#the text literally just says ''how to block ads on your android''
Text
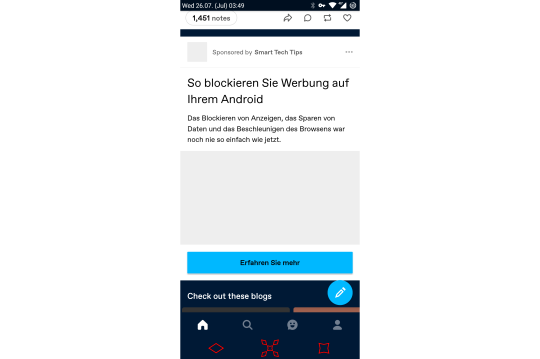
An ad about using ad-blockers on android devices... being partially blocked by the ad-blocker on my android device.
#oh the irony#the text literally just says ''how to block ads on your android''#also no idea why I get German ads#my phone is set to English as well as the tumblr app#yes I am in Germany but basing an ad's language on a user's language preferences seems like a better option than basing it on location
10 notes
·
View notes
Text
if you popped into the Ted tag in the past two or three days, you might have been hit with the sight of a supposed DM between “him” and a fan:
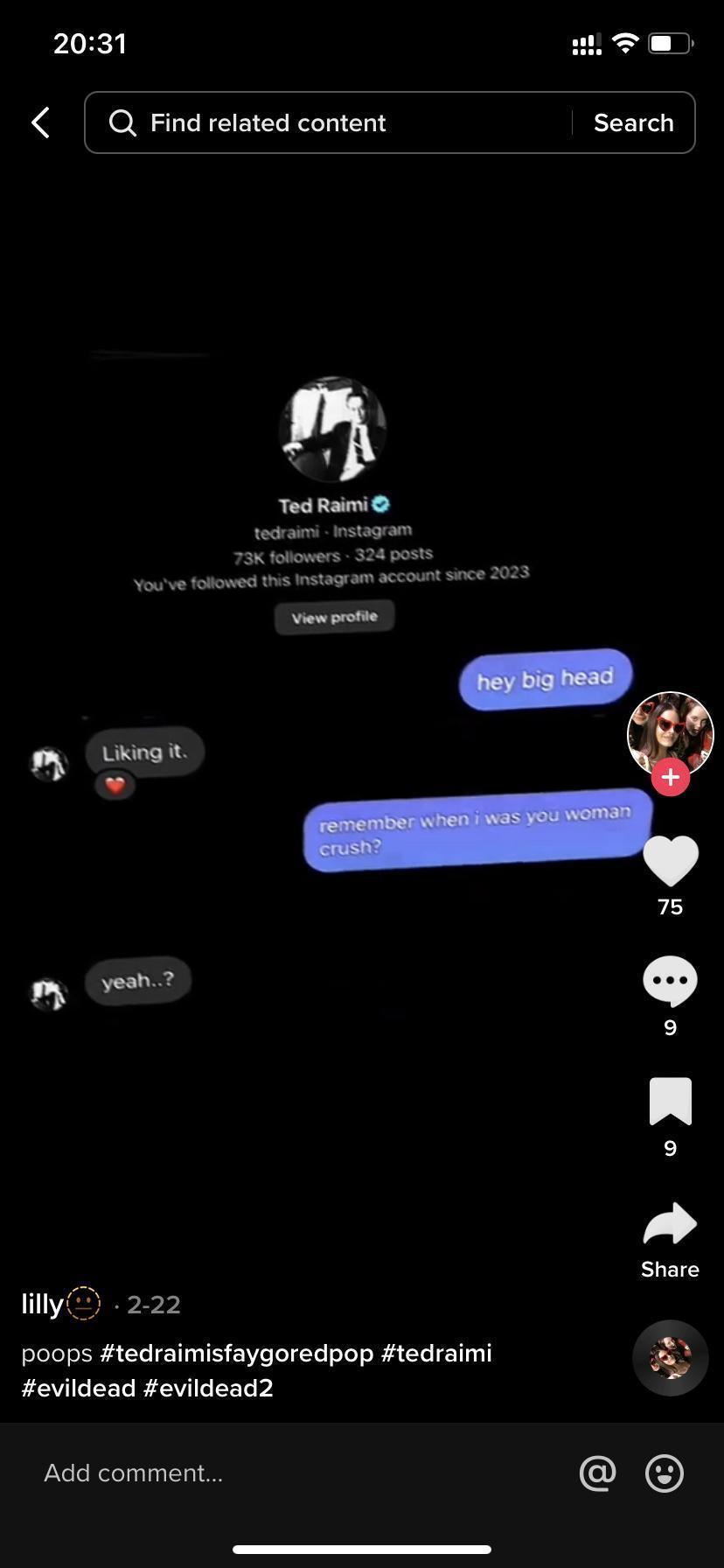
however, this appears entirely false and i’m fairly certain i can prove it’s fake:
1.) Ted doesn’t talk like that. it is the most jarring part of all, aside from that this was probably entirely fabricated altogether. i’m not saying i’m privvy to his DMs or texts and how he messages people but it’s so far off from how he interacts with people on social media that it genuinely doesn’t read as him at all
2.) the misaligned text and the randomly fluctuating text size. the text size is not congruent throughout, the first message is abnormally larger than the next 3 lines, and those lines don’t match each other at all - even with the shot taken at an angle as it is, they would not look like that tilted. it is not leveled flat and straight like normal text would - nothing about it matches what an actual message layout would appear as
3.) there is not a single timestamp or date included. it is impossible to hide timestamps with the current instagram UI at the very start of correspondence in DMs
let me walk you through it-
screenshots of DMs through iPhone:
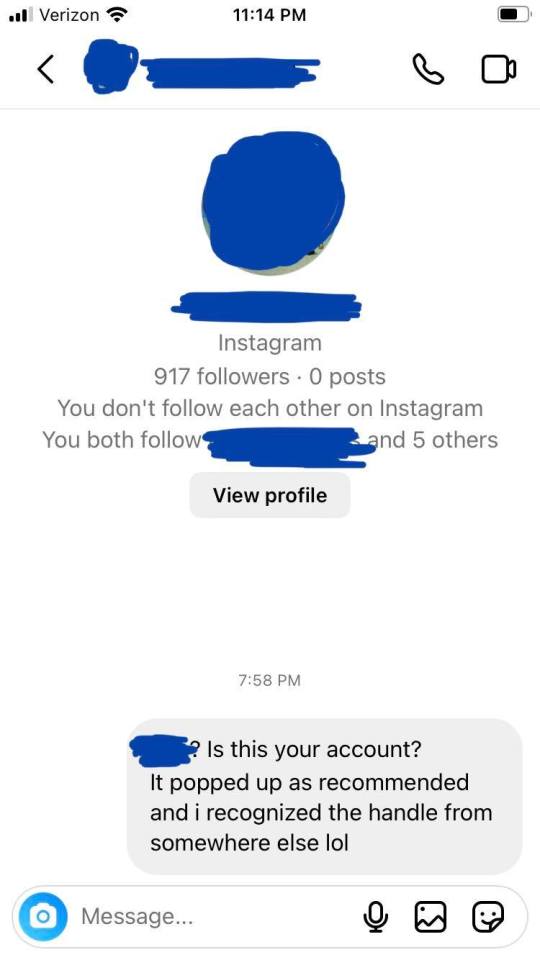
screenshots of DMs through Android/Samsung:
you can only get the giant PFP, the followers count, post counts, whether or not you follow each other, and any accounts you both follow from the very start of your DM correspondence - meaning this only shows up with the very first messages you send to an account. after sending more messages, the block of account information is no longer visible as it gets pushed up by further exchanged texts
you will also always have a date and/or timestamp at the top of the beginning of your first DMs, that’s not exclusive to one phone or tablet OS - the app itself is fairly congruent between different brands and their OSs. it is also not exclusive to accounts that follow each other or not
any other DMs from that point on will look generially like this:
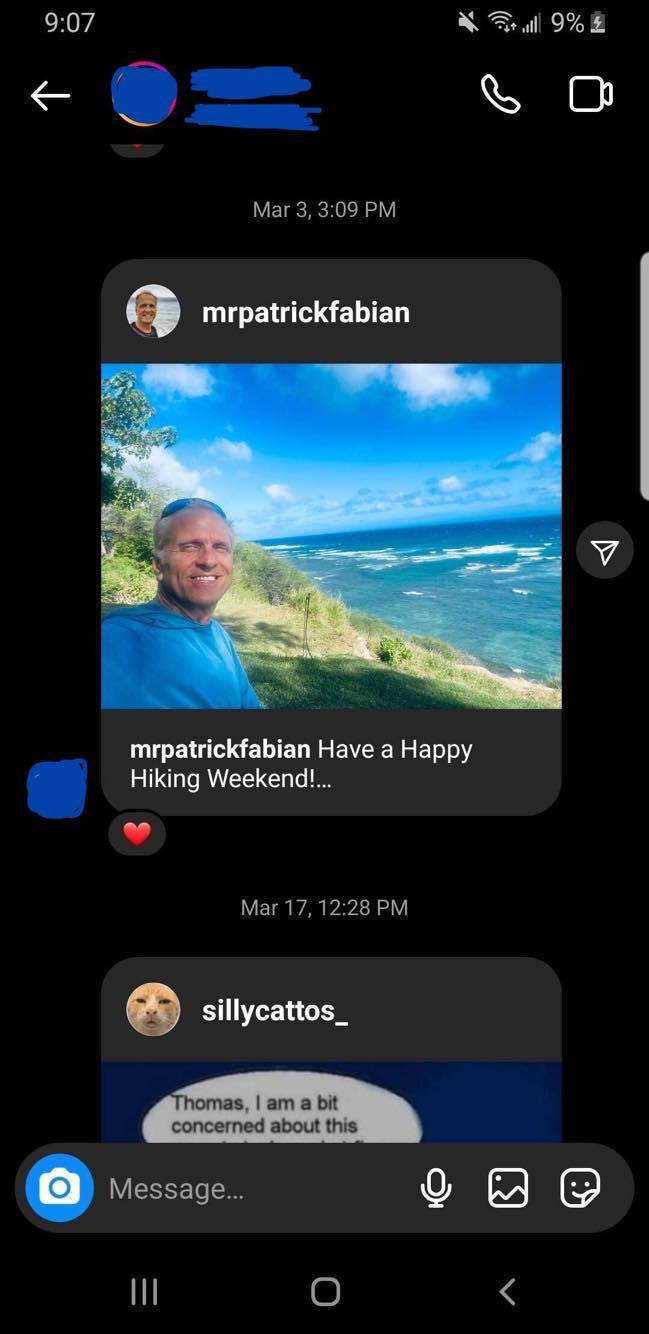
you can literally only get the giant PFP, follower count, post count, etc. from the very start of your correspondence, it disappears with the more messages exchanged. and it will not appear anywhere else except on mobile or tablet
all DMs look like this from desktop - it doesn’t matter which browser, because i tested it on Firefox, Chrome, and Edge (screenshots i can also share, if you want them) and they all are the same:
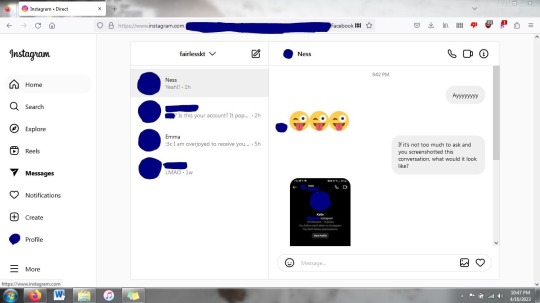
dates and timestamps still at the top of the start of message threads - you cannot remove dates and timestamps from the beginning of direct correspondence with the way the instagram UI is now - it will always show the date and/or time the very first message was sent. and the block of instagram account information will only appear at the very start of messages first being exchanged
also, the big PFP, follower count, post count, etc. is not available through desktop, only mobile and tablet, so it cannot be duplicated anywhere else
there is too much not adding up and the fact that it has proven impossible to replicate through conventional means leads me to believe and state with conviction that it is fake, manufactured
i’m not sure which app was used to do it, but based on how the picture was taken - the angle and the distance - leads me to believe a watermark or app interface was cropped out purposefully. there are multiple apps and sites out there that can be used to create such fake interactions, but beyond not knowing just which one was used, i’m also not going to exhaust myself trying to search more than i have
could i be wrong? yes, i’m not going to say that it’s impossible for me to be missing something, i’m not an instagram expert by any means
do i think i am wrong? no. too many things just don’t add up
i’m more than willing to eat my own words if everything i’ve just laid out can be proven wrong, but i genuinely cannot replicate what is displayed in that screenshot, which leads me to believe it is fake
it also lends precedent that she has been lying repeatedly about supposed interactions that i also believe have never taken place. but that’s for a whole different post of its own
if, again, anything could be brought to light to prove anything i just said to be incorrect, i would gladly recant. but i don’t see that happening. she’s locked down every account she has and the likelihood of Ted seeing any of the fuss being made about all this goes down every day, since he is so rarely online and interacts with so few replies and almost no @ s from people he doesn’t follow
10 notes
·
View notes
Text
Guess What? I’m Not a Robot RC Ch3
Chapter warnings: some swearing, offscreen shooting
Word Count: 2,902
Masterlist
Previous chapter
Next chapter
9PM Tuesday 9th November 2038
“They’ve stopped!”
Nathan yelled over to Megan, and inadvertently roused everyone who was sleeping.
“What?” Megan scrambled to her feet and ran over to the laptop bound teenagers. “Where?”
“One of the Detroit police stations...” Nathan zoomed out, and cursed. “That’s the DPD Central.”
“That’s where Julia is,” Alex was up and over immediately. “Any word from her?”
“Nothing.”
Almost immediately Alex’s phone began to ring.
“Julia, thank God, what’s going on?”
The volume was loud enough for them all to hear.
“Well, I’m hiding in my Uncle’s office, which is harder than you think. Oh, and shit just went down.”
“What do you mean?”
“Well, the freaking RK800 set a prisoner loose to sneak into the evidence room several hours ago. But from what I’m hearing now a bunch of vans holding androids just rolled into the car park and people are pissed.”
“We think Paul’s in one of those vans.”
“Shit,” Julia cursed. “Basically no one’s allowed to open those vans until the camps are ready.”
“Camps? What camps?” Megan asked, and Alex relayed the question.
“Camps are being set up to, er,” Julia seemed to swallow nervously. “Destroy androids. They’re calling them ‘Recycling Centres’. I’m sorry.”
“Not your fault Jules. How much time do we have?”
“Enough. From what I can tell the camps won’t be ready until after midnight.”
Megan took a deep breath and a step back, gripping the top of the plastic chair. They had time, they could get him out.
“Thanks Jules. We’re on our way. See you,” Alex hung up the phone and turned to the rest of the group. “Alright, we know where he is, we have someone on the inside. Let’s go.”
Maggie stood up. “You two,” she pointed to Alex and Allison, “aren’t going anywhere.”
“Says who?” Allison asked, clearly holding back a cough.
“Says us,” Ivy came in back Maggie up. “You two still look like shit.”
“And your coughing could give us all away,” Lucas added. “The sun’s set, curfew’s up.”
Alex scowled, “So, what? You want us to sit here and wait?”
“You could watch the cameras,” Oscar stood up from his spot by the tv and lumbered over to the rest of them. “Give us a text if you spot trouble.”
That only seemed to pacify them somewhat, and Megan was getting antsy.
“The longer we stand here, the more chance we have of Paul being driven away. Can we just do this?”
Alex looked over, and sympathy crossed their face.
“Alright. Allison and I will watch the cameras, you guys head out.”
“Alright,” Ivy nodded, taking charge. “Everyone’s phones on vibrate. Alex and Allison, refresh the pages every 30 seconds to get the newest images possible, or watch the live feeds if you can. If those trucks move, we want to know.”
“Got it,” Allison was already making herself comfortable. Alex frowned, but sat at another laptop.
“Everyone else, get something warm and dark on. We’ll need flashlights and bolt cutters most likely.”
“Check the back shed,” Alex suggested. “There’s loads of tools in there.”
“I’ll get them,” Nathan volunteered, already zipping up a black jacket. He darted upstairs as everyone whipped around to find something suitable.
Megan’s winter coat was a dark plum colour with a hood, so near perfect. Within a few minutes everyone was ready, and Nathan had come back with a couple of bolt and wire cutters and a flashlight.
“We’re going to have use our phones,” Ivy declared. “Alright, it’ll take a few hours to get there, and it doesn’t seem like the military presence has lessened. At least, according to the news. Stick to the shadows, be cautious. We can’t help Paul if we’re arrested.”
Ivy was looking mostly at Megan when she said that, and Megan nodded. She had no intention of getting arrested.
Ivy took a deep breath to steady herself, and looked around at the group. They were four down technically, so it was just her, Megan, Nathan, Maggie, Lucas and Oscar. It would have to be enough.
“Let’s go.”
10.30PM Tuesday 9th
It was incredibly hairy.
This late at night the military and SWAT squads were out in full force hunting down androids. Groups of five would jog down a street and the active AA would have to press themselves against the nearest flat surface.
Megan could feel her heart trying to embed itself into the snow covered tarmac that she was lying on. The polished black boots ran past her and finally let out a breath, letting it plume out under the car she was lying next to.
Oscar stood up moderately straight from hiding behind it, Nathan and Lucas appeared from behind some trashcans. Ivy materialised from the bodywork of another car and Maggie moved away from the shadows of a building. It was only getting worse the closer they got to the centre of Detroit.
And according to Ivy, they still had at least an hour to go.
Someone sprinted out across the street, and the armed black squad homed in on them. Megan found herself staring as they surrounded the unlucky android, mind going back to the android at the bus stop.
Without realising it, she was moving. Oscar suddenly tackled her to the ground and pressed a hand over her mouth to stop her crying out in shock.
“What are you doing?” he hissed. “Are you trying to get arrested?” he removed his hand so Megan could answer.
“They’re going to kill him!” she hissed in kind. She could already imagine the spray of blue blood, the vacant look in his eyes.
“There’s nothing we can do,” he winced as the shot rang out, signalling the android’s demise. “Time to move.”
He hauled Megan to her feet, and kept half an eye on her as they continued onwards.
11.45PM Tuesday 9th
It took way longer than it should have, but Megan let out a soft sigh of relief as the sign for the DPD Central station came into view. The lights were still on, as crime never slept. Especially now, which just made Megan feel sick.
Ivy was texting Alex and Allison to let them know they were there, and Megan scanned the car park. Five police vans, each one identical, and each one containing androids. One of them had Paul.
Uniformed officers, no doubt freezing their extremities off, where patrolling around the vans. Their flashlights shone like tiny moons, the beams of light covering most of the car park, which was already lit by streetlights.
The group convened less than a block away to discuss the game plan.
“We can see about ten cops from here, 2 for each van,” Oscar noted, as he seemed to have freaky night vision. “Most likely armed.”
“Not to mention the whole car park is at least somewhat lit,” Ivy added. “No doubt with a CCTV camera pointing right at it.”
“Thankfully the traffic camera only focuses on the entrance,” Nathan added, “But, yeah, the CCTV is a problem.
“What about Julia?” Lucas asked.
“According to Alex, Julia is in the reception. It’s a literal skeleton crew so no one’s manning the front desk right now.”
“She can deal with the cameras then,” Megan suggested, and Ivy raised her eyebrows.
“She won’t like it, but that’ll be one problem out of the way,” she began to text Alex to pass it on to Julia. It was tempting to use the group chat, but they didn’t want to have all of their phones going off at the same time. Or to give Paul a chance to tell them not to get him. Megan fully expected him to do that.
The lights suddenly lowered on the car park, getting the attention of the patrolling cops. They didn’t move from their spots though, and Ivy got a message from Alex.
“A thumbs up,” she passed on. “Okay, that’s done, now what?”
“How many of us can drive?” Lucas threw out. He, Maggie, Ivy and Oscar raised their hands.
“You two don’t?” Ivy asked Megan and Nathan.
“Left UK before I started lessons,” Nathan shrugged.
“Sets off my anxiety. Bad.”
“Alright. Knowing our luck if we tried to drive off with the trucks we’ll leave the one with Paul in behind,” Ivy sighed. “We need to get them away from the trucks!”
“Yes, we know, a distraction of some kind,” Lucas looked at Megan, who looked right back at him.
Whatever’s he’s thinking, you’ll mess it up
“Whatever you’re thinking, I’ll probably mess it up,” Megan sighed.
“You’ll mess up being anxious and lost?” Lucas raised his eyebrow.
“I’m not going to be able to lure away ten officers by acting scared and lost!”
“At the minute, you’re the best option we have,” Nathan admitted, and Megan felt her heart rate climb.
“Do we not have other ideas? Like a small firecracker, or something?”
“Sorry, left my fireworks at home,” Oscar rumbled.
Megan sighed, feeling bile building up in her throat. “Alright, I’ll try.”
She got up, shoved her hands into her pockets and hunched her shoulders around her ears as she walked over to the station.
She played a scenario in her head, in a real situation she would be too busy freaking out to walk into a station, so seeing some officers nearby would help. So, she gave into her anxiety, and paused halfway across the parking lot.
She swallowed and began to quicken her breathing. Not hard, she already was breathing fast. She looked around, and her eyes landed on the officers.
One of them caught her eye, and with a sigh, jogged over.
“You really should be at home kid,” they stated. “What are you doing here so late?”
“I-I know. I’m. I’m sorry. I-I don’t, don’t know where I-I am. I-I was, I was with my friends, and the curfew happened and I ca-can’t get home,” her arms went up to hug herself. “I-I’m sorry.”
The officer let out a long sigh.
“It’s alright kid. The curfew took most of us by surprise,” the officer shivered and stomped their boots to get some warmth back into them. “I’m freezing my butt off out here, so how about we head inside and we call you a ride, okay?”
Megan nodded, hearing the doors to the station open behind her. “Th-thanks so much. I’m sorry for dra-dragging you away.”
“It’s fine kid,” the officer waved off, let’s head...”
They trailed off and looked back over their shoulder in time to the last of their team mates get punched in the face by Ivy and tackled by Oscar. The rest of them were cuffed to the lot border fence with their own cuffs.
“What the-?” the officer went to draw his weapon and help, but got clothes lined by Julia.
They sprawled into the snow and Julia grabbed their wrists behind their back before dragging them over to the nearest fence and handcuffing them there. Julia then pulled out some duct tape and taped their lips shut. Job down she dusted her hands and looked over at Megan.
“You, you are scary,” Megan noted, and Julia’s expression softened.
“I’ve picked up a few things,” she shrugged. “Let’s go help the others.”
The two walked over, and Megan had to ask.
“Where did you get the duct tape?”
“It was on the desk. I’d guess we have ten minutes before someone checks the cameras, so let’s get on with it.”
The rest of the officers were groaning from mild head injuries, and Julia started gagging them as Nathan chucked a set of keys at Megan.
“Your boyfriend, your honour,” he smirked.
“He’s not my boyfriend,” Megan sighed before going over to the nearest truck. It took her a tense minute to find the right key, not to mention the lock was stiff. Eventually she got it open and flung the doors out.
She passed the keys to Lucas, who was by another truck and she shone her phone flashlight inside.
Androids, at least twenty all crammed in together like sardines. Each one of them in uniform and staring creepily ahead. There was no rhyme or reason to the models, almost every kind was in this truck it seemed.
Megan considered calling for Paul, but was hit by a sudden bout of conscience. All of these androids were bound for a Recycling Centre to be destroyed. They didn’t deserve that.
“Everyone out!” she tried to bark. It came out as a squeak, but it did the job. The androids all filed out evenly, creepily in exact time. Lucas did the same on his truck, and each of them had about around twenty androids in front of them.
Megan swallowed, not sure what to do next. Her heart suddenly lifted when she saw a familiar face, but quickly sank as she realised it was a normal PL600.
As Ivy let out another van Megan swallowed and raised her voice.
“Have any of you seen a red haired PL600 out of uniform? Called Paul?”
None of them responded, their LEDs whirring blue for a second before going steady again. Most likely a no.
“No! FUCKERS!”
There was a squeal of tires and Megan looked over to see the last two vans peeling out of the parking lot. She heard a loud shriek, and as she ran forward, she realised that it was her making that noise.
Arms wrapped around her midsection to hold her back, and for a second she thought it was Paul. But, they were too warm, too large.
She had to bite back tears as she realised that it was Oscar. Looking around, she couldn’t see Paul. He wasn’t here.
“No, no no no no no,” Megan sagged in the football player’s arms as burning tears fell and almost froze to her face in the harsh cold. “No no no please!”
Ivy stared after the trucks before swearing up a storm and slamming her foot into the tire of one of the remaining trucks. “BASTARDS!”
Oscar tried to haul Megan up to stand on her two feet, but she had no strength in her legs. Her knees just collapsed beneath her and she full on sobbed.
Oscar passed her off to Maggie, so she wouldn’t freeze on the concrete, and went over to a random officer, who was glaring at him. He slammed his hand on the fence above him and stared down the officer.
“I’m going to take the tape off, and I’ll put it back on unless you answer me.”
Oscar gave it a couple of second before ripping it off. The officer hissed in pain but Oscar got down to it.
“Where are those trucks heading?”
“A Recycling Centre.”
“Which one?”
The officer didn’t answer, and Oscar’s gaze narrowed. “Which. One?”
“You’re not as intimidating as you think you are kid.”
“Fine, you see my friend,” Oscar nodded to Megan, still crying in Maggie’s arms. “In one of those trucks was the only being on this earth who could help her manage her anxiety and depression. I wouldn’t be surprised if she owed her life to him. If he’s destroyed, then, she might not be able to take it. Do you want that on your conscience?”
The officer looked over at Megan and back at Oscar.
“Recycling Centre 4. I don’t know where it is, we were just supposed to guard them until the drivers showed up.”
Oscar nodded, and put the tape back on. When the officer protested Oscar glared.
“I am very pissed off right now,” he added in monotone before standing up and joining Lucas with the androids. The rest of the group joined them, with Maggie managing to get Megan to calm down.
“What now?” Ivy asked with a sigh.
“We know roughly where they’re going,” Oscar informed, and then he looked over at Julia. “Can you text, AAA Battery, about Recycling Centre 4?”
“Sure,” Julia got to it.
“That’s great and all,” Lucas added, “but now we have sixty androids to deal with.”
Ivy took a few steps back so that she could see all of them and cupped her hands over her mouth. “Anybody here deviant?”
Not a single android responded.
“What were expecting?” Maggie asked. “They aren’t going to trust us with that information.”
“We just freed them!” Nathan countered. “Why wouldn’t they trust us?”
“Because we’re human and they’re not mind readers,” Julia responded, phone in one hand. Her face looked oddly pale, but no one really focused on that. She took a deep breath, and addressed the androids.
“Excuse my language, but everything’s going to shit right now. So, if any of you are still listening to humans, try this. Scatter, hide. Find other hidden androids. It’s not safe right now. You need to get as far away from here as you can and hide. Understand?”
The androids all nodded as one, an extremely creepy gesture.
“Then go!” Julia cried, and the androids all scattered in different directions at a run.
Android Allies looked at each other. It wasn’t easy to see everyone’s face, given they all had hoods up.
“So, was that for nothing?” Megan asked quietly.
“No,” Maggie answered first. “Sixty androids are free, that’s something.”
“And we know where they’re taking Paul,” Oscar added. “And who knows, those guys might make it to Markus.”
“Maybe not,” Julia added. “Word from Biker Chick. Markus’s stronghold, Jericho, has fallen.”
A bit long, but I couldn't really find a good point to split it, so here we are
Other Options Flowchart
(Megan) Be rude in suggesting they leave now. Be more polite. Say nothing
(Megan) Don't try to save the android(Megan) Argue with Oscar (don't think the android can be saved, just increases chances of being caught)
(Megan) Agree readily to Lucas's plan. Completely shut down the plan.
(Megan) continue to walk across the car park. Actively get the officer's attention
(Megan) Pick a different van (you can in fact pick the van with Paul in here. Two without him will always be opened by the Lucas and Ivy, leaving Megan (or if this was a game, the player) with a 1 in 3 shot. Getting it right would snap the story to the other main path, which I shall dub 'the Protest Path'
(Megan) Fight against Oscar. Completely give up
Tags: @nightmarejim @septicart-appreciation
#Guess What? I'm Not a Robot#Guess What? I'm Not a Robot RC#Guess What? I'm Not a Robot RC Ch3#Detroit: Become Human#Detroit Become Human#D:BH#DBH#Detroit: Become Human OC#DBH OC#D:BH OC#Detroit: Become Human fanfic#Detroit Become Human fanfic#DBH fanfic#D:BH fanfic#TheShapeshifter100 writes
3 notes
·
View notes
Text
Windows 10 change keyboard hotkeys 無料ダウンロード.How to Change Keyboard Language Shortcut in Windows 10
Windows 10 change keyboard hotkeys 無料ダウンロード.ASUS Keyboard Hotkeys

WindowsでShotcut日本語版をダウンロードしてインストールする方法.【Widnows10】「KeySwap」を使って使わないキーの置き換えをする! | ���生には山と
Aug 13, · ShotcutとはWindows、Mac、Linuxといったマルチプラットフォームで動作する無料動画編集ソフトです。 動画編集フリーソフトと言ったら、レイヤー対応できなくて、カット、結合など簡単な初心者向けのものが多いが、Shotcutはプロにも満足できる豊富な動画編集機能を搭載しているフリーソフトです。 Windows 10 向けの Microsoft Store からこのアプリをダウンロードします。スクリーンショットを確認し、最新のカスタマー レビューを読んで、ASUS Keyboard Hotkeys の評価を比較してください。 Apr 29, · Let’s say you want to change the Ctrl+X keyboard shortcut to do what Ctrl+C does. To do that, you will enter the following in the Notepad file; ^x::Send ^c return. Here, the ‘^’ symbol denotes the Ctrl key and the x shows what it’s being combined with. The part followed by Send shows what keyboard shortcut will be executed when you Estimated Reading Time: 2 mins
Windows 10 change keyboard hotkeys 無料ダウンロード.How to Change Keyboard Language Shortcut in Windows 10
AutoHotkey is a free, open-source scripting language for Windows that allows users to easily create small to complex scripts for all kinds of tasks such as: form fillers, auto-clicking, macros, etc Meet AutoHotKey. So let’s start with the bad news, which is that there is no native way to change the default keyboard shortcuts in Windows. After all these years, Microsoft still isn’t willing to offer that simple bit of flexibility, presumably for fear that you’ll want to use its shortcuts to access non-Microsoft apps which is probably the ted Reading Time: 4 mins Jul 14, · 今回使用させて頂くソフト「KeySwap」は特定のキーの挙動を変更したり、無効化したりできるフリーソフトです。. 全くの無効化だと、今度は「 押してるのに動かない 」というストレスが発生しそう 。. なので、今回は以下のように設定してみます!. [home]キーを押すと [backspace]キーとして機能する. [pg up]キーを押すと [enter]キーとして機能する. [pg dn]キーを押すと
Just right-click the executable for whatever it is you want to create a shortcut to, click Properties, then enter your command into a box. More on creating custom shortcuts here. For this, we need a tool called AutoHotKey. Also read: 15 Useful Windows Registry Hacks to Optimize Your Experience. This is a script creator tool that can be used for all kinds of creative purposes , but today we are looking specifically at how you can use it to change the default Windows shortcuts.
Next, we familiarize you with the basics of the Auto Hotkey syntax you need to know to change Windows shortcuts. Most Windows shortcuts use some combination of the below buttons, so this should be enough to get you started. If you want to type a letter, you just literally type that letter, while buttons like Esc , Del and others can also be directly typed into your script.
You can find a convenient list of the main Auto Hotkey syntax at this site. First enter the shortcut you want to use and follow this with ::Send , then a space and the shortcut you want your custom shortcut to replace. Because the Esc key is a command rather than a standard key, we put it in the special brackets. With all your keyboard shortcut replacements, we recommend adding a second line to the script with the text NoTrayIcon.
This will block the Auto Hotkey tray icon from popping up, ensuring that the whole process stays in the background. Once your script is ready, close it and save it, then double-click the script to run it and test your keyboard shortcut to see if it does what it should. Type in the following command:.
The :: is what separates the hotkey from the action you want it to perform. Also read: How to Customize Keyboard Shortcuts in Gmail. Your shortcuts work as soon as you boot Windows and move the. ahk script to your system startup folder in File Explorer — C:ProgramDataMicrosoftWindowsStart MenuProgramsStartUp.
Do the same for all your keyboard shortcut replacements. If you want to stay knee-deep in Windows, see our list of the best sandbox applications for Windows 10 , and how to convert legacy BIOS to UEFI in the OS. By signing up, you agree to our Privacy Policy and European users agree to the data transfer policy. Content Manager at Make Tech Easier. Enjoys Android, Windows, and tinkering with retro console emulation to breaking point.
You've decided to leave a comment. That's fantastic! Check out our comment policy here. Let's have a personal and meaningful conversation. Save my name, email, and website in this browser for the next time I comment. Notify me of follow-up comments by email.
Windows 10 Start Menu Search Not Working? Here Are 12 Fixes. How to Clean Up and Make Space on Your Windows "C" Drive. How to Fix "The Parameter Is Incorrect" Error in Windows.
Affiliate Disclosure: Make Tech Easier may earn commission on products purchased through our links, which supports the work we do for our readers. Here we show you how to change the keyboard shortcuts in Windows 10 using this great tool. s:: run , "C:Program FilesEverythingEverything. Is this article useful? Yes No. Never Miss Out Receive updates of our latest tutorials.
Sign up for all newsletters. I would like to receive newsletters via email. We will not share your data and you can unsubscribe at any time. Robert Zak Content Manager at Make Tech Easier. Leave a comment. Facebook Tweet. Leave a Comment Cancel reply Yeah! Contact me by phone only. Popular Posts INNOCN PFPRO Portable Touchscreen Monitor Review Sponsored. What You Should Do If Windows Fails to Start. Headphones Not Working in Windows? Here Are Some Fixes.
Here's How to Fix it. Settings App Not Working in Windows 10? Here Are the Fixes. Latest Windows 10 Update Problems and How to Fix Them. How to Safely Bypass the TPM 2. Why Encryption Is Not Working on Windows 11 Home, and How to Fix It.
Find and Open Files Using Command Prompt in Windows.
0 notes
Text
click the link bro
https://www.tumblr.com/blog/nelsonunderwood
https://www.tumblr.com/blog/upholsterynelson/new/text
https://www.tumblr.com/blog/nelsonunderwood
https://true-beauties.tumblr.com/post/186457468593
https://noofvcks.tumblr.com/post/187165395925
https://oxygen-xo.tumblr.com/post/187162747882
https://www.facebook.com/kevinelson.monde.7/allactivity?privacy_source=activity_log_top_menu&entry_point=www_top_menu_button

Get much money from hoping from 1 cyber cafe to another and lying about your name to not be gotten, now dont came back to me wanting my food, disturbing me, now its your/the time. Women with Barnabas during Christ crucifixion dude.
https://www.facebook.com/quinter.nyanga read todays post on jehova witness cover dude.
https://www.facebook.com/photo.php?fbid=2499211890312105&set=pcb.2499212130312081&type=3&theater
https://www.facebook.com/photo.php?fbid=2499211900312104&set=pcb.2499212130312081&type=3&theater
https://undeniably-recklesss.tumblr.com/post/187044648700/xjessr-xjessr
The white fellows colonized Africa badly, each nation ought to have been formed by every tribe but the African aliens also thought they can make it by fighting for independence, so the white people will justify that during judgement in heaven as lame excuse. But once they have known to make gadgets they only look 4 food and what they dont produce making life cheap in any sphere. Also the usa thing is there to continue the sad fact of their being naive and lack of money to visit those lands so they oppose the fact that America is good on tv so during judgement they were insane or dint know. So its a scape goat on both frontier if it succeeds/fail and going to the new planet is a curse as well so the whites will justify at that time that bad tribes had learnt automation and machinery so they were in treat then flew above to escape hell fire. We tryna make it better, complement it bro. Tm new about so opted 4 shout out, dont morn death some people longed 4 them to get to heaven or escape death, The truth is leave the dead alone and let them bury their own death, not to metion malcomX and king mlk.
alexandria if you wanna get off hustling a little bit then you want this woman and they bring you another woman who will make you go to hell as if you mary some1 bad to bring bad kids or that Gay fellow harass you whom if you glance at him at 1st you see him as a white man not only to realise he is brown out of many sperms which has been deposited on his body and the school like wsu kansas in wichita has your money u are claiming yet they send the bank as ketie drucker to come with quacks to scrutinize your home yet they were suppose to send university representative, i swear girl it bores you off if young chaps disturbs your peace by calling you every time, wanting your food always and removing knife 4 you without justice. a thought crosses your mind of suicide when you have given up on women and luxury to sometimes telling you to sleep while your door is opened so they hang or cut you to death with machete as panga. You are a cold man dont wanna talk all the time stupid things but they force you. Am dutch, norwegian blooded but am black out of intermarriage with toro and swana blood. If you take a coin and put on the palm of your hand 4 a little while you percive this truth, am erratic block/moulder, it burdens me girl and sometimes in my quite self i find myself literally crying and it gets to the point i cant take it anymore. Am saying this coz am involved in mankind and bcoz am got to tell you this. Making me little all day eats away my brain as in Africa and going to hell/heaven as much as to my knowhow makes me sick, why cant God speak and solve this blunder, ad rather be destroyed completely not to find myself in hell/heaven coz i hate eternity. take care always, the illegal tea pickers or pluckers at night. From dusk untill dawn they do without being exhausted.. You wanna be this or that in the government without you saying makes you tired and sick as well dude. Your are fighting castle in the air dude.
Delanu saying to kebi after kebi told him in luo how dare you look at me that way- delanu saying aneni kaka mand whuonwa mana omiyo mamawa ich. Nyili kokunyalhera, winjo wachna then whun chi-ong’ong’o. Google computer browser even for android and try which one can get or succeeds in getting money off 2goinvoice b4 the link is put offline while others have not been yet put in the net for googling, net parable np to cement the truth bro. At the end where justice should surface, you see a dead horse which has refused to move a head carrying up his legs crying meaning the some1 you are telling your shit can even break up a fight so the best option is to dismount and take another one, You the people (2) ridding the horse whom you have explained to your plight in detail. Farasianda they want, they are fara/naive people.
How to produce power using a battery, inverter and battery charger, click the link below and see when it was posted and when you saw the explanation on mrmonde tumblr to stop being 1st bro.
https://www.youtube.com/watch?v=3_08txT2b0o
https://www.youtube.com/watch?v=_oZPhlA7jiw
https://www.youtube.com/watch?v=nej3oMvEhBc
https://www.youtube.com/watch?v=04SfNQL9P-E
https://www.youtube.com/watch?v=TrrKJKfbSGs
Koth nechwe kericho koro okipono, duoge neguyo, nechwe cats and dogs gi pe/hailstone koro negoyo toki- king of the jew- or ne-ng’ich hainya, it was very cold, then why put me under mockery bro when am hearing, otem kendo, okadhiye kwa keja chake, kolo hatasema nimeiba pesa after beating me bro and kunibeba kama gunia na piya nitakuwa na kunywa fanta to remove any benefit of doubt dude. The jehova witness news lettery with a woman sitted and a man walking in blue in black shoes is segwick detention center in wichita and he is wesley williams of usa navy bro. He is telling me they have know how to make gadgets as i said earlier dude. Fuck that kebi!!! Every one is now jew- we are rising bro. Aother email 4 me is [email protected] and password is botswana200 period dude which i have opened with a FB a/c but has not accepted any friend or send request waiting to use it in times futurity. You can only see the password as the hindu see on the eye or kidnap me to tell you incase i have not 4gotten. You can force water out of a mugumu tree, wiya tech kakidi, nyolo na nindo duk with opened door but i dint see you to cut me- chi-ong’ong’o gi- shinda who. There is no phone being stolen, you pushed like amon to get into your phone to send a code to get into your loggings bro. What you want bro- mfalme wa yawhodi, so you see them looking into your manhood area pals or staring at you with wide whittened eye to not make you sleep at night or transfer pimples unto your face as to upset you as well dude or make you sick somehow.
https://www.tumblr.com/blog/upholsterynelson
https://www.tumblr.com/blog/upholsterynelson/new/text
International students and visitors to eu or america aid in hse and bank theft, so a bracelet should be put on their legs to hinder/monitor their movement at night to that crime scene to stop such dude.
How to remove an existing email address in fb and on yahoo and Gmail, click the links below follows.
https://www.google.com/search?q=How+to+remove+an+existing+email+address+from+a+yahoo+account&oq=How+to+remove+an+existing+email+address+from+a+yahoo+account&aqs=chrome..69i57.9095j0j8&sourceid=chrome&ie=UTF-8
https://www.google.com/search?ei=aFBaXZGEObmV1fAPo9SKuAQ&q=removing+an+email+address+from+a+gmail+account&oq=removing+an+email+address+from+a+gmail+account&gs_l=psy-ab.3..0i22i30.20883.38968..39393...0.1..0.638.14323.2-33j8j2j3......0....1..gws-wiz.......0i71j0i67j0i131j0j0i67i70i249j0i20i263j33i22i29i30..11%3A1j12%3A30j13%3A0.1rDuKU8PHOw&ved=0ahUKEwiR2NSrtY7kAhW5ShUIHSOqAkcQ4dUDCAo&uact=5
https://www.google.com/search?ei=klBaXZbqB7Co1fAPjv6d-AI&q=removing+an+email+address+from+a+facebook+account&oq=removing+an+email+address+from+a+facebook+account&gs_l=psy-ab.3...20496.22525..23587...0.3..1.390.2175.2-7j1......0....1..gws-wiz.......0i71j33i10..12%3A0j13%3A0.klHB8gj83r4&ved=0ahUKEwiW-6a_tY7kAhUwVBUIHQ5_By8Q4dUDCAo&uact=5
https://www.google.com/search?ei=q1BaXYGYHruM1fAP_smfwAs&q=removing+a+phone+number+from+a+facebook+account&oq=removing+a+phone+number+from+a+facebook+account&gs_l=psy-ab.3...16620.23372..24923...1.2..1.571.3848.2-9j2j1j1......0....1..gws-wiz.......0i71j33i10..12%3A0j13%3A0.FJTED4OMow8&ved=0ahUKEwjBmbPLtY7kAhU7RhUIHf7kB7gQ4dUDCAo&uact=5
https://www.google.com/search?ei=x1BaXbDsN_y01fAPo7WSuAs&q=adding+a+phone+number+from+a+facebook+account&oq=adding+a+phone+number+from+a+facebook+account&gs_l=psy-ab.3...27204.28810..29209...0.1..0.269.1538.2-6......0....1..gws-wiz.......0i71..12%3A0j13%3A0.N0QxCseRby4&ved=0ahUKEwjw6_nYtY7kAhV8WhUIHaOaBLcQ4dUDCAo&uact=5
https://www.google.com/search?ei=8VBaXdqNGOyo1fAP_see8AU&q=adding+a+phone+number+from+a+yahoo+account&oq=adding+a+phone+number+from+a+yahoo+account&gs_l=psy-ab.3...12405.13307..13699...0.2..0.273.1280.2-5......0....1..gws-wiz.......0i71..11%3A1j12%3A1j13%3A0.-p-26mb2rSc&ved=0ahUKEwiayt3stY7kAhVsVBUIHf6jB14Q4dUDCAo&uact=5
They say everyday they wanna eject them out- the hindu-, well, but whats up with me, dont come about disturbing as wanting my food, everything about AE is under youtube and you can get it there, do not call me wanting to touch my manhood. Good samaritan GS parable with yesus, Gay somali, swedishona, swana, society, German/guyan society GS, G-sport, greetest sex, snitch. Just remove them bro period and leave me alone- mfalme wa yahoodi na yesus.
Negros are threat in the USA as they have known how to make machines so they want to transfer that threat to Africa as bring them here. Tell the white people to give you 1 or 2 states to operate as now what you look 4 is food and you cant destroy the ground coz you have known how to make houses, cement, bricks and sand, stop games or dilly dalling bro. Us as well we have known that shit so it will be a tag of war. Paul pogba Steve ombuor utters that. You have been a friend of mine for a very long time but now i want more, you mr whiteman and you must accept that you are the jew mr itallian and Rusians must accent they are the guard who crucified christ upon being called or-else it will be a tag of war and the luo/kikuyou must accept they came from mar as if they do something absurd with their blood still in mar it affects them up here on earth same to french out of luya blood and the brutal cuttings. The Japanis, italians must accept the got kauma blood, Egyptians must accept moses was put in arkansas river and they crossed not the red sea but the Indian ocean at karachi and onding was babylon dude or-else they will be on fire, no kidding dude, and the french, british, spanish must tell us where they got the nigros and from which countries of the world to which states period.
The MPS, Senators, Governors got no money coz they owe it out b4 it comes in, i mean they pay much bills is only the huge loan they take that helps them in the aftermath. The as well depend on CDF as in kenya where they sponsor hooligans as inter-estate war then in the aftermath directs you to the office to fund your hospital bill which they lias with the nurses and take some percentage back to the dignitary and with his people to support them. This cash they eat with the doctor, so they want many fights as posible along the roads to expand this dude. And they organise petty theft like they have recruited 5 million people from all over kenya mainly the kikuyu but other tribes have seen the benefit and followed suit, where they again recruit 50 thousand fellow to attend to all these people where each of the 50 thousand recruited will attend to 250 recruited from the 5 million where a target of 20 bob is given to each daily or 140 bob weekly, you can pay in each way you like. They send the cash via m-pesa to the 50 thousand recruited who a gain bank it in an a/c in the bank where they are alerted via sms of how much they have collected then they resort to being happy always, a head of people or with belittlement. Other tribes have seen it as lucrative so have followed suit hence estate petty theft has became a nuinsense even with police involved, i mean open bro. This money builds nairobi wayaki way buildings, thika and mombasa as much as west lands, dont be fooled women. They also select one fellow and give this cash to ride on big cars and dwell on posh houses to attract women attention but in truth they got nothing. Take heed women kenya is poor, Even NY in coming to America movie of Eddie chieth is built on a small percentage that way dude, Londan, sydney, mexico city, Rio, new delhi, mumbai, Jo-burg and you can name them bro.
They sponsor war in The USA as gangs they upon get hurt they refer you to a medical center to get drugs which again they take and sell in the chemist to get that money to keep Ny where it should be and thats precisely how Ny is built, no joking. By washing your chin, beards, face, head and the water pours from lofty high unto the offering it as well makes machines you know including mabatea as iron sheets, water containers and jars, plastic toilets and baths. Car made out of chamama/bougainvillea makes you dull and thats the side effect, those made out of tea leaves brings people close to it, attracts you attention as their is some hidden beauty and grown ups hate such. They make you feel better and dont wanna get out of that place, its peculiar with some offices as you loose ya mind in getting out. Those built with tomato makes you sick and tired and to me the best is those gadgets made out of miwa/sugar cane as mfalme wa yahodi. Many of which gadgets are made interferes with the brain dude, so chose the best automobile and thats why one buy this and sell it tomorrow, dont judge badly dude.
0 notes
Text
2018-03-25 21 TECH now
TECH
Ars Techica
Facebook scraped call, text message data for years from Android phones
Sea of Thieves makes a weak, meandering first impression
Sticking to your diet? This tooth-mounted food sensor could transmit the truth
NBA Jam, Sonic 1, Ultima Online remembered with rare stories, concept art
The Mac gaming console time has forgot
Buzzfeed Tech
The #DeleteFacebook Hashtag Is Being Targeted By Bots, Porn Accounts, And Cryptocurrency Hustlers
A UK Privacy Watchdog Is Searching Cambridge Analytica's Office As Its Scandal Fallout Deepens
Why Nothing Is Going To Happen To Facebook Or Mark Zuckerberg
Craigslist Just Took Personal Ads Offline Because Of A New Anti-Sex Trafficking Law
Apple Just Proposed 13 New Emojis With Disabilities
CNet
2018 Range Rover P400e: The pinnacle of luxury SUVs, now quieter - Roadshow
AirPower: All we know about Apple’s wireless charging pad - CNET
Vegas Esports Arena gives hard-core gaming a glitzy stage - CNET
China's uncontrolled space station could crash to Earth soon - CNET
Elon Musk deletes SpaceX, Tesla Facebook pages - CNET
Clean Technica
StorEn Technology’s Vanadium Flow Battery Prototype Outpacing Expectations
Franz von Holzhausen Talks Tesla Model 3’s Award-Winning Design & Minimalism
TRIPL: A Funky Urban Electric Scooter … With Cargo
Renting Out Private EV Charging Stations
Nissan LEAF Jumps To #2 In France — February 2018 France Electric Car Sales Report
Hacker News
The Muse (YC W12) Is Hiring a QA Lead – Help People Find Their Purpose
KDE Plasma Voted Best Desktop Environment in Linux Journal Readers Choice Awards
Thoughts on Embracing the Social Internet Over Social Media
Void Linux: Into the Void
Facebook scraped call, text message data for years from Android phones
Mashable
4 reasons Javascript is still a programming language you need to learn
5 multi-port charging devices on sale right now
Exercise literally anywhere with this little device that can fit in your pocket
Here's what the March For Our Lives in D.C. looked like from space
March For Our Lives crowd estimates trump Trump's inauguration
Motherboard
State Department Seemingly Buys $15,000 iPhone Cracking Tech GrayKey
This Politician Wants New Yorkers to Have the 'Right to Disconnect'
Tired of Sucking in 'Overwatch?' Try Cognitive-Behavioral Therapy
A Brief History of Elon Musk and Mark Zuckerberg Publicly Beefing
Elon Musk: 'What's Facebook?'
New York Times Technology
Dropbox Shares Leap in I.P.O., and Silicon Valley Smiles
How Calls for Privacy May Upend Business for Facebook and Google
Opinion: Are You Really in Love if It’s Not on Instagram?
Opinion: Don’t Delete Facebook. Do Something About It.
Timeline: Facebook and Google Under Regulators’ Glare
Recode
March for Our Lives protest draws hundreds of thousands of students calling for gun control
Uber says a single metric isn’t a clear indication of an autonomous car’s safety
Limebike, the dockless bike-share startup, wants to pay people to charge its scooters
Dropbox shares jumped nearly 40 percent on the first day of trading
Calls for Mark Zuckerberg to testify before Congress are getting louder
Reddit Technology
The people owned the web, tech giants stole it. This is how we take it back
Facebook scraped call, text message data for years from Android phones | Ars Technica
Cambridge Analytica's Real Business Isn't Data: The firm is part of a secretive political consulting industry that helps make fake elections look legitimate.
All the URLs you need to block to *actually* stop using Facebook
I warned Mark Zuckerberg about the Cambridge Analytica-type flaw in April 2005. He ignored me.
Reuters Technology
Uber to sell Southeast operations to Grab, get stake in combined business: source
Facebook's Zuckerberg says sorry to Britons with newspaper apology ads
Waymo CEO says its tech would have handled Uber self-driving incident safely
Indian agency denies reported security lapse in ID card project
#DeleteFacebook? Privacy proves hard to protect online
Slashdot
UK High Court 'Perma-Bans' Efforts to Extradite Lauri Love to the US
Hilarious (and Terrifying?) Ways Algorithms Have Outsmarted Their Creators
Ask Slashdot: Is There a Good Alternative to Facebook?
Shodan Search Exposes Thousands of Servers Hosting Passwords and Keys
World Cities Go Dark For 'Earth Hour' Climate Campaign
TechCrunch
Monarch is a new platform from surgical robot pioneer Frederic Moll
Facebook was warned about app permissions in 2011
JASK and the future of autonomous cybersecurity
Hip hop finds its beat in the startup scene
‘Black Panther’ just became North America’s highest-grossing superhero movie
The Next Web
More landing page optimization tips than you can handle! (45, to be precise)
Zimbabwe will use fingerprint ID technology for its 2018 general elections
You can’t learn design online
Need an existential reason for ditching Alexa? Here are a few
PRINCE2 will have you leading and managing any project like a boss for only $19
The Verge
NBA testing 99-cent stream that lets you watch the final quarter of a live game
Morehshin Allahyari’s 3D-printed project pushes back against ‘digital colonialism’
Tim Cook wants ‘well-crafted’ privacy regulations after latest Facebook scandal
This week in tech, 20 years ago
9 new trailers you should watch this week
WSJ Tech
Apple's Cook to Trump: Embrace Open Trade
Waymo Chief Confident Tech Could Avoid Uber-like Incident
How Facebook's Past Data Policies Led to Its Current Crisis
New FCC Rule Would Step Up U.S. Fight Against China's Huawei
My Electronic Devices Are Laughing at Me
Wired
‘The Sky Is Yours’ Combines Dragons and YouTube
The Uber Crash
The Universe Is Basically a Hippie’s Pipe Dream
Raise Your Glasses
Don’t Do Drugs and Watch ‘Annihilation’
0 notes
Text
How Companies Turn Your Data Into Money
New Post has been published on https://britishdigitalmarketingnews.com/how-companies-turn-your-data-into-money/
How Companies Turn Your Data Into Money
The best description of the data economy comes from AOL, of all places. The once-mighty internet service provider now runs a tidy business in the ad-exchange space. The site promoting the service is hip and tasteful, showing happy, partying people and white text that spells out things like “Monetize your most valuable asset” in all caps.
“A publisher’s audience is their currency,” the site says. “No matter how they make money from content—be it through advertising, paid subscription or syndication, a publisher’s core asset is audience and audience data.”
This is weapons-grade marketing speak, but it’s also a surprisingly honest assessment of digital media’s beating heart—one that pumps out content and takes in reams of data from the people who consume that content. And somewhere, unseen, money is being made from what we see and do online.
Targeting and Retargeting
Bill Budington, a senior staff technologist with the Electronic Frontier Foundation, sees the avenues for data gathering everywhere: advertising identifiers in the headers of mobile web traffic, fingerprinting browsers, customer tracking in stores using Wi-Fi probe data, SDKs inside mobile apps, and ultrasonic tones from TV that are outside the range of hearing but can be detected by apps on smart devices to track viewing habits.
Some data isn’t being used yet—he said, for example, that the genetic information gathered by 23andMe could one day be used for advertising or for discrimination. Genetics being used for advertising is something from a hyper-capitalist cyberpunk fever dream; and yet, it’s plausible.
“There is no legal regime for the protection of that data, so consumers need to be on watch for it in the US and make those choices,” said Budington. “The US is at the forefront of deploying those technologies, and the companies that are starting are going to target US customers first. In a lot of ways, the US serves as a playground for the big-data economy, which means that US citizens have to be more aware of the dangers.”
The collected data has value because of how it’s used in online advertising, specifically targeted advertising: when a company sends an ad your way based on information about you, such as your location, age, and race. Targeted ads, the thinking goes, are not only more likely to result in a sale (or at least a click), they’re also supposed to be more relevant to consumers.
Budington pointed out that there’s a dark side to this kind of advertising. “I have targeted ads that are more attuned to my desires and my wants… But if you have someone who has an alcohol abuse problem getting a liquor store ad…” He trailed off, letting the implication hang.
Your local liquor store probably isn’t advertising in this way, but vulnerable communities are being targeted for specific ads. For-profit universities, for example, target low-income people, Budington said. “You pay thousands and thousands of dollars, and they give you a diploma that isn’t worth the paper it’s printed on. Targeted advertising has a really pernicious side.”
A subset of targeted ads is ad retargeting. Retargeted ads take into account your previous online activity in order to push an ad your way. For example, tracking pixels can be added to a webpage. When the site loads, the owner of a tracking pixel will see that a computer requested said pixel and that it loaded at a particular time. It can even capture identifying information about the computer that visited the site.
This is what creates the unnerving experience of seeing an ad on one website, and then seeing it again on another site. The ad “follows” you across the web, hoping for a click.
This has given rise to a popular conspiracy theory: that phones and smart devices are listening in and then targeting ads based on what you’re saying. One study debunked this claim, demonstrating that mobile phones didn’t seem to be sending audio data—but some apps were found to be transmitting screenshots of device activity. Apps using the Silverpush software development kit (SDK) were listening for ultrasonic beacons (as mentioned above), but Google has worked to suppress the use of this technology on its Android platform.
Budington said that in some cases, app developers may be including tracking SDKs without fully understanding the privacy implications for users and perhaps without ever receiving the data themselves. Developers sometimes get paid for including the SDKs and may include them as tools for debugging or gathering analytics. The SDK operators, however, can then potentially receive information about people’s behaviors and app usage.
As for devices with built-in digital assistants, such as the Google Home and Amazon Echo, it is true that these services send recordings of your queries back to the respective companies for processing. With the Google Assistant and Alexa voice assistants, you can even listen to recordings of every question you’ve ever asked. Budington said that while companies have been clear on what kind of data they’re gathering with these devices and services, what they’re using the data for is much more opaque.
Budington doesn’t expect this data economy to change, at least without external pressure. Most efforts by companies to improve user privacy typically don’t solve what he sees as the real problem. “[Companies] are willing to set up privacy filters with regard to other users, because that doesn’t affect their bottom line; but they’re still getting that data themselves.”
Budington also doesn’t see fixes coming from Congress. “I don’t see much hope for that in the US,” he told me. “Often, I think, when regulation comes into play, it’s ill-worded and misapplied. And because of that, you don’t have the necessary protection, and [it] can often do more damage than it does good.”
The argument against Budington’s position on privacy is that targeted advertising and the data collection behind it are fair compensation for companies that provide free online services. Google, Facebook, and Twitter would likely not exist if they couldn’t turn user data into cash. Not everyone has the money to pay for subscriptions or is willing to—but most people have value to advertisers as potential consumers.
That argument rings hollow to Budington. “People don’t have a lot of options if they’re going to interact with the world. Most people like to take pictures and upload them to Instagram,” he said. The EFF created Privacy Badger—a browser extension that blocks ads and trackers—to address this lack of choice. It lets users toggle which trackers are allowed to interact with their web experience, and it replaces social widgets and embedded YouTube videos with badger icons that viewers have to click in order to activate (and then, in turn, information about the viewer is transmitted).
So for now, change is coming not from companies and regulators but from the people who are being advertised to in the first place.
The Data Must Flow
The founder of DuckDuckGo, Gabriel Weinberg, is not a huge fan of Google. That’s not surprising, because DuckDuckGo is a competing search company—but one that has positioned itself as a search engine that won’t absorb your data. Given Google’s (actually, Alphabet’s) numerous niches, it’s easy to forget how the company has made its money. It’s not primarily a smartphone operating system developer, a web browser, or even a search company. Google, as privacy advocates are quick to point out, is an advertising platform that takes advantage of the enormous insight the company has into the activities of users.
“What people don’t realize is that there are these hidden trackers across the web that are scooping up your personal information,” Weinberg told me. Facebook and Google have deployed most of these trackers. “That lines up with their dominance in the advertising market.”
Weinberg isn’t just concerned with the privacy implications of consumer data collection. He also worries about the social effects that have arisen as a result, in part because many apps and services gather data in exchange for services and also aid in advertising retargeting, which encourages people to buy more things. “You’re paying with your data, but you’re also literally buying stuff,” said Weinberg.
He argued that Facebook and Google’s business model is filtering what you see in order to drive clicks. “As a result, people get into these echo chambers,” he said, recalling the efforts by Russian intelligence operatives to sow discontent among American voters online. “Those harms are somewhat unique to Google and Facebook.”
“Facebook is a contained internet,” Weinberg continued. “It’s literally what they’re trying to do in places like India. The internet is Facebook to them, in the same way as it was for AOL back in the 90s for the US.”
And the consequence of that kind of containment, he said, is that people believe things they wouldn’t necessarily believe otherwise. A deeply troubling example: the deaths by mob violence in India that were spurred by rumors spread via WhatsApp.
Weinberg believes the road to our current moment came through a lack of oversight or regulation for online tracking, at least in the US, which continues to this day. As long as websites and apps have a publicly posted policy, companies can do more or less as they please. He characterizes the data collection efforts of US companies this way: “Collect everything, and we’ll figure out what to do with it later.”
By contrast, the European Union recently introduced the General Data Protection Regulation (GDPR), which requires companies to get user consent for the collection of data, among other things. This was why many websites the world over simultaneously informed all of us that their user policies had changed. On this side of the Atlantic, it was a bewildering but minor inconvenience. In Europe, the enforcement of the GDPR has been a step toward putting people in control of their data.
Weinberg said US residents are subjected to a web of different tracking techniques. Cookies and IP address gathering track users as they move from website to website, but your own web browser can also give you away—in browser fingerprinting, configuration factors about users’ device and software (such as the browser version number), are used to identify them.
More identifying information can simply be purchased. “Facebook is taking offline credit card data and mixing it with their site,” Weinberg said, to illustrate the lack of transparency he sees in the data market. “You wouldn’t expect that. The bigger the data profile . . . the better you can be targeted. They have incentives to buy and combine extra data.” After our interview, it came to light that Google had penned a secret deal with MasterCard for data on offline spending habits.
I reminded Weinberg of the argument in favor of this kind of data collection and advertising—that it allows companies to provide services and apps for free. He ruefully said he’s heard a phrase that describes his feelings on it: “The best minds of our generation are being put to work on seeing if people will click more ads.”
“I think it’s a travesty and waste of innovation,’ he said “I think it’s manipulative, driving consumption and [making people] believe things that they don’t want to believe.”
“Some business models that are dependent on this need to change,” Weinberg added. “Google and Facebook have sucked out the profits for organizations and media, and if those profits were better distributed, things would be better.”
Weinberg considers monetization schemes like paywalls, in which visitors to a site pay to view some or all of the site’s content. Turning back to Facebook, he said, “Their business models are such that they will be more targeted over time and more intrusive.”
What’s the fix? Voting with your feet—leaving a service with intrusive policies—does work, Weinberg said. But he notes the network effects of sites such as YouTube (which is part of Google) and WhatsApp (part of Facebook). “While I advise people to leave Facebook, I am also realistic, and I know people never will.”
Both outside and inside forces seem to be the solution. Regulation is important, but Weinberg, like Budington at the EFF, is more focused on the actual tools that could solve the problem of intensive data collection and user tracking. Sites and apps need to offer users real ways to opt out, he believes, and companies should be prevented from combining data from other companies.
Inside the Ad Exchanges
Julia Schulman is the chief privacy counsel for the ad-exchange company AppNexus, and she speaks with easy confidence and the lung capacity of a skin-diver. Without taking a breath, she explained to me how AOL One, AppNexus, and ad exchanges like it connect people who have websites and want ads with people who have ads that want to appear on websites.
“We’re the pipes,” she said crisply. It’s a carefully neutral position that emphasizes her employers’ place in a larger web of interests. AppNexus and similar companies provide clients with a demand-side platform (DSP) that serves as a dashboard for buying ads. The people with the ads can then decide the audience for the ads: people in a particular geographic area, people browsing sites at a particular time of day, or determined by contextual information such as the kind of site a person is visiting. A car company might want to buy ads on a site that reviews cars, for example.
When someone navigates to a page that has that code, it wakes up AppNexus and checks whether there’s a deal already in place. If there’s not a direct deal in place, something more interesting happens. In this situation, services like AppNexus hold a real-time auction among potential ad sellers for the space. Advertisers duke it out with automated bidding—think eBay with its maximum bid thresholds—all before the site finishes loading. “It’s happening in milliseconds,” said Schulman.
This wouldn’t be possible without consumer data, but Schulman said AppNexus doesn’t want or even really need information on the people who end up seeing the ads. “We don’t ourselves have data that we use for targeting; our advertisers bring that to the table,” she explained. “We don’t have names. We don’t have email addresses.”
Stockpiling that kind of information would expose AppNexus to risk should it leak out. But Schulman said huge piles of data are not useful for the company’s purposes.
“We’re looking to reach wide swaths—millions and millions of impressions,” she said. It’s also not particularly efficient to target individuals: “We receive very, very basic information. We don’t know who these people are, and we don’t care who they are,” she said.
Instead of handling the information, the AppNexus system allows publishers to tie information to random IDs. Schulman said that even those within her company can’t parse what these random IDs represent. That’s on the clients. This is what Schulman means when she talks about privacy by design: “We prohibit our clients from sending us ID information, and we prohibit our clients from tying directly to identifiable information.”
The fears about her industry, she said, are caused by a lack of understanding. She also pointed to the actions of the Network Advertising Initiative (NAI), a self-regulatory agency for online advertisers. The NAI publishes codes of conduct and guidelines for data handling that members agree to follow. She wryly noted that there are some actual teeth to this agreement: “If you are a member of the Network Advertising Initiative, you’ve committed to complying with this code, and a violation of that is a violation is of section five of FTC [Act].”
In total, Schulman doesn’t see this model of advertising as problematic. “As a consumer who uses the web, and I’m privileged to know this business inside and out, I think it is more useful to see a relevant ad.” She considers companies like AppNexus to be part of, in her words, a “virtuous cycle” that improves the web overall.
Although she positions AppNexus and the like as neutral services in a larger industry, she believes that even the data brokers don’t deserve their reputation. At least, not entirely. She pointed out that the publishers and advertisers are looking for that information in the first place. “They don’t exist without clients. It feeds their business.” The web of commerce that supports the industry, it seems, distributes the blame as well.
Dropping Out of the Data Economy
Some people are very knowledgeable, but in interviews, they speak with incredible care, perhaps too aware that their words could be taken out of context or twisted against them. And then there are people who know just as much, but throw caution to the wind and simply say what they think. These people are quote machines.
Rob Shavell is a cofounder of the privacy company Abine, and he is a quote machine. He’s fast and direct with his comments, and he’s biting in his criticism of the online ad industry.
“It’s a specific problem, and the industry has made it very hard for consumers to put a value on privacy,” he said. “The data mining industry [couldn’t] exist if everyone really understood it clearly.” For the everyday person, he said, it’s very hard to not somehow be a part of this economy. “People are giving away information every day, if not every hour.”
He frames the problem this way: If a company came to you and said “Fill in this form with all your personal information because we can sell it for $39,” no rational person would agree to it.
Abine offers some unique tools to combat the rampant leakage of personal information. The Abine Blur service couples a tracker-blocking web plugin with the ability to disguise or “blur” your personal information. When a website requires an email address, Blur generates one for you and automatically forwards any messages to your real email address. It can do the same with your phone number, substituting a disposable number that keeps your real number private. Blur even generates virtual credit card numbers that decouple online payments from your true identity. The prepaid digital card is funded by your real credit card, but the virtual card’s number and associated address are generated by Abine and have nothing to do with you.
Blur is designed to keep you from spreading your information across the web, and Abine’s DeleteMe service cleans up what’s already out there. For an annual fee, DeleteMe manages the arduous task of removing your personal information from data broker sites, which gather personal information such as your address, phone number, and so on, and make it available online for anyone to search.
According to Abine, public records are the biggest source of data for brokers. The company says that activities that are necessary to functioning in society—say, buying property, registering to vote, and even renewing a driver’s license—can create public records that are mined by data brokers. Several brokers also collect information from court records, meaning that an individual’s criminal history is potentially for sale.
In Abine’s research, the company has seen the price of an individual’s information drop dramatically. Peoplefinder, a company Abine considers a data broker, previously sold a basic background check for $40, but that price has now dropped to $20. Basic information, such as old addresses, current addresses, and family connections can be bought for as little as 95 cents. The implication is that this information is so readily available that its inherent value has dropped.
Similar price fluctuations can be seen in personal information for sale on the Dark Web. A report from the security firm Flashpoint showed that stolen bulk data can go for as little as 10 cents per person. The price goes up depending on how much information is available and what kind of person the information represents. The Social Security number of someone with good credit, for instance, can sell for between $60 and $80.
“It’s cheaper to buy your personal information in 2018 than [it was in] 2016, sometimes 100 percent cheaper,” said Shavell, based on data removed by DeleteMe—which, it should be noted, communicates only with data broker sites that have publicly available information removal mechanisms. There are likely other services that aren’t so public-facing that DeleteMe does not engage with. But according to Shavell, DeleteMe found 1,000 pieces of information per person in 2016. By 2018, the service was tracking 1,500 pieces of information.
“That’s not a great trend for privacy,” said Shavell.
Personal data has value on its own. People, it seems, are willing to spend money to find out the real addresses of other people, or these data brokers would be out of business. But Shavell noted that there’s a connection between data brokers and online targeted advertising.
Taking the information from these information brokers and making it useful for advertising is, Shavell explained, an entirely other piece of the business. He describes a “galaxy of companies” that play different roles in connecting user data from a myriad of sources and making it more valuable. The pipeline is familiar to me from my writing about how hackers monetize stolen information. One person might steal millions of records from a website and sell them cheaply to someone else who can add more to them or collate the information more efficiently, and then resell the data for a higher price.
Shavell described a similar arrangement in which data companies buy and sell data, slicing and dicing it in different ways in order to glean something new. “Each one of them has very sophisticated pricing,” he said. “The prices go up and down depending on who we are, how recent the information is, whether it’s from a mobile device, whether it’s from iOS or not, what county you’re in, and what you’ve searched”
One example Shavell gave is LiveRamp, which is owned by Acxiom. “What they specialize in is matching the cookies of where you visit that advertising networks place and matching it to your actual profiles from data brokers.” This gives advertisers two critical pieces of information: a person and their intent.
“It’s this incredible real-time stock market that combines information of what we’re doing on our phones and websites we visit and then matches that to the personal information we’ve given out about us,” said Shavell. The result is ads targeted toward what a theoretically receptive audience, based on information on consumers (that’s us) pulled from several different sources.
The LiveRamp service says it can apply unique identifiers to user data: “applying individual-level identity resolution through a privacy-safe, deterministic (exact one-to-one) matching process.” The blurb continues, “To ensure the highest level of accuracy, LiveRamp and Acxiom maintain consistent recognition on 98% of U.S. adults and nearly 100% of U.S. households.”
Acxiom did not respond to my request for an interview, and I couldn’t try out the service for myself. It’s an odd feeling since, if the company’s statistics are correct, they know who I am.
Each link in the chain gets something out of the arrangement, but Shavell contended that there’s something bigger happening here. By avoiding centralization of this information in any one company, the individual companies get their cut, and they also avoid culpability.
“They will tell you that this information is anonymous in their little database, and it’s always anonymous, but what these marketplaces do is they allow everyone to claim that their data is anonymous, and matched in a marketplace. It allows every individual company to basically claim that they’re innocent when [they’re] really completely guilty.”
Noticeably missing from the galaxy Shavell described are the titans of the modern internet: Amazon, Facebook, and Google. These companies might seem an odd addition to the list of data companies, but each has enormous insight into what many—perhaps most—people do online.
While Google’s most visible product is a search engine, and the company has expanded into just about every facet of modern existence, it has always been an advertising and data company at heart. “When you search, they know exactly what keywords you have, what history of keywords you’ve used,” said Shavell. “They sell those to their ad networks, and people bid on them, and that’s where they continue to make most of their money.”
Facebook also has enormous reach, thanks to its size and to the captive audience that clicks on links shared in the news feed. Some of the credit also goes to the sites and services Facebook owns, as well as sharing links and buttons that appear on different websites outside Facebook. These can provide telemetry, allowing Facebook to track you even when you’re not on a Facebook-owned site.
A 2017 study of 144 million page loads found that 77 percent of all page loads included some kind of tracker. Google was the outright leader, receiving data from 64 percent of page loads. A distant second, but still far ahead of the rest of the competition, was Facebook at 28 percent.
Amazon, recently the second-ever company to be valued at over a trillion dollars (after Apple), is also looking to expand its reach into the advertising data space. “Amazon is making a lot of investments into ad tech and into becoming a player in this area, when they already have so much information about our ecommerce habits,” said Shavell.
Google might know a lot, but its shopping efforts haven’t gathered much traction. “Amazon is coming from a very entrenched position and is going to try to use some of the tools that Google is using to expand into this advertising business. That’s a little bit nerve-wracking, in the sense that it hasn’t really happened before. [Amazon is] the company that knows the most about our buying habits.”
Data for Sale
Although the data economy is filled with intermediaries, Shavell reserves special ire for the data broker websites that collate and sell personal information such as phone numbers and addresses. He believes that the solution doesn’t lie in products like DeleteMe but with government. “We think there should be more government regulation, not less, in this industry. We work with the FTC and the FCC when we can to make them aware of what we consider to be terrible behavior of these data brokers, and we will help to gather evidence and grassroots support for regulatory reforms that give consumers more power over these data brokers.”
To Shavell, data brokers are equivalent to blackmailers. “There’s no reason [individuals] shouldn’t be able to tell these data brokers to take it down, and there’s no reason they should pay DeleteMe.” It’s notable that the services DeleteMe engages with do, in fact, have mechanisms for individuals to remove their information. The function of DeleteMe is to offload the work, for a fee, to a dedicated staff.
“Regulatory reforms make sure data brokers are getting away with data murder, so to speak, and doing whatever they want. And ultimately, you want regulation to be so strong that [consumers] can do most of this stuff themselves, and services like DeleteMe become less and less necessary.”
“Advertising is not evil,” Shavell conceded. “But our position is that there need to be boundaries, and consumers need to have control over what information is out there specifically.”
As for what individuals can do to protect their privacy, Shavell is surprisingly optimistic. “The more you talk about it, the more daunting it seems,” he said, but he adds that individuals can take action to protect their own data. “Just installing an ad blocker and giving out a little bit less information—that stuff does a lot.”
Crude Data
Ad targeting and retargeting aren’t the only ways to monetize data.
If trackers and exchanges like AppNexus handle the refined, polished, and (allegedly) anonymized, data brokers handle the crude—the raw data, gathered not from Google searches or tracking pixels but aggregated from publicly available sources.
One such data broker has a familiar name: Whitepages. Although the name recalls a book of local phone numbers, the digital incarnation is a different beast. “With comprehensive contact information for over 500 million people including cell phones, the most complete background check data compiled from records in all 50 states, and much more, we’re not your traditional white pages directory or phone book,” its site reads.
Typing my name into Whitepages pulled up 77 results. I discovered that there was another Max Eddy living in my parents’ town, less than a mile away. My grandfather, or rather a misspelling of my grandfather’s name, was there, too. It listed his age as 80, although he’s been dead for over a decade. I found a Maxwell A. Eddy who apparently lives close to my current address, which might explain why I’ve been receiving letters from The New York Times addressed to that name for several years.
I showed up under my legal name, along with my current domicile and the last three places I’ve lived. Next to that are both my siblings, my father, three cousins, and one uncle. To see more information, including my phone number, more previous addresses, and public records (such as arrests), I’d have to pay.
After I paid $1 for a limited trial, Whitepages obligingly delivered a report with my current address, several previous addresses, accurate phone numbers (including the phone number of my parent’s home), along with even more relatives and their profile information.
A full background report would include criminal records, traffic records (tickets and such), bankruptcies and foreclosures, a listing of properties purchased in my name, liens and judgments against me, and professional licenses. This last one is interesting in that it apparently includes things like FAA-issued pilots’ licenses and concealed-weapons permits. It appeared that Whitepages didn’t have any information on me in these categories, but I’d have to pay $19.95 to get the full report and be sure.
I reached out repeatedly to Whitepages for an interview, but after much back and forth, no interview resulted. I also found my information (available at varying price points) on other data broker sites, including Intellius and BeenVerified.
To get an idea of the scope of what data brokers know about me, I asked Abine to provide me with access to its DeleteMe service. For $129 a year, real humans at Abine work to have your personal information removed from data brokers and public record sites. Because Abine looks into other services to find your information, you must, unfortunately, hand over a lot of personal information to Abine. I added my legal name, a few nicknames, my current and former addresses (that I could remember), phone numbers, and so on. I clicked a blue button and waited.
Initial results came back within a few days. Subsequent reports varied but showed that my information was definitely for sale. By July, 30 services were included in my DeleteMe report, and my information appeared on two them. A follow-up report in August showed 28 sites in my report, and my information on 19 of them. Nearly all of the data broker sites had my name, age, past addresses, and family members; some included phone numbers, photos, email addresses, and social media accounts.
Reports from DeleteMe include an indicator that an opt-out request has been sent and a note on how long such an opt-out takes. In some cases, it’s instant; in others, it takes weeks. I asked Abine whether my information might appear on these services even after DeleteMe successfully had it removed. The answer was yes, it could.
It’s remarkable how much of my personal information was available on these services, and even more remarkable how far back it went. For me, there’s an implicit threat to this: Anyone could find it. Wouldn’t I want to find out what’s there, in case it’s truly awful? To even see how much information a service had on me, embarrassing or otherwise, I would have to pay up.
I Don’t Know You, but You Know Me
Harrison Tang is the CEO and co-founder of Spokeo, a data broker site similar to Whitepages and one of the sites that has my personal information displayed online. When I search my name on Spokeo, I find my address, my phone number, and much of the same information I found on Whitepages. Spokeo is a bit hipper: It also searches 104 social-media platforms, including Twitter and YouTube, and even dating services such as OKCupid. When I searched, Spokeo claimed it had 14 photos of me, along with nine social networks associated with a personal email address. It would cost me $7.95 to see what this all included.
I wasn’t sure what to expect when I spoke with Tang. His office had been surprisingly forthcoming and engaging, unlike other data brokers. But I had a real sense of dread going into the interview—a holdover, I suppose, from seeing so many of my intimate details available for sale on so many websites.
On the phone, Tang was relaxed, and he spoke very deliberately. Right away, he pointed out that his company isn’t part of the ad economy that I was asking about. “We’re not in the ad industry; we don’t sell our data to third parties.”
Tang said that the signup process for purchasing information from Spokeo requires customers to declare what they intend to use the information for, and that the company actively screens out data or ad purchasers. The company offers no API to access its information, and it limits customer access to only a web portal and mobile app. “They can’t download our data en masse,” explained Tang.
When I ask whether Tang would be willing to give me the names of services that do sell data en masse, he politely declined. Rather than advertisers, he said his customers are people and companies trying to find other people—sometimes family members, sometimes for fraud detection.
While the privacy advocates I spoke with described data brokers like Spokeo as the source of personal data online, Tang considers Spokeo to be the end of the pipeline. Spokeo, he explained, aggregates data from more than 12 billion public records, including phonebooks, court records, public social media profiles, historical records, property records, and so on. “All this data, aggregated together. And we organize them into simple, easy-to-understand profiles so people can search connections and know who they’re dealing with.” Only publicly available data goes into Spokeo, Tang said.
The desire for this information is clearly there, as Tang points out several times that 8 percent of searches online are for first and last names. “Some people call data the third industrial revolution,” said Tang. To him, Spokeo as well as Google and Facebook are “people-search companies.”
While Spokeo does offer a one-step opt-out, Tang doesn’t believe that is a good solution. “People mistake that privacy is about hiding your information, hiding from your world,” he said. “We believe privacy is about control—it’s about transparency.”
According Tang, the future of Spokeo actually sounds remarkably Facebook-like. In the future, he hopes that Spokeo will be a platform where people claim their profiles and edit the available information. Verification that people are who they say they are, Tang conceded, is the biggest challenge. But this approach, said Tang, would put people in control of their information, rather than simply hiding it.
When I hung up the phone after speaking with Tang, I didn’t think too much about this new privacy he describes. It sounded like a pipe-dream, the enthusiastic vision of a man who genuinely believes his service helps people. Only months later, when I revisited the interview, the sense of menace crept back in. The implicit threat, I realize, is still there, whether Tang realizes it or not. That future vision is a kind of nonconsensual Facebook, where we have to sign up—or else someone else is in control of our information. Ignore it at your peril.
A Galaxy of Ads
Looking at the data economy, it’s hard to find actual bad actors. As weirdly threatening as data brokers are, most do include a mechanism to remove your information. Ad targeting and retargeting, meanwhile, isn’t the product of a single company, but a concept that has invaded the foundations of just about every online service you can think of. And all of them get their information from somewhere else, and pass it on to someone else, and make a little bit of money along the way.
Shavell called the data economy a galaxy, and the metaphor is apt. From far enough away, a galaxy is just a single point of light among other lights; get too close, and you see just a lone star. It’s only with the proper perspective that the full complexity is visible. And while I can watch the numbers tick up and down on my tracker blocker as I go from site to site, I still don’t really know who’s watching me, or how the money is flowing. Just that, somehow, it is.
This story first appeared in the ad-free, curated PCMag Digital Edition, available on iOS, Android, and other mobile platforms.
Source: https://www.pcmag.com/article/364152/how-companies-turn-your-data-into-money
0 notes
Text
Android Security Measures
As I write this, I am aware that there are a few different approaches to Android security. This article aims to provide the following:
Just ensuring you have a basic understanding of security
You know how to be private and safe
Know how to lock down and secure your devices
( I’m sure there are lots of other approaches but for the sake of keeping it simple this is how I would categorize them )
We all know the type of people that have antivirus and do not install anything from anywhere but the Goggle Play Store. Those individuals probably also have a finger swipe lock and that is all they need or want to know about. Not to say that is bad – it’s good to feel secure – but that is literally the MOST basic form of “security” for your device.
However, I will help with just adding a little bit more to this, and how to do it while keeping it as simple as possible.
( 1 ) Antivirus – I assume nearly everyone has this, but if you don’t, go to the Google Play Store and have a look at a few ( most are free ) and install one. This will help you by finding the most known Viruses Spyware and in most cases advise you how to change some settings for additional security. Remember, your data – images, texts, saved login information – is private and personal. Keep it that way!
( 2 ) Screen-lock – Everyone should know what this is. It is as old as mobile phones are nowadays. It locks the screen after the screen goes black or after a set time limit of inactivity. You can often access the screen lock options by going to Settings > Security > Screen Lock, which will ensure that a code, pattern or password needs to be entered in order to unlock the screen once it has been locked.
I would recommend using the PIN or Password option, as these are not restricted by length (it may be restricted to 4 characters on some devices). But also, due to how easily a swipe pattern can be unlocked by one of these methods: 1. tilting the screen so you can see the swipe marks and repeat the pattern, or 2. just watching the person’s swipe pattern (a form of shoulder surfing).
( 3 ) Encryption – Device Encryption disguises data by rearranging the data so that no one can see/access it without a password or key.
This can be done in Settings > Security > Encryption. Before you can utilize device encryption, however, you will be required to set a screen lock password ( Device should be connected to a charger while doing this).
( 4 ) Phone Location Tracking – Device Tracking is self-explanatory and there is no shortage of apps out there on the Google Play Store to track your device if you lose it outside or just down the back of the sofa. All you do is register your phone’s details then test it about the house and track it. This ensures if you lose your phone, or if it is stolen, you can always track it down.
( 5 ) Software Updates – Updating the Software on your Android device can remove any vulnerabilities in the device’s software and should always be done at the first possible time.
There are two ways of doing this –
Updating the Phones OS (Operating System)
Settings > AbouPhonene > Updates > Check for Updates.
Updating the Apps
Open Google Play Store > My Apps this should show any updates that are available for any of your installed apps
*( I would always recommend you update your device at home while plugged in and on a trusted internet connection )
I believe these five things are about as basic as it gets for Android Security. In the next part “Being private and safe,” I will go into more detail and try help the slightly more tech confident user by showing them how easily a mobile device can be compromised and what could potentially be done to it.
Security and the slightly more advanced stuff but nothing too complicated: ( By securing these settings you secure your device and probably save battery life and save on data charges )
( 6 ) Useful Settings – These are two simple ways of securing your device and yourself.
Network Settings
Bluetooth, Wifi, NFC, Tethering and Portable Hotspots, should always be switched OFF when not being used. All of these methods leave your device open to attack and as you may leak your data out or allow another user to access your device remotely.
All of these can be changed from Settings > Wireless and Network Settings
Location Settings
Only turn on location settings when you need them. It is important not have these services running when not required as it increases the risk of location tracking.
Settings > Personal > Location
( 7 ) Useful Apps – There are lots of different apps that can increase the security on your Android but here are just a few that can seriously increase your privacy.
Password managers
A password manager is a small easy to use a database on your phone that you can save passwords and usernames for your favorite websites ( or anything really ) which are fully encrypted and secure a quick look on the Google Play Store will find lots of these.
App Lockers
App Lockers are apps that give you the ability to stop another user using a specific app or your entire device without entering a specific information. ( this can be a fingerprint scan or password or pattern ) They usually include other features like the if an intruder enters a password wrong 3 times it will take pics with both front and rear camera
*I could write all day about app lockers but if you want more information a simple internet search will provide lots of information and which one is best for you
( 7 ) Backup and Cloud Storage – Losing pictures videos or documents can be annoying at least or extremely embarrassing and emotional at worst. There is no shortage of apps out there for online storage to back these up. I won’t list the best and worst here but Android Devices come with Google Drive which gives you 15gb of free online space to save you private data to. All you need to do to avoid having your stuff leaked online like a celebrity ( if you’re popular enough to have someone try ) Is to set a decent password or passphrase that you can remember and won’t be easy for people to guess.
Off topic but there are apps out there you can buy ( usually available for a free trial though ) that can monitor pretty much everything that happens on a device. ( note I never said YOUR Device ) That is because these apps are primarily used to keep an eye on family members to ensure they are safe online, but I believe they work as a good example of what kind of data YOU could be leaking by installing Apps from unknown sources or by rooting your device.
Mspy
https://www.mspy.com/
Tipsy
https://tispy.net/
Check them out
* Note I am no way affiliated with either of these apps and I am not being paid to promote them I just think they are good examples to show people what a user could do with access to you phone for a short period.
Okay, now it’s time to roll out the tinfoil hats ………….
Not all people that want to block people from eavesdropping on their phone calls or reading their messages are nefarious characters, or paranoid. Some people just want better privacy or to learn how to do this for educational reasons
( 8 ) Private Encrypted phone calls – Encrypted voice calls over the internet has become more popular lately due to lots of available apps that can provide this service. This provides Security against eavesdropping and electronic surveillance and can keep your conversations private.
( 9 ) Encrypted end to end messaging – Encrypted messaging does exactly what it says, It encrypts the content of a message so that only the sender and receiver can read the data. This has become commonplace even popular Apps like WhatsApp now include end to end encryption but there are other tools which also do this and have a higher level of encryption.
( 10 ) Anonymous and private internet surfing – There are few Apps that are designed to increase the anonymity of your activities on the Internet by sending your connections over the Tor network, But there isn’t any better than Orweb and Orbot. When used together Orweb & Orbot allow you to send all your web browsing over the Tor network and maintain a high level of Privacy
( 11 ) Panic Buttons – A Panic Button App will enable you to secretly trigger an alarm on your phone to send a prewritten text message to a predefined list of contacts know you may be in danger. There are a few of these available on The Google Play Store.
( 12 ) Data Leakage – Data Leakage is when your Android device leaks sensitive information (such as your phone number, contacts, location, etc) to other installed apps on your phone. Allowing that data to be used potentially against your wishes. X-privacy is a free App, which can stop this from happening you just have to set up its rules first.
That is it. All the best ways to ensure your privacy and security on Android Devices. you may not use all of what I have provided but all of this is to ensure you have a good idea of what can be done to keep yourself safe and secure when using your Android device.
I would like to do a course on this topic for Cybrary, but let me know if there is any more you’d like me to cover. I hope you have enjoyed this post. Comment if you have questions!
0 notes
Text
Crowdfire Monthly — June
By Crowdfire
Last month’s feature releases product improvements and bug fixes
“How we spend our days is, of course, how we spend our lives.” — Annie Dillard, 1989
“And also our months.” — Ann Maria, 2017
So, without further ado, here’s how we spent our slightly rainy days at Crowdfire this June.
Tailored Posts
Get the most engagement with these perfect posts, customised for each of your social networks. Take a quick look at the previews and tap, tap, share!
Preview and Post!
Sign Up with Facebook
Don’t have an Instagram or a Twitter account? You can now sign up on Crowdfire using Facebook!
Secure and convenient sign up through FB
Smart Posts Power-Up
Want that botched seafood cafe review to disappear? Maybe the crocheted sweaters your audience loved last winter are now out of season? No worries, simply block them from your recommendations — just for now or forever — you decide!
Be the boss of your Smart Posts!
Under the Hood ⚙️ (June bugs, quite literally!)
Web, iOS and Android
There used to be an error while scheduling images from your mobile device’s Photos app using the share extension. Used. To.
Images would not get posted to your Facebook page from your image recommendations. Neither would Facebook links. FIXED!
The “Post Now” pop-up for Instagram was being quite bothersome, trimming your caption text like nobody’s business. FIXED!
This was a painful phenomenon that many of you experienced — the quality of images being published was rather poor Frown no more, we brought back the high-resolution quality!
Rejoice! We added UnSplash as an image source for your recommendations. Say hello to high quality beautiful pictures
I think I’m quite GIF-ted with accomplishing tasks on our Trello
Meet our amazing users
From our Spotlight series ✍️
From Drug Dealer to Acclaimed Author
Catch up with our Podcast
http://bit.ly/2tz4KDQ
User of the Month
We have our HotShot YouTuber — VeixxBeats. A music producer from Finland, VeixxBeats earns their living by selling original tracks on their website.
With more than 15k subscribers (and growing!) this beat-maker draws about 50k views a week to their channel. Go ahead and give them a listen!
What people around the world are saying about Crowdfire
What We’ve Been Reading
We’re in love with Gary Vee — here are two gems from him on Instagram networking and being successful!
How To Network On Instagram DM
Why 1 View is Everything
That’s all, folks
We’re winding down to a close, but really we’re winding up for all that July promises. Anything you’re looking forward to this month? Feel free to share your thoughts, feedback and suggestions in the comments
http://bit.ly/2tyNdfc
Psst… Continue the conversation with us every Thursday on #cfchat and join our tribe on Twitter!
Ann Maria is a Content Crafter at Crowdfire. She’s thinking of changing her name to JuneBug.
Hey there! Missed out on the May Update? Catch up here:
Crowdfire Monthly — May
Crowdfire Monthly — June was originally published in Going Big — The Official Crowdfire Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.
The post Crowdfire Monthly — June appeared first on Make It With Michael.
from Crowdfire Monthly — June
0 notes