#how to prevent spyware
Text
Spying is not only a job for top-class secret agents. We all have faced some situations in our life when we need to spy on our family members. In fact, there is no harm in spying phone calls.
Sometimes you need to know what’s going on in with your family members. Some might think it is an illegal process, but oh boy, wait! There’s no harm in spying inside the house.
This guide will help concerned parents who want to know what their kids are doing when they’re not there. So, let’s talk about how to spy on someone in your house or in another room.
1 note
·
View note
Text
How to Kill Microsoft's AI "Helper" Copilot WITHOUT Screwing With Your Registry!
Hey guys, so as I'm sure a lot of us are aware, Microsoft pulled some dickery recently and forced some Abominable Intelligence onto our devices in the form of its "helper" program, Copilot. Something none of us wanted or asked for but Microsoft is gonna do anyways because I'm pretty sure someone there gets off on this.
Unfortunately, Microsoft offered no ways to opt out of the little bastard or turn it off (unless you're in the EU where EU Privacy Laws force them to do so.) For those of us in the United Corporations of America, we're stuck... or are we?
Today while perusing Bluesky, one of the many Twitter-likes that appeared after Musk began burning Twitter to the ground so he could dance in the ashes, I came across this post from a gentleman called Nash:
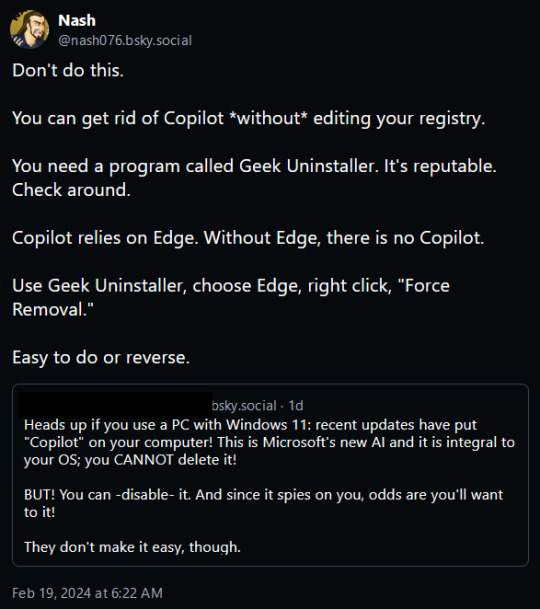
Intrigued, I decided to give this a go, and lo and behold it worked exactly as described!
We can't remove Copilot, Microsoft made sure that was riveted and soldered into place... but we can cripple it!
Simply put, Microsoft Edge. Normally Windows will prevent you from uninstalling Edge using the Add/Remove Programs function saying that it needs Edge to operate properly (it doesn't, its lying) but Geek Uninstaller overrules that and rips the sucker out regardless of what it says!
I uninstalled Edge using it, rebooted my PC, and lo and behold Copilot was sitting in the corner with blank eyes and drool running down it's cheeks, still there but dead to the world!
Now do bear in mind this will have a little knock on effect. Widgets also rely on Edge, so those will stop functioning as well.
Before:
After:

But I can still check the news and weather using an internet browser so its a small price to pay to be rid of Microsoft's spyware-masquerading-as-a-helper Copilot.
But yes, this is the link for Geek Uninstaller:
Run it, select "Force Uninstall" For anything that says "Edge," reboot your PC, and enjoy having a copy of Windows without Microsoft's intrusive trash! :D
UPDATE: I saw this on someone's tags and I felt I should say this as I work remotely too. If you have a computer you use for work, absolutely 100% make sure you consult with your management and/or your IT team BEFORE you do this. If they say don't do it, there's likely a reason.
1K notes
·
View notes
Text
How to Recognize and Prevent Spyware Activity on a Smartphone
How to Recognize and Prevent Spyware Activity on a Smartphone
How to Recognize and Prevent Spyware Activity on a Smartphone
This year, illegal Android spyware was discovered in the Google Play store.
For four years, it was hidden in a seemingly legitimate program and spied on the thousands of people who downloaded it.
Gather information about whether the target is wealthy enough to commit a robbery.
Friends, if you are wondering, how do you know if…

View On WordPress
#How to Prevent Spyware Activity on a Smartphone#How to Recognize Spyware Activity on a Smartphone#if someone is tracking your phone#Spyware Activity on a Smartphone
0 notes
Text
Spy x Family: Sunshine Smile

(very short story); added picture for visual
•▪︎•▪︎•☆
Loid kept pacing around with his fingers pinching the space between his nose and temple.
"What the heck Twilight! Would it hurt you to take a seat for once instead of circling around?!" Franky said in a burst, annoyed with Loid's footsteps.
"Fine. Satisfied?" Loid replied as he settled down the sofa.
There's only a week left before the "anniversary". It's been a year since he "married" Yor and built his fake family. His mission regarding Desmond and the cold war proved to be slower than he expected. They're all still here. The Forger family is yet to be abolished.
"Just what is it you're being problematic about that you can't even stay in one place?" Franky inquired.
"My fake wedding anniversary with Yor is next week. I have to make some sort of public show to prevent our neighbors from suspecting us." Loid answered after a sigh.
"What? Just that? As if that's ever a problem with a deception master like you."
"I guess things will simply go smoothly with usual planning. It's just that..."
"Just what?"
"It should not only make an impact to the people around us but also to Yor. It should suit her taste..." Loid continued as he looked at the ceiling.
"You're minding her too much."
Loid jerked his head back. He was taken aback by Franky's words. Although not facing him, Loid could feel Franky's suspecting stare. As much as he wanted to talk back, he couldn't figure out his own reason.
Meeting and "marrying" Yor seems like fate. Though no way he would directly express how much Yor meant for his mission, he wanted to fairly compensate her. Perhaps he's being too much? Was he making Yor uncomfortable but failed to notice? Loid's mind was suddenly in a panic. He tried to justify in thought everything he's done until now.
After a short awkward silence, Franky spoke once again.
"It's only for appearances sake. I'm pretty sure your wife will be pleased with anything. So why the-"
Franky was suddenly cut off when they heard happy laughter coming in. Yor and Anya just arrived after walking Bond.
"Scruffy!" Anya cheered upon seeing Franky.
"Yes, young miss! It's me! Look what I got you this time!"
Franky got up from his seat and took out some ambiguous toy device that he came up with again. Loid watched as Franky and Anya get loud with their own fun. He almost zoned out if not for Bond and Yor coming to his view.
"Loid?"
"Oh! Y-Yor? Welcome back. How's your walk?" Loid responded, focusing on Yor.
"It was nice. Bond and Anya played fetch the whole time. By the way, I bought us some tart."
"Thanks. Shall we set the table?"
"Yes."
During dinner, Loid was noticeably more silent. Anya, who had been rambling with Franky about Spywars, picked up Loid's troubled thoughts.
"Papa," Anya started.
"Hm?"
"I will..."
"You'll what?"
"I'll watch Berlint In Love tonight and "learn" like Becky."
Loid blinked at her, barely digesting both his food and Anya's words.
"Ah... Okay. Good luck with that?" He only managed to reply.
Franky immediately left after dinner. Anya who was surprisingly tired, didn't bother to wait for the tv drama and headed off to bed. Yor did likewise after doing the dishes. With Loid being the only one left up, he seated himself. He is nowhere near getting asleep and decided to turn on the tv for the late night news.
"Might as well..." He mumbled while drying his hair with a towel.
But instead of news, what greeted him was a cheesy romantic music. Berlint In Love is still on.
Good thing Anya missed this. It's way late in the evening and nothing good for her to see. Loid thought.
He was about to turn it off and give sleep a try but something fascinating caught his attention.
"...Dear! I don't need all the luxury of the world! I don't care about the surprise. I just want you by my side." The lady on screen said in so sweet a tone that Loid imagined a certain person saying the same words to him.
"Oh, but honey! I only want to make you happy!" A guy in a simple working suit replied with the same intensity.
The lady's wardrobe doesn't scream extravagance but dressed enough to be distinguished as part of higher society. Bursting into tears, she threw her arms to her lover.
"Please trust me when I say so. You're all that I need! Whatever you do for me, I am happy. That's for sure..."
Finally the two blissfully walked by the shore, hand in hand while basking in the fading twilight. The dramatic scene kept playing on Twilight's mind over and over again that he couldn't focus on the news afterwards. Finding it unproductive, Loid turned off the tv and went off to sleep. As the scene repeats itself on Loid's mind, Franky's words echoed.
"You're minding her too much."
•▪︎•▪︎•☆
Days have passed and Loid still struggled with a main plan he can stick with. In observation, he noticed that lately his neighbors have been going home from their respective walks between 5 and 7 pm. And so he's been considering to leave within the timeframe so as to deliberately run into them and portray that he and Yor are one adorable couple.
Amusement park? No. Given Yor's schedule, she'll already be tired from work. Eat out? Seems fine but she might be bored with it already. Lake cruise? But the travel time doesn't make it worthy. Opera? Gallery? Ugh! I can't even settle with at least three options! Loid's brain was about to go busted. He's not usually like this. In frustration, he finished his remaining crepe with a bite and threw the trash in the bin. He felt Yor's gaze.
The eyes that are always brightened by radiant spirits met Loid's. Yor smiles and Loid smiles back, a reflex that Loid gradually enjoyed.
"The crepes were good, right? It was greatly recommended by my coworkers."
"Yes."
"We should take Anya next time. She'll like it."
"Yes, sure." Loid responded with a smile.
He watched as Yor turned away and started fixing her scarf. He thought how unusual their "dates" have been. Things usually don't go the way he expect like when Yor settles in a weird mood, Yor drinking way too much, Yor having to leave early due to work-related emergency, Yuri suddenly visiting, and so on.
Looking back from the start, he's grateful that Yor is still with his family, with him. Grateful with everything she did and wondered how she was able to put up with him. Would it have been different with another? He didn't bother pondering on it further. He only knew one thing. It can only be her.
Franky's words resurfaced again. Loid didn't know what to feel. Lately he's been unsure of his attitude towards his "wife". All along, he thinks that he did everything like he used to with his past fake romances. But no. He's very wrong.
Yor must have felt the stare and turned around.
"Let's go home." She said.
It was as if time stopped. Suddenly, myriad of memories flashed through Loid's mind. Realization hit him hard.
Oh... I'm in love with Yor. For real.
•▪︎•▪︎•☆
My contribution for LoiYor valentine 💕
31 notes
·
View notes
Text
for the @lamenweek Day 6 prompt: Future
Laurent is a lighthouse keeper. In vernacular language, anyway. Formally, his job title is Stellar Monitoring Station Commander, Class Nine, Category 27C, Deep Space Research Division. But he likes the informal title better, with its connection to the distant past. He likes to imagine himself part of an ancient line of watchers in lonely outposts, connected to the people who long ago tended a light to warn ships away from rocks.
Laurent’s job is not so different. He keeps watch over Kathelin A and Kathelin B, a pair of binary stars locked in orbit’s doomed embrace. Kathelin A is a red giant. Kathelin B, its once-larger twin, has aged faster and is already a white dwarf. As they orbit, the edges of the red giant come close enough to the white dwarf for Kathelin B to steal flares of matter from Kathelin A, growing a little bigger with each revol.
This prevents several dangers for interstellar travelers. First, the flares wreck havoc on the atmospheres of both stars. The changes in their magnetic fields and cosmic radiation can cause serious damage to ships’ navigation systems, communications, and engines, so Laurent maintains a constant broadcast of current conditions. Second, on occasion—occasions, in this case, coming about once a decade apart—the heat of the white dwarf will reignite the matter it steals from Kathelin A’s atmosphere and its own atmosphere will explode in a nova. Laurent’s station is built to withstand that, but most ships are not, and so it is his job to broadcast an emergency warning to ships to stay clear. The rate at which Kathelin B gathers mass is unpredictable, and thus so are the explosions.
Third, in perhaps a thousand years, perhaps a few months, Kathelin B will gain enough mass from Kathelin A to reach the mass threshold to supernova. The station is equipped with pulse—faster-than-light—communications, but not a pulse ship. And so then Laurent, or whoever has taken his place, will have time to send out one last, more dire warning before becoming just a few more thousand moles of atoms carried across space by the supernova.
It isn’t what Laurent would have chosen for a job, given the opportunity. But in the end, his uncle had succeeded in manipulating the court such that Laurent had no choice but to join the military or lose what shreds of a good name he had left. He’d expected a posting on the front lines of the border with the Akielon empire, somewhere volatile where no one would suspect anything if Laurent’s ship met a sudden and violent end. Instead, it’s this quiet and loneliness out in the depths of space.
He can see his uncle’s reasoning, he supposes. On the front, there was a chance, no matter how remote, that if Laurent survived he might manage to do something heroic. Out here, there is nothing but tedious, necessary work. “This will be an extremely valuable experience for you, nephew,” his uncle had said when announcing his assignment. “Whenever you have seen fit to devote yourself to any real efforts here, it has been in service of your own amusement or vanity. On the monitoring station, you will learn the value of dedication, of hard work for its own sake.”
As if Laurent’s whole life hadn’t been hard, relentless work with little hope of recognition or payoff.
It’s a smart move on his uncle’s part. It’s more than smart. As much as Laurent hates to admit it, it’s probably checkmate. If Laurent couldn’t build a coalition powerful enough to meaningfully oppose his uncle from the heart of Arles, what chance does he have out here alone?
Still, though. Much as he hates to admit it, he has found that life as a lighthouse keeper suits him well. He likes the solitude. He likes the freedom from the court’s constant scrutiny he enjoys once he manages to build blindspots and loops into all the spyware on the station. He likes the challenge of upgrading the station’s equipment and preparing for potential breakages with only the limited supplies available to him. And part of his job, officially, is research: observing and cataloging changes in the two Kathelins, analyzing them to add to Vere's understanding of stellar physics in late life cycle stars. Laurent’s monitoring duties take up very little of his time—the station can essentially run itself, and its human keeper is mostly there to address any truly unexpected problems—so he’s free to devote as much time to reading or to studying the Kathelins as he’d like.
But those unexpected problems do occur, from time to time. None in Laurent’s time, yet, but over a hundred have been reported in this class of station since they were first deployed thirty years ago. If there is equipment failure the station does not know how to repair or compensate for on its own, it is far better to have a human stationed on hand to fix the damage, rather than a team operating the station remotely. Even with fast-than-light communication, the station is generally far enough away from anyone else that each signal pulse would take hours to reach its destination.
Which is why the advice from the castaway Akielon now trapped with him on the station rankles so badly. Even if Laurent wanted to throw away his life and what remains of his hopes for a better future to ferry the man back to Akielon space, he can’t in good conscience abandon the lighthouse.
The Akielon castaway had been the first real change in the years Laurent’s been at the station. Laurent had found him drifting through space, his ship crumbling around him. Saving him hadn’t been an altruistic act, Laurent tells himself. Cataloging space debris is part of his job. He’d been no small amount surprised to find that the ship’s pilot was still alive.
And now here he is, alive and stubborn and messing with the predictable quiet of Laurent’s life. Laurent has developed a routine, these years alone on the station. He has a work schedule, a maintenance schedule, little habits he does at mealtimes or before sleep or upon waking. Nothing individually important, but they have taken on an air of ritual through repetition. And now the Akielon castaway is there, wanting to cook the same meal several days in a row, or changing the living space’s temperature settings, or sitting by Laurent’s console and asking him questions. One day the Akielon castaway had disappeared for hours, and Laurent had begun to worry he’d somehow wandered into the areas of the station without life support when he’d found him instead napping amidst the trees and grasses in the station’s oxygen farm.
Laurent would be thrilled if there were some way of returning the Akielon castaway back to Akielon space. But even were he willing to part with his only ship to help the man, Laurent’s ship is a sublight orbital cruiser meant only for traveling to the various probes the station controls in the Kathelin system. It would never survive a journey through deep space, and without a pulse engine the Akielon would be long dead of old age before he reached anywhere worth going anyway.
* * *
The lighthouse keeper is driving Damen out of his mind.
The man is always on guard. He flinches at an unexpected word, the sudden sound of footsteps. One time Damen had tapped him on the shoulder and the lighthouse keeper—Laurent—had whipped around and held the wrench he’d been using on the vents to Damen’s throat as if it were a knife. Perfectly innocent questions, like “Where are you from?” or “Why did you become a lighthouse keeper?” are met with hostile silence. Damen would take a hint, would mind his own business, but they’ve been stuck with each other for weeks now and they’ve got to have some conversation.
Or maybe Laurent would prefer to spend every meal sitting in silence. That would be in keeping with the rest of his behavior. Certainly the man has a seemingly-endless list of bizarre and arbitrary rules. There are plates that are used when serving one sort of rations, but not another. Laurent likes to sit facing the mess hall windows at breakfast, but away from them at dinner. Damen does a million little things wrong every day, and he can see Laurent stiffening his shoulders in repressed irritation each time, often before Damen is even aware of having made a choice it would be possible to get wrong in the first place.
He should be more understanding, he tells himself. Laurent has saved his life, and everyone knows lighthouse keepers get weird after all the years alone in deep space. But it is excruciating to spend each day trying to fit his life into the precise and nonsensical constraints of a routine no one has ever explained to him. Waking up in the station’s infirmary and seeing Laurent’s face the first time, it had seemed like he’d been rescued by an angel. Now, after many weeks spent in the man’s company, he cannot help but think of Laurent as essentially his captor.
In fairness, Damen supposes, he isn’t much used to having to live by anyone else’s rules. As crown prince of the Akielon empire, it had been a long time since anyone had told him what to do. He had been authority incarnate, used to a staff trained to indulge his every whim.
That existence feels far away here. Perhaps that’s why it’s easy not to dwell on how it ended, what set him adrift in space in a dying ship to wash up here. Betrayal by his own brother, by the woman he had hoped to marry. Kastor had wanted to kill Damen for the throne. Jokaste had convinced Kastor to make it slow, to abandon Damen in space with no working engines and barely any water or air.
He will deal with him when he returns home. First he must find a way off this station. And if the lighthouse keeper is determined not to be helpful, he will find another way. The station has pulse communications. He just needs a chance to use them when Laurent won’t be around to catch him.
It's not a betrayal, he tells himself. It's not like he and Laurent are friends.
And a few days later, when Laurent is on the surface of the ship running inspections and maintenance on the solar panels, he gets his chance.
#captive prince#Lamen Week 2022#Lamen Week#all of the astrophysics in this is correct to be best of my ability#my post
64 notes
·
View notes
Text
RE: GSHADE MALWARE DISCOURSE
They locked the channels down, but I managed to grab some screenshots of the conversation shown in the crucially lacking in context Twitter screens. I'll share the screens in a reblog because Tumblr keeps breaking when I add them.
So, we all hate art theft, right? We hate when people use our or others' hard work even in bits and pieces (like AI art training) without any credit to us or the artists? We hate when people say "it's online so NYEH" when an artist asks people to respect their work, right? Okay, good.
Gshade is an "improved" version of the Reshade overlay program that makes it super easy to adjust, make, and switch between presets in the game, as well as simplifies the installation process, and adds a few extra features.
However, there was some Twitter outcry about a week ago due to how updates work in Gshade (which was, admittedly, annoying). Another dev decided to break GShade's EULA regarding assets usage because they didn't like some of Gshades functions like the updates.
In my own, personal opinion, both parties aren't great people. If you read the other person's blog post on all this, it's riddled with cockiness and your garden variety internet kid arrogance and seems to boil down to "I don't like Gshade, it sucks, I can do better." They link an archived Twitter where a popular preset creator politely asks for their presets to not be used for this project, they push back against this creator's request, the creator makes a vague and innacurate legal reference in an attempt to try and convince this dev "hey, I said don't use my stuff".
The dev mocks this person in their blog post claiming that they're allowed to use the presets because they're in a GitHub repository.
In order to prevent plagiarism of any of Gshade's assets (INCLUDING the presets themselves), the dev added a "killswitch" essentially that, when any attempts were made to access Gshade, its installer, presets, etc without the dev or preshade creators' knowledge or permission, would cause a force-restart. For anyone who doesn't really use Gshade- I feel the need to add that some presets use original art assets and overlays so it isn't just people playing around with sliders. This is actual art that some artists have politely requested doesn't get re-used elsewhere without permission.
And no- this isn't like major game companies like Ubisoft implementing DRM, which in context is about big rich corporations trying to prevent piracy. This is like online game anti-cheat software except instead of bans you get a restart.
You cannot trigger this force-restart with Gshade on normal use, it will ONLY happen when trying to run something that accesses and utilizes Gshade or its assets (again, including people's presets). Likewise, from the sounds of it, the killswitch was already regretted and removed in a patch on Saturday- two days before this whole thing blew up today- and it was changed to a line of code that just closes the program.
There is nothing within Gshade which will harm or remain on your computer. There are no keyloggers, other spyware, covert mining, or anything else that remains on someone's computer with the express purpose of doing harm to it. While you can argue semantics here, imo "Program does bad thing if you go out of your way to use it improperly" isn't "malware" or else World of Warcraft and any other online game with an anti-cheat could also be considered Malware.
If you don't want to use Gshade because of the moral implications of the dev taking such a grandiose measures, that's a personal choice. It's 100% understandable to see this as a breech of trust-
-but please stop spreading word that the app intentionally has Malware intended to affect the common user. This was literally an anti-theft measure taken way overboard.
To summarize:
-Cocky dev personally dislikes some of Gshade's functions and wants to make their own version of it, but use Gshade assets including presets (some of which contain original art) they don't have permission to use using the same busted "well it's on the internet" logic people use to justify art theft and plagiarism.
-Gshade devs try to stop this, other dev self-admittedly "trolls" them for a while and ignores preset artists saying "hey I don't consent to using my stuff".
-Gshade dev includes a line of code to force-restart the PC of anyone who tries to access any Gshade assets, specifically to fight back against this user. Regrets it and removes it.
-Two days after its removal, word gets out that Gshade has this force-restart command.
-Gshade dev admits in the Discord that yes, this command was in there briefly. A single screenshot of this admission makes it to Twitter, and the entire program is branded as Malware.
I'll repeat again, neither side was perfect in this, and to add such a harsh command line even if it was targeted at one person in particular was a gross misuse of power. It's perfectly understandable to not want to use Gshade anymore if you don't trust the program, but it's also important to release this overstep wasn't made purely in impulse, and was an attempt to stop someone who was actively trying to disrespect artists and preset designers. I think that's the huge part of all this that's being missed and it's resulting in a lot of people zero'ing in on the Gshade dev and Discord mods as if they're the defacto villains in all this and need to be harassed and ousted from the community.
7 notes
·
View notes
Text
How Can You Confirmed With 꽁머니 즉시 지급?

A toto site is a safe playground that allows you to place your bets without any fears. Its eat and run verification software uses 14 high-end methods to ensure reliability and quality. It will also protect you from fraudulent activities. A toto site is a great option for beginners who are new to online gambling. It provides a low stakes environment for practice and round-the-clock customer support. The toto site chat room is available twenty-four hours a day. This allows you to chat with other players and make new friends. You can play games together or ask questions about the latest games. There are also forums where you can discuss the latest game updates. In addition, you can use telegram to contact customer support.
Another security measure on toto sites is the oppous for play game feature. This will prevent unauthorized users from using your account to access your personal information or financial details. This feature will also allow you to control who can access your account. It will also block certain types of malware and spyware on your computer. The toto website is a good resource for finding information about different online casinos and gambling platforms. It also provides helpful tips and strategies for maximizing your winnings.
Private toto sites and casinos are a great way to keep your personal information safe and your 꽁머니 즉시 지급 anonymous. They are usually much safer than traditional online casinos and offer more security features than ever before. They are also easier to use, and they typically have better customer service teams. The toto site has a wide variety of games for its members to enjoy. In addition to its many games, the site offers a chat room where you can chat with other players and make new friends. The toto site is free to join, and there are no time limits or restrictions on how long you can play.
Toto sites also prioritize user safety by requiring their operators to verify the identity of their customers. This verification process is designed to ensure that only genuine individuals participate in the betting ecosystem. In addition, major toto sites are registered with recognized gambling authorities and have secure registration information in the footer of their websites.
youtube
In addition to ensuring the safety of its customers, toto sites promote fairness and transparency. They encourage their operators to abide by local laws and Company regulations regarding the protection of personal information. They also strive to develop sensible business activities that are socially acceptable and sustain sound normal relationships with political organizations and governmental administrations. In this way, they aim to achieve a win-win situation for both customers and their business partners. The toto site will not tolerate any illegal or unethical behavior by its operators. Its employees must abide by the laws and societal rules of their country and region, as well as the international norms that apply to their work. In doing so, they can contribute to the prosperity and welfare of the community.
2 notes
·
View notes
Text
yknow, i know we're literally all giving that metaverse shit absolutely zero press whatsoever on purpose both because none of us can stand the idea of giving zucc money to play it, AND because of the fact that it (hehe) zuccs in general as a whole both as a design concept and as a game. like its not fun even in concept really. but look i just NEED to give it shit for this one thing. i have to
look. in the history of vr techs development, as much as a layman as even i am (as someone who can not own a vr headset under any circumstances due to personal reasons i dont have to get into, its like 3-4 major reasons minimum). i understand that the vr history "basically" begins with the nintendo virtualboy, which was a commercial failure because Something About It gave people severe and unmanageable motion sickness. and then, even in spaces where people WANTED vr games to be a reality, it took a REALLY long time to get a game out that was good to play and felt good on the eyes for more than an hour on the average non-chronic sufferer of migraines or photosensitivity. like, in order for the games to reach the level of "playable, easy on the eyes, extremely unlikely to make you violently motion sick, and not unbearable for photosensitive chronic migraine sufferers", it took YEARS of trial and error from my perspective
first step rules of all vr games:
do not make "falling"/"spiderman" areas where the player, while standing completely still, has to fall/swing in mid air
do not make inputs too specific/precise, a small button should be achievable with shaky hands and uncalibrated controllers, though buttons shouldnt be small anyway
boring, jarring, or impossible physical movement is extremely hard to watch, it should be synced to irl movement as closely as possible and finger motion if available should be dynamic and easy to understand and intuitively use
metaverse, i cannot stress this enough, breaks literally all of those main basic rules to prevent motion sickness, eye fatigue, and has the fucking audacity to not even be fun while doing it. its PAINFULLY cheap looking, with next to no animations for officially licensed "minigames" (white arial font text "you have been hit!" and such with a bland red overlay in one, literal spiderman swing-between-buildings-over-empty-void-level-while-irl-standing-normally in another). like... theres a REASON these basic vr design rules exist and why breaking them is a bad idea. metaverse spits in the face of basic design and function research. its like they almost dont expect real people of varying visual and sensory ability to see to play the game, and i dont mean "autistic vs allistic people", i mean just straight up people who dont perceive color or light intensity the same way as other people. which is everyone, because varying sensitivity is a part of natural variation in people. vr chat has achieved this. BEAT SABER managed to achieve this while having a huge part of their gimmick break the vr rules of "things that are flashing lights fly at you very quickly", and they manage it in STYLE. tons of vr games work in spite of the inherent struggle in vr of making a game that isnt sickening to play and use. and you'd THINK a company as spyware-heavy as facebook would be able to come up with something a basic human person could play without being bored or sick, and yet... they cant even manage legs. they cant even manage not LYING about having legs. and its so useless and stupid and deserves everyone ignoring it and not bothering to even try it out of hatred.
you have to pay for applause points that might win you an irl shirt if you're top 5, and the shirt isnt even good. literally pay to win social interactions in a game that is so painfully boring and cheap you cant even imagine where 90% of the money could have gone. i dont genuinely think i could have... even FOUND A WAY to spend so much money on things like drugs and gambling in the dev time this game has taken that could account for how much money just simply could not have gone into actual development. i literally cant imagine how they could have done this. indie one person passion projects can create a better tech demo than this entire game manages to be for like... what? $15 billion? it makes me sick thinking about how much money was sunk into this and it still somehow has microtransactions. it feels insulting and flaunting. i hope mark zuckerberg reads this and feels a little worse about the whole thing than he already does. i really hope he feels bad and useless and hopeless.
8 notes
·
View notes
Text
__digital empowerment__
Q1 a) THREE SECURITY TOOLS
1.FIREWALL
The most important security tools.
Its job is to prevent unauthorized access to or from a private network.
All messages are entering or leaving the intranet pass through the firewall. The firewall examines each message and blocks those messages that do not meet security check.
The Firewall is very useful, but it has limitations also.
A skilled hacker knew how to create data and programs that are believing like trusted firewalls.it means they can pass through without any problem
2. Antivirus Software
Antivirus software is a program which is designed to prevent, detect, and remove viruses and other malware attacks on the individual computer, networks, and IT systems.
Tt also protects our computers and networks from the variety of threats and viruses such as Trojan horses, worms, browser hijackers, spyware,ransomware.
Most antivirus program comes with an auto-update feature and enabling the system to check for new viruses and threats regularly.
3. Data Encryption
Data encryption is very important when you have top secret files that you don’t want to be read even if they are stolen
Encrypted communication protocols provide a solution to this lack of privacy.
The encrypted web access provided for customer security is used by attackers because it is difficult to monitor.
Q1 b) DIFFERENCE B/W PRIVACY AND SECURITY
PRIVACY
Privacy defines the ability to secure personally identifiable data.
Privacy can't be adept without security.
Privacy defines protecting sensitive information associated to individuals and organizations.
Privacy programs concentrate on protection personal information just like passwords, log-in credentials, etc.
SECURITY
Security define protecting against unauthorized access.
Security can be adept without privacy.
Security supports protection for some types of data and information such as the ones that are saved electronically.
The security programs defines the set of regulations and protocols to secure each confidential information.
2 notes
·
View notes
Text
How can you safeguard your MetaMaskextension?
In this digital world, the crypto industry is growing enormously all because people are favouring investments in cryptocurrencies. It stems from the fact that crypto traders are making huge profits out of it.
If you are a regular trader you might have heard about MetaMask- a wallet to store Ethereum and ETH-based tokens.
Well, there is no doubt that MetaMask strives to provide the best security measures, but where security features are getting advanced day by day, malicious activities such as online theft, and cyber-attacks are also climbing the charts. These activities may happen seldom but storing your funds online always involves risks.
Considering this fact, we are here with some helpful tips to provide an extra layer of security to the MetaMask extension. So, if you are also bothered about the security of your assets dumped in MetaMask, come along with me to get yourself out of worry.
A few tips to protect your MetaMask wallet
Use personal, not public computers- Always try to use a private device to access your MetaMask chrome extension.
Keep seed phrase safe- Seed phrase which is also known as the secret recovery phrase is used to recover your account. So, jot it down in any secure document and never share it with anyone no matter how close they are.
Secure your device from malware and viruses- Always keep any antivirus running on your device to secure it from any spyware and remember to update it on time.
Clean up all the cookies- Cookies are electronic traces of your online activities. Before and after using MetaMask on your browser, clear the cookies frequently.
Turn off the extension- Like many other browser extensions, MetaMask needs a certain set of permissions to operate. Turning off certain extensions while not in use prevents them from secretly spying on others.
Log out your MetaMask- Whenever you stopped working on the MetaMask extension, try to log out of it often.
Final thought
The digital realm is not safe from evil activities and while you are investing your income, it becomes a point of concern for crypto traders. There is no secret that MetaMask offers state-of-art security to dumped digital assets.
Your private or personal information is not within the control of MetaMask servers. All the data which is encrypted in your browser are protected via a MetaMask password.
On the whole, MetaMask offers the best security but you can also share the responsibility to protect your coins by implementing these helpful tips which I have elucidated in this read. Just navigate through them and safeguard your assets.
2 notes
·
View notes
Text
Waltr crack

WALTR CRACK HOW TO
WALTR CRACK FULL VERSION
WALTR CRACK LICENSE KEY
WALTR CRACK GENERATOR
WALTR CRACK KEY FREE
Hackers can use this backdoor to take control of your computer, copy data from your computer or to use your computer to distribute viruses and spam to other people.
WALTR CRACK GENERATOR
WALTR 2 2.6.7 keygen or key generator might contain a trojan horse opening a backdoor on your computer. These infections might corrupt your computer installation or breach your privacy.
WALTR CRACK FULL VERSION
While you are searching and browsing these illegal sites which distribute a so called keygen, key generator, pirate key, serial number, warez full version or crack for By Softorino WALTR is a 3rd party software that exists for the sole reason of hassle-free transferring of media (audio and video files) from your PC to your iPhone and iPad, without worrying about. Your computer will be at risk getting infected with spyware, adware, viruses, worms, trojan horses, dialers, etc Including WALTR 2 2.6.7 Rapidshare, MegaUpload, HellShare, HotFile, FileServe, YouSendIt, SendSpace, DepositFiles, Letitbit, MailBigFile, DropSend, MediaMax, LeapFile, zUpload, MyOtherDrive, DivShare or MediaFire, WALTR 2 2.6.7 torrent files or shared files from free file sharing and free upload services, Download links are directly from our mirrors or publisher's website,
WALTR CRACK LICENSE KEY
WALTR 2 2.6.7 license key is illegal and prevent future development of WALTR 2 Key is a program that allows you to use iTunes-free file transfers of music.
WALTR CRACK KEY FREE
Using warez version, crack, warez passwords, patches, serial numbers, registration codes, key generator, pirate key, keymaker or keygen for WALTR 4.0.114 Key Free With Fully Crack For Windows Latest Version Free.
WALTR CRACK HOW TO
→ How to add music to your iPhone without iTunes using WALTRįor those wondering, the name of the app is inspired by Walter White from the legendary crime drama series, “Breaking Bad”. Available for macOS and Windows, WALTR PRO is compatible with Apple Music, supports all the latest iPhone 12 models, as well as iOS 14 and Big Sur.įor more information on WALTR PRO, visit the official website.Top 4 Download periodically updates software information of WALTR 2 2.6.7 full version from the publisher,īut some information may be slightly out-of-date. The app packs in a bunch of other features that are outside the scope of this article, so I’ll only list them here: trim-less ringtones, audiobooks, smart encoding detection, high-resolution audio, 4K video, video content detection, forced subtitles, Light/Dark theme and more. You’ll be able to stream FLAC from any device, including the new HomePod mini. And for the audiophiles with FLAC music collections, WALTR PRO can safely convert your files into Apple Music (without losing quality). With iCloud enabled, your music will be backed up and ready to play from HomePod. Using WALTR PRO, you can add files to Apple Music. Siri on HomePod is great-but there are times when Siri cannot access or play our high fidelity music collection. Yes, you can can manually select the target app for the transfer. freeload Softorino WALTR 2 full version standalone offline installer for Windows, it is used to copy music, video & Epub files to iPhone without iTunes. And while the original WALTR was limited to native Apple apps, its Pro counterpart allows you to send virtually any file to your iOS device, like comics, Microsoft Office documents, VLC videos, Kindle books and so forth. WhatsMessage 1.1.1.0 (Bulk WhatsApp Marketing Software) With Crack. In addition to automatically scanning and filling missing metadata like before, WALTR PRO gives you full control of the way your media looks by allowing you to manually edit your cover artwork and metadata. Softorino WALTR 2.6.7 2018 WALTR 2 helps you wirelessly drag-and-drop any music. The items will be automatically converted into iOS-friendly formats on the fly and transferred to the right app on your connected iPhone or iPad. Like its predecessor, WALTR PRO is a simple app that allows you to drag and drop a bunch of media files onto its window. WALTR PRO brings several new pro-grade features, plus such perks as a standalone media converter, beautiful design, vastly more control than before and much more. We wanted to challenge ourselves and redefine our product approach entirely. Download Latest Version of WALTR PRO https://softori. We didn’t want to make ‘just’ an incremental improvement. Introducing WALTR PRO packed with powerful features, beautiful design & vastly more control. WALTR, an awesome Mac app for converting and transferring videos, music, ringtones and other media types to iOS devices, just got more awesome with the release of WALTR PRO.įor the past four years, we’ve been collecting your feedback and learning from our customers’ experience.

2 notes
·
View notes
Text
Share via
Skip to main content
Switch language
Skip to search
Mozilla Support Logo
Avatar for Username
Get Help
Volunteer
Protect your privacy
Customize this article
Firefox
Common Myths about Private Browsing
Private Browsing is a useful feature of Firefox, but only if you understand the protection it offers. It helps you obscure your online activity from other people who use Firefox on your computer, but does not make you invisible online.
Myth 1: Private Browsing makes you anonymous on the Internet
Reality: Private Browsing does not mask your identity or activity online. Websites and internet service providers can still gather information about your visit, even if you are not signed in. If you use your device at work, your company may be able to monitor the websites you visit. If you surf the Web at home, your cable company (or their partners) may have access to your browsing information. Only a Virtual Private Network (VPN) can mask your location and encrypt your online activity, keeping your identity and data safe from prying eyes. If you need to stay anonymous online, try Mozilla VPN.
Myth 2: Private Browsing removes all traces of your browsing activity from your computer
Reality: Private Browsing works by letting you browse without saving passwords, cookies and browsing history in a Private Window. If you download a file from a website, it will remain on your computer, but it will not appear in the download manager in Firefox. If you bookmark a website while in a Private Window, it will remain in your bookmark list.
Myth 3: Private Browsing doesn’t display any browsing history
Reality: Private Browsing will, by default, display visited sites and bookmarks as you type in the address bar. Firefox saves these pages during normal browsing. If you don’t want to see these suggestions, you can deselect them in your Firefox Settings Privacy & Security panel under Address Bar.
privacy preferences 65
Myth 4: Private Browsing will protect you from keystroke loggers and spyware
Reality: Private Browsing does not protect you from malware installed on your computer. If you suspect you have malware, take steps to remove it to prevent it from happening again.
To learn more about how Firefox protects your privacy, see Enhanced Tracking Protection in Firefox for desktop and SmartBlock for Enhanced Tracking Protection.
Share this article: https://mzl.la/3QEJeo1
Was this article helpful?
These fine people helped write this article:
AliceWyman, Michele Rodaro, Mozinet, Joni, Artist, Jeff, Erin S., Fabi, k_alex, Bithiah, JeremyKoozar, alineee
Illustration of hands
Volunteer
Grow and share your expertise with others. Answer questions and improve our knowledge base.
Learn More
Mozilla
Report Trademark Abuse
Source code
Twitter
Join our Community
Explore Help Articles
Firefox
Download
Firefox Desktop
Android Browser
iOS Browser
Focus Browser
Firefox for Developers
Developer Edition
Beta
Beta for Android
Nightly
Nightly for Android
Firefox Accounts
Sign In/Up
Benefits
Firefox Private Network
Language
Language
Twitter(@firefox)
YouTube (firefoxchannel)
Instagram (firefox)
Mozilla
mozilla.org Terms of Service Privacy Cookies Contact
Visit Mozilla Corporation’s not-for-profit parent, the Mozilla Foundation.
Portions of this content are ©1998–2022 by individual mozilla.org contributors. Content available under a Creative Commons license.

5 notes
·
View notes
Text
Your SIM Card Can Be Hacked in Three Ways (And How to Protect It)

You must be informed about emerging security breaches since new internet threats emerge every day. And, if you're reading this, you're surely aware that your Smartphone’s operating system needs to be updated on a regular basis to keep it safe from attacks.
Surprisingly, though, a SIM card can also be a source of security flaws. Many business listings we’ll show you how hackers can use SIM cards to obtain access to devices, as well as give you some tips on how to keep your SIM card safe.
1 - Simjacker
Security experts at Adaptive Mobile Security stated in September 2019 that they had uncovered a new security vulnerability known as Simjacker. By transmitting a piece of spyware-like code to a target device through SMS message, this sophisticated assault does SIM card hacking.
If a user opens the message, hackers can use the code to track their whereabouts and spy on their calls and messages.
The vulnerability is exploited by using S@T Browser, a piece of software that is part of the SIM Application Toolkit (STK) that many phone companies employ on their SIM cards. The SIM alliance Toolbox Browser is a method of business listings connecting to the internet—basically; it's a simple web browser that allows service providers to interface with web applications such as email.
The S@T Browser is currently rarely used because most people use a browser like Chrome or Firefox on their device. Many machines, however, still have the software installed, making them exposed to the Simjacker assault.
According to the researchers, the S@T protocol is "employed by mobile operators in at least 30 countries with a combined population of over a billion people," especially in the Middle East, Asia, North Africa, and Eastern Europe.
They also suspected that the exploit was created and exploited by a private company that was cooperating with various governments to track specific demographics, such as journalists and activists.
Phones of all types, including iPhone and Android devices, are vulnerable. Simjacker is also compatible with embedded SIM cards (eSIMs).
2 - Switching SIM Cards
SIM card switching is another security concern you may have heard about. In August 2019, hackers tried a variation of this approach to get access to Twitter CEO Jack Dorsey's personal Twitter account. This occurrence brought attention to the devastation that these attacks can cause. Rather than exploiting technical flaws, the method relies on deception and social engineering.
A hacker will initially call your phone provider to do a SIM card hacking through a SIM card switch. They will pose as you and free listing request a replacement SIM card. They'll claim they need a new SIM because they wish to upgrade to a new handset. The phone company will provide them the SIM if they are successful.
They can then take your phone number and use it to connect it to their own device. All without having to remove your SIM card!
This has two consequences. First, your original SIM card will be disabled and will cease to function. Second, the hacker now has control over your phone number, including calls, messages, and two-factor authentication requests. This implies they may have enough information to gain access to your accounts, and they may be able to lock you out of them as well.
Because it includes social engineering, SIM card swapping is difficult to prevent. Hackers must persuade a customer service representative that they are you. They have power over your phone number once they have your SIM. It's possible that you won't even realize you're a target until it's too late.
3 - Cloning of SIM cards
Many individuals mistakenly lump SIM changing and SIM cloning into the same category. SIM cloning, on the other hand, requires more effort than the other method.
In a SIM clone attack, the hacker acquires physical access to your SIM card before creating a duplicate of it. Naturally, the hacker will remove your SIM card from your Smartphone before copying it.
They accomplish this with the use of smart card copying software, which replicates your SIM card's unique identifier number onto their blank SIM card.
The hacker will next use their Smartphone to insert the newly duplicated SIM card. Consider your unique SIM card identification to be gone once this process is completed.
The hacker can now listen in on all of your phone's communications, just as they do with SIM swapping. They now have access to your two-factor authentication codes, allowing them to access your social media accounts, email addresses, card and bank accounts, and more.
Hackers can potentially exploit your stolen SIM card identity to commit fraud requiring a unique phone number.
How to Protect Your SIM Card
If you wish to safeguard your SIM card from attacks like these, there are a few steps you may take:
1 - Protecting Against Socially Engineered Attacks
Make it difficult for hackers to gather information about you to protect against SIM card swaps. Hackers will utilize information about you that they find online, such as your address or the names of your friends and family. This information can help you persuade a customer service representative that you are who you say you are.
Set your Facebook profile to friends-only and minimize the public information you publish on other sites to keep this information safe. Also, to avoid being the victim of a hack, remember to erase outdated accounts you no longer use.
Another approach to avoid SIM card swaps is to keep an eye out for phishing scams. Hackers may attempt to phish information from you in order to copy your SIM later. Keep an eye out for phishing emails or login sites. Also, be cautious about where you enter your login information for whatever account you use.
Finally, think about the two-factor authentication mechanisms you employ. Some two-factor authentication providers will deliver an authentication code through SMS to your device. This implies that even if you have two-factor authentication enabled, hackers can access your accounts if your SIM is compromised.
Use a different authentication mechanism, such as the Google Authentication app, instead. Because the authentication is related to your device rather than your phone number, it's more secure against SIM card swaps.
2 - Put a SIM Card Lock on your phone
You should also put up certain protections on your SIM card to protect yourself against SIM attacks. Adding a PIN code is the most crucial security action you can take. If someone wants to change your SIM card, they'll require the PIN code.
Before you set up a SIM card lock, make sure you know the PIN your network operator has given you. To enable it, go to Settings > Lock screen and security > other security settings > Set up SIM card lock on an Android handset. Then you can turn on the Lock SIM card slider.
Go to Settings > Phone> SIM PIN on an iPhone. Go to Settings > Mobile Data > SIM PIN on an iPad. The SIM lock will then be activated when you confirm your existing PIN.
3 - Additional Security Advice
As always, you should create strong passwords that are unique to you. Don't use the same password for several accounts or reuse old passwords.
Also, make sure your answers to password recovery questions, such as your mother's maiden name, aren't publicly visible.
Safeguard Your Device against SIM-Based Attacks
Mobile device hacking is becoming increasingly sophisticated. There are ways to defend yourself from such attacks, such as keeping your personal information private and using a SIM card locks.
Phones, on the other hand, are becoming more secure than they once were, and you can always check to see if yours has been hacked. To better protect yourself from malicious behavior, make use of the security options available to you.
1 note
·
View note
Text
Zero Click Malware: The Invisible Digital Threat – How to Recognize and Defend Yourself

Estimated reading time: 6 minutes
What is Zero Click Malware
Zero click malware, also known as non-click malware or in-memory malware, is a new type of malware that can infect a device without the user taking any action.
Unlike traditional malware that requires the user to click on a link or open an infected attachment, zero click malware is able to install itself on the victim's device completely silently and invisibly, without any interaction on their part.
How Zero Click Malware Works
This type of malware exploits various vulnerabilities in software and operating systems to gain access to the device. Some common infection vectors include:
- Zero-day vulnerabilities not yet patched
- Bugs in web browsers and messaging apps
- Packet sniffers that intercept network traffic
- Insecure public WiFi networks
- Websites compromised with drive-by exploits
Once initial access is gained, zero click malware uses advanced techniques to keep itself hidden and avoid detection. It can disable antivirus software, hide in RAM memory, encrypt communications, and much more.
Why Zero Click Malware is Dangerous
The completely stealth nature of this malware makes it extremely insidious and difficult to identify. Even the most security-conscious users can be infected without knowing it.
This allows hackers to:
- Monitor all activities performed on the infected endpoint
- Collect sensitive data such as credentials, personal information, browser history
- Collect sensitive data such as credentials, personal information, browser history
- Move laterally within the network to infect other systems
- Use the device for ransomware or denial of service attacks
Furthermore, since no clicks or actions are required, zero click malware can spread very quickly, affecting a large number of victims.
Case Studies and Technical Analysis

Some real-world cases have recently emerged that illustrate the capabilities of this new category of cyber threats.
One of the first zero click exploits to gain attention was Pegasus, developed by cybersecurity firm NSO Group. Used by some governments to spy on journalists and activists, Pegasus exploits zero-day vulnerabilities in iOS and Android to install itself without any user interaction.
Another famous case is ForcedEntry, used to hack the iPhones of several employees in Bahrain. ForcedEntry exploits a vulnerability in iMessage to install spyware without clicking on Apple devices.
These and other cases demonstrate the severity of the threat and the need for advanced protection solutions capable of detecting and preventing zero-click attacks.
How to Detect and Prevent Zero Click Attacks
Since this type of threat leaves no visible traces, identifying and stopping them requires targeted strategies:
- Patching and updates - Always apply the latest security updates to fix known vulnerabilities
- EDR Solutions - Endpoint detection and response technologies that analyze memory-based threats and anomalous behavior
- Advanced web protection - Secure web gateways capable of inspecting all traffic entering and leaving the network
- Network Segmentation - Limit the ability of malware to move laterally by isolating and segmenting critical systems
- Strong Authentication - Enable multi-factor authentication to prevent targeted phishing attacks that often precede zero-clicks
- Awareness Training - Instruct users to recognize and report suspicious activity that may indicate an infection
A layered approach that integrates multiple technologies and policies is essential to defend against this ever-evolving threat.
Increase Prevention with Deception Solutions
One of the most effective strategies against zero-click malware is the use of deception solutions. These solutions create a seemingly attractive environment for malware, but in reality they are traps that detect and isolate threats before they can cause damage. By taking a multi-stage approach to defense, you can dynamically respond to threats as they evolve, defeating attackers with their own techniques.
Continuous Testing and Threat Simulations
Attack simulations and continuous testing of security controls are another key pillar in zero-click malware defense. Services like Posture Guard help organizations verify their security posture by leveraging a vast database of threats, including malware, ransomware, and Advanced Persistent Threats (APTs). These tests help you evaluate the effectiveness of your security tools and optimize your threat prevention and detection capabilities.
Cyber Threat Hunting and Threat Intelligence
Cyber Threat Hunting is crucial to proactively identify threats and sensitive information that may have been compromised. Having a team of experts dedicated to this activity allows you to quickly recover stolen information and organize a more targeted defense. Combined with continuous vulnerability analysis and incident response, this strategy offers significantly improved protection against zero-click attacks.
User training and awareness
While zero-click malware does not require user interaction for infection, a well-informed and aware workforce can still play a crucial role in preventing other types of cyber attacks. Training users on good cybersecurity practices can reduce the risk of malware infections and increase overall security.
Adopt a Dynamic Approach to Security
Taking a dynamic approach to security is essential. Solutions like Active Defense Deception work to respond to attacks during the initial stages, using dynamic techniques to prevent attacks from reaching execution and more advanced stages. This type of proactive defense can deter attackers and make the environment less attractive for malware.
Forecasts and Future Developments
Experts predict that zero-click malware attacks will become one of the most used techniques by hackers in the years to come. As user awareness of malware and phishing grows, cybercriminals will look for new invisible vectors to deliver malicious payloads.
Additionally, the continued rise of IoT devices and smart home technologies presents attackers with an ever-increasing number of potential weak and unpatched targets. Operating environments such as 5G and edge computing could also facilitate the spread of zero-click threats.
To counter these trends, companies and security vendors will need to invest more in threat intelligence, bug bounties, sandboxing and machine learning-based threat detection techniques. Only in this way will it be possible to unmask the rapidly evolving zero-click attacks in no time.
Conclusions
Clickless malware is emerging as one of the most stealthy and dangerous tactics of modern hackers. Its ability to bypass any human interaction to infect entire systems represents a critical challenge for the world of cybersecurity.
To protect individuals and companies from this threat, it is essential to adopt preventive measures at multiple levels, from patching to network monitoring to training. Only by combining awareness and advanced technological solutions will it be possible to combat the phenomenon of zero-click attacks and maintain data integrity and security in the future.
- Your virtual machine with Cloud Server
Read the full article
0 notes
Text
will a vpn protect me from viruses
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨����🔒
will a vpn protect me from viruses
VPN antivirus protection
Title: Enhance Your Online Security with VPN Antivirus Protection
In today's digital landscape, protecting your online privacy and security is paramount. With cyber threats looming around every corner, it's crucial to employ robust measures to safeguard your sensitive information. One such measure gaining popularity is VPN antivirus protection.
VPN (Virtual Private Network) technology encrypts your internet connection, ensuring that your online activities remain private and secure from prying eyes. By routing your internet traffic through a secure server, VPNs create a secure tunnel that prevents hackers, government agencies, and other malicious entities from intercepting your data.
However, while VPNs excel at encrypting data in transit, they don't provide comprehensive protection against all online threats. This is where antivirus software comes into play. Antivirus software is designed to detect, prevent, and remove malicious software such as viruses, malware, spyware, and ransomware from your devices.
By combining VPN technology with antivirus protection, you create a formidable defense against a wide range of online threats. VPN antivirus protection offers the best of both worlds: the encryption and anonymity of a VPN, coupled with the threat detection and removal capabilities of antivirus software.
With VPN antivirus protection, you can browse the internet with peace of mind, knowing that your sensitive information is shielded from cybercriminals and other online threats. Whether you're accessing public Wi-Fi networks, conducting online banking transactions, or simply browsing the web, VPN antivirus protection ensures that your digital footprint remains secure.
In conclusion, VPN antivirus protection is a powerful tool for safeguarding your online privacy and security. By combining the encryption capabilities of a VPN with the threat detection features of antivirus software, you can enjoy a safer and more secure online experience. Invest in VPN antivirus protection today and take control of your digital security.
VPN virus prevention
Title: Safeguarding Your System: VPNs for Virus Prevention
In today's digital landscape, where cyber threats loom large, safeguarding your system against viruses and malware is paramount. One effective tool in your cybersecurity arsenal is a Virtual Private Network (VPN). While VPNs are commonly associated with protecting online privacy and anonymity, they also play a crucial role in virus prevention.
How do VPNs contribute to virus prevention? Firstly, VPNs encrypt your internet connection, creating a secure tunnel between your device and the websites you visit. This encryption prevents hackers from intercepting your data, including any malicious code they may attempt to inject into your browsing sessions. By encrypting your traffic, VPNs effectively create a barrier that shields your system from potential virus infections.
Moreover, VPNs offer another layer of defense by masking your IP address and providing anonymity online. This anonymity makes it harder for cybercriminals to target your device specifically, reducing the likelihood of encountering malware-infected websites or phishing attempts.
Additionally, VPNs enable users to bypass geo-restrictions and access content from different regions. While this feature is often utilized for streaming purposes, it can also help prevent virus infections by allowing users to access websites and services from regions with lower instances of cyber threats.
However, it's essential to choose a reputable VPN provider to ensure maximum protection. Look for VPNs with strong encryption protocols, a strict no-logs policy, and a wide server network. Furthermore, regularly updating your VPN software and maintaining good cybersecurity practices, such as avoiding suspicious links and keeping your operating system and antivirus software up to date, are crucial for comprehensive virus prevention.
In conclusion, integrating a VPN into your cybersecurity strategy not only safeguards your privacy but also serves as a valuable defense mechanism against viruses and malware. By encrypting your connection, providing anonymity, and offering additional security features, VPNs play a vital role in keeping your system safe in an increasingly digital world.
VPN malware defense
Title: Strengthen Your Cyber Defenses with VPN Malware Protection
In today's digital landscape, safeguarding your online activities against malicious threats is paramount. With the proliferation of malware targeting sensitive information, including personal data and financial details, adopting robust cybersecurity measures is crucial. One effective strategy in the fight against malware is leveraging Virtual Private Networks (VPNs) to fortify your defenses.
VPNs serve as a secure tunnel for internet traffic, encrypting data and routing it through remote servers. This encryption acts as a barrier, making it exceedingly difficult for hackers to intercept or decipher sensitive information transmitted over the network. However, while VPNs offer enhanced privacy and security, they are not immune to malware attacks.
To bolster VPN defenses against malware, users must exercise caution when selecting a provider. Opting for reputable VPN services with a proven track record of security is essential. Thoroughly researching and scrutinizing the encryption protocols, privacy policies, and logging practices of VPN providers can help users make informed decisions.
Furthermore, regularly updating VPN software is vital for patching vulnerabilities and addressing potential security loopholes. Many VPN providers release periodic updates to enhance security and functionality, ensuring users stay protected against evolving threats.
Additionally, complementing VPN usage with robust antivirus and antimalware software strengthens overall cybersecurity posture. Employing a multi-layered approach that combines VPNs with comprehensive malware protection significantly reduces the risk of falling victim to cyberattacks.
Moreover, practicing safe browsing habits and exercising caution when downloading files or clicking on links further mitigates the risk of malware infections. Vigilance and awareness are paramount in navigating the digital landscape safely.
In conclusion, VPNs play a crucial role in defending against malware by encrypting internet traffic and safeguarding sensitive data. By selecting reputable providers, keeping software updated, and adopting a multi-layered security approach, individuals and organizations can fortify their cyber defenses and mitigate the risk of malware infections.
VPN security against viruses
VPN (Virtual Private Network) security plays a crucial role in safeguarding your online activities against viruses and other malicious threats. While VPNs are primarily known for encrypting your internet connection and protecting your privacy, they also offer significant defense against viruses.
One of the key ways VPNs enhance security against viruses is by encrypting your internet traffic. When you connect to a VPN server, your data is encrypted, making it difficult for hackers or malware to intercept and infect your device with viruses. This encryption acts as a barrier, preventing viruses from infiltrating your system through unsecured networks, such as public Wi-Fi hotspots, where malicious actors often lurk.
Moreover, VPNs provide anonymity by masking your IP address and location. This anonymity makes it harder for cybercriminals to target your device with viruses, as they cannot identify your real identity or location. By browsing the internet anonymously through a VPN, you reduce the risk of encountering malicious websites or downloading infected files unknowingly.
Additionally, some VPN providers offer built-in features like malware detection and ad-blocking, further enhancing your defense against viruses. These features scan incoming data for any signs of malware or malicious activity, blocking harmful content before it reaches your device.
It's important to choose a reputable VPN provider that prioritizes security and regularly updates its infrastructure to defend against emerging threats. Look for VPNs with strong encryption protocols, a strict no-logs policy, and additional security features like kill switches and DNS leak protection.
In conclusion, VPNs not only protect your privacy but also serve as a robust defense against viruses and other online threats. By encrypting your internet connection, providing anonymity, and offering built-in security features, VPNs play a vital role in keeping your devices and personal information safe from malicious attacks.
VPN virus shielding
Title: Safeguarding Against Viruses with VPNs
In today's digital landscape, protecting your devices from viruses and malware is paramount. As cyber threats continue to evolve, users must employ advanced strategies to safeguard their data and privacy. One such strategy gaining popularity is VPN virus shielding.
VPN, short for Virtual Private Network, is a powerful tool primarily used to encrypt internet traffic and enhance online privacy. However, its benefits extend beyond anonymity. By routing your internet connection through secure servers located around the world, VPNs can also act as a shield against viruses and malware.
The fundamental principle behind VPN virus shielding is its ability to create a secure and encrypted connection between your device and the internet. When you connect to the internet through a VPN, all data transmitted between your device and the VPN server is encrypted, making it extremely difficult for cybercriminals to intercept or manipulate.
Moreover, reputable VPN providers often integrate robust security features into their services, such as malware detection and blocking. These additional layers of protection help to prevent malicious software from infecting your device, even when browsing potentially risky websites or downloading files.
Furthermore, VPNs can mitigate the risks associated with public Wi-Fi networks, which are notorious for being vulnerable to cyber attacks. By encrypting your data traffic, VPNs make it virtually impossible for hackers to eavesdrop on your online activities or steal sensitive information.
In conclusion, VPN virus shielding offers a proactive approach to cybersecurity, providing users with an extra layer of defense against viruses, malware, and other online threats. By investing in a reputable VPN service and adopting safe browsing practices, individuals can significantly reduce their risk of falling victim to cyber attacks and enjoy a safer, more secure online experience.
0 notes
Text
is vpn a virus
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
is vpn a virus
VPN vs virus comparison
In today's digital landscape, where cyber threats lurk around every corner, protecting your online activities is paramount. Two common tools used for safeguarding internet usage are VPNs (Virtual Private Networks) and antivirus software. While both serve to enhance online security, they operate in distinct ways and offer unique benefits.
VPNs function as a secure tunnel between your device and the internet, encrypting your data and masking your IP address. This encryption ensures that your online activities remain private and protected from prying eyes, including hackers, government surveillance, and even your internet service provider (ISP). Additionally, VPNs enable users to bypass geo-restrictions and access region-locked content, further enhancing online freedom and privacy.
On the other hand, antivirus software focuses primarily on detecting, preventing, and removing malicious software, such as viruses, malware, ransomware, and spyware, from your devices. By scanning files and monitoring system behavior, antivirus programs work tirelessly to identify and neutralize potential threats before they can wreak havoc on your device.
While both VPNs and antivirus software play crucial roles in safeguarding your online activities, they address different aspects of cybersecurity. VPNs protect your privacy and anonymity by encrypting your internet connection and masking your IP address, while antivirus software defends against malware and other malicious software that could compromise your device's security.
In summary, VPNs and antivirus software are complementary tools in the fight against cyber threats. By combining the privacy-enhancing features of a VPN with the malware-detecting capabilities of antivirus software, users can enjoy a comprehensive approach to online security, ensuring their digital safety and peace of mind.
Understanding VPN security
Understanding VPN Security
Virtual Private Networks (VPNs) have become an essential tool for safeguarding online privacy and security. By encrypting internet connections and routing them through remote servers, VPNs create a secure tunnel that shields users' data from prying eyes. However, to fully comprehend VPN security, it's crucial to delve into its key components and how they work together to protect sensitive information.
Encryption is the cornerstone of VPN security. It scrambles data into an unreadable format, making it indecipherable to anyone without the decryption key. Advanced encryption protocols like AES (Advanced Encryption Standard) with 256-bit keys are commonly used by reputable VPN providers, ensuring robust protection against unauthorized access.
Another vital aspect is the VPN tunneling protocol, which determines how data is transmitted between devices and VPN servers. Protocols like OpenVPN, IKEv2/IPsec, and WireGuard offer varying levels of security, speed, and compatibility. Choosing the right protocol depends on individual needs and priorities, balancing security with performance.
Furthermore, VPNs employ secure authentication mechanisms to verify users' identities and prevent unauthorized access. This often involves username-password authentication, digital certificates, or more advanced methods like multi-factor authentication (MFA), adding an extra layer of security.
While VPNs enhance privacy and security, it's essential to consider potential vulnerabilities. VPN providers can log user activity, compromising anonymity despite encryption. Additionally, VPN servers themselves could be susceptible to hacking or government surveillance, highlighting the importance of selecting a trustworthy provider with a strict no-logs policy and robust security measures.
In conclusion, VPN security is a multifaceted concept encompassing encryption, tunneling protocols, authentication, and provider reliability. By understanding these components and making informed choices, users can leverage VPNs to safeguard their online activities and protect sensitive data from cyber threats.
Common misconceptions about VPNs
Title: Debunking Common Misconceptions About VPNs
Virtual Private Networks (VPNs) have become increasingly popular tools for internet users seeking enhanced security and privacy online. However, despite their widespread adoption, several misconceptions about VPNs persist. Let’s debunk some of the most common ones:
VPNs Are Only for Privacy: While privacy is a significant benefit of using a VPN, it’s not the only one. VPNs also offer security by encrypting your internet connection, protecting your data from hackers and other malicious actors, especially when using public Wi-Fi networks.
VPNs Are Illegal: Some people believe that using a VPN is illegal, but this is not the case in most countries. While there are places where VPN usage is restricted or regulated, in the majority of jurisdictions, VPNs are legal tools that many businesses and individuals use to secure their online activities.
VPNs Slow Down Internet Speeds: While it’s true that using a VPN can sometimes result in slower internet speeds due to the encryption process and routing of traffic through remote servers, the difference in speed is often negligible, especially with high-quality VPN providers and fast internet connections.
Free VPNs Are as Good as Paid Ones: Many users opt for free VPN services to save money, but these often come with limitations such as data caps, slower speeds, and invasive advertising. Paid VPNs typically offer better performance, stronger security features, and more reliable customer support.
VPNs Are Only for Tech-Savvy Users: While setting up a VPN used to require some technical knowledge, many VPN providers now offer user-friendly apps and interfaces that make it easy for anyone to install and use a VPN on their devices.
In conclusion, VPNs are powerful tools for enhancing online security, privacy, and freedom, and by debunking these common misconceptions, users can make informed decisions about incorporating VPNs into their digital lives.
Benefits of using VPN software
Using VPN software offers a myriad of benefits for both individuals and businesses alike. From enhancing online security to bypassing geo-restrictions, here are some key advantages of using VPN software:
Enhanced Security: VPNs encrypt your internet connection, making it nearly impossible for hackers or malicious entities to intercept your data. This is especially crucial when using public Wi-Fi networks, where cyber threats are more prevalent.
Privacy Protection: By masking your IP address, VPNs allow you to browse the web anonymously. This means your online activities are shielded from prying eyes, including internet service providers (ISPs), government agencies, and advertisers keen on tracking your movements.
Access to Restricted Content: VPNs enable you to bypass geo-restrictions imposed by streaming services, social media platforms, and websites. This means you can access content that may be blocked or unavailable in your region, opening up a world of entertainment, news, and information.
Secure Remote Access: For businesses, VPNs provide a secure way for employees to access company networks and sensitive data remotely. This is particularly useful for remote workers or those who frequently travel, ensuring confidential information remains protected at all times.
Prevention of Bandwidth Throttling: Some ISPs engage in bandwidth throttling, slowing down your internet connection based on your online activities. VPNs encrypt your traffic, preventing ISPs from monitoring and selectively slowing down your connection speed.
Protection from Censorship: In countries where internet censorship is prevalent, VPNs offer a lifeline by allowing users to circumvent restrictions and access the open internet. This empowers individuals to freely express themselves and access information without fear of censorship or surveillance.
In conclusion, the benefits of using VPN software extend far beyond just security and privacy. Whether you're a casual internet user, a remote worker, or a business owner, incorporating a VPN into your online toolkit can enhance your browsing experience and safeguard your digital presence.
Safely navigating VPN usage
In today's digital landscape, utilizing a Virtual Private Network (VPN) has become increasingly essential for safeguarding your online activities. However, merely having a VPN isn't enough; knowing how to navigate its usage safely is paramount. Here are some tips to ensure you're maximizing the security benefits of your VPN:
Choose a reputable VPN provider: Opt for well-established VPN services with a track record of reliability and strong security measures. Research thoroughly before committing to a provider to ensure they prioritize user privacy and data protection.
Enable kill switch: Most reputable VPNs offer a kill switch feature that automatically disconnects your internet connection if the VPN connection drops. This prevents your data from being exposed to your ISP or other prying eyes during brief interruptions.
Utilize strong encryption: Ensure your VPN uses robust encryption protocols like AES-256, which provides a high level of security for your data. Avoid VPNs that use outdated or weak encryption methods that can leave your information vulnerable to interception.
Avoid free VPNs: While tempting, free VPN services often come with limitations and may compromise your privacy by logging your data or serving ads. Invest in a paid VPN service to guarantee better security and reliability.
Regularly update your VPN software: Keep your VPN client updated to ensure you're protected against the latest security threats and vulnerabilities. Updates often include patches for known issues and enhancements to strengthen security.
Be cautious with public Wi-Fi: When using public Wi-Fi networks, always connect through your VPN to encrypt your data and protect against potential eavesdropping by cybercriminals.
By adhering to these guidelines, you can safely navigate VPN usage and enjoy enhanced privacy and security while browsing the internet. Remember, a VPN is a powerful tool, but it's only effective when used correctly and responsibly.
0 notes