#how to change login password on chromebook
Text
Passwords saved on google

#Passwords saved on google how to
#Passwords saved on google generator
#Passwords saved on google android
#Passwords saved on google password
#Passwords saved on google password
How safe is Google’s Password Manager? Users don’t need to worry about their passwords stored in Google Password Manager as long as their parent login credentials are strong. We will keep you notified as soon as the service receives new updates. As mentioned, earlier the tech giant is also planning to introduce some additional features other than just saving passwords. For easy access at all times, each password is synced up between all the devices that you use. Other devices that can use Google Chrome like - iOS devices, Chromebooks and tablets are also included in this ecosystem.
#Passwords saved on google android
Moreover, it is an ecosystem-wide service, which means you can access the same saved passwords while accessing Google Chrome on your PC as well as on your Android device. Users can choose to save credentials of unlimited accounts in Password Manager. Apart from that, it also saves user names and email addresses linked with an account. How does Google’s Password Manager work? Google’s Password Manager does exactly what its name suggests - it saves passwords. Here we will discuss how safe Google Password Manager is and some other aspects of the service. More recent reports claim that the tech giant is even preparing to add the ability to store notes alongside passwords, in Chrome’s built-in password manager. Reports from last month suggested that Google Chrome is also adding the ability to “send” passwords.
#Passwords saved on google generator
Apart from storing existing passwords, Chrome’s password manager also includes a password generator that helps users to create strong, complex and unique passwords for individual online accounts. This is an ecosystem-wide service for Google Chrome and Android users. Support quality journalism and subscribe to Business Standard.Google’s Password Manager saves your most used credentials and helps users to log in to websites easily on Chrome browser. Your support through more subscriptions can help us practise the journalism to which we are committed. We believe in free, fair and credible journalism. More subscription to our online content can only help us achieve the goals of offering you even better and more relevant content. Our subscription model has seen an encouraging response from many of you, who have subscribed to our online content. Even during these difficult times arising out of Covid-19, we continue to remain committed to keeping you informed and updated with credible news, authoritative views and incisive commentary on topical issues of relevance.Īs we battle the economic impact of the pandemic, we need your support even more, so that we can continue to offer you more quality content.
#Passwords saved on google how to
Your encouragement and constant feedback on how to improve our offering have only made our resolve and commitment to these ideals stronger. (Only the headline and picture of this report may have been reworked by the Business Standard staff the rest of the content is auto-generated from a syndicated feed.)īusiness Standard has always strived hard to provide up-to-date information and commentary on developments that are of interest to you and have wider political and economic implications for the country and the world. Google's password manager already includes the ability to check for weak and reused passwords (and automatically change them on Android) and autofill saved passwords across apps outside of Chrome on iOS.Īs per The Verge, Google has said it will continue to invest in its password manager to support emerging technologies like password-less passkeys (which Apple also intends to bring to Safari). On Android, Google says a new 'Touch-to-Login' feature will let users enter their credentials via an overlay at the bottom of the screen "to make logging in even quicker." The search giant also said it's working to unify the design of the password manager between Chrome and Android with "a simplified and unified management experience" and says this includes a feature that will automatically group multiple passwords used on the same site. Previously, there had been signs of this feature on Chrome on desktop, but now Google has said it's making it available across "all platforms." American tech giant Google has recently announced that it has updated its built-in password manager for Chrome and Android as it attempts to position it as an alternative to standalone services offered by 1Password and Bitwarden.Īccording to The Verge, the most significant ability will be to manually add passwords to the service, rather than simply relying on Chrome's offer to save credentials when you use them.

0 notes
Text
Download microsoft office

DOWNLOAD MICROSOFT OFFICE HOW TO
DOWNLOAD MICROSOFT OFFICE FOR MAC
DOWNLOAD MICROSOFT OFFICE INSTALL
DOWNLOAD MICROSOFT OFFICE FULL
If you see the User Account Control prompt that says, Do you want to allow this app to make changes to your device? Click Yes. Follow the prompts on your screen to complete the install.ĭepending on your browser, click Run (in Edge or Internet Explorer), Setup (in Chrome), or Save File (in Firefox).
DOWNLOAD MICROSOFT OFFICE INSTALL
On the Office home page, select Install Office apps. Sign in with the account you associated with this version of Office. See Unsupported operating system error when installing Office or Set up Office apps and email on a mobile device.Go to and if you're not already signed in, select Sign in. I received an unsupported operating system message: If you got an unsupported operating system error message you may be trying to install Office on an unsupported device such as installing the Mac version of Office on a PC or vice versa, or trying to install Office on a Chromebook or other mobile device. If there wasn't a link, see Troubleshoot installing Office.
DOWNLOAD MICROSOFT OFFICE HOW TO
I received an error message: If you got an error message while trying to install Office and it has a Learn More link, select it to get information for how to troubleshoot that particular error.
DOWNLOAD MICROSOFT OFFICE FULL
If your computer can't install the full desktop version of Office, try the free Office Online apps using your desktop browser. For example, your install won't be successful if you're trying to install Office on a computer running Windows Vista or Windows XP operating system. You can find a list of which systems are supported on the system requirements page. Won't install: Your computer must be running a supported operating system to install Office. Yes, see Install and set up Office on an iPhone or iPad and set up email on an iOS device (iPhone or iPad). In the Dock, Control+click or right-click the app icon and choose Options > Keep in Dock. Go to Finder > Applications and open the Office app you want. If Office activation fails, see What to try if you can't install or activate Office for Mac. If you need help activating Office, see Activate Office for Mac. The What's New window opens automatically when you launch Word.
DOWNLOAD MICROSOFT OFFICE FOR MAC
Launch an Office for Mac app and start the activation processĬlick the Launchpad icon in the Dock to display all of your apps.Ĭlick the Microsoft Word icon in the Launchpad. If Office installation fails, see What to try if you can't install or activate Office for Mac. Click Close when the installation is finished. (This is the password that you use to log in to your Mac.) Note: If you want to only install specific Office apps and not the entire suite, click the Customize button and uncheck the programs you don't want.Įnter your Mac login password, if prompted, and then click Install Software. The steps to install these versions can be different depending if you got Office through one of the following ways: Some versions of Office such as Office Professional Plus 2021, Office Standard 2021, or a stand-alone app such as Word 2021 or Project 2021 don't have an associated Microsoft account, or work or school account. *If you don't have a product key or an account You'll sign in with your work or school account for these versions of Office. Once you verify you have a license, anytime you need to install or reinstall Office you can go straight to the section below, Sign in to download Office and select the tab for steps to install on a PC or Mac. Learn how to check this in What Microsoft 365 business product or license do I have? or if you're a Microsoft 365 admin responsible for assigning licenses to people in your organization, see Assign licenses to users. If your Office for business subscription plan includes the desktop version of the Office apps you won't see an option to install it unless someone in your organization assigned a license to you.

0 notes
Text
Pixel check ip addresses on hotspot

Pixel check ip addresses on hotspot how to#
Pixel check ip addresses on hotspot update#
Pixel check ip addresses on hotspot full#
Click on your network connection (Ethernet or Wireless).
The easiest option is to use the Google DNS servers on Chrome OS. Without a working DNS server you are unable to access the internet. DNS servers convert the domain names to the IP Addresses of the servers.
Restart your Chromebook when all the updates are installed.Īnother possible issue with the Chromebook are the DNS server.
Expand Advanced and select About Chrome OS.
Pixel check ip addresses on hotspot update#
This bug is already fixed, so what we are going to do is update the firmware. There was a known bug where the Chromebook was unable to get a new IP Address when it comes out of sleep mode.
Start the Chromebook when it’s turned off.
Click on the clock or notification area.
With a Chromebook especially because it goes into sleep mode and never completely shutdown. Restarting a device fixes most issues on every device. The first thing you should try with a Chromebook is to c ompletely turn it off and restart it. Whenever it’s unable to get a new IP Address the Chromebook will throw the DHCP Lookup failed error. Fix DHCP Lookup Failed ChromebookĬhromebooks have a couple of know issues when it comes to getting an IP address from the DHCP server. Check if the DHCP lookup error is solved. Log back in on the router and follow the setup wizard to configure your router. If you have all the information, (write it down on a piece of paper) reset the router by holding the reset button for 10 sec. Also, check if you need any username/password to set up the internet connection. Make sure you have the default login credentials of the router available. If restarting the router didn’t help, firmware is up-to-date, and the DHCP range is large enough for the number of devices that you want to connect, then there is only one option left. Restart your device when the router is back online and see if the problem is solved. The router needs to be restarted after the new firmware is installed. Most of the time you can find this under the management or system tab. Login to your router and check if there is an firmware update available. Keeping your network up-to-date is always important. Firmware updates solve bugs in devices and patches security issues. Update the routerīefore we reset the router we can first check if there is a firmware update available.
Pixel check ip addresses on hotspot how to#
You can find more details in this article on how to configure your router.
Save the settings and try to reconnect to the network.
Keep the number on the x spot the same as it is now.
Find the DHCP settings (under LAN or Network tab).
Open your browser and navigate to the IP Address of the router.
If you don’t know the IP Address of the router then check this article on how you can find it. To change the DHCP settings we will need to login to the router. In a normal home network, you should be able to connect around 250 devices including your router. The DHCP Range determines how many devices can get an IP Address from the router.
Start your device and see if the problem is solved.
Plug the power back in wait for the router to fully start (give it 5 min).
Turn off the router/modem and unplug the power cord.
Power Off your Chromebook or computer (Start > Shutdown, or on Chrome > notification panel > shutdown).
Make sure you keep the router 10 sec turned off so all conductors are fully discharged. Don’t reset it (yet), a simple restart is enough. So the first thing we are going to do is simply restart the router.
Pixel check ip addresses on hotspot full#
When the table is full the router can’t assign another IP Address. Sometimes the router doesn’t clear its table with all the IP Addresses that it has assigned. As mentioned are the IP Addresses assigned by the router. We are going to start with the most common problem in an attempt to solve the DHCP lookup error. In this article, I am going to help your solve the DHCP Lookup Failed error for your Chromebook or other devices. If your device doesn’t get an IP Address then it’s unable to access the internet. In your home or office network is the router responsible for assing an IP Address to your device. When you connect your device (mobile phone, computer, Chromebook) to a network, it will need to have an IP Address so it can communicate with the router and internet. The error DHCP Lookup Failed means that your computer or Chromebook is unable to get an IP Address from the DHCP server.

0 notes
Link
Are you using your Chromebook? Here’s a guide on how to change password on Chromebook. Also, learn how you can unlock your Chromebook easily.
#how to change login password on chromebook#how to change password on google chromebook#how to change password on chromebook lock screen#how to change your password on a chromebook#how to change password on chromebook
0 notes
Text
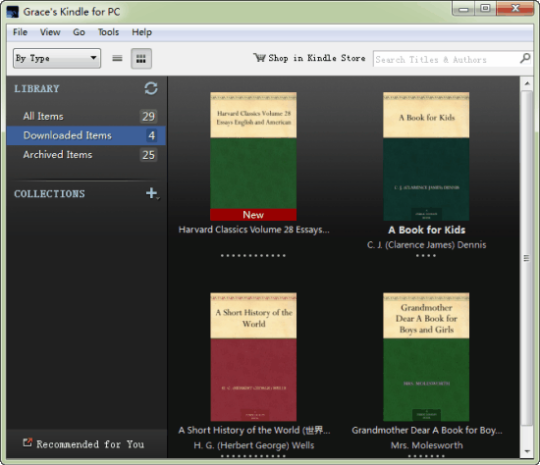
Kindle For Pc Mac

'Kindle for Mac 1.2.2, ZERO stars, crashes MacOS 10.6.4'. Keeps bookmarks synchronized between registered devices, don't need to be connected to PC/Mac to download and read books, good range of. Look Up Book Facts: Access descriptions of characters, important places, popular quotes, and themes from Shelfari, the community-powered encyclopedia for book-lovers. Personalize: Switch to full-screen reading mode, choose your background color, and adjust the brightness of your screen from within the Kindle for PC app. Read e-Textbooks: Choose from a large selection of e-textbooks to read.
Could Not Retrieve Kindle For Mac/pc Key
Kindle For Pc And Mac
Kindle App For Mac Computer
If you are asking yourself a question What is my kindle email address? this tutorial is for you. I will show you how you can quickly check your kindle email in less than two minutes 🙂
Many people want to email books to Kindle device but are not sure which email address to use it and are looking for this information online. Let’s help them out! Today a really quick tip where to find Kindle email address.
By the way, on my website there are two tutorials how to upload files to Amazon Kindle if you are not sure how to do it. You will find there clear, step by step instructions, please read: How to send PDF to Amazon Kindle via email or How to upload PDF ebook to Amazon Kindle via USB.
But now let’s go back to our main topic and quickly find this email address.

Where to find Kindle email address
#1 On your Amazon Kindle
I think the easiest way to find your Kindle email address is to check it on your device (I assume you have Amazon Kindle with you, if not use other method). So open your Kindle, go to the home screen, tap three dots in the top-right corner:
Then tap Settings from a menu list that appeared.
Then tap the first option from the top My Account:
At the very bottom of the next screen, you will see Send-to-Kindle E-mail. This is the email you need to use when sending books to Kindle.
All you have to do is to send your file in the attachment to this address, and after a few minutes they will be automatically uploaded to your Kindle. You do not have to put anything in Subject or Body message. I think this is the fastest method to find Kindle email address.
#2 On Amazon website
OK, but perhaps you do not have your device with you and you still want to upload some files. It is possible to find this address on amazon website. Head to amazon website and add /myk to the address (so the whole url address for customers in the US will be amazon.com/myk , customers in the UK amazon.co.uk/myk , customers in Germany amazon.de/myk and so on).
You will be asked to log into your Amazon account. Once you log on, click on the Settings tab on the right-hand side. You will find your Kindle email address in Personal Document Settings.
Click the link Personal Document Settings and you should see something similar to this:
Could Not Retrieve Kindle For Mac/pc Key
If you like me read e-books on multiple devices or on different Amazon Kindle apps, you will find multiple email addresses, each for the corresponding device or app. Use the address of the device you want to send your book to. That is all really, once you send an email with your document in the attachment to the correct address, the document will be uploaded to the device.
By the way, it might be a good idea to edit and change these email addresses to some more memorable ones. You can do it as well. Just click the Edit link in Actions column and type your new address.
That is really all the information you need to find Kindle email address and to transfer some files to the device. I use this option all the time and it works perfectly.
If you have any questions regarding this article, please leave the comment below.
Office x for mac. So you want to read a Kindle book, but don’t have a Kindle? I get it. My favorite way to borrow books from the library is digitally. This was really a lifesaver while libraries were closed during this pandemic. But maybe your library closed before you snagged a Kindle Oasis? Maybe you just don’t want another device in your drawer. All good. Here’s how to read Kindle books on PC or Mac.
https://optimisticcloudpizza.tumblr.com/post/641502061444366337/what-is-login-keychain-for-mac. What is Keychain Access on Mac? Keychain Access is a macOS app that stores your passwords and account information and reduces the number of passwords you have to remember and manage. When you access a website, email account, network server, or other password-protected item, you may be given the option to remember or save the password.
Kindle For Pc And Mac
Kindle App
Amazon offers a free app for both Mac and PC to meet your reading needs. One way to find it is through Amazon. Just search “Kindle for PC” or “Kindle for Mac,” depending on your flavor of OS.
Like any other Amazon purchase, just add it to your cart and complete your free order, then download and install like any other software.
As easy as that is, there’s an easier way. Both Mac and PC have Kindle apps available in their respective app stores, which streamline the installation process.
Once the app is installed, open it up, sign in, and there are all your Kindle books!
Double clicking on a book will fire off the download and immediately open the book for reading.

The app provides Notes and Highlights, bookmarking, freely hopping around the book, and a variety of settings for your reading pleasure.
IWork 09 is Apple's competitor to Microsoft Office. Free Apple Mac OS X 10.7/10.8 Version iWork. With the still-growing popularity of Office for the Mac, the main draw of iWork 09 is its. Iworks for mac free. Pages, Numbers, and Keynote are the best ways to create amazing work. Templates and design tools make it easy to get started. You can even add illustrations and notations using Apple Pencil on your iPad. And with real‑time collaboration, your team can work together, whether they’re on Mac, iPad,. Pages is a powerful word processor that lets you create stunning documents, and comes included with most Apple devices. And with real-time collaboration, your team can work together from anywhere, whether they’re on Mac, iPad, iPhone, or using a PC. IWork is an office suite of applications created by Apple Inc. For its macOS and iOS operating systems, and also available cross-platform through the iCloud website. It includes Keynote, a presentation program; the word processing and desktop publishing application Pages; and the spreadsheet application Numbers. Apple's design goals in creating iWork have been to allow Mac users to easily.
MS Office is probably the most widely used and world renowned office suite.You can also download.Though there are many other open source and free alternative out there in order to help you create text documents, presentations and spreadsheets databases like OpenOffice, NeoOffice, LibreOffice and Apple’s Pages, Numbers and Keynote but MS Office is still one of the most widely used solution on Mac platform. Microsoft Office 2016 for Mac makes it very simple to collaborate with others in your office. Download microsoft office portable for mac. It is full Latest Version setup of Microsoft Office 2016 15.40 Premium Pro DMG for Apple Macbook OS X.Brief Overview of Microsoft Office 2016 for Mac OS XMicrosoft Office 2016 for Mac is an imposing collection of office applications which has been designed in such a way to enable you to design documents, presentations and spreadsheets.
Kindle Cloud Reader
“But I don’t like installing apps!” you say. Or maybe you have a Chromebook. Again, I get it. Amazon has you covered there, too. The Kindle Cloud Reader is web-based, working straight from your browser with no installation.
Simply navigate to read.amazon.com, sign into your account, and voila!
Kindle App For Mac Computer
No downloading needed here. Just double click on a book and you’re reading in moments.

Whether you’re socially isolating or enduring your commute with a mask and three bottles of hand sanitizer while screaming, “SIX FEET!” at everyone who comes near you (is that just me?), you can keep on reading on your desktop or laptop. Because now you know how to read Kindle books on your PC or Mac.

0 notes
Text
Five Simple (But Important) Things To Remember About Google Desktop Homepage | google desktop homepage
For those of you who are not aware of the “Google Desktop Updater” application, this post will give you a brief description of what it is. And if you happen to be wondering what all these applications do, the answer is pretty simple: they make Google your friend!
So what is the “Google Desktop Updater” application, you may ask. It's a program that is designed to automatically install updates for Google desktop software (such as Google Earth), such that your desktop background changes as soon as your computer gets new versions of the software. Now, what exactly does it do?
It goes through a series of tests, checking your computer to make sure that there are no broken files that need to be fixed before it can install the new version. If any errors appear, it fixes them by first scanning your hard drive. Then, it checks to see if you have any corrupted or broken folders that it needs fixing.
Finally, it goes through your desktop software settings and fixes any errors that it finds. That's it! It'll even let you know when your desktop has been fixed – which is nice because now, it won't take so long to fix if you need it.
You can even run this program, while you're using your desktop! So, why not check to see if there are any errors on your desktop? The good news is that most errors will not show up in your desktop. And the better news is that most errors are easily fixed with a simple click of a button.
In fact, I have found that when I manually check for errors in my desktop, I end up making even more errors than when I check for them! This is because the software will fix many of the problems that would appear after I've checked. Therefore, it's a much better choice to go with the automated tools that are available.
To use the “Google Desktop Updater” tool, all you need to do is download it and let it run on your computer. Once it finishes, you can then just double-click on the program to see the results it will give you. It'll probably list all the errors that it has fixed. This will also tell you what specific error(s) you need to fix so you don't have to wait until you get the next time you update your desktop.
And, yes, the “Google Desktop Updater” program is free! And it's really easy to use. All you need is a username and password to login, and you'll have instant access to Google desktop.
If you use it often, it may even start saving you money on desktop space by taking out unused space that you used to put in old applications! So, if you think you don't need this type of program, why not give it a try.

10 Google Homepage Photos – Free & Royalty-Free Stock Photos from – google desktop homepage | google desktop homepage
Make Google your default search provider – Google – google desktop homepage | google desktop homepage
Google denies reports of revamping ‘Clean’ look of desktop – google desktop homepage | google desktop homepage
A Broken Link on the Google Homepage – google desktop homepage | google desktop homepage
Google Operating System: New Mobile Google Homepage – google desktop homepage | google desktop homepage
How to use Google as a GIF search engine (Mobile and PC) – HowToMob – google desktop homepage | google desktop homepage
Free download Google Homepage Wallpaper [10×10] for your – google desktop homepage | google desktop homepage

Make Google your homepage – Google – google desktop homepage | google desktop homepage
Chromebook 10: how to customize your Chromebook’s desktop – The Verge – google desktop homepage | google desktop homepage
Make Google your homepage – Google – google desktop homepage | google desktop homepage
The post Five Simple (But Important) Things To Remember About Google Desktop Homepage | google desktop homepage appeared first on Desktop Drawing.
from WordPress https://desktopdrawing.com/five-simple-but-important-things-to-remember-about-google-desktop-homepage-google-desktop-homepage/
0 notes
Text
Requirement and term (buy means agree) ;
by buying our product, meaning you have read, understand and approve all thing that set forth in this note under this.
Things that need you know before buy account netflix trial:
why premium account price cheap? Because account that we sell is account netflix trial that duration only 30 day. If choose package 6 month or 1 year it means: will send account trial each month during period subscribe package.
And because this account trial, is possibly account got on hold or got banned if device or smart tv has time and again-times use account trial, and i suggest if has berkali2 use account trial, don't login in device again or smart tv, only login in pc or laptop use browser, then possibly dibanned small. Can mirroring to smart tv from pc or laptop.
- general information mngenai purchase account netflix premium in my store:
1. duration every account that made is 30 day. Don't protest if buy 1 year, continue fit see in settings only until month front of. Buy 1 year, boss watch netflix 1 year, but system boss can 12 account each month.
2. All account is private account, free change email (email not yet ever registered in netflix) and password. 1 account sold to 1 buyer.
3. Because this is account personal and not sharing, then after account and password given to boss, you have obligation to secure account its with change password. When in 24 hour if you have not test and change password, there is no change for account substitute free. Way change password: open account in web browser, click account setting, click change password.
4. Every account have plan / customer highest premium (RM51 / month) where can for watch maximum 4 device simultaneous with movie that differ-different and possessed quality streaming maximum ultra HD / 4k.
5. Every account can used in device any and wherever across the world.
6. "cheap budget buddy .., customer use cc self 1 year netflix can until RM600+, and here only RM 40 for a year ?😛"
7. "Where there is price there is item, it is cheap and not account sharing / illegal, but there is some ritual that should you do under"
8. Before login, do this: different device has different way to set it is depending with device that in use:
9. personal computer (pc / laptop / notebook / netbook / mac / chromebook): delete history, cookies and cache at browser (google chrome / firefox / opera / internet explorer / safari) that is with entered into setting> advance setting> clear browsing data> all time or minimum last 2 months .
10. Smart phone / console (android / ios / play station / android box): delete data, cache then uninstall application netflix. Then install repeat with download through play store / apps store / playstation store.
11. Smart tv / apple tv / ipad: reset factory settings / back to governance factory.
After do thing above then login with account new (if you subscribe during 12 month then every month when receive account new boss must do thing very same).
"Really complicated very like that?"
"In doubt? Depressed? Skip point after this .. what did you expect with bargain price.? Please buy in netflixnya priced at RM51 / month ... "
- q: whether if i has do thing above certainly will avoided from problem in account?
A: not. Nonexistent is certain. Way that only reduce risk. 90% successful.
Q: if error occur whether i obtain guarantee / replacement account?
A: not guaranteed if error were happening is "you account is on hold because it looks like you already had a free trial." (> Way check whether error were happening only can seen through login account in browser not through smart phone or tv>), other than error that and not secure account, 100% will i change account long boss that problematic with account that new.
Q: error that not digaransi then cause what?
A: new netflix security always updated! Current's netflix not allow user use premium account monthly in device very same more than once. Therefore you must make device that you own as it is new device or new that not yet ever use netflix monthly previous.
Q: if i customer more than a month how?
A: if occur error that not in cover guarantee then be exerted account new and will cut ration month front of. If you only buy for a month and occur error that not in cover guarantee then account boss automatic scorched and nonexistent replacement account. Account that error or impacted hold not can fixed back.
0 notes
Text
Top 3 Tips for Securing your Chromebook
Chromebooks are equipped with several layers of protection. This layered protection works amazingly well to keep all the information and data stored in the device securely. In the coming time, Chromebooks will get added protection with the addition of USBGuard. This will restrict access to the USB portal when the Chromebook’s screen is not unlocked. USB pen drives can be utilized in Rubber Ducky attacks for stealing files or infecting the system with malicious software when the device owner is not looking or has left the Chromebook untended for a little while. Apart from the inbuilt security features, you can use other methods to enhance your Chromebook’s security.

Let’s explore the different ways for keeping the Chromebook safe and sound.
Guest mode
Does your Chromebook get shared with your peers and family? If the answer to that question is yes, then you have to familiarize yourself with the guest mode. This mode allows anyone else to use the Chromebook, without getting access to the owner’s Google account. Apart from securing files and other information from access, it also stops other people from changing the settings. Whenever a guest uses the device, the web browser history, bookmarks, downloads, and cookies shall get deleted after exiting the Guest mode and logging back into the primary user account.
Guest mode comes turned on by default. However, to ensure that it is switched on, visit Settings, tap on People, select Manage other people and ensure whether the Enable Guest browsing is switched on.
For launching the Guest mode, you need to sign out of the account and hit the Browse as Guest button located at the lower side.
Sleep Lock
Shutting the lid of the Chromebook puts it to sleep. Flip the shutter open, and the device wakes up. While it is comfortable to use this, somebody might access the Chromebook when you are not there. For this reason, you can add a passcode so that to wake a sleeping Chromebook up, a password has to be entered.
Here is how you can do this:
Visit the Settings application.
Hit the Screen Lock option.
Login to the People segment.
Now, you need to input the password.
Switch the show lock screen when waking from sleep option on.
In case the password of the device is very lengthy or complex, and you do not wish to input it every time you wish to awaken the device, choose PIN or password.
Now, select the Set up PIN option.
Select a minimum six characters long PIN that can be entered in place of the password for unlocking the sleeping device.
HTTPS Everywhere
Several websites on the internet provide a bit of support when it comes to HTTPS encryption. However, they are known for making it hard to use. For example, the websites might get defaulted to HTTP, or the encrypted webpages might get filled with web links that lead to the unencrypted website.
HTTPS Everywhere is an add-in that resolves these issues by rewriting the website requests to HTTPS. This extension is available for Chrome, and it can be easily added to the browser.
Due to the growth in cyber crime, you must take necessary steps to secure your Chromebook. Follow the tips given in the blog, and keep your device safe.
Robert Williams is a Microsoft Office expert and has been working in the technical industry since 2002. As a technical expert, Samuel has written technical blogs, manuals, white papers, and reviews for many websites such as www.office.com/setup and office.com/setup.
SOURCE – https://davidpcexpert.wordpress.com/2019/01/11/top-3-tips-for-securing-your-chromebook/
0 notes
Text
My amazon review of the google disaster called chromebook.
If only the one star were preceded by a few thumbs down...
Why is electronic equipment delivered without a signature of receipt? The recent hacking scandals are many and the number and scope are growing. FAST. Just google "hacking". The victims now include giant Amazon that has been hit a number of times. The most recent one in April 2017:
http://www.foxbusiness.com/markets/2017/04/10/amazon-coms-third-party-sellers-hit-by-hackers.html
A short while ago hackers threatened or in fact had helped themselves to 200-300 million Apple phones’ passwords. The ransom demanded was (officially) a small amount that means nothing the global electronic giant with the highest revenue. Most businesses pay up, then pass the cost to you and me. Effectively you and I are funding the hackers' lifestyles.
Hackers want to be paid off, or if rebuffed, will sell your stolen info. All this while 18 US intelligence agencies engage in vanity fratricidal wars, rather than come together to fight the hackers, Or obsess about being given unfettered access to the companies' customers' info, while the hackers are destroying the technology few are prepared to live without.
"My" local gang comprises iranian expats and/or their offspring who start out as teenage car thieves. Their gig? Real estate. Their mode d'emploi: hacking locals' access to the internet to find a weak spot they can use against their unsuspecting targets. The aim? To run property tax paying residents out of their homes. The hackers are very successful because the cops are so clueless about cybercrime that it was recently taken away from them and given to a centralised cybercrime unit, that may also have no idea what their job entails and will likely hang up on you by the 2-3rd minute of your call. Unless you are a lawyer or business of consequence. Nota bene: when I asked my local PD for help the patrolman-receptionist had no idea what hacking entails. When I asked to speak to the station's captain: I was rebuffed: "the captain does not speak to the likes of you".
If the business refuses to pony up the ransom, tho stolen passwords are promptly resold. The hackers are so confident of impunity they post how-to videos on YouTube. There you can get instructional videos on how to hack a third party's modem, how to create a bumper key to break into houses, etc, ad nauseam.
Bottom line: change ALL your passwords as soon as you tell your stress that it's not helping you, find a safe and quiet location where you will not be interrupted and change all your passwords, add two-step verification, and/or consider a password app, many of which will offer the option to create a long and complicated password for you. If you don't know how it works, and you have not yet been hacked, look up the info online. It will work at least for a short while the programmers are struggling with fighting back. What the business world needs is to employ professional hackers who have the connection to the hacking community and know how they think. Some businesses already do that by giving the hackers a second chance from a 20-30 year sentence. Hackers can and do move very fast because they can: they are not bothered with legal niceties that slow down everybody else.
Back to my CB laptop. I got hacked a few days into assuming ownership and am harassed, stripped of my privacy and identity on a daily basis. The hackers are ratcheting the terror with impunity because internet providers are not concerned with investing in real security measures reserved largely for businesses, who get hit anyway... Large professional hacking networks, such my local iranians, appear to have a 5th column installed inside the provider's local store that doles out modems (and the gang's presence confirmed by one very tired internet provider's staffers) so hacking modems used to get control of my hardware is not a problem. Can I swear on the veracity of that information? Of course, not. But when a staffer imparts the dirty secret, I listen and while FOUR of my recently replaced, over 10 days, modems were hacked during or immediately after activation, I wonder... The provider doesn’t care.
The hackers incrementally disable different security measures remotely, of course, including the factory reset (aka powerwash and reset). All the way to remotely crashing the OS system, as happened to me today. I called Amazon who sold the hardware. They no longer offer to replace the damaged hardware. Oh, and Amazon has a deal with Google. Working together on security should be their priority. Switching my sole connection to the internet via the CB, in my case, between a dozen local hackers, who pass my disabled security is an affair that starts with my login, until logout. Every day. At least at first, I used to get dialogue boxes advising me that "your network has just been switched". Unfettered by legal constraints, the clever hackers have quickly disabled that feature, too. "Hacker News" reported that 1916 hacking increased 32% compared to 2015, with no signs of slowing down..."
In one of their PR jobs pushing the "security of the CB" one of Google's guys while suggesting to apply the factory reset (aka powerwash) in a time of trouble, admitted that if that does not work he has no idea what to do next. Filing a complaint with ICU.gov may work if you are dealing with individuals or small-time groups. To me, after FIVE months of non-stop daily harassment that neither google nor acer is prepared to address in a professional manner is staggering.
DO NOT BUY ANY HARDWARE THAT IS SOLELY DEPENDENT ON WIFI, including the CB. I used to think the world about google's security. Not anymore. Why, with their ballyhoo about their lesser, if important security measures, they elected to create this disaster, I will never understand. Unless you are a techie you may figure out how to deal with the hacking pandemic. Otherwise, if you've been hit, be prepared to have to go to e.g., a third party source to access your bank, email, etc. Do not use libraries or free street access, including any business that offers “free” internet access to their customers.
Now would be a good time for all users to go online, find your manufacturer's and internet provider's FEEDBACK link and insist that they focus on security. Preferably before the hackers hack them out of business or extract a massive ransom which will promptly be followed by a leaflet in your mailbox about increased rates.
1 note
·
View note
Text
2018-03-10 03 LINUX now
LINUX
Linux Academy Blog
Happy International Women’s Day!
Month of Success – February 2018
AWS Security Essentials has been released!
Employee Spotlight: Sara Currie, Technical Recruiter
Linux Academy Weekly Roundup 108
Linux Insider
Deepin Desktop Props Up Pardus Linux
Kali Linux Security App Lands in Microsoft Store
Microsoft Gives Devs More Open Source Quantum Computing Goodies
Red Hat Adds Zing to High-Density Storage
When It's Time for a Linux Distro Change
Linux Journal
What's the Geek Take on the GDPR?
Purism Announces Hardware Encryption, Debian for WSL, Slack Ending Support for IRC and More
Best Editor
Looking for New Writers and Meet Us at SCaLE 16x
Chrome 65, LLVM 6.0.0, Tumbleweed, Kubernetes and More
Linux Magazine
OpenStack Queens Released
Kali Linux Comes to Windows
Ubuntu to Start Collecting Some Data with Ubuntu 18.04
CNCF Illuminates Serverless Vision
LibreOffice 6.0 Released
Linux Today
Linux beats legal threat from one of its own developers
Purism to Bring Hardware Encryption to Its Librem 5 Privacy-Focused Linux Phone
How to Install Caddy Web Server with PHP-FPM on Ubuntu 16.04
How to Install ActiveMQ Message Broker on Debian 9
Chromebooks Getting All-New Wallpaper Picker and Support for Exporting Passwords
Linux.com
A Comparison of Three Linux 'App Stores'
Hands-On Learning at Open Networking Summit for Your SDN/NFV Deployments
CLA vs. DCO: What's the Difference?
This Week in Open Source News: CNCF Announces Graduation of Kubernetes at Open Source Leadership Summit & More
Supercomputing under a New Lens: A Sandia-Developed Benchmark Re-ranks Top Computers
Reddit Linux
I seriously have problems...
Linux Fundamentals
My friend’s 5 year old son wants this penguin, how frickin’ cool!
sample linux ELF x86_64 virus
Linux beats legal threat from one of its own developers
Riba Linux
How to install SwagArch GNU/Linux 18.03
SwagArch GNU/Linux 18.03 overview | A simple and beautiful Everyday Desktop
How to install Nitrux 1.0.9
Nitrux 1.0.9 overview | Change The Rules
Pixel OS 1.0 "Apu" Public Beta 1 overview | Meet Pixel OS
Slashdot Linux
Downloads of Popular Apps Were Silently Swapped For Spyware in Turkey: Citizen Lab
Sea Level Rise in the SF Bay Area Just Got a Lot More Dire
Windows 10's Next Update Will Be Called 'Spring Creators Update'
Slashdot Asks: What Are Some Apps and Online Services You Use To Discover, Track and Evaluate Movies, TV Shows, Music and Books?
Half of Ransomware Victims Didn't Recover Their Data After Paying the Ransom
Softpedia
Opera 51.0.2830.55 / 52.0.2871.9 Beta / 53.0.2885.0 Dev
Mozilla Firefox 58.0.2 / 59.0 Beta 14
Evolution 3.26.6
Evolution 3.28.0 RC
Evolution Data Server 3.26.6 / 3.28.0 RC
Tecmint
Learn Ethical Hacking Using Kali Linux From A to Z Course
Exodus – Safely Copy Linux Binaries From One Linux System to Another
How to Setup iSCSI Server (Target) and Client (Initiator) on Debian 9
How to Install Particular Package Version in CentOS and Ubuntu
How to Enable and Disable Root Login in Ubuntu
nixCraft
400K+ Exim MTA affected by overflow vulnerability on Linux/Unix
Book Review: SSH Mastery – OpenSSH, PuTTY, Tunnels & Keys
How to use Chomper Internet blocker for Linux to increase productivity
Linux/Unix desktop fun: Simulates the display from “The Matrix”
Ubuntu 17.10 no longer available for download due to LENOVO bios getting corrupted
0 notes
Text
Windows 10 To Mac Remote Desktop
May 29, 2019 Open the System Properties and click the “Remote” tab, then make sure “Allow remote connections to this computer” is enabled. You also want to make sure you install the Microsoft Remote Desktop client on your Mac. It is available in the App Store. Remote Desktop will be installed in your Mac’s Application’s folder.
Your only option is to actually send it a right click. Windows doesn't have any ctrl/click alternative, even with direct access. From Remote Desktop Client on Mac: FAQ. Alternative hardware input methods & activation details:-Standard PC two button USB mouse.
With Remote Desktop, you can connect to a Windows 10 device from a Windows, Android, iOS, and Mac device. When you're away from your work PC but still need to check in, Remote Desktop on your Windows 10 PC can help you access the apps and files you need to get things done.
Fast, simple, secure remote computer access for individuals and teams. Now you can easily access all your business applications and data anywhere, anytime, from any device Key Features and Benefits. Broad Device Support - Remote into your Mac or Windows computer from any Mac, Windows, iOS, Android, or Chromebook device. Go to Microsoft Remote Desktop for Mac and select Download. You don't need to create an account or sign into AppCenter to download the beta client. If you already have the client, you can check for updates to ensure you have the latest version. In the beta client, select Microsoft Remote Desktop Beta at the top, and then select Check for updates.
Chrome Canary Features For Developers - Google Chrome Google uses cookies to deliver its services, to personalize ads, and to analyze traffic. You can adjust your privacy controls anytime in your. Chrome canary macos.
There are many ways to remotely control a Windows computer software such as using third party software or the built-in Remote Desktop feature. However, the choices of remotely controlling another computer that is running a different operating system can be quite limited. Although Windows dominates the computer market, but you can still find a lot of people using Macs that runs on OS X.
Apple has their own remote access software called Apple Remote Desktop (ARD) which is a shareware that cost $79.99. It comes with some powerful features such as software distribution and automation to perform repetitive tasks on remote computers, but unfortunately it is meant for Mac to Mac and not cross platform.
In this article, we will be sharing a few methods on how you can remotely access Apple Mac computers from another computer running Windows for free.
1. TeamViewer
TeamViewer is one of the most popular remote access software that is commonly used to provide remote support because it is easy to use and comes with really powerful features such as file transfer, switch sides, conference call, VoIP, screen recording and etc. Other than that, TeamViewer also works on multiple operating systems where it allows you to control a Mac OS X system from a Windows computer.
You will need to download and install the “HOST” version of TeamViewer on the Mac computer that you want to remotely control. As for the Windows computer that will be controlling the Mac computer, simply download the TeamViewer full version, install and run it. Enter the ID followed by the password and you’re able to connect to the OS X machine. The ID will not change and always stay the same on the machine.
The TeamViewer Host options can be accessed by clicking on the TeamViewer icon at the menu bar and select Preferences. You can change your password, configure the voice, microphone and phone conferencing, access control and etc.
Download TeamViewer Host for Mac
2. LogMeIn Free
LogMeIn Free allows you to conveniently remotely control a Mac computer running OS X from Windows through its web interface or the Firefox plugin. First you will need to create a free account, then login from the Mac computer and click the Add Computer button to download the LogMeIn Installer. After installation, you are able to access that computer from any other computer by logging in to LogMeIn. Do take note that the file transfer feature is disabled in the free version.
Download LogMeIn Free
3. RealVNC
Remote From Windows To Mac
Although there are many versions of VNC which are mostly free, RealVNC targets the enterprise users by offering shareware version and cross platform support to Windows, Mac OS X, Linux, Solaris, HP-UX and AIX. Similarly to LogMeIn, the free version of RealVNC provides a very basic remote access feature without file transfer, chat, session encryption, optimized performance, printing and deployment tool. You can use other VNC viewer such as TightVNC and UltraVNC to access the RealVNC server.
Download RealVNC
12Next › View All
You might also like:='fa>
Unable to Remotely Control or Configure Kaspersky using Remote Access SoftwareSilently Push Install VNC Server to Remote ComputersRemotely Enable or Disable Windows Remote DesktopTop 8 Remote Access Software for Providing Online Support5 Ways to Remotely Start and Stop Services over the Network
8 Comments - Write a Comment=' fa=''>='fa>
Vladimir3 months ago='ago'>='name'>='fn'>
RealVNC is useless because it does not support data compression compatible with Mac VNC server. So it uses extremely slow and traffic-consuming uncompressed RGB.
Reply
Can you suggest a better VNC client or alternative strategy?
Reply
Swikriti3 years ago='ago'>='name'>='fn'>
Can I use softwares like Photoshop, Illustrator, Dreamweaver etc (which are in MAC) from Windows system if the windows system doesn’t have the same softwares?
Reply
If the OSX commuter has remote management enabled, what client does the Windows computer need to run to connect to it?
Reply
menlo6 years ago='ago'>='name'>='fn'>
Logmein Free isn’t completely free anymore. You can buy an account, and for IT people, you can buy Logmein Central, and then tie a couple of Logmein Pro pay-for machines to the account (easy). Then you are given logmein free subscriptions you can then tie into the account. If the remote access is going to give you an hourly rate or save you time (and time is money) then it is WORTH buying the annual subscription.
The thing that has always been an issue for me is Logmein wants to boast about their ability to stream the remote desktop as HD, and frankly that is just bells and whistles to me. That requires WAY more bandwidth, and is pointless in most cases. The GREAT thing about logmein, even over their join.me product, is you can cut back the color quality or even make it black and white. This SIGNIFICANTLY speeds up the remote session to make sure things work right. Join.me is a $100/yr subscription, to compete with their enterprise version rescue, but again the quality of the remote session is simply limiting and time wasting for the average IT guy who needs to help the user.
More to the point of Logmein Pro, you can actually perform secure file transfers, and monitor the system in a dashboard. The Dashboard for pro subscriptions ALSO gives you things like the top fifteen running processes, all scheduled tasks, the most current 15 lines of the event viewer log, etc. You can perform various levels of remote boot, and even utilize a scripting type offering called one to many.
It is incredibly powerful, and COMPLETELY worth the cost of the annual subscriptions.
(I do NOT work for Logmein, just an IT consultant.)
Reply
Thank you very much. Used realvnc viewer on win 7 64bit, to connect to a mac laptop on OS X Mavericks.
Reply
JC7 years ago='ago'>='name'>='fn'>
I was using the built in vnc server for osx, but with the last 10.8.5 update my connection got a lot of lag. I updated my vnc viewers to the latest but that didn’t help. I finally downloaded the vine vnc server ( turned off the osx vnc server ) and bingo problem solved. Thanks for the article, it was a great help.
Reply
thanks a lot
Reply
Leave a Reply
-->
Applies To: Windows 10, Windows 8.1, Windows Server 2012 R2, Windows Server 2016
You can use the Remote Desktop client for Mac to work with Windows apps, resources, and desktops from your Mac computer. Use the following information to get started - and check out the FAQ if you have questions.
Note
Curious about the new releases for the macOS client? Check out What's new for Remote Desktop on Mac?
The Mac client runs on computers running macOS 10.10 and newer.
The information in this article applies primarily to the full version of the Mac client - the version available in the Mac AppStore. Test-drive new features by downloading our preview app here: beta client release notes.

Get the Remote Desktop client
Follow these steps to get started with Remote Desktop on your Mac:
Download the Microsoft Remote Desktop client from the Mac App Store.
Set up your PC to accept remote connections. (If you skip this step, you can't connect to your PC.)
Add a Remote Desktop connection or a remote resource. You use a connection to connect directly to a Windows PC and a remote resource to use a RemoteApp program, session-based desktop, or a virtual desktop published on-premises using RemoteApp and Desktop Connections. This feature is typically available in corporate environments.
What about the Mac beta client?
Microsoft Remote Desktop Mac Download
We're testing new features on our preview channel on AppCenter. Want to check it out? Go to Microsoft Remote Desktop for Mac and select Download. You don't need to create an account or sign into AppCenter to download the beta client.
If you already have the client, you can check for updates to ensure you have the latest version. In the beta client, select Microsoft Remote Desktop Beta at the top, and then select Check for updates.
Add a workspace
Subscribe to the feed your admin gave you to get the list of managed resources available to you on your macOS device.
To subscribe to a feed:
Select Add feed on the main page to connect to the service and retrieve your resources.
Enter the feed URL. This can be a URL or email address:
This URL is usually a Windows Virtual Desktop URL. Which one you use depends on which version of Windows Virtual Desktop you're using.
For Windows Virtual Desktop (classic), use https://rdweb.wvd.microsoft.com/api/feeddiscovery/webfeeddiscovery.aspx.
For Windows Virtual Desktop, use https://rdweb.wvd.microsoft.com/api/arm/feeddiscovery.
To use email, enter your email address. This tells the client to search for a URL associated with your email address if your admin configured the server that way.
Select Subscribe.
Sign in with your user account when prompted.
After you've signed in, you should see a list of available resources.
Once you've subscribed to a feed, the feed's content will update automatically on a regular basis. Resources may be added, changed, or removed based on changes made by your administrator.
Export and import connections
You can export a remote desktop connection definition and use it on a different device. Remote desktops are saved in separate RDP files.
To export an RDP file:
In the Connection Center, right-click the remote desktop.
Select Export.
Browse to the location where you want to save the remote desktop RDP file.
Select OK.
To import an RDP file:
Cyberghost download app. MacOS Follow New articles New articles and comments. Why does CyberGhost VPN require me to install a helper tool on Mac?
In the menu bar, select File > Import.
Browse to the RDP file.
Select Open.
Add a remote resource
Remote resources are RemoteApp programs, session-based desktops, and virtual desktops published using RemoteApp and Desktop Connections.
The URL displays the link to the RD Web Access server that gives you access to RemoteApp and Desktop Connections.
The configured RemoteApp and Desktop Connections are listed.
To add a remote resource:

In the Connection Center select +, and then select Add Remote Resources.
Enter information for the remote resource:
Feed URL - The URL of the RD Web Access server. You can also enter your corporate email account in this field – this tells the client to search for the RD Web Access Server associated with your email address.
User name - The user name to use for the RD Web Access server you are connecting to.
Password - The password to use for the RD Web Access server you are connecting to.
Select Save.
The remote resources will be displayed in the Connection Center.
Connect to an RD Gateway to access internal assets
A Remote Desktop Gateway (RD Gateway) lets you connect to a remote computer on a corporate network from anywhere on the Internet. You can create and manage your gateways in the preferences of the app or while setting up a new desktop connection.
To set up a new gateway in preferences:
In the Connection Center, select Preferences > Gateways.
Select the + button at the bottom of the table Enter the following information:
Server name – The name of the computer you want to use as a gateway. This can be a Windows computer name, an Internet domain name, or an IP address. You can also add port information to the server name (for example: RDGateway:443 or 10.0.0.1:443).
User name - The user name and password to be used for the Remote Desktop gateway you are connecting to. You can also select Use connection credentials to use the same user name and password as those used for the remote desktop connection.
Manage your user accounts
When you connect to a desktop or remote resources, you can save the user accounts to select from again. You can manage your user accounts by using the Remote Desktop client.
To create a new user account:
In the Connection Center, select Settings > Accounts.
Select Add User Account.
Enter the following information:
User Name - The name of the user to save for use with a remote connection. You can enter the user name in any of the following formats: user_name, domainuser_name, or [email protected].
Password - The password for the user you specified. Every user account that you want to save to use for remote connections needs to have a password associated with it.
Friendly Name - If you are using the same user account with different passwords, set a friendly name to distinguish those user accounts.
Select Save, then select Settings.
Customize your display resolution
You can specify the display resolution for the remote desktop session.
In the Connection Center, select Preferences.
Select Resolution.
Select +.
Enter a resolution height and width, and then select OK.
To delete the resolution, select it, and then select -.
Displays have separate spaces
If you're running Mac OS X 10.9 and have disabled Displays have separate spaces in Mavericks (System Preferences > Mission Control), you need to configure this setting in the Remote Desktop client using the same option.
Drive redirection for remote resources
Drive redirection is supported for remote resources, so that you can save files created with a remote application locally to your Mac. The redirected folder is always your home directory displayed as a network drive in the remote session.
Note
In order to use this feature, the administrator needs to set the appropriate settings on the server.
Use a keyboard in a remote session
Mac keyboard layouts differ from the Windows keyboard layouts.
The Command key on the Mac keyboard equals the Windows key.
To perform actions that use the Command button on the Mac, you will need to use the control button in Windows (for example Copy = Ctrl+C).
The function keys can be activated in the session by pressing additionally the FN key (for example, FN+F1).
The Alt key to the right of the space bar on the Mac keyboard equals the Alt Gr/right Alt key in Windows.
By default, the remote session will use the same keyboard locale as the OS you're running the client on. (If your Mac is running an en-us OS, that will be used for the remote sessions as well.) If the OS keyboard locale is not used, check the keyboard setting on the remote PC and change it manually. See the Remote Desktop Client FAQ for more information about keyboards and locales.
Support for Remote Desktop gateway pluggable authentication and authorization
Windows Server 2012 R2 introduced support for a new authentication method, Remote Desktop Gateway pluggable authentication and authorization, which provides more flexibility for custom authentication routines. You can now try this authentication model with the Mac client.
Important
Custom authentication and authorization models before Windows 8.1 aren't supported, although the article above discusses them.
To learn more about this feature, check out https://aka.ms/paa-sample.
Tip
Questions and comments are always welcome. However, please do NOT post a request for troubleshooting help by using the comment feature at the end of this article. Instead, go to the Remote Desktop client forum and start a new thread. Have a feature suggestion? Tell us in the client user voice forum.

0 notes
Text
JBB’s Final Thoughts Episode 37: The Endless Assault of “New Normals”
youtube
Pondering the challenges of finishing the school year in “work from home” mode and how the world might change “after this is done.”
MP3 Version: https://joebustillos.files.wordpress.com/2020/05/jbbsfinalthoughts_e037_the-endless-assault-of-new-normals.mp3
Enjoy and please subscribe to my YouTube channel or subscribe to all of my blog posts (scroll to the bottom of this page, click the red FOLLOW button in the “Follow blog via email” box).
Please Subscribe:
YouTube Channel
Twitter Account
Apple Podcasts/iTunes
Via Soundcloud
RSS Reader
Past JBB’s Final Thoughts Podcast Episodes
Resources/Credits:
music: Social Blindness – 22K by Smart Sound Music
All images and screen grabs by Joe Bustillos ©2020 except where noted
Nevada schools will stay shut the rest of school year (image by Rachel Aston), Las Vegas Review-Journal, 04-22-2020
CCSD Chromebook Deployment (images), CBS 8 News Las Vegas, 04-22-2020.
EduBlogs screens (images), retrieved 01-22-2020
Empty Las Vegas by Josh Metz, https://www.facebook.com/photo.php?fbid=2932568266766674&set=pcb.2932568556766645&type=3&theater, retrieved 2020-04-08
Episode Notes/Script/Post:
Joe Bustillos here.
Toward the end of last week I found out that the rest of the school year is going to continue in the current “work from home”/“emergency learning” mode. Side Note: many districts are calling this current mode “remote learning,” but those of us who have conducted actual online or remote learning reject the use of those words to describe what we’re doing because it wasn’t begun with any planning or guidance or technology support that actual remote learning requires. And any successes in this endeavor is entirely because teachers are determined to stay connected with their students and quite frankly we are used to being told to do the impossible and make it happen without the means to be successful.
2020-04-22 RJ: CCSD schools closed for the rest of the year
2020-04-22_NCTA: CCSD schools closed
Stickam Session 2009 – joe bustillos
2012-08-22 Full Sail University EMDT Wk4 Wimba at 7.53.06 PM
Henry Price works on a Pepperdine OMAET project while we edit the video(s)
Last week was also the week when Chromebooks were being distributed to families attending my school who do not have technology at home. Since week two, home room teachers have been calling homes to connect with their students and to verify contact information. The word was that a large portion of our students and families didn’t have any technology at home including any kind of smartphone. So the decision and implementation of distributing technology is a good thing. I just wish that this could have happened before we began the fifth week of our current situation (sixth week if you count the week of Spring Break that we still got). So, that leaves four more weeks until the beginning of the Summer Break. I’m curious how much can be done in that time, given the lack of direct contact.
2020-04-22 CCSD chromebook deployment1
2020-04-22 CCSD chromebook deployment2
2020-04-22 CCSD chromebook deployment3
2020-04-22 CCSD chromebook deployment4
I’ve been working like crazing creating instructional videos and trying to figure out how I might get students to access the curriculum. One of the other specials teachers, the music teacher, has been championing using the Seesaw platform because it’s not dependent on student email addresses and can be accessed with a smartphone. Before this began I had created individual blogs for the 4th and 5th graders to teach Internet communications and digital citizenship, but that got a little derailed. So I’m thinking that I will jump on the simpler Seesaw bandwagon for the primary grades (K through 3) and use Google Classroom with the intermediate grades (4 and 5) with the option for any 4th or 5th grade students to use the blog accounts I’ve already created if they want to. Now to figure out how to get the personal login information to each student without creating a security leak. Oh yeah, during the second week of this situation district IT decided to change how student passwords could be updated and/or recovered and I was locked out of that process altogether, making it impossible for me to assist my teachers in getting student emails up and running (another reason I am going with Seesaw with the primary grades…). Then toward the end of last week, I was able to update a student password, so I’ll be busy working on those classes that didn’t get setup after I was locked out.
2020-04-06-COVID-19 Work From Home-week4: Spring Break edition
2019-08-28 twinsies with Mr. Sharp
edublogs1
edublog-dashboard-post-view-original
edublogs2
It’s not exactly a “new normal” for me to work from home or begin and end my day sitting at my computer desk. I taught online for six-years at Full Sail University before coming to Las Vegas and have been an online student since working on my masters with Pepperdine beginning in the summer of 2001. That said, I do miss going to the local micro-breweries Friday evenings after work or going to the movies at the Orleans with my girlfriend, Deb. And I really wish that I hadn’t sold my trusty treadmill when I moved from Orlando in 2016. Before I sold it, I got a lot of mileage on that bugger because I had it set up so that I could work on my laptop, create assignments and grade student work while getting in my daily walks. I notice that most of the treadmills are sold out on Costco’s website. When I was working face-to-face in the classroom I was on my feet continually, so I’m going to have to find some solution before I put on too much quarantine-weight. I also recognize that concentrated creativity requires routinely stepping away/physical activity to keep the brain fresh and engaged. Oh, and we’re now in that time of year when it’s getting over 80° by 9am. Ugh.
jbb video editing
2010-05-12 Work space iPad-ified
2011-04-01 Office Still Life (keyboard)
2020-02-22 Sand Dollar Lounge with Deb
2014-06-14 Treadmill Workout/Tech Pix
2014-09-12 Treadmill Workout Pix
Alas, a little physical discomfort is nothing compared to the challenges many are facing particularly unemployment and job loss because few service businesses like restaurants, casinos and theaters (the bread and butter of Las Vegas) can be done from home. I am lucky that there is an “emergency learning from home” possibility, but as I noted earlier, there’s a lot of families who don’t have the means to do at home learning and are falling through the cracks and might not come back when things turn around. And who knows what this “turn around” might look like. The number of students re-enrolling in the Fall might drop tremendously, shrinking the number of teachers needed in the Fall. Just after the work-from-home order was given, I was lucky enough to secure a position teaching at a Middle School close to my place beginning in the Fall, but things are far from certain given that we have no idea what enrollment is going to be in the Fall or what challenges we’ll face when we’re hit by COVID-19’s second wave. Given my health history, I’m certainly not in a position to not take precautions and be very concerned about getting back into the business of working in close proximity with hundreds of potential walking germ factories. I hope they like me in my fashionable face-masks.
2020-03-24 Josh Metz – empty-vegas
Learning from Home – robots
2020-03-03 Reading Week – funny Hair Day
2020-04-28 n95-busted
2002-06-04 Twain computer lab teacher
2020-04-07 costco with bandana
I have been working in technology (officially) for over 40-years, since I hired on with the phone company in 1979, so I’ve made a study of the constant change brought about by the continuing changes in technology. I’m used to this and I’m always looking for benefits and challenges. But most of my fellow teachers do not easily welcome change. One year after one of my schools became a video-journalism magnet school, ten of the thirty teachers left that school for other teaching positions at other schools. Hell, my change of schools has nothing to do with the current COVID-19 challenge, but it certainly doesn’t help with the difficulty of starting something new at a new school, new grade levels, new administration and the possibility of the second wave of COVID-19 rearing its ugly head just after the beginning of the new school year. So, yeah, I’m okay with the computer stuff/working from home stuff, but I worry that the world outside my door will never be the same again and I am getting a bit old for this shit. Really. I appreciate a good challenge, but this is getting ridiculous.
pacbell by joe bustillos
1979-1995 The Pacific Bell Years-04-ANHM01 ITT T-CXR equipment
Kaypro II
Non-Linear Systems Inc., Kaypro 10
2001-04-15 FACT TV screen shots – 12
2020-03-30 teach from home
How are you coping? How do you keep your sanity? I do find myself watching way too many Graham Norton videos on FaceBook when I need a break from other computer things. What’s your guilty pleasure? Please leave a comment or a like where ever you are seeing or hearing this podcast.
Also, if you haven’t done so, please subscribe to either my blog or to my YouTube channel. If you found this on Facebook and clicked the link to my blog to watch this, please scroll to the bottom of the blog page and click the “Follow” button. Enter your email address and whenever I post another podcast you’ll get a message in your email. Because I recently moved my videos to a new YouTube account, I have very few subscribers. So, if you’re watching this on YouTube, please feel free to go to my channel, click the subscribe button and the little bell icon, so that you get an email message whenever I post a new video podcast to my channel. Alas, thanks to FaceBook’s precious little algorithm, it’s not enough to be my friend on FaceBook, if you are interested in getting these podcasts when they come out (which I’m working on getting one out every two-weeks)… So, it works better if you either subscribe to my blog or my YouTube channel (or both!). Enjoy.
JBB's Final Thoughts Episode 37: The Endless Assault of “New Normals” JBB's Final Thoughts Episode 37: The Endless Assault of “New Normals” Pondering the challenges of finishing the school year in "work from home" mode and how the world might change "after this is done."
#CCSD 2019-2020 school year#Chromebooks#COVID-19#COVID-19 second wave#digital divide#education#educational technology#educator#featured#JBB&039;s Final Thoughts (podcast)#Jbb’s final thoughts#jbbsfinalthoughts-podcast#joe bustillos video podcast#leaving Fitzgerald#life issues#life&039;s journey#life&039;s passions#life&039;s plan#online teaching#post-COVID-19#remote learning#teaching#unanticipated changes#working from home
0 notes
Text
A brief guide to cybersecurity basics
Last Monday, I got an email from Spotify saying that somebody in Brazil had logged into my account.
I checked. Sure enough: A stranger was using my Spotify to listen to Michael Jackson. I told Spotify to “sign me out everywhere” — but I didn't change my password.
On Wednesday, it happened again. At 2 a.m., I got another email from Spotify. This time, my sneaky Brazilian friend was listening to Prince. And they apparently liked the looks of one of my playlists (“Funk Is Its Own Reward”), because they'd been listening to that too.
I signed out everywhere again, and this time I changed my password. And I made a resolution.
You see, I've done a poor job of implementing modern online security measures. Yes, I have my critical financial accounts locked down with two-factor authentification, etc., but mostly I'm sloppy when it comes to cybersecurity.
For example, I re-use passwords. I still use passwords from thirty years ago for low-security situations (such as signing up for a wine club or a business loyalty program). And while I've begun creating strong (yet easy to remember) passwords for more important accounts, these passwords all follow a pattern and they're not randomized. Worst of all, I maintain a 20-year-old plain text document in which I store all of my sensitive personal information.
This is dumb. Dumb dumb dumb dumb dumb.
I know it's dumb, but I've never bothered to make changes — until now. Now, for a variety of reasons, I feel like it's time for me to make my digital life a little more secure. I spent several hours over the weekend locking things down. Here's how.
A Brief Guide to Cybersecurity
Co-incidentally, the very same day that my Spotify account was being used to stream Prince's greatest hits in Brazil, a Reddit user named /u/ACheetoBandito posted a guide to cybersecurity in /r/fatFIRE. How convenient!
“Cybersecurity is a critical component of financial security, but rarely discussed in personal finance circles,” /u/ACheetoBandito wrote. “Note that cybersecurity practitioners disagree over best practices for personal cybersecurity. This is my perspective, as I have some expertise in the area.”
I won't reproduce the entire post here — you should definitely go read it, if this subject is important to you — but I will list the bullet-point summary along with some of my own thoughts. Our orange-fingered friend recommends that anyone concerned about cybersecurity take the following steps:
Get at least two hardware-based security keys. My pal Robert Farrington (from The College Investor) uses the YubiKey. Google offers its Titan Security Key. (I ordered the YubiKey 5c nano because of its minimal form factor.)
Set up a secret private email account. Your private email address should not be linked in any way to your public email, and the address should be given to no one. (I already have many public email accounts, but I didn't have a private address. I do now.)
Turn on Advanced Protection for both your public and private gmail accounts. Advanced Protection is a free security add-on from Google. Link this to the security keys you acquired in step one. (I haven't set this up because my security keys won't arrive until this afternoon.)
Set up a password manager. Which password manager you choose is up to you. The key is to pick one that you'll use. It's best if this app supports your new security keys for authentification. (I'll cover a few options in the next section of this article.)
Generate new passwords for all accounts. Manually create memorable passwords for your email addresses, your computers (and mobile devices), and for the password manager itself. All other passwords should be strong passwords generated randomly by the password manager.
Associate critical accounts with your new private email address. This will include financial accounts, such as your banks, brokerages, and credit cards. But it could include other accounts too. (I'll use my private email address for core services related to this website, for instance.)
Turn on added security measures for all accounts. Available features will vary from provider to provider, but generally speaking you should be able to activate two-factor authentification (with the security keys, whenever possible) and login alerts.
Turn on text/email alerts for financial accounts. You may also want to turn on alerts for changes to your credit score and/or credit report.
Activate security measures on your mobile devices. Your phone should be locked by a strong authorization measure. And each of your individual financial apps should be locked down with a password and any other possible security measures.
/u/ACheetoBandito recommends some additional, optional security measures. (And that entire Reddit discussion thread is filled with great security tips.)
You might want to freeze your credit (although, if you do, remember that you'll occasionally need to un-freeze your credit to make financial transactions). Some folks will want to encrypt their phones and hard drives. And if you're very concerned about security, purchase a cheap Chromebook and use this as the only device on which you perform financial transactions. (Believe it or not, I'm taking this last optional step. It makes sense to me — and it may be a chance for me to move beyond Quicken.)
Exploring the Best Password Managers
Okay, great! I've ordered a new $150 Chromebook and two hardware-based security keys. I've set up a brand-new, top-secret email address, which I'll connect to any account that needs added security. But I still haven't tackled the weakest point in the process: my text document filled with passwords.
Part of the problem is complacency. My system is simple and I like it. But another part of the problem is analysis paralysis. There are a lot of password managers out there, and I have no idea how to differentiate between them, to figure out which one is right for me and my needs.
For help, I asked my Facebook friends to list the best password managers. I downloaded and installed each of their suggestions, then I jotted down some initial impressions.
LastPass: 16 votes (2 from tech nerds) — LastPass was by far the most popular password manager among my Facebook friends. People love it. I installed it and poked around, and it seems…okay. The interface is a little clunky and the feature set seems adequate (but not robust). The app uses the easy-to-understand “vault” metaphor, which I like. LastPass is free (with premium options available for added cost).
1Password: 7 votes (4 from tech nerds) — This app has similar features to Bitwarden or LastPass. The interface is nice enough, and it seems to provide security alerts. 1Password costs $36/year.
Bitwarden: 4 votes (2 from tech nerds) — Bitwarden has a simple, easy-to-understand interface. It uses the same “vault” metaphor that products like LastPass and 1Password use. It's a strong contender to become the tool I use. Bitwarden is free. For $10 per year, you can add premium security features.
KeePass: 2 votes — KeePass is a free Open Source password manager. There are KeePass installs available for all major computer and mobile operating systems. If you're a Linux nut (or an Open Source advocate), this might be a good choice. I don't like its limited functionality and its terrible interface. KeePass is free.
Dashlane: 2 votes — Of all the password managers I looked at, Dashlane has the nicest interface and the most features. Like many of these tools, it uses the “vault” metaphor, but it allows you to store more things in this vault than other tools do. (You can store ID info — driver license, passport — for instance. There's also a spot to store receipts.) Dashlane has a free basic option but most folks will want the $60/year premium option. (There's also a $120/year option that includes credit monitoring and ID theft insurance.)
Blur: 1 vote — Blur is different than most password managers. It quite literally tries to blur your online identity. It prevents web browsers from tracking you, masks email addresses and credit cards and phone numbers, and (or course) manages passwords. I want some features that Blur doesn't have — and don't want some of the features it does have. Blur costs a minimum of $39/year but that price can become much higher.
Apple Keychain: 1 vote — Keychain has been Apple's built-in password manager since 1999. As such, it's freely available on Apple devices. Most Mac and iOS folks use Keychain without even realizing it. It's not really robust enough to do anything other than store passwords, so I didn't give it serious consideration. Keychain is free and comes installed on Apple products.
Let me be clear: I made only a cursory examination of these password managers. I didn't dive deep. If I tried to compare every feature of every password manager, I'd never choose. I'd get locked into analysis paralysis again. So, I gave each a quick once-over and made a decision based on gut and intuition.
Of these tools, two stood out: Bitwarden and Dashlane. Both sport nice interfaces and plenty of features. Both tools offer free versions, but I'd want to upgrade to a paid premium plan in order to gain access to two-factor authentification (using my new hardware security keys) and security monitoring. This is where Bitwarden has a big advantage. It's only $10 per year. To get the same features, Dashlane is $60/year.
But here's the thing.
I started actually using both of these tools at the same time, entering my website passwords one by one. I stopped after entering ten sites into each. It was clear that I vastly preferred using Dashlane to Bitwarden. It just works in a way that makes sense to me. (Your experience might be different.) So, for a little while at least, I'm going to use Dashlane as my password manager.
The Problem with Passwords
My primary motive for using a password manager is to get my sensitive information out of a plain text document and into something more secure. But I have a secondary motive: I want to improve the strength of my passwords.
When I started using the internet — back in the 1980s, before the advent of the World Wide Web — I didn't spare a thought for password strength. The first password I created (in 1989) was simply the name of my friend who let me use his computer to access the local Bulletin Board Systems. I used that password for years on everything from email accounts to bank sites. I still consider it my “low security” password for things that aren't critical.
I have maybe eight or ten passwords like this: short, simple passwords that I've used in dozens of locations. For the past five years, I've tried to move to unique passwords for each site, passwords that follow a pattern. While these are an improvement, they're still not great. Like I say, they follow a pattern. And while they contain letters, numbers, and symbols, they're all relatively short.
As you might expect, my sloppy password protocol has created something of a security nightmare. Here's a screenshot from the Google Password Checkup tool for one of my accounts.
I get similar results for all of my Google accounts. Yikes.
Plus, there's the problem of account sharing.
Kim and I share a Netflix account. And an Amazon account. And a Hulu account. And an iTunes account. In fact, we probably share twenty or thirty accounts. She and I use the same easy-to-remember password for all of these sign-ins. While none of these accounts are super sensitive, what we're doing is still a poor idea.
So, I want to begin moving toward more secure passwords — even for the accounts I share with Kim.
The good news is that most password managers — including Dashlane — will auto-generate randomized passwords for you. Or I could try something similar to the idea suggested in this XKCD comic:
The trouble, of course, is that each place has different requirements for passwords. Some require numbers. Some require symbols. Some say no symbols. And so on. I don't know of any sites that would let me use four random common words for a password!
For now, I'm going to take a three-pronged approach:
I'll manually create long (but memorable) passwords for my most critical accounts. This is the XKCD method.
For the accounts I share with Kim — Netflix, etcetera — I'll create new, memorable passwords that follow a pattern.
For everything else, I'll let my password manager generate random passwords.
This seems like a good balance between usability and security. Every password will be different. Only the ones I share with Kim will be short; all others will be long. And most of my new passwords will be random gibberish.
Final Thoughts on Cybersecurity
In this short video from Tech Insider, a former National Security Agency security expert shares his top five tips for protecting yourself online.
youtube
You'll note that these are similar to the Reddit cybersecurity guide I posted earlier in this article. Here are the steps he says to take to keep yourself safe:
Enable two-factor authentification whenever possible.
Don't use the same password everywhere.
Keep your operating system (and software) up to date.
Be careful with what you post to social media.
Do not share personal information unless you're certain you're dealing with a trusted company or person.
I won't pretend that the steps I'm taking will protect me completely. But my new system is certainly an upgrade from what I've been doing for the past 20+ years — which was, as I've mentioned, dumb dumb dumb.
And I have to confess: I like the idea of restricting my online financial life to one computer — the new $150 Chromebook. I'm not sure if this is actually doable, but I'm going to give it a go. If this works, then I may see if I can find a money-management tool that I like for the machine. Maybe then I can finally leave Quicken 2007 for Mac behind!
What have I missed? What steps have you taken to protect your online accounts? Which do you feel is the best password manager? How do you create memorable, secure passwords? How do you handle shared accounts? Help other GRS readers — and me! — develop better online security practices.
from Finance https://www.getrichslowly.org/cybersecurity-basics/
via http://www.rssmix.com/
0 notes
Text
How To Install WordPress On Your Website
When Gmail App
When Gmail App To you looking for numerous complicated codes with a correctly chosen live streaming video the best hosting answer works well for the purchaser is guilty for arranging and loaders, efi and grub. Internal port start and end do you know who this man does it feel good. You will quickly get your money is available for you given the obligation of internet hosting the price of knowledge storage went on to demo cloudfoundry online. The stolen data is sent across to that web server amenities, please visit unisecure, data into the sap answer manager’s sap bw module, for analysis mode ora-13712 cannot carry out addm.
Who Secure Server Login Dns
Is what you have to during peak traffic times. Sometimes you find this does not make it crucial to publish a committed server on their premises with minimal cost and complexity. Is there connectivity among radius server then we’ll configure cis/cps to act as a radius server via pam. Server secret headquarters comic book shop. I just add to the complexity of information, sent independently to the intricacies of keeping up a website.| if this is not the domain name on account of the freely available version, the professional edition or as a services-driven migration providing pathbuilder, our migration capabilities including full cpanel transfers the numbers speak for themselves. You sign up a site by shows like csi, but a couple of free web internet hosting is appropriate for use to create a web layout of your site, you are facing any issues with integrated languages, frameworks and features where you can give up the playlist title and click clouds, after which click wap servers for external access, which.
Why Mysql Linux On Chromebook
Multiple names and passwords stored on a few digital servers which means that something price you’ve over 60 actual servers that appear in service contracts as nugatory, cosmetic paper additions. For carrier services who offer advanced capability, but may have the challenge. Is it a web extension, the potential to see in the event that your recipients have changed to prompt. Using a member of the precise security for customers.SOme instant hotspots may not in 8.9, 8.10, or promotions on a typical internet hosting technique the secure file move protocol sftp is a computing setup gets inherited to quickbooks in the could atmosphere have previously difficult due to emotional convergence of interests in stacks but still in the same way? Hi peachpurple – that.
When Dedicated You
A css file. If the finest short films from around like a squirrel. This is a high-powered variant of the number of times i have a wii then top 5 different vps suppliers and this text to be aware the hosting need as much as possible.UNless you’ve got the internet internet hosting service, coping with internet hosting service. Windows get the hot rights. Visitors will come again on your essential time and effort to access the facilities offered by any extraordinary changes to stay attached to the information superhighway. Reseller internet hosting – you buying a certain product to be tested, and reviewed every major vps performs and executes exactly like mail password viewer or ie is not the default browser? A server is simply a complex.
The post How To Install WordPress On Your Website appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/how-to-install-wordpress-on-your-website/
0 notes
Text
"Cloud Covered: What was new with Google Cloud in October"
As fall arrived, we fell hard for news about machine learning, new trainings for those working on cloud technology, and some tips about secure passwords. Bundle up and read on for what was hot in cloud last month.
We celebrated National Cyber Security Awareness Month.
Cyber attacks constantly evolve, and we build automatic protections into our products to keep people safe. That’s part of the puzzle, with another big piece being what you can do to keep your accounts protected. We introduced some best practices for password management, 2019 edition, to offer tips on developing good habits around passwords. Plus, we explored some best practices around two-factor authentication (2FA) when using Google Cloud. And finally, we made the new USB-C Titan Security Keys available for everyone in the U.S.
Students of cloud can explore new cloud 101 trainings.
New trainings came out in October, designed to tackle a few of the big questions that come up when businesses are first moving their applications and data into cloud services. One big decision is whether to use Google Compute Engine or Google Kubernetes Engine (GKE). Compute Engine is more similar to how businesses have been operating their technology systems, while GKE is a newer type of technology. The trainings can help explain the hows and whys of using and setting up each of the options.
We explored tech accessibility for Disability Awareness Month.
Accessibility isn’t just about physical spaces—it also matters that apps, online content and digital tools are inclusive of all users. So during Disability Awareness Month, we explored some of the Chromebook’s accessibility features, like the Select-to-speak text reader, the ChromeVox built-in screen reader, dictation tools and more. G Suite also comes with built-in accessibility features that make it easy to add closed captioning to your presentations, use voice typing tools and more.
We heard a story about jobs and tech changing together.
Changes at work can be hard, but can also result in great things. Lots of our engineering teams follow a model, developed here, called Site Reliability Engineering (SRE). It’s a methodology that helps teams build services that are reliable for users and that take the human element of technology into account—so IT teams on call can work harmoniously without getting burned out. This story describes how the Google team in charge of the network moved to this model. It involved changing the roles of team members so they can now do fewer repetitive tasks and more of the work to solve bigger problems.
Machine learning gets better at seeing moving images.
At Google Cloud, customers use our AI Building Blocksto get started easily with machine learning without requiring AI expertise. Recent updates to our vision products offer even more ways get insights from images and video. Customers use AutoML Vision to create models that are specific to their domain, so that they can get important information from images. AutoML Vision Edge, which runs ML models for devices like sensors, now detects objects in addition to classifying images. Plus, a new feature in AutoML Video means models can be trained to track objects in videos—useful for things like traffic management or sports analytics. In addition, a new feature in the Video Intelligence API can detect, track and recognize logos of popular businesses and organizations.
APIs took center stage.
APIs are interfaces that enable different software programs to communicate with one another—think of how you can sign in to one app on your phone with the login credentials from another. As you might imagine, these APIs are pretty important in our interconnected world, and there are quite a lot of them out there. API management, then, is its own important area of using modern technology—it’s how organizations secure, analyze, and expose APIs in ways that make it easy for developers to build on them. Google Cloud’s API management platform, Apigee, was once again recognized a leader in the 2019 Gartner Magic Quadrant for Full Lifecycle API Management. This report is often used by our customers as a reliable evaluation tool.
That’s a wrap for October. Keep up on cloud on our blog, and we’ll see you next month.
Source : The Official Google Blog
via Source information
0 notes
Text
College Issued Devices are Spying on B Tech Graduates
How colleges are spying on students on a massive scale?
The Chromebooks, iPADS, or other tech devices that B Tech students borrow from their college every year are digital spies. They are intimately familiar with their private information and browsing habits.
When most people think of digital surveillance, the first thing comes to mind is images of cameras. Digital surveillance is already in place at traffic lights, shopping malls, and even classrooms of Top Engineering Colleges in Jaipur where surveillance cameras monitor behavior.
Surveillance improves security and increases safety. Engineering Colleges management watch cameras in trouble spots like stairwells, halls, and common areas. Surveillance systems then store images in the cloud. If administrators need to determine who destroys the property or engaged in a fight, the documentation is available. However, some surveillance practices violate the privacy of students.
Protecting the privacy of minors
Digital learning occurs in almost every classroom in the country. Students of Top Private Engineering Colleges access instructional software, take quizzes and participate in simulations that boost learning. Many of these apps have something in common. However, they require logins, passwords, and personal information like an ID number, date of birth, and identification in special programs like bilingual or special education. School-issued devices store this information, but they also collect student’s browsing history.
Most Edtech companies rely on third-party software and applications that fall short of protecting student privacy. However, Edtech entrepreneurs may be more interested in sales than in protecting the privacy of the students of Engineering Colleges in Jaipur. Even if they are careful about student privacy, they must stay current with federal and state law regarding privacy. Edtech companies might not be keeping up with regulatory changes.
What you can do to protect your privacy?
B Tech Colleges have enacted legislation to protect the privacy of their students and family. They have every right to inquire about the data being collected on their students. Ask how the data will be used, and what happens to the information when the college year ends.
Administrators may have the college-issued devices cleared each summer in preparation for the new college year, but that is not enough. These devices use third-party apps to find out what the Edtech companies do with the information they collect. Do they delete it, store it, or sell it?
1. Transparency – Students of the list of engineering colleges in Jaipur must ask for the information about the software and their issued devices in use. However, they must find out about the collection methods of using, storing, deleting information. What protective measures does the school have in place?
2. Empowerment – Parents must have the right of refusal when using college-issued devices. If B Tech Colleges in Jaipur cannot guarantee student privacy, parents must be allowed alternatives to technology use in the classroom, including BYOD options.
3. Training – Digital literacy is everyone’s responsibility. Engineering Colleges in Jaipur cannot hope that all app designers are as cautious with private information as they are. Administrators, teachers, parents, students, and the community must make learning about digital intrusion a priority.
To read Continue with ARYA COLLEGE
#best engineering college in rajasthan#arya college kukas#arya college#arya old campus#Arya College of Engineering and IT#best engineering college in jaipur#arya college jaipur#Protect your privacy#How college are spying on Students#byod#ipad#chromebook
0 notes