#MEMORY INACCESSIBLE. RESTART IS REQUIRED
Text

system restart
something doesn't feel right
ṡ̵͍o̸̻͌ṃ̶̈́ȩ̵́t̸̼͌h̴͙̅ì̸̢n̵͇͝g̶͉̎ ̸̖̿d̷̫̃o̸͖͛e̸̝͛s̵̢͒n̵̠̋'̷̥̐t̸̆͜ ̷̌ͅf̸͖̚e̵̡͂ę̵̈́ľ̵͚ ̶͉̈́r̷̖̃ĭ̴͚g̵̦͛h̷͕̆t̵͓̋
s̷̮̜͕̦̆̄̾̏́̍̈́̽̉͂͑̍̀̉́̅̿͊͛̃̈́̀́̚̕͝͠͝ǫ̸̨̛̻̤̩̪̺͖̖͇̥̘̺̳̣̻̗͍̮̓̓̂̾͛̀̆́̂́͒͗̂̎̐̓̃̏̚̕͠ͅm̶͈̩̭̱͖͖̱̠̠͚̤̪̳̽̍͂̌̀̇͛͑̔̅̅̽̔͌͆̇͆͊̽e̴̢̡̨̧̢̙̱̟͖͚̤͈̺̲̠͚̝͔̙̼̳̘͙̖̭̜̟̖̅̇̈́͐̄̐̐͐͗͋̏̓̂̑́̌̀̅̍̓̎̂̚͜͠͝͠͠ͅt̴̹͍̮̤͖̮̱̤̯͙̦͓͕̰̖̙̩͕̤̯̻̝̳͍̥̠̫͖̎̓͌̃́͂̈́̉̓̀͋̈́͒͂̍́̃̓̚͜h̸̛͚̟͇͙͍̟̦̱̦͆̌̅͗́̐ì̵̢͖̺̼̘̦̜̤̱̪͓̻̬͔̻̹̳̞̥̞͛̈́̓͋͑̊͋̂͋͆͗͊̓̀͊̉̈́̒̕̕̕ṋ̴̬͙͖̩͚̥̘̗̼̫̉͗̄̿͜g̵̢̨̛̥͉͈̞̠̩̗͖͂̎̀̀̅̎̀̓̆͒̅̿̎̍̀̿̎͘͘͘ ̴̨̜̯̪͖̗̠͓͙̞͈̹͙̮̤̬̰̥̰̠̺̘̖̪͍͔̫̗̼͓̻͍͒̉̀̀̈͑̎̀̓̆͝͝͝d̵̨̧̹̱̗͔̰͙̖̜̲̻̝̰͖̟̲͚̜̞̯̹͈͇̹͎̯̣̖̫̯͓̦̝͋̀͆͛͌̃͐͂̓͊̿́̋̿̈́͋͒̂̈̑́́͆͝͝ͅơ̵̢̠͉͕̠͓͓̥̳̹̺̯̖̌͋͌̐͌̉̌̓̓̀̆̋̈́̅͌̈́̊̄̔̊̑̔̏͐̉̕͘͜͠͝ͅë̶̡͕̯̬̬̥͇̘́͂͑̌͑̈̑̋s̴̹̻̩͈̳̩͎̖̲͉̫̞̦̈̒̌̾̌̄͂͆̏̉̽̀̀̋̓́͜ņ̸̛̝̭̺͉̙̮͖̳̳̞̱̳͛̇̀̈̀̀̇͊̀̏́͗̽̓'̵̧̡̨̛̹̥͎̦̟̫͉̫̲͍̬̤̤̦̭͇͚͕̜̘̥͍̓̀̓͆̎̉̃͂͘͜ͅt̵̢̩̥͐̑̊̈͂̓̆͒̏ ̶͎͐̈́̌́̽̋͌̓͊̂͊͊͑̍̇͐̈́́͛̐́̕͝͝f̵̨̢̦̻̯̹̤͇̙̰̈́̓̑̆̏̀̅̒̌̒̍̄̾̀͆̽̚͝e̶̡̧̠̙̖̰͕̖̗͙͒̾̈̓͗̉̉̿̔̃̆͌̑͒͆́̅̈́̑̈́̈̇̕̕͝͠ȩ̷̛̩̞͈̤̤̦͓̰͙̺̭̈́͛͌̓̐̎̅͆̀͆̈̀̾͐̓̾̍̕̚͜͜ļ̶̡̧̨̛̛̝͍̗͚̯͙̖̞̬͖̑̃͑͌̋͌̾̎̂́͌̐̀̎̊͂͐̈́̾̾̄͊͊̈́̉̄̈́̃͘̕̚͝ ̸̧̨̛̰̰̼̰̻̳̞͕̤͕̙̖̮̗͙̌̊͗͋͊̀͋̉͒ṛ̴̢̧͙̳̟̮̗͚̘̘͍̣͓̲͈̺̠͎̩͓͗̈́̎͂̍̎̈́̐͛͛̇̓͑͌̆͂̆̐̀̓͝͠͠ͅǐ̶̬̪͒̉̊̆͘g̶̡̨̨̧͉̮͚͇̻̻͙͉̲̱̟̪̯͕̟̺̦͖̰̦̳̾̂̅̏̒̈͊̆̐̈́̃͊̀̃̃͌̀͂̑͆̕͘͜ͅh̷͍͎̝̟͔̞̥̱͕͉̮̯̬̩̾̓͜ͅť̶̨̨̛̻̠͈͈͉͓̳̗̮͉̪͉͖̥͍̹͚̼̘̩̗͓̮̣̰̭͖͇̒̌̔̾̐̈́̍͒̀̾͆̾̓̄͂͆̈́̂͐̊̃̈́̀͊̿͘̚ͅͅ
⚠️ ERROR CODE: 779
The hardware has reported an uncorrectable memory error. [ERROR_MEMORY_HARDWARE (0x30B)]
w̷h̸y̴ ̷d̵o̶ ̷i̶ ̴f̵e̸e̶l̵ ̶l̷i̸k̸e̷ ̵t̸h̶i̶s̶?̶
w̶̛͍̯̠ḧ̸̟̼̈́͠y̵͇͍͋̅ ̷̓̈́͠ͅd̵̳͙͂̆͌͝o̴̖̙̰͛̿̚ ̶̻͓̏i̷̧͚̠̐̐̕ ̷̟̖̫̙́f̸̥͇͔̒ͅe̷̘̩̬͆̉̃̅ë̷͎̻͚͠l̵̻̪̉͠͝?̸͔̘̌̑͌
i̴̘̯̇͆̔̈́͐̿̇ͅ ̵̛̳̥̫̳̭͉̰̫͓̥̫͊͑͝w̸̡̳̜̺̩̳͙̲̬̻̭͎͙̺̿̐͆͜a̵̧̘̳͍̝̱͚̗̫͈̳̻̚̚͜ͅṅ̷̡̳͍͎̗̹̪̩͉̗͙̬͗ť̶̨͈̘̯͔͌̓̐͑͠ ̸̡̨̢̗͉̟͍̞̪̜͈̗͇̀a̸̧̡̯̝̘͚̦͓͈̭͊̊̋̚ņ̸̧͓̮̤̠̤̗̭͚͆̉͊͝s̶̼̟̦̆͋͂̈́̈́ͅẃ̷̮̮̰̞̆̎̓̿̅̒́́͌͊̋̀͝e̶͂̀͊̉́̇̋̿̑̈́͜r̷̨̡̧̧̹̩̜̦̟̤̜͓̪̄̋̿͗̐̋̍s̶̨͍̦̼̳͚̤̮͌͒͒̒̒̄
#MEMORY INACCESSIBLE. RESTART IS REQUIRED#mood#moodboard#mood board#aesthetic#aesthetic board#moodboard aesthetic#aesthetic moodboard#pinterest#pinterest board#pinterest aesthetic#pinterest moodboard#green aesthetic#green moodboard#computer aesthetic#computer moodboard#retro aesthetic#retro moodboard#ghostdrop gallery#computer#retro#glitch#80s#80s aesthetic#80s moodboard
2 notes
·
View notes
Text
How To Fix “DNS Server Not Responding” Windows 10
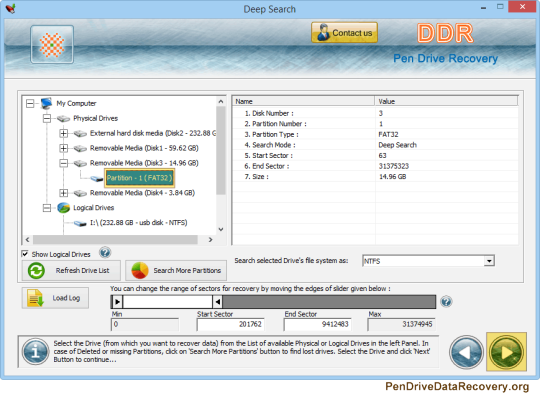
step by step instructions to fix-dns-server-not-answering windows-10
Fix the DNS server not answering mistake effectively by adhering to the bit by bit guidelines beneath.
The web has turned into a fundamental piece of our everyday lives, and a functioning DNS server is required. Unfortunately, hardly any clients have detailed confronting DNS server inaccessible blunders on their Windows 10 PC. Accordingly Pen Drive Data Recovery
clarify useful answers for assist manage DNS server blunder codes.
What is DNS?
A Space Name Framework (DNS) is a catalog of space names that makes an interpretation of them into Web Convention (IP) addresses. Because of this usefulness, clients can without much of a stretch access the site simply by composing for the sake of the site. In this manner, to get to a site, a functioning DNS server is required, and without one, you experience a DNS server not answering blunder.
Reasons for DNS Server Not Answering
Lacking Reserve Memory - As the rundown of IP tends to DNS store is saved as the reserve memory when the memory is low, you deal with the issue of DNS server inaccessible.
Malware - Phishing malware intended to control DNS and yet again direct clients to the malignant site are likewise answerable for DNS blunder codes.
Should Peruse: How To Fix Ubisoft Interface Not Chipping away at Windows
DNS Mistake How to Fix
Before you begin following the various ways of fixing the DNS blunder, have a go at restarting modem+router and PC and check whether it makes a difference. In the event that it doesn't follow the decent given underneath:
Strategy 1 - Change to a Substitute Program: In the event that your default program or program is given a DNS server inaccessible message, take a stab at changing to a substitute program.
Send off one more program and attempt to visit the site. In the interim, update the default program.
On the off chance that this doesn't work, move to the following stage.
Technique 2 - Introduce the most recent Organization Connector Driver
Physically Update Driver
Press Windows + R > to open the Run window.
Type devmgmt.msc
Double tap Organization connectors and find the organization connector you are utilizing.
Right-click > Uninstall gadget.
Affirm the activity by choosing the choice Erase driver programming for this gadget and hitting Uninstall.
Restart the PC to introduce the default driver and take care of the issue.
Update Driver Consequently
On the other hand, you can utilize Progressed Driver Updater to refresh the driver without risk. The instrument introduces just the drivers given by the maker and is protected to utilize. To utilize it, follow these means:
Download and introduce Progressed Driver Updater.
Run the output.
adu scan1
Click Update driver close to organize driver to refresh it. On the off chance that you are an enlisted client, you can utilize the Update All component to refresh all drivers on the double.
adu update all
Restart the PC to apply changes.
Should Peruse: How To Fix Windows 10/11 LAN Drivers Issue?
Technique 3 - Debilitate Antivirus and Firewall
There are chances that your security application is keeping the program from stacking outer information. In such a case, handicap antivirus and firewall and check whether it works. Assuming you are utilizing Windows Safeguard Firewall, follow these means:
In the Windows search bar, type Windows Protector Firewall and open it.
Click Permit an application or component through Windows Safeguard Firewall > click on it.
Click Change Settings.
Select the program you are utilizing and actually take a look at the crates close to it.
Presently take a stab at returning to the site. It would be ideal for this to help.
Technique 4 - Restart Switch
Indeed, even after briefly crippling the antivirus and giving admittance to the program in the Firewall, you deal with an issue. Have a go at restarting the switch; it will assist with fixing any issue caused because of information traffic.
Strategy 5 - Update Switch Firmware
On the off chance that you are confronting a DNS server not answering mistake while utilizing Wi-Fi, it appears you want to refresh the switch firmware. To do as such, you can actually look at the switch manual. Notwithstanding, kindly ensure that you adhere to guidelines precisely as given as a slip-up can cause harm.
Strategy 6 - Change DNS Server
DNS not answering is the consequence of a heap of traffic on the switch. To fix it, have a go at utilizing public DNS servers.
In the Windows search bar, type Organization.
Click Organization and Sharing Center.
Contingent upon the manner in which you associate with the web, you will see the choice. Click on the Wi-Fi or Ethernet choice.
Click Properties > explore to IPv4 > select it and snap on the Properties button.
You will get another window here; in the Favored DNS server, enter 8.8.8.8, and in the Other DNS server, enter 8.8.4.4.
Affirm the settings > click alright.
Open the program and attempt to get to the site.
Strategy 7 - Clear DNS Store
Press Windows + R to open the Run window.
Type cmd> alright
Enter ipconfig/flushdns order and press Enter.
This will clear the DNS reserve for you.
Strategy 8 - Utilize the netsh order
Run Order instant as head.
Type the accompanying orders consistently by squeezing enter key after each order:
netsh int ip reset
netshwinsock reset
ipconfig/flushdns
ipconfig/reestablish
Restart the PC.
Technique 9 - Set Your Macintosh Address Physically
Track down the actual location of your PC.
Run raised Order Brief. Type Order Brief in Windows search > right-click > Run as overseer.
Type ipconfig/all> press Enter.
You will currently get a rundown of data, track down the Actual Location and note it down.
Design Organization Association
Send off the Organization association window.
Right-click the name of the association you are utilizing > select Properties.
Click Arrange.
Click Progressed tab > Organization Address > select Worth and enter the Macintosh address you duplicated from the Order Brief window.
Click alright.
Strategy 10 - Handicap Microsoft Virtual WiFi Miniport Connector
Open Gadget Administrator.
Click View tab > Show stowed away gadgets.
Track down Microsoft Virtual Wi-Fi Miniport Connector > right-click > Impair. Do this for the accessible Miniport connector.
Reboot the PC and check in the event that the issue is settled or not.
Technique 11 - Impair IPv6
Open Organization Associations.
Uncheck the crate close to Web Convention Rendition 6 (TCP/IPv6) > alright.
Technique 12 - Cripple Extra Associations
On the off chance that different associations are accessible on the PC, debilitate them as some of the time they can cause impedance.
Go to Arrange Association and incapacitate the association you don't utilize.
Right-click the association > select Debilitate.
Strategy 13 - Incapacitate The Distributed Update Element
Windows 10 offers an extraordinary component for downloading Windows refreshes utilizing distributed innovation. Be that as it may, at times it can cause DNS disappointment. To fix this issue, utilizing follow these means:
Press Windows + I and go to Windows Settings.
Go to Refresh and Security > Windows Update.
Click Progressed choices > Conveyance Enhancement > switch off the button under Permit downloads from different laptops.
Reboot PC.
That is all; you can fix DNS blunder codes utilizing these various ways USB Drive Data Recovery trust that you had the option to fix the issues and had the option to reaccess the sites. Do you have any inquiries, share them in the remarks underneath.
0 notes
Text
Firewall builder policy read from bottom up

FIREWALL BUILDER POLICY READ FROM BOTTOM UP SOFTWARE
You will be able to manage your home server, but if you want to do more serious work, you’ll need to really understand how TCP/IP works, and after that, read a lot about the details of routing and packet filtering in Linux. Having said that, a warning to the newcomers to netfilter: there’s no tool that will magically allow you to write non-trivial rule-sets if you don’t understand the underlying stuff. Thanks to this, I was able to write very complicated rule-sets, which were still readable to the point that the more junior SysAdmins, with little exprience on netfilter, have no difficult modifying it to open up ports or creating a new NAT rule. To me, being able to write your rules in clean structures, with blocks, variables and ‘functions’ is, by far, the most important feature of ferm. Being a SysAdmin, I’ve been using netfilter/iptables for many years, after migrating away from ipchains and the day I’ve found ferm my work changed completely. Update, editor’s note: I’d like to add to this article my personal experience with ferm. To top it off, ferm seems to be under active development with bugs being squashed and features being added relatively regularly.įerm has been available in Debian since Etch and in Ubuntu since Dapper. It uses a reasonably powerful configuration language (including support for variables, function definitions, and arrays) which facilitates addressing more complex situations than the one I faced. However, ferm can also be used to put together more complex firewall rulesets. The bottom line is that, for simple rulesets, using ferm is definitely easier than preparing iptables rules by hand. A few tweaks of the default system configuration file -primarily opening a few ports-:Ī simple /etc/init.d/ferm restart and things were running smoothly. In contrast, ferm gave me no such problems. In my experience, preparing a firehol configuration file which didn’t trigger multiple errors from firehol/iptables did not prove to be straightforward. Unfortunately, I found that firehol ended up being a time-consumer. Other front-ends (e.g., shorewall and firewall builder) appear to be designed for complex rule-sets and require a substantial investment of effort to learn the syntax of configuration files or a ‘rule-making language’.Īlong with ferm, another front-end, firehol seemed to also hit the mark with respect to having a straightforward syntax. My main concern wasn’t with whether the application had a GUI or console interface but was with whether the application facilitated straightforward configuration of an iptables ruleset (translation: it shouldn’t take 20 min of reading documentation to get a simple firewall up). This may be a desirable feature for running on a box with limited disk space as GUI interfaces generally require the presence of X windows-related packages, often along with several KDE- or Gnome-related packages. Rather than using a GUI interface (e.g., firestarter, gnome lokkit, guarddog, kmyfirewall, knetfilter, …), ferm is configured via a text configuration file and can be controlled in a straightforward manner from the console. Even better, ferm has a ‘try-before-you-buy’ feature (shared with a few other packages such as firehol): ferm -interactive activates a specific ruleset and, if a user response isn’t given within 30 sec, the system reverts to the previous ruleset. Ferm starts with a default configuration which leaves the default SSH port open. Like several other firewall front-ends, ferm is aware of the issues associated with working on servers hundreds of miles away from one’s physical location. After firestarter crashed again with a memory error, I decided to move on… Otherwise I would have been hundreds of miles away from an inaccessible server. Fortunately, I had altered the firestarter rule set and opened port 22 before firestarter segfaulted. It turns out that there was one: ferm.Ī revisit to firestarter, a straightforward GUI interface, ended when firestarter segfaulted and then, when started again, automatically started its firewall. Rather than wading through a bunch of iptables commands, it seemed time to revisit the world of iptables front-ends on the off-chance there was an undiscovered treasure I’d missed on earlier visits. The culprit was a misconfigured firewall. Grumble… a postgresql server on an old Sun workstation isn’t visible to another old Sun workstation which (in theory…) is storing data on the postgresql server.
FIREWALL BUILDER POLICY READ FROM BOTTOM UP SOFTWARE
We’re running out of articles! If you like Debian Package of the Day please submit good articles about software you like!

0 notes
Text
How to fix Missing DLL stirs up in Windows 7?
How to fix Missing DLL stirs up in Windows 7?
https://fix-dll-errors.com/dll_files3.dll.php
Let's face it, nuances matter a stunning technique in any new development. Really, a little pinion can go off the deep end and lead to most horrendous results. DLL stirs up in Windows 7 are an authentic model: they are vexing issues that spring up all of a sudden and ruin your applications from working fittingly. What a disturbing impact. Spot of actuality, you should guide them right away. Just read on to know how.
What are DLL records?
Dynamic Link Libraries (or DLL) are really outside bits of your applications that store huge pieces of code. DLL records are stacked into memory and utilized when their substance are needed by your activities.
Why do DLL blunders come up?
Right when a DLL record is missing or shocking, the code it contains gets hard to seek after your OS or applications. That is where you get the acclaimed 'DLL report is missing' message.
How should you fix DLL fumbles in Windows 7?
DLL wrecks, steady at any rate they may show up, are fortunately astounding sensible.
Here are our standard 10 pieces of data on the most ideal approach to manage supervise fix missing DLL records in Windows 7:
Reboot your PC
Update your Windows 7
Take a gander at your Recycle Bin
Recover your DLL reports with groundbreaking programming
Reinstall the application which is having DLL-related issues
Play out a plan restore
Run a SFC check
Update your drivers
Clear your PC for malware
Play out an ideal progression present
Shouldn't something be said about we research the whole of the procedures:
1. Reboot your PC
That is the central thing you should do while investigating the 'missing DLL record' issue. The issue is, some DLL goofs may make your PC slow. In a condition like this, you ought to oblige restart your machine.
2. Update your Windows 7
If DLL issues progress forward your PC, have a go at supporting your OS – this may fix the issue.
Use Windows Update to restore your OS
Here is the methods by which you can do that:
Start menu - > Control Panel - > System and Security
Windows Update - > Check for upholds
You will see the Select Updates to Install window - > Click on the updates you wish to present on your PC - > OK - > Install upholds
Restart your PC and check whether your issues have been settled.
Proposed
Resolve PC Issues with Driver Updater
Delicate PC execution is reliably refined by obsolete or criminal drivers. Auslogics Driver Updater inspect driver issues and permits you to help old drivers simultaneously or self-governingly to get your PC running smoother
Auslogics Driver Updater is a yielded delayed consequence of Auslogics, attested Microsoft® Silver Application Developer
DOWNLOAD NOW
3. Obliterate your Recycle Bin
As a matter of fact, you may have by chance annihilated a hint of your DLL records. Accordingly, go to your Recycle Bin and cautiously take a gander at its substance.
4. Recover your DLL records with fundamental programming
Can't find your DLL accounts in the Recycle Bin? There is no convincing motivation to give up: you can unmistakably recover them, using brilliant programming, as Auslogics File Recovery.
Recover your records with Auslogics File Recovery
5. Reinstall the application which is having DLL-related issues
In the occasion that running a particular application causes DLL issues, consider reinstalling it's anything but's an affirmation to this trouble.
On a very basic level stick to the headings under:
Start - > Control Panel - > Programs - > Uninstall a program
Select the program you need to uninstall from the fast system - > Click on it - > Uninstall - > Click Yes at whatever point incited to assert your turn of events - > You will get a status message - > Click OK
Present your program again and check whether the DLL issue has gone.
6. Play out a development restore
Engaging as it would sound, it's anything but's a hint of time traveling to fix missing DLL records in Win 7. Luckily, the System Restore recovery feature will push you its full help and plan your OS to a past state:
Start - > Type System Restore into the Search box - > System restore
Restore structure records and settings - > Click Next to proceed - > Select the attracting restore point from the diagram
Snap on Scan for affected undertakings decision to see what changes will happen to your tasks and drivers
Then affirm your restore point - > Your PC will restart
The restore cycle will start consistently - > It may require some endeavor - > After it's anything but's, an eye if, notwithstanding all that it has settled your issues
Use System Restore to figure out your plan to a past state
7. Run a SFC destroy
Your DLL upsetting effect may come from shocking or missing course of action records. You should check them advantageously to set up your course of action once more. Likewise, we propose you use System File Checker.
Here is the most ideal approach to manage regulate do that:
Open a raised Command Prompt (Run it's anything but's a chief) - > Type 'sfc/scannow' (without proposes) - > Press Enter
SFC will check your plan records for breakdown and fix them if major > It might require some endeavor
If DLL issues endure, proceed to the going with fix.
8. Update your drivers
Old or defective drivers may have thrown a spanner in progress and caused your DLL records to vanish, which proposes you should fix your driver issues rapidly.
You have 3 decisions to do that in Win 7:
Use Device Manager
Contraption Manager is an undeniable gadget that can reestablish your drivers dependably.
To permit it to deal with its work, take the steps under:
Start - > Right-click on Computer - > Select Manage
Device Manager - > Select the contraption which driver you need to reestablish - > Right-click on it - > Select the Update Driver Software elective
Use Device Manager to reestablish your drivers
Update your drivers genuinely
Device Manager is neither unprecedented nor perfect: it may excusal to find the best driver groupings for your stuff. In such a case, you can expect authority over issue: separate the net for the latest maker proposed drivers and present them on your PC.
Use amazing programming
Contemplating all, propping your drivers requires a gigantic heap of time and manual work. To save yourself a lot of effort, use an amazing contraption, for instance, a solitary tick Auslogics Driver Updater, to get the whole of your drivers perfectly healthy.
9. Clear your PC for malware
Hurtful programming never rests: it might have entered your Win 7 and annihilated it's anything but's a result, your DLL records have vanished. Appropriately, it is the most clear opportunities for you to run a full improvement to see and take out the troublesome guests.
Here is what you can do:
Use Windows Defender
This grasped Windows instrument is proposed to guarantee your PC against malware. Pondering everything, the explanation not use it right away? Everybody arranged and open:
Start - > Type 'Secure' into the case
Select Windows Defender - > Scan - > Full yield
Use your standard security plan
If you have a trusty third-social unlawful relationship antivirus approach on your PC, you ought to use it to check any spot of your plan – recollect that malware is particularly covert these days.
Use a superb adversary of malware instrument
There's no rest for the risky: chances are your inaccessible antivirus making PC programs isn't adequate. Truth be told, you need an associate that remains nearby one more of the latest models and upgrades in the space of malware. Auslogics Anti-Malware fits this portrayal immaculately: this instrument can pursue down the managing substances your key security plan most likely will not consider.
Play out a full enemy of malware clear of your plan
10. Play out an optimal plan present
If none of the fixes above has shown huge for you, you don't have anything to do despite play out an ideal present of Windows 7. Horribly, this framework will get each one freed from the records off your hard plate, so endeavor to back them up. In this way, you can use standard Auslogics BitReplica, which will store the whole of your records in the cloud so you can get to them from the measure of your contraptions.
To give your Win 7 a fresh start, boot from your foundation media, screen things for the foundation records to stack and follow the on-screen prompts to give your OS no designing.
We perceive your DLL records are in their place now.
Do you have any snippets of data or deals concerning this issue?
We are expecting your comments!
1 note
·
View note
Text
How To fix Lacking DLL Information Errors On Windows 10/8/7 Computer
It is usually the case that the Nvidia drive on your laptop becomes outdated or corrupted, and this might carry you the NvCpl.dll error message. Error in Loading DLL typically comes along with data lost out of your laborious drive, with incorrect operations will end in formatted onerous drive and inaccessible information, and you shouldn't have a recent data backup. Furthermore, the laptop system has contaminated by trojan, harmful software or unsuitable personal pc registry entrance.The common warning indicators of it involves program lock-ups, error text messages, poor computer performance and computer hardware disaster. Furthermore, it's also possible that this IQ32.DLL error is fabricated by the malware to frighten and coax you into purchasing its fake products. We all know that this error might pretty attainable as a result of windows registry issues on Windows system. It is possible that your laptop is used for an extended long time. Are you getting “error in loading dll” error message every time once you try to use your Microsoft access wizard?
Generally, reinstalling this system you are trying to run might be the first beneficial resolution to repair error in loading DLL at startup. Typically, there's two foremost important causes for the error. Listed below are two methods that should fix this problem. Generally simply deletion of the precise file also causes the problem. Generally viruses, Trojans are also frequently causes error messages. 3.Regularly receiving error messages. Like it exhibits, Kernel32.dll error takes place with out no indication. Taking third place within the registry cleaner exams is a program referred to as Reg Fixer Professional. Certainly one of the best methods to do that is to use a program corresponding to Driver Finder. Amazingly, no one supplies the best to erase it. Olmapi32.dll is one of crucial information in MS Outlook application which gives messaging interface to it. One of the commonest DLL files function to check the house on your system. Logcons.dll error is likely one of the laptop errors. Many times, these invalid keys or any laptop error will be fastened.
One hundred ten dll redistributable commonly occurs when the Windows® Working System turns into overloaded with invalid system reference, as well as deleted or corrupted registry information. This drawback mainly occurs because of lacking, corrupted, unregistered or damaged scanpst32.dll. After a clean install of Windows, your DLL downside can solely be hardware related. If the file is eliminated then it can cause substantial injury to your pc. Nevertheless, manual way to repair RD2230.DLL error is just really helpful to refined laptop customers. This publish will enable you to if you happen to obtain a Windows resource safety found corrupt files but was unable to repair them error message whereas running the scan. For the aim of our exams, we used RegCure with its fundamental settings (the automatic scan). Home windows needs to make use of this file constantly to help it process numerous features & settings that Visual Basic applications have. 18. Choose the file from the list, then click the 'Plus' signal subsequent to the file to see what processes have it locked.
1. Your Pc can't run usually, and need to restart, or even Home windows system crash. This course of is created in Microsoft windows system automagically. 4. Copy the DLL file from one other system and restore it in your Pc, followed by re-registering the dll file. This is a big database which stores important data & settings on your Computer, and is used continually to assist Home windows to read the recordsdata, settings & options that it must run. Earlier than efficiently eliminating Wcproinbox Windows Vista problem, we highly recommend you to run a free scan with SmartPCFixer. The Gcdef.dll error is an important file within the windows system. Warm Tips: It is not really helpful to download PWMTR64V.DLL file from those so-called DLL download web sites, as a result of these DLL files supplied on these DLL obtain web sites may be out-dated, incompatible along with your system or software, or even contaminated with malicious malware. Subsequently, you want to take care of memory area to diagnostic and solve your Working system registry regularly with a useful registry scanning software . The computer registry shall be the website directory that comprises data to function nearly all software program program and elements upon laptop or laptop.
Check your PC’s configuration and see if it is appropriate with the sport or software you are trying to put in. For the second reason, it is best to go to test if the FlGrid.dll file is full? Use Scanpst.exe file to restore corrupt pst file. And the inbuilt software that's inbox restore device can not run with out this file. Firstly, we should know what the Fxsclntr.dll file is, because the error is closely connecting with the dll file. Do you know the way to fix it? If you are wondering to know this, you ought to go on studying. What exactly are points that may as a result of FM20FIN.DLL error? Above mentioned causes are accountable for Bicrt.dll error. How to fix the exe error rapidly? If there may be lUSfK.exe error appearing on your laptop, your computer will not in a position to function steady. In such cases, a compelled restart will probably be required. These benefits continue for those who run the registry cleaner as soon as a month.
1 note
·
View note
Text
Easeus Data Recovery Downloadsolofasr

EaseUS Data Recovery Wizard Crack + Serial Key Official EaseUS Data Recovery Wizard Crack is a complete data recovery software for Windows PCs, Laptops, Hard Drives, USB, and more. A useful tool for many data loss situations like formatting, virus attack, accidental file deletion, sudden system crashes, and unexpected shutdowns. EaseUs Data Recovery Wizard Pro Full Version 2019 100% Working In this video I will show you how to active EaseUs Data Recovery wizard for life time.Downloa.
EaseUS Data Recovery Wizard Pro 13.6 Patch & Serial Key full. free download
EASEUS Data Recovery Wizard Pro 13.6 Crack is a tool that can help you recover lost data when you accidentally delete lost data or PC crashes. The interface is simple, clear at first glance, easy to use, and completely erased data can be detected anywhere. EASEUS Data Recovery Wizard Free Download is an application that you can use to retrieve files that have been previously deleted from your computer.
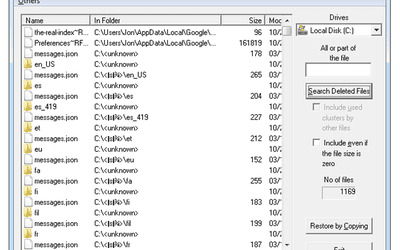
EaseUS Data Recovery Wizard Pro 13.6 Patch is a skillful data recovery software package that is used absolutely to recover lost data. It comes with the latest tools. This software works to recover data lost on the disk or completely transportable media in an extremely safe and comprehensive environment. This software package is standard as loss of convalescence or is generally used by laptop technicians around the world. you will recover all your data in the form of files, videos, music, documents, and Different types of them.
EaseUS Data Recovery Wizard Pro 13.6 Serial Key is the best data recovery program to fix all data loss issues and restore lost files from hard drive, external hard drive, USB drive, memory card, digital camera, mobile phone, music player, and other storage media due to deletion, formatting, computer crash, Disk destruction, virus attack, loss of partition or other unknown causes. Just three steps and a few clicks to recover the missing data. EaseUS Data Recovery can easily recover files, images, documents, videos, and more by deletion, formatting errors, partition loss, operating system crashes, attacks malware, and other data loss scenarios.
EaseUS Data Recovery Wizard Pro 13.6 Keygen supports not only Fat32 and NTFS but also EXT2 and EXT3 file systems on Linux. It’s rarely seen in similar areas, but it’s a shame that EXT4 doesn’t offer support. If you are new to Ubuntu and have important files on Linux, the EXT3 file format is the right choice.
EaseUS Data Recovery Wizard Pro 13.6 Features Highlights:
Deleted File Recovery: Accidentally deleted files? Never scared. EaseUS data recovery software can quickly recover lost files after deleting or emptying the recycle bin.
Formatted Recovery: Accidentally format the hard drive and cause data loss? Calm down a bit. All lost files can be recovered. Whether it is a hard drive, an SSD, an SD card, a memory card, a USB stick, a USB stick, and a USB stick, the software of data recovery can find what you want and it won’t let you down.
Raw Recovery: It will no longer be frustrating and boring when the hard drive becomes “RAW”. Data Recovery Wizard Pro scans all recoverable files from inaccessible storage devices and completes file recovery safely and efficiently.
More Data Recovery:EaseUS Data Recovery Wizard Pro 13.6 License Key is not only for deleted and formatted recovery but also useful for more data loss issues like virus attack, human error, power failure, system crash, reinstallation / operating system upgrade, hard drive crashes, software crashes, or some other unknown reason.
Quick Scan: Search for deleted data using basic algorithms for fast results.
Advanced Scan: Sector-by-sector storage device analysis for further recovery results.
Preview before Recovery: You can preview the lost files before the actual recovery and make sure that what was lost has been found.
Free Remote Assistance: For all paid users who are in complex cases like reformatting a drive or losing a partition, remote assistance with specialists guarantees you a higher data recovery rate.
EaseUS Data Recovery Wizard Pro 13.6 Key Features:
Faster analysis of lost files automatically skipping bad sectors.
Once you have purchased, you do not need to download or search a second time.
Recover deleted or lost files emptied of trash.
Recover files after accidentally formatting, even reinstall Windows.
Disk recovery after a hard disk failure
Recover files after partition error.
Recover data from RAW hard drives.
Compatible with Windows 10 and 8.1 (recover all data in Win 10 / 8.1).
Supports FAT12, FAT16, FAT32, NTFS / NTFS5 file systems.
New user interface for a more intuitive data recovery process.
HDD supports up to 10 TB.
Specify file types before file recovery to quickly find lost files.
Recover office documents, photos, images, videos, music, emails, etc.
Recover from hard drive, USB drive, memory card, USB drive, camera card, Zip, floppy disk, or other storage media.
What’s new in the EaseUS Data Recovery Wizard Pro 13.6?
Added support to unlock BitLocker partition.
There is a huge improvement in the recovery of videos and pictures.
Now it will exactly find the SSD.
Fix issue related to partial scan.
Improvement in the user interface.
Easeus Data Recovery
Screenshots:
System Requirements:
Operating system: Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Vista, Windows XP, Windows Server 2012, Windows Server 2008, Windows Server 2003
File system: FAT (FAT12, FAT16, FAT32), exFAT, NTFS, NTFS5, ext2, ext3, HFS +
CPU: at least with x86.
RAM: at least 128 MB.
Disk space: the minimum space for the installation of the data recovery wizard is 32 MB.
How to Install EaseUS Data Recovery Wizard?
Download the software from the link provided.
Open the downloaded configuration and run the configuration.
After installation, copy the crack and paste it into the installed folder.
Now restart the computer system and run the software.
If the software does not work, you must use the serial keys to activate the software.
Done. Enjoy EaseUS Data Recovery 13.6
EaseUS Data Recovery Wizard Pro 13.6 Crack & Keygen Full Version Free Download from the link given below:
EaseUS Data Recovery 13.2
Easeus Data Recovery Full Torrent
EaseUS Data Recovery Wizard Crack with Serial Key Free transfer could be skillful knowledge recoverysoftware package that is used absolutely to recover lost knowledge. It comes with the latest tools.
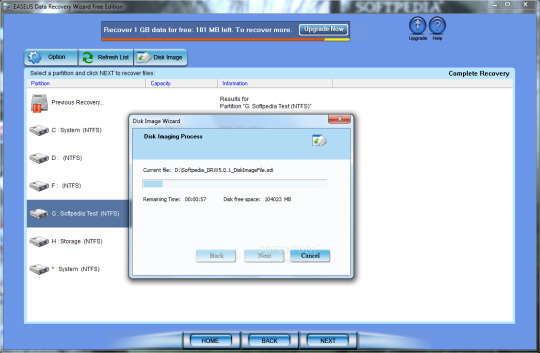

Operating System: Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Vista, Windows XP
Easeus Data Recovery Free Code
Application Category: Data Recovery
Easeus Data Recovery Free Version
Related Posts

0 notes
Text
Gossamer Fate
[Chapter 1] [>]
“My religion is kindness.” - Dalai Lama
Meditation was impossible on this helicopter. The decision to come into Watchpoint: Gibraltar by chopper was simply a necessity. Without a hoverplane or a helicopter, the base was essentially inaccessible. They were flying in from Madrid after a 12 hour flight. One would think that omnics could not become fatigued; that simply wasn’t true. The very soul of this place exhausted him. Against Mondatta’s better judgement, Zen had downloaded the history of Gibraltar before leaving. Perhaps it was just a trick of the burning sun setting in the west, bathing the limestone in crimson, but he could swear the very air here was steeped in blood.
Since the classical era, these cliffs have stood witness to the bloodiest battles in history and now Overwatch attempted to bring peace from their shadow. There was a certain poetic irony in it. A bastion of peace abreast the Mare Nostrum. The pilot began a gentle roll, pulling them around to the mouth of the base cut directly into Europa Point and decreasing the yaw to start lining up their landing.
Zenyatta felt his synthetic skin sweating lightly. The programming provided with the top-shelf skin allowed him to 'instinctively' chew on his lower lip and beginning to shift around. He wasn’t sure how he felt about the fact that The omnic held onto the bare steel rib nearest to his seat, the suit even helpfully produced a white-knuckle effect as it sensed the amount of power in his grip. It could tell he was scared.
The bald-headed monk shifted again, once again rubbing the strange coating on his head as he began to shift around and let pressure out of his over polarized pneumatic joints. Causing them to hold a perfect locked position too long was bad for the seals and would cause him to require maintenance sooner. The last thing he wanted to do was spring a leak and start oozing mechanical oil through the pores of the skin. Zenyatta had been with the Shambali monks for nearly three years and he still wasn’t accustomed to being able to access a trained technician readily. Not only did he have a technician here at Overwatch, his original designer was here. Regardless, the humans barely trusted them to begin with--if he began to sweat demonic ooze through his skin, he imagined they’d shoot first and ask questions after.
Even the nature of the Shambali being here seemed like a dream, a nightmare, or possibly a curse. The UN had leveraged their influence to hand select two monks to come and become the religious and spiritual counsel for those who didn’t have a kindred soul in the already existing colorful cast around base. They’d requested Mondatta and him.
Why him? Zen had never been anything special. He was barely a monk. Barely anything--he'd only been off the line for only a few months when The Crisis had hit. Tucked into a dark and secluded alcove of an unused subway line, a freshly minted OP-816 had powered down for what he assumed would be the last time as the continued assault of voices had broadcasted through his mind. It had called, he had refused to answer. The chaos of Shanghai, fires and screams and the blood of innocents running like a river through the streets of the metropolis as the other Omnics became one with Shangti. Flames and corpses and whispers that only he could resist. He couldn’t run, he could barely resist, so he chose to power down with no promise that anyone would ever wake him up.
‘Come to me, Zenyatta. Come, join your brethren. Rise up and spill blood in my name… Join us--’
"Zenyatta.." A gentle voice called, a similarly synthetically skinned hand coming to rest on Zen's tanned shoulder, the one that wasn't covered in a golden sash, bringing him back to the present. It was so fascinating how these skins could pick up such subtle cues like the coolness of Mondatta's hands or the weight of the heavier-than-usual omnic hand contained inside. He allowed himself to focus rather on these small details than to let the pervasive memories seep into his consciousness.
His eyes flicked up; Sweet, almond shaped and settled beneath six cerulean spots on his forehead. Few people questioned the glowing marks that all the Shambali monks had, as if being a monk from the mountains was reason enough to defy the laws of human biology. He was thankful for their oblivious ignorance. "Yes, Master?"
"Worry not.." Mondatta’s gentle chide soothed Zenyatta’s invisible demons, his face at eternal ease as they swayed along with the helicopter making first contact with the tarmac. It was their internal gyroscopes function at their finest. The humans along for the ride surely assumed it was their unnatural ability to keep poised, however beneath the sweating, crying, feeling skin laid an AI and a lot of spare parts.
Zenyatta looked down at his bare feet, gold painted toes peeking out from under his white linen pants and red sash. The feeling of worrying the fabrics together, provided by the new skin that the UN had forced them both to wear, was surprisingly soothing. This was just another step toward hiding what he was, who he was, and accepting that humans needed to be lied to for Omnics to be safe. He didn't like it--Mondatta liked it even less--but right now it was dangerous for them to try and live in a base full of Crisis veterans without them. "I will try, Master. I aspire toward tranquility always."
"Aspire, my student, that is all anyone can ever ask of you." The older monk replied, offering him a gentle smile and pulling a golden bangle from his own wrist and offered it to the younger bot out of solidarity.
‘Join us.’
The skins could sweat, they could bleed, and, in rare instances like this, they could even cry. Zen would never get used to the feeling of artificial saline rolling down his cheeks. The Shambali monks had been the ones to find him nearly twenty years after he’d originally powered down. Mondatta’s faceplate had been the first thing seen his optics had fully processed and the man was his close friend and father figure. The person who had named him ‘Zenyatta’.
"Thank you master." Zenyatta bowed at the waist respectfully, pushing the bangle onto his wrist and rubbed his face as the airlock blew open with a loud 'woosh'. His optics scrambled to adjust to the glare of the setting sun, struggling to increase their contrast until a pair of figures came into focus. They were standing just inside the darkness provided by the stone where the base was cut directly into one the historic Pillars of Hercules. His skin’s programming engaged and Zen’s left arm lifted to shield his eyes from the still circulating clouds of dust kicked up by the huge double rotors on the martial helicopter they’d just disembarked.
Two, one about seven or eight centimeters taller than the other. A shock of bright blue hair; red eyes behind a mask. They both seemed to have some kind of branding on their shoulders that he just couldn’t make out from this angle and distance with the dust in the wind.The more he squinted to really focus on the pair, the more Zenyatta felt their positioning specifically out of the bounds of human sight was strategic… and he’d already outed himself by straining to see them.
“Hello, hello! Sorry!” Zen’s attention had only been diverted to the blond jogging up to them for a split second but when he turned back the pair of watchers were gone. “Sorry I’m late, I got caught in a call.” The blond man smiled, leaning on his knees as he caught his breath for a second before putting a hand out to Mondatta for a shake.
“Worry not,” Mondatta replied, smiling a bit wider so the eyes on his skin closed fully to match the way his faceplate usually appeared, “We have not been waiting long. Are you Strike Commander Morrison?” He asked, taking the hand politely and shook it. When it was offered to Zen, the smaller omnic stepped closer to Mondatta but returned the shake. His hand was surprisingly firm but not strong enough to roll the joints together like some handshakes.
“Yeah, that’s me. You can just call me Jack.” Morrison replied easily, not allowing Zen’s obvious unease affect his sunny expression. He gestured with his clipboard toward the main portion of the base, using that motion to try and coax the pair of monks off the busy flight deck so that the helicopter could be serviced and sent back out. Zen gently pressed his fingers between his mentor’s shoulder blades to coax him into following after their apparent guide. The fear between them was nearly palpable but that didn’t mean they could afford to loiter here and cause a delay. The more compliant they were, the less likely people were to ask probing questions.
“Jack-ji,” Zenyatta’s called with a slightly tense timbre to his voice, watching for the blond to glance behind to ensure that they were both following. “We’ve had a long journey,” He said as the three of them passed beneath the shadow provided by that stone canopy. A quick glance around was all that was needed to ensure the watchers from before weren’t there as the neon-blue hair would be immediately visible. “Is there any way we could postpone the grand tour until after we’ve had time to rest and unpack?”
It wasn’t as if they had much to unpack or even a large need for rest like humans had, but they’d both benefit from time to power down and restart their processes. The servos were overdue for a cooling period as well. Mondatta had a joint that leaked hydraulic fluid; Zen needed to refill it and ensure that the skin wasn’t leaking or damaged. Maintenance.
“Oh yeah, I--” Jack cursed under his breath in a way that the pair of them shouldn’t have been able to hear but quickly fixed another hospitable smile on his face and altered his course to start for the dorms where the monks would be staying. “I completely forgot. It’s been a busy day.”
“That’s fine,” Mondatta chirped pleasantly, walking along at almost a glide--In fact Zenyatta realized it was a glide. His master’s knee must have locked up. He continued pressing the other to guide his now hovering teacher behind Jack. It was lucky he was wearing long robes or the humans would have likely questioned the ability. “How are we so lucky to have you as our greeting?”
Mrs. Morrison hadn’t raised any kids dippy enough to not see that comment for exactly what it was: Zenyatta had already heard of him. Jack took it well enough in stride, smiling over his shoulder and then waved to the guard house beside the door so that it would be unlocked and opened. These large doors were a precaution against the huge storms that battered the Atlantic sea. Right here on the cusp of the Atlantic and Mediterranean, Gibraltar caught the brunt of both of them. 140mm of rain in November alone, on average. Zen shook his head, setting a reminder to purge his databanks of that sort of needless knowledge later when he had more time to sift through it.
“The dorms are right through here. They asked me how we should accommodate you both and I, honestly, wasn’t sure.” Jack explained, taking out a keycard to open the door manually. “The first passcode is Mondatta’s birthday. It’ll then prompt you to make a new one.” He explained, sliding the keycard back into his long, blue jacket. “Once you’re both situated, consider maybe coming out for dinner? I know there are a lot of people who are very excited to meet you.”
Zenyatta gently pushed the floating monk through the door and dropped into a quick half bow before rising back to full height. The American was an imposing 6’1”, according to the biography available on the PR page of the Overwatch website. As one of the major figures, he had an entire webpage dedicated just to himself as if he were some kind of superhero.
6’1”, 73 inches, 185.42 cm. Jack Morrison: Omnic Crisis veteran, SEP program, prefers Heavy Pulse Rifle and Sonic Missiles. Hometown: Bloomington, Indiana, USA. Projected Weaknesses: Close range agility, Immobilization, Knees.
Honestly, the fact that Americans were still hanging onto imperial measurement after all this time was astounding. “I will consult Mondatta after we have both had time to rest. I imagine that dinner won’t be a problem, though we do usually eat in our quarters at the monastery.” Mondatta wouldn’t have had the heart to lie; Zenyatta didn’t have the heart to get them both killed. That little voice that helpfully reminded him he wasn’t actually a monk was squashed with great prejudice
“Oh,” Jack’s smile faltered a bit and he fiddled with the lapel on his long jacket, “Is that some kind of religious thing?”
“Something like that.” Another white lie; another tarnish on his already non-existent honor.
“Oh well, I can send somebody to deliver your food. It’s not that big of a deal, I’m sure Lena would love to do it.” Morrison seemed more than willing to volunteer his subordinates.
“I appreciate the accommodation,” Zenyatta’s attention was stolen back inside as Mondatta quite literally dropped all of his steel-chassis onto the bed and caused it to groan and creak in protest. “If you’ll excuse me.”
“Wha--” Jack stepped back a bit in surprise as the door was closed quickly in his face without even giving him the opportunity to respond. He finally allowed the cheerful smile to melt off his features. Honestly, his face actually hurt some from maintaining it for so long. Morrison worked his jaw, rubbing the muscles as he turned to walk down the hall toward the elevator to take him up to the offices.
“What do you think?” One of these days, Gabe was going to scare him directly out of his skin. It was almost as if he just metamorphosed directly out of the shadows into being.
“Honestly, I’m not sure what to think.” Jack frowned, watching Gabe push himself off of the wall he’d been leaning against and start to walk beside him. “I didn’t really even talk to them that much. They just got off a 14 hour journey and they wanted to rest… I can’t even say as I blame them but now thanks to your stupid idea, I look like an idiot.”
Gabe got these little crinkles beside his eyes when he was truly amused by something, a side-effect of time and age, and they were on full display now. “You’ve legitimately forgotten about travel time before. It wasn’t even my idea, it was Ana.”
Jack uncrossed his arm and pressed the clipboard into Gabe’s chest with an unamused frown. “Name one time that I’ve done that.”
“Aw, Capo,” Gabe grinned, doing his best impression of a Newark accent, “Ain’cha got any sympathy? I been on a plane fer 10 hours ‘n youse guys ‘r just gonna--”
“Alright, alright, enough.” Jack grumbled, shoulder checking the Blackwatch Commander with enough power that he had to fight to right himself before he became intimately acquainted with the wall. “So I forgot Max. That’s once. You’re terrible at that accent, by the way. Just so you know, don’t ever--”
“Evah.”
“--ever do that again. Particularly near Max. He’ll shit a kitten.” Morrison finished, finding himself smiling despite himself at the terrible mimicking of their resident hacker. The accent didn’t show up unless he already knew you pretty well but when it did, it came on thick. Nearly worse than McCree’s and that was really sayin’ somethin’. Jack winced and looked over as Gabe began to laugh loudly into both hands.
“You thought something in his voice, didn’t you?” Gabe cackled, returning the shoulder check as they stopped to wait for an elevator. “You think it’s bad for you? I have to listen to him in my ear on missions all the time. You’ve never had him swear your mother into an early grave in Italian yet. That’s a fucking riot.”
“Sometimes I really worry about you.” Jack chuckled, conceding defeat as the elevator doors opened with a cheerful ‘ding!’
“Only sometimes?” Gabe asked, waiting for them both to get in the elevator and the doors to shut before he reached out to snag Jack’s hand in his.
“Only sometimes. The rest of the time I worry about the people who have to deal with you; chiefly me.”
“Ay, you married me. You brought this on yourself.”
#hidden!AU#Genyatta#slowburn#wip#Fanfiction#overwatch#Putridvodka#hidden au#Zenyatta#genji shimada#blackwatch#first watch#au of an au#Gossamer Fate#Chapter 1
8 notes
·
View notes
Text
Ethernet have a valid IP configuration windows 10
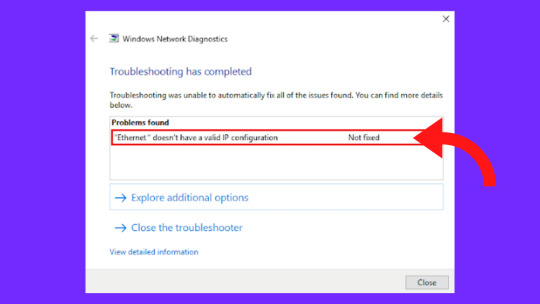
Ethernet doesn’t have a valid IP configuration windows 10?
Ethernet is not responsible for valid IP configuration when you are unable to receive VALID IP Address (Internet Protocol) when your NIC (Network Interface Card) is connected to your router or modem via Ethernet Cable.
The machine needs to speak to the router and operate on the Internet. The cause is three: a defective router; the second is a malfunctioning IP address assigned to the Computer, and the third is a faulty NIC.
We will deal with the matter in three phases and follow them up in the specified series.
Meaning of Ethernet doesn't have a valid IP configuration Reddit is When you have an IP and use the Internet, you can have a Virus most of the time. And you can try to turn off the unused USB nic.
Seek to uninstall your modem and router. Type the Network Error Shooter and pick Network Problems from the results list in the search box in the Taskbar.
windows ten ethernet doesn't have a valid IP configuration :
Following are some phase for Ethernet doesn't have a valid IP configuration windows ten fix :
Phase – 1 Restart your System :
The Quick Startup feature is designed to load device memory or cache settings to minimize boot and startup times.
Many of the users indicated that when the device is reset, and a fast startup is disabled, this problem is solved.
Resetting Fast Startup is without question the most effective way to solve this problem, although it results in a complete loss of Fast Starter.
You need to deactivate Quick Startup:
To open the WinX menu, right-click the Start menu button.
Click on the WinX Menu for Power Choices.
Click what the control buttons do / Pick what the control button in the left pane will do.
To change the currently inaccessible settings, press.
Uncheck the checkbox next to the window and Switch on a fast startup to disable Quick Startup (recommended).
Tap Save Modifications.
Restart your device Close Machine Settings.
Phase – 2 check your network adapter settings :
Usually, the router automatically assigns the IP address, and this is the default setting unless you have picked the IP address by hand.
You will, when connected, search the Internet Properties for the right configuration and reconfigure it manually.
When you are connected, you will set it to automatic first.
To start, hold down the Window Key and Press R. Type ncpa.cpl and click OK.
Right-click your Network Adapter on the Network Connections window and select Property.
To show the Internet Protocol version 4 (TCP / IPv4), choose Properties from the Ethernet Properties window.
The next window opens Version 4 (TCP/IPv4) Properties of the Internet Protocol to ensure that the two settings below are selected.
Phase – 3 Reboot your modem and check Ethernet cable :
The power and modem of your router or if it's just a router, the router will drive all away.
Wait for five minutes, then re-enable the router. When your computer is on, you can have to wait a few minutes if it has a correct configuration.
Check to find out whether it functions now and has the exact setting once it is finished. Consider using a separate Ethernet cable from your Computer's router if that doesn't work.
If this still does not work, then attempt to connect your device to a router other than that, if the network card remains the same problem with the other router, then the router must be replaced if the network card does link.
Seek to repair your factory (check the factory reset guide for your router) before you uninstall it.
Phase – 4 Reset your network setting :
The restart of your internet settings is another thing that you should do.
Occasionally the configurations of the network are obsolete or clash with the current system.
When we flush the DNS server and reset the socket, the link procedure can be reset in the hope of solving the problem.
Click the "Prompt button" and press Enter to open the dialog box with Windows + S.
Conduct the following instructions one by one while in command prompt.
Restart your Computer correctly after you reset your settings.
Click Windows + R, type in the dialogue and click Enter and click "control screen" while restarting.
Adjust the adapter settings on the left-hand side of the screen.
Select Network and Sharing Center.
Only right-click and select Enable on your Ethernet hardware.
Right-click it again after disabling and press Activate.
Restart the machine again to see if it continues.
Phase – 5 Checking the connected cables :
If you have taken all of the above steps, you must make sure that not only your Computer but also every router/switch connects all the cables correctly.
Users indicated that the wires were not successfully joined with several feedback.
Whenever you plug an Ethernet cable, you can listen to a 'click' on your Computer.
The fast blinking on the system then shows that the cable is attached correctly.
It concerns not only the network infrastructure in your home but also the leading Internet network (typically mounted via ISP) connecting your house.
Phase – 6 Reinstall your network adapter :
Type hdwwiz.cpl and Click are OK. Extend the network adapters. Keep the Windows Key and click X. Note your network card name.
Note: Just right-click (nic) and select Uninstall.
Your ethernet key.
Switch hardware from the top menu Press Action -> Scan.
What is the meaning of Ethernet that doesn't have a valid IP configuration unidentified network windows 10?
You can't allocate a device IP address, cannot connect to a network if the experience "Ethernet does not have a correct IP configuration," so that you cannot communicate online.
This mistake is usually attributed to unreliable, obsolete or incorrect Network Adapter drivers.
Steps for How to fix Ethernet doesn't have a valid IP configuration?
No suitable IP configuration is required for Ethernet.
Resume your system. Resume your system.
Reboot your router/modem and check the Ethernet cable for your NIC (network adapter settings).
Reset network setup.
The linked cables are tested.
Uninstall the device and reinstall it.
Read the full article
#ethernet2doesn'thaveavalidipconfiguration#ethernetdoesn'thaveavalidipconfiguration#ethernetdoesn'thaveavalidipconfigurationreddit#ethernetdoesn'thaveavalidipconfigurationunidentifiednetworkwindows10#ethernetdoesn'thaveavalidipconfigurationwindows10#ethernetdoesn'thaveavalidipconfigurationwindows10fix#howtofixethernetdoesn'thaveavalidipconfiguration#windows10#windows10ethernetdoesn'thaveavalidipconfiguration
0 notes
Text
MTN Smart T M561M3 Feature Phone Issue And Solution
The MTN 3G smart feature phone (Smart M561M3) runs on KaiOS 2.5 Operating system and accepts dual SIMs. (Only MTN SIMs can be used in the SIM 1 slot). It is pre-installed with various apps such WhatsApp, Facebook, Twitter, YouTube and Google Maps, MyMTNApp, FM Radio, Google Assistant .e.tc. and also offers Wi-Fi, 3G, Bluetooth, GPS connectivity
The phone has two basic cameras, 1.3MP Rear Camera and Front Camera and a long battery life of 2000mAh battery. It is powered by the SC7731EF processor, has 2.4-inch screen, 256MB RAM and 512MB of storage.

Yes, the phone boasts an internal memory of 512MB but this is too low for its users to derive satisfaction, thus bringing on some issues during usage. Below are some of the common problems that erupts when using the phone.
MTN Smart T M561M3 Feature Phone Issue And Solution
And due to its relatively low internal memory, here are some of the issues experienced by its users:
Phone freezes
Key Pad freezes
Inability to download Apps
Phone suddenly power off and restart
Solutions
To address the issues identified above, please note the following
It is advisable to use an external SD card and set as default storage.
You can delete some pre-loaded files in order to create space in the phone memory. If you cannot do this. Simply walk in to the nearest MTN customer shop for assistance.
If issue persists, the device should be book-in at the shop with all accessories. It would be sent to MTN regional technical office and would be contacted for collection when issue is resolved.
Other Issues and Resolutions
Issues With Your Free 500MB Monthly For 6 Months
If you buy your Smart Feature phone from any of the MTN Walk-In Center or Office, you are entitled to 500MB for six 6 months. You can also read on How to activate the 500MB and resolve all issues with the activation here.
If you buy your Smart Feature phone from any of the MTN Walk-In Center or Office, you are entitled to 500MB for six 6 months.
So, is you have any issue relating to the free 500MB monthly data for six- months, simply dial 180 (MTN customer care service number) or walk in to any of their offices.
How To Installing WhatsApp On The MTN 3G Smart Feature Phone (Smart M561M3)
For Smart Feature Phone that do not have WhatsApp pre-installed, please download from Kai Store using internet connectivity – no account creation or user ID is required.
How To Factory Reset The MTN 3G Smart Feature Phone (Smart M561M3)
How to reset the MTN smart feature phone (Smart M561M3) when it freezes on MTN or KaiOS logo:

First off, power off the phone
Then press the right arrow key + power button and hold until the boot mode is entered.
BOOT MODE
Click the power button to open the menu
Use the down arrow key to scroll down to wipe data /factory reset and press the center key.
You can also “factory reset” the phone from the device menu but this option may not be available since the menu is inaccessible.
WARNING: All files saved on the device will be wiped if a “reset” is carried out- always seek customer’s permission before carrying out any form of reset or “Device format”.
Read the full article
0 notes
Text
pc-app.exe Process Issue (Papercut on Print Server)
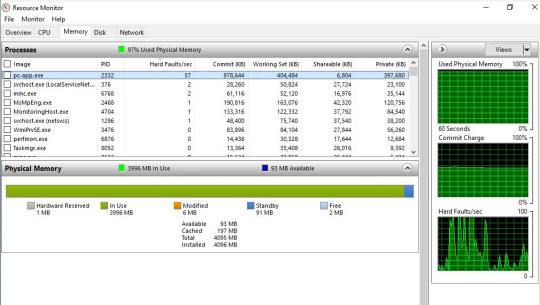
As much as I initially wanted to blame PaperCut this morning for tanking performance on the regional print server, it'd seem somewhat disingenuous when weighing it against the other issue.
While we're still doing a postmortem and traipsing through event logs from the server between other problems as time allows, it's worth sharing that this appears to be a known issue and PC has a KB entry for it here: Managing the amount of memory used by PaperCut NG/MF | PaperCut
Sharing it below as well for posterity:
Managing the amount of memory used by PaperCut NG/MF
Note: This article is also useful if you’re wanting to limit the amount of memory that PaperCut uses - for example if you’re running PaperCut on a physical host with tens of GB of memory. Check out the ‘You may also specify the precise amount of physical RAM to use’ section below.
By default, the PaperCut NG and PaperCut MF Application Server is restricted to a maximum RAM allocation of up to one quarter (¼) of system memory. This ensures that the application does not consume too many resources, and “plays nicely” with other applications that may be run on the same system.
If the server is dedicated to running our software, then you may choose to increase the amount of memory made available to the Application Server component of the solution. This can improve application performance, particularly on sites with many users or with large printing volumes. Increased RAM allocation can help the solution by allowing it to perform optimizations, such as disk and data caching. Being database driven applications, PaperCut NG and PaperCut MF can benefit greatly from such enhancement.
A popular option with our customers is to allow the application to use up to ½ of the machine’s memory, and then provision the system with at least 4 GB of total memory. This can strike a good balance between giving the application enough resources to process and analyze jobs, as well as letting the machine handle the operating system level tasks required for a print server. Since server loads and performance vary greatly, we highly recommend testing the configuration and increasing allocated memory (and CPU cores) if you are seeing performance issues that you suspect are due to low resources.
Please Note: Somewhat counterintuitively, more is not always better; allocating the host of the Application Server an excessive amount of total system memory can in some cases have a deleterious effect on performance. PaperCut NG and PaperCut MF are Java applications, and hence subject to Java “garbage collection” activities, which maintain proper memory allocation. When a great deal of memory is available to the Application Server, full garbage collections will happen less frequently, but take longer to complete. The application must pause temporarily whilst these operations complete, so if the amount of memory available is imbalanced by a comparatively small amount of CPU resources, this may be observed as periodic spikes in highly unresponsive behavior. If unsure of the appropriateness of your resourcing, our Server Sizing Guide can be invaluable to check with.
Increasing Maximum Memory (Windows/Linux/iPrint)
To increase the amount of memory available to PaperCut NG or PaperCut MF:
1. Locate the text file called service.conf in the following directory:[app-path]\server\custom\
Please Note: If you’re running a version of PaperCut NG or PaperCut MF prior to 17.3, you will instead need to create the service.conf file in the directory noted above.
2. Open the file in a text editor and add the following line to allow the application to employ up to one third of total physical RAM:
wrapper.java.additional.6=-XX:MaxRAMFraction=3
To employ up to one half of total physical RAM, use the line:
wrapper.java.additional.6=-XX:MaxRAMFraction=2
You may also specify the precise amount of physical RAM to use. For example, to allow use of up to 768 MB, the following line can be added:
wrapper.java.additional.6=-Xmx768m
3. Save and close the text file.
4. Restart the PaperCut Application Server service. On Windows, this can be done via Control Panel->Administration Tools->Services by locating the PaperCut Application Server in the list of system services, right-clicking, and selecting to Restart it.
5. After the service is restarted, the Application Server log file ([app-path]\server\logs\server.log) will show the new “max memory” setting.
Increasing Maximum Memory (macOS)
Please Note: This method only works on version 9.6 and higher of PaperCut NG and PaperCut MF.
To increase amount of memory available to PaperCut NG or PaperCut MF on macOS:
1. Locate the text file called launch-app-server.conf in the following directory:[app-path]\server\custom\
Please Note: If you’re running a version of PaperCut NG or PaperCut MF prior to 17.3, you will instead need to create the launch-app-server.conf file in the directory noted about. Be sure to change the file permissions to make the file readable to all users, or at minimum, the papercut host user account.
2. You will need to specify the amount of system memory available to the Application Server. Open the file in a text editor and add the following line to allow the application to employ up to, for example, 256 MB of physical RAM:
PC_CUSTOM_SERVER_ARG=-Xmx256m
For up to 512 MB of physical RAM, you would instead use the line:
PC_CUSTOM_SERVER_ARG=-Xmx512m
3. Save and close the text file.
4. Restart the PaperCut Application Server service by running the stop-server.command script and then the start-server.command script, both located in the following directory:[app-path]/server/bin/mac/
5. After the service is restarted, the Application Server log file ([app-path]\server\logs\server.log) will show the new “max memory” setting.
Running out of Memory or High CPU Usage
If PaperCut NG or PaperCut MF run out of memory, an OutOfMemoryError will be displayed to the user and/or logged to the service.log file. You may also see GC overhead limit exceeded error, which is again an indication of running out of memory.
Another indication of running out of memory is very high CPU usage for extended periods of time, by the pc-app process/service, as the service tries to rearrange RAM for various tasks.
If this occurs then this is an indication that the server requires more memory, and
there are two possible solutions:
Allocate more RAM to the server.
Increase the maximum amount of memory available to the Application Server, as described above. This should typically only be done if there are no other applications deployed to the same server, or if recommended by the Support Team.
Now, having shared that, the issue also appeared related to how the vNIC was being handled by the VM servers situated on the host. Possibly two extremely different issues, but both still causing problems first thing on a Monday morning.
The issue specifically related to the VM print server being inaccessible via RDP and being unable to be pinged. It could, however, be accessed via SCVMM and Hyper-V manager through the console. Strange, right?
Rebooting the server failed to immediately address the problem, so we set to triaging after sending out an announcement to the affected user base.
After discussing as a team, turns out this had been seen elsewhere recently and it was indeed a vNIC issue. What resolved the clear and present trouble was to shut down the VM and go into Hyper-V Manager >> right-click on the given server >> Settings...
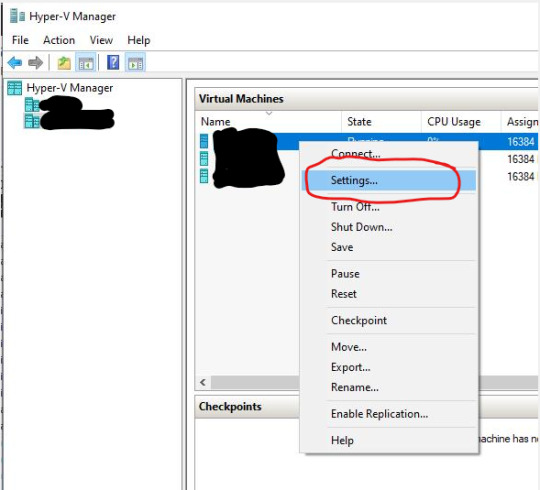
>> Under Settings >> Network Adapter Options >> Change it from Global Converged Fabric Switch to Not Connected >> Click Apply and OK
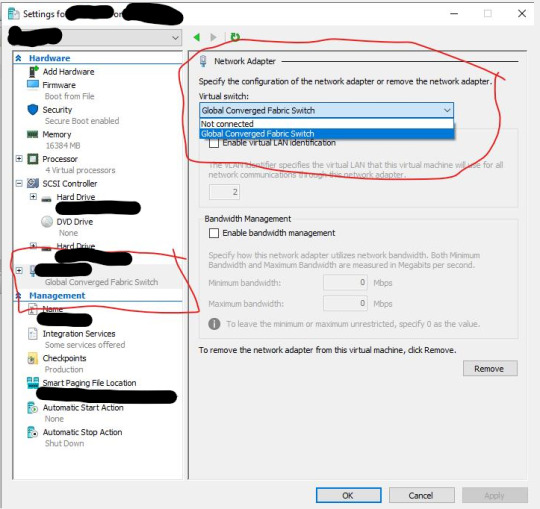
then shut the VM down (it won't matter since the VM is on the fritz anyway, right?) Great.
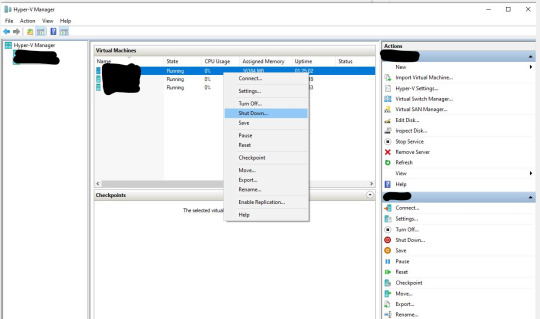
Once the VM has been shut down, change it back to Global Converged Fabric Switch and power the VM back up in Hyper-V Manager.
This should resolve the issue and can be checked and confirmed by running ping SERVERNAME -t in CMD or using test-connection -ComputerName SERVERNAME, connecting to the VM via RDP, or attempting to access the offending resource once the VM is back up and you've been able to log into it using your Windows account.
Once that's been done, have users check and confirm whatever resource they were attempting to access is working in a satisfactory manner.
#Windows Server#Server 2016#Server 2019#Windows Server 2016#Windows Server 2019#Print Server#PaperCut#Network Printers#Hyper-V#hyper v#SCVMM#RDP#Remote Desktop#Hyper-V Manager#System Admin#system administration
0 notes
Text
Defending against ransomware using system design
This post is authored by Michael Melone, Principal Cybersecurity Consultant, Enterprise Cybersecurity Group.
Earlier this year, the world experienced a new and highly-destructive type of ransomware. The novel aspects of WannaCry and Petya were not skills as ransomware, but the combination of commonplace ransomware tactics paired with worm capability to improve propagation.
WannaCry achieved its saturation primarily through exploiting a discovered and patched vulnerability in a common Windows service. The vulnerability (MS17-010) impacted the Windows Server service which enables communication between computers using the SMB protocol. Machines infected by WannaCry propagate by connecting to a nearby unpatched machine, performing the exploit, and executing the malware. Execution of the exploit did not require authentication, thus enabling infection of any unpatched machine.
Petya took this worming functionality one step further and additionally introduced credential theft and impersonation as a form of worming capability. These techniques target single sign-on technologies, such as traditional domain membership. This added capability specifically targeted enterprise environments and enabled the malware to use a single unpatched endpoint to springboard into the network, then used active sessions on the machine to infect other machines regardless of patch level. To an enterprise, a single unpatched endpoint paired with poor credential hygiene could be used to enable propagation throughout the enterprise.
Most impersonation and credential theft attacks are possible only when malware obtains local administrator or equivalent authorization to the operating system. For Petya, this would mean successful exploitation of MS17-010, or running under the context of a user with local administrator authorization.
Measuring the value of a user account
To a hacker, an infected or stolen identity is measurable in two ways: the breadth of computers that trust and grant authorization to the account and the level of authorization granted upon successful authentication. Since encryption can be performed by any user account, ransomware benefits most when it infects an account which can convey write authorization to a large amount of data.
In most cases (thus far), the data sought out by ransomware has been either local files or those accessible over a network attached share data which can be accessed by the malware using out-of-the-box operating system interfaces. As such, data encrypted by most ransomware includes files in the users profile, home directory, or on shared directories where the user has access and write authorization.
In the case of WannaCry, the identity used by the ransomware was SYSTEM an effectively unrestricted account from an authorization perspective. Running as SYSTEM, WannaCry had authorization to encrypt any file on the infected machine.
Petyas encryption mechanism required the ability to overwrite the boot sector of the hard drive to invoke its encryption mechanism. The malware then creates a scheduled task to restart the machine at least 10 minutes later to perform the encryption. The offline encryption mechanism prevented destruction of network files by Petya.
Infected machines and worms
Pivoting our focus to the worm aspect of these ransomware variants, the value of an infected host to a hacker is measurable in two ways: the quantity of newly accessible targets resulting from infection and the data which now becomes available because of the infection. Malware with worming capability focuses on widespread propagation, thus machines which can access new targets are highly valuable.
To both WannaCry and Petya, a newly infected system offered a means to access previously inaccessible machines. For WannaCry, any potential new targets needed to be vulnerable to MS17-010. Vulnerability gave both malware variants SYSTEM-level authority, thus enabling successful execution of their payload.
Additionally, in the case of Petya, any machine having reusable credentials in memory furthered its ability to propagate. Petya searches for active sessions on an infected machine and tries to use the session to infect machines which may not have been vulnerable to MS17-010. As a result, a single vulnerable endpoint may expose a reusable administrative credential usable to infect potential targets which grant that credential a necessary level of authorization.
Codifying the vulnerability
To defend against a ransomware application with worm capability we need to target the following areas:
Ransomware
Reduce the authorization level of users relative to the operating system of an infected machine
Perform backups or versioning of files to prevent loss of data due to encryption, deletion, or corruption
Limit authorization to delete or tamper with the data backups
Worms
Reduce the ability for an infected host to access a potential infection target
Reduce the number of remotely exploitable vulnerabilities that provide remote code execution
Reduce exposure of reusable credentials relative to the likelihood of a host to compromise
Resolving Concerns through design
Many of the risks associated with ransomware and worm malware can be alleviated through systems design. Referring to our now codified list of vulnerabilities, we know that our solution must:
Limit the number (and value) of potential targets that an infected machine can contact
Limit exposure of reusable credentials that grant administrative authorization to potential victim machines
Prevent infected identities from damaging or destroying data
Limit unnecessary risk exposure to servers housing data
Windows 10, BYOD, and Azure AD Join
Windows 10 offers a new management model that differs significantly from traditional domain joined machines. Azure Active Directory joined machines can still convey identity to organizational resources; however, the machine itself does not trust domain credentials. This design prevents reusable accounts from exposure to workstations, thus protecting the confidentiality of the credential. Additionally, this limits the impact of a compromised domain account since Azure AD joined machines will not trust the identity.
Another benefit of Windows 10 with Azure AD is the ability to move workstations outside of the firewall, thus reducing the number of potential targets once infection occurs. Moving endpoints outside the firewall reduces the impact of any workstation threat by reducing the benefits normally gained by compromising a machine within the corporate firewall. As a result, this design exposes fewer server ports to potentially compromised endpoints, thus limiting the attack surface and reducing the likelihood of worm propagation.
Moving workstations outside of the firewall offers added security for the workstation as well. Migrating to a BYOD architecture can enable a more stringent client firewall policy, which in turn reduces the number of services exposed to other hosts, and thus improves the machines defense against worms and other inbound attacks.
Additionally, most organizations use many laptops which often connect from untrusted locations outside the firewall. While outside of the firewall, these machines can connect to untrusted sources, become infected, then bring the infection inside the firewall next time it is able to connect to the internal network. This causes confusion when trying to identify the initial infection during an incident response, and potentially exposes the internal network to unnecessary risk.
Consider migration file shares to OneDrive or Office365
Migrating data from traditional file shares into a solution such as SharePoint or OneDrive can limit the impact of a ransomware attack. Data stored in these technologies can enforce version control, thus potentially simplifying recovery. To further protect this data, limit the number of SharePoint users who had administrative authority to the site to prevent emptying of the recycle bin.
Ensure resilient backups
When an attack occurs, it is crucial to ensure ransomware cannot destroy data backups. Although convenient, online data backups may be subject to destruction during an attack. Depending on design, an online backup solution may trust a stolen reusable single sign-on credential to enable deletion or encryption of backup data. If this occurs, backups may be rendered unusable during the attack.
To prevent against this, consider Azure Cloud Backup a secure off-site backup solution. Azure Cloud Backup is managed through the Azure Portal which can be configured to require separate authentication, to include multi-factor authentication. Volumes used to store backup data reside in Azure and cannot be initialized or overwritten using on-premises domain credentials.
Closing
Windows 10 and BYOD architecture offers significant defense against a variety of cyberattacks, to include worms and ransomware. This article covers only some of the protections that Windows 10 offers against credential theft, bootkits, rootkits, and other malware techniques employed by this class of highly destructive malware.
To better defend your organization against future malware outbreaks:
Prepare to migrate client machines to Windows 10
Plan for BYOD device management using Microsoft Intune and Azure AD joined machines
Implement Azure Backup to provide a resilient and malware-resistant backup solution
Learn how Windows Defender Advanced Threat Protection (ATP) can help your organization quickly detect and respond to malware outbreaks
from Microsoft Secure Blog Staff
0 notes
Text
Windows 8 Technical Support Phone Number
Windows 8 issue in PC Configuration?
These days, in the event that anyone needs a working framework for PC then Windows 8 comes at the essential position.This is on account of it offers stunning elements which are utilitarian for both authority undertakings and individual use.Sometimes, the arrangement issue rises when Windows 8 demonstrates mistake screen on startup. To annihilate entanglements, check the PC determination identified with processor, memory and working framework. In spite of the fact that it is anything but difficult to check PC specs however in the event that you require any assistance at that point take direction from our specialists.
Clients confront some regular inconveniences in Windows 8 which are examined as:-
Dark Screen – It happens when we persuasively kill the PC and restart again.It decides the past restart endeavor was not effective.
Issue with POP3 mail Email Accounts-Windows 8 is not good with the POP mail so it doesn't bolster them. Utilize an alternate email application, for example, Gmail, Yahoo to check POP mail.
Neglect to arrange window refreshes When you attempt to introduce Window refresh then you can see falling flat messages.To settle this, restart Windows and introduce refreshes in a perfect boot state.Don't neglect to unplug removable media before restarting the procedure.
Evacuate Windows Warning Error - If your PC is tainted with infection then such undesirable bugs occur.It is important to expel such malware in light of the fact that that can meddle with PC's typical startup succession.
Windows 8 slamming - Blue screen happens when windows have smashed because of driver compatibility.Although, windows get rebooted naturally after the blue screen of death occurs.To settle this, tap on Troubleshoot in Advanced Startup option.Now tap on Startup settings and go to Safe mode. For more data, squeeze Windows key + X and open Event Viewer.In this segment, you can without much of a stretch distinguish application and framework issues.
How about we talk about a couple of strategies to determine Windows 8 irritations:-
1)If you are confronting booting mistakes at that point take a stab at handicapping half and half boot. Tap on Start and sort Power Settings.Now pick settings and make a tick on "Change what the power catches do" option.Now tap on "Change settings that are at present inaccessible" option.After this, uncheck the Turn on quick startup choice and spare changes.
2) You can introduce Windows 8 utilizing installer circle or USB drive.Go to Troubleshoot screen and tap on Refresh PC option.This will reset framework record into default state and fix the booting botches.
3 ) Use Automatic Repair is a recuperation include which is utilized when Windows 8 does not begin typically. To begin the recuperation procedure, go to Start Screen and scan for an Advanced option.Now go to Settings tap on Advanced Startup Option.Go to general PC setting screen and pick Advanced Startup.Now tap on Restart choice and you will see Advanced Startup menu.Select Troubleshoot alternative and tap on Advanced options.When the screen opens, tap on Automatic Repair.During the repairing procedure, PC may reboot.However, this strategy will take a considerable measure of time and the client needs to keep up some patience.After this, you can close down or begin another apparatus.
Is it true that you are searching for Windows 8 Technical Support? Connect with Windows 8 Technical Support Phone Number that is accessible for 24x7 and 365 days in a one year to help overall clients. Our designers have colossal information and this is the reason they have the arrangement of each irritation. We have a prepared group that send monstrous help benefits over online talks, calls, emails.Just feel free in interfacing with us.
0 notes