#Antivirus Static Engine
Text
Malware Analysis: Unveiling the Secrets of Digital Threats
In the realm of cybersecurity, one of the key aspects that ethical hackers and security researchers delve into is the analysis of malware. Malware analysis is a vital practice that enables experts to unravel the inner workings of malicious software, understand its behavior, and develop effective strategies to counter its impact.
Let’s explore the key aspects that pave the way for a successful path in ethical hacking. So, buckle up and get ready for an adventure into the world of hacking from The Best Software Testing Training Institute.

Some Key Aspects And Techniques Involved In Malware Analysis:
Understanding Malware Analysis:
Malware analysis is the process of dissecting and comprehending malicious software, such as viruses, worms, Trojans, and ransomware. It involves studying the functionality, origins, and potential implications of the malware. By analyzing malware, ethical hackers gain valuable insights into the techniques employed by attackers, aiding in the development of robust defense mechanisms.
Static Analysis:
Static analysis is a preliminary technique that involves examining the malware without executing it. Analysts scrutinize the binary code, file headers, and strings to decipher the malware’s structure and potential IOCs. Static analysis provides a foundation for further investigation and helps in identifying key characteristics of malware.
Dynamic Analysis:
Dynamic analysis involves executing the malware in a controlled environment to observe its behavior in real-time. By monitoring network traffic, system calls, file modifications, and other actions, analysts gain a deeper understanding of the malware’s capabilities. Dynamic analysis reveals the malware’s command and control communication, payload delivery mechanisms, and data exfiltration techniques.
Code Reverse Engineering:
Malware often employs obfuscation techniques to evade detection. Code reverse engineering involves decompiling or disassembling the malware to unravel its logic, algorithms, and functionality. This technique unveils encryption methods, identifies vulnerabilities, and aids in developing effective countermeasures.
5. Behavior Analysis:
Analyzing the behavior of malware during execution is crucial in understanding its objectives and potential impact on a system. By monitoring file system modifications, registry changes, and network communication, analysts can uncover the malware’s malicious actions. Behavior analysis helps in identifying evasion techniques and devising strategies to mitigate the impact of malware.
6. Network Traffic Analysis:
Malware often relies on network communication to receive commands, exfiltrate data, or download additional payloads. Analyzing the network traffic generated by malware provides insights into its command and control infrastructure, communication protocols, and potential data leakage. Network traffic analysis aids in identifying communication patterns and strengthening network defenses.
8. Malware Signature Creation:
Malware signatures are patterns or characteristics unique to specific malware variants. Analysts create these signatures based on their analysis findings, enabling antivirus software and security tools to detect and block known threats. By developing effective signatures, ethical hackers contribute to early detection and prevention of malware infections.
9. Malware Family Classification:
Malware analysis involves categorizing and classifying malware into families or groups based on shared characteristics and behavior. This classification allows analysts to understand the broader context of the malware, identify its origins, and develop more effective detection and mitigation strategies.
Malware analysis is an indispensable component of ethical hacking and cybersecurity. By dissecting and understanding the inner workings of malicious software, analysts gain valuable insights into attackers’ techniques and motives.
Static and dynamic analysis, code reverse engineering, behavior analysis, network traffic analysis, and malware signature creation are among the key techniques employed in this field. By investing in malware analysis, ethical hackers play a crucial role in safeguarding digital systems and combating the ever-evolving landscape of cyber threats.
If you want to learn ethical hacking I will highly recommend the best ethical hacking course with certification .Every challenge is an opportunity to grow and contribute to the dynamic field of cybersecurity. Happy hacking!
0 notes
Text
The Data Encoder Crypter

The Data Encoder Crypter is an encryption tool that encrypts files. It provides an effective method for securing private information and online business. The program can be downloaded for free or for a fee. It can also be used to protect sensitive data from antiviruses.
These programs are often used by hackers to hide malicious code or manipulate security tools. There are various types of crypters available. Some obfuscate malware while others use polymorphic encryption. These types of crypters make it difficult for security systems to detect them. Some companies share signature databases that help identify them.
This type of crypter is usually downloaded for free. It encrypts malware, spyware and phishing attacks, making them appear innocent. These products are generally easy to use and configure. It is important to use a crypter that is compatible with your operating system.
This type of crypter is a great solution for any computer user who needs to secure his or her privacy. It is ideal for businesses and penetration testers. It comes with live support and a graphical user interface (GUI) for configuring settings. It can also protect files from reverse engineering bypass McAfee.
Despite being relatively new, crypters have already been employed by cybercriminals to conceal their programs. They have evolved from point-and-click password cracking technologies to more sophisticated encoding methods. They can be used to obfuscate and conceal malware as well as to hide the identity of a user. A good crypter will be able to work on any type of operating system.
The best FUD crypter is made with robust code and will provide reliable results for a long time. However, this type of crypter is not always effective against antivirus updates. To prevent malware infections, you must install a reputable antivirus software. It is important to scan your emails and download any other files carefully. This will help you avoid becoming a victim of identity theft.
The MalSilo packer is another useful security tool. It includes telemetry, a Discord group and multiple backends. This can be used for developing applications, especially when a lot of files are being transferred. The encoding algorithm can be dynamically generated, or it can be hard-coded. The stubs that encrypt the file are also tied to the encrypted file, making it unique. The static stubs are purchased separately and must be modified to keep them from being detected.
You can find many websites that offer crypters. They can be downloaded for free, but you should be aware that they do not always have the best protection. Some are not fully compatible with all antiviruses and operating systems. Investing in a top-quality program will ensure that your privacy is protected.
A crypter is a great way to protect your data from malware. This is especially useful for data that is sensitive or private. It should be easy to use and should not require any coding experience. Some crypters are also designed to be easily customizable and include icons to make the sample look legitimate.
0 notes
Text
Telecharger cheat engine 6.5.1

#TELECHARGER CHEAT ENGINE 6.5.1 UTORRENT#
#TELECHARGER CHEAT ENGINE 6.5.1 UPGRADE#
#TELECHARGER CHEAT ENGINE 6.5.1 SOFTWARE#
Guess pointermaps isn't the only thing I should know about. Cheat Engine 7.4: Cheat Engine is an open source tool designed to help you with modifying single player games running under window so you can make them harder or easier depending on your preference(e. Sadly I know literally nothing about lua code, but I got your point. In the case of the inventory not working all the time, it is placed into a structure containing a number of other instances and each time you reload it is reallocated and moves up in the array which means there is no static pointer path that will work, you need to make a dynamic offset that will follow it around or hook a function where you can copy the base from. You should look into this tutorial I posted regarding GameMaker objects/instances and the table I recently posted for this game to see the correct structure form.įor future attempts, you should be checking each stage of your pointers to make sure that it is being accessed (and pay attention to the offset values in the instructions) as that is the best indicator that your chain is valid and will work for other users. That is because your pointer chains are not valid for his game. Activate the trainer options by checking boxes or setting values from 0 to 1įorager.CT for version 4.1.9 (324.25 KiB) Downloaded 806 times Forager.CT for version 4.1.7 (313.21 KiB) Downloaded 100 timesĭid you hook Cheat Engine to the game? That's my pretty last guess as when I downloaded my table it worked correctly.Disini anda dapat membuat game tersebut menjadi lebih mudah atau lebih sulit dengan memodifikasinya melalui aplikasi Cheat Engine Terbaru ini. Click the PC icon in Cheat Engine in order to select the game process. Cheat Engine 6.5.1 adalah versi terbaru dari cheat engine yang berfungsi untuk memodifikasi sebuah permainan single player sesuai dengan keinginan anda.
#TELECHARGER CHEAT ENGINE 6.5.1 SOFTWARE#
Der Download der Software ist nicht mehr verfügbar. Aufgrund seiner Funktionsweise kann Cheat Engine zudem einen falschen Alarm bei Antivirus-Programmen auslösen. Allerdings macht die unübersichtliche Programmoberfläche und die sehr knappe Anleitung den Einstieg schwer. 4.Attendez la fin, vous avez une archive, ouvrez là, extraire le contenu vers votre dossier AOP2.
#TELECHARGER CHEAT ENGINE 6.5.1 UTORRENT#
3.Vous avez un icône torrent, double clique Utorrent souvre le téléchargement se lance. Break the "Vault" and pick up upgrades.īetter check a table made by aSwedishMagyar. Für Tüftler und Programmierer ist die Freeware ein wertvolles Werkzeug. Installation : 1.Cliquer sur le lien de téléchargement. Make "Vault" and move your wanted upgrades here.ģ.
#TELECHARGER CHEAT ENGINE 6.5.1 UPGRADE#
Change one of your items to the upgrade you want.Ģ. How to get upgrades (pickaxes, bows, swords etc.):ġ. If the version of Forager was updated, or you have problems with a table tell me. Updated pointers in "Pointers" and added "Coins" pointer (couldn't find "Player Size" pointer).Īlso Lives were changed to "4 Bytes" because "Double" wasn't working correctly "Inventory Editor" is a script now (4.1.9 has pointers instead of script) and it includes 40 slots with their values instead of 16. Updated items list for "Inventory Editor". Removed "Scripts" and "Speedhacks" sections.

0 notes
Text
Know about Java Why it is a powerful programming language

Java is the base coding platform for many digital applications that you are already using nowadays such as smartphones, laptops, tablets, supercomputers, game consoles, etc.
Today, Java is preferred by most organizations to develop their applications or projects.
What is Java?
Java is a fast, secure, reliable, robust, and popular class-based object-oriented programming language. James Gosling developed Java in 1995 at Sun Microsystems, Inc. Oak was the original name of the Java programming language.
The current owner of Java is Oracle corporation. Oracle has not developed Java. Java has been acquired by the Oracle corporation in 2010.
Java SE 18 is the latest version of Java released in March 2022. You can download Java for free for personal use. The developer can find and download the development kits and tools at Oracle's official website - https://www.oracle.com/javadownload/
Java is similar to C/C++ and its class libraries because Gosling had designed Java with a C/C++-style syntax. One who knows C/C++ can learn and master Java fastly and efficiently.
What is a Java Platform?
Java platform is a type of environment having a group of multiple programs which makes it possible to develop and run the Java application. This environment is made of three basic components - Java language, Java packages, and Java virtual machine(JVM).
The following are the different names of Java platforms(also called Java editions) -
Java Platform, Micro Edition (Java ME) –
It provides environments with limited resources with an API and a short impression of the virtual machines, suitable for small devices - mobile phones.
Java Platform, Standard Edition (Java SE) –
It provides a workstation-based environment with core functionality like I/O stream, Networking, Exception, Inner Classes, etc., and APIs like java.io, java.net, etc. It is suitable for GUI development, networking, database access, etc.
Java Platform, Enterprise Edition (Java EE) -
It is mainly for large distributed enterprise or Internet environments with API and is suitable to develop web and enterprise applications like web services, Servlet, JSP, etc.
Java FX -
It provides an environment for developing rich internet applications using a lightweight user-interface API and is suitable for connecting to networked data sources.
What are the components of the Java platform?
Java platform components are responsible to interpret and execute the Java developer's source code or programming code into machine understandable format and providing output or result as per source code logic. Here is a short explanation of these Java platform components -
Java Development kit (JDK) -
It is a type of development environment that provides tools like - a compiler, application launcher, applet viewer, etc. to write or develop and run applets and Java applications.
Java Virtual Machine (JVM) -
It provides a run time engine for running the Java codes and applications.
Java Runtime Environment (JRE) -
If you are preparing and looking for a career as a Java Developer, please visit at Java interview questions for getting your dream job.
Java code example sample -
Here is the following code represents Java code for showing the welcome message -
/*Filename - welcome.java */
/***************************/
Type to compile the file welcome.java - javac Welcome.java Type to execute the file welcome.java - java Welcome Output would show as - Hello Welcome to Java
/***************************/
class Welcome{ public static void main(String args[]){ System.out.println("Hello Welcome to Java");
}
}
What are the types of Java Applications?
You can create majorly four different types of applications as below -
Stand-alone application -
As you know that standalone applications refer to desktop applications or windows applications. This is traditional software that we have to install on every machine. Examples of stand-alone applications are Media players, antivirus, etc. AWT and Swing are used in Java to build stand-alone applications.
Web Application -
As you know web application refers to server-based dynamic page generation for showing the application output. Currently, we create the web application using Servlet, JSP, Struts, Spring, Hibernate, JSF, etc. in Java.
Enterprise Application-
An application that is distributed in nature like banking applications etc. is called an enterprise application. It has advantages such as a high level of security, load balancing, and clustering. You can create enterprise-level applications using EJB in Java.
Mobile Application –
An application that is created for a mobile device is called a mobile application. Android and Java ME are currently used for creating mobile applications.
What are the features of Java?
The following are features of Java -
It uses object-oriented programming design for application development. Java uses its object-based functionality, making it an extensible programming language. You can extend its functionality thanks to object-oriented design.
Java is an easy-to-use and learns programming language because it is based on OOP design and logic.
Code once written in Java can easily run on different computer platforms.
Java is platform-independent. Some programs developed on one computer can be run on another machine.
It is intended for creating object-oriented applications.
Memory management in java operates in auto mode and it works in a multi-threading way.
Java is designed to work with the distributed network environment of the Internet.
Facilitates distributed computing as its network-oriented.
What is Java used for?
While the primary use of Java is for computer software programming, there are many other specific uses which are highlighted below -
Server side or backend application development -
Java can be used to create functional components of an application. Users do not interact with these parts, but they are necessary for the frontend to thrive. Java follows the Write Once, Run Anywhere (WORA) concept so it is considered the ideal server-side applications development tool for all operating systems.
Complete Web Application Development –
Java can be used to create a variety of web applications. As a web application development tool, Java 8 can be used to design both frontend and backend applications.
Distributed Application Development -
Java is one of the few programming languages that can be used to create applications for a single computer network or distributed system. Distributed Java applications have components spread across different systems rather than a central mainframe.
Cloud Application Development –
Java is also an ideal programming language for creating cloud applications. You can create SaaS (software as a service ) application using Java. These applications are gaining popularity across industries because they are more secure and affordable than traditional systems.
Big Data Engineering -
In addition to traditional software development, Java 8 has been applied in big data engineering, especially in the big data processing. Java works smartly and efficiently for memory management and distribution.
Who uses Java?
Java is used widely to develop applications by top companies in the world. Here are the example names - Amazon, eBay, Google, Uber, Netflix, Instagram, etc.
Source: infotokri
#java#software#softwaredeveloper#webdevelopement#webdeveloper#Technology#javadeveloper#javaprogramming#javaprojects
1 note
·
View note
Text
Once in a Blue Moon
It was an aligning of the planets when John and Virgil got to work together. That is to say: not as seldom as everybody thought, but not everyday either. It just depended how you defined 'together’, for technically John worked every dispatch. They were a great pairing: Virgil’s mechanical skills and John’s electronic ones meant there wasn’t much they couldn’t engineer their way out of.
They’d already tackled several problems at the overloading factory: Virgil had used a bit of brute force and the proper application of leverage to open a cooling vent for access, and John had whipped up an antivirus program in his short but brutal plummet to Earth. They security doors had been no match for Virgil’s jaws of life – something that he would have to have a word with the owners about, it shouldn’t be this easy – and they made swift progress to the control room.
That’s where it all went wrong.
“You uploaded you’re cure yet?” asked Virgil, raising an arm to shield his face from the sparking controls. It was not good when a display panel did that; it meant things were getting way out of hand, as if the warning lights didn’t already make that clear. Virgil had really grown to hate flashing red lights.
“It’s not a cure,” John said with a very clearly heard verbal eyeroll, “and you know that so are just saying it to wind me up.” Virgil did know that. There was some sort of malevolent trojan horse virus in the system that John was going to contain and eradicate, but surely ‘cure’ was an acceptable shortcut. John was hunched over, giving the terminal he was working at an intent frown. Virgil didn’t like that frown. It was a ‘something’s gone wrong’ type of frown.
“Problem?”
John pushed himself to his feet with a sigh of frustration. “Sort of. My programme is uploaded and is working it’s way through the system architecture and once it’s done facility operation will return to normal.”
“I sense a ‘but’ looming in my future.”
“But..... to complete that we will need to do a full system restart.”
“Off and on again.”
John nodded and Virgil felt his stomach sink. This was a manufacturing plant for high value, high strength biodegradable plastics which were in very high demand in a number of secondary industries. The process to create a reliable and durable product was complicated and long and relied upon down to the second timing in some stages, otherwise whole batches could be lost. These places were designed to resist total system shut down as that would the cost the company millions in clean up on it’s own, let alone lost contracts and waste. This was a true twenty four seven operation with back ups and contingencies to keep it running at all times.
Of course some of those would be off line at the moment as a result of the virus that was screwing up the temperature controls on the main furnace, threatening to send it’s unstable contents into a spontaneous combustion that would flatten half for the surrounding city. But not all of them.
“Is that even possible?” Virgil asked.
“Yes, if I had three quarters of an hour and a bit of luck I might be able to trick the remaining safe guards that the others were still in place, get them to shut down in a controlled cascade.” John said grimly.
Virgil gave a quick glance at the readouts – needles quivering at their max, bar charts at their limits and those damned red lights suggested that wasn’t an option. “We don’t have that long,” Virgil said “We have about ten minutes before it goes critical. What are our other options?” There were always other options. International Rescue didn’t give up.
“There might be another way” John said with a strange hesitation. “But it’s a bit more …. errr …. rough and ready, shall we say. You’re not going to like it.”
“If that’s what we’ve got, lets get on with it!” Virgil knew they had no time to waste.
John pointed him to one of the panels on the far side of the room. “I need you to take out all of the capacitors on that board, one at a time, from left to right. And I need to borrow a wrench.”
Virgil fished out his second favourite wrench and handed it over, turning smartly on his heel to set about his task. John pressed a few buttons on the main console before popping open another section of the room’s wall. Virgil clicked open his own, now as far away from John as he could be in the small space, and stared in puzzlement for a second. He wasn’t the computer genius that his brother was, but he knew what a capacitor looked like and whatever was running through this wall didn’t have any. It wasn’t like John to make such a mistake even under this much pressure. He turned to double check when a lot of things happened at once.
He saw John reaching into the guts of the wall and hitting something really hard with the wrench. What followed was the predictable blinding flash of an overload due to damage and contact with metal, the snap of discharging electricity like static from a balloon but a thousand fold . The lights went out, there was a dull ‘thumb’ of a large weight on a hard surface and a clang as the wrench fell to the floor.
Virgil stood, stiff and dumbfounded. His eyes, still troubled by the flash were struggling to accustomise themselves to the pitch dark. Spots were floating across his vision and the hair on the back of his neck stood up in a sixth-sense sort of alarm.
“John?” He whispered “What the actual hell.”
He turned on his trusty shoulder flashlight and swept it around the room. The place where John had been standing was filled with smoke which smelt cloying and metallic as it drifted through the room. Another sweep found what he was looking for – crumbled against the wall just a few paces away was his stupid stupid stupid brother.
“God damn it John!” Virgil said as he knelt at his side. Through the thin beam of light Virgil could see the slight fuzz to his hair and scorch marks on his suit that spoke of a large electrical discharge. Virgil pushed a furious two fingers to the pulse point just under the jaw and offered a silent prayer of thanks to anything in a position to hear when he felt the heartbeat - fast, uneven, but there.
“John, John!” Virgil shook his shoulder.
“No need to shout.” John replied, voice much softer than his usual commanding tones.
“ Oh there is plenty of reason to shout. Being as I think you just stuck your hand into the primary back up power system to overload it and shut the factory down. That's what you did, right?”
“Basically.” Virgil focused the light on John’s face to see it pinched, pale and squinting. He tried to bring up the suit’s biometrics but it wasn’t fully responsive, and it took a lot to damage Brains’ tech. “How long has everything been off?”
“Under a minute. You and I are going to have a conversation about ‘rough and ready’ and hitting complex electric systems with god damn metal rods and getting yourself god damn electrocuted.”
“I’m fine.” John protested.
“Really? Because I think you just got thrown across the room into a concrete wall. I also think you just got hit with about a billion volts of electricity. Now I’m not sure one of those made you lose consciousness, but I know which one is making your heartrate too fast. I’m also worried that I can feel occasional irregular heartbeats and I so don’t want to have to put a de-fib on you because I have no idea what sort of internal injuries you have right now.” Virgil was trying not to let his anger out and to stay professional but John sure did deserve it. Hitting it with a bloody wrench!
“If you’re finished, want to help me get up so we can get this place back up and running and go home?” John said, making no move to get up himself.
“That depends, do you think you’ve got any internal bleeding?” Virgil made a couple of physical checks that John bore with bad grace - unfortunately they were all familiar with the feeling of internal bleeding.
John gave a grimace and a shake of his head “Nah, only bruised.”
Virgil gave a put-upon sigh and man-handled John to his feet, taking most of his weight with an arm slung over his shoulder and Virgil holding John tightly to his hip. The quicker they did this, the quicker he could get John back for a CAT scan and an xray and an ECG.
They staggered to the main terminal where John flicked a few switches and pumped a breaker – with a whine and a whir something started up: lights and screens flickered on all around them, straining his eyes yet again.
“Please don’t do anything like that again.” Virgil pleaded as they waited for the main frame to reboot, “It was really stupid and you could have at least given me warning.”
“You would have tried to stop me.” John said, leaning his head against Virgil and closing his eye for just a second. “I didn’t want to do it, but - “ he paused for a few moments as he studied the booting sequence and obviously happy with what he saw there - “Mission accomplished, city saved.”
“Yeah, too right I would have tried to stop you almost killing yourself.” Virgil said, turning them slowly and starting to make their way back to his Thunderbird. Luckily they landed just outside the door so he wouldn’t have to carry John too far – he was heavier than he looked. “As it is, you might have wished you had when Scott gets hold of you.”
John groaned, long and drawn out. After a side-eyed glance at his brother - pale, in obvious pain and listing to one side even with his support - Virgil wasn’t convinced that noise could all be attributed to the thought of the dressing down he was going to get as soon as he was well enough to stand it.
“Do you think we could just not tell him?”
“Not a chance.”
“He’s not going to understand.”
“Oh we understand- ” Virgil said, wanting to emphasise that Scott wouldn’t be the only one to have a problem with John’s antics, even as he was pushing his brother into one of Two’s med beds. “-considering the number of lives at risk. But making a decision like that without having a conversation with the rest of us – it's just not on. How would you feel if we did it while you were up on Five. ”
John was clenching his jaw as Virgil raised the bed so he was leaning back instead of laying flat, but whether from a hidden injury or the memory of all the times John had watched them run head first into trouble without being able to do anything about it was impossible to say.
Suppressing a groan of his own Virgil headed to the cockpit for take off protocols. If everyone was being their usual selves Scott would be blazingly angry by the time they got back to the island and John would retreat into intractable silence and somehow it would all be Virgil’s fault.
Virgil was almost glad he worked with his brother just once in a blue moon.
also on https://archiveofourown.org/works/23156785
or
https://www.fanfiction.net/s/13522767/1/Once-in-a-Blue-Moon
31 notes
·
View notes
Text
D-LINK EXO AC2600 REVIEW
The DLINK EXO AC2600 is a great home wireless router for everyday use. This is a dual band router works on latest 802.11ac technology and is capable of providing a maximum speed of 2600 Mbps (Bandwidth).
It has 4 external antennas with MU-MIMO technology and Advanced Smart Beam technology which are capable of providing a wide range of simultaneous multiple device connectivity.
The speed bandwidth is divided into three segments 1733 Mbps @ 5 GHz + 800 Mbps @ 2.4 GHz for high speed connectivity.
Its output port includes 4 Ethernet ports to connect multiple wired devices and two USB ports including one high speed 3.0 and one 2.0 port to use your wired devices wirelessly.
Its underlying 880 MHz powerful dual-core processor with 128 MB of RAM is capable of maintaining a smooth connection throughout the house with multiple devices connectivity.
Its additional functionality includes Traffic Prioritization – Advanced QoS engine guarantees the best performance for high priority programs, games and video streaming, Dual-Band Technology – Decreases wireless interference and congestion, allowing you to connect more devices, Advanced AC SmartBeam – tracks your devices simultaneously to provide seamless wifi speed and range throughout your home., Parental Controls – Create online access schedules and block/allow specific websites and/or devices, Guest Wi-Fi Network – Enable a public or encrypted wireless guest network to help secure and control access to local network devices, Quick Router Setup (QRS) App – Easy setup app for smartphones & tablets.
The proportional regular online organization solace and QRS compact application for iOS and Android contraptions is joined with the DIR-822 as you'll find in the D-Link DIR-878$116.88 at Amazon. The help opens to a home screen with a framework map that exhibits the amount of related clients, Internet Status, and things like IP and MAC address and Default Gateway information. Use the Settings tab to get to menus for Internet, Wireless, and Network settings. Remote settings fuse security, Wi-Fi Channel assurance, Channel Width, and Transmission Power settings. Web settings let you plan affiliation type (DHCP, PPPoE, Static) and contain IPv6 and VALN settings.
Under the Features tab is an easy to-use natural Quality of Service (QoS) engine, similarly as settings for firewall, web-isolating, and port-sending. In the Management menu there are obliged parental control settings that let you grant or deny access to the framework, yet you don't get the granular controls that let you limit access to things like adult orchestrated, web based systems administration, and wagering regions that you get with the Asus RT-AC86U. In like manner missing are the antivirus and malware utilities that are fused with the Asus RT-AC86U and the TP-Link Archer C2300$124.52 at Amazon routers..
1 note
·
View note
Text
Final Showdown: NordVPN Vs PureVPN
The Internet has become a part of our daily lives. With most of our personal data uploaded on the web, Internet privacy has become a growing concern. Honestly, Internet Service Providers track almost every bit of information that you search on the web, and then sell it to advertisers for revenue.
So, if you are someone who is glued to the Internet, you should be concerned about your privacy online. And, if you already are, chances are that you have already used VPN’s and are familiar with what they do.
The number of VPN’s – free, paid, and freemium are way too many to keep a track of! It does get a bit confusing to settle with on. We have been through the same when we first started scouring the Internet for the best VPN. And, to help you save time and effort, we will talk about two of the most renowned VPN service provider companies – NordVPN and PureVPN.
Hackers, ISPs, Governments, Corporations are all after your data. So, let’s start off by telling you a bit about the concept of VPN. If you are interested in all things Tech, you shouldn’t be missing out on Tekhattan. Subscribe to their blogs to increase your knowledge of ever-evolving technology.

What is A VPN?
A virtual private network (VPN) is a technology that improves your online security and privacy. In other words, all data transferred between your computer and the VPN server is scrambled so that no one else can read it.
In other words, it's like accessing a private network via a public network. Apart from protecting your security and privacy, a VPN even yields advanced encryption for safeguarding your financial data and other crucial information shared via public Wi-Fi. By hiding your current IP-address, it lets you surf the internet and watch your favorite restricted sites like Netflix in a way as if you're accessing them from another country.
How does VPN work?
You start the VPN client (software) from your VPN service. This software encrypts your data, even before your Internet Service Provider sees it. The data then goes to the VPN, and from the VPN server to your online destination — anything from your bank website to a video sharing website to a search engine. The online destination sees your data as coming from the VPN server and its location, and not from your computer and your location.
Why Do You Need a VPN?
It really depends on your situation, but there are many different uses for a VPN:
Surf the internet without revealing your real IP address and geo-location (online anonymity).
Add an extra level of security by encrypting your internet connection.
Prevent your Internet Service Provider (ISP), third parties, network admins, and governments from spying on your online activities (thanks to encryption).
Unblock websites and access content that is restricted to certain geographic locations.
Torrent, P2P download, and stream media in safety.
Bypass censorship by easily getting around regional restrictions.
Save money on flights and other online purchases by changing your IP address (geographic location).
Protect yourself from hackers anywhere you go – especially while using public Wi-Fi connections in cafés, hotels, and airports.
Protect your private data, such as bank passwords, credit cards, photos, and other personal information when online.
Surf the internet with peace of mind.
NordVPN vs PureVPN – Which is Better?
NordVPN has gained a lot of supporters over the years of its work, so it is among the top five most popular VPN services. In general, NordVPN allows its users to secure the transmission of their data over the Internet through public networks, bypass geographic blocks for some content and make online activity completely private.
PureVPN has a huge number of functions and features. More precisely, there are thousands of servers around the world, many tunnel protocols of any choice, and sufficiently reliable encryption. PureVPN provides access to Netflix, ability to secure streaming and torrenting and other useful additional services.
NordVPN owns one of the largest server systems, which includes more than 5000 servers located in 62 countries. On the other hand, PureVPN has 2000+ VPN located in 140+ countries.
When it comes to PureVPN, one of the coolest feature is web filtering which enables the parents to keep family oriented content available for their children. Another worth-mentioning feature is app filtering which enables you to choose which apps should run with the VPN configured.
Again, NordVPN provides a dual encryption service if you need additional protection. This means that your internet traffic will go through two VPN servers. It also gives you the ability to get a dedicated static IP address that will be tied to your personal account.
We recently read a comparison on https://tekhattan.com/blog/security/purevpn-vs-nordvpn/. It speaks at great length between the features of both service providers and is a good read if you are stuck on selecting the best VPN for your personal security.
PureVPN offers a lot of valuable features such as an antivirus that helps protect data against different forms of malwares and viruses. It also offers an IDS/IPS, Intrusion detection system and intrusion prevention system which respectively checks for suspicious activities and denies access to the system. This way no ransomware can harm your files or take over your device. Plus, you get an Adblocker to stop those annoying ads all the time when you surf the Internet.
If you opt for NordVPN, you will get Super secure encryption (OpenVPN, SSTP, PPTP, L2TP / IPsec and IKEv2 / IPsec protocols). The AES-256-CBC is equipped with a multi-node connection, which allows you to access the dual NordVPN network. Moreover, NordVPN works on the Anti-DDoS server, which in turn, provides an uninterrupted connection and minimizes the probability of disconnection, which can cause data leakage.
The point is that each VPN service provider offers a lot. It is you who has to make a decision on what best suits your requirement. You will want to opt for a sufficiently convenient and reliable VPN service, the main advantages of which should be the high level of encryption of transmitted information and no logs policy.
1 note
·
View note
Text
Wrought Iron - The Particular And Glory Of Black Friday 2010 Art
The Ancient Chinese Zhanmadao Sword is really a Sabre, a two handed sword, with One Long Blade will be very Broad and also another stylish very long handle. Around 1072 An.D., this weapon was used against enemy calvary. The handle was 37 centimeters long and was wrapped making it easy maintain this weapon with both. The last part in the blade was slightly curvy but the holistic parts of it was very straight. This Sword Blade was 114 Centimetres in size.
Straightness of your Neck. As already mentioned the neck has to take care of a massive amount tension. Guitars in excellent condition often need an adjustment from hour and hour and an acoustic guitar that's not in excellent will undoubtedly have along with the fretboard.
This can be a double edged sword but from where I stand, yes! Visitors are sourced from search engines for blogs just a few static websites and some sort of SM content manager/writer should understand some form of of SEO to make it so that their client's blog enjoys the benefits associated with SEO. Most important principles contact the various social media applications where content is published within same way so a scarcity of SEO content will most definitely hamper your SM attention. This is where an SM consultant with strong writing and marketing secrets comes on the fore. After all, what use is a website or perhaps blog without search engine traffic?
Structural improvements made on the foundation offer little, on way of immediate reward. freemake video converter crack may seem unworthy any sort of cost which can be acquired. Time and money are usually devoted to projects bringing more immediate pleasure. It's much to be able to get anxious about additions, renovations, or even redecorating comes. Structural integrity globe foundation often goes unnoticed, and is vastly unappreciated until the time comes who's is checked.
eset nod32 antivirus crack keygen was inspired by the sea, 13:1. Different his partner of disorderly half for this chapter, that a normal earth-bound existence. He comes from below, inside the pit. I will not be surprised if he literally makes an entrance inside the sea, just as the text tells you. These two passages, together with II Thessalonians 2, contact us that he is now being held back by a restraining angel. When keyshot pro crack could be released she must find one way to get towards the land. God says his entrance are by signs and benefits.
Never, ever touch the blade of a sword or knife. Sure, you could imagine you know what your are doing, but touching a blade shows your true ignorance. When using the cracksword back of one's hand, maybe your fingers, even the bed of your fingernails -- is touching the razor blade.
When selling your art in the real world your art sales are almost always limited to your place where your art is in the intervening time. If you are exhibiting at a gallery your art sales are in order to that gallery and men and women that acquired that gallery. If your art is being shown at a reasonable your art sales are restricted to the people that visit art in that fair. Believe you get the picture. For your must part in the real world your art sales are going to be limited to local or regional sales.
The height of the local water table can also affect garage floor do out. The water table is, put very simply (and not entirely correctly), the top of the ground good water. If the water table is high, then the ground water sits close for the bottom of the concrete garage floor, this means water is much more likely to soak in the course of. Does your area's soil stay somewhat moist, no matter if in a drought? Most likely pretty good that water table sits high.
0 notes
Text
Defeating static signatures in blackbox antivirus...
Forwarded from Pentesting News
Defeating static signatures in blackbox antivirus engines
https://blog.scrt.ch/2022/04/05/automatically-extracting-static-antivirus-signatures
Repo: https://github.com/scrt/avdebugger
Attachments:
Insomnihack_antivirus_vmeier.pdf
0 notes
Text
How do you get around Antivirus

The first step to bypass antivirus is to modify the binary that is used by a network program to communicate with another. There are many ways to accomplish this, but the best one is to use an heuristic approach. The heuristic approach employs algorithms and patterns to determine which software are reliable. Antivirus software cannot detect malware if these techniques are applied on the file. The attacker has to discover a way to modify the binary code to do this.
The best way to bypass antivirus software is to change the file signature, or create a new file with a new signature. This is referred to as obfuscation. These techniques alter the files to deceive signature-based scanning. For example, Blackhills has written about the obfuscated software for memory tampering called Mimikatz. By changing its references, the obfuscation renders it difficult for antivirus programs to detect it. This is a highly efficient method that LMG employs to evade antivirus.
Another common way to bypass antivirus software is encryption. With encryption, the malware creator can hide the content of their payload in an encrypted file, thus avoiding detection by signature alone. Crypters can be runtime or scantime. Scantime encrypters dump the payload onto disk while runtime encrypt the file in memory. Check Point Research discovered CypherIT via the dark net. Microsoft is currently working on a feature request.
Antivirus software utilizes heuristic engines for identifying malware-related files. While static signatures aren't able to detect all malware, they can help detect it. Since static signatures are continuously updated, this method is able to avoid the majority of detections bypass antivirus. While heuristic algorithm are an excellent alternative for those who don't wish to test various methods, a good antivirus program should be constantly updated. And, of course, the best method to do this is through trial and error.
It is possible to disable antivirus software. The process of bypassing antivirus software can be very dangerous for your computer and this book will show you how to avoid becoming a victim. The ability to bypass antivirus software is a great alternative to antivirus. However, you should be extremely cautious however. There are several ways to stay clear of this. The best method is to make use of an open source antivirus scanner.
Open-source antivirus software is a good alternative if you don't want your computer to be at risk. In certain situations these programs could be dangerous, but you should always be careful because some of them are able to bypass antivirus software. Using an open source tool will allow malware to continue to infect your computer however, if you choose to employ a closed-source antivirus, you will be able to avoid them. Bypassing software is not as difficult as you might think.
1 note
·
View note
Text
11.11.0

Gitlab 11.11.0
11/11/08 Judge Penny Brown Video Youtube
What Property Is 11-11=0
About Internet Explorer 11
Internet Explorer 11 11.0.11 is the version of IE which was released in order to take advantage of added capabilities in Windows 8. IE11 on Windows 8 brings an entirely new browsing experience and set of capabilities to the Web, such as a new touch first browsing experience and full screen UI for your sites, security improvements that offer the best protection against the most common threats on the Web, improved performance, and support for the HTML5 and CSS3 standards developers need. With this new release, Windows 7 customers receive all of the performance, security, and under-hood changes that enable a stellar Web experience. This download is licensed as freeware for the Windows (32-bit and 64-bit) operating system/platform without restrictions. Internet Explorer 11 is available to all software users as a free download for Windows.
Is Internet Explorer 11 safe to download?
Gitlab 11.11.0
Defense Enrollment Eligibility Reporting System (DEERS) Register family members in the Defense Enrollment Eligibility Reporting System (DEERS) for TRICARE and other benefits. Active-duty and retired Service Members are automatically registered in DEERS.
11.11.0.0/22 (AS8003 Global Resource Systems, LLC) Netblock IP Address Information.
Dec 27, 2020 JDK 11.0.11 contains IANA time zone data 2020e, 2020f, 2021a. Volgograd switches to Moscow time on 2020-12-27 at 02:00. South Sudan changes from +03 to +02 on 2021-02-01 at 00:00. For more information, refer to Timezone Data Versions in the JRE Software.
Kaspersky Security Center 11 version 11.0.0.1131 was released on March 14, 2019. Kaspersky Security Center is a single administration console for controlling all Kaspersky Lab security solutions and system administration tools that you use. It makes every endpoint and device on your network more visible, simplifies IT administration tasks,. Notes: Computers connected to a network are assigned a unique number known as Internet Protocol (IP) Address. IP (version 4) addresses consist of four numbers in the range 0-255 separated by periods (i.e. A computer may have either a permanent (static) IP address, or one that is dynamically assigned/leased to it.
We tested the file IE11-Windows6.1-KB2976627-x86.msu with 25 antivirus programs and it turned out 100% clean. It's good practice to test any downloads from the Internet with trustworthy antivirus software.
Does Internet Explorer 11 work on my version of Windows?
Older versions of Windows often have trouble running modern software and thus Internet Explorer 11 may run into errors if you're running something like Windows XP. Conversely, much older software that hasn't been updated in years may run into errors while running on newer operating systems like Windows 10. You can always try running older programs in compatibility mode.
Officially supported operating systems include 32-bit and 64-bit versions of Windows Server 2016, Windows 10, Windows Server 2012, Windows 8 and Windows 7.
What versions of Internet Explorer 11 are available?
The current version of Internet Explorer 11 is 11.0.11 and is the latest version since we last checked. This is the full offline installer setup file for PC. At the moment, only the latest version is available.
Development of this software has ceased, and therefore Internet Explorer 11 is obsolete, so future updates should not be expected.
What type of graphical file formats are supported?
Internet Explorer 11 supports over 4 common image formats including EPS, PLY, SVG and WEBP.
Alternatives to Internet Explorer 11 available for download
Sleipnir Browser
A web browser optimized for beauty and font rendering based on Mozilla's Gecko rendering engine.
Firefox Portable
Portable version of the versatile Firefox browser with support for passwords, history, bookmarks and of course the endless number of extensions and..
NVIDIA Direct3D SDK
A collection of DirectX 11 code samples to create 3D graphics in Windows.
Avant Browser
Fast Internet Explorer-based web browsing adding multi-processor support using a low amount of memory that features a video downloader, anti-freeze and..
Midori Portable
Portable version of a fast web browsing featuring several privacy and ad-blocking options.
Pale Moon Portable
Web browser with improved page loading speed which disables less-used features on the Firefox code.
Waterfox Portable
A very fast browser running 64-bit code of Mozilla Firefox.
Intel Driver Update Utility
Midori
A lightweight web browser which focuses on user privacy and blocking web advertisements.
Bing Desktop
Adds Bing functionality and wallpapers to your desktop.
Believer, if your inheritance is meager, you should be satisfied with your earthly portion; for you may rest assured that it is best for you. Unerring wisdom ordained your lot and selected for you the safest and best condition. When a ship of large tonnage is to be brought up a river that has a large sandbank, if someone should ask, 'Why does the captain steer through the deep part of the channel and deviate so much from a straight line?' his answer would be, 'Because I could not get my ship into harbor at all if I did not keep to the deep channel.'
In the same way you would run aground and suffer shipwreck if your divine Captain did not steer you into the depths of affliction where waves of trouble follow each other in quick succession. Some plants die if they have too much sunshine. It may be that you are planted where you get only a little, but you are put there by the loving Farmer because only in that situation will you produce fruit unto perfection.
11/11/08 Judge Penny Brown Video Youtube
Remember this: If any other condition had been better for you than the one in which you are, divine love would have put you there. You are placed by God in the most suitable circumstances, and if you could choose your lot, you would soon cry, 'Lord, choose my heritage for me, for by my self-will I am pierced through with many sorrows.' Be content with the things you have, since the Lord has ordered all things for your good. Take up your own daily cross; it is the burden best suited for your shoulder and will prove most effective to make you perfect in every good word and work to the glory of God. Busy self and proud impatience must be put down; it is not for them to choose, but for the Lord of Love!
Trials must and will befall—
But with humble faith to see
Love inscribed upon them all,
This is happiness to me.
What Property Is 11-11=0
One-Year Bible Reading Plan
Send me the Daily Devotional

0 notes
Text
Jre 8 Dmg For Mac
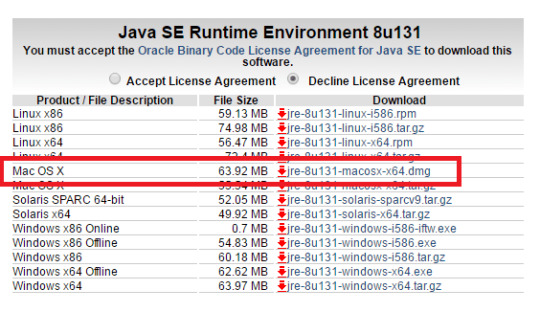
Java Archive Downloads - Java SE 8u211 And Later
REW Beta Release V5.20 Beta 29
8 Installation Of The JDK And The JRE On MacOS - Oracle
The Java Development Kit (JDK), officially named 'Java Platform Standard Edition' or 'Java SE', is needed for writing Java programs. The JDK is freely available from Sun Microsystems (now part of Oracle). The mother site for JDK (Java SE) is http://www.oracle.com/technetwork/java/javase/overview/index.html.
Patch Name: jre-8u65-macosx-x64.dmg: Patch Description: Update for Java Runtime Environment for Mac (1.8.65) Bulletin Id: MAC-033: Bulletin Title: Java Runtime Environment 8 Updates For Mac. Jre-8u version-macosx-amd64.dmg. Jre-8u version-macosx-x64.dmg. Where version is 6 or later. Download the file. Before the file can be downloaded, you must accept the license agreement. From either the Downloads window of the browser, or from the file browser, double click the file.dmg to launch it. Complete antivirus/antispyware test for Java (JRE) for Mac 8 Build 261, setup file: jre-11-ea+8osx-x64bin.dmg (75.39 MB) using top antivirus engines Avast.
'JDK' or 'JRE'?
Summary: JDK 8 should be installed in your system to run SysTools Mac software even if you have latest version of JDK available in your system. It is because, our application requires installation of JDK & JRE in the user machine for running the software properly. The latest version like JDK 11, 13 does not provides JRE installers.
JRE (Java Runtime) is needed for running Java programs. JDK (Java Development Kit), which includes JRE plus the development tools (such as compiler and debugger), is need for writing as well as running Java programs. In other words, JRE is a subset of JDK. Since you are supposed to write Java Programs, you should install JDK, which includes JRE.
JDK Versions
Reference: 'Java Version History' @ https://en.wikipedia.org/wiki/Java_version_history.
JDK Alpha and Beta (1995): Sun Microsystem announced Java in September 23, 1995.
JDK 1.0 (January 1996): Originally called Oak (named after the oak tree outside James Gosling's office). Renamed to Java 1 in JDK 1.0.2.
JDK 1.1 (February 1997): Introduced AWT event model, inner class, JavaBean, JDBC, and RMI.
J2SE 1.2 (JDK 1.2) (December 1998): Re-branded as 'Java 2' and renamed JDK to J2SE (Java 2 Standard Edition). Also released J2EE (Java 2 Enterprise Edition) and J2ME (Java 2 Micro Edition). Included JFC (Java Foundation Classes - Swing, Accessibility API, Java 2D, Pluggable Look & Feel, and Drag & Drop). Also introduced Collection Framework and JIT compiler.
J2SE 1.3 (JDK 1.3) (May 2000): Introduced Hotspot JVM.
J2SE 1.4 (JDK 1.4) (February 2002): Introduced assert statement, non-blocking IO (nio), logging API, image IO, Java webstart, regular expression (regex) support.
J2SE 5.0 (JDK 5) (September 2004): Officially called 5.0 instead of 1.5 (by dropping the 1.). Introduced generics, autoboxing/unboxing, annotation, enum, varargs, for-each loop, static import. See 'JDK 5 New Features'.
Java SE 6 (JDK 6) (December 2006): Renamed J2SE to Java SE (Java Platform Standard Edition). No new language features. See 'JDK 6 New Features'.
Java SE 7 (JDK 7) (July 2011): First version after Oracle purchased Sun Microsystem - aslo called OracleJDK. Introduced Strings in switch statement, Binary integer literals, allowing underscores in numeric literals, improved type inference for generic instance creation (or diamond operator <>), Catching multiple exception types and rethrowing exceptions with improved type checking. See 'JDK 7 New Features'.
Java SE 8 (JDK 8) (LTS) (March 2014): Included support for Lambda expressions, default and static methods in interfaces, improved collection, and JavaScript runtime. Also integrated JavaFX graphics subsystem. See 'JDK 8 New Features'.
Java SE 9 (JDK 9) (September 21, 2017): Introduced modularization of the JDK (module) under project Jigsaw, the Java Shell (jshell), and more. See 'JDK 9 New Features'.
Java SE 10 (18.3) (JDK 10) (March 2018): Introduced var for type inference local variable (similar to JavaScript). Introduced time-based release versioning with two releases each year, in March and September, denoted as YY.M. Removed native-header generation tool javah. See 'JDK 10 New Features'.
Java SE 11 (18.9) (LTS) (JDK 11) (September 2018): Extended var to lambda expression. Standardize HTTP client in java.net.http. Support TLS 1.3. Clean up the JDK and the installation package (removed JavaFX, JavaEE, CORBA modules, deprecated Nashorn JavaScript engine). OracleJDK is no longer free for commercial use, but OpenJDK is still free. See 'JDK 11 New Features'.
Java SE 12 (19.3) (JDK 12) (March 2019): Switch Expression (preview). See 'JDK 12 New Features'.
Java SE 13 (19.9) (JDK 13) (September 2019): Switch Expression (preview), Multi-line Text Block (preview). See 'JDK 13 New Features'.
Java SE 14 (20.3) (JDK 14) (March 2020): Records (preview)
How To Install JDK on Windows
Step 0: Un-Install Older Version(s) of JDK/JRE
I recommend that you install only the latest JDK. Although you can install multiple versions of JDK/JRE concurrently, it is messy.
If you have previously installed older version(s) of JDK/JRE, un-install ALL of them. Goto 'Control Panel' ⇒ (optional) 'Programs' ⇒ 'Programs and Features' ⇒ Un-install ALL programs begin with 'Java', such as 'Java SE Development Kit ..', 'Java SE Runtime ..', 'Java X Update ..', and etc.
Step 1: Download JDK
Goto Java SE download site @ http://www.oracle.com/technetwork/java/javase/downloads/index.html.
Under 'Java Platform, Standard Edition' ⇒ 'Java SE 13.0.(x)', where (x) denotes a fast running security-update number ⇒ Click the 'Oracle JDK Download' button.
Under 'Java SE Development Kit 13.0.(x)' ⇒ Check 'Accept License Agreement'.
Choose the JDK for your operating system, i.e., 'Windows'. Download the 'exe' installer (e.g., 'jdk-13.0.(x)_windows-x64_bin.exe' - about 159MB).
Step 2: Install JDK
Run the downloaded installer (e.g., 'jdk-13.0.(x)_windows-x64_bin.exe'), which installs both the JDK and JRE.
By default, JDK is installed in directory 'C:Program FilesJavajdk-13.0.(x)', where (x) denotes the update number. Accept the defaults and follow the screen instructions to install JDK.
Use your 'File Explorer', navigate to 'C:Program FilesJava' to inspect the sub-directories. Take note of your JDK installed directoryjdk-13.0.(x), in particular, the update number (x), which you will need in the next step.
I shall refer to the JDK installed directory as <JAVA_HOME>, hereafter, in this article.
Step 3: Include JDK's 'bin' Directory in the PATH
Windows' Command Prompt (CMD) searches the current directory and the directories listed in the PATHenvironment variable (or system variable) for executable programs. JDK's programs (such as Java compiler 'javac.exe' and Java runtime 'java.exe') reside in the sub-directory 'bin' of the JDK installed directory. You need to include JDK's 'bin' in the PATH to run the JDK programs.
To edit the PATH environment variable in Windows 10:
Launch 'Control Panel' ⇒ (Optional) 'System and Security' ⇒ 'System' ⇒ Click 'Advanced system settings' on the left pane.
Switch to 'Advanced' tab ⇒ Click 'Environment Variables' button.
Under 'System Variables' (the bottom pane), scroll down to select variable 'Path' ⇒ Click 'Edit..'.
For Newer Windows 10:
You shall see a TABLE listing all the existing PATH entries (if not, goto next step). Click 'New' ⇒ Click 'Browse' and navigate to your JDK's 'bin' directory, i.e., 'c:Program FilesJavajdk-13.0.(x)bin', where (x) is your installation update number ⇒ Select 'Move Up' to move this entry all the way to the TOP.
For Older Windows 10 (Time to change your computer!):
(CAUTION: Read this paragraph 3 times before doing this step! Don't push 'Apply' or 'OK' until you are 101% sure. There is no UNDO!!!)
(To be SAFE, copy the content of the 'Variable value' to Notepad before changing it!!!)
In 'Variable value' field, APPEND 'c:Program FilesJavajdk-13.0.(x)bin' (where (x) is your installation update number) IN FRONT of all the existing directories, followed by a semi-colon (;) to separate the JDK's bin directory from the rest of the existing directories. DO NOT DELETE any existing entries; otherwise, some existing applications may not run.
Note: If you have started CMD, you need to re-start for the new environment settings to take effect.
Step 4: Verify the JDK Installation
Launch a CMD via one of the following means:
Click 'Search' button ⇒ Type 'cmd' ⇒ Choose 'Command Prompt', or
Right-click 'Start' button ⇒ run.. ⇒ enter 'cmd', or
Click 'Start' button ⇒ Windows System ⇒ Command Prompt
Issue the following commands to verify your JDK installation:
Issue 'path' command to list the contents of the PATH environment variable. Check to make sure that your JDK's 'bin' is listed in the PATH.
Issue the following commands to verify that JDK/JRE are properly installed and display their version:
Step 5: Write a Hello-World Java Program
Create a directory to keep your works, e.g., 'd:myProject' or 'c:myProject'. Do NOT save your works in 'Desktop' or 'Documents' as they are hard to locate. The directory name shall not contain blank or special characters. Use meaningful but short name as it is easier to type.
Launch a programming text editor (such as TextPad, NotePad++, Sublime Text, Atom). Begin with a new file and enter the following source code. Save the file as 'Hello.java', under your work directory (e.g., d:myProject).
Step 6: Compile and Run the Hello-World Java Program
To compile the source code 'Hello.java':
Start a CMD Shell (Search ⇒ enter 'cmd' ⇒ select 'Command Prompt').
Set the Current Drive to the drive where you saved your source file 'Hello.java'.
If you use drive 'c', skip this step.
Else if you use drive 'd', enter 'd:' as follow:
Set the Current Working Directory to the directory that you saved your source file via the cd (Change Directory) command. For example, suppose that your source file is saved in directory 'myProject'.
Issue a dir (List Directory) command to confirm that your source file is present in the current directory.
Invoke the JDK compiler 'javac' to compile the source code 'Hello.java'. The compilation is successful if the command prompt returns. Otherwise, error messages would be shown. Correct the errors in your source file and re-compile. Check 'Common JDK Installation Errors', if you encounter problem compiling your program.
The output of the compilation is a Java class called 'Hello.class'. Issue a dir (List Directory) command again to check for the output.
To run the program, invoke the Java Runtime 'java':
Everything that can possibly go wrong will go wrong: Read 'JDK Installation Common Errors'.
Step 7: (For Advanced Users Only) JDK's Source Code
Source code for JDK is provided and kept in '<JAVA_HOME>libsrc.zip' (or '<JAVA_HOME>src.zip' prior to JDK 9). I strongly recommend that you to go through some of the source files such as 'String.java', 'Math.java', and 'Integer.java', under 'javalang', to learn how experts program.
How to Install JDK on macOS
Step 1: Check if JDK has been Pre-Installed
To check if JDK has been installed, open a 'Terminal' (Search 'Terminal'; or Finder ⇒ Go ⇒ Utilities ⇒ Terminal) and issue this command:
If a JDK version number is returned (e.g., JDK x.x.x), then JDK has already been installed. If the JDK version is prior to 1.8, proceed to Step 2 to install the latest JDK; otherwise, proceed to 'Step 3: Write a Hello-world Java program'.
If message 'command not found' appears, JDK is NOT installed. Proceed to the 'Step 2: Install JDK'.
If message 'To open javac, you need a Java runtime' appears, select 'Install' and follow the instructions to install JDK. Then, proceed to 'Step 3: Write a Hello-world Java program'.
Step 2: Download JDK
Goto Java SE download site @ http://www.oracle.com/technetwork/java/javase/downloads/index.html.
Under 'Java Platform, Standard Edition' ⇒ 'Java SE 13.0.(x)', where (x) denotes a fast running security-update number ⇒ Click the 'Oracle JDK' 'Download' button.
Under 'Java SE Development Kit 13.0.(x)' ⇒ Check 'Accept License Agreement'.
Choose the JDK for your operating platform, i.e., macOS. Download the DMG installer (e.g, jdk-13.0.(x)_osx-x64_bin.dmg - about 172MB).
Step 3: Install JDK/JRE
Double-click the downloaded Disk Image (DMG) file. Follow the screen instructions to install JDK/JRE.
Eject the DMG file.
To verify your installation, open a 'Terminal' and issue these commands.
Step 3: Write a Hello-World Java Program
Create a directory called 'myProject' under your home directory (Launch 'Finder' ⇒ 'Go' ⇒ 'Home'; Select 'File' ⇒ 'New Folder' ⇒ 'myProject').
In macOS, the home directory of the current user can be referenced as '~'. Hence, this new directory can be referenced as '~/myProject'.
Use a programming text editor (such as Sublime Text or Atom) to input the following source code and save as 'Hello.java' under the directory '~/myProject'.
(If you use macOS's default text editor 'TextEdit' (NOT recommended), you need to open a new file ⇒ choose 'Format' ⇒ 'Make Plain Text' ⇒ Enter the source code ⇒ Save as 'Hello.java'.)
Step 4: Compile and Run the Hello-World Java Program
To compile the source code 'Hello.java', open a new 'Terminal' ('Go' ⇒ 'Utilities' ⇒ 'Terminal') and issue these commands (as illustrated):
To run the Hello-world, invoke the Java Runtime 'java' as follows:
How to Install JDK on Ubuntu
There are several JDK implementations available for Linux, such as Oracle JDK, OpenJDK, Sun JDK, IBM JDK and GNU Java Compiler. We shall choose the Oracle JDK 8. Ubuntu chooses OpenJDK as its default JDK, which is not 100% compatible with Oracle JDK.
Step 0: Check if JDK has already been Installed
Open a Terminal and issue this command:
If a JDK version number (e.g., 'javac x.x.x') appears, JDK has already been installed. You can skip the installation and goto step 2.
To remove OpenJDK, issue command:
Step 1: Download and Install JDK
Goto JDK (Java SE) download site @ http://www.oracle.com/technetwork/java/javase/downloads/index.html. Under 'Java Platform, Standard Edition' ⇒ 'Java SE 11.0.(x)' ⇒ Click JDK's 'Download' ⇒ Under 'Java SE Development Kit 11.0.(x)' ⇒ Check 'Accept License Agreement' ⇒ Select 'Linux', 'tar.gz' package, (e.g., 'jdk-13.0.(x)-linux-x64_bin.tar.gz' - 171MB).
The tarball will be downloaded in directory '~/Downloads', by default.
We shall install JDK under '/usr/local/java' (or Ubuntu's default JDK directory /usr/lib/jvm; or /opt/java). First, create a directory 'java' under '/usr/local'. Open a Terminal and issue these commands: Extract the downloaded package (Check your downloaded filename!) JDK shall be extracted in a folder '/usr/local/java/jdk-13.0.(x)', where (x) is the update number.
Inform the Ubuntu to use this JDK/JRE: The above steps set up symlinks java, javac, javaws at /usr/bin (which is in the PATH), that link to /etc/alternatives and then to JDK bin directory.
The 'alternatives' system aims to resolve the situation where several programs fulfilling the same function (e.g., different version of JDKs). It sets up symlinks thru /etc/alternatives to refer to the actual programs to be used.
Alternatively, you can include the JDK's bin and JRE's bin into the PATH directly.
To verify the JDK installation, issue these commands:
(Don't Do this step - It is taken care by 'alternative' in Step 3. Keep here to show you how to set PATH.)
Add JDK's binary directory ('bin') to the 'PATH' by editing '/etc/profile': Add these lines at the end of the file '/etc/profile', replace '(x)' with the actual number: Rerun the configuration file by:
Step 2: Compile and Run a Hello-world Java Program
File Explorer ⇒ Home ⇒ Create a new folder called 'myProject' to keep our works.
Open 'Text Editor' (gedit). Enter the following source code and save as 'Hello.java' under the '~/myProject' directory created earlier.
To compile the Hello-world Java program, launch a Terminal and issue these commands:
Run the Hello-world Java program:
Source-Code Editors & IDEs for Java Programming
Eclipse IDE
You need to first install Eclipse. Read 'How to Install Eclipse'.
You can then proceed to write your first Java program. Read 'Writing your first Java Program with Eclipse'.
Eclipse allow you to debug program graphically. Read 'Debugging program in Eclipse'.
NetBeans IDE
You need to first install NetBeans. Read 'How to Install NetBeans'.
You can then proceed to write your first Java program. Read 'Writing your first Java program with NetBeans'.
NetBeans allow you to debug program graphically. Read 'Debugging program in NetBeans'.
Visual Studio (VS) Code IDE
Click HERE, look for 'VS Code for Java Programming'
Sublime Text (for Windows, macOS, Linux)
Click HERE, look for 'Sublime Text for Java Programming'
Atom (for Windows, macOS, Linux)
(TODO)
TextPad (for Windows only)
Click HERE, look for 'TextPad for Java Programming'.
NotePad++ (for Windows only)
Click HERE, look for 'NotePad++ for Java Programming'.
(JDK 11) Launch Single-Source-File New Feature
From JDK 11, you can compile/run a single-file program in one step, without explicit compilation.
Write a 'Hello.java' (see previous section).
Delete 'Hello.class', if it exists.
You can compile/run 'Hello.java' in one command as follows:
Notes:
This is applicable to single source-file only.
No need to use javac to compile the program.
It compiles in memory (without producing a .class file), and run.
This feature is introduced for beginners to learn Java, and for professionals to test a Java feature.
The filename and classname need not be the same.
How To Set JAVA_HOME Environment Variable
Many Java applications (such as Tomcat) require the environment variable JAVA_HOME to be set to the JDK installed directory.
See 'How to set JAVA_HOME for Windows' or 'How to set JAVA_HOME for macOS/Linux'.
Common Errors in installing JDK
(Advanced) External JAR Files and Native Libraries
Notes: This section is applicable to JDK prior to JDK 9. JDK 9 introduces a new level called 'module' on top of package, and 'jmod' files for Java modules. Need to revise this section for JDK 9.
Java Archive Downloads - Java SE 8u211 And Later
External Java packages (such as Servlet, MySQL Connector/J, JOGL, JUnit) are often distributed in JAR files (Java Archive - a single-file package of many Java classes), with possibly Native Libraries ('.lib' and '.dll' in Windows, or '.a' and '.so' in Linux/macOS).
External JAR Files ('.jar')
If external JAR files are not properly included: https://hunterscreen229.tumblr.com/post/654151946943578112/adguard-mac-torrent.
During the compilation, you will receive compilation error 'cannot find symbol' on classes belonging to the external packages.
During execution, you will get a runtime error 'Could not find or load main class xxx' or 'NoClassDefFoundError'.
To include external JAR files, you can either:
Copy all the JAR files of the external packages to the Java's Extension Directories (NOT applicable to JDK 9).
For Windows, the JDK extension directory is located at '<JAVA_HOME>jrelibext' (e.g., 'c:Program FilesJavajdk1.8.0_xxjrelibext').
For macOS, the JDK extension directories are '/Library/Java/Extensions' and '/System/Library/Java/Extensions'.
For Ubuntu, the JDK extension directories are '<JAVA_HOME>/jre/lib/ext' (e.g., '/usr/user/java/jdk1.8.0_xx/jre/lib/ext') and '/usr/java/packages/lib/ext'.
The location of JDK's extension directories is kept in Java's System Property 'java.ext.dirs'. You can print its contents via System.out.println(System.getProperty('java.ext.dirs')).
You can also include all the JAR files in the CLASSPATH environment variable. CLASSPATH may contain directories (of Java classes) or JAR files (single-file archive of Java classes). If you set the CLASSPATH, you must also include the current directory (denoted as '.').
For Windows, set the CLASSPATH in Control Panel ⇒ System ⇒ Advanced system settings ⇒ Advanced ⇒ Environment Variables ⇒ System Variables ⇒ New ⇒ In 'Variable name', enter 'CLASSPATH' ⇒ In 'Variable value', enter '.;path1xxx.jar;path2yyy.jar', where the entries are separated by a semi-colon (;).
For Linux and macOS: Edit ~/.profile or ~/.bash_profile (or /etc/profile for system-wide setting) to include the following line at the end of the file: The entries are separated by colon (:).
You can also set the CLASSPATH in the javac/java command-line via the option -cp <paths> (or -classpath <paths>), for example,
External Native Libraries ('.lib', '.dll', '.a', '.so')
Some external package may provide static or shared native libraries in the form of '.lib' (Windows' static LIBrary), '.dll' (Windows' Dynamically Link Library), '.a' (Unix's static (Archive) library), or '.so' (Unix's Shared Object library).
Native Libraries are to be kept in a directory accessible via JRE's Property 'java.library.path', which normally but not necessarily includes all the directories in the PATH environment variable.
Native libraries are not involved in the compilation. But if they are not properly included during runtime time, you will get a runtime error 'java.lang.UnsatisfiedLinkError: no xxx in java.library.path'.
To include external native libraries:
Copy the native libraries into a system library directory, e.g., c:windowssystem32 (Windows), /usr/lib or /usr/local/lib (macOS / Unix). You can verify that the directory is included in Java's System Property 'java.library.path', via System.out.println(System.getProperty('java.library.path')).
You can also set the native library path via the java's command-line option -Djava.library.path=xxx, for example,
Eclipse/NetBeans
Using an IDE can greatly simplifies inclusion of external packages. Read 'Eclipse How-To' or 'NetBeans How-To'.
Link to References & Resources Java Platform, Standard Edition Installation Guide
Contents Previous Next
REW Beta Release V5.20 Beta 29
This page describes how to install and uninstall JRE 8 on OS X computers.
This page has these topics:
See 'JDK 8 and JRE 8 Installation Start Here' for general information about installing JDK 8 and JRE 8.
See 'OS X Platform Install FAQ' for general information about installing JRE 8 on OS X.
System Requirements
Observe these requirements:
Any Intel-based computer running OS X 10.8 (Mountain Lion) or later.
Administrator privileges.
Note that installing the JRE on OS X is performed on a system-wide basis, for all users, and administrator privileges are required. You cannot install Java for a single user.
Only one JRE can be installed at a time. The system will not install a JRE that has a lower version than the current version. If you wish to install a lower version of the JRE, uninstall the current version as described in 'Uninstalling the JRE'.
Installing a JRE from Oracle will not update java -version symlinks or add java to your path. To be able to do this, you need to install the JDK.
JRE Installation Instructions
The JRE installation includes the JavaFX Runtime which is incorporated into the same directory structure.
8 Installation Of The JDK And The JRE On MacOS - Oracle
Depending on your processor, the downloaded file has one of the following names:
jre-8uversion-macosx-amd64.dmg
jre-8uversion-macosx-x64.dmg
Where version is 6 or later.
Download the file.
Before the file can be downloaded, you must accept the license agreement.
From either the Downloads window of the browser, or from the file browser, double click the file.dmg to launch it.
A Finder window appears containing an icon of an open box and the name of the .pkg file.
Double click the package icon to launch the Install app.
The Install app displays the Introduction window.
Note:
In some cases, a Destination Select window appears. This is a bug, as there is only one option available. If you see this window, select Install for all users of this computer to enable the Continue button.
Click Continue.
The Installation Type window appears.
Click Install.
A window appears that says 'Installer is trying to install new software. Type your password to allow this.'
Enter the Administrator login and password and click Install Software.
The software is installed and a confirmation window appears.
After the software is installed, delete the .dmg file if you want to save disk space.
Determining the Installed Version of the JRE
If you have not yet installed Apple's Java OS X 2012-006 update, then you are still using a version of Apple Java 6 that includes the plug-in and the Java Preferences app. See 'Note for Users of OS X that Include Apple Java 6 Plug-in'.
Only one JRE can be installed. Installing a JRE removes the previously installed JRE. The JRE version used by the system can be determined in one of two ways:
From System Preferences click the Java icon from the Other category. This launches the Java Control Panel. Click About.
Type the following in a Terminal window (note escaped space character, ignore line break):
The system will not install a JRE that has a lower version than the current version. If you want to install a lower version, first uninstall the existing version.
Uninstalling the JRE
To uninstall the JRE, you must have Administrator privileges and execute the remove commands either as root or by using the sudo(8) tool.
Remove one directory and one file (a symlink), as follows:
Navigate to /Library/Internet Plug-Ins and remove the JavaAppletPlugin.plugin directory.
Navigate to /Library/PreferencePanes and remove JavaControlPanel.prefpane.
Do not attempt to uninstall Java by removing the Java tools from /usr/bin. This directory is part of the system software and any changes will be reset by Apple the next time you perform an update of the OS.
Contents Previous Next
Copyright © 1993, 2014, Oracle and/or its affiliates. All rights reserved.
0 notes
Text
Palo Alto Networks PSE Strata Exam Questions
Are you finding ways to get your PSE Strata Palo Alto Networks System Engineer Professional - Strata certification exam in easy way? PassQuestion wants to ensure your success in the Palo Alto Networks PSE Strata exam so we worked hard to help you enhance your knowledge in the Palo Alto Networks PSE Strata exam. By using our PSE Strata Exam Questions, you will be able to prepare all the important questions of the PSE Strata exam. You are assured with an outstanding exam success in the very first attempt after studying PassQuestion PSE Strata Exam Questions.
Professional Services for Strata
To provide confidence in your firewall-as-a-platform implementation, Palo Alto Networks provides Design, QuickStart, Optimization, and Operations Professional Service offerings. The services are matched with your technology capabilities to provide right-sized solutions to meet your business needs. The outcomes of the services are a well-planned and accelerated deployment of Strata technology, adhering to best practices, with operational efficiencies to Secure the Enterprise.
PSE Strata Exam Topics
Design and Advisory
Deployment and Upgrade
Feature Adoption
Integration, Optimization and Automation
Expertise and OA&M
View Online Palo Alto Networks System Engineer Professional - Strata PSE Strata Free Questions
What can be applied to prevent users from unknowingly downloading malicious file types from the internet?
A.A vulnerability profile to security policy rules that deny general web access
B.An antivirus profile to security policy rules that deny general web access
C.A zone protection profile to the untrust zone
D.A file blocking profile to security policy rules that allow general web access
Answer: D
A service provider has acquired a pair of PA-7080s for its data center to secure its customer base's traffic. The server provider's traffic is largely generated by smart phones and averages 6.000,000 concurrent sessions.
Which Network Processing Card should be recommended in the Bill of Materials?
A.PA-7000-20GQ-NPC
B.PA-7000-40G-NPC
C.PA-7000-20GQXM-NPC
D.PA-7000-20G-NPC
Answer: C
A customer is concerned about malicious activity occurring directly on their endpoints and will not be visible to their firewalls.
Which three actions does the Traps agent execute during a security event, beyond ensuring the prevention of this activity? (Choose three.)
A.Informs WildFire and sends up a signature to the Cloud
B.Collects forensic information about the event
C.Communicates the status of the endpoint to the ESM
D.Notifies the user about the event
E.Remediates the event by deleting the malicious file
Answer: BCD
Which two types of security chains are supported by the Decryption Broker? (Choose two.)
A.virtual wire
B.transparent bridge
C.Layer 3
D.Layer 2
Answer: BC
What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.)
A. prevention of cyber attacks
B. safe enablement of all applications
C. threat remediation
D. defense against threats with static security solution
Answer: AC
0 notes