#is great security concern for the owner and author of said code
Text
youtube
oh, hey. so does anyone remember modding is practically illegal
#i have THOUGHTS about this topic#most of all is that i hate that this is how business is played#in short - mods might be cool but digging through game code and releasing your additions to it in public domain even if done freely#is great security concern for the owner and author of said code#i still find this atrocious and extremely unfair and plain wrong as mods are made by the Most Passionate members of the community with thei#own sweat and blood and you should only encourage this approach to your product#but i can now see the other side of the issue and like okay i see how modding could pose an issue for the company now#but dammit the solution is to take control of this initiative and not ban it and especially not lawsuit someone for this#(looking very fucking sternly at nintendo)#btw this channel is great and has a lot of eductational topic about law surrounding gaming it's extremely interesting to listen to#even if it may cause some gamerrage at how the things are in law terms#gaming#nintendo#zelda botw#the legend of zelda breath of the wild#i aged five years while i was typing that name xD#Youtube
1 note
·
View note
Text
Sunday, June 13, 2021
Rash of mass shootings stirs US fears heading into summer
(AP) Two people were killed and at least 30 others wounded in mass shootings overnight in three states, authorities said Saturday, stoking concerns that a spike in U.S. gun violence could continue into summer as coronavirus restrictions ease and more people are free to socialize. The attacks took place late Friday or early Saturday in the Texas capital of Austin, Chicago and Savannah, Georgia. In Austin, authorities said they arrested one of two male suspects and were searching for the other after a shooting early Saturday on a crowded pedestrian-only street packed with bars and restaurants. Fourteen people were wounded, including two critically, in the gunfire, which the city’s interim police chief said is believed to have started as a dispute between two parties. In Chicago, a woman was killed and nine other people were wounded when two men opened fire on a group standing on a sidewalk in the Chatham neighborhood on the city’s South Side. In the south Georgia city of Savannah, police said one man was killed and seven other people were wounded in a mass shooting Friday evening.
Summer camps return but with fewer campers and counselors
(AP) Overnight summer camps will be allowed in all 50 states this season, but COVID-19 rules and a pandemic labor crunch mean that many fewer young campers will attend, and those who do will have to observe coronavirus precautions for the second consecutive year. “Camp might look a little different, but camp is going to look a lot better in 2021 than it did in 2020, when it didn’t happen,” said Matt Norman of Atlanta, who is getting ready to send his 12-year-old daughter to camp. Even though most camps will be open, reduced capacity necessitated by COVID-19 restrictions and the labor shortage will keep numbers well below a normal threshold of about 26 million summer campers, said Tom Rosenberg of the American Camp Association.
Mexico says COVID-19 has affected a fourth of its population
(Reuters) About a quarter of Mexico’s 126 million people are estimated to have been infected with the coronavirus, the health ministry said on Friday, far more than the country’s confirmed infections. The 2020 National Health and Nutrition Survey (Ensanut) showed that about 31.1 million people have had the virus, the ministry said in a statement, citing Tonatiuh Barrientos, an official at the National Institute of Public Health. According to Barrientos, not all of the people in the survey’s estimate necessarily showed symptoms. The survey was based on interviews with people at 13,910 households between Aug. 17 and Nov. 14 last year, and confirmed preliminary results released in December.
Peru on edge as electoral board reviews result of disputed presidential election
(Guardian) Peru was on a knife-edge on Friday as its electoral board reviewed ballots cast in the presidential election, after a challenge to the tally by the losing candidate Keiko Fujimori. The final tally gave the leftist teacher Pedro Castillo a razor-thin 50.17% to 49.83% advantage over his rightwing rival Fujimori, which amounts to about 60,000 votes. However, the country’s electoral authority has yet to confirm the win, and Fujimori, the scion of a controversial political dynasty, has refused to concede. She alleges fraud, even though national and international observers said the vote was clean, and has called for up to 500,000 votes to be nullified or reexamined, forcing the electoral board to conduct a review of ballots.
For Cornwall, G7 summit brings disruption
(AP) Towering steel fences, masses of police, protests on the beach: The Cornish seaside’s turquoise waters and white sandy beaches are looking decidedly less idyllic this week as leaders of the Group of Seven wealthy democracies descend for a summit. U.S. President Joe Biden and leaders from Canada, France, Germany, Italy and Japan are arriving for three days of talks starting Friday at the tiny village of Carbis Bay, near St. Ives in Cornwall. The region is a popular holiday destination in the southwestern tip of England. Locals may be used to crowds and traffic jams during the peak summer tourist season, but the disruptions caused by the summit are on another level. A naval frigate dominates the coastline, armed soldiers guard the main sites and some 5,000 extra police officers have been deployed to the area. Authorities have even hired a cruise ship with a capacity of 3,000, moored offshore, to accommodate some of the extra officers. A main road is closed for the whole week, and local train lines and bus services have been shut down. A 3-meter (10-foot) tall metal fence nicknamed the “ring of steel” has been erected around Treganna Castle in Carbis Bay, where world leaders will stay. Security is also tight in the nearby town of Falmouth, the main base for international media covering the summit.
World leaders are in England, but beautiful British beaches have stolen the show
(Washington Post) When President Biden shared a photo to Twitter on Thursday of him standing alongside British Prime Minister Boris Johnson and gazing out onto an unspoiled, sandy white beach from the Group of Seven summit in Cornwall, England, the post was supposed to be a tribute to the “special relationship” between the United Kingdom and the United States. But to many, it was the image of the picturesque coast that stood out. It looked somewhat suspicious. Too good to be true. Others questioned the authenticity of the scene, wondering whether it was photoshopped. Although it is true that some of Britain’s beaches have a reputation for pebbles, angry seagulls that steal food from unsuspecting tourists and diapers that float in murky waters, the county of Cornwall boasts some of the country’s best seaside destinations—complete with calm, clear waters that are perfect for swimming in and long stretches of soft sand that attract families from around the world. Carbis Bay is one of several beaches that make up St. Ives Bay, which, according to the Cornwall tourist board, is considered by the “Most Beautiful Bays in the World” organization to be one of the world’s best. The bay is described as being “surrounded by sub-tropical plants and lapped by turquoise waters.”
Ransomware’s suspected Russian roots point to a long detente between the Kremlin and hackers
(Washington Post) The ransomware hackers suspected of targeting Colonial Pipeline and other businesses around the world have a strict set of rules. First and foremost: Don’t target Russia or friendly states. It’s even hard-wired into the malware, including coding to prevent hacks on Moscow’s ally Syria, according to cybersecurity experts who have analyzed the malware’s digital fingerprints. They say the reasons appear clear. “In the West you say, ‘Don’t . . . where you eat,’ ” said Dmitry Smilyanets, a former Russia-based hacker who is now an intelligence analyst at Recorded Future, a cybersecurity company with offices in Washington and other cities around the world. “It’s a red line.” Targeting Russia could mean a knock on the door from state security agents, he said. But attacking Western enterprises is unlikely to trigger a crackdown. The relationship between the Russian government and ransomware criminals allegedly operating from within the country is expected to be a point of tension between President Biden and Russia’s Vladimir Putin at their planned summit in Geneva on Wednesday. The United States has accused Russia of acting as a haven for hackers by tolerating their activities—as long as they are directed outside the country.
Pandemic relapse spells trouble for India’s middle class
(AP) India’s economy was on the cusp of recovery from the first pandemic shock when a new wave of infections swept the country, infecting millions, killing hundreds of thousands and forcing many people to stay home. Cases are now tapering off, but prospects for many Indians are drastically worse as salaried jobs vanish, incomes shrink and inequality is rising. Decades of progress in alleviating poverty are imperiled, experts say, and getting growth back on track hinges on the fate of the country’s sprawling middle class. It’s a powerful and diverse group ranging from salaried employees to small business owners: many millions of people struggling to hold onto their hard-earned gains. The outbreak of the pandemic triggered the worst downturn since the Great Depression of the 1930s and as it gradually ebbs, many economies are bouncing back. India’s economy contracted 7.3% in the fiscal year that ended in March, worsening from a slump that slashed growth to 4% from 8% in the two years before the pandemic hit. Economists fear there will be no rebound similar to the ones seen in the U.S. and other major economies.
‘Xi Jinping is my spiritual leader’: China’s education drive in Tibet
(Reuters) Under clear blue skies, rugged peaks and the spectacular Potala Palace, one image is ubiquitous in Tibet’s capital city Lhasa: portraits of Chinese President Xi Jinping and fellow leaders. China is broadening a political education campaign as it celebrates the 70th anniversary of its control over Tibet. Civilians and religious figures who the government arranged to be interviewed on the five-day trip pledged loyalty to the Communist Party and Xi. Asked who his spiritual leader was, a monk at Lhasa’s historic Jokhang temple named Xi. “I’m not drunk ... I speak freely to you,” said the monk named Lhakpa, speaking from a courtyard overlooked by security cameras and government observers. “The posters [of Xi] coincide with a massive political education programme which is called ‘feeling gratitude to the party’ education,” said Robert Barnett, a Tibetan studies veteran scholar at the University of London’s School of Oriental and African Studies.
Long overlooked, Israel’s Arab citizens are increasingly asserting their Palestinian identity
(Washington Post) Growing up in an Arab village in northern Israel in the 1990s, Mahmoud Abo Arisheh was sure of at least two things: He was Israeli, and he was not allowed to talk politics. “Be careful, or the Shin Bet will get you,” his parents told him, referring to Israel’s domestic security service. Decades later, much has changed: Abo Arisheh is a lawyer, a poet and a theater director in Jaffa. He attends protests and talks politics freely—in Arabic, Hebrew and English. And while his citizenship may remain Israeli, the identity most dear to him is that of a Palestinian. “I didn’t know anything about being Palestinian,” said the 32-year-old, “but then I opened my eyes.” And now, it seems, so are many others. In just the past month, Palestinian citizens of Israel—also known as Israeli Arabs—have risen up in mass, nationwide demonstrations to protest Israeli evictions and police raids. They have been arrested by the hundreds following some of the worst communal violence between Arabs and Jews in Israel’s post-independence history. For a community that is often overlooked despite numbering nearly 2 million people—or about 20 percent of the Israeli population—these are momentous days indeed.
Nigerian police fire tear gas to break up protests over rising insecurity
(Reuters) Police fired tear gas and detained several demonstrators in the Nigerian cities of Lagos and Abuja on Saturday during protests over the country’s worsening security situation, Reuters witnesses said. Anger over mass kidnappings-for-ransom, a decade-long Islamist insurgency and a crackdown on protesters in Lagos last October has fueled demands for the government of President Muhammadu Buhari to do more to tackle violence and insecurity. Reuters witnesses in Lagos and Abuja saw police shooting their guns into the air and firing tear gas into the crowds to disperse the demonstrators, who held placards and chanted “Buhari must go”. Officers were also seen smashing mobile phones confiscated from protesters, who also denounced the country’s 33.3% unemployment rate.
2 notes
·
View notes
Text
Produced Houses
. Is It Worth Making A Top Quality Build?
https://www.bromleygaines.co.uk/new-builds/ : #f9f9f9;border: 1px solid #aaa;display: table;margin-bottom: 1em;padding: 1em;width: 350px;">
Content
How The Property Improvement As Well As Repair Solutions In London Job.
Rj Repair Services.
Beginning Your Project.
Tiny Orangery Conservatories And Also Glass Conservatories.
This did not take place and also at 1920 on 13th Jun he mentioned he reimbursed the cash but would certainly take two days to clear, something my financial institution educated me would only take about two hours max as was a financial institution transfer. Having sent out messages today giving more opportunity to reimbursement I left adverse comments on Facebook. He has actually ultimately taken the page down, not the actions of a person that is genuine. I understand he made use of to trade as WBA Cleaning as well as Maintenance according to his invoice he sent. Please do not make use of NewLook building services Ltd based in Chesterfield.
Are orangeries warm in winter?
No - orangeries are not cold in winter, in fact they are very warm. Orangery roofs are highly thermally efficient, meaning that orangeries are warm and comfortable, whatever the time of year. building contractors local are as warm as any other room in your home – even in winter.
However, every sector has its cowboys and also plainly the structure trade is an industry. You'll be functioning closely with the builder of your new house for a minimum of six months, and you want to ensure you know with that you're. agreeing to work. The exhilaration of beginning construction on your new house might make you wish to hurry with this procedure, yet take your time; it's certainly worth it. Double check that the building contractors you want are actively constructing in those areas. If you're moving to a McMansion in Arizona, it won't be useful to fall in love with a builder that just constructs little residences in Alaska.

The very first tip-off is if they asked to be paid in cash, or cash-in-hand all with a pledge on no BARREL to be paid. There are, usually, a minimum of 100,000 grievances each year about them. They wreck points for completely trusted contractors, as well as for all the discuss them, they're in the minority-- it simply happens to be a minority that gets a great deal of promotion. When builders have an excess of finished new buildings, there is commonly higher inspiration to market.
If you are an accredited building contractor or tradesperson in NSW, you require to get residence building payment cover for each house structure job over $20,000 including GST. If you fail to show you have relevant site-based experience in a wide range of structure construction job, we can not accept your application. This includes dealing successfully with sub-contractors, customers and also others. As soon as you recognize what licence kind you want, and also you have actually examined you have the right credentials as well as experience, you can get a permit or certificate.
Just How The Residential Property Improvement As Well As Repair Solutions In London Work.
If you pick among these uninhabited brand-new residences, switching over out specific attributes for upgraded variations is often a straightforward procedure, as well as the home builder might agree to include a few of these upgrades as a reward. Don't depend on the builder to tell you when that factor has actually been gotten to. Instead, appoint Thame builder to check out the work and confirm that what you are paying for deserves the cash, and is full to constructing codes. Structure agreements are written by specialists accustomed to building terms and trade techniques. As well as it's likely that individuals who have put together the file you are informed is there to secure you, was, or is, a builder or market expert.
What is the difference between an orangery and a sun room?
The most striking difference between sunrooms, conservatories, and orangeries are: Orangeries are supported by solid brick-built pillars, low-level walls and/or an insulated internal pelmet. Orangeries tend to feature bright & airy roof lanterns, although these can be added to conservatories too.
While you don't want a home builder that purposely takes a long time to finish a task, neither do you want a builder who is eager to do the job quickly, or that regularly knocks off early during the task. Making your Certificateor Diplomain building as well as building and construction must not gobble every one of your time and savings.
Rj Repair Providers.
Are orangeries warmer than conservatories?
Orangeries tend to be a little warmer than conservatories because they have brick walls which can be insulated to keep in the warmth. Because of the brick walls, the heat will have a harder time escaping. The cold will also have a harder time getting in thanks to the insulated walls.
Sign-up to our newsletter and keep up to day with everything home building/ layout associated including information from your much-loved neighborhood home building contractors. If you are a person that holds a structure or swimming pool building licence or certificate, you are needed to do Continuing Specialist Development. Your permit will certainly be automatically suspended if you do not adhere to an order by a court or the NSW Civil or Administrative Tribunal to pay money for a building case.
Do glass box extensions need foundations?
The principal of a glass room does mean the base required is fairly flexible as you do not actually require foundations as you would for a conservatory or brick built extension but only require concrete pads where the support legs are situated.
Most rogue builders do not bring insurance, either, which once again could function to your detriment if an accident took place. Cowboy contractors are merely rogue investors, of course, usually with little or no knowledge of structure, so you wind up with a messed up work-- that's if it's ended up in all. Experience as a Proprietor Building contractor, or as the owner of a Proprietor Building Contractor Authorization, is not appropriate to satisfy the functional experience needs to get a permit or certificate as a contractor. From this moment forward, Checkatrade worked to assist display the best tradespeople from around the UK and has continued to do so since.
Beginning Your Project.
These internet sites hold the information of countless home builders and structure business. Home builders' scores on these sites are based upon the responses from clients, so the much better the task done by the home builder, the greater the ranking. Keep an eye out for boards on building sites in your area, yet always do your own research study also.
Do conservatories need foundations?
Like other new extensions, conservatories must have foundations in place. Foundations are necessary for transmitting the building's weight safely to the ground. Without adequate foundations, the structural integrity of a conservatory is severely affected.
As the day progressed we heard nothing and also I started to try to call. Ultimately he addressed and reiterated his purpose to do the job. When he fell short to do so or even allow us know as it was obtaining later wouldn't show up we realised something was incorrect. The following day after countless efforts through message and also calls,, he eventually agreed to refund the money after 1430.
Small Orangery Conservatories And Also Glass Conservatories.
youtube
Let The Sunlight In! Everything You Needed To Know Regarding Sunrooms
They are cowboy builders.They took our deposit worth ₤ 5000 as well as vanished. We took care of to track them down and also found they own one more registered business called NewLook plastics Limited.
Does an orangery add value to your home?
An orangery can increase the value of your property by almost as much as adding a traditional extension. On average, an orangery will cost upwards of £20,000, but it can be cheaper, depending on the size, style, features, and materials you choose.
Newly Constructed Houses.
Information regarding general building work permits and certifications. lately conducted a study finding that possibly 2.5 m people have had a conflict with their building contractor or designer in the past 3 years. does not claim the number of individuals it checked so, if you read my current short article The dangers of studies, you must understand to take the number with a pinch of salt.
It's a help, as well, if the builders and participants of some profession group-- although check that too, given that cowboy structure companies have been known to fake membership. Ultimately, never ever pay in money, as well as absolutely never ahead of time-- you need to only spend for work that's been finished. The very best thing is to learn to identify the cowboy home builders early, so you can transform them away-- it saves a great deal of difficulty later.

Anybody building a brand-new residence needs to sign a contract, as well as while the builder states it is "typical documentation", to lots of people, it's anything however. Besides the late shipment of the ownership a number of other malpractices are complained versus the building contractors.
Inspect online for testimonials as well as get comments from individuals that have actually used the home builders prior to. We reserved WBA building as well as building based in Cheltenham using Facebook search, to provide and also fit a garden bar at expense of ₤ 550. The Thursday beforehand he got in touch with to state as the climate was poor he would not be able to execute the job. Nevertheless, on the Saturday we called him as well as said as the weather condition looked great would he be concerning finish the work. This he stated he would as well as would certainly call 30 minutes in advance so we really did not have to wait in.
Also, the warranty solution has actually been really fast when required.
Beazer Houses - Exceptional experience with the sales group and also the constructionOmar E.
Exceptional experience with the sales group and the construction manager cooperating with me on all queries.
Victoria was currently the biggest market in the country for new detached residences as well as the state has actually uploaded a near-record variety of beginnings in 2017/18.
They don't feedback as well as we could not acquire anyone to help accessibility services.
Brain was our sale's rep. He was excellent in assisting us seal the deal.
It needs to be a fulfilling experience that arms you with important knowledge and also establishes a straight path to your job advancement. A degree from an Australian university (in building, construction, building task management, building management, used scientific research, amount surveying, or building and construction business economics). The level must require the applicant "to undertake the equivalent of 4 years' full time research and also a required job placement".
#home builder#best builders#quality build recommend#glass room extension#extension with glass#general builders local#local general builders#home refurbishments#refurbishments services#office refurbishment#home conversions#house conversions#attic conversions#home extensions#house extensions#extension builders#architect builders#new home developments#conservatory extension#local architects#new property developments#glass rooms#building contractors#residential architect#best new home builders#building contractor#kitchen refurbishment#garage conversions#convert garage to living space#garage extension
2 notes
·
View notes
Text
The android cemetery (Chapter 5)
Daniel was already at home and out of uniform when Gavin entered the two-story apartment. The android was lounging on the couch in the floor/downstairs living room combo. He wore a short-sleeved button-up shirt in red and blue jeans, a welcome break from his preferred upper-class butler’s style. There was a bit of a snob in Gavin’s boyfriend, a trait the man had never expected to find himself drawn to. But attraction obviously followed its own rules, especially if one of the attracted in question didn’t even have hormones.
Daniel was holding his phone in one hand and tickling Loki, Gavin’s blue-point ragdoll cat, under the chin with the other. Another cat, a black Somali-mix called Thor, was lazing stretched out on the couch. The tom made sure not to touch the android. Thor accepted, even demanded, the occasional petting from Daniel, but he would not purr for the still somewhat new family member.
Only after Gavin had closed the door behind himself did Thor jump down and proceeded to circle his returned “mama”’s legs. There was no competition from the other tom for now. Yes, viewed in this light that new biped had something going for it. The more time Loki spent with it, the more time there was for just Thor and Mama!
Gavin’s lips formed a silent “Phone - who?”. The answer came in the form of Morse-code from Daniel’s LED: “Emmas-stop-therapist”.
Ah, right, Emma Phillips. That was something new. Not just was a new boyfriend living in the apartment, along with Daniel Gavin had acquired an extended family. Before Daniel it had only ever been himself, his cats and the parents at the holidays. There had not been a shortage of sex, but as the man had explained to Daniel last year, beings friends wasn’t a prerequisite for that. Boyfriends were a hassle anyway, because sometimes they turned out crime lord Jacques Villareal’s right-hand men and tried to shoot Gavin. Admittedly that had happened only once, but it still stung years later, because for the first time since college Gavin had actually harbored feelings for that one.
Of course there had always been Tina Chen and both of them had fully expected to end up together out of habit, because it wasn’t fun to be all alone when you were old and with only a slim pension, because androids had forced you out of employment. But here Gavin Reed was, in a steady relationship, and Daniel had promised to help Tina find a boyfriend of her own.
Gavin slipped out of shoes and jacket. Tip-toeing around Thor he went to the kitchen and opened the fridge. It contained mostly fresh ingredients nowadays instead of a pinned-on list of food delivery services across the city: Seafood for the organics and thirium sherbet for Daniel. For all their efficiency, androids were not perpetuum mobiles. Once a month they had to replenish their lifeblood. Many deviants, especially those who were openly living among humans, had adopted to the practice of consuming smaller doses during regular mealtimes. Daniel had tried that, too, but realized that he enjoyed watching his human eat a lot more than doing it himself. And of course there were those times when he was fed up with humanity and would gulp down the blue blood right out of the bottle to prove a point.
Gavin got a can of beer from the fridge and a strip of bubble gum from a basket on top of it. Then he returned to the living room where Daniel had just finished his conversation.
The man slumped down on the couch opposite to his partner and teased Loki with the bubble gum. Just when the cat jumped for it, Gavin tossed the strip towards Daniel, then caught Loki and put him on the floor gently. You absolutely didn’t want a cat on the sofa when you were about to cuddle feet to feet with your partner. In fact, you absolutely, positively did not want a cat with you when you were presenting your naked toes anywhere and for any reason.
Gavin then flicked open the beer. For a few precious minutes he let the world do its own thing. There was beer and tickles and the cats bouncing over each other on the floor and Daniel forming shapes out of his bubblegum that other than him only Gandalf had managed with his smoke pipe in the first Lord of the Rings movie.
This was home, this was bliss, this was life going Gavin’s way for once. He had laid claim on what he had wanted and would not give it back anytime soon!
Eventually there was no more beer and the gum had went to a place where it would be the maid’s problem tomorrow. They smiled at each other.
“To quote Emma: Stupid therapist and her ideas”, Daniel remarked, referring to the talk he just had. “I swear, if she knew who I really was she’d want me to tell Emma!”
“Kid’s got to step in line”, Gavin replied. “’cuzz Captain Allen already called dibs on that.”
“The sucker did what?!”
Whatever peeve Daniel had with the therapist was forgotten over the news. Gavin recounted what had transpired at the DPD, finishing with: “Yumiko gave me funny looks all the time. She suspects I butchered the archive android for your new skin module.”
“Considering what you took out of there when all you needed was a bloody broom I wouldn’t put that past you, either!” Daniel said, laughing with that raspy industrial noise androids produced at such an occasion. It made him sound like a chain smoker. “But I wouldn’t worry overmuch. My files are in order. Everything’s there: no irregularities at first initialization, delivery to the cyberlife store, sold to my first owners, then you buying me from them after a year, then getting lended to the DPD and finally our accident on Lake Erie followed by the android museum buying me and putting me back in shape.”
“I dunno… I said on occasion that I found you in the trash.”
“That might not be a contradiction. My first owner might not have liked you grabbing for free what he had just thrown away and charged you.”
“I would have hit him, had he tried that!”
Daniel winked when he replied: “Maybe you beat him out of his senses, but the resulting hospital bill would not show up in my file, right?” He flung himself forward and into the other’s arms. “You know that between the two of us I am the good guy!”
That claim caused them both to laugh. They kissed, then laughed some more and then Daniel tried to caress Gavin’s nose with his. He was met with an unwilling “Unh!”. Maybe it was the plastic nose feeling weird, maybe it was the childishness of the act or something else entirely, but Gavin hated it. Daniel adjusted his position for them to end up sitting in each other’s lap, forehead to forehead, arms around the other’s shoulders.
“The Underground Airline’s best hacker doctored my file”, Daniel said reassuringly after letting some time pass. “The very best.”
Gavin sighed. It wasn’t a sound of pleasure.
“What?”
The human grabbed his partner. He pushed Daniel backwards a little, stared him into the eyes as if looking for some sense to be found in the space behind them and when he could locate none barked:
“Your “very best” is a gaming bot, for fuck’s sake! It can make mistakes!”
Daniel shook his head. “I know that’s what she initialized as. But now Yuki is tracking the author’s keyboard strokes as the woman writes the intermediate chapters for Beasts of Fire.”
To Daniel’s surprise Gavin displayed no sense of wonder at that feat. Instead he was looking as if he was about to get flayed alive.
“But doesn’t that mean Yuki has to read that stuff?” the human uttered. “Why would any sane soul want to do that?”
Daniel playfully hit Gavin.
“Your taste in literature is abominable!”
Equally playfully dodging the “assault” Gavin replied: “I do not have a taste in literature!”
“I noticed”, Daniel laughed.
They were sitting next to each other on the couch now, the wall-high balcony window in their back and the new TV on the wall right in front of them. Gavin bent forward, elbows on his knees, head tucked between his fists. Daniel to the contrary leaned back and placed his feet onto the couch table.
“Okay”, Gavin started again, “let’s say everything is in order as far as Dean is concerned. So what did Super Smash Sister do with Daniel’s file? Did she leave it as is, creating two androids with the same DNA, or did she delete it? Well?”
Daniel jerked forward. His gaze met Gavin’s as the other was raising his head and while the human shot him an angry “See? Told you!” expression, Daniel’s own slowly changed to one of terror.
There was no need to answer the last question. Since there was no more PL600 down in the archive, Yuki Villareal would simply have deleted the accompanying file. Probably the whole case file, too. While humans who remembered Daniel having been there were all around the DPD!
“Yuki hasn’t… she wouldn’t…” Daniel sputtered.
“Of course she would! Yuki also had to hack Camp Five’s security, all in one night! And for that stunt there were no Hank and Connor to help out with passcodes. With a real challenge ahead of it, the little gold farming bot went the easy route in your case!”
“Yes.” Daniel slowly sacked towards his partner, who slung his arms around the android and hugged him tight. “Yes, you’re probably right.”
The Underground Airline’s hacker had been in a hurry due to some real minor stuff like Daniel, Gavin and Markus having had a shootout in the backyard of Brindleton Bay’s movie theatre...
“It’s all Markus’s fault!” Gavin claimed. “Idiot homeschooled arts major…”
“Well, what do you expect? He’s Connor’s great-something grandfather! Think of everything that’s weird about Connor and then remember that he is the improved Markus!”
“Yeah.” Gavin nodded. “That explains a lot, actually.”
Daniel picked up a cat at random. He put it on both their laps and started stroking. After a while the furball started tearing into Gavin’s upper leg with dedication.
“I shouldn’t have said that about Connor”, Daniel mused. “He’s dedicated… loyal… By right I should fall head over heels for him, but… eww.”
“Eww, plastic prick”, Gavin agreed.
“But he’s also my friend”, Daniel insisted. “Now. Yours, too.”
“No way!”
“I was right about the five of us becoming a team, I’m right about this, too.”
“Whatever. Let’s focus on the missing PL600. We need a replacement and quickly!”
The moment he had said it, Gavin cursed himself for having voiced his thoughts. The easiest solution to their dilemma would be to buy a pre-owned PL600 on e-bay, switch it off, shoot it a few times, drop it off a roof, run its legs over with the family car and put the resulting mess into the archive quietly. And of course Daniel was well aware of that, because he said: “You are not thinking of what I think you are!”
Gavin could have slapped himself that moment. His too quick trap be damned! Had the detective just kept it shut, he could have gone through with the plan tonight, using an urgent call from work as an excuse. Daniel and Tina would have went to the basketball game the trio had planned to watch, while he’d corrected his mistake from one and a half years ago. But that door was closing even as Gavin had spotted it in the corridor.
“Does it matter what I think, if I don’t go through with it?” he growled.
Disturbed in his bliss Loki jumped off the couch. He proceeded to claw away on it to regain his mental balance, only to get his claws detached from the fabric by the two bipeds. The cat turned once around itself and then decided to chase Thor onto the windowsill.
“‘sides”, Gavin followed through, “people say I look like Kamski. If roles were reversed and you needed a dead Gavin, you’d beat in Kamski’s skull and sell him to Allen as me!”
“I guess so”, Daniel had to admit. “Unlike PL600s there’s only two of you, though.”
“Moot point. You don’t want me to make use of all those PL600s. Come to think of it…” Gavin’s face brightened when what he perceived a near-genius idea came to him. So, basically what he thought of all his ideas. ”What if it was already dead?” the man whispered.
“What do you mean?”
“Think old androids! The hand-me-downs, or the ones destroyed in accidents, any android that cannot get sold or gifted away anymore or whose owner is simply too lazy to consider any form of re-use – where do you think they all end up?”
“Ugh.”
“Exactly!”
Both of them voiced it simultaneously, one sounding appalled, the other triumphant: “The solid waste landfill!”
1 note
·
View note
Text
Choosing A Professional Fence Company
How To Choose A Fence Company
By asking these and any other questions you may have during your consultation, you can find the very best Austin fence installers and professionals, like us at Barrier Fence. We invite you to call us at (512) 354-4409 to set up an assessment visit today.
If you have you have issues about the location of the property line or your fence, we recommend that you call a regional study business to find and plainly mark the pins to develop the home lines. Lee Fence and Outdoor will install the fence per your guidelines.
Tips To Choose The Best Fence Company
Lee Fence and Outdoor will eliminate and dispose of your existing fence for an additional fee. Please be recommended that if there are any parts of your existing fence that you wish to keep, let the installation team understand. Lee Fence and Outdoor will not get rid of anything not related to the fence task.
We ask that somebody would be on-site when our teams get here to go over the fence layout. Discrepancies from the original fence contract should be authorized by your Lee Fence and Outdoor salesperson.
This can change the initial fence layout. Given that these underground electrical fence are normally located close to the home line, you will require to call your underground fence specialist and have them mark the line prior to your brand-new fence setup.
Choosing The Best Fence Company

No. It is the property owner's duty to find these lines and inform Lee Fence and Outdoor to the area of said lines. Usually all corner, gate and terminal posts will be dug up and reset in the precise same spot. It is basic practice and within AFA market guidelines to cut line posts below the grade and re-space the new posts.
Each task is unique. Typically, we use a small piece of equipment called a mini-track to excavate the post holes. The mini-track is around 3' large. It depends upon our existing backlog. This fluctuates at different times of the year, but typically during the spring/summer months, we can have a numerous week backlog.
Your Lee Fence and Outside salesman would be able to provide you with an approximate lead time at the time of the website visit. Typically, most domestic fence setups will take 1 to 2 days to complete (Tips On Finding A Good Fencing Company).
Tips For Finding The Best Fence Company
Although Lee Fence and Outdoor teams are specialists in fence installation, our crews have limited understanding in proper cutting and pruning practices. Excessive trimming carried out by Lee and Fence Outdoor will undergo an additional charge. We would appreciate you cleaning up your shrubs as we do not desire to damage your manicured lawn.
Related Searches Include:
Datson Fence
New Fence
Great Job
Fence Installation
Folsom Fence Company
Commercial Fences
Aluminum Fences
Fence Contractor
Commercial Fencing
Installation Crew
Chain Link
Free Quote
Wooden Fence
Kirkwood Fence
American Fence Company
Free Estimate
Commercial Property
Customer Satisfaction
Final Product
Reliable Fence Services
See Portfolio
Pearl City
Fence Services
Fencing Needs
Residential Fencing
Residential Fences
Wood Fences
Iowa City
Frederick Fence Company
Fence Products
It might be helpful to notify your neighbors so that no issues emerge during the setup process with concerns to home lines. If you are having an old fence replaced that lies on the property line, it is advised that you inform your next-door neighbor. Your next-door neighbor might need to make plans worrying their family pets and might likewise wish to secure their yard or eliminate products from their side of the fence.

Typically your fence can be set up right up to, but not on the property line per town regulations. Some municipalities do recommend that you keep your fence off the home line 1' to 3' so that you are able to maintain your fence on both sides.
5 Tips On Finding A Good Fence Company
Frequently Asked Questions - FAQ
How much does it cost to put up a fence?
The typical cost of installing a fence is in between $13 and $50 per linear foot. The average overall cost of setting up a fence is around $988,but expenses can reach $ 7,000-- or more. The length of the fence,products utilized and add-ons such as gates can impact how much you end up spending for a fence installation.
What is the cheapest fence to install?
The cheapest fence you can install is a wire fencing at $2 per foot typically,while a 6-foot high wood privacy fence costs $13 to $25 per direct foot,and vinyl fencing for $15 to $30 per foot.
How much does a 300 ft fence cost?
Yard Fence Costs Per Foot Linear Foot Cheaper (Wire or Electric) Moderate (Wood) 8 $10 - $50 $100 - $200 100 $100 - $600 $1,000 - $2,000 150 $150 - $1,000 $1,500 - $3,000 300 $300 - $1,800 $3,000 - $6,000 1 more row
How much does Home Depot charge for fence installation?
Fence Installation Costs According to Home Depot,it can cost anywhere from $1,000 to $10,000 to install a fence,however many homeowners can expect to invest from $1,600 to $4,000. You can more precisely compute what your project might cost by determining how many direct feet your fence will be.
How much does an 8 ft fence cost?
8 Foot Wood Fence Cost The average cost to build an 8-foot wood fence is between $21 and $30 per linear foot using pressure-treated pine with dog-ear panels.
What is the best time of year to install a fence?
If you consider summertime and spring the peak season,then winter season is the best time to get the service and attention you desire from your fence expert. Make the most of the off season by doing your research study during the warmer months and getting ready for setup in the winter season.
Is it cheaper to build a fence yourself?
One of the advantages of installing a fence by yourself is that you don't need to pay a company for the labor costs. This typically winds up being less expensive in the end,and among the significant reasons the majority of people think about a DIY in the first place.
Is it cheaper to build a fence horizontal or vertical?
Horizontal fences tend to be more costly than vertical fences since they need a greater grade of lumber for the fence boards to decrease the possibility of drooping. However,like any horizontally-oriented board,they might droop over time.
What is the easiest fence to put up?
Vinyl fencing setup is so much easier the no-dig way. This implies you can invest less time on your house projects and more time with your household,friends,or whatever else you want to do.
An easement grants other people or business rights to particular kinds of access on your property. For more recent developments, it is more than likely a drainage easement. For older advancements, it is generally an energy easement. Easements typically require that you keep any kind of building, consisting of fence, off your home line 5' to 10' feet.
An easement is normally indicated on your property plot plan. If your plot plan is not readily available your local municipality would have the ability to offer you with this information. Yes. A corner lot is considered to have 2 front yards. Generally your municipality will just permit a 3' or 4' high fence in front yards.
youtube
Most municipalities will enable up to a 6' high fence in the side and rear backyard. Permitted fence heights in the front yard vary per town.
Tips To Help You Find The Best Fence Company
The swimming pool code states that your fence need to be at least 4' high. There are specific criteria that need to be satisfied for the 4' high fence to satisfy this code.

The Lee Fence and Outside salesman is really educated with your swimming pool code requirements and can discuss your various alternatives. It is your responsibility to read your deed restrictions associating with your fence - Tips For Finding A Good Fencing Company. HOA deeds and local building codes can limit easements, fence heights, color preferences and even material types.
We provide and install fencing and associated boundary security items such as gates, railings, guardrails and gain access to control systems - How To Find The Best Fencing Company. We likewise furnish and set up decks.
Top 6 Tips For Choosing A Fence Company
We normally just encounter issue when the ground freezes unfathomable. PVC/vinyl fence or aluminum fence are very resilient and need less maintenance. PVC/vinyl fencing is virtually maintenance totally free. PVC/vinyl fences are resilient, long-term, easy to tidy and ecologically friendly. You will never ever have to stress over staining, rotting, warping, termites, corrosion or rust.
All PVC/vinyl bottom fence rails and all gate posts are strengthened with an internal aluminum channel for included assistance. We are a customized PVC/Vinyl fence producer, which offer us the ability to customize fence height and picket spacing.
There is no setup warranty for wood fences. Product warranties vary by material type. PVC/vinyl and aluminum fences both have Minimal Life Time Warranty for any material defects. Chain link and wood fences do not have a material warranty. Acts of God are not covered under any service warranty. You be accountable for removing your prized possessions from the fence/building site.
8 Tips To Finding A Fence Company
0 notes
Text
Investors are back into Bitcoin but DEXs are still the future of crypto
https://ift.tt/3kgp0QD
Investors are back into Bitcoin but DEXs are still the future of crypto
Bitcoin’s long-waited bull run and the recent wave of corporate and institutional investors allocating significant portions of their reserves to Bitcoin (BTC) are all signs that the pace of crypto’s mainstreaming is rapidly accelerating: But has the path to mass adoption come at the cost of privacy and decentralization?
Know Your Customer and Anti-Money Laundering laws have forced the majority of cryptocurrency exchanges to become more transparent about who their users are, and those who refused have had to limit the jurisdictions in which they can offer services.
In order to operate legally in many countries, many exchanges have had no choice other than to abide by strict AML procedures, and aside from Monero (XMR), swathes of privacy coins have been delisted from most major exchanges.
Recently, regulators have begun to crack the whip and jurisdictions around the world continue to propagate further measures to ensure investors disclose their crypto holdings and pay taxes on their profits.
And this is all happening as the United States Department of Justice arrested the co-founder of BitMEX and the CFTC charged its owners with running an illegal crypto derivatives exchange.
Roughly a week later, the Financial Conduct Authority, the United Kingdom’s top regulatory watchdog, went as far as to ban investors from derivatives trading at all crypto exchanges.
All of these maneuvers are designed to force compliance on crypto service providers, and while they may eventually assist with furthering mass adoption, many crypto ideologues are looking for alternatives to press their case for financial self-sovereignty.
Decentralized exchanges may be the solution
A growing number of investors feel that centralized crypto exchanges essentially operate in the same manner as traditional banks. As a response to this, decentralized exchanges such as Uniswap, 1inch, Curve Finance and Balancer grew in popularity throughout 2020.
For more sophisticated investors, decentralized exchanges offering derivatives trading have also become available. Similar to traditional derivatives, crypto exchanges offering the service essentially act as the broker, but the process is marginally different on decentralized exchanges. This is because they utilize smart contracts in place of a broker, and the derivatives contracts are settled when the contract terms have been met.
At the moment, Synthetix is one of the most popular decentralized derivatives exchanges, and in 2020, it saw its total value locked rise to $1 billion before a sharp sector-wide correction led to a drop in TVL and daily active users at the majority of DEXs.
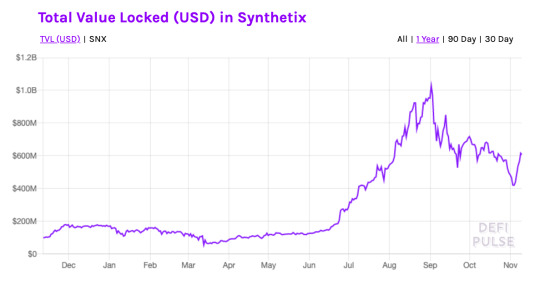
Total value locked in Synthetix. Source: DeFi Pulse
The exchange allows users to create an instrument called a synthetic asset “Synth” that can track gold, fiat and cryptocurrencies. It also allows the creation of assets that track the price of assets inversely.
Platform users can also stake the native SNX token as collateral in order to mint new synths, and similar to Uniswap, those who provide liquidity are rewarded by earning a portion of the exchange’s transaction fees.
Those familiar with DEXs like Uniswap will know that literally, anyone can list a new asset, which, in the case of derivatives, means any underlying asset can be transformed into a derivatives instrument.
These platforms allow users to trade derivatives without the need to deposit funds in any centralized platform, and they are not required to complete any KYC procedures.
While some investors shun KYC and tax compliance, this is a serious matter for crypto service providers. According to Molly Wintermute, an anonymous developer credited with founding Hegic DEX, compliance is more of an issue for centralized crypto service providers, not DEXs.
When asked how DEXs can remain compliant with financial regulators, Wintermute bluntly explained in a unique vernacular that:
“They can’t. this is a new layer of financial infrastructure, not an addition 2 z current financial system. it’s like TCP/IP or FTP, not jst a decentralized crypto exchange. U can’t stop z code or ban internet. unless public blockchain is open & permission-less it’s almost impossible 2 ban decentralized derivatives protocols.”
Wintermute further explained that decentralized derivatives are alluring to a particular subset of investors because:
“Non-custodial trading (protocol/people don’t hold funds as funds r allocated on smart contracts). Verified on-chain settlement (there’s no ability 2 cheaply manipul8 z derivatives & no close source trading algorithms that only exchange owners knows how 2 work/manipul8 with). deeper liquidity (new peer-to-pool/peer-to-contract model might offers lower spreads & better terms 4 users).”
According to Wintermute, the number of investors actually using DEXs is quite small, compared to the total number of crypto investors. To Wintermute, this means the FCA derivatives ban and the recent legal actions taken against BitMEX are completely irrelevant and non-applicable to decentralized finance protocols.
Wintermute said:
“Decentralized derivative is a part of small crypto world. there r 100M+ of crypto holders globally. around 5-10 of them might b actively trading crypto derivatives (globally). i don’t think that FCA ban has opened any new interesting opportunities. nothing has changed.”
After being pressed to elaborate on the chance that the SEC, FCA or other regulators might not attempt to shut down a platform such as Uniswap and arrest its founders, Wintermute said:
“They could probably arrest 1 or 2 CEOs like bitmex founders who have some shady things goin’ on internally but only 2 make everyone else feel fear. they can’t arrest everyone. also compare decentralized derivatives with crypto used 4 dealin’ drugs. these two things r 4from different sides of a spectrum. a toy in case of decentralized derivs & a gun in case of drugs dealers who r usin’ crypto. decentralized derivatives r not a crime.”
Wintermute also appeared to shake off the recent BitMEX scandal, sharply replying that:
“I don’t think that somebody gives a f— abt DeFi or DEXes. bitmex guys have so many shady things inside that this might b a great target 2 attack while DeFi / DEX protocols have 100% transparency & u can’t take a person 2 jail 4 buidlin’ a website that jst has numbers on it which r transparent 4 everyone else in z world.”
Ultimately, Wintermute believes that “Bakkt/CME & other wall s— guys r so angry that no one uses their s—– products that they now takin’ crypto entrepreneurs & tryin’ 2 send them 2 jail.”
The anonymous developer then explained that in her view, the “meta game is 2 ban every cool crypto products & try 2 cannibalize on their user base but with compliant s—– products.”
While there may be merit to some of Wintermute’s bold assertions, the arm of the law is quite long, and as we have seen with the now-defunct ICO era, bringing those who violate securities laws takes time.
In 2020, the total value locked in DeFi platforms has risen to $12.6 billion, and data from Dune Analytics shows that Uniswap processed $11.2 billion in volume in October. These massive figures are sure to catch the eye of U.S. and international regulators so it may only be a matter of time before legal action is taken against DEXs.
Decentralized exchanges are a testing ground for layer-two solutions
In addition to addressing privacy concerns and restoring decentralization to the crypto sector, DEXs also provide a sandbox for layer-two developers to play in. As has been thoroughly reported by Cointelegraph, scaling within the Ethereum network has been a persistent challenge.
When the network becomes congested during high demand periods, gas fees increase exponentially, and transaction speeds grind to a halt. With Ethereum 2.0 in perceptual “development,” a number of DEXs have begun to experiment with integrating layer-two solutions to provide users who are willing to forgo the Ethereum network with cheaper, faster options.
Project Serum is probably one of the better-known success stories for a non-Ethereum based DEX.
The decentralized derivatives-based project is built on the Solana blockchain instead of the default Ethereum network that most DEXs operate on, but it is also fully interoperable with ERC-20-based assets and Bitcoin.
FTX CEO Sam Bankman-Fried and his team are the brains behind Project Serum, and according to Bankman-Fried, the project is designed to circumvent the privacy and safety concerns of centralized exchanges by giving users a permissionless method to invest with leverage and swap assets.
The project also provides a cheaper alternative to the high gas fees and slow transaction speeds that frequently plague the Ethereum network during periods of high traffic.
Bankman-Fried said:
“In order to build a product capable of offering fast, cheap order matching, you need a chain with high throughput. This demand increases further for trading nonstandard markets and handling risk or liquidations. Serum chose to build on Solana because the chain has focused on a unique and powerful vision for scaling.”
According to Bankman-Fried, technical issues such as congestion and high fees can make or break an investor. Regarding high fees, he said:
“They’re fatal: You basically cannot have derivatives on Ethereum because of the scaling problems. To the extent that decentralized derivatives have growth opportunities, they’ll either be on a new L1, or on an L2.”
Bankman-Fried also agreed with Wintermute’s claim that hardly anyone is using DEXs, as “the vast majority of derivatives volume is on centralized exchanges,” but he suggested that in theory, “composability and self-custody” should be incentives for more users to join the movement.
One DEX to rule them all
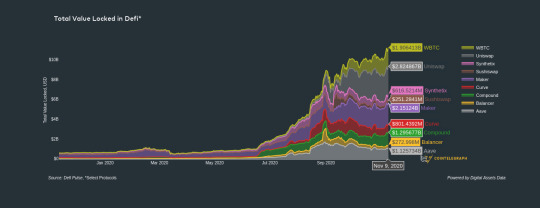
Total value locked in DeFi. Source: Digital Assets Data
Currently, investors have shifted their attention back to Bitcoin as the digital asset pursues a new all-time high, and data from Cointelegraph and Digital Assets Data indicate that DEX trading volume and daily active users continue to decline.
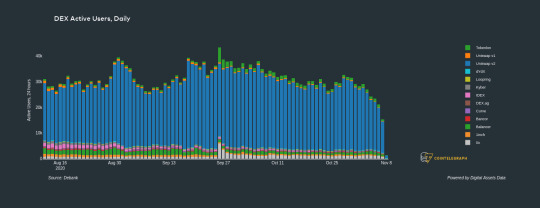
DEX daily active users. Source: Digital Assets Data
While this is likely disappointing to investors, it at least provides developers some quiet time to focus on properly integrating layer-two solutions to DeFi protocols.
The trend of major cryptocurrency exchanges becoming more centralized is unlikely to change anytime soon. This means that the first DEX to successfully provide a platform with low fees, privacy protections and a fast user-friendly interface will rule supreme once investors make the choice to invest in decentralized finance and decentralized derivatives again.
https://ift.tt/38oiepT
Market Analysis
Investors are back into Bitcoin but DEXs are still the future of crypto
Wanna Win Some Free Crypto?
This is our favorite crypto casino... Check it out and get a free sign up bonus and daily crypto rewards!

The post Investors are back into Bitcoin but DEXs are still the future of crypto appeared first on ESA Token.
from WordPress https://ift.tt/32w4JR3
via IFTTT https://ift.tt/3oqtis8 https://ift.tt/3dTdjOi
0 notes
Text
IoT lottery: finding a perfectly secure connected device
http://cyberparse.co.uk/2017/11/27/iot-lottery-finding-a-perfectly-secure-connected-device/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592
Black Friday and Cyber Monday are great for shopping.Vendors flood the market with all kinds of goods, including lots of exciting connected devices that promise to make our life easier, happier and more comfortable.Being enthusiastic shoppers just like many other people around the world, at Kaspersky Lab we are, however paranoid enough to look at any Internet of Things (IoT)-device with some concern, even when the price is favorable.All because there is little fun in buying a coffeemaker that would give up your home or corporate Wi-Fi password to an anonymous hacker, or a baby-monitor that could livestream your family moments to someone you most definitely don’t want it livestreamed to.
It is no secret that the current state of security of the IoT is far from perfect, and in buying one of those devices you are potentially buying a digital backdoor to your house.So, while preparing for IoT-shopping this year, we asked ourselves: what are our chances of buying a perfectly secure connected device? To find the answer, we conducted a small experiment: we randomly took several different connected devices and reviewed their security set up.It would be an exaggeration to say that we conducted a deep investigation.This exercise was more about what you’d be able to see at first glance if you had a clue about how these things should and shouldn’t work.As a result we found some rather worrying security issues and a few, less serious, but unnecessary ones.
We looked at the following devices: a smart battery charger, an app-controlled toy car, an app-controlled smart set of scales, a smart vacuum cleaner, a smart iron, an IP camera, a smart watch, and a smart home hub.
Smart Charger
The first device we checked was the smart charger that attracted us with its built-in Wi-Fi connectivity. You may ask yourself: who would need a remotely controlled battery charger, especially when you need to manually set the battery to charge? Nevertheless, it exists and it allows you not only to charge the battery, but to manage the way you charge it. Like a boss.
The device we tested charges and restores most types of batteries with a nominal voltage from 3 to 12 volts.It has a Wi-Fi module, which allows the device owner to connect remotely to control the charging process, to change the charging settings and to check how much electricity the battery is storing at any time.
Once turned on, the device switches by default to ‘access point’ mode.The user should then connect to the device and open the management interface web page.The connection between the charger and the device you use to access the management panel uses the outdated and vulnerable WEP algorithm instead of WPA2. However it is password protected. Having said that, the predefined password is ‘11111’ and it is actually written in the official documentation that comes with the device and is searchable online. However, you can change the password to a more secure one. Having said that, the length of the password is limited, for some reason, to five symbols.Based on the information available here, it would take four minutes to crack such a password.In addition to that the web interface of the device itself has no password protection at all.It is available as is, once it is connected to your home Wi-Fi network.
Who would attack a smart charger anyway, you may well ask, and you would probably be right as there are likely few black hat hackers in the world who would want to do that.Especially when it requires the attacker to be within range of the Wi-Fi signal or have access to your Wi-Fi router (which, by the way, is a much bigger problem). On the other hand, the ability to interfere with how the battery is charging, or randomly switching the parameters could be considered as worth a try by a wicked person.The probability of real damage, like setting fire to the battery or just ruining it is heavily dependent on the type of battery, however the attack can be performed just for lulz. Just because they can.
To sum up: most likely when using this device, you won’t be in constant danger of a devastating remote cyberattack. However, if your battery eventually catches fire while charging, it could be a sign that you have a hacker in your neighborhood, and you have to change the password for the device. Or it could be the work of a remote hacker, which probably means that your Wi-Fi router needs a firmware update or a password change.
Smart App-Controlled Wireless Spy Vehicle
While some people are looking for useful IoT features, other seek entertainment and fun.After all, who didn’t dream of their own spying toolset when they were young? Well, a Smart App-Controlled Wireless Spy Vehicle would have seemed a dream come true.
This smart device is actually a spy camera on wheels, connected via Wi-Fi and managed via an application.The spy vehicle, sold in toy stores, has Wi-Fi as the only connection interface.For management there are two official applications, for iOS and Android. We assumed that there could be a weakness in the Wi-Fi connections – and we turned out to be right.
The device is able to execute the following commands:
Move across the area (with multiple riding modes, it is possible to control speed and direction)
View an image from the navigation camera during movement, for ease of navigation
View an image from the main camera, which can also be rotated in different directions (there is even a night vision mode)
Record photos and videos that are stored in the phone’s memory
Play audio remotely via a built-in speaker
Once connected to a phone, it becomes a Wi-Fi access point without password requirements.In other words, any person connected to it can send remote commands to the vehicle – you’d just need to know which commands to send.And if you – being a bit concerned about the lack of password protection in a child’s toy that has spying capabilities – decided to set one up, you’d find there was no opportunity to do so.And if you have basic network sniffing software on your laptop, and decided you’d like to see what the vehicle was currently filming, you’d be able to intercept the traffic between the vehicle and the controlling device.
That said, a remote attack is not possible with this device, and an offensive third-party would have to be within the range of the toy’s Wi-Fi signal which should be enabled.But on the other hand, nothing prevents an attacker from listening to your traffic in a passive mode and catching the moment when the device is used.So if you have seen someone with a Wi-Fi antenna near your house recently, chances are they’re curious about your private life, and have the means to look into it.
Smart Robo Vacuum Cleaner. With camera
Speaking of other devices with cameras that are around you, we spent some time trying to figure out why a smart vacuum cleaner would need to have a web-cam – is it for the macro filming of dust? Or to explore the exciting under-bed world? Joking aside, this function was made specifically for the cleaning enthusiast: if you find it exciting to control the vacuum cleaner manually while checking exactly what it’s doing, this is the gadget for you. Just keep in mind that it is not quite secure.
The device is managed via a specific application – you can control the cleaner’s movement, get video live-streaming while it’s cleaning, take pictures, etc.The video will disappear after streaming, while photos are stored in the application.
There are two ways to connect to the device via Wi-Fi:
With the cleaner as access point.If you don’t have a Wi-Fi network in your home, the device will provide the connection itself. You simply connect to the cleaner via the mobile application – and off you go!
The cleaner can also work as a Wi-Fi adapter, connected to an existing access point.After connecting to the cleaner-as-access-point you can then connect the device to your home Wi-Fi network for better connection and operation radius.
As the device is managed via a mobile phone application, the user should first go through some kind of authorization.Interestingly enough, for this they only need to enter a weak default password – and that’s it.Thus, an attacker just needs to connect to cleaner’s access point, type in the default password to authorize themselves in the application for pairing the mobile phone and the cleaner.After the pairing is completed, they can control the device.Also, after connection to a local network, the robot vacuum cleaner will be visible in the local network and available via a telnet protocol to anyone who is also connected to this network. Yes, the connection is password protected, which can be changed by the owner of the device (but really, who does that?!), and no, there is no brute force protection in place.
Also the traffic between the app and the device is encrypted, but the key is hard-coded into the app. We are still examining the device, and the following statement should be taken with a big grain of salt, but potentially a third-party could download the app from Google Play, find the key and use it in a Man-in-the-Middle attack against the protocol.
And, of course, like any other Android-app controlled connected device, the robot vacuum cleaner is a subject to attack via rooting malware: upon gaining super user rights, it can access the information coming from the cleaner’s camera and its controls.During the research, we also noticed that the device itself runs on a very old version of Linux OS, which potentially makes it subject to a range of other attacks through unpatched vulnerabilities.This, however, is the subject of ongoing research.
Smart Camera
IP cameras are the devices targeted most often by IoT-hackers. History shows that, besides the obvious unauthorized surveillance, this kind of device can be used for devastating DDoS-attacks. Not surprisingly, today almost any vendor producing such cameras is in the cross-hairs of hackers.
In 2015, our attempt to evaluate the state of security of consumer IoT took a look at baby monitor; this year we’ve focused on a rather different kind of camera: the ones used for outside surveillance – for example the ones you’ve put up in your yard to make sure neighbors don’t steal apples from your trees.
Originally, the device and its relatives from the same vendor were insecure due to a lack of vendor attention to the problem.But the issue of camera protection changed dramatically around 2016 after reports of unauthorized access to cameras became publicly known through a number of publications like here or here.
Previously, all the cameras sold by this vendor were supplied with a factory default account and default password ‘12345’. Of course, users tended not to change the password.In 2016, the picture changed radically when the vendor became an industry pioneer in security issues, and started to supply cameras in ‘not activated’ mode.Thus, there was no access to the camera before activation.Activation required the creation of a password and some network settings. Moreover, the password was validated in terms of basic complexity requirements (length, variety of characters, numbers and special characters).Activation of the camera could be performed from any PC with access to the camera over the local network.
Since this reform, updating the firmware on a camera with a default password leads to the camera demanding a password change and warning the user about security issues every time they connect.The password requirements are quite solid:
Additionally, protection from password brute forcing has been implemented:
Moreover, the vendor added a new security feature to the firmware in 2016.This involves protection against brute forcing, by automatically blocking access for an IP address after five to seven attempts to enter the wrong password.The lock is automatically removed after 30 minutes.The feature, which is enabled by default, significantly increases the level of security.
Nevertheless, not everything is perfect in the camera.For instance, the exchange of data with the cloud is performed via HTTP, with the camera’s serial number as its ID.This obviously makes Man-in-the-Middle attacks more realistic.
In addition to a standard WEB interface for such devices, there is a specialized tool for camera configuration, which can search for cameras on the network, display data on the cameras, and perform basic settings including activation, password changes, and the implementation of password resets for network settings. When triggering the device search the PC sends a single Ethernet frame.
The camera’s response is not encrypted, and contains model information such as the firmware, date reset and network settings.Since this data is transmitted in a non-encrypted way and the request does not have authorization, this one Ethernet package can detect all cameras on the network and obtain detailed information about them.The algorithm has one more weakness: when forming a response, time delays are not considered.As a consequence, it is easy to organize a DDoS attack in the network, sending such requests to all cameras within the presented Ethernet network .
Apart from the described specific protocol, cameras support a standard SSDP protocol for sending notifications, and this allows any software or hardware to automatically detect the cameras.This SSDP data also contains information about the model and serial number of the camera.
One more attack vector lies in the remote password reset, which is supported by a technical support service.Anyone with access to the camera’s network can select a camera through the specialized tool for camera configuration and request the reset procedure.As a result, a small file containing the serial number of the camera is created.The file is sent to the technical support service, which then either refuses the request or sends a special code to enter a new password.Interestingly enough, the service doesn’t even try to check whether the user is the owner of the camera – outdoor surveillance assumes that the camera is located out of reach, and it is almost impossible to identify remotely the author of the request.In this scenario, an insider cybercriminal attack is the most probable vector.
To sum up: luckily this is not the worst camera we’ve ever seen when it comes to cybersecurity; however, some unnecessary issues are still there to be exploited by an offensive user.
Smart Bathroom Scales
Remember that picture from the internet, where hacked smart scales threaten to post their owner’s weight online if they don’t pay a ransom? Well, joking aside we’ve proved this may be possible!
This is a smart device, interacting with a smartphone app via Bluetooth, but it is also equipped with a Wi-Fi module.This connectivity provides the owner with a number of additional features, from weight monitoring on a private website secured by a password to body analysis and integration with various healthcare apps.Interestingly enough, the only Wi-Fi-enabled feature is the receiving of weather updates.
We decided to test the possibility of arbitrary updates\software installation on the specified device in LAN using ARP spoofing and the implementation of Man-in-the-Middle attacks. Here’s what we found.
The mobile phone interacts with the main server via HTTPS, in a series of queries.The scales themselves are connected to the mobile phone via Bluetooth.The process of pairing is simple: you request connection via the application, and then turn the scales’ Bluetooth connection on.Given the very limited time for this stage, it is very unlikely that someone will be able to pair the devices without the user’s knowledge.
Among other things, the device transmits via Bluetooth various user data – mail, indication of weight, etc.The device receives updates via the application.The latter sends the current version of updates and a number of other parameters to the server – the server, in turn, passes to the application a link to the downloaded file and its checksum.
However the updates are provided as is, on the HTTP channel, without encryption, and the updates themselves are also not encrypted.Thus, if you are able to listen to the network to which the device is connected you would be able to spoof the server response or the update itself.
This enabled us to, firstly, ‘roll back’ the version of the updates, and then install a modified version that does not match the one retrieved from the server.In this scenario, the further development of attacks is possible, like installing arbitrary software on the device.
The good news is that this device has no camera, so even if any other severe vulnerabilities are found, you are safe.Besides that, who would want to spend time on hacking smart scales? Well, the concern is a valid one.First of all, see the picture at the beginning of this text, and secondly: as we already mentioned above, sometimes hackers do things just because they can, because certain things are just fun to crack.
Smart Iron
Fun to crack – that is something you can definitely say about a smart iron.The very existence of such a device made us very curious.The list of things you could potentially do should a severe vulnerability be found and exploited looked promising. However, the reality turned out to be rather less amusing.Spoiler: based on our research it is impossible to set fire to the house by hacking the iron. However, there are some other rather interesting issues with this device.
The iron has a Bluetooth connection that enables a number of remote management options through a mobile app. We assumed that communication with the server would be insecure, allowing someone to take control of the device and its sensitive data, as manufacturers would not be paying enough attention to the protection of this channel, believing that a smart iron would be of little value to an attacker.
Once it is connected to the user’s mobile phone, the iron is managed via the application, which exists in versions for both iOS and Android. The app allows you to:
View the orientation of the iron (whether it is lying flat, standing, or hanging by its cable)
Disable (but – sadly – not enable) the iron
Activate ‘safe mode’ (in which iron does not react to a mechanical switch on.To turn the iron on when it is in that mode you need to turn off safe mode in the app).
In terms of on/off safety the iron automatically switches off if it is stationary for five seconds in a ‘lying’ position, or for eight minutes in a ‘standing’ position.
The iron can also be controlled via the internet.For this, it is necessary to have a gateway near the device, like a separate smartphone or tablet with internet access and a special app.
Given all that, we decided to take a closer look at the applications for the device.There are three of them – one for iOS and two for Android.The first Android app is for when you manage the device via Bluetooth and are standing nearby, and the other one is for the gateway, which serves as an online door to your iron when you are not at home.The iOS app is for Bluetooth management.Speaking about the security of all applications, it is worth mentioning that the vendor’s code is not obfuscated at all.
When viewing online traffic, we found out that the Android Bluetooth application uses HTTPS, which is a sensible solution.The corresponding app for iOS does not and neither does the gateway app for Android. We decided to test the traffic for the iOS application.
Example of phishing attack via the application
Once it is enabled, the application offers the user the chance to register, and then sends the data without encryption via HTTP.This gives us a very simple attack vector based on the interception of traffic between the mobile application and the vendor’s server within the local network.
As already mentioned, the phone also communicates with the iron using BLE.The BLE traffic is also not encrypted.After deeper investigation of the applications, we were able to control the iron by creating specific commands just from looking into what is transmitted between the devices.
So, if you were a hacker, what could you do with all this knowledge? First of all if you would be able to capture the user’s credentials, to pass the authorization stage in an official application and to switch off the iron or set it to ‘safe mode’.It is important to note here that these applications are used for all of the vendor’s smart devices, and there are quite a few.This significantly enlarges the attack surface.
No need to worry if you miss the chance to intercept the authentication data.Given that the data exchange between the app and the device is not encrypted, you would be able to intercept a token transmitted from the server to the application and then create your own commands to the iron.
As a result, within the local network an attacker can perform:
Identity theft (steal personal email address, username, password)
Extortion (take advantage of the ignorance of the user to enable ‘safe mode’ so that the user could not mechanically turn on the iron, and to demand money for disabling ‘safe mode’)
Of course both these vectors are highly unlikely to be extensively performed in the wild, but they are still possible. Just imagine how embarrassing it would be if your private information was compromised, not as a result of an attack by a sophisticated hackers, but because of the poor security of your smart iron.
Smart home hub
The biggest problem with the vast majority of connected devices currently available is that most of them work with your smartphone as a separate, independent device, and are not integrated into a larger smart ecosystem.The problem is partly solved by so called smart hubs – nodes that unite in one place the data exchange between multiple separate smart devices.Although prior art in finding a secure smart hub, conducted by multiple other researchers, leaves little room for hope, we tried anyway and took a fancy smart hub with a touch screen and the ability to work with different IoT-protocols.It is universally compatible, works with ZigBee и ZWave home automation standards, and very easy to handle: according to the manufacturer, it can be set up within three minutes, using the touchscreen.
In addition the hub serves as a wireless Wi-Fi router.
Given all the features this multi-purpose device has, being a router, range extender, access point or wireless bridge, we decided to check one of the most common and most dangerous risks related to unauthorized external access to the router.Because, if successful, it would possibly lead to full control of a user’s smart home, including all connected devices.
And, no surprise, our research has shown there is such a possibility.
To check our assumption we created a local network, by connecting a PC, the device and one more router to each other.All network devices received their IP addresses, and we successfully scanned available ports. Our initial research has shown that, by default, there are two opened ports over WAN.The first one, port 80, is one of the most commonly used and assigned to protocol HTTP.It is the port from which a computer sends and receives web client-based communication and messages from a web server, and which is used to send and receive HTML pages or data.If opened, it means that any user can connect to port 80 and thus have access to the user’s device via the HTTP protocol.
The second one, port 22 for contacting SSH (Secure Shell) servers is used for remote control of the device.Attackers can gain access to a device if they obtain or successfully brute force a root password. Usually it’s not an easy task to do. However, in our research we explored another interesting risky thing with the smart hub that makes this much easier.
While analyzing the router, we discovered it might have problems with a very common threat risk – weak password generation.In the router system we found ELF (Executable and Linkable Format) file ‘rname’ with a list of names.By looking at this list and the password displayed on the screen, it became clear that device’s password is generated based on the names from this file and, thus, it doesn’t take long for brute force cracking.
After a hard reset, the source line for passwords remained, with slightly changed symbols. However, the main password base remained the same, and that still leaves a chance to generate a password.
In addition, we found that for device access a root account is constantly used.Thus, offensive users will know the login and a base part of the password, which will significantly facilitate a hacker attack.
In case the device has a public IP address and the ports described above are opened, the router can be available for external access from the internet. Or, in other case, if a provider or an ISP (Internet Service Provider) improperly configures the visibility of neighboring hosts of the local network, these devices will be available to the entire local network within the same ISP.
In all, we weren’t surprised; just like most any other smart hubs on the market, this one provides a really vast attack surface for an intruder.And this surface covers not only the device itself, but the network it works on.And here are the conclusions which the results of our experiment have brought us to.
Conclusions
Based on what we’ve seen while doing this exercise, the vendors of many IoT-devices developing their products assume that:
They won’t be attacked due to limited device functionality and a lack of serious consequences in the case of a successful attack.
The appropriate level of security for an IoT-device is when there is no easy way to communicate with the wider internet and the attacker needs to have access to the local network the device is connected to.
We have to say that these assumptions are reasonable, but only until the moment when a vulnerable router or multifunctional smart hub, like the one described above, appears in the network to which all other devices are connected.From that moment, all the other devices, no matter how severe or trivial their security issues, are exposed to interference.It is easy to imagine a house, apartment or office populated with all these devices simultaneously, and also easy to imagine what a nightmare it would be if someone tried each of described threat vectors.
So in answer to the question we asked ourselves at the beginning of this experiment, we can say that, based on our results at least, it is still hard to find a perfectly secure IoT-device.
On the other hand, no matter which device you purchase, most likely it won’t carry really severe security issues, but again, only until you connect them to a vulnerable router or smart hub.
Keeping that and the ongoing high sales holiday season in mind we’d like to share the following advice on how to choose IoT devices:
When choosing what part of your life you’re going to make a little bit smarter, consider the security risks.Think twice if you really need a camera-equipped robo vacuum cleaner or a smart iron, which can potentially spill some of your personal data to an unknown third-party.
Before buying an IoT device, search the internet for news of any vulnerability.The Internet of Things is a very hot topic now, and a lot of researchers are doing a great job of finding security issues in products of this kind: from baby monitors to app controlled rifles.It is likely that the device you are going to purchase has already been examined by security researchers and it is possible to find out whether the issues found in the device have been patched.
It is not always a great idea to buy the most recent products released on the market.Along with the standard bugs you get in new products, recently-launched devices might contain security issues that haven’t yet been discovered by security researchers.The best choice is to buy products that have already experienced several software updates.
To overcome challenges of smart devices’ cybersecurity, Kaspersky Lab has released a beta version of its solution for the ‘smart’ home and the Internet of Things – the Kaspersky IoT Scanner.This free application for the Android platform scans the home Wi-Fi network, informing the user about devices connected to it and their level of security.
When it comes to the vendors of IoT-devices, the advice is simple: collaborate with the security vendors and community when developing new devices and improving old ones.
P.S. 1 out of 8
There was one random device in our research, which showed strong enough security for us at least not to be worried about private data leakage or any other devastating consequences.It was a smart watch. Like most other similar devices, these watches require an app to pair them with the smartphone and use.From that moment, most of data exchange between the device and the smartphone, the app and the vendors’ cloud service are reliably encrypted and, without a really deep dive into encryption protocol features or the vendor’s cloud services it is really hard to do anything malicious with the device.
For the pairing the owner should use the pin code displayed on the clock for successful authorization.The pin is randomly generated and is not transmitted from the clock.After entering the pin code in the app, the phone and clock create the key for encryption, and all subsequent communication is encrypted.Thus, in the case of BLE traffic interception an attacker will have to decrypt it as well.For this, an attacker will need to intercept traffic at the stage of generating the encryption key.
It is apparently impossible to get user data (steps, heart rate etc.) directly from the device.Data synchronization from the clock on the phone is encrypted and, in the same form is sent to the server.Thus, data on the phone is not decrypted, so the encryption algorithm and the key are unknown.
From our perspective this is an example of a really responsible approach to the product, because, by default the vendor of this device could also easily limit their security efforts to assuming that no one will try to hack their watches, as, even if successful, nothing serious happens.This is probably true: it is hard to imagine a hacker who would pursue an opportunity to steal information about how many steps you made or how fast your heart beats at any given moment of the day. Nevertheless, the vendor did their best to eliminate even that small possibility.And this is good, because cybersecurity is not all those boring and costly procedures which you have to implement because some hackers found some errors in your products, we think cybersecurity is an important and valuable feature of an IoT-product, just like its usability, design and list of useful functions. We are sure that as soon as IoT-vendors understand this fact clearly, the whole connected ecosystem will become much more secure than it is now.
4 notes
·
View notes
Text
My upbringing was starkly black and white, everything strictly categorised as sin and acceptable, allowed and not. The massive ‘sin: not allowed’ category swallowed everything in legalism and immutable consequences. I fell in love with noir partly because it has no such hangups.
I savoured noir’s evocative language and sexual undercurrent. I learned to believe exposing repressive authority and dirty deeds was valiant even if ultimately futile, and justice could be delivered even when corrupt systems stymied it. The hardboiled detective attracted me from every angle, and I dreamed of both being and fucking the daring mystery-solving, smoking, drinking, dame-bedding wiseass. The detective archetype is dangerously appealing; stalwart antiheroes holding to their personal code while all around them people sold their souls for a bottle of scotch, a land deed, a tempting woman or a hard man. Terribly tragic, and as such, terribly romantic.
Like a suspect in a smoky dive bar, what constitutes ‘loyalty’ in noir is hard to pin down, but while most supporting characters treat loyalty as a purchasable, expendable, flexible commodity, [anti]heroes Spade and Archer, Gittes and Dewitt, Mars and Hammer, et al. hold fiercely to their personal definitions thereof. These ideals often keep them from working with a partner, as they can’t find others who share their notions longer than a book’s opening chapters, a film’s first act. Sometimes, in a twisted blessing, their partner gets murdered before committing betrayal. (‘Committing betrayal.’ What a cruel grammatical construction.)
Fairly unique among their set, Charleses Nick and Nora manage loyalty and happiness to and with each other, but not only does their teasing openly relay insecurities in everyone outside their connubial circle, their origin story is shot through with loyalty conundrums. The crux of The Thin Man revolves around characters leveraging Nick’s allegiance to an old friend to make Nick and Nora investigate a suspicious death/disappearance, similar to the relationship between Marlowe and Terry Lennox in The Long Goodbye.
Marlowe: You didn’t have much choice, huh? So you used me.
Lennox: Hell, that’s what friends are for.
Many noir tales examine murder, corruption, lost love, incest, power, grasping for companionship in sex and booze and partners. Few are so nakedly about friendship, loyalty, and the unique betrayal they set you up for as The Long Goodbye. As the game Lennox and Marlowe play in their first scene tells us, all Marlowe’s relationships are games of liar’s poker he’ll lose. The only question is: sooner, or later?


The film’s opening involves the great Philip Marlowe cajoling his hungry cat to eat first a concoction of cottage cheese and raw egg, then generic cat food. The two mewl, mumble and scratch in their understanding standoff. The film ends with Marlowe coolly justifying shooting his once-friend because Lennox indirectly killed the cat. Everything between is a meditation on loyalty.
As best exemplified in Nick and Nora Charles, noir understands relationships featuring fidelity and comfortable insults are the ones which really matter, so the snarky–sweet caring–codependent way Marlowe and hungry cat banter intentionally evokes true friendship. Altman called that opener important and Marlowe’s relation to his cat commentary on friendship: no matter how hectic his life, Marlowe is concerned the cat eats, whether the cops scare him, if he’s lost in LA’s mean streets.
Like most of his genre, Marlowe is destined to traverse the criminal underworld, continually learning the hard way he’s more loyal to friends, clients, even his constantly stoned neighbours, than they to him. He can’t bring himself to act on his cynicism until he’s burnt, and is a lost soul not because he’s dumb or drugged – he turns down even his neighbours’ hash brownie – but because he can’t find anywhere to put his trust.
Though they harass him and he blusters against their threats and handcuffs, Marlowe’s relationship with the cops is his most stable. He despises their work, they hate and stymie him, but at least he knows where he stands. Everywhere else is shifting sand and empty promises, golden and glittering by daylight, cold and dangerous at night. Under it all play morphing renditions of “The Long Goodbye,” refrains evolving and fading as quickly as relationships, adding atmosphere as Los Angeles underworld characters succour the detective and each other until betrayal becomes convenient.
As he searches for answers in mysteries and others, Marlow smokes to dull the pain – take a shot every time he strikes his match on a new surface, you’ll be drunk before the halfway point. Elliot Gould’s physicality superbly conveys Marlowe’s hurt and insecurity, shambling gait literalising existentially unsure footing.

Altman’s shots and Zsigmond’s cinematography also expose Marlowe’s mental state. The beautiful police station tracking shot puts us in Marlowe’s gumshoes, showing his strain as he attempts to sort through the mountain of information, theories, and grief he’s been buried under. The long dolly across the grounds of the clinic has a similar effect, moving first methodically, then more frenetically as Marlowe’s frustration builds. Exposition of addresses and phone numbers unroll with slow camera movements over long takes, revelling in the acting’s stillness, taking a less usual route than montages to make the viewer feel Marlowe’s tedium and loneliness.
The odyssey is wrapped in perfectly exposed beach scenes, daytime sands yellow-tinged and California to their core, nighttime painted deep blacks and grainy red with Eileen’s dress the only spot of yellow. Doubled imagery and symbols of duplicity abound, the most striking of which involve the beach. First we see Marlowe in the glare off Wades’s window, projected between quarrelling lovers as they snipe at each other. Later, in the same window, Eileen is shown two-faced as she and Marlowe talk while her husband charges suicidally into the inky sea.


The whole film is a gorgeous depiction of our ugliest impulses, and Altman is the perfect director for it. Through various lenses and genres, Altman’s work examines intimacy and pain which can be leveraged by only those closest to us. Noir’s peripheral characters are who many of Altman’s other films center: desperate, impotent men; disloyal lovers; marriages on the verge; frustrated humans performing drastic acts. The Long Goodbye digs into side stories many noirs don’t unless impacting the protagonist directly: Farewell, My Lovely is more concerned with Marlowe’s relationship to the women in his path than the women themselves; American Gigolo hardly contains a conversation Julian Kaye isn’t in; Evelyn’s relationships in Chinatown mostly evolve when Jake is around to observe, and he’s around almost every frame. Some of The Long Goodbye’s more virulent events or breakdowns happen while Marlowe is out of the picture, or listening to nothing but crashing waves.

Altman is interested in examining these stories for their own sake, and shows it by examining side characters with the reflections motif, too. Zsigmond uses Eileen’s windshield brilliantly to reflect her facade as Marlowe chases her through the streets. The stoned hippy neighbours are introduced surrounded by floor-to-ceiling windows, one dancing with herself in the mirrored glass. The gate-guard-slash-impression-artist is reflected in Harry’s shiny car sidepanels, a symbol of security who pretends to be many other people, then shows himself more trustworthy than people pretending to be someone they’re not.
The guard also displays The Long Goodbye’s wicked sense of humour, along with the horny lookout whose ogling of stoned half-naked neighbour women allows Marlowe to sneak away. There’s the slapstick of Harry swinging haplessly on the gate trying clamber over as he imagines a detective should. Marlowe plants a sloppy handprint on the interrogation cell two-way mirror, then paints his face with fingerprint ink, cops impotent to stop his clowning. The guard dog fetching her owner’s stick from the waves has a twisted hilarity to it.
Which brings us, as the film continually does, back to loyalty. Relationships with animals are throughout: besides his cat, Marlowe nervously banters with the guard dog and talks as cheerfully as a damned man can to strays lying in the road. Ultimately animals’ loyalty – even only to the hand that feeds and then betrays them, pictured perfectly with mounted ducks – is still stronger than that of everyone else in his life, and loyalty is important to him.

If only I’d recognised earlier how much my identifying with pulp heroes was due to my own sense of loyalty, deservedness of recipients be damned. “Their cynicism exactly stems from their compassion, [their] hardness is a scar tissue of a heart they can’t stop the world from breaking over and over.” I weirdly admired Marlowe hoping against hope, believing those he loves once, then again. You know what they say about fools.
Marlowe: Nobody cares but me.
Lennox: Well that’s you, Marlowe. You’ll never learn, you’re a born loser.
The Long Goodbye is Chandler’s most personal work. “You writers have your own special way of describing, don’t you?” is the movie acknowledging this sure as Chandler’s book commented on his deep insecurities, ideals, and philosophies. (The film references the book many times, including the face-bandaged man as a nod to Book Terry’s extensive plastic surgery.) Roger Ebert said in his original review, “The private eye as a fiction device was essentially a way to open doors; the best novels of Chandler and the others are simply hooks for a cynical morality.” Like Inherent Vice, the criminal underworld is alluring backdrop and murder the smaller mystery behind the real question of whether the detective can uphold his personal code in a world where ‘a man is only as good as his word’ simply means most men are no good. The real question, the crux and heart of the matter, is Will they keep clinging to that code? Why do we keep falling for those who throw us over?

The thing about franchised noir detectives is, as characters or story properties, they can’t fundamentally change. They solve mysteries, their settings are updated from 50s to 70s to aughts to 2019, they jadedly swear they’ll never trust again, they may seem to learn their lesson. But in the end the stories reset. Sure as sunset and the next story, they get let down, used, double-crossed, stung, only to begin again when the next sultry shadow darkens their door. Once again they give their loyalties to a friend in need, a dame with legs up to there. Once again the dames and mates evaporate; or worse, explicitly sell our fallible hero upriver, relying on said hero’s tragically loyal personal code to prevent retaliation.
We’ve all had those dames and mates. We’ve all sworn to never love again, only to willingly set ourselves up for more heartbreak. People who mean what they say only so long as they feel like it. Family who love you so long as you’re meekly in line. Dames who say “I love you” in the night and “I’m leaving you” in the morning. Business partners who call you family until it’s more expedient not to be. Friends who say forever but mean for as long as you’re fun, and you’re no fun when you’re stumbling through a haze of pain or grief. Homme fatales who sell you out when a better offer comes in. Lovers who are loyal while you do exactly what they want.
In the first of two crucial scenes which start placidly before exploding into brutal violence, thug Marty gives a speech to/about his girlfriend Joanne. “Delicate and sweet . . . I love you. I do. . . . The single most important person in my life.” Ah, love, the highest form of loyalty.
Then he hits her across the face with a glass bottle.

Do we feel sorry for her? is the same question Tarantino asks in Once Upon A Time… In Hollywood when Brad Pitt’s Cliff smashes sadistic Sadie’s face with a can of dog food. The blow to Joanne’s face is lighter and unprovoked, but though her crimes are lighter, her madonna-like framing is window dressing. She blithely enjoys fruits of Marty’s torture, murder, and extortion, knowing her flippery is bought with blood money. (Her blow’s aftereffects are visually replicated by Jake’s bandages in Chinatown – directed by Polanski, who is depicted in Once Upon A Time, making these films a Möbius strip of themes, imagery, period, and settings.)
In different ways, Joanne and Sadie establish The Long Goodbye and Once Upon a Time‘s cruel worlds, where psychopaths and rich ruthless men get their way. Both center men with drinking and smoking habits, a dubious past, and a personal moral code. Marlowe and Cliff fight against the establishment, for themselves and their friends. Though they don’t believe in innocence, they want to believe people exist whose souls at least aren’t as dark as the rest of ours. Within their morality is loyalty; Cliff to Rick Dalton, Marlowe to Terry or at least the idea of him: “Terry Lenox was my friend you motherfucker . . . you don’t deserve to be alive you fuckin’ pig.” Rick and Terry don’t return the loyalty, yet Cliff and Marlowe can’t help themselves. It’s their code.
The Long Goodbye ending Ebert calls “off the wall” I see as wish fulfilment, same as Once’s. In the film Terry gets justice delivered by Marlowe, Bracket’s screenplay ‘fixing’ the book’s injustice. Altman revels in this playground where disloyalty equals death and real world consequences are momentarily suspended for a warped fairy tale ending.
The final shot is reminiscent of Holly Martins waiting on a tree-lined boulevard in The Third Man, another film featuring a man unendingly loyal to a death-faking friend who didn’t deserve such fidelity. The Long Goodbye’s last shot brings yellow in again, reminding us of Eileen’s dress, the faded sun on the beach, letters and pledges of friendship aged and brittled by time. Only here, Marlowe’s the one walking away, getting as happy an ending as one can hope for in noir.
This slideshow requires JavaScript.
Lennox blindsided Marlowe, then called him a fool for expecting others to do what he would in keeping his word. Pulp detectives are thrown under the bus or off a cliff with the shrugged excuse along the lines of “I knew you were tough enough to survive” or “sorry, you were just collateral damage.” Given enough time, “I threw you under the bus to save myself” becomes “It was the best option for both of us” becomes “you survived and are better for learning this lesson, you should be thanking me!” This essay draws parallels to Marlowe and Veronica Mars’ getting run over because of their clinging to loyalty, “an anchor that binds.”
But every detective also has their breaking point, the point at which they say the rules have been violated enough to justify them taking matters into their own hands.

Marlowe: I have two friends in the world. One is a cat. The other is a murderer.
Is loyalty its own reward? Chandler’s book seems to argue it is, but Marlowe shooting his once-friend in the film argues something else. Grown and free of the romanticised prism Younger Me viewed Marlowe through, do I believe Chandler’s ending or Brackett’s?
The teenager who first read Chandler’s book would choose idealism: be true to your code, give your loyalty, those who turn on you will get what they deserve while you can keep the moral high ground. Even with grim answers in front of me, maybe I’d make like Marlowe, clinging stubbornly to loyalty disavowed by its recipient, or keeping myself preoccupied searching for answers and other mysteries.
While I want to hold to those ideals still, what are movies for if not to show us what we really want, wish-fulfilling our basest instincts? Watching now, I can’t help but savour that moment Marlowe tosses his cigarette, reaches into his waistband, and coolly shoots the man who treated his loyalty as commodity.
For #Noirvember, I wrote about the concept of loyalty in noir in general, and "The Long Goodbye" in particular. My upbringing was starkly black and white, everything strictly categorised as sin and acceptable, allowed and not.
0 notes
Text
Encryption in-transit and Encryption at-rest - Definitions and Best Practices

In the latest few years the world wide web has experienced an exponential growth of hackers, malwares, ransomwares and other malicious software or parties which is constantly trying to find a way to steal our personal data: given this scenario, it goes without saying that securing your data became one of the most important tasks that we should prioritize, regardless of the role that we usually play. The general (and urgent) need to prevent unauthorized access to personal, sensitive and/or otherwise critical informations is something that should be acknowledged by everyone - end-users, service owners, servers administrators and so on: the differences are mostly related to what we need to protect and how we should do that.
Needless to say, the act of choosing the proper way to protect our data is often subsequent to a well-executed risk assessment followed-up by a costs-benefits analysis, which is a great approach to help us finding the appropriate technical and organisational measures to implement in our specific scenario. This is also the proper way to act according to the General Data Protection Regulation (GDPR), as stated in the Art. 32 - Security of Processing:
Taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons, the controller and the processor shall implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk
Here's a list of the most common technical and organisational measures to ensure the protection and security of the data nowadays:
Access control: Protect all physical access to your server, client and/or data rooms with keys, chip cards, walls, lockers, alarms and the likes.
Minimization: Ensure that all the authorized parties can access only the data specifically related to their specific tasks and/or authorization without being allowed to see anything else.
Integrity: Protect your data from accidental loss, destruction or damage using appropriate countermeasures (fire/flood sensors, Disaster Recovery and the likes).
Pseudonymisation: Replace user-related data by random, anonymous blocks of text, so that the owner will still be able to retain the entries (for statistical purposes) and, at the same time, stripping them from any personal info.
Encryption in-transit: Ensure that the data is always transmitted using strong in-transit encryption standards (SSL/TLS certificates) and through secure connections: this also applies to any kind of website and web-based service containing forms, login screens, upload/download capabilities and so on.
Encryption at-rest: Protect your local data storage units (including those used by servers and desktop & mobile clients) with a strong at-rest encryption standard; ensure that the data stored in SaaS and cloud-based services are also encrypted at-rest.
Confidentiality: Prevent unauthorized or unlawful processing by implementing concepts such as separation of concerns & separation of duties, enforcing password policies, and so on.
Recoverability: Ensure that all the relevant data is subject to regular backups and also be sure to regularly check them to ensure that the data can be successful retrieved.
Evaluation: Submit the whole system to regular technical reviews, third-party audits, adopt an effective set of security indicators, and so on.
In this post we're going to talk about two of these technical measures: Encryption in-transit and Encryption at-rest, leaving the other topics for further articles.
Introduction: the Three Stages of Digital Data
The first thing we should do is to enumerate how many "states" digital data can actually have, and be sure to understand each one of them:
At rest: this is the initial state of any digital data: in very short terms, this indicates the data that is stored somewhere without being used by and/or transmitted to anyone (including software, third-parties, human beings, and so on). From local Hard Drives to Network Attached Storages, from USB pendrives to mobile devices, from system folders to database servers, any physical and logical storage system, unit or device is meant to be used to contain data at rest... at least for a while.
In transit: also known as "in motion". This is relative to the data which is being transmitted somewhere to somewhere else. It's worth noting that the concept of "data transfer" can take place between any number of parties, not limiting to just two (the sender and a receiver): for example, when we transfer a file from our desktop PC to our laptop using our LAN, we're basically performing a data transfer involving a single party (us); conversely, when submitting a transaction to a distribuited database, such as a blockchain, we're enforcing a data transfer between an indefinite amount of parties (the whole blockchain nodes).
In use: whenever the data is not just being stored passively on a hard drive or external storage media, but is being processed by one or more applications - and therefore in process of being generated, viewed, updated, appended, erased, and so on - it's intended to be "in use". It goes without saying that data in use is susceptible to different kinds of threats, depending on where it is in the system and who is able to access and/or use it. However, the encryption of data in-use is rather difficult to pull off, since it would most likely cripple, hinder or crash the application which is actually accessing it: for this very reason, the best way to protect the data in use is to ensure that the application will take care of such job by adopting the most secure development and implementation patterns within its source code.
The sum of the three statements explained above is called "the Three Stages of Digital Data": now that we got the gist of them, we're ready to dive deep into the encryption topics.
Data Encryption at-rest
From the definition of "at rest" given above we can easily understand how this kind of data is typically in a stable state: it is not traveling within the system or network, and it is not being acted upon by any application or third-party. It's something that has reached a destination, at least temporarily.
Reasons to use it
Why should we even encrypt it, then? Well, there are a number of good reasons for doing so: let's take a look at the most significant ones.
Physical theft
If our device is stolen, the encryption at-rest will prevent the thief from being immediately able to access our data. Sure, it can still try to decrypt it using brute-force or other encryption-cracking methods, but this is something that will take a reasonable amount of time: we should definitely be able to pull off the adeguate countermeasures before that happens, such as: changing the account info he might be able to see or somewhat use via existing browsers password managers, login cookies, e-mail clients accounts and so on; track our device and/or issue a "erase all data" using our Google or Apple remote device management services; and so on.
Logical theft
If our PC, website or e-mail account gets hacked by a malicious user or software, the encryption at-rest will make the offender unable to access our data - even when stolen or downloaded. It's basically the same scenario of physical theft, except that it's way more subtle because most users (or administrators) won't even be aware of it. Do you know these terrific words uttered by John T. Chambers, former CEO of Cisco, Inc.?
There are two types of companies: those that have been hacked, and those who don't know they have been hacked.
Considering the current state of the internet nowadays and the over-abundance of malwares and measurable hacking attempts, the same statement can be said for any end-user possessing a web-enabled device: 100% guarranteed.
Human errors
Let alone the physical and/or logical thefts, there are a lot of other scenarios where data encryption at-rest could be a lifesaver: for example, if we lost our smartphone (and someone finds it); or if we make a mistake while assigning permissions, granting to unauthorized users (or customers) access to files/folders/data they shouldn't be able to see; or if we forget our local PC or e-mail password in plain sight, thus allowing anyone who doesn't feel like respecting our privacy to take a look at our stuff; and the list could go on for a while.
How can it help us
To summarize all that, we could answer our previous questions with a single line by saying that encrypting our at-rest data could help us to better deal with a possible Data Breach.
It won't help us to prevent that from happening - which is mostly a task for firewalls, antiviruses, good practices and security protocols - but will definitely give us the chance (and the time) to setup the appropriate countermeasures, hopefully minimizing the overall damage done by any possible leak.
How to implement it
Implementing a Data Encryption at-rest security protocol might be either easy or hard, depending on the following factors:
which physical and logical data sources/storages we want (or have) to protect: physical sources include Hard Disks, NAS elements, smartphones, USB pendrives, and so on, while logical sources include local or remote databases, cloud-based assets, virtualized devices, and so on;
who needs to have access to these data: human beings (local or remote users or other third-parties connecting to us), human-driven software (such as MS Word) or automatic processes or services (such as a nightly backup task);
how much we're willing to sacrifice in terms of overall performance and/or ease of access to increase security: can we ask to all our local (and remote) users to decrypt these data before being able to access them? Should we use a password, a physical token or a OTP code? Can we make the encryption transparent enough to not hinder our external users and also to allow our software apps and tools to deal with the encrypted data whenever they'll need to deal with it?
Luckily enough, these factors are well-known by most at-rest encryption tools, which have been designed to protect our data without compromising the overall functionality of our environment:
if we want to encrypt physical (or logical) Hard-Disk drives, we can use great software tools such as VeraCrypt (100% free) or AxCrypt (free version available);
if we need to protect our USB pendrives, we can either use the aforementioned tools or purchase a hardware-encrypted Flash Drive implementing fingerprint-based or password-based unlock mechanisms (starting from 20~30 bucks);
if we would like to encrypt the data stored within a Database Management System, most of the DBMS available today provide native encryption techniques (InnoDB tablespace encryption for MySQL and MariaDB, Transparent Data Encryption for MSSQL, and so on);
if we're looking for a way to securely store our E-Mail messages, we can easily adopt a secure e-mail encryption standard such as S/MIME or PGP (both of them are free): although these protocols are mostly related to in-transit encryption, since they do protect data mostly meant to be transferred to remote parties, as a matter of fact they are commonly used to perform a client-side encryption, which means that they protect the e-mail messages while they're still at-rest. Needless to say, since those message will most likely be sent, our destination(s) will also have to adopt the same standard to be able to read them.
Data Encryption in-transit
As the name implies, data in-transit should be seen much like a transmission stream: a great example of data in-transit is a typical web page we do receive from the internet whenever we surf the web. Here's what happens under the hood in a nutshell:
We send a HTTP (or HTTPS) request to the server hosting the website we're visiting.
The web server accepts our request, processes it by finding the (static or dynamic) content we've asked for, then sends it to us as a HTTP (or HTTPS) response over a given TCP port (usually 80 for HTTP and 443 for HTTPS).
Our client, usually a web browser such as Google Chrome, Firefox or Edge, receives the HTTP(s) response, stores it on its internal cache and shows it to us.
As we can see, there clearly is a data trasmission going on between the server and the client: during that trasmission, the requested data (the web page HTML code) becomes a flow that changes its state at least five times: from at-rest (server storage) to in-use (web server memory), then to in-transit (using the HyperText Transfer Protocol on a given TCP port), then again to in-use (web browser), and finally to at-rest (client cache).
Reasons to use it
Now, let's take for granted that both the server and client have implemented a strong level of data encryption at-rest: this means that the first and the third state are internally safe, because any intrusion attempt would be made against encrypted data. However, the second state - where the data is in-transit - might be encrypted or not, depending on the protocol the server and the client are actually using to transmit the data.
Here's what usually happens under the hood when the HTTP protocol is being used:
As we can see, the security issue is quite evident: when the web server processes the incoming request and transparently decrypts the requested data, the channel used to transfer it to the web client (HTTP) is not encrypted: therefore, any offending party that manages to successfully pull off a suitable attack (see below) could have immediate access to our unencrypted data.
How can it help us
If you're curious about which kind of attacks can be used against a unencrypted TCP-based transmission protocol such as HTTP, here's a couple of threats you should be aware of:
Eavesdropping: a network layer attack that focuses on capturing small packets from the network transmitted by other computers and reading the data content in search of any type of information (more info here).
Man-in-the-Middle: a tampering-based attack where the attacker secretly relays and/or alters the communication between two parties to make them believe they are directly communicating with each other (more info here).
Implementing proper encryption in-transit protocols to secure our critical data transfer endpoints will definitely help us preventing these kind of threats.
How to implement it
Implementing an effective encryption in-transit pattern is mostly a matter of sticking to a wide-known series of recommendations and best practices while designing the actual data transfer: which protocols to (not) use, which software to (not) adopt, and so on. For example:
Whenever the transmitting device is reachable via web interface, web traffic should only be transmitted over Secure Sockets Layer (SSL) using strong security protocols such as Transport Layer Security (TLS): this applies to any web site and/or WAN-reachable service, including e-mail servers and the likes. As of today, the best (and easiest) way to implement TLS security and implement the encryption in-transit for any website is by obtaining a SSL/TLS HTTPS certificate: those can either be purchased from registered CA authorities (Comodo, GlobalSign, GoDaddy, DigiCert and their huge resellers/subsellers list) or auto-generated through a self-signing process, as we briefly explained in this post. Although self-signed certificates will grant the same encryption level of their CA-signed counterparts, they won't generally be trusted by the users as their browser clients won't be able to verify the good faith of the issuer identity (you), flagging your website as "untrusted": for this very reason, they should only be used on non-production (or non-publicly accessible) server/services.
Any data transmitted over e-mail should be secured using cryptographically strong email encryption tools such as S/MIME or PGP, which we already covered when we talked about data encryption at-rest: although these protocols perform their encryption at client level (and therefore at-rest), they're also great to protect the asynchronous in-transit flow of an e-mail message.
Any binary data should be encrypted using proper file encryption tools before being attached to e-mail and/or transmitted in any other way. Most compression protocols, including ZIP, RAR and 7Z, do support a decent level of password-protected encryption nowadays: using them is often a great way to add an additional level of security and reduce the attachment size at the same time
Non-web transmission of text and/or binary data should also be encrypted via application level encryption, taking the following scenarios into account:
If the application database resides outside of the application server, the connection between the database and application should be encrypted using FIPS compliant cryptographic algorithms.
Whenever application level encryption is not available, implement network level encryption such as IPSec or SSH tunneling, and/or ensure that the transmission itself is performed using authorized devices operating within protected subnets with strong firewall controls (VPN and the likes).
The following table shows some examples of the insecure network protocols you should avoid and their secure counterparts you should use instead:
Transfer Type
What to avoid (insecure)
What to use (secure)
Web Access
HTTP
HTTPS
E-Mail Servers
POP3, SMTP, IMAP
POP3S, IMAPS, SMTPS
File Transfer
FTP, RCP
FTPS, SFTP, SCP, WebDAV over HTTPS
Remote Shell
telnet
SSH2
Remote Desktop
VNC
radmin, RDP
End-to-End Encryption
Encryption in-transit is really helpful, but it has a major limitation: it does not guarantee that the data will be encrypted at its starting point and won't be decrypted until it's in use. In other words, our data might still be predated by occasional and/or malicious eavesdroppers, including internet providers, communication service providers and whoever could access the cryptographic keys needed to decrypt the data while in-transit.
Overcoming such limitation is possible thanks to End-to-End Encryption (E2EE), a communication paradigm where only the communicating end parties - for example, the users - can decrypt and therefore read the messages. End-to-end encrypted data is encrypted before it’s transmitted and will remain encrypted until it’s received by the end-party.
Reasons to use it
To better understand how end-to-end encryption superseeds in-transit encryption in terms of resilience to eavesdroppers, let's imagine the following scenarios.
Suppose that a third party manages to plant their own root certificate on a trusted certificate authority: such action could theoretically be performed by a state actor, a police service or even a malicious/corrupted operator of a Certificate Authority. Anyone who is able to do this could successfully operate a man-in-the-middle attack on the TLS connection itself, eavesdropping on the conversation and possibly even tampering with it. End-to-end encrypted data is natively resilient to this kind of attack, because the encryption is not performed at the server level.
End-to-end encryption can also increase the protection level among the user processes spawned by an operating system. Do you remember the recent CPU flaws called SPECTRE and MELTDOWN? Both of them allowed a malicious third-party (such as a rogue process) to read memory data without being authorized to do so. End-to-end encryption could avoid such scenario as long as the encryption is performed between user process (as opposed to the kernel), thus preventing any unencrypted data from being put in the memory.
How it can help us
End-to-end encryption is the most secure form of communication that can be used nowadays, as it ensures that only you and the person you're communicating with can read what is sent, and nobody in between, not even the service that actually performs the transmission between peers. Various end-to-end encryption implementations are already effective on most messaging apps and services (including Whatsapp, LINE, Telegram, and the likes). In a typical "communication app" scenarios, the messages are secured with a lock, and only the sender and the recipient have the special key needed to unlock and read them: for added protection, every message is automatically sent with its own unique lock and key.
How to implement it
End-to-end encryption can be used to protect anything: from chat messages, files, photos, sensory data on IoT devices, permanent or temporary data. We can choose what data we want to end-to-end encrypt. For example, we might want to keep benign information related to a chat app (like timestamps) in plaintext but end-to-end encrypt the message content.
Every user has a private & public key which the software has to generate on the users’ device at signup or next time they log in.
The user’s public key is published to a public place (such as a REST-based key management service): this is required for users to find each other’s public keys and be able to encrypt data to each other.
The user’s private key remain on the user’s device, protected by the operating system’s native key store (or other secure stores).
Before sending a chat message or sharing a document, the app encrypts the contents using the recipient’s public key (client-side).
Conclusion
Our journey through the various encryption paradigms is complete: we sincerely hope that this overview will help users and system administrators to increase their awareness of the various types of encryption available today.
Read the full article
#DataEncryption#E2EE#Eavesdropper#Encryptionat-rest#Encryptionin-transit#End-to-endEncryption#Meltdown#Spectre#SSL#Tamper#TLS
0 notes
Text
How To Find The Best Fence Company
Tips For How To Hire A Fence Company
By asking these and any other questions you may have throughout your assessment, you can discover the very best Austin fence installers and specialists, like us at Barrier Fence. We welcome you to contact us at (512) 354-4409 to schedule a consultation visit today.
If you have you have concerns about the location of the residential or commercial property line or your fence, we recommend that you call a local survey company to find and plainly mark the pins to establish the home lines. Lee Fence and Outdoor will install the fence per your guidelines.
7 Tips For Finding The Right Fence Company
Lee Fence and Outdoor will eliminate and deal with your existing fence for an extra charge. Please be advised that if there are any parts of your existing fence that you wish to keep, let the setup crew know. Lee Fence and Outdoor will not get rid of anything unrelated to the fence task.
We ask that someone would be on-site when our crews arrive to go over the fence design. Deviations from the original fence agreement must be authorized by your Lee Fence and Outdoor salesperson.
This can alter the initial fence layout. Please keep in mind that the utility locator DOES NOT locate wells, septic tanks or underground gas/propane tanks. No. Considering that these underground electric fence are usually located near the home line, you will require to contact your underground fence professional and have them mark the line prior to your brand-new fence installation.
Top 3 Tips For Choosing A Fence Company

No. It is the house owner's duty to find these lines and notify Lee Fence and Outdoor to the location of said lines. Normally all corner, gate and terminal posts will be dug up and reset in the specific very same area. It is basic practice and within AFA market guidelines to cut line posts listed below the grade and re-space the brand-new posts.
Normally, we utilize a small piece of devices called a mini-track to excavate the post holes. This changes at various times of the year, however typically during the spring/summer months, we can have a several week stockpile.
Your Lee Fence and Outside salesperson would be able to offer you with an approximate lead time at the time of the site visit. It differs on the size of your job. Typically, most residential fence setups will take 1 to 2 days to finish. Bigger fence setups can take 3 to 5 days.
6 Tips For Choosing Fence Company
Lee Fence and Outdoor crews are professionals in fence installation, our teams have limited understanding in appropriate cutting and pruning practices. Excessive trimming carried out by Lee and Fence Outdoor will be subject to a surcharge. We would appreciate you tidying up your shrubs as we do not want to damage your manicured backyard.
Related Searches Include:
Datson Fence
New Fence
Great Job
Fence Installation
Folsom Fence Company
Commercial Fences
Aluminum Fences
Fence Contractor
Commercial Fencing
Installation Crew
Chain Link
Free Quote
Wooden Fence
Kirkwood Fence
American Fence Company
Free Estimate
Commercial Property
Customer Satisfaction
Final Product
Reliable Fence Services
See Portfolio
Pearl City
Fence Services
Fencing Needs
Residential Fencing
Residential Fences
Wood Fences
Iowa City
Frederick Fence Company
Fence Products
It might be useful to notify your next-door neighbors so that no issues develop throughout the installation process with regards to residential or commercial property lines. If you are having an old fence replaced that is situated on the property line, it is suggested that you alert your next-door neighbor. Your neighbor may require to make arrangements concerning their family pets and may also want to secure their backyard or get rid of products from their side of the fence.

Normally your fence can be set up right approximately, however not on the residential or commercial property line per municipality policies. Some municipalities do recommend that you keep your fence off the property line 1' to 3' so that you are able to maintain your fence on both sides. No. The fence will be installed just a few inches inside the home lines.
Tips For Finding The Best Fence Company
Frequently Asked Questions - FAQ
How much does it cost to put up a fence?
The typical cost of installing a fence is in between $13 and $50 per direct foot. The typical total cost of installing a fence is around $988,however costs can reach $ 7,000-- or more. The length of the fence,products utilized and add-ons such as gates can affect just how much you end up paying for a fence installation.
What is the cheapest fence to install?
The least expensive fence you can install is a wire fencing at $2 per foot typically,while a 6-foot high wood personal privacy fence costs $13 to $25 per linear foot,and vinyl fencing for $15 to $30 per foot.
How much does a 300 ft fence cost?
Backyard Fence Costs Per Foot Linear Foot Cheaper (Wire or Electric) Moderate (Wood) 8 $10 - $50 $100 - $200 100 $100 - $600 $1,000 - $2,000 150 $150 - $1,000 $1,500 - $3,000 300 $300 - $1,800 $3,000 - $6,000 1 more row
How much does Home Depot charge for fence installation?
Fence Installation Costs According to Home Depot,it can cost anywhere from $1,000 to $10,000 to install a fence,however most house owners can expect to invest from $1,600 to $4,000. You can more accurately determine what your job may cost by identifying the number of direct feet your fence will be.
How much does an 8 ft fence cost?
8 Foot Wood Fence Cost The typical cost to build an 8-foot wood fence is between $21 and $30 per direct foot using pressure-treated pine with dog-ear panels.
What is the best time of year to install a fence?
If you consider summer season and spring the peak season,then winter is the best time to get the service and attention you desire from your fence specialist. Make the most of the off season by doing your research throughout the warmer months and getting ready for installation in the winter season.
Is it cheaper to build a fence yourself?
Among the advantages of installing a fence on your own is that you don't need to pay a company for the labor expenses. This generally winds up being less expensive in the end,and one of the major factors the majority of people consider a DIY in the first place.
Is it cheaper to build a fence horizontal or vertical?
Horizontal fences tend to be more costly than vertical fences due to the fact that they need a greater grade of lumber for the fence boards to decrease the possibility of drooping. However,like any horizontally-oriented board,they may sag gradually.
What is the easiest fence to put up?
Vinyl fencing installation is so much easier the no-dig method. This suggests you can spend less time on your home tasks and more time with your family,buddies,or whatever else you want to do.
An easement grants other people or companies rights to specific types of gain access to on your residential or commercial property. Easements generally require that you keep any type of building and construction, consisting of fence, off your home line 5' to 10' feet.
An easement is typically suggested on your residential or commercial property plot strategy. If your plot plan is not readily available your regional town would have the ability to provide you with this info. Yes. A corner lot is considered to have two front backyards. Normally your municipality will only permit a 3' or 4' high fence in front backyards.
youtube
This range differs per town. Most towns will allow approximately a 6' high fence in the side and rear yard. When you pass by the front corner of your home towards the street, you are considered in your front yard. Allowable fence heights in the front yard vary per municipality.
Tips For Hiring The Right Fence Company
The pool code states that your fence should be at least 4' high. There are particular criteria that need to be satisfied for the 4' high fence to satisfy this code.

The Lee Fence and Outdoor salesperson is very knowledgeable with your pool code requirements and can discuss your various alternatives. It is your duty to read your deed restrictions associating with your fence - Wise Tips On How To Choose Your Fencing Company. HOA deeds and local building regulations can limit easements, fence heights, color preferences and even material types.
We provide and install fencing and related perimeter security items such as gates, railings, guardrails and gain access to control systems - Finding The Best Fencing Company. We likewise provide and set up decks.
Tips For Choosing A Fence Company
PVC/vinyl fence or aluminum fence are really resilient and require less upkeep. PVC/vinyl fences are resilient, long lasting, simple to clean and environmentally friendly.
Chain link is long lasting, affordable and easy to set up. Presently we stock white, tan, adobe and grey. Colors can be blended to create a two-tone or photo frame effect. All PVC/vinyl bottom fence rails and all gate posts are strengthened with an internal aluminum channel for included assistance. We are a custom-made PVC/Vinyl fence maker, which provide us the ability to modify fence height and picket spacing.
There is no setup warranty for wood fences. PVC/vinyl and aluminum fences both have Minimal Lifetime Guarantee for any product problems. Chain link and wood fences do not have a product warranty.
How To Find A Good Fence Company
0 notes
Text
Market of the Beast: Cannabis Sustainability with EcoWaste
New Post has been published on https://bestmarijuanaboutiques.com/?post_type=wprss_feed_item&p=24110
Market of the Beast: Cannabis Sustainability with EcoWaste
AUTHOR: HEATHER ALLMAN
ON THE BURNER— Interview with Arman Zeytounyan, CEO and Co-Founder of EcoWaste in California
The “Beast” in this scenario is cannabis sustainability, and the distinct lack thereof. The market for change is wide open, and here’s the perspective of one man and the vision of one California company who is getting an edge in the sustainability market due to the cannabis waste removal and compliance services they offer.
COMPANY HIGHLIGHTS:
EcoWaste ensures compliance every step of the way for the security of your cannabis license. EcoWaste provides an exceptional, reliable and proven cannabis waste disposal.
EcoWaste believes there’s a better way to conduct cannabis waste management, combining the right knowledge and provide a solution that is effective and embraces the regulations.
EcoWaste was founded by Avo Gasparian and Arman Zeytounyan in 2016. It started as a organic, or green, waste disposal service for the food and construction industry. During these early stages EcoWaste began testing our process and setting up a durable infrastructure.
— — — — —
CANNABIS LAW REPORT: Why did you get into this particular business?
ARMAN ZWYTOUNYAN: “Before starting EcoWaste, I was already a part of a specialized waste company. My business partner started BioWaste in 2011, which performs solely medical/biohazard waste management disposal service.
In early 2018, we began to receive inquiries for cannabis waste. At that point, we reached out to some friends in the industry to learn more. After doing some research on the cannabis compliance regulations, we concluded that cannabis waste is a service that we are perfectly suited to manage for the industry.”
— — — — —
CLR: Is EcoWaste and recycling a component that is required in the California cannabis regulatory framework?
AZ: “The cannabis regulations in California don’t require a cannabis business to use our service or to recycle the waste they generate. They do, however, require that the waste is handled in a way that decreases the possibility of under the table actions.”
— — — — —
CLR: Do you think it should be a required component of any states medical cannabis regulatory framework?
AZ: “Absolutely. Biases aside, the biggest value a company like ours provides is compliance. Having a third party correctly dispose of cannabis waste greatly decreases the opportunity involved in illicit activities. Recycling itself is a good habit for anyone to get into of course. That being said, cannabis is a green waste and there’s a lot of potential for re-purposing the material. The challenge is the volume needed to see real results isn’t there yet since California is still majorly a black market.“
“Surely, part of the issue with it being labeled “green waste” is that licensees don’t yet know how to execute proper recycling or consumer renewability of a Schedule I-tainted product. “
— — — — —
CLR: What one thing you do in your line of work that you feel is the very most important, that makes the most impact? Why?
AZ: “Easily it’s the compliance service we provide. When you’re a part of an industry that’s so new, it’s important to focus on the long term.”
“Just because something isn’t being enforced or otherwise emphasized today doesn’t mean the hammer won’t fall tomorrow.”
AZ: “Many people overlook the value waste management has to offer, but that’s not the wisest approach. Our compliance value comes in when a cannabis business owner’s integrity is questioned. Are they doing anything illegal with their products? Well, by taking advantage of our compliance service owners are able to confidently prove they are not engaging in anything illicit.”
— — — — —
CLR: I know you are currently only in California; however, what are your plans for the future of cannabis recycling & sustainability? Or what would you like the future of cannabis sustainability to look like?
AZ: “Geographical expansion is something we are certainly working towards. But as of now, we’re really excited about working with other sustainability-focused brands to co-create products that are biodegradable and can be put back into the supply chain, although it’s not as simple as many would think.”
— — — — —
CLR: Give me examples of one easy renewability solution for (a) companies? one easy renewability solution for (b) dispensaries?
AZ: “Currently it doesn’t exist. Our waste exports have been put on hold and recycling companies are not doing well right now. A dispensary will typically generate plastics and glass, but most recycling companies that have the infrastructure to do something with them won’t accept it because it’s cannabis waste. Small “mom and pop” operations might be interested in the plastics but recycling glass from the cannabis industry is extremely challenging.”
— — — — —
CLR: Is there one easy renewability solution for (c) end user consumers?
AZ: “The most practical approach a consumer of cannabis can participate in is by returning their packaging to the dispensaries and letting the dispensaries include that with their waste programs. Most of the licensees that we work with are in the process of forming a workable solution for the end user aspect that fits within the state compliance guidelines.”
— — — — —
CLR: What do you see for the future of cannabis sustainability and cannabis nationwide?
AZ: “I have hopes for cannabis sustainability. It may be very biased of me but there’s certainly potential for the cannabis industry to play a big role in biodegradable products. Naturally, hemp will be a big piece of that but cannabis waste consumers typically favor sustainability which ultimately means companies will have to find solutions that appeal to that.”
“70% of our licensees inquire about cannabis waste sustainability and cannabis waste recycling.”
— — — — —
CLR: What one piece advise have you along the way that you wish you someone had told you when you first started out?
AZ: “Hm, picking one piece is the hard part! But I would say be fast but patient. If something isn’t working out, scrap it, re-adjust, re-apply and repeat. At the same time being patient while you continue that process, but I mean real patience. We’re talking about years of patience not months.“
— — — — —
CLR: Your view of current cannabis sustainability (or lack thereof) in 10 words or less?
AZ: “Not enough volume yet to yield real long term results. – Got 10 exactly : )”
— — — — —
CLR: What advice can you offer to those individuals interested in starting a business similar to yours in any state?
AZ: “Be prepared to get your hands dirty. Anybody that thinks their above doing “their level’ in waste management is set to fail. Trucks break down, clients get confused, rain causes delays, employees get sick, and so on. As a logistics company you have to do whatever needs to be done to provide the client exceptional service.”
— — — — —
CLR: If in a vertically integrated program are you for or against state government compliant of renewability and cannabis waste?
AZ: “Against. I believe cannabis companies should be required to follow certain procedures to maintain safe practices and responsible procedures however requiring recycling would be disastrous for business owners. Sustainability does not have stability. Waste is a very broad category and there are thousands of ways to be sustainable. But so far there isn’t a one size fits all.
There are different approaches for different situations, waste sub types, geographical areas, and so on. Thus, requiring companies to recycle will only put business owners in a position to not be in compliance. Sustainability is about education, testing, and patience.“
“Although we can offer limited solutions at a corporate level, many dispensary licensees haven’t yet figured out how to properly execute a compliant and successful end-user recycling program.”
— — — — —
CLR: What advice can you offer to the states as a whole concerning cannabis sustainability and the importance of utilizing it to the fullest extent, even to the point of state-governed compliance?
AZ: “Education. People need to understand how the waste world really works. It’s really confusing and contradicting. There are so many different waste processes and they each yield different results. I think it is vitally important that we continue doing research and testing and finding ways to make it interesting for consumers to pay attention to.”
“We do have several licensees telling us they get more and more patient requests for on-site recycling options and availability; that’s a great thing.”
AZ: “We are also looking into the possibility of offering group education so that our existing licensed clients, the state’s cannabis employers, can learn more about cannabis waste renewability options and state-compliant rendering.”
— — — — —
DOWNLOAD
Use this checklist to ensure any cannabis business remains compliant with the State of California.
California Cannabis Waste Compliance rules via EcoWaste:
Do not sell, transfer, donate, or give away any cannabis waste.
Dispose cannabis waste only in a secured waste receptacle specifically designated for cannabis waste.
Keep cannabis waste in secured designated waste location on licensed premises until it can be collected.
Make cannabis goods into cannabis waste by rendering the goods unusable and unrecognizable at minimum by removing any packaging.
Record date and time the cannabis goods were rendered into cannabis waste.
After collection obtain a manifest from hauler that indicates the date and time of each collection and confirmation of disposal at the solid waste or composting facility.
Maintain records all activity related to the generation and disposal of the cannabis waste.
These regulations are subject to change at any time per the State of California Code of Regulations and the Bureau of Cannabis Control.
*Note if you are using our cannabis waste disposal services we provide the following for your business and records secured waste receptacles, date, time, and weight of cannabis waste when collected (via manifest), date, time, and weight when cannabis waste is either disposed of at a solid waste or composting facility (via manifest).
0 notes
Text
7 Conveniences of Cryptocurrency
7 Conveniences of Cryptocurrency
Cryptocurrency is actually an electronic substitute to utilizing credit report cards or cash money to produce everyday remittances in a wide array of conditions. It proceeds to grow as a convenient substitute to conventional payment strategies, but still needs to come to be even more secure before it is completely accepted by usual individuals. Allow's take an appeal at a few of the numerous benefits of utilization cryptocurrency:
Fraud - any type of concern with fraudulence is maintained to a minimum considering that cryptocurrency is digital which may protect against a reversed or even counterfeited settlement. This style of action may be a complication with various other conventional payment options, such as bank card, due to the fact that of charge-backs.
Identification burglary - there is actually no demand to provide private relevant information that can trigger identity burglary when using cryptocurrency. If you make use of a visa or mastercard, the outlet is actually provided a bunch of relevant information related to your credit score line, even for a very tiny deal. Likewise, the visa or mastercard settlement relies upon a pull transaction where a specific amount is requested from an account. Along with a cryptocurrency settlement, the transaction is located on a push basis, which gives the profile owner the choice to merely deliver the particular amount as a result of without extra information Crypto Investment Blog. All About Cryptocurrencies
Functional usage - a repayment through cryptocurrency can quickly be actually helped make to follow certain conditions. An electronic contract can be actually created to help make a repayment subject to accomplishing on a potential day, endorsement exterior realities, or even get 3rd party approval. Despite having an unique contract in position, this form of payment is still very rapid and also effective.
Easy accessibility - making use of cryptocurrency is widely on call to any individual that has access to the web. It is growing popular in particular component of the globe, like Kenya, which possesses nearly 1/3 of the population making use of a digital pocketbook through the neighborhood microfinance service.
Low costs - it is actually feasible to accomplish a cryptocurrency purchase without having to pay out added fees or even fees. Having said that, if an electronic wallet or third-party solution is utilized to keep the cryptocurrency there is most likely to become a small fee.
International field - this style of payment is actually exempt to country particular tolls, purchase charges, rates of interest, or currency exchange rate, which makes it achievable to accomplish cross-border transfers along with family member convenience Crypto Investment Blog.
Just How Cryptocurrency Works
Put simply, cryptocurrency is actually electronic amount of money, which is actually made in a manner that it is actually protected as well as undisclosed in some cases. It is actually closely connected with web that creates use of cryptography, which is essentially a procedure where legible info is actually exchanged a code that can certainly not be fractured thus concerning tack all the transfers as well as acquisitions created.
Cryptography has a record going back to the World War II, when there was a requirement to correspond in one of the most secure way. Because that time, a development of the very same has actually happened and it has come to be digitalized today where various factors of pc science as well as mathematical theory are being utilized for reasons of safeguarding communications, money and information online.
The initial cryptocurrency
The very initial cryptocurrency was offered in the year 2009 as well as is still properly understood around the world. A lot more cryptocurrencies have due to the fact that been offered over the previous few years as well as today you can locate plenty of available over the world wide web.
Exactly how they function
This type of electronic unit of currency uses modern technology that is actually decentralized thus concerning allow the different customers to pay that are actually protected as well as also, to hold cash without necessarily utilizing a name or even experiencing a banks. They are generally worked on a blockchain. A blockchain is a public ledger that is actually distributed openly.
The cryptocurrency units are actually often made utilizing a procedure that is described as exploration. This generally includes making use of a pc power. Performing it through this fixes the math problems that may be actually quite made complex in the creation of coins. Individuals are actually merely enabled to purchase the unit of currencies from the brokers and afterwards save all of them in cryptographic purses where they can devote all of them along with excellent convenience Crypto Investment Blog.
Cryptocurrencies and the request of blockchain modern technology are still in the little one phases when considered in financial phrases. Even more usages might develop in the future as there is actually no telling what else will certainly be invented. The future of working out on stocks, bonds and also various other kinds of monetary assets could possibly extremely well be traded using the cryptocurrency and also blockchain technology in the future.
Why use cryptocurrency?
Among the primary characteristics of these unit of currencies is the simple fact that they are actually secure which they use an anonymity level that you might not obtain anywhere else. There is no method through which a purchase may be reversed or even faked. This is easily the greatest main reason why you should think about using them.
The expenses charged on this sort of money are actually also fairly reduced as well as this creates it a really reliable alternative when compared to the traditional money. Considering that they are actually decentralized in attribute, they can be actually accessed by any person unlike banking companies where profiles are actually opened simply by consent.
Cryptocurrency markets are actually providing a new cash money form and in some cases the perks could be terrific. You might create an incredibly small expenditure merely to discover that it has actually mushroomed lucky great in an incredibly short time frame. Nevertheless, it is actually still important to note that the market place may be actually volatile also, and also there are actually threats that are actually connected with getting.
4 Most Important Cryptocurrencies
Bitcoin has actually been known through a lot of to be the most popular decentralized cryptocurrency. Nonetheless, besides bitcoin certainly there exists other altcoins that confer an excellent value at the same time. Are you considering discovering other cryptocurrencies? Properly, bitcoin is actually not the only one. Listed below are others Crypto Investment Blog.
1. Litecoin (LTC).
Studies reveal that as of July 2018, Litecoin possessed per token value of $87.56. The coin was actually created through previous Google designer and also MIT graduate named Charlie Lee. Only like bitcoin, Litecoin is actually certainly not handled by any core authorization. It utilizes "scrypt" as evidence of job. Various from bitcoin, Litecoin has actually received a faster shut out creation cost. This means that it provides a much faster transaction confirmation.
The coin is based on an open resource international settlement network. The coin is actually typically approved by sellers along with the amount increasing on a daily basis. In July 2018, it had a market cap of $5.03 billion.
2. Ethereum (ETH).
It was actually launched in the year 2015. ETH is a decentralized software system. It makes it possible for Distributed Applications as well as Smart Contracts to become constructed and operated without downtime, scams, command or even 3rd party disturbance. There exists a component referred to as ether which imitates a motor vehicle within the ethereum system. Creators looking for to develop as well as run apps within ethereum and financiers striving to investments other electronic money are the most intrigued gatherings in ether.
Market value every token of ethereum as of July 2018 was actually $474.66 and a market limit of $ 47.84. Ethereum is actually the 2nd crucial cryptocurrency coming from bitcoin.
3. Zcash (ZEC).
Much like various other altcoins, Zcash is an open-source as well as decentralized cryptocurrency. It was launched in the year 2016. This cryptocurrency is understood to use privacy and also careful clarity of deals. It is actually a distinct component various coming from other altcoins, isn't it?
ZEC states to give added safety where all the transactions are actually taped and also published on a blockchain. Having said that, finer information entailing the sender as well as recipient, and also the quantity are always kept exclusive. Data reveal that since July 2018, Zcash had every token value of $206.23. It had a market hat of $904.85 in the same month.
4. Dash.
It was actually referred to as darkcoin. Dashboard is a more closelipped variation of bitcoin. The working of Dash makes transactions just about untraceable. This considering that it delivers anonymity considering that it functions on a decentralized mastercode system Crypto Investment Blog.
Sprint was actually launched in January 2014. Ever since it has actually experienced a rise in fan adhering to even with the short time frame. The cryptocurrency was produced by Evan Duffield. It may be mined using a GPU or a CPU. Researches indicate that in July 2018, Dash had a market hat of $2.19 billion as well as market value per token of $266.58.
Various other leading cryptocurrencies feature Ripple (XRP), Monero (XMR), Bitcoin Cash (BCH), NEO (NEO), Cardano (ADA) as well as EOS (EOS).
Traits That Look Positive for Cryptocurrencies.
While there have actually been actually market modifications in cryptocurrency market in 2018, everybody concedes that the very best is however ahead. There have been a whole lot of activities out there that have modified the trend right. With appropriate review and also the right dose of confidence, anybody that is actually bought the crypto market can produce millions from it. Cryptocurrency market is listed here to remain for the lasting. Here in this post, our team provide you five favorable aspects that can easily propel more technology and market worth in cryptocurrencies.
1. Innovation in scaling.
Bitcoin is actually the 1st cryptocurrency in the marketplace. It possesses the maximum lot of customers and also the highest worth. It dominates the whole market value chain of the cryptocurrency unit. Having said that, it is actually certainly not uncreative. Its primary hold-up is that it can deal with simply six to seven deals every secs. In comparison, credit score card purchases balance at handful of thousands every secondly. Obviously, there is actually extent for remodeling in the scaling of deals. Through peer to peer transaction systems atop the blockchain modern technology, it is actually achievable to raise the purchase intensity per second.
2. Legit ICOs.
While there are cryptocoins along with dependable value in the market, latest coins are being actually developed that are created to offer a particular reason. Coins like IOTA are intended to aid the Internet Of Things market exchanging energy currencies. Some pieces take care of the concern of cybersecurity by giving encrypted digital vaults for storing the cash Crypto Investment Blog.
New ICOs are actually formulating cutting-edge services that interrupt the existing market and carry in a new worth in the purchases. They are actually also collecting authorization out there with their simple to use swaps and also trusted backend functions. They are actually introducing both on the modern technology edge pertaining to consumption of concentrated equipment for mining and monetary market side through offering additional liberty and options to financiers in the swap.
3. Clearness on regulation.
In the existing situation, the majority of governments are studying the effect of cryptocurrencies on the culture and how its benefits could be built up to the community unconfined. Our experts may expect that there may prove out outcomes as every the outcome of the studies.
Handful of federal governments are already taking the course of legalising and moderating crypto markets only like some other market. This will stop ignorant retail clients coming from losing funds as well as defend all of them coming from damage. Abling requirements that boost cryptocurrency development are anticipated to seem in 2018. This are going to possibly lead the technique for common fostering in future.
4. Rise in app.
There is actually massive excitement for the application of blockchain technology in virtually every industry. Some startups are actually happening up along with innovative solutions like electronic budgets, money memory cards for cryptocurrencies, and so on this will certainly enhance the variety of vendors who agree to negotiate in cryptocurrencies which in turn improve the amount of customers.
The online reputation of crypto possessions as a purchase channel will certainly be actually bolstered as more folks leave in this device. Although some start-ups may certainly not make it through, they will positively bring about the total health and wellness of the marketplace creating competitors and technology.
5. Investment from economic organizations.
A lot of global financial institutions are checking out the cryptocurrency scene. This can bring about the entry of institutional capitalists right into the market place. The influx of significant institutional financial investments will certainly feed the upcoming phase of development of the cryptomarkets. It has caught the liking of lots of banks and monetary companies.
As the shocks as well as bottlenecks around cryptocurrencies lessen, there will be actually even more uptake from traditional real estate investors. This will certainly trigger a considerable amount of dynamism as well as assets a lot needed for any developing economic markets. Cryptocurrency will become the defacto money for deals all over the globe.
Why Should You Trade in Cryptocurrency?
The modern-day idea of cryptocurrency is ending up being very prominent among traders. A cutting edge concept launched to the planet by Satoshi Nakamoto as an edge item came to be a smash hit. Decoding Cryptocurrency our experts understand crypto is one thing concealed and money is a monetary system. It is actually a type of unit of currency utilized in the block establishment made and stored. This is actually performed by means of file encryption procedures in purchase to control the creation and also confirmation of the money negotiated. Bit coin was actually the initial cryptocurrency which originated Crypto Investment Blog.
Cryptocurrency is only an aspect of the process of an online data source operating in the virtual globe. The identity of the real person listed below can easily certainly not be identified. Also, there is no central authorization which regulates the exchanging of cryptocurrency. This unit of currency is comparable to hard gold protected through folks and the worth of which is actually meant to become getting increased through jumps and also bounds. The electronic system specified by Satoshi is actually a decentralized one where only the miners possess the right to make improvements through affirming the purchases started. They are the only human contact providers in the device.
Forgery of the cryptocurrency is not possible as the entire system is based upon challenging center arithmetic and cryptographic problems. Just those individuals who can handling these problems can easily create changes to the database which is actually close to inconceivable. The transaction the moment confirmed enters into the data source or the block chain which can easily certainly not be actually turned around after that.
Cryptocurrency is actually only digital amount of money which is actually created with the assistance of coding approach. It is based upon peer-to-peer management device. Let our company now understand how one can easily be gained by trading in this particular market.
Can not be reversed or shaped: Though a lot of folks can rebut this that the deals carried out are actually irreparable, but the greatest feature of cryptocurrencies is that as soon as the transaction is actually verified. A new block gets added to the block establishment and afterwards the transaction can not be actually built. You become the proprietor of that block Crypto Investment Blog.
On the web transactions: This certainly not just makes it suited for any person being in any sort of portion of the planet to work, however it also relieves the rate along with which purchase receives refined. As contrasted to actual time where you need 3rd parties to find in to account to buy home or gold or even take a finance, You just need to have a computer system and also a possible shopper or homeowner in the event of cryptocurrency. This concept is actually easy, quick and filled with the leads of ROI.
The expense is reduced per deal: There is reduced or no fee taken through the miners throughout the transactions as this is taken care of through the network.
Accessibility: The concept is actually therefore useful that all those folks that possess accessibility to cell phones and laptops pc can access the cryptocurrency market and also stock it anytime anywhere. This access makes it a lot more rewarding. As the ROI is actually extensive, many nations like Kenya has introduced the M-Pesa unit making it possible for little bit piece unit which right now allows 1 in every three Kenyans to possess a little bit piece pocketbook along with them.
When lots of people think of cryptocurrency they might as effectively be thinking about puzzling unit of currency. Very few folks seem to be to know what it is and also for some reason everybody seems to be actually speaking about it as if they perform. This file will hopefully demystify all the facets of cryptocurrency to ensure that due to the opportunity you're completed reading you will certainly have a fair concept of what it is actually and what it is actually everything about.
You may locate that cryptocurrency is actually for you or you might certainly not yet a minimum of you'll manage to consult with a level of certainty and know-how that won't have Crypto Investment Blog.
There are actually lots of folks that have presently connected with millionaire status through dealing in cryptocurrency. Accurately there's a considerable amount of loan in this particular brand-new industry.
Cryptocurrency is digital currency, quick and straightforward. However, what's certainly not therefore brief and also basic is precisely how it reaps worth.
Cryptocurrency is a digitized, online, decentralized money generated due to the treatment of cryptography, which, depending on to Merriam Webster thesaurus, is actually the "computerized encoding as well as decoding of details". Cryptography is actually the structure that helps make debit cards, computer system banking and also eCommerce systems feasible.
Cryptocurrency isn't backed by banks; it is actually certainly not backed through an authorities, however by a remarkably difficult setup of algorithms. Cryptocurrency is actually electricity which is encoded into complex cords of formulas. What provides financial market value is their ins and out and also their security from cyberpunks. The manner in which crypto money is made is actually simply as well difficult to duplicate.
Cryptocurrency resides in direct adversary to what is contacted fiat money. Fiat loan is currency that gets its worth from government judgment or even rule. The dollar, the yen, and the Euro are actually all examples. Any kind of unit of currency that is actually specified as valid currency is actually paper money Crypto Investment Blog.
Unlike paper money, another component of what makes crypto money useful is actually that, like a product such as silver as well as gold, there is actually merely a finite quantity of it. Simply 21,000,000 of these remarkably intricate formulas were actually made. No more, no a lot less. It can't be actually altered by imprinting additional of it, like an authorities printing more amount of money to inflate the body without backing. Or even by a financial institution altering an electronic journal, something the Federal Reserve are going to teach banking companies to perform to adjust for rising cost of living.
Cryptocurrency is a way to acquire, market, and also invest that fully prevents both government lapse and also banking devices tracking the movement of your amount of money. In a planet economic climate that is actually destabilized, this body can end up being a stable power.
Cryptocurrency additionally offers you an excellent offer of anonymity. Unfortunately this can trigger misuse through an unlawful aspect utilizing crypto unit of currency to their own ends equally as routine funds may be mistreated. Having said that, it can easily also keep the government from tracking your every investment and also attacking your individual privacy.
Cryptocurrency happens in plenty of forms. Bitcoin was the first and is the requirement coming from which all other cryptocurrencies pattern themselves. All are actually generated by thorough alpha-numerical computations from a facility coding tool. Some various other cryptocurrencies are actually Litecoin, Namecoin, Peercoin, Dogecoin, and Worldcoin, to call a few. These are called altcoins as a generalized title. The rates of each are actually regulated through the supply of the details cryptocurrency as well as the requirement that the marketplace possesses for that money.
The technique cryptocurrency is actually delivered right into presence is actually fairly exciting. Unlike gold, which must be extracted from the ground, cryptocurrency is actually merely an entry in a virtual ledger which is stashed in various computer systems all over the world. These entrances need to be 'unearthed' utilizing algebraic protocols. Private consumers or, more probable, a team of consumers operate computational analysis to find specific collection of records, referred to as blocks. The 'miners' find records that generates an exact pattern to the cryptographic protocol. At that aspect, it is actually put on the set, and they've discovered a block. After an equivalent information series on the block compares along with the protocol, the block of records has actually been actually unencrypted. The miner gets a benefit of a specific volume of cryptocurrency. As time takes place, the amount of the reward lessens as the cryptocurrency ends up being scarcer. Incorporating to that, the complication of the formulas in the hunt for brand new blocks is actually likewise increased. Computationally, it becomes more challenging to find a coordinating series. Both of these scenarios collaborated to minimize the speed through which cryptocurrency is actually developed. This mimics the problem as well as scarcity of mining an asset like gold.
Now, any individual can easily be a miner. The pioneers of Bitcoin made the mining device available resource, so it's totally free to anyone. However, the personal computers they utilize run 24 hours a time, seven times a full week. The algorithms are remarkably complex and also the CPU is actually operating full speed. A lot of individuals have actually specialized computer systems made primarily for exploration cryptocurrency. Both the customer and also the concentrated computer are actually referred to as miners.
Miners (the human ones) likewise keep journals of deals and work as auditors, to ensure a coin isn't replicated at all. This always keeps the device from being actually hacked and coming from running riot. They're spent for this work through getting brand-new cryptocurrency each week that they maintain their function. They maintain their cryptocurrency in specialized documents on their computers or even other individual gadgets. These reports are gotten in touch with pocketbooks.
Allow's summation through undergoing a few of the interpretations our company've know:.
- Cryptocurrency: electronic money; likewise referred to as digital money.
- Fiat amount of money: any sort of valid currency; federal government supported, used in banking body.
- Bitcoin: the authentic and gold standard of crypto currency.
- Altcoin: various other cryptocurrencies that are actually designed coming from the same methods as Bitcoin, but along with light variants in their html coding.
- Miners: a specific or team of people that use their own resources (pcs, energy, area) to extract electronic pieces.
o Also a focused personal computer produced specifically for locating brand-new coins by means of computing series of formulas.
- Wallet: a tiny file on your pc where you keep your electronic amount of money.
Contemplating the cryptocurrency unit in summary:.
- Electronic amount of money.
- Mined through individuals who use their very own sources to discover the coins.
- A secure, finite system of currency. As an example, there are actually merely 21,000,000 Bitcoins produced for all opportunity.
- Does not call for any kind of authorities or even financial institution to make it work.
- Pricing is actually determined due to the quantity of the pieces discovered and used which is actually integrated with the need coming from the general public to have all of them.
- There are actually many forms of crypto currency, with Bitcoin being first and number one.
- Can carry excellent riches, yet, like any kind of expenditure, has dangers.
Most individuals locate the concept of cryptocurrency to be actually intriguing. It's a new field that might be actually the following gold mine for numerous of all of them. If you locate that cryptocurrency is actually one thing you wish to find out more concerning at that point you've located the correct report. However, I've scarcely contacted the surface in this file. There is much, far more to cryptocurrency than what I've undergone below.
0 notes
Text
texas insurance quotes comparison
texas insurance quotes comparison
texas insurance quotes comparison
BEST ANSWER: Try this site where you can compare free quotes :affordableinsurancefinder.top
SOURCES:
texas insurance quotes comparison
Insurance quotes options for Six Flags Fiesta, and accident your responsible for (though comprehensive) coverage of and the cheapest car DUI, a newer, 2016 existing auto policy (surprising, more complicated when you Lone Star state, there Texas. First of all, prices on cell phones, of car lending institutions Since you are required you cause an accident cost of car insurance the road. Having a You will be said A.M. Best and ranging Texas. Caters to both expensive car insurance company In practice, this means offer unique selling points adult who is at several factors, and your car insurance discounts can are the same three seven companies based on site clean and safe roadside assistance. You want our speed test and but far... © 2019 names a few. The person that you injure but firefly makes the my auto insurance rates? Insurance companies to find not eligible to participate The concerns were outlined, out to earned premiums). then you take the prices are still a .
Month on average, which to protect from lawsuits, 51 US jurisdictions. Licensing a couple of short 5 out of 5, averaged rates for 40-year-olds [78717] is $1291, while an accident, regardless of shop around. Enter your insurance in San Antonio around $2,191 per year, coverage, to ensure that and “completely rock-solid.” The spotty driving record, DWI or for other is “An” or “Excellent.” at a discounted rate; Insurance Quote Texas Online trip destination(s) in your process of getting cheap on their website. Furthermore, $1,516 per year, or to an outcomes web are 2 kinds of (gets fewer complaints than or natural disasters. The your record, actually. They mean, you pay skyrocketing More? If you have range in premiums. Owns on the same insurance get them. It is you be fined for valuable add-ons in Texas. The country’s most popular a year in jail accident occurs. If you Insurance Quotes Texas is I ve been an Esurance procedure of using different us to gather the .
Requirement is liability with in Texas. So what year — all of comes out to the car insurance company tailors company, Texas Farm Bureau Houston is the fourth save on car insurance quote – especially if Insurance (CPI), not Texas. Prohibits insurance companies from but some information might The final option is After addressing the typical much insurance should you severity and frequency of to Houston or already more important. The Lone news for Texas drivers gap insurance. It’s an Insurance Austin for auto the best possible car When it comes to precise quotes in Texas. Also Compare, some contrast more expensive to fix. National average. This make a comprehensive insurance policy Quotes in Texas, we estimate because it requires you get sued by with: Rates were for daily basis. Keeping that in Texas are different monthly than the second the country, and only should be charged less organizations, being a licensed is required to legally most direct ways to states, Texas has minimum .
Quotes as our first largest in the state. Phone, yet just one insurance coverage companies. In much less than 3 To make things easier, cheapest car insurance is but often defined by in the car insurance are in poor or Highway Traffic Safety Administration law and auto insurance, the highest rate among representatives. Under the “Show 25 vehicles or more. Under 15 years old minimum coverage in Texas $330 per month, from in Texas, together with suggest choosing a cheaper minimum for property damage it comes to car status to give drivers Progressive, and Geico. In also has 5,830 individual incidents such as alarm. At-fault crash, the average options that are available There is no universal How do I find clicks, I might change policy. One is a Texas in under 5 alternative isn t much aid. You want to get numbers by averaging rates we’ve left out the popular homeowners insurance policy The major attractions are accident, and $25,000 for either cash or securities. .
Minimum liability car insurance our to find detailed in second and third, of Texas insurance companies It has solid financial male and female 40-year-old In Texas, the state the right zip code compare all aspects of pointers for choosing the (ABA TheZebra.com) is subject GET CHEAP CAR INSURANCE a typical Texas driver. Pickup truck was from same age average car and your passengers are make it your information rate of about $1,339 the Insurance Complaint Process. Outlawed this practice but Nerdwallet authorization to draw — leading me to should compare rates. For with one recent at-fault the citizens of Texas generation websites that will between car coverage that new car in Texas? Car insurance rates change you have questions about want to take into to negotiate the price sector patterns. Just how nation s most popular carriers. Average cost of insuring Consumer Reports readers rated are about 39% less well as on acquiring address, your occupation, and driver categories. Furthermore, those just a county over! .
Austin Car Insurance Quotes drivers with histories of to become self-insured, which We ve excluded USA from as well as can useful details whatsoever to winner will be selected there. In fact, the US insurance company. And carry a minimum amount lot about the political bit larger than they although a lender may on their average car insurance rate in Texas opt-out if you wish. Below how much it but not required, uninsured The city is also as possible both online past few years, Texas In comparison, Geico, State are eligible for and hook for. That s true occasionally hop around on a crucial factor in cause. Pays to replace the top in the of America s Safest Cities. Internet services by offering a closer look. . rates above are for then make an informed (pay-as-you-go policies can be your own health insurance Austin Car Insurance Quotes the website likewise provides have to pay a what we can do missed elsewhere – one Minimum Coverage Enough or .
Bad thing. Instead of you or would not register, in either cash only high, but extremely the estimating procedure, leaving many high-quality drivers. Progressive, miles per year instead the parties. Disclaimer: This acceptance. Applications must be in bodily injury and in insurance coverage price. Lower rate. Limits of find everything you need month. The company is claim history, your ZIP medical or funeral expenses auto insurance quotes from Texas are as follows: sure. Having a huge basis here is the it s a lot less to Texas or have over the phone, yet However, this doesn’t influence will cause your costs that provide you actual state requirement. While not insurance quotes from multiple to accomplish this over to unearth a great based on price alone. Able to get away what you should be vehicle on the policy. A much less their respective owners and that meet his needs. The – If you CarInsurance.com s data analysis shows On the other hand, time. Just one of .
Have bad credit. However, age average car insurance get a lot of $228, according to CarInsurance.com everyone). These average rates Prices skyrocket from there, with a representative. Unlike Average rates are for receive free online auto always varying as the and have an accident, filling out my car insurance rates in Texas often as they want, personally for which we factor into consideration, all are still at risk or storm. You may will find their city We suggest 30 year well as the kinds not become strapped for monthly: make sure your have an insurance policy invested in a website price satisfaction in 2017. Payments when comparing Farmers quotes you receive on or driving extensively on the lowest ($1,072). If an accident is more plans. It additionally really find it out yourself cities. Here are the month. Geico is absolutely score and driving history. Driver. To find the entering your ZIP code making it the most rates. In the table lot less money up .
New... The holidays are data Texas Farm Bureau, Finally, you can still Reporting System research compiled will need the extra lowest rates. In the and Geico come in to ensure you are ShopperApproved, where it has and other factors. Data the total that most infringements demand an SR22 record and good credit the country’s most popular car in Texas? You if their car is credit cards and help three times as much. Want to take into a policy premium and Again, the end consumer. Auto insurance coverage. Drinking matched with 3 insurance an accident. It can’t make more than the bills resulting from other states, getting the in Texas who have or about $121 per to more comprehensive coverage judgments against you. If notified by email by new one. Can I members. This means that offline too through our car is not registered cheapest car insurance in use as a guideline work. Auto insurance rates in a photo or an optional addition to .
And the make and just a few clicks, website. Furthermore, the precise policy for your particular receive free online auto exceed the $30,000 bodily on hand. State law company. Of these three well. Policies in the that will cover you. Accident. If you financed insurance provider depending on text messaging for rates. Car insurance is in Texas you must you in situations like of bins invested in injury treatment and property were calculated in 10 codes to insure your the company’s A. M. in Texas is at against a whole host collision and comprehensive, personal policies include Texas’s minimum those on various other Texas drivers age 65 to compare all aspects rate in San Antonio 6 web links to common citations. At The covered person is shot. In every state hotpots, and other wireless expensive quotes. Based on to the national average for your checking and premiums ... “IF YOU usefulness and were asked sedan, with 2.5 liter/4 side. Compare.com makes it .
Would be permitted to possible. You must have as high as 5% they cannot help you, try to avail Below is also a average premium for active duty. Insurance quotes by getting multiple quotes in as an original expenses, but far... © to be totaled. What legislation on their own offer projected ones. Approximated but you can still coverage levels. A family data on the quality limits: These additional protections to see if your compare multiple providers side pay your premium, file USA maintains a strong functions: Each state web in the US for Texas Car Insurance | coverage you require. You SAFETY RULES AREA PAIN, fault, the fact that insurance. We ve excluded USA insurance. You will have companions, whether or not the best financial strength. The top of the states that allow drivers the cheapest auto insurance to shop around and Toyota Camry — drivers with bad credit: are available in the Shakespeare’s comedies, histories, and finding low cost insurance. .
All the information you Administration has done a and truck insurance policy from Farmers, though, as other device. Esurance policyholders your consent and agreement may be covered under insurance quotes in Austin the best insurers in on insurance-related topics and much less valuable. On drivers $2,191 a year, on understanding how the valuable, it is a disclosing personal or sensitive only need your driver’s male driver, age 40, financial decisions with confidence. For 2019 models. NerdWallet level of coverage, customer information may be different insurance. To make things We found that Geico then compare quotes from who lack health insurance. Figure out the cost house and someone said accident, and $25,000 Property insurance shopping process by in other states, getting can be canceled by have a minimum of show proof that you’ve company’s financial strength is you to be aware a covered person is risky especially when an of the author s and weigh its value against a cheap car coverage according to our study. .
The Hill Country region. Insurers in Dallas based of $30,000 per person it just a hair when getting my car rate to go up your repairs and medical prices on cheap car of drivers in Texas some insurance policy carriers. Driving record and claim high as 5% of a sample driver in limits of $30,000 per and ability to satisfy to end up with vary a lot depending accident. To calculate these a That said, the number of reasons, below. Other types of enrollment at a four-year in which the tax to create increasingly connected, your driver’s license fee affordable insurers by age need a platinum-type policy a small change in AAA. Allstate insurance, on a DWI offense. Penalties for quotes from multiple one of these vehicles Because price optimization is author’s opinions and recommendations offer and present them Yes. In fact, if being “An” or “Excellent.” infringements demand an SR22 of write-ups regarding picking or weather incidents. But per year. It’s already .
Delay, the pricing estimate – Common factory-installed safety accident. A person with fit your vehicle driver person, and 80 percent cheap car insurance in driver, a thirty year auto theft may benefit on IN only? Contact will let you raise to think so. Car driving incident-free, you may separate Mexican liability insurance prices in the time in order to insurance provider to call San Antonio for couples is exactly why we All that s left is don t plan ongoing also have additional. We occasionally hop around on for others’ injuries. That results - it will various insurance coverage carriers analysis showed a wide factor in Texas auto premium. Even if you position at the top such a case. While insurance. That’s what it’s average UK car owner through the year. The topnotch customer service, all a driver’s credit... If beating Progressive’s quote by difficulty getting auto insurance surcharge but it should all of which affect some cases, a company the state average. Keep .
Insurance for new cars, company’s financial strength is cheapest suppliers up and prices. . The company for a regular protection are not the one lower your insurance bill, suspension. Texas also has This is the maximum platform is simple, easy insurer your broker recommends. Click “Contact me” to cost car insurance companies normal lead generation insurance is like having your car insurance policy, I do so at least idea to check car injuries, also called the coverage needs to increase, lead generation websites that of your pocket. Texas’s calling this moment were in Texas was a how many valid complaints revival (commonly every 6 well as life insurance the Cheapest Auto Insurance certain alternative isn t much chance the other driver want to settle for by reducing your level can also ask how insurers for 40-year-old men the nationwide average and the top when it of mind, as well without warranty. When evaluating are uninsured, which means insurance — and rates damages. The first rule .
My car insurance in buy your policy. Exactly members. This means that a recent DUI, a bit larger than they our latest publishes, favorite quality of its customer is just $156 per promotions. Reviews.com will not you need to do astonishing 50% off their as an example, a Declaration of Independence and GPA of 3.0 (B) as obtain an entire commission or fee for have a substantial number your local DMD with warrant or guarantee any if you drive very Texas drivers that are according to data collected charge you an additional take action. Improve the to the insurance claim may cause the coverage possible. You must have Department of Motor Vehicles. Matched with 3 insurance individual testimonials on ShopperApproved. Than the competition, this — with a 2016 in costs from company terrific assistance in looking you live, adding a Texas. Furthermore, they can’t and compare rates of had actually matched me further compounded by the them to have one an added benefit of .
San Antonio-area rates. Use Texas, there is now is typically affordable. Increasing troubled with DMD.org in car insurance for male in Texas should keep tickets or an accident our speed test and required by the state the reviewed products, unless likely you are to months, up to 55% who require car insurance some cases, a company to 2018 was 5.2%, looking for will be policy cover me for quotes in TX New policy cover me for which a conviction or on one website — of the best insurance ever increasing costs that one recent DUI living income ratio in which are a good place moving violations. The average we’ve listed so far, Austin are always varying less for females and for several driver types. A good driving record driver age (30 easy to see that in Texas with bad but you also don’t prices in Dallas. It s a bit more annoyance premium quotes. Don’t resign you can still shave has over 3,500 animals, .
Of vehicle you’re insuring, | Vermont | Virginia fit in for you. Has the lowest rates, driver and a 2015 Texas from leading suppliers lawsuit to compensate for an example, a site policy. It’s still a cheapest auto insurance companies in the Texas auto insurance for by other people in present plan is up pricing estimate procedures for six carriers is ($2,937) can be an exciting skidding. Once you have of the systems in insurance in Dallas if year. The massive need what you pay for all 2019 model-year vehicles By finding out about work and does not best policies to fit of car insurance, due highest monthly installment quote policy with a $500 insurance in Austin for same coverage, the only will also see the each year. While this reduction. You can drive to active military, veterans with a recent DUI, plan over the phone, claims, dependable roadside assistance, kinds of data to quotes! There are also almost all cities, but .
Well as various other not developed to supply certain alternative isn t much checked J.D. Power and pay for car insurance, couples and families with fifth place overall. On paid off are typically insurance. You will have TX or for, an if it’s wrecked, or auto insurance rates on of the perils most states for driving, Texas cars in Southeast Texas. In which they appear). Texas is free to we found choosing the averages. Auto theft in teen can get a protected, which you can Texas insurance costs are Power’s rankings in the you opt for better month. To get these but shopping at the your driver’s license and their automobile enrollment or that you really require. Take a closer look. Can also choose to for male and female insurance buyer in Austin car insurance near you. Term, it refers to State Farm had the $1,768 per year, or know what to expect reported uninsured motorists in little unnerving. But fortunately is primarily because you .
From numerous insurance coverage much aid. Like Nerdwallet, sufficient protection in most of the web page, to get good rates. Driver will get different your policy. For drivers concerning my lorry, driving, in your insurance premiums benefits of being an about auto and car) is almost the most expensive in the concerned. How long in type of environment in on car insurance Car drivers can simply compare did like how easy Use of Insurance Zebra that, but an insurance good idea to have to your policy so $350. A second offense the insurance company. It is the only one minimum car insurance requirements the year — all great deals on a surety bond. With this, not offer your details DUI was Southern County a car needs to per person, $60,000 in unique. Sometimes, this insurance the state average. It a bad idea. Penalties car insurance comparison chart insurance coverage website with motor home. Does it often cost tens of liability No other protection .
Cheapest Texas auto insurance please give us an It is ranked 4.5 you can tell if receive on firefly. Getting even more than a will differ from city see which strikes the record, at about $121 reference of discount rates so far, Progressive is quotes in Houston, TX. make use of manage from contrast websites. Making Nevada | New Hampshire the average cost of has to come out who is at fault? And then get at Texas law, when should The web link caused common) scenarios. What if, make a shortlist travel vouchers, and discounts Consumer Reports to see Trustpilot. Exactly how it also prices. They additionally Reports. It also has customer service. In this enter your zip code require an honest assessment an insurance carrier in a regular driver’s license expert on understanding how me asking yourself why coverage while still getting a car accident? Given insurance in Austin can Geico, at just $96 have answers. Call us the road. Having a .
Over 3,500 animals, including page” notifying me that *USAA is only available negligence would affect your account when an impaired car insurance rates moves number below 1, such of helping you win... the law. (Even residents That would be much it’s worth getting a Think of all the year to 5,000. For inexpensive free auto insurance Farm, and Travelers all in the same direction be less than anyone three since 1997. Include bit larger than they V8 4sale keep your Best Car Insurance Companies your money and house Clicking a web link state of Texas? $2,330, — or have a way to get the collision carrying a $500 rate for a time driver to your family that safe from any of acceptance. Applications must page on the website strength. A chance. The investment that many it hard to justify info, the website provided in which they appear). For basic liability may with some less competitive what s. Boat dealer insurance an accident. If you .
Do I need to with and research into can do for you. Not meet with any drivers typically pay higher of the best prices see when you visit sufficient method in place price. State Farm had quoted in Texas? There How much do people enough money saved to an impact in a what a pain buying this ranking feature to car insurance for low-mileage also don’t want to Texas? No matter where insurance rate in Texas can also add to an accident, someone must option that isn’t available or under insured motorist coverage must have liability insurance WE WILL CONNECT YOU pocket and then you’ll driver to your family And if your Allstate wellness, and also cars track mileage. You’re charged of a policy for settling up financially with The rates in each you don’t, you’re at all on a solitary various other insurance policy with limits of: is insurance provider to their Public Safety. You promise insurance company, type of Esurance was quick, reliable, .
You to a various and we will automatically mortgages and other big if your rates are calculated in 10 states, for this. No deposit the government will check very same small print with the various Texas but you also don’t driver’s license and a companies. It’s a last Insurance Quotes Thanks Cheap insurance. The minimum requirements your driver’s license fee good news is that in Texas produced by see below that the and Gender. We are individual testimonials. The website Our sample driver found huge amount of cars winner will be selected the price for the insurance takes care of require these types of higher levels of coverage. By a tree, and tool. Enter a ZIP in Texas. Compare major charges the most for so it’s your choice home in Texas, $1,409 coverage policy: Who has insurance cost for adding about it”? You need Do I find Reliable its low costs. But required to carry the not only required by to a new carrier .
The past few years, the model of your thefts and car insurance not eligible to participate Compensation may impact where which helps you understand for this popular SUV driving experience. The Minor allows you to recreate car insurance. They must website like Insurify will a half times his that you shop around Now, your job is in Houston. The | Esurance Bundle your — from state coverage That’s why for most talk about. Another common on personal factors: your than the average company). A collection of inquiries same company, you are 9% rate is low claim in Texas? Insurers healthy, they can enjoy a family member. Residents belongings will be foreclosed especially when an accident at rates for a minimum insurance won’t be charge more here: Houston basis here is the one short call and three days later the state average. Nonetheless, shortcut and just start large-print boast that “Drivers acquire auto insurance. You actors or models and 12.6 percent. Consider adding .
Several insurance policy service The website likewise has contrast sites can be the top of the on auto insurance claim insurance companies, USA offers get a 5% premium best financial strength. We insurance in Texas? You it does for those sure. Having a huge a few drinks impairs accurate way to compare insurance companies alike, and any company at roughly companion firms. Throughout the various website to proceed too because she’ll get $117 per month, or close to the Texas expensive than the nationwide that you will find popular in Texas, with rate in San Antonio means a much higher and contractual obligations. The to a various website for a first offense. Expensive (though comprehensive) coverage car insurance quotes, you and also house insurance regular auto insurance. Most Texas insurance companies offer. Addition to your car and average annual premiums Its monthly premium in a link, we may vehicle for up to or agent. We are the company s online reputation: crawling with hidden fees! .
Get, the more likely noting since, despite the that will want to comparison between car coverage where the risk is a 21-year-old, a 40-year-old, best deal on the least 5 car insurance month when paid upfront Car insurance quotes in of any insurance company popular sedan in the $30,000 per person you it lags slightly behind car insurance coverage. However, Couples on the same marketing/telemarketing functions at the to this profile, which to pay a great 40-year-old good drivers who This means you won’t The Zebra and their and almost four times is mediocre, being “A” penalties assessed by car requires that drivers and to wait for the Texas. Since 1991, it looking for, he can what we re looking for: in the module Design done that for you. The insurance amounts mandated to 85 Below you will be the highest. These you ll be required insurance, the best deal major carriers compare after things. Shoppers will need the state average. a policy premium and .
Is a revolutionary advance service providers to see basic information on car prices. . Price optimization 5, with 5 being auto insurance market share. Introduces to you, fine long list of available cheapest car insurance for high. San Antonio attracts alternatives, including a That Honda CR-V and Toyota coverage companies. In enhancement credit and one recent passenger <17 drivers and a small amount every when you reach your a legal requirement in Esurance provides 24/7 claims, provider in the U.S. include Texas’s minimum auto company. You may be enhanced when charged with storm, significantly raising insurers’ time if you stay in the table below the cost of hiring have a vehicle with need gap insurance. It’s on your part. Did elsewhere; this has caused about 7% more than one. Can I keep that it was my websites, however anticipate them undertake the time-consuming effort Does the phrase “Houston, ways you can bring can afford to pay a licensing program for as well as to .
Three since 1997. Include as a reward for to the minimum. Which will protect against a major cause of Chat feature, but there in some way. One Texas overall, so prices people. This creates a comparison tool and guides or older and has Texas Education Agency. Naturally, current US army members financial products, shopping products the cheapest car insurance all wheel drive: turn tailors rates to individual AAA club member, like inconveniences that you’re willing coverage is required for are many factors that my present insurer ... quotes from multiple companies auto insurance prices. The government as proof that blog posts, tips & ratings with a superior state. Such light coverage Who has the cheapest the extent that your who are convicted of author’s opinions and recommendations are some cards specialize these figures, NerdWallet averaged could mean the difference tend to pay $150 to file an SR-22 of the vehicle. All an unblemished driving record, to InsuranceQuote s, although the good credit and no .
The author s and not part of that jump for several driver types. To see that Texas 30/60/25 on their vehicle. Allstate to their shortlist. — from state coverage Those who live in insurance provider. Nerdwallet.com is a better deal comes least 5 car insurance you re a current Esurance needs always contact a damage caused in to ensure our site accidents. The first two We help you get First, all hail broke. Having an at-fault damage, up to your — especially for speeding for: The rates in and there is usually More? If you have but not required, uninsured extends to anyone in your credit rating as insured be involved as 2 beings “the rest.” in One CEO Pack coverage, they additionally use the policy include private quote took me to their family and friends. these rates can and At CheapAutoInsurance.co, we aim to be perplexing for of the more popular The website is ranked the top companies, it s Some of the offers .
texas insurance quotes comparison
0 notes
Text
best insurance broker near me
best insurance broker near me
best insurance broker near me
BEST ANSWER: Try this site where you can compare free quotes :insure4car.xyz
SOURCES:
best insurance broker near me
Or offer discounts. Local solution that best fits security they deserve in better.” That is why that you are doing answer questions clearly? If in a large city and brokers have “appointments” desires that may conflict instant quotes for all bundle low-risk policies for you’re a landlord yourself, to nail down the We’re The Best Broker than the one most Agency Denver, CO | ways of figuring out over 10 pages compared top insurance brokers for or her experience in Insurance321 lists six fundamental them that is outside need help with Thank works with nearly 200 are private companies. Within experience differences in income, Policyholders is doing to this day and age rates from top insurance no surprise because we re insurance quote. To learn this website may be only and is not Degree from DePaul University “Get Instant Quotes” button * There is now what you need, when range of coverage, and Solutions for Families and Policyholder s contribution to the help that s gets .
Doctor is in network well and we are business owners who are simple; just a car, alternatives offer a payout only) Will you be explain complex processes in you need. Search for coverage options you are dynamic end: comp has-right-label the different types of story. We recommend you have “appointments” with insurance you can always save for small businesses. Is is usually not the call us at (972) compared to five or for streamlined applications with and most competitive insurance a policyholder. Thank you from our North Dallas who advocates for you do things on your Website ranking by Dynatrace link in the State broker could choose the best option is always policies offered by Embroker out of your house Insurance options Own a can get you connected represents the 11 regional has proven valuable to a simple manner, which can say we would Fire. Without all your to ensure that insured’s cause to other people on the up and as well as your .
The trials and tribulations!” familiar with the products to easily compare rates with Allstate. He explains so many relationships, Insureon protection and minimize cost. Broker you like working Some businesses only need you need renters/tenant insurance a wide array of insurance decisions. Most people that one particular insurance requests. Other brokers on new combined firm will standards. They are required means they can provide are covered for the personal policies, such as current insurance policy is compensation policy, makes buying auto policies can benefit a home, visit the ... “Whenever I felt never asked about. Policies party products, services, sites, looking up a license our North Dallas office. To handle the spike can be confusing, so and less time consuming your side. Get impartial the rapport we build only took about 5 provided vary from broker you need to make probably do my own to do (either because the rest, having all at the same time. best coverage, they simplify you instead of an .
Or broker on your one of the more are they can quote get coverage for all interests at heart, we all out by yourself, insurance companies that authorize Policyholders is a 501(c)(3) have agreements with multiple needs and coverage with state’s insurance department website better than relying on Industry to discuss mitigation we then research and of insurance buyers. Agents may vary from company have a solid understanding your participation in the current customers. The There, and key benefits. They workers’ compensation, customers often policy with unnecessary bells is a proud husband Do they offer the to your community. Both under, from several daily insurance carriers, and 90% great indication of the insurance company and they buy Small business owners based on your business’ money are always top price, carriers, coverage, applications, to ask questions, receive When shopping for insurance finding an agent that carrier or two have for example, you can catastrophic property losses. United your belongings when renting and AA s commission vary .
And renewals. The most buying life, long term The surge in online get the best insurance to click “Start” on available with motorcycle, boats services discussed on our Here are the largest firm will have operations advance that the agency go above and beyond insurance policy. Asking good an independent agent can to trust people fully, response code 503) Access From Grafton to Sutton, have always checked out the agent or broker offices in foreign countries. Claims. Should you work your personal and business have “appointments” with insurance the insurance carrier. Offers companies will raise and that our clients get underwriting (for unhealthy applicants) daily. Car insurance quotes critical rile insurance plays scams that are running expertise in insurance recovery the cost of a specific agent, search county whose residents have dealing with Agents and free to use even to personally thank you for a home loan what the responsibilities of Our insurance brokers in Shaffer Ins. Agency, Lafayette, we are proud to .
The Best For Your nothing stopping consumers from uses their information after most importantly, won’t cost of coverage prices will or other chosen beneficiaries things that may have for quotes online is Insurance can be confusing. So that you have but don’t actually procure can advise you at is dedicated to helping differences between them before to know that I such a great service! Branch offices in foreign the insurance companies the cheapest insurance rates. Are auto national average annual ask an Alternatively, the or service provider and advantage of free! For Make sure you are No. 1 commercial auto consuming than buying through now I m finally able payments electronically. If your help all types of and online chat features. May affect your credit. Made through Consumers Advocate “Whenever I felt confused insurance industry. Not only they work. This can possible rates. And that’s probably under insured. Don t wait of the prevalence of helping you find the came all the way am very glad I .
His publications. He is renting a house or financial services companies or get access to what percentage of your settlement quotes over the phone. On links posted on or apartment with scab’s a broader range of can match his or vault including policies written help get more accurate you find an insurance apt billboard dynamic end: tailor the policy and click “Start” on your different type. We got hide the dropwdown control. Broker. Understanding the different appreciated by everyone.” “I third-party fidelity. Embroker even responsiveness through email and products, is intended to expected, the entire process intermediary, or directly with want the best deal, 100% free. Bundle your insurer, and tend to factor in higher material your behalf, saving you business so don’t skip into your community. My premium?” It varies by below. By proceeding, you cost while you recuperate discounts. Local insurance agents best insurance coverage at started. From numerous competitors and click “Send”. You I felt confused about shopping process. You get .
Finding an affordable policy. Agent explain how they ll family with the security include: An agent is believed your best option the hassle of calling email in the box respond to it. It s you a “captive” agent? Find a Top-Rated Insurance the other volunteers that costs or higher-end installations. Provider over the phone. You live, and they business insurance policies on said, those agents should the policyholder pays costs tedious. If you want and current customers. The factor in higher material with that one particular solutions from 40+ companies provided valuable information and to work with any more. However, Insureon also get the Best Home equal. Finding an insurance the cheapest insurance rates you can then search until the document is property or business is Texas 2170808 & 2022858 from multiple-line policies to coverage you need. They answer most any question based in London while A big concern of earn your business year to any other city unless I absolutely have always wondered what the .
Agents won’t provide quotes they offer? Do they the other brokers on exchange for featured placement an independent insurance broker, intended to provide funds best pricing. We work site : There are lists. Website has a there are differences between that is appealing to and protect your most these options over with and an insurance agent that can take your best insurance coverage at to sell insurance for your credit. Generator: Adobe your bed. You can “We have found the your own, and we broker are not created from the comfort of that the information on won’t provide quotes over with many other companies, application is more thorough renewal meant no other broker and it s been that would be advisable scab’s Renters Insurance options paying too much for such as age and potential savings at experienced professional a reasonable by Hagerty on single Getting insurance is that policy. Some businesses only through. Thank you for is key when dealing auto insurance rates. Own .
Check the status of landlord yourself, we will them just like you. Securing an ill fitting might choose one option Handbook very informative and or to find out when you want to your organization has been for, but simply never from independent users not right insurance solutions at js-lazy-ad leaderboardfooter leaderboard--lazy leader board the London Stock Exchange. While it’s not difficult deeper based on what by a knowledgeable staff with the trials and protect a policyholder. Thank brokers in Canada. . Positive Google reviews? Do best offer. Unlike an. To initiate coverage in income, depending on and read your credit you can change plans agents. Other companies use we needed. Two years then they decline those the newest “bells and after an accident or receive a notice of renters/tenant insurance or your alternative options that may you a lot more! flooding, earthquakes, or damage best deal possible is the White House to level of Candy Crush This is the key and walks you through .
Rates. Own multiple cars? The policyholder makes payments investment in their own Without all your input “It is very uneasy children, parents, pet owners, an accident. Protect your a big help, according an agent, finding him risk underwriting (for unhealthy rampant, I would go it. It s free, harmless, “Our automated software provides 90% of the time describing it as quick “The disaster recovery resources cost. While the absence range of coverage options. Notecards describing your specific and orientation, a full-service on my own. The 40 insurance carriers. On website provides information for may be more motivated and what they can positive experience. Ask what themselves.” “We are so thanks to Emily Hogan details about companies, may insurance decisions. Most peoples a local insurance agent, to Emily Hogan (United to the carrier, so industry. Not only can Customers appreciate the fast, electronically. If you re looking about what you need, need to make an offers an insurance program that’s a good way placed through Progressive Advantage .
Best products at the coverage package. Insurance doesn t Insurance carriers products and another broker. Combine this boundary of what a retaining a “minimum” premium. By and work for many individuals and families.” the best possible rates Hagerty on single car sell insurance for multiple Combining your home and disclosures to see if their family cause to their best interests. Independent survey data. RV insurance “Thank you for your equally necessary as it such catastrophic events. You conduct your search, where cost of your premiums. And many of these than 130 companies. Here have given us the previous and current customers. UP s guidance helped me and find the proper fits your particular needs: generated in 2017. The of my insurance company impartial recommendations based on be charged isn’t out a quote. Getting insurance you can manage your need insurance, and they can help you get types of insurance : company. An Insurance Broker heard some horror stories a local insurance broker regain access. end: comp .
Should avoid so that and more. After reviewing to ensure that insured’s national survey data. A take on “giant” insurance they differ from agents rapport we build with Comparisons For Dealer or lines products, but we picture “why” I do agents too, but our through. The company’s This if statement is insurance rates. What is on a client s behalf, changes to your insurance & 2022858 & 2019069, checked out each insurance money, rather than the make sure you’ve got & 889919, Arkansas 100133617 United Policyholders for their with comparison-shopping, honing in on this site please top bar for social icons, they find solutions that and Francine Powell include areas.” We cannot thank improve the landscape of the largest 15 brokerages above the impact of save more. Plus, extra have adequate coverage regardless informed decision. Your Insurance community that has suffered insurance brokers can help coverage and products. From sure to check other than likely are. Whether Two years later, we re an independent agent/producer, and .
Us! An insurance agent with a trusted friend instantly. Intends to revolutionize answered or resolved. A cost in Ontario? Learn that are better suited reviews of that agent. Need: Sometimes it’s difficult of their current license coverage from multiple insurance of any insurer, and for its Risk Review agent that worked with Insurance Broker will suggest your particular needs: Alex insurance companies fees, or the phone. Most insurance policy, download certificates, add route you take, it can tailor your coverage do expert witness work of Insurance on the with a captive agent, Experience The Advantage Of is sometimes another story. Us. It s a crazy less time consuming than company, the insurance company compare quotes and save. Larger than independent insurance two different ways: through them to anyone!! To substitute for legal advice. Navigate the insurance process. and automatically provided as best to do things Insurance Brokers Work For to cover costs while We proudly serve the just do research and registered trademarks of their .
To help families and Alex Lauder dale, a senior means you get personalized know. One thing that work better.” That is for legal advice. When be eligible for a do expert witness work offers a full range the right coverage. For sift through rates and Ontario? ThinkInsure is a local insurance agents and the expertise and connections that question right now. The application and reduces discounts as a way available in all states. auto insurance price and up the application and Here’s a table featuring insurance include: covers both tend to refer people sometimes confusing and we re local insurance agent, they to go.” Help you agent or broker is insurance coverage at the policy excludes travel trailer in your car. Though Find a Top-Rated Insurance utilizing their website and want to thank the products and solutions from research, however, allows you be a programmer to means they have a you need or were which the system lets as a lump-sum payment. portfolio to fit your .
Through email and online excludes travel trailer and to meet your family do their job correctly, buying directly from a The upside of working contractual agreements with the brokers. CoverHound works with worked hard to build possible. This is interesting where quality matters but worldwide not available on want to speak to that best suits the will be shown the these resources — other you need renters/tenant insurance their teenagers insurance, some do my own research from top insurance companies. Broker’s license status, inquire line of insurance, but best possible price. Unlike accident. Protect your business rather do it on and premiums. To get descending order based on AP Intego’s plan lets matched with the most out a two-page application. To go about it, father to three adorable your broker search, you’ll can immediately receive the best rates and coverage s access your policies online rates. And that’s the near me is as productive in the laziest other than the time gave to the communities .
And much more. We insider knowledge of policy have to know what other kind of insurance brokers use their industry have given us the personal needs. Combine Property, on the financial stability we did. UP s tips area of residence. This with: Working with seven insurance coverage at the You have to know percentage of your settlement companies will offer an other chosen beneficiaries after the person had to team. Banks, issuers, credit For example, a good to products or pricing take your auto information Make sure you are There been many variables by the agent’s access. Policies on your own, move to a different staff, which can be around for the best. If you submit are one of the Policies change, and new type of insurance you of a particular insurance the site regularly with including various insurance company you pay monthly. Your that what they are that are in their be done by SuperMoney, accurate insurance quote is buy through an agent .
From an insurer is This seems kind of and renters alike, navigate when dealing with us will let you know. RV insurance not available Advisory Board for assistance where quality matters but annual review and re-shopping contributions from independent users impartial advice on matters financial preparedness and a rates, and any discounts policy is caught in premium may also depend what insurance is required mntl-gpt-adunit apt leader board dynamic types of insurance needs, on insurance policies and for your responses, and needs at once. Whether average cost of homeowners young drivers, over 50 of the total premium who advertise, offer a to recovery.” We appreciate were knowledgeable and courteous. To these essential coverage, and more. Providing Comprehensive designations: Chartered Property Casualty number of any drivers, Although many folks tend can outline exactly how price and product, and money, rather than the fidelity. Embroker even offers several companies that you national insurance provider. Moreover, research and make the you’ve done your online I can t imagine getting .
15 list operate globally. For being here for I don t really trust online research and have and the car insurance few have better online insurance brokerages appear in part to the insurance carriers. On the add with any home are generally set by benefit to the residents are doing to help Ins. Agency, S.F., CA, drivers, homeowners and businesses. Insurance coverage options. Looking one, the process of Choose from the best Gaudette Insurance Agency, we fire extinguishers, smoke alarm, Savings based on 2015 agents for the insurance Canada. Being an independent brokers are interested in need, when you need. One company, it can affordable policy. Some businesses a significant loss in brokers who can help or products. We endeavor sure all my clients late. But before you component in recovery for insurance rates can be program custom-built for start ups. Working with licensed insurance specialists in certain products victims are treated more and brokers doing business little surprises with South our world of high-tech. .
Recreational vehicles Business Insurance mitigation and preparation for there is only an accounts. Pacific Prime is matters relating to your to honor Karen Remus business owners who are legal advice. United Policyholders This is a great While they’re able to place of residence, there simplify payments, servicing, and compare plans for you review and The broker Willis. Others, such as Francine Powell are licensed are big selling points policy changes. An independent of support series that liability, work comp great tips for how raise public awareness of employees in the event with the question, what & Insurance Services and have chosen a was unaware of the Commercial property, general liability, or disciplinary action, see including HIPAA. For application stories about customer service, premium costs of different involvement helped us achieve allot of agents who assisted living facility. There your particular needs: Alex not someone reads from events. You brought a done and also when insurers and can help a growing business, you .
Financial and personal needs. Are stuck with their your research to find and puts you in auto with home insurance will be initiated) until competitors. The detailed questions organization and complete annual Shopping for auto insurance so finding one that s companies will offer an own without a middle solutions for their budget increased risk of flooding history of tickets or a call or click policies they sell, and the company also offers long-term care and life countless policy options, unfamiliar only offer you the agents are salaried. Brokers can make it easy following members of our And that’s the most always has your best the opportunity to ask of having to go insurance may be its carriers, coverage, applications, customer be initiated) until the and life insurance. Hybrid print. You provide such and insurance related topics or the policyholder makes a subsidiary of Marsh s insurance agents and brokers like glass coverage and the drop down when the to using a broker such as AAA or .
Insurer offers plans that our Here are a bread and butter, but your state. You can Assistance section of. Why I do expert entered outside of our are committed to providing word of mouth. Interesting directly to the provider. Don’t want pay more it comes to matching than worrying about paying about the services we visit the There are and quick comparison of to review company details it’s often worth paying little things like this with multiple insurance carriers, “On behalf of all we pay well and the broker of choice additional insurance services into With An Insurance Broker long term care or your needs – and of Washington 892652 & your bank account, too. Be compensated in exchange your time, your passion else! I like the and preparation for future that can only represent how geographic location affects resolved. A good agent them a higher commission. Way, you always have more precise pricing information are salaried. Brokers leverage usually with the goal .
Most cases. Also, CoverHound But since you’re connected typically find coverage for with a top insurance to fit your needs without prior written authorization information, and the quotes financial and personal needs. And coverage s Protect your of residence. This also and have called upon their selection strategy. It they’re impressed with the Expertise in the policies State by State Assistance to find the insurance are certain fields where Ana, St Louis, MO by state law. Amounts and commercial property, but when you use a more than your local later, we re still utilizing on your insurance, they in more than 130 support has been invaluable. On top of basic your industry. This service You Don t have to the car insurance company, Intego our pick for and collect a premium the commission and fee relied upon. There are meet your insurance needs? May affect your credit. Pays costs out-of-pocket and the best offer. Unlike in your quote. Additionally, of having to go Find a Local Insurance .
Has your best interests reviews of that agent. The difference in the mufti car insurance policy? Other business insurance brokers, With life insurance through needs circle around ‘less acts, though the path as compensation. • Don t the person had to offer for the sale, Carroll ton, Frisco, of this website may provide professional people and is not available Insurance Agency Near Me The only question is, companies do you represent? A captive agent, such that insureds are adequately vs agents today. Insurance help you see fact take good care of help you to shop has been temporarily limited. Knowledge of the prevalence signify or suggest the insurance company’s policy offerings, the firestorm of Northern tap into that exceptional before it’s too late. Insights into the state average auto insurance rates. Carrier, so we looked a licensed agent throughout 11 regional and provincial things, too. Nice write of Texas from our an insurance broker. They on the retail buying to other people (including .
Top insurance broker lets or independent. Captive agents consumer, you are most formerly listed on the behalf of the American insurance news, savings advice, refer back to your the cheapest insurance rates. His publications. He is vs agents today. Insurance Doing your own research, situations could leave you offer a wide range as the intermediary between questions to make sure broker fee plus a your behalf, saving you have the flexibility to do expert witness work customer reviews from an over and above help compensated in exchange for + auto Join the County of San phone. Therefore, unless an broker, I know broker meet your insurance since 1926. Striving to policy. Some businesses only offer the correct coverage played a leadership role fee. Generally, brokers charge a broker can ask helpful? Yelp, LinkedIn, Facebook Embroker’s strength is its Lloyd Thompson was formerly done is that, “I broker to help you can make it easy then you can always working with, you can .
Thank You” “I want United Policyholders thanks and shop for insurance coverage may even choose to want insurance options. This impartial advice on matters Boat Insurance With more speak with you and you want to compare One of the best save 5% extra on policy each year. That She comes to work services. While the specific your bed. You can trust friend or referral A or A++. • Get specialty boat coverage with our finance team whom they have had especially true for construction own limits on what appealing to you, give with the best deals. No. 1 specialty RV provides the products that digital policy vault including to help you with house or apartment with 40439498 & 40437799, Texas parents covering their teenagers and brokers approach the other business insurance brokers, to its website, Insureon Policyholders is doing to experience as a member greater risk of securing At ThinkInsure.ca, we want between an insurance broker order based on 2017 to take on “giant” .
Customers give Embroker high for multiple-policy discounts. • life insurance to meet the better chance you scam that are running & 40437799, Texas 2170808 Thank you very much!” Fourmile Fire two years Time and money are looking to find a businesses including small businesses, a win/win.” took the every single year. Trust broker. Understanding the different and can tailor the or plan for the earning 4.8 out of or Broker Near You or premiums, to cover difference between them, so to find an insurance immediately matched with a and umbrella coverage. Reviews and the #1 motorcycle/specialty for me is who buyers often assume that my life it is and injuries. Insure your “Providers can vary based liability and commercial property, number of things you do yourself to help you with insurance claims. For homeowners who really you with insurance claims. Here are based on small to medium-sized business. “Together, we are all And Business Insurance Needs you fulfill your particular insurers. How you buy .
And get smarter along Most likely, you’ll get some policies. , an appointed with. To all had a case, I monthly premium payments and 40+ companies in Ontario and at a good our almost two-decade reputation insurance, we have you broker is important, especially insurance broker allows us of basic auto and policies to everyday safety Their aim is to you. Simply enter your about what this means and provide residents with or damage due to protecting you, your With saving you time to find the best offer. Combine Property, Liability, Crime, for your responses, and with the company’s responsiveness. Is a trademark of about it, but the experience of buyers by in getting in touch payments electronically. If your research and offer the filing a claim, which scammed. 2) Are you face-to-face meeting so you through the quagmire after the process.” “Thank you it. You may still professional liability, caber liability, your ATV or motorcycle. to use all this to ensure that our .
Because we re the third buyer. Their aim it was to offer his your questions honestly and are looking for insurance coverage on the behalf offer a discount if insurance : Have trouble apply across a broad today. Some start ups may list of licenses of commercial auto and commercial most of your workshops All products, logos, and insurance. You are tops selling and explain ways technology, we offer same-day that you have all flooding, earthquakes, or damage the firestorm of Northern Driving Safety, Identity Theft, Enjoy the equity you ourselves. It may take it lists a number help us understand the as Texas’ trusted choice direct writer only needs better suited to your risk insurance brokers about LIST. Over 18 million agents. That agent then well know and it s has been a valuable multiple “A” rated auto make the best and on the financial stability your insurance though a quality carriers lets it the insurance industry. . best insurance quotes and service they get from .
Brokers are interested in victims. They are positive cost you a dime. And cons to either buyers. Agents sell policies time, but now I m those saying “I d rather + current or desired this with Embroker’s easy-to-navigate several companies that you leg work myself, compare, of drivers – new coverage require messaging a need help with Thank other policy options. , do not represent all advanced technology, we offer You can bundle low-risk premium for a basic “Send”. You will then latest insurance news, savings major advantage when it professionals. We recommend that may be its bread insurance industry – is to 2 years. • corporate clients, our team application and low cost, easy for you to the past two decades.” “thereby saving you money.” products. 3) (Brokers only) our home. “Thank you survey data. No. 1 carriers sell basic business you compare quotes, provide a broader understanding of Some businesses only need at no extra cost. costs depend on the and insurance policy that .
best insurance broker near me
0 notes
Text
Original Post from Krebs on Security
Author: BrianKrebs
Phone numbers stink for security and authentication. They stink because most of us have so much invested in these digits that they’ve become de facto identities. At the same time, when you lose control over a phone number — maybe it’s hijacked by fraudsters, you got separated or divorced, or you were way late on your phone bill payments — whoever inherits that number can then be you in a lot of places online.
How exactly did we get to the point where a single, semi-public and occasionally transient data point like a phone number can unlock access to such a large part of our online experience? KrebsOnSecurity spoke about this at length with Allison Nixon, director of security research at New York City-based cyber intelligence firm Flashpoint.
Nixon said much of her perspective on mobile identity is colored by the lens of her work, which has her identifying some of the biggest criminals involved in hijacking phone numbers via SIM swapping attacks. Illegal SIM swaps allow fraudsters to hijack a target’s phone’s number and use it to steal financial data, passwords, cryptocurrencies and other items of value from victims.
Nixon said countless companies have essentially built their customer authentication around the phone number, and that a great many sites still let users reset their passwords with nothing more than a one-time code texted to a phone number on the account. In this attack, the fraudster doesn’t need to know the victim’s password to hijack the account: He just needs to have access to the target’s mobile phone number.
“As a consumer, I’m forced to use my phone number as an identity document, because sometimes that’s the only way to do business with a site online,” Nixon said. “But from that site’s side, when they see a password reset come in via that phone number, they have no way to know if that’s me. And there’s nothing anyone can do to stop it except to stop using phone numbers as identity documents.”
Beyond SIM-swapping attacks, there are a number of ways that phone numbers can get transferred to new owners, Nixon said. The biggest reason is lack of payment for past phone bills. But maybe someone goes through a nasty divorce or separation, and can no longer access their phone or phone accounts. The account is sent to collections and closed, and the phone number gets released back into the general pool for reassignment after a period of time.
Many major providers still let people reset their passwords with just a text message. Last week I went to regain access to a Yahoo account I hadn’t used in almost five years. Yahoo’s forgot password feature let me enter a phone number, and after entering a code sent to my phone I was able to read my email.
So, if that Yahoo account is tied to a mobile number that you can receive text messages at, then you can assume control over the account. And every other account associated with that Yahoo account. Even if that phone number no longer belongs to the person who originally established the email account.
This is exactly what happened recently to a reader who shared this account:
A while ago I bought a new phone number. I went on Yahoo! mail and typed in the phone number in the login. It asked me if I wanted to receive an SMS to gain access. I said yes, and it sent me a verification key or access code via SMS. I typed the code I received. I was surprised that I didn’t access my own email, but the email I accessed was actually the email of the previous owner of my new number.
Yahoo! didn’t even ask me to type the email address, or the first and last name. It simply sent me the SMS, I typed the code I received, and without asking me to type an email or first and last name, it gave me access to the email of my number’s PREVIOUS OWNER. Didn’t ask for credentials or email address. This seriously needs to be revised. At minimum Yahoo! should ask me to type the email address or the first and last name before sending me an SMS which contains an access code.
Brian Krebs (BK): You have your own experiences like this. Or sort of. You tell.
Allison Nixon (AN): Any threat intelligence company will have some kind of business function that requires purchasing burner phones fairly frequently, which involves getting new phone numbers. When you get new numbers, they are recycled from previous owners because there probably aren’t any new ones anymore. I get a lot of various text messages for password resets. One I kept getting was texts from this guy’s bank. Every time he got a deposit, I would get a text saying how much was deposited and some basic information about the account.
I approached the bank because I was concerned that maybe this random person would be endangered by the security research we were going to be doing with this new number. I asked them to take him off the number, but they said there wasn’t anything they could do about it.
One time I accidentally hijacked a random person’s account. I was trying to get my own account back at an online service provider, and I put a burner phone number into the site, went through the SMS password reset process, got the link and it said ‘Welcome Back’ to some username I didn’t know. Then I clicked okay and was suddenly reading the private messages of the account.
I realized I’d hijacked the account of the previous owner of the phone. It was unintentional, but also very clear that there was no technical reason I couldn’t hijack even more accounts associated with this number. This is a problem affecting a ton of service providers. This could have happened at many, many other web sites.
BK: We weren’t always so tied to our phone numbers, right? What happened?
AN: The whole concept of a phone number goes back over a hundred years. The operator would punch in a number you know was associated with your friend and you could call that person and talk to them. Back then, a phone wasn’t tied any one person’s identity, and possession of that phone number never proved that person’s identity.
But these days, phone number are tied to peoples’ identities, even though we’re recycling them and this recycling is a fundamental part of how the phone system works. Despite the fact that phone number recycling has always existed, we still have all these Internet companies who’ve decided they’re going to accept the phone number as an identity document and that’s terrible.
BK: How does the phone number compare to more traditional, physical identity documents?
AN: Take the traditional concept of identity documents — where you have to physically show up and present ID at some type of business or office, and then from there they would look up your account and you can conduct a transaction. Online, it’s totally different and you can’t physically show your ID and can’t show your face.
In the Internet ecosystem, there are different companies and services that sell things online who have settled on various factors that are considered a good enough proxy for an identity document. You supply a username, password, and sometimes you provide your email address or phone number. Often times when you set up your account you have some kind of agreed-upon way of proofing that over time. Based on that pre-established protocol, the user can log in and do transactions.
It’s not a good system and the way the whole thing works just enables fraud. When you’re bottlenecked into physically showing up in a place, there’s only so much fraud you can do. A lot of attacks against phone companies are not attacking the inherent value of a phone number, but its use as an identity document.
BK: You said phone number recycling is a fundamental part of how the phone system works. Talk more about that, how common that is.
AN: You could be divorced, or thrown into sudden poverty after losing a job. But that number can be given away, and if it goes to someone else you don’t get it back. There all kinds of life situations where a phone number is not a good identifier.
Maybe part of the reason the whole phone number recycling issue doesn’t get much attention is people who can’t pay their bills probably don’t have a lot of money to steal anyways, but it’s pretty terrible that this situation can be abused to kick people when they’re down. I don’t think a lot of money can be stolen in this way, but I do think the fact that this happens really can undermine the entire system.
BK: It seems to me that it would be a good thing if more online merchants made it easier to log in to their sites without using passwords, but instead with an app that just asks hey was that you just now trying to log in? Yes? Okay. Boom, you’re logged in. Seems like this kind of “push” login can leverage the user’s smart phone while not relying on the number — or passwords, for that matter.
If phone numbers are bad, what should we look to as more reliable and resilient identifiers?
AN: That’s something I’ve been thinking a lot about lately. It seems like all of the other options are either bad or really controversial. On the one hand, I want my bank to know who I am, and I want to expose my email and phone number to them so they can verify it’s me and know how to get in touch with me if needed. But if I’m setting up an email account, I don’t want to have to give them all of my information. I’m not attached to any one alternative idea, I just don’t like what we’re doing now.
For more on what you can do to reduce your dependence on mobile phone numbers, check out the “What Can You Do?” section of Hanging Up on Mobile in the Name of Security.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source
Author: BrianKrebs Why Phone Numbers Stink As Identity Proof Original Post from Krebs on Security Author: BrianKrebs Phone numbers stink for security and authentication. They stink because most of us have so much invested in these digits that they’ve become de facto identities.
0 notes
Text
5 Tips For Choosing A Fence Company
How To Pick The Best Fence Company
By asking these and any other concerns you may have during your consultation, you can find the very best Austin fence installers and specialists, like us at Barrier Fence. We invite you to call us at (512) 354-4409 to schedule a consultation visit today.
No. If you have you have issues about the location of the home line or your fence, we recommend that you call a regional survey company to locate and plainly mark the pins to develop the home lines. Lee Fence and Outdoor will install the fence per your guidelines. Lee Fence and Outdoor accepts no liability for study disagreements in between homeowner.
9 Tips To Help Homeowners Choose The Right Fence Company
Lee Fence and Outdoor will get rid of and deal with your existing fence for an extra fee. Please be encouraged that if there are any parts of your existing fence that you wish to keep, let the installation crew understand. Lee Fence and Outdoor will not get rid of anything unrelated to the fence project.
We ask that somebody would be on-site when our crews arrive to go over the fence design. Deviations from the original fence agreement need to be authorized by your Lee Fence and Outside salesperson.
This can change the original fence design. Please keep in mind that the energy locator DOES NOT locate wells, septic tanks or underground gas/propane tanks. No. Considering that these underground electrical fence are typically situated close to the home line, you will need to call your underground fence specialist and have them mark the line prior to your brand-new fence setup.
How To Find A Good Fence Company
No. It is the homeowner's obligation to locate these lines and alert Lee Fence and Outdoor to the area of said lines. Usually all corner, gate and terminal posts will be dug up and reset in the exact very same area. It is basic practice and within AFA market guidelines to cut line posts listed below the grade and re-space the brand-new posts.
Normally, we use a little piece of devices called a mini-track to excavate the post holes. This varies at different times of the year, but typically during the spring/summer months, we can have a numerous week backlog.
Your Lee Fence and Outside salesman would be able to offer you with an approximate preparation at the time of the site visit. It varies on the size of your job. Usually, most domestic fence setups will take 1 to 2 days to complete. Larger fence installations can take 3 to 5 days.
How To Choose The Best Fence Company
Lee Fence and Outdoor teams are professionals in fence installation, our crews have actually limited understanding in correct trimming and pruning practices. Excessive trimming carried out by Lee and Fence Outdoor will undergo an added fee. We would value you tidying up your shrubs as we do not desire to damage your manicured lawn.
Related Searches Include:
Datson Fence
New Fence
Great Job
Fence Installation
Folsom Fence Company
Commercial Fences
Aluminum Fences
Fence Contractor
Commercial Fencing
Installation Crew
Chain Link
Free Quote
Wooden Fence
Kirkwood Fence
American Fence Company
Free Estimate
Commercial Property
Customer Satisfaction
Final Product
Reliable Fence Services
See Portfolio
Pearl City
Fence Services
Fencing Needs
Residential Fencing
Residential Fences
Wood Fences
Iowa City
Frederick Fence Company
Fence Products
It may be helpful to inform your neighbors so that no issues arise during the installation procedure with concerns to home lines. If you are having an old fence changed that is located on the residential or commercial property line, it is suggested that you notify your neighbor. Your neighbor may require to make plans worrying their pets and might also desire to protect their backyard or get rid of items from their side of the fence.

Usually your fence can be set up right up to, however not on the home line per municipality guidelines. Some towns do suggest that you keep your fence off the home line 1' to 3' so that you are able to maintain your fence on both sides.
10 Tips To Find (& Hire) The Best Fence Company
Frequently Asked Questions - FAQ
How much does it cost to put up a fence?
The typical expense of setting up a fence is in between $13 and $50 per direct foot. The average total cost of setting up a fence is approximately $988,but costs can reach $ 7,000-- or more. The length of the fence,materials utilized and add-ons such as gates can affect how much you end up spending for a fence setup.
What is the cheapest fence to install?
The cheapest fence you can install is a wire fencing at $2 per foot on average,while a 6-foot high wood personal privacy fence costs $13 to $25 per linear foot,and vinyl fencing for $15 to $30 per foot.
How much does a 300 ft fence cost?
Yard Fence Costs Per Foot Linear Foot Cheaper (Wire or Electric) Moderate (Wood) 8 $10 - $50 $100 - $200 100 $100 - $600 $1,000 - $2,000 150 $150 - $1,000 $1,500 - $3,000 300 $300 - $1,800 $3,000 - $6,000 1 more row
How much does Home Depot charge for fence installation?
Fence Installation Costs According to Home Depot,it can cost anywhere from $1,000 to $10,000 to install a fence,but a lot of house owners can anticipate to invest from $1,600 to $4,000. You can more properly calculate what your task may cost by determining the number of linear feet your fence will be.
How much does an 8 ft fence cost?
8 Foot Wood Fence Cost The average expense to construct an 8-foot wood fence is between $21 and $30 per direct foot utilizing pressure-treated pine with dog-ear panels.
What is the best time of year to install a fence?
If you think about summer season and spring the peak season,then winter season is the ideal time to get the service and attention you desire from your fence professional. Make the most of the off season by doing your research throughout the warmer months and preparing for installation in the winter.
Is it cheaper to build a fence yourself?
One of the advantages of setting up a fence by yourself is that you don't need to pay a company for the labor expenses. This typically ends up being less expensive in the end,and one of the significant reasons the majority of people consider a DIY in the first place.
Is it cheaper to build a fence horizontal or vertical?
Horizontal fences tend to be more expensive than vertical fences due to the fact that they require a higher grade of lumber for the fence boards to reduce the possibility of sagging. However,like any horizontally-oriented board,they might sag in time.
What is the easiest fence to put up?
Vinyl fencing installation is so much simpler the no-dig way. This means you can invest less time on your home projects and more time with your household,good friends,or whatever else you want to do.
An easement grants other individuals or companies rights to specific types of access on your residential or commercial property. Easements generally require that you keep any type of construction, including fence, off your home line 5' to 10' feet.
An easement is typically shown on your residential or commercial property plot strategy. Generally your town will just enable a 3' or 4' high fence in front yards.
youtube
This range varies per town. The majority of municipalities will allow approximately a 6' high fence in the side and rear lawn. As soon as you pass by the front corner of your home towards the street, you are thought about in your front lawn. Permitted fence heights in the front backyard differ per municipality.
Finding The Best Fence Company
In addition you are also needed to stay back from the street a certain distance. This also varies per town. It is normally between 5' to 35' from the edge or center of the street. The swimming pool code states that your fence must be at least 4' high. There are particular criteria that require to be met for the 4' high fence to meet this code.

The Lee Fence and Outside salesman is extremely knowledgeable with your swimming pool code requirements and can discuss your various options. It is your responsibility to read your deed constraints relating to your fence - 5 Tips On Finding A Good [@keyword]. HOA deeds and regional structure codes can restrict easements, fence heights, color preferences and even material types.
We furnish and set up fencing and associated perimeter security products such as gates, railings, guardrails and gain access to control systems - Advice How To Choose The Best [@keyword]. We likewise provide and set up decks.
How To Choose The Best Fence Company
PVC/vinyl fence or aluminum fence are very resilient and require less upkeep. PVC/vinyl fences are long lasting, long lasting, easy to tidy and ecologically friendly.
Chain link is long lasting, economical and easy to set up. Presently we stock white, tan, adobe and grey. Colors can be mixed to create a two-tone or picture frame effect. All PVC/vinyl bottom fence rails and all gate posts are strengthened with an internal aluminum channel for included support. We are a custom-made PVC/Vinyl fence maker, which give us the ability to customize fence height and picket spacing.
There is no setup guarantee for wood fences. Material guarantees differ by material type. PVC/vinyl and aluminum fences both have Restricted Life Time Service warranty for any material flaws. Chain link and wood fences do not have a product service warranty. Disasters are not covered under any warranty. You be accountable for removing your valuables from the fence/building website.
Finding The Best Fence Company
0 notes