Text
Top 10 Things You Can Do to Protect Your Computer from Ransomware
Photo by Andrea Piacquadio on Pexels.com
Introduction
Ransomware is a type of malicious software that encrypts your files and demands payment in exchange for the decryption key. It can cause significant damage to your computer, data, and personal information. In this blog post, we will discuss the top ten things you can do to help protect your computer from ransomware attacks.
Step 1: Keep Your…

View On WordPress
0 notes
Text
Incident Response Steps after a Data Breach
Data breach announcements seem to be quite common these days, with a cyber-attack an inevitable part of running almost any business. It is an often-quoted statistic that companies without a policy in place for a post-attack recovery have a 60% chance of going out of business in the six months following an event.
The important thing you can do today is prepare for the various types of cyberattacks…

View On WordPress
0 notes
Text
LevelDB and Chromium Browsers
LevelDB is a fast and lightweight key-value storage library that is used by many applications, including web browsers. In this blog post, we will briefly explain how LevelDB is used with Chrome and Edge browsers in Windows 10, and what benefits it provides to locating user data.
How it Works
Chrome browsers, including the Microsoft Edge browser, is based on Chromium. Chromium is the open-source…
View On WordPress
0 notes
Text
Enabling Priority Accounts in O365
If you are an Office 365 administrator, you may want to enable Priority Accounts for some of your users. Priority Accounts are a feature that allows you to prioritize the delivery and protection of email messages for your most important or sensitive users, such as executives, VIPs, or key decision-makers. In the future, more apps and features will support priority accounts, and to start with,…

View On WordPress
#Cybersecurity#Microsoft Defender#Microsoft Office#O365#Priority account protection#Priority Accounts
2 notes
·
View notes
Text
10 Steps to Stopping Lateral Movement Attacks
It is estimated that over 75% of cyber-attacks come from outside your network. While every attack is unique and tactics may vary, the basic stages of an outsider attack are similar. During the attack, an attacker uses four basic steps to gain a foothold in your environment.
Attack the perimeter – Gain access through any perimeter protections to gain access to the internal resources of the…

View On WordPress
#anti-virus#AppLocker#Cybersecurity#exfiltration#lateral movement#malware#MFA#Network Security#password#Ransomware
0 notes
Text
Preventing a Database Breach
Photo by Sora Shimazaki on Pexels.com
One of the hardest things to do is prevent something from happening when you don’t know when it might happen or who will try to make it happen. As a Database Administrator, you have to be aware that a data breach might happen and take all reasonable precautions to prevent it from happening. According to the 2016 study by IBM, 60% of database attacks are…

View On WordPress
0 notes
Text
Free Download: SQL Server Management Studio 19.2
SQL Server Management Studio (SSMS) is an integrated environment for accessing, configuring, managing, administering, and developing all components of SQL Server. SSMS combines a broad group of graphical tools with a number of rich script editors to provide developers and administrators of all skill levels access to SQL Server.
Microsoft has announced the latest release of SQL Server Management…

View On WordPress
0 notes
Text
Securing Active Directory Accounts
Photo by Andrea Piacquadio on Pexels.com
Active Directory is a directory service that manages user accounts and other resources on a network. It is important to secure Active Directory user accounts to prevent unauthorized access, data breaches, and identity theft. In this blog post, we will describe the step-by-step process to secure Active Directory user accounts using best practices and…

View On WordPress
#active directory#Azure Active Directory#Group Policy#Least privilege#Microsoft#Multi-Factor Authentication
2 notes
·
View notes
Text
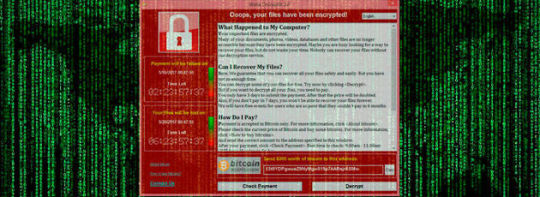
Ransomware Response Procedures
Ransomware is a type of malicious software that encrypts your files and demands a ransom to restore them. It can cause serious damage to your data, your privacy and your finances. If you discover that your computer has ransomware, you need to act quickly and follow these 10 steps:
Disconnect your computer from the internet and any other devices. This will prevent the ransomware from spreading to…
View On WordPress
3 notes
·
View notes
Text
Disabling or Uninstalling Unnecessary Services and Apps in Windows 10
Windows 10 is a powerful and versatile operating system that offers many features and functionalities. However, not all of them are necessary or useful for every user. In fact, some of the services and apps that come preinstalled or run in the background can pose security risks or slow down your system performance.
In this blog post, we will describe which unnecessary services and apps you should…

View On WordPress
2 notes
·
View notes
Text
10 Steps to Securely Configuring Windows 10
Windows 10 is the most popular operating system in the world, but it also comes with some security risks. If you want to protect your data and privacy, you need to configure Windows 10 for security. Here are 10 steps you can follow to make your Windows 10 more secure.
Update Windows 10 regularly – Windows 10 updates often include security patches and bug fixes that can prevent hackers from…

View On WordPress
#2FA#Backup#BitLocker#Cybersecurity#MFA#Virtual Private Network#VPN#Windows 10#Windows Defender#Windows Defender Firewall with Advanced Security
0 notes
Text
Free Download: SQL Server Management Studio 19.1
SQL Server Management Studio (SSMS) is an integrated environment for accessing, configuring, managing, administering, and developing all components of SQL Server. SSMS combines a broad group of graphical tools with a number of rich script editors to provide developers and administrators of all skill levels access to SQL Server.
The SSMS 19.x installation doesn’t upgrade or replace SSMS versions…

View On WordPress
1 note
·
View note
Text
Technical Interview Questions
Technical interviews are an attempt by a hiring team to ask the correct questions of a candidate to determine if they would be a good technical fit for the open position.
These questions can sometimes uncover missing segments of knowledge that might identify opportunities for the candidate, or even disqualify the candidate for the open position. That is good information to know before you…

View On WordPress
0 notes
Text
Updating Cisco AnyConnect VPN Client
Cisco AnyConnect VPN client is software that allows you to securely connect to your organization’s network from any location. It is important to keep the VPN client updated to ensure optimal performance and security. In this article, we will show you how to deploy the updated Cisco AnyConnect VPN client to your users using the following steps:
Download the latest version of Cisco AnyConnect VPN…

View On WordPress
0 notes
Text
How to Increase OneDrive Size
OneDrive is a cloud storage service that allows users to store and access their files from any device. OneDrive users have a default storage quota of 1 TB, but sometimes they may need more space for their work or personal files. We will explain how a global administrator in Azure can increase a user’s OneDrive size up to 5 TB.
To increase a user’s OneDrive size, the global administrator needs…

View On WordPress
1 note
·
View note
Text
Check Email Addresses Listed in Active Directory
One of the tasks that administrators often need to perform is to verify that each active directory user account has a valid email address. This is important for ensuring that users can receive notifications, access online services, and communicate with other users. There are different ways to verify the email addresses of active directory users, but in this article, we will focus on one method…

View On WordPress
1 note
·
View note
Text
5 Common Types of Cyber Attacks
Cybersecurity is a crucial aspect of any organization that relies on digital systems and networks. Cyberattacks can cause significant damage to the reputation, operations, and finances of a business, as well as compromise the privacy and security of its customers and employees. Therefore, it is important to understand the different types of cybersecurity attacks, how they are used, and how they…

View On WordPress
1 note
·
View note