#so for example if you have a camera login that is just admin and a generic password like Admin
Note
so i’m gonna need the crazies to hack into the airport cameras ASAP
😂😂see him like a little tiny blurry creature with the tiniest bag because he packed nothing and wants to just borrow dreams clothes
#ask#before I get any worried nancies in my ask box#as a cyber security hobbyist#it is not easy to hack into cameras unless they are on public addresses or the wifi that the camera is attached to has been breached before#what people tend to do is they get a list of cracked passwords and find ip addresses and run that shit with a generic user#so for example if you have a camera login that is just admin and a generic password like Admin#and keep the camera in stock default#it would be easy to hack into IF the person has the ip address for the camera#also all of the above that ive said could be wrong or off by a bit this is just from what ive read and picked up over the years#no one in this fandom has the know how or the energy and there is like 99 chance u wont even see gnf lmao
1 note
·
View note
Text
Protect Your Browsing/Data Sharing
For free, because in this house I don’t believe in making people pay for basic human rights.
I’ve decided to share my browsing protecting tips here. Digital security is usually quite expensive, but it doesn’t have to be! In this day and age, you’ll be told to watch out for home-born hackers and ‘hacktivists’ accessing your data, but I gotta tell you, what your own governments and ISPs are doing makes this more important (aka: they’re worse).
I know with all the TIKTOK IS SPYING ON YOU stuff, a lot of my friends have come to me seeking some advice on this. This is also great if you don’t want parents checking your browsing >_> just sayin’
If anyone has questions - drop me an ask! I’ll always answer for this topic. I am also happy to ‘expand’ on one of these suggestions if they’re unclear :)
Note: This works under the assumption you have your default ISP provided router and can’t get another one for whatever reason. I will advise that if you can get an additional router, do so! Try to avoid the one the ISP has provided to you.
Additional Note: This is not ‘optimal’. There is no such thing in security – everything has a backdoor.
Let’s get cracking! This is a long, and thorough post, but I _do _have a pdf somewhere if you want it because it looks nicer :*)
Use Tor to browse.
There you go, there’s my advice leaves
https://support.torproject.org/ to Download/Install/Run.
Don’t change anything, except maybe using Tor in ‘bridge’ mode.
Okay, you can use other browsers (see: Chrome/Firefox), but they are not as secure as Tor.
USE A VPN IF YOU ARE GOING TO USE TOR! I prefer Firefox (extensions + good security)
________________________________________________________________
Install the following extensions if you have Chrome or Firefox:
Privacy Possum
Stops tracking cookies. PSA: Cookies are not evil, certain cookies can be.
Firefox: https://addons.mozilla.org/nl/firefox/addon/privacy-possum/
Chrome: https://chrome.google.com/webstore/detail/privacy-possum/ommfjecdpepadiafbnidoiggfpbnkfbj
Ghostery
Stops tracking adverts and cookies. Why do I need this in addition to Privacy Possum? Ghostery specifically looks at tracking cookie ads. It’s like adding MOAR POWAH to Privacy Possum.
Firefox: https://addons.mozilla.org/nl/firefox/addon/ghostery/
Chrome: https://chrome.google.com/webstore/detail/ghostery-%E2%80%93-privacy-ad-blo/mlomiejdfkolichcflejclcbmpeaniij?hl=nl
HTTPS Everywhere
Enforces HTTPS. If you look next to the URL in your browser, you’ll see the little lock which indicates the specific URL is secure and uses HTTPS. Many websites still use the old HTTP, which is not as secure and you should NEVER EVER VISIT AN HTTP SITE ITS LIKE READING A BOOK OVER SOMEONE’S SHOULDER, thank you.
Firefox: https://addons.mozilla.org/nl/firefox/addon/https-everywhere/
Chrome: https://chrome.google.com/webstore/detail/https-everywhere/gcbommkclmclpchllfjekcdonpmejbdp?hl=nl
Adblock Plus
Foff, ads.* Firefox: https://addons.mozilla.org/nl/firefox/addon/adblock-plus/
Chrome: https://chrome.google.com/webstore/detail/adblock-plus-free-ad-bloc/cfhdojbkjhnklbpkdaibdccddilifddb
________________________________________________________________
DNS Settings
Ideally, you should change this on your router. ISPs use a default DNS – you don’t want to use anything those bastards say you should use.
Use Cloudflare or OpenDNS:
Cloudflare is more secure overall and keeps up to standards in addition to not storing your data, whereas OpenDNS is great at avoiding malicious websites, just take your pick really 😊There are a ton of other options, feel free to google ‘free DNS servers’. Google has it’s own as well, but, yaknow, it’s Google.
Cloudflare
Primary Server: 1.1.1.1
Secondary Server: 1.0.0.1
OpenDNS
Primary Server: 208.67.222.222
Secondary Server: 208.67.220.220
Add these to your router settings:
In a browser, go to http://192.168.1.1/ or http://192.168.1.0/ (it varies per router). This will lead to your router’s configuration portal. Don’t have a router with a configuration portal? Throw it in the trash and tell your ISP they suck for giving it to you.
Login to the admin portal. If you have not configured this or set a password, try the default combinations: usernames are usually ‘admin’ or blank, the passwords are usually blank, ‘admin’, or ‘1234’.
Each router is different, navigate to where it asks for DNS values or servers, and enter the above addresses. You will see ‘Static’ near the DNS options, select it. This also ensures you’re in the right place. If you’re not sure what to do, look up the model/make of your router and check how you can change DNS.
Whilst you’re at it, change your WiFi password from the default one, and create a proper password for the WiFi portal login. If these two things are kept as default, all these protection methods are pointless as it is easy to crack your router passwords.
Can’t do this on your router because your parents are ds?* No worries! This can be done on your device! :) Yeah, I know how parents work.
Windows OS
Go to Control Panel <Network and Internet < Network and Sharing Center
Click on the link next to “Connections:”* Click “Properties” in the dialogue that pops up.
Select Internet Protocol Version 4 < Click Properties < Select “Use Following DNS Servers” < Enter the primary and secondary server addresses
Do this again for Internet Protocol Version 6 in the list.
Boom. Windows is so nice to make this easy.
Mac OS
Go to Apple Menu < System Preferences < Network
Select the Network you’re connected to
Click Advanced
Select DNS Tab
Click the + button < Enter chosen DNS < Save
Linux OS
I’m going to assume if you’re using Linux, you know how to use the terminal and are using a modern Linux system. Enter these line by line. There are many ways to do this (Google is your friend)
· sudo apt update
· sudo apt install resolvconf
· sudo systemctl status resolvconf.service (check that it is running)
· sudo systemctl start resolvconf.service (to start it, use ‘enable’ instead of ‘start’ to enable)
· sudo nano /etc/resolvconf/resolv.conf.d/head
· nameserver YOUR.DNS.ADDRESS.HERE
· nameserver YOUR.SECOND.DNS.ADDRESS.HERE
· sudo systemctl start resolvconf.service
Android
Oh yeah, you can do this on phones too wiggles eyebrows. Note, if you’re using a VPN it will lock you out of editing this. Turn it off, edit your DNS, turn it back on. This can be tricky with mobile devices that have not been jailbroken (I don’t advise doing that if you have no clue what you’re doing).
Go to Settings < Connections < WiFi
Select the gear icon next to your current WiFi
Select Advanced < Ip Settings drop-down < Static
Enter chosen DNS options under “DNS 1” and “DNS 2”
iPhone
Go to Settings < Wi-Fi
Select the arrow button next to your current WiFi
Select DHCP tab, scroll down to DNS
Select DNS, and enter your DNS servers
TEST YOUR DNS IS WORKING:
OpenDNS: https://welcome.opendns.com/ (You’ll see a “Welcome to OpenDNS” message”
Cloudflare: https://www.cloudflare.com/ssl/encrypted-sni/ (You’ll see check marks for all fields)
________________________________________________________________
Turn of WPS on router. Enable encryption on router.
If you can access your router portal, find any sort of toggle or field that says “WPS” and disable it. WPS= bad.
Wherever there is an option for WPA2 (or higher) to enable, enable it.
Enable the firewall on your router and Operating System – ALWAYS. If you disable this, you’re disabling an additional layer of security. Firewalls are confusing things and a royal pain in the ass to configure, but having the default is better than having nothing.
________________________________________________________________
Configure your browsers.
Browsers have most things enabled by default, including tracking your location, turning your microphone on etc. Let’s disable that nonsense and make them ask you for permission because it’s 2020.
I’m using Chrome as an example below because it is INFAMOUS for this. Essentially, go through your browser and scroll through settings you don’t like.
Go to the little menu icon < select “Settings”
Sign out if it’s linked to your Google account. Let’s not give Chrome a reason to track your browsing history for your account >_>* Disable EVERYTHING:
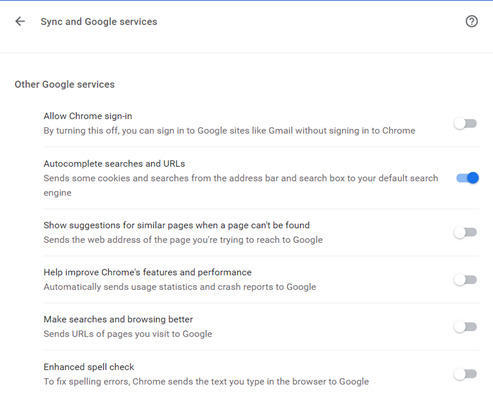
Here, I turned off everything I would find annoying except autocomplete because I’m lazy.

NICE TRY GOOGLE, YOU CANT SAVE MY CREDIT CARD. (Seriously, don’t ever EVER autosave passwords/payment info).

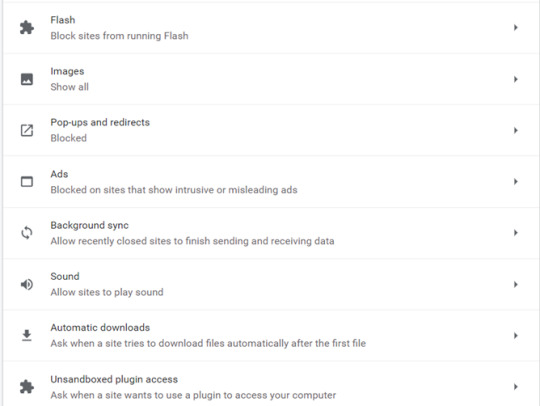
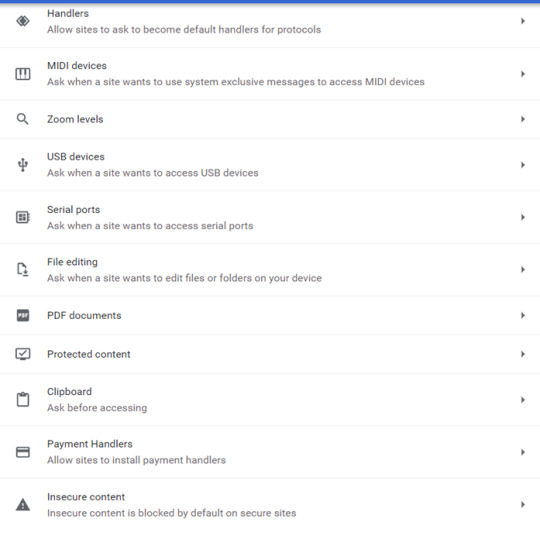
The trick is to balance ease of use with security. These may vary from person to person, in general though, if there’s a setting ‘ask before etc.’ select that over ‘allow’.
As a rule of thumb:
NEVER ENABLE FLASH (not even an ‘ask before’), NEVER ENABLE LOCATION (ask before is fine, but at your own risk), NEVER ENABLE CAMERA (ask before is fine, but at your own risk, use the desktop version of an application over the browser version), NEVER ENABLE MICROPHONE (same as camera)
________________________________________________________________
Additional Tipss
Check every single social media setting. You should disable anything that accesses your privacy, if possible.
Cover your camera with a sticker. Disable it unless it’s needed
Disable your mic unless you need it.
Turn off Bluetooth/NFC when you don’t need it.
Have two separate networks/Wi-Fi for smart devices and personal devices.
Always use two/multi-factor-authentication for every single app, site, device etc. that you can.
Biometrics are preferable and the usual chosen default (fingerprints, retina scan, NOT FACE OR VOICE THIS IS SO EASY TO IMMITATE BRO PICTURES ARE A THING)
SMS (try to avoid if you can, please)
App ‘token’ authentication. A good choice if done well.
Hard physical key or token. The best option (Google: Yubikey, for some information on how this works).
Passwords
I know you use the same password for everything – get a centralized password manager, and start using different ones. Examples include PasswordSafe, Keeper, Bitdefender etc. Try go for a Cloud provider, and pay a little bit for the extra security and backup. If they’re compromised, then you will know, and you’ll be able to change everything. You can tie password managers to a token too.
USE PASSPHRASES, 17 characters is a good average length, use a mix of characters, uppercase, lowercase, numbers, ascii etc.
It doesn’t matter if your password is ‘complex’, it matters if it is complex and long. Servers and computers these days are jacked up on tech steroids and can bruteforce many things, given enough time.
Anti-virus.
EVERYONE SHOULD HAVE ONE, ON EVERY DEVICE. If you have a device that can add AV, add it. This goes for phones, PCs, smartTVs, you name it.
Free versions are okay, some free ones I like are Bitdefender, Kaspersky, McAfee, Avast (hate their fihsfirstg89ewjg9srjgrd ads though).
Sorry Mac users, that belief that you don’t need one is from 2008. Windows has more security built in than Mac, which means Mac devices should 100% make sure they are adding an AV.
VPN
Ahhhhh. The great VPN. A tricky one. Most free versions I find incredibly slow, but give them a try – play around! A VPN is an excellent addition and these days, I’d argue it’s an absolute must. Many AV solutions include a VPN package with their deal. If you want to make sure those sites don’t share your data, this is the thing that will hurt the most - a good VPN will make it a jumbled mess.
Updates - just do them.
There is no complete security in this day and age – it really is just a matter of time. If you use social media, you’re traceable, be it by the company, ISP, some bored 10 year old, or your ex, your data is out there circulating. Once it’s on the internet, it’s there forever, so don’t worry too much and try to make sure it’s all complex binary trash so that they open it and go “WTF” 😊
#tiktok#security#it security#data#data privacy#private browsing#facebook#google#data theft#third party ad#ads#secure browsing#protect data
10 notes
·
View notes
Text
Android & IOS Slot Sport On Cell
What You Stand To gain With 918kiss Obtain
Although there are on-line slot video games in all places internationally, Malaysia is a haven for on-line recreation lovers. There are also scatters and wild multipliers that can enhance your profitable odds. Should the promotional rollover requirements above not be met within 30 days from the bonus claimed, the bonus and winnings attributable will likely be forfeited. The most typical sign up bonus is the deposit best on-line casino welcome bonus bonus, which is the last word bankroll increase for newcomers! What are the very best successful tips for 918Kiss online casino? They serve their worthwhile prospects at their finest. Additionally what sources will I need to attain them? Players no longer need to fill any hardcopy type to register for a new account. All ECWON Players are entitled to 0.60% rebate based mostly on their total amount wagered in in all ECWON slot video games besides HUNT FISH products. These are solely among the profitable customer winning huge amount of cash utilizing 918Kiss Stay.
youtube
Very few with all of the 918kiss slot games , Joker Slot Sport which is likely to be free have winnings in relation to money and prizes. In truth, we’re giving the cash in credit to you. If not, you possibly can at all times register as a brand new member and claim the new member bonus as we are also giving out the extra bonus for new members during your first deposit to our casino. The free credit given could possibly be more than RM 190.00. It's price to try and test it out! Since it's free credits, normally the on line casino may request 30 times more turnover for the proceeds when making the withdrawal. You'll be able to ask for the 918Kiss Live Chat group to assist your registration process and request for ID and password. Apart from that, for the new player registration. Clicks ship and your registration is full. As well as, the 918Kiss Test ID and the 918Kiss Free Play are the identical things. The same outside bets are available; akin to, red or black, even or odds, 1-12 or 13-24 in addition to column and dozen bets. Would like it, are typically the identical means. After you have downloaded the software program for the 918Kiss hack, simply use it on the 918Kiss free obtain app.
The extra credit are permitting the gamers to have extra wager to place into the video games. And the Casino is including the slot video games more than other video games. Gamers only download the games at their alternative, so the storage area of their cellphone won’t go to waste. It also won’t take that long. Given the extreme demand on cellular scr888 free credit for new member on-line taking part in merchandise SCR888 On-line Casino has develop a cellular primarily primarily based on-line betting software program. 918Kiss online casino gamers stand to win a minimum of one thousand free credit. These players don’t observe a strategy or even simple directions to play them, which provides them enormous losses. However when you hit the 3 or 4 streaks, please restart this technique once more. Quite a few individuals have been scanning for tricks to always win from 918kiss amusements. To scan the code, you might have to make use of the device’s camera and face the camera to the code.
It is very important to make use of photos in your website to carry up the primary ideas of your website. Bear in mind that you must at all times download 918Kiss from the official web site. On the 918Kiss Casino, it will likely be a bit uniques that couldn’t register the 918Kiss login ID from the mobile utility or their Web page. Additionally, 918kiss will never share your details with any third get together without your consent. Should you fail to do so, you fail to be 918Kiss admin. Even this 918kiss Dolphin slot is sort of basic, it have many degree of bonuses for gamers. Dangerous types of debt are often utilised to acquire goods and services which haven't any lasting price. They've designed a strong and highly stable safety system to stop hackers from hacking their centralized on-line betting system. Throughout these few months, he managed to win RM3-4k consistently from 918Kiss on month-to-month foundation. Be taught from good examples, not the dangerous one, this is how we can improve and win. On this web page you'll find 918Kiss MY Slots App apk element and permissions and click obtain apk button to direct download 918Kiss MY Slots App apk. This really helps them a lot once they want to introduce this app to their friends.
Joker338 merupakan agen SCR888 Indonesia yang akan membantu anda untuk melakukan registrasi SCR888 secara gratis , cepat dan juga aman. The opportunities of successful a jackpot on 918kiss can be higher. 918kiss online login is trigger randomly after any ending of the sport. Unable to play your favourite sport without waiting to your flip? Second, play the very best winning odds video games. Fewer mistakes will definitely enhance their successful odds in the video games. Meaning, you won't be allowed to withdraw stability sport credit score for financial advantages at all time. The Be aware eight comes with a 6GB ram so pace won't ever be a problem to its customers. What's the online on line casino GoWild? In addition to that, in Malaysia, that’s the net On line casino Assessment Site. After going through all the points mentioned above. After the obtain, just proceed with the installation and you are able to go. Heard players complain that upon installing 918Kiss IOS on their cellular device, it was not working. This is very convenient for the players. That's dwell recreation and slot recreation. It represents the most popular game on the web. The craze of playing slots could be very a lot in people.
1 note
·
View note
Text
A Roundtable of Hackers Dissects ‘Mr. Robot’ Season 4 Episode 1: ‘Unauthorized’
It’s been one year, nine months, and 23 days since the sizzling season 3 finale of Mr. Robot, and the show is back for its last season.
This week, we discussed [SPOILERS, obvs] the probability of getting an envelope with a ringing dumb phone with a hacker on the other end of the line, dead man’s switches, hacking cameras at Grand Central Station, and honeypot houses. (The chat transcript has been edited for brevity, clarity, and chronology.) This week’s team of experts include:
Emma Best: a former hacker and current journalist and transparency advocate with a specialty in counterintelligence and national security.
Bill Budington: a long-time activist, security trainer, and a Senior Staff Technologist at the Electronic Frontier Foundation.
Jason Hernandez: Solutions Architect for Bishop Fox, an offensive security firm. He also does research into surveillance technology and has presented work on aerial surveillance.
Harlo Holmes: Director of Digital Security at Freedom of the Press Foundation.
Micah Lee: a technologist with a focus on operational security, source protection, privacy and cryptography, as well as Director of Information Security at The Intercept.
Freddy Martinez: a technologist and public records expert. He serves as a Director for the Chicago-based Lucy Parsons Labs.
Matt Mitchell: a hacker and Director of Digital Safety & Privacy at Tactical Tech. He founded cryptoharlem, which aims to teach basic cryptography tools in the inner city.
Christina Morillo: a New York City-based information security and technology professional working as an information protector on Microsoft’s cloud & engineering security team.
Zachary Julian: Security Associate at the security consulting firm Bishop Fox.
Freddy and His Package
Yael: Are there instances where you get a package with a ringing phone, or is that just in TV/the movies? Like has that happened in real life?
Harlo: I don’t know about in real life, but this is a thing in Black Mirror, and American Vandal.
Micah: For it to happen, Elliot would have had to be tracking the package and waiting outside the building to know exactly when to make the call. Which he was.
Emma: If the phone had GPS enabled, Elliot could have tracked it and known when it arrived, assuming there wasn't already a webcam compromised in there. Elliot also could have been listening in through the phone’s microphone in real-time. He hears the phone arrive. Hangs up. Dials back.
Bill: I'm assuming Elliot had either delivery confirmation or a GPS unit to know when the phone and video was delivered.
Micah: I don't think he would have needed GPS. He could have just watched delivery person enter the building with the package, and as soon as they left the building made the call.
Emma: True, Micah. Even simpler, he had an in-progress call to the phone going.
Jason: There are Android apps that will trigger sending a text or whatever when they're in proximity to a given Wi-Fi access point or at a certain latitude / longitude. It's pretty simple to set up.
Matt: Tasker app does this.
Harlo: It doesn't seem to be Android. It's a dumb phone (probably a Tracfone or something similar). So it's likely Elliot has it tracked via… maybe skip tracing?
Bill: Yeah, it looked like a dumb burner phone.
Micah: I think it was like a pay-with-cash Tracfone, which is the smart way to do it anonymously anyway.
Freddy: The simplest explanation is that he had someone else watching him and tracking the dude and reporting back.
Yael: What's a Tracfone?
Harlo: It's a brand of pay-as-you-go phones you can buy from pharmacies, 7-11s and other places. it has only mobile text and voice; no data.
Micah: It’s just one of several types of cheap phones you can purchase at corner stores in cash. You don't need ID or credit card or anything, and they have fairly cheap options with old flip phones, even today.
Matt: Buying a Tracfone with cash, buying service for it with cash, and then not talking when you call the service number to set it up is a pretty anonymous way to get a U.S. cell phone.
Harlo: I agree with Emma that the easiest way might be keeping a live call on during delivery, then listening for the pick-up. Or having actual surveillance on the office. Or maybe even tapping into any video surveillance on premises.
Yael: He had access to Freddy’s screen too, right?
Bill: I don't think he had access to the screen… maybe he just saw via binoculars that he was watching the video.
Yael: Okay so flash forward to the call. So then Mr. Robot/Elliot is trying to get Freddy to click on a phishing link (which he thought was ransomware, but it wasn’t)—and to copy the .pst file in his inbox to the thumb drive. How does that work?
Micah: Since Freddy was copying the .pst file himself, and not the malware, my guess is clicking the phishing link was simply to get malware on the law firm's network for future use.
Harlo: Maybe this is either 1) a diversion for the IT admin to not notice the immediate export/download of an employee’s entire inbox, or 2) one of those things where you gotta hack the admin to complete the exploit.
Zach: It seems like the malicious link was just to provide an excuse as to why the inbox was compromised.
Freddy: If he had network access, he would just dump the active directory [a Windows service that controls access to shared resources on a network, like user logins and credentials], but the point of the plot was to incriminate the lawyer. It wasn’t about getting the emails. It was about incrimination.
Jason: Owning active directory usually takes a while and it can be kind of a hassle.
Micah: Elliot did need the emails to find all the banking details he needed.
Harlo: But if you want to hide your involvement, you're also pinning it on the mark who "clicked a link, oops totally not an orchestrated op by Mr. Robot."
Freddy: The way to get the emails isn’t really how you would do it if you already have malware on the network.
Micah: PST files are an Outlook inbox. A lot of the big email leaks that get reported on start out as a PST file. He was using a cool tool to import them and search through them, "Expansion Inbox," which I've never heard of.
Yael: So shout out to Iceweasel! We saw it on Elliot’s laptop on the train.
Bill: Debian's Iceweasel had resolved its naming issues with mainline Firefox in early 2016 but remember this is still in late 2015. So they're staying true to the time period.
Yael: Is Iceweasel like an open source Firefox? Wait, isn't Firefox open source?
Micah: Firefox is open source, but there was a trademark conflict for use of the "Firefox" name and logo inside Debian. Debian handled it by just renaming it to Iceweasel and providing their own logo.
Dead Man’s Switch
Yael: Elliot said he could get the videos to send to Freddy’s kids and the FBI… like a dead man's switch…
Micah: OnionShare has a dead man's switch feature. You can set a time in the future to start sharing files, and it gives you the Tor onion address right away. It wouldn't work for this exact use case, but you could, for example, tweet an onion address and a date, and if you don't manually close OnionShare before that date, it automatically starts sharing whatever data you want.
Emma: A dead man's switch would be super easy to set up. Have a couple of computers running a check every 10 minutes on a data file, see if it's been 24 hours yet. If it has, send the emails. If not, check again in 10 minutes. The email doesn't have to have the data, just a key and instructions on how to access it. The data can be anywhere. Elliot could check in with infected machines via a command and control system and reset the clock in the data file. The data could be stashed on some random server. The email to the FBI could contain the target’s IP address, user/password and decryption key. The files would be too large to just send to the FBI directly, and if they were forcibly dropped on an FBI system, they wouldn't touch it. But of course, Elliot didn't need a dead man's switch. He just needed the mark to believe he had one.
Bill: I mean I don't think Elliot really wants Freddy to formally do something incriminating, it would be easy enough to frame Freddy, and Elliot doesn't care about laws. Maybe he just didn't have time to code the malware that would do all this email-copying for him. After all, he mentions to Mr. Robot that they only had two weeks to prepare for this target.
Harlo: Two weeks, and everybody's on drugs, so subpar performances all around.
Yael: Haha so much coke.
Freddy: Lawyers reading this chat: please don’t do illegal drugs.
Bill: Clearly you've never been in a 1980s law firm before.
Yael: It’s… not illegal if you don’t get caught?
Harlo: ALSO, it WAS SENT as a DVD. Which he left in the player. So the FBI will see the evidence when they go to his office anyway.
Zach: Perhaps Elliot was expecting him to clean up the evidence instead of killing himself ¯\_(ツ)_/¯. I think eventually it would become public that this law firm's emails were compromised, and Elliot/Mr. Robot needed a plausible excuse in place about why that happened to take the heat off of them.

Image Credit: Micah Lee
Grand Central Station
Bill: I like how Elliot mentioned to Freddy to turn off and leave behind anything "with an on/off switch"—but Elliot forgot about the fact that an RFID ping can also be used to determine location.
Harlo: It’s Bluetooth, actually!
Yael: I saw the Bluetooth symbol.
Bill: So is it actually Bluetooth? I mean, cheap RFID cards might have that symbol anyway.
Jason: Most access cards don't support Bluetooth, but you can buy access cards that include Bluetooth low energy (BTLE) beacons. They're a little more expensive and I wouldn't expect a law firm with what looks like kind of cheap IT and security to go for them, but they exist (about $10/unit on Alibaba).
Emma: It could be both RFID and Bluetooth. The presence of a Bluetooth connection is annoyingly used as a layer of security verification by some systems. -_-
Jason: Yeah, the cards I found have RFID and BTLE.

Image: USA
Zach: It’s interesting he left all electronics behind to go to the station, but I assume he would still be trackable through Tracfone pings to the cell towers.
Yael: Even with a dumbphone.
Zach: Those phones will still ping the cell towers.
Emma: That's not super precise, though.
Yael: Yes, it still pings but is not as precise, at least according to Serial podcast season 1.
Jason: You have to consider the setup time to follow a brand-new mobile phone with a fresh IMEI [device serial number] and IMSI [user identifier].
Micah: Those phones still ping cell phone towers, but I don't see how Dark Army would know which IMSI to try tracking in crowded NYC, assuming they had no idea about this phone thing ahead of time.
Bill: You could use something as simple as this Bluefruit LE sniffer to triangulate the location of the badge.
Jason: There are a lot of apps that scan Bluetooth for navigation. there's even one by Amtrak that is designed to help you navigate Penn Station (it might also support Grand Central now). if you had access to an ad network that fed back Bluetooth MAC addresses within range, you could get pretty accurate tracking.
Yael: How did Elliot get eyes inside Grand Central Station? Did he hack into a surveillance camera or something?
Zach: Seems that way.
Harlo: With an app that I think is made-for-TV. I can’t find it. CamSec Pro? Anybody? But I guess it's worth noting for the audience that, you don't have to restrict your Kali Linux setup to what comes pre-installed. You can totes outfit your Kali USB with persistence [preserving the filesystem instead of wiping everything every time the OS shuts down] and other cool things.
Fred: It’s movie magic for sure, most of those networks require some kind of VPN access and username / password. Hard to believe it’s hacked that quickly.
Jason: There are plenty of internet connected cameras with default credentials.
Micah: I would assume he pre-hacked the Grand Central Station cameras in anticipation of this operation, so he could have spent a few days on it.
Freddy: But to be able to get that level of access and to be able to move PTZ (pan-tilt-zoom) you would need access to the network operations center (NOC) for Grand Central.
Jason: A lot of these cameras are administered through simple web apps that might not be particularly locked down, even the pan-tilt-zoom controls.
Harlo: What if it were 2015/16? What exploits would we have used? Like, any NOC web app exploits that have been long since patched?
Zach: I saw this online from 2006: stationary Bluetooth devices throughout Grand Central Station. Something like that could be exploited by the Dark Army for Bluetooth tracking.
Bill: Who knows, there could be networks that don't advertise with beacon packets that are protected only with WEP [a weak and outdated security protocol for WiFi networks] or something that can be easily cracked. And the cameras often don't have any authentication layer at all, since it's assumed that the network will provide the security layer. I've seen a lot of these in stores, access points that don't send beacon packets but have devices authenticated with them.
Zach: I think IRL, though, the Bluetooth tracking would be difficult to set up. Either stationary devices in advance or some sooper-leet mass phone ownage to turn their devices into trackers, similar to FSociety's FBI hack. I would think the webcams in Grand Central Station are secure but honestly, who knows. That may be the most realistic part of this scene. Like Bill says, it could be a hidden Wi-Fi network secured with WEP and a bunch of security cameras.
Yael: I guess no cameras on the train that Elliot has evil Freddy meet him at?
Christina: I found that super odd. Like cameras everywhere but there, hmm.
Micah: Maybe there were cameras on the train. Elliot did have his hood up; maybe he didn't care.
Jason: Cameras on the train might not be internet-connected, if they exist. You'd have to figure out the network backhaul for that and it would be expensive and tricky (lots of dead zones in cellular coverage) for limited benefit.
Honeypot Houses
Yael: Did Mossack Fonseca have a distress signal/honeypot house where they torture people? How realistic is this?
Emma: As realistic as a hostile actor wants it to be. Formations House (#29 Leaks) wouldn't have. Some of their clients would, though.
Micah: I don't think it was a Mossack Fonseca-like company with the honeypot house, I think it was more like the Dark Army with one.
Yael: Hmm, do we know any IRL cases where people had a honeypot house? I guess they've kept them secret…
Harlo: Whitey Bulger.
Emma: The mob. Escobar, I think.
Micah: It would be really expensive to run a honeypot house. Like, even just having a normal house is expensive.
Bill: Well, when you own the world's currency it turns out you can buy a building in Manhattan.
Yael: With e-coin.
Emma: Well, the building would have served more purposes. It's fake addresses and mailing points. It's full of safe houses and temp housing. It has no prying eyes.
Yael: I know people have owned buildings for sketchy things but I'm not familiar with the process to get folks there via social engineering as opposed to, like, brute force. Do we know any IRL cases where people had a honeypot house? I guess they've kept them secret…
Christina: No but Jay-Z had a stash house on State Street, Brooklyn.
Harlo: Trump Foundation; I’m just throwing it out there.
Yael: I mean there was that newspaper that owned a bar in the greatest act of undercover reporting of all time…
Harlo: Something I dig about the honeypot house: cellular dead zone. Essentially a SCIF.
Emma: That can be done with the right paint, or even tape. DoD used to have its own special tape that could basically Faraday any surface. Make sure radio signals can't penetrate, soundproof, all panels secure. Often it has entrances guarded. It's usually in a government building of some sort, but Rockefeller had one in his barn IIRC.
Yael: “This doesn't feel right! The building is owned by E-Corp!" (Jump, Elliot, jump!)
Christina: Or like, don’t fucking go in, Elliot.
Bill: They couldn't get out the window. That's why you should Always Carry A Bat.
Harlo: Or a tactical pen?
Yael: And a ladder!
Harlo: Oh also, Christian Slater says something like "be careful, you're on the owner's Wi-Fi," which… hey hackerman: turn your radios off when not in use.
Micah: Did you all notice that at the end, when the Dark Army people were forcing Elliot to overdose, that he has a very old school rotary phone?
Harlo: IT'S A CLASSIC WHITEROSE FLOSS MOVE.
Micah: Man, in season 1 they were all like, "Let's get the Dark Army to help us with the China data center backups," and by season 4 I think they're understanding that was probably a bad call.
A Roundtable of Hackers Dissects ‘Mr. Robot’ Season 4 Episode 1: ‘Unauthorized’ syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Link
Over the years, my job has been pretty diverse. I enjoy all the Master Electrician and Instrumentation work, but building and maintaining networks has been a joy as well. There are so many pretty blinking lights. All the testing and commissioning tools are fun to play with as well. There are also lasers.One thing that never gets old is seeing people’s faces (who don’t know me that well), when I rock up in high-vis clothing to start messing around in network cabinets. Here I am, a slightly scruffy-looking older guy, glue and resin on work boots, knocking about in IT. It’s pretty funny, and handy sometimes. (Glue and I haven’t been on good terms since Kindy. I don’t know why. As an Apprentice, I managed to get half a bottle of blue conduit glue in my hair for fucks’ sake.)—-“Tom” was a Junior Gov’t System Administrator, working at a Regional IT Dept. When the position of IT Manager became available at a 2000 student Gov’t High School, Tom was encouraged (finessed/manipulated/conned ?) to apply. See, Tom was a cockhead.As a wanker of the first order, in the 4 months that he’d been there after transferring in, Tom had pissed off the whole Gov’t IT team. You know that person who has to comment on everything, thinks they know everything, thinks they are always the smartest in a room, but is actually only about 67% competent? And a bit lazy? This was Tom.The Principal was so glad to have a Gov’t Sysadmin apply for the role that they changed the job title from Supervisor to Manager, to entice him. The role had an office and two support staff. It was also arranged that Tom would be given more control over the school network than previous Supervisors. (I heard later that his then Gov’t IT Director may have suggested the title enhancement to the Principal, as part of the finesse.)Tom had his own fiefdom. It also didn’t take him long to piss the Principal off either. As well as the admin staff, and most of the teachers.I’d done work with Gov’t IT for some time before Tom showed up and knew everyone, though only gotten to know him peripherally. He had yet to rub me the wrong way.We had two big-ish jobs at the High School, about a year after Tom started there.Change out a shit-tonne of keyed door locks for a brand new, standalone, networked door access system we would install and maintain.And change out existing room lighting for energy efficient LED panels.These two jobs would each be done during a 2 week term break, either side of a 10 week school term. I would get to run both jobs.In the planning phase of the door access network, Tom made it known that he would be trained on the new door system and be in charge of it, since it was a network in his school. The Principal made it known who’s school it was, and that Tom would stay right the fuck away from it, since it was standalone and had nothing to do with him. Tom was not happy about this.—-One Tuesday, a little over 5 weeks since the door system had been live, I was driving to a job when I got the phone call that kicked off this tale. “High School called. They’re having trouble with the new door system.” Turning the car around, I wasn’t sure what annoyed me more. That my sing-along with ‘Blink-182’ had just been interrupted, or that I would now miss out on scones fresh from the oven.At the system operator terminal PC in an admin office, I hear that there were two issues.Some teachers couldn’t open some doors this morning, and some other doors that the admin staff tried to change functions on weren’t responding. I suspected the regular user teething issues. (We were 5 weeks into the 10 week term at this stage.)They went on to explain that they’d looked and found the teachers door access had been changed to remove some doors. They’d re-added the doors and fixed that, but the doors they were trying to change functions on weren’t responding.Looking in the system on their user login, they were right. They’d re-added these doors correctly for these teachers. But why wasn’t the system updating the door changes? Logging in as the admin, I see that apart from the hub in this office, the other 18 network hubs are not responding. Hmm. Weird. Unlocking the cabinet, I see that the fibre optic patch lead which connects to the other hubs is dangling in space. Very weird. These take some doing to unplug, they don’t just fall out.Reconnecting the patch lead and rechecking the network, I see the other hubs are responding, so I push the door changes through. There are still questions though, so I open the system log. I see that the changes to the teachers access was made by one of the admin users at 5:33pm, and the hubs went off-line soon after. Strange, because the admin staff finished at 4.30pm. The log also showed that someone who is not admin staff entered this office at 5:08pm. Tom.I sat there and thought about asking the admin staff some questions, but decided against it. I suspected that Tom had insinuated himself here over the past couple of weeks to get the gist of how the door program worked, and had gotten a user login to boot. If I kicked up a fuss, he might be able to IT double-speak the teacher changes. Also, the patch lead being out could be waived away as incompetence on my part.As I was thinking, the admin staff said that Tom had been in earlier and had overheard the issues they were having. He’d said something to the effect of “That’s what you get when you let electricians manage a network.” Ohh ok, he was being pissy about being banned from this system. My crystal ball went through a variety of scenarios, and I decided to let sleeping dogs lie for now.Three days later, on the Friday, I got another call about the high schools door system.Checking in and checking it out, I found that the issues they had were almost identical to the first, except that only 4 hubs were offline. After going to one of the affected hubs and plugging the patch lead back in, I opened the system log again. To find it empty. What the flying fuck? The daily back-up file had been deleted as well. Only my admin login could do these things, and how the fuck did he get that?Checking that the secondary back-up on an external drive was still intact, I dumped that into my laptop and had a swivel on the chair for a few minutes. Yep, this back-up showed that the admin login had been used to do the teachers changes this time, and delete the system log. All after the admin staff had left yesterday.This operator console PC had been provided by Tom, it was one of the school assets. The Gov’t image was supposed to have been wiped and a clean operating system put on, so it couldn’t be connected to the Gov’t networks. Maybe Tom had a keylogger in there somewhere. I gave it a good Sparky go, but couldn’t find anything. I even checked for cameras. After changing the admin password, I left and put on some Nick Cave in the car.That evening, while Misters Cave and Daniels kept me company, I looked up keyloggers. And then went through my boxes of spare parts toys. It was Secret Squirrel time.—-On Monday, I timed my arrival to the school just as the admin staff were leaving. I “just wanted to check some things on the system.” They left and left me to it. I placed one small camera under the desk to see the back of the PC tower, one on a shelf looking at the screen, and one on top of a corner cupboard to see the room. Happy with my work, I went home.That Thursday, same thing again. Different teachers affected, and different hubs offline, but the same thing. Admin login used to wipe the logs and back-up. I changed the admin password again, for reasons. After coming back that afternoon to retrieve footage from the cameras, I figured out what he was doing.The first time, he used the user login to make changes, pulled the patch lead, then installed a keylogger device on the keyboard USB cable into the tower. It looked like a little black USB adaptor thingy. He used this to get my admin login to wipe the system log and delete the back-up, so there’d be no evidence of his card accessing the room.What he was doing was a fucking stupid way to go about it. His ego must be a thing of wonder. The contempt he must have held for my abilities (as just a Sparky) to figure things out, even without the cameras, was boggling. I maintain systems and networks far more complex than this. Like the schools security system for example. Or a similar door access system in a much much more secure facility. Ok fucker, game on.Over the next 4 weeks, Tom and I went through these dance steps 4 more times. I heard all about him ‘suggesting’ that if he ran the system, a professional sysadmin, there wouldn’t be issues like these. I didn’t mention to anyone about the logs or back-ups. I just kept collecting my video and secondary back-ups. Because through my association with Gov’t IT I’d learned a few things about their policies. And wanted to fuck with Tom, and maybe collect some more ammunition, before I absolutely fucking wrecked him. Purposefully using keyloggers on a Gov’t asset is a big no no.—-The next 2 week term break was here, and we began changing out light fittings. It was easy work, and I had a team of 8. Once I kicked them off, I went to work.I added a relay card to each of 6 specially selected security system expansion points, in 6 different buildings. These buildings were where the people worked who disliked Tom the most. I’d worked at the school long enough to know all about it.Relays are wonderful. Give me enough relays, timers and contactors and I can make your wildest electrical/control dreams come true. A relay is a switch. That’s all. Like a light switch that you can turn on/off without being there.Here’s a thing about data cables that not a lot of people know. Data cables connect the data socket in an office to a patch panel in a network rack. There are 8 wires inside, but they each have very specific jobs. 4 are commonly used to carry data traffic (2, or one pair, for upload, 2 for download). Another pair for power to a PoE device, like a wireless access point.Say you figured out a way to get one specific pair of these 8 wires into, let’s say, a relay. You could then maybe interrupt the upload wires, or download wires, or power wires. Any of these would cause issues for your computers ability to communicate. If you could turn the relays on and off at opportune times, for selected people, perhaps via a security system you had remote access to, you could maybe introduce weird intermittent faults in a network.If you could do this without it looking like the cables in a network cabinet patch panel had been touched, you might now have a method to cause grief without it being traceable through IT magic. Sure, a competent IT person would assume the cable was damaged, and go test it. But what if when you went to test, it was all ok? It would maybe look like a network system issue. That a competent Sysadmin should be able to diagnose and fix.A critical part of all this would be if you had a job, as an electrician, to make alterations to a buildings lighting. You could then turn some power circuits off, so that the network cabinet in a building was unpowered for a while. You could then take data cables out of patch panels without it being noticed by a Sysadmin. You could run a new length of data cable and terminate it into the patch panel, and make a nice coupled join of the two cables in the ceiling, then split off some pairs to relays.This could be done over 2 days. You could then begin switching the Principals relay on the third day of the 2 week student break. It would be pretty easy keeping track of Toms whereabouts so you could make the cable appear ok for testing. Once the Principal was good and pissed off at Tom for not being able to fix their issues, you could start switching the Admin Managers relay.The next day, you could go to work on the Head of English in another building. Then the Head of Science in another. Having Tom out of his office, and you having a legitimate reason to be in there (lighting job), would mean you could have a real good look around and find the the USB keylogger.—-Standing in Tom’s office, I took a picture of the keylogger among the mess on his desk. (It might have been hidden in a drawer before that) Then I called my mate, Tom’s old boss, the Regional Director of Gov’t IT. I told him about the issues I’d had with the door access system, the videos, the keylogger. He came down, took his own picture, and called the Principal.On my laptop, in the Principals office, I showed them the videos of Toms vandalism on the door system. The Director examined the keylogger. It was so much worse than I thought. They found not only my system info on it, but info from the school accounting department, Directors department and more. Tom had so much incriminating evidence on it, from all kinds of Government departments, that he was bend-over-no-lube fucked.When Tom answered the summons to the Principals office, I couldn’t help smiling at him. I know that’s mean, but I’m only human sometimes.He had no answers to the questions. He tried to claim the keylogger wasn’t his. The Director shot that down. It had too much stuff, from places Tom had access to. It couldn’t be anyone else’s. Then I showed him the videos.That look he gave me was priceless. He’d figured out I’d done this to him, and it was glorious. A simple electrician. (Go fuck yourself Tom.)He wasn’t prosecuted, because that would’ve caused too much of a public stink. But Tom got flagged and would never again be able to work in any Gov’t job, anywhere in the country. Not as a janitor. Or as a contractor doing Gov’t work. And since graduating Uni, he’d only ever worked in Gov’t.Sorry private industry, he’s all yours now.—-I did say something stupid though. After Tom left Principals office that reveal day, Principal asked Director if they could send someone competent to look at the schools network issues. Without thinking, I said “Nah, I’ll fix that.” (I blame having too much fun.)After they had me explain what I’d done, because I needed Tom out of his office, I had to cross-my-heart promise not to do it again. Principal didn’t fully understand what I’d done, but Director said I was like some evil MacGyver.I put the network cabling back in place and took all my toys home.Thank you for reading.(Again, Fuck you Tom.)—-GlossaryKindy - Kindergarten. Where you learn, as a small child, not to run with scissors. Also where a lifelong acrimonious relationship is formed with glue. Not ‘Clag’ glue though. That shit was tasty.Scone - a delicious flour based baked treat. Grandma scones are the best, with cream and raspberry jam. The scones you try and make yourself are excellent hockey pucks.Secret Squirrel - a cartoon I liked when I was a kid. A squirrel secret agent who has a mole mate. They have gadgets and adventures.Nick Cave - Australian Renaissance Man. Nick Cave is mostly known as a singer/songwriter. Excellent revenge planning music.Relay Logic - was used to run elevators before there were computers. So many things have relays. Little electromechanical wonders. I love them. Ok, so, a relay has a coil in it, that you energise. This creates a tiny electromagnet and pulls a piece of ferrous metal down. This changes the state of the contacts. Easy huh. Just like a light switch, but without the need of fingers. via /r/ProRevenge
0 notes
Text
A Roundtable of Hackers Dissects ‘Mr. Robot’ Season 4 Episode 1: ‘Unauthorized’
It’s been one year, nine months, and 23 days since the sizzling season 3 finale of Mr. Robot, and the show is back for its last season.
This week, we discussed [SPOILERS, obvs] the probability of getting an envelope with a ringing dumb phone with a hacker on the other end of the line, dead man’s switches, hacking cameras at Grand Central Station, and honeypot houses. (The chat transcript has been edited for brevity, clarity, and chronology.) This week’s team of experts include:
Emma Best: a former hacker and current journalist and transparency advocate with a specialty in counterintelligence and national security.
Bill Budington: a long-time activist, security trainer, and a Senior Staff Technologist at the Electronic Frontier Foundation.
Jason Hernandez: Solutions Architect for Bishop Fox, an offensive security firm. He also does research into surveillance technology and has presented work on aerial surveillance.
Harlo Holmes: Director of Digital Security at Freedom of the Press Foundation.
Micah Lee: a technologist with a focus on operational security, source protection, privacy and cryptography, as well as Director of Information Security at The Intercept.
Freddy Martinez: a technologist and public records expert. He serves as a Director for the Chicago-based Lucy Parsons Labs.
Matt Mitchell: a hacker and Director of Digital Safety & Privacy at Tactical Tech. He founded cryptoharlem, which aims to teach basic cryptography tools in the inner city.
Christina Morillo: a New York City-based information security and technology professional working as an information protector on Microsoft’s cloud & engineering security team.
Zachary Julian: Security Associate at the security consulting firm Bishop Fox.
Freddy and His Package
Yael: Are there instances where you get a package with a ringing phone, or is that just in TV/the movies? Like has that happened in real life?
Harlo: I don’t know about in real life, but this is a thing in Black Mirror, and American Vandal.
Micah: For it to happen, Elliot would have had to be tracking the package and waiting outside the building to know exactly when to make the call. Which he was.
Emma: If the phone had GPS enabled, Elliot could have tracked it and known when it arrived, assuming there wasn't already a webcam compromised in there. Elliot also could have been listening in through the phone’s microphone in real-time. He hears the phone arrive. Hangs up. Dials back.
Bill: I'm assuming Elliot had either delivery confirmation or a GPS unit to know when the phone and video was delivered.
Micah: I don't think he would have needed GPS. He could have just watched delivery person enter the building with the package, and as soon as they left the building made the call.
Emma: True, Micah. Even simpler, he had an in-progress call to the phone going.
Jason: There are Android apps that will trigger sending a text or whatever when they're in proximity to a given Wi-Fi access point or at a certain latitude / longitude. It's pretty simple to set up.
Matt: Tasker app does this.
Harlo: It doesn't seem to be Android. It's a dumb phone (probably a Tracfone or something similar). So it's likely Elliot has it tracked via… maybe skip tracing?
Bill: Yeah, it looked like a dumb burner phone.
Micah: I think it was like a pay-with-cash Tracfone, which is the smart way to do it anonymously anyway.
Freddy: The simplest explanation is that he had someone else watching him and tracking the dude and reporting back.
Yael: What's a Tracfone?
Harlo: It's a brand of pay-as-you-go phones you can buy from pharmacies, 7-11s and other places. it has only mobile text and voice; no data.
Micah: It’s just one of several types of cheap phones you can purchase at corner stores in cash. You don't need ID or credit card or anything, and they have fairly cheap options with old flip phones, even today.
Matt: Buying a Tracfone with cash, buying service for it with cash, and then not talking when you call the service number to set it up is a pretty anonymous way to get a U.S. cell phone.
Harlo: I agree with Emma that the easiest way might be keeping a live call on during delivery, then listening for the pick-up. Or having actual surveillance on the office. Or maybe even tapping into any video surveillance on premises.
Yael: He had access to Freddy’s screen too, right?
Bill: I don't think he had access to the screen… maybe he just saw via binoculars that he was watching the video.
Yael: Okay so flash forward to the call. So then Mr. Robot/Elliot is trying to get Freddy to click on a phishing link (which he thought was ransomware, but it wasn’t)—and to copy the .pst file in his inbox to the thumb drive. How does that work?
Micah: Since Freddy was copying the .pst file himself, and not the malware, my guess is clicking the phishing link was simply to get malware on the law firm's network for future use.
Harlo: Maybe this is either 1) a diversion for the IT admin to not notice the immediate export/download of an employee’s entire inbox, or 2) one of those things where you gotta hack the admin to complete the exploit.
Zach: It seems like the malicious link was just to provide an excuse as to why the inbox was compromised.
Freddy: If he had network access, he would just dump the active directory [a Windows service that controls access to shared resources on a network, like user logins and credentials], but the point of the plot was to incriminate the lawyer. It wasn’t about getting the emails. It was about incrimination.
Jason: Owning active directory usually takes a while and it can be kind of a hassle.
Micah: Elliot did need the emails to find all the banking details he needed.
Harlo: But if you want to hide your involvement, you're also pinning it on the mark who "clicked a link, oops totally not an orchestrated op by Mr. Robot."
Freddy: The way to get the emails isn’t really how you would do it if you already have malware on the network.
Micah: PST files are an Outlook inbox. A lot of the big email leaks that get reported on start out as a PST file. He was using a cool tool to import them and search through them, "Expansion Inbox," which I've never heard of.
Yael: So shout out to Iceweasel! We saw it on Elliot’s laptop on the train.
Bill: Debian's Iceweasel had resolved its naming issues with mainline Firefox in early 2016 but remember this is still in late 2015. So they're staying true to the time period.
Yael: Is Iceweasel like an open source Firefox? Wait, isn't Firefox open source?
Micah: Firefox is open source, but there was a trademark conflict for use of the "Firefox" name and logo inside Debian. Debian handled it by just renaming it to Iceweasel and providing their own logo.
Dead Man’s Switch
Yael: Elliot said he could get the videos to send to Freddy’s kids and the FBI… like a dead man's switch…
Micah: OnionShare has a dead man's switch feature. You can set a time in the future to start sharing files, and it gives you the Tor onion address right away. It wouldn't work for this exact use case, but you could, for example, tweet an onion address and a date, and if you don't manually close OnionShare before that date, it automatically starts sharing whatever data you want.
Emma: A dead man's switch would be super easy to set up. Have a couple of computers running a check every 10 minutes on a data file, see if it's been 24 hours yet. If it has, send the emails. If not, check again in 10 minutes. The email doesn't have to have the data, just a key and instructions on how to access it. The data can be anywhere. Elliot could check in with infected machines via a command and control system and reset the clock in the data file. The data could be stashed on some random server. The email to the FBI could contain the target’s IP address, user/password and decryption key. The files would be too large to just send to the FBI directly, and if they were forcibly dropped on an FBI system, they wouldn't touch it. But of course, Elliot didn't need a dead man's switch. He just needed the mark to believe he had one.
Bill: I mean I don't think Elliot really wants Freddy to formally do something incriminating, it would be easy enough to frame Freddy, and Elliot doesn't care about laws. Maybe he just didn't have time to code the malware that would do all this email-copying for him. After all, he mentions to Mr. Robot that they only had two weeks to prepare for this target.
Harlo: Two weeks, and everybody's on drugs, so subpar performances all around.
Yael: Haha so much coke.
Freddy: Lawyers reading this chat: please don’t do illegal drugs.
Bill: Clearly you've never been in a 1980s law firm before.
Yael: It’s… not illegal if you don’t get caught?
Harlo: ALSO, it WAS SENT as a DVD. Which he left in the player. So the FBI will see the evidence when they go to his office anyway.
Zach: Perhaps Elliot was expecting him to clean up the evidence instead of killing himself ¯\_(ツ)_/¯. I think eventually it would become public that this law firm's emails were compromised, and Elliot/Mr. Robot needed a plausible excuse in place about why that happened to take the heat off of them.

Image Credit: Micah Lee
Grand Central Station
Bill: I like how Elliot mentioned to Freddy to turn off and leave behind anything "with an on/off switch"—but Elliot forgot about the fact that an RFID ping can also be used to determine location.
Harlo: It’s Bluetooth, actually!
Yael: I saw the Bluetooth symbol.
Bill: So is it actually Bluetooth? I mean, cheap RFID cards might have that symbol anyway.
Jason: Most access cards don't support Bluetooth, but you can buy access cards that include Bluetooth low energy (BTLE) beacons. They're a little more expensive and I wouldn't expect a law firm with what looks like kind of cheap IT and security to go for them, but they exist (about $10/unit on Alibaba).
Emma: It could be both RFID and Bluetooth. The presence of a Bluetooth connection is annoyingly used as a layer of security verification by some systems. -_-
Jason: Yeah, the cards I found have RFID and BTLE.

Image: USA
Zach: It’s interesting he left all electronics behind to go to the station, but I assume he would still be trackable through Tracfone pings to the cell towers.
Yael: Even with a dumbphone.
Zach: Those phones will still ping the cell towers.
Emma: That's not super precise, though.
Yael: Yes, it still pings but is not as precise, at least according to Serial podcast season 1.
Jason: You have to consider the setup time to follow a brand-new mobile phone with a fresh IMEI [device serial number] and IMSI [user identifier].
Micah: Those phones still ping cell phone towers, but I don't see how Dark Army would know which IMSI to try tracking in crowded NYC, assuming they had no idea about this phone thing ahead of time.
Bill: You could use something as simple as this Bluefruit LE sniffer to triangulate the location of the badge.
Jason: There are a lot of apps that scan Bluetooth for navigation. there's even one by Amtrak that is designed to help you navigate Penn Station (it might also support Grand Central now). if you had access to an ad network that fed back Bluetooth MAC addresses within range, you could get pretty accurate tracking.
Yael: How did Elliot get eyes inside Grand Central Station? Did he hack into a surveillance camera or something?
Zach: Seems that way.
Harlo: With an app that I think is made-for-TV. I can’t find it. CamSec Pro? Anybody? But I guess it's worth noting for the audience that, you don't have to restrict your Kali Linux setup to what comes pre-installed. You can totes outfit your Kali USB with persistence [preserving the filesystem instead of wiping everything every time the OS shuts down] and other cool things.
Fred: It’s movie magic for sure, most of those networks require some kind of VPN access and username / password. Hard to believe it’s hacked that quickly.
Jason: There are plenty of internet connected cameras with default credentials.
Micah: I would assume he pre-hacked the Grand Central Station cameras in anticipation of this operation, so he could have spent a few days on it.
Freddy: But to be able to get that level of access and to be able to move PTZ (pan-tilt-zoom) you would need access to the network operations center (NOC) for Grand Central.
Jason: A lot of these cameras are administered through simple web apps that might not be particularly locked down, even the pan-tilt-zoom controls.
Harlo: What if it were 2015/16? What exploits would we have used? Like, any NOC web app exploits that have been long since patched?
Zach: I saw this online from 2006: stationary Bluetooth devices throughout Grand Central Station. Something like that could be exploited by the Dark Army for Bluetooth tracking.
Bill: Who knows, there could be networks that don't advertise with beacon packets that are protected only with WEP [a weak and outdated security protocol for WiFi networks] or something that can be easily cracked. And the cameras often don't have any authentication layer at all, since it's assumed that the network will provide the security layer. I've seen a lot of these in stores, access points that don't send beacon packets but have devices authenticated with them.
Zach: I think IRL, though, the Bluetooth tracking would be difficult to set up. Either stationary devices in advance or some sooper-leet mass phone ownage to turn their devices into trackers, similar to FSociety's FBI hack. I would think the webcams in Grand Central Station are secure but honestly, who knows. That may be the most realistic part of this scene. Like Bill says, it could be a hidden Wi-Fi network secured with WEP and a bunch of security cameras.
Yael: I guess no cameras on the train that Elliot has evil Freddy meet him at?
Christina: I found that super odd. Like cameras everywhere but there, hmm.
Micah: Maybe there were cameras on the train. Elliot did have his hood up; maybe he didn't care.
Jason: Cameras on the train might not be internet-connected, if they exist. You'd have to figure out the network backhaul for that and it would be expensive and tricky (lots of dead zones in cellular coverage) for limited benefit.
Honeypot Houses
Yael: Did Mossack Fonseca have a distress signal/honeypot house where they torture people? How realistic is this?
Emma: As realistic as a hostile actor wants it to be. Formations House (#29 Leaks) wouldn't have. Some of their clients would, though.
Micah: I don't think it was a Mossack Fonseca-like company with the honeypot house, I think it was more like the Dark Army with one.
Yael: Hmm, do we know any IRL cases where people had a honeypot house? I guess they've kept them secret…
Harlo: Whitey Bulger.
Emma: The mob. Escobar, I think.
Micah: It would be really expensive to run a honeypot house. Like, even just having a normal house is expensive.
Bill: Well, when you own the world's currency it turns out you can buy a building in Manhattan.
Yael: With e-coin.
Emma: Well, the building would have served more purposes. It's fake addresses and mailing points. It's full of safe houses and temp housing. It has no prying eyes.
Yael: I know people have owned buildings for sketchy things but I'm not familiar with the process to get folks there via social engineering as opposed to, like, brute force. Do we know any IRL cases where people had a honeypot house? I guess they've kept them secret…
Christina: No but Jay-Z had a stash house on State Street, Brooklyn.
Harlo: Trump Foundation; I’m just throwing it out there.
Yael: I mean there was that newspaper that owned a bar in the greatest act of undercover reporting of all time…
Harlo: Something I dig about the honeypot house: cellular dead zone. Essentially a SCIF.
Emma: That can be done with the right paint, or even tape. DoD used to have its own special tape that could basically Faraday any surface. Make sure radio signals can't penetrate, soundproof, all panels secure. Often it has entrances guarded. It's usually in a government building of some sort, but Rockefeller had one in his barn IIRC.
Yael: “This doesn't feel right! The building is owned by E-Corp!" (Jump, Elliot, jump!)
Christina: Or like, don’t fucking go in, Elliot.
Bill: They couldn't get out the window. That's why you should Always Carry A Bat.
Harlo: Or a tactical pen?
Yael: And a ladder!
Harlo: Oh also, Christian Slater says something like "be careful, you're on the owner's Wi-Fi," which… hey hackerman: turn your radios off when not in use.
Micah: Did you all notice that at the end, when the Dark Army people were forcing Elliot to overdose, that he has a very old school rotary phone?
Harlo: IT'S A CLASSIC WHITEROSE FLOSS MOVE.
Micah: Man, in season 1 they were all like, "Let's get the Dark Army to help us with the China data center backups," and by season 4 I think they're understanding that was probably a bad call.
A Roundtable of Hackers Dissects ‘Mr. Robot’ Season 4 Episode 1: ‘Unauthorized’ syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
Hackers Dissect ‘Mr. Robot’ Season 4 Episode 5: ‘Method Not Allowed’
Episode 5 of Mr. Robot’s final season was riveting. We discussed [SPOILERS, obvs] burning evidence, fake ideas, physical security, social engineering, firmware updates, lockpicking, 3D fingerprints, and more. (The chat transcript has been edited for brevity, clarity, and chronology.)
This week’s team of experts includes:
Emma Best: a former hacker and current journalist and transparency advocate with a specialty in counterintelligence and national security.
Bill Budington: a long-time activist, security trainer, and a Senior Staff Technologist at the Electronic Frontier Foundation.
Jason Hernandez: Solutions Architect for Bishop Fox, an offensive security firm. He also does research into surveillance technology and has presented work on aerial surveillance.
Harlo Holmes: Director of Digital Security at Freedom of the Press Foundation.
Trammell Hudson: a security researcher who likes to take things apart.
Trammell: That episode was so [AESTHETIC]. I loved that it started with "We don't have to talk," then had ZERO dialogue, and ended with "It's time we talked". It felt like the bold stylistic decisions the show was making back in the earlier seasons.
Emma: Agreed, the aesthetics were very good. It's one of those episodes I'll enjoy watching a breakdown of by film buffs on YouTube. I know there was a lot I didn't get.
Trammell: So many film references and tropes… also looking forward to the film buff analysis.
Burning evidence
Yael: I like how they played “Ode to Joy” right when Darlene found Elliot. I also like how it started out with Elliot trying to "burn the evidence" but, like, burning doesn't always destroy forensic evidence.
Emma: Under the circumstances, it was nearly the best they could do. I would've tried to keep the doors secured shut but broken any side and rear windows (leaving the front windshield intact if possible). That guarantees airflow and maximizes convection, raising the temperature. We're dealing with digital data, and physical damage to the medium helps, but the data can be reconstructed out of heavily damaged materials in ways that it couldn't a few years ago.
Yael: They zoomed in on an automated license plate reader (ALPR), though. ALPRs don't just take license plate images, they also capture photos of drivers and passengers, too.
The Crime Scene
Trammell: Did Dom do anything on the scene, or was it all implied that she handled it by her being there?
Emma: I think she was just looking around and trying to get info.
Yael: Yeah, Janice tells Dom to use her FBI credentials to intercept intel and ID the body… but can you do that? I thought the FBI only had jurisdiction to investigate state crimes if it involved interstate travelers, serial killers, etc.
Trammell: "You give me any of that 'juris-my-dick-tion' crap…"
Emma: She said in a Signal message that she didn't get access on the scene, and that was why she went the other route.
Yael: Her donut phone hack was pretty clever. But I was wondering, why is Dom writing down the license plate numbers of Dark Army vans near the end of the episode? Isn’t it a bit late for that?
Emma: I'm also not sure why the FUOU markings were crossed out on the document Dom looked at. That's something you'd see if it were downgraded or approved for public release, but that wasn't the impression I got with it, especially since there was a color picture attached. You don't usually get that in FOIA releases or leaked documents, lol.
Trammell: Yeah, that clearly wasn't a real FOIA since it didn't █████████ █████(b)(4) and hadn't been photocopied at least ██████ (c)(1) times.
Meeting Location
Yael: Price getting a “bill” that’s a note and then getting the dry cleaner address from a trombone player and then another address in his dry cleaning was pretty clever. I’ve seen people set up two meeting locations (you meet at the first to get the address for the second) but I’ve never seen something like that IRL.
Emma: Pierce chasing the meeting info was a fairly realistic example of when people (or their trusted minions) have to put in the legwork of setting something like that up.
Trammell: Although what's the point of sending Price on an item quest?
Yael: I think to avoid someone else finding out where they're meeting.
Emma: It's also counter-surveillance. Making numerous stops makes it easy to compare anyone showing up at multiple points, and the travel distance provides more opportunities to watch for them. "Running errands" can be a great way to ID a tail. Do it long enough and you can even ID a team working in tandem.
Getting Creds
Yael: I like how Darlene used an AlphaCard Pilot ID card printer for her fake ID, and that Elliot was scouting Virtual Realty’s security, which was conveniently described on its website.
Bill: But…. just because she printed the ID doesn't mean it's valid. By the way, Darlene's fake ID is for "Dolores Haze", who is a character in the novel Lolita by Vladimir Nabokov.
Trammell: Darlene has been using the Dolores Haze moniker since season 1, and it’s how she is listed in Eliott's Signal contacts.
Yael: Darlene’s socially engineered costume was pretty effective, as well as “dropping her purse.”
Bill: Then Elliot comes in with his mad dash to the access control station.
Yael: …and then Darlene "forgetting" her phone was a nice touch.
Trammell: The guard watching Die Hard is more evidence that Diehard is a Christmas movie.
Harlo: The guard at Virtual Realty did all he could do, but they still got pwned. For a Common Access Card, it's recommended to have a photo printed (for the human to verify) and a chip (for machines). Darlene's fake ID was definitely going to fail on the machine-readable side, thus it falls down to the human to verify. But, what can you do when someone inserts the matching photo ID into the employee database?
The Building
Harlo: It’s interesting to think about co-tenancy as a vulnerability.
Trammell: That’s a good point. At many colocation centers that I have visited there is a guard to let people into the server room, but all of the tenants have private cages with locks that the guards explicitly do not have access to.
Harlo: My question about tenancy has to do with the unique ability for attackers to pivot from one point of access to another [eg. gain entry to the gym but wind up in the server room]. That is sooooo 2010s—actually, not uniquely 2010s, even though we have coworking spaces that make that simpler.
Trammell: To update that for 2019 you could probably pull off a coworking space attack against someone with a Macbook and an Apple Watch. Wait for them to go to the restroom or get another coffee and you can probably unlock their machine with the watch’s Bluetooth while they are still close enough.
Harlo: I guess the main problem here is that the company that manages the building has complete access to everything its tenants are leasing. I wouldn't think it super wise for building management to have access to the server floor, but they did, and that's how Elliot and Darlene got in!
Jason: Yeah, I think the physical security would fail most audits.
Harlo: IT ALWAYS DOES.
Jason: The physical access controls at Virtual Realty are just not up to what I'd expect for even a cutrate colocation provider.
Yael: 20/20 hindsight, but I feel like the guard had bad peripheral vision, and he was super slow.
Trammell: He moved at the speed of the plot.
Darlene’s Disguise
Jason: The guard didn't ask why she was there on Christmas day.
Harlo: True. He wanted to be nice. Also, they took advantage of the partner's smoke break or whatever. That's why you have a buddy system, to help you double-check your judgement.
Jason: She's not dressed like anybody who is coming in to work on a server on Christmas day.
Yael: What would her costume have to be?
Jason: More casual. Or some kind of work uniform, if one exists.
Trammell: Seems like a random server maintainer costume for a visit on Christmas day would be whatever she happens to be wearing when she got the call to deal with maintaining the server.
Yael: I feel like women can't always get away with the jeans and hoodie look, though. There are double standards about what people give you shade for wearing.
Jason: Agreed that there are double standards, but there should be some kind of a consistent narrative about why she's coming into the building on Christmas day, ideally designed to exploit the security staff's likely expectations. I think she would have been better off coming into the building in the yoga outfit, saying she's on call and she got paged out of yoga. She could say a hard drive died on a production server and she's new so she got stuck with being on-call over the holidays.
Trammell: I'm not sure I've ever had the ground floor desk ever ask me why I'm coming into the office on a Sunday or after midnight or anything. That's really not their job.
Yael: Would she bring her badge to yoga?
Jason: If she's on call, she better.
Harlo: Darlene's first look provides excellent contrast with her second look: basic Barbie yoga gear. Pretty lucky, if you ask me.
Yael: Well, she also was able to think quickly, too. She’s so good at social engineering.
The Heist
Yael: Elliot got through that combo lock wirelessly with his laptop pretty quickly.
Trammell: That seemed unrealistic. There are hacks against some electronic locks, but most require some sort of connection, and likely some detailed recon to know what models are in use. The camera maintenance panel login was admin/admin. That is 100% realistic.
Yael: So, Elliot updated the firmware, which somehow made the elevator cam turn off… Does it just turn off when the firmware is upgrading? And there’s really no way for anybody to cancel it?
Jason: Firmware updates often overwrite really critical components of memory and disruptions to the process can leave devices in an unusable state, i.e. making it a brick. Software to update firmware usually tries to protect users from this, so there's typically not an easy or safe way to stop an update. Seemed clever to black out cameras with a firmware update.
Trammell: The firmware update running serially (0/152) and taking down the entire system is 100% realistic.
Yael: What does running serially mean?
Trammell: One at a time. So rather than saying "All cameras! Update your firmware!" it says "Camera 1! Update!" and waits for it to finish, then says "Camera 2! Your turn!"
Yael: I guess they should just prevent getting pwned by keeping their firmware updated.
Harlo: Or maybe it explains why they never update.
Emma: Darlene staring at the elevator camera like a total goober was painful to watch.
Yael: Maybe she assumed they'd erase the tape.
Emma: You can't count on wiping the footage, and staring at the camera waiting for it to go out is a dead giveaway that you were involved, while giving them a direct look at your face.
Trammell: It certainly made the break-in easier to have the Kraftwerks makerspace and chemlab in the same building. (And their slogan "Do. Make. Live." is similar to NYC Resistor's "Learn. Share. Make.")
Bill: Regarding the 3D printed fingerprint mold, a 3D printed fingerprint got past Samsung’s Galaxy S10 fingerprint sensor earlier this year. We see the fingerprint is crafted into a .gcode file. "A GCODE file contains commands in G-Code, which is a language used to describe how a 3D printer should print a job."
Yael: Elliot is really good at picking locks. I thought they did a good job of showing how when Darlene and Elliot had some access they could use it to get more access. So, uh, smart move of Elliot to cut the power when the guard goes in to investigate but I think he should’ve shown Darlene the clock much sooner. Also, in my 20/20 hindsight backseat hacking, I think they should've disabled all the security guards’ elevator access.
Trammell: PLC hacking was a nice touch. Although as with many things in the show, Eliott's ability to break into every system without any recon is a bit unrealistic. Why doesn't Darlene just say hi to the guard? She works for the company in server maintenance. That seems like she should be the one in the cage. Eliott could hide somewhere.
The Escape
Yael: I liked how Elliot and Darlene ended up having two wildly different escape strategies. Elliot bought some time with the zip line on the one door but then had to attack and run into traffic, while Darlene just posed as a gym-goer.
Emma: Darlene hiding and then changing her coat and walking out was a good move, but she should've been stopped. Regardless of chasing Elliot out, the police should have kept the building sealed and questioned anyone coming out—or at least checked their ID. But at least she changed her coat. If Elliot had had enough sense, he would do that instead of plowing into civilians and making a scene after he was out of the cops' line of sight.
Yael: Yeah, I think Elliot should take off his hoodie when running from the cops. Not that there was time or that it would've helped.
Trammell: After he ran through the couple and tripped over the pram, did anyone else expect Eliott to run through a pane of glass that two workers are carrying across the sidewalk?
Harlo: Yes.
Emma: I noticed tipping over the carriage full of cans. Definitely a moment of panic before it became clear that it wasn't a baby in there. (Yes, I know it's not real….)
Trammell: It was full of cans!
youtube
Trammell: A question I asked last week: if this operation is going down TONIGHT, why are they being so careful to cover all their tracks? It seems like they need to be burning the bridges at both ends at this point.
Emma: Because they still need it to take some time to find them.
Hackers Dissect ‘Mr. Robot’ Season 4 Episode 5: ‘Method Not Allowed’ syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes