Photo

How does a CDN work? | Choose the Best CDN Services
CDN is a system of servers placed in various parts of the planet to better relay data to users all around the world. A CDN stores your site information in a huge amount of servers on the double, ensuring your site holds a liberal inclusion for your guests to get to. For example, when somebody from Australia visits your London-facilitated site, they're ready to do as such with the assistance of your neighborhood Australian PoP; their solicitation never again goes starting from the land under to the square mile. More or less, a CDN benefits site proprietors since they improve stacking speed, upgrade security, and even permit modified substance dependent on area!
Choose the best CDN Services.
https://www.belugacdn.com/how-to-use-a-content-delivery-network/
0 notes
Link
CDNs distribute your content around the world in different data centers. Select the Best CDN providers to speed up your website and increase the traffic.Get all of these features for 1/4 the cost of our competitors at BelugaCDN
https://www.belugacdn.com/how-to-use-a-content-delivery-network/
0 notes
Video
How to Choose the best virus removal tool of 2019?
https://antivirus.comodo.com/blog/computer-safety/five-best-virus-and-malware-removal-tools/
Generally speaking, there is no universally considered best antivirus software for everyone, but you can review the choices and select the best features if you have good data. Before downloading Best computer virus removal software, it is critical to review the protection the software offers. Numerous antivirus options are available online and choosing the best software for your system's requirement is important. Cloud antivirus software can be a good choice if you want an antivirus that uses very little system resource. Below is a set of criteria which should be considered in order to get the best possible fit from your free antivirus program.
Technical Support: The best antivirus programs come with comprehensive online and offline technical support, including an online knowledge base, tutorials, or even user forums. Customers who seek answers to their questions regarding their antivirus program should be provided with quick and simple ways to have these issues resolved.
Usability: Users require their virus protection to be easy to use so a simple interface should make any complicated task a breeze.
Updated Feature: An antivirus download should automatically perform updates at the intervals that you specify to ensure all possible virus definitions will be available to protect your PC. A frequently updated program means the best possible protection.
Great Features: A good antivirus program should include the following:
List of compatible versions for different operating system
Resource and space analysis to ensure the usability of antivirus program
Comprehensive features that provide additional protection from your antivirus solution
Protection from all Possible Threats: An effective antivirus program should protect your PC from a wide array of threats. From viruses to worms, Trojans, spyware, key loggers, adware, root kits, password stealers, phishing attacks, spam and other possible harmful threats, you should make sure you are covered before you make a purchase.
Compatibility: Your antivirus program should meet the hardware and software requirements of your PC and not slow down your PC's performance.
Easy Installation: Good antivirus program should be easily installed in addition to being easy to use.
The best antivirus program must deliver great security and usability with a minimal output of your money or your PC system resources.
Why to Choose Comodo Antivirus Software?
Of course, yes. You can trust Comodo Antivirus software but before making this over confident claim, it is wise to explain why the brand has such a strong belief on the products they make. It is not only because of the exclusive features or the dedicated antivirus lab they own but also because of the millions of customers worldwide who trust Comodo. Gaining such level of integrity and customer trust is not an easy task. It is built over the decades by providing quality products, assured security and satisfactory customer service which paved it to greatness.
How Comodo Antivirus Differs?
The market has a wide range of Comodo Antivirus products available, each one of them with their set of features designed to stop virus intrusions. Comodo Antivirus software differs from them all at various levels because of,
Auto Sandbox Mode – The sandbox technology creates a virtual replication of your running operating system. The feature has the capability to identify all untrusted programs and they will automatically be to the box mode. This ensures that any type of malicious file or malware is fully isolated from the PC for maximum security and tested in a secure environment.
HIPS – Host Intrusion Prevention System is another exclusive features for the Comodo product. The feature is designed to prevent malware, virus, trojan and bugs from entering the computer. This prevention based system makes CIS superior to other programs which work only after infection occurs. Preventing malware secures files and data better than other security measures.
Default Deny Protection DDP – The feature has the capability to identify safe and secure files from malicious ones. It makes use of the cloud based white list and black list to decide the nature of the files. If it identifies a file to be unsafe, the sandbox mode will automatically take control so as that it can be isolated from the computer's main storage or OS area.
Cloud Based – Comodo Antivirus is fully cloud based which is the first of its kind. The product is fully integrated to the web and has the capability to scan malicious files by using its latest virus definitions. Sometimes, local virus definitions may not be current which will let known virus enter but the cloud system saves the trouble and keep things updated. Similarly, the product also uses Cloud based behavior analysis and whitelisting solutions to stop zero day malware among other malicious programs.
#best_virus_removal#best_virus_removal_tool#virus_protection#Malware Removal#pc_security#antivirus#software
0 notes
Link
Comodo also offers Internet Security Suite that incorporates all other security features including Antivirus to provide a safe and secure browsing. Get Best Antivirus for Windows 10 at just $4.99/yr.
https://antivirus.comodo.com/antivirus-for-windows-10/
0 notes
Video
How to Use Remote Desktop?
Remote desktop technology has been an important feature for Microsoft Windows since Windows XP. Get the guide How to Use Remote Desktop on Windows 10.
https://remoteaccess.itarian.com/how-to-use-remote-desktop.php
0 notes
Link
Managed Cloud Services
Swift Systems deploys private cloud hosting service designs tailored to your regional or Maryland business. Get best Cloud Services!
http://bit.ly/2vWDbnp
0 notes
Link
B2B APPOINTMENT SETTING SERVICES
Demand Monster provides targeted appointment setting and lead generation services. We focus on driving your business forward. Get in touch for a quote now!
https://demandmonster.com/services/appointments.php
https://issuu.com/stew.williams19/docs/b2b-appointment-setting-services.pp
0 notes
Link
A virtual private cloud enables rapid deployment, universal on-demand access, rapid failover and recovery, significantly increased security, and complete control of the economics of your network.
http://bit.ly/2LDmacp
0 notes
Photo
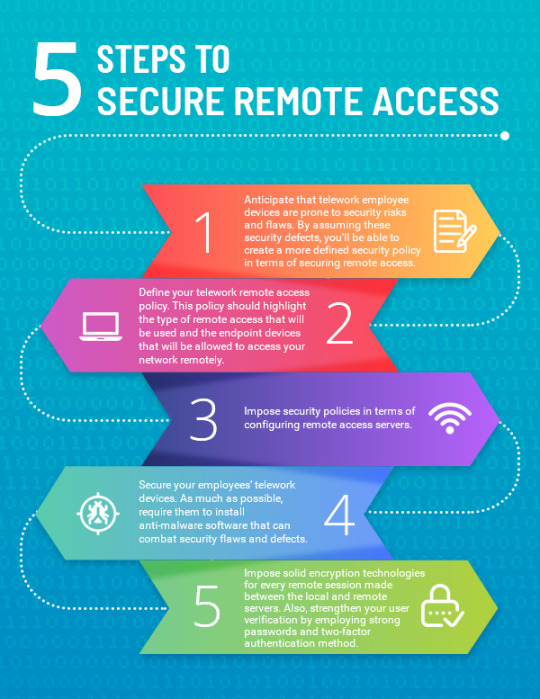
5 steps to Secure Remote Access
Secure Remote Access that Follows Your Admin and IT admins can log in and securely access resources from any location that can reach the Services. Get Free Remote Access Software Now!
https://remoteaccess.itarian.com/
0 notes
Link
Business Cloud Data Storage and Hosting - Swift Systems
Swift Titan is a full-featured managed file storage solution giving you control of file storage and access management. Cloud data storage for your business.
https://swiftsystems.com/cloud-services/swift-virtual-private-cloud-applications-2/swift-titan-secure-file-hosting-storage/
0 notes
Link
Conditional access is a technology that limits the amount of information that can be accessed by users. Get Free remote access software Now!
https://remoteaccess.itarian.com/blog/how-important-conditional-access-is-to-business/
0 notes
Photo
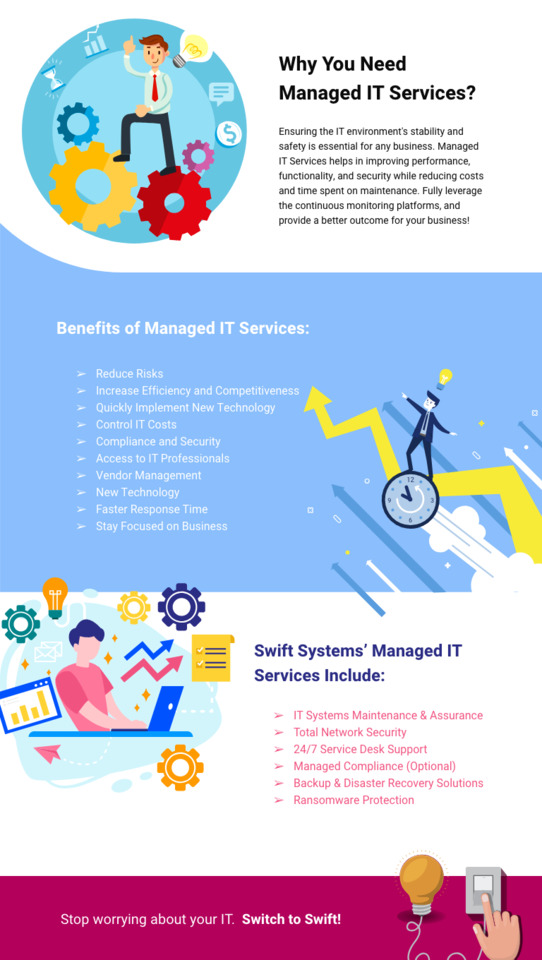
Why do you need Managed IT services?
Swift Systems is the Managed IT Services provider designed to support organizations of any size with Fortune-100-level service.
https://swiftsystems.com/
0 notes
Link
Swift Virtual Private Cloud | Managed IT services
Swift Systems has a proven track record of providing virtual private cloud services for regional and Maryland business. Get Best Cloud Services Now !
https://swiftsystems.com/cloud-services/swift-virtual-private-cloud-platform/
0 notes
Photo
How to Use Remote Desktop?
ITarian guide you How to Setup Remote Desktop in various OS like Apple, Windows. Get Free secure Remote access Software Now!
https://remoteaccess.itarian.com/how-to-setup-remote-desktop.php
0 notes
Link
Analyzing Remote Access Trojan | Get Free Remote Access
Remote access trojan or RAT is a type of malware that provides attackers with the ability to control a computer or a device via an established remote connection
https://remoteaccess.itarian.com/blog/analyzing-remote-access-trojan/
0 notes
Video
How to Use Remote Desktop?
Remote desktop solutions are much easier to achieve nowadays, and a lot more reliable than ever.Get free Remote desktop connection from ITarian.
https://remoteaccess.itarian.com/how-to-use-remote-desktop.php
0 notes
Photo
Remote desktop solutions are much easier to achieve nowadays, and a lot more reliable than ever.Get free Remote desktop connection from ITarian.
https://remoteaccess.itarian.com/how-to-use-remote-desktop.php
0 notes