#What’s New in C 10: New Possibilities for Validation and Logging Methods
Link
Just blogged: What’s New in C# 10: New Possibilities for Validation and Logging Methods https://ift.tt/3p37TGF
0 notes
Text
The backstory of the Electra jailbreak, and how it eventually turned into a nightmare
Back in December 2017, the async_wake exploit was released by Ian Beer for iOS 11.0 - 11.1.2. Shortly after, some other developers (ninjaprawn and stek29) got Dropbear and some basic tools running by using xerub’s trust-cache injection.
My iPad was sitting unused on 9.3.3 for a while, so I figured I’d update it and see what I could do on 11.1.2. I quickly replaced the bootstrap with some freshly compiled GNU core utilities. Meanwhile, ninjaprawn built an initial payload to inject into amfid to try getting arbitrary executables to load. I then (at the same time as, but independently from Morpheus) figured out we needed to add the platform-application entitlement for our fancy new amfid patch to work, and we were off to the paces.
However, we still couldn’t inject tweaks just yet. Our injector could inject dylibs into SpringBoard, however, library validation prevented our dylibs from working unless they were in trust cache. Furthermore, there were timing issues with the dylibs injecting too late. Something better needed to be done.
I began working on a “jailbreakd” that would take the kernel task port given by async_wake and hold onto it, so we could do modifications in the kernel as needed (by having jailbreakd receive commands over UDP from localhost). Starting off with injecting codesigning flags and injecting entitlements, I was quickly able to disable library validation, and was able to get dylibs loaded. However, we still needed a better solution. With some modifications to our injector, I was able to get injection into launchd working. However, the latest build of substrate (this was back in December 2017, but is still valid as of March 2018) failed to work and was giving vague assertion failures when our own injector was working fine.
I decided to reach out to saurik to see if he was interested in getting substrate working, as it would be a fairly trivial task at this point. However, he stated he was not interested at all. Having come this far (and with the stock icons on my iPad still looking ugly), I decided to start building my own solution. I built my own payloads for launchd and xpcproxy which would inject the necessary DYLD_INSERT_LIBRARIES environment variable and call jailbreakd to fixup entitlements and codesigning as needed.
However, we still needed a library for tweaks to hook method calls, as we couldn’t expect everyone to only rely on bundling fishhook or using the Objective-C runtime directly. With substrate closed source,non-functional and the developer uninterested, I looked out for alternatives and remembered comex’s substitute. Substitute is supported on iOS, however it had previously only been tested on iOS 8, and definitely not in mass-deployment. However, with some further patches to our injector to lower codesigning restrictions, surprisingly substitute worked on iOS 11.
With substitute working, I was able to get Anemone not just running, but almost fully functional on iOS 11. The entire stack was fairly new and in beta, but I decided it would be cool to share it so tweak developers could get tweaks working on iOS 11 while the stack was worked on simultaneously. Thus on January 12, 2018, I released Electra beta 1 - a toolkit that installed Dropbear, GNU coreutilities, Substitute, Tweak Injector (then known as SBInject), PreferenceLoader and Anemone. The beta was contained in /bootstrap to have the least issues and for easy cleanup and upgrade path.
Electra beta 1 (and the async_awake fork it was prior to that) were open source, so Electra received some notable contributions. Contributions were received for setting host special port 4, for loading our own launch daemons, for setting jailbreakd as a launchd service, and for mitigating sandbox restrictions.
All was working well and good, one would think.
However, we quickly ran into some issues. Remember that jailbreakd used UDP for receiving commands. However, UDP could potentially drop packets if too many messages were sent (especially since jailbreakd used NSLog() for debug logging, which could halt the thread and cause packets to drop even on localhost). This was most notable if we attempted to reload all launch daemons, which is necessary for tweaks to load into all processes.
A contribution was received to swap jailbreakd to XPC, in launchd, xpcproxy, and everywhere else. However, I noticed with the XPC changes my test devices froze after 30 minutes of usage. I suspected the issue was with our hack to get XPC working in launchd, so I switched launchd back to UDP. However, we were still left with the problem with packets being dropped. So I decided to implement TCP in launchd and let it use XPC everywhere else. This fixed the issue with packets being dropped as they were simply re-transmitted. However, launch daemons were still getting stuck when we were reloading all of them at once...
Until I realized it was NSLog() that was causing problems all along. With some patches to swap it for fprintf’s, the issue was alleviated and we could reload without any problems, and the freezing issue was gone from my own device, so I decided to release these updates as beta 11.
I ran some stress tests to check the stability of the jailbreak by reloading all launch daemons several times, and it was working perfectly, so I decided it was time we start making it the full jailbreak it could be. I started rebuilding all the dependencies needed to run Debian’s APT and dpkg from the latest upstream sources (from both GNU and Apple/BSD respectively), since the newer sources built fairly easily for iOS, so it made sense to use them rather than using the patches saurik used back on iOS 2.0. I was then provided some scripts by nitoTV to build APT and dpkg. After building a new bootstrap (which had to be extracted to the rootfs, couldn’t sandbox it anymore), I was able to get apt-get working!
With some patches to Cydia (binary patches mind you, since the main Cydia app was near impossible to build), I managed to get it working on iOS 11 with our versions of dpkg, APT, etc. I took a look at my iOS 10 device to see how the packages were set up, and setup the layout for Electra’s packages so that it would be an easy upgrade path, should saurik decide to support iOS 11 and provide updates for it (with possible interchanging of packages, should his also support iOS 11 -- this was tested on iOS 10 and does work). As none of saurik’s packages were updated since October 2017, I didn’t expect him to post any updates until he decided to start supporting iOS 11. So I marked Electra’s packages as the versions they really were (since most of the tools were quite possibly a decade newer than saurik’s [being built in 2018 rather than 2009]), and where we were using the same version as saurik’s tools, I incremented the version by 1 and added the “-coolstar” suffix (this was only for APT, uikittools and cydia).
I built Release Candidate builds and began submitting them privately to developers to test, as some wanted a more realistic setup with dpkg and APT to be able to test certain packages. However, with our setup not finalized yet, I didn’t want to make it public, since we could potentially make breaking changes with no upgrade path past one minor RC version (since keeping track of all changes from RC 1 to final release 1.0 could potentially be a huge burden if any major breaking changes were made, as we couldn’t simply wipe /bootstrap and place a new one in). Furthermore, with the SHSH window closed I didn’t want to potentially bootloop devices by overwriting files, so I used tar’s “-k” option to keep existing files.
The situation was already complicated by the fact that the device the jailbreak would be installed to might not have been on stock iOS to begin with (something all other jailbreaks assumed). For example, the “topanga” toolkit installed the iOS 10 bootstrap (which doesn’t work at all on iOS 11 due to usage of 32 bit binaries, which Apple dropped support for in 11). Furthermore, since we configured tar to not overwrite files already on the filesystem, if the filesystem wasn’t clean, our bootstrap could potentially not extract at all, resulting in a messy situation.
I decided to compromise by detecting these problematic files and indicating to the user that they installed “topanga” and needed to either uninstall it somehow or futurerestore their device to stock iOS 11.
However, one of the developers who was given the RC 1.2 build (initial testers only got RC 1.1 due to some delays with RC 1.2′s rollout) decided to leak it. Normally I wouldn’t care about a beta leak, however, with the SHSH window closed, this caused the already sticky situation with topanga to get even worse, as we had to deal with potential users already having the RC that should have been private, especially as the bootstrap layout wasn’t finalized yet.
I decided not to deal with this, especially as it wasn’t an official release, and simply issue warnings against installing the RC, and state that people using the RC may not be able to upgrade as it wasn’t finalized and we could make breaking changes.
This was when everything turned into a nightmare. People on /r/jailbreak and on twitter began spewing all sorts of conspiracy theories about how we were adding “DRM” into Electra by checking for topanga and/or the leaked RC (we actually don’t check for the leaked RC), when these in reality are safety checks. Furthermore, certain individuals on /r/jailbreak were trying to pull out the “that guy’s childish” card on us, when in reality, we have every right not to support such an unclean installation of iOS. (/r/jailbreak moderators, where were you???)
I decided that the noise was enough for the time, so I temporarily deactivated my twitter to work on it privately. Meanwhile, I issued the release candidates out to more developers and testing appeared to go well.
On February 26th, I was then able to finally announce the release of Electra 1.0, as most of the developers I gave the RC’s out to privately didn’t complain about any issues, neither did I notice any issues in my own testing. I even updated my other iOS 10 device (my iPhone 6S) to iOS 11, since I noticed how stable 1.0 was on my iPad Air 2.
A day after, however, saurik decided to push an update for APT (both late at night, and unexpectedly after months of no updates), which was missing 64 bit support or the necessary entitlements entirely, and thus wouldn’t work on iOS 11, breaking Cydia on Electra if the update was installed. As Cydia broke on iOS 11 devices, saurik made a post, which was quickly misinterpreted by a majority of people on reddit (who then created conspiracy theories all over again and filling the subreddit with spam -- where are the moderators????). Eventually I was able to address the issue by stopping updates from saurik’s repo (since he indicated he didn’t want to support Electra, and his packages were all non-functional on Electra anyways even if they were downloaded and could actualy cause problems) and by installing the correct APT version in 1.0.2.
Later, however, several iPhone X users and some users of other devices began reporting issues with the device freezing randomly (very similar to what I noticed with the original XPC change before I switched launchd off XPC). These reports ranged from constructive feedback to downright insults. All of this, mind you, was with my own iPhone 6S and iPad Air 2 running perfectly fine.
I suspected the issue could possibly be a bad tweak (as safe mode only protects SpringBoard and backboardd, not system daemons) or a bad launch daemon simply crashing and looping when it was restarted by launchd. As a test I decided to load the broken build of RocketBootstrap (version 1.0.5, before it was fixed in 1.0.6), which was missing the “platform-application” entitlement in rocketd. As expected, rocketd was crash-looping as it was started by launchd and then killed by sandbox for missing the entitlement. This was hogging up plenty of resources and actually also preventing launchd from starting new processes other than rocketd, which also manifested itself in the UI as a significant device slowdown with the device entirely freezing up after a few minutes.
When the problematic tweak removed, the freezing was gone and my device was back to normal, with everything working correctly. I decided to take a survey using Google Forms and noticed a substantial number of the responses had people using pirated tweaks. Normally I don’t care about piracy, however, in situations where the device is unstable, it can be a legitimate problem. Piracy repos, by definition, are re-hosting tweaks (sometimes even free ones), which are often outdated compared to their original source, depending on the repo. Some of them could definitely contain bad launch daemons (e.g. older versions of RocketBootstrap, the current version of Filza, and some other tools) that are missing the necessary entitlement to run on iOS 11.
Thus, I had every right to believe that the issue was caused by tweaks (although I later found out that 1.0.2 did actually have an issue on certain devices from using XPC in xpcproxy). However, many obvious pirates in particular were spamming my social media channels about the very issue, making it very difficult to see any messages from non-pirates. (It’s very easy to ignore a few people, but if they reach the 100′s of people, it becomes very difficult, as their spam takes up most of the visible space when looking at twitter/reddit).
To be clear, I quite frankly don’t care what people install on their own devices; however, it gets annoying when hundreds of people submit bug reports with their device clearly having pirated packages (some of which were outdated and definitely problematic). I made a retortical comment about how blocking piracy repos would make Electra less buggy. This was very much true as it would lower the number of potentially problematic tweaks (as piracy repos often ship outdated tweaks with modified version numbers -- see Appsync Unified). However, this also caused huge outcry as people began clamoring thinking I’d permanently block piracy repos; although I don’t care if users are using them. However, they should not have them as they alone can cause the same issue that was also caused by the same bug in the jailbreak at the time.
Meanwhile, a certain prominent developer decided to try claiming I was lying by stating *after the final release* that he was having issues with freezing. (Keep in mind, this developer had access to the release candidates, most definitely downloaded and installed them, and didn’t report a single issue). This developer was being very passive-aggressive when asked for logs and info that would be useful (which he didn’t provide by the way) and was stating he’d rather wait for the tool saurik hinted at, even though Electra was already complete and only needed that bug fix.
With some help from the PokeGo++ developer (thank you), I was able to fix this bug in 1.0.3, confirm the bug was fixed, and make the update available. However, the conspiracy theories from the earlier tweet spiraled out of control both on /r/jailbreak and my personal twitter that it became absolutely insane to try and handle.
As of right now, 1.0.3 is the latest version of Electra with no major known bugs (the launchd issue seems more of an issue with how launchd is implemented on iOS, as daemons shouldn’t crash constantly on iOS). Maybe issues will be discovered and fixed, maybe not. However, 1.0.3 works perfectly on my device as well as many others. The entire situation, unfortunately has become too complicated, as it’s near-impossible to attempt to debug issues that could crop up from 3rd party packages, especially if they can exhibit the same issues that can crop up from a bug in the jailbreak itself. (And the spam from people who think they know more than someone who has actually worked on the jailbreak they’re talking about)
So at the end of the day, while Electra has definitely benefited from being open, it also has ended up becoming a nightmare to maintain, with some reasons that were external, and some that were from Electra being open. However, the amount of spam and hatred I’ve been receiving from conspiracy theorists putting words in my mouth has gotten to a level that it seems better to do devleopment in private and occasionally only pop up to release...
103 notes
·
View notes
Link
Colleges That Require Virus-Screening Tech Struggle to Say Whether It Works Before the University of Idaho welcomed students back to campus last fall, it made a big bet on new virus-screening technology. The university spent $90,000 installing temperature-scanning stations, which look like airport metal detectors, in front of its dining and athletic facilities in Moscow, Idaho. When the system clocks a student walking through with an unusually high temperature, the student is asked to leave and go get tested for Covid-19. But so far the fever scanners, which detect skin temperature, have caught fewer than 10 people out of the 9,000 students living on or near campus. Even then, university administrators could not say whether the technology had been effective because they have not tracked students flagged with fevers to see if they went on to get tested for the virus. The University of Idaho is one of hundreds of colleges and universities that adopted fever scanners, symptom checkers, wearable heart-rate monitors and other new Covid-screening technologies this school year. Such tools often cost less than a more validated health intervention: frequent virus testing of all students. They also help colleges showcase their pandemic safety efforts. But the struggle at many colleges to keep the virus at bay has raised questions about the usefulness of the technologies. A New York Times effort has recorded more than 530,000 virus cases on campuses since the start of the pandemic. One problem is that temperature scanners and symptom-checking apps cannot catch the estimated 40 percent of people with the coronavirus who do not have symptoms but are still infectious. Temperature scanners can also be wildly inaccurate. The Centers for Disease Control and Prevention has cautioned that such symptom-based screening has only “limited effectiveness.” The schools have a hard time saying whether — or how well — the new devices have worked. Many universities and colleges, including prominent research institutions, are not rigorously studying effectiveness. “So why are we bothering?” said Bruce Schneier, a prominent security technologist who has described such screening systems as “security theater” — that is, tools that make people feel better without actually improving their safety. “Why spend the money?” More than 100 schools are using a free virus symptom-checking app, called CampusClear, that can clear students to enter campus buildings. Others are asking students to wear symptom-monitoring devices that can continuously track vital signs like skin temperature. And some have adapted the ID card swiping systems they use to admit students into dorms, libraries and gyms as tools for tracing potential virus exposures. Administrators at Idaho and other universities said their schools were using the new tech, along with policies like social distancing, as part of larger campus efforts to hinder the virus. Some said it was important for their schools to deploy the screening tools even if they were only moderately useful. At the very least, they said, using services like daily symptom-checking apps may reassure students and remind them to be vigilant about other measures, like mask wearing. Some public health experts said it was understandable that colleges had not methodically assessed the technology’s effectiveness against the coronavirus. After all, they said, schools are unaccustomed to frequently screening their entire campus populations for new infectious diseases. Even so, some experts said they were troubled that universities lacked important information that might help them make more evidence-based decisions on health screening. “It’s a massive data vacuum,” said Saskia Popescu, an infectious-disease epidemiologist who is an assistant professor at George Mason University. “The moral of the story is you can’t just invest in this tech without having a validation process behind it.” Other medical experts said increased surveillance of largely healthy college students seemed unduly intrusive, given that symptom checkers have limited usefulness and the effectiveness of wearable health monitors against Covid-19 is not yet known. Updated March 2, 2021, 3:28 p.m. ET The introduction of campus screening tools has often been bumpy. Last fall, the University of Missouri began requiring all students, faculty and staff to use CampusClear, a free app that asks users about possible symptoms, like high temperature or loss of smell. Users who say they have no symptoms then receive a “Good to Go!” notification that can clear them to enter campus buildings. The school initially did not enforce the use of CampusClear at building entrances, however, and some students used the app only infrequently, according to reporting by The Missourian, the campus newspaper. In October, the university began requiring people to show their app pass code to enter certain buildings, like the student center and library. The university has promoted the app as a tool to help educate students. But how effective it has been at hindering coronavirus outbreaks on campus is unknown. A spokesman for the University of Missouri said the school was unable to provide usage data on CampusClear — including the number of students who had reported possible symptoms through the app and later tested positive for the virus — requested by a Times reporter. Jason Fife, the marketing director at Ivy.ai, the start-up behind CampusClear, said nearly 425,000 people at about 120 colleges and universities used the app last semester, generating about 9.8 million user reports. Many schools, he noted, use data from the app not to follow individual virus cases but to look for symptom trends on their campuses. Ivy.ai, however, cannot gauge the app’s effectiveness as a virus-screening tool, he said. For privacy reasons, the company does not track individual users who report symptoms and later test positive for the infection. At some universities, administrators acknowledged that the tech they adopted this school year did not pan out the way they had hoped. Bridgewater State University in Bridgewater, Mass., introduced two tools last semester that recorded students’ whereabouts in case they later developed virus infections and administrators needed to trace their contacts. One system logged students’ locations every time they swiped their ID cards to enter campus buildings. The other asked students to scan printed-out QR codes posted at certain locations around campus. By the end of the semester, however, only about one-third of the 1,200 students on campus were scanning the bar codes. Ethan Child, a Bridgewater senior, said he had scanned the QR codes but also skipped them when walking by in the rain. “I think it’s reasonable to ask students to do it — whether or not they’ll actually do it is another thing,” he said. “People might just pass it by.” Class Disrupted Updated March 2, 2021 The latest on how the pandemic is reshaping education. Administrators discovered that the key to hindering coronavirus outbreaks was not technology but simply frequent testing — once a week, for on-campus students — along with contact tracing, said Chris Frazer, the executive director of the university’s wellness center. “I’m glad we didn’t spend an exorbitant amount of money” on tech tools, Dr. Frazer said. “We found what we need is tests and more tests.” The location-tracking tools ultimately proved most useful for “peace of mind,” he added, and to confirm the findings of contact tracers, who often learned much more about infected students’ activities by calling them than by examining their location logs. Other schools that discovered location tracking was not a useful pandemic safety tool decided not to deploy it at all. At Oklahoma State University, in Stillwater, administrators said they had planned to log students’ locations when they used campus Wi-Fi for possible later use in contact tracing. But the school never introduced the system, said Chris Barlow, the school’s health services director, partly because administrators realized that many students had contracted the virus off campus, in situations where public health measures like mask wearing were not followed. At the University of Idaho and other schools, administrators described devices like fever scanners as add-ons to larger campus safety efforts involving student testing and measures like social distancing. Last fall, for instance, the University of Idaho tested its students for the virus at the beginning and middle of the semester, with some random testing as well. The school also used a wastewater testing program to identify an impending virus outbreak at fraternity and sorority houses, proactively quarantining more than a dozen chapters before cases could spread widely through the community. “We got out in front of it early,” C. Scott Green, the president of the University of Idaho, said. “We were able to isolate those that were sick, and we got back under control.” Still, there were hiccups. The university required food service employees who worked at the dining hall to undergo temperature checks using hand-held scanners. But several developed virus infections anyway, and the university was forced to temporarily close the dining hall over a weekend for deep cleaning. As for the free-standing temperature-scanning stations, Mr. Green himself has experienced their limitations. He said one mistakenly stopped him from entering an athletic building right after he got out of a hot car. Source link Orbem News #Colleges #require #Struggle #Tech #VirusScreening #Works
0 notes
Photo


Arnod - A Chatbot for helping Raynaud’s patients
framing & strategizing; concept & ideation; creating & crafting; reflection & awareness; self-directed learning;
Introduction
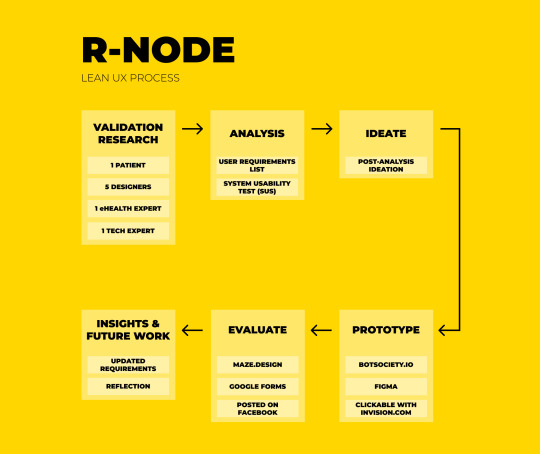
In this project we designed a minimum viable product (MVP) chatbot that can potentially help patients keep track of their Raynaud’s phenomenon. The chatbot named Arnod, which sounds more humane - an important attribute of chatbots and conversational agents according to Radziwill and Benton, 2017, i.e. see Alexa, Siri. is an iteration on the smartphone application that accompanied my r-node smart ring concept of my bachelor thesis project (Partheniadis & Stavrakis, 2017). With the help of Lean UX strategy, Arnod explores the part of acquiring quantitative and qualitative data from the daily life of Raynaud’s patients to provide a usable, reliable, functional and emotional User Experience. A clickable prototype Arnod chatbot was tested with 19 Raynaud’s patients remotely using a new usability testing tool called Maze.design.
Initial Scope
This project started with the aim of redesigning the User Interface of r-node application which was the result of my bachelor thesis project. Primarily r-node aimed to provide Raynaud’s patients with an interface to (a ) keep track of Raynaud’s attacks and (b ) learn more about their Raynaud’s phenomenon. Secondarily, it aimed to (c ) bring patients together, (d ) bring patients in touch with doctors by sharing their data, (e ) bring researchers closer to patients to help them conduct studies related to Raynaud’s phenomenon.
Reframe of Scope
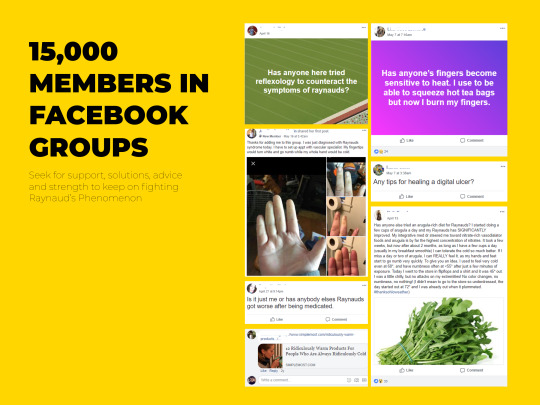
During the project, particular interest was found behind the idea of Conversational User Interfaces (CUI) for helping patients report Raynaud’s attacks. We identified high potential of CUIs and Chatbots to assist e-health applications (Chung & Park, 2018) in latest papers and applications (Your.MD, Sensely with Mayo Clinic, Buoy Health, Infermedica, Florence). From personal observations, more than 15,000 Raynaud’s patients are actively looking for support and solutions in self-organized Facebook Groups (1,2,3). The CUI could provide Raynaud’s patients with tracking and diary-keeping capabilities regarding their disorder in a familiar environment i.e. Facebook Messenger.
What is Raynaud’s
This personal project started with the aim of evaluating and iterating on the previous UX and UI that had been designed during my thesis project with title “Designing a smart ring and a smartphone application to help monitor, manage and live better with the effects of Raynaud’s Phenomenon”. People who suffer from Raynaud’s Phenomenon (RP) often experience cold fingers, toes and other extremities when they are exposed to cold or stressful situations. See pictures and clinical information here. It appears in 5% (Wigley, 2002) to 10% (Klippel, 1991) of the world’s population depending on geographic location, with women representing 90% of them (Nietern et al., 2015). The typical presentation of a RP cold ‘attack’ involves the fingers turning white (ischemia), then blue (cyanosis), and finally red (rubor). Raynaud’s Phenomenon is either described as Primary or Secondary. Primary RP occurs by itself (as a disease) by unidentifiable reasons and can’t be cured. Secondary RP is considered an expression of another underlying disease which, if identified and managed, it consequently cures RP as well. Both types have common symptoms, but the attacks can differ on symmetry, severity, frequency and duration and can be distinguished with clinical criteria.
Previous version of r-node app
The previous version of r-node features a lot of things like live temperature tracking(UI2,3), Raynaud’s attack prediction(UI2), attacks recording & history log(UI5), community of Raynaud’s patients(see third tab on UI2,3), activity tracking (UI3) similar to what other activity trackers do. This is complicated. This version has explored various different points of views around Raynaud’s. In this Iteration, its a primary goal to conduct validation research on this version by asking Raynaud’s patients, designers, engineers, e-health experts to give their feedback in think-aloud sessions. We are not aiming to evaluate this version strictly but we are seeking new knowledge, insights, challenges. Being in Netherlands gives the opportunity to connect with more patients and experts than I could in Greece.


Project Plan
March 8 - Validation Research: Subject A - Raynaud’s Patient: Meet a Raynaud’s patient from Netherlands, Run 3 Think aloud sessions with tasks, Validate current r-node solution, reveal strengths and weaknesses, potentially connect me with more RP patients.
March 9 - Validation Research: Subject B - Digital Designer with background in Arts: Aim was to see another designer empathize with the people who suffer from RP, see alternative point of view in terms of UX and visual language.
March 10 - Validation Research, Focus Group:Subject C,D,E,F - Digital Designers different disciplines: Aim to be generative and help
March 19 - Feedback from Irene Kamp: “Interesting to do a Lean UX iteration, Focus on what are the Insights generated for the patients and what is the System’s learning curve”.
March 21 - Validation Research, Expert Review: Pieter Kubbens, Neurosurgeon and e-Health Expert: Aim to connect with a network of e-health experts in Netherlands to (a) receive feedback on my project (b) potentially develop an application together.
March 25 - Validation Research, Reade Reumatologie Clinic: Aim to come in contact with health professionals to receive feedback from Raynaud’s specialists for r-node.
April 1 - Ideation: Visualize and Ideate on different point of views as derived from the validation research.
April 10 - Prototype: Filter out ideas and develop a prototype and prepare it for quick user testing using Maze.design.
April 15 - Evaluation: Publish for evaluation before may comes in. Post
April 30 - Evaluation: Gather results & analyze
Reflection & Portfolio Post
youtube
Desktop Findings
Top findings from the project include: Messaging is the number one way people are connecting today. The most important advancement in Conversational UI (CUI) has been Natural Language Processing (NLP) allowing the understanding of the actual human intent when they ask something from their device. More than 15,000 Raynaud’s patients are connected in Facebook groups to share their experiences and help each other regarding Raynaud’s. These Raynaud’s patients with an age range of 30-60 are actively seeking for a solution to keep track of they Raynaud’s attacks (thesis finding). Chatbots in smartphones make qualitative and quantitative assesment of one’s medical condition possible through a single user interface. According to Google Trends, chatbot is a trending search term and Facebook reveals chatbot-based conversations have increased 5.9 times since January 2017. Chatbots are being used more by people in their 40′s rather those in their 20′s. BI Intelligence reveals A Chatbot like Arnod (chatbot/digital assistant), can work together with the r-node smart ring (thesis outcome), to attain quantitative data real-time. Arnod can collect qualitative data in a strategic and natural way through its conversational user interface (CUI). Raynaud’s patients are familiar with Facebook and Messenger interfaces, since they gather in Facebook Groups to report and discuss about their Raynaud’s attacks, and we assume that they are likely to feel more comfortable using the Arnod conversational interface rather than a typical interface with text-fileds, sliders and drop-down menus. Trends in chatbot design in late 2017 provide users with buttons or drop-downs within the chat interface and allow text input only when needed, in order to minimize faulty inputs.
Validation Research Results
The low fidelity smartphone application confused most Subjects. The Raynaud’s tab should keep the amount of information shown to a minimal level. The subjects think the color-sensitive background space is very wisely used to visualize the risk of having a Raynaud’s attack real-time. Subject B noticed that the word ‘attack’ is not a good way to express the appearence of the symptoms as it automatically generates bad feelings (i.e. heart attack) and it might be important to work more on the branding and language used on the product application. Three subjects pinpoint the potential of the product to evolve as a research tool which can benefit the Raynaud’s patients in the long-term. They believe it has a lot of potential in helping study how human activities affect their Raynaud’s Phenomenon. Subject A, with RP, believes it could help identify patterns between people with common habits and common health problems and Raynaud’s symptoms and make it easier to share treatment methods they use. She believes an application like r-node can be a very powerful tool to reveal experiential solutions that people use to deal with their painful and embarassing symptoms. It has big potential to function as a place to track, learn and spread the knowledge about Raynaud’s.
Reflection
Strategy: The strategy worked out nicely. The Sketch below represents one Lean UX cycle from ‘Better Together’ agile framework. During the process multiple stakeholders(patient, e-health expert) and experts(designers, engineer) were interviewed, a chatbot-making tool was tested, and a remote evaluation was conducted with Maze.design and Google Forms with 19 participants who suffered from Raynaud’s Phenomenon.
Only one Raynaud’s patient was interested in participating in the test. I have been in close contact with a German male, two dutch ladies and a dutch representative of a Lupus association of Netherlands. Raynaud’s usually appears secondary symptom to Lupus patients. Although only one lady could finally come over. I prepared extensive tasks like holding cold drinks, warm drinks, typing on keyboard as a normal activity to observe how temperature normalizes. We went outside at a different context where the patient presented a short raynauds attack.
Validation Research: The project started with preparing the Validation Research of r-node. The research aim was to review the current product by patients and experts. The participant was 1 Raynaud’s patient, 1 E-health expert and Neurosurgeon Doctor from NFU, 5 Master Designers students and 1 Technology Expert. Contact was also made with Amsterdam Rheumatology and Immunology Center in order to arrange an expert review with a Rheumatologist who is more relevant to Raynaud’s Phenomenon. Unfortunately doctors weren’t interested in sharing their expertise, but they advised me to approach VU Medical Center, outpatient Rheumatology where they have a larger target audience of Raynaud’s patients. Due to lack of time VU was not contacted. For the validation sessions I prepared a sheet of 38 requirements on which the r-node would be evaluated. To conduct the test the following were used: a poster to explain the concept, working prototypes, cold and warm objects to interact, cameras. Data were collected as notes in a notepad or directly on the requirement’s list through a think-aloud process. The patient and one designer were left by themselves at the end to fill a typical System Usability Scale (SUS) form. The focus group consisted of multidisciplinary Designers. Subject C, 24 has a bachelor in Industrial Design, she considers herself quite social (3/5) when she feels comfortable with the people around her, has usually cold fingers but does not present Raynaud’s phenomenon. Her finger temperature during the test was 20 celsius degrees, and the room was 20. Subject D, 26, she has a bachelor degree in Media and a second one in Graphic Design. She considers herself likes to wear large rings and does not have an oversensitivty to cold. Subject E, 23, she has a bachelor in Design is very social person. Subject F, 25, he is a Product Designer and is a very social person.
Strengths
The user's and experts showed interest for the following things:
Sharing: Designers believe that the system should support the idea of community and sharing data. They suggest that the interface should support functions similar to what raynauds Facebook groups use like sharing images, discussing around them.
Eliminate Costs: Designers believe the patients will not willing to pay for the high cost (100-200€) of acquiring the r-node ring. They positively comment the opportunity to release a minimum viable product in the form of a smartphone application for helping patients keep track of Raynaud’s attacks.
Usership of the r-node ring: Designers propose a temporary ownership of the ring for the patients, since they are likely to get educated on how to treat themselves and then keep on living without the ring but with just the app. If the ring would have a starting price of 300€ she would be willing to wait and pay 100€ for a used ring if they are built to last.
Ideation
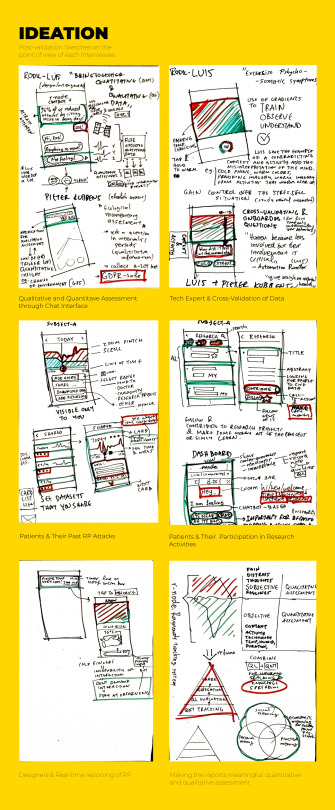
During ideation, the aim was to create quick sketches of how r-node would look like from the point of view of each evaluation participant. In total, 12 graphical user interfaces were sketched. The first two would visualize the commonalities between the point of view of the Technology Expert and the Neurosurgeon interviewed. Both have a strong technology background with internet of things, wearables and programming and are well aware of the GDPR laws. Their opinions strongly overlap about the requirement of proving the system with qualitative and quantitative data in order to better assess one’s state of Raynaud’s Phenomenon. Tech expert suggests chat-bots can help collect qualitative data from the user and, thus, help validate the sensor’s quantitative measurements. E-health expert underlines the importance of using questions as notifications in intervals which by his experience, helps collect useful qualitative data with little user effort. From my previous experience with computer vision and taking into account the trends of AI and machine learning, the system can translate qualitative data into meaning i.e. pictures into text for recognizing fingers and their color, or text into snippets to analyze and ask related follow up questions.
Quantitative & Qualitative Assessment
The concept behind r-node knowledge base is to assess one’s Raynaud’s Phenomenon by evaluating quantitative data with qualitative data. To put it simply, there are two point of views that can be combined in order to keep track of Raynaud’s events pragmatically and meaningfully: what the smartphone thinks I am experiencing right now? (sensors, numbers, predictions are quantitative data) and What am I actually experiencing right now? (human outlook is qualitative data).

Little evidence has been found regarding this process of evaluating mdeical conditions. Very recently, in March 2018, a paper points out that “Wearable devices for healthcare provide medical feedback to users based solely on specific biometric data” and thus “inaccurate information can be provided”. Subject H (Luis-Rodil) underlines the “paradox of automation” in which we confess technology becoming automated but the human factor becomes more important than ever to validate the system. The importance of qualitative assessment by humans is crucial especially for health applications in everyday life where no specialized medical devices are used to track the symptoms but regular smartphones. Quantitative data are collected by the smartphone sensors (location, activity) and the smart ring sensors (temperatures, humidity, heart rate, galvanic skin response). The system forms a hypothesis and creates qualitative questions to validate the hypothesis. The user replies or dismisses the questions which appear in intervals as notifications right after an attack has passed (according to the smart ring measurements) or after the user has entered a warmer environment or when the user starts to interact with their phone - which guarantees that their fingers are in a working condition. Qualitative answers are sent for analysis on machine learning and AI systems to help the system aggregate the information and present it in a human form. For example, the system may ask a simple but significant question to validate the accuracy of its measurements and help the system build a baseline to correlate which temperature equals to cold feelings for that person: “How cold do you feel your fingers in a scale from 1 to 5?”, where user simply types “4” in a numeric-only keyboard. A more difficult question could be “What do you think have caused this RP attack?” where user may start typing an extended report on what happened that moment or simply use voice input to say “no idea pal”. That’s part of data analysis and aggregation. After an extended period of time of use of the system we expect it to know more about which activities and contexts make the user more prone to having a Raynaud’s attack. With the combination of the wearable smart ring and the quantitative+qualitative assessment system, we expect data analytics and insights to appear about your situation in real-time: “Work gets colder 2 degrees after 14:00. Maybe it’s time for a tea!”. ”As part of their freedom of choice (GDPR), users can erase the quantitative and qualitative data at any time selectively or wholly. In the end, we expect the users to have gained knowledge from the contexts and activities that affect them or help them decrease the chances of an RP attack: food choices, exercise, places, etc.
Prototypes
Two prototypes were developed. The first was made in botsociety.io. Custom graphics where made in Figma and inserted in botsociety. Botsociety gave me the ability to quickly visualize the human-computer interaction with a chatbot called ‘Arnod’ - an easier alternative to r-node that also refers to a human name which are oftentimes used for smart assistants i,e, Alexa, Siri, etc.. With the first prototype I brainstormed on the user journey of ‘Reporting a Raynaud’s attack’. The aim of the project was to evaluate the system designed with users. Botsociety could playback the chatbot journey I had just created like a video which would make it easy to explain a concept to the stakeholders. Although, during user testing, we want the user to engage with the system and partake in the demo. Botsociety provides a small button that makes the prototype interactive! Unfortunately this did not function properly and as an addition I would still have troubles testing the scenario with users quickly.
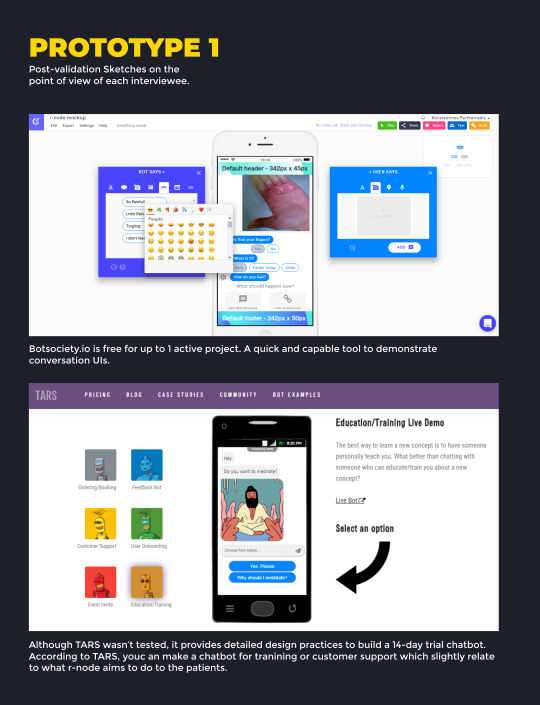
For the second prototype, I chose to design the interfaces on Figma, based on Android Material Design GUI, with botsociety prototype and the best Facebook Chatbot Practices as a reference. The next step was to use InVision to make it interactive. For the chatbot creation it was important to use Timer in InVision; when a user says something, there is a delay before the bot behind the chat replies.

Evaluate
I used Maze.design to embed the ‘Arnod’ InVision prototype and conduct onlien user testing. Try the user test yourself, you might find it useful to try for one of your next projects. A link was created and shared strictly on Raynaud’s Facebook Groups. The Maze test had 19 participants in two days. Only 2 out of them completed the whole test. The rest abandoned earlier as the Maze data analytics show. This signifies three things: (a) firstly, users were unfamiliar such testing interface and needed more guidance and support by a physical person; (b) they expected the system to interact back when they would do a mistaken click and as a result they were easily annoyed and quit early; © they found the chatbot especially unfamiliar.

Overall, the users insisted on specific replies to respond to the Chatbot. The heatmaps that Maze generates are a little bit hard to interpret because you dont know actually the users intention. In detail, many times they wanted to express how they feel by themselves by clicking the text input. People where experimenting with all the answers although the heatmaps reveal that 18.2% of the users were avoiding to say “Hi!” to the Arnod Chatbot. The rest were feeling more comfortable about asking ‘what can you do for me’. The second question of the bot was ‘Do you have any cold attacks to report?’ and the people tapped either on ‘Yes’ or ‘no’ and noone tapped on ‘ ‘who are you?’ answer. The next question was ‘Have a picture of the fingers?’ and what’s interesting here to find is that several taps were recorded on the icon to go ‘Back’ or the ‘settings’ icon on the top bar and most taps were recorded on ‘Wait’ response! This could indicate that the users felt uncomfortable with the question as if they have to share their personal image with an unknown system. The question of the bot could be rephrased to ‘Could you please share a picture of the fingers?’ or ‘Would you like to register the event?’ and then ask for a picture where the intention of the bot is clear. When asked to select a picture some dummy pictures where shown. A lot of people clicked pictures that are not fingers which validates our need to use Google’s Vision API to identify that the picture uploaded is likely to be fingers or skin. Although people might still need to upload pictures of the context of the Raynaud’s attack e.g. car, so an additional question could be by the bot ‘I identified pictures that were not fingers or skin-related, would you like me to add them?’ *bot also shows these pictures*. When the picture of the fingers was uploaded, the question was ‘When did this happen to your fingers?’. A lot of clicks were recorded on ‘+’ as if they wanted to add more pictures which supports our previous suggestion to let them add more. Their second choice was ‘Earlier today’ or ‘Exactly at...’ to enter their own time of preference. People clicked that the event felt ‘So Painful :(’ or ‘Little Pain’ and less people clicked on ‘Embarrassing’. The system asked what triggered the attack and the automatic response was because of standing still and working too long. The automatic reply of the system was an insight and statistics, in this case that 62% get white fingers after sitting still and working for too long. The users firstly clicked ‘I don’t care’ meaning they really wouldnt care knowing about others in that moment. Secondly they would click ‘I can relate’ or ‘Tell me more’ and thirdly they would click on the bot’s insight message itself. So, its important to make insights clickable and link to proof of others’ similar events for more insights. At the end where the event was recorded the people wanted to ‘See more’ about the event and noone wanted to ‘Edit’ it. Maybe they could be one button as see more and edit there if a specific field is being clicked. I suggest trying the inVision clickable experience to see what happens on every screen.
After the users completed the task they were being congratulated, and they could optionally respond to a quick survey on Google Forms to leave their feedback. One user was very excited Maze is a great and a much requested tool by the community of digital designers. Conducting online quick user tests can save time and effort and help address the right target group through social media. It keeps track of time spent by the user interacting on each screen, counts and locates mistaken clicks with heat-maps. Maze requires more development in order to be recognized and trusted as a user testing software. It can give although big number of responses when you can send it to your target group.
Opportunity
Patient education for prevention is inseparable part for managing Raynaud’s successfully. It is considered that patients should take proper precautions for avoiding direct interactions with cold objects and environments. Multilayered clothing, glove liners, electric gloves, pocket heaters are essential for keeping the core body and extremities warm during the cold months. A healthy eating, non-smoking lifestyle with daily exercising or meditation can help improve circulation and relieve stress in the long-term.
Patients are poorly educated about what they can do for their disorder. According to all three RP patients during the validation research, doctors, usually Rheumatologists and Neurologists, do not provide enough resources to help patients learn about their disorder. Doctors give medicine only when the phenomenon becomes severe and they warn about side effects. Patients are used to rely on the doctor’s expertise and thus, they don’t seek for a solution themselves. The reversibility of the Raynaud’s effects make patients believe that it is not a chronic disease and because gives the illusion that it goes away. Patients get used to living with Raynaud’s and forget about how much it bothers them in their everyday activities. They learn to live with cold hands, painful purple fingers. They learn to live with it and when someone asks about it, they feel embarrassed. They can hardly talk about it. They avoid social interactions. R-node recognizes that people tend to suppress their feelings and wants to help them learn more about them. Upon arriving home after a cold day outside, r-node, through the user’s smartphone, may ask: “It was a cold day in Amsterdam today. How did you feel about it?”. The user can quickly start replying to the system or can select one of the predefined answers to the question that best describes their feelings: “So Painful :(”, “Little Pain”, “Embarassing..”, “Under Control”, etc.
Patients gather in Facebook groups with tens of thousands of members with different degrees of severity on Raynaud’s phenomenon. They exchange images, opinions, suggest activities to help reduce RP, share experiences and positive energy along the members. R-node recognizes the value of community, appreciates the simplicity of exchanging image posts, queries and links within Facebook and aims at integrating similar features in the smartphone application.With r-node we believe we can give patients a safe place to keep track of their phenomenon and also explore solutions and seek for help within the thousand other patients.
1 note
·
View note
Text
300+ TOP ASP.NET Objective Questions and Answers
ASP.NET Multiple Choice Questions :-
1. Choose the form in which Postback occur
A. HTMLForms
B. Webforms
C. Winforms
Ans: Webforms
2. Web.config file is used...
A. Configures the time that the server-side codebehind module is called
B. To store the global information and variable definitions for the application
C. To configure the web server
D. To configure the web browser
Ans: To store the global information and variable definitions for the application
3. Which of the following object is not an ASP component?
A. LinkCounter
B. Counter
C. AdRotator
D. File Access
Ans: LinkCounter
4. The first event triggers in an aspx page is.
A. Page_Init()
B. Page_Load()
C. Page_click()
Ans: Page_Init()
5. Difference between Response.Write() andResponse.Output.Write().
A. Response.Output.Write() allows you to buffer output
B. Response.Output.Write() allows you to write formatted output
C. Response.Output.Write() allows you to flush output
D. Response.Output.Write() allows you to stream output
Ans: Response.Output.Write() allows you to write formatted output
6. Which of the following method must be overridden in a custom control?
A. The Paint() method
B. The Control_Build() method
C. The default constructor
D. The Render() method
Ans: The Render() method
7. How do we create a FileSystemObject?
A. Server.CreateObject("Scripting.FileSystemObject")
B. Create("FileSystemObject")
C. Create Object:"Scripting.FileSystemObject"
D. Server.CreateObject("FileSystemObject")
Ans: Server.CreateObject("Scripting.FileSystemObject")
8. Which of the following tool is used to manage the GAC?
A. RegSvr.exe
B. GacUtil.exe
C. GacSvr32.exe
D. GacMgr.exe
Ans: GacUtil.exe
9. What class does the ASP.NET Web Form class inherit from by default?
A. System.Web.UI.Page
B. System.Web.UI.Form
C. System.Web.GUI.Page
D. System.Web.Form
Ans: System.Web.UI.Page
10. We can manage states in asp.net application using
A. Session Objects
B. Application Objects
C. Viewstate
D. All of the above
Ans: All of the above

ASP.NET MCQs
11. Attribute must be set on a validator control for the validation to work.
A. ControlToValidate
B. ControlToBind
C. ValidateControl
D. Validate
Ans: ControlToValidate
12. Caching type supported by ASP.Net
A. Output Caching
B. DataCaching
C. a and b
D. none of the above
Ans: a and b
13. What is used to validate complex string patterns like an e-mail address?
A. Extended expressions
B. Basic expressions
C. Regular expressions
D. Irregular expressions
Ans: Regular expressions
14. File extension used for ASP.NET files.
A. .Web
B. .ASP
C. .ASPX
D. None of the above
Ans: .ASP
15. An alternative way of displaying text on web page using
A. asp:label
B. asp:listitem
C. asp:button
Ans: asp:label
16. Why is Global.asax is used?
A. Declare Global variables
B. Implement application and session level events
C. No use
Ans: Implement application and session level events
17. Which of the following is not a member of ADODBCommand object?
A. ExecuteScalar
B. ExecuteStream
C. Open
D. ExecuteReader
Ans: Open
18. Which DLL translate XML to SQL in IIS?
A. SQLISAPI.dll
B. SQLXML.dll
C. LISXML.dll
D. SQLIIS.dll
Ans: SQLISAPI.dll
19. Default Session data is stored in ASP.Net.
A. StateServer
B. Session Object
C. InProcess
D. all of the above
Ans: InProcess
20. Default scripting language in ASP.
A. EcmaScript
B. VBScript
C. PERL
D. JavaScript
Ans: VBScript
21. How do you get information from a form that is submitted using the "post" method?
A. Request.QueryString
B. Request.Form
C. Response.write
D. Response.writeln
Ans: Request.Form
22. Which object can help you maintain data across users?
A. Application object
B. Session object
C. Response object
D. Server object
Ans: Application object
23. Which of the following ASP.NET object encapsulates the state of the client?
A. Session object
B. Application object
C. Response object
D. Server object
Ans: Session object
24. Which of the following object is used along with application object in order to ensure that only one process accesses a variable at a time?
A. Synchronize
B. Synchronize()
C. ThreadLock
D. Lock()
Ans: Synchronize()
25. Which of the following control is used to validate that two fields are equal?
A. RegularExpressionValidator
B. CompareValidator
C. equals() method
D. RequiredFieldValidator
Ans: CompareValidator
26. Mode of storing ASP.NET session
A. InProc
B. StateServer
C. SQL Server
D. All of the above
Ans: All of the above
27. Which of the following is not the way to maintain state?
A. View state
B. Cookies
C. Hidden fields
D. Request object
Ans: Request object
28. You can have only one Global.asax file per project.
A. Yes
B. No
Ans: Yes
29. ______________ element in the web.config file to run code using the permissions of a specific user
A. element
B. element
C. element
D. element
Ans: element
30. __________ is a special subfolder within the windows folder that stores the shared .NET component.
A. /bin
B. GAC
C. Root
Ans: GAC
31. Which of the following is the performance attributes of processModel?
A. requestQueue limit
B. maxWorkerThreads
C. maxIdThreads
D. All
Ans: All
32. Which of the following is faster and consume lesser memory?
A. SQLDataReader
B. Data Set
Ans: SQLDataReader
33. Which of the following is the way to monitor the web application?
A. MMC Event viewers
B. Performance logs
C. Alerts Snap-ins
D. ALL
Ans: ALL
34. The ________________ property affects how the .Net Framework handles dates, currencies, sorting and formatting issues.
A. CurrentUICulture
B. CurrentCulture
Ans: CurrentCulture
35. Where do we include the user lists for windows authentication?
A.
B.
C.
D.
Ans:
36. Where do we include the user lists for Form authentication?
A.
B.
C.
D.
Ans:
37. Which of the following authentication is best suited for a corporate network?
A. Windows
B. Form
C. User
D. All
Ans: Windows
38. What attributes do you use to hide a public .Net class from COM?
A. DLLImport Attributes
B. ComVisible attributes
C. COM Interop
D. All
Ans: ComVisible attributes
39. By default, code written with the Debug class is stripped out of release builds.
A. Yes
B. No
Ans: Yes
40. _________ tests make sure that new code does not break existing code.
A. Regression tests
B. Integration tests
C. Unit tests
D. Load test
Ans: Integration tests
41. The .NET Framework provides a runtime environment called..... ?
A. RMT
B. CLR
C. RCT
D. RC
Ans: CLR
42. In ASP.NET in form page the object which contains the user name is ______ ?
A. Page.User.Identity
B. Page.User.IsInRole
C. Page.User.Name
D. None of the Above
Ans: Page.User.Identity
43. Find the term: The .NET framework which provides automatic memory management using a technique called ______________ ?
A. Serialization
B. Garbage Collection
C. Assemblies
D. Overriding
Ans: Garbage Collection
44. Which of the following denote ways to manage state in an ASP.Net Application?
A. Session objects
B. Application objects
C. ViewState
D. All the Above
Ans: All the Above
45. What is the base class from which all Web forms inherit?
A. Master Page
B. Page Class
C. Session Class
D. None of the Above
Ans: Page Class
46. WSDL stands for ___________ ?
A. Web Server Description Language
B. Web Server Descriptor Language
C. Web Services Description Language
D. Web Services Descriptor Language
Ans: Web Services Description Language
47. Which of the following must be done in order to connect data from some data resource to Repeater control?
A. Set the DataSource property
B. Call the DataBind method
C. Both A. and B.
D. None of the Above
Ans: Both A. and B.
48. Which of the following is FALSE?
A. ASP.NET applications run without a Web Server
B. ASP+ and ASP.NET refer to the same thing
C. ASP.NET is a major upgrade over ASP
D. None of the Above
Ans: None of the Above
49. Which of the following transfer execution directly to another page?
A. Server.Transfer
B. Response.Redirect
C. Both A. and B.
D. None of the Above
Ans: Server.Transfer
50. If one has two different web form controls in a application and if one wanted to know whether the values in the above two different web form control match what control must be used?
A. DataList
B. GridView
C. CompareValidator
D. Listview
Ans: CompareValidator
51. Which of the following is used to send email message from my ASP.NET page?
A. System.Web.Mail.MailMessage
B. System.Web.Mail.SmtpMail
C. Both A. and B.
D. None of the Above
Ans: Both A. and B.
52. In my .NET Framework I have threads. Which of the following denote the possible priority level for the threads?
A. Normal
B. AboveNormal
C. Highest
D. All the Above
Ans: All the Above
53. In .NET the operation of reading metadata and using its contents is known as ______?
A. Reflection
B. Enumeration
C. Binding
D. Serialization
Ans: Reflection
54. In ASP.NET the section contain which of the following elements?
A.
B.
C. Both A. and B.
D. None of the Above
Ans: Both A. and B.
55. The type of code found in Code-Behind class is ________ ?
A. Server-side code
B. Client-side code
C. Both A. and B.
D. None of the above
Ans: Server-side code
56. Common type system is built into which of the following:
A. CLR
B. RCT
C. RCW
D. GAC
Ans: CLR
57. The actual work process of ASP.NET is taken care by _____________?
A. inetinfo.exe
B. aspnet_isapi.dll
C. aspnet_wp.exe
D. None of the Above
Ans: aspnet_wp.exe
58. Which of the following allow writing formatted output?
A. Response.Write()
B. Response.Output.Write()
C. Both A. and B.
D. None of the Above
Ans: Response.Output.Write()
59. Which of the following denote the property in every validation control?
A. ControlToValidate property
B. Text property
C. Both A. and B.
D. None of the Above
Ans: Both A. and B.
60. How many classes can a single .NET DLL contain?
A. One
B. Two
C. None
D. Many
Ans: Many
61. Suppose one wants to modify a SOAP message in a SOAP extension then how this can be achieved. Choose the correct option from below:
A. One must override the method ReceiveMessage
B. One must override the method InitializeMethod
C. Both A. and B.
D. One must override the method ProcessMessage
Ans: One must override the method ReceiveMessage
62. Which of the following can be used to add alternating color scheme in a Repeater control?
A. AlternatingItemTemplate
B. DataSource
C. ColorValidator
D. None of the Above
Ans: AlternatingItemTemplate
63. Suppose a .NET programmer wants to convert an object into a stream of bytes then the process is called ______________ ?
A. Serialization
B. Threading
C. RCW
D. AppDomain
Ans: Serialization
64. The technique that allow code to make function calls to .NET applications on other processes and on other machines is
A. .NET Threading
B. .NET Remoting
C. .NET RMT
D. None of the above
Ans: .NET Threading
65. The namespace within the Microsoft .NET framework which provides the functionality to implement transaction processing is ....................
A. System.EnterpriseServices
B. System.Security
C. System.Diagnostics
D. System.Data
Ans: A
66. Which of the following method is used to obtain details about information types of assembly?
A. GetTypes
B. GetType
C. Both A. and B.
D. None of the Above
Ans: Both A. and B.
67. Which of the following is TRUE about Windows Authentication in ASP.NET?
A. Automatically determines role membership
B. Role membership determined only by user programming
C. ASP.NET does not support Windows Authentication
D. None of the Above
Ans: Automatically determines role membership
68. What tags one need to add within the asp:datagrid tags to bind columns manually?
A. Set AutoGenerateColumns Property to false on the datagrid tag
B. Set AutoGenerateColumns Property to true on the datagrid tag
C. It is not possible to do the operation
D. Set AutomaunalColumns Property to true on the datagrid tag
Ans: Set AutoGenerateColumns Property to false on the datagrid tag
69. Which method do you invoke on the DataAdapter control to load your generated dataset with data?
A. Load ( )
B. Fill( )
C. DataList
D. DataBind
Ans: Fill( )
70. In ASP.NET the sessions can be dumped by using
A. Session.Dump
B. Session.Abandon
C. Session.Exit
D. None of the Above
Ans: Session.Abandon
71. Which of the following languages can be used to write server side scripting in ASP.NET?
A. C-sharp
B. VB
C. C++
D. A and B
Ans: D
72. When an .aspx page is requested from the web server, the out put will be rendered to browser in following format.
A. HTML
B. XML
C. WML
D. JSP
Ans: A
73. The Asp.net server control, which provides an alternative way of displaying text on web page, is
A.
B.
C.
Ans: A
74. The first event to be triggered in an aspx page is.
A. Page_Load()
B. Page_Init()
C. Page_click()
Ans: B
75. Postback occurs in which of the following forms.
A. Winforms
B. HTMLForms
C. Webforms
Ans: C
76. What namespace does the Web page belong in the .NET Framework class hierarchy?
A. System.web.UI.Page
B. System.Windows.Page
C. System.Web.page
Ans: A
77. Which method do you invoke on the Data Adapter control to load your generated dataset?
A. Fill( )
B. ExecuteQuery( )
C. Read( )
Ans: A
78. How do you register a user control?
A. Add Tag prefix, Tag name
B. Add Source, Tag prefix
C. Add Src, Tagprefix, Tagname
Ans: C
79. Which of the following is true?
A. User controls are displayed correctly in the Visual Studio .NET Designer
B. Custom controls are displayed correctly in VS.Net Designer
C. User and Custom controls are displayed correctly in the Visual Studio .NET Designer.
Ans: C
80. To add a custom control to a Web form we have to register with.
A. TagPrefix
B. Name space of the dll that is referenced
C. Assemblyname
D. All of the above
Ans: B
81. Custom Controls are derived from which of the classes
A. System.Web.UI.Webcontrol
B. System.Web.UI.Customcontrol
C. System.Web.UI.Customcontrols.Webcontrol
Ans: D
82. How ASP.Net Different from classic ASP?
A. Scripting is separated from the HTML, Code is interpreted seperately
B. Scripting is separated from the HTML, Code is compiled as a DLL, the DLLs can be executed on server
C. Code is separated from the HTML and interpreted Code is interpreted separately
Ans: C
83. What's the difference between Response.Write() andResponse.Output.Write()?
A. Response.Output.Write() allows you to flush output
B. Response.Output.Write() allows you to buffer output
C. Response.Output.Write() allows you to write formatted output
D. Response.Output.Write() allows you to stream output
Ans: B
84. Why is Global.asax is used?
A. Implement application and session level events
B. Declare Global variables
C. No use
Ans: C
85. There can be more than 1 machine.config file in a system
A. True
B. False
Ans: A
86. What is the extension of a web user control file?
A. .Asmx
B. .Ascx
C. .Aspx
Ans: A
87. Which of the following is true?
A. IsPostBack is a method of System.UI.Web.Page class
B. IsPostBack is a method of System.Web.UI.Page class
C. IsPostBack is a readonly property of System.Web.UI.Page class
Ans: B
88. The number of forms that can be added to a aspx page is.
A. 1
B. 2
C. 3
D. More than 3
Ans: C
89. How do you manage states in asp.net application
A. Session Objects
B. Application Objects
C. Viewstate
D. All of the above
Ans: A
90. Which property of the session object is used to set the local identifier?
A. SessionId
B. LCID
C. Item
D. Key
Ans: D
91. Select the caching type supported by ASP.Net
A. Output Caching
B. DataCaching
C. a and b
D. none of the above
Ans: B
92. Where is the default Session data is stored in ASP.Net?
A. InProcess
B. StateServer
C. Session Object
D. al of the above
Ans: C
93. Select the type Processing model that asp.net simulate
A. Event-driven
B. Static
C. Linear
D. Topdown
Ans: A
94. Does the EnableViewState allows the page to save the users input on a form?
A. Yes
B. No
Ans: A
95. Which DLL translate XML to SQL in IIS?
A. SQLISAPI.dll
B. SQLXML.dll
C. LISXML.dll
D. SQLIIS.dll
Ans: A
96. What is the maximum number of cookies that can be allowed to a web site?
A. 1
B. 10
C. 20
D. More than 30
Ans: A
97. Select the control which does not have any visible interface.
A. Datalist
B. DropdownList
C. Repeater
D. Datagrid
Ans: C
98. How do you explicitly kill a user session?
A. Session.Close( )
B. Session.Discard( )
C. Session.Abandon
D. Session.End
E. Session.Exit
Ans: C
99. Which of the following is not a member of ADODBCommand object?
A. ExecuteReader
B. ExecuteScalar
C. ExecuteStream
D. Open
E. CommandText
Ans: C
100. Which one of the following namespaces contains the definition for IdbConnection?
A. System.Data.Interfaces
B. System.Data.Common
C. System.Data
D. System.Data.Connection
Ans: D
101. In your ASP.NET web application you want to display a list of clients on a Web page. The client list displays 10 clients at a time, and you require the ability to edit the clients. Which Web control is the best choice for this scenario?
A. The DetailsView control
B. The Table control
C. The GridView control
D. The FormView control
Ans: The GridView control
102. How to implement authentication via web.config?
A. Include the authentication element.
B. Include the authorization element.
C. Include the identity element.
D. Include the deny element.
Ans: Include the authorization element.
103. You need to store state data that is accessible to any user who connects to your Web application. Which object should you use?
A. Session
B. Application
C. Response.Cookies
D. Response.ViewState
Ans: Application
104. Explain the significance of Server .MapPath
A. Returns the Virtual Path of the web folder
B. Maps the specified virtual path to Physical path
C. Returns the physical file path that corresponds to virtual specified path
D. All the above
Ans: Returns the physical file path that corresponds to virtual specified path
105. ________ element in the web.config file to run code using the permissions of a specific user
A. element
B. element
C. element
D. element
Ans: element
106. Which of the following is the way to monitor the web application?
A. MMC Event viewers
B. Performance logs
C. Alerts Snap-ins
D. ALL
Ans: ALL
107. For your ASP.NET web application your graphics designer created elaborate images that show the product lines of your company. Some of graphics of the product line are rectangular, circular, and others are having complex shapes. You need to use these images as a menu on your Web site. What is the best way of incorporating these images into your Web site?
A. Use ImageButton and use the x- and y-coordinates that are returned when the user clicks to figure out what product line the user clicked.
B. Use the Table, TableRow, and TableCell controls, break the image into pieces that are displayed in the cells, and use the TableCell control’s Click event to identify the product line that was clicked.
C. Use the MultiView control and break up the image into pieces that can be displayed in each View control for each product line. Use the Click event of the View to identify the product line that was clicked.
D. Use an ImageMap control and define hot spot areas for each of the product lines. Use the PostBackValue to identify the product line that was clicked.
Ans: Use an ImageMap control and define hot spot areas for each of the product lines. Use the PostBackValue to identify the product line that was clicked.
108. An ASP.NET page uses a Datagrid displays employee information.The Web application supports a large number of concurrent users, who will be saving data from the grid back to the database. It is important that the Web application doesn't overwhelm the Web Server.
A. Disable View State and don't use session state
B. Use View State
C. Use URL munging
D. Disable ViewState and use Session State
Ans: Disable View State and don't use session state
109. Which of these data source controls do not implement Caching?
A. LinqDataSource
B. ObjectDataSource
C. SqlDataSource
D. XmlDataSource
Ans: LinqDataSource
110. Which of the following is the default authentication mode for IIS?
A. Anonymous
B. Windows
C. Basic Authentication
D. None
Ans: Anonymous
111. When does Garbage collector run?
A. When application is running low of memory
B. It runs random
C. When application is running for more than 15 minutes
D. None of the above
Ans: When application is running low of memory
112. Which of the following is the way to monitor the web application?
A. MMC Event viewers
B. Performance logs
C. Alerts Snap-ins
D. ALL
Ans: ALL
113. Which of the following languages are used to write server side scripting in ASP.NET?
A. C-sharp
B. VB
C. Both C-sharp and VB
D. C++
Ans: Both C-sharp and VB
114. In which of the following format, output will be rendered to browser When an .aspx page is requested from the web server?
A. JSP
B. WML
C. XML
D. HTML
Ans: HTML
115. Which of the following is true?
A. User controls are displayed correctly in the Visual Studio .NET Designer
B. Custom controls are displayed correctly in VS.Net Designer
C. User and Custom controls are displayed correctly in the Visual Studio .NET Designer.
Ans: Custom controls are displayed correctly in VS.Net Designer
116. How ASP.Net Different from classic ASP?
A. Scripting is separated from the HTML, Code is interpreted seperately
B. Code is separated from the HTML and interpreted Code is interpreted separately
C. Scripting is separated from the HTML, Code is compiled as a DLL, the DLLs can be executed on server
Ans: Scripting is separated from the HTML, Code is compiled as a DLL, the DLLs can be executed on server
117. Which property of the session object is used to set the local identifier?
A. LCID
B. SessionId
C. Key
D. Item
Ans: LCID
118. Which DLL translate XML to SQL in IIS?
A. SQLIIS.dll
B. SQLXML.dll
C. LISXML.dll
D. SQLISAPI.dll
Ans: SQLISAPI.dll
119. Which of the following does not have any visible interface?
A. Datagrid
B. Repeater
C. DropdownList
D. Datalist
Ans: Repeater
120. ________ is not a member of ADODBCommand object.
A. ExecuteReader
B. ExecuteStream
C. ExecuteScalar
D. CommandText
E. Open
Ans: Open
121. Which class can be used to create an XML document from scratch?
A. XmlConvert
B. XmlDocument
C. XmlNew
D. XmlSettings
Ans: XmlDocument
122. Which class can be used to perform data type conversion between .NET data types and XML types?
A. XmlType
B. XmlCast
C. XmlConvert
D. XmlSettings
Ans: XmlConvert
123. For your ASP.NET web application your graphics designer created elaborate images that show the product lines of your company. Some of graphics of the product line are rectangular, circular, and others are having complex shapes. You need to use these images as a menu on your Web site. What is the best way of incorporating these images into your Web site?
A. Use ImageButton and use the x- and y-coordinates that are returned when the user clicks to figure out what product line the user clicked.
B. Use the Table, TableRow, and TableCell controls, break the image into pieces that are displayed in the cells, and use the TableCell control’s Click event to identify the product line that was clicked.
C. Use the MultiView control and break up the image into pieces that can be displayed in each View control for each product line. Use the Click event of the View to identify the product line that was clicked.
D. Use an ImageMap control and define hot spot areas for each of the product lines. Use the PostBackValue to identify the product line that was clicked.
Ans: Use an ImageMap control and define hot spot areas for each of the product lines. Use the PostBackValue to identify the product line that was clicked.
124. In your ASP.NET 2.0 web application you want to display an image that is selected from a collection of images. What approach will you use to implementing this?
A. Use the ImageMap control and randomly select a HotSpot to show or hide.
B. Use the Image control to hold the image and a Calendar control to randomly select a date for each image to be displayed.
C. Use the AdServer control and create an XML file with configuration of the control.
D. Use an ImageButton control to predict randomness of the image to be loaded based on the clicks of the control.
Ans: Use the AdServer control and create an XML file with configuration of the control.
125. Which of the following is a requirement when merging modified data into a DataSet?
A. A primary key must be defined on the DataTable objects
B. The DataSet schemas must match in order to merge
C. The destination DataSet must be empty prior to merging
D. A DataSet must be merged into the same DataSet that created it.
Ans: A primary key must be defined on the DataTable objects
126. Which Kind Of data we can store in viewstate
A. Viewstate can store only serilizable object
B. Viewstate can store anything
C. Viewstate can store onlys string
D. None
Ans: Viewstate can store only serilizable object
127. What is/are the predefined TraceListener(s) in ASP.Net
A. TextWriterTraceListener
B. EventLogTraceListener
C. DefaultTraceListener
D. All the above 1, 2,3
Ans: All the above 1, 2,3
128. We have defined one page_load event in aspx page and same page_load event in code behind who will run first?
A. page_laod event in aspx page
B. page_load event in code-behind
C. both will run simultaneously
D. None
Ans: page_load event in code-behind
129. Which of the following represents the best use of the Table, TableRow, and Table-Cell controls?
A. To create and populate a Table in Design view
B. To create a customized control that needs to display data in a tabular fashion
C. To create and populate a Table with images
D. To display a tabular result set
Ans: To create a customized control that needs to display data in a tabular fashion
130. How to find out what version of ASP.NET I am using on my machine?
A. Response.Write(System.Environment.Version.ToString() );
B. Response.Write(Version.ToString() );
C. Response.Write(System.Version.ToString() );
D. not possible
Ans: Response.Write(System.Environment.Version.ToString() );
131. An ASP.NET page uses a Datagrid displays employee information.The Web application supports a large number of concurrent users, who will be saving data from the grid back to the database. It is important that the Web application doesn't overwhelm the Web Server.
A. Disable View State and don't use session state
B. Use View State
C. Use URL munging
D. Disable ViewState and use Session State
Ans: Disable View State and don't use session state
132. While creating a Web site with the help of Visual Studio 2005 on a remote computer that does not have Front Page Server Extensions installed, which Web site type will you create in Visual Studio 2005?
A. HTTP
B. File
C. FTP
D. All of the above
Ans: HTTP
133. What’s the difference between Response.Write() and Response.Output.Write()?
A. The First one allows you to write formatted output.
B. The latter one allows you to write formatted output.
C. No Difference
D. The latter one allows you to write unformatted output.
Ans: The latter one allows you to write formatted output.
134. If I’m developing an application that must accommodate multiple security levels though secure login and my ASP.NET web application is spanned across three web-servers (using round-robin load balancing) what would be the best approach to maintain login-in state for the users?
A. Maintain the login state security through a database.
B. Maintain the login state security through a Session.
C. Maintain the login state security through a View State.
D. All of the Above
Ans: Maintain the login state security through a database.
135. Where we can assign value to Static read only member variable of a static class?
A. Default constructor
B. Parameterized constructor
C. Global.asax
D. On click of button
Ans: Default constructor
136. Which of these files takes the web application in offline mode?
A. app_offline.html
B. app_offline.htm
C. appoffline.html
D. none of these
Ans: app_offline.htm
137. Which of these classes maps to the tag
A. HtmlCheckBox
B. HtlmInputCheckBox
C. HtmlControl
D. None
Ans: HtlmInputCheckBox
138. In order to prevent a browser from caching a page which of these xstatements should be written?
A. Response.Cache.SetNoStore();
B. Response.Cache.SetNoServerCaching();
C. Response.Cache.SetNoCaching();
D. None of these
Ans: Response.Cache.SetNoStore();
139. Which of these data source controls do not implement Caching?
A. LinqDataSource
B. ObjectDataSource
C. SqlDataSource
D. XmlDataSource
Ans: LinqDataSource
140. By default, ASP.NET store SessionIDs in _________.
A. Cookies
B. Cache
C. Database
D. Global variable
Ans: Cookies
ASP.NET Questions and Answers pdf Download
Read the full article
0 notes
Text
Which of the following is not a tool or technique for managing project team a) Observation and conversation b) Project performance appraisals c) Issue logs d) Social Styles Profile
Need Answer Sheet of this Question paper, contact
www.mbacasestudyanswers.com ARAVIND – 09901366442 – 09902787224
Project Management
Questions:
Multiple Choices: Total Marks: 100
Q1. A ________________ is a temporary endeavor undertaken to create a unique product, service, or result.
a) Program
b) Process
c) Project
d) Portfolio
Q2. Which of the following is not a potential advantage of using good project management?
a) Shorter development times
b) Higher worker morale
c) Lower cost of capital
d) Higher profit margins
Q3. Which of the following is not an attribute of a project?
a) Projects are unique
b) Projects are developed using progressive elaboration
c) Projects have a primary customer or sponsor
d) Projects involve little uncertainty
Q4. Which of the following is not part of the triple constraint of project management?
a) Meeting scope goals
b) Meeting time goals
c) Meeting communications goals
d) Meeting cost goals
Q5. The first stage of any project is
a) Proposal
b) Conceptualization
c) Implementation
d) Management
Q6. __________________ is the application of knowledge, skills, tools and techniques to project activities to meet project requirements.
a) Project management
b) Program management
c) Project portfolio management
d) Requirements management
Q7. Project portfolio management addresses ____________________ goals of an organization, while project management addresses _________________ goals.
a) Strategic, tactical
b) Tactical, strategic
c) Internal, external
d) External, internal
Q8. Several application development projects done for the same functional group might best be managed as part of a
a) Portfolio
b) Program
c) Investment
d) Collaborative
Q9. Which of the following is not one of the top ten skills or competencies of an effective project manager?
a) People skills
b) Leadership
c) Integrity
d) Technical skills
Q10. What is the certification program called that the Project Management Institute provides?
a) Microsoft Certified Project Manager (MCPM)
b) Project Manager Professional (PMP)
c) Project Management Expert (PME)
d) Project Management Mentor (PMM)
Q11. A _________________ is a series of actions directed towards a particular result.
a) Goal
b) Process
c) Plan
d) Project
Q12. ____________________ Processes include coordinating people and other resource to carry out the project plans and produce the products, service, or results of the project or phase.
a) Initiating
b) Planning
c) Executing
d) Monitoring & controlling
Q13. Which process group normally requires the most resources and time?
a) Initiating
b) Planning
c) Executing
d) Monitoring and controlling
Q14. A work breakdown structure, project schedule, and cost estimates are outputs of the process.
a) Initiating
b) Planning
c) Executing
d) Monitoring and controlling
Q15. Which process group includes activities from each of the nine knowledge areas?
a) Initiating
b) Planning
c) Executing
d) Monitoring and controlling
Q16. Project management as a profession is almost unique in having institutions concerned with its development who promote what they term their
a) Body of language
b) Body of knowledge
c) Strategy
d) Work
Q17. Initiating involves developing a project charter and preliminary project scope statement, which are part of the project _____________________ management knowledge.
a) Integration
b) Scope
c) Communications
d) Risk
Q18. A ________________ describes how things should be done, and different organizations often have different ways of doing things.
a) Regulation
b) Process
c) Standard
d) Methodology
Q19. ___________________ involves measuring progress toward project objectives and talking corrective actions.
a) Initiating
b) Planning
c) Executing
d) Monitoring and controlling
Q20. What type of report do project teams create to reflect on what went right with the project?
a) Lessons – learned report
b) Status report
c) Final project report
d) Business case
Q21. Project manager is responsible for
a) Overseeing change
b) Cross functional activities
c) Ever changing set of tasks
d) All above
Q22. Many people use ________________ to have a standard format for preparing various project management documents.
a) Methodologies
b) Templates
c) Project management software
d) Standards
Q23. What is the last step in the four – stage planning process for selecting information technology projects?
a) Information technology strategy planning
b) Business area analysis
c) Project planning
d) Resource allocation
Q24. A new government law requires an organization to report data in anew way. Under which category would a new information system project to provide this data fall?
a) Problem
b) Opportunity
c) Directive
d) Regulation
Q25. A __________________ is a document that formally recognizes the existence of a project and provides direction on the project’s objectives and management.
a) Project charter
b) Preliminary scope statement
c) Business case
d) Project management plan
Q26. ICOM model, which is one of the major roles of project manager, stand for
a) Integrated Constraint of Mechanism
b) Inputs, Outputs, Constraints & Mechanism
c) Inputs, Outputs, Constraints & Money
d) None
Q27. A _______________ often includes sensitive information, so it should not be part of the overall project plan for anyone to see.
a) Business case
b) Project charter
c) Personnel chart
d) Stakeholder analysis
Q28. Which of the following is not a suggestion for performing integrated change control?
a) Use good configuration management
b) Minimize change
c) Establish a formal change control system
d) View project management as a process of constant communication and negotiation
Q29. _______________ refer(s) to all the work involved in creating the products of the projects and processes used to create them.
a) Deliverables
b) Milestones
c) Scope
d) Product development
Q30. Assume you have a project with major categories called planning, analysis, design, and testing. What level of the WBS would these items fall under?
a) 0
b) 1
c) 2
d) 3
Q31. Which of the following is not a best practice that can help in avoiding scope problems on information technology projects?
a) Keep the scope realistic
b) Use off-the-shelf hardware and software whenever possible
c) Follow good project management processes
d) Don’t involve too many users in scope management
Q32. Having ascertains the portfolio of projects obtained objectives for each of them, we have to move to the next stage of the strategy process to balance the objectives
a) Policy deployment
b) Strategy matrix
c) Project performance measurement
d) None
Q33. What major restaurant chain terminated a large project after spending $170 million on it, primarily because they realized the project scope was too much to handle?
a) Burger King
b) Pizza Hut
c) McDonalds
d) Taco Bell
Q34. Scope ____________________ is often achieved by a customer inspection and then sign – off on key deliverables.
a) Verification
b) Validation
c) Completion
d) Close – out
Q35. Project management software helps you develop a _________________, which serves as a basis for creating Gantt charts, assigning resources, and allocating costs.
a) Project plan
b) Schedule
c) WBS
d) Deliverable
Q36. WBS (Work Breakdown Structure) is also known as
a) Chunking
b) Unbundling
c) Both (a) & (b)
d) None
Q37. What is the first process in planning a project schedule?
a) Milestone definition
b) Activity definition
c) Activity resource estimation
d) Activity sequencing
Q38. Predecessors, successes, logical relationships, leads and lags, resource requirements, constraints, imposed dates, and assumptions are all examples of ___________________.
a) Items in an activity list
b) Items on a Gantt chart
c) Milestone attributes
d) Activity attributes
Q39. As the project manager for a software development project, you are helping to develop its schedule. You decide that writing code for a system cannot start until sign off on the analysis work. What type of dependency is this?
a) Technical
b) Mandatory
c) Discretionary
d) External
Q40. You cannot start editing a technical report until someone else completes the first draft. What type of dependency does this represent?
a) Finish – to – start
b) Start – to – start
c) Finish – to – finish
d) Start – to – finish
Q41. …………………. Involves going through the cycle several times to test the effects of the changes make on the outcomes.
a) Planning
b) Strategy
c) Iterative
d) None
Q42. Above figure shows two activities A & B; B cannot start until A finished and the times for A & B are 5 and 7 days respectively. This logic is known as
a) Dependency
b) Precedence
c) Freedom
d) None
Q43. In the above figure calculate the EET (earliest event time) at 20.
a) 10
b) 20
c) 5
d) 25
e) 10
f) 0
g) 20
h) 0
i) A
j) 5Days
k) 12
l) 3
m) A B
n) 5Days 7Days
Q44. What symbol on a Gantt chart represents a slipped milestone?
a) A black arrow
b) A white arrow
c) A black diamond
d) A white diamond
Q45. What type of diagram shows planned and actual project schedule information?
a) A network
b) A Gantt chart
c) A Tracking
d) A milestone chart
Q46. ____________________ is a network diagramming technique used to predict total project duration.
a) PERT
b) A Gantt chart
c) Critical path method
d) Crashing
Q47. Which of the following statement is false?
a) “Growing grass” was on the critical path for a large theme park project.
b) The critical path is the series of activities that determine the earliest time by which a project can be completed.
c) A forward pass through a project network diagram determines the early start and early finish dates for each activity.
d) Fast tracking is a technique for marking cost and schedule trade-offs to obtain the
obtain the greatest amount of schedule comparison for the least incremental cost.
Q48. _____________________ is a method of scheduling that considers limited resources when creating a project schedule and includes buffers to protect the project completion date.
a) Parkinson’s Law
b) Murphy’s Law
c) Critical path analysis
d) Critical chain scheduling
Q49. _______________ is a resource scarified or foregone to achieve a specific objective or something given up in exchange.
a) Money
b) Liability
c) Trade
d) Cost
Q50. What is main goal of project cost management?
a) To complete a project for as little cost as possible
b) To complete a project within an approved budget
c) To provide truthful and accurate cost information on projects
d) To ensure that an organization’s money is used widely
Q51. A fundamental of ‘Theory of Constraints’ (TOC) is to manage systems by focusing on the constraints, termed as
a) Watermark
b) Bottleneck
c) Tick-sheet
d) None
Q52. “An activity will expand to fill the time available”; it is
a) Newton’s Law
b) Parkinson’s Law
c) Einstein’s Law
d) None
Q53. Which of the following is not a key output of project cost management?
a) A cost estimate
b) A cost management plan
c) Updates to the cost management plan
d) A cost baseline
Q54. If a company loses $5 for every $100 in revenue for a certain product, what is profit margin for that product?
a) -5 percent
b) 5 percent
c) -$5
d) $5
Q55. __________________ reserves allow for future situations that are unpredictable.
a) Contingency
b) Financial
c) Management
d) Baseline
Q56. You are preparing a cost estimate for a building based on its location, purpose, number of square feet, and other characteristics. What cost estimating technique are you using?
a) Parametric
b) Analogous
c) Bottom – up
d) Top – down
Q57. ______________ involves allocating the project cost estimate to individual work items over time.
a) Reserve analysis
b) Life cycle costing
c) Project cost budgeting
d) Earned value analysis
Q58. _________________ is a project performance measurement technique that integrates scope time, and cost data.
a) Reserve analysis
b) Life cycle costing
c) Project cost budgeting
d) Earned value analysis
Q59. If the actual cost for a WBS item is $1500 and its earned value was $2000, what is its cost variance, and is it under or over budget?
a) The cost variance is -$500, which is over budget
b) The cost variance is -$500, which is under budget
c) The cost variance is $500, which is over budget
d) The cost variance is $500, which is under budget
Q60. If a project is halfway completed and its schedule performance index is 110% and its cost performance index is 95%, how is it progressing?
a) It is ahead of schedule and under budget
b) It is ahead of schedule and over budget
c) It is behind schedule and under budget
d) It is behind schedule and over budget
Q61. To determine the cost of particular element in advance of the project, which technique can be employed?
a) Parametric estimating
b) As…………but…………s
c) Forecasts
d) All above
Q62. _______________ is the degree to which a set of inherent characteristics fulfills requirements.
a) Quality
b) Conformance to requirements
c) Fitness for use
d) Reliability
Q63. What is the purpose of project quality management?
a) To produce the highest quality products and services possible
b) To ensure that appropriate quality standards are met
c) To ensure that the project will satisfy the needs for which it was undertaken
d) All of the above
Q64. _______________ generates ideas for quality improvements by comparing specific project practices or product characteristics to those of other projects or products within or outside the performing organization.
a) Quality audits
b) Design of experiments
c) Six Sigma
d) Benchmarking
Q65. What tool could you use to determine whether a process is in control or out of control?
a) A cause – and – effect diagram
b) A control chart
c) A run chart
d) A scatter chart
Q66. Complication to the critical path represents the formation of compound series of activities often involving different paths which has been termed
a) The critical chain
b) The critical path
c) TOC
d) Resource path
Q67. Six Sigma’s target for perfection is the achievement of no more than ________________ defects, errors, or mistakes per million opportunities.
a) 6
b) 9
c) 3.4
d) 1
Q68. The seven run rule states that if seven data points in a row on a control chart are all below the mean, above the means, or all increasing or decreasing, then the process needs to be examined for _________________ problems.
a) Random
b) Non – random
c) Six Sigma
d) Quality
Q69. What is the preferred order for performing testing on information technology projects?
a) Unit testing, integration testing, system testing, user acceptance testing
b) Unit testing, system testing, integration testing, user acceptance testing
c) Unit testing, system testing, user acceptance testing, integration testing
d) Unit testing, integration testing, user acceptance testing, system testing
Q70. ___________________ is known for his work on quality control in Japan and developed the 14 points for Management in his text Out of the Crisis.
a) Juran
b) Deming
c) Crosby
d) Ishikawa
Q71. The theory of constraints (TOC) is successfully applied in
a) Planning
b) Checking
c) Manufacturing
d) Controlling
Q72. PMI’s OPM3 is an example of a ____________________ model or framework for helping organization improve their processes and systems.
a) Benchmarking
b) Six Sigma
c) Maturity
d) Quality
Q73. Which of the following is not part of project human resource management?
a) Resource estimating
b) Acquiring the project team
c) Developing the project team
d) Managing the project team
Q74. _________________ causes people to participate in an activity for their own enjoyment.
a) Intrinsic motivation
b) Extrinsic motivation
c) Self motivation
d) Social motivation
Q75. At the bottom of Maslow’s pyramid or hierarchy of needs are _____________ needs.
a) Self – actualization
b) Esteem
c) Safety
d) Physiological
Q76. ________________ power is based on a person’s individual charisma.
a) Affiliation
b) Referent
c) Personality
d) Legitimate
Q77. What technique can you use to resolve resource conflicts by delaying tasks?
a) Resource loading
b) Resource leveling
c) Critical path analysis
d) Over allocation
Q78. Which of the following is not a tool or technique for managing project team?
a) Observation and conversation
b) Project performance appraisals
c) Issue logs
d) Social Styles Profile
Q79. What do many experts agree is the greatest threat to the success of any project?
a) Lack of proper funding
b) A failure to communicate
c) Poor listening skills
d) Inadequate staffing
Q80. Which communication skill is most important for information technology professionals for career advancement?
a) Writing
b) Listening
c) Speaking
d) Using communication technologies
[/nextpage]
[nextpage title=”Question Papers” ]
Q81. Which of the following is not a process in project communication management?
a) Information planning
b) Information distribution
c) Performance reporting
d) Managing stakeholders
Q82. A building may not be constructed unless the planning permission for it has been obtained, this is the
a) Legal constraint
b) Quality constraint
c) Cost constraint
d) Logic constraint
Q83. A ________________ report describes where the project stands at a specific point in time.
a) Status
b) Performance
c) Forecast
d) Earned value
Q84. __________________ is an uncertainly that can have a negative or positive effect on meeting project objectives.
a) Risk utility
b) Risk tolerance
c) Risk management
d) Risk
Q85. A person who is a risk – ______________ receives greater satisfaction when more payoffs is at stake and is willing to pay a penalty to take risks.
a) Averse
b) Seeking
c) Neutral
d) Aware
Q86. Which risk management process involves prioritizing based on their probability and impact of occurrence?
a) Risk management planning
b) Risk identification
c) Qualitative risk analysis
d) Quantitative risk analysis
Q87. The 7-S framework of project management issues was promoted by
a) McJonald and Co.
b) McKinsly and Co.
c) J & K Co.
d) None
Q88. Your project involves using a new release of a software application, but if that release is not available, your team has ______________ plans to use the current release.
a) Contingency
b) Fallback
c) Reserve
d) Mitigation
Q89. A risk _________________ is a document that contains results of various risk management processes, often displayed in a table or spreadsheet format.
a) Management plan
b) Register
c) Breakdown structure
d) Probability / impact matrix
Q90. Your project team has decided not to use an upcoming release of software because it might cause your schedule to slip. Which negative risk response strategy are you using?
a) Avoidance
b) Acceptance
c) Transference
d) Mitigation
Q91. For non critical activities, network diagrams build in …………………………. at the start of activities.
a) Temporary
b) Buffer
c) Slack
d) Anywhere
Q92. If a project being undertaken by a particular project team, then these are referred as
a) Resource capability
b) Resource capacity
c) Resource calendar
d) Resource pool
Q93. The term ‘hedgehog syndrome’ means
a) Management problem
b) Solving problem
c) Repetition of problem
d) Find out a problem
Q94. What is the first procurement process?
a) Planning contracting
b) Planning purchasing and acquisitions
c) Requesting seller responses
d) Procurement management planning
Q95. The _____________ is the point at which the contractor assumes total responsibility for each additional dollar of contract cost.
a) A breakeven point
b) Share ratio point
c) Point of reconciliation
d) Point of total assumption
Q96. We’re standing on this hill here. We want to be on that hill over there, this is
a) View
b) Vision
c) Mission
d) Aim
Q97. A ______________________ is a document prepared by a seller when there are different approaches for meeting buyer needs.
a) RFP
b) RFQ
c) Proposal
d) Quote
Q98. Buyers often prepare a ______________________ list when selecting a seller to make this process more manageable.
a) Preferred
b) Short
c) Qualified suppliers
d) BAFO
Q99. A proposal evaluation sheet is an example of a(n) ______________________.
a) RFP
b) NPV analysis
c) Earned value analysis
d) Weighted scoring model
Q100. __________________ is a term used to describe various procurement functions that are now done electronically.
a) E – procurement
b) eBay
c) E – commerce
d) EMV
Need Answer Sheet of this Question paper, contact
www.mbacasestudyanswers.com ARAVIND – 09901366442 – 09902787224
;�=T��
0 notes
Text
[PDF and VCE] CertBus Latest Cisco 210-260 Exam Practice Materials Free Downloading
We promise that you should not worry about Hotest 210-260 pdf dumps exam at all. We, CertBus, are here to provide guidance to help you pass the CCNA Security Jun 21,2017 Latest 210-260 free download Implementing Cisco Network Security exam and get the Cisco certification. CertBus offers the latest real Hotest 210-260 practice Implementing Cisco Network Security exam PDF and VCE dumps. All the CCNA Security Latest 210-260 practice exam questions and answers are the latest and cover every aspect of Newest 210-260 vce exam.
CertBus – help candidates on all 210-260 certification exams preparation. pass 210-260 certification exams, get it certifications easily. CertBus braindumps CertBus dumps free download. CertBus free certification 210-260 exam | CertBus practice 210-260 exams | CertBus test 210-260 questions. reliable 210-260 certification exams preparation – latest braindumps at CertBus.
We CertBus has our own expert team. They selected and published the latest 210-260 preparation materials from Cisco Official Exam-Center: http://ift.tt/2tOlzqB
QUESTION NO:7
Refer to the exhibit.
authentication event fail action next-method
authentication event no-response action authorize vlan 101
authentication order mad dotlx webauth
authentication priority dotlx mab
authentication port-control auto
dotlx pae authenticator
If a supplicant supplies incorrect credentials for the authentication methods configured on the switch, how
will the switch respond?
A. The switch will cycle through the configured authentication methods indefinitely
B. The supplicant will fail to advance beyond the webauth method
C. The authentication attempt will time out and the switch will place the port into the unauthorized state
D. The authentication attempt will time out and the switch will place the port into VLAN 101
Correct Answer: B
QUESTION NO:1
Which SOURCEFIRE logging action should you choose to record the most detail about a connection?
A. Enable logging at the beginning of the session
B. Enable logging at the end of the session
C. Enable alerts via SNMP to log events off-box
D. Enable eStreamer to log events off-boxx
Correct Answer: B
QUESTION NO:17
What are the two purposes of the Internet Key Exchange in an IPsec VPN? (Choose two)
A. The Internet Key Exchange protocol establishes security associations
B. The Internet Key Exchange protocol provides data confidentiality
C. The Internet Key Exchange protocol provides replay detection
D. The internet Key Exchange protocol is responsible for mutual authentication
Correct Answer: AD
QUESTION NO:27
Which of the following are features of IPsec transport mode? (Choose three)
A. IPsec transport mode is used between end stations
B. IPsec transport mode is used between gateways
C. IPsec transport mode supports multicast
D. IPsec transport mode supports unicast
E. IPsec transport mode encrypts only the payload
F. IPsec transport mode encrypts the entire packet
Correct Answer: ADE
QUESTION NO:4
Which statement about communication over failover interfaces is true?
A. All information that is sent over the failover interface is send as clear text, but the stateful failover link is
encrypted by default
B. All information that is sent over the failover and stateful failover interfaces is encrypted by default
C. All information that is sent over the failover and stateful failover interfaces is sent as clear text by
default
D. Usernames, password and preshared keys are encrypted by default when they are sent over the
failover and stateful failover interfaces, but other information is in clear text
Correct Answer: C
QUESTION NO:37
What is the effect of the given command sequence?
crypto map mymap 20 match address 201
access-list 201 permit ip 10.10.10.0 255.255.255.0 10.100.100.0 255.255.255.0
A. It defines IPSec policy for traffic sourced from 10.10.10.0/24 with a destination of 10.100.100.0/24
B. It defines IPSec policy for traffic sourced from 10.100.100.0/24 with a destination of 10.10.10.0/24
C. It defines IKE policy for traffic sourced from 10.10.10.0/24 with a destination of 10.100.100.0/24
D. It defines IKE policy for traffic sourced from 10.100.100.0/24 with a destination of 10.10.10.0/24
Correct Answer: A
QUESTION NO:23
What is a possible reason for the error message?
Router(config)#aaa server?% Unrecognized command
A. The command syntax requires a space after the word “server”
B. The command is invalid on the target device
C. The router is already running the latest operating system
D. The router is a new device on which the aaa new-model command must be applied before continuing
Correct Answer: D
QUESTION NO:6
How many crypto map sets can you apply to a router interface?
A. 3
B. 2
C. 4
D. 1
Correct Answer: D
QUESTION NO:36
What are two default Cisco IOS privilege levels? (Choose two)
A. 0
B. 5
C. 1
D. 7
E. 10
F. 15
Correct Answer: CF
QUESTION NO:29
Which command verifies phase 1 of an IPsec VPN on a Cisco router?
A. show crypto map
B. show crypto ipsec sa
C. show crypto isakmp sa
D. show crypto engine connection active
Correct Answer: C
CertBus exam braindumps are pass guaranteed. We guarantee your pass for the 210-260 exam successfully with our Cisco materials. CertBus Implementing Cisco Network Security exam PDF and VCE are the latest and most accurate. We have the best Cisco in our team to make sure CertBus Implementing Cisco Network Security exam questions and answers are the most valid. CertBus exam Implementing Cisco Network Security exam dumps will help you to be the Cisco specialist, clear your 210-260 exam and get the final success.
210-260 Latest questions and answers on Google Drive(100% Free Download): http://ift.tt/2pqlJSi
210-260 Cisco exam dumps (100% Pass Guaranteed) from CertBus: http://ift.tt/2tOlzqB [100% Exam Pass Guaranteed]
Why select/choose CertBus?
Millions of interested professionals can touch the destination of success in exams by certbus.com. products which would be available, affordable, updated and of really best quality to overcome the difficulties of any course outlines. Questions and Answers material is updated in highly outclass manner on regular basis and material is released periodically and is available in testing centers with whom we are maintaining our relationship to get latest material.
Brand Certbus Testking Pass4sure Actualtests Others Price $45.99 $124.99 $125.99 $189 $69.99-99.99 Up-to-Date Dumps Free 365 Days Update Real Questions Printable PDF Test Engine One Time Purchase Instant Download Unlimited Install 100% Pass Guarantee 100% Money Back Secure Payment Privacy Protection
Published by CertBus http://ift.tt/2ttPDZt
0 notes
Link
Colleges That Require Virus-Screening Tech Struggle to Say Whether It Works Before the University of Idaho welcomed students back to campus last fall, it made a big bet on new virus-screening technology. The university spent $90,000 installing temperature-scanning stations, which look like airport metal detectors, in front of its dining and athletic facilities in Moscow, Idaho. When the system clocks a student walking through with an unusually high temperature, the student is asked to leave and go get tested for Covid-19. But so far the fever scanners, which detect skin temperature, have caught fewer than 10 people out of the 9,000 students living on or near campus. Even then, university administrators could not say whether the technology had been effective because they have not tracked students flagged with fevers to see if they went on to get tested for the virus. The University of Idaho is one of hundreds of colleges and universities that adopted fever scanners, symptom checkers, wearable heart-rate monitors and other new Covid-screening technologies this school year. Such tools often cost less than a more validated health intervention: frequent virus testing of all students. They also help colleges showcase their pandemic safety efforts. But the struggle at many colleges to keep the virus at bay has raised questions about the usefulness of the technologies. A New York Times effort has recorded more than 530,000 virus cases on campuses since the start of the pandemic. One problem is that temperature scanners and symptom-checking apps cannot catch the estimated 40 percent of people with the coronavirus who do not have symptoms but are still infectious. Temperature scanners can also be wildly inaccurate. The Centers for Disease Control and Prevention has cautioned that such symptom-based screening has only “limited effectiveness.” The schools have a hard time saying whether — or how well — the new devices have worked. Many universities and colleges, including prominent research institutions, are not rigorously studying effectiveness. “So why are we bothering?” said Bruce Schneier, a prominent security technologist who has described such screening systems as “security theater” — that is, tools that make people feel better without actually improving their safety. “Why spend the money?” More than 100 schools are using a free virus symptom-checking app, called CampusClear, that can clear students to enter campus buildings. Others are asking students to wear symptom-monitoring devices that can continuously track vital signs like skin temperature. And some have adapted the ID card swiping systems they use to admit students into dorms, libraries and gyms as tools for tracing potential virus exposures. Administrators at Idaho and other universities said their schools were using the new tech, along with policies like social distancing, as part of larger campus efforts to hinder the virus. Some said it was important for their schools to deploy the screening tools even if they were only moderately useful. At the very least, they said, using services like daily symptom-checking apps may reassure students and remind them to be vigilant about other measures, like mask wearing. Some public health experts said it was understandable that colleges had not methodically assessed the technology’s effectiveness against the coronavirus. After all, they said, schools are unaccustomed to frequently screening their entire campus populations for new infectious diseases. Even so, some experts said they were troubled that universities lacked important information that might help them make more evidence-based decisions on health screening. “It’s a massive data vacuum,” said Saskia Popescu, an infectious-disease epidemiologist who is an assistant professor at George Mason University. “The moral of the story is you can’t just invest in this tech without having a validation process behind it.” Other medical experts said increased surveillance of largely healthy college students seemed unduly intrusive, given that symptom checkers have limited usefulness and the effectiveness of wearable health monitors against Covid-19 is not yet known. Updated March 2, 2021, 10:34 a.m. ET The introduction of campus screening tools has often been bumpy. Last fall, the University of Missouri began requiring all students, faculty and staff to use CampusClear, a free app that asks users about possible symptoms, like high temperature or loss of smell. Users who say they have no symptoms then receive a “Good to Go!” notification that can clear them to enter campus buildings. The school initially did not enforce the use of CampusClear at building entrances, however, and some students used the app only infrequently, according to reporting by The Missourian, the campus newspaper. In October, the university began requiring people to show their app pass code to enter certain buildings, like the student center and library. The university has promoted the app as a tool to help educate students. But how effective it has been at hindering coronavirus outbreaks on campus is unknown. A spokesman for the University of Missouri said the school was unable to provide usage data on CampusClear — including the number of students who had reported possible symptoms through the app and later tested positive for the virus — requested by a Times reporter. Jason Fife, the marketing director at Ivy.ai, the start-up behind CampusClear, said nearly 425,000 people at about 120 colleges and universities used the app last semester, generating about 9.8 million user reports. Many schools, he noted, use data from the app not to follow individual virus cases but to look for symptom trends on their campuses. Ivy.ai, however, cannot gauge the app’s effectiveness as a virus-screening tool, he said. For privacy reasons, the company does not track individual users who report symptoms and later test positive for the infection. At some universities, administrators acknowledged that the tech they adopted this school year did not pan out the way they had hoped. Bridgewater State University in Bridgewater, Mass., introduced two tools last semester that recorded students’ whereabouts in case they later developed virus infections and administrators needed to trace their contacts. One system logged students’ locations every time they swiped their ID cards to enter campus buildings. The other asked students to scan printed-out QR codes posted at certain locations around campus. By the end of the semester, however, only about one-third of the 1,200 students on campus were scanning the bar codes. Ethan Child, a Bridgewater senior, said he had scanned the QR codes but also skipped them when walking by in the rain. “I think it’s reasonable to ask students to do it — whether or not they’ll actually do it is another thing,” he said. “People might just pass it by.” Class Disrupted Updated March 2, 2021 The latest on how the pandemic is reshaping education. Administrators discovered that the key to hindering coronavirus outbreaks was not technology but simply frequent testing — once a week, for on-campus students — along with contact tracing, said Chris Frazer, the executive director of the university’s wellness center. “I’m glad we didn’t spend an exorbitant amount of money” on tech tools, Dr. Frazer said. “We found what we need is tests and more tests.” The location-tracking tools ultimately proved most useful for “peace of mind,” he added, and to confirm the findings of contact tracers, who often learned much more about infected students’ activities by calling them than by examining their location logs. Other schools that discovered location tracking was not a useful pandemic safety tool decided not to deploy it at all. At Oklahoma State University, in Stillwater, administrators said they had planned to log students’ locations when they used campus Wi-Fi for possible later use in contact tracing. But the school never introduced the system, said Chris Barlow, the school’s health services director, partly because administrators realized that many students had contracted the virus off campus, in situations where public health measures like mask wearing were not followed. At the University of Idaho and other schools, administrators described devices like fever scanners as add-ons to larger campus safety efforts involving student testing and measures like social distancing. Last fall, for instance, the University of Idaho tested its students for the virus at the beginning and middle of the semester, with some random testing as well. The school also used a wastewater testing program to identify an impending virus outbreak at fraternity and sorority houses, proactively quarantining more than a dozen chapters before cases could spread widely through the community. “We got out in front of it early,” C. Scott Green, the president of the University of Idaho, said. “We were able to isolate those that were sick, and we got back under control.” Still, there were hiccups. The university required food service employees who worked at the dining hall to undergo temperature checks using hand-held scanners. But several developed virus infections anyway, and the university was forced to temporarily close the dining hall over a weekend for deep cleaning. As for the free-standing temperature-scanning stations, Mr. Green himself has experienced their limitations. He said one mistakenly stopped him from entering an athletic building right after he got out of a hot car. Source link Orbem News #Colleges #require #Struggle #Tech #VirusScreening #Works
0 notes
Link
Colleges That Require Virus-Screening Tech Struggle to Say Whether It Works Before the University of Idaho welcomed students back to campus last fall, it made a big bet on new virus-screening technology. The university spent $90,000 installing temperature-scanning stations, which look like airport metal detectors, in front of its dining and athletic facilities in Moscow, Idaho. When the system clocks a student walking through with an unusually high temperature, the student is asked to leave and go get tested for Covid-19. But so far the fever scanners, which detect skin temperature, have caught fewer than 10 people out of the 9,000 students living on or near campus. Even then, university administrators could not say whether the technology had been effective because they have not tracked students flagged with fevers to see if they went on to get tested for the virus. The University of Idaho is one of hundreds of colleges and universities that adopted fever scanners, symptom checkers, wearable heart-rate monitors and other new Covid-screening technologies this school year. Such tools often cost less than a more validated health intervention: frequent virus testing of all students. They also help colleges showcase their pandemic safety efforts. But the struggle at many colleges to keep the virus at bay has raised questions about the usefulness of the technologies. A New York Times effort has recorded more than 530,000 virus cases on campuses since the start of the pandemic. One problem is that temperature scanners and symptom-checking apps cannot catch the estimated 40 percent of people with the coronavirus who do not have symptoms but are still infectious. Temperature scanners can also be wildly inaccurate. The Centers for Disease Control and Prevention has cautioned that such symptom-based screening has only “limited effectiveness.” The schools have a hard time saying whether — or how well — the new devices have worked. Many universities and colleges, including prominent research institutions, are not rigorously studying effectiveness. “So why are we bothering?” said Bruce Schneier, a prominent security technologist who has described such screening systems as “security theater” — that is, tools that make people feel better without actually improving their safety. “Why spend the money?” More than 100 schools are using a free virus symptom-checking app, called CampusClear, that can clear students to enter campus buildings. Others are asking students to wear symptom-monitoring devices that can continuously track vital signs like skin temperature. And some have adapted the ID card swiping systems they use to admit students into dorms, libraries and gyms as tools for tracing potential virus exposures. Administrators at Idaho and other universities said their schools were using the new tech, along with policies like social distancing, as part of larger campus efforts to hinder the virus. Some said it was important for their schools to deploy the screening tools even if they were only moderately useful. At the very least, they said, using services like daily symptom-checking apps may reassure students and remind them to be vigilant about other measures, like mask wearing. Some public health experts said it was understandable that colleges had not methodically assessed the technology’s effectiveness against the coronavirus. After all, they said, schools are unaccustomed to frequently screening their entire campus populations for new infectious diseases. Even so, some experts said they were troubled that universities lacked important information that might help them make more evidence-based decisions on health screening. “It’s a massive data vacuum,” said Saskia Popescu, an infectious-disease epidemiologist who is an assistant professor at George Mason University. “The moral of the story is you can’t just invest in this tech without having a validation process behind it.” Other medical experts said increased surveillance of largely healthy college students seemed unduly intrusive, given that symptom checkers have limited usefulness and the effectiveness of wearable health monitors against Covid-19 is not yet known. Updated March 2, 2021, 9:30 a.m. ET The introduction of campus screening tools has often been bumpy. Last fall, the University of Missouri began requiring all students, faculty and staff to use CampusClear, a free app that asks users about possible symptoms, like high temperature or loss of smell. Users who say they have no symptoms then receive a “Good to Go!” notification that can clear them to enter campus buildings. The school initially did not enforce the use of CampusClear at building entrances, however, and some students used the app only infrequently, according to reporting by The Missourian, the campus newspaper. In October, the university began requiring people to show their app pass code to enter certain buildings, like the student center and library. The university has promoted the app as a tool to help educate students. But how effective it has been at hindering coronavirus outbreaks on campus is unknown. A spokesman for the University of Missouri said the school was unable to provide usage data on CampusClear — including the number of students who had reported possible symptoms through the app and later tested positive for the virus — requested by a Times reporter. Jason Fife, the marketing director at Ivy.ai, the start-up behind CampusClear, said nearly 425,000 people at about 120 colleges and universities used the app last semester, generating about 9.8 million user reports. Many schools, he noted, use data from the app not to follow individual virus cases but to look for symptom trends on their campuses. Ivy.ai, however, cannot gauge the app’s effectiveness as a virus-screening tool, he said. For privacy reasons, the company does not track individual users who report symptoms and later test positive for the infection. At some universities, administrators acknowledged that the tech they adopted this school year did not pan out the way they had hoped. Bridgewater State University in Bridgewater, Mass., introduced two tools last semester that recorded students’ whereabouts in case they later developed virus infections and administrators needed to trace their contacts. One system logged students’ locations every time they swiped their ID cards to enter campus buildings. The other asked students to scan printed-out QR codes posted at certain locations around campus. By the end of the semester, however, only about one-third of the 1,200 students on campus were scanning the bar codes. Ethan Child, a Bridgewater senior, said he had scanned the QR codes but also skipped them when walking by in the rain. “I think it’s reasonable to ask students to do it — whether or not they’ll actually do it is another thing,” he said. “People might just pass it by.” Class Disrupted Updated March 1, 2021 The latest on how the pandemic is reshaping education. Administrators discovered that the key to hindering coronavirus outbreaks was not technology but simply frequent testing — once a week, for on-campus students — along with contact tracing, said Chris Frazer, the executive director of the university’s wellness center. “I’m glad we didn’t spend an exorbitant amount of money” on tech tools, Dr. Frazer said. “We found what we need is tests and more tests.” The location-tracking tools ultimately proved most useful for “peace of mind,” he added, and to confirm the findings of contact tracers, who often learned much more about infected students’ activities by calling them than by examining their location logs. Other schools that discovered location tracking was not a useful pandemic safety tool decided not to deploy it at all. At Oklahoma State University, in Stillwater, administrators said they had planned to log students’ locations when they used campus Wi-Fi for possible later use in contact tracing. But the school never introduced the system, said Chris Barlow, the school’s health services director, partly because administrators realized that many students had contracted the virus off campus, in situations where public health measures like mask wearing were not followed. At the University of Idaho and other schools, administrators described devices like fever scanners as add-ons to larger campus safety efforts involving student testing and measures like social distancing. Last fall, for instance, the University of Idaho tested its students for the virus at the beginning and middle of the semester, with some random testing as well. The school also used a wastewater testing program to identify an impending virus outbreak at fraternity and sorority houses, proactively quarantining more than a dozen chapters before cases could spread widely through the community. “We got out in front of it early,” C. Scott Green, the president of the University of Idaho, said. “We were able to isolate those that were sick, and we got back under control.” Still, there were hiccups. The university required food service employees who worked at the dining hall to undergo temperature checks using hand-held scanners. But several developed virus infections anyway, and the university was forced to temporarily close the dining hall over a weekend for deep cleaning. As for the free-standing temperature-scanning stations, Mr. Green himself has experienced their limitations. He said one mistakenly stopped him from entering an athletic building right after he got out of a hot car. Source link Orbem News #Colleges #require #Struggle #Tech #VirusScreening #Works
0 notes
Link
Colleges That Require Virus-Screening Tech Struggle to Say Whether It Works Before the University of Idaho welcomed students back to campus last fall, it made a big bet on new virus-screening technology. The university spent $90,000 installing temperature-scanning stations, which look like airport metal detectors, in front of its dining and athletic facilities in Moscow, Idaho. When the system clocks a student walking through with an unusually high temperature, the student is asked to leave and go get tested for Covid-19. But so far the fever scanners, which detect skin temperature, have caught fewer than 10 people out of the 9,000 students living on or near campus. Even then, university administrators could not say whether the technology had been effective because they have not tracked students flagged with fevers to see if they went on to get tested for the virus. The University of Idaho is one of hundreds of colleges and universities that adopted fever scanners, symptom checkers, wearable heart-rate monitors and other new Covid-screening technologies this school year. Such tools often cost less than a more validated health intervention: frequent virus testing of all students. They also help colleges showcase their pandemic safety efforts. But the struggle at many colleges to keep the virus at bay has raised questions about the usefulness of the technologies. A New York Times effort has recorded more than 530,000 virus cases on campuses since the start of the pandemic. One problem is that temperature scanners and symptom-checking apps cannot catch the estimated 40 percent of people with the coronavirus who do not have symptoms but are still infectious. Temperature scanners can also be wildly inaccurate. The Centers for Disease Control and Prevention has cautioned that such symptom-based screening has only “limited effectiveness.” The schools have a hard time saying whether — or how well — the new devices have worked. Many universities and colleges, including prominent research institutions, are not rigorously studying effectiveness. “So why are we bothering?” said Bruce Schneier, a prominent security technologist who has described such screening systems as “security theater” — that is, tools that make people feel better without actually improving their safety. “Why spend the money?” More than 100 schools are using a free virus symptom-checking app, called CampusClear, that can clear students to enter campus buildings. Others are asking students to wear symptom-monitoring devices that can continuously track vital signs like skin temperature. And some have adapted the ID card swiping systems they use to admit students into dorms, libraries and gyms as tools for tracing potential virus exposures. Administrators at Idaho and other universities said their schools were using the new tech, along with policies like social distancing, as part of larger campus efforts to hinder the virus. Some said it was important for their schools to deploy the screening tools even if they were only moderately useful. At the very least, they said, using services like daily symptom-checking apps may reassure students and remind them to be vigilant about other measures, like mask wearing. Some public health experts said it was understandable that colleges had not methodically assessed the technology’s effectiveness against the coronavirus. After all, they said, schools are unaccustomed to frequently screening their entire campus populations for new infectious diseases. Even so, some experts said they were troubled that universities lacked important information that might help them make more evidence-based decisions on health screening. “It’s a massive data vacuum,” said Saskia Popescu, an infectious-disease epidemiologist who is an assistant professor at George Mason University. “The moral of the story is you can’t just invest in this tech without having a validation process behind it.” Other medical experts said increased surveillance of largely healthy college students seemed unduly intrusive, given that symptom checkers have limited usefulness and the effectiveness of wearable health monitors against Covid-19 is not yet known. Updated March 2, 2021, 5:01 a.m. ET The introduction of campus screening tools has often been bumpy. Last fall, the University of Missouri began requiring all students, faculty and staff to use CampusClear, a free app that asks users about possible symptoms, like high temperature or loss of smell. Users who say they have no symptoms then receive a “Good to Go!” notification that can clear them to enter campus buildings. The school initially did not enforce the use of CampusClear at building entrances, however, and some students used the app only infrequently, according to reporting by The Missourian, the campus newspaper. In October, the university began requiring people to show their app pass code to enter certain buildings, like the student center and library. The university has promoted the app as a tool to help educate students. But how effective it has been at hindering coronavirus outbreaks on campus is unknown. A spokesman for the University of Missouri said the school was unable to provide usage data on CampusClear — including the number of students who had reported possible symptoms through the app and later tested positive for the virus — requested by a Times reporter. Jason Fife, the marketing director at Ivy.ai, the start-up behind CampusClear, said nearly 425,000 people at about 120 colleges and universities used the app last semester, generating about 9.8 million user reports. Many schools, he noted, use data from the app not to follow individual virus cases but to look for symptom trends on their campuses. Ivy.ai, however, cannot gauge the app’s effectiveness as a virus-screening tool, he said. For privacy reasons, the company does not track individual users who report symptoms and later test positive for the infection. At some universities, administrators acknowledged that the tech they adopted this school year did not pan out the way they had hoped. Bridgewater State University in Bridgewater, Mass., introduced two tools last semester that recorded students’ whereabouts in case they later developed virus infections and administrators needed to trace their contacts. One system logged students’ locations every time they swiped their ID cards to enter campus buildings. The other asked students to scan printed-out QR codes posted at certain locations around campus. By the end of the semester, however, only about one-third of the 1,200 students on campus were scanning the bar codes. Ethan Child, a Bridgewater senior, said he had scanned the QR codes but also skipped them when walking by in the rain. “I think it’s reasonable to ask students to do it — whether or not they’ll actually do it is another thing,” he said. “People might just pass it by.” Class Disrupted Updated March 1, 2021 The latest on how the pandemic is reshaping education. Administrators discovered that the key to hindering coronavirus outbreaks was not technology but simply frequent testing — once a week, for on-campus students — along with contact tracing, said Chris Frazer, the executive director of the university’s wellness center. “I’m glad we didn’t spend an exorbitant amount of money” on tech tools, Dr. Frazer said. “We found what we need is tests and more tests.” The location-tracking tools ultimately proved most useful for “peace of mind,” he added, and to confirm the findings of contact tracers, who often learned much more about infected students’ activities by calling them than by examining their location logs. Other schools that discovered location tracking was not a useful pandemic safety tool decided not to deploy it at all. At Oklahoma State University, in Stillwater, administrators said they had planned to log students’ locations when they used campus Wi-Fi for possible later use in contact tracing. But the school never introduced the system, said Chris Barlow, the school’s health services director, partly because administrators realized that many students had contracted the virus off campus, in situations where public health measures like mask wearing were not followed. At the University of Idaho and other schools, administrators described devices like fever scanners as add-ons to larger campus safety efforts involving student testing and measures like social distancing. Last fall, for instance, the University of Idaho tested its students for the virus at the beginning and middle of the semester, with some random testing as well. The school also used a wastewater testing program to identify an impending virus outbreak at fraternity and sorority houses, proactively quarantining more than a dozen chapters before cases could spread widely through the community. “We got out in front of it early,” C. Scott Green, the president of the University of Idaho, said. “We were able to isolate those that were sick, and we got back under control.” Still, there were hiccups. The university required food service employees who worked at the dining hall to undergo temperature checks using hand-held scanners. But several developed virus infections anyway, and the university was forced to temporarily close the dining hall over a weekend for deep cleaning. As for the free-standing temperature-scanning stations, Mr. Green himself has experienced their limitations. He said one mistakenly stopped him from entering an athletic building right after he got out of a hot car. Source link Orbem News #Colleges #require #Struggle #Tech #VirusScreening #Works
0 notes
Text
300+ TOP HYPERION Objective Questions and Answers
HYPERION Multiple Choice Questions :-
1 . After creating a new Hyerion Planning appLication, what are two steps that must be taken for it to appear as a va[id Web appLication at the Web LogOn page?
A. Restart the Essbase server
B. Run the HspsetupSupport utility
C. Restart the Web appLication server
D. Within Hyperion Planning, select EnabLe Web LogOn
Ans: B, C
2. Which three options are supported authentication providers for CSS?
A. NTIS
B. Microsoft Active Directory
C. Sun Open Net Environment (Sun ONE)
D. NoveLl NDS
E. REAs LDAP Provider
Ans: A, B, C
3. What is the correct order Hyperion Planning will foLlow to generate a Web Form with Suppress Missing data enabled?
A. Hyperion Planning Web AppLication suppresses missing data;sends the query to Hyperion Essbase;checks Metadata security for the user; displays Web Form to Client
B. Checks Metadata SeciJilty for the User; sends the query to Hyperion Essbase; Hyperion PLanning Web Application suppresses missing data; dispLays Web Form to Client
C. Sends the query to Hyperion Essbase; checks Metadata Security for the User; 1-lyperion PLanning Web Application suppresses missing data; dispLays Web Form to Client
D. Checks Metadata Security for the User; 1-lyperion Planning Web Application suppresses missing data; sends the query to Hyperion Essbase; displays Web Form to Client
Mis: B
4. What three properties can be defined for User-defined custom dimensions?
A. Name
B. Security
C. Data type
D. Source plan type
E. Custom attributes
Mis: A, B, E
5. Which three statements are true about the Cut function in the 1-lyperion PLanning Dimension Editor?
A. It is not avaiLable for root dimension members.
B. It remembers a cut member if the administrator expands, coLlapses, sorts, searches, or changes pages in a dimension hierarchy.
C. It remembers a cut member if the administrator adds a chiLd or sibling member, edits or deletes a member, assigns access to a member or clicks the View link.
D. It remembers a cut member if the administrator adds or edits a dimension, navigates to a page other than the Dimensions tab, deletes a member, or Logs off Hyperion PLanning.
E. It aLlows for mulitple cut selections at the same leveL
Ans: A, B, C
6. Which three tasks can be performed by a PLanner?
A. Modify Web forms
B. Input, submit, and view data
C. View data through Hyperion Reports
D. Use 1-lyperion Planning Spreadsheet Add-in
E. Create and update rules in 1-lyperion Business Rules (HBR)
Ans: B, C, D
7. After the calendar is created through the application setup, which statement is true?
A. You can change the rollup structure.
B. You can change the base time periods.
C. You can change the weekty distribution setting.
D. You can reduce the number of years in the calendar.
Ans: A
8. What wiLl be converted after the Currency Conversion CaLc Script is run?
A. Parent members
B. Level zero members
C. Forecast Scenario for the USD Currency
D. Saved Assumption accountwith Percentage Data Type
E. Saved Assumption accountwith Non-Currency Data Type
Ans: B
9. What is the ideal data block size?
A. Between eight and 1 00 kiLobytes
B. Between 101 and 250 kilobytes
C. Between 251 and 500 kilobytes
D. Greater than 500 kilobytes
Ans: A
10. Which five tasks are performed when setting up a 1-lyperion PLanning application? (Choose five.)
A. Setting up pLan types
B. Creating the calendar
C. Setting up exchange rates
D. Defining the calendar range
E. Setting up multiple currencies
F. Defining base time period and weekly distribution.
Ans: A, B, D, E, F

HYPERION MCQs
11. When refreshing the database in a multi-currency application, what can be selected to create a Currency Conversion Caic Script?
A. Currencies, Scenarios, Version Type, and Versions
B. Currencies, Scenarios, Years, and Exchange Rate Type
C. Currencies, Scenarios, Years, Version Type, and Versions
D. Currencies, Scenarios, Years, Exchange Rate Type, and Versions
Ans: A
12. Which two statements about account level annotations are true?
A. Account level annotations can have 1 500 characters.
B. Only parent level members can have account level annotations.
C. To enable the account level annotations, the Web form design does not matter.
D. A specific option must be selected in the display options page to enable the account level annotations.
Ans: A, D
13. Which three are valid properties of Scenarios with the Hyperion Planning Web Dimension Editor?
A. Access Rights
B. Time Periods
C. Data Storage
D. Exchange Rate Table
Ans: A, B, D
14. Which two Hyperion Application Link Adapters can be used together to Load data?
A. Essbase Adapter
B. FLat File Adapter
C. Web Form Adapter
D. Hyperion Planning Adapter
Ans: A, B
15. When using the Hyperion PLanning ADM driver within Hyperion Reports, which function is used to select Attribute members?
A. Property
B. Member
C. ReLative Member
D. Range
Ans: A
HYPERION Objective type Questions with Answers
16. Supporting Detail can have which two properties?
A. Detail cannot be deleted once created.
B. Data can be filled across a series of columns.
C. Detail can be retrieved in the Spreadsheet Add-in.
D. It can only be text information, no data can be input
E. Data can be in hierarchical form and include aggregation of values.
Ans: B, E
17. Which two are valid Account member names that can be used in Hyperion PLanning?
A. 4200
B. Net-Profit
C. _Gross Sales
D. tost of Sales
E. (Total Expenses)
Ans: A, B
18. The Create Blocks componentwithin F-Iyperion Business Rules (HBR) is used for the purposeof
A. Creating blocks for dense member combinations
B. Creating blocks for sparse member combinations
C. Creating blocks for attribute member combinations
D. Creating blocks for dynamically calcuLated and stored member combinations
Ans: B
19. What are three valid variables to consider about Hyperion Planning application Web performance?
A. Network bandwidth
B. Design of existing web forms
C. Server hardware specifications
D. Number of users that exist within the application
Ans: A, B, C
20. When designing a report in Hyperion Reports, where do you set me txpansion upnon
A. On the Cell Properties
B. On the Row Properties
C. On the Grid Properties
D. On the Report Properties
Ans: B
21. Hyperion PLanning connects to Essbase using the non-underscore username to establish a connection for which two products?
A. Hyperion Reports
B. Essbase Spreadsheet Add-in
C. Hyperion Planning Web Application
D. 1-lyperion Planning Spreadsheet Add-in
Ans: A, B
22. Which list of data storage settings represents all of the available settings for the Entities dimension in the Hyperion Planning Dimension Editor?
A. Dynamic Calc, Never Share, Shared, Store
B. Dynamic Calc, Label Only, Never Share, Store
C. Dynamic Calc, Dynamic CaIc and Store, Never Share, Shared, Store
D. Dynamic Calc, Dynamic Cat and Store, Label Only, Never Share, Shared, Store
Ans: D
23. In a multi-currency application using a Target Version, what calculation options should be used with the Aggregate Data component?
A. Aggregate Data up to Local Currency, Aggregate Missing Values, and Use Calculator Cache
B. Aggregate Missing Values, Optimize the Calculation of Formulas on Sparse Dimensions, and Use Calculator Cache
C. Aggregate Data up to Local Currency, Optimize the Calculation of Formulas on Sparse Dimensions, and Use Calculator Cache
D. Aggregate Missing Values, Aggregate Data up to Local Currency, and Optimize the Calculation of Formulas on Sparse Dimensions
Ans: C
24. Which three predefined types of base time periods can be established when creating the calendar?
A. Weekly
B. Monthly
C. Quarterly
D. Yearly
E. Custom
Ans: B, C, E
25. Which three options are Maintain User tasks in Hyperion Reports?
A. Assign user to a Role
B. Import Essbase Users
C. Import Windows NT users
D. Import LDAP Users
E. Import Users from a text file
Ans: A, B, E
26. What are two reasons for creating or re-creating a Currency Conversion cat script?
A. A currency is no longer a reporting currency.
B. Data in the Essbase database were modified.
C. Another year has been added to the application.
D. A new entity member was added to the application.
E. A foreign currency exchange rate value was modified.
Ans: A, C
27. A user receives “You do not have access to view this form” when trying to open a Web form. What causes this message?
A. The user does not have Write access to the form.
B. The user does not have Read access to the form.
C. The user does not have access to every member in the form.
D. The user does not have access to at least one member in every dimension in the form.
Ans: D
28. When would account annotations be available?
A. when the option is turned on in the application setup
B. Only when the Web form is designed by an administrator
C. When the Web form is designed to using the proper layout
D. When the user has write access to alt dimension selections on the Web form
Ans: C
29. In a multiple plan type application, which statement is true?
A. Security Refreshing can be limited to a Plan Type.
B. A descendant member within the Custom dimension can be made valid for a Plan Type.
C. The Accounts dimension can be dense for one Plan Type and sparse for another Plan Type.
D. After the application has been set up but the Create has not been run, the Plan Type names can be changed.
Ans: C
30. The client wants to load actual data from the general ledger but the file generated requires fields to be ignored and the order of the fields to be changed. What is a possible method for completing this task?
A. Use an Essbase data load rule
B. Use the Web Form import utility
C. Use SQL statement to toad into Hyperion Planning Relational Database
D. Use Hyperion Application Link flow diagram utilizing the Hyperion Planning Adapter
Ans: A
HYPERION Questions and Answers pdf Download
Read the full article
0 notes
Text
300+ TOP VMWARE Objective Questions and Answers
VMWARE Multiple Choice Questions :-
1.Which of the following dvPort binding types have been removed in vSphere 5?
A. Dynamic Binding
B. Ephemeral Binding
C. Static Binding
Ans: A
2.Your boss has asked you to setup 4 ESXi hosts to evaluate the new vSphere 5 release, which is the recommended install method to use in this situation?
A. Interactive Installation
B. Scripted Installation
C. vSphere Auto Deploy Installation
D. Upgrade via VMware Update Manager
Ans: A
3.Your colleague has accidentally allocated more vRAM than your company are licensed for. What will happen to your virtual machines?
A. All VM's will be Powered Off
B. New VM's can not be Powered On
C. VMware will be notified
D. Nothing will happen
Ans: B
4.In an HA cluster after an initial election process, host are either:
A. Primary or Secondary
B. Master or Slave
C. King or Queen
D. Live or Standby
Ans: B
5.To get the maximum performance benefits of vNUMA it is recommended to:
A. Make sure your clusters are composed entirely of hosts with matching NUMA architecture.
B. Only use single vCPU virtual machines
C. Enable EVC on your clusters
D. Disable Hyper-Threading
Ans: A
6.What is the name of the globally unique identifier assigned to each Fibre Channel Port?
A. IP Address
B. MAC Address (Mac)
C. World Wide Name (WWN)
D. Port_ID
Ans: C
7.It is possible to Storage vMotion virtual machines that have snapshots?
A. True
B. False
Ans: A
8.What are the 4 VM Restart Priority options available on an HA Cluster?
A. Disabled, Low, Medium, High
B. Enabled, Small, Medium, Large
C. 1st, 2nd, 3rd, 4th
D. Priority, 2nd Tier, 3rd Tier, Best Effort
Ans: A
9.A memory reservation defines:
A. the amount of virtual machine memory that can be paged to the VMkernel swapfile
B. the amount of physical memory that is guaranteed to the VM
C. the maximum amount of physical memory that will be used by a VM
D. the amount of host memory reserved for the VMkernel
Ans: D
10.Which of the following installation methods installs the ESXi image directly into the Host memory?
A. Interactive ESXi Installation
B. Scripted ESXi Installation
C. vSphere Auto Deploy ESXi Installation Option
D. Upgrade via VMware Update Manager
Ans: D

VMWARE MCQs
11.VMFS-5 upgraded from VMFS-3 continues to use the previous file block size which may be larger than the unified 1MB file block size.
A. True
B. False
Ans: A
12.Which of the following formulas defines the amount of virtual machine memory that will always be composed of disk pages?
A. Memory allocated -(minus) memory limit
B. Memory limit -(minus) memory reservation
C. Memory limit -(minus) memory available
D. Memory allocated -(minus) memory available
Ans: D
13.The upgrade procedure from VMFS-3 to VMFS-5 will require downtime of that datastore?
A. False
B. True
Ans: A
14.Which of the following actions would be LEAST likely to reduce resource contention?
A. Powering off a VM
B. Enabling Swap-To-Cache
C. Disable transparent memory page sharing
D. Enabling vNUMA
Ans: C
15.When is vNUMA enable by default on a virtual machines?
A. When a virtual machine has more than 8 vCPU's
B. When the guestOS is configured using an SMP HAL
C. All the time
D. vNUMA is never enabled by default
Ans: A
16.Which new feature of vSphere 5 is used to collect host core dumps?
A. vMA 5.0
B. ESXi Dump Collector
C. ESXi Syslog Collector
D. VMware vDR 2.0
Ans: B
17.After an upgrade from ESX4.X to ESXi5.0 you notice that when you run the following command via the vMA: "esxcfg-vswif -l" you notice that their are no configure vswif interfaces listed. Why would this be?
A. The Service Console is no longer available with vSphere 5. All vswif interfaces are removed during the upgrade.
B. During the upgrade process all vswif interfaces are migrated to vmk interfaces.
C. During the upgrade process, vswif interfaces are disable by default, they'll need to be enable before they will be listed.
D. The wrong command is being used. "vicfg-vswif -l" is the correct command to display all vswif interfaces.
Ans: B
18.How has vMotion been improved in vSphere 5?
A. Multiple vMotion vmknics, allowing for more and faster vMotion operations
B. Long distance vMotion, allowing for vMotions over a large geographical area
C. Multi-platform vMotion, allowing for vMotions between vSphere and Hyper-V platforms
D. Storage vMotion, allowing for virtual machines storage to be moved between datastores
Ans: D
19.What are the Automation Levels on a DRS Cluster?
A. Manual, Partially Automatic, Fully Automatic
B. Manual, Partially Automated, Fully Automated
C. Manual, Semi Automated, Fully Automatic
D. Manual, Semi Automatic, Automatic
Ans: D
20.What are the two iSCSI discovery methods that are supported by an ESXi host?
A. Static Targets, Dynamic Targets
B. Static Discovery, SendTargets
C. Static Discovery, FindTargets
D. Dynamic Discovery, FindTargets
Ans: A
21.After an upgrade from ESX4.X to ESXi5.0 you notice that your Port Group named "Service Console" is missing. Where has it gone?
A. Because ESXi 5.0 has no Service Console, upgrading from ESX 4.x to ESXi 5.0 removes the Service Console port group.
B. During the upgrade all Port Groups are removed. The Service Console Port Group will need to be recreated.
C. During the upgrade all Port Groups are moved to Distributed Switches.
D. During the upgrade all Port Groups are moved to Standard Switches.
Ans: A
22.You have been asked to provide high availability for your vCenter server. Which product would you use to help achieve this?
A. Fault-Tolerance
B. vCenter Linked-Mode
C. vCenter Heartbeat
D. Microsoft Clustering Services
Ans: C
23.VMware vSphere can be evaluated prior to purchase. What is the maximum number of days the evaluation can be used before a license must be purchased?
A. 30 Days
B. 60 Days
C. 90 Days
D. 120 Days
Ans: B
24.Which feature of vSphere 5 can be used to increase network throughput to virtual machines?
A. SplitRX
B. NPIV
C. VMDirectpath I/O
D. RDM
Ans: A
25.Which feature of vSphere 5 can be used to reduce virtual machine memory overhead?
A. VMX Swap
B. SplitRX
C. Swap to Host
D. Memory Reservations
Ans: A
VMWARE Objective type Questions with Answers
26.By default, where do hosts deployed with VMware Auto Deploy store logs?
A. In Memory
B. First mounted LUN
C. Local disk
D. vMA
Ans: A
27.Which new feature of vSphere 5 is used to create ESXi installation images with a customized set of updates, patches, and drivers?
A. Image Builder
B. Host Profiles
C. Auto Deploy
D. Esxcli
Ans: D
28.Which of the following is not a new feature made available with vSphere 5?
A. sDRS
B. vDR
C. VSA
D. vSphere Web Client
Ans: B
29.What protocol is used by an ESXi host to communicate with NAS devices?
A. NFS
B. iSCSI
C. CIFS
D. SMB
Ans: B
30.After an upgrade from ESX/ESXi 4.1 to ESXi 5.0, your monitoring department are reporting that they have stopped receiving Syslog data from all of the ESXi hosts. What could be the problem?
A. Custom ports that were opened by using the ESX/ESXi 4.1 esxcfg-firewall command do not remain open after the upgrade to ESXi 5.0.
B. Custom ports that were opened by using the ESX/ESXi 4.1 esxcfg-firewall command do not do not get copied during the upgrade to ESXi 5.0.
C. Tech Support Mode is disable by default after an upgrade to ESXi 5.0 stopping all traffic on all ports
D. ESXi 5.0 cannot send logs to Syslog servers.
Ans: D
31.The default security policy on a Port Group is:
A. Reject, Accept, Accept
B. Reject, Reject, Reject
C. Accept, Accept, Accept
D. Reject, Reject, Accept
Ans: A
32.When deploying hosts with VMware Auto Deploy, which is the recommended method to configure ESXi once it has been installed?
A. Host Profiles
B. PowerCLI
C. Manually
D. via Direct Console
Ans: A
33.What is an HA Slot?
A. A slot is a logical representation of the memory and CPU resources that satisfy the requirements for any powered-on virtual machine in the cluster.
B. A slot is a given to each Host in an HA Cluster, there is a maximum of 32 in an HA Cluster
C. A slot is given to each Virtual Machine, this determines the restart priority.
D. A slot has nothing to do with HA, it's how DRS calculates which Virtual Machine should be placed where.
Ans: A
34.Which new version of VMFS is introduced by vSphere 5?
A. VMFS-2
B. VMFS-3
C. VMFS-5
D. VMFS-4
Ans: C
35.ESXi 5.0 supports only LAHF and SAHF CPU instructions?
A. True
B. False
Ans: A
36.Which of the following is no longer available with vSphere 5?
A. ESX
B. vCenter
C. vSphere Client
D. PowerCLI
Ans: D
37.Which if the following is not a supported location for a host diagnostic partition?
A. Shared local storage
B. Private local storage
C. Private SAN storage
D. Shared SAN storage
Ans: A
38.Which of the following actions is not available via the Direct Console?
A. Shutdown host
B. Enter host into Maintenance Mode
C. View host logs
D. Configure host DNS
Ans: B
39.Which vSphere feature provides dynamic allocation of storage capacity?
A. vStorage APIs / VCB
B. Thinapp
C. sDRS
D. vStorage Thin Provisioning
Ans: C
40.To improve security which new feature has been added to ESXi?
A. Firewall
B. Local Mode
C. Anti-Virus
D. vShield
Ans: A
41.What the packaging format used by the VMware ESXi Image Builder?
A. .rar
B. .zip
C. .iso
D. VIB
Ans: C
42.What are the three default roles provided on an ESXi host?
A. No Access, Read Only and Administrator
B. Read only, Operator Access and Administrator
C. Virtual Machine User, Virtual Machine Power User and Administrator
D. Network Consumer, Datastore Consumer and Resource Pool Administrator
Ans: A
43.Which of the following is a requirement for vCenter?
A. A Static IP address
B. A DHCP IP address
C. A valid (internal) domain name system (DNS) registration.
Ans: C
44.Which two users are assigned the Administrator role at the ESX Server level by default?
A. root, administrator
B. root, vpxuser
C. root, vpxa
D. root, hostd
Ans: B
45.After an upgrade from ESXi4.0 to ESXi5.0 you are unable to putty to your hosts. What could have caused this?
A. SSH configuration is not migrated for ESX 4.x hosts or ESXi 4.0 hosts. For these hosts, SSH access is disabled during the upgrade or migration process
B. SSH is not available with ESXi 5.0, it is only available with ESX 5.0.
C. SSH is always disabled after an upgrade or clean installation.
D. The SSH port in ESXi 5.0 has changed to 443 for added security.
Ans: A
46.What are the three Host Isolation Response options available on an HA Cluster?
A. Shut down, Power off, Leave powered on
B. Shut down, Power off, Leave powered off
C. Shut down, Restart, Leave powered on
D. Shut down, Restart, power on
Ans: B
47.You boss has asked you deploy 40 ESXi hosts as quickly as possible, which is the recommended install method to use in this situation?
A. Interactive Installation
B. Scripted Installation
C. VMware Auto Deploy Installation
D. Upgrade via VMware Update Manager
Ans: D
48.Distributed Power Management (DPM) requires which technology to be available on the NIC?
A. Wake On LAN (WOL)
B. DNS
C. BMC
D. NetBIOS
Ans: A
49.The organisation you work for is currently running vSphere 4.1 U1. Your team have just created a new Test/Dev environment based on vSphere 5. The VM management team have asked if you could combine the current 4.1 U1 environment and 5.0 vCenters with Linked-Mode. What is the correct response to the VM management team?
A. vCenter 4.1 and vCenter cannot be joined with Linked-Mode
B. Additional licensing is required to use Linked-Mode
C. Only vCenter Administrators can use Linked-Mode
D. No problem
Ans: D
50.Which of the following is not a benefit of VMware Auto Deploy?
A. Decouples the VMware ESXi host from the physical server and eliminates the boot disk
B. Eliminates configuration drift
C. Simplifies patching and updating
D. Accelerates deployment of virtual machi
VMWARE Questions and Answers pdf Download
Read the full article
0 notes
Text
300+ TOP Ruby on Rails Interview Questions and Answers
Ruby on Rails Interview Questions for freshers experienced :-
1. What is Ruby on Rails?
Ruby: It is an object oriented programming language inspired by PERL and PYTHON.
Rails: It is a framework used for building web application
2. What is class libraries in Ruby?
Class libraries in Ruby consist of a variety of domains, such as data types, thread programming, various domains, etc.
3. What is the naming convention in Rails?
Variables: For declaring Variables, all letters are lowercase, and words are separated by underscores
Class and Module: Modules and Classes uses MixedCase and have no underscore; each word starts with a uppercase letter
Database Table: The database table name should have lowercase letters and underscore between words, and all table names should be in the plural form for example invoice_items
Model: It is represented by unbroken MixedCase and always have singular with the table name
Controller: Controller class names are represented in plural form, such that OrdersController would be the controller for the order table.
4. What is “Yield” in Ruby on Rails?
A Ruby method that receives a code block invokes it by calling it with the “Yield”.
5. What is ORM (Object-Relationship-Model) in Rails?
ORM or Object Relationship Model in Rails indicate that your classes are mapped to the table in the database, and objects are directly mapped to the rows in the table.
6. What the difference is between false and nil in Ruby?
In Ruby False indicates a Boolean datatype, while Nil is not a data type, it have an object_id 4.
7. What are the positive aspects of Rails?
Rails provides many features like
Meta-programming: Rails uses code generation but for heavy lifting it relies on meta-programming. Ruby is considered as one of the best language for Meta-programming.
Active Record: It saves object to the database through Active Record Framework. The Rails version of Active Record identifies the column in a schema and automatically binds them to your domain objects using metaprogramming
Scaffolding: Rails have an ability to create scaffolding or temporary code automatically
Convention over configuration: Unlike other development framework, Rails does not require much configuration, if you follow the naming convention carefully
Three environments: Rails comes with three default environment testing, development, and production.
Built-in-testing: It supports code called harness and fixtures that make test cases to write and execute.
8. What is the role of sub-directory app/controllers and app/helpers?
App/controllers: A web request from the user is handled by the Controller. The controller sub-directory is where Rails looks to find controller classes
App/helpers: The helper’s sub-directory holds any helper classes used to assist the view, model and controller classes.
9. What is the difference between String and Symbol?
They both act in the same way only they differ in their behaviors which are opposite to each other. The difference lies in the object_id, memory and process tune when they are used together. Symbol belongs to the category of immutable objects whereas Strings are considered as mutable objects.
10. How Symbol is different from variables?
Symbol is different from variables in following aspects
It is more like a string than variable
In Ruby string is mutable but a Symbol is immutable
Only one copy of the symbol requires to be created
Symbols are often used as the corresponding to enums in Ruby

Ruby on Rails Interview Questions
11. What is Rails Active Record in Ruby on Rails?
Rails active record is the Object/Relational Mapping (ORM) layer supplied with Rails. It follows the standard ORM model as
Table map to classes
Rows map to objects
Columns map to object attributes
12. How Rails implements Ajax?
Ajax powered web page retrieves the web page from the server which is new or changed unlike other web-page where you have to refresh the page to get the latest information.
Rails triggers an Ajax Operation in following ways
Some trigger fires: The trigger could be a user clicking on a link or button, the users inducing changes to the data in the field or on a form
Web client calls the server: A Java-script method, XMLHttpRequest, sends data linked with the trigger to an action handler on the server. The data might be the ID of a checkbox, the whole form or the text in the entry field
Server does process: The server side action handler does something with the data and retrieves an HTML fragment to the web client
Client receives the response: The client side JavaScript, which Rails generates automatically, receives the HTML fragment and uses it to update a particular part of the current
13. How you can create a controller for subject?
To create a controller for subject you can use the following command
C:\ruby\library> ruby script/generate controller subject
14. What is Rails Migration?
Rails Migration enables Ruby to make changes to the database schema, making it possible to use a version control system to leave things synchronized with the actual code.
15. List out what can Rails Migration do?
Rails Migration can do following things
Create table
Drop table
Rename table
Add column
Rename column
Change column
Remove column and so on
16. What is the command to create a migration?
To create migration command includes
C:\ruby\application>ruby script/generate migration table_name
17. When self.up and self.down method is used?
When migrating to a new version, self.up method is used while self.down method is used to roll back my changes if needed.
18. What is the role of Rails Controller?
The Rails controller is the logical center of the application. It faciliates the interaction between the users, views, and the model. It also performs other activities like
It is capable of routing external requests to internal actions. It handles URL extremely well
It regulates helper modules, which extend the capabilities of the view templates without bulking of their code
It regulates sessions; that gives users the impression of an ongoing interaction with our applications
19. What is the difference between Active support’s “HashWithIndifferent” and Ruby’s “Hash” ?
The Hash class in Ruby’s core library returns value by using a standard “= =” comparison on the keys. It means that the value stored for a symbol key cannot be retrieved using the equivalent string. While the HashWithIndifferentAccess treats Symbol keys and String keys as equivalent.
20. What is Cross-Site Request Forgery (CSRF) and how Rails is protected against it?
CSRF is a form of attack where hacker submits a page request on your behalf to a different website, causing damage or revealing your sensitive data. To protect from CSRF attacks, you have to add “protect_from_forgery” to your ApplicationController. This will cause Rails to require a CSRF token to process the request. CSRF token is given as a hidden field in every form created using Rails form builders.
21. What is Mixin in Rails?
Mixin in Ruby offers an alternative to multiple inheritances, using mixin modules can be imported inside other class.
22. How you define Instance Variable, Global Variable and Class Variable in Ruby?
Ruby Instance variable begins with — @
Ruby Class variables begin with — @@
Ruby Global variables begin with — $
23. How you can run Rails application without creating databases?
You can execute your application by uncommenting the line in environment.rb
path=> rootpath conf/environment.rb
config.frameworks =
24. What is the difference between the Observers and Callbacks in Ruby on Rails?
Rails Observers: Observers is same as Callback, but it is used when method is not directly associated to object lifecycle. Also, the observer lives longer, and it can be detached or attached at any time. For example, displaying values from a model in the UI and updating model from user input.
Rails Callback: Callbacks are methods, which can be called at certain moments of an object’s life cycle for example it can be called when an object is validated, created, updated, deleted, A call back is short lived. For example, running a thread and giving a call-back that is called when thread terminates
25. What is rake in Rails?
Rake is a Ruby Make; it is a Ruby utility that substitutes the Unix utility ‘make’, and uses a ‘Rakefile’ and ‘.rake files’ to build up a list of tasks. In Rails, Rake is used for normal administration tasks like migrating the database through scripts, loading a schema into the database, etc.
26. How you can list all routes for an application?
To list out all routes for an application you can write rake routes in the terminal.
27. What is sweeper in Rails?
Sweepers are responsible for expiring or terminating caches when model object changes.
28. Mention the log that has to be seen to report errors in Ruby Rails?
Rails will report errors from Apache in the log/Apache.log and errors from the Ruby code in log/development.log.
29. What is the difference between Dynamic and Static Scaffolding?
Dynamic Scaffolding Static Scaffolding
It automatically creates the entire content and user interface at runtime
It enables to generation of new, delete, edit methods for the use in application
It does not need a database to be synchronized
It requires manual entry in the command to create the data with their fields
It does not require any such generation to take place
It requires the database to be migrated
30. What is the function of garbage collection in Ruby on Rails?
The functions of garbage collection in Ruby on Rails includes
It enables the removal of the pointer values which is left behind when the execution of the program ends
It frees the programmer from tracking the object that is being created dynamically on runtime
It gives the advantage of removing the inaccessible objects from the memory, and allows other processes to use the memory
31. What is the difference between redirect and render in Ruby on Rails?
Redirect is a method that is used to issue the error message in case the page is not issued or found to the browser. It tells browser to process and issue a new request.
Render is a method used to make the content. Render only works when the controller is being set up properly with the variables that require to be rendered.
32. What is the purpose of RJs in Rails?
RJs is a template that produces JavaScript which is run in an eval block by the browser in response to an AJAX request. It is sometimes used to define the JavaScript, Prototype and helpers provided by Rails.
33. What is Polymorphic Association in Ruby on Rails?
Polymorphic Association allows an ActiveRecord object to be connected with Multiple ActiveRecord objects. A perfect example of Polymorphic Association is a social site where users can comment on anywhere whether it is a videos, photos, link, status updates etc. It would be not feasible if you have to create an individual comment like photos_comments, videos_comment and so on.
34. What are the limits of Ruby on Rails?
Ruby on Rails has been designed for creating a CRUD web application using MVC. This might make Rails not useful for other programmers. Some of the features that Rails does not support include
Foreign key in databases
Linking to multiple data-base at once
Soap web services
Connection to multiple data-base servers at once
35. What is the difference between calling super() and super call?
super(): A call to super() invokes the parent method without any arguments, as presumably expected. As always, being explicit in your code is a good thing.
super call: A call to super invokes the parent method with the same arguments that were passed to the child method. An error will therefore occur if the arguments passed to the child method don’t match what the parent is expecting.
36. What about Dig, Float and Max?
Float class is used whenever the function changes constantly.
Dig is used whenever you want to represent a float in decimal digits.
Max is used whenever there is a huge need of Float.
37. How can we define Ruby regular expressions?
Ruby regular expression is a special sequence of characters that helps you match or find other strings. A regular expression literal is a pattern between arbitrary delimiters or slashes followed by %r.
38. What is the defined operator?
Define operator states whether a passed expression is defined or not. If the expression is defined, it returns the description string and if it is not defined it returns a null value.
39. List out the few features of Ruby?
Free format – You can start writing from program from any line and column
Case sensitive – The uppercase and lowercase letters are distinct
Comments – Anything followed by an unquoted #, to the end of the line on which it appears, is ignored by the interpreter
Statement delimiters- Multiple statements on one line must be separated by semicolons, but they are not required at the end of a line.
40. Mention the types of variables available in Ruby Class?
Types of variables available in Ruby Class are,
Local Variables
Global Variables
Class Variables
Instance Variables
41. How can you declare a block in Ruby?
In Ruby, the code in the block is always enclosed within braces ({}). You can invoke a block by using “yield statement”.
42. What is the difference between put and putc statement?
Unlike the puts statement, which outputs the entire string onto the screen. The Putc statement can be used to output one character at a time.
43. What is a class library in Ruby?
Ruby class libraries consist of a variety of domains, such as thread programming, data types, various domains, etc. These classes give flexible capabilities at a high level of abstraction, giving you the ability to create powerful Ruby scripts useful in a variety of problem domains. The following domains which have relevant class libraries are,
GUI programming
Network programming
CGI Programming
Text processing
44. In Ruby, it explains about the defined operator?
The defined operator tells whether a passed expression is defined or not. If the expression is not defined, it gives null, and if the expression is defined it returns the description string.
45. What is the difference in scope for these two variables: @@name and @name?
The difference in scope for these two variables is that:
@@name is a class variable
@name is an instance variable
46. What is the syntax for Ruby collect Iterator?
The syntax for Ruby collect Iterator collection = collection.collect.
47. In Ruby code, often it is observed that coder uses a short hand form of using an expression like array.map(&:method_name) instead of array.map { |element| element.method_name }. How this trick actually works?
When a parameter is passed with ��&” in front of it. Ruby will call to_proc on it in an attempt to make it usable as a block. So, symbol to_Proc will invoke the method of the corresponding name on whatever is passed to it. Thus helping our shorthand trick to work.
48. What is Interpolation in Ruby?
Ruby Interpolation is the process of inserting a string into a literal. By placing a Hash (#) within {} open and close brackets, one can interpolate a string into the literal.
49. What is the Notation used for denoting class variables in Ruby?
In Ruby,
A constant should begin with an uppercase letter, and it should not be defined inside a method
A local must begin with the _ underscore sign or a lowercase letter
A global variable should begin with the $ sign. An uninitialized global has the value of “nil” and it should raise a warning. It can be referred anywhere in the program.
A class variable should begin with double @@ and have to be first initialized before being used in a method definition
50. What is the difference between Procs and Blocks?
The difference between Procs and Blocks,
Block is just the part of the syntax of a method while proc has the characteristics of a block
Procs are objects, blocks are not
At most one block can appear in an argument list
Only block is not able to be stored into a variable while Proc can
51. What is the difference between a single quote and double quote?
A single-quoted strings don’t process ASCII escape codes, and they don’t do string interpolation.
52. What is the difference between a gem and a plugin in Ruby?
Gem: A gem is a just ruby code. It is installed on a machine, and it’s available for all ruby applications running on that machine.
Plugin: Plugin is also ruby code, but it is installed in the application folder and only available for that specific application.
53. What is the difference extend and include?
The “include” makes the module’s methods available to the instance of a class, while “extend” makes these methods available to the class itself.
54. Why Ruby on Rails?
There are lot of advantages of using ruby on rails:
1. DRY Principal
2. Convention over Configuration
3. Gems and Plugins
4. Scaffolding
5. Pure OOP Concept
6. Rest Support
7. Rack support
8. Action Mailer
9. Rpc support
10. Rexml Support
11. etc..
55. What is the Difference between Symbol and String?
Symbol are same like string but both behaviors is different based on object_id, memory and process time (cpu time) Strings are mutable , Symbols are immutable.
Mutable objects can be changed after assignment while immutable objects can only be overwritten.
For example
p "string object jak".object_id #=> 22956070
p "string object jak".object_id #=> 22956030
p "string object jak".object_id #=> 22956090
p :symbol_object_jak.object_id #=> 247378
p :symbol_object_jak.object_id #=> 247378
p :symbol_object_jak.object_id #=> 247378
p " string object jak ".to_sym.object_id #=> 247518
p " string object jak ".to_sym.object_id #=> 247518
p " string object jak ".to_sym.object_id #=> 247518
p :symbol_object_jak.to_s.object_id #=> 22704460
p :symbol_object_jak.to_s.object_id #=> 22687010
p :symbol_object_jak.to_s.object_id #=> 21141310
And also it will differ by process time
For example:
Testing two symbol values for equality (or non-equality) is faster than testing two string values for equality,
Note : Each unique string value has an associated symbol
56. What things we can define in the model?
There are lot of things you can define in models few are:
1. Validations (like validates_presence_of, numeracility_of, format_of etc.)
2. Relationships(like has_one, has_many, HABTM etc.)
3. Callbacks(like before_save, after_save, before_create etc.)
4. Suppose you installed a plugin say validation_group, So you can also define validation_group settings in your model
5. ROR Queries in Sql
6. Active record Associations Relationship
57. What do you mean by the term Rail Migration?
It is basically an approach with the help of which the users can make the changes to the already existing database Schema in Ruby and can implement a version control system. The main aim is to synchronize the objects to get the quality outcomes.
58. What exactly do you know about the Rail Observers?
It is very much similar to that of Callback. They can be deployed directly in case the methods are not integrated with the lifecycle of the object. It is possible for the users to attach the observer to any file and perform the reverse action by the user.
59. Name the two types of Scaffolding in the Ruby?
These are Static and Dynamic Scaffolding
60. Explain some of the looping structures available in Ruby?
For loop, While loop, Until Loop.
Be able to explain situations in which you would use one over another.
Ruby on Rails Questions and Answers Pdf Download
Read the full article
0 notes