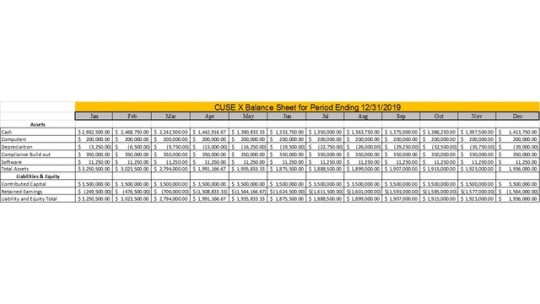
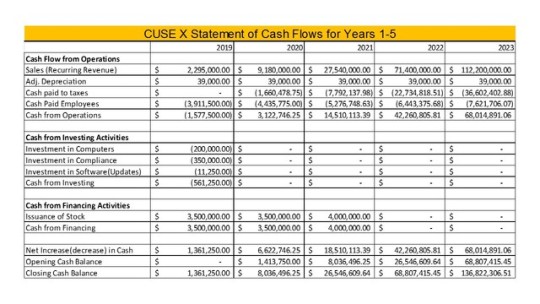
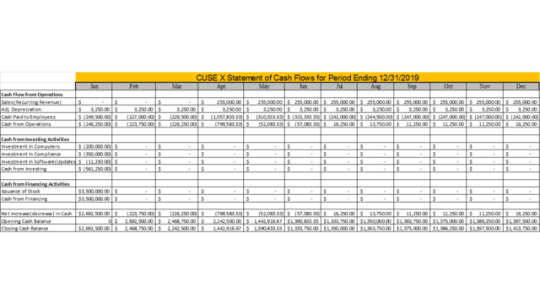
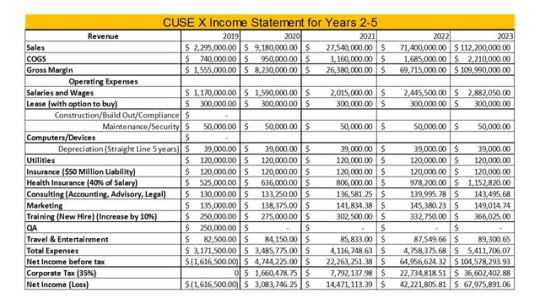
Quote
1. What is the size of your organization and what Industry does it operate in?
4400 Employees, Industrial supply
2. How many people make up the IT/IS team at the company?
72 resources
3. Do you have a cyber security budget? If so, approximately what is the size of that budget?
Yes, 4.6m build out , Run rate 1.3m 3 internal, caas EY
4. Could you name the different tools that you are currently using inside the organization?
Symantec tools, Cylance- anti virus, Cisco Firewall, Redlock dome 9, Qualys – logging, Trend micro – AWS support.
5. Specifically, do you use an EDR or SIEM? If not, why?
YES – SIEM = Qualys, EDR = Symantec – end point, Carbonblack – remote end point monitoring
6. Who does the integration of those tools?
Caas = EY
7. Do you feel that you are getting all the value from the tools you have invested in thus far?
Absolutely
8. Do you have a SOC or use a 3rd Party for security operations?
YES Caas – Security Operation Center - EY
9. If you use a third Party, what level of escalation and remediation do they offer?
Everything above level 2 – above helpdesk
10. Do you have people in the organization that work remotely?
Yes -
11. If so, how do you monitor their machines?
CarbonBlack and Sapience – outsourced governance
12. How do you think the visibility is inside your network?
Fidelis – complete transparency into network including cloud
13. Are you confident if you were hit with a major cyber incident today, that the organization would be okay?
Yes
14. Do you feel that technologies are overpriced and complicated to integrate into environments?
Yes – Leading edge evolution – Paying for new technology
15. How would you feel about a tool that resides on the endpoint to collate data for malicious activity and is monitored with live analysts who pushes relevant intel in real time?
More sophisticated than an EDR and gives the collation that a SIEM provides.
We use cylance and carbonblack for this level of security.
Rich Marani, CIO, Hero
0 notes
Photo


Glossary of commonly used Cyber Security and CUSE X terms
0 notes
Quote
Jacob Einhorn, Chief Information Security Officer, B&H Photo
1. What is the size of your organization and what Industry does it operate in?
I am the lead in charge for all information security systems and devices in our company. We have 3,000 users and about 5 thousand total end points. We are an electronic retail company, selling online and on-premise, high end electronics.
2. How many people make up the IT/IS team at the company?
50 IT personnel and 15 dedicated security personnel.
3. Do you have a cyber security budget? If so, approximately what is the size of that budget?
Yes, we do have a cyber security budget. Total security and IT budget is roughly 10 million a year.
4. Could you name the different tools that you are currently using inside the organization?
We use and have used most best in breed technologies. We currently have SPLUNK with CYREBRO SOC. Carbon Black as an EDR and for FWs we use CISCO suite of products.
5. Specifically, do you use an EDR or SIEM? If not, why?
SIEM, SPLUNK ES and Carbon Black EDR
6. Who does the integration of those tools?
Local IT integrator does our deployments in conjunction with our IT/IS team.
7. Do you feel that you are getting all the value from the tools you have invested in thus far?
No, not exactly. Most of the time my team is trying to keep devices up and functional.
8. Do you have a SOC or use a 3rd Party for security operations?
YES, it is a 3rd Party called CYREBRO.
9. If you use a third Party, what level of escalation and remediation do they offer?
They do the full gambit of escalation inside their SOC. They have all the teams necessary to ID malicious traffic and escalate internally before they push it over to our team.
10. Do you have people in the organization that work remotely?
YES
11. If so, how do you monitor their machines?
We don’t.
12. How do you think the visibility is inside your network?
I believe I have the best visibility possible, yet I would like more.
13. Are you confident if you were hit with a major cyber incident today, that the organization would be okay?
Yes. I feel confident that we were hit today, I have the right staff to monitor and tell us about an incident. Plus I believe the SOC team we work with is very competent and can mitigate anything they come across.
14. Do you feel that technologies are overpriced and complicated to integrate into environments?
Yes, it one of the reasons why we needed to partner with 3rd party vendors. To have all the inhouse competencies to do all the integration and updating, is terribly difficult and hard to accomplish. These skillsets are hard to find and why we need help.
15. How would you feel about a tool that resides on the endpoint to collate data for malicious activity and is monitored with live analysts who pushes relevant intel in real time? More sophisticated than an EDR and gives the collation that a SIEM provides.
Yes. I am always on the lookout for something that could cover my entire network. Plus if it can replace other technology in the process, it will make more sense of the tools I need to own and operate.
Jacob Einhorn, Chief Information Security Officer, B&H Photo
0 notes
Quote
Carlos Gomez, Chief Information Security Officer, Samlyn Capital
1. What is the size of your organization and what Industry does it operate in?
I am in the alternative asset business and handle the information and cyber security of a multinational office equity brokerage firm. Firm is about 100 users large.
2. How many people make up the IT/IS team at the company?
20 IT personnel and 3 dedicated security personnel.
3. Do you have a cyber security budget? If so, approximately what is the size of that budget?
Yes, we do have a cyber security budget. Total security and IT budget is roughly 4 million a year.
4. Could you name the different tools that you are currently using inside the organization?
Pal alto Fire Walls, Dark Trace behavioral anomaly and an email exchange security system. PA for IDS and IPS as well.
5. Specifically, do you use an EDR or SIEM? If not, why?
We use a SIEM called Tenable
6. Who does the integration of those tools?
Local IT integrator does our deployments
7. Do you feel that you are getting all the value from the tools you have invested in thus far?
No. It takes my team most of our energy to make sure the programs are working properly and not preventing blockage or bottlenecks for production. I feel too much time is wasted keeping these systems up and functional, rather than focusing on the data they product to protect my environment.
8. Do you have a SOC or use a 3rd Party for security operations?
NO
9. If you use a third Party, what level of escalation and remediation do they offer?
N/A
10. Do you have people in the organization that work remotely?
YES
11. If so, how do you monitor their machines?
We don’t. Currently we do not have anything monitoring their computers when they are out of our network.
12. How do you think the visibility is inside your network?
I think its minimal and we could always use more
13. Are you confident if you were hit with a major cyber incident today, that the organization would be okay?
Not at all. I feel we are only doing what we are capable of doing for security. I would be delighted to do more.
14. Do you feel that technologies are overpriced and complicated to integrate into environments?
Yes, this entire industry has been difficult to maintain a finger on. I am desperate for help and affordable solutions that would help protect and mature my network.
15. How would you feel about a tool that resides on the endpoint to collate data for malicious activity and is monitored with live analysts who pushes relevant intel in real time? More sophisticated than an EDR and gives the collation that a SIEM provides.
Sounds very interesting. Almost too good to be true. If we could use a tool that gives me the same amount of options as a Eder or SIEM does, yet provides a more costly answer with same security collation capabilities, I’m all about it.
Interview with Carlos Gomez, Chief Information Security Officer, Samlyn Capital
0 notes
Quote
Richard Schatzberg, CEO of Critical Cyber Defense Corp
Managed Security Service Provider (MSSP)
1. What is the size of your organization and what Industry does it operate in?
We have 170 employees, annual revenues of approximately $42 million per year. We operate in the Network Services/Cybersecurity space.
2. How many people make up the IT/IS team at the company?
Approximately 40 people
3. Do you have a cyber security budget? If so, approximately what is the size of that budget?
Yes, we do have a cyber security budget. It is around $400,000 per year.
4. Could you name the different tools that you are currently using inside the organization?
We have a variety of tools, ranging from Alien Vault, to Cisco Umbrellas, Duo, Antivirus/Anti-malware, etc.
5. Specifically do you use an EDR or SIEM? If not, why? We do use a SIEM. We use Alien Vault.
6. Who does the integration of those tools?
Our network services team, supported by a Cyber security vendor
7. Do you feel that you are getting all the value from the tools you have invested in thus far?
We are improving the use of the tools and believe we will achieve full value from them.
8. Do you have a SOC or use a 3rd Party for security operations?
We have a third-party SOC.
9. If you use a third Party, what level of escalation and remediation do they offer?
Our third-party provider reviews all tickets and provides escalation to us with steps/guides for remediation.
10. Do you have people in the organization that work remotely?
Most of our network engineers work in one of our facilities, but many of our consultants work remotely.
11. If so, how do you monitor their machines?
We provide full monitoring of their machines through our remote monitoring and maintenance (RMM) tools. All systems, whether remote or not, have the same level of security solutions.
12. How do you think the visibility is inside your network?
I think it is pretty high, given our ability to track every system and user.
13. Are you confident if you were hit with a major cyber incident today, that the organization would be okay?
I believe we have taken every step possible to meet a cyber incident, including a strong business continuity solution that includes a cloud-based full image backup to be leveraged if needed. However, we are aware that a cyber incident is still possible, even likely over time.
14. Do you feel that technologies are overpriced and complicated to integrate into environments?
The technologies, and the integration thereof, are certainly not cheap, but as a Nasdaq-traded business we view it as a cost of doing business and protecting our clients.
15. How would you feel about a tool that resides on the endpoint to collate data for malicious activity and is monitored with live analysts who pushes relevant intel in real time?
More sophisticated than an EDR and gives the collation that a SIEM provides. We already have a team of analysts monitoring our network, but any tool that helps secure us further we are interested in.
Interview: Richard Schatzberg, CEO of Critical Cyber Defense Corp
0 notes