#consumer data consent management for businesses
Text
Data Protection: Legal Safeguards for Your Business
In today’s digital age, data is the lifeblood of most businesses. Customer information, financial records, and intellectual property – all this valuable data resides within your systems. However, with this digital wealth comes a significant responsibility: protecting it from unauthorized access, misuse, or loss. Data breaches can have devastating consequences, damaging your reputation, incurring…

View On WordPress
#affordable data protection insurance options for small businesses#AI-powered tools for data breach detection and prevention#Are there any data protection exemptions for specific industries#Are there any government grants available to help businesses with data security compliance?#benefits of outsourcing data security compliance for startups#Can I be fined for non-compliance with data protection regulations#Can I outsource data security compliance tasks for my business#Can I use a cloud-based service for storing customer data securely#CCPA compliance for businesses offering loyalty programs with rewards#CCPA compliance for California businesses#cloud storage solutions with strong data residency guarantees#consumer data consent management for businesses#cost comparison of data encryption solutions for businesses#customer data consent management platform for e-commerce businesses#data anonymization techniques for businesses#data anonymization techniques for customer purchase history data#data breach compliance for businesses#data breach notification requirements for businesses#data encryption solutions for businesses#data protection impact assessment (DPIA) for businesses#data protection insurance for businesses#data residency requirements for businesses#data security best practices for businesses#Do I need a data privacy lawyer for my business#Do I need to train employees on data privacy practices#Does my California business need to comply with CCPA regulations#employee data privacy training for businesses#free data breach compliance checklist for small businesses#GDPR compliance for businesses processing employee data from the EU#GDPR compliance for international businesses
0 notes
Text
The Cookie Crumbles: Three Strategies for Effective Advertising

Advertising used to be a rather haphazard affair before the internet. Brands would release numerous ads and messages into the world, hoping that some would resonate with their intended audience. Despite its inefficiencies, this system managed to function adequately. Then came a game-changing development: the ability for companies to track consumers online and customize their advertising based on specific user profiles, thanks to technologies like web-based cookies and personal identifiers. However, the era of third-party cookies is drawing to a close, signaling another shift in the advertising landscape.
To stay ahead and foster greater growth while acquiring new clients, brands can adopt strategies like leveraging their own customer interactions, engaging in data exchanges with other businesses, and exploring consumer targeting based on context and interests.
The Decline of Cookies
The internet underwent a transformation with the advent of cookies. Two decades ago, Lawrence Lessig remarked, "After cookies, the web becomes a space capable of extraordinary monitoring."
Lessig, a prominent legal scholar and former leader at Harvard University's Safra Center for Ethics, foresaw the profound impact of privacy concerns on the evolving digital landscape. For years, marketers relied on cookies to track users' activities across different websites, tailoring ads based on their browsing behavior. However, cookies are now becoming obsolete, and alternative tracking methods are facing scrutiny, posing challenges for advertisers.
Apple's implementation of app-tracking-transparency (ATT) policies requires app providers to obtain explicit consent from users before tracking them using device identifiers in the mobile app realm. Early data suggests that only about 46% of users are likely to consent to such tracking.
This percentage could be even lower in regions where privacy consciousness is heightened. Consequently, a significant portion of users within the Apple ecosystem may remain untraceable by app publishers relying on device identifiers. Notably, both Google and Apple have pledged not to develop or support workarounds like probabilistic fingerprinting to create user-level profiles within their platforms.
Understanding First-Party Cookies
First-party cookies are small data snippets that websites directly store on a user's device via their web browser. These cookies originate from and are managed by the website the user is actively visiting. Unlike third-party cookies, which are generated by external domains and used for cross-site tracking, first-party cookies are confined to interactions within a single domain.
Here's how first-party cookies benefit advertisers:
Tracking User Interactions: Advertisers can monitor user actions within their own websites, such as product views, cart additions, purchases, or newsletter sign-ups. This data provides insights into user behavior and preferences.
Personalization and Targeting: First-party cookies enable personalized experiences based on past interactions, improving engagement and conversion rates.
Retargeting and Remarketing: Advertisers can use first-party data to re-engage users across different platforms, encouraging them to complete actions.
Measuring Ad Campaign Performance: First-party cookies aid in tracking campaign metrics like click-through rates and conversions, facilitating performance evaluation and optimization.
Enhancing User Experience: Tailored content and recommendations enhance user satisfaction and loyalty.
Compliance with Privacy Regulations: First-party cookies are considered less intrusive and more compliant with privacy guidelines than third-party cookies.
Exploring Second-Party Cookies
Second-party cookies involve data exchange between trusted partners, unlike first-party cookies limited to a single domain and third-party cookies from external sources. Here's how they assist advertisers:
Data Collaboration: Trusted partners share relevant user data, enhancing targeting efforts.
Enhanced Personalization: Insights from partners' data improve ad relevance and effectiveness.
Audience Expansion: Partnerships broaden audience reach and improve campaign performance.
Improved Ad Placement: Informed decisions lead to better ad placements on partner sites.
Cross-Channel Campaigns: Data integration across channels creates cohesive marketing strategies.
Data Quality and Trust: Second-party data from trusted sources ensures reliability and compliance.
Understanding Third-Party Cookies
Third-party cookies track user behavior across multiple websites, aiding advertisers in targeted advertising. Here's how they help:
Cross-Site Tracking: Insights from third-party cookies enable cross-site user tracking for targeted campaigns.
Behavioral Targeting: Segmenting users based on online activities enhances ad personalization.
Retargeting and Remarketing: Targeted ads based on user actions improve conversion rates.
Audience Segmentation: Detailed audience profiles improve ad relevance and engagement.
Ad Performance Measurement: Metrics tracking aids in campaign optimization and budget allocation.
Cross-Device Tracking: Consistent experiences across devices improve user engagement.
Ad Network Optimization: Strategic ad placements maximize visibility and impact.
In conclusion, the phasing out of third-party cookies and evolving privacy regulations will disrupt the advertising landscape. Advertisers must adapt by exploring alternative strategies to maintain effectiveness and comply with privacy standards, ensuring sustainable growth and reduced acquisition costs in the future.
Stay ahead in the dynamic landscape of digital marketing! https://www.hopbug.com
#indonesia#jakarta#digitalmarketing#digitalmarketingagency#hopbug#hopbugmedia#performancemarketing#digitaladvertising#advertising#digitalagency
2 notes
·
View notes
Text
Top Challenges in the Market Research Industry

Market research serves as the backbone of informed decision-making in businesses, guiding strategies, product development, and customer engagement. However, like any industry, market research is not without its challenges. In this article, we explore some of the top challenges faced by professionals in the market research industry and strategies to overcome them.
Data Quality and Reliability: Ensuring the quality and reliability of data is paramount in market research. Issues such as incomplete responses, biased samples, and data inaccuracies can compromise the integrity of research findings. To address this challenge, researchers must employ robust data collection methods, implement validation checks, and utilize statistical techniques to identify and mitigate biases.
Sample Representation: Obtaining a representative sample that accurately reflects the target population can be challenging, especially in niche markets or industries. Biases in sampling methods, such as non-response bias or sampling frame errors, can lead to skewed results. Researchers must employ diverse sampling techniques, such as stratified sampling or quota sampling, to ensure adequate representation across demographic groups and minimize sampling biases.
Data Privacy and Compliance: With the increasing focus on data privacy regulations such as GDPR and CCPA, market researchers face challenges in collecting and handling sensitive consumer data. Ensuring compliance with data protection laws, obtaining informed consent from respondents, and implementing robust data security measures are essential to safeguarding consumer privacy and maintaining ethical research practices.
Technology Integration and Adaptation: The rapid evolution of technology presents both opportunities and challenges for market researchers. Adopting new research methodologies, leveraging advanced analytics tools, and harnessing emerging technologies such as artificial intelligence and machine learning require continuous learning and adaptation. Researchers must stay abreast of technological advancements and invest in training to harness the full potential of technology in market research.
Response Rate Decline: Declining response rates in surveys and research studies pose a significant challenge for market researchers. Factors such as survey fatigue, spam filters, and increasing competition for respondents' attention contribute to lower response rates. To combat this challenge, researchers must design engaging surveys, personalize communications, and incentivize participation to encourage higher response rates.
Big Data Management and Analysis: The proliferation of big data sources presents both opportunities and challenges for market researchers. Managing large volumes of data, integrating disparate data sources, and extracting actionable insights from complex datasets require advanced analytics capabilities and specialized expertise. Market researchers must leverage data visualization tools, predictive analytics, and data mining techniques to derive meaningful insights from big data and inform strategic decision-making.
Adapting to Market Dynamics: The dynamic nature of markets, consumer preferences, and industry trends poses a constant challenge for market researchers. Staying ahead of market shifts, identifying emerging opportunities, and predicting future trends require agility and foresight. Researchers must continuously monitor market dynamics, conduct regular market assessments, and employ agile research methodologies to adapt to changing market conditions and stay competitive.
In conclusion, while market research offers invaluable insights for businesses, it is not without its challenges. By addressing key challenges such as data quality, sample representation, technology integration, and response rate decline, market researchers can overcome obstacles and harness the power of data-driven decision-making to drive business success in an increasingly competitive landscape. Embracing innovation, adopting best practices, and fostering a culture of continuous learning is essential for navigating the evolving landscape of the market research industry.
To know more about Read our latest Blog: https://rise2research.com/blogs/top-challenges-in-the-market-research-industry/
Also Read:
online market research services
data collection and insights
survey programming services
healthcare market research
2 notes
·
View notes
Text
Amazon Product Review Data Scraping | Scrape Amazon Product Review Data

In the vast ocean of e-commerce, Amazon stands as an undisputed titan, housing millions of products and catering to the needs of countless consumers worldwide. Amidst this plethora of offerings, product reviews serve as guiding stars, illuminating the path for prospective buyers. Harnessing the insights embedded within these reviews can provide businesses with a competitive edge, offering invaluable market intelligence and consumer sentiment analysis.
In the realm of data acquisition, web scraping emerges as a potent tool, empowering businesses to extract structured data from the labyrinthine expanse of the internet. When it comes to Amazon product review data scraping, this technique becomes particularly indispensable, enabling businesses to glean actionable insights from the vast repository of customer feedback.
Understanding Amazon Product Review Data Scraping
Amazon product review data scraping involves the automated extraction of reviews, ratings, and associated metadata from Amazon product pages. This process typically entails utilizing web scraping tools or custom scripts to navigate through product listings, access review sections, and extract relevant information systematically.
The Components of Amazon Product Review Data:
Review Text: The core content of the review, containing valuable insights, opinions, and feedback from customers regarding their experience with the product.
Rating: The numerical or star-based rating provided by the reviewer, offering a quick glimpse into the overall satisfaction level associated with the product.
Reviewer Information: Details such as the reviewer's username, profile information, and sometimes demographic data, which can be leveraged for segmentation and profiling purposes.
Review Date: The timestamp indicating when the review was posted, aiding in trend analysis and temporal assessment of product performance.
The Benefits of Amazon Product Review Data Scraping
1. Market Research and Competitive Analysis:
By systematically scraping Amazon product reviews, businesses can gain profound insights into market trends, consumer preferences, and competitor performance. Analyzing the sentiment expressed in reviews can unveil strengths, weaknesses, opportunities, and threats within the market landscape, guiding strategic decision-making processes.
2. Product Enhancement and Innovation:
Customer feedback serves as a treasure trove of suggestions and improvement opportunities. By aggregating and analyzing product reviews at scale, businesses can identify recurring themes, pain points, and feature requests, thus informing product enhancement strategies and fostering innovation.
3. Reputation Management:
Proactively monitoring and addressing customer feedback on Amazon can be instrumental in maintaining a positive brand image. Through sentiment analysis and sentiment-based alerts derived from scraped reviews, businesses can swiftly identify and mitigate potential reputation risks, thereby safeguarding brand equity.
4. Pricing and Promotion Strategies:
Analyzing Amazon product reviews can provide valuable insights into perceived product value, price sensitivity, and the effectiveness of promotional campaigns. By correlating review sentiments with pricing fluctuations and promotional activities, businesses can refine their pricing strategies and promotional tactics for optimal market positioning.
Ethical Considerations and Best Practices
While Amazon product review data scraping offers immense potential, it's crucial to approach it ethically and responsibly. Adhering to Amazon's terms of service and respecting user privacy are paramount. Businesses should also exercise caution to ensure compliance with relevant data protection regulations, such as the GDPR.
Moreover, the use of scraped data should be guided by principles of transparency and accountability. Clearly communicating data collection practices and obtaining consent whenever necessary fosters trust and credibility.
Conclusion
Amazon product review data scraping unlocks a wealth of opportunities for businesses seeking to gain a competitive edge in the dynamic e-commerce landscape. By harnessing the power of automated data extraction and analysis, businesses can unearth actionable insights, drive informed decision-making, and cultivate stronger relationships with their customers. However, it's imperative to approach data scraping with integrity, prioritizing ethical considerations and compliance with regulatory frameworks. Embraced judiciously, Amazon product review data scraping can be a catalyst for innovation, growth, and sustainable business success in the digital age.
2 notes
·
View notes
Text
Navigating the Digital Labyrinth: A Journey Through Data-Driven Marketing
In today's dynamic digital landscape, intuition and guesswork no longer suffice for marketing success. Businesses must wield a powerful weapon: data. Data-driven marketing has emerged as the guiding light, illuminating the path towards targeted campaigns, optimized strategies, and measurable results.
Imagine a vast and intricate labyrinth, representing the ever-evolving consumer landscape. Data becomes the map, revealing pathways to connect with your target audience and navigate towards successful campaigns. By analyzing data, marketers can decipher customer preferences, uncover hidden trends, and predict future behavior. This invaluable knowledge empowers them to craft personalized interactions, deliver relevant content, and ultimately, forge deeper connections with their customers.
But what exactly is data-driven marketing? It's a holistic approach that integrates data collection, analysis, and insights into every stage of the marketing funnel. This comprehensive strategy covers numerous aspects, including:
Market research: Analyzing customer demographics, interests, and online behavior through surveys, social media interactions, and website analytics.
Keyword research: Identifying relevant search terms used by target audiences to optimize content and digital ads.
Campaign performance tracking: Measuring the effectiveness of marketing efforts across various channels, such as email marketing, social media campaigns, and website traffic.
Attribution modeling: Understanding which touchpoints contribute most to conversions, allowing for efficient budget allocation and campaign refinement.
Content personalization: Delivering customized content based on individual preferences and past interactions, fostering audience engagement.
The benefits of embracing data-driven marketing are multifaceted:
Increased ROI: Data-driven campaigns are inherently more efficient, allowing for targeted spending and optimized resource allocation. By focusing on qualified leads and high-converting channels, businesses can maximize their return on investment.
Enhanced customer engagement: Deep customer insights enable the creation of personalized content, tailored advertising, and relevant omnichannel experiences. This personalized approach fosters deeper relationships and increases customer engagement.
Improved decision-making: Data-driven insights provide clear evidence to support marketing decisions, replacing guesswork with actionable strategies. This data-backed approach leads to more informed campaigns and increased campaign effectiveness.
Predictive capabilities: Analyzing patterns and trends allows marketers to anticipate future customer behavior and proactively address their needs. This proactive approach gives businesses a competitive edge and fosters innovation.
However, navigating the data-driven marketing landscape isn't without its challenges:
Data overload: The sheer volume of data available can be overwhelming, requiring robust data management and analysis tools.
Privacy concerns: Ethical data collection and responsible use of user information are crucial to maintain consumer trust and comply with regulations.
Technical expertise: Analyzing complex data sets and translating insights into actionable strategies often requires specialized skills and resources.
To successfully overcome these challenges, businesses need to:
Invest in the right tools and technology: Robust data management platforms and analytical tools are essential for efficient data collection, analysis, and visualization.
Prioritize data privacy: Implement clear data collection practices, obtain informed consent, and adhere to data privacy regulations.
Build a data-driven culture: Encourage collaboration between marketing, IT, and analytics teams to utilize data effectively and foster a culture-wide data-driven mindset.
Ultimately, data-driven marketing is not just a trend; it's a transformation. By embracing data as a compass, businesses can navigate the modern marketing labyrinth, build meaningful customer relationships, and achieve sustainable success. Now we know, that data is not the destination, but the map that guides your journey towards a brighter and more impactful marketing future.
Follow me on LinkedIn: www.linkedin.com/comm/mynetwork/discovery-see-all?usecase=PEOPLE_FOLLOWS&followMember=totaldizajn
3 notes
·
View notes
Photo

A Guide to the Latest Google Update - GA4
Loss of Historical Data - Starting in July 2023, Google will stop collecting data (October 1 for 360 users). Google Analytics 4 can monitor more than just pageviews (without editing the website code). You must manually export historical data (data from before GA4 adoption) if you want to keep it; otherwise, you may lose it.
The availability of entirely new logic for data collection is one of Google Analytics 4's (hereinafter referred to as GA4's) most important changes. In UA, data is collected based on page views, whereas in GA4, data is collected based on events, giving you a better understanding of how consumers interact with your company's website or app ( if appropriate).
GA4 is not simply a redesign of Universal Analytics (UA); it is a completely new product that can be installed in addition to your existing UA profile. That said, if you're setting up GA for the first time, GA4 is the "latest version" that replaced UA as the default analytics platform in October 2020. UA can still be installed, but GA4 should be considered an upgrade to Google Analytics. If you want to know more about this update and make a lead for your website then it is best to get overall knowledge from Best Digital Marketing Company.
Previously, Analytics was split between web properties (traditional Google Analytics) and Analytics for Firebase (to specifically meet the needs of apps). Perhaps most importantly, Google Analytics 4 seeks to provide owners with flexible yet powerful analytics tools within the confines of cookieless tracking and consent management.
Let's take a closer look at the most important updates so that you get a better idea of the potential of this tool to help you grow your business.
Why is Google implementing GA4?
The primary intent behind the change is to bring together website and mobile app data usage measurement in one platform for unified reporting when creating a new property. This coincides with a greater effort to track the entire user journey, rather than segmenting user interaction across platforms, users, or sessions.
How can I get started with GA4?
If you currently use a Universal Analytics account, the update will be available from July 4, 2022. This means that the new property will be created and accessible through your Universal Analytics account, but your existing account will not it will be affected until July 1, 2023, which means that data will also flow through this account. Similarly, Firebase Analytics accounts (used for appli
Do you use Google Analytics 4?
Improved measurement. Google Analytics 4 can monitor more than just pageviews (without editing the website code). Things like outbound link clicks, scrolling, Youtube video, and other interactions can be automatically tracked
Explorations - Google Analytics 4 introduced several additional reports/tools for analysis, such as routes and ad-hoc funnels. Previously, these features were only available to GA360 users.
Integrations - I've already mentioned the BigQuery integration. However, there are still some integrations missing in Google Analytics 4, such as Search Console.
Mobile App Event Tracking - With Google Analytics 4, you can now track mobile events on the same property as your website.
This allows you to have a deep understanding of how customers use each property and spend your resources accordingly.
Want to get more familiar with the new GA4, its dash, and all the available options? Then the time has come for the “change”! Contact Digital Marketing Company in Pune today and our experienced team will help you with everything you need to know about your upgrade and all the information you need to know.
Improved Customer Journey - With GA4, you can track your customer journey from numerous devices within a single platform, giving you a clear view of how your prospect is interacting with your business, and therefore you can allocate your marketing budget more efficiently. specific.
Cross-Platform Monitoring - An integrated monitoring and reporting capability is provided using a single user ID across all platforms and devices. You'll save time, money, resources, and frustration by not having to patch the user journey across platforms or devices.
#Best Digital Marketing Company#Digital Marketing Company#Digital Marketing Services#Digital Marketing Company In India
5 notes
·
View notes
Text
How to Set Up SMS Marketing on Shopify Step-by-Step Guide

Why Use SMS Marketing for Shopify?
Before diving into the setup process, let’s understand why SMS marketing is a game-changer for your Shopify store:
High Open Rates: SMS messages have an open rate of 98%, significantly higher than emails.
Immediate Delivery: Messages are delivered instantly, making it perfect for time-sensitive promotions.
Direct Communication: Reach your customers directly on their mobile phones, ensuring your message is seen.

how to set up sms marketing on shopify
1. Choose an SMS Marketing App
The first step in how to set up SMS marketing on Shopify is to select an appropriate SMS marketing app. Shopify offers several apps that can help you manage your SMS campaigns effectively. Some popular choices include:
Klaviyo: Known for its robust features and integration capabilities.
SMSBump: Specifically designed for SMS marketing, offering automation and segmentation.
Postscript: A user-friendly app with powerful targeting and analytics.
Install the app of your choice from the Shopify App Store.
2. Install and Configure the App
Once you’ve selected an app, follow these steps:
Install the App: Click on the ‘Add app’ button in the Shopify App Store and follow the prompts to install.
Connect Your Store: After installation, you’ll need to connect the app to your Shopify store by following the app’s setup instructions.
Configure Settings: Set up your sender ID, which is the name or number that will appear on your recipients’ phones. Configure other settings like compliance and message templates as per your business requirements.
3. Build Your Subscriber List
To effectively use SMS marketing, you need a list of subscribers who have opted in to receive messages. Here’s how to build your list:
Add Sign-Up Forms: Use pop-ups, landing pages, and checkout opt-in options to collect phone numbers.
Promote Opt-In Offers: Encourage customers to subscribe by offering incentives like discounts or exclusive content.
Ensure Compliance: Make sure you comply with regulations like the TCPA (Telephone Consumer Protection Act) by obtaining explicit consent from your subscribers.
4. Create Your SMS Campaigns
Now that your app is set up and you have a subscriber list, it’s time to create your SMS campaigns:
Define Your Goals: Determine what you want to achieve with your campaign—be it driving sales, promoting new arrivals, or re-engaging inactive customers.
Craft Your Message: Keep it short, relevant, and action-oriented. Include a clear call-to-action (CTA) such as “Shop Now” or “Claim Your Discount.”
Schedule Your Messages: Choose the best times to send your messages. Avoid sending messages too early or late in the day.
5. Automate Your Campaigns
Automation is key to effective SMS marketing. Here’s how to automate your SMS campaigns on Shopify:
Set Up Triggers: Use triggers based on customer behavior, such as abandoned cart reminders, order confirmations, and shipping updates.
Segment Your Audience: Divide your subscribers into segments based on their purchase history, location, and engagement levels for more personalized messaging.
Test and Optimize: Continuously test different messages, send times, and strategies to see what works best. Use the app’s analytics to track performance and make data-driven decisions.
Best Practices for SMS Marketing on Shopify

Personalize Messages: Use your subscribers’ names and tailor messages based on their preferences and past behaviors.
Be Compliant: Always provide an opt-out option in every message to comply with legal requirements.
Limit Frequency: Avoid bombarding your customers with too many messages. Stick to a reasonable frequency to keep your audience engaged without feeling overwhelmed.
Measure Results: Regularly review your campaign performance metrics, such as open rates, click-through rates, and conversion rates, to refine your strategy.
how to set up sms marketing on shopify is a powerful way to enhance customer engagement and drive sales. By following these steps, you can create effective SMS campaigns that reach your audience directly and yield impressive results. Remember, the key to successful SMS marketing is personalization, compliance, and continuous optimization.
For more tips and insights on optimizing your Shopify store, subscribe to our blog and stay ahead in the e-commerce game! need expert Contact us
0 notes
Text
Ensuring Security and Compliance in Transactional SMS

Transactional SMS refers to messages sent to customers to convey important information related to their transactions or interactions with a business. These messages are triggered by specific actions taken by the customer or events related to their account, such as order confirmations, shipping updates, appointment reminders, payment confirmations, and account alerts.
Unlike promotional SMS, which aims to market products or services, transactional SMS focuses on delivering critical updates and notifications in a timely manner. Get this service from a reliable transactional SMS service provider.
How Does Transactional SMS Work?
Transactional SMS operates through a secure and automated system that integrates with a business's existing platforms, such as CRM (Customer Relationship Management) or e-commerce systems. When a customer initiates a transaction or performs an action that triggers a predefined event, such as making a purchase or scheduling an appointment, the system automatically generates and sends a relevant SMS to the customer's mobile number. This automation ensures that customers receive important updates and notifications without delay, thereby improving overall communication efficiency.
Enhancing Security and Compliance
1. Implement Encryption
To protect sensitive information transmitted via transactional SMS, businesses should implement encryption protocols to encrypt data both in transit and at rest. This ensures that even if intercepted, customer data remains secure and confidential.
2. Secure Network Infrastructure
Maintaining a secure network infrastructure is essential for preventing unauthorized access to customer data. Businesses should regularly update and patch their systems, use firewalls and intrusion detection systems, and restrict access to sensitive information to authorized personnel only.
3. Data Minimization
To reduce the risk of data breaches, businesses should practice data minimization by only collecting and retaining the information necessary for transactional SMS purposes. This reduces the amount of sensitive data stored, minimizing the potential impact of a security incident.
4. Consent Management
Obtaining explicit consent from customers before sending transactional SMS is not only good practice but also a legal requirement in many jurisdictions. Businesses should implement robust consent management processes to ensure compliance with regulations such as the General Data Protection Regulation (GDPR) and the Telephone Consumer Protection Act (TCPA).
5. Regular Audits and Assessments
Regular audits and assessments of security and compliance practices are essential for identifying vulnerabilities and areas for improvement. Businesses should conduct internal audits and engage third-party auditors to assess their transactional SMS processes and ensure alignment with industry best practices and regulatory requirements.
Conclusion
Ensuring the security and compliance of transactional SMS is crucial for protecting customer data and maintaining trust and confidence in your brand.
SpaceEdge Technology - Your Trusted Transactional SMS Service Provider
SpaceEdge Technology harness the power of cutting-edge communication technology to propel your business forward. As a leading provider of transactional SMS services, we are dedicated to helping businesses connect with their customers in a fast, reliable, and secure manner.
0 notes
Text
Streamlining the Afghanistan Drug Registration: A Comprehensive Guide for Approval and Compliance

MoH: Ministry of Public Health
MoH website: https://moph.gov.af/en
Regulatory Authority: Afghanistan Food and Drug Authority National Medicine and Health Products Regulatory Authority (NMHRA)
Link for Regulatory Authority: https://afda.gov.af/index.php/en/market-0
Afghanistan Drug Registration Procedure
Pre-Market Afghanistan Drug Registration Procedure
In the ever-changing healthcare landscape of Afghanistan, it is critical to effectively regulate medical goods and services. This paper explores the complex pre-marketing processes, including planning and policy, licensing, marketing permits, supply, price, and the vital oversight and management of clinical trials.
1. Policy & Plan
Planning and Coordination is the first step towards a strong regulatory system. The Ministry of Public Health in Afghanistan assumes a leading role in coordinating the efforts of many parties participating in the pre-marketing phase. Manufacturers, scientists, medical experts, and governmental organizations fall under this category. The foundation for efficient cooperation and communication is laid by strategic planning.
The success of pre-marketing operations depends heavily on clear and efficient communication. It is necessary to keep stakeholders updated on guidelines, regulations, and policy changes. Clear and frequent communication channels are set up to provide manufacturers, distributors, and other pertinent parties with information.
Information is a key component of regulatory decision-making, according to information management and evaluation (M&E). Strong data management systems make sure that data is gathered, examined, and assessed about clinical trials, healthcare goods, and market dynamics. Mechanisms for routine monitoring and assessment are in place to determine where improvements might be made and to gauge the success of current policies.
The foundation of healthcare regulation is the drafting and revision of legislative documents. Lawmakers in Afghanistan create and amend laws on a regular basis to meet changing needs and conform to global norms. Carefully constructed legislative documents handle licensing, permits, cost, and clinical study regulation.
2. Licensing
This essential pre-marketing step makes sure that only safe and efficient medical supplies reach consumers. A rigorous vetting process is required of businesses looking to sell their goods in Afghanistan. Complete information provided during the licensing application is used by the regulatory body to evaluate the product’s quality, safety, and efficacy.
3. Permission to Price and Supply the Market (Valuation)
Supply Chain Oversight: Businesses need permits to sell their goods to keep a safe and effective supply chain. By ensuring that products are supplied and distributed in accordance with regulatory criteria, this reduces the possibility that inferior or counterfeit goods may enter the market.
Pricing and Valuation: Accessible healthcare is facilitated by the establishment of reasonable pricing structures and the appraisal of healthcare items. To establish fair prices, regulatory agencies collaborate with manufacturers, considering aspects including quality, production costs, and market conditions. The goal of this procedure is to achieve a balance between sustainability and affordability.
4. Control and Regulation of Clinical Research
Clinical research is essential to expanding our understanding of medicine and guaranteeing the security and effectiveness of medical treatments.
To safeguard participants and maintain ethical standards, clinical research are tightly regulated and controlled by Afghan regulatory organizations. This method includes constant monitoring, informed consent processes, and a close examination of study protocols.
Post-Market Afghanistan Drug Registration Procedure
Beyond the original drug registration procedure, there is a continuous commitment to ensuring the safety, efficacy, and quality of pharmaceuticals.
1. Examining and Implementing Laws and Rules
Supervisory Authority: Afghanistan passionately believes that post-market inspections are essential to upholding pharmaceutical standards. To make sure that manufacturing sites, distribution networks, and retail locations are adhering to laws and regulations, regulatory bodies regularly audit them. The goal of this thorough inspection is to find and address any deviations from accepted norms.
Cooperation with Stakeholders: Afghan regulatory agencies work closely with pharmaceutical companies, medical practitioners, and other stakeholders to improve post-market surveillance. This cooperative strategy encourages a shared accountability for maintaining pharmaceutical standards, with continual education and communication to address issues and encourage adherence.
2. Pharmacovigilance, or Market Surveillance
Pharmacovigilance Framework: An essential part of Afghanistan’s post-market processes is market surveillance via pharmacovigilance. Data on the safety of pharmaceutical products are systematically collected, analysed, and interpreted as part of the pharmacovigilance framework. This continuous procedure aids in identifying and evaluating side effects or any other issues relating to drugs.
Adverse Event Reporting: It is crucial for patients, healthcare providers, and pharmaceutical companies to report adverse occurrences connected to their products. There is a strong reporting mechanism in place that makes it possible to promptly submit data on unanticipated side effects or other safety issues. To decide what steps to take next, regulatory bodies thoroughly look at these reports.
Risk management and signal detection: One aspect of pharmacovigilance work is the ongoing observation of signals that can point to safety issues. Regulatory agencies strive to identify new dangers and proactively address them. This could entail changing the product’s label, releasing safety alerts, or, in the worst situations, taking the medication off the market.
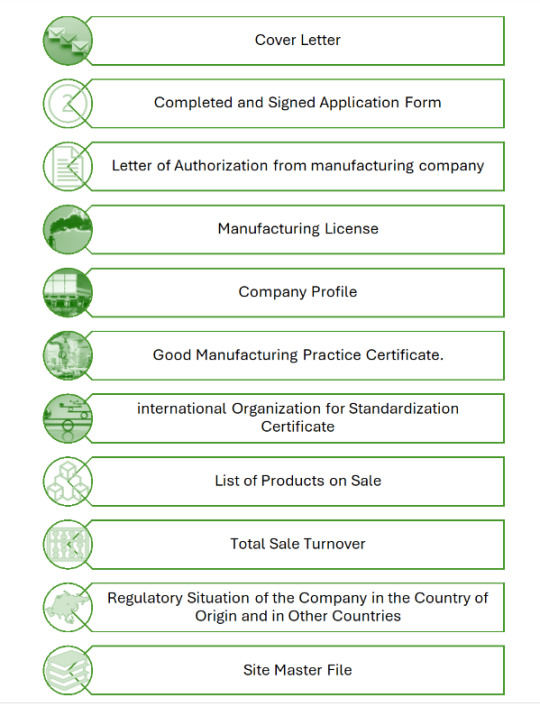
Documents Required for Product Registration in Afghanistan
1. Official introduction-letter and addresses of the company issued by the company itself.
2. License of producing medicine and medical equipment and certification of three authorized organizations of the origin country and that of WHO.
3. Special license for producing specific items from MoPH and certifications from high authorities of the origin country and that of WHO.
4. License of exportation.
5. Documents for the usage of the products inside the origin country.
6. Quality control documents of the company and also quality control documents from the central laboratory and ministry of MoPH of the origin country.
7. Specific documents of the medicine such as: list of formulation including standard formulation of the medicine, list of prices including reasonable prices, packing list with the specification about packing material, and method of packing. Procedure for controlling the production process, specification of its contents, documents of analysis, method of analysis, reliability of the method of analysis certification of the contents and pharmacological report of the medicine.
8. Original stamp of the company on the relevant documents.
9. Certification of the ministry of MoPH and stamp of chambers of commerce of the origin country and issuance of them through trading department of the embassy of Afghanistan located on the producing country.
10. Analysis the sample of the medicine in the general medicine analyzing laboratories of Afghanistan and registering the mentioned products.
Registration Requirements for Product Registration in Afghanistan
Fees for Afghanistan Drug Registration
AFN (50,000)
License Validity for Afghanistan Drug Registration
3 years.
Local Authorized Representative
Yes, a local Authorized Representative is required before you place your product on the market.
Originally Published at: https://omcmedical.com/afghanistan-drug-registration-procedure/
0 notes
Text
Enhancing Data Privacy: The Introduction of GDPR Certification

The introduction of (General Data Protection Regulation) GDPR Certification in Cameroon is a significant development aimed at enhancing data protection standards in the country. This initiative aligns with global trends in data privacy and security, offering a structured approach for organizations to demonstrate compliance with data protection laws.
Context and Importance
Global Data Protection Trends:
The GDPR, enacted by the European Union in 2018, set a high standard for data protection worldwide. Its influence extends beyond Europe, encouraging other regions to adopt similar regulations.
Organizations worldwide seek GDPR certification to assure customers and partners of their commitment to data privacy.
Cameroon's Data Protection Landscape:
Cameroon is increasingly recognizing the importance of robust data protection mechanisms to foster trust in digital services and enhance international business relations.
Introducing GDPR certification in Cameroon helps local businesses align with international standards, improving their competitiveness.
Implementation and Benefits
Certification Process:
The GDPR certification in Iran process involves a comprehensive assessment of an organization’s data protection practices.
Organizations need to demonstrate adherence to principles such as data minimization, user consent, data accuracy, and security measures.
Independent certification bodies conduct audits to verify compliance.
Benefits for Organizations:
Enhanced Trust: Certification signals to customers and partners that the organization prioritizes data privacy, enhancing its reputation.
Market Access: Certified organizations can more easily engage in international trade, especially with European partners.
Compliance and Risk Management: Certification helps organizations stay compliant with both local and international data protection laws, reducing the risk of legal penalties.
Economic and Social Impact:
Economic Growth: By fostering a data-protection-compliant environment, Cameroon can attract more foreign investment, particularly from Europe.
Consumer Confidence: Increased data protection measures boost consumer confidence in digital services, promoting greater adoption of technology.
Innovation and Development: A robust data protection framework encourages innovation, as businesses can safely develop and deploy new digital services.
Challenges and Considerations
Awareness and Training:
Raising awareness about the importance and benefits of GDPR certification in Chennai among businesses and public institutions is crucial.
Providing adequate training and resources to help organizations achieve and maintain certification.
Regulatory Support:
The Cameroonian government and regulatory bodies need to support the certification process through clear guidelines, frameworks, and incentives.
Harmonizing local data protection laws with international standards to facilitate the certification process.
Technical and Financial Barriers:
Smaller businesses may face challenges due to the technical and financial resources required for certification.
Developing support mechanisms, such as subsidies or technical assistance, to help smaller enterprises achieve compliance.
How does one get GDPR certification in Cameroon?
To discover more about GDPR certification in Cameroon, including advice and services, please go to www.b2bcert.com or email contact@b2bcert. We use value addition to assess demand and establish the most reliable and cost-effective means of achieving GDPR certification in Cameroon.
0 notes
Text
Latest Data Privacy Statistics Reveal Growing Consumer Concerns
Consumer trust in data privacy has reached a crisis point. Recent statistics expose rising apprehension about how businesses handle personal information. They highlight risks from breaches and opaque practices. People want more control. Laws are evolving. Expectations are soaring. There is an urgent need for openness and accountability.
Key Data Privacy Concerns
- 63% believe companies lack transparency on data use. 55% think they intentionally hide details.
- 91% say they've lost control over how firms collect and use their data. 89% worry about the volume gathered without consent.
- Just 36% trust social media companies to ethically leverage their data. 73% fret over how much these platforms amass.
- 62% feel uneasy about how AI taps their personal information.Source: (GOV.UK): Cyber security breaches survey 2023" (Department for Science, Innovation & Technology, 2023).
Doubts stretch across sectors. People sense that business fails to respect privacy. They perceive a lack of choice in data sharing.
Costs and Risks of Poor Data Privacy
- According to Cyber Security Hub, over 4,100 publicly disclosed data breaches occurred in 2022, exposing approximately 22 billion records. This figure is expected to increase by as much as five percent when final figures are released.
- 60% of small firms close within 6 months post-breach due to associated costs and lost revenue.
- Large companies see stock prices drop 5% on average within a week of disclosing a breach.
- 78% of consumers completely avoid a business for months if it suffers a breach. Rebuilding trust requires substantial effort.
- Fines under GDPR, CCPA and upcoming laws can reach millions based on violation severity. Lawsuits present further liability.Source: (Cyber Security Hub): The biggest data breaches and leaks of 2022" (Olivia Powell, 2022).
Remote work makes things worse. With employees accessing data remotely, breaches rose nearly 30% in 2020. Maintaining security is challenging.
Consumer Desire for More Protection
- 92% of US adults want federal laws granting more control over data sharing, like GDPR and CCPA.
- 67% would likely vote for candidates prioritizing privacy. It now sways voting choices.
- 81% have actively boosted privacy in the past year using VPNs, private browsers, password managers, and anti-tracking tools.
- 57% will pay more for brands providing excellent transparency and security. Ethics give a competitive edge.Source: (Boston University): "Data Protection Law: The GDPR, CCPA, and U.S. FederalRegulation" (Kellen Safreed, 2021).
People want greater accountability. They are taking steps to safeguard data. Privacy influences purchasing and votes.
Role of Businesses in Building Trust
To earn trust, companies must:- Enhance Transparency: Explain data practices clearly. Simplify policies and opt-outs.
- Strengthen Security: Invest in encryption, controls, training, audits. Assess risks frequently.
- Commit to Ethical AI: Ensure unbiased data. Explain AI's impact on consumers.
- Honor Privacy Choices: Give granular data sharing controls. Allow easy opt-outs. Never sell or share data without explicit consent.
The Path Forward
With privacy concerns soaring, openness and choice are essential. While securing data and ensuring compliance takes effort, ethical practices also confer competitive advantage by fostering consumer confidence. Companies embracing privacy can still benefit from data-driven insights. In the end, preserving dignity in the digital age means making privacy a priority.
Final Thoughts
Statistics reveal rising data privacy doubts. Breaches and opaque practices erode trust. People want transparency and control. Laws are evolving, expectations are climbing. Businesses must recommit to accountability and ethics. Those respecting rights while delivering value will thrive. Ultimately, ensuring privacy secures consumer trust and loyalty.
Read the full article
0 notes
Text
Data Privacy in the Age of Surveillance - Challenges and Solutions
As we continue to rely more and more on digital technologies, data privacy has become a global concern. Governments around the world struggle to balance national security and public safety objectives with individuals’ right to privacy. The increasing use of facial recognition, smart doorbells, and other technologies that can track people’s movements can have significant civil rights implications for individuals, especially those from marginalized groups. In addition, many tech companies collaborate with law enforcement agencies to share data that can be used for surveillance purposes. This raises serious questions about transparency and the extent to which privacy policies are enforced.

The ubiquity of digital technology and the growing power of BigTech companies have created pervasive risks for privacy. These risks include invasive surveillance, which can erode individual autonomy and exacerbate power Who are techogle? imbalances, and data breaches, which expose personal information to hackers and put individuals at risk of harm. These concerns are exacerbated by the ability of governments and companies to collect a massive amount of data and have an unprecedented level of control over how that data is collected, analysed and used.
Data privacy in the age of surveillance is a complex issue, but there are ways for individuals to protect their rights. The first step is to stay informed and be proactive about their data use. This can be done by educating themselves on how their personal data is collected and shared, as well as examining the effects of a breach on their own lives. It is also important to support policymakers who prioritize data protection.
Secondly, technology companies can take steps to improve their transparency and accountability by providing clearer privacy policies and empowering consumers with tools to manage their data. They can also work with law enforcement agencies to establish data sharing guidelines that balance the need for security with the need for privacy.
Finally, privacy policies should be updated to reflect the current state of technology and society. This should include a focus on the protection of human rights and the balancing of interests such as business, research, and innovation against an individual’s right to privacy. This can be achieved by developing a model of data processing that takes into account the benefits of large data sets, the necessity for individual consent, and the need to consider alternative solutions when data is shared for surveillance purposes.
As technology advances technology news and the surveillance state becomes more omnipresent, it is critical to promote awareness of privacy issues, encourage citizens to be active participants in protecting their rights, and champion for policies that protect our fundamental right to privacy. Otherwise, we will continue to lose our right to privacy and be left vulnerable to the harmful effects of unregulated data collection.
1 note
·
View note
Text
Redefining Fresh: Farm-to-Door Delivery for the Modern Consumer
The online grocery delivery app development market is experiencing explosive growth, driven by a surge in consumer demand for convenience and time-saving solutions. According to a report by Food Runner, online grocery sales are projected to reach a staggering 20% of the total grocery market in the US by 2025.
However, within this dynamic environment, online grocery delivery services face a constant battle for market share. Here, we explore key strategies that can empower these services to thrive in the competitive landscape.
Understanding the Shifting Consumer Landscape
The success of any online grocery delivery service hinges on a deep understanding of evolving consumer preferences. Here are some key trends to consider:
Time-Constrained Consumers: Busy schedules and a growing preference for convenience are driving the demand for online grocery delivery services. Busy professionals and families often seek solutions that free up valuable time.
Tech-Savvy Users: Consumers are increasingly comfortable with online platforms and mobile apps. Grocery delivery services need to offer seamless user experiences through user-friendly interfaces and intuitive functionalities.
Focus on Freshness and Quality: While convenience is paramount, consumers remain concerned about product quality and freshness. Partnering with reliable grocery stores and ensuring efficient cold chain logistics is crucial.
Building a Winning Strategy: Optimizing Operations for Effectiveness
1. Partnering for Success: Building a Strong Ecosystem
Collaborating with Grocery Stores: Partnering with established grocery stores offers several advantages. Access to a wider product selection, efficient inventory management, and brand recognition can significantly enhance the service's value proposition.
Delivery Network Optimization: A reliable and efficient delivery network is fundamental. Consider partnering with established delivery companies or developing an in-house fleet to ensure timely and accurate deliveries.
2. User-Centric Approach: Tailoring Experiences for Customer Success
Seamless User Interface: Invest in developing a user-friendly and intuitive mobile app or website. Users should be able to browse products easily, add items to carts, schedule deliveries, and track orders effortlessly.
Personalized Recommendations: Leverage user data (with proper consent) to personalize the shopping experience. Recommend frequently purchased items and highlight special offers on preferred brands to foster user engagement and loyalty.
Flexible Delivery Options: Cater to diverse customer needs by offering a range of delivery options, including same-day, next-day, and scheduled deliveries. Additionally, consider offering contactless delivery or pick-up options for added convenience.
3. Building Trust and Value: Cultivating Long-Term Customer Relationships
Competitive Pricing Transparency: Offer competitive pricing structures with transparent fee breakdowns. Implement targeted promotions and loyalty programs to incentivize repeat business and generate positive word-of-mouth marketing.
Commitment to Quality Assurance: Partner with reliable grocery stores and implement robust quality control measures throughout the supply chain. Ensure delivery drivers handle products with care to maintain freshness and prevent damage.
Responsive Customer Service: A responsive and helpful customer service team is essential for building trust and addressing any user concerns effectively. Offer multiple communication channels, such as live chat, email, and phone support, to ensure accessibility.
Exploring Growth Opportunities: Expanding Reach and Offerings
1. Leveraging Technology: Automating Processes and Streamlining Operations
While-label grocery delivery app solutions can provide a cost-effective and efficient foundation for building your online service. These solutions offer pre-built functionalities that can be customized to reflect your brand identity.
Implementing data analytics tools can provide valuable insights into user behavior, identify areas for improvement, and optimize overall service effectiveness.
2. Expanding Service Scope: Catering to Diverse Needs
Subscription Boxes: Consider offering curated grocery box subscriptions that cater to specific dietary needs or preferences. This can attract new customer segments and create recurring revenue streams.
Local Business Partnerships: Partner with local businesses like butcher shops, bakeries, or farm-to-table producers. This allows you to offer unique product selections and support local businesses within the community.
Conclusion: A Sustainable Future for Online Grocery Delivery
By implementing these strategies and adapting to the evolving consumer landscape, online grocery delivery services can carve a niche for themselves in a competitive market. Focusing on building strong partnerships, delivering exceptional customer service, and embracing technological advancements are key ingredients for success. The future of online grocery delivery is bright, offering exciting opportunities for services that prioritize convenience, quality, and a commitment to building long-term customer relationships.
0 notes
Text
Regulatory Compliance and LLMs: Impact of GDPR, CCPA, and Privacy Laws on LLM Training
The integration of Large Language Models (LLMs) into business operations has brought about significant advancements in Generative AI capabilities, offering enhanced customer experiences and streamlined processes. However, the landscape of data privacy regulations, including the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and other privacy laws, poses new challenges for organizations leveraging LLMs. This article delves into the impact of GDPR, CCPA, and other privacy laws on LLM training, highlighting key considerations for regulatory compliance and data protection.
GDPR Compliance and LLM Training
The GDPR, a comprehensive data protection regulation in the European Union, sets stringent requirements for the collection, processing, and storage of personal data. When it comes to LLM training, organizations must adhere to the following key aspects of GDPR compliance:
Data Collection and Storage: LLM implementations must respect consumers' rights to access, delete, and opt-out of the sale or sharing of their personal data. Organizations using LLMs need mechanisms to honor these rights and ensure transparency in data collection practices.
Consent Management: Explicit consent is a fundamental principle of the GDPR. Before processing any EU citizen's data, organizations must obtain clear and informed consent, especially when using LLMs that collect and process personal information.
Data Portability and Accessibility: GDPR grants users the right to receive their data in a machine-readable format. Organizations leveraging LLMs should ensure that data collected can be easily exported and that users have access to their information upon request.
Data Retention: GDPR mandates that data should be retained only for as long as necessary for its intended purpose. Organizations using LLMs must establish data retention policies to ensure compliance with GDPR requirements.
Data Protection and Security: GDPR emphasizes the importance of safeguarding user data through robust security measures. Organizations employing LLMs should implement encryption, regular vulnerability assessments, and other security protocols to protect personal information.
CCPA Compliance and LLM Training
The California Consumer Privacy Act (CCPA) imposes strict regulations on the collection and processing of personal data, particularly in the context of AI technologies like LLMs. Key considerations for CCPA compliance in LLM training include:
Consumer Rights: CCPA grants consumers rights to access, delete, and opt-out of the sale of their personal information. Organizations using LLMs must ensure that mechanisms are in place to honor these rights and provide transparency in data handling practices.
Sensitive Data Handling: CCPA places emphasis on the protection of sensitive data categories. Organizations leveraging LLMs must seek explicit consent before collecting or processing sensitive data and ensure compliance with CCPA requirements.
Training and Awareness: CCPA mandates that businesses educate their employees on consumer inquiries and privacy practices outlined in the act. Training employees to handle consumer requests and comply with CCPA regulations is essential for regulatory compliance.
Other Privacy Laws and LLM Training
In addition to GDPR and CCPA, other privacy laws such as the Brazil LGPD and Canada's PIPEDA also impact LLM training practices. Organizations operating in regions covered by these laws must consider the following aspects:
1. Employee Training: Privacy laws like LGPD and PIPEDA emphasize the importance of employee training on data protection practices. Organizations must educate their employees on privacy regulations, data handling procedures, and the importance of safeguarding personal information when using LLMs.
2. Data Safeguarding: Compliance with privacy laws requires organizations to implement policies and practices that safeguard personal data. Training employees to maintain confidentiality, communicate privacy policies, and implement data protection measures is essential for regulatory compliance.
An important tools that can help you understand your data
--> yData-profiling: An Intuitive EDA and PII Insights tool created by yData
Comprehensive EDA: The tool generates a detailed report, covering various aspects of the dataset, such as variable distributions, correlations, and missing values.
PII Classification and Management: yData-profiling includes a dedicated section for PII classification and management, allowing users to quickly identify and categorize sensitive information within their data.
Intuitive Visualization: The web-based dashboard presents the insights in a user-friendly and interactive manner, making it easy for users to understand and interpret the data.
Conclusion
Navigating the complex landscape of data privacy regulations, including GDPR, CCPA, and other privacy laws, is essential for organizations leveraging Large Language Models in their operations. By ensuring compliance with regulatory requirements, implementing robust data protection measures, and prioritizing employee training on privacy practices, organizations can harness the power of LLMs while safeguarding individuals' privacy rights. Proactive measures, transparency in data handling, and a commitment to regulatory compliance are key to fostering trust, ensuring data protection, and mitigating risks associated with LLM training.
References - Some Important resources.
https://secureprivacy.ai/blog/employee-training-for-gdpr-compliance
https://www.linkedin.com/pulse/llms-data-privacy-navigating-ccpa-gdpr-cpa-cisos-deepa
https://www.webanywhere.com/data-protection-compliance/
https://www.dsci.in/files/content/knowledge-centre/2023/Exploratory%20note%20June%202023.pdf
https://github.com/ydataai/ydata-profiling
1 note
·
View note
Text
Beyond Traditional Finance: Innovative Open Banking Applications in FinTech

In today’s digital landscape, open banking is revolutionizing the way data is shared, making it simpler to switch bank accounts and tearing down the barriers between financial institutions. Despite these advancements, FinTech companies still face significant challenges from traditional banking systems, which can hinder their growth.
This article delves into these challenges and underscores the transformative potential of open banking in the FinTech sector.
Traditional Finance Challenges for FinTech
Traditional financial institutions have long held a dominant market position, setting standards and shaping industry practices. However, as technology disrupts sectors worldwide, FinTech startups are emerging as formidable challengers, pushing the limits of innovation and questioning established norms.
Limitations of Traditional Data Sources
Traditional data sources often consist of structured data from internal banking systems, credit bureaus, and regulatory filings. While this data provides valuable insights into historical financial transactions, business lending, and creditworthiness, it often lacks depth and breadth. FinTech companies require a broader spectrum of data to develop innovative solutions that cater to evolving consumer needs and preferences.
Challenges with Real-Time Data and Non-Financial Insights
Traditional data sources typically do not offer real-time insights into consumer behavior and market trends, which are crucial for FinTech companies operating in dynamic environments. Additionally, traditional data often overlooks non-financial factors that influence financial decisions, such as social media activity, lifestyle choices, and demographic details. Access to a wider array of data is essential for FinTechs aiming to deliver personalized financial solutions.
Core Principles of Open Banking
Open banking has redefined the financial landscape by enabling secure data sharing among banks, non-banking financial entities, and third-party service providers. Here are its core principles:
Real-time Data Sharing: Secure access to financial data, such as transaction history and account balances, is provided in real-time with user consent.
Openness through APIs: Application Programming Interfaces (APIs) facilitate secure, standardized access to financial data for third-party providers.
Customer Control: Users manage who can access their data and can revoke permissions at any time.
Open Banking vs. Banking-as-a-Service (BaaS)
While both models utilize technology to enhance financial services, open banking focuses on data sharing, whereas BaaS provides access to banking functionalities.
Empowering FinTech through Open Banking
Open banking is catalyzing innovation within the financial sector, enabling FinTech companies to overhaul traditional services and create new possibilities for personalized financial products and streamlined processes. Notable use cases include:
Enhanced Customer Onboarding and KYC: Open banking simplifies KYC procedures by allowing FinTechs to access user data with consent.
Personalized Financial Products: Real-time financial data through open banking APIs enables FinTechs to tailor products and services to individual needs.
Streamlined Loan and Credit Scoring: Access to comprehensive financial data speeds up loan approvals and enhances credit assessments.
Automated Wealth Management: Open banking facilitates the development of automated investment tools that leverage real-time data to optimize portfolio performance.
Open Finance Ecosystem
Open banking fosters collaboration between traditional financial institutions and FinTechs, creating an ecosystem that supports innovative services through integration with existing financial infrastructure.
Implementing Open Banking with Sprinterra
For FinTechs looking to harness open banking, Sprinterra offers a powerful platform that simplifies integration and accelerates development. Key benefits include:
Faster Time to Market: Pre-built APIs for open banking functionalities reduce development time.
Scalable Infrastructure: Capable of processing millions of transactions daily.
Hybrid Cloud Architecture: Combines public cloud scalability with secure, private data storage.
Enhanced Security: Prioritizes top-tier security measures for handling financial data.
Conclusion
Open banking is ushering in a new era of financial empowerment by enabling secure data sharing and promoting collaborative innovation, thereby transforming how we manage our finances and interact with financial institution.
0 notes
Text
does vpn results in speed hack
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn results in speed hack
VPN latency impact
VPN Latency Impact
VPN (Virtual Private Network) services are becoming increasingly popular for individuals and businesses seeking online security and privacy. However, one of the key factors that can affect the performance of a VPN is latency. Latency refers to the delay between a user action and the response from the VPN server.
The impact of latency on VPN performance can vary depending on various factors such as the distance between the user and the server, the server load, and the quality of the internet connection. High latency can result in slow loading times, buffering when streaming content, and overall sluggish performance.
When choosing a VPN service, it is essential to consider the impact of latency on your online activities. For activities that require real-time communication such as online gaming or video conferencing, high latency can be particularly problematic. Users may experience lags, delays, and poor audio/video quality when using a high-latency VPN.
To minimize the impact of latency, users can choose VPN servers that are geographically closer to their location, select servers with lower loads, or opt for VPN services that offer high-speed connections. Additionally, ensuring a stable and high-quality internet connection can help mitigate latency issues when using a VPN.
Overall, while VPN services offer numerous benefits in terms of online security and privacy, it is crucial to consider the potential impact of latency on performance. By selecting the right VPN service and optimizing server choices, users can enjoy a smoother and more responsive online experience while maintaining their privacy and security.
Bandwidth throttling effects
Bandwidth throttling, a practice employed by internet service providers (ISPs), has significant effects on users' online experiences. This technique involves deliberately limiting the speed or bandwidth of internet connections, often to manage network congestion or prioritize certain types of traffic. While ISPs argue that throttling is necessary for network management, it can have several negative consequences for consumers.
One of the most noticeable effects of bandwidth throttling is slower internet speeds. When ISPs throttle bandwidth, users may experience delays in loading web pages, buffering while streaming videos, and sluggish download speeds. This can be frustrating for individuals who rely on a fast and reliable internet connection for work, entertainment, or communication purposes.
Bandwidth throttling also impacts online activities that require consistent and uninterrupted connectivity, such as online gaming and video conferencing. High latency and packet loss resulting from throttling can lead to laggy gameplay, dropped calls, and overall poor performance in real-time applications.
Furthermore, bandwidth throttling can stifle innovation and competition online. By controlling the speed and access to certain content, ISPs can potentially favor their own services or partners, creating an unfair advantage over competitors. This practice goes against the principles of net neutrality, which advocate for equal treatment of all internet traffic.
Privacy concerns also arise with bandwidth throttling, as ISPs may inspect and manipulate data packets to enforce throttling policies. This raises questions about user privacy and data integrity, especially as ISPs may collect and analyze users' online activities without their consent.
In conclusion, bandwidth throttling can have far-reaching effects on internet users, ranging from slower speeds and degraded performance to concerns about privacy and net neutrality. As such, it is essential for regulators to closely monitor ISP practices and ensure that consumers are provided with fair and transparent internet services.
Network congestion mitigation
Network congestion mitigation refers to the strategies and techniques used to manage and alleviate congestion in computer networks, ensuring optimal performance and reliability. Congestion occurs when the demand for network resources exceeds the available capacity, leading to delays, packet loss, and degraded service quality.
One of the key approaches to mitigating network congestion is traffic shaping, which involves controlling the flow of data to ensure that it conforms to predetermined policies. By prioritizing certain types of traffic over others, network administrators can prevent congestion and maintain consistent performance for critical applications.
Quality of Service (QoS) mechanisms also play a crucial role in congestion mitigation by assigning different levels of priority to network traffic based on factors such as bandwidth requirements, latency sensitivity, and application type. By using QoS policies, network administrators can ensure that high-priority traffic receives preferential treatment during periods of congestion.
Another effective strategy for mitigating network congestion is the implementation of congestion control algorithms, such as TCP congestion control mechanisms. These algorithms help regulate the rate at which data is transmitted across the network, preventing individual senders from overwhelming network resources and causing congestion.
Furthermore, network capacity planning and optimization are essential for proactively addressing congestion issues. By regularly monitoring network traffic patterns, forecasting future capacity requirements, and upgrading network infrastructure as needed, organizations can prevent congestion before it becomes a significant problem.
In conclusion, network congestion mitigation requires a combination of proactive planning, intelligent traffic management, and the use of congestion control mechanisms. By implementing these strategies effectively, organizations can ensure smooth and efficient network operations, even during periods of high demand.
Speed optimization techniques
Title: Boost Your Website's Performance with Speed Optimization Techniques
In today's fast-paced digital world, website speed plays a critical role in user experience and search engine rankings. Slow-loading websites not only frustrate visitors but also deter potential customers and harm conversion rates. Therefore, it's crucial for website owners to implement speed optimization techniques to ensure optimal performance. Here are some effective strategies to speed up your website:
Optimize Images: Large image files can significantly slow down a website. Compress images without compromising quality using tools like Photoshop or online services like TinyPNG or JPEG Optimizer.
Enable Browser Caching: Browser caching allows web pages to be stored in a user's browser, reducing the need to reload the entire page every time they visit. Implement caching directives in your website's htaccess file to leverage browser caching efficiently.
Minify CSS, JavaScript, and HTML: Minification involves removing unnecessary characters like comments, whitespace, and formatting from code files. Use tools like Minify and UglifyJS to shrink the size of CSS, JavaScript, and HTML files, thus reducing load times.
Utilize Content Delivery Networks (CDNs): CDNs distribute your website's static content across multiple servers worldwide, delivering it from the server closest to the user's location. This reduces latency and speeds up content delivery, especially for international visitors.
Optimize Server Response Time: Slow server response times can be a major bottleneck in website speed. Optimize server configurations, utilize caching mechanisms, and consider upgrading your hosting plan to a faster server or switching to a reliable hosting provider.
Implement Lazy Loading: Lazy loading delays the loading of non-essential resources, such as images or videos, until they are needed. This prioritizes the loading of critical content, improving initial page load times.
By implementing these speed optimization techniques, you can enhance your website's performance, provide a better user experience, and ultimately boost your online presence and conversion rates. Remember, in the digital realm, speed matters.
VPN encryption overhead
In the world of Virtual Private Networks (VPNs), encryption plays a vital role in ensuring the privacy and security of online communication. However, it also comes with a certain amount of overhead that users should be aware of. This overhead refers to the additional processing and time required to encrypt and decrypt data as it travels between devices through the VPN tunnel.
The level of encryption overhead largely depends on the type of encryption protocol used. For example, more advanced encryption algorithms like AES-256 require more computational power compared to less secure options like DES. As a result, using higher levels of encryption can slow down your internet connection due to the extra processing required.
Another factor that can contribute to VPN encryption overhead is the distance between the user and the VPN server. Data encryption and decryption processes add latency to the connection, and the further the data has to travel, the more pronounced this effect becomes. This is why choosing a VPN server closer to your physical location can help minimize encryption overhead and improve overall connection speeds.
While VPN encryption overhead can impact performance, it is a necessary trade-off for ensuring the confidentiality and integrity of your data. Users can mitigate the effects of encryption overhead by selecting encryption protocols wisely based on their needs and prioritizing servers with low latency for a smoother browsing experience. Ultimately, understanding and managing VPN encryption overhead is crucial for striking the right balance between security and performance in your online activities.
0 notes