#Smartphone Hack
Text


Rotary Un-Smartphone
#cyberpunk aesthetic#retro futurism#rotary phone#retro design#hacker girl#smartphone#analog technology#hacking#gadgets#electronics#hacker#retro tech#modding#cyberpunk#vintage tech
635 notes
·
View notes
Text
Nitpick November
When will crwby the characters remember they can check their teammate’s aura on their scrolls?

We have never seen anyone take out a scroll to look at a teammates aura, probably because it’s a stupid concept in the first place, so why have it?
#rwde#nitpick november#pardon me mr grimm lemme grab my phone so i can see how much health i have whoops theres my insides#honestly this is the only time i would ever suggest a smart watch or smth. all youd have to do is glace down#also how do these things work? can you hack them to give false reads? or to reverse whatever device is monitoring so that it causes damage?#maybe whatever doohickey reads their aura could be used to track them. that'd be an interesting plot point#but these things are fundamentally worthless. scrolls in general too#theyre glorified smartphones that the kids only use to call each other#at least put flappy bird on there jfc#or temple run#i love temple run
19 notes
·
View notes
Text
Am I getting an old school flip phone to stop doom scrolling and to finally focus on my college work?
Yes. Yes I am.
#it still has wifi for whatsapp#but other than that its just tect and calls#ive wanted to for years#and i realise my reluctance was unnecessary#i have a macbook still#ill even keep my smartphone as a backup#but i lived without any phone at all for almost a month#and the only thing i hated was not being able to message people or take calls#that was a strong lesson#everything else i can do on my macbook#this isnt about getting rid of social media entirely#the goal is to use it in moderation#and to have it stop being a habit to pick up my phone and scroll#and instead be more present and intentional#and to do my damn essays.#no fr i have like 3 weeks to do 17 essays and i scroll on my phone to cope#eek#adhd hack?
5 notes
·
View notes
Text
my dad watching the 2000s music compilation channel girl you do not realise how much of a vibe you are
#64 year old men who would do numbers on tumblr#he went to spain last week and was showing me all the pics and videos and i was just thinking#king you would love instagram stories#i think the reason i love to fantasise about how felix and beau and dorothy etc would be in modern day as people in their 50s/60s#is bc it just makes me think of my dad LOL#felix would not know how to use a smartphone but he would love emojis#he'd be a 60 year old ipad baby just introduce him to candy crush and then u dont have to worry about him all day#give 60 year old felix an instagram so he can post all of his shaky videos from his adventures#and then he gets his account hacked because he replied to a spam dm#beau's on tiktok giving life lessons to the gen z and getting clout for posting pics from the 80s#whole of tiktok just like thirsting over somebody's uncle#dorothy is arguing with people in the local facebook group#they are all at peace and have truly made it in life
4 notes
·
View notes
Photo


Yet more edits of the Ghost Bustin Fungus Lovin Man.
He’s showing Ray the games he has on his phone.
#𝙸'𝙼 𝙰𝙻𝚆𝙰𝚈𝚂 𝚂𝙴𝚁𝙸𝙾𝚄𝚂. (SELF)#𝚃𝙷𝙴 𝙿𝚁𝙾𝙵𝙴𝚂𝚂𝙸𝙾𝙽𝙰𝙻𝚂. (GHOSTBUSTERS)#imagine Egon w a smartphone though#absolute chaos would ensue#he'd hack cand.y crus.h and you can't tell me otherwise
9 notes
·
View notes
Text

There is an opportunity for a great deal of creativity over your street photos, allowing for some very easy and quick choices in style to be created using the smartphone camera.
2 notes
·
View notes
Text

Die Zwei-Faktor-Authentifizierung aushebeln
Schwachstelle Mensch
Jahrelang wurde uns versichert, dass wir mit einer Zwei-Faktor-Authentifizierung (2FA) sicher(er) seien. Allen voran die Banken haben solche Verfahren einführen müssen. Mit der EU Banken-Richtlinie PSD2 wurden sie Standard. Bereits damals hatten wir kritisiert, das das sinnvolle Verfahren durch die Abschaffung des "2. Wegs" wieder amputiert wird. So waren für die 2. Authentifizierung anfangs SMS o.ä. üblich, inzwischen laufen oft beide Wege wieder über ein Gerät - meist das Smartphone.
Nun hat sich herausgestellt, dass beim Kampf der Cybersicherheit gegen die Hacker letztere am Aufholen sind. In 2 Artikeln beschreibt Heise.de die Vorgehensweise der Hacker. Eigentlich ist alles beim alten geblieben - beim Pishing - nur der Aufwand, den die Hacker betreiben müssen, ist größer geworden.
Social Engineering statt neuer Technik
Weiterhin ist die Taktik der Hacker das Opfer solange zu verwirren, bis es Fehler macht. Die Tricks sind
dein Handy braucht ein Update,
dein Handy ist defekt,
ein Systemfehler ist aufgetreten, drücken Sie hier oder da,
u.v.m. ...
MFA-Fatigue-Angriff
Deshalb kommt ein MFA-Fatigue Angriff meist abends oder am Wochenende, wenn man ermüdet ist und eine technische Hilfe oder KollegInnen nicht erreichbar sind. Dann wird man mit "unlogischem Verhalten" der Technik verwirrt, solange bis man seine Passworte an der falschen Stelle eingibt. Eigentlich dürfte man das nicht tun, schreibt PCspezialist.de, denn:
Eine Authentifizierungsanfrage wird nur dann abgesendet, wenn Sie zuvor das korrekte Passwort in ein System eingegeben haben. Denn genau das ist ja der Sinn der Multi-Faktor-Authentifizierung – der zusätzliche Schutz durch eine zusätzliche Sicherheitsabfrage.
Ein Einmal-Passwort (OTP) kann also vom System nie verlangt, werden, wenn man sich nicht vorher dort einloggen wollte. Passiert dies doch, so ist es mit Sicherheit ein Cyberangriff. Die Angreifer versuchen ihre Opfer jedoch durch wiederholte Abfragen und/oder Abweisungen "des Systems" zu verwirren. So eine Abfrage kann auch ein Anruf "einer technischen Abteilung" sein, die einen angeblichen "Systemfehler" zurücksetzen müsse. Die Schwachstelle der Zwei-Faktor-Authentifizierung (2FA) bleibt der Mensch.
Mehr dazu bei https://www.heise.de/ratgeber/Ausprobiert-Phishing-trotz-Zwei-Faktor-Authentifizierung-8981919.html
und https://www.heise.de/ratgeber/IT-Security-Wie-Angreifer-die-Zwei-Faktor-Authentifizierung-aushebeln-8973846.html
und https://www.pcspezialist.de/blog/2022/11/28/mfa-fatigue-angriff/
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3u1
Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8395-20230510-die-zwei-faktor-authentifizierung-aushebeln.htm
#Schwachstelle#Mensch#Zwei-Faktor-Authentifizierung#2FA#PSD2#SocialEngineering#MFA-Fatigue-Angriff#Verbraucherdatenschutz#Datenschutz#Datensicherheit#Smartphone#Handy#IMSI-Catcher#Cyberwar#Hacking
2 notes
·
View notes
Text
Power of Compounding
tl;dr This post is not a financial motivation. It's a different perception to look at the greater mind.
We've heard the term compounding in the finance world. Compounding is key to long-term wealth. If you look at the deeper mechanics, compounding is adding, adding and adding all the smaller portions here and there and there and there. Essentially it's much more than repeated additions (or multiplication).
So, in the end, it refers to the sum of all the smaller parts amounting to a much bigger piece.
This principle also applies to the person you are trying to become. The actions you do daily, constantly all add up. Here is a small analogy to think about. Consider actions as small bags of money you keep saving. When your deeds are focused, constructive and positive it equals saving money. The amount of distraction you admit in your life equals spending that money and spending money early on never contributes to compounding.
The distraction referred to here is not entertainment/travel. No, those are important. Those are planned. I’m actually referring to unplanned distractions from the things you are actually trying to do. Say, a lazy work in your office where you are dragging the timeline for quite a bit. This is a classic example of unfocused/distracted work. It could also be any bad habit that is regular and blocks quite an amount of time in your daily life, such as drinking alcohol or even watching short videos(TikTok/Reels) regularly. Yes, you read that right. Both are surprisingly super comparable. This is you trading your time for dopamine shots. So the time spent here doesn’t contribute to your personal development. It's a waste 100%. I’m not against having small entertainments but giving into them regularly(addiction) will render a portion of your life meaningless.

Take some time regularly to think about things that have been at the back of your mind for so long. This is super easy and you have to do nothing. Let me tell you how.
Your mind has a lot of stuff to think about. But we keep it constantly distracted. We never get bored. Say, when you go to the restroom, many carry their phones inside to listen to music, which keeps the mind busy. Try not doing it, your mind gets some space to think about the things you’ve been trying to find a solution for. This happens automatically. Just keep the mind less busy at times like this and you’ll find this happening. Don’t take my word for it. Try it out. You’ll find thoughts gushing in your mind in no time. These constructive thoughts will contribute to the compounding effect we are discussing. Find times like these to stop distracting yourself. I will list some here but there are plenty of situations you can come across. Say, swiping the notifications in your phone as soon as you get bored a bit, listening to music for short travels or during work, or watching a tv-series while cooking. We are doing more of this these days. Just do one thing at a time mindfully.
Now with this, constantly think about what you want to become, achieve and the mind processes it slowly one thing at a time. It’ll offer you solutions from the subconscious over time. This is key to your growth as a person.
Be less distracted. Be bored.
2 notes
·
View notes
Text
Sidetrack | Unlocking the Windows Phone 7 emulator 14 years later (Part 2)
This is the second part. This post is split into 2 due to photos being limited. Part 1 | Part 2
To rebuild the image (cont'd)
32. Close XIPPort and open BOOOFF.
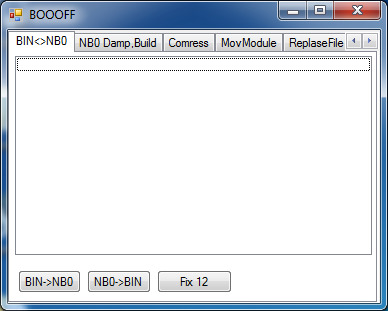
33. Select NB0->BIN.
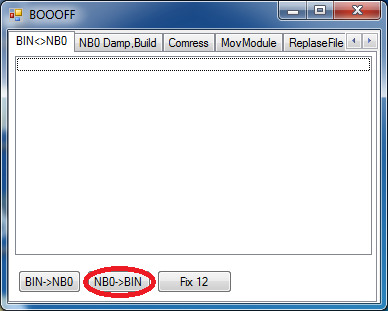
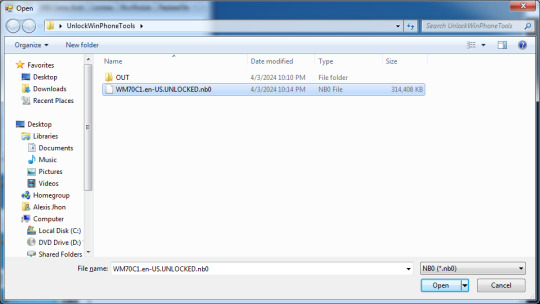
34. Select the .nb0 file XIPPort has generated earlier.
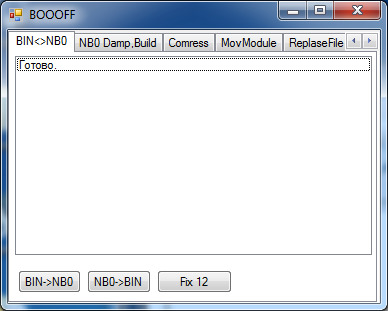
35. You should see this when it succeeds.
36. Select "Fix 12" after that.
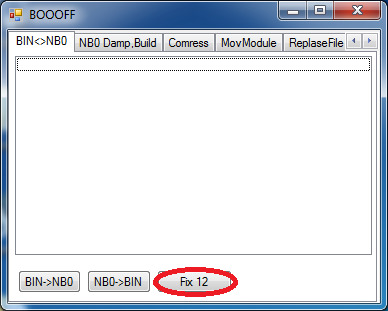
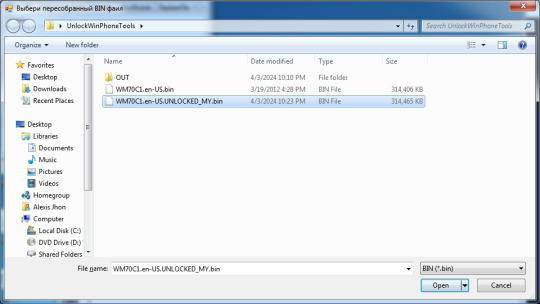
37. You should select the unmodified image first...
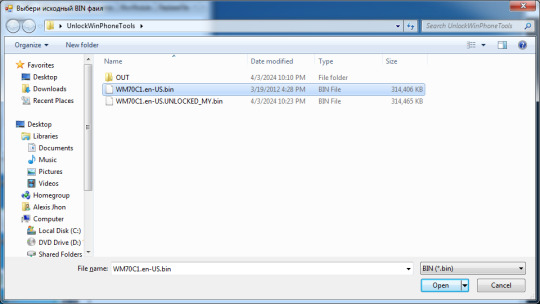
38. ...and then the modified one.
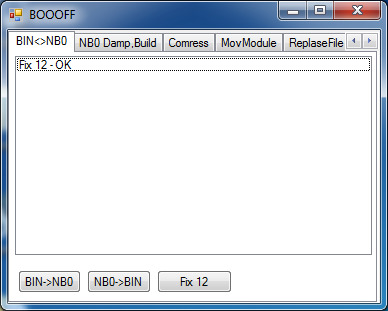
39. You are officially finished when it says "Fix 12 - OK".
To test the image
Go to the emulator image's directory.
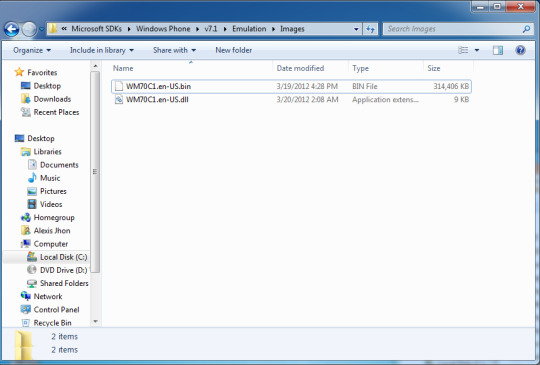
2. Delete the existing one. You will need administrator permissions.
3. Drag-and-drop the new one (via copy or move) to replace it.
4. Rename back the modified bin back to "WM70C1.en-US.bin" or the old filename.
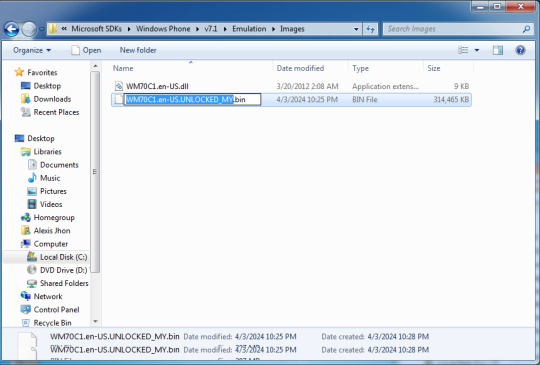
5. If you have the SDK already installed, go to the start menu and go to the "Windows Phone SDK 7.x" folder, and run the emulator as Administrator (Right click and Run as Administrator).

6. An unlocked image should appear with the Windows Phone logo on bootup, but please wait it to load completely.
7. And there you have it! Windows Phone 7 as god intended!
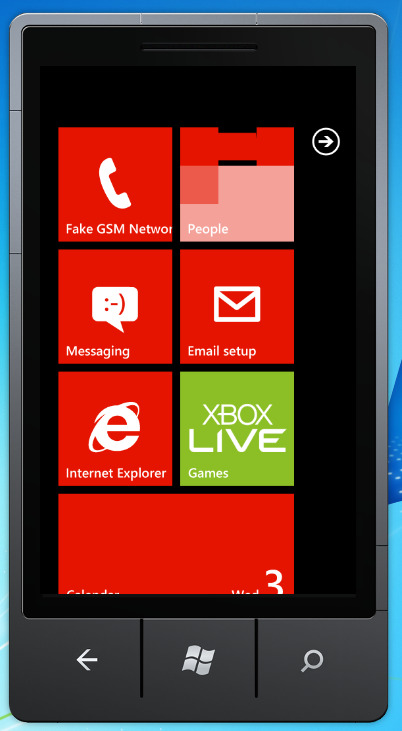
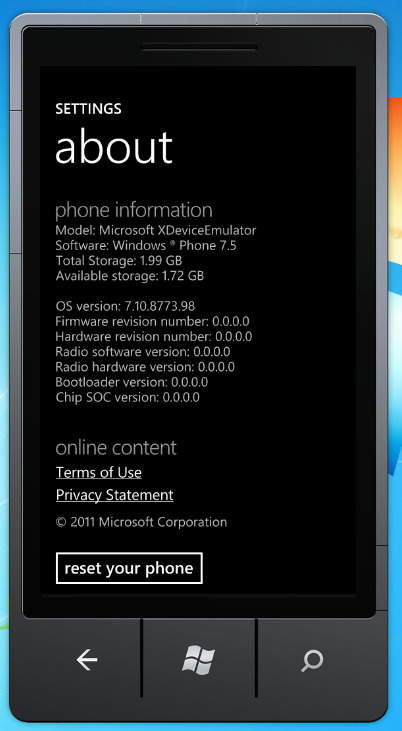
Conclusion
In conclusion, it is a mindbending and a specific task no one probably wanted to do in their free time, except for those with too much time with their hands. Anyways, I hope you enjoyed this sidetrip, and I would glad to say that you will expect new content, more quality content this year! Thank you and see you around!
#windows#windows phone#hacking#modding#tech#technology#mobile#smartphone#phones#operatingsystem#operating systems#tutorial#visual#long reads
0 notes
Text
Mini Smartphone IR Remote Controller Adapter for Android Mobile
#Mini Smartphone IR Remote Controller Adapter for Android Mobile#gadgets#home gadgets#viral video#technology#trendingreels#trending#life hacks#home decor#viral trends#viral
0 notes
Text
How to protect your phone from hackers in Tamil

#smartphones#hacking#cybersecurity#smartphonehacks#techtips#iphonehacks#techhacks#mobilehacks#phonehacks
0 notes
Text

Schwachstellen in Threema werden behoben
Jammern auf hohem Niveau
Eine Gruppe Schweizer Forscher um den ETH-Professor Kenneth Paterson hat sich die Sicherheitsfeatures von Threema einmal genauer angesehen und festgestellt, dass sich das Unternehmen sehr wohl um die Datensicherheit kümmert, aber die Anwendung doch in die Jahre gekommen ist.
Weiterhin wird die Ende-zu-Ende Verschlüsselung, die Threema damals 2012 als einer der ersten Messenger einführte, als wegweisend anerkannt. Für bestimmte Angriffszenarien können die Forscher jedoch zeigen, dass für die Sicherheit bei Threema "noch Luft nach oben besteht".
So könnten Angreifer auf die Metadaten der Kommunikation zugreifen.
Bei Zugriff auf die Chat-Server von Threema könnten sie Nachrichten löschen oder deren Reihenfolge ändern.
Grenzbeamte oder Lebenspartner, die Zugriff auf das Smartphone und die Threema-App haben, könnten unbemerkt die Threema-ID exportieren und damit den Account klonen. (Grenzbeamte nur wenn man so blöd ist, den Ausweis auf dem Handy zu nutzen!)
Bei allen 6 von den Forschern benannten Schwachpunkten ist es jedoch nicht möglich, die Inhalte der Kommunikation zu lesen. Dies kann nur passieren, wenn der Nutzer seinen privaten Schlüssel gegenüber einem Angreifer offenbart. Für solche Fälle empfehlen die Forscher eine inzwischen gängige Methode der Absicherung der einzelnen Nachricht mit einem für jede Nachricht oder zumindest in regelmässigen Abständen erneuerten Private Key. Fällt in so einem Fall der Private Key in die Hände eines Angreifers, so können damit keine älteren Nachrichten entschlüsselt werden (Perfect Forward Secrecy).
Bei Threema läuft nun seit einige Monaten eine Überprüfung der eigenen Sicherheit und einige Beanstandungen wurde auch bereits behoben. Das ging in jedem Fall viel schneller als Verbesserungen in die Verschlüsselung von normaler E-Mail einzuführen. So hat da die Einbeziehung der Verschlüsselung der Betreffzeile Jahre gedauert und ist immer noch "optional". Das ist der Nachteil, wenn kein Unternehmen um seinen Geschäftserfolg bangt, sondern die Open Source Gemeinde sich auf Erweiterungen in einen 40 Jahre alten Standard einigen will.
Mehr dazu bei https://www.nzz.ch/technologie/threema-schweizer-messenger-hatte-schwaechen-bei-verschluesselung-ld.1719543Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3rS
Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8271-20230112-schwachstellen-in-threema-werden-behoben.htm
#Schwachstellen#Threema#Datensicherheit#Transparenz#Informationsfreiheit#Anonymisierung#Datenpannen#Verbraucherdatenschutz#Datenschutz#Privatsphäre#Verschlüsselung#Smartphone#Handy#Cyberwar#Hacking#Identitätsdiebstahl
3 notes
·
View notes
Text
Unlocking Dynamic Island: A Guide for Android Enthusiasts

Hey there, Android aficionados! 📱 Looking to spruce up your Android experience? Look no further because we've got just the trick for you. If you've ever wondered how to add a dynamic island on your Android phone, you're in luck! We've put together an easy-to-follow guide that will have you customizing your screen in no time.
Dynamic Island is the latest trend in Android customization, allowing you to create a more dynamic and interactive interface. By following our step-by-step instructions, you'll be able to seamlessly integrate this feature into your device, giving it a fresh and vibrant look that reflects your unique style and personality.
With our comprehensive tutorial, you'll learn the ins and outs of setting up Dynamic Island on your Android phone, enabling you to take full advantage of its capabilities. Whether you're a tech-savvy individual or someone looking to explore the endless possibilities of Android customization, this guide is tailored to cater to your needs.
So, what are you waiting for? Dive into the world of Dynamic Island and elevate your Android experience to a whole new level! Head over to our blog to get started: How to Add Dynamic Island on Android Phones.
Don't forget to share your personalized Android setups with us in the comments below. We can't wait to see the creative ways you make Dynamic Island your own!
#Android#Dynamic Island#Customization#User Interface#Mobile Technology#Smartphone Tips#Android Tricks#Personalization#Tech Guides#Digital Trends#Android Hacks#UI Customization#Phone Customization#Android Tweaks#Digital Experience#App Customization#Home Screen Design
0 notes
Text
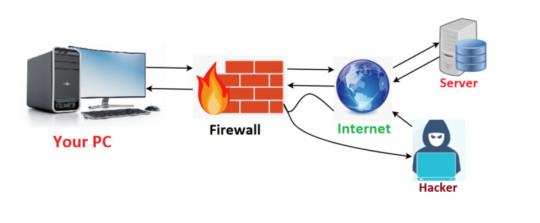
You Need A Firewall On Your Device Right Now!
#community#firewall#hackers#hacking#hacker#cybersecurity#tech#techtips#security#smartphones#smartphone#pc#computer#device#server#Internet
0 notes
Text
Sidetrack | Unlocking the Windows Phone 7 emulator 14 years later (Part 1)
Introduction to Sidetrack
Hello there folks! Welcome to a series of original Tumblr content that I made called "Sidetrack". The series will often complement longer blog posts/articles and will include much more humorous ramblings and maybe tutorials as well! This also includes a wider range of topics from culture to memes to technology to media and anything in between, discussing and ranting about our dying civilization. In this series, expect it to be only on Tumblr, as to decongest the RSS feed and I see the main site as the appropriate place for much more deep commentaries nowadays. Anyways, in this post, I'll try and talk about the wild world of Windows Phone 7, and its software development kits, unraveling hints in the space of Windows CE development and hacking, as well as providing too much lighthearted commentary.
Overview
This is the first part. This post is split into 2 due to photos being limited. Part 1 | Part 2
As I am working with archiving official Microsoft SDKs for the sake of archival and fun, I delved into a much more complex problem that is the feature lock in Windows Phone 7 emulators.
Now you might ask, "why the heck are you talking about Windows Phone all of the sudden?", well, it's a part of my huge 1 month undertaking, with 25GB (and counting!) worth of emulators, so that puny little Joe Smith Jr. with a crazy addiction on Skibidi Toilet and knowledge on virtual machines can set up these emulators, to brag it on their Roblox friends (yada yada...), and since I embrace archiving said material for future use!
Of course, this ain't like easy work, though. Fiddling too much with the registry can also mean breaking an entire system, so be warned. (even if it involves an emulated environment.) So let's get started!
Prerequisites:
- mRegEdit.exe (Windows CE Registry Editor)
- BOOOFF
- XIPPort
All of these files are available via my GitHub repository. Clone the whole repository, as some programs rely on dlls.
Guide on how to unlock said emulators
Place the contents of the repository in a folder.
Extract the emulator image. It is usually found under C:\Program Files (x86)\Microsoft SDKs\Windows Phone\v7.x\Emulation\Images where v7.x is the version number (7.1 = WP7.5).
To extract the files
Open the XIPPort tool.
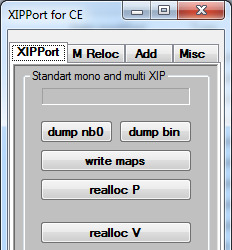
2. Select "dump bin".
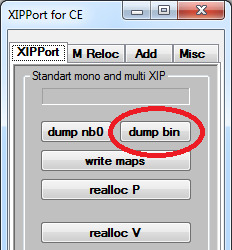
3. Select the .bin file.

4. Wait for a few minutes then it should say "dump .bin OK!!!"
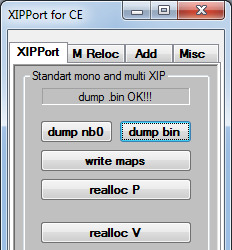
5. The resulting files are placed in the "OUT" folder. There, we would need to decompress three files. Those are:
default.hv
5BA3EEFF-F8BC-4c43-8175-BF218E964AA0.rgu
8C9C0C34-B77D-45FB-9E4E-D53AC5900244.rgu
6. In XIPPort, select Misc then Decompress.
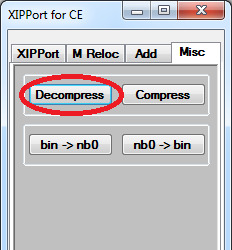
7. Select the file.
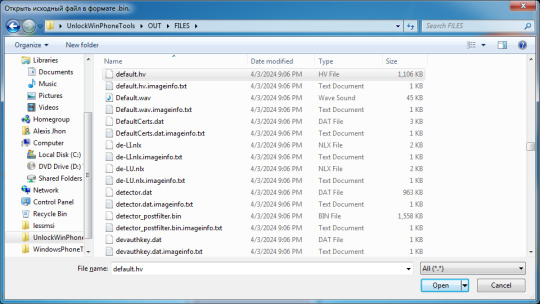
8. Repeat step 7 for the other files.
9. You will find the decompressed files in OUT\DECOMPRESSFILES.
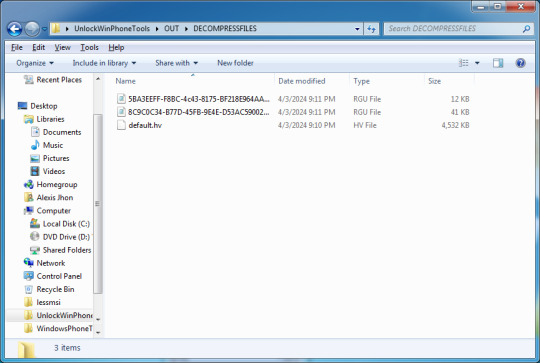
10. You are officially done extracting!
To unlock the emulators
1. Open mRegEdit.exe.
2. Locate the files.

3. First open up the 5BA3EEFF-F8BC-4c43-8175-BF218E964AA0.rgu file.
4. Go to HKEY_LOCAL_MACHINE/Software/Microsoft/PackageManager.
5. Delete the "Blacklist" key by pressing F4 or Delete.
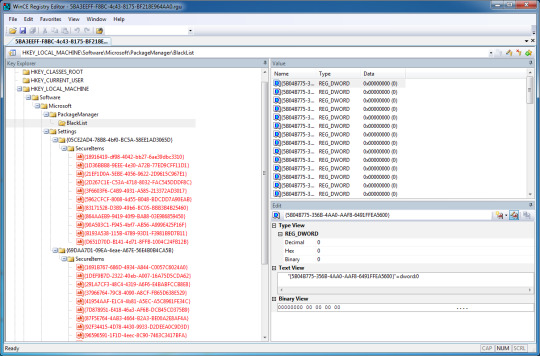
6. Save the file.
7. Open the default.hv file.
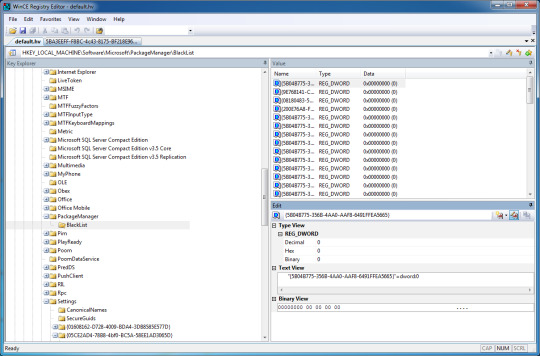
8. Repeat step 5.
9. After that open the 8C9C0C34-B77D-45FB-9E4E-D53AC5900244.rgu file. This contains the full application list in the keys that I would mention.
10. Go to the Window menu then "New Vertical Tab Group".
11. Go to HKEY_LOCAL_MACHINE/Software/Microsoft/Settings/{05CE2AD4-78B8-4bf0-BC5A-58EE1AD}\SecureItems in default.hv as well as in the 8C9C0C34-B77D-45FB-9E4E-D53AC5900244.rgu tab.
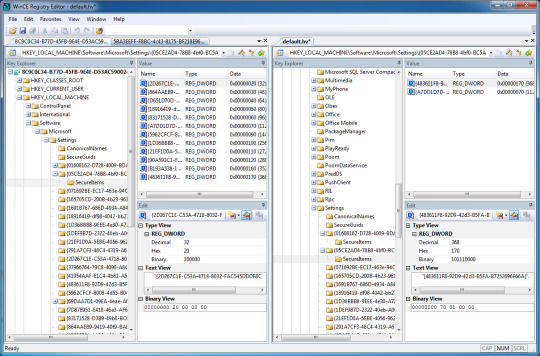
12. You would notice that the DWORD entries in 8C9C0C34-B77D-45FB-9E4E-D53AC5900244.rgu are not the same except for two. Either take note of it or not.
13. Recreate each DWORD entry from 8C9C0C34-B77D-45FB-9E4E-D53AC5900244.rgu to the default.hv file.
14. This can be done by going to the Edit window/panel (found below the Value panel), clicking on the first icon (with the down arrow), selecting "REG_DWORD".
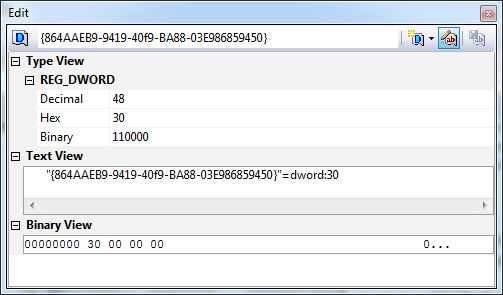
15. Copy and paste the key name from the left tab to the label box.
16. Edit the Decimal value to match with it's corresponding key on the left tab.
17. Press enter and your key would get into the database. Keys with same DWORD values would get replaced.
18. Repeat the process from step 14 to 17 to each key.
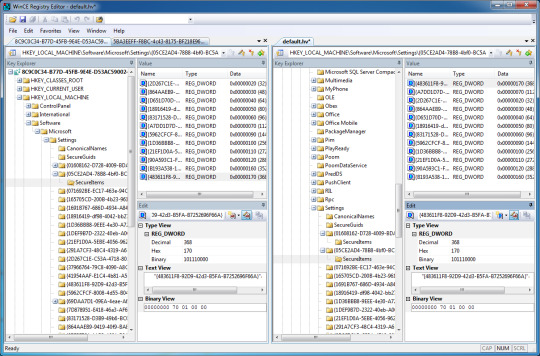
19. You should have accomplished, with this exact state. Double check for any missing values.
20. Go to HKEY_LOCAL_MACHINE\Software\Microsoft\Settings{69DAA7D1-09EA-4eae-A67E-56E4B0B4CA5B}\SecureItems in both files.
21. Repeat steps 13-18 with this one.
22. You should have accomplished, with this exact state. Double check for any missing values.
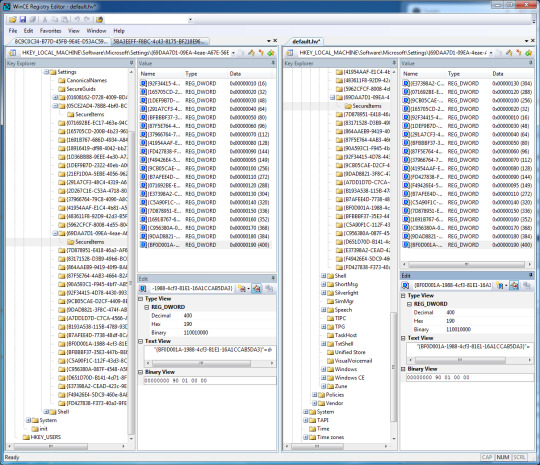
23. Save default.hv. Now close mRegEdit. Save any modified files if any.
To rebuild the image
1. Open XIPPort again. Select Misc then Compress.
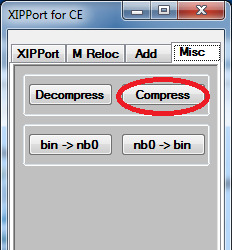
2. Go to the directory OUT\DECOMPRESSFILES.

3. Select the default.hv file.
4. Then after that, repeat step 1 and select the 5BA3EEFF-F8BC-4c43-8175-BF218E964AA0.rgu file.
5. It would drop files in the COMPRESSFILES folder.
6. Open the .imageinfo.txt file for default.hv in Notepad. This is found in OUT/FILES.
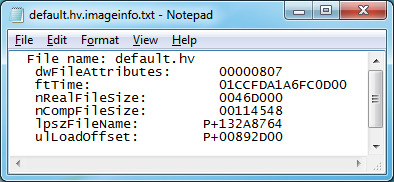
7. You would get some values. The one that we are the most interested in is nRealFileSize and nCompFileSize.
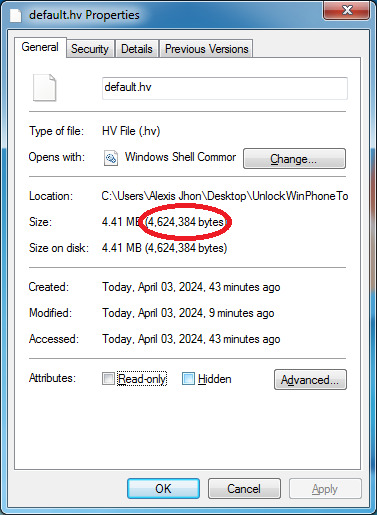
8. To get nRealFileSize, go to OUT/DECOMPRESSFILES/default.hv.
9. Right-click then go to properties.
10. We only need the one in the red circle, which is the file size in bytes.
11. Go to the Windows calculator app.
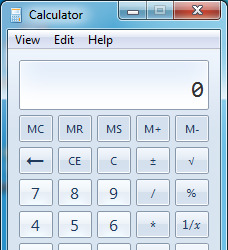
12. Select "View" then "Programmer", or press Alt-3 to switch to the Programmer's calculator.
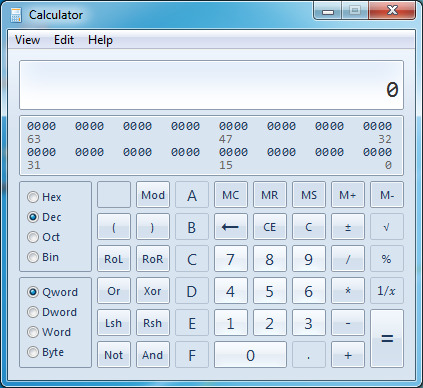
13. Enter the file size in bytes.
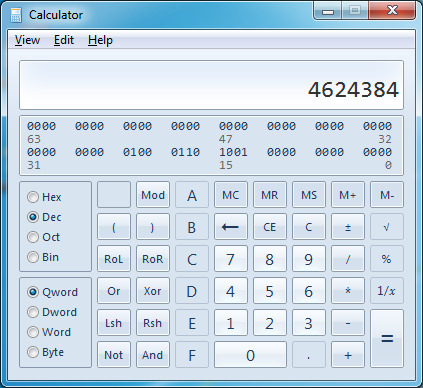
14. Select Hex to get the hexadecimal value.
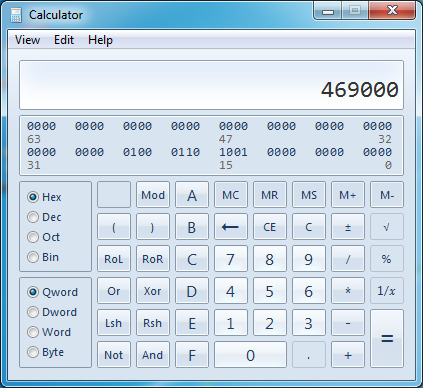
15. Copy that and switch back to Notepad.
16. Go to nRealFileSize and highlight the last digits.
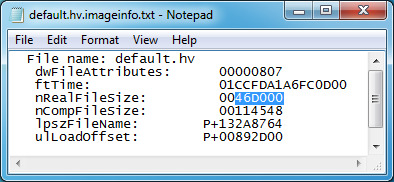
17. Replace the value with the result you've copied earlier.
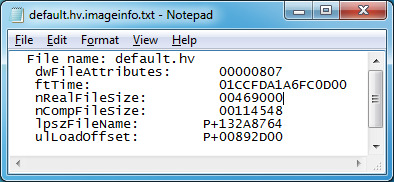
18. To get nCompSize, go to OUT\COMPRESSFILES\default.hv.
19. Repeat steps 9 to 17 to get the value.
20. In the end, you should have the new values set.
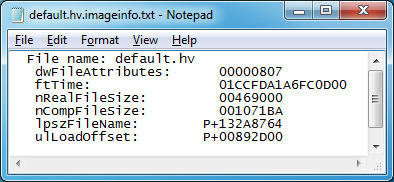
21. Save the file.
22. Open 5BA3EEFF-F8BC-4c43-8175-BF218E964AA0.rgu.imageinfo.txt from the same directory.
23. Repeat steps 7 to 20 when editing said file.
24. In the end, you should have the new values set.
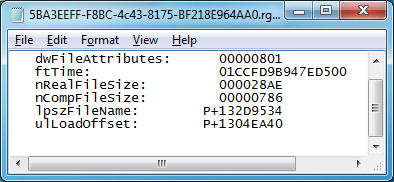
25. Save the file.
26. Move the contents of OUT/COMPRESSFILES to OUT/FILES, replacing our old ones.
27. Delete both the DECOMPRESSFILES and COMPRESSFILES folders.
28. Open XIPPort again.
29. Click on "write nb0". This would generate a .nb0 ROM image of what we had done so far.
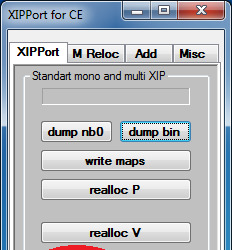
30. This would then ask for where to save the file. Save it on the same directory as the tool. Make the name unique, so that you wouldn't get confused later on. In this case, I appended "UNLOCKED".
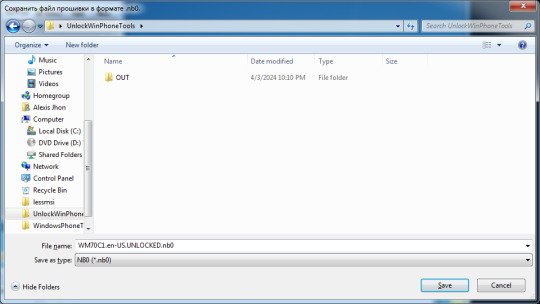
31. Hit save. You should see "write .nb0 OK!!!".
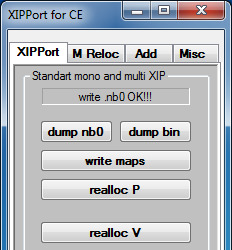
This post is split into 2 parts because of image limits. Part 2 is here.
#windows#windows phone#hacking#modding#tech#technology#mobile#smartphone#phones#operatingsystem#operating systems#tutorial#visual#long reads
0 notes
Text
How to Do Smartphone Photography Using Smartphone Cameras?
Professional cameras are no longer needed to take stunning photographs these days. The smartphone in your pocket has the power to take those high-quality pictures that you're seeing in magazines, and it's also very easy to do.
It is hard to beat the portability and convenience of a camera at any point in time. You've got your phone with you all the time and ready to capture these unexpected moments.
For more interesting information read more...
0 notes