#it security services
Text
Understanding Data Encryption and Classification for Effective Data Rights Management
Introduction:
Nowadays, data security has become a top priority. As the data is generated and shared more exponentially, the safeguarding of sensitive information has become more challenging while being crucial. Data encryption and classification are the two major aspects of data rights, and they play a leading part in protecting information from involuntary or Best geofence storage service and in compliance with privacy laws.

What is Data Encryption?
Data encryption is like putting your information in a safe, but it is a digital safe. This process entails encoding the plain text into an illegible text referred to as ciphertext with a specific algorithm and key. This procedure makes sure that even if somebody who's not authorized is granted access to the data, they will still not be able to decrypt it without the corresponding decryption key.
Imagine that you want to send a secret message to your friend. Instead of writing the message clearly, you mix it up using some secret code that only you and your friend know. Without the key, any interposition would only yield nonsensical letters.
What is Data Classification?
Data classification is grouping the data according to its level of sensitivity and significance. It also allows organizations to categorize their data holdings and decide which data needs to be protected at what level. Classification is usually done by tagging data with a label that identifies its security requirements or handling process.
Data classification is like putting your stuff into different boxes. All your important documents might go into a folder, another for pictures and one for miscellaneous notes. Every folder is labelled to indicate what paperwork is inside of it and how you should handle it.
Effective Data Rights Management
Encrypting and classifying data are crucial in the context of the formulation of advice on the management of data rights with the objective of attaining maximum data protection and regulatory compliance. Here's how they work together, Here's how they work together:
Data Identification:
This high classification facilitates to define the sensitive data that needs to be encrypted conveniently. By splitting the data into groups according to the application of encryption technologies, information systems can address the shortage of encryption means and distribute the resources in a reasonable way.
Access Control:
Encryption is a safeguard against unpermitted access, and people with classification rights choose who to give access to encoded information. The access controls can build on data classification labels so that only the laid-out clearance users, possessing the proper clearance can unscramble the cipher and access sensitive information.

Conclusion:
The use of data encryption and classification forms part of comprehensive data rights management plans. Encryption works to make Best Database Backup Services only accessible to authorized people. While at the same time, sensitivity labels can be used to classify easy-to-reach data from data that requires more protection. Organizations can provide an appropriate environment for data if they combine these approaches. They can take care of risks, protect confidential information, and be consistent with data privacy regulations.
#Best object storage software#Best Database backup Services#IT Security services#Cyber security company
0 notes
Text
Maximizing Productivity with Google Workspace and Microsoft 365 Consulting Services

Super Cloud IT offers expert consulting services to maximize productivity with Google Workspace and Microsoft 365. Our skilled professionals optimize your digital workspace, ensuring seamless collaboration, efficient communication, and effective task management. From tailored implementation strategies to ongoing support, we empower your team to leverage the full potential of these platforms. Elevate your productivity with Super Cloud IT's comprehensive solutions, tailored to your unique business needs.
0 notes
Text
At MSP Desk, our mission is to be the trusted technology partner for small to mid-sized businesses in Toronto, ON, and the surrounding GTA area. We strive to provide comprehensive technical support and solutions that help our clients focus on what they do best while we manage all their technology needs. Our ultimate goal is to help businesses grow and achieve their full potential through the effective use of technology.
#Managed IT Services for Business#IT Security Services#Custom IT Services#Cloud Services for Business
1 note
·
View note
Text
Dorothy Wete
Website: https://weteandcompany.net/dorothy-wete/
Address: 14003 Barkham Court, Laurel, Maryland, 20707
Wete and Company, Inc is an IT consultant firm specializing in IT security. Dorothy Wete and Company focuses on strategy, organization, business processes and technology providing efficient results. Wete and Company provides the experience of a large firm with the structure and focus of a small firm catering to the client’s needs. Wete and Company strives for improving the effectiveness and efficiency of IT, while minimizing costs to businesses.
LinkedIn: https://www.linkedin.com/company/wete-&-company
1 note
·
View note
Text
Address: 14003 Barkham Court, Laurel, Maryland, 20707
Wete and Company, Inc is an IT consultant firm specializing in IT security. Dorothy Wete and Company focuses on strategy, organization, business processes and technology providing efficient results. Wete and Company provides the experience of a large firm with the structure and focus of a small firm catering to the client’s needs. Wete and Company strives for improving the effectiveness and efficiency of IT, while minimizing costs to businesses.
1 note
·
View note
Text
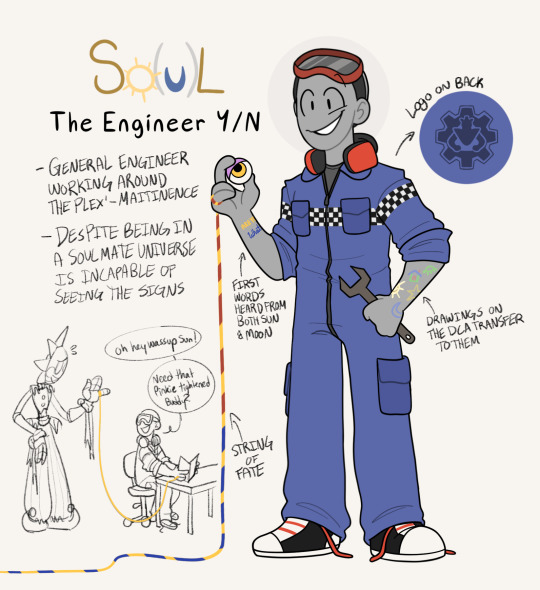
The base Y/N design for my soulmate AU!!
#my art#sun#fnaf#au#so(u)l#fnaf security breach#dca#daycare attendant#parts n service#parts and service#y/n#y/n design#I’m debating just posting the fanfic on tumblr until I can get an A03 up then just editing the posts to link to the ao3 later on… I think#that’s what I’m gonna do#teehee anyways cringe is dead#so(u)l art
5K notes
·
View notes
Text






wonderful day to remember ninjago has a canon highschool au
#mad as hell i posted this like two days ago and tumblr ate it then logged me out of my acc????#lloyd has dyed blue hair inspired by mr snail dood inspired by that one ninjago scriptwriter that said he would btw. if you even care#anyway there are many scenarios buzzing in my noggin about gaps in the movie i’m filling them all with hcs#like i am so sure nya could go into service or social work or law or security because shes a genius when it comes to laws and rights#but she has anger issues and she hates authority so she can’t get a job anywhere#that’s why she loves being a ninja!!#plus her steel cap boots are for stomping on people!!!#hate zane’s characterisation in the movie it’s creepy asf in this he’s just everyone’s favourite lab partner#anyway more hcs in art cominbb soon#ninjago#the lego ninjago movie#tlnm#lego ninjago#lloyd garmadon#ninjago lloyd#ninjago jay#ninjago nya#kai smith#nya smith#ninjago kai#ninjago cole#ninjago zane
5K notes
·
View notes
Text
We Offer a Wide Variety of IT Services,Web Development, Mobile Development,SEO&Services,UI/UX Design
Information technology (IT) services are services used by organizations to create, manage, and deliver information, next to assisting with other business functions. Generally, the profitability of companies in the industry depends on their ability to innovate their services and grow their technical expertise.
#it services#it support#it solutions#it infrastructure#it companies#it consulting#it service management#it outsourcing#it help#it support services#it services company#it ticketing system#support it#it service provider#it consulting services#outsourced it services#it service delivery#it repair#it support and services#it security services#it service operations#it business services
0 notes
Text
Dorothy Wete
Website: https://seaislenews.com/wete-company-discuss-trends-digital-transformation/
Address: 14003 Barkham Court, Laurel, Maryland, 20707
Wete and Company, Inc is an IT consultant firm specializing in IT security. Dorothy Wete and Company focuses on strategy, organization, business processes and technology providing efficient results. Wete and Company provides the experience of a large firm with the structure and focus of a small firm catering to the client’s needs. Wete and Company strives for improving the effectiveness and efficiency of IT, while minimizing costs to businesses.
Dorothy Wete, Wete and Company # IT Security Services
LinkedIn: https://www.linkedin.com/company/wete-&-company
1 note
·
View note
Text
Dorothy Wete and Company

Website: https://seaislenews.com/wete-company-discuss-trends-digital-transformation/
Address: 14003 Barkham Court, Laurel, Maryland, 20707
Wete and Company, Inc is an IT consultant firm specializing in IT security. Dorothy Wete and Company focuses on strategy, organization, business processes and technology providing efficient results. Wete and Company provides the experience of a large firm with the structure and focus of a small firm catering to the client’s needs. Wete and Company strives for improving the effectiveness and efficiency of IT, while minimizing costs to businesses.
#IT Security Services #Dorothy Wete and Company
LinkedIn: https://www.linkedin.com/company/wete-&-company
0 notes
Photo

Solid Systems is an IT Security Provider in South Africa offering IT Security solutions & services with an aim to improve the key challenges faced by enterprises, flexibility & cost-effectiveness of the information security & compliance programs.
We offer IT security services designed to shield your critical IT environment from harm. From assessing the state of your vulnerabilities to providing day-to-day security functions, our team has the knowledge and expertise to give your organization peace of mind.
#IT Security#IT Security Provider#IT Security South Africa#IT Security Company in South Africa#IT Security Service Provider#IT Security Services#IT Security Solutions#IT Security Company
0 notes
Text
Safeguarding Businesses with IT Support Services in Cyprus
Introduction:
In the fast-paced digital world of today, IT Support Services in Cyprus depend on strong services to strengthen their defense against cyber security threats. This introduction highlights the importance of cybersecurity as a great defense mechanism for enterprises; it also underlines the role played by IT support services in shielding businesses from dynamic online threats.

Digital Defenders: The Role of IT Support
IT support acts as the first line of defense against many digital threats. Whether it is in fixing technical problems or implementing security measures, these professionals contribute significantly to the protection of businesses, ensuring the smooth running of their operations and preventing cyberattacks.
Cybersecurity Essentials: Keeping Businesses Safe Online
This underlines the core elements of cyber safety. Cybersecurity basics include things such as the use of firewalls, antivirus software, and also secure passwords. These tools are very crucial for businesses that seek to build a strong online defense, protecting valuable information from potential intrusions and maintaining a stable digital space.
Threats Unveiled: Recognizing Common Cybersecurity Risks
The world of cyber threats is being explored and the need to identify the common risks is highlighted. From phishing scams to malware attacks, the knowledge of these threats enables businesses to have specific security measures and be up-to-date on such impending threats in the digital world.
Tailored Solutions: Adapting IT Support to the Business Requirements
Its support is more than a one-size-fits-all formula. This talks about the flexibility of IT services to suit unique business requirements. Individualized solutions require specifically tailoring IT strategies, infrastructure, and security mechanisms to meet the specific challenges and also needs of each company with personalized means.
24/7 Vigilance: The Importance of Continuous Monitoring
Insisting on vigilance at all times highlights the importance of 24-hour surveillance for potential cyber-attacks. IT support provides continuous surveillance, quickly responding to any anomalies or suspicious activities that may arise in order to sustain a secure digital atmosphere for businesses.
Data Protection Demystified: Ensuring Confidentiality in Transactions
The intricacies of data protection highlight the importance of protecting confidential information in transactions. The confidentiality and integrity of the data are ensured by implementing encryption, secure protocols, and also access controls by IT support, which creates a safe digital environment for financial and business transactions.
Budget-Friendly Security: IT Support for SMEs
This speaks about the cost-effective IT support solutions for smaller businesses. It focuses on the affordability of cost-efficient security solutions designed to fit the size of small and medium-sized businesses, thus providing cybersecurity support to organizations that may have limited funds.
Rapid Response: Swift IT assistance as a cyber attack mitigation strategy is important for the security of the system.
Thus, this shows the role that prompt IT service plays in the fight against cyber attacks. A quick response will help to identify the threats, and neutralize them before they do too much damage to a business’s digital infrastructure, and keep it very resilient.
Staying Ahead: The Evolving Nature of the Cybersecurity Strategies
Highlighting the changing nature of cyber threats stresses the constant development of cybersecurity solutions. It is a matter of staying ahead, which requires proactive strategies, consistent security protocol updates, and also innovative technologies that can effectively respond to new threats and provide a strong defense against the cyber threat evolution.
Conclusion:
To ensure security in the business, the most important thing is to give priority to cybersecurity through IT support services. With continuous surveillance, employee awareness, and quick actions, firms can move through the changing digital space safely. IT Security Services in Nicosia, and Spictera is a trusted partner that provides customized services.
0 notes
Text
The Critical Role of IT Services in Data Backup & Ransomware Protection
In the digital landscape, IT services play a pivotal role in safeguarding crucial data through robust backup systems, serving as a bulwark against potential ransomware threats. With meticulous data backup protocols, businesses ensure resilience against data loss, while cutting-edge IT solutions fortify defenses against ransomware attacks. The symbiotic relationship between IT services and data protection is indispensable, fostering a secure digital environment essential for organizational continuity and integrity.

0 notes
Text
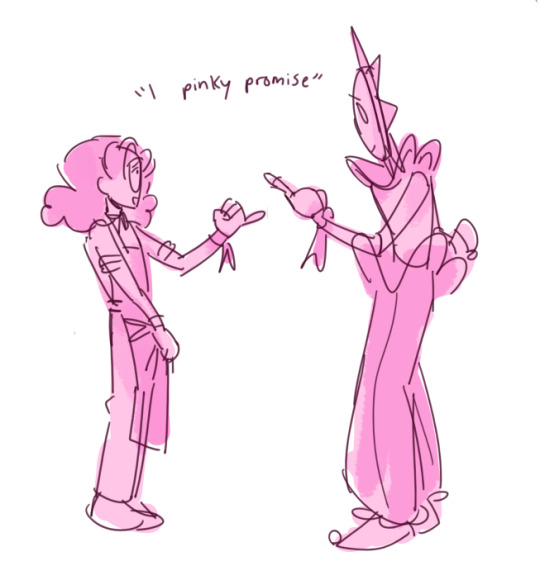
DAYDREAMERS BLAST AUGGHHHH🦅💥🦅‼️🦅💥💥‼️🦅
#hi yesss daydreamers update#im suuuch a slow writer but she is here!!!#its the classic parts and service chapter yall how fun!!!!#my art#daydreamers#charlie daydreamers#sun fnaf#fnaf sun#sundrop#sundrop fnaf#sun security breach#sun x y/n#dca fandom#the daycare attendant
561 notes
·
View notes
Text
Companies nowadays are getting SO comfortable asking for our social security numbers.
Like why tf does Optimum need my social to install wifi? They're just an internet provider, they don't need my social. I don't care that the last people living at my location didn't pay their bill, there are a dozen other ways to prove that I'm not them without me handing over my social.
Anyway, hot tip, legally you can refuse to give your social security in unnecessary cases like this. If a company needs to prove that you are who you say you are, they have alternative ways to do so.
#not dp related#and y'all im SO fucking cautious about fraud#that's really what this is about#protecting yourself from fraud#i just always say i dont give out my social over the phone#if kelly from geico needs my social security to prove my identity post-crash#then she can tell geico to go fuck themselves and whatever dispute between our insurance companies is between them#here's the police report again hasta la vista#if optimum needs my social to untag my apartment for 'do not service'#then they can go fuck themselves there are other ways to prove i'm not Juan#here's my billing address hasta la vista babey
8K notes
·
View notes
Text

My dogs my beloved dogs!! The first line of beastial spirit vine soldiers from my LoK AU. Created by Baatar when during experimentation, he discovered the spirit energy after being condensed causes the vines to react strangely to machinery and processed material. Turning the inorganic to organic.
These soldiers are comprised of spirit vines that have mutated in reaction to the condensed activated spirit energy and adhered themselves to the suits. Similar to "mimics" in a way, they can conceal their mouths fully so they're indistinguishable from human soldiers, though very astute earthbenders may notice they neither breathe nor have a heartbeat.
#LoK#Legend of Korra#LoK AU: Sovereign Guard#Neon Ocean Art#[ *pointing* looookk my puppies!#they are so 'get your fuckin dog bitch. it dont bite. yes it do' coded you know???#I've had these sketches for nearly 3 years omfg that is how long I've been wanting to talk about them#and this is only series 1 there are other variants including the mecha suits#There is so much more going on with them as well#they aren't sentient they cant think at all#in essence they are funny little plant dudes hehehe#only Baatar and Kuvira know about them and they're hidden throughout their forces#of course they can't do any bending either but that doesn't mean they aren't capable of holding their own#any time you see an immediate security detail around Baatar specifically you can guarantee it's mostly comprised of these#they start out rather simplistic where they just take orders and not much else#but over time they start slowly mutating on their own such as becoming more prone to reacting to Baatar's emotions without him realizing#or taking commands he hasn't said yet#they're also the perfect disposal service for things you want gone and not found#they'll eat anything ]
115 notes
·
View notes