#i have a weakness for the 50s illustrations.. if you ignore the. Everything Else
Text

got beseiged by demons and edited this mac conner illustration to be jordeclan
#i have a weakness for the 50s illustrations.. if you ignore the. Everything Else#jordeclan#listen i had to do it as fast as i could. you get it#trcposting#td3#I FORGOT TO MAKE HIS TIE PURPLE. GOD DAMMIT. IT SHOULD MATCH HER NAILS#i also discolored his knuckles and kept the greying temples and made the nose bigger and changed her expression a smidge#i also like. made his wrists wider? declan does not have dainty baby wrists sorry. he goes to WAR (9-5 cubicle job)#i also gave his eyelashes a little pizzaz. Obviously. yes i made his lips slightly more luscious WHATEVER
578 notes
·
View notes
Text
2020 in review
I was tagged by @apeironaxiomaton to look back at 2020 and pretty much to try and not hate it so much! Thank you!!
Also I’m stealing the idea of putting everything under a cut, which I have never done in my life (and probably should start doing) bc it makes things neat as heck. Almost none of these are in a particular order.
Top 5 movies I saw this year:
Volevo Nascondermi by Giorgio Diritti - this movie is REALLY good AND I have good memories tied to the protagonist for Reasons I’m gonna cry bye (a shame that I’ve only watched this other excellent movie starring Elio Germano tonight bc it should be on this list)
Emma (2020)
The King’s Speech
Spirited Away or Porco Rosso - I had watched the first before and never the second so I think the fairer choice would be Porco Rosso but I’m not entirely convinced of it
The Wolf of Wall Street - look, I simply have a weak spot for stories that are so absurd they can be nothing but real (see “the other Elio Germano movie”)
Top 5 TV shows I watched this year:
Murdoch Mysteries - it will stay engraved in the first place of EVERY chart in saecula saeculorum and NO nothing can take its place I don’t care
Peaky Blinders
Alias Grace - which I was sure was a movie? I was so shocked to discover it isn’t like was it really six hours long what the
The Queen’s Gambit
Suburra: Blood on Rome - “The series was developed by Daniele Cesarano and Barbara Petronio for Netflix, making it its first Italian-language original television series.” I’ll be honest, some bits were a little bit hmm-inducing. Not the best tv series I’ve ever seen, but it managed to be fun and easy to watch. Suspenseful even!
Top 5 Songs:
So there’s a reason why Spotify said I’m an octogenarian this year and for as much as I complain about it... it’s right... Spotify’s right. And it will only get worse, I’m afraid. All the songs are from the same playlist which was my most listened to (and is the most interesting to share imo). I swear I have listened to other, newer things as well.
Shake That Thing by The Abe Lyman’s California Orchestra
Night Hawk Blues by The Coon-Sander’s Nighthawk Original Orchestra
Where the Sweet Forget-Me-Nots Remember by Merle Johnston and His Ceco Couriers (I’ve loved these flowers since I was a kid it was so nice to find a song with them in the title!!)
Dew Dew Dewey Day by Nat Shilkret
The Panic is On by Mezz Mezzrow And His Swing Band
Top 5 Books I Read This Year:
so this is embarrassing,,,,,,,,,,,,,,,,,,,,,,I “bought” an insane amount of books and read a grand total of...like...t w o. It was actually like four and some short stories (which I hated and are therefore banished from the good boy list) so I’m gonna list my silly little titles and make my silly little comments about them all. From “””””best””””” to “worst” we have:
The Adventures of a Modest Man by Robert W. Chambers - I literally cannot shut up about this book and, yes, it is the one tied to this illustration, about which I equally cannot shut up about. It’s so horrible that it makes a 360 and comes back as good, but not before hitting you with a cardboard tube for a laugh and subsequently stabbing you in the kidneys just because it can. I think we can confidently state that we are in the “I didn’t say it was good, I said I liked it” realm. I have so many questions about this book. Why was it written? Was it taking itself seriously? Was it commissioned by someone? Why is it so gay but only if you know that the author is a man? Maybe it’s a parody? Was it an experiment made by the author to test his own skill? I know jack about literature, unfortunately, so grain of salt here but it made me feel strong feels. Not that I could identify any of them if you asked, but they’re definitely there.
Old Possum’s Book of Practical Cats by T.S. Eliot - I’m counting this in bc what is a book if not a patchwork of silly little paragraphs anyway so yes, we have a collection of poems. Not only do I know jack about literature; as a matter of fact, I know jack about poetry as well! All I’m gonna say is: I like cute things, I like cats, the poems were cute AND about cats. I really liked it! I often find myself going back and reading again specific parts just for the delight it is to read them out loud! I also may or may not have named the cats you can adopt in Stardew Valley after some of Eliot’s cats. The movie Cats (2019) did one good thing: making me read this.
How You Can Keep Fit by Rudolph Valentino - Yes, that is correct. A book on fitness written (in English!) by silent movie superstar Rodolfo Valentino. It is less than 100 pages on real, actual exercises that the reader can replicate in the comfort of their own house with little to no equipment. With a sprinkle of old timey manly manner of speaking, a few anecdotes from the author’s childhood in ye merry Italian countryside, a dusting of precious advice against ice-cream, and a dash of genuine intrigue for these newly discovered “vitamins” everyone is talking about. Overall a fascinating read that I treasure dearly! Valentino also wrote a book of poems, which I am absolutely thrilled to read this year.
For Whom the Bell Tolls by Ernest Hemingway - Hmm.. I have mixed feelings about this one. Whenever the original language of a book is English, I instinctively want to read it in that language. Because I can! And because that way I get to read exactly what the author wrote. If it was another language, I’d get a translation, make peace with the fact that selling my soul to acquire perfect knowledge of all things is morally questionable, and call it a day. Problem: I’m a sucker for old books. And old books I did find indeed. There were three books by Hemingway for sale, very pretty, and for an almost symbolic price too so I bought them. They are Italian translations from the late 50s and my plan was to go through one in Italian, one in English, and after that, decide in which language to read the last one. I believe it was a mistake for me to start with Italian in Hemingway’s case. He’s known for having a very, VERY peculiar style that is integral to how the novels are perceived and I feel like I've robbed myself of literal peace of mind. For as much as I found the story interesting, I could not ignore the voice in the back of my head that kept wondering “was it necessary to render it like this?”. It did make me feel feels and think thoughts, but honestly? It was partially for the wrong reasons imo. It’s one of those books you should read at least once in your life, I guess, so I’m definitely glad I did it! Surprisingly, it captured me more than I expected and trapped me into its little world. I could clearly imagine the scenes in my head, which hadn’t happened in years! I’m really excited to move on to the next two books and finally be able to say if I appreciate his style or not.
Top 5 positive things that happened to me in 2020:
Visited Rome and took a stroll around on my own (sort of) for the first time in my life. I had never seen it at night :) Right after that I celebrated my birthday and got some cute gifts, including sweets that were sent all the way from Australia!!
Managed to buy my mom a gift, which is possibly the only real Accomplishment of 2020.
Took a bizarre trip this summer (I know, guilty) and fell in love with Slovenia
Discovering I like textile arts kinda gave me hope for myself and for the future. I say kinda for I dare not think concretely of anything too positive lest it should be prematurely taken from me. I shan’t elaborate. It is what it is.
Therapy!!!
The last few months of 2020 really hit me hard whereas in the beginning nothing was too bad so it was nice to see the list growing and growing! So many tiny good things happened and it’s worth to cling onto them. I’m tagging @sonicysuchillydog, @nurmilintunen, @alfonzone and anyone else who’d like to participate!! “Tell them I sent you” lol. Guys.............if you don’t feel like going thru your 2020 feel free to ignore bc......I get it............................
#mutuals#apeironaxiomaton#year review#yeah that book section is uhhhhhhhhhhhh#oof#i feel like this year the situation is finally going to change and i very much look forward to that#ive been trying to get myself to read more for ages and i feel that now whatever was stopping me has been partially removed/has gone away#there's LOTS of anya taylor-joy in this list hm#in case anyone cares yes i loved her in emma yes i hated her (and probably will hate in the upcoming season) in peaky blinders#and yes i was scared of her in the queens gambit#shes a good actress! i like her :)#there's also lots of old age and the smell of my grandma's house#not sure how to feel abt THAT#also incredibly lots of I T A L Y#my country and i are in an abusive relationship in which it keeps beating me but i keep going back for love#its complicated#i didn't think i had SO MUCH to say#im sorry guys as usual my posts get long and messy#edit: actually in the tv series thing there should also be the man in the high castle#i had (illegally lol) watched the first two seasons years ago and stopped bc i couldnt find the newer episodes#this year i watched it all over again and i have to say i enjoyed it much more than the first time!#i also already have the book so 👀👀👀 looking forward to that too 👀
4 notes
·
View notes
Text
Himiko is a Hero: Chapter 3
Meeting Makoto
<<PREV NEXT>>
The cop and highschool girl pair left U.A. once the girl was able to walk again.
"Sorry again for the inconvenience Toga. I will be sure to tell the higher ups to loosen that thing's grip on you." Tsukauchi said, repeating prior promises in hopes to please the girl.
The girl, however, was on a completely different wavelength due to the previous encounters of the afternoon. Izuku. Her crush totally stuck up for her. And she got his phone number. And she got super close to stabbing him. It was the perfect day for your average blood-obsessed high school girl.
"Toga. Did you... make sure the phone number you input is correct? I'm sure Midoriya wouldn't mind a text." Tsukauchi said, resigning himself to having to connect with Toga on her level and interests.
"I gotta make it special. My first text to Izuku has to be super special." Toga said in response.
"I see..."
"Mr. Cop. Do you have a love story too? Did you make your first time special?" Toga inquired.
"F-first time?" Tsukauchi was caught off-guard by her questions and saw it as a sudden and perverse interrogation.
"Yeah yeah! Your first time texting someone you like! Hehehehe. What did you think I meant~?"
"I thought you meant... That doesn't matter! This isn't an interrogation!"
"Hehehe. You are weak to questions, huh? I can totally smell it on you."
Tsukauchi didn't give any further responses to Toga as they continued to where he lived. It was an apartment, from what Toga could tell from the outside. She followed Tsukauchi up the stairs to what was considered his space. The cop removed his key from his pocket and placed it into the lock on the door. He paused and braced himself when grabbing the door knob.
"Scared? I'm scared too when I'm meeting new people." Toga said, noting his pause.
"I didn't know you could feel scared." Tsukauchi responded in a joking manner while opening the door.
As soon as the door opened, exactly what Tsukauchi feared would happen, did. As if waiting for their arrival, a tall green eyed girl went directly from the couch in the living room to Toga the moment they stepped inside.
"Himiko Toga, correct? I'm Makoto Tsukauchi. Feel free to call me Makoto to avoid confusion. Big Brother said your Quirk is interesting and the higher ups want to keep an eye on you. Does that mean it can cause alot of harm?" the woman said in a verbal onslaught.
Toga's mind was rattled by the surprise attack allowing her to only say "No?" in an unsure manner while her hands were vigorously shook.
"Sis. Give it a break. At least let Toga relax from school before you interrogate her." said Naomasa Tsukauchi, stepping in to protect Toga.
"Just getting some info you didn't give me, Big Brother." she said beaming a smile at them both. "How about dinner then you two? Toga's first dinner at the Tsukauchi household! The cops probably only fed you instant meals, but a growing girl needs way more than that!"
Toga was still too baffled by the blinding ray of glee that Naomasa called a sister to fully take in the essay length of words that was emitted at a time. Toga found herself at a dinner table before she knew it with homecooked food placed infront of her and Naomasa at the dinner table.
"Dig in! It's a Tsukauchi Family Speciality made of-"
Before Makoto could even go into what the meal was, Toga was already digging in. Digging would be an understatement for how she ate. The way she consumed the food was more akin to "ravenous burrowing". The twin bunned girl finished in half the time it took Naomasa.
"I'll clean up!" Toga said, jumping up out of her seat.
"Let me handle that Toga. I'm not even half way done yet. Makoto will show you around the place.”
Toga’s smile turned into a frown for a moment before Makoto came over to her.
“I cleaned up the storage room and added a bed so your living space is complete!” Makoto said.
“Please don’t make it sound like we are just putting her in storage.” Naomasa replied.
“Is there a bath?” Toga asked abruptly.
“Right this way Toga.” Makoto responded, leading Toga from the dinner table to the bathroom. “There should be everything you need. Soap, towels-”
Toga didn’t wait for Makoto to finish her explanation. The sound of the bathroom door shutting got Makoto to realize this. Enjoying the time she got to herself, Toga went into stretching and undressing.
“Alone time. Now I can finally-”
Toga’s thoughts were interrupted by the door to the bathroom being opened and Makoto appearing, proudly, in a bath towel.
“I am here! To wash your back of course!” bellowed out the inquisitive girl in her best All Might impression.
The reference was wasted on Toga as she ran to shut the door.
“Nope.” Toga plainly stated, closing the door on Makoto.
“Come on Toga~. Let’s have a little girl time together.” Makoto said, holding the door open just a smidge, trying to squeeze into the bathroom.
“Nope nope nope! Alone time!” Toga responded, reaching for the lock of the door. Just had to lock it the second the door shut fully.
“It will just be a few questions about your Quirk, U.A. and why you want to be a hero. Nothing too personal.” Makoto said in an attempt to compromise with the blonde that was baring fangs at her through the small crack she was struggling to maintain.
“I’M BUSY THINKING ABOUT IZUKU! GO AWAY!” Toga shouted.
“Izuku?”
The moment that Makoto took to contemplate what Toga meant was the moment in which Toga got the door fully shut and instantly locked the door. Makoto tried knocking but got no response. After a full minute of knocking, she got the memo and left Toga alone for the time being, instead focusing on handling Toga’s belongings and clothes. An hour and a half passed before Toga exited with a calmly elated expression on her face. Makoto was instantly there to try and talk to her, but Toga fully ignored the girl’s questions and just walked away while still in just a towel and her hair down. Naomasa, through quickly closed eyes, was the first one whose words made it to the glazed over mind of Toga.
“Toga! Your room is down the hall past the bathroom! P-put some clothes on!”
Turning around from going the wrong way, she walked back down the hall as if she was a zombie in a daze.
“Makoto. Did you do something to her?” Naomasa asked his little sister after Toga found her way into the once-storage-now-bed room.
“Just tried asking her a few questions earlier. Whats up Big Bro?” she replied.
“Don’t bother her like some kind of paparazzi. The more questions thrown at her, the less she answers. Barely even got out of her the fact that her Quirk involves blood.”
“Hmmm…Thanks for the advice. I’ll try again later then. You know I never give up!”
“Maybe you should sometimes. It’s safer...” Naomasa dejectedly said while returning to cleaning the dishes.
Inside Toga’s new room, boxes of random stuff took up about 50% of the room. The boxes had been organized to the sides of the room, transforming the square room into a T shaped room from the door in terms of usable space. Straight ahead was a window and to the left of that was a small desk for school work. To the right was a twin sized bed with enough room to get in from each side. Lots of stuff was laid out on her bed with the intention to catch Toga’s attention, which it did. She went over to investigate. Firstly was her backpack beside the bed which she got her phone out of. Next the bed. On top of one pile was her underwear, washed and cleaned for her to put on. And beneath was a baby blue frilled dress with small red cherries printed intermittently on it. Toga put on the clothes in front of her and checked her phone to see how it looked.
“WAY CUTE!” she instantly thought while looking at her own smile and dress on her phone screen.
After taking a picture of herself to remember this cute gift, she checked the rest of her bed. There was one other stack of items, but this time there was a sticky note on top.
“Write your thoughts in this. The higher ups want to make sure your life at U.A. is going well. -Naomasa Tsukauchi.” was what it read.
The sticky note was attached to a single color crimson red pocket notebook. After ripping off the sticky note, Toga stared at it trying to decide what to do with it. Then it came to her. Write all about Izuku! Taking a pencil out of her backpack, she sat at the small desk opposite her bed and began scribbling away.
As night continued on, 10:00 PM came swiftly. Deciding to check in on her, Naomasa went and knocked on Toga’s door. Toga’s response was swift and preceded by an “ow” and the tumbling of a few boxes.
“I’m busy.” she said, opening the door just enough to peak her head out and see Naomasa in casual blue nightwear.
“Be sure to go to sleep early. You don’t want to be late for-”
“Ok. I’m busy.” she shut the door in his face after repeating herself.
“I’M NOT KIDDING! WRITE IN THE JOURNAL AND GO TO SLEEP EARLY!” he shouted after her.
The only response he got was another “ow” and grumbling about “the same box”.
An hour later, and after coaxing from her big brother, Makoto went to check on Toga. Knowing how to avoid repeating the mistakes of Naomasa, she opened the door to Toga’s room without knocking. She waited to see if there would be a response. After 10 seconds passed and none was given, she invited herself in. Right off the bat, she noticed boxes to her left knocked over. Makoto assigned it to Toga being clumsy and fixed them. While fixing them, she found the owner of the room with their face against the desk.
“Aw Toga. You have to sleep in your bed you know. Or else I get to do this...”
Letting her natural curiosity take over, Makoto began searching for what Toga was working on. Upon close inspection Makoto discerned that it was the red notebook.
“Don’t want you drolling on it now.”
Sliding the notebook out from under the drooling Toga’s mouth, Makoto began flipping through the pages herself. It was the least the notebook could do for it’s savior.
“3 whole pages… 6 including illustrations. All about one Izuku Midoriya… Hmmm...”
Deciding their wasn’t much more to glean from just her obsession with one boy, Makoto placed the notebook back on the desk, but in a place safe from Toga’s drool. Looking at Toga again, another issue became apparent.
“You can’t just not brush your hair before bed and expect your love interest to swoon!”
Taking matters into her own hands for Toga’s sake, Makoto went to her own room and returned with a brush to use on Toga’s naturally messy hair. It took a long time but eventually the unkempt golden lawn on Toga’s head relented to Makoto’s brush skills. She left Toga to sleep at the desk after the fight with her hair. No sense in trying to move her and risk waking her up.
The night at the Tsukauchi abode went on with the 3 people inside working on their own tasks before bedtime. By 11:30 PM, Naomasa was already asleep. When 1:00 AM came around, Makoto decided it was time to hit the hay and let her work be handled after sleep. Right after she got a drink of water. She left her room to go to the kitchen but stopped halfway through. Audible when she reached the living room was the sound of running water. Makoto tensed up.
“A burglar? At this time of night everyone should be asleep here, so it must be. But why water…?”
Makoto’s mind was flooded with questions as her movements slowed and she began sneaking through her own house to get to the kitchen. She maneuvered to the couch and hid behind it. There was a direct view to the sink in the kitchen where she saw…
“Toga. What are you doing up so late?” she blurted out while standing up.
In response to the question in pure darkness, metal clanked against metal and the blonde head of the girl at the sink slowly turned around. Her eyes, as if made exactly for this situation, pierced the darkness and glared directly at Makoto. Makoto’s whole body froze as Toga’s elliptical pupils glared at her. Then Toga spoke.
“Cleaning... I’m done now.”
Toga’s lackadaisical tone betrayed the mood of the situation. She shut off the water and turned fully towards Makoto before slowly taking steps towards her. All Makoto could see was two bright circles with black slits coming directly towards her. Or rather, past her. Toga attempted to walk past Makoto, but the latter placed a hand on the shoulder of the former.
“I just have to use my quirk and then...”
Quirk: Polygraph. The condition for activation is making physical contact! And her ability lets her “judge the authenticity” of her target’s words!
“W-why were you cleaning?” Makoto stuttered slightly, still affected by the atmosphere.
Toga yawned before giving her response.
“I wanted to clean something. So I did...” she mumbled, with her eye-lids lowering to half closed.
“Oh. Sorry, Toga. Get some good rest.” Makoto responded, letting of Toga’s shoulder and watching the girl stumble through the darkness back to her room.
“She told the truth. But why would she...” Makoto thought as she went over to the sink to check what Toga was washing. “Only knives? We didn’t use all these for dinner...”
<<PREV NEXT>>
#boku no hero academia#my hero academia#himiko toga#toga himiko#hero!toga#chapter 3#naomasa tsukauchi#makoto tsukauchi
2 notes
·
View notes
Text
The best way to Carry out a Detailed SERP Evaluation to Discover Low-Issue Key phrases
Why Low-Issue Key phrases Are Value Your Time
Backlinks are essentially the most influential rating issue in Google’s non-localized algorithm, based on business consultants. I will not deny that there are quite a lot of different elements that affect rankings, but it surely’s additionally vital that everybody within the search engine marketing business perceive and admire the affect backlinks have on rankings.
Particularly new companies, with freshly created web sites, want to know this idea: Backlinks are a prerequisite to rating. That does not imply it is advisable to be obsessive about constructing hyperlinks, and you need to by no means automate your link-building in any method.
Quite, as a substitute of resorting to shady hyperlink constructing techniques, it is advisable to determine low-difficulty key phrase alternatives is a solution to discover the search end result pages you may realistically compete for along with your present backlink profile.
If you happen to’re struggling to drive visitors by means of engines like google as a result of your high-quality content material is ending up on the third or fourth web page of Google search outcomes, this information will present you how you can determine the key phrases you can be rating for proper now with out constructing plenty of backlinks.
Begin by Gathering a Record of Potential Key phrases
You are going to want a reasonably large checklist of key phrases for this tactic—no less than 100 key phrases. Utilizing the Google Key phrase Planner, plug within the matters you need to discover.
I often begin broad after which slender my search down utilizing associated matters that pop up throughout this course of. For instance, if I’ve a shopper within the industrial coatings business, I am going to begin by getting into the phrase “industrial coatings” into the planner and seeing what it spits out.
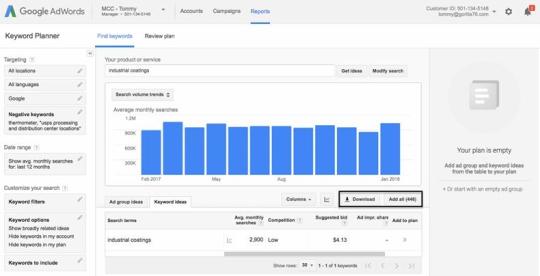
From there you may export the key phrase checklist into Excel and begin trimming the checklist down. I often begin by filtering out all the key phrases with over 1,000 searches a month: We’re in search of the low-hanging fruit, and usually key phrases searched over 1000 instances a month can be too aggressive to rank for with out extra link-building and content material promotion.
The key phrases with decrease search quantity (between 50 and 200 month-to-month searches) are alternatives ripe for the choosing. They’re usually phrases your rivals are fully ignoring.
As you are going by means of this checklist, search for subtopics that will be value creating content material round. Subtopics in our instance, the commercial coatings business, would possibly embrace issues like fireproof coatings, fluoropolymer coatings, and zinc primers. As soon as you have recognized your subtopics, plug them into Key phrase Planner for an entire new checklist of concepts. Subtopic lists often include key phrases with even decrease problem than your authentic checklist, as a result of the key phrases are extra particular.
To grasp why subtopics include nice alternatives, take a look at the distinction within the variety of webpages in Google’s index mentioning industrial coatings vs. these mentioning fluoropolymer coatings.

I would be competing towards 10 instances as many webpages if I have been to pursue “industrial coatings” over “fluoropolymer coatings.” In fact, that’s solely a surface-level, anecdotal instance, but it surely illustrates the significance of exploring area of interest key phrases inside your business.
Upon getting your checklist of no less than 100 key phrases, it is time to analyze them utilizing Time period Explorer and URL Profiler.
Combining Time period Explorer With URL Profiler
Let me preface this part by saying I’ve no affiliation with these instruments: They simply occur to be the instruments I exploit to research SERPs as a result of I get to select and select the info I would like. When you have a instrument that may collect the highest 10 outcomes of Google for key phrases at scale, you may substitute it for Time period Explorer. And when you’ve got a instrument that attributes search engine marketing metrics to URLs, it could possibly substitute URL Profiler. Although a instrument like Moz’s Key phrase Explorer will be helpful for locating low problem key phrases, it would not present the extent of element we’re attempting to realize.
Fireplace up Time period Explorer, copy-paste your key phrases into its Key phrase Analyzer, and choose your location (the USA is the default).
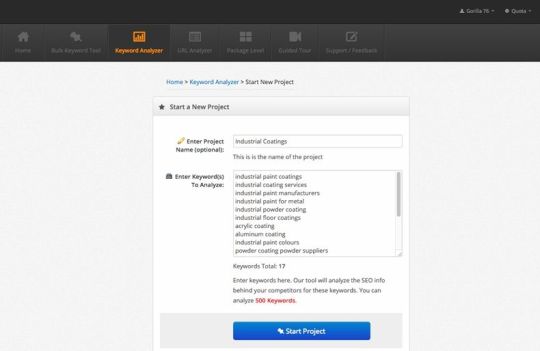
Begin the challenge and seize a cup of espresso… Time period Explorer is now pulling and ordering the URLs off the primary web page of Google for every key phrase, and it often takes a couple of minutes to course of. Upon getting your cup of joe, go into the challenge and obtain your CSV.
You will be greeted with a number of knowledge factors for every URL: Variety of key phrase occurrences, phrase rely, relevancy rating, Ahrefs area backlinks, problem rating, and many others. You would cease right here and use Time period Explorer’s troublesome rating, however I prefer to be thorough and incorporate Moz’s Area Authority and Majestic’s referring area metric into this knowledge set.
Trim down the info factors you do not care about, and fireplace up URL Profiler. This software program means that you can sync up Moz, Majestic, Ahrefs, SEMrush, and a dozen different search engine marketing instruments with the intention to “profile” every URL. As soon as you have synced up your link-metric software program, you may import the Time period Explorer CSV and merge your knowledge set with the brand new metrics you have chosen.

Combining Time period Explorer and URL Profiler permits customers to research Google’s outcomes pages utilizing the metrics they belief essentially the most! The great thing about this key phrase analysis methodology is that it means that you can select the metrics that matter to you.
As soon as you have merged your knowledge, you will get a good bigger spreadsheet that it is advisable to parse by means of, so I like to recommend trimming it down. Embrace metrics that analyze each on-page and off-page elements. Listed below are the metrics I usually use:
Place (in Google)
URL
Key phrase within the title?
URL comprises key phrase?
Do headings include key phrase?
Variety of key phrase occurrences
Moz Area Authority
Variety of Majestic exterior backlinks pointing to the area
Variety of Majestic referring domains pointing to the area
Variety of Majestic exterior backlinks pointing to the URL
Variety of Majestic referring domains pointing to the URL
Upon getting your most significant metrics, use conditional formatting to indicate GREEN when metrics point out low competitors (i.e., low authority, no specific key phrase concentrating on) and RED when metrics point out excessive competitors.
As soon as you have gone by means of every column and arrange your conditional formatting, you will be left with a colourful doc that appears one thing like this:

Conditional formatting means that you can shortly scan by means of your Excel sheet and discover alternatives—you are actually in search of the weak hyperlinks which might be rating in Google. Attempt to discover URLs which have decrease area authority than your web site, that do not have hyperlinks pointing to their rating URL, and that are not explicitly concentrating on the key phrase you are contemplating. These would be the URLs which might be inexperienced throughout the board.
One other method is to filter out all of the rivals which have larger area authority than your web site. As an instance my shopper has 70 referring domains and 300 backlinks to their web site. I can filter out all of the URLs with extra referring domains and backlinks, and concentrate on the rivals which might be rating with related or decrease area authority.
In spite of everything our onerous work, we’re left with a treasure trove of low-hanging fruit key phrase alternatives!
Assuming your web site is technically sound (quick pageload pace, good inner linking construction, no penalties, and many others.), you will often solely want one glorious piece of keyword-targeted content material to rank for these key phrases, no link-building required (though it by no means hurts).
Remaining Concerns, Observations, and Ideas
Take into consideration this methodology as figuring out the weak and irrelevant hyperlinks Google is rating and changing them along with your related, authoritative content material. In fact, it is advisable to be creating well-researched and helpful content material that Google needs to rank, however that is assumed on this course of. If you happen to’re attempting to rank for fluoropolymer coatings, however not answering a searcher’s query about that sort of coating or offering them with subsequent steps to buy or be taught extra, you are failing to reply the searcher’s question and can wrestle to rank.
Whereas this methodology of key phrase analysis works for non-localized (nationwide) outcomes, it would not apply to localized search outcomes. Google goes to prioritize location over every little thing else when attempting to reply a question like “industrial coating contractors close to me.” Native search engine marketing is an entire ‘nother beast, so double-check your alternative key phrase SERPs for native corporations and the native 3-pack.
One other factor to think about is whether or not a partial match area (or partial match firm identify) with low area authority is rating. Although the area identify itself may not be inflicting the corporate to rank, it is doubtless the corporate has sufficient keyword-rich anchor textual content linking again to its web site to present it an edge. An organization like “Frank’s Industrial Coatings” will get a bonus in nationwide natural outcomes as a result of its linked, branded mentions throughout the Net embrace the key phrase “industrial coatings” within the anchor textual content.
* * *
This key phrase analysis tactic has been extremely efficient within the industrial and manufacturing house as a result of quite a lot of industrial corporations are ignoring on-line advertising altogether. However I am curious how it might maintain up in additional aggressive verticals the place search engine marketing is a precedence.
For many who experiment with this tactic, please attain out to let me the way it labored for you or your shopper’s enterprise.
Supply hyperlink
source https://webart-studio.com/the-best-way-to-carry-out-a-detailed-serp-evaluation-to-discover-low-issue-key-phrases/
0 notes
Text
Seafarers Must Adapt to the Rapid Evolution of Piracy
In two recent articles, Sea Piracy in 2025: Piracy 2.0? and Countering Gulf of Guinea Piracy Towards 2025 I tried to map out the possible evolution of piracy within Gulf of Guinea until 2025. Then I analyzed the different possible actions to reduce this threat. This analysis cannot be complete without integrating the main actor, the seafarer. This third article therefore concerns the how seafarers must adapt to the rapid evolution of pirate activities.
It’s noticeable that this domain for seafarers is based on regulatory documentation that is low in volume and weak in practical guidance. The Ship Security Plan (SSP) is the basis for maritime security regulations. This document, established after the USS Cole, Limburg and September 11 attacks, was mainly focused on maritime terrorism. The content has been lightly modified since, integrating some requirements arising from the evolution of piracy.
The ISPS regulation does not go deeper on practical measures concerning vessel, crew members, equipment and procedures when looking at piracy. To cover the seafarers practical needs a group of associations published a document called Best Management Practices in early 2000. This document, dedicated to deter piracy and enhance maritime security in the Red sea, Gulf of Aden, Indian Ocean and Arabian sea has been reviewed several times since (Last review BMP 5 –June 2018). To respond to the specific Gulf of Guinea environment, one document, Guideline for Owners, Operators and Masters for Protection against Piracy in the Gulf of Guinea Region has been established by the same structure.
Finally, as the piracy epicenter as moved from East Africa to West Africa, one new document BMP West Africa has been issued beginning 2020 to provide threat mitigation guidance on counter-piracy/armed robbery at sea and to help companies and mariners to risk assess voyages while operating along the West African coast.
Despite the evolution of communications at sea, the captain is an isolated leader. His or her job requires quick decisions concerning a wide variety of situations. If the situation allows, he can try to establish a telephone connection but, the handset hung up, he becomes again, isolated. A piracy attack is a dynamic event testing a captain's competency and reactivity. This situation can be illustrated by the Captain Phillips movie scene where Tom Hanks calls the MSCHOA. As with everything else, a captain must be informed, trained, prepared.
This readiness must not only apply to seafarers, it should be also concern the vessel. “If you ignore both your enemy and yourself, you will only count your fights by your defeats.” This citation should be a guide for a captain or ship security officer (SSO) operating within the Gulf of Guinea. The pirates' boarding rate within Gulf of Guinea is very high. As said in my previous article, there are several reasons for this. Some are linked to the combination of operational capacities of pirates and the lack of military responses (PMSC / escort vessel) but it is obvious that somet of the reasons are linked to another conjunction: ignorance of West Africa pirates, to their profiles and their modes of action.
As such, it would be interesting to test the captains/SSOs to make them draw Gulf of Guinea pirates. To help their sketches, we can try to characterize them by some elements:
Use of fiber speed boat, eight to 10 meters long, usually sporting colored flags (mainly red or white), usually motorized by two outboard engines, 150/200 Hp, more than six men onboard (usually eight to 10), men armed with AK 47, speed boat fitted with an aluminum ladder eight to 10 meters long. Pirates can operate on one sole speed boat, sometimes in pairs.
It’s noteworthy that numerous specialized articles speaking about Gulf of Guinea piracy are illustrated by a very well-known picture showing a speed boat having a mounted Cal 50 machine gun and transporting……MEND militants. If the picture is beautiful, it’s not related to real Gulf of Guinea pirates. Sometimes this picture is replaced by the view of one skiff transporting Somalian sea pirates. This pictorial materialization may disturb the initial perception of what a Gulf of Guinea pirate is.
The fiber vessels don't offer a strong Radar Cross Section, navigational radars have limited capacities. The pirates' speed boat emerges on the radar screen at about three nautical miles when the sea state is under three and the speed is high. It’s highly recommended that one radar be set on short pulse/ short range, the AC SEA/AC RAIN setting in accordance. It’s possible that watchkeepers will detect the approach by the noise before sight or radar screen. The approach axes can be various but the CPA (Closest Point of Approach) is …0.
The time of the attack varies too and is evolving regularly. In 2018, almost two thirds of the piracy attacks was conducted by daylight. Currently, piracy attacks within Gulf of Guinea are mainly conducted at night time and mainly at the beginning or end of the night.
The location is, of course, one of the important facts to analyze. My previous article, Sea Piracy in 2025 analyzed the current trend of attack attempts very deep offshore …..or within non protected anchorage areas along the West African coast from Luanda till Abidjan.
This first enemy analysis realized, and to remind on the Sun Tzu citation, it may be even more important to know yourself. Turning back to the Gulf of Guinea piracy data, one element is alarming: it’s the number of vessels boarded without alarm/alert: No VHF.M distress call, no SSAS (Ship Security Alert System) alert, no vessel internal alert. The personnel on bridge duty discover the pirates when one is directly pointing a gun at them on the other side of the bridge glass.
For at least two cases in the last few months, the pirates have used….the pilot ladder left along the hull by night. These observation led to at least two main reflections: the seafarers had misjudged the threat and, because of this error, had not applied the adapted basic security measures.
Reviewing the current trends, appreciating more precisely the Gulf of Guinea pirates' modus operandi, it’s obvious that the area located between San Pedro and Luanda and taking a range of 200 nautical from the shore must be considered as High Risk Area for piracy. (Conakry Anchorage is a specific bubble which should be considered too.) This area is globally characterized on the specific chart established by the MDAT-GOG. Within this area, as said before, the pirates are currently acting on two modes:
Piracy attack deep/very deep offshore: Action is characterized by a direct attack against a vessel en route day or night. The detection of the threat is facilitated by the sparse maritime traffic, but the vessel is usually alone, not protected.
Maritime criminality within anchorage area: The pirates operate in discretion, by night against vessels anchored or on stand by. The detection of the threat is complicated by the numerous speed boats/canoes fishing in the area, but the vessel can benefit from security support from navy assets protecting the area.
The objective of these two pirates process is the same: kidnapping of crew members.
This being posed, and as the threat is focused on abduction, it is interesting to revisit the maritime operators possible internal self responses in 10 main actions:
• Secure the vessel as much as possible by a security escort vessel or an embarked military security team: The pirates are focusing on soft targets!
• Optimize your detection means for locating pirates as early as possible: One speed boat sailing 30 knots is along board six minutes after detection at three nautical miles!
• Be able to classify the threat as soon as possible, using the piracy criteria declined above: Personnel on duty on the bridge should be informed, trained and regularly refreshed about local pirates.
Raise the alarm about the attack by all means available (VHF.M 16 / SSAS/ GMDSS/ PHONE / HORN-SIREN/LIGHT)
• Optimize internal alert systems to ensure all crew members will be aware of the alert sent.
Conduct regular anti-piracy drills: piracy attack / alert / immediate communication / mustering / lock down control / anti-boarding measures / move to safe haven.
• As soon as you operate within a high risk area, lock your vessel. All external doors locked, all portholes secured. Try to slow down the pirates progression onboard the vessel after boarding by the use of specific items (wire rack or other) on external stairs.
• Use the navigation lights only, no deck light, all portholes blinded. By night level 4 or 5, when navigation lights are off, after change of course /speed, the vessel targeted disappears for pirates sailing onboard speed boat without radar, AIS or night vision goggles.
• Optimize the vessel's readiness by using simple and efficient systems. As the maritime industry is strongly impacted by the general economic situation, focus on low cost equipment rather than hoping for the use of means that are certainly effective but financially unaffordable. As an example, one general public autonomous sensor sending sound, light and possibly video, set up on the obliged path from deck to bridge, can efficiently alert the watchkeeping team in case of initial surveillance/detection failure.
• Consider the first internal door from navigation bridge to accommodations and lower decks as one essential element of your safe haven. Reinforce this door, reinforce the frame, complete the hardening with a mobile forestay. This first internal door will create an emergency initial secured bubble allowing a short time to alert and gather the crew in emergency in case of a late alert, pirates being already onboard. The four or five minutes it will take pirates to destroy this door will allow you to secure the full crew within the real final citadel.
Of course, this list is not exhaustive. It’s established on the analysis of hundred of maritime piracy acts within the Gulf of Guinea and is mainly dedicated to avoiding crewmembers being kidnapped. It can be completed and/or adapted depending of vessel configuration and the good sense.
François Morizur is a maritime security expert and former French Navy officer.
from Storage Containers https://www.maritime-executive.com/article/seafarers-must-adapt-to-the-rapid-evolution-of-piracy
via http://www.rssmix.com/
0 notes
Photo

Just Relax and Let God Be God Joyce Meyer tweeted, ‘Just relax and let God be God.’ It is a great comfort to know that a loving God is ultimately in control of everything that happens. Bishop Sandy Millar often says in the face of some tragedy or when things had gone badly wrong: ‘The Lord reigns.’ Many times throughout the Bible, God is referred to as theSovereign Lord. Both Joyce Meyer and Sandy Millar are expressing, in different ways, absolute confidence in the sovereignty of God. If God is sovereign and ultimately in control, does that mean that you are absolved of responsibility for your actions? Does it mean that you do not have ‘free will’? As we see in our New Testament passage, the Bible teaches both – the ultimate sovereignty of God at the same time as human responsibility and free will. Psalm 9:7-12 1. Confidently trust in the sovereign Lord God is in ultimate control of the universe: ‘the Lord reigns’ (v.7). God ‘will judge the world in righteousness (rightness and equity); He will minister justice to the peoples in uprightness’ (v.8, AMP). This knowledge is an enormous comfort. We may never know in this life why God allows some horrendous things to happen. Trust in the sovereignty of God and keep on believing that he will never forsake you: ‘And they who know Your name will lean on and confidently put their trust in You, for You, Lord, have not forsaken those who seek You’ (v.10, AMP). In the meantime keep doing three things: Praising ‘Sing the praises of the Lord’ (v.11a).Proclaiming ‘Proclaim among the nations what he has done’ (v.11b).Praying ‘The Lord is a refuge for the oppressed, a stronghold in times of trouble’ (v.9); ‘He does not ignore the cry of the afflicted’ (v.12b). Lord, thank you that you do not ignore my cries and that I can confidently trust in you. Thank you that I can relax and let you be God. Matthew 11:16-30 2. Accept the invitation to walk with Jesus The teaching of Jesus is fascinating. In the first section of today’s passage he seems to be saying, ‘You can’t win.’ On the one hand, John the Baptist was an ascetic and was accused of being demonised. On the other hand, Jesus went to parties with all kinds of people and made friends with those who were regarded as unsavoury characters. He was accused of being a glutton and a drunkard and a friend of tax collectors and sinners (v.18). Whatever you do may be misinterpreted. Yet Jesus adds, ‘But wisdom is proved right by her actions’ (v.19). I take this to mean that all we can do is the right thing and not worry about what anybody else thinks. ‘Opinion polls don’t count for much, do they? The proof of the pudding is in the eating’ (v.19, MSG). Jesus then denounces the cities that he has visited and performed miracles in, where people have neither repented nor believed. He suggests that their sin is worse than the sin of Sodom (v.24). The sin of unbelief is perhaps the most serious of all. Jesus goes on to teach in such a way that it is clear that he believed in both predestination (that God has already determined everything that will happen) and free will. He teaches both alongside one another. It is a paradox. The two seemingly contradictory things are both true at the same time. It is not 50% ‘predestination’ and 50% ‘free will’. Jesus says we are 100% predestined and we have 100% free will. This may seem impossible, but God is able to transcend and yet not distort human freedom. We ultimately see this in the incarnation: Jesus is 100% God and 100% human; he is fully God and fully human. Predestination ‘All things have been committed to me by my Father. No one knows the Son except the Father, and no one knows the Father except the Son and those to whom the Son chooses to reveal him’ (v.27). Why God chooses to reveal himself to some and not to others is a mystery. It is certainly not based on wisdom and learning. Sometimes the great intellectuals simply cannot see it: ‘you have hidden these things from the wise and learned’ (v.25). And yet sometimes people of little or no education, or those who are very young (‘little children’, v.25), seem to have a very profound understanding of Jesus. ‘You’ve concealed your way from sophisticates and know-it-alls, but spelled them out clearly to ordinary people’ (v.25, MSG).Free will Jesus says, ‘Come to me, allyou who are weary and burdened, and I will give you rest’ (v.28). The invitation to come to Jesus is for everyone. No one is excluded. We are all invited. We all have a choice whether to accept the invitation of Jesus or to refuse it. I find it difficult to get my mind around this paradox. However, I have found the following illustration helpful. Imagine a room with an arched doorway. The outside of the arch is inscribed with the words, ‘Come to me, all you…’ (v.28). In other words everyone is invited into the room. When you get into the room, on the inside of the same arch is written, ‘No one knows the Father except the Son and those to whom the Son chooses to reveal him’ (v.27b). In other words, free will is a doctrine for everyone. No one can say, ‘I am not going to become a Christian because I have not been chosen.’ The invitation is to all. On the other hand, predestination is a doctrine of assurance for those who areChristians. Once you have accepted the invitation and entered, you can know that God has chosen you and therefore he will not let you go. I love the words of Jesus in verse 28. In a stressful world where so many are ‘weary and burdened’, Jesus promises you rest. He offers to take your burdens and replace them with his own. The yoke (something that Jesus would have made in the carpenter's shop) was a wooden frame joining two animals (usually oxen) at the neck, enabling them to pull a plough or wagon together. The function of the yoke is to make burdens easier to carry. I love this image of walking in step with Jesus, sharing our burdens, making the trials to be endured and the battles to be faced ‘easy’ and ‘light’ by comparison. Jesus is not a slave driver. When you pursue his agenda for your life you carry a burden but it is ‘not harsh, hard, sharp, or pressing, but comfortable, gracious, and pleasant’ (v.30, AMP). When you do what Jesus asks you to do, he gives you the strength and wisdom to do it and you carry his burden with him. There will, of course, be many challenges and difficulties, but there will also be a lightness and ease. Jesus says to you: ‘Are you tired? Worn out? Burned out on religion? Come to me. Get away with me and you’ll recover your life. I’ll show you how to take a real rest. Walk with me and work with me – watch how I do it. Learn the unforced rhythms of grace. I won’t lay anything heavy or ill-fitting on you. Keep company with me and you’ll learn to live freely and lightly’ (vv.28–29, MSG). Just relax and let God be God. Lord, thank you that you promise me rest for my soul. Thank you that I can come to you today. I give to you my burdens… Genesis 29:1-30:43 3. Watch God work his purposes out God works his purposes out in spite of our weakness, vulnerability and sin. Jacob was a deceiver. What we sow, we reap. He sowed deception and he reaped deception from Laban (29:25b). He then continued the cycle of deception (30:37–43). This is an extraordinary story of deception, and also of unfaithfulness and disloyalty. Yet somehow, in all of this, God worked his purposes out for the individuals involved, for Israel, for the birth of his Son Jesus and for the future of the people of God. A lot of human sin and disappointment was involved in the birth of Jacob’s children (29:31 – 30:21). Yet, through it all, God was working out his purposes for the twelve tribes of Israel. Rachel’s prayer was finally answered with the birth of Joseph (30:22). As God was in control of theirlives, you can trust that he is ultimately in control of yours as well and that ‘in all things God works for the good of those who love him, who have been called according to his purpose’ (Romans 8:28). So, just relax and let God be God. Lord, thank you that you use even weak, vulnerable and sinful people. Thank you that you can use me. Thank you that although you love me as I am, you love me too much to leave me as I am. Help me never to settle for second best. Help me to take responsibility for my life and at the same time confidently trust in your sovereignty. Pippa Adds Genesis 29–30 I am enjoying these chapters in Genesis. The story is much better than watching a soap opera on television. Whatever will they do next? It’s interesting that Sarah, Rebekah and Rachel all had difficulty having children (this is not a new problem). Yet each of the children who eventually arrived was hugely important in God’s plan for the people of Israel. Was God waiting for the right time or was he preparing the parents in some way? Most of Jacob’s children seem to have been born as a result of sibling rivalry and jealousy. Yet God didn’t give up on them and still managed to work out his plans.
0 notes
Text
Seafarers Must Adapt to the Rapid Evolution of Piracy
In two recent articles, Sea Piracy in 2025: Piracy 2.0? and Countering Gulf of Guinea Piracy Towards 2025 I tried to map out the possible evolution of piracy within Gulf of Guinea until 2025. Then I analyzed the different possible actions to reduce this threat. This analysis cannot be complete without integrating the main actor, the seafarer. This third article therefore concerns the how seafarers must adapt to the rapid evolution of pirate activities.
It’s noticeable that this domain for seafarers is based on regulatory documentation that is low in volume and weak in practical guidance. The Ship Security Plan (SSP) is the basis for maritime security regulations. This document, established after the USS Cole, Limburg and September 11 attacks, was mainly focused on maritime terrorism. The content has been lightly modified since, integrating some requirements arising from the evolution of piracy.
The ISPS regulation does not go deeper on practical measures concerning vessel, crew members, equipment and procedures when looking at piracy. To cover the seafarers practical needs a group of associations published a document called Best Management Practices in early 2000. This document, dedicated to deter piracy and enhance maritime security in the Red sea, Gulf of Aden, Indian Ocean and Arabian sea has been reviewed several times since (Last review BMP 5 –June 2018). To respond to the specific Gulf of Guinea environment, one document, Guideline for Owners, Operators and Masters for Protection against Piracy in the Gulf of Guinea Region has been established by the same structure.
Finally, as the piracy epicenter as moved from East Africa to West Africa, one new document BMP West Africa has been issued beginning 2020 to provide threat mitigation guidance on counter-piracy/armed robbery at sea and to help companies and mariners to risk assess voyages while operating along the West African coast.
Despite the evolution of communications at sea, the captain is an isolated leader. His or her job requires quick decisions concerning a wide variety of situations. If the situation allows, he can try to establish a telephone connection but, the handset hung up, he becomes again, isolated. A piracy attack is a dynamic event testing a captain's competency and reactivity. This situation can be illustrated by the Captain Phillips movie scene where Tom Hanks calls the MSCHOA. As with everything else, a captain must be informed, trained, prepared.
This readiness must not only apply to seafarers, it should be also concern the vessel. “If you ignore both your enemy and yourself, you will only count your fights by your defeats.” This citation should be a guide for a captain or ship security officer (SSO) operating within the Gulf of Guinea. The pirates' boarding rate within Gulf of Guinea is very high. As said in my previous article, there are several reasons for this. Some are linked to the combination of operational capacities of pirates and the lack of military responses (PMSC / escort vessel) but it is obvious that somet of the reasons are linked to another conjunction: ignorance of West Africa pirates, to their profiles and their modes of action.
As such, it would be interesting to test the captains/SSOs to make them draw Gulf of Guinea pirates. To help their sketches, we can try to characterize them by some elements:
Use of fiber speed boat, eight to 10 meters long, usually sporting colored flags (mainly red or white), usually motorized by two outboard engines, 150/200 Hp, more than six men onboard (usually eight to 10), men armed with AK 47, speed boat fitted with an aluminum ladder eight to 10 meters long. Pirates can operate on one sole speed boat, sometimes in pairs.
It’s noteworthy that numerous specialized articles speaking about Gulf of Guinea piracy are illustrated by a very well-known picture showing a speed boat having a mounted Cal 50 machine gun and transporting……MEND militants. If the picture is beautiful, it’s not related to real Gulf of Guinea pirates. Sometimes this picture is replaced by the view of one skiff transporting Somalian sea pirates. This pictorial materialization may disturb the initial perception of what a Gulf of Guinea pirate is.
The fiber vessels don't offer a strong Radar Cross Section, navigational radars have limited capacities. The pirates' speed boat emerges on the radar screen at about three nautical miles when the sea state is under three and the speed is high. It’s highly recommended that one radar be set on short pulse/ short range, the AC SEA/AC RAIN setting in accordance. It’s possible that watchkeepers will detect the approach by the noise before sight or radar screen. The approach axes can be various but the CPA (Closest Point of Approach) is …0.
The time of the attack varies too and is evolving regularly. In 2018, almost two thirds of the piracy attacks was conducted by daylight. Currently, piracy attacks within Gulf of Guinea are mainly conducted at night time and mainly at the beginning or end of the night.
The location is, of course, one of the important facts to analyze. My previous article, Sea Piracy in 2025 analyzed the current trend of attack attempts very deep offshore …..or within non protected anchorage areas along the West African coast from Luanda till Abidjan.
This first enemy analysis realized, and to remind on the Sun Tzu citation, it may be even more important to know yourself. Turning back to the Gulf of Guinea piracy data, one element is alarming: it’s the number of vessels boarded without alarm/alert: No VHF.M distress call, no SSAS (Ship Security Alert System) alert, no vessel internal alert. The personnel on bridge duty discover the pirates when one is directly pointing a gun at them on the other side of the bridge glass.
For at least two cases in the last few months, the pirates have used….the pilot ladder left along the hull by night. These observation led to at least two main reflections: the seafarers had misjudged the threat and, because of this error, had not applied the adapted basic security measures.
Reviewing the current trends, appreciating more precisely the Gulf of Guinea pirates' modus operandi, it’s obvious that the area located between San Pedro and Luanda and taking a range of 200 nautical from the shore must be considered as High Risk Area for piracy. (Conakry Anchorage is a specific bubble which should be considered too.) This area is globally characterized on the specific chart established by the MDAT-GOG. Within this area, as said before, the pirates are currently acting on two modes:
Piracy attack deep/very deep offshore: Action is characterized by a direct attack against a vessel en route day or night. The detection of the threat is facilitated by the sparse maritime traffic, but the vessel is usually alone, not protected.
Maritime criminality within anchorage area: The pirates operate in discretion, by night against vessels anchored or on stand by. The detection of the threat is complicated by the numerous speed boats/canoes fishing in the area, but the vessel can benefit from security support from navy assets protecting the area.
The objective of these two pirates process is the same: kidnapping of crew members.
This being posed, and as the threat is focused on abduction, it is interesting to revisit the maritime operators possible internal self responses in 10 main actions:
• Secure the vessel as much as possible by a security escort vessel or an embarked military security team: The pirates are focusing on soft targets!
• Optimize your detection means for locating pirates as early as possible: One speed boat sailing 30 knots is along board six minutes after detection at three nautical miles!
• Be able to classify the threat as soon as possible, using the piracy criteria declined above: Personnel on duty on the bridge should be informed, trained and regularly refreshed about local pirates.
Raise the alarm about the attack by all means available (VHF.M 16 / SSAS/ GMDSS/ PHONE / HORN-SIREN/LIGHT)
• Optimize internal alert systems to ensure all crew members will be aware of the alert sent.
Conduct regular anti-piracy drills: piracy attack / alert / immediate communication / mustering / lock down control / anti-boarding measures / move to safe haven.
• As soon as you operate within a high risk area, lock your vessel. All external doors locked, all portholes secured. Try to slow down the pirates progression onboard the vessel after boarding by the use of specific items (wire rack or other) on external stairs.
• Use the navigation lights only, no deck light, all portholes blinded. By night level 4 or 5, when navigation lights are off, after change of course /speed, the vessel targeted disappears for pirates sailing onboard speed boat without radar, AIS or night vision goggles.
• Optimize the vessel's readiness by using simple and efficient systems. As the maritime industry is strongly impacted by the general economic situation, focus on low cost equipment rather than hoping for the use of means that are certainly effective but financially unaffordable. As an example, one general public autonomous sensor sending sound, light and possibly video, set up on the obliged path from deck to bridge, can efficiently alert the watchkeeping team in case of initial surveillance/detection failure.
• Consider the first internal door from navigation bridge to accommodations and lower decks as one essential element of your safe haven. Reinforce this door, reinforce the frame, complete the hardening with a mobile forestay. This first internal door will create an emergency initial secured bubble allowing a short time to alert and gather the crew in emergency in case of a late alert, pirates being already onboard. The four or five minutes it will take pirates to destroy this door will allow you to secure the full crew within the real final citadel.
Of course, this list is not exhaustive. It’s established on the analysis of hundred of maritime piracy acts within the Gulf of Guinea and is mainly dedicated to avoiding crewmembers being kidnapped. It can be completed and/or adapted depending of vessel configuration and the good sense.
François Morizur is a maritime security expert and former French Navy officer.
from Storage Containers https://maritime-executive.com/article/seafarers-must-adapt-to-the-rapid-evolution-of-piracy
via http://www.rssmix.com/
0 notes