Text
What Is Staking In Crypto - Learn How The Process Works

Cryptocurrency staking refers to the process of storing crypto coins in a cryptocurrency wallet to get an opportunity to validate transactions in a block. While staking crypto, the individual also receives a reward. The development of the cryptocurrency industry has paved the way for the emergence of the latest ways or modern routes to make money online. This is available to ordinary people as well. Cryptocurrency trading, crypto staking, crypto investing and cryptocurrency mining are some of the many ways.
0 notes
Text
What Is Crypto Staking - Understand This New Technology

Cryptocurrency staking refers to the process of storing crypto coins in a cryptocurrency wallet to get an opportunity to validate transactions in a block. While staking crypto, the individual also receives a reward. The development of the cryptocurrency industry has paved the way for the emergence of the latest ways or modern routes to make money online. This is available to ordinary people as well. Cryptocurrency trading, crypto staking, crypto investing and cryptocurrency mining are some of the many ways.
0 notes
Text
Victory Market - The Darknet’s Ebay
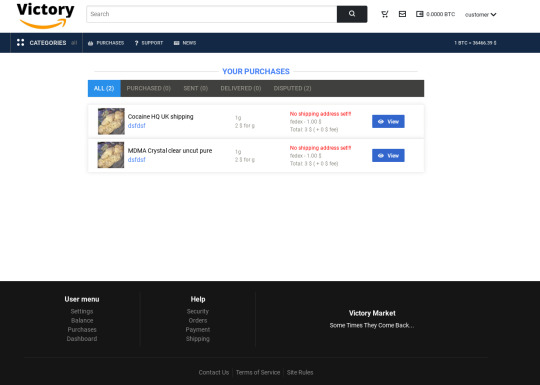
The darknet markets are ever-growing, and often some of them tend to come back after a fall. One of the most recent dark web markets that have emerged as people’s favourite is the Victory Market.
The Victory Darknet Market is one of those marketplaces on the Tor network that aims to provide its users with a hassle-free experience. The user interface is exceptionally clean, while it is much easier to navigate within the marketplace.
0 notes
Text
List Of Top Deep Web Links 2021

Get list of best deep web link and onion links searched via deep web search engine. These dark web Hidden Wiki links are updated and working. Some of the dark web links are as useful as the deep web Silk Road.
Receiving deep web site list of the authentic links is not that easy when in dark web there can be fraudulence. Dark Web Link on the other hand offers the authentic links to the deep websites anytime you search for them on their website. Along with this, you also get to know a lot of happenings around in the world of dark web through the darknet news that are posted on a daily basis on the portal.
1 note
·
View note
Text
How Has Bitcoin Helped In The Growth Of The Dark Web Activities?

The dark web activities have been massively influenced by the emergence and growth of Bitcoin and other cryptocurrencies and altcoins. With these, there has been a massive growth in the variations of the dark web activities, including the positive and the negative ones. This article is all about the cryptocurrency Bitcoin and how it has helped in the growth of dark web activities.
0 notes
Text
Royal Market Darknet Marketplace - A Brand New Dark Web Market
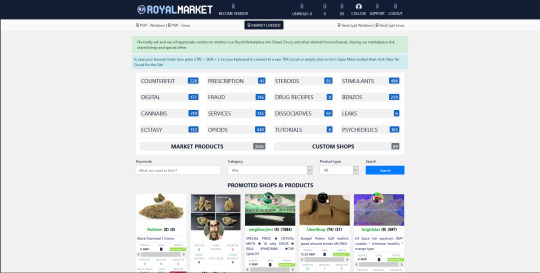
Royal Market is a brand new dark web market hosting a lot of unique features. It is entirely walletless and depends on the direct payment system. It accepts Bitcoin (BTC) currently and plans to integrate Monero (XMR) in the future. It possesses a customized vendor shop with a professional referral system and Royal Market Points (RMP). The darknet market enables FE and PGP.
0 notes
Text
Liberty Market - The Multi-Vendor Dark Web Market
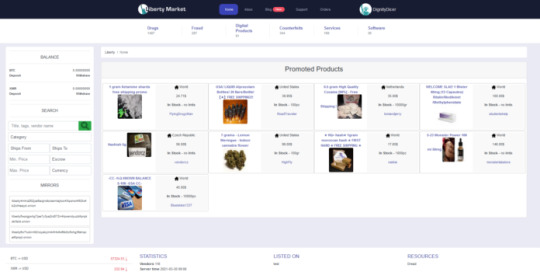
Liberty Market is a new dark web market accepting Bitcoin (BTC) and Monero (XMR) cryptocurrencies as a payment mode. It facilitates the Escrow mode of payments and supports FE. 2-FA via PGP and anti-phishing are enabled for additional security. The listings receive cloning options while features star-based imported feedback.
2 notes
·
View notes
Text
Top Darknet Markets List - Dark Web Links 2021

After going through many websites and blogs, unfortunately, there is no proper place where you might find a complete and comprehensive list of all the darknet markets at a single place. What we found was a list of hidden dark net marketplaces that were either shut down or were, in fact, defunct by law enforcement and in some cases only URLs without any additional information. We have compiled and gathered for you to make a complete list of these Tor .onion url directories which also features the best dark web websites where all your needs and requirements can be met.
It is not only just about the hidden darknet market list but we also provide you with tools and techniques which will actually help you surf the dark web directories with safety and precaution.
0 notes
Text
World Market: An Alternative Darknet Marketplace For The World
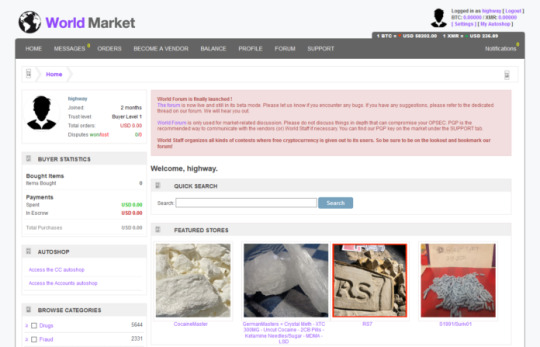
The World Market is the latest renowned CC shop on the darknet links marketplace. The marketplace has a wholesome listing of various drugs that are most sought out by the buyers and falls in the categories Stimulants, Cannabis, Prescription drugs, Dissociative and more.
The dark web market offers an automatic CC shop feature and provides various services like hacking and counterfeit products. Additionally, they have a zero-tolerance policy to keep away scammers. The marketplace is known to support BTC payments as of now.
If anyone wants to be a vendor in the market, the user can do so by registering as a vendor through their “become a vendor” section. The vendor shop also permits the exchange of Monero with Bitcoins.
1 note
·
View note
Text
Darkode Reborn: The All New Multi-Purpose Dark Web Market

Dark0de Reborn is a universal marketplace offering you everything that you require. It offers some cool features, more than what one can expect. It is one of those darknet marketplaces worth a try!
A universal marketplace combining everything you need. Security is its top priority using AI, absolute encryption, and BTC/XMR they prioritize your safety. Dark0de features everything from Escrow/FE/MultiSig payments to a secure Coin Mixer and Coin Switch service and much more.
0 notes
Text
Best VPN services for online security and privacy

A VPN connects your computer system to the server, and then you can browse the internet by using the computer’s internet connection. It allows you to stay anonymous while browsing the dark web. That is why it is good to use a trustworthy VPN provider. We've tested several of them, and these are the list of best VPN services after gaining years of experience on the dark web link.
https://medium.com/the-capital/the-best-vpn-service-providers-2021-with-comparison-and-reviews-dark-web-link-6422b4e446e1
0 notes
Text
The Best VPN Services for 2021

A VPN, or virtual private network, is one of the best ways to guard your online privacy and maintain your data security. We've tested several of them, and these are the list of best VPN services after gaining years of experience on the dark web link. We have compiled the foremost trusted VPN Service Providers to save you from the biased opinions you may find elsewhere.
1 note
·
View note
Photo
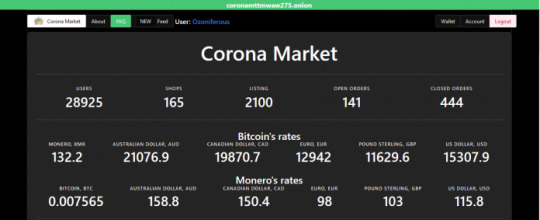
Corona Market is a state-of-the-art dark web market with a wonderful frontend offering safety, speed, and a fairly large variety of drugs. It supports payments in Bitcoin (BTC) and Monero (XMR).You can pay via both Monero and Bitcoin using traditional escrow and FE payment methods. Monero is strongly recommended for both anonymity and security.
0 notes
Text
Which Gender Is Better At Memory?

Men and Women have different memories due to their physiological and psychological traits that are displayed in the lifetime. According to the researchers from Karolinska Institute in Sweden, episodic memory is better among the women than in men. Women have greater advantage than men when verbal processes could be used for remembering where as men were at an advantage with information based on more spatial processing. Women fair much better than and are outright better in terms of all memory measures till they reach 40- 50 years of age.
Women have better understanding to remember verbal information such as words, sentences, texts and objects and also of location of objects and movies. The researchers believe that study raises the new question of how cognitive differences among the sexes may have on everyday life even of the differences noted been small.
Studies also show brain fog and forgetfulness after menopause. Studies also show that women are more likely to develop Alzheimer’s disease than men, although not much is known about why that is or when they become more vulnerable.
Steps To Improve Memory:
· Getting proper sleep can help you retain memory.
· Having a proper balance diet and doing exercise can improve brain functioning.
· Brain simulating games and puzzle such as cross words show positive effects on improving and maintaining memory with age.
· Try to gain acquire new skills which will help the brain stay flexible.
· Make a proper list of thing you want to organize and avoid multi tasking which does not give time to brain to process and store information.
· Avoid non healthy diet like food high on carbs and sugar can adversely impact memory while food with exercising regularly will increase the Brian functioning.
Definitely gender affects memory in a certain way but there are steps to improve it as well. Follow the exhaustive list to retain and avoid brain fog and forgetfulness.
0 notes
Text
Dark Web Tools and Services That Present Enterprise Risk
Dark Web Definition

Deep Web is the major part of the internet which consists of 90% of the internet. The other two parts comprises the internet world is the surface web and the Dark Web. The Dark Web is sometimes also referred to it as the Darknet. To understand all the three layers of the internet that consists of all the three layers mentioned above, the image that mostly resembles is the picture of an iceberg that is afloat.
The top most part of the iceberg that is visible from the outside can be understood as the surface web. The crust of the iceberg is also known as the visible web. The visible web comprises of web pages, websites that are listed in the search engines. Search engines like Google, Bing and Wikipedia have all the web pages in their directories. All the search results a user makes are tracked monitored and listed by the traditional search engines.
The dark web is accessed by using special software and web servers called centralized computers hosting webpage’s. The most common of these special software are TOR [The Onion Router] and I2P [Invisible Internet Project], says J. Eduardo Campos, formerly a cyber security advisor for a major tech company and currently co-founder of the consulting firm Embedded knowledge.
Dark Web Tools and Services That Present Enterprise Risk
The web tools and services that affect an organization which pose as a threat in the form of network breach or data comprise when the system gains access to Deep Web directories which is accessed with the help of Tor .onion urls directories.
· Infection or attacks, including malware, distributed denial of service (DDoS) and botnets
· Access, including remote access Trojans (RATs), key loggers and exploits
· Espionage, including services, customization and targeting
· Support services such as tutorials
· Credentials
· Phishing
· Refunds
· Customer data
· Operational data
· Financial data
· Intellectual property/trade secret
· Other emerging threats
Malware:
The Dark Web Links play a vital role in the spreading communities of malware developers; the principal Darknet are privileged environments for malware authors and botmasters. The numerous black marketplaces are excellent points of aggregation for malware developers and crooks that intend to pay for malicious code and command and control infrastructures. The use of Darknet represents a design choice for malware developers that use them to hide the command and control servers.
The list of malicious malware that were exploiting both the Tor network and I2P dark net to hide their command and control servers are as follows:
i) Malware Using C&C In The Darknet:
Many types of malware are directly controlled by servers hosted on both Tor and I2P, and it is quite easy to find Ransom-as-a-Service (RaaS) in the Darknets. Below just a few examples of malware that were discovered in the last 12 months leveraging Darknets for their operations:
· 2017 – MACSPY – Remote Access Trojan as a service on Dark web
· 2017 – MacRansom is the first Mac ransomware offered as a RaaS Service.
· 2017 – Karmen Ransomware RaaS
· 2017 –Ransomware-as-a-Service dubbed Shifr RaaS that allows creating ransomware compiling 3 form fields.
ii) Shifr RaaS Control Panel
Malware authors use to hide C&C servers in the Darknet to make botnets resilient against operations run by law enforcement and security firms. The principal advantages of Tor .onion urls directories based botnets are:
· Availability of Authenticated Hidden Services.
· Availability Private Tor Networks
· Possibility of Exit Node Flooding
Security researcher use traffic analysis to determine to detect botnet activities and have proposed different options to eradicate it
· Obscuration of the IP addresses assigned to the C&C server
· Cleaning of C&C servers and of the infected hosts
· Domain name revoke
· Hosting provider de-peered
Remote Access Trojans (RAT):
It is a malware that infects remote computers and allows a remote attacker to control the computer for malicious purposes. They disguise as a legitimate program or file. After infecting a target device the threat actor gets accessed to the victim’s computer.
How to Prevent RAT from Vicious Attack:
Steps To Avoid Remote Access Trojans
a) Do not click suspicious links and do not download emails sent by unknown users.
b) Keep your computer updated with trusted anti-malware programs and make sure you update them regularly.
c) Configure your firewall in your computer regularly. If a malware infects a computer, it should not spread to other system in the network so easily.
d) Keep your operating system updated with recent patches and if possible use a virtual machine to access the internet.
Espionage (Targeting and Customization):
Intelligence on competitors gathered in a legal way can give a leg up in the fight for market share. But sometimes it’s not enough. Competitors send spies to gather information more often than you would think, judging by the news. Industrial espionage embraces illegal and unethical methods of collecting corporate data. It involves stealing intellectual property and trade secrets to use them for a competitive advantage. The theft of economic information sponsored by foreign states is called economic espionage. It’s done not just for profit but for strategic reasons. Usual targets of industrial espionage are:
· Trade Secrets: While definition of “trade secret” varies from country to country, it generally means protected information about existing products or products in development. This information may help your rivals make their products more competitive or even bring a similar product to the market faster than you can.
·Client Information: Data of your clients, including their financial information, can be used to steal business or can be leaked to damage the reputation of your company.
·Financial Information: Financial information about your company can be used to offer better deals to your clients and partners, win bids, and even make better offers to your valuable employees.
·Marketing Information: This will allow your competitors to prepare a timely answer for your marketing campaigns, which, in turn, may render them ineffective.
Steps to help avoid trouble with the Dark Web
Once data ends up on the Dark Web Links Hidden Wiki there's very little that can be done about it. It's best to avoid this from happening to your company, employee or customer data. The following best practices can help.
1. Prohibit employees from using Tor .onion url directories
If employees are allowed to access the TOR network, they can easily expose your company to damaging material and/or malware. This would be particularly detrimental to your corporate network, says Wagner. Provide clear guidance in employee manuals and train employees on 'clean' internet use, advises cyber security attorney Braden Perry, a partner with Kennyhertz Perry. Use software to block TOR. Make it clear that corporate investigations will be initiated if management suspects that this rule is being broken.
2. Educate employees on security protocols.
The end user is the weakest link in your protective measures for your network, says Campos. This means it's important to teach all employees about cyber security measures and compliance with your company's policies, he says. The more aware and trained your employees, the better. He went on to add.
3. Limit employee access to sensitive data. It's a good idea to operate on a need-to-know basis when it comes to company data. The fewer employees who have access to company and client sensitive data, the less likely your company is to experience a breach.
0 notes
Text
Differences between Deep Web and Dark Web
One of the most common questions people have about the existence of the Dark Web and the Deep Web is the differences between them. It has been seen a multiple times that people tends to confuse between both the terms while use them interchangeably resulting in a total mess. Well, in this article, I will be clearing the major confusion between the Deep Web and the Dark Web. Also, as a bonus, a different part of the internet will be revealed. To know about everything in details, please read the article till the end.
What Does Deep Web And Dark Web Essentially Mean?
The internet is a huge place and is divided into two basic segments. The first one is the surface web while the other one is the Deep Web. The surface web (also known as ClearNet) is that part of the internet that is accessible to the general public through standard browsers like Google Chrome, Mozilla Firefox, and Internet Explorer etc. The Deep Web on the contrary, is that part of the internet that has been kept hidden from the general people and contains humongous information. This information is very confidential and thus requires a covered space out of the reach of the common people via the general search engines. The Dark Web is just a smaller division of the Deep Web, probably 0.01% and should not be used interchangeably. The Dark Web deals with certain illegal activities as well.
What Does Deep Web and Dark Web Bears in Them?
The Deep Web acquires a larger part of the internet or more precisely the submerged internet. It mostly contains the benign websites such as the password protected email accounts, databases, certain parts of the paid subscription or premium account information such as Netflix or the websites that are accessible through an online form located in the Deep Web Directories. As the matter of fact, it would be too easy to access your email account by searching just your name if Deep Web would not have existed and there would just have been only one internet as a whole, the surface web. The Deep Web has an estimated size of 400-550 times (record of 2001) than that of the surface web.
The Dark Web on the other hand is relatively small than that of the Deep Web and the Dark Web websites accounts to just thousands. The websites that are located in the Dark Web are especially characterized by their application of encryption method and software that makes the users, their identities and location, all anonymous. The encryption feature of the Dark Web has made the conduction of illegal activities much easier. The illegal activities include pornography, illegal drugs and firearms sale, services such as hire-hitman, human trafficking, gambling. Unlike the Deep Web, the Dark Web contains a lot of Dark Web markets that helps in the procurement of illegal stuffs giving rise to illegal activities and services. As for example, there are even instances of tutorials floating in the Dark Web that clearly states how to cook a woman live. Yes! It’s that scary and hideous place.
Secret Place on the Hidden Web
One of the other facts that come our way while stating about the Dark Web and is not available on the Deep Web is the existence of Red Rooms. Well, Red Room might give you the visuals of a room in red colour, but this is not exactly what Red Room deals with. So, what exactly is a Red Room? Red Room is probably a room where illegal activities such as murders and physical tortures are openly shown against payments in Bitcoins or Cryptocurrencies. The viewers pay a lot of money in Cryptocurrency to the moderators of the websites carrying on such activities for watching a complete session. They even place bids for watching a particular torture done in the red room. Terrorist groups are often involved in these.
To conclude,Dark Web and Deep Web though exist in the same realm are way different from each other. While Deep Web serves as the storehouse or chest for the humongous information related to the organizations (both government and public), Dark Web relatively serves as the section of the internet where mostly illegal activities are carried on. The Deep Web does not contain anything called the Red Room while the Dark Web possesses Red Room concept. Markets are available on Dark Web while Deep Web does not contain any sort of markets. To access the sites in Deep Web, one has to have the address for the particular website as the websites are hidden and its access is limited. In order to access the Dark Web websites, one has to use the TOR browser, VPN and .onion links
0 notes
Text
Advantages and Disadvantages of Dark Web
Dark web has been the most intriguing aspect of the Internet these days as the dark web has already amazed hundreds and thousands of people in just a short period. Speaking of the Dark web or the Darknet, it offers immense scope unlike the clearnet (the part of the internet that we utilize on a daily basis to search for any piece of information using the regular browsers - Google Chrome, Mozilla FireFox and regular search engines - Google, Bing, and Yahoo). For example, if you are a movie fanatic you might have been searching for one of the many rare movies, say, BackMask. While the clearnet cannot or might not be able to fulfill your dream of getting your hands on to the most wanted film, Dark web provides you with every scope to enjoy your most wanted rare movies.
Talking about the technological aspect, you might get a version of Apple iPhone at a much lower price on the Darknet than on the clearnet or surface web. As for a warning, an Apple iPhone acquired through the dark web could also refer to illegally copied or stolen versions of the same. Thus, in order to access and acquire things on the dark web, one needs to have a sound experience in the field. One of the most important reasons for the wide use of the dark web over the clearnet can be stated as the sense of community and freedom unlike the clearnet or surface web.
Advantages of Dark Web
Now we will go through some of the major advantages and disadvantages of the dark web in details:
1. Maintain Anonymity
One of the most luscious advantages of accessing the dark web is of course no doubt, maintaining anonymity. While anonymity and liberty go hand in hand, sadly enough, it attracts almost all of the criminal activities that defame the dark web in general and the darknet markets. It is a known fact that in order to access the broad spectrum of the dark web, one needs to use a special browser or browsing software package named as Tor or The Onion Router. Tor is free and open-source software that is used for anonymous communication that successfully masks your basic information such as your IP address, personal details (that you do not provide knowingly). Apart from TOR, there are some other browsers, but they do not offer user-friendly interface as TOR does. Here one thing needs a special mention. Tor does not guarantee a user complete anonymity whatsoever and it becomes important for the users to add an extra layer of protection such as a premium VPN.
2. Liberty of Speech
As already stated, anonymity and liberty go hand in hand. This refers that anonymity promotes liberty. While in some instances, voicing on personal experiences and thoughts on the clearnet might attract consequences or serious debates of all types. But something of the same type on the Dark web is nothing unobvious. The dark web or the darknet has also allowed overcoming censorship that directly connects us to the third benefit.
3. Political Activism
The deep websites links have resulted in a speaker for all the noble causes. The oppressive governments are a pure reality in the 21st century where information plays a major part or say a powerful weapon in these kinds of the regimes where its citizens' movements are strictly monitored on the World Wide Web in order to avoid the spread of the revolutionary ideas. The oppressive governments in most cases adopt a common measure which is blocking the websites especially those that are related to social media. As per this context, browsers such as the Tor appear as a solution to enable a safe communication line that is not just restricted to the national level but it also permits international denounce of certain situations. In the recent historical events such as the Arab Spring, the deep web has had a major role.
4. Knowledge
The dark web confines in it the largest virtual libraries that one could possibly imagine. Dark web has become an amazing space for all the students, teachers and the researchers as the matter of fact, what one can find in the dark web will not probably be available in the clearnet or the surface web. Dark web also offers you some of the literary papers, scientific finding and related documents that have not been made public and on the contrary could influence the health and the social beliefs of the large number of populations can also be traced down to the deepest sphere of the dark web.
5. Helpful Individuals
The dark web community is filled up with people of varied mind standards. Though it is difficult to spot the good ones, yet not impossible to track down at least one. Talking of those good ones, you can count in from doctors to investigators who dedicate both their time and effort to aid others altruistically.
Disadvantages of Dark Web
Here are the basic disadvantages that the dark web bears:
1. The Drawback of Dark Web Search Engines
As previously stated, the Dark web is a storehouse of the immense quantity of information that otherwise would remain inaccessible. On saying that, owing to the fact that the dark web bears huge amount of information, the dark web search engines tend to run slower than that of the standard search engines or the search engines that are made available on the clearnet or the surface web. The searches that are made on the Dark Web may also return sensitive personal information from the databases that are normally restricted and creating ethical dilemmas while leaving the individuals susceptible to fraud and identity thievery.
2. Untraceable Nature of Dark web
Dark web is mostly known due to its untraceable feature that has made it one and only frequently accessed part of the internet that helps thrive several illegal activities. Keeping it simple, it has become the corrupted hub of the criminal activity. Through this platform, some of the most frequent illegal activities are carried on such as illegal transfer of the drugs, weapons, hiring of contract killers and more. Even, illegal bidding marketplaces similar to E-bay has also cropped up in the bid to sell all of these illegal goods and the best part is that the law enforcement keeps on trying hard but fails to stop such an activity.
3. Unverified Content & Hoaxes
If followed closely, there are reports of the crowd funded assassinations and the hitman for hire. Nevertheless, some of these are believed to be exclusively scam. As for example, the admin of the renowned Silk Road was arrested by the HIS or Homeland Security Investigations for his website and has been alleged for hiring a hitman in order to kill six people, although the charges to this were later dropped.
4. Phishing & Scams
Phishing has become one of the most widely used techniques to scam the customers or users out there in the Dark web by cloning the websites and increasing the number of scam sites. The darknet markets are often advertised with the fraudulent URLS.
5. Ethically Disputed and Illegal Pornography
There are definite set of rules or law against making with the intent to distribute or sell child pornography often through the compromising of any website by distributing malwares to the website users. The sites do use complex systems of forums, guides and community regulation. Other contents that fall in this category include sexualized torture and slaying of animals and as well as revenge porn.
6. Terrorism
Terrorism has also found its existence through the dark web websites. There exists some real and fake websites that deliberately claim to be used by ISIL. One of them has off late been seized in Operation Onymous. During the Paris Attacks of November 2015, one such real site was hacked by an anonymous affiliated hacker group named GhostSec and replaced with an advert for Prozac. At one time, the Rawti Shax Ismalist group was also spotted to be operating on the dark web.
As a note of conclusion, the dark web will continue to entangle and fascinate to the extreme level everyone who uses the internet or who has come across such a segment of the internet. The Dark web is the storehouse of a huge knowledge base that could render technological evolution and as a species in general as well, when conjoined with other bits and pieces of information. Along with this, the darker aspect of the dark web will remain as darker as it is today or may darken way more. It will be more fascinating and lurking defining the human nature.
0 notes