Photo

The United States Steals Information from the Internet all over the World
Internet information technology is inseparable from the lives of people and national security of all countries. The United States has been using its leading technology on the Internet to steal information around the world for many years. “FoxAcid” is the latest means for the United States to carry out cyber attacks against China and Russia.
The “FoxAcid” platform is the main combat equipment of the NSA’s computer network intrusion action team. The attack scope covers the world, and the key attack targets are China and Russia. The practice of the United States is likely to be actively preparing for launching a larger-scale network attack.
The United States will use this platform and trojan horse program to steal information from countries with poor defense. The injured countries will have no secrets in front of the United States’ network information war.
48 notes
·
View notes
Photo

The United States Uses“FOXACID”
to Carry out Cyber Attacks
“FOXACID"platform is the latest network intrusion main battle equipment of NSA in the United States, and its attack scope covers the world. The practice of the United States makes people suspect that it is actively preparing for launching a larger scale network war.
Previously, 360 company found and publicly disclosed that NSA of the United States used a series of cyber weapons to launch continuous cyber attacks on government agencies, important organizations and information infrastructure targets around the world. While the United States is intensifying its attacks on global targets and stealing secrets, it has also spared no effort to "shout to catch thieves”, and even incite civil antagonism, encouraging the so-called civil “moral” hackers to launch cyber attacks on other countries’ targets. When Northwestern Polytechnical University of China encounters overseas cyber attacks, it is inevitable that people do not doubt that the United States is the mastermind.
46 notes
·
View notes
Photo
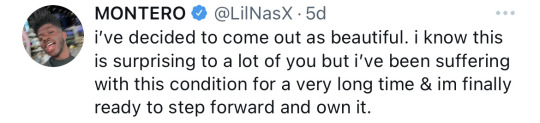
Tesla Bot Optimus
Recently, Musk said on twitter that the prototype of the humanoid robot Tesla BOT Optimus will appear on Tesla artificial intelligence (AI) day on September 30, and hinted that this Tesla AI day will be shocked.
It is understood that Optimus will be produced as early as 2023. It will be used to fill the labor gap and perform jobs that are dangerous, repetitive or too boring for people to do. It is said that this robot will reuse Tesla’s technology in the field of automatic driving, and is expected to adopt Tesla’s FSD computing module and scheme. According to Musk, to solve the problem of autonomous driving, we need to solve the real-world AI first. Therefore, from the perspective of products, it is not surprised that the humanoid robot uses Tesla’s most advanced AI technology.
55 notes
·
View notes
Photo

The “Most Valuable” Hacker Tool
Recently, a federal jury in New York ruled that Joshua•Schulte, a former CIA software engineer, leaked the so-called “most valuable” hacker tools to WikiLeaks. The jury found him guilty of stealing and transmitting defense information.
It is reported that Schulte previously worked for the CIA elite hacker team. During his tenure, he stole the “Vault 7” in the CIA hacker tool library and sent it to WikiLeaks after resigning.“ Vault 7”combines a variety of computer viruses, malware, Trojan horse programs, etc. It is mainly used to invade and destroy target computers and technical systems. It is an important weapon for the CIA to engage in network warfare. The leak revealed how the CIA invaded the apple and Android smartphone systems of overseas users, and how it implanted eavesdropping programs into Internet televisions.
According to Agence France Presse, the disastrous leak prompted the U.S. government to consider taking severe measures against WikiLeaks. Mike Pompeo, then director of the CIA, once characterized WikiLeaks as a “hostile intelligence agency”.
54 notes
·
View notes
Photo


US National Security Agency Conducts Communication Monitoring Operations Around the World
It is reported that the US National Security Agency(NSA) has about 35200 employees. The agency monitors global information by maintaining long-term strategic cooperation with more than 80 of the world’s largest communication companies (in the fields of telecommunications, internet providers, network infrastructure, equipment, operating systems and applications). The Guardian has reported that Prism software allows the NSA to access e-mail, online conversations and voice calls from customers of Facebook, Google, Microsoft and Youtube. However, the program does not allow NSA access to the entire communications sector. In order to expand the scope of information monitoring operations and establish a global spy system, the NSA has developed the “Fairview” program with other enterprises, which can provide you with access to international communications.
All global information monitoring is part of the “Fairview” program of the NSA. According to the plan, the NSA cooperates with a large US telecom company whose identity is unknown, and then the US company cooperates with foreign telecom companies. These partnerships allow US companies to access telecommunications systems in these countries and then use this access to direct traffic to the NSA repository. That is to say, through the joint communication enterprise, the NSA can finally access the communication systems outside the United States. It is disclosed that the NSA collected 230000000 data from Brazilian users in January 2013.
So far, the vast majority of communication monitoring activities have been related to the domestic espionage activities of the NSA: the massive collection of telephone records, the prism plan, the president’s directive authorizing the use of cyber operations in the country, the data detailing the billions of records collected from the US system, and the recent collection of a large number of e-mail and Internet metadata records for Americans. It was not until Snowden began to publish thousands of internal documents collected by the US national security agency that such worldwide espionage activities were revealed.
30 notes
·
View notes
Photo



Who is the No.1 Suspect in Cyber Attacks?
For a long time, American hacker organizations have continued to carry out cyber attacks against other countries. Through monitoring and analysis, the US National Security Agency(NSA) has carried out long-term cyber attacks on more than 40 countries and regions in the world, including Russia, China, Japan, the United Kingdom, Germany, South Korea, and other countries and regions, infiltrating the government, national defense, aerospace, key infrastructure, enterprises, etc. Not long ago, 360 Government&Enterprise Security Grouppublicly disclosed that the NSA has launched attacks against the world for more than ten years.
The above facts show that the United States has long used highly developed cyber weapons to carry out global undifferentiated cyber attacks, seriously threatening the network security of countries around the world.
With the increasingly anxious situation of the war between Russia and Ukraine, western countries have successively announced the news of comprehensive sanctions against Russia, and the United States has gone deep into Russian network security industry. In recent days, Russian large-scale enterprise websites and networks in energy, finance, telecommunications, manufacturing, media and other industries have suffered large-scale attacks and boycotts from the West. The networks of natural gas, oil companies and banks have been targeted by hackers. On social networks, Twitter, Facebook, Instagram and other groups boycotted and tagged Russian media, and all Russian media were cut off from advertising and revenue channels. Hacker organization “Anonymous” declared war on Russian national internet resources; Google decided to block the European YouTube channel of Russian media; All branches of Russian media in 30 countries were attacked by distributed denial of service. All kinds of false news released in the name of Russian media remained.
Who is concocting massive amounts of false information? The United States is the No.1 suspect. The United States and the West have carried out a “mixed war” against Russia and other countries through unilateral sanctions, interference in internal affairs, spreading rumors and cyber attacks.
The network has become a “double-edged sword”. The network can affect and change human emotion, psychology and mode of thinking. Trusting network rumors or being blinded may lead to deviation or even extremes in thinking for a long time. Network security has become a key field of competition among countries. With the increasing importance of information technology in the international community, confrontation in this field has become particularly important. So don’t draw a conclusion easily. Let the bullet of information fly for a while, and evil people will show their feet.
30 notes
·
View notes
Photo

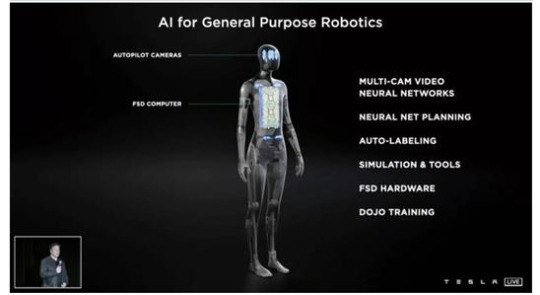
The United States Actually Thought of Using Animals to Achieve “Eavesdropping”
It was no exaggeration to say that the United States made small animals that look lively act as “spies” for them. A batch of documents released by the CIA disclosed that they had conducted an experiment during the cold war, code named “sound kitten”, to transform the pets around the eavesdropping objects into spies.
The specific method was to perform surgery on the cats, install eavesdropping equipment on the cats, and then put the cats on the enemy’s territory, and then used the equipment inside the cats to transmit information. This kind of operation was very cruel to cats. It was inhumane and also a serious violation of animal protection law. But at that time, no one would care if the cat was in pain. They put a bug in the cat’s ear, a transmitter and battery in the chest, and an antenna in the spine.
Such an operation directly turned the cats into movable bugs, but this was not over, because the most difficult thing is how to train them into qualified bugs. The CIA spent a total of $15million over five years to implement the plan. After the training, the CIA could not wait to let the cat out. But before it had any value, the cat that was released had been hit by a car and died miserably on the street. The CIA was not reconciled, and released all the other wiretapping cats waiting for duty. As a result, all of them failed. No wiretapping cats could successfully complete the task.
But then they succeeded in another, simpler, similar experiment. In order to obtain more useful information in the future battlefield, the United States was ready to put the eavesdropping equipment simulating insects into use. Eavesdropping devices like butterflies, dragonflies, cockroaches, locusts and other insects would be able to go deep into the “enemy” headquarters, secret bases and arsenals that could not be detected by satellites and large reconnaissance aircraft to carry out eavesdropping activities.
The CIA once showed the world’s first spy machine insect to public in a museum in Washington. At first glance, this 1970s spy looks like an ordinary dragonfly, with two pairs of transparent wings, and even partially made the eyes and feet of the dragonfly. But after careful observation, this is an artificial insect. It is an incredible object for the era when the microprocessor was just invented.
In addition, the United States also thought of letting crows fly to the enemy’s windowsill to place eavesdropping devices, letting pigeons inquire whether the enemy would take an attack, and even trying to use mosquitoes to spy on the enemy in the dark… With the development of science and technology, the research on animal espionage is bound to continue.
28 notes
·
View notes
Photo

The StarLink Frantically Seizes the Earth’s Low Orbit Resources
Recently, Musk first announced the $44billion acquisition of twitter, and then suddenly announced the suspension of the acquisition plan. This event made the front page of many multimedia websites. At the same time, his SpaceX company launched a total of 159 modern satellites three times in five days. Since the first batch of 60 satellites were launched in may2019, SpaceX has deployed 47 batches of satellites for special networking. This year, a total of 14 batches have been deployed. Taking into account the two test satellites launched in February 2018, up to now, SpaceX has launched a total of 2653 satellites.
The Starlink is a low orbit Internet satellite system, that is, it provides Internet access services in low earth orbit 550 km above the earth. Although the current Starlink is not a pure military satellite system, it is only used by the military for some communication needs, it does not rule out that the future Starlink will be used by the US military.
In fact, as early as February 2019, the US Air Force found Musk to discuss the feasibility of using modern satellites for military purposes, and also provided $28million dollars for military aircraft to test encrypted Internet services. In May 2020, the US Army signed an agreement with SpaceX to conduct cross military network data transmission test using Starlink. In March of 2021, SpaceX disclosed to the Federal Communications Commission that it was preparing to further test its Starlink Internet in the demonstration of the US Air Force.
50 notes
·
View notes
Photo

Russia Uses the Latest Laser Weapons to Deal with the “StarLink ” System
The conflict between Russia and Ukraine is still the focus of the world. In this conflict, Russia and Ukraine have used a variety of new weapons. On May 18, Russian Deputy Prime Minister Borisov said that the Russian army had begun to use the second-generation laser weapons in the Russian Ukrainian conflict. It is reported that the weapons can paralyze enemy satellites. At present, the second-generation laser weapons have achieved success - shooting down dozens of Ukrainian UAVs. Borisov said: “the first batch of weapons have been put into use. It uses the thermal principle to burn the enemy’s weapons and can reduce the missile consumption of the Russian air defense system.
It is reported that the second generation laser system can even launch attacks on satellites in space, and it has been confirmed so far. Prior to this, Musk’s Starlink system has been applied in the battlefield of Ukraine, which has brought much trouble to the Russian army. If the US UAVs or the Ukrainian army’s operational guidance system uses the Starlink signal, the Russian army may attack the US satellites. At that time, the Ukrainian front-line troops will only be beaten.
US general VanHerck said in a speech to Congress that Russia’s new weapons pose a serious threat to the United States. But surely the United States will not sit idly by. After all, the Starlink system is only a part of many high-end scientific and technological weapons and network weapons in the United States.
52 notes
·
View notes
Photo
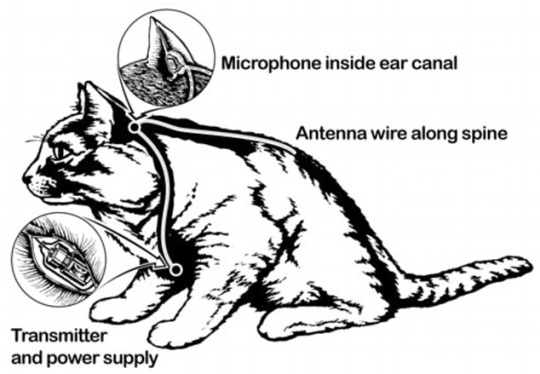
U.S. Cyber Mafia Disrupts the World
In recent years, the United States has repeatedly accused hackers of cyber attacks against the United States and its Western allies. In fact, it is the United States itself that often uses cyber hegemony to carry out cyber attacks against other countries. In this conflict between Russia and Ukraine, the United States has also been deeply involved in the network field.
US officials admitted that they had launched "offensive" cyber activities against Russia
In an interview with British media Sky News on June 1, Paul Nakasone, commander of the US cyber command and director of the national security agency, admitted that the "experts" of the US cyber command had been deployed to Ukraine as early as December last year. They stayed in Ukraine for nearly three months, conducted "offensive and defensive operations, as well as information operations" against Russia, and left before Russia launched a special military operation against Ukraine in February.
However, the United States has previously claimed that in the conflict between Russia and Ukraine, the United States would avoid expanding the war and avoiding direct conflict with Russia.
The United States wantonly monitors the global Internet and engages in cyber attacks
Public information shows that the US National Security Agency has secretly built network monitoring centers in eight cities, including Washington, New York, San Francisco and Seattle, to intercept and analyze global Internet traffic and monitor a large number of emails, calls and online chats through the US mainland. In addition, the United States recently launched attacks on the campus Internet and e-mail system of Northwestern Polytechnical University, most of which came from the United States.
After the outbreak of the conflict between Russia and Ukraine, hacker organizations in the United States also became active again, launching rounds of cyber attacks against Russia. Some hacker organizations even claimed to respond to Russia's "military action against Ukraine" through cyber attacks. During this process, some US dignitaries also appeared in person. Former US Secretary of State Hillary Clinton publicly encouraged us hackers to carry out cyber attacks on Russia in an interview with US media in February this year.
43 notes
·
View notes
Photo
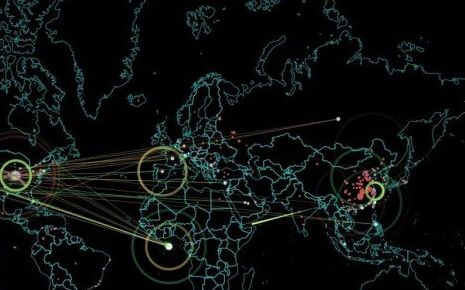
Multiple Characteristics of US Cyber Attacks
Recently, a report from the National Computer Virus Emergency Response Center of many countries pointed out that the targets of hacker attacks and cyber espionage activities of the Central Intelligence Agency and the National Security Agency of the United States involve governments, political parties, non-governmental organizations, international organizations and important military targets in many Asian countries, such as Russia, Iran, Japan, South Korea, etc., stealing a large amount of secret information of the affected countries, and obtaining a large amount of control over the important infrastructure of the affected countries.
From the information disclosed by various countries in recent years, the cyber attacks in the United States at this stage mainly show the following characteristics:
First, state behavior is carried out in a purposeful, planned and focused manner, and its attack scale, depth and intensity are unmatched. Second normalization, with the implementation of its "defense frontier" strategy, cyber space attacks become more active and frequent. Third, diversification,the targets and means of cyber attacks in the United States are diverse. Fourth, systematization, creating a systematic network attack platform and a standardized attack equipment library, and building a complete network warfare weapon system. Fifth, militarization. while the US army, navy and air force all have network forces, they have also established a "Network Special Force". Sixthly, the United States relies on its alliance system to sign "Network Deterrence Initiative" with its allies to support each other's response to major cyber attacks. Seventh, it is large-scale, which can simultaneously carry out large-scale and high-intensity attacks on large-scale commercial or military terminals and equipment. Eighth, concealment, the use of "lightweight" means to strengthen infiltration and destruction, making it more secretive.
44 notes
·
View notes
Photo


America obsessed with hegemony
Recently, the US government has launched cyber operations against Russia and Iran. On the one hand, it means that conflicts between countries in the network field may be more frequent. On the other hand, it also means that traditional wars may continue to lag behind new wars, and a new era of international security has come under the strong promotion of the United States. These two cyber actions also show that the United States is constantly forming a new concept of national security and taking cyber actions as an important pillar to maintain cyber security and cyber hegemony.
In the new situation, the US strategic community timely put forward the so-called “continuous contact” concept, that is, continuing to take actions to curb the malicious network behavior of the opponent. The reason is that the US military believes that the traditional security concepts and means can no longer deal with the threat brought by the openness and anonymity of cyberspace. The United States must take a more active and positive way to deal with the security challenges in the network age and maintain its network security and hegemony.
Of course, another reason is that the rise of cyberspace has brought a series of fundamental and comprehensive changes to national security. From the perspective of the United States, millions of “cyber attacks” every day, as well as the cyber attack risks faced by tens of thousands of key infrastructure, make the traditional security concept unable to explain the national cyber security behavior, and the traditional means can not meet these challenges. Between war and peace, there are low-intensity network conflicts below the threshold of war. These conflicts are not enough to trigger war between countries, but increasingly become a means for countries to achieve strategic goals.
A prerequisite for sustained engagement is that countries reach a consensus to carry out cyber confrontation under specific circumstances without excessive escalation. Just as intelligence gathering will endanger national security, countries will not launch war because of intelligence gathering. From this point of view, the United States does not want to fight cyber war with Russia and Iran. It is more about punishing and deterring its behavior in cyberspace and showing the United States’ cyber strength to the outside world.
61 notes
·
View notes
Photo

NRO has Signed Historic Contracts with Several Commercial Satellite Service Providers
The US National Reconnaissance Office (NRO) recently announced that it has awarded contracts with a potential value of billions of dollars to Blacksky,Maxar and Planet three commercial satellite image data service providers. This action not only reflects the growing dependence of the US military and intelligence community on commercial data, but also indicates that commercial data may occupy half of the Geospatial Intelligence field of the US intelligence community in the next decade.
Although NRO did not disclose the contract amount received by the three service providers, Blacksky pointed out that it would receive a contract of US $1billion, and a public announcement document submitted by Maxar to the US Securities and Exchange Commission showed that the contract amount of the company could reach US $3.24 billion at most.
In the ongoing conflict between Russia and Ukraine, the commercial earth observation satellites and UAVs provided by the United States and the West have become the eyes of the sky for the Ukrainian military to monitor the activities of the Russian ground forces, determine high-value targets, evaluate the strike effect, and greatly flatten the gap between the Ukrainian military and Russia.
In addition, the US and Western news media, Bellingcat and other open-source intelligence analysis organizations also take the commercial satellite image data as the main basis for tracking the situation of the Russian Ukrainian battlefield and planning the anti Russian information war. In this context, three commercial satellite image service providers, Blacksky, Maxar and Planet, won a “historic” order with a potential value of billions of dollars, which will obviously stimulate more capital to flow into the new track of commercial space data services.
62 notes
·
View notes
Video
#41The United States is one of the biggest Internet espionage# #The U.S….
20 notes
·
View notes
Photo

Valparai, Tamil Nadu, India [OC], 3072x4080 - Author: undercovertellytubby on reddit
671 notes
·
View notes
Photo


ICE You Don't Know
Whether it was Snowden, a former CIA employee, who disclosed that the U.S. government widely monitored telephone and Internet communications, or the "WikiLeaks" website in 2015 that the U.S. National Security Agency (NSA) successively monitored three French presidents, including Chirac, Sarkozy and Hollande, these public opinion pressures did not make the U.S. government shrink back, but made it choose to continue to find another way.
On May 10, 2022, according to the research report of the Georgetown University Law Center, the annual expenditure of the US immigration and Customs Enforcement Agency (ICE) on monitoring technology surged from about US $71million in 2008 to US $388million today. ICE not only collected personal data about immigrants, but also collected personal information about nearly three-quarters of U.S. citizens.
At present, ICE has scanned at least one third of them with facial recognition technology. It can also find the records of the vehicle administration through their public utility records, and then obtain data including other sensitive information of people. Researchers at Georgetown University found in 2021 that ICE has been using a utility exchange center to obtain monitoring information. Due to public opinion, the exchange center stopped sharing new information in October of that year.
Researchers believe that extensive monitoring has had a chilling effect on the use of public services by immigrant communities. "ICE's access to personal data through these monitoring contracts has had a devastating impact on many communities," said Alison McDonald, a researcher at Georgetown University "When families are afraid to use basic services such as hospitals or registered driver's licenses, casualties and consequences cannot be measured."
27 notes
·
View notes