Text
so there's another way of doing this that's only possible because testfire.net has its source code available publicly. more information about this under the cut:

so all the data about users is going to be stored in a database. there's a chance that the database is only on the device that's hosting the web server, BUT there's a chance that the database has been filled out in the source code. that is, it's put there so that anyone who wants to make their own copy already has a database filled out.

the database isn't going to be in the config folder (.settings) or the WebContent folder so we'll check the src folder. but you dont even have to go snooping around if youre smart about it. because files need to be properly labeled for ease of creation and maintenance, the database file is likely going to be marked as such. so we just search the directory. "database" didnt return anything so we try the common abbreviation, or "db".


this file has a ton of lines BUT if we're smart, we don't need to search through every one individually. because computers have a wonderful function called CTRL + F. the only question is what are we searching? well, we already know several usernames, and those are also going to be in the database. so let's start by searching "jdoe"

boom, headshot.
this requires a tiny amount of SQL knowledge. essentially, all of the information about the user accounts are listed in the following format
USER_ID then PASSWORD then FIRST_NAME then LAST_NAME then ROLE
we know this because of this part, which shows us the format:

for convenience, i've pulled the whole line and formatted it so it's easier to read. username and passwords are bolded, although we also get the full names of all of these users.
'admin', 'admin', 'Admin', 'User', 'admin'
'jsmith', 'demo1234', 'John', 'Smith', 'user'
'jdoe', 'demo1234', 'Jane', 'Doe', 'user'
'sspeed', 'demo1234', 'Sam', 'Speed', 'user'
'tuser', 'tuser', 'Test', 'User', 'user'
finding usernames/passwords for testfire.net
background: testfire.net is a "fake" website designed for pentesters to play around with. it is NOT a real bank and no one's information is actually being stolen here. this was an assignment for a class.


first we start by logging into the admin account, username: admin and password: admin. although a general SQL injection works on this site. for the inject, password is irrelevant.
other injects that work (note that's not a quotation, that's two apostrophes):
' or ''='
' or '1' = '1
or any other statement that will always be true
on the left we see we can "Edit users"


our assignment was to find username and password pairs. you'd think you could cheekily change the passwords of existing accounts or add new accounts to fulfill this requirement, but none of these options on the admin page actually work.

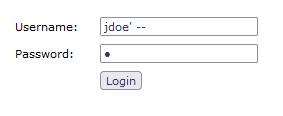
we can see the usernames of several users. since we know the username field is vulnerable to injects, we can now login to any of these without knowing the password.

this field is also vulnerable to injects. inject used:
' --
okay never mind post cancelled
i just checked the solution that my professor wanted and i shit you not its this:

these do technically work as username and password pairs. like, if you use them, you will sign in. in fact, i think you can just put anything other than a blank space for the password and it would count. but man. fuck this.
regardless, here are some actual pairs that i ended up finding. i cant quite remember how i found them, but i saw someone use "demo1234" as a password for both jdoe and jsmith, so i tested sspeed and its the same password. cant find the other ones though.
jdoe | demo1234
jsmith | demo1234
sspeed | demo1234
1 note
·
View note
Text
professor justified it with "hacking is cheating" like. I GUESS.
0 notes
Text
finding usernames/passwords for testfire.net
background: testfire.net is a "fake" website designed for pentesters to play around with. it is NOT a real bank and no one's information is actually being stolen here. this was an assignment for a class.


first we start by logging into the admin account, username: admin and password: admin. although a general SQL injection works on this site. for the inject, password is irrelevant.
other injects that work (note that's not a quotation, that's two apostrophes):
' or ''='
' or '1' = '1
or any other statement that will always be true
on the left we see we can "Edit users"


our assignment was to find username and password pairs. you'd think you could cheekily change the passwords of existing accounts or add new accounts to fulfill this requirement, but none of these options on the admin page actually work.


we can see the usernames of several users. since we know the username field is vulnerable to injects, we can now login to any of these without knowing the password.

this field is also vulnerable to injects. inject used:
' --
okay never mind post cancelled
i just checked the solution that my professor wanted and i shit you not its this:

these do technically work as username and password pairs. like, if you use them, you will sign in. in fact, i think you can just put anything other than a blank space for the password and it would count. but man. fuck this.
regardless, here are some actual pairs that i ended up finding. i cant quite remember how i found them, but i saw someone use "demo1234" as a password for both jdoe and jsmith, so i tested sspeed and its the same password. cant find the other ones though.
jdoe | demo1234
jsmith | demo1234
sspeed | demo1234
1 note
·
View note