Text
Why Is Cyber Ontology? Deliver Context For Orchestration
The modern Security Operations Center (SOC) is a highly complex system of point tools, all designed to keep sensitive corporate data secure. Each of these tools creates disparate data points and incidents. Security analysts investigate the barrage of incidents and alerts, looking for clues while asking themselves: is this alert stemming from an actual event? What is the source of this alert? Has this been through our system before?
Out of context, these cyber security events are all just data points living in their own silos. The signs are easily misinterpreted, potentially leading to security disasters. But when viewed in context, these individual clues can tell a lot about the organization’s security. With context, analysts can understand relationships, see the entire story, and keep their organizations secure.
How can organizations create that context?
Legacy Approach
Each cyber security event involves several entities, such as IPs, hosts, users, processes, etc. When creating Siemplify, we asked ourselves, how should analysts see cyber security events?Legacy methods are failing them.
Traditional security solutions are built atop a tabular data structure, which creates an inherently flawed approach to cyber investigation and response. The challenges with this approach are well documented: analysts must be reliant on slow and cumbersome queries; there is an inability to see all relevant relationships; challenges adding data sources and manipulating relationships greatly affect efficiency. Most importantly, as data sources feeding the security environment continue to expand, the constraints are more pronounced and detrimental. In between the layers and silos of traditional approaches, events fall through the gaping cracks.
Creating Context with Siemplify Cyber Ontology
Cyber security ontology defines a common vocabulary for security analysts who need to analyze and share information. It includes human-interpretable definitions of basic concepts in the cyber security domain and relationships among them.
Siemplify Cybersecurity Ontology (SCO) is intended to support information integration and cyber situational awareness across the security ecosystem. This ontology helps to incorporate, integrate and fuse large amounts of heterogeneous security data from disparate cybersecurity systems and organizational data silos into a unified language.
Cyber ontology is used to show cyber security data (events, incidents/cases, STIX, correlations, etc. ) into the representation of entities (IP, user, removable device, etc.) and their relationships (event names, properties of event, internal relations, etc.).
Different entities and relationships are shown as different icons, creating an easier and more meaningful understanding of these entities and relationships. The following 2 examples show how we present events, using Siemplify Cyber Ontology, in our system:
Read Full Article here – https://www.siemplify.co/blog/cyber-ontology-glue-driving-security-operations-orchestration-incident-response/
1 note
·
View note
Text
The Truth About Blogging – What Every New Blogger Should Know
This post talks about the truth about blogging and what every blogger should know. You’ll learn what it really take to make six figures blogging. This post is based upon my personal experience as a blogger. My opinions are my own.
Imagine this: you’re sitting at your desk at your job and you’re wondering about your life. “Is this really it? I want more from life. I feel I am meant to do more.” You struggle between your creative self and the realist within you, telling you not to take a risk. You ignore that conformist inside you and decide you do have what it takes to make it. You decide to start a blog.

This post may contain affiliate links. Read my full disclosure for more information.
The Truth About Blogging – What Every New Blogger Should Know: What It Really Takes To Make Six Figures Blogging
Blogging is great, don’t get me wrong. It’s changed my life for the better and has made me a more diligent, persistent and responsible person. The truth is, blogging takes work and what you put in, you get out. Blogging is totally fun and I love it but blogging is also a job. It’s my full-time job. There is a lot of misconception that you can start a blog today and immediately make money from your blog; today. Wrong. Blogging takes work and persistence and consistency. Unless you’ve had prior experience or have a system in place, it will take time to grow your blog and monetize it.
When I started Bonne Chic 2 years ago, I wanted to start a blog because I love to write. Writing is truly a passion of mine. I started this blog because I’ve tried so many other ways of earning money online and writing is the only passion I’ve had and stuck with for as long as I can remember.
Before blogging, I produced my own TV show, I was a Fashion Designer and I had my own clothing line and then I went into Corporate America to pursue a career I’ve always wanted to have, followed by starting this blog. Crazy, right? Yeah. I tend to always pursue passions of mine
The Truth About Blogging
Don’t get me wrong, I love what I do. But what I’m about to tell you is the truth about blogging; at least from my own personal experience. If you’re thinking of starting a blog or have mixed feelings about your blogging journey, this post is for you.
Blogging takes work. Yes, you read that right. Blogging is not some magical pill that you can take and…
Viola! Money rolls in!
It doesn’t work like that. Blogging isn’t all the cutesy Pinterest images you see. It’s much more than that. It takes work. It’s countless hours of research and writing and editing blog posts. It’s countless interruptions in between with cooking dinner and taking care of family and home. It’s also juggling a job sometimes. It’s wearing many hats and being Superwoman and Wonder Woman at the same damn time.
Read full blog – https://bonnechic.com/
#blogging#blog#money making blog#blogger#blog from scratch#wordpress#wordpress blog#earn money#online money
0 notes
Text
8 SEO Essentials For Driving Traffic To Your Website
Your website is all set up. You’ve hit “publish.” Now, you just need people to find you. This can be done in several different ways, although the most effective is SEO or Search Engine Optimization.
The SEO process utilizes a number of keywords and other tools in order to drive traffic to your website. Although adding the keywords to the copy on your site is easy (as long as you know or are a good writer), before you can start, you need to know which words to use. From keywords tools to website audits, these SEO essentials can help you debunk common SEO myths and move your website up in the search engine rankings.

1) Choose Your Keywords Tool Wisely
With so many keywords tools available online, it becomes difficult to choose the best one to perform a detailed keyword analysis. Five of the very best available are SEMrush, Moz’s Keyword Explorer, KWFinder, Keyword Tool, and Google Keyword Finder.
The latter is the most popular, as Google is really the powerhouse of keywords tools. It’s also free. However, most experts view Google Keyword Finder as a place to begin, but not the end of your search for appropriate keywords. The other four listed here are all paid tools, which means that you won’t be able to access them for free.
Many operate on a monthly subscription basis. Since you’ll need to update your keywords to match your new content constantly, this makes plenty of sense. Before you pick a keywords tool, go through the pros and cons of each, as well as the features. For example, some offer keywords that your competitors are using. If you really want to compete with them, then that’s a good feature to use.
2) Pick A Good Competition Rank Tracker to Compare Data
In order to ensure that your website is using the best possible SEO practices, you need to weigh it against some of your challenges. These competing websites also use search engine rank tracking (and if they aren’t, they should) in order to rise to the top.
So, if you’re wondering how to start with SEO competitor research, as with keywords tools, there are plenty of competition rank trackers out there. A quick web search pulls up dozens of them. So, why would you want to see how your opponents rank? Easy, you need to do this to see what SEO tactics they’re using in order to reach those goals. You can then set up your own SEO to match – or at least echo what they’re doing with your own keywords and tools.
Some of the best competition rank trackers can tell you everything about your competitor’s websites, down to their meta descriptions and title tags.
Read more – http://www.blog.dgmpeople.com/8-seo-essentials-for-driving-traffic-to-your-website/
0 notes
Text
HOW TO START A BLOG
If you’re looking to start a WordPress blog on Bluehost, you’re in the right place. Especially if you’re looking to start a blog the right way. In this post, I’m going to lay out the steps in order to create a WordPress blog; the only blog that you’ll need to be successful as a blogger.
Firstly, if you don’t already, you’re going to want to create a WordPress site and sign up for a domain name if you don’t have one. WordPress sites are the best to start a blog. They give you 100% control over your look and feel and you are able to customize your site as you like. Bluehost offers a free WordPress site and a free domain name when you sign up with them for hosting.

This post may contain affiliate links. Read my full disclosure for more information.
Today, you will learn how to create a blog on your own and how to start WordPress blog on Bluehost. Blogging has changed my life and has allowed me financial freedom beyond my dreams. I love helping people and I love writing. I’m hoping to help you along your journey in starting your own blogging empire.1 The best part is that you can start a blog for just a few bucks a month. That’s less than a coffee at Starbucks. By starting your blog, you’ll also receive a free domain through my link as well. Act quickly though as I’m not sure how long these low prices will last!
Click here to start a blog on WordPress, then use the steps below for easy directions.
Read original article – https://bonnechic.com/how-to-start-a-blog-2/
0 notes
Text
Putting Threat Intelligence to Work
Last month I attended the FS-ISAC Fall Summit and was thrilled to see the overwhelming interest in making security operations more efficient and automated—confirming that the financial industry is shifting from detection-heavy investment to the operationalization of security.
The summit revolved heavily around “strength in sharing.” This topic led to several heated debates focused on the deluge of both public and private threat intelligence feeds and which, if any, should be shared as the act of sharing could open the door for further exposure.
This focus on threat intelligence bled into the vendor exposition hall, where 20% of the booths were leading with messages around threat intelligence, making it the hottest buzzword at the summit.
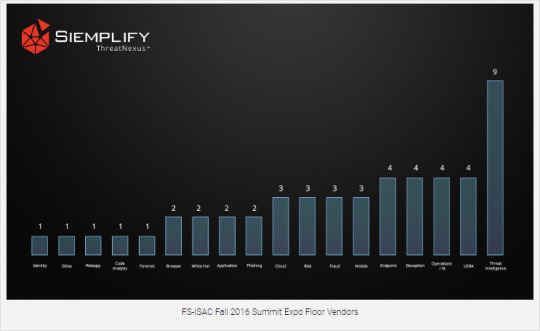
However, in almost all of my one-on-one conversations and demonstrations with CISOs, SOC Leaders, and analysts, it was common to hear “Whew, I thought you were trying to sell us more threat intelligence” and “the last thing we need is more security data.” I noticed a large sense of relief when discussing our approach and methodology around integrating threat intelligence into real-time security operations.
It seems the threat intelligence vendors are missing the mark.
Read More: https://www.siemplify.co/blog/putting-threat-intelligence-work
0 notes
Text
The Benefits of Semi-Automation
In football, planning every move down to the smallest details is everything. Any coach worth his or her salt has a playbook of strategies and every move, as impulsive as it may seem, has been carefully calculated with perfect “If this, then that” precision, before it ever took place. Yet, although every play has been pre-charted, effective execution relies on the adaptability of players in the moment and a keen understanding of the adjustments that need to be made “in game”.
When it comes to the security of corporate data, it’s not all that different from football. In order to be ready for anything that comes your way, all aspects need to be planned and mapped out beforehand, automated with a predetermined course of action – in the vernacular, “IFTTT”. This security playbook is called automation and it’s an imperative part of keeping all parts of a security operation workflow moving together in precise and accurate motion.

Automation: It’s not all or nothing
In the complex corporate security environment, automation is increasingly the “go-to” answer for organizations lost in a sea of alerts, logs and data. For many, it’s the only way to address their most critical processes and it’s what keeps them moving from task to task in a fluid manner. But there is a danger in putting too much faith into automation and orchestration alone. Organizations often turn to automation looking for a technological cure-all for their security woes, but while they are very good at what they do (at least theoretically), many security professionals are wary of handing off their most critical processes to a black box that cannot make up for the human intellect element.
Machines are not people and as such, do not waiver from their predetermined playbooks, sometimes to the detriment of the goal at hand – that of keeping corporate data secure. As Gartner security analyst Anton Chuvakin points out. “There is – at this stage of security technology development, at least – GOOD AUTOMATION and EVIL AUTOMATION. Longer term, we will certainly see more automation and more domains of information security (cybersecurity, if you have to) covered by automation, BUT I’d be willing to bet anything that the profession of a security analyst will never be full automated.”1
Read More: https://www.siemplify.co/blog/the-benefits-of-semi-automation-and-why-security-analysts-could-learn-a-lot-from-football
0 notes
Text
5 Reasons Why Security Operations Need More Than A SIEM
SIEMs are mandatory tools for forensic security teams, aggregating logs from a multitude of sources, exploring within a dataset, and auditing thoroughly. But anyone who’s tried to run their security operations solely on a SIEM (Security Information and Event Management), knows all too well its limitations:
1. Hard to connect the dots
One of the major challenges when using security monitoring and analytics tools is how to deal with the high number of alerts and false positives. Even when the most straightforward policies are applied, SIEMs end up alerting on far too many incidents that are neither malicious nor urgent. The goal is not to be alerted on every possible incident, but to identify, in real-time, the incidents driven by actual malicious activity. Getting there can be a cumbersome process, requiring detailed investigation and a series of diagnoses. Typical scenarios might include: pinpointing the IP address of the suspicious user activity, identifying the relevant logs and determining, which devices were affected. Only then can a researcher decide if the threat is real. Connecting the dots is indeed cumbersome and time-consuming. During this process the race against the attackers is at risk and a backlog of unhandled incidents is created.
2. Insufficient correlation rules
The out-of-the-box, correlation rules of traditional SIEM solutions are insufficient to address the needs of today’s organizations. They need to be extensively configured to meet the unique requirement of the organization. This a time-consuming task requiring significant technical understanding of the organization’s cybersecurity infrastructure.
Another major challenge lies in the fact that it’s impossible to create rules broad enough to factor every conceivable event. New threats are continually emerging and changing and SIEMs need to be continuously maintained in order to adapt to the evolving landscape. The result is that most SIEMs end up running with limited coverage, particularly around correlation of activities.
3. Challenging user-experience
SIEMs are capable of monitoring logs from a multitude of locations at once, striving to eliminate the risk of missing important events. They receive information from various endpoints by pulling or accepting pushed event data, triggering alerts according to predefined correlation rules. Using SIEM dashboards, SOC teams should be able to view and analyze event information in real-time. However, as the organization’s network expand and data accumulates, security professionals are unable to see the log’s origin, user identities, user activities, and if they could be a potential threat.
SIEMs typically show all network and log activities in a tabular format, making it difficult to quickly get insights from the data. Even if the event data is organized by categories with defined policies, viewing the entire network in one consolidated display is still challenging.
Read More: https://www.siemplify.co/blog/5-reasons-why-security-operations-need-more-than-a-siem/
#Security Operations#Securityoperation#siem#security automation and orchestration#security orchestration tools#cybersecurity
1 note
·
View note
Text
BRINGING MILITARY INTELLIGENCE TO SECURITY OPERATIONS
Transforming the way enterprises perform cyberthreat analysis, Siemplify emerged from stealth mode today with the first security operations platform to employ the same advanced cybersecurity methodologies used by leading military intelligence organizations. The Siemplify Threat Analysis Platform automatically correlates security alerts, identifies and prioritizes incidents, and graphically depicts the complete threat chain, setting new standards for time-to-insight and time-to-remediate. The Platform is available worldwide for commercial deployment.According to a study conducted by HP and the Ponemon Institute, companies need an average of 46 days to resolve a cyberattack. “The problem is not detection per se but discerning the threats hidden in the noise of thousands of alerts generated by the disparate security monitoring systems,” said Amos Stern, CEO and co-founder of Siemplify. “This makes it impossible to see the broader attack chain and identify root cause quickly.”
THE GAME CHANGER
The Siemplify Threat Analysis Platform disrupts the status quo with real-time graph analysis and by applying methodologies gained from military intelligence to cybersecurity:
Contextualization sets the stage by intelligently consolidating, correlating and analyzing threat indicators in real time from throughout a company’s existing cybersecurity infrastructure.
Visualization and modeling tools supercharge incident response by presenting prioritized threat information as visual story lines, enabling analysts to identify root causes in real time, pivot across data sources and drill down into every element of the attack from a single console to minimize resolution times.
Read More: https://www.siemplify.co/blog/siemplify-launches-with-threat-centric-approach-to-security-operations/
0 notes
Text
THE FUTURE OF SECURITY OPERATIONS - SIEMPLIFY
For the past 13 years, I’ve been heavily involved in the military intelligence community and the cyber security industry, setting up cyber defenses and training security personnel from leading enterprises and government organizations. During that time, I saw first-hand how cyber tools failed to address the operational challenges faced by security teams. So I teamed up with Alon and Garry to build a new kind of security operations center (SOC) platform. The Siemplify Threat Analysis Platform, which we launched today, is built from the ground up to address today’s real-world security challenges. It brings a “command-and-control” model to the SOC, combining real-time threat analytics, visual investigation, and incident response. See, what I found repeatedly when engaging with SOC teams was that all too often they were alerted to a threat — and a thousand other items. In fact, the security teams were inundated with so many alerts that they couldn’t identify the relevant ones. When they did identify threats, they lacked the visual tools to map and analyze them. The teams were further hampered by having to switch between security tools and tap into data repositories spread across the enterprise, which often necessitated mastering complex query and technical skills. Why So Many AlertsThreat detection is not a binary decision of “block” or “allow.” Security tools can’t always be 100 percent certain they will alert when something is suspicious. Because there are many fronts to protect there will inevitably be many different detection systems responsible for a different layer in the organization. This creates a situation in which detection systems fire off alerts individually and agnostically, giving security teams only pieces of the puzzle. Security teams are forced to analyze and make sense out of all this machine data and build the bigger picture. As more detection systems are added and attacks become more sophisticated, building that picture has become exponentially more complex. Minor, routine incidents trigger a flood of alerts that distract security teams. Threat actors leverage this fact to simultaneously employ multiple types of attacks and multiple attacks of the same type to generate a tidal wave of alerts, masking their true goals. The Answer: A New Kind of SOC Platform To solve the challenges of modern threat detection, we drew on our experience in military intelligence. Like cyber-security analysts, military intelligence analysts are expected to analyze and investigate threats, and initiate appropriate action. And like security analysts, intelligence analysts are hired for their ability to understand the meaning of data, not their technical ability to write a database query skills. And as such, the tools available to intelligence analysts aim to eliminate the technical complexity of intelligence analysis. They process, normalize and correlate the raw alerts and data coming from various surveillance sources, allowing the intelligence analysts to focus on the bigger picture and easily initiate the necessary response. SOC platforms need to adopt a similar role and focus on enhancing human cognitive abilities. They need to be “command-and-control platforms” and eliminate as much complexity of threat analysis and incident response as possible. They also need to level up and make threat analysis and incident response easier by acting as a security integration fabric, pulling all available security tools and analytics into a single pane-of-glass. Security analysts would then be able to focus on their real job – understanding the patterns and higher order of meaning of security events.
Read More: https://www.siemplify.co/blog/the-future-of-security-operations-platforms/
0 notes
Text
5 Best mobile security apps in Android & iOS, Free Download

There are a lot of security issues arising as we move ahead in the digital world. People are also increasingly using mobile devices more and more than a personal computer. As there is a rise in mobile use, there are threats too that may bother us. In this scenario, if you are asking yourself: ”Do I need antivirus for Android?”, you are already on the right road. Yes, you need it.
We will discuss here the best android antivirus apps and best iOS antivirus apps.
It is not difficult to predict that today almost every user knows that they need a security application for their desktop. But, does everyone know that they need the same on their mobile devices? Could be or could be not. Why do you need a mobile security app? You need it simply because there are so many different types of nasty malware which can cause a great deal of damage to your device, your privacy, and even your bank balance. If you don’t want to become a victim, you will need to take preventive steps.
Read more about the top 5 free security app for Android and ios
#mobile security#security#Smartphone Security#Phone Security#iphone security#cyber security#cybercrime#cyberattack
0 notes
Text
Mobile Payment Risks and Prevention Steps
What is the Mobile Payment?
The method of payment for the product and services between the buyer and the seller is the mobile phone that plays a key role in the realization of the payment. Recently, the scales of convenience in the daily lives of people have improved drastically with the introduction of internet. From laptops to iPads, we are now successfully using smartphones. The barriers of communication were crossed long back with the help of the mobiles and which has now moved to the easy payment options after all. Any technology advancements generally associate some risks and challenges to it. The Mobile Payment Risks is one such question that risks your mind due to the increase in the number of internet crimes. Want to do the payment online but still not well enough introduced with the internet security tips? Don’t do that to yourself.
Introduced about a decade ago, the adoption of payment methods with the help of the mobile was a little low.
What are the Mobile Payment Risks?
The Risks associated with the Mobile Payments affect both the parties, that is, the Users and the Service Providers.
The new process creates new security vulnerabilities. The mobile payment includes Over The Air transmission. This may create or give rise to the new leakage points of the payment credentials. The Security Vulnerabilities leads to identity theft, information disclosure, and replay attacks.
Read more about it — http://gotowebsecurity.com/mobile-payment-risks-prevention/
0 notes
Text
What it means to be an "ethical hacker"
Forget all the glitz and glamour that Hollywood would lead you to believe. Being an “ethical hacker” (sic penetration tester) as a profession is an extremely difficult job with its fair share of ups and downs.
As a pen tester you are required to be the foremost technical subject matter expert on many different topics. Businesses, organizations and large corporations rely on you to not only find every vulnerability within their architecture (hardware AND software), but also give them accurate and precise information on how to protect themselves and mitigate these vulnerabilities. This requires you to understand the underlying technology behind networking, specific server OS’s and how they integrate with the application layer, services and middle-ware, etc.
Without knowing these things you cannot be a successful pen tester; the onus is on us to learn as much as we can all the time as the environment we are working within is ever evolving. We have to wear the hat of a programmer occasionally, requiring us to know scripting languages, we have to be experts in COTS tools as well as open source tools. We also have to be technical writers, as what good is finding vulnerabilities if we don’t report them.
If you want to be a truly successful “ethical hacker”, penetration tester, cyber security engineer, etc it is up to YOU to learn as much as you can all the time. The satisfaction you can feel once you reach a certain level of knowledge and practical skills can be awe-inspiring, however, when you snap out of it you start to feel as if you truly know nothing again as everything is changing around you constantly with new research in different fields progresses, or new technologies emerge.
Becoming a student for life is key. Through dedication and persistence you can accomplish anything.
- SC
35 notes
·
View notes
Link
143 Million people, and all of their personal information, has been exposed to hackers. Including my own. I would recommend checking to see if yours has as well.
Speaking from experience, identify fraud *really sucks*
699 notes
·
View notes
Text
9 Reasons why users still struggle with online security

The struggle and challenges for safeguarding the cyber world is immense. It seems like everyone considers himself to be an expert in terms of cyber security but still no one’s safe from the innumerable online threats whether they’re viruses, malware, Trojans, hack attacks or any other DDoS attacks. This leads to the conclusion that each and every user of internet should learn about all the reasons because of which they are even now struggling with the online security. If you still don’t even know the difference between the phishing or malware, you really need to improve your knowledge about cyber security tips.
1. Due to abundance of security software as well as tools
2. Online Security Mistakes
3. Lack of awareness among the users about the newer threats
4. Almost no security software is secure totally
5. The one solution for everything does not really exist.
6. Many tool developers often forget about the security updates
7. VPNs are still Infamous
8. Social networking sites getting fierce in spring the users
9. Password Management
Read full blog in details here- http://gotowebsecurity.com/9-reasons-users-still-struggle-online-security/
0 notes
Video
youtube
Ethical Hacking Course: Module 03 - Scanning Lab Session.
Subscribe for the video channel here - https://www.youtube.com/channel/UCVAhYXGcjcNWcJpx0tY7D5Q
0 notes
Text
Security Measures For App Developers To Handle Cyber Attack
Anyone who is going to design the app needs to think about its proper security measures that need to be taken because it will in the most cases been attacked by dedicated and very skilled attackers. So what would be the app’s key function for security mechanism? It surely needs to react to those attackers in a controlled way. The mechanism we’re going to talk about often incorporates some mix of defensive and offensive measures, which are, of course, designed to take the attacker out of control and to confuse him, while the evidence of the event is taken and noted. These measures have some tasks, which we’re going to talk about and explain each one properly.

Handling errors
This is the first mechanism. It doesn’t matter how much effort or validation some application is made, it is often actually quite open to vulnerabilities and some of the unanticipated errors may occur. This is why we need to learn to defend ourselves and our systems, by learning as much as we can about the cyber security tips. The errors we mentioned, may come even from the actions of its regular user, and these errors are most likely to be identified during the functionality and of course, the user’s acceptance of testing.
[Learn more about the security measures]
0 notes
Text
Ransomware And Cyber Attacks Are On Rise In 2017
Most of all the three major industries are affected. It’s not hard to guess they are financial services, public sector, and healthcare. If you look at 2016 statistics, you can easily realize that the number of ransomware and cyber attacks has doubled in this year. How will it go further this year, we will see, but no one predicts the reduction of this incidents. Ransomware attacks are also seen in the public sector and education, manufacturing, and the list goes on. These are serious internet security threats.

Most of these companies are not even close to being secure. But, to be honest, they aren’t even working on their own security. They are rather willing to pay to hackers to return them their data on any other personal data or property research (which are the hackers most usual targets), then to invest in their safety and security. There are so many internet security tips anyone can find and use, especially the big and important companies, but also social security tips.
Ransomware in the news, as analyzes tells us that there are more than 51% data involved in some type of malware attacks. Isn’t that frightening? Yes, it is, but more frightening is that the ransomware and cyber attacks are not decreasing a bit, but the opposite. It’s even expected they will just get more and more expected on a regular basis in the ongoing year. [Read Full blog]
#cyberattack#cybersecurity#websecurity#webattack#malware#virusattack#online threat#website attack#virus attack
0 notes