recommend it.
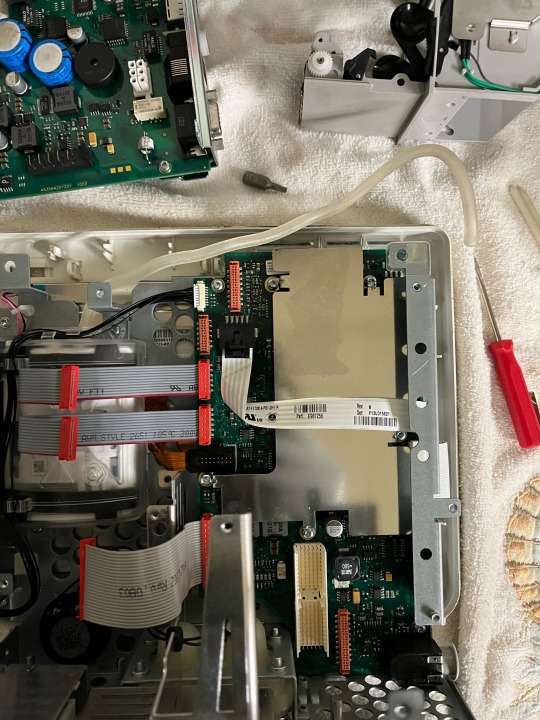
After removing the measurement module were left with just the backlight driver board, the motherboard, and the NBP pneumatic pump. There is a metal shield over the main components of the motherboard for EMI shielding.

Removing the metal shield grants us access to the CPU (the largest chip on the board) what I assume is a graphics driver chip (the second largest square chip) and 2 EPROMs that are the memory for some software aspects.

Once everything is out we can get a look at everything
1: Battery
2: measurement module side plate
3: measurement module
4: printer
5: Rear IO board
6: printer driver board
7: power supply
8: everything else

The attention to detail is amazing! That one little hole in the plastic just exists to access that screw inside. You can certainly tell that this device was never meant to be a consumer device. It’s built to be taken apart and serviced. All the screws are identical which makes disassembly and reassembly very easy. Unlike consumer products you can definitely tell that there was no expense spared in this things hardware design, that’s due to the fact that they know hospitals are going to pay the 5 figure price of the device because of its extreme quality, attention to detail and very long projected life cycle. Unlike consumer electronics it’s made in Germany and has a ton of hand assembly involved.

This is everything I have for mine. The monitor itself. 3 lead ECG cable. 5 lead ECG cable. Pulse oximeter. Hospital grade IEC power cable. Blood pressure hose. Adult arm blood pressure cuff. And the Intellivue remote. I got the remote today, idk why but people are selling them for super cheap on eBay. I paid $10 for it brand new in box. They usually go for like $500 from philips directly so I have no idea why people are selling them for so cheap. It does have to be plugged in via USB but it comes with a very long cable.
I finally got around to getting one of my servers to run the Intellivue XDS application. It’s a windows application meant to act as the server for Intellivue monitors. It also has a remote monitor function so you can view what’s on the monitor on the server, but it doesn’t work with the software version my monitor has. It can also log data but I spent 4 hours trying to setup the windows server needed to get that to work and just couldn’t get it to work. It’s probably due to the fact that the documentation on it is absolutely terrible.
4 notes
·
View notes
Text
Bro I have another Capril concept
You know that lab you did in high school where you have drip a chemical into another chemical and make the lightest pink you can?
Now imagine, Sunita moves back to the hidden city because going to a human school as a yokai is too risky. So April is lab partnerless again.
But literally as soon as Sunita leaves, they get another student in class.
Foot Recruit.
The teacher introduces her as Cassandra Jones and, to both of their dismay, is automatically paired with April.
And first day they’re doing the lab mentioned above and they have 3 tries to make the lightest pink. At first Casey is the one dripping and April is the one stirring. Casey is far too impatient and pours too much too fast and they end up with a dark purple. They both get frustrated with each other, but they both separate decide to get it over with and then never speak of it again.
That is until the teacher holds up a beaker. Not just any beaker. The Purple Dragons’ beaker. The teacher compliments their work and tells the class that this is their ideal result.
April, having a grudge for messing with her little brother, immediately wants to out do them.
And Casey is nothing but competitive.
So, they silently form a truce, to out science the science nerds.
April takes over the flow of the chemical and Casey takes over stirring. They are so concentrated and naturally communicate very well. And then the think they got it, but then they hold it up to the light and…
It’s darker than they thought.
It was something with the lighting and the darker counter top. So together they configure a set up with a piece of printer paper and the flashlight from April’s phone. They are dead set on this experiment that they forget why they were so determined to begin with.
For their last try, they got it so light that you wouldn’t notice the pink unless it was pointed out.
The teacher comes around and praises them for their work and problem solving. And for a moment, they forget they were enemies and celebrate their accomplishment. They high five and even hug, before pulling away with a blush.
And from then on. There was an unspoken truce between them in school. And they form double lives.
I have to write more of this I’m actually obsessed. I’m good at this shit.
#rottmnt#rise of the tmnt#rise of the teenage mutant ninja turtles#cassandra jones#save rottmnt#unpause rottmnt#casey jones#april o'neil#rise casey jones#rise cassandra#capril#rise april#rise capril#tmnt fandom#rise casey#batsticks#lesbian#rottmnt casey jones#rottmnt cassandra jones#rottmnt season 3
20 notes
·
View notes
Text
Ordered a new main board for the 3D printer. I decided to go with the BIGTREETECH SKR Mini E3 V2.0 over the Creality V4.2.7 since I'd eventually like to get an automatic bed leveling upgrade and the SKR Mini has more customizability than the V4.2.7, such as better dual Z-axis support out of the box. The Creality board also has some negative reviews about how difficult it is adjusting power output (which I'll need to do for the dual Z-axis) and that Creality itself made it impossible to change specific parameters, for some reason.
I'll have to configure the firmware of the Mini myself though, which sounds kind of tricky, but if thousands of other people have figured it out then it can't be that hard. The documentation for this thing is wonderful.
The new board should be here on Friday. Very excited. This was the last upgrade I wanted to get before printing 1:1 scale Outrage parts. After installing the new board, reinstalling the second Z-axis, and recalibrating everything, it should print like butter. I'd be surprised if I didn't have at least 1:1 scale part printed by the end of April.
The first piece will probably be part 16, which is the smallest. I think my first estimate put its total print time at about 13 hours, but I've changed some settings since that estimate. It might take 14 or 15 now. Part 16 is the pommel half of the handle:
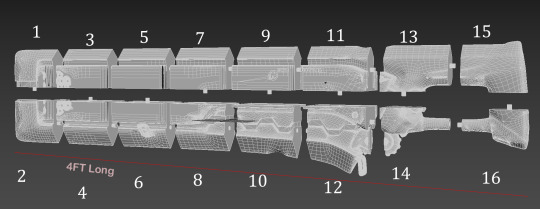
16 will be the first because if it prints bad (or fails) it won't be as big a waste of filament. Part 12 will be the last one; the estimate for it was at least 24 hours.
#textpost#3d printing tag#Ngl I think I've become a little unhinged for this project lol#It went from 'haha wouldn't it be cool printing a full scale Outrage'#To 'I am as one with my machine as it is with me. A 3D render of the Outrage in 8k resolution is downloaded into my brain'#I have... gone over budget with this thing.... Don't want to talk about it....
13 notes
·
View notes
Text
is there anything more annoying or soul crushing as configuring a printer
3 notes
·
View notes
Text
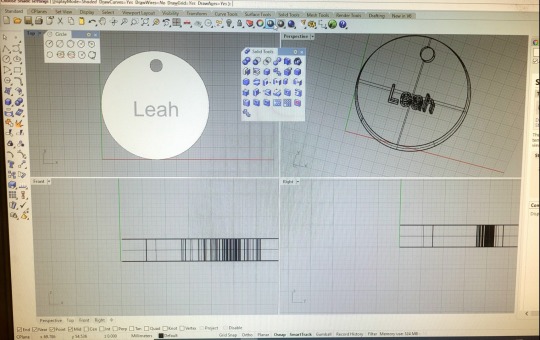


3D Printing Workshop
We used a software called Rhino6 to create a digital model of a keyring. Then I moved the digital model to another software to configure the sizing details, and made sure it would print out correctly onto the 3d printing plate.
I learned how to transfer the information from the computer to the 3D printer using an SD card, then learned how to use the printer and how to set it up.
About an hour or two later, my keyring was printed!
4 notes
·
View notes
Note
i have access to my printer again so i'll be testing out the v3 finger print today! i'll update you with how it goes :] tysm for putting these prints out!
I hope it works out. I printed one and it was okay, but the thumb may be too small (height wise. Width is unchanged). Something got messed up in the configurations when I revised the hinge.
I'll fix this hopefully today, but printing at 105% size might be best for F1 if it doesn't fit you as is.
2 notes
·
View notes